Patents
Literature
539 results about "Application object" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
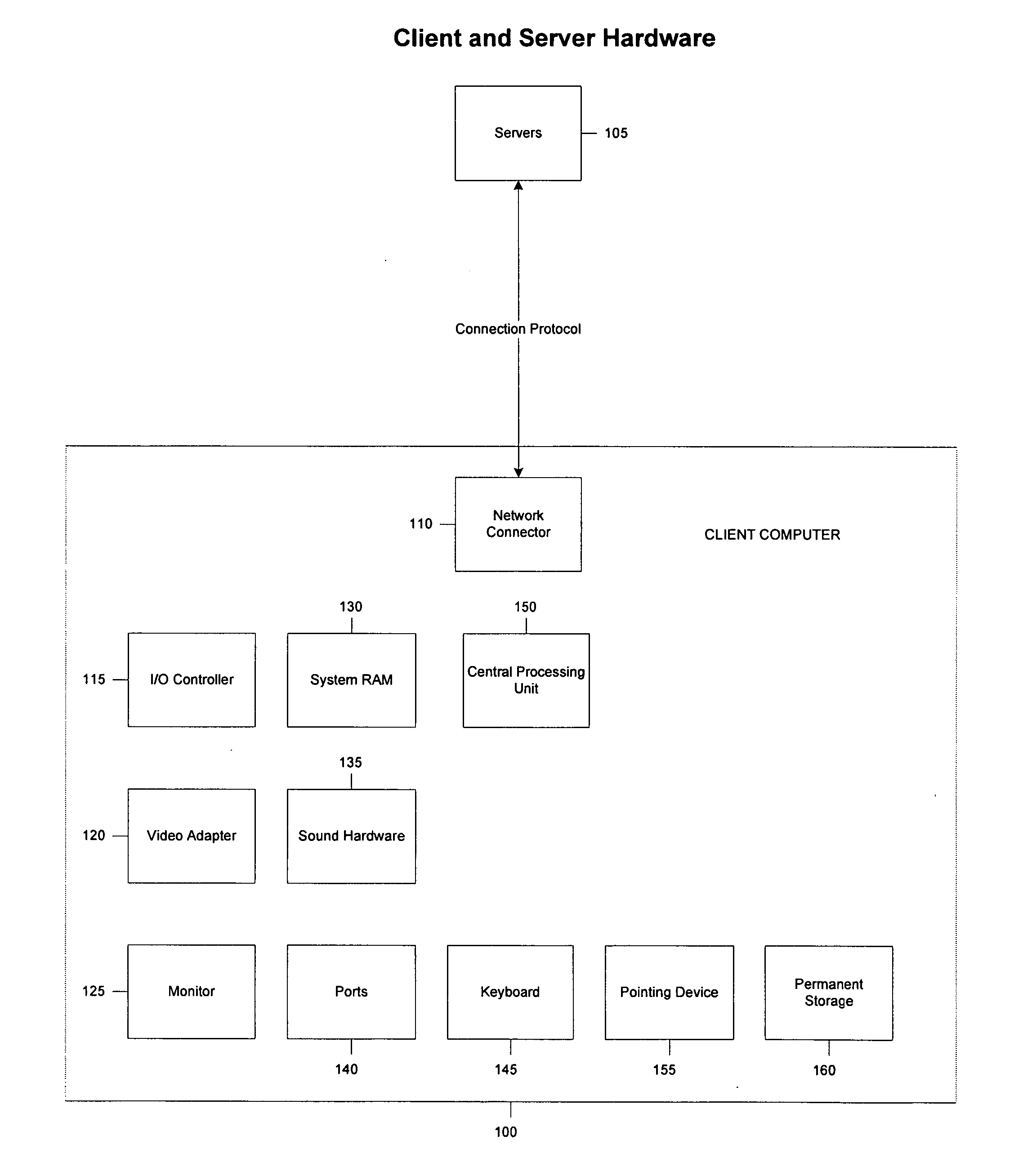
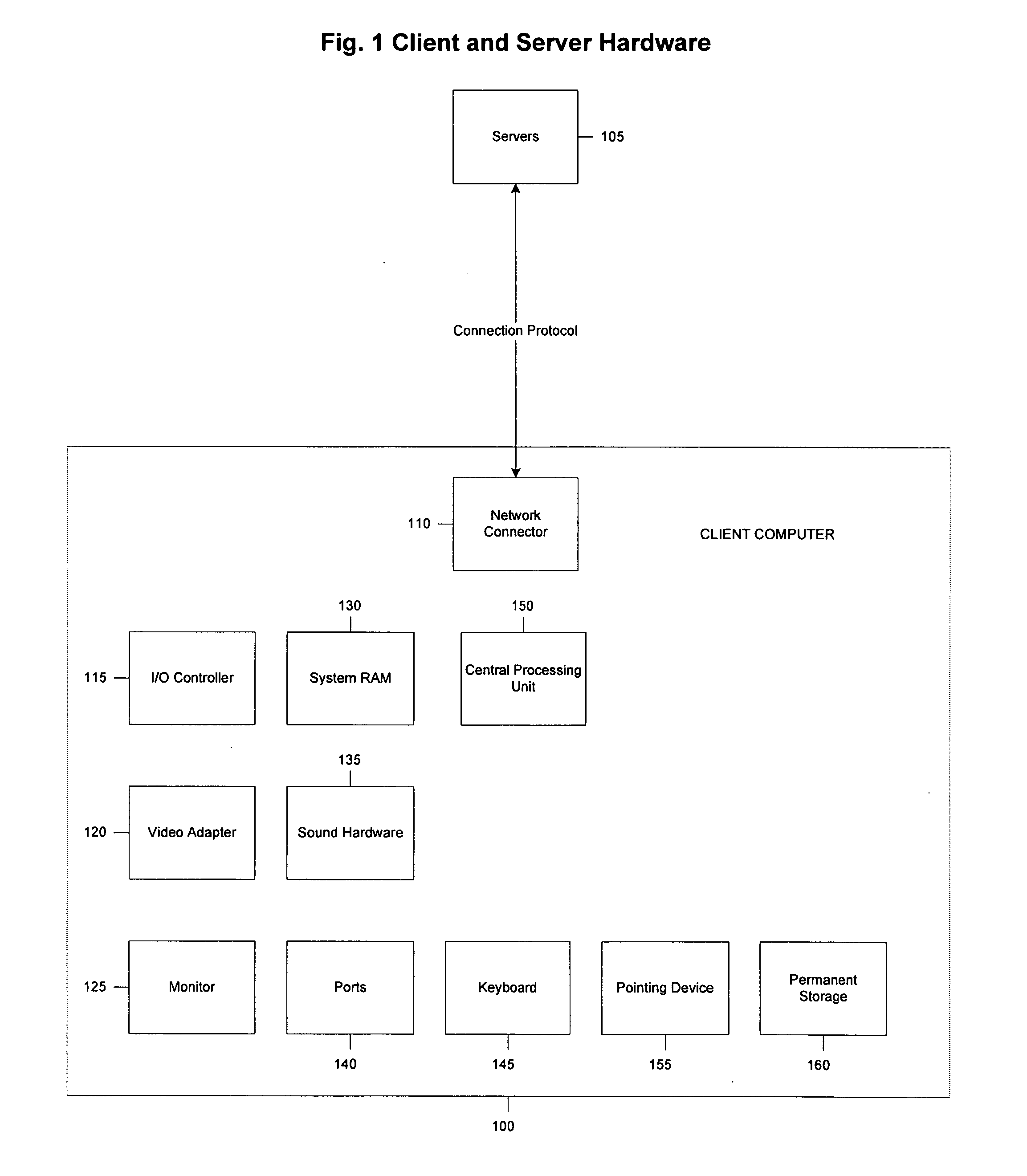
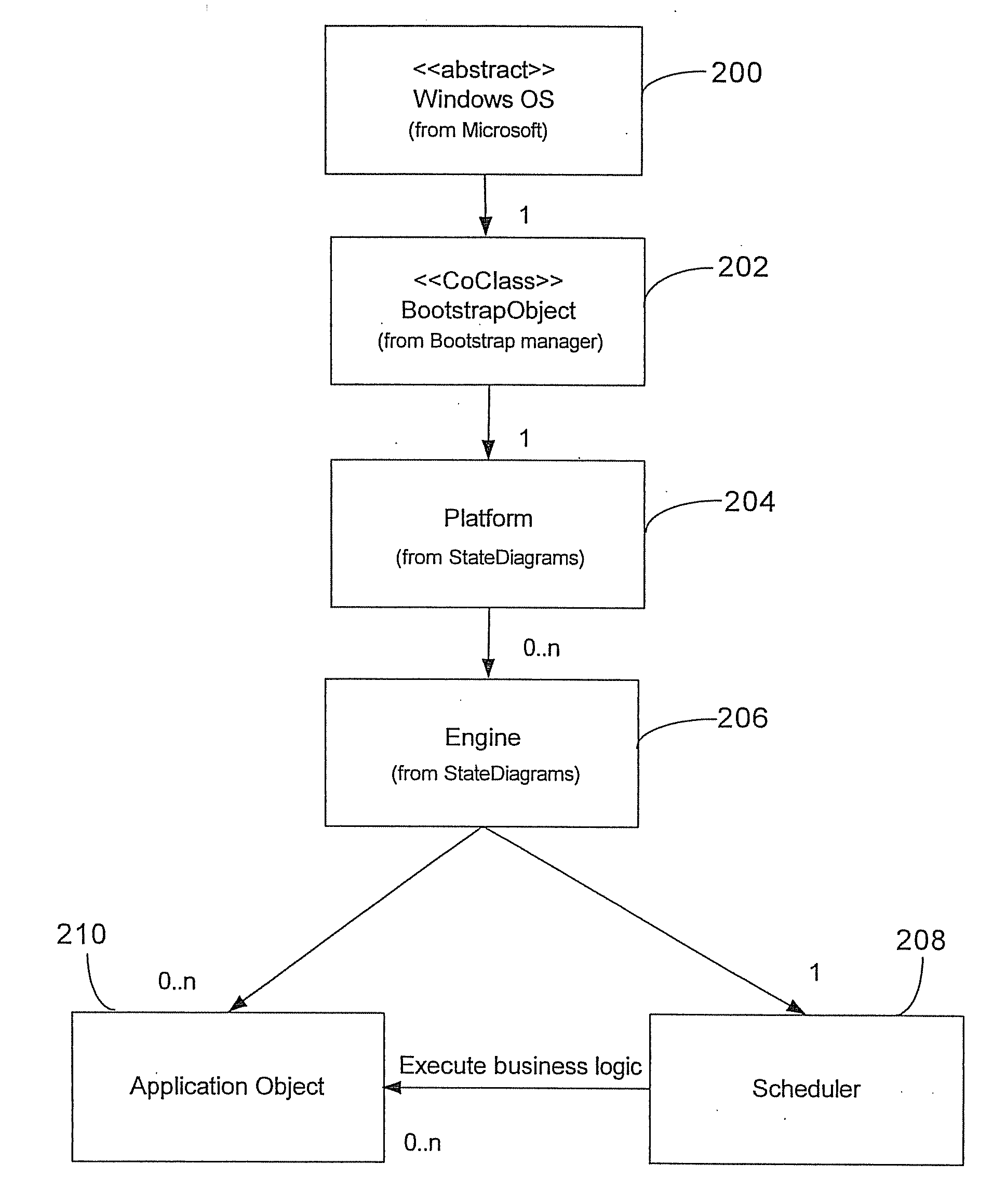
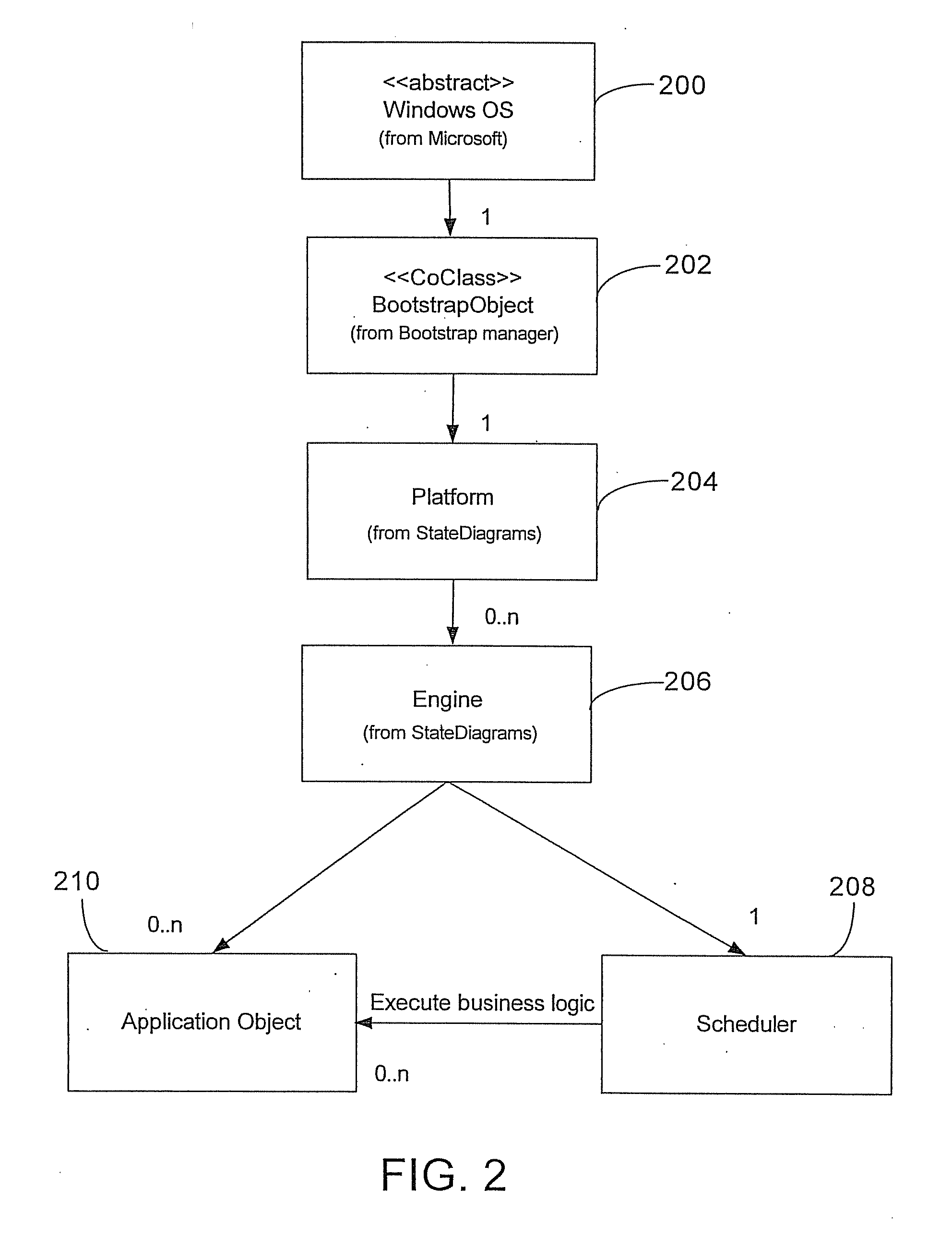
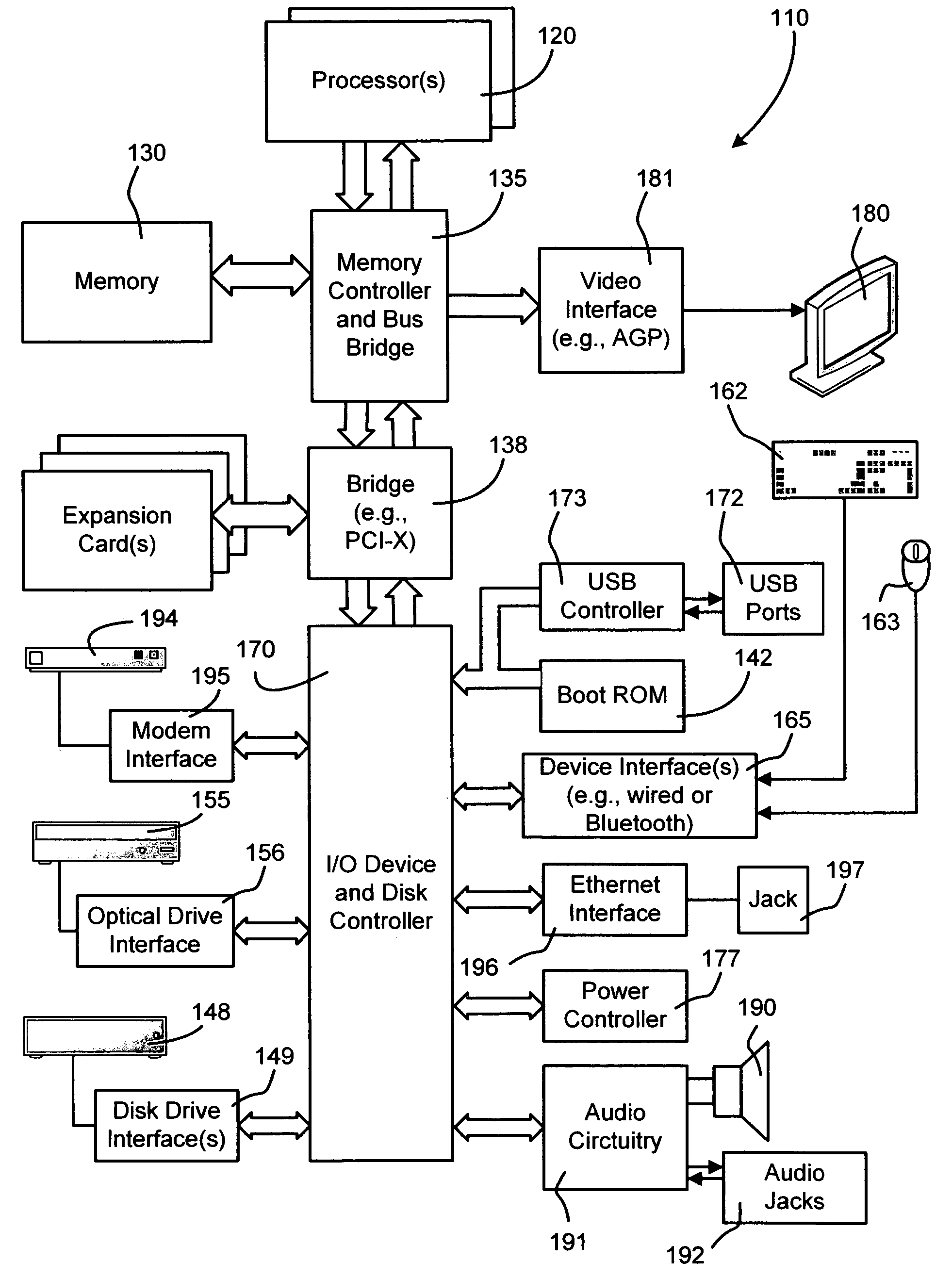
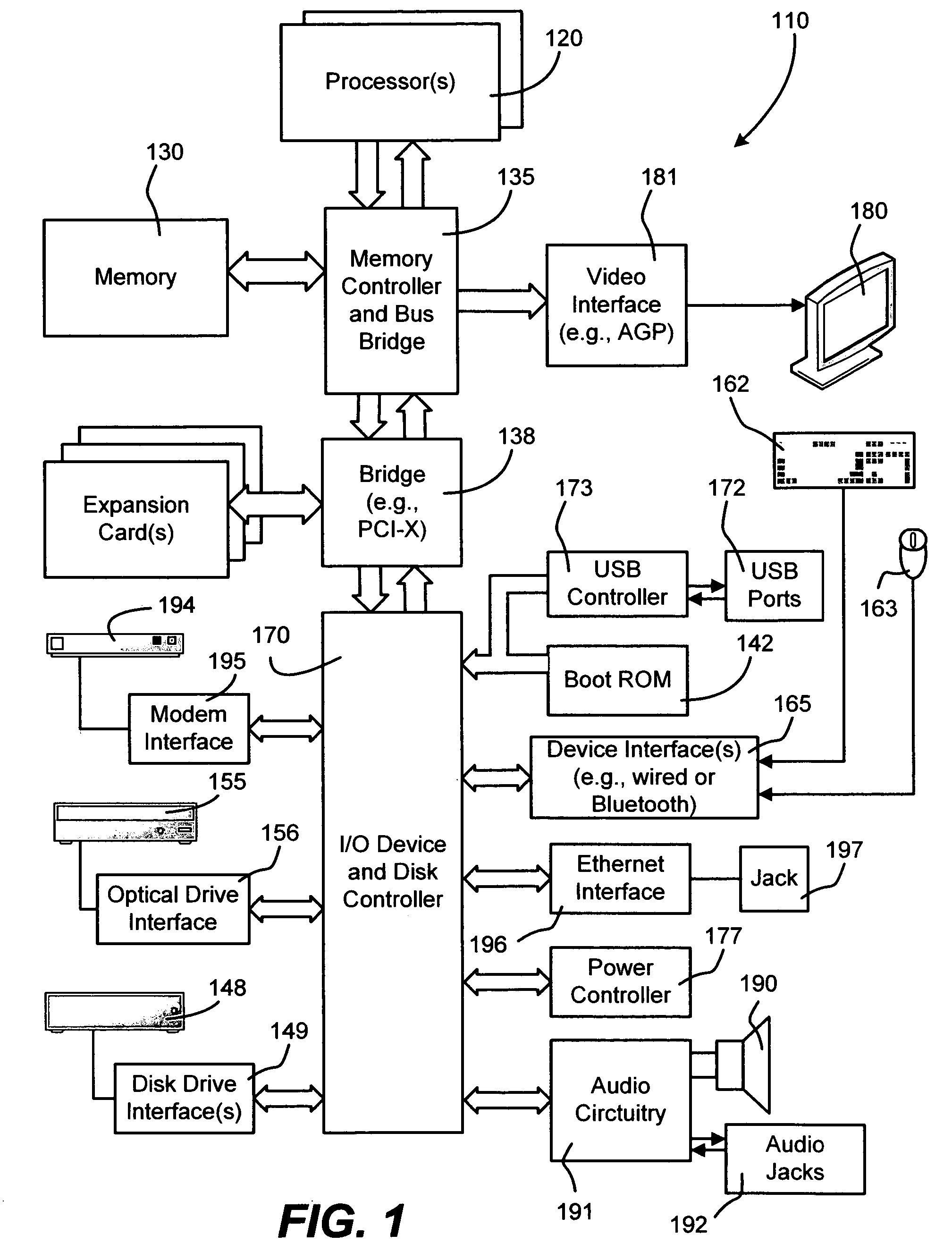
An Application Has a Single Application Object. The application object is a singleton—that is, a single instance is available to all objects in an application. In iOS, the application object is an instance of the UIApplication class (or a subclass of that class); in OS X, the application object derives from the NSApplication class.
Generic, multi-instance method and GUI detection system for tracking and monitoring computer applications
ActiveUS20070083813A1Facilitates code reuse and modular packagingPromote publicationError detection/correctionDigital computer detailsObject structureClient-side
Presented is a system and method for monitoring events derived from a computer target application presentation layer including the steps of providing, independent of recompiling the target application's source code, a script running at a level within the target application. The script scans run-time instantiations of objects of the target application, and allocates structures in real-time to the object instantiations. These allocated structures are adapted to create a reflection of the target application structure, which is used along with detected object instantiations that match a predetermined object structure to capture a portion of an environmental spectrum of the detected object. Further, the system can process state machine events occurring on at least one of a server machine and a client / localized machine, correlate the state machine events with the environmental spectrum, and deduce a user experience based on the correlated state machine events.
Owner:KNOA SOFTWARE INC
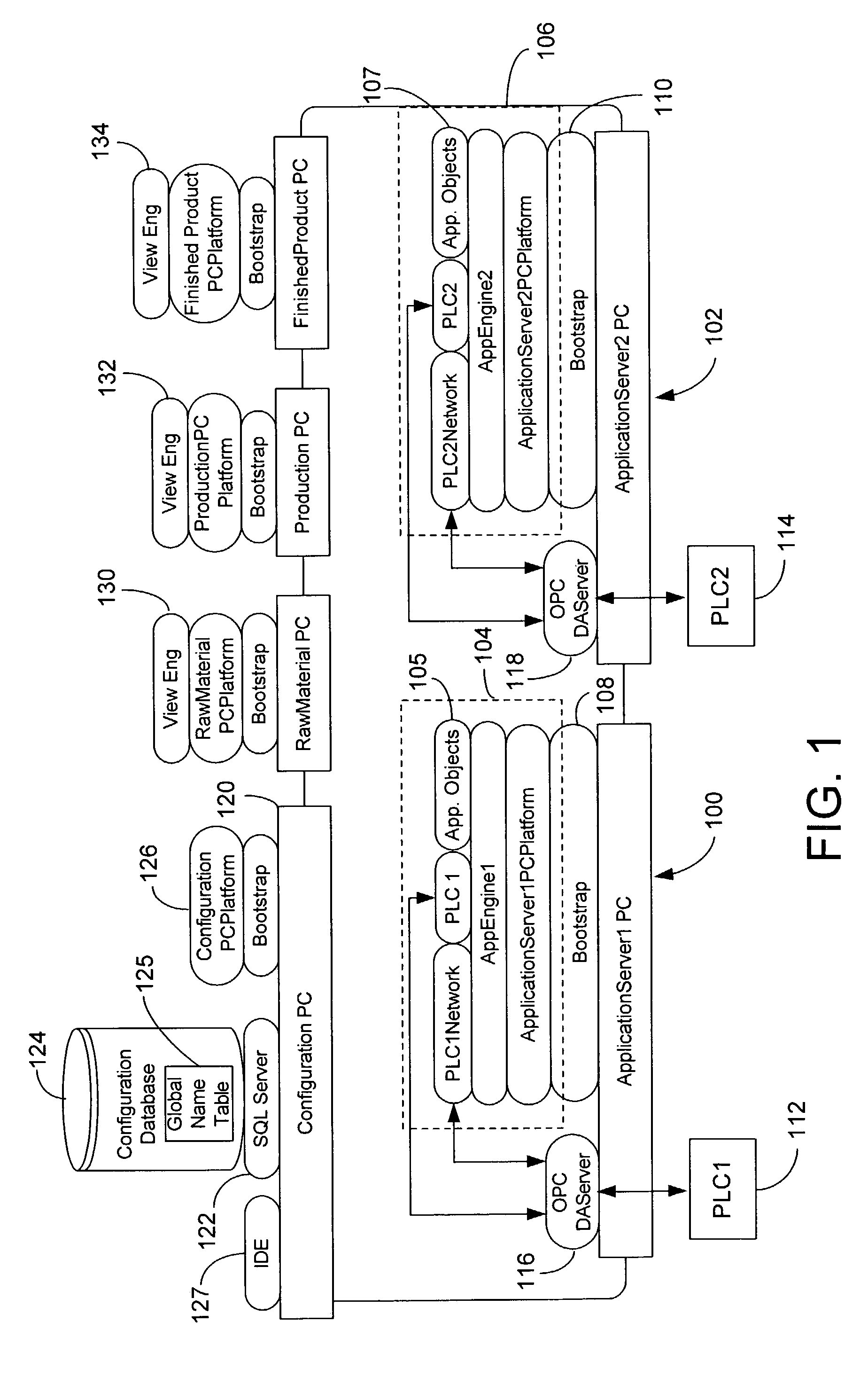
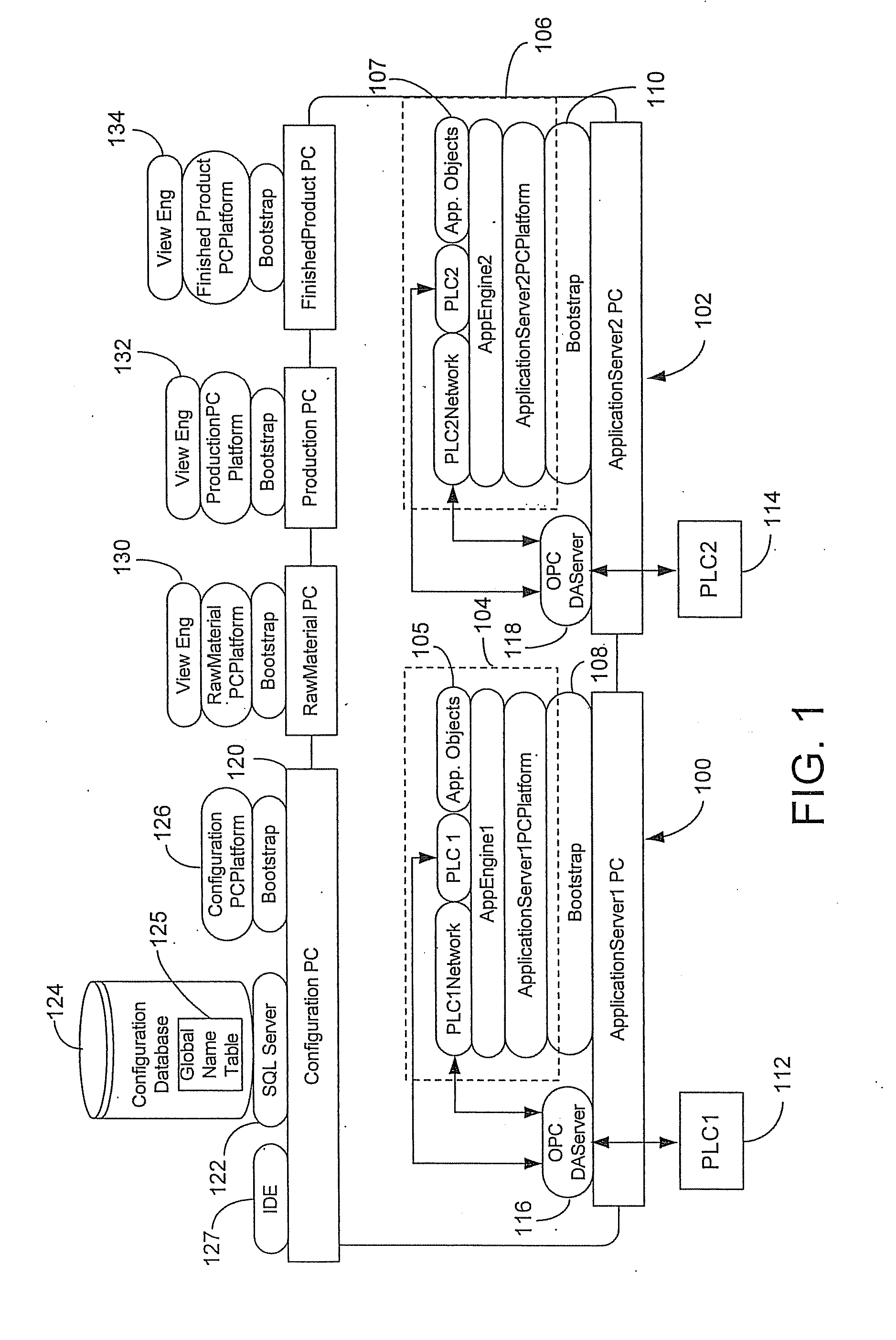
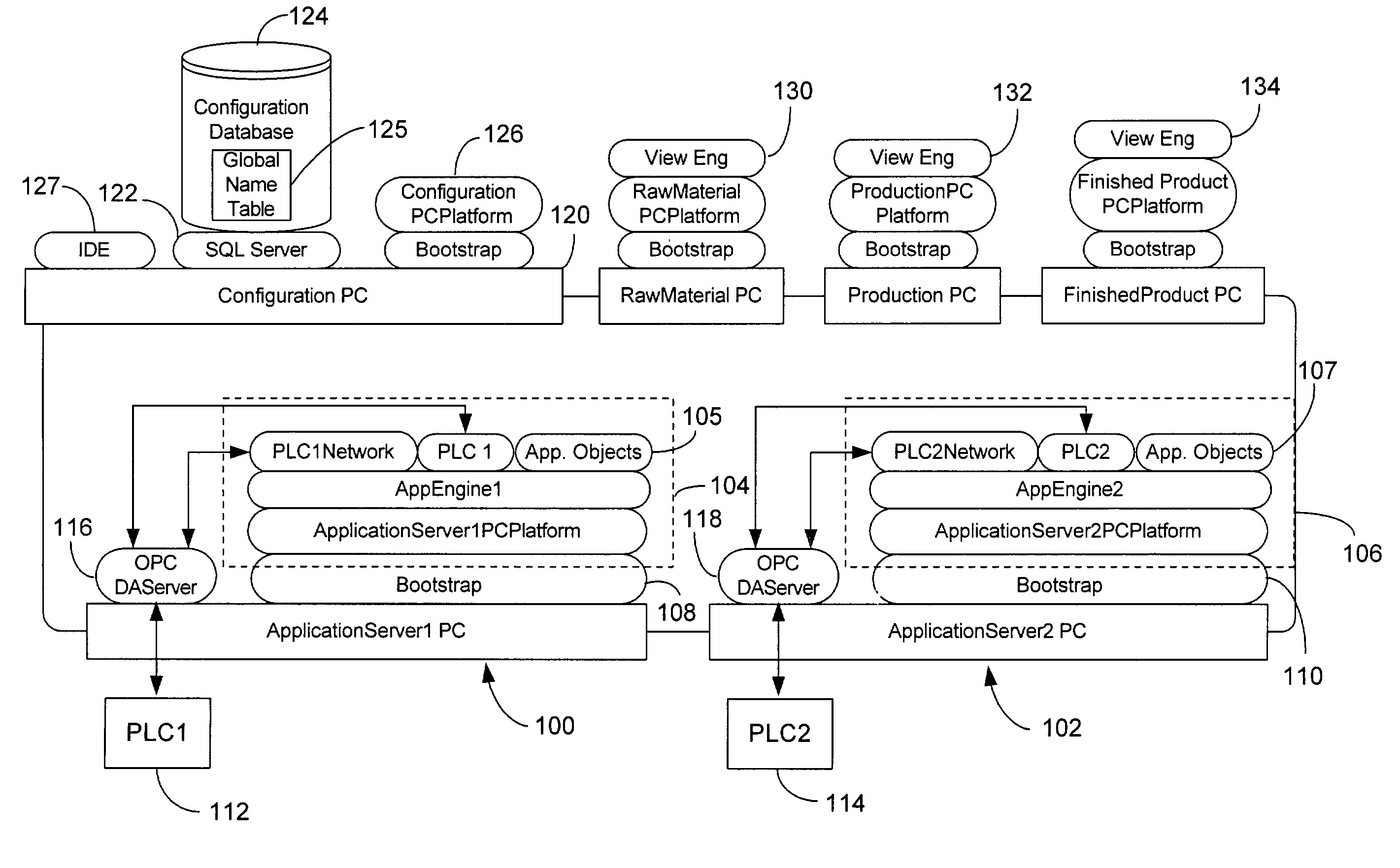
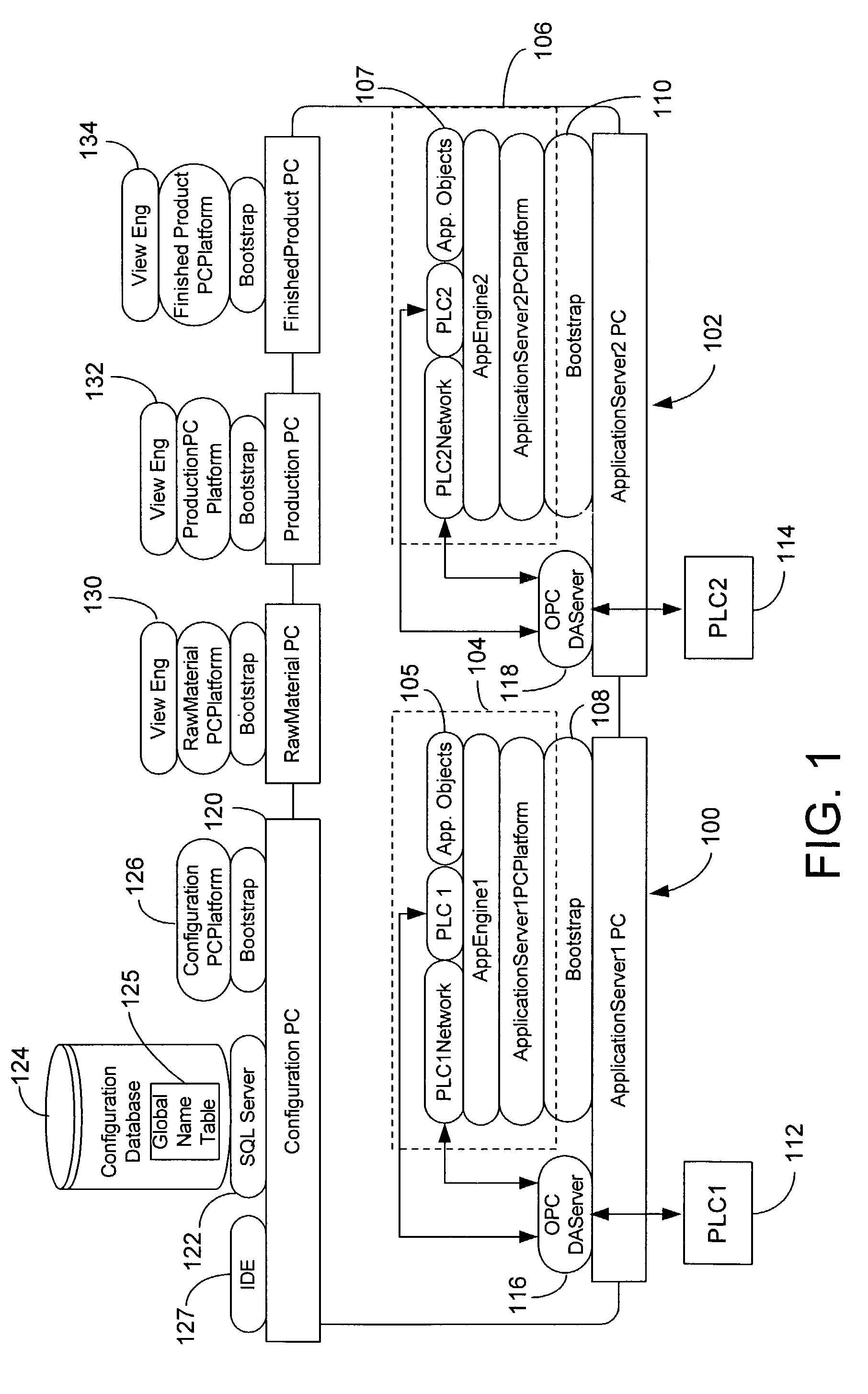
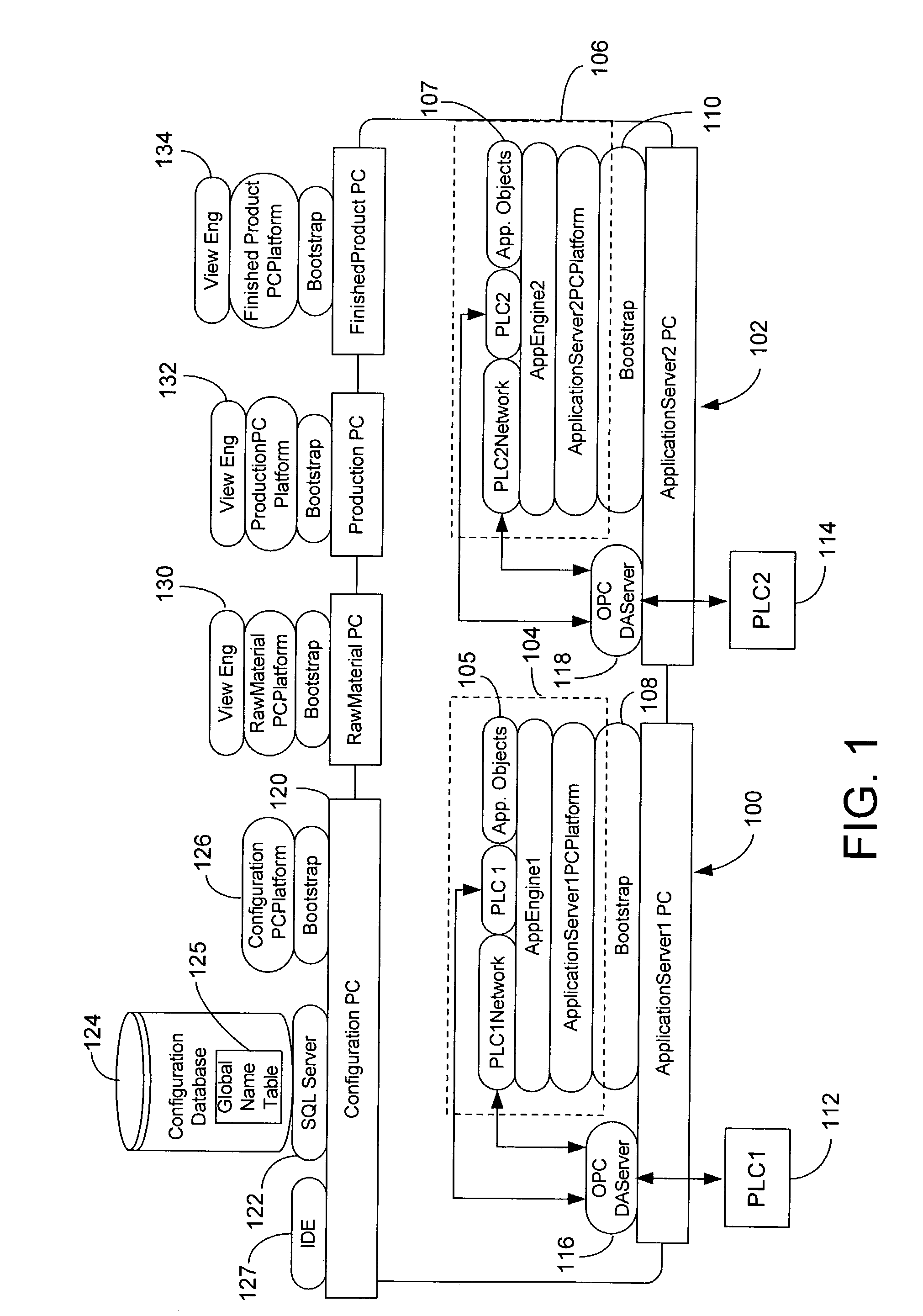
Customizable system for creating supervisory process control and manufacturing information applications
ActiveUS7086009B2Enhanced product offeringIntegration changesSoftware designSoftware simulation/interpretation/emulationThird partyDocumentation procedure
An extensible base process control and manufacturing information application development and execution software suite is disclosed that facilitates streamlined third party (e.g., OEM) development of derivative applications for particular vertical markets. The suite includes an object design toolkit that provides object template derivation tools for accessing and editing a set of base object templates. The objects derivable from the base templates include at least application objects deployed upon lower level hosting component objects of a supervisory process control and manufacturing information application. The toolkit also includes development tools for creating new base object templates that are added as extensions of the set of base object templates.In addition to the toolkit, the suite includes a set of marketing package customization tools facilitating seamlessly integrating changes by developers to the extensible base development and execution software suite. The marketing package customization tools include electronically editable base user documentation.
Owner:SCHNEIDER ELECTRIC SOFTWARE LLC
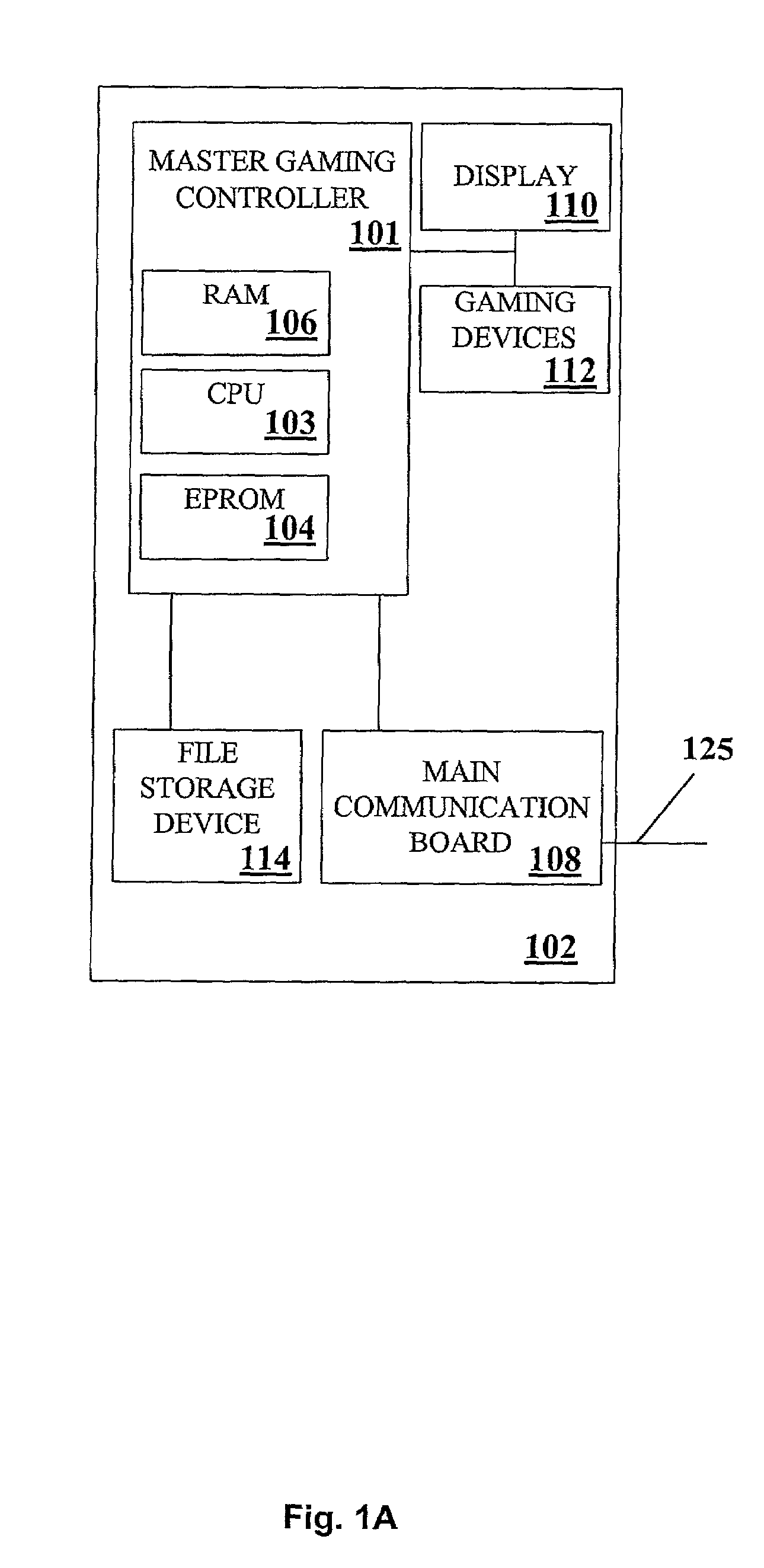
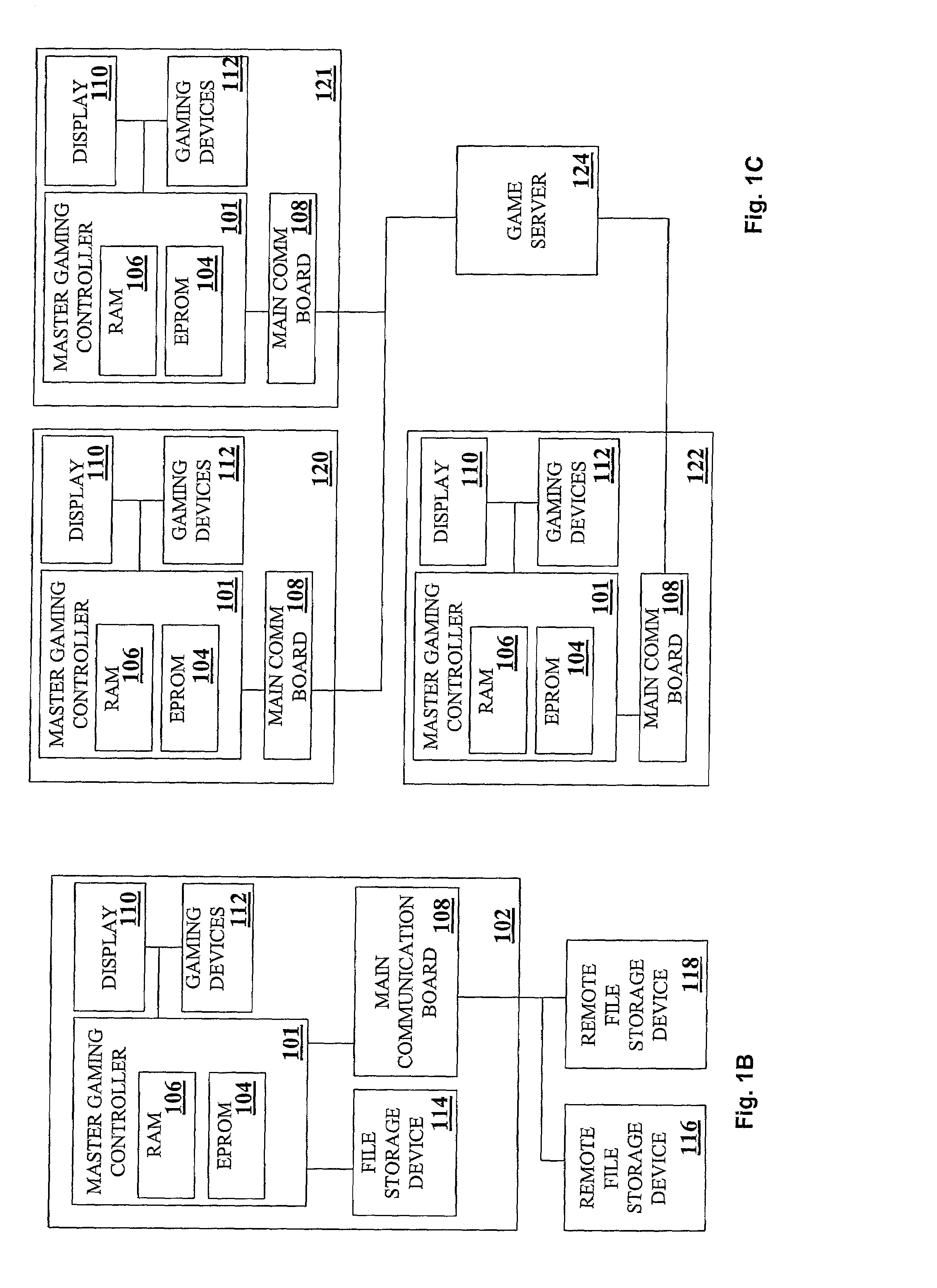
Dynamic configuration of gaming system
InactiveUS6939234B2Digital computer detailsApparatus for meter-controlled dispensingApplication softwareHuman–computer interaction
A gaming system comprises a plurality of common objects, a plurality of application objects, and a central system. The common objects are shared by a plurality of applications and include gaming devices and games. Each gaming device includes at least one of the games. The application objects are used in one of the applications. The central system is linked to the gaming devices and includes a common database and an application database. The common database defines the common objects and first associations between the common objects. The application database defines the application objects, second associations between the application objects, and third associations between the common objects and the application objects. The central system is adapted to dynamically configure the one of the applications based on a change to one or more of the first, second, and third associations.
Owner:BALLY GAMING INC
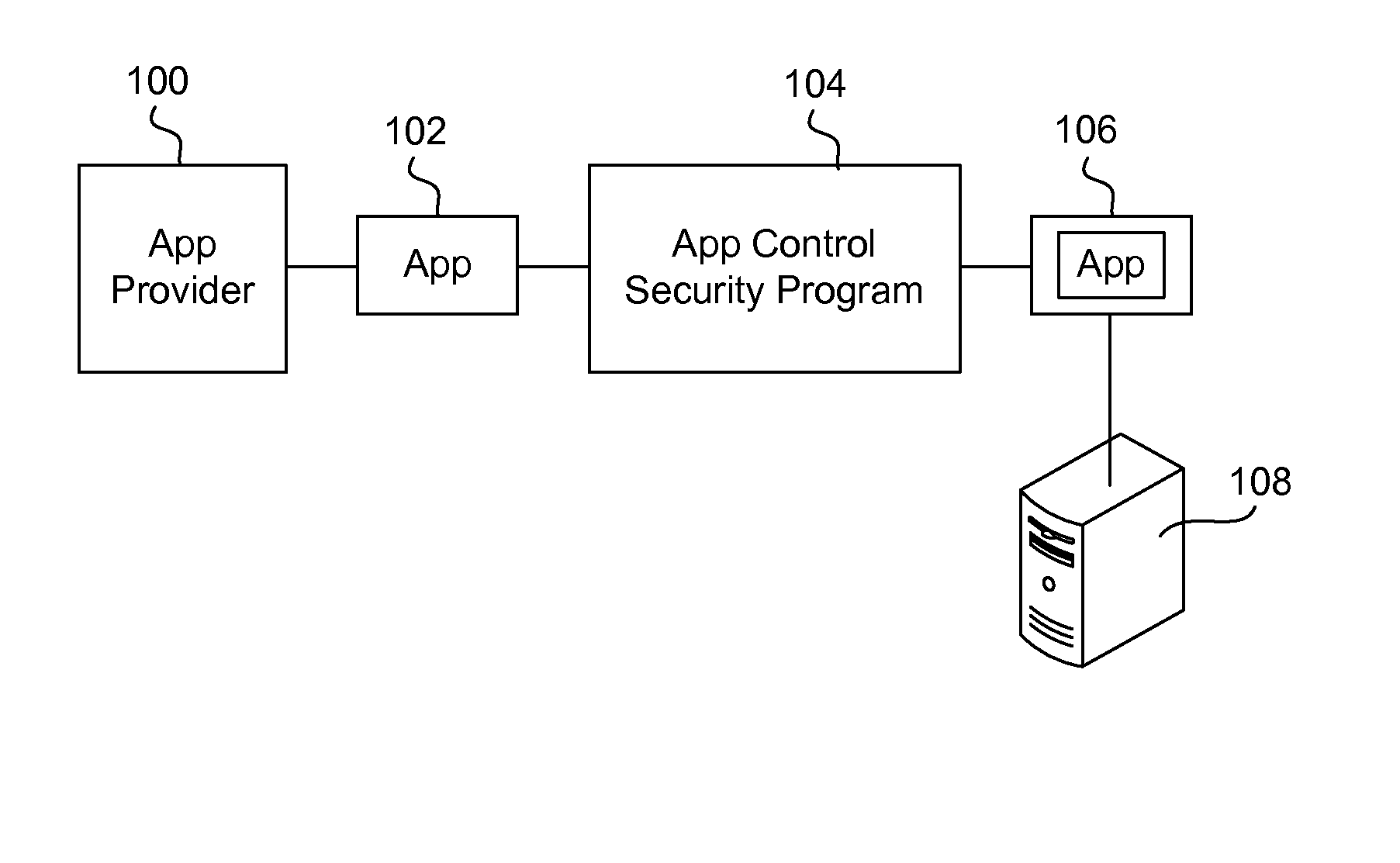
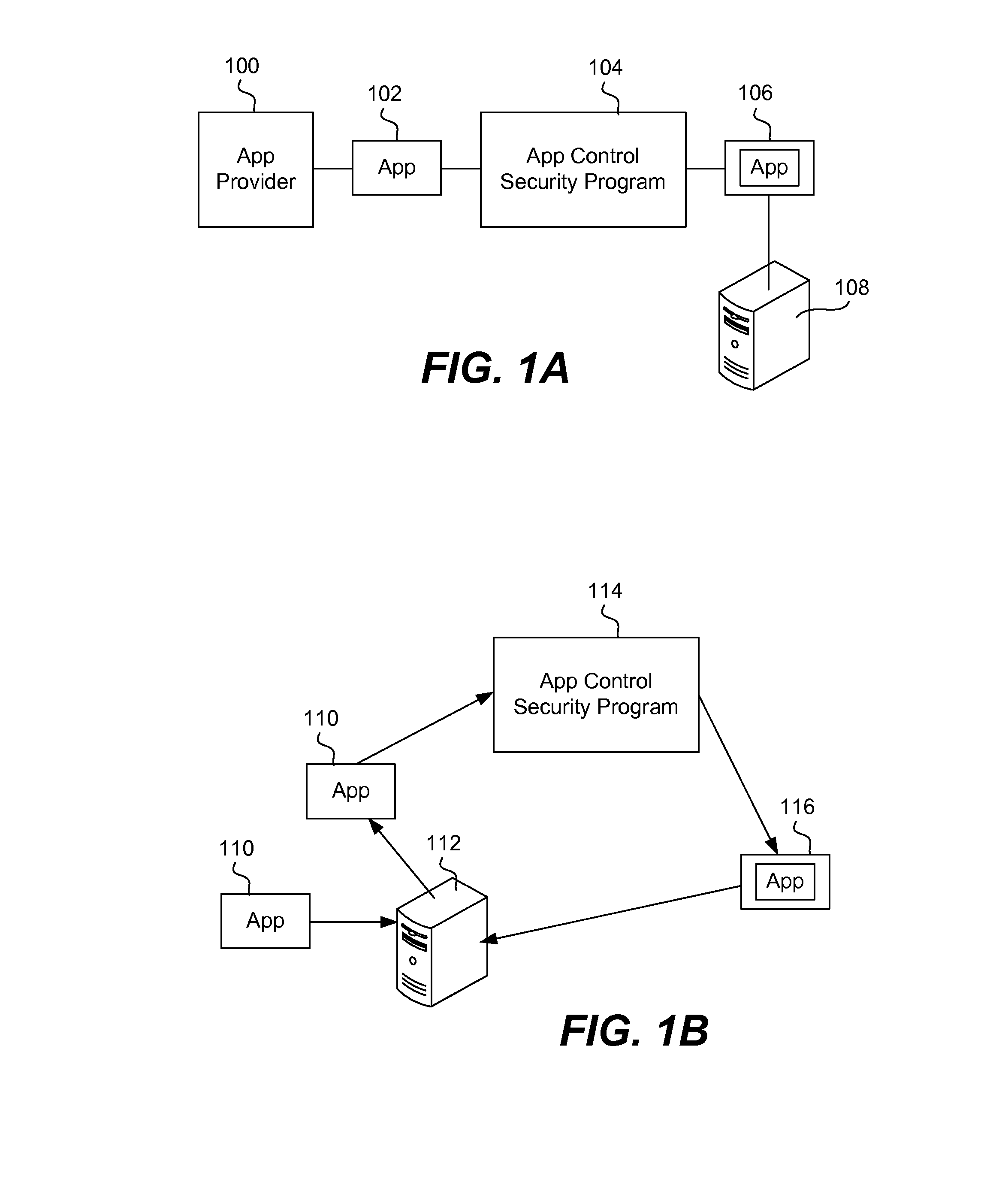
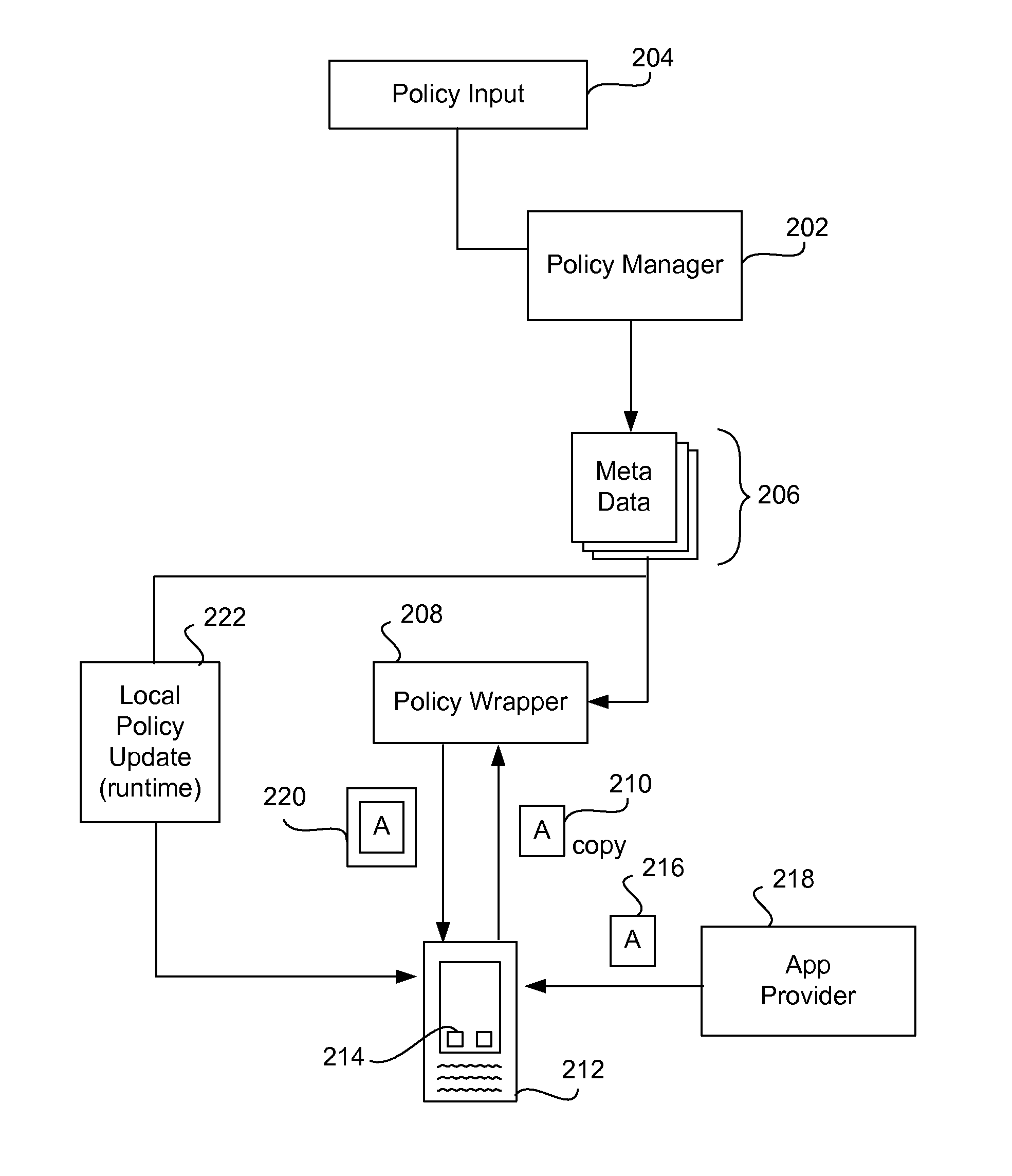
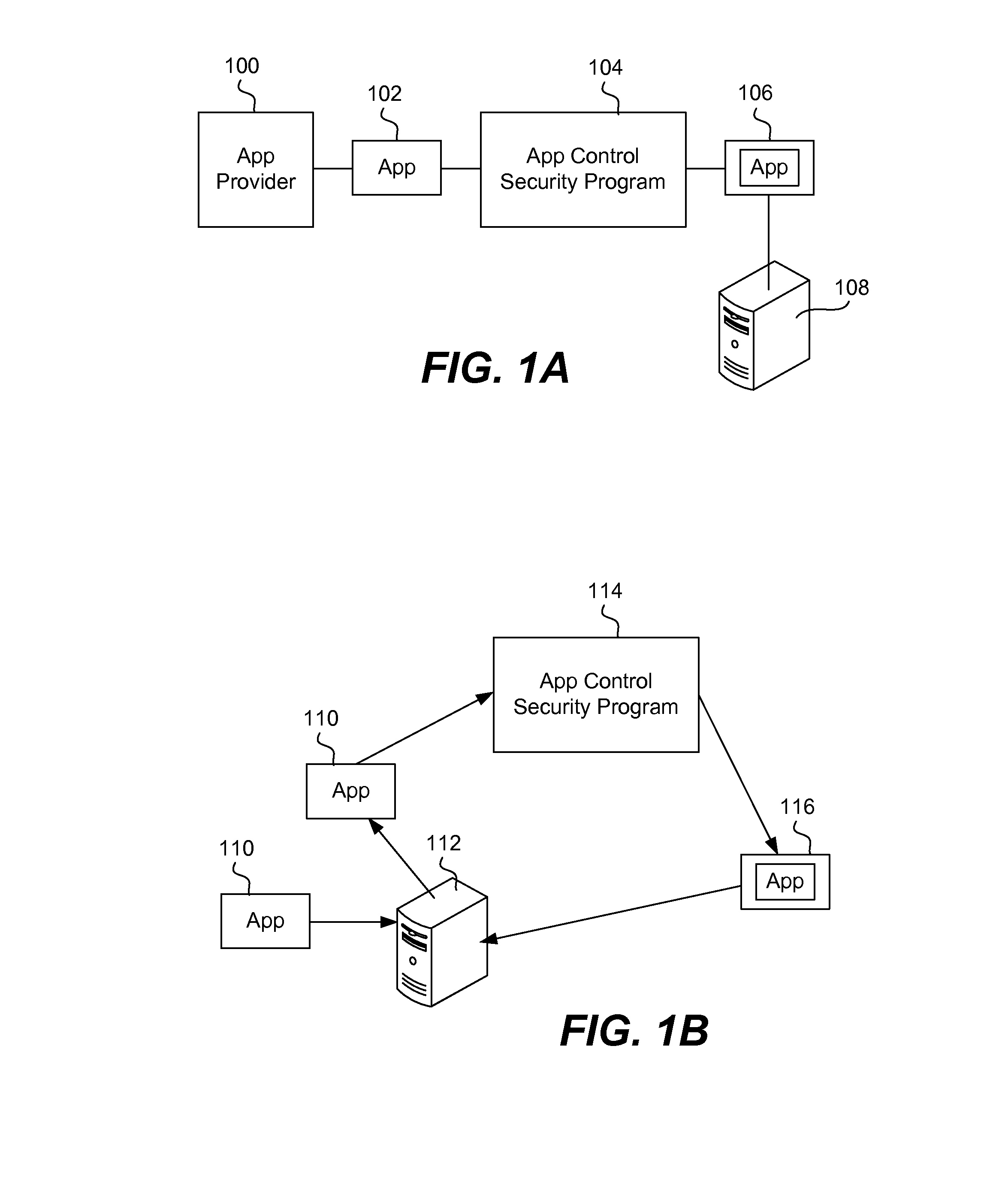
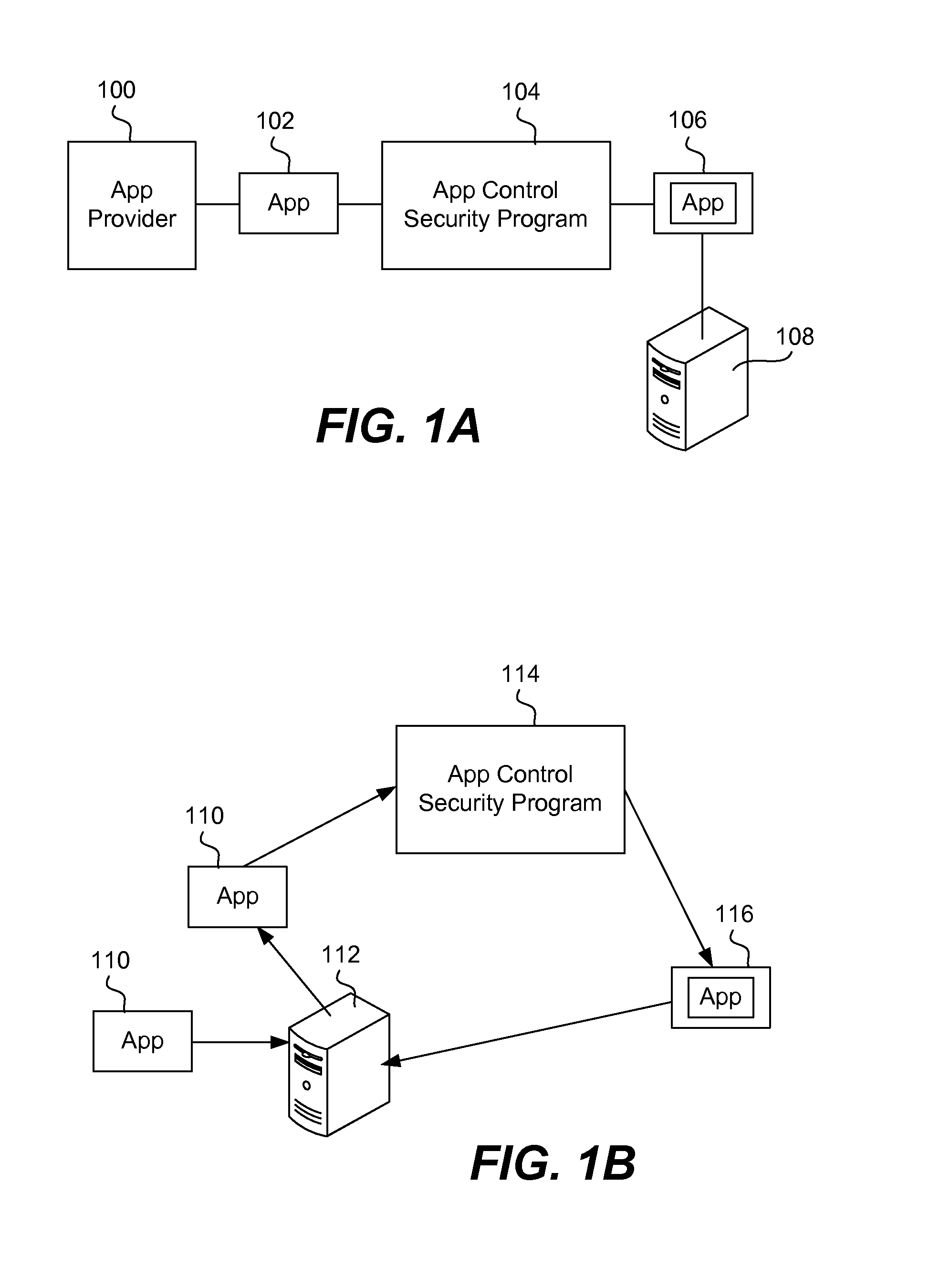
Securing and managing apps on a device
ActiveUS20120210443A1Preventing the app from malicious behavior on the deviceDigital data processing detailsAnalogue secracy/subscription systemsTablet computerOperational system
Apps are secured or security-wrapped either before they are downloaded onto a device, such as a smartphone or tablet device, or after they are downloaded but before they are allowed to access the device operating system and cause any potential damage to the device. An app provider, such as an employer or a cellphone provider, can secure its apps before consumers download an app from their app store or marketplace. The app is secured before it is allowed to access the operating system of the device, thereby preventing the app from malicious behavior. Core object code of the app is obtained and the digital signature is removed. App object code is substituted with security program object code, thereby creating a security-wrapped app. The security-wrapped app is prepared for execution on the device and is re-signed with a new key.
Owner:BLUE CEDAR NETWORKS INC
Method and system for session based authorization and access control for networked application objects
Owner:PRISMTECH
System for replicating and associating file types with application programs among plurality of partitions in a server
InactiveUS6047312AComputer security arrangementsMultiple digital computer combinationsApplication softwareWorkstation
A method and apparatus according to various aspects of the present invention provides a system for associating files with relevant application programs in a network. The applications are available on a network, suitably as application objects. Each application object also includes file type information associated with the application. When a user logs onto the network, the file type information is retrieved from each accessible application object. The application launcher stores the retrieved information in the local memory of the user workstation. When a file is selected at the user workstation, the user workstation checks its local memory for the file type information corresponding to the selected file. Because the information is periodically updated by the application launcher, the current information is available to associate a particular file type extension with an application stored remotely. As a result, the appropriate application may be initiated.
Owner:EMC CORP
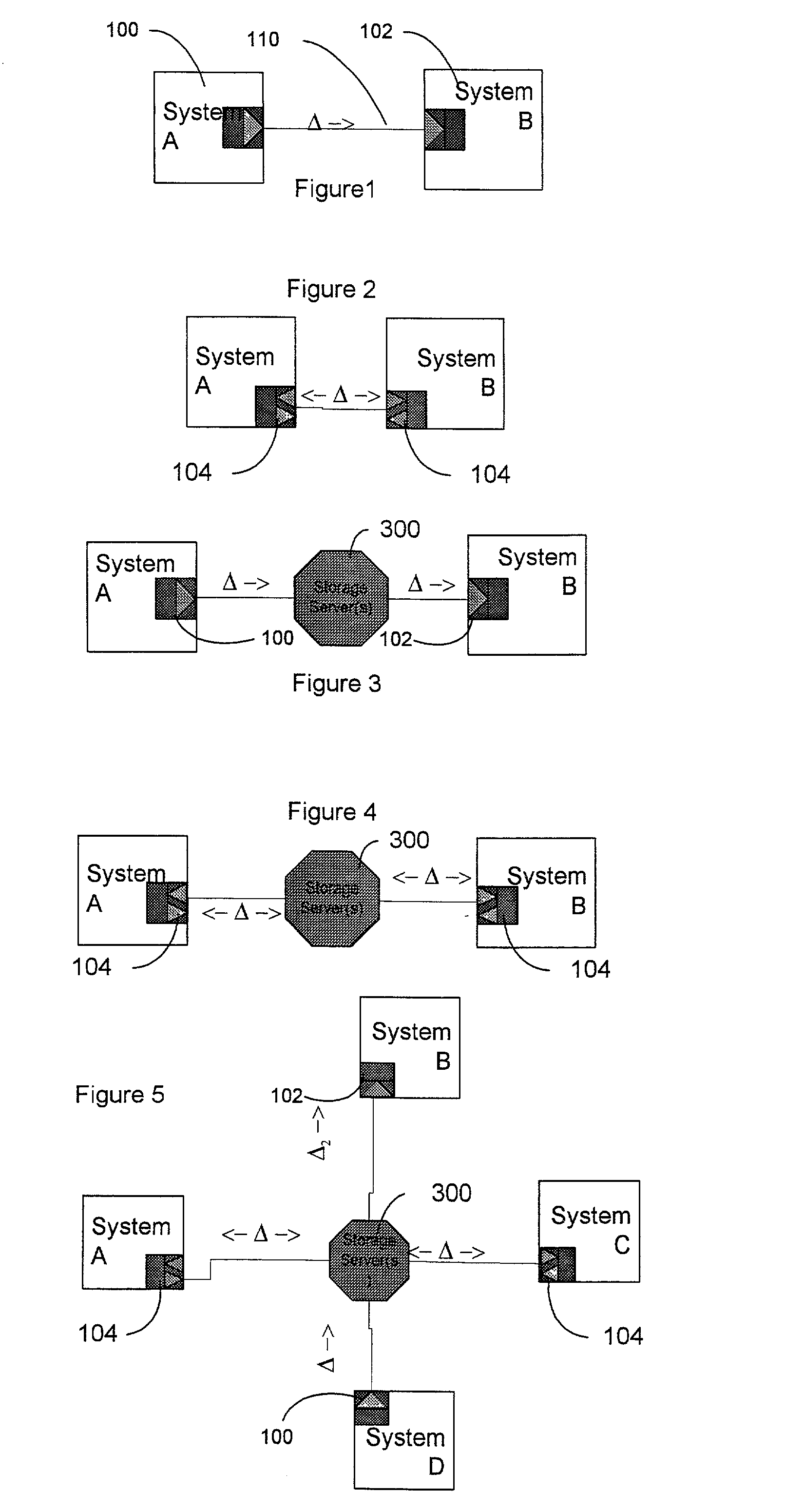
Data package including synchronization data
InactiveUS20020010807A1Digital data information retrievalData processing applicationsNetwork packetData source
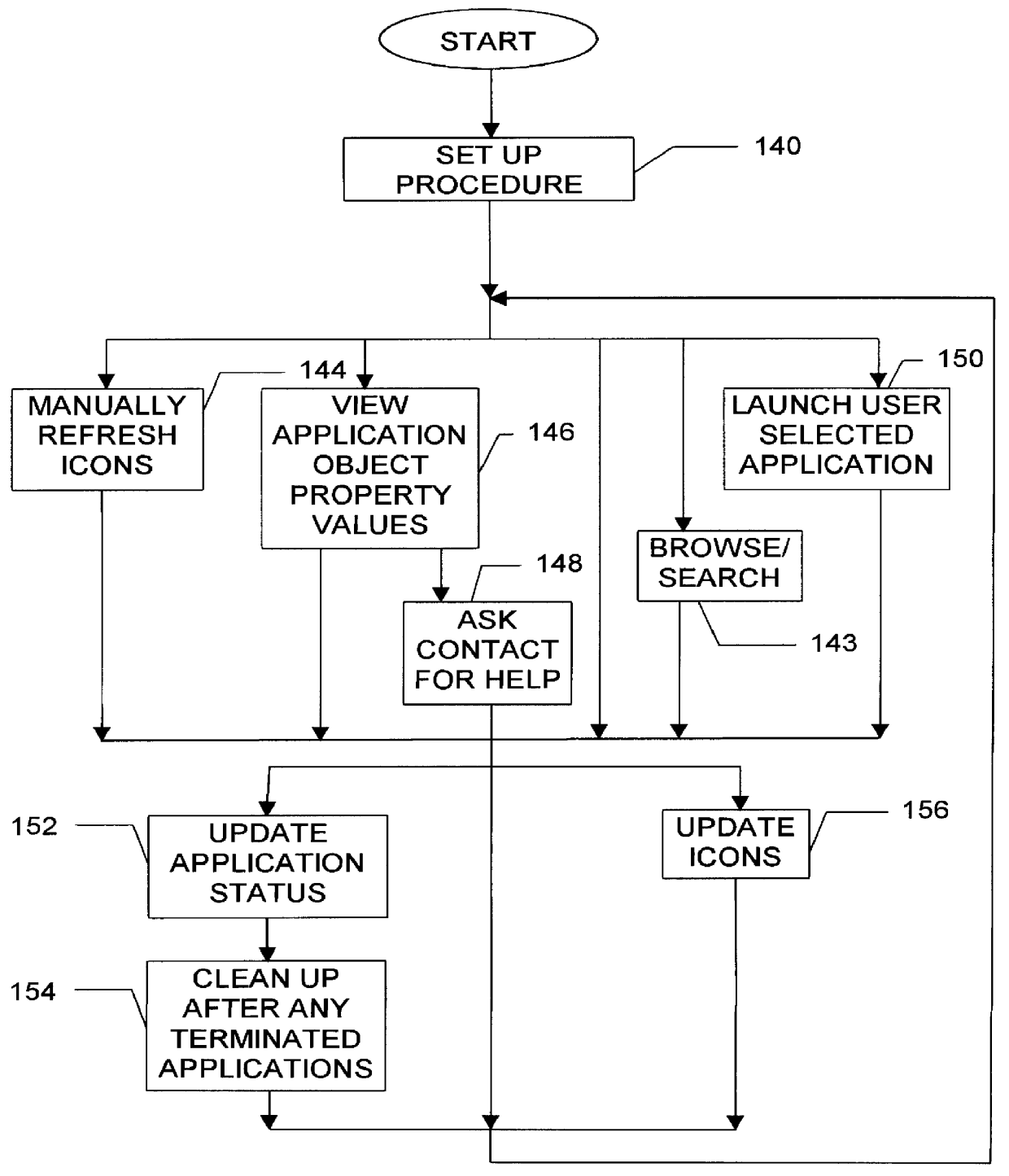
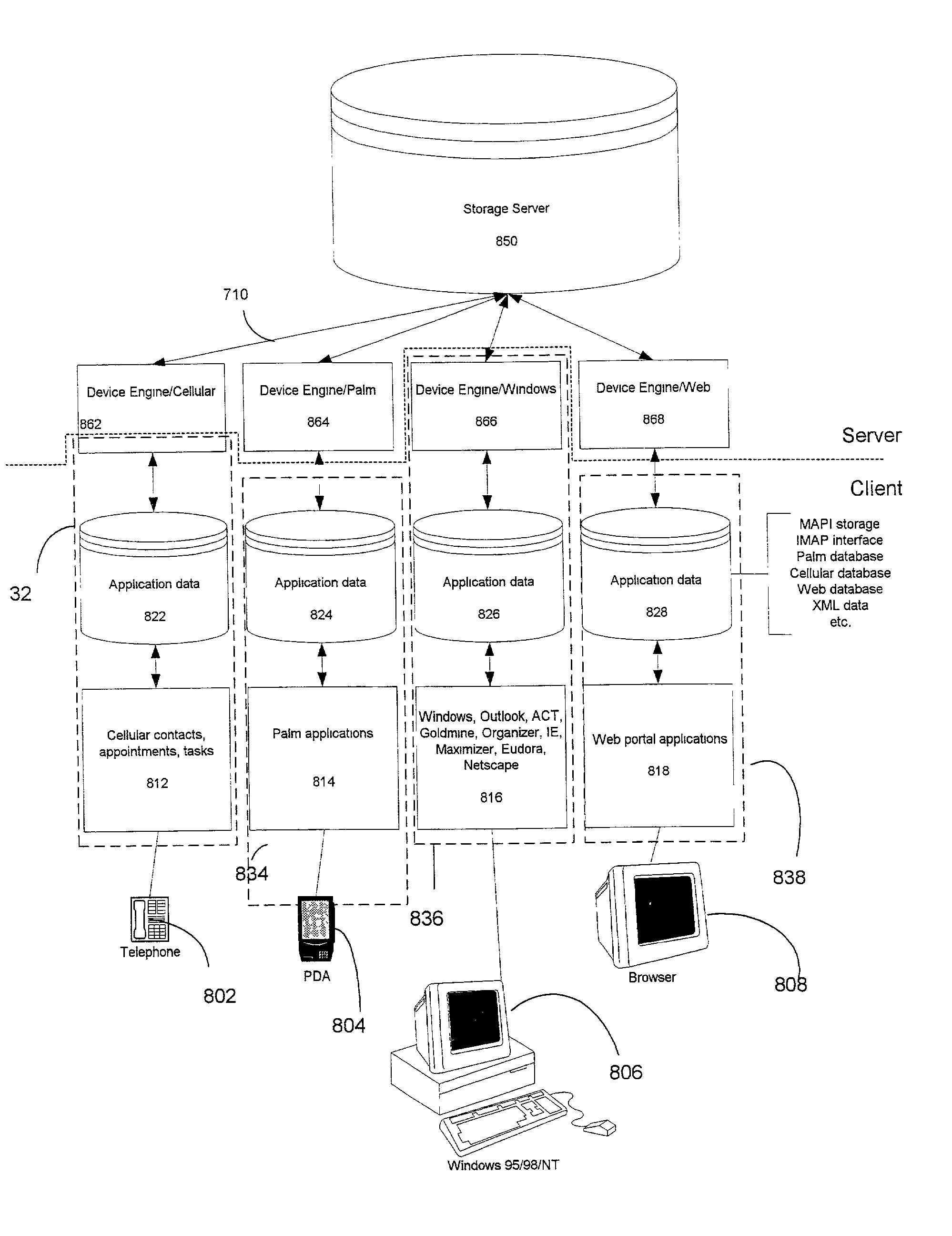
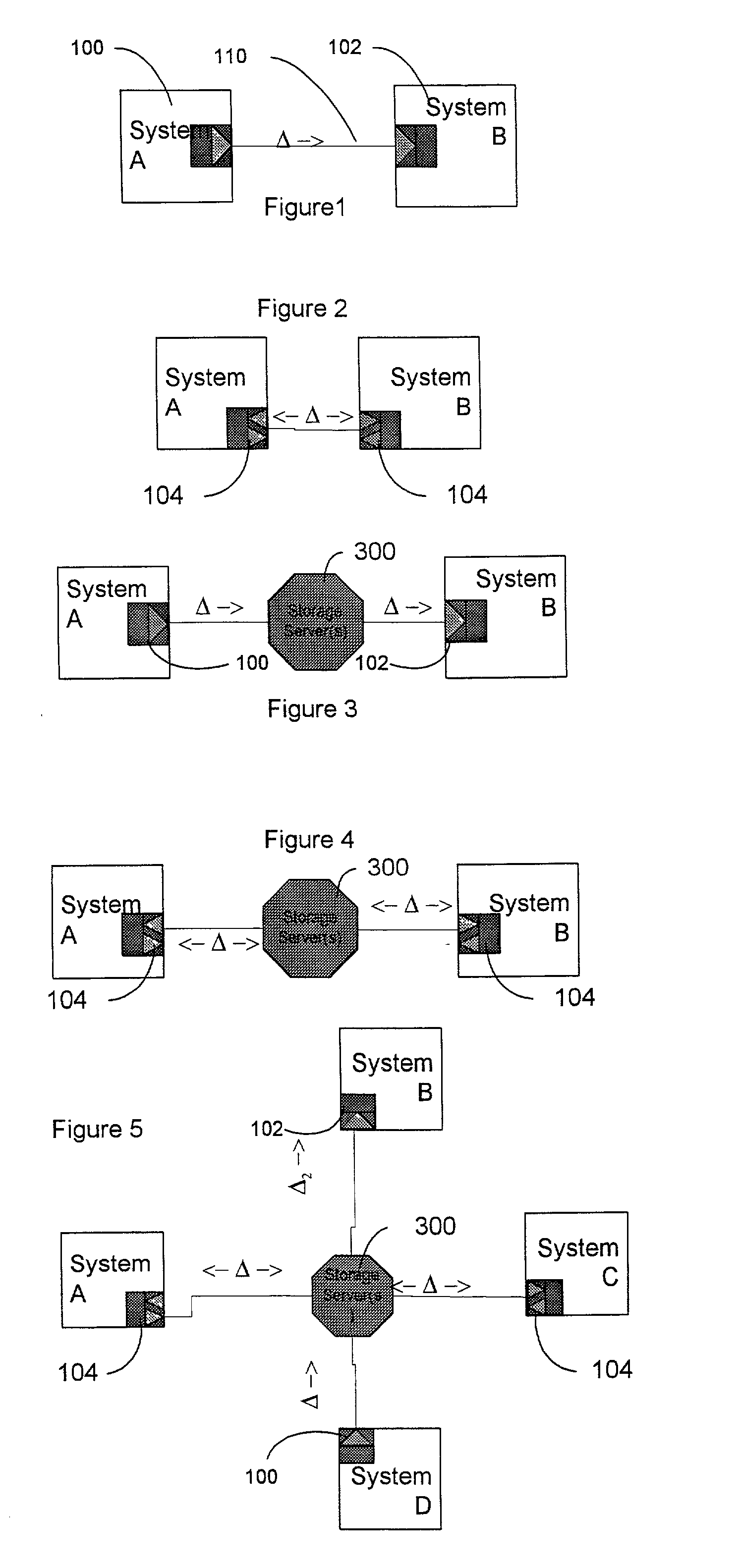
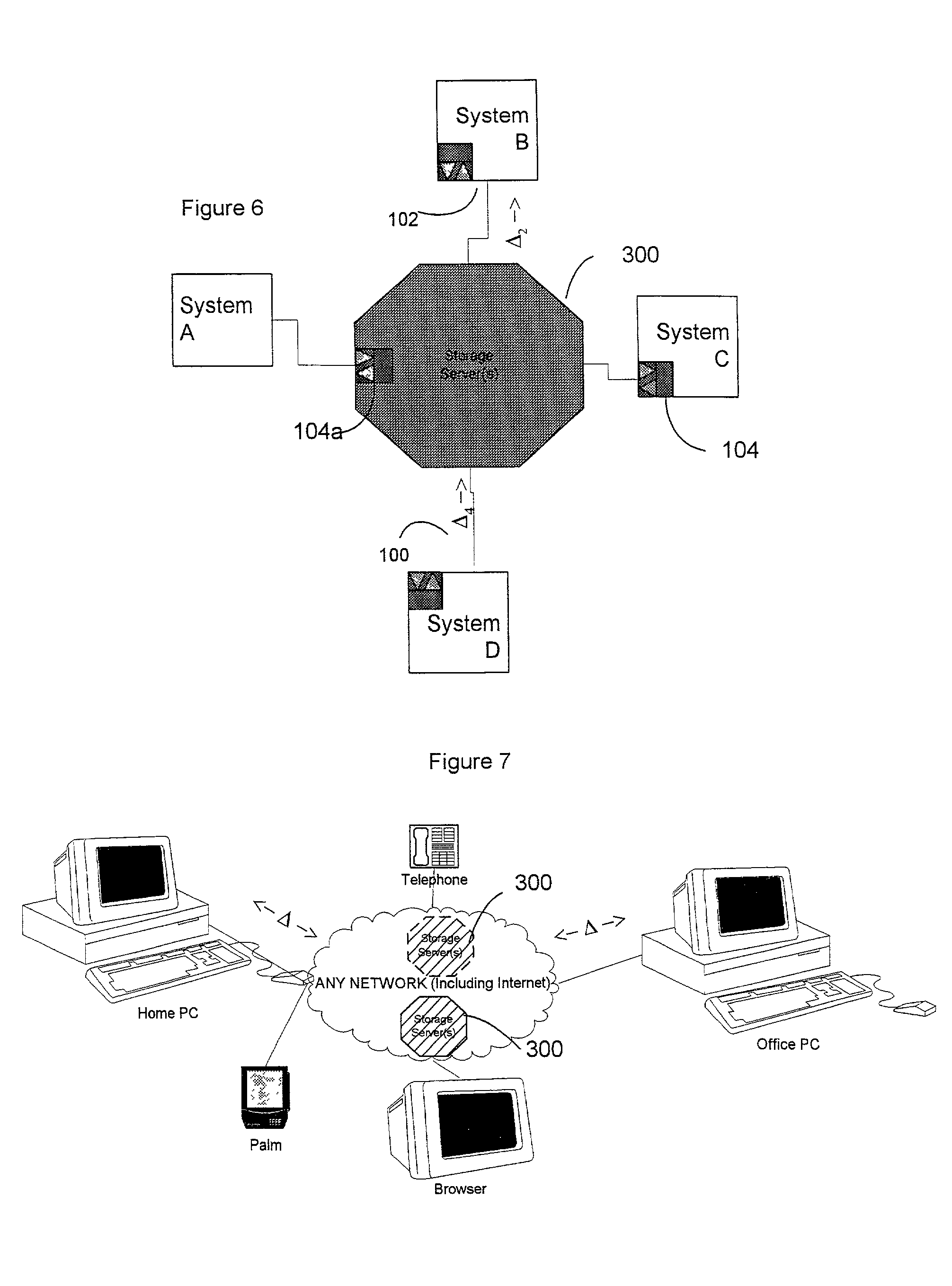
A difference information receiver, a difference information transmitter and a difference information synchronizer which cooperate in a system or device to update data in the device with data received from other systems, or provide data for other systems to use in updating themselves are disclosed. A difference receiver in a device having at least one application data destination having a format includes a difference engine receiving difference information associated with a change to said at least one application data destination; and an application interface, applying said difference information to said at least one data destination. A method for updating data files in a system is also disclosed. The method may include the steps of: receiving difference information for a subset of said data files; and applying said difference information to said subset of said data files. In particular said step of receiving may comprise: receiving a change log detailing changes to data files on another system; and applying said changes to a data store containing data identical to said data files to generate changed data. A difference transmitter comprises an application in a system having a data source in a source format. The application may include an application interface, extracting data from said data source; and a difference engine receiving said data and outputting difference information associated with changes to said data source. A method for updating a data source in a system is also disclosed. The method may include the steps of extracting difference information from at least a subset of said data source; and outputting difference information for at least the subset of said data source. The step of extracting may comprise determining whether changes have been made to the subset of data source in the system; and generating a change log detailing changes to the subset of data source on another system. A difference synchronizer includes an extraction routine for extracting a first set of difference information resulting from changes to the data files; a differencing transmitter for transmitting said first set of difference information to an output; a differencing receiver for receiving a second set of difference information from an input; and a reconstruction routine for applying the second set of difference information to the data files. In a particular embodiment, the invention comprises a device engine including an application object; an application object store; and a delta module.
Owner:SYNCHRONOSS TECH
System for development, management and operation of distributed clients and servers
InactiveUS20060031237A1Facilitate the processData processing applicationsDigital data processing detailsApplication serverDistributed decision
Owner:MUSOLINO PATRICIA IDA
Binary data synchronization engine
InactiveUS20020040369A1Data processing applicationsDigital data information retrievalData synchronizationData source
A difference information receiver, a difference information transmitter and a difference information synchronizer which cooperate in a system or device to update data in the device with data received from other systems, or provide data for other systems to use in updating themselves are disclosed. A difference receiver in a device having at least one application data destination having a format includes a difference engine receiving difference information associated with a change to said at least one application data destination; and an application interface, applying said difference information to said at least one data destination. A method for updating data files in a system is also disclosed. The method may include the steps of: receiving difference information for a subset of said data files; and applying said difference information to said subset of said data files. In particular said step of receiving may comprise: receiving a change log detailing changes to data files on another system; and applying said changes to a data store containing data identical to said data files to generate changed data. A difference transmitter comprises an application in a system having a data source in a source format. The application may include an application interface, extracting data from said data source; and a difference engine receiving said data and outputting difference information associated with changes to said data source. A method for updating a data source in a system is also disclosed. The method may include the steps of extracting difference information from at least a subset of said data source; and outputting difference information for at least the subset of said data source. The step of extracting may comprise determining whether changes have been made to the subset of data source in the system; and generating a change log detailing changes to the subset of data source on another system. A difference synchronizer includes an extraction routine for extracting a first set of difference information resulting from changes to the data files; a differencing transmitter for transmitting said first set of difference information to an output; a differencing receiver for receiving a second set of difference information from an input; and a reconstruction routine for applying the second set of difference information to the data files. In a particular embodiment, the invention comprises a device engine including an application object; an application object store; and a delta module.
Owner:SYNCHRONOSS TECH
Securing and managing apps on a device
ActiveUS8549656B2Preventing the app from malicious behavior on the deviceDigital data processing detailsAnalogue secracy/subscription systemsTablet computerOperational system
Apps are secured or security-wrapped either before they are downloaded onto a device, such as a smartphone or tablet device, or after they are downloaded but before they are allowed to access the device operating system and cause any potential damage to the device. An app provider, such as an employer or a cellphone provider, can secure its apps before consumers download an app from their app store or marketplace. The app is secured before it is allowed to access the operating system of the device, thereby preventing the app from malicious behavior. Core object code of the app is obtained and the digital signature is removed. App object code is substituted with security program object code, thereby creating a security-wrapped app. The security-wrapped app is prepared for execution on the device and is re-signed with a new key.
Owner:BLUE CEDAR NETWORKS INC
Information processing apparatus and method, and storage medium
InactiveUS6981220B2Efficient and effectiveInformation can be presentedCathode-ray tube indicatorsMultiple digital computer combinationsInformation processingVirtual space
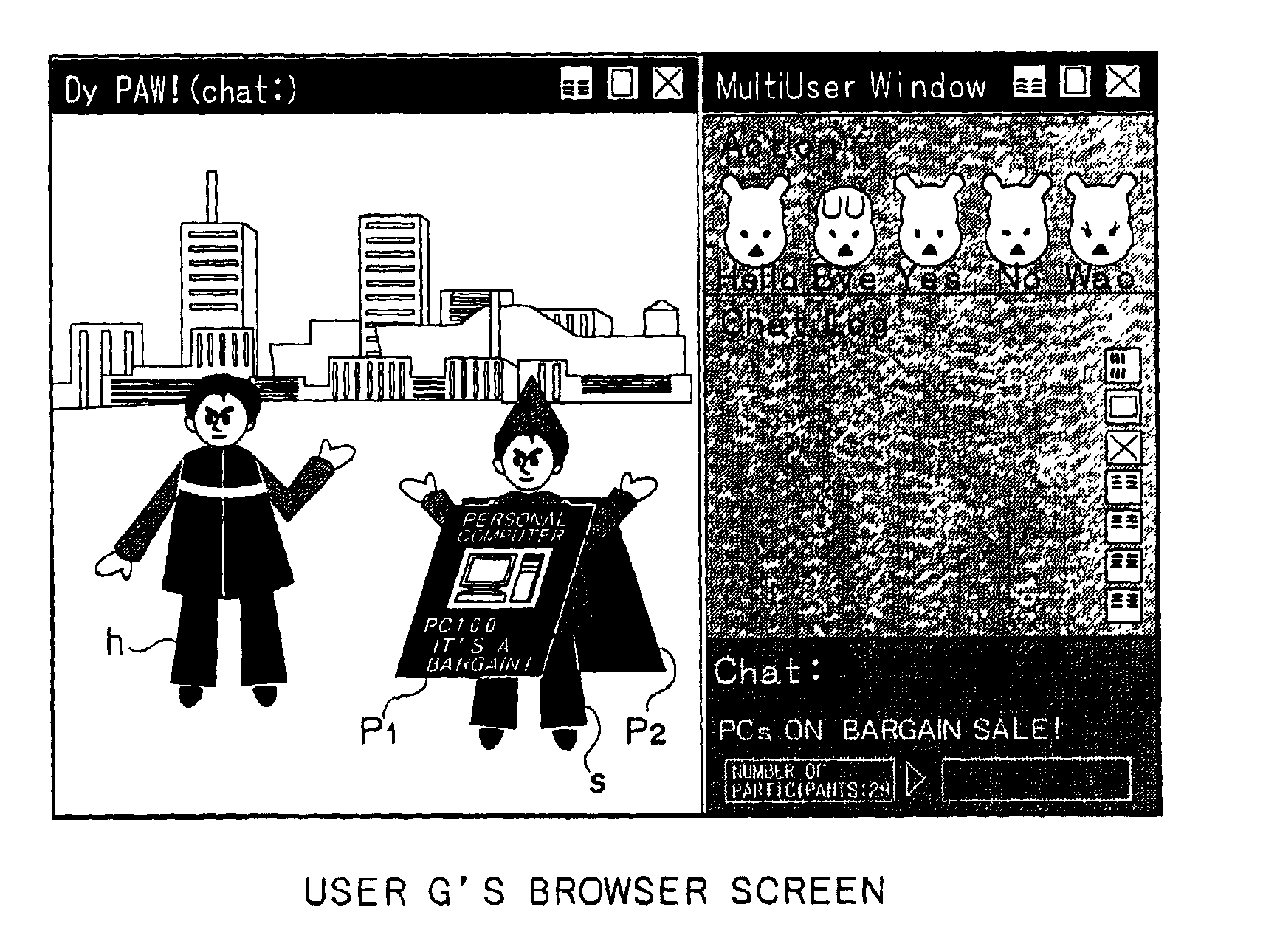
Disclosed is an information processing apparatus for controlling an application object moving autonomously in a shared virtual space in which avatars representing users of other information processing apparatuses are active. The apparatus comprises a distribution examining element for examining distribution of the active avatars in the shared virtual space, a coordinate controlling element for controlling coordinates of the application object in accordance with results of the examination by the distribution examining element and a display controlling element for controlling display of information by the application object controlled in coordinates by the coordinate controlling element.
Owner:SONY CORP
Monitoring and performance management of component-based applications
ActiveUS7627671B1Error detection/correctionDigital computer detailsManagement toolApplication software
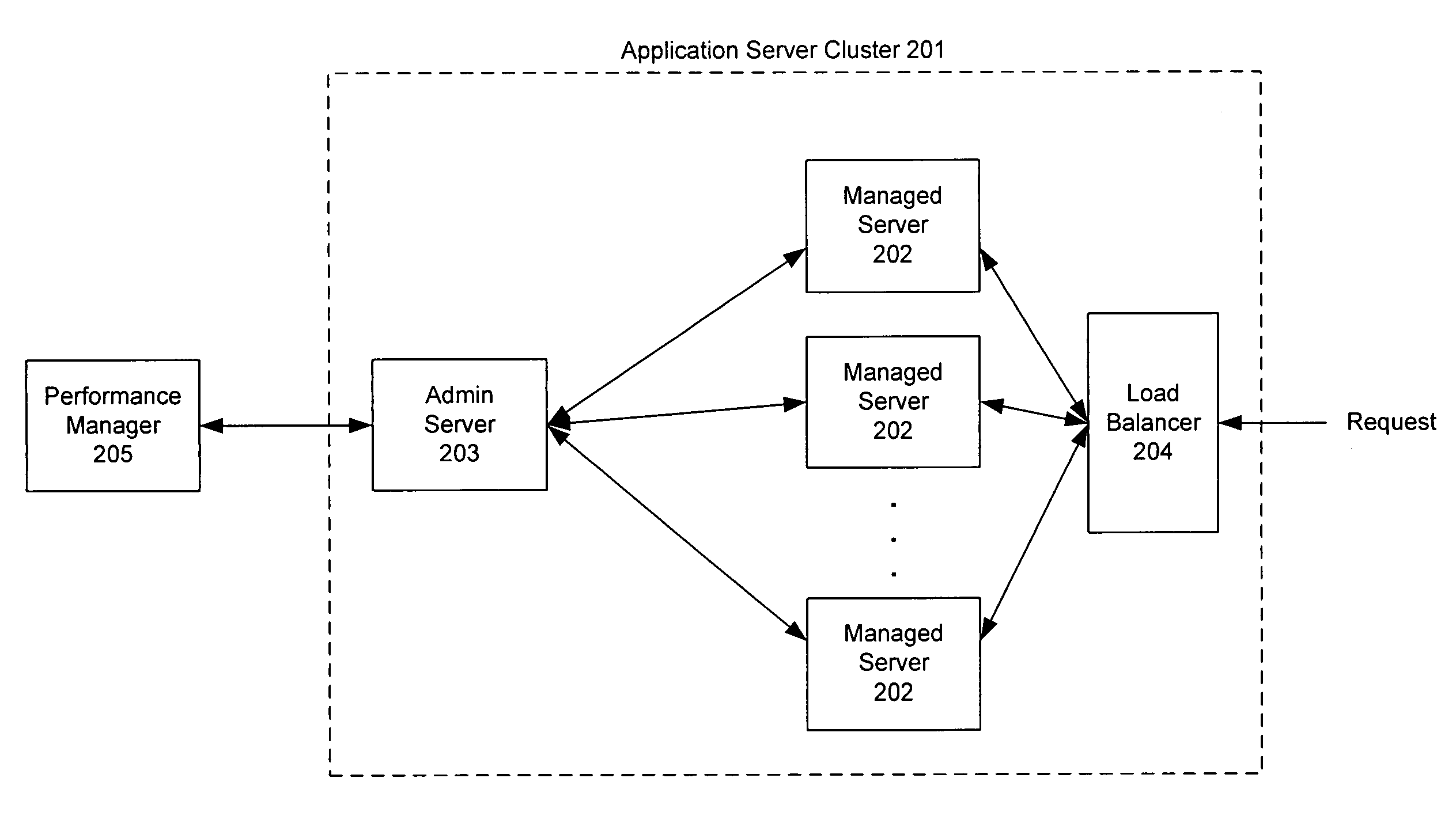
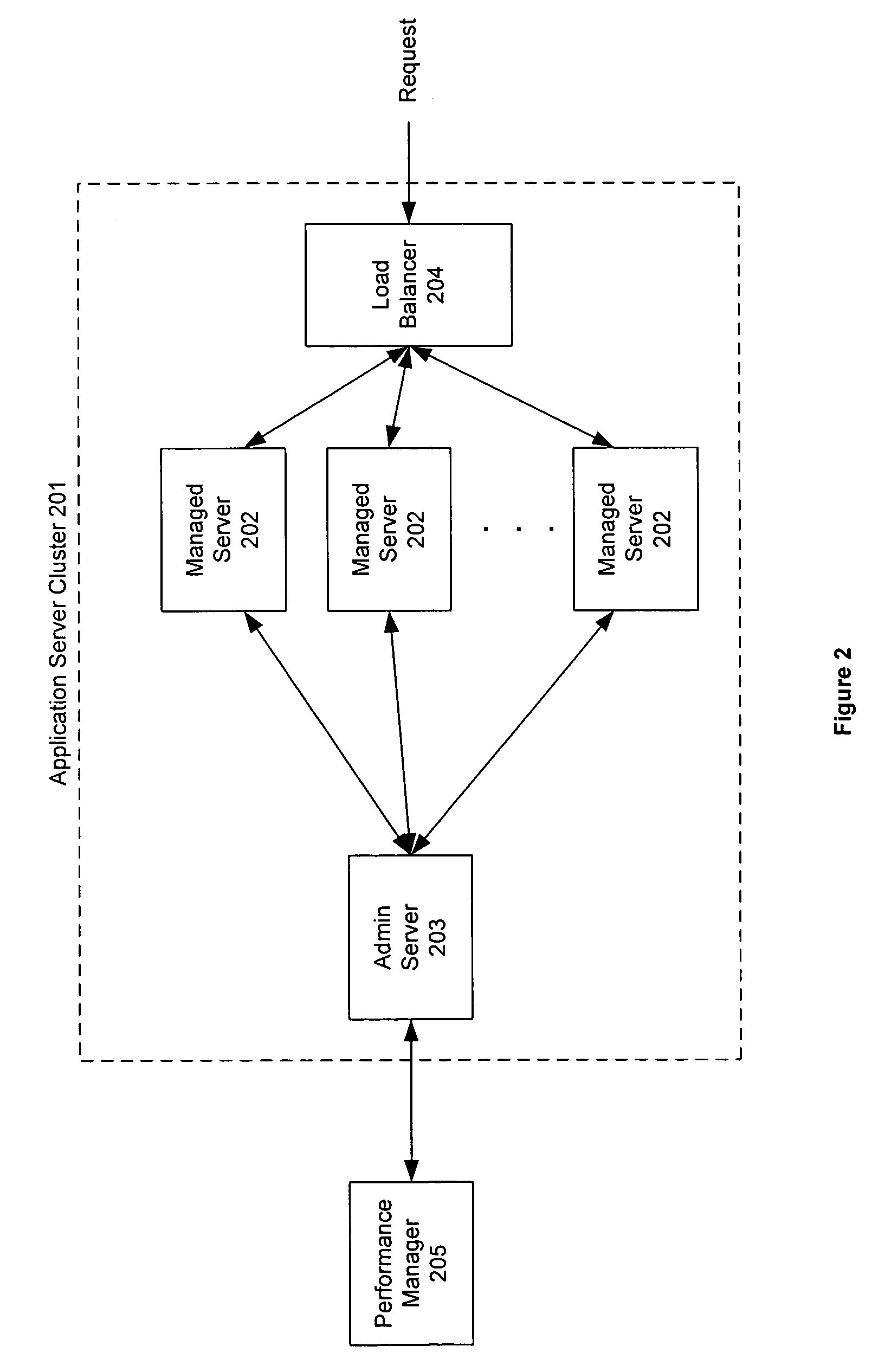
Invention manages underlying application objects that support implemented business functions. A performance manager accesses and interprets application metadata and execution environment metadata, using a hierarchical entity to model complex relationships between application abstractions, components and resources. The performance manager encodes common behavioral and architecture information in models resulting from analysis of component architecture standards, vendor application servers, development tools and administration tools. The performance manager conducts inter-component dependency and control flow analysis, for example by generating control flow graphs from application metadata and performing byte code analysis without access to application source code. The performance manager collects metrics from standardized and vendor-specific sources, instruments interpreters (such as the Java Virtual Machine), and collects and utilizes resource metrics, code performance metrics, configuration parameters, and transaction, failure and lifecycle events.
Owner:ORACLE INT CORP
Geographical restrictions for application usage on a mobile device
ActiveUS20140208397A1Digital data processing detailsComputer security arrangementsOperational systemObject code
Apps are secured or security-wrapped either before they are downloaded onto a device, such as a smart phone or tablet device, or after they are downloaded but before they are allowed to access the device operating system and cause any potential damage to the device. The app is secured before it is allowed to access the operating system of the device, thereby preventing the app from malicious behavior. App object code is substituted with security program object code, thereby creating a security-wrapped app. The app is provisioned with a geo-fencing policy which prevents execution of an app outside a pre-defined geographical area. If the device is within the defined area, the app is allowed to execute. The geographical area, such as a building or company campus, is defined using longitude and latitude coordinates and a location accuracy value. Device location is obtained using location / GPS services on the device.
Owner:BLUE CEDAR NETWORKS INC
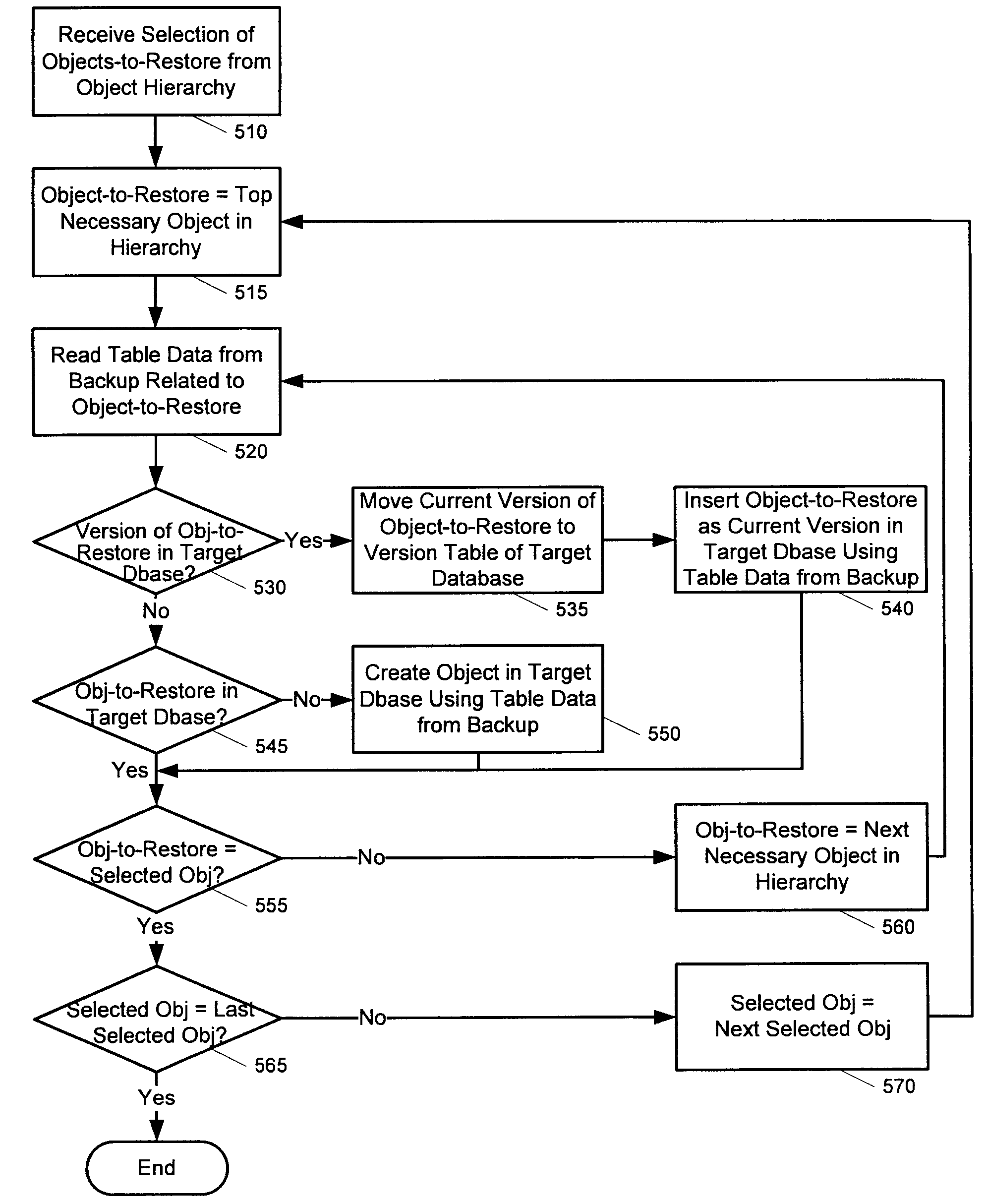
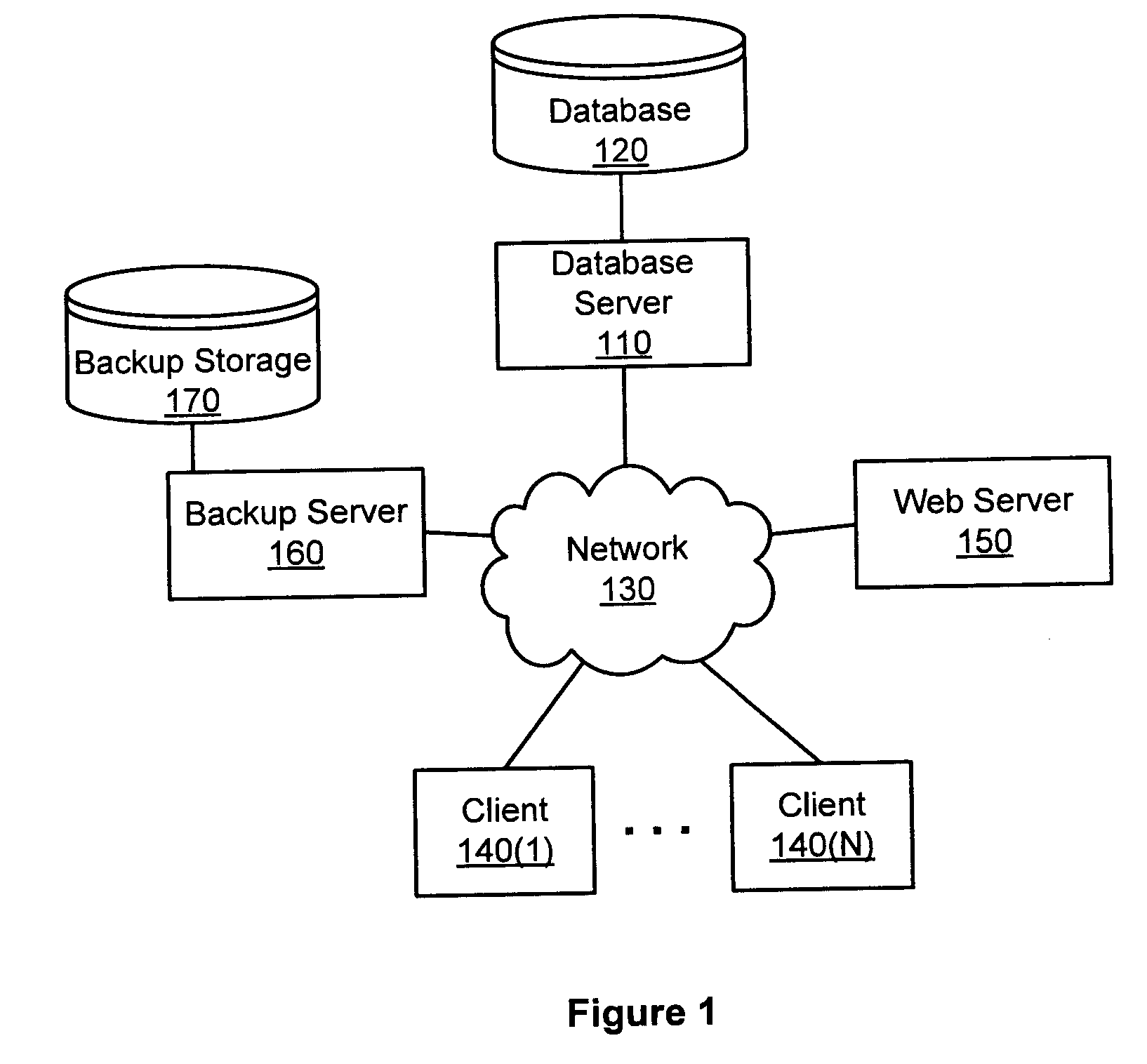
Backing up and restoring selected versioned objects from a monolithic database backup
ActiveUS20100082553A1Maintain relationshipMemory loss protectionDigital data processing detailsDatabase backupApplication software
A mechanism to selectively restore a version of an application object stored in a monolithic backup of a database, while maintaining hierarchical and other metadata relationships of the restored portion of the database, is provided. Embodiments of the present invention provide a method, system and computer-readable storage medium that provide a mechanism for receiving a request to restore a version of a selected object from among a plurality of backed up objects in a database backup, locating information associated with the selected object in the backup, and restoring the version of the selected object to a target storage area using information associated with the selected object. Aspects of the present invention use database table metadata gathered from the backed up database at the time the backup was created in order to locate the information associated with the selected object.
Owner:SYMANTEC OPERATING CORP
Glance and click user interface
A user interface includes a first region configured to provide information on and access to content applications of a device and services accessible via the device, a second region configured to provide information on and access to communication applications of the device and services accessible via the device, and a divider between the first area and the second area. The divider includes a time based segment that includes a movable icon. Each of the first and second region can be divided into a first section for creating new and available content and communication application objects, a second section for active content and communication application objects, and a third section for created / received / stored content and past / recent communication objects. The movable icon can be used to select sections for viewing the underlying objects and links.
Owner:NOKIA CORP
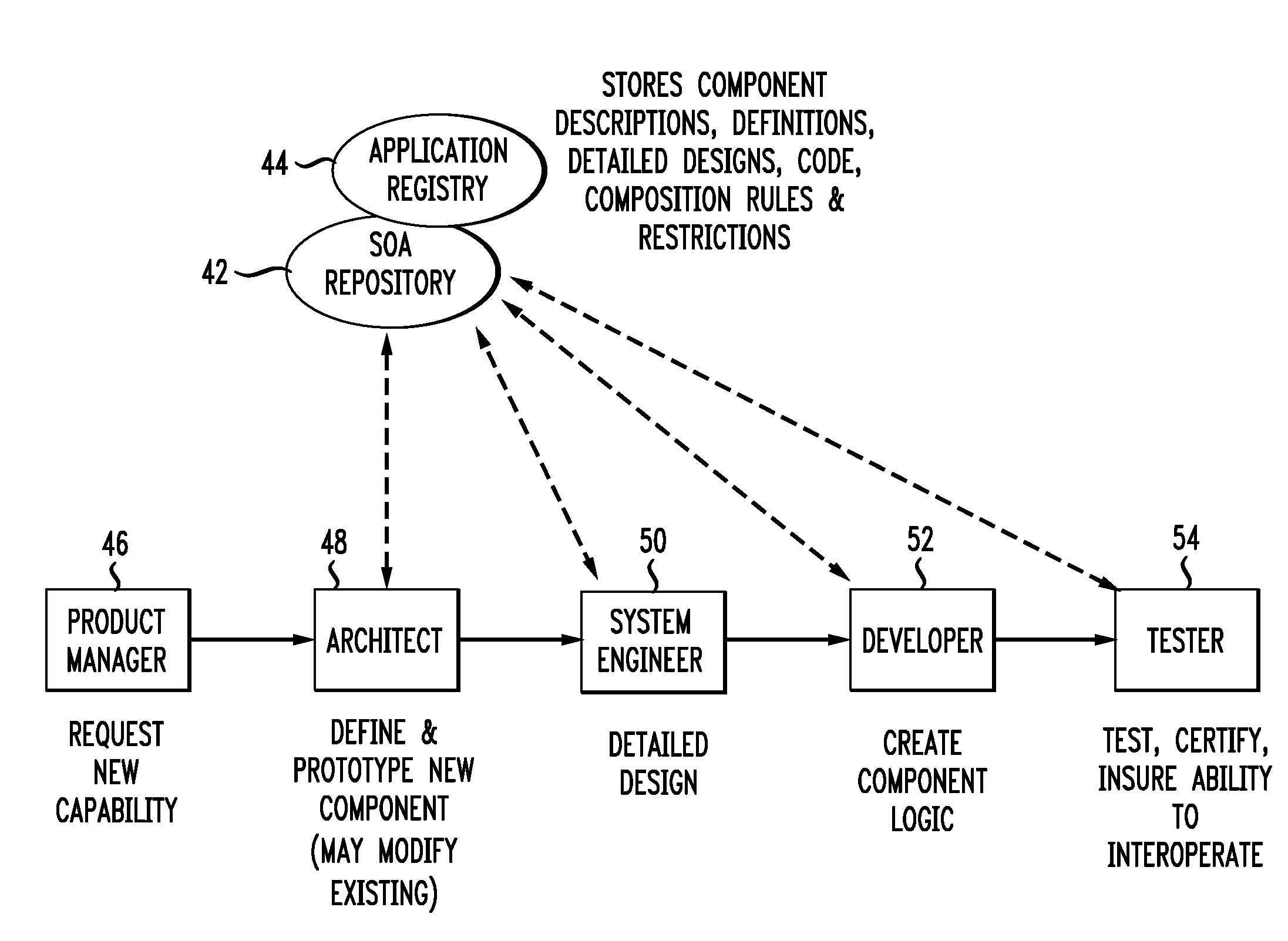
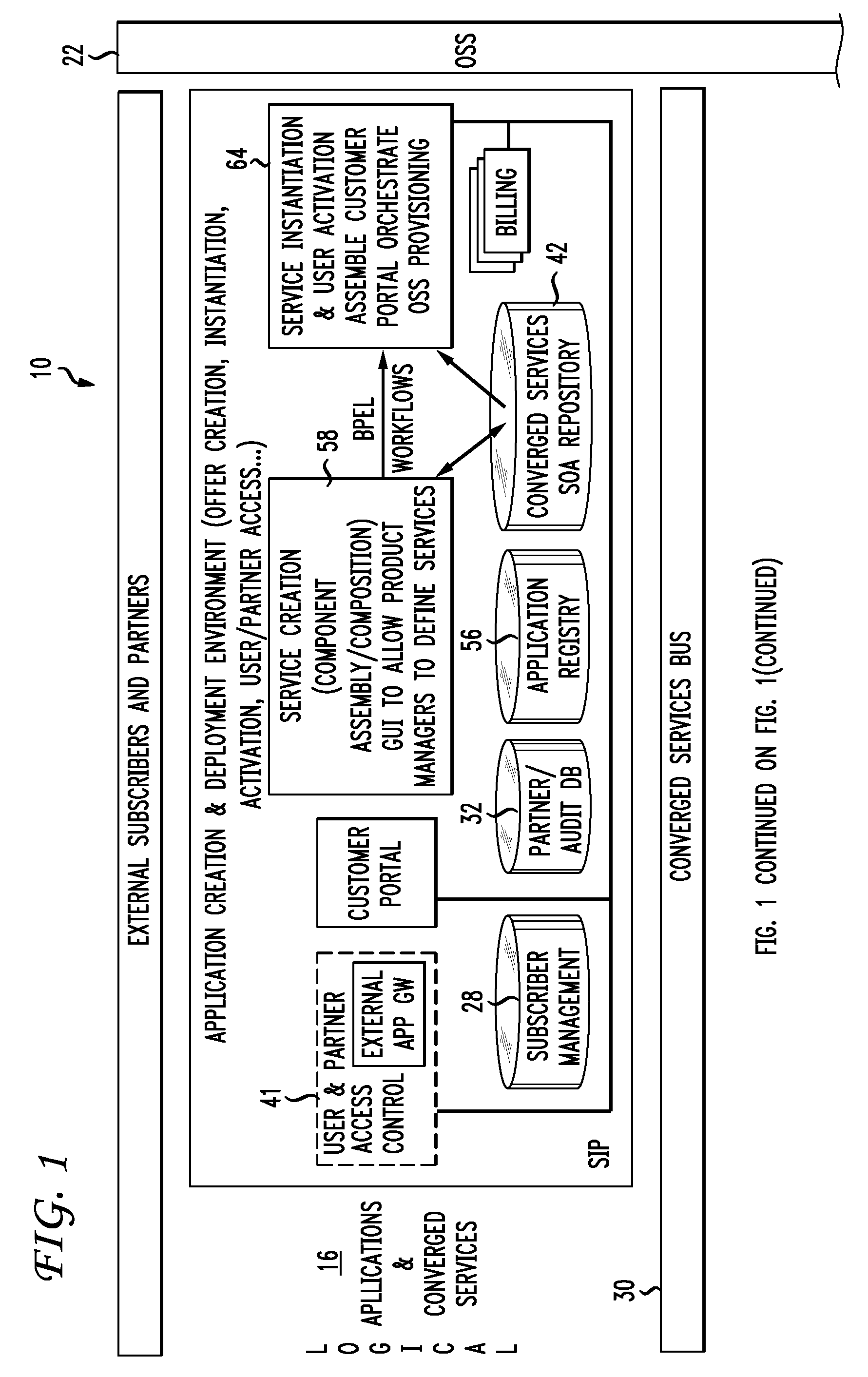
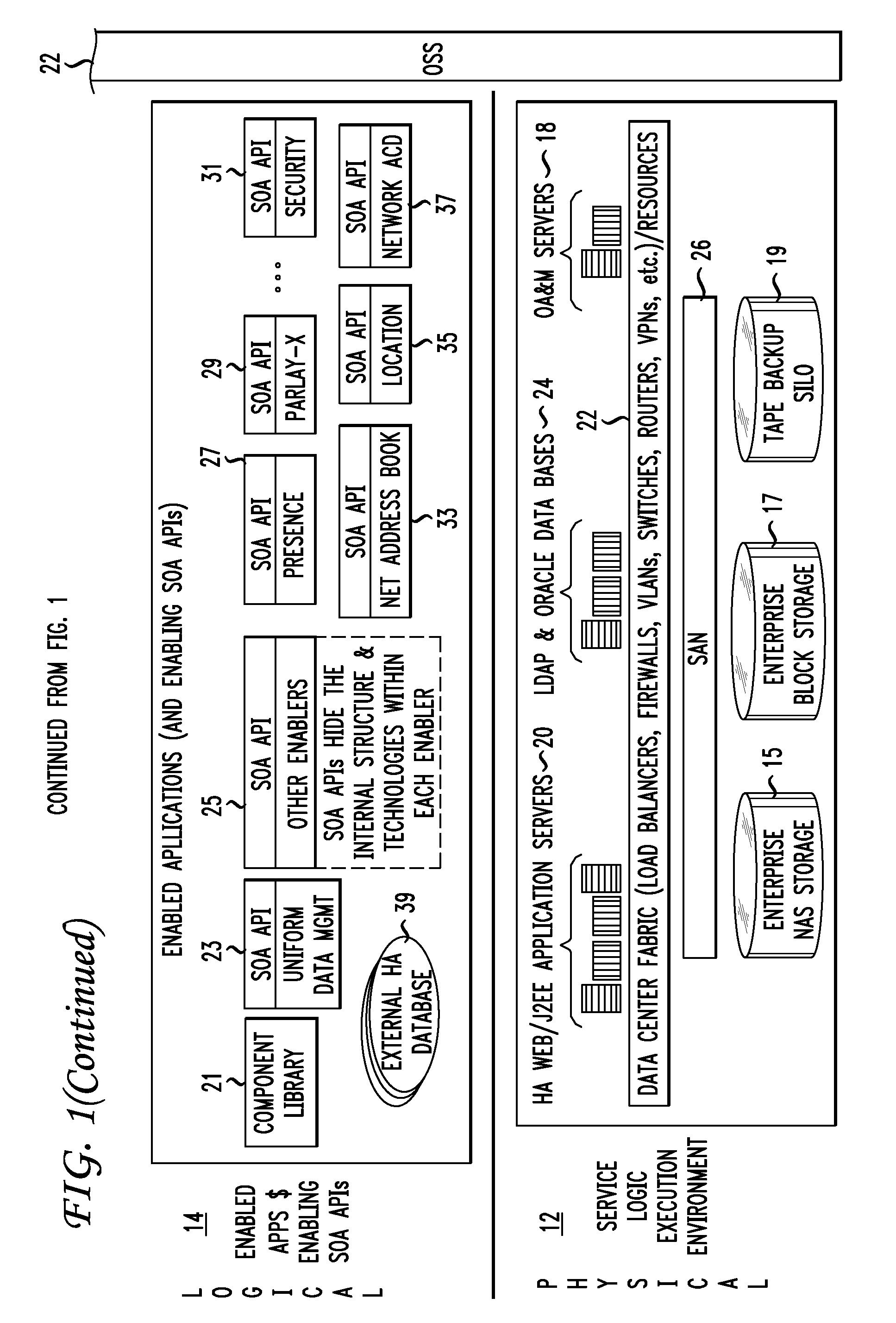
Aiding Creation of Service Offers Associated with a Service Delivery Framework
InactiveUS20090182565A1Rapid productionTightly coupledVisual/graphical programmingResourcesService provisionApplication software
A method of aiding creation of a service offer associated with a Service Delivery Framework (SDF) includes providing a plurality of reusable Application Objects (AOs) that may be associated with an Interactive Development Environment (IDE). The AOs are prototype customer facing service offers that include standardized functions supporting ordering, billing, management and monitoring. The AOs also include standardized event formats and configurable attributes that affect the behavior and pricing of service offers derived from the AOs. A Services Marketplace facilitates reuse of AOs and supports relationships between customers, application creators, service providers and OSS / BSS providers. A computer-readable medium includes instructions that when executed by a computing device aids in creation of a service offer associated with a SDF by providing a plurality of reusable Application Objects (AOs) in the context of a services marketplace.
Owner:AT&T INTPROP I L P
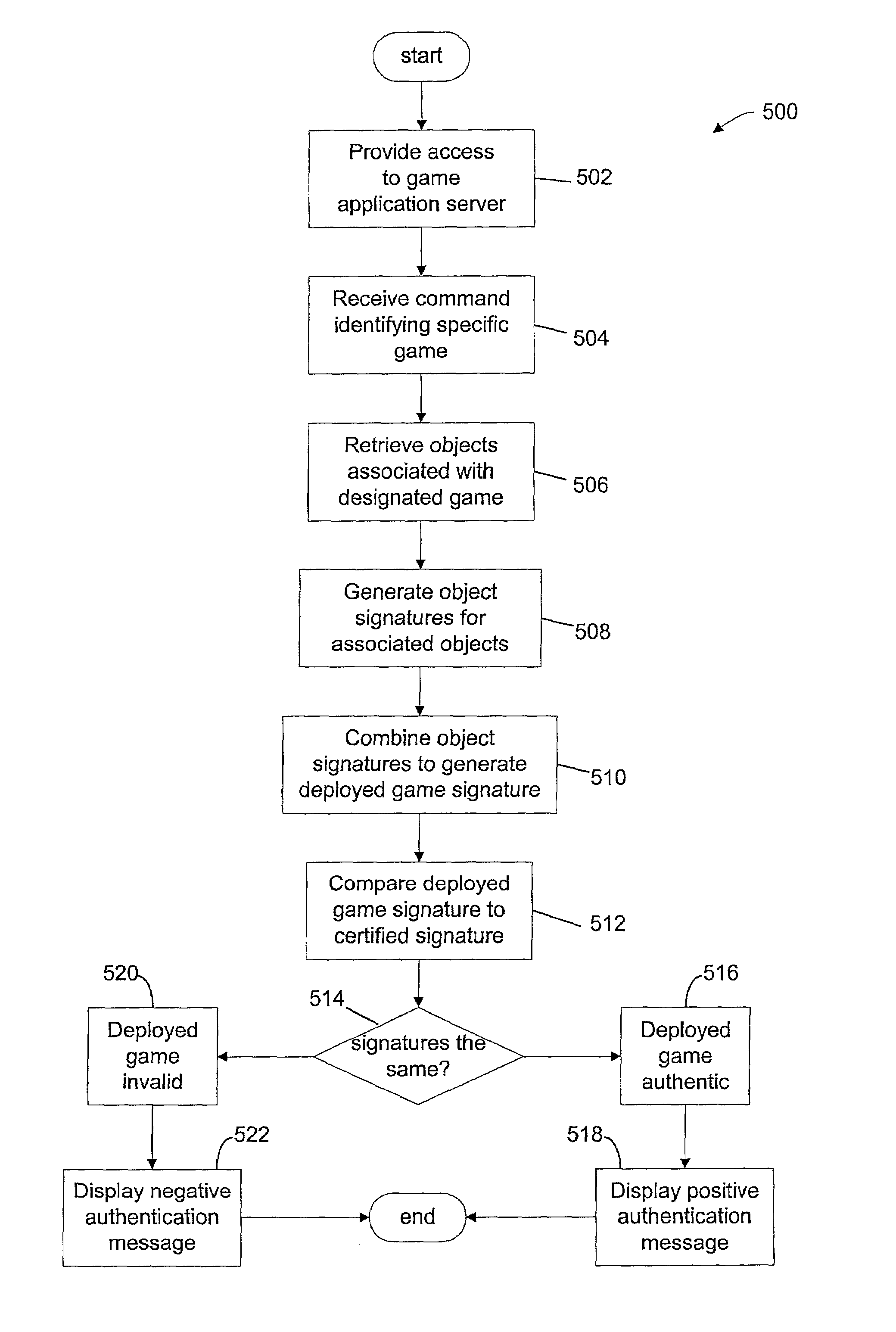
Digital identification of unique game characteristics
ActiveUS7162036B2User identity/authority verificationSecret communicationApplication softwareHuman–computer interaction
Owner:IGT
Customizable system for creating supervisory process control and manufacturing information applications
ActiveUS20070006149A1Enhanced product offeringIntegration changesSoftware designSoftware simulation/interpretation/emulationThird partyDocumentation procedure
An extensible base process control and manufacturing information application development and execution software suite is disclosed that facilitates streamlined third party (e.g., OEM) development of derivative applications for particular vertical markets. The suite includes an object design toolkit that provides object template derivation tools for accessing and editing a set of base object templates. The objects derivable from the base templates include at least application objects deployed upon lower level hosting component objects of a supervisory process control and manufacturing information application. The toolkit also includes development tools for creating new base object templates that are added as extensions of the set of base object templates. In addition to the toolkit, the suite includes a set of marketing package customization tools facilitating seamlessly integrating changes by developers to the extensible base development and execution software suite. The marketing package customization tools include electronically editable base user documentation.
Owner:SCHNEIDER ELECTRIC SOFTWARE LLC
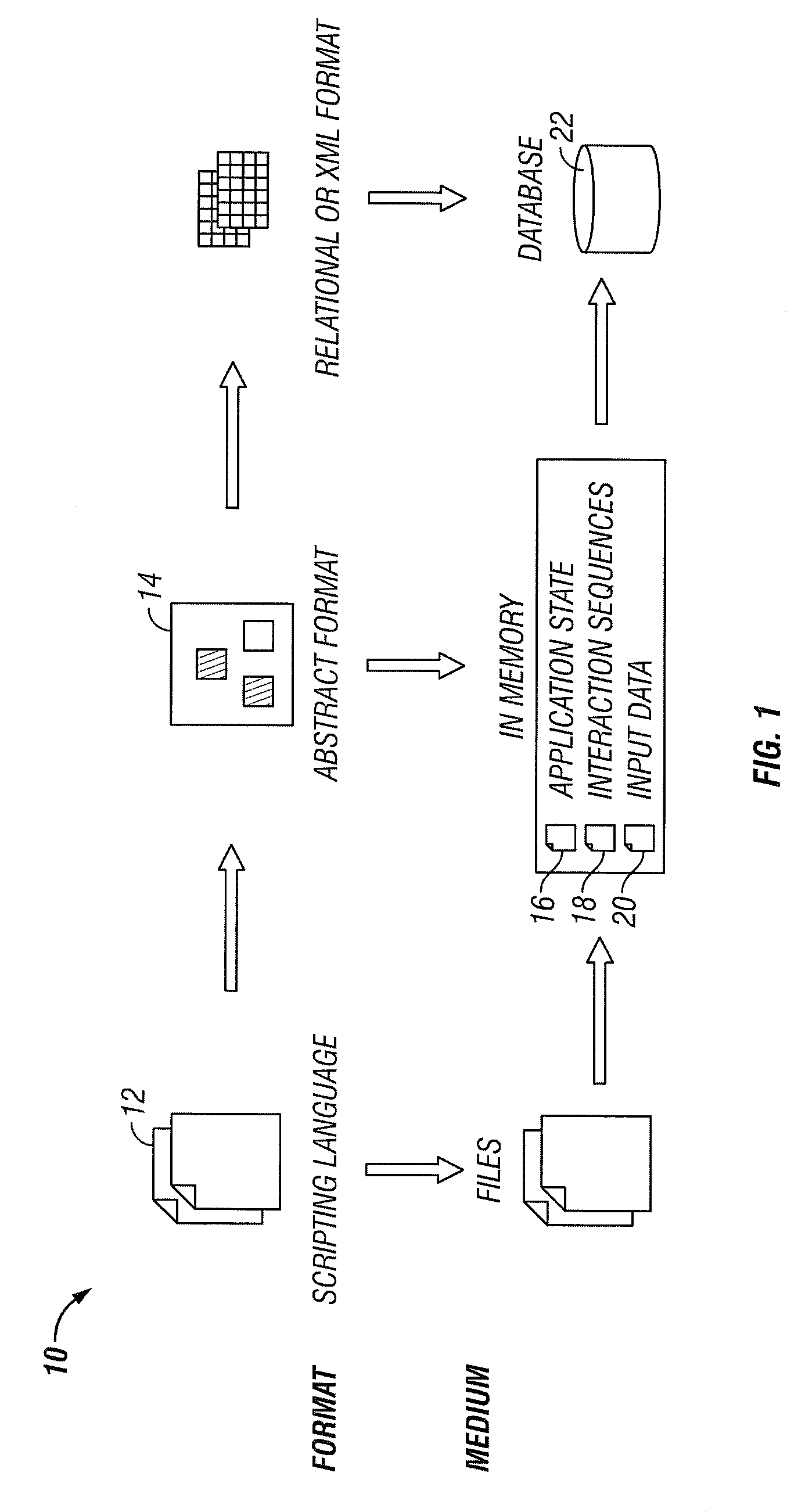
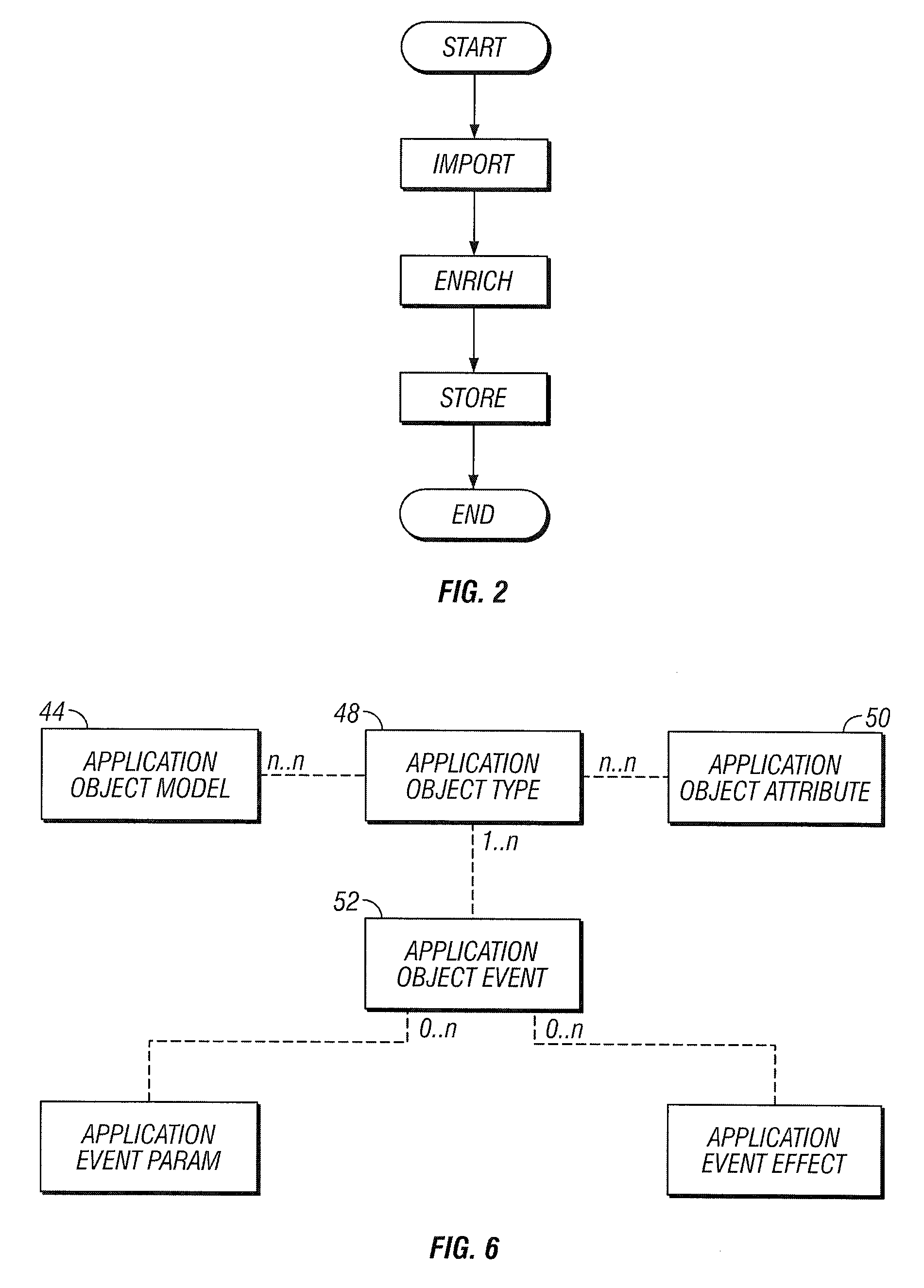
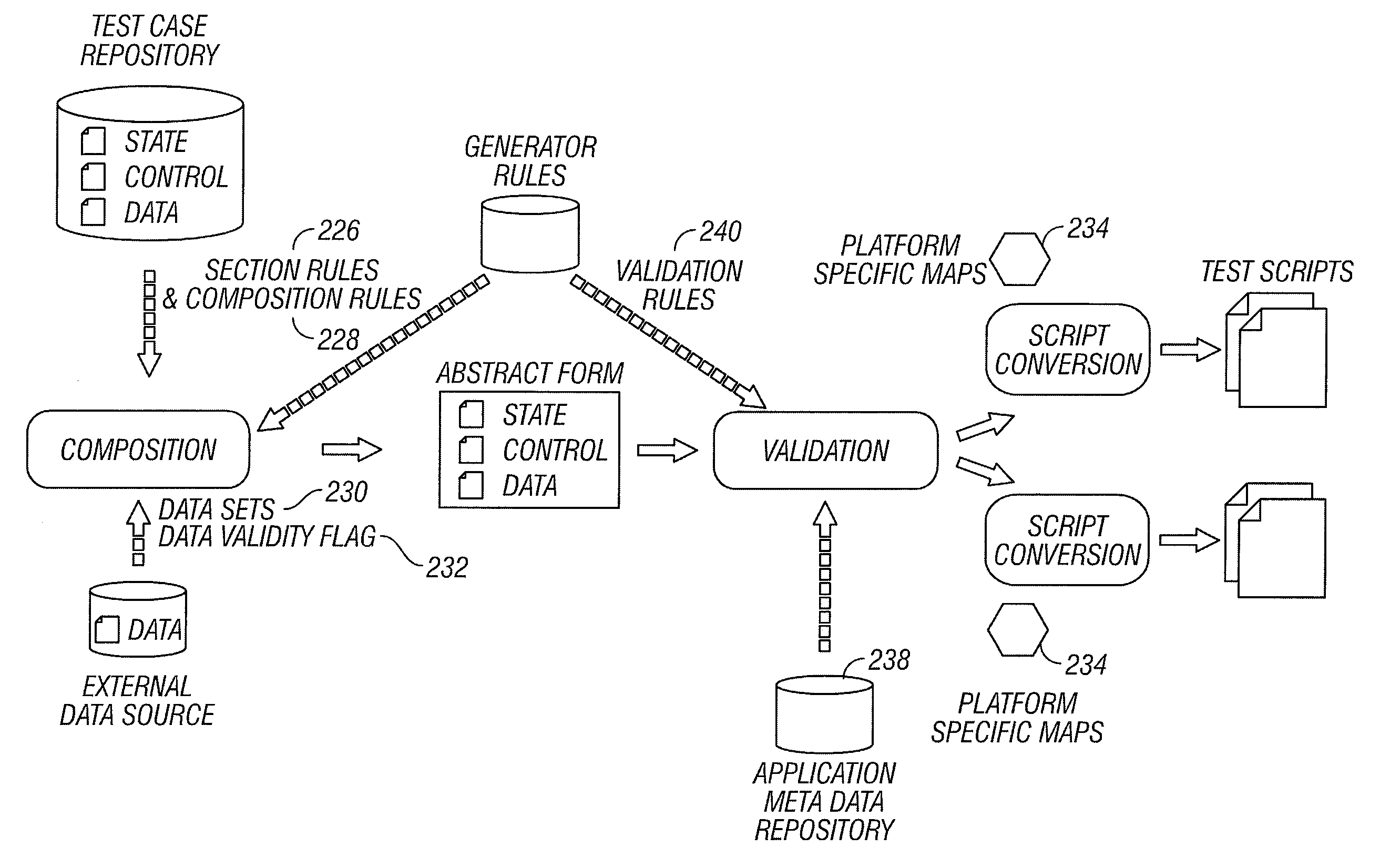
Method and system for conversion of automation test scripts into abstract test case representation with persistence
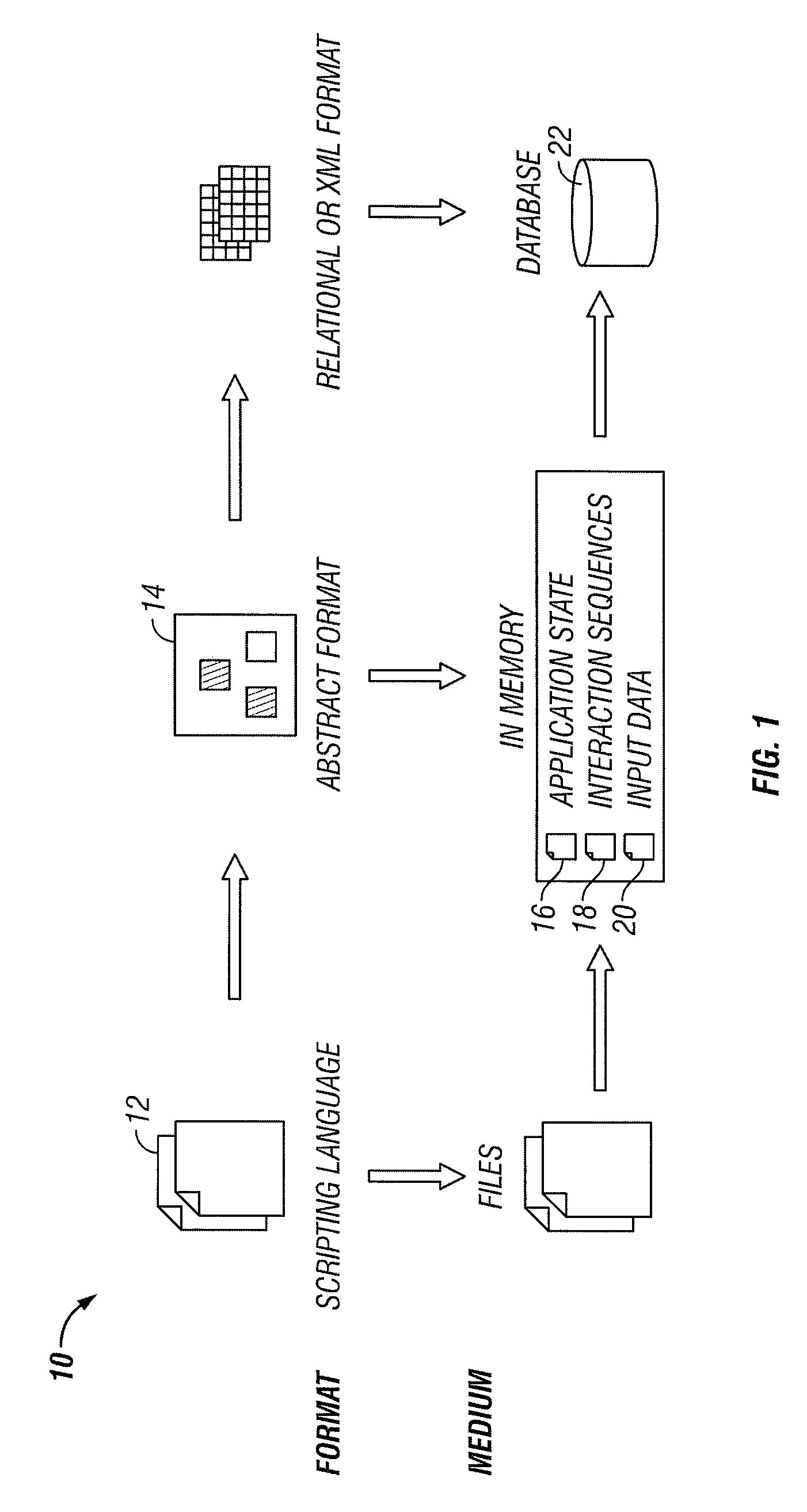
A general technique using semantic analysis is provided that can be used for converting a specific automation test script (and its underlying test case), generated from generally available or proprietary test automation tools, into an abstract test case representation. The abstract test case representation is based on a test case representation model that includes application states (state information), external interaction sequences (control flow information) and input data. The abstract representation in essence provides a platform independent representation of test cases. An application object model provides the representational capabilities required for capturing structural and behavioral properties of the application under test. The abstract test case representation can be validated against and further enriched by specific object information from an application metadata repository. Finally, object information and input data can be separated from control flow information to provide automatic parameterization of the test script.
Owner:SILICON VALLEY BANK
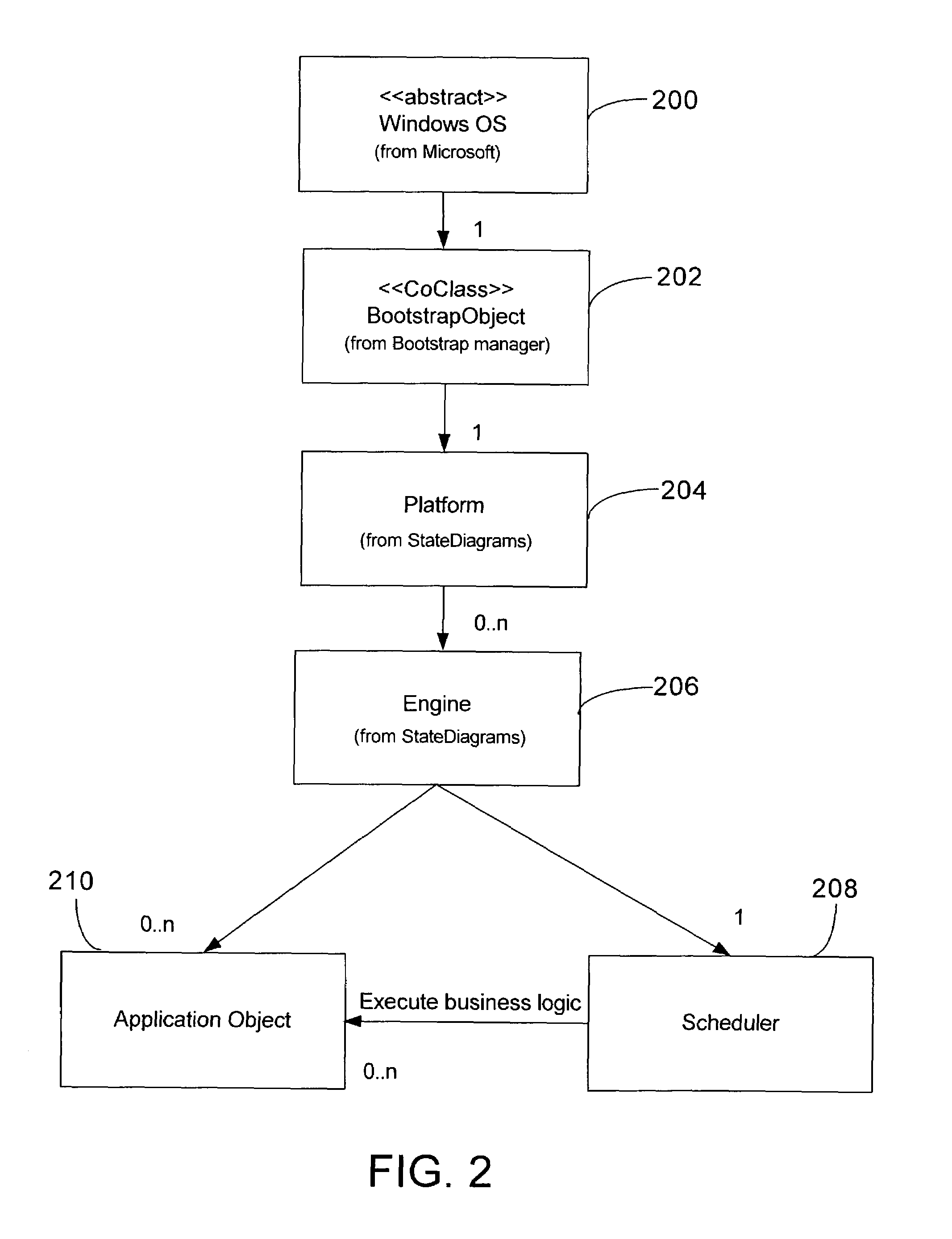
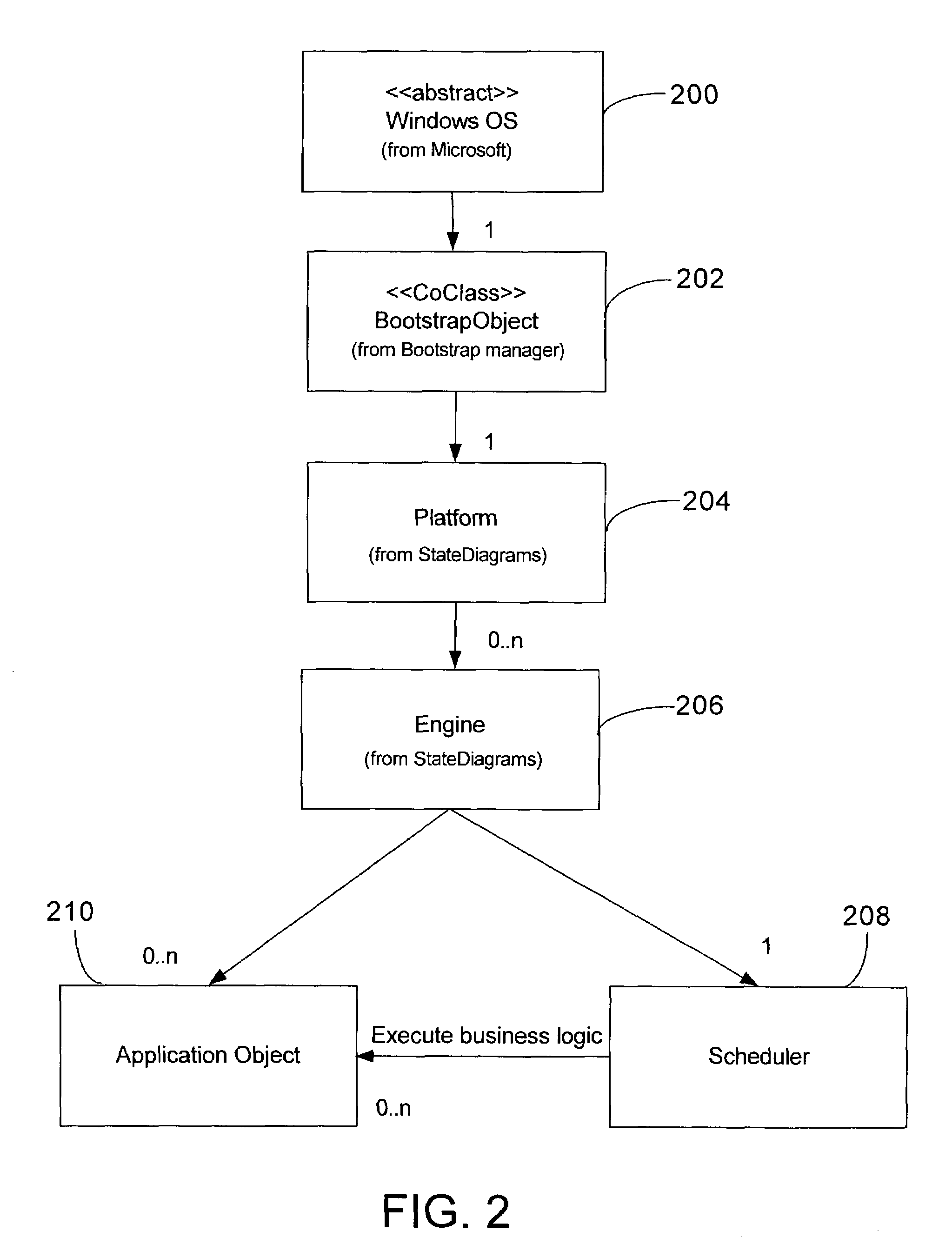
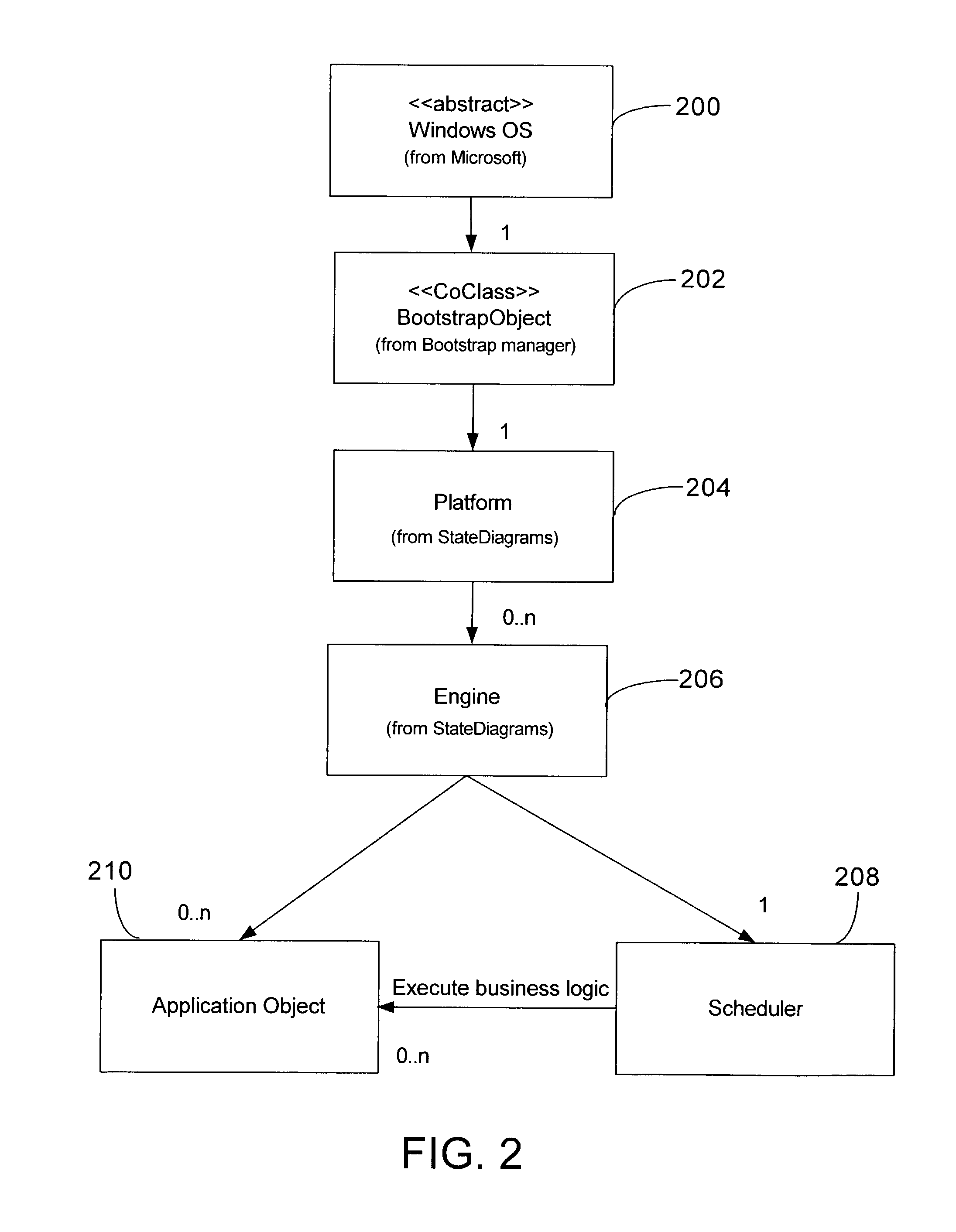
Supervisory process control and manufacturing information system application having an extensible component model
InactiveUS7707550B2Improve design productivityFacilitates specifying instancesInterprogram communicationElectric testing/monitoringProduction rateSoftware engineering
A template-based supervisory process control and manufacturing information application development facility is disclosed that includes a number of time-saving application development tools that significantly enhance design productivity and allow re-using of previously developed application building blocks. The development facility includes an application object template library that stores a set of previously defined application object templates. The template library is accessed by developers through a configuration utility that facilitates specifying instances of the set of previously defined application object templates to be included in an application. Thereafter, application objects are instantiated from the selected ones of the set of previously defined application object templates in a build of the specified application.
Owner:SCHNEIDER ELECTRIC SOFTWARE LLC
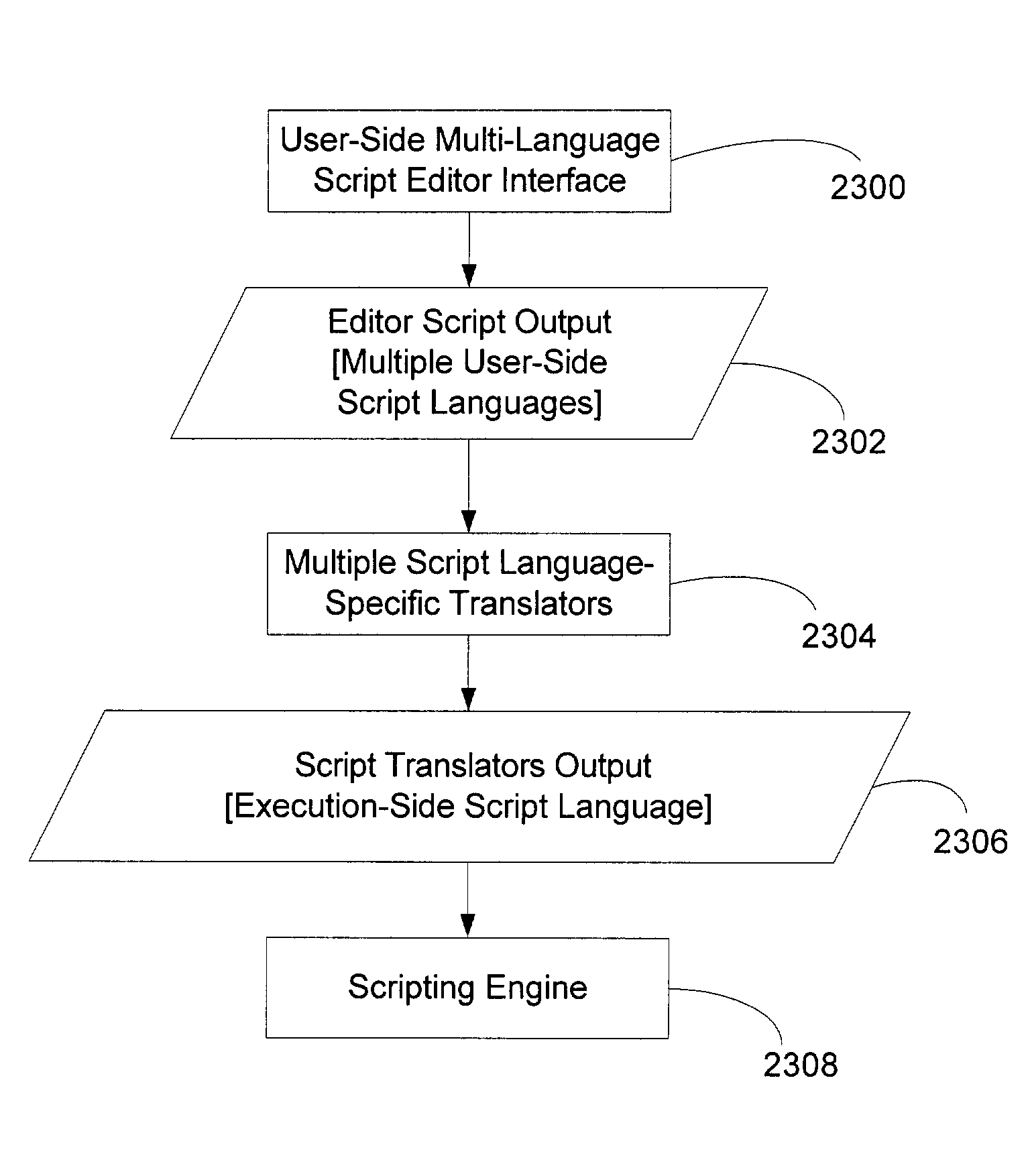
Process control script development and execution facility supporting multiple user-side programming languages
A supervisory process control and manufacturing information application development and execution system is disclosed that supports the execution of application object scripts derived from multiple different scripting languages. In particular, the system includes a script editor interface that enables submission / specification of scripts for application objects. The script editor interface supports multiple distinct user-side script languages (e.g., user-supplied script text). A script translation component that receives the user-side script includes routines for rendering execution-side script (executable by a script engine) from source script rendered by the script editor and written according to any of a set of user-side script languages supported by the script translation component. The translator supports at least a first scripting language and a second scripting language. Finally, an execution portion of the system includes an engine for processing the commands within the translated output execution-side script generated by the script translation component.
Owner:SCHNEIDER ELECTRIC SOFTWARE LLC
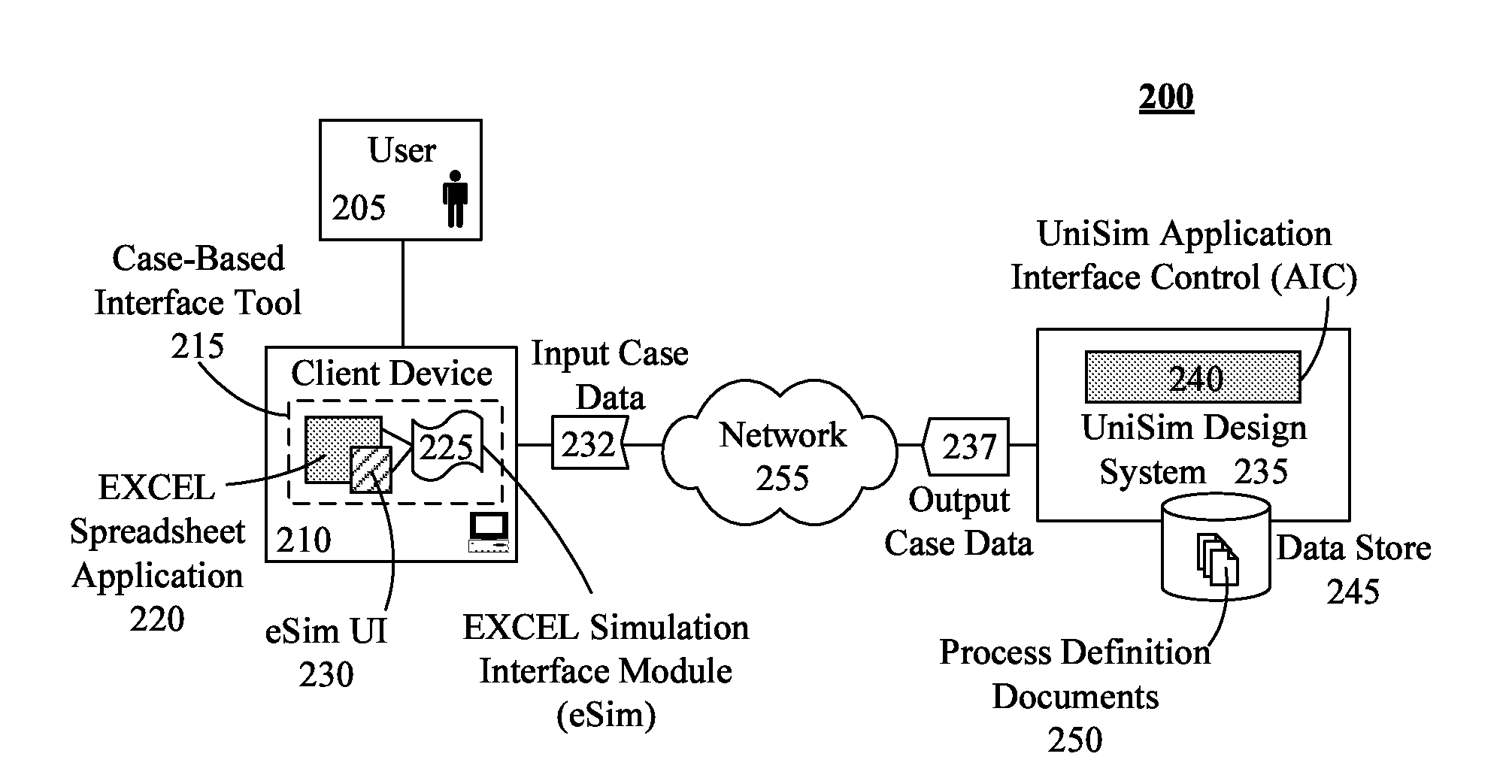
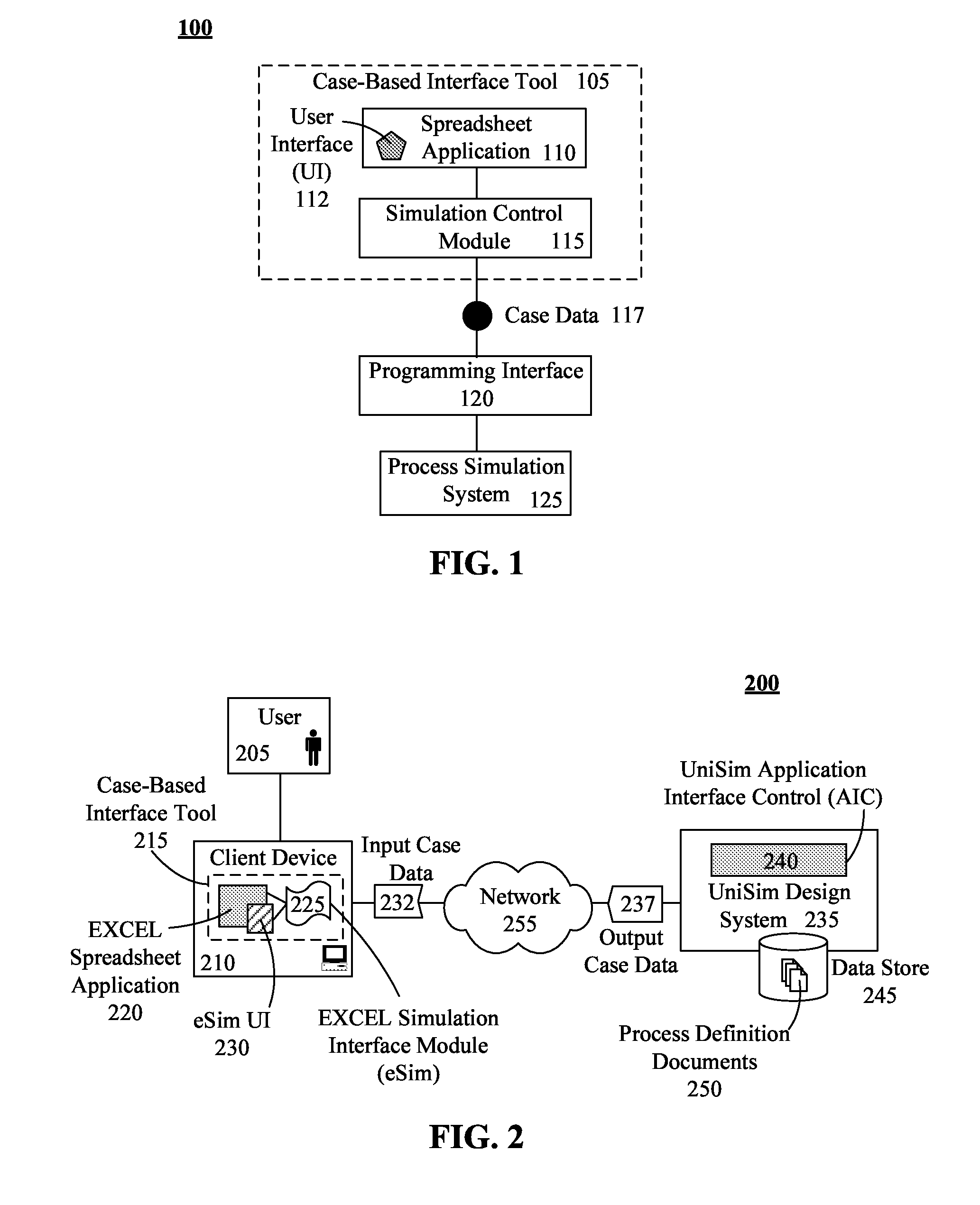
Utilizing spreadsheet user interfaces with flowsheets of a cpi simulation system
InactiveUS20100262900A1Shorten the timeSimulator controlAnalogue computers for chemical processesElectronic formParallel computing
A simulation system includes at least one processor configured to execute a computer program product, stored upon a storage medium. The computer program product includes a spreadsheet application, a process simulation application, and an integration tool (e.g., eSim), where the spreadsheet application and the process simulation application are discrete, stand alone products. The process simulation application can simulate chemical processes using at least one flowsheet, which models a general flow of chemical plant processes and equipment. The integration tool can map process simulation application objects and properties to spreadsheet application objects, can convey information between mapped objects, can perform case management functions, and can perform orchestrated calculation functions.
Owner:HONEYWELL INT INC
Display apparatus and touch detection apparatus
ActiveUS20100295804A1Increase frequencyLower latencyStatic indicating devicesNon-linear opticsElectricityEngineering
A display apparatus includes: a display face; a display function layer adapted to vary display on the display face in response to an inputted image signal; a plurality of driving electrodes disposed separately in one direction; a detection scanning control section configured to apply a detection driving voltage to some of the plural driving electrodes and carry out detection driving scanning while shifting an application object of the detection driving voltage in the one direction on the display face and then control the detection driving scanning such that jump shift of carrying out shift with a pitch of twice or more times a driving electrode pitch is included; and a plurality of sensor lines disposed separately in a direction different from the one direction and responding to touch or proximity of a detection object with or to the display face to exhibit an electric variation.
Owner:JAPAN DISPLAY INC
Method and system of providing access to various data associated with a project
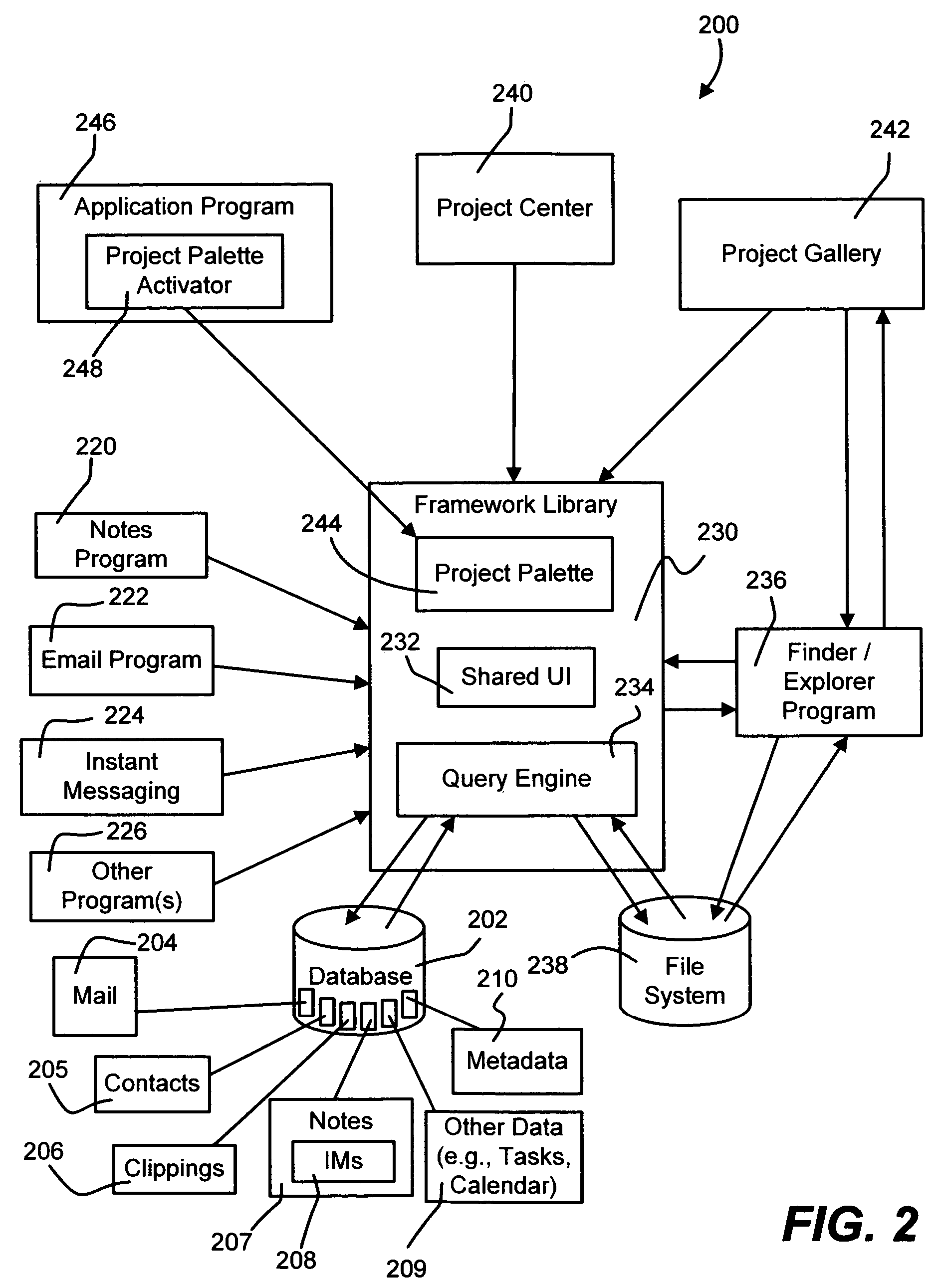
InactiveUS20060047811A1Digital computer detailsData switching networksWord processingProject management
Described is a system and method that enables project management across application programs, including an email program, calendar program, spreadsheet program, word processing program, note taking program and others. A central project-related view provides access to project-related data items and may display a schedule, a task list of tasks filtered as being relevant to a project, a note page related to a project, and emails relevant to the project. In addition, other application objects (file, documents, presentations and spreadsheets) are also captured in the view and presented for easy access. Metadata including a project identifier is maintained in a database for the various data items, allowing rapid location of the data items related to a project via query techniques. A project palette allows access to the items from within another application program, and a project gallery allows a user alternative access to the files related to a project.
Owner:MICROSOFT TECH LICENSING LLC
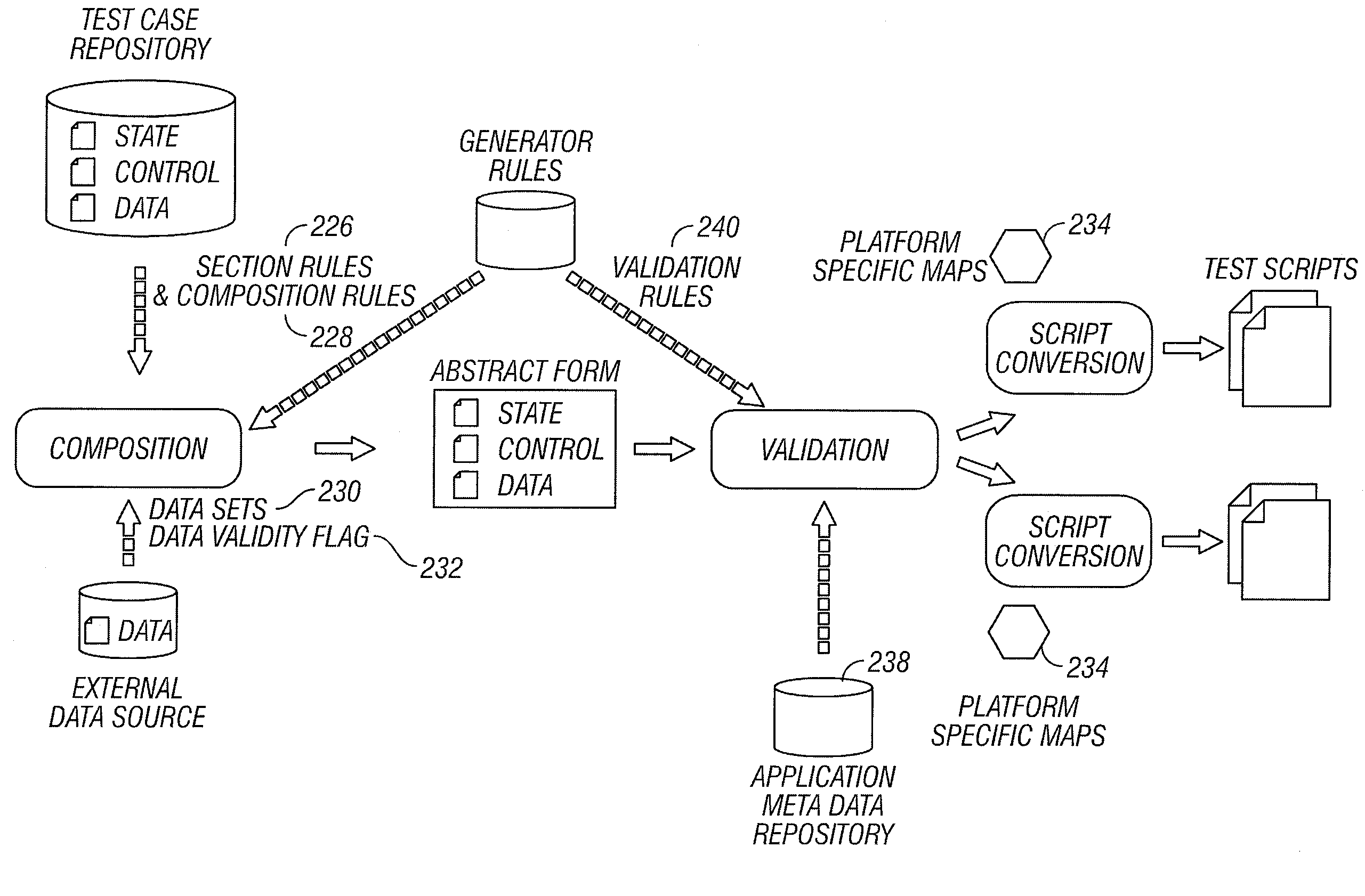
Method and system for rule-based generation of automation test scripts from abstract test case representation
A general rule-based technique is provided for generating a test case from an abstract internal test case representation. The abstract internal test case representation is based on a test case representation model that includes application states (state information), external interaction sequences (control flow information) and input data. The abstract representation in essence provides a platform independent representation of test cases. An application object model provides the representational capabilities required for capturing structural and behavioral properties of the application under test. Rules can be specified to define which application states (state information), external interaction sequences (control information) and input data sets should be used in the generation of the test case. A technique based on platform mapping is provided to convert a test case into an automation test script for any specific test script execution environment for any specific application platform.
Owner:SILICON VALLEY BANK
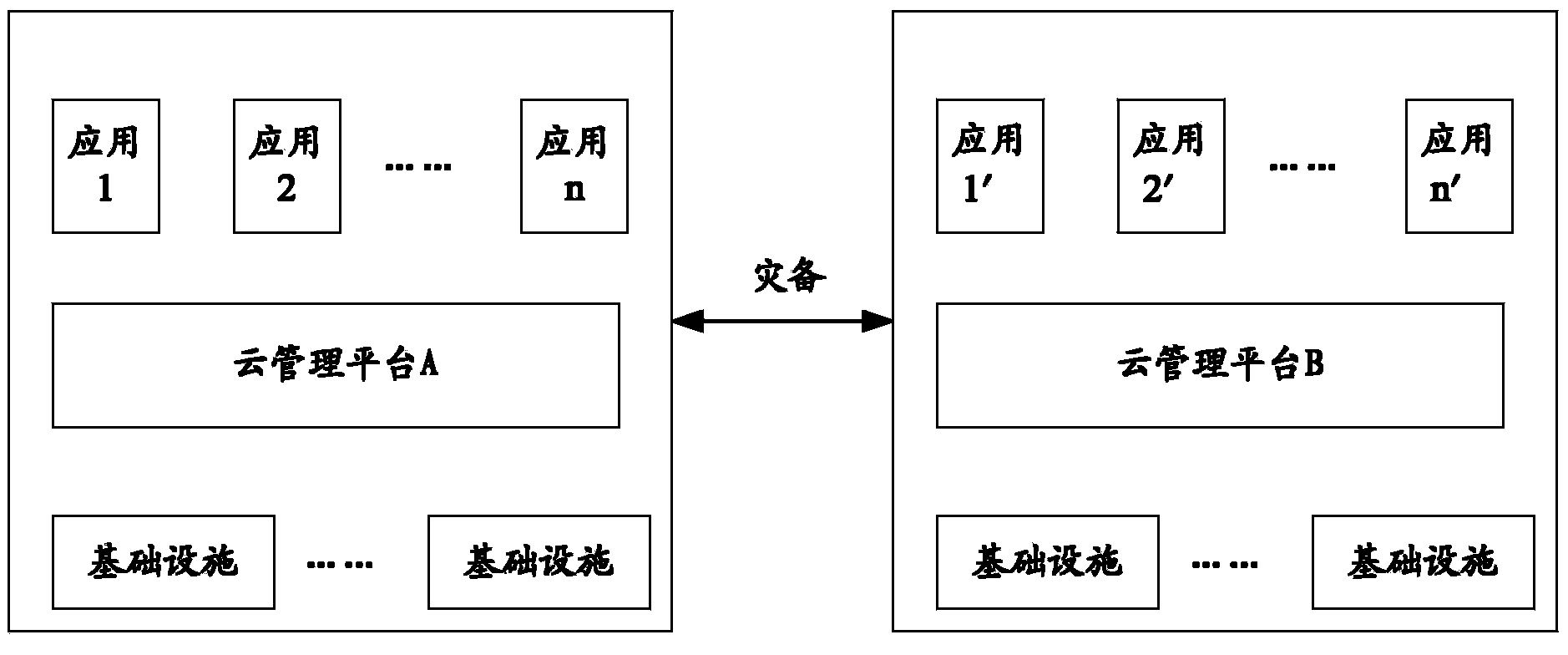
Disaster recovery data center configuration method and device under cloud computing framework
ActiveCN104137482AError detection/correctionData switching networksInformation repositoryResource information
The invention relates to the communication and information technical field, and especially relates to a disaster recovery data center configuration method and device under a cloud computing framework, and aims to solve the problems of poor flexibility of an artificial planning disaster recovery DC mode, and system total management is inconvenient; the method comprises the following steps: receiving a disaster recovery DC configuration request aiming at a set network service; obtaining affinity and / or anti-affinity relation information between application objects and supporting the set network service from an application object affinity relation information data center according to the disaster recovery data center DC configuration request, wherein the application objects with affinity relation can be deployed in the same DC, and the application objects with anti-affinity relation are deployed in different DC; selecting the disaster recovery DC for the set network service from the deployed DCs according to the disaster recovery source information of the deployed DCs and the obtained affinity and / or anti-affinity relation information.
Owner:HUAWEI TECH CO LTD
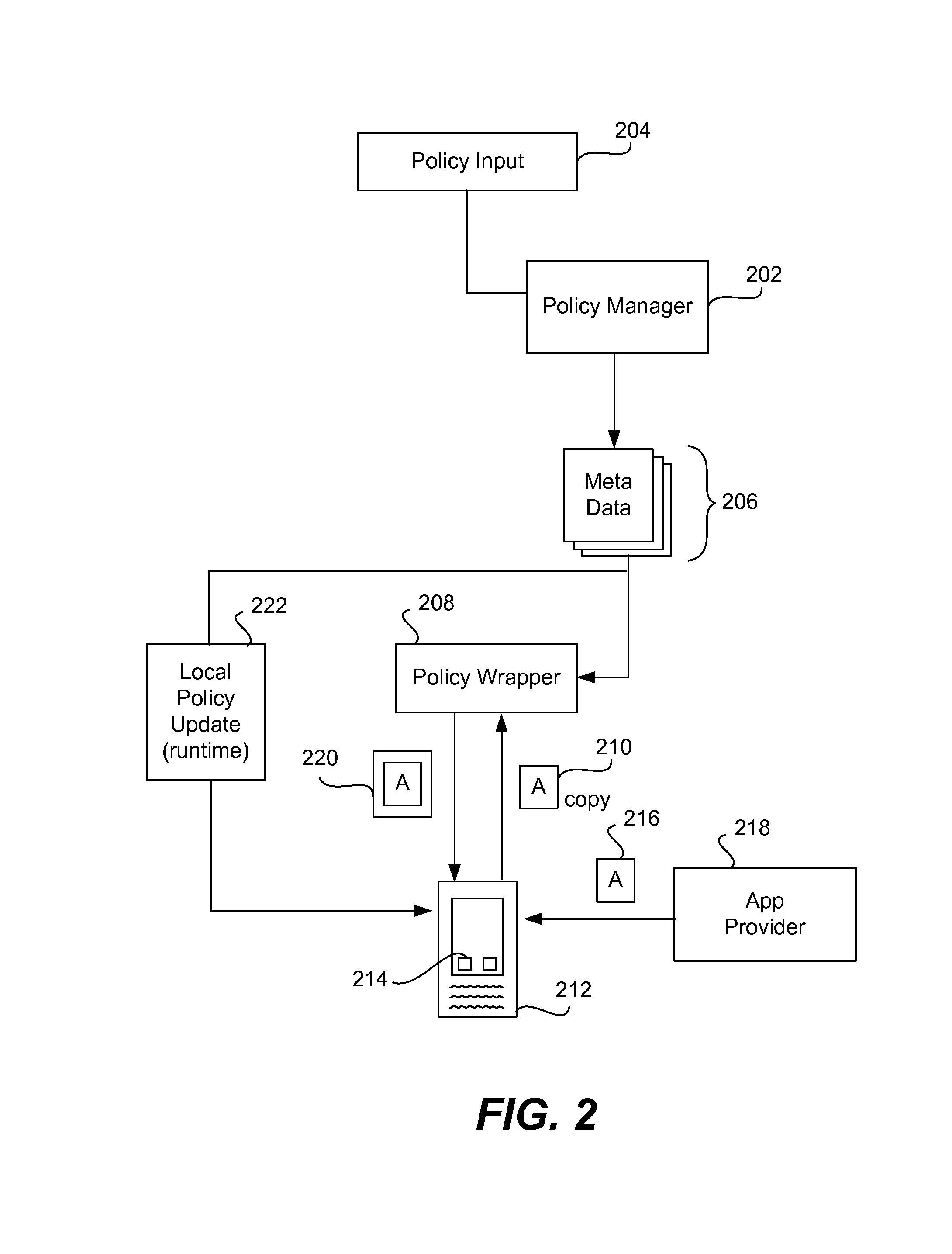
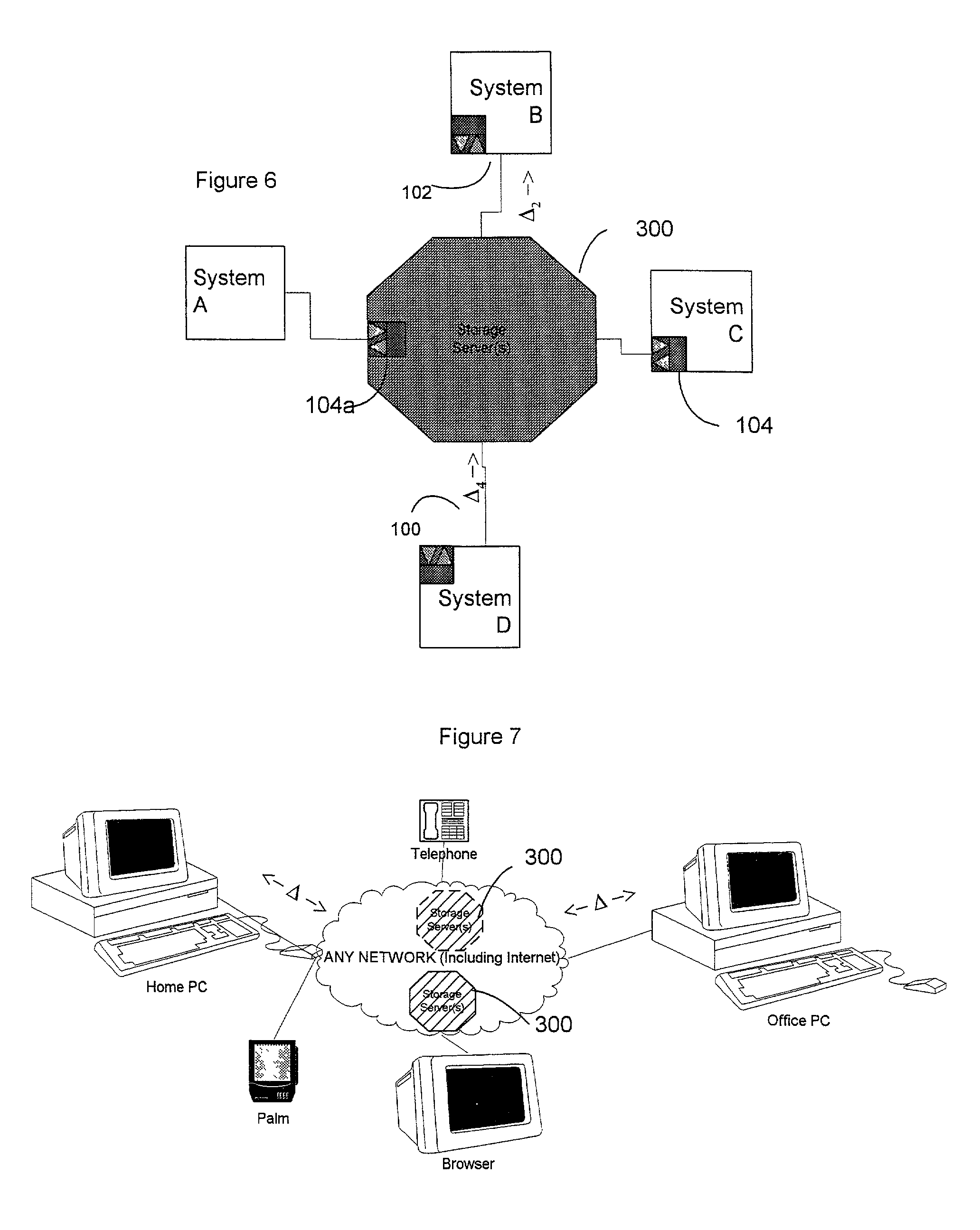
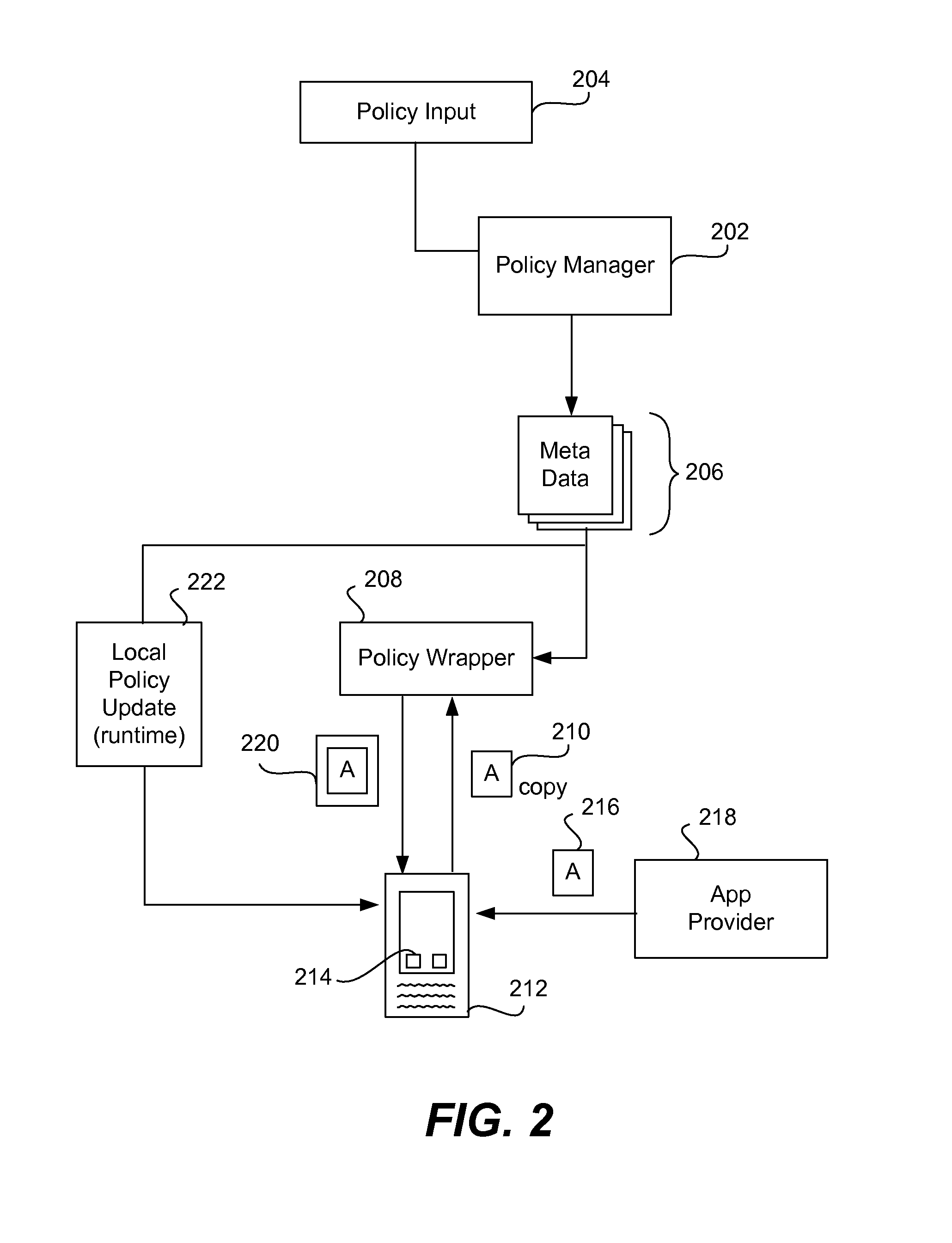
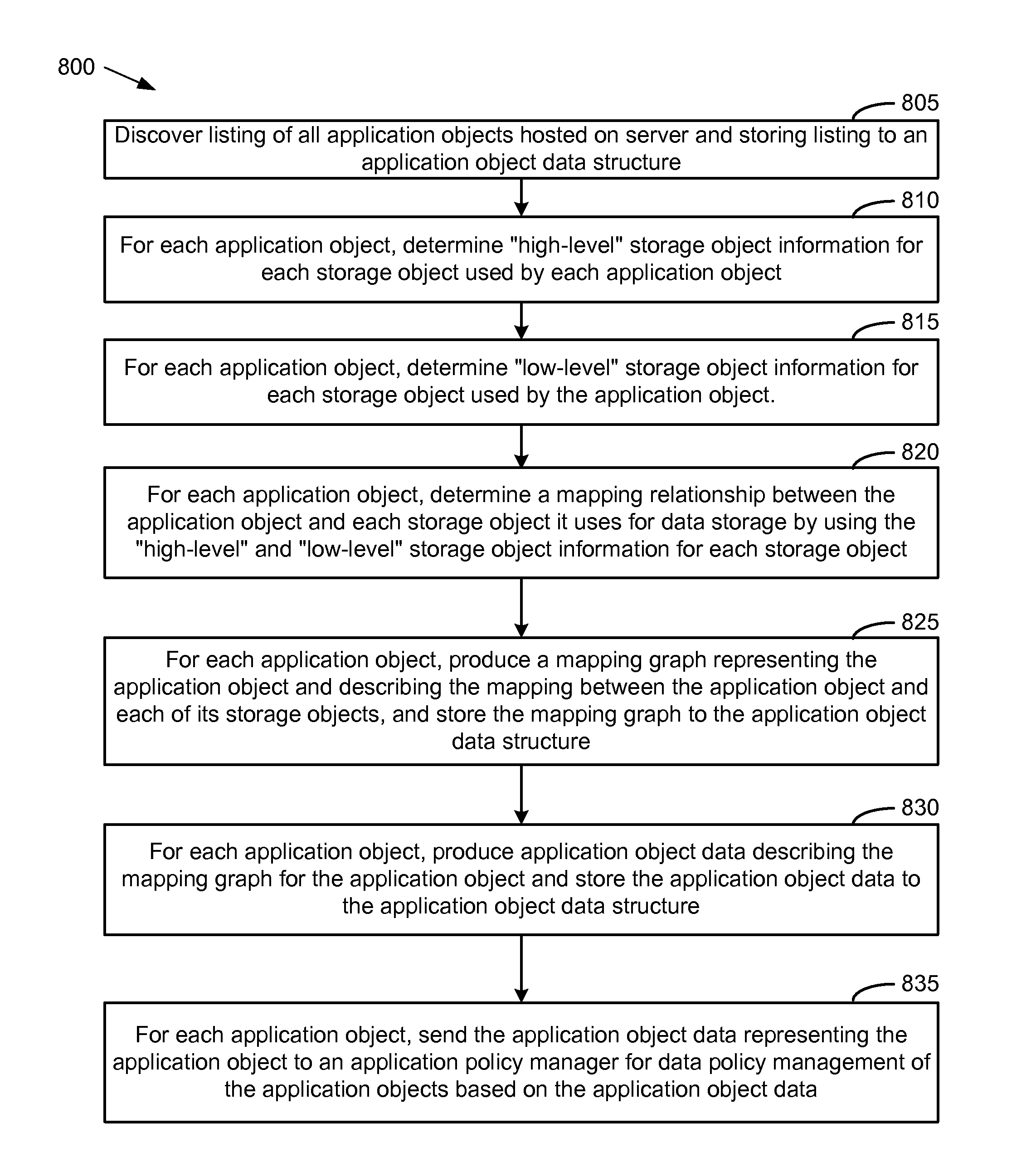
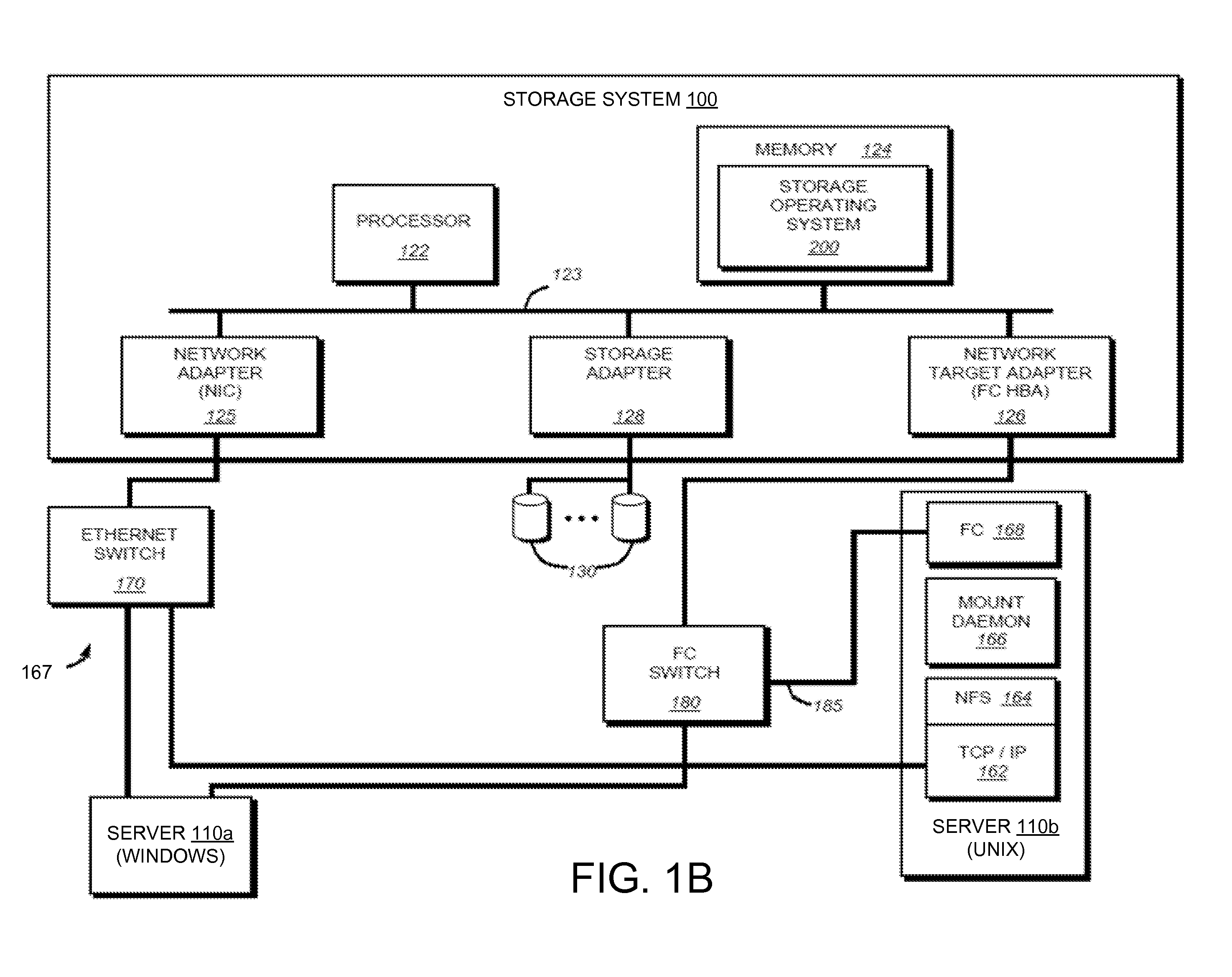
System and Method for Managing Data Policies on Application Objects
ActiveUS20120109958A1Error detection/correctionDigital data processing detailsData managementApplication software
Described herein are systems and methods for providing data policy management over application objects in a storage system environment. An application object may comprise non-virtual or virtual objects (e.g., non-virtual-based applications, virtual-based applications, or virtual storage components). An application object manager may represent application objects by producing mapping graphs and / or application object data that represent application objects in a standardized manner. A mapping graph for an application object may describe a mapping between the application object and its underlying storage objects on a storage system. Application object data may describe a mapping graph in a standardized format. Application object data representing application objects may be received by an application policy manager that manages data policies on the application objects (including virtual applications and virtual storage components) based on the received application object data. Data policies may include policies for backup, service level objectives, recovery, monitoring and / or reporting.
Owner:NETWORK APPLIANCE INC
System, method and apparatus for creating and using a virtual layer within a web browsing environment
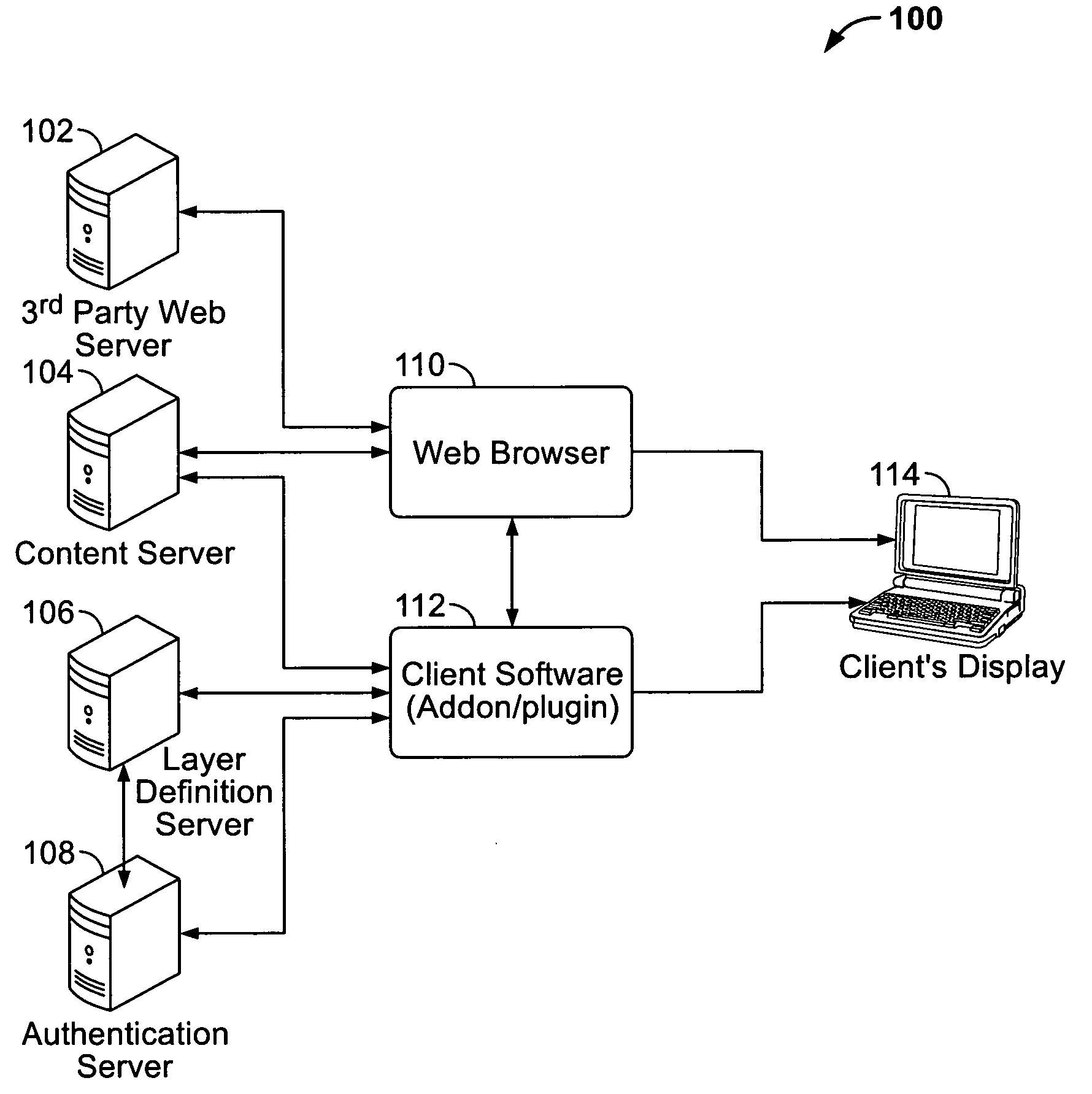
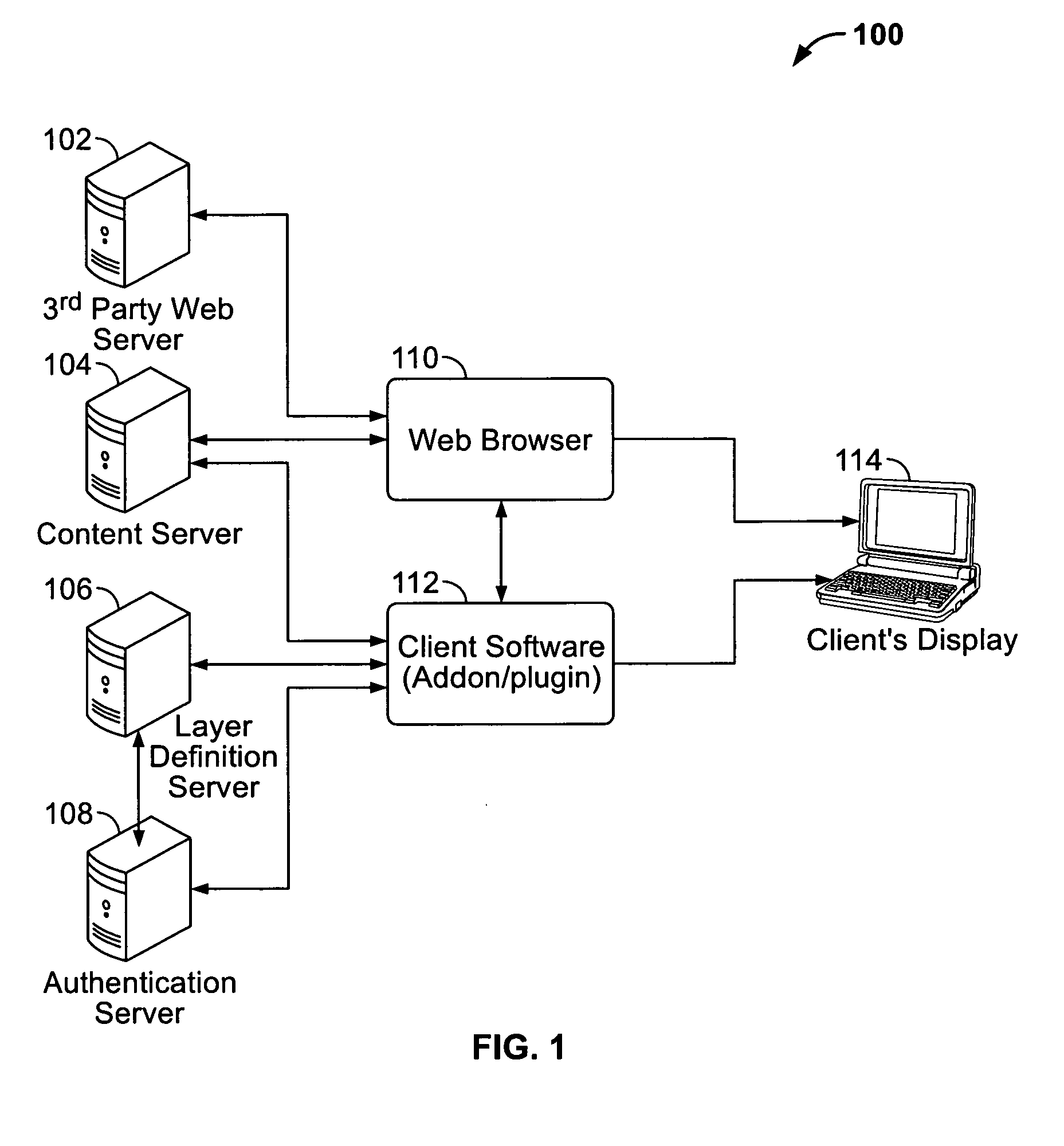
InactiveUS20100313252A1Avoid the needDigital data processing detailsUser identity/authority verificationWeb browserClient-side
A system and a method for configuring a user-editable layer within a network are disclosed. The system includes a client computing system including a web browser. The web browser further includes a loaded webpage configured to obtain web content from a universal network server through a web address. The system further includes an application object model to collect objects from the client computing system and the universal network server. The system for configuring the user-editable layer within the network further includes a plug-in unit coupled to a layer definition server and an authenticating server for authenticating user credential information. The user-editable layer may include at least one of a virtual layer, an emulating layer, an upgradable layer and the like.
Owner:REVIZER TECH
Dynamic configuration of gaming system
InactiveUS20060019750A1Apparatus for meter-controlled dispensingVideo gamesApplication softwareHuman–computer interaction
A gaming system comprises a plurality of common objects, a plurality of application objects, and a central system. The common objects are shared by a plurality of applications and include gaming devices and games. Each gaming device includes at least one of the games. The application objects are used in one of the applications. The central system is linked to the gaming devices and includes a common database and an application database. The common database defines the common objects and first associations between the common objects. The application database defines the application objects, second associations between the application objects, and third associations between the common objects and the application objects. The central system is adapted to dynamically configure the one of the applications based on a change to one or more of the first, second, and third associations.
Owner:BALLY GAMING INC
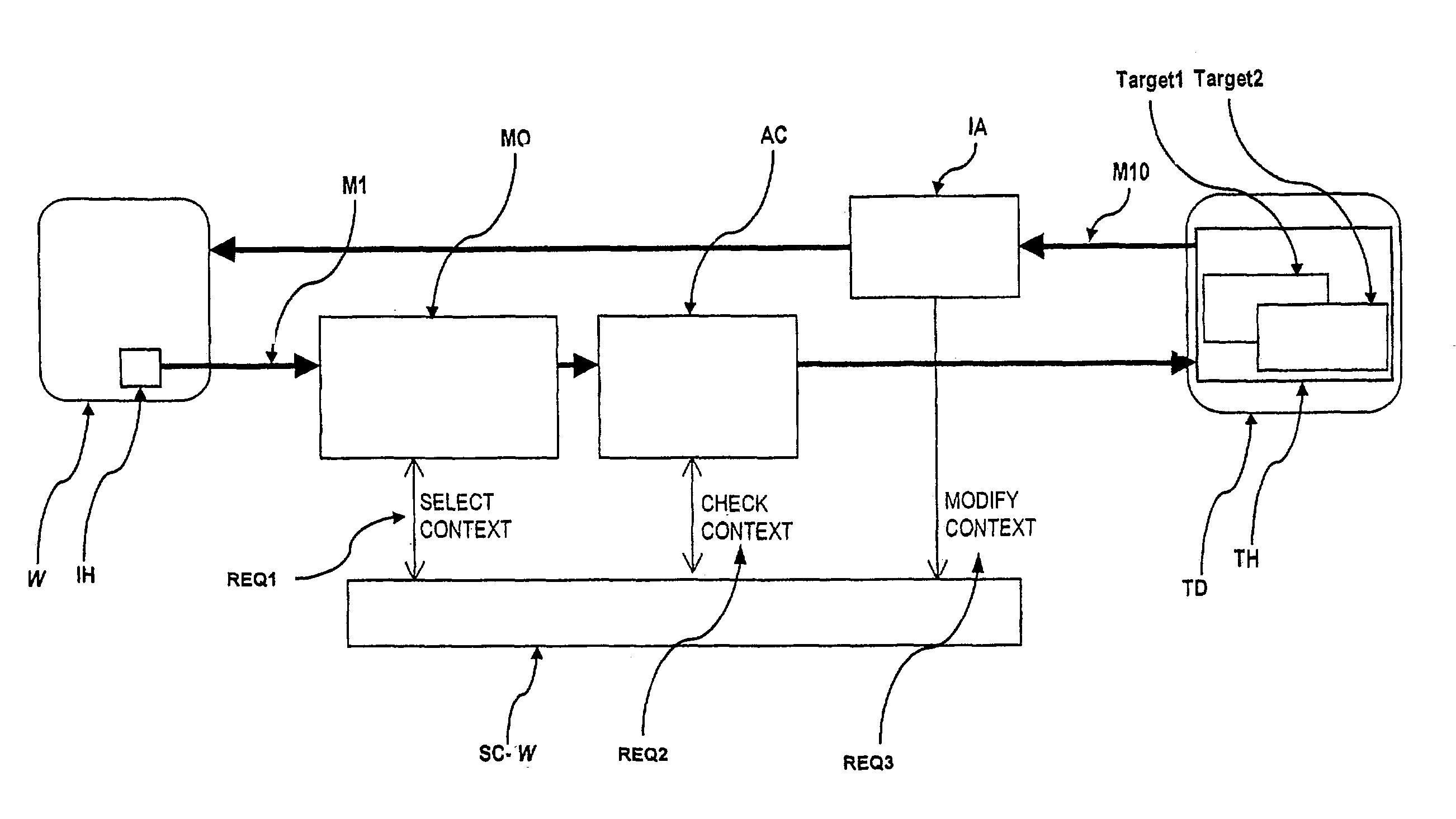
Method and system for session based authorization and access control for networked application objects
InactiveUS20030145094A1Avoid accessLimited to decisionSpecific access rightsError preventionMedia access controlApplication object
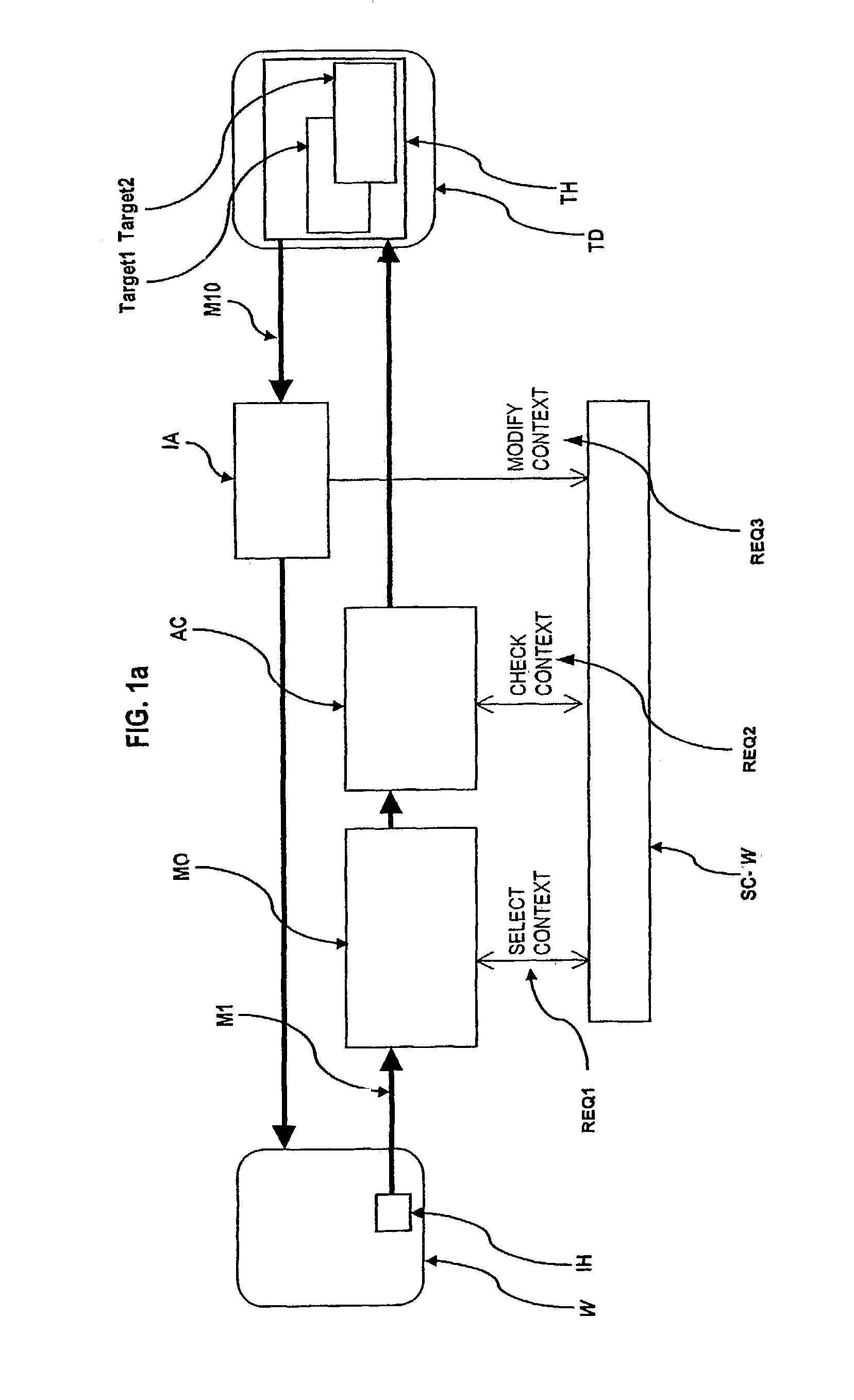
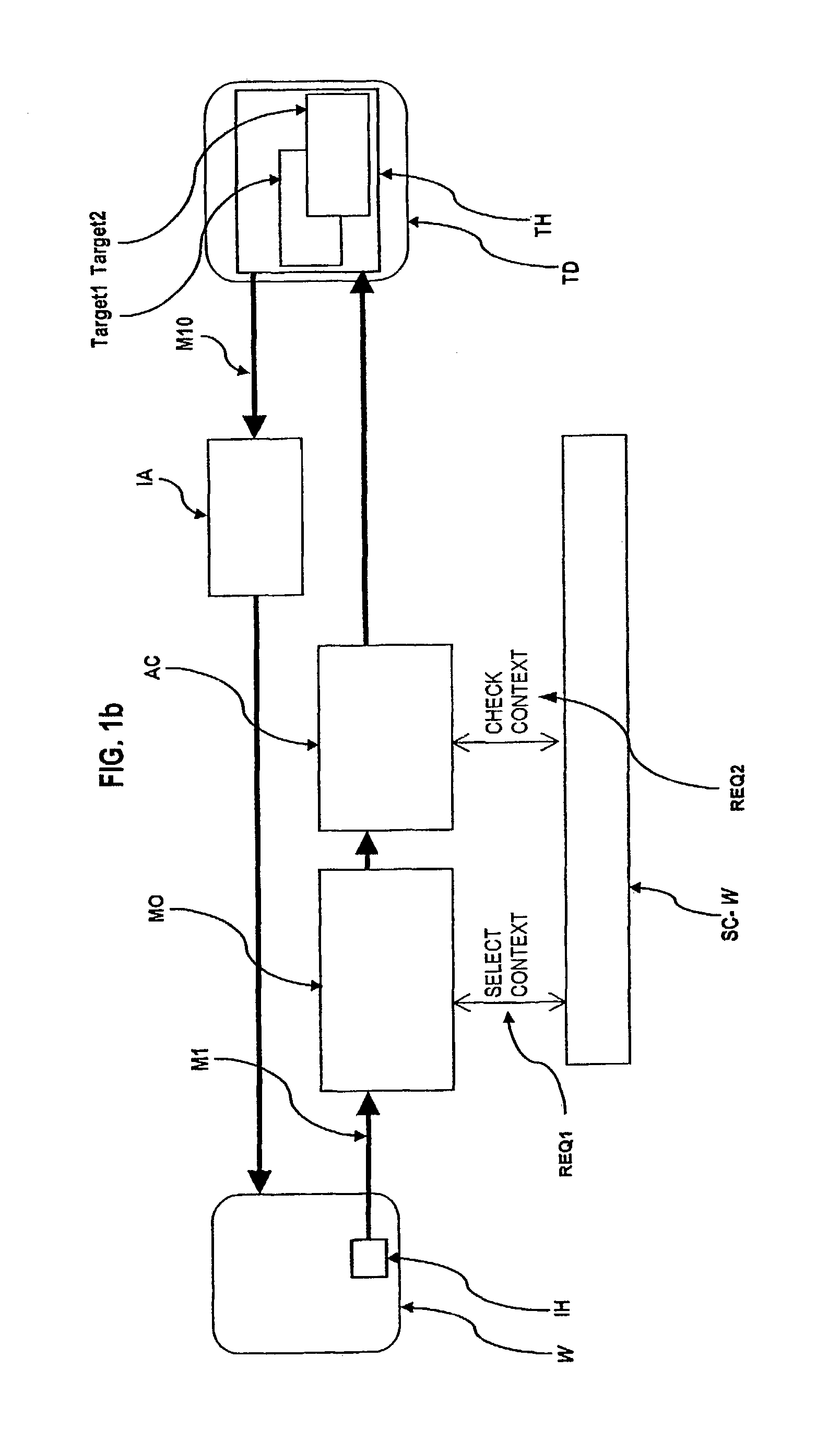
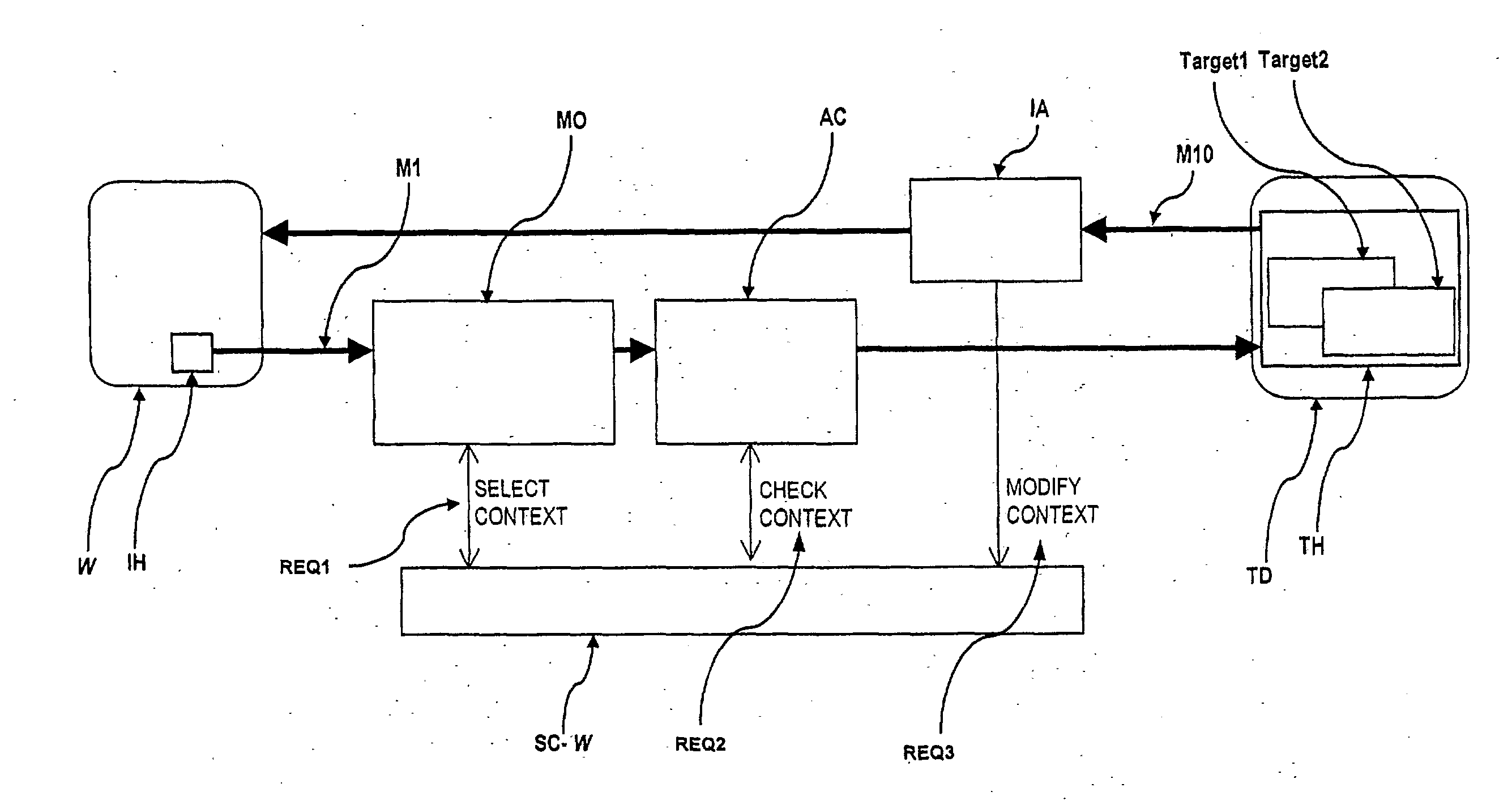
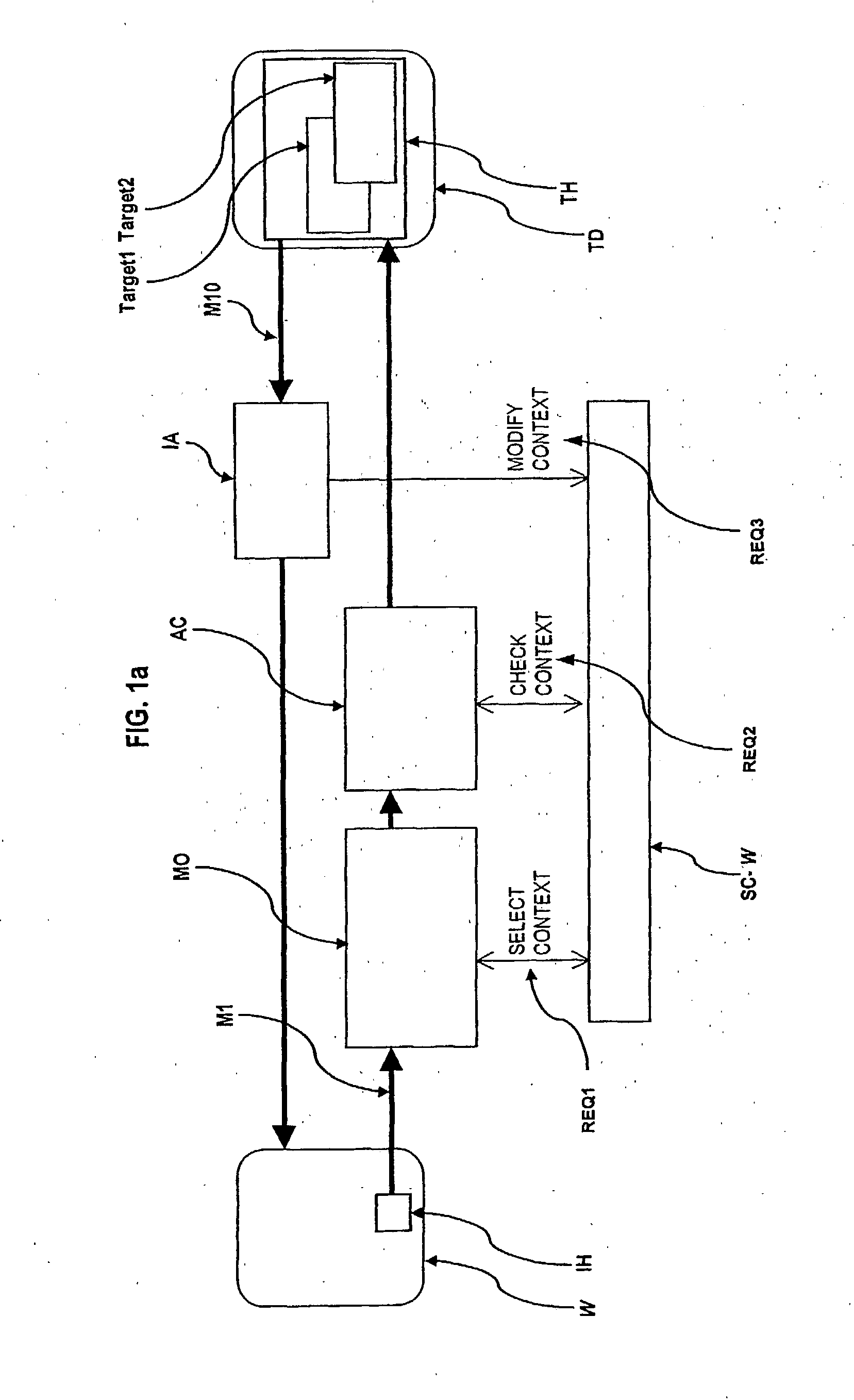
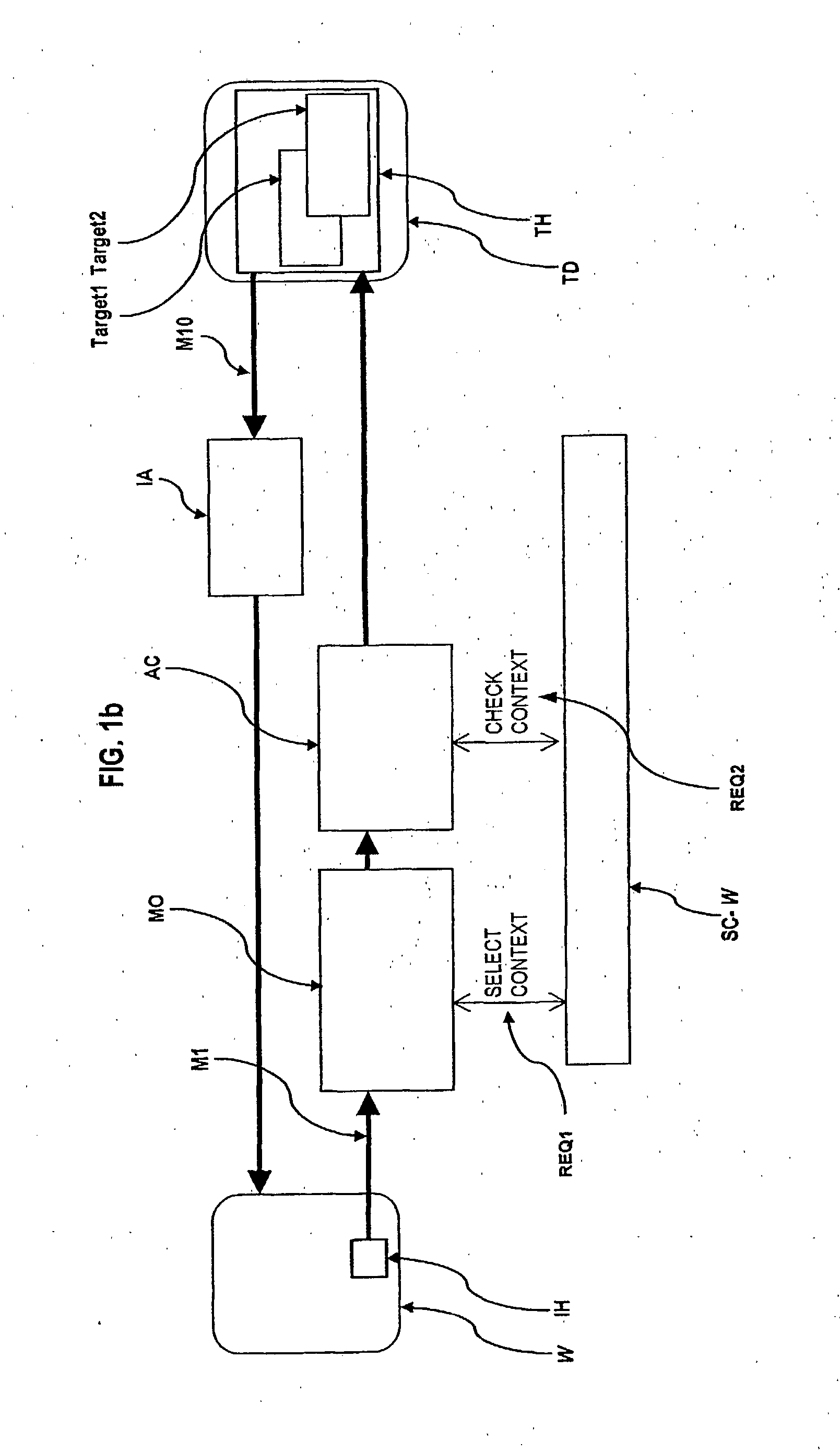
The present invention relates to an ingress-session-based authorization and access control method and system to control access from an initiator-host (IH) to objects (Target 1, Target 2) on a target host (TH) by receiving an access-request, preferably a request-message (M1), originally coming from the initiator-host (IH), that references an object (Target 1, Target 2) on the target host (TH) to access, assigning the access-request (M1) to an ingress-session and selecting a session-context (SC-U, SC-W, SC-Y) belonging to that ingress-session, checking whether the access to the referenced object (Target 1, Target 2) is authorized in the selected session-context (SC-U, SC-W, SC-Y)or not wherein references to objects (Target 1, Target 2) on the target host (TH) were handed over to the initiator-host (IH) as a response to an access-request already granted and wherein the object the reference is handed over for is authorized for access under the handed over reference in that session-context (SC-U, SC-W, SC-Y)the already granted access-request is assigned to.
Owner:PRISMTECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com