Big data security threat processing method and system based on smart service
A threat processing and big data technology, applied in the fields of electronic digital data processing, digital data protection, computer security devices, etc., can solve the problems of increasing the risk of data leakage and the difficulty of data security protection for smart business activities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
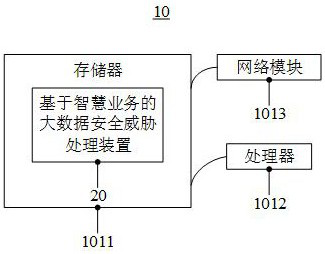
[0030] figure 1 A block diagram of a large data security threat processing system 10 provided in the present application embodiment is shown. The large data security threat processing system 10 in the present application embodiment can be a server having data storage, transmission, processing, such as figure 1 As shown, the big data security threat processing system 10 includes: memory 1011, processor 1012, network module 1013, and artificial intelligence new media resource processing device 20.
[0031] The memory 1011, the processor 1012, and the network module 1013 are electrically connected directly or indirectly to achieve transmission or interaction of data. For example, these elements can be electrically connected to each other by one or more communication bus or signal lines. The memory 1011 stores a new media resource processing apparatus 20 based on artificial intelligence, which includes at least one software function that can be stored in the memory 1011 in the form o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com