Method and system for accessing big data system
A big data and access request technology, applied in the field of big data security, can solve problems such as hidden dangers of big data systems, and achieve the effects of improving security, facilitating unified management, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
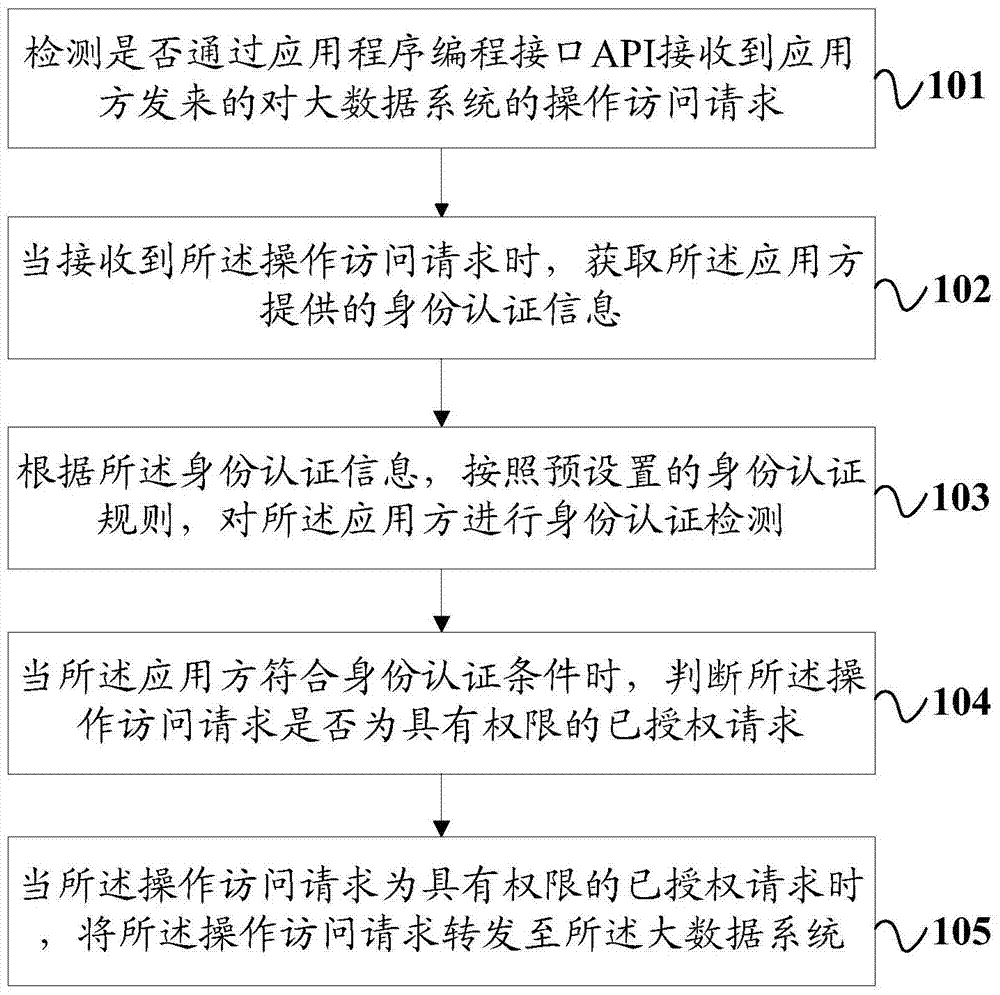
[0074] Such as figure 1 As shown, the present invention discloses a method of accessing a big data system, the method comprising:
[0075] Step 101: Detect whether an operation access request to the big data system from the application side is received through the application programming interface API.
[0076] Specifically, the application party may be an application object of a big data system including users, system application programs, and the like.
[0077] Step 102: When the operation access request is received, obtain the identity authentication information provided by the application side.
[0078] Step 103: According to the identity authentication information, perform an identity authentication test on the application party according to a preset identity authentication rule.
[0079] Step 104: When the application meets the identity authentication conditions, determine whether the operation access request is an authorized request with authority.
[0080] Step 105:...
no. 2 example
[0084] In order to make the technical solution of the present invention more perfect, this embodiment will describe a preferred embodiment of the implementation process of the method for accessing the big data system in the first embodiment on the basis of the first embodiment.
[0085] Here, when the application party does not meet the identity authentication conditions, or when the operation access request is an unauthorized request without permission, a reminder message can also be sent to the application party through the API.
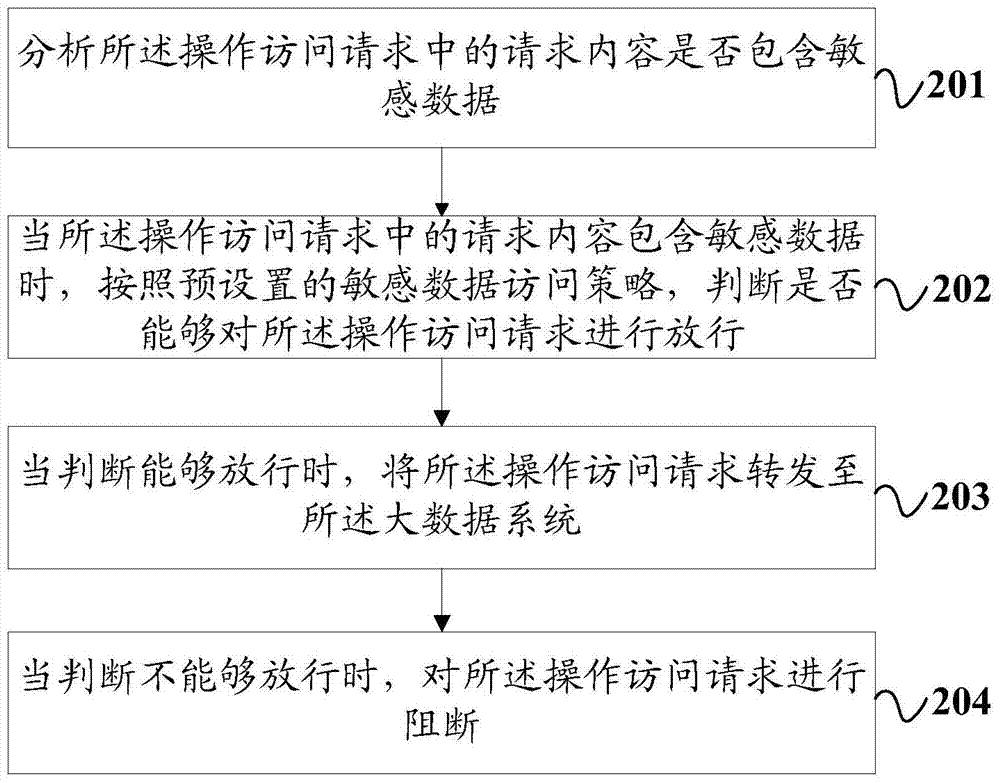
[0086] Further, as figure 2 As shown, based on the first embodiment, before the operation access request is forwarded to the big data system in step 104, the method also includes judging the request content in the operation access request sent by the application side, and the specific steps include:
[0087] Step 201: Analyzing whether the request content in the operation access request contains sensitive data.
[0088] Specifically, the sensitiv...
no. 3 example
[0115] Specifically, in this embodiment, the specific composition and structure of the agent platform formed in the previous two embodiments will be described in detail.
[0116] Such as Figure 5 , Figure 6 , Figure 7 , Figure 8 As shown, the scheme has constructed a proxy layer based on the big data system as a whole. The application interface API of the proxy layer is called by the application side. After the API of the proxy layer receives the operation and access request from the application side, the proxy platform The functions include identity authentication, access control, data security protection, operation records, etc. for the application side; the authentication of the application side can be carried out through the authentication center, specifically based on the network authentication protocol Kerberos to realize the unified authentication of the application side's access to the big data platform ,sign in. Administrators, analysts, and maintainers of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com