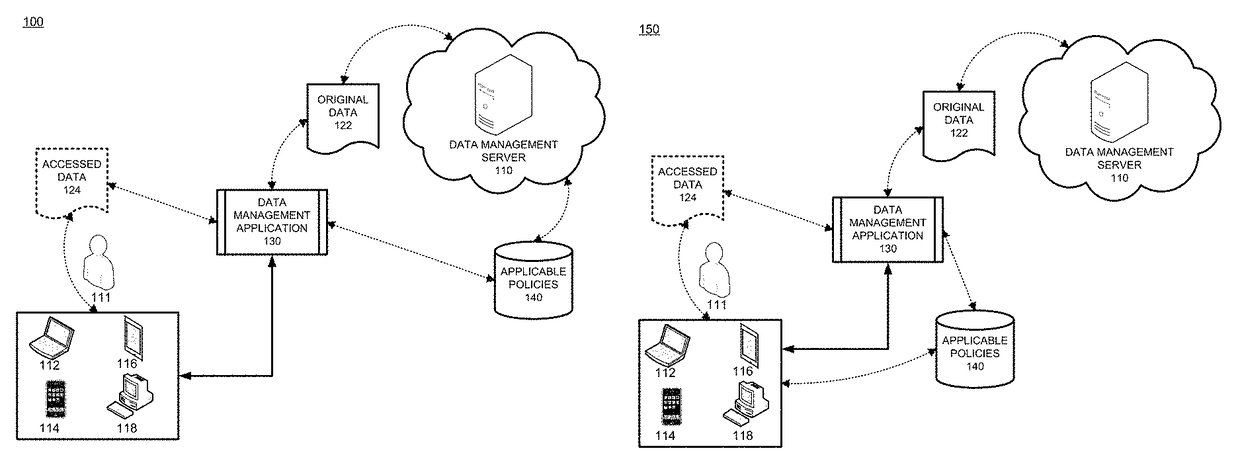
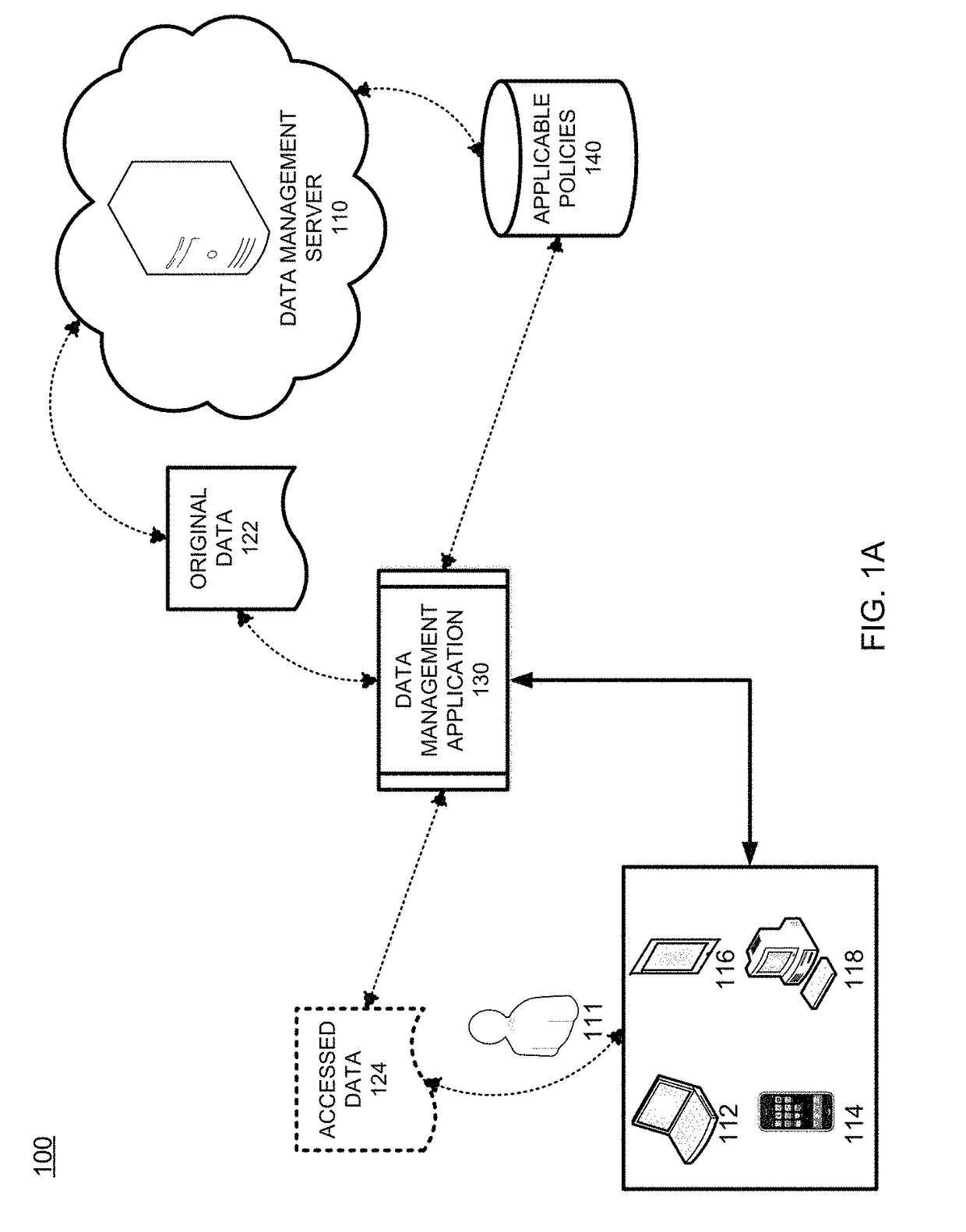
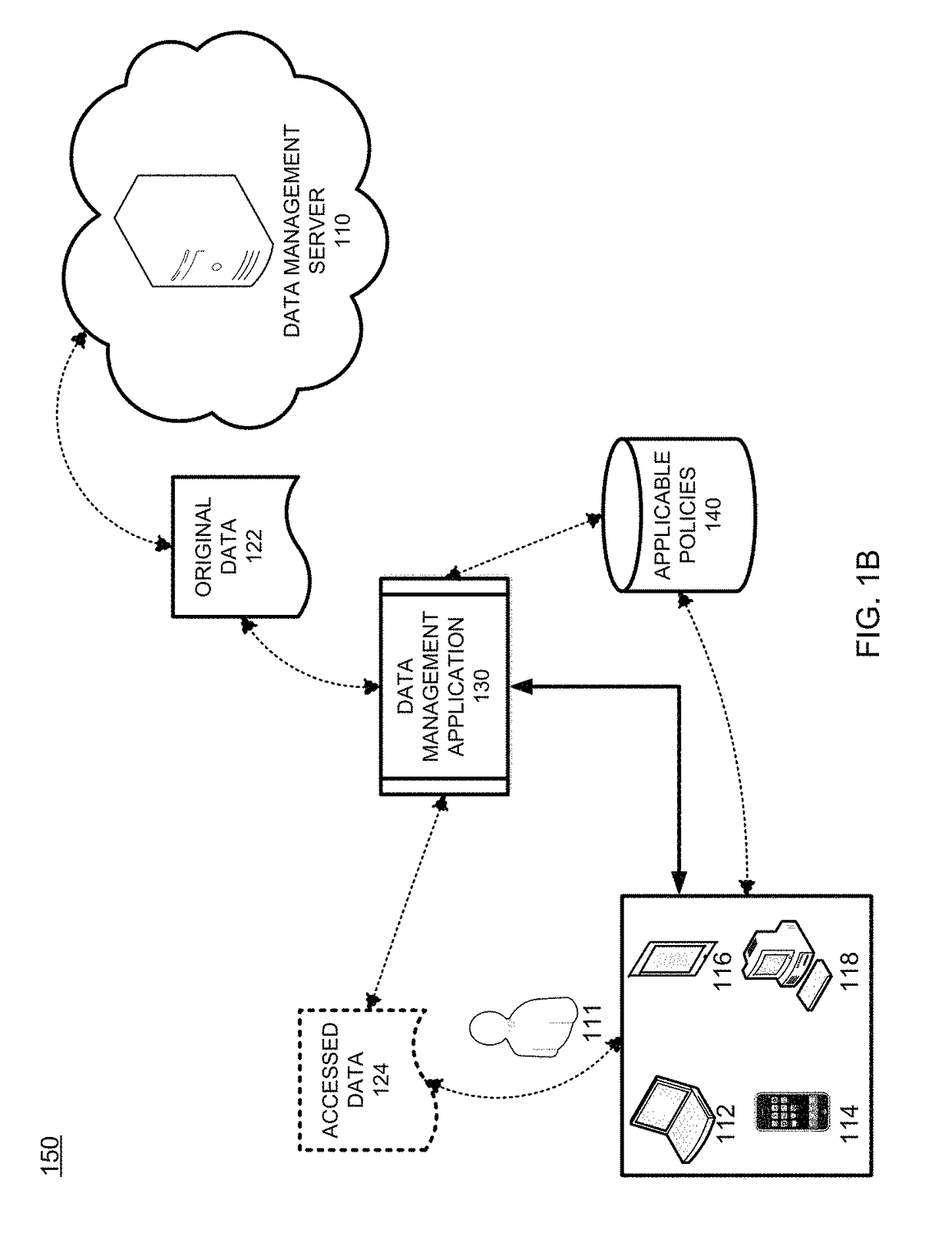
Patents
Literature
37 results about "Data policy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A data governance policy is a living document, which means it is flexible and can be quickly changed in response to changing needs. An effective data governance policy requires a cross-discipline approach to information management and input from executive leadership, finance, information technology ( IT) and other data stewards within the organization.
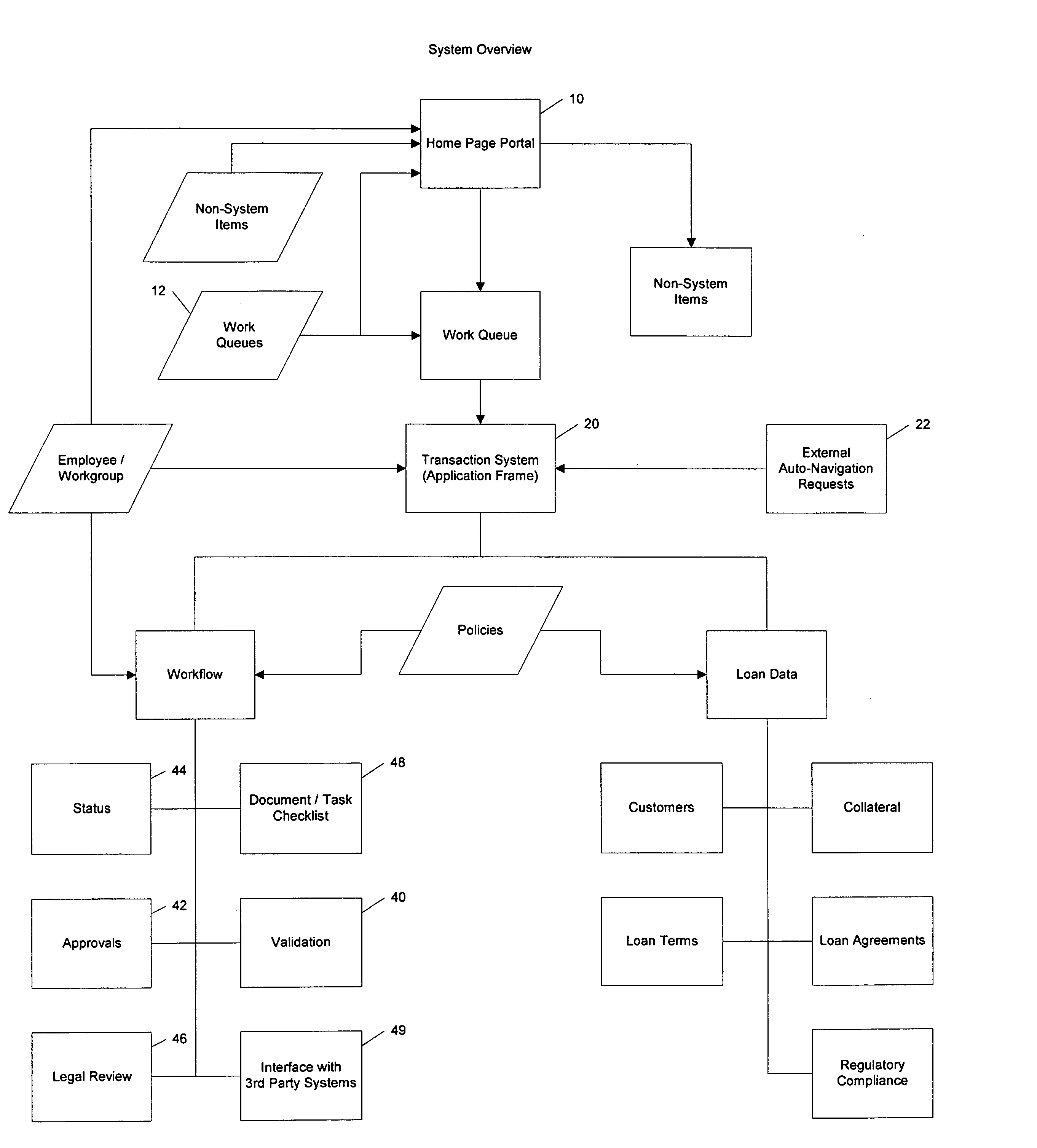
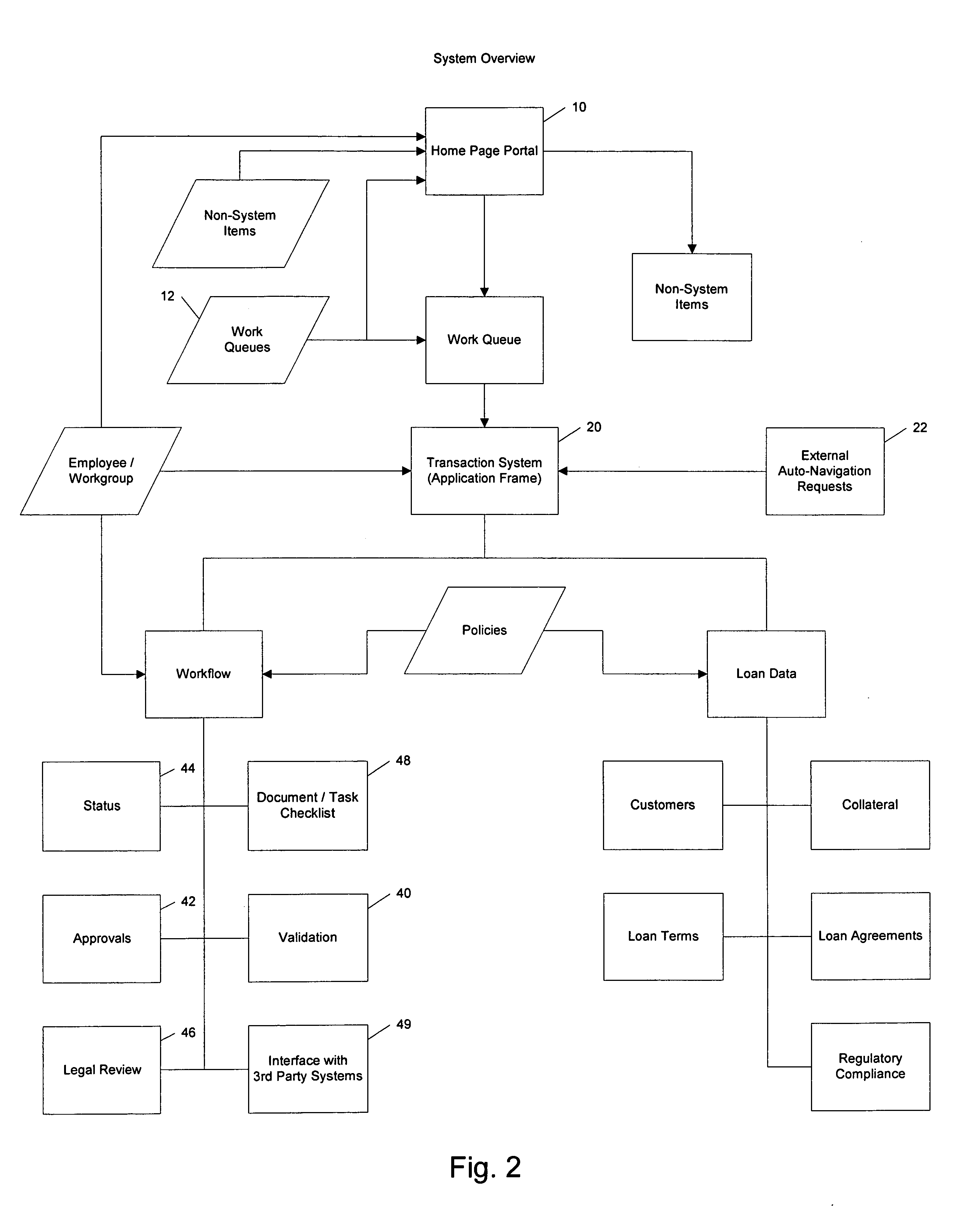
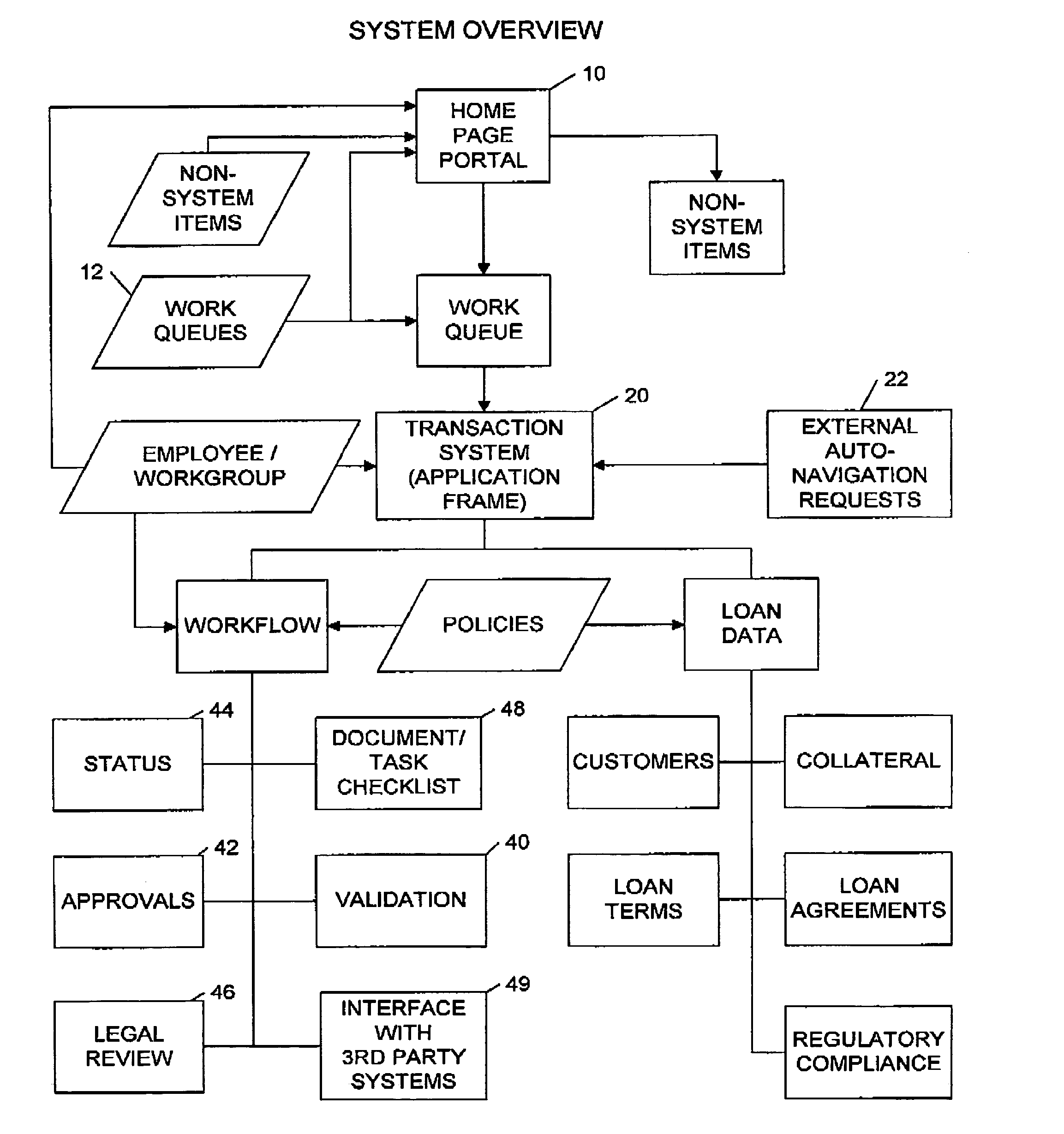
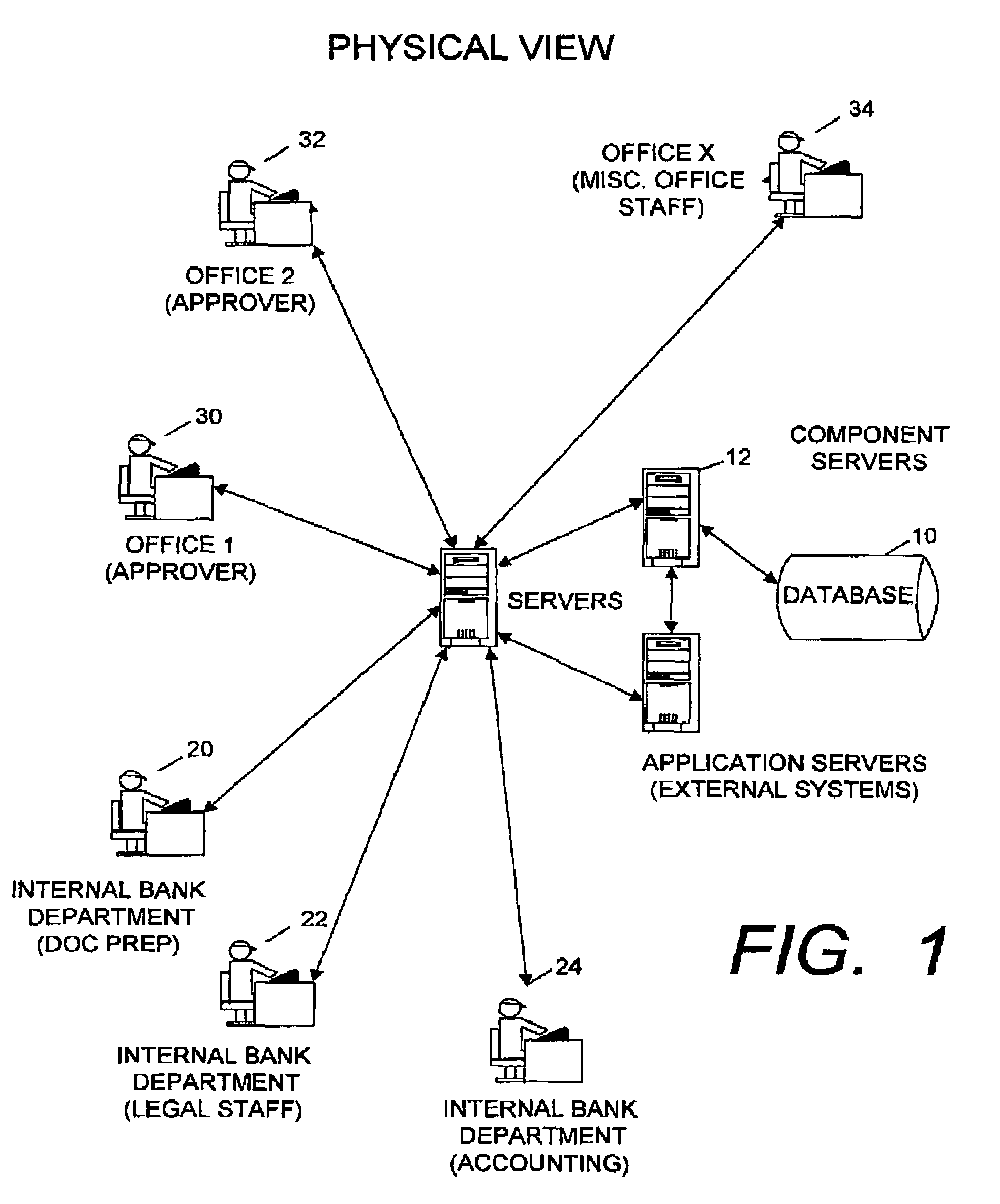
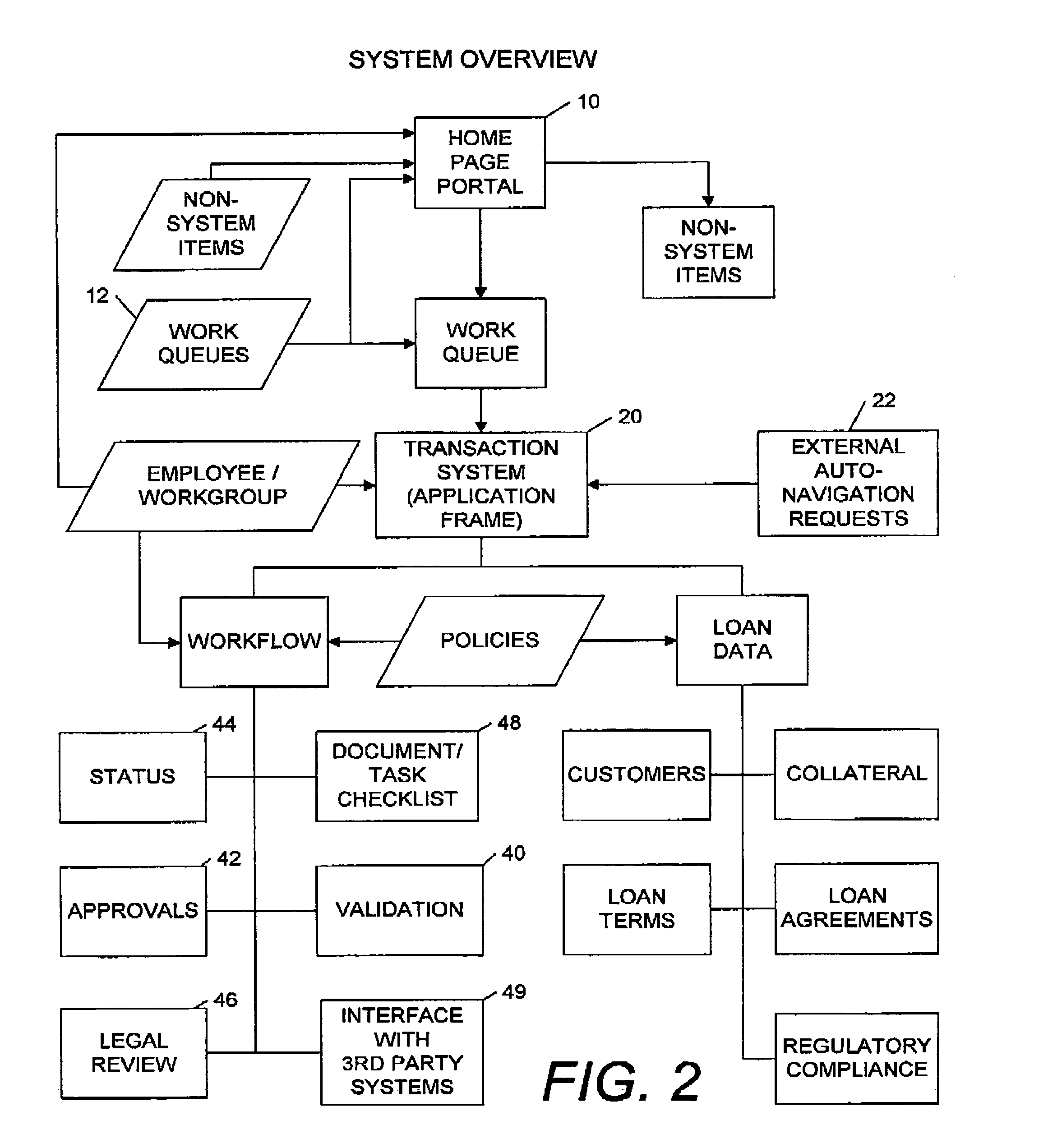
Transaction workflow and data collection system
A transaction workflow and data collection system including the steps of configuring multiple user profiles and system-wide loan data policies, process the loan transaction using a workflow system during which loan data is collected and validated using the system-wide loan data policies and communicating the validated loan transaction data to third-party systems. This Abstract is provided only for searching purposes as required by the U.S.P.T.O., and is not intended to narrow the scope of the present invention as defined by the attached claims in any way.
Owner:DEVAULT RICKY W
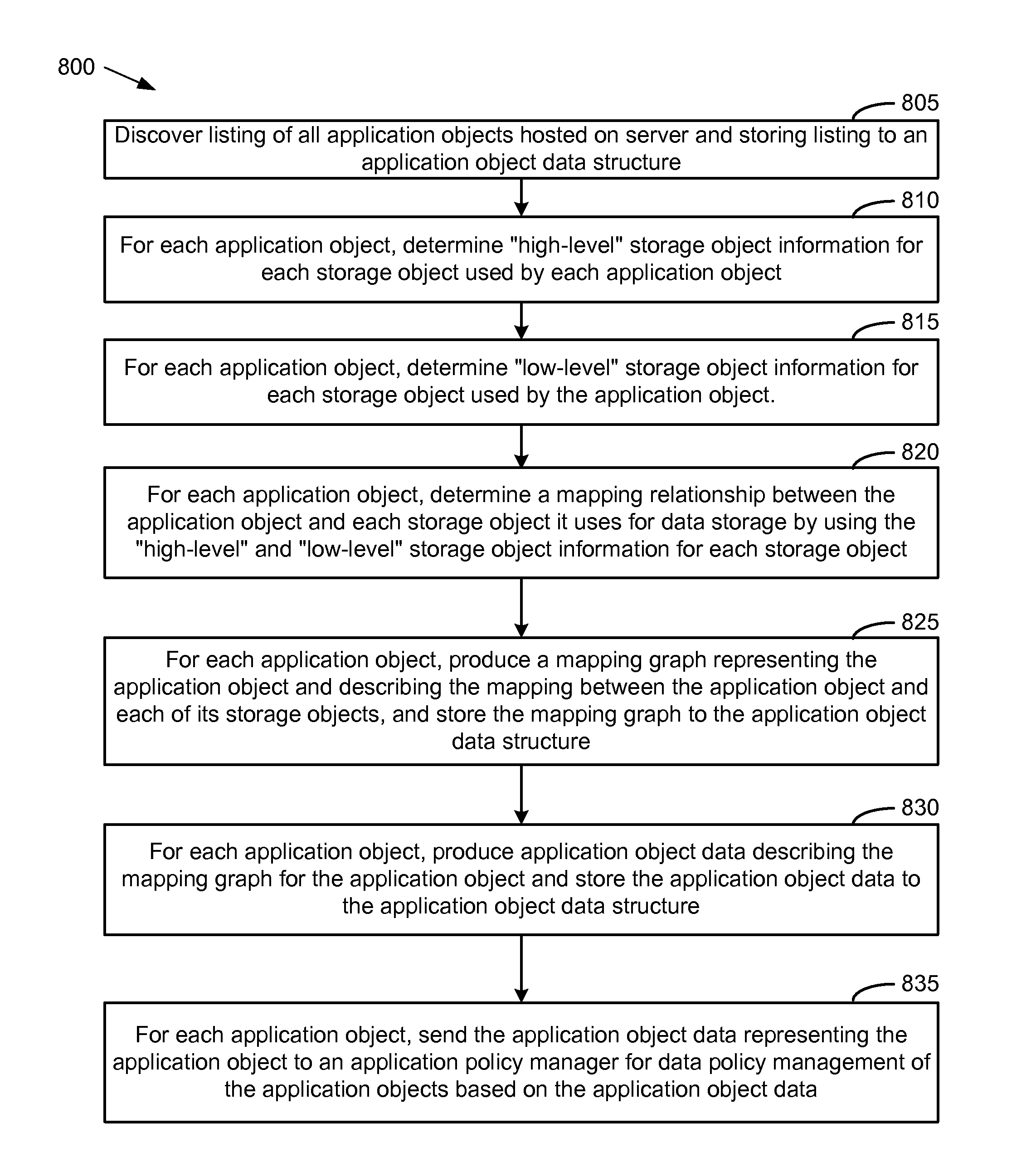
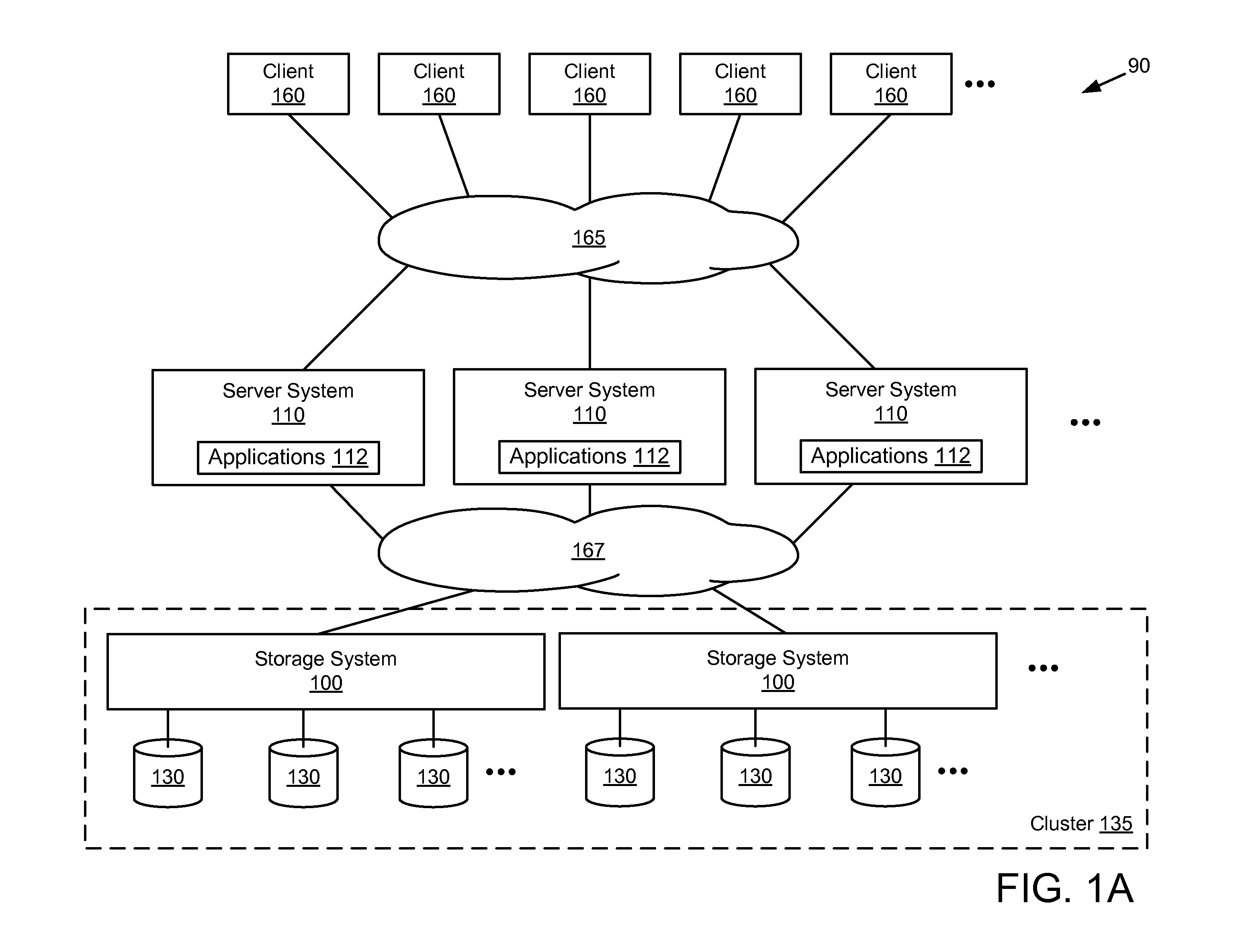
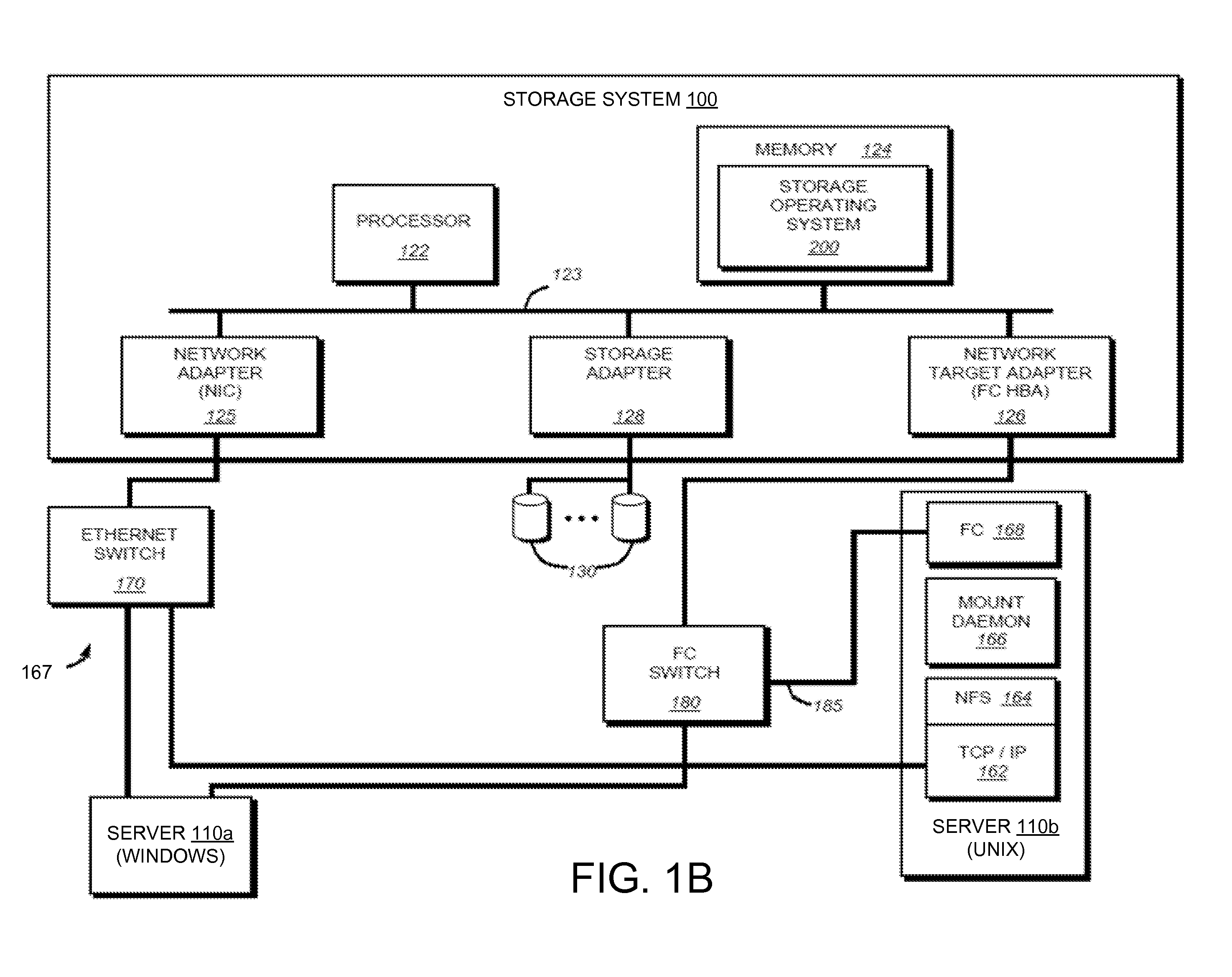
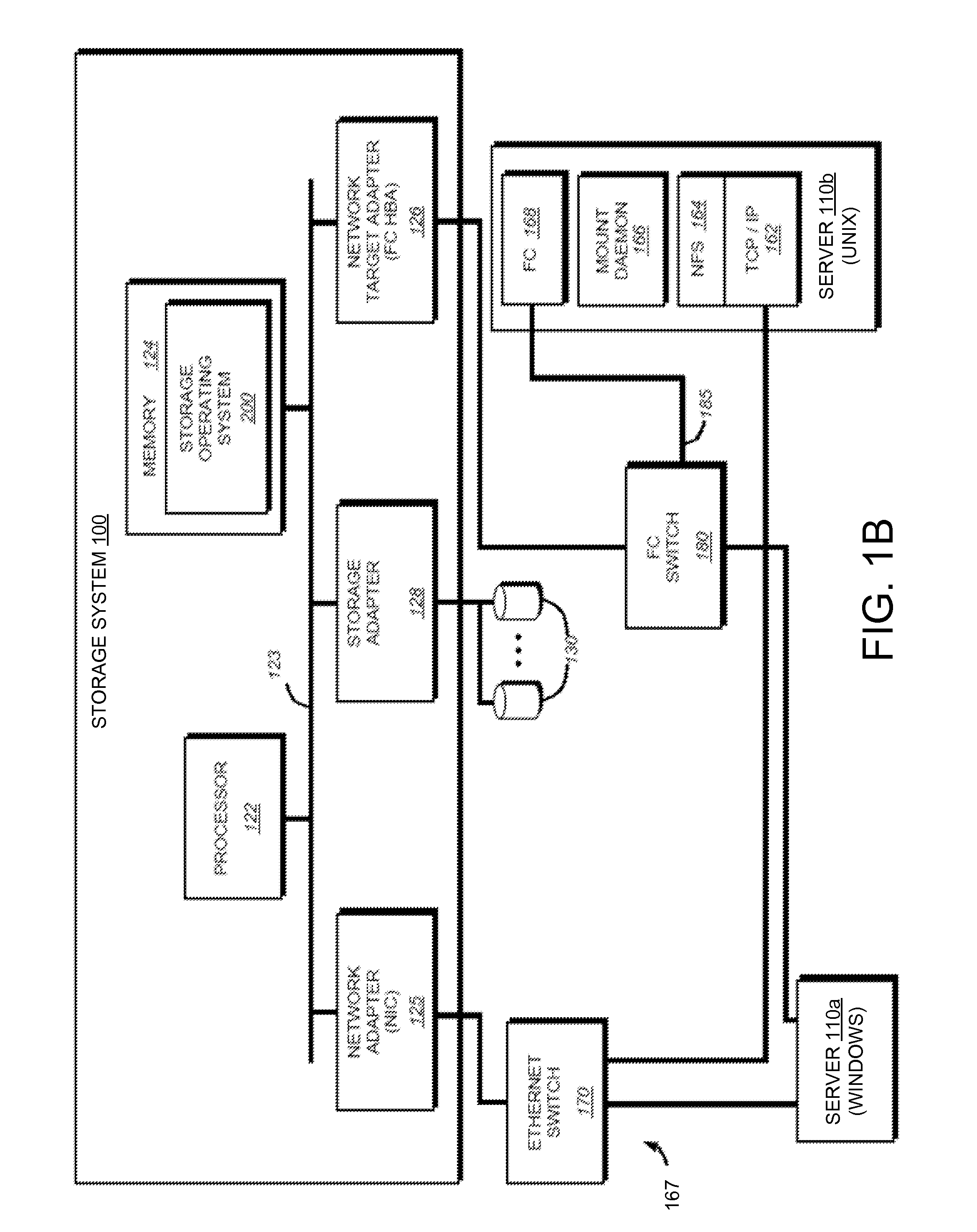
System and Method for Managing Data Policies on Application Objects
ActiveUS20120109958A1Error detection/correctionDigital data processing detailsData managementApplication software
Described herein are systems and methods for providing data policy management over application objects in a storage system environment. An application object may comprise non-virtual or virtual objects (e.g., non-virtual-based applications, virtual-based applications, or virtual storage components). An application object manager may represent application objects by producing mapping graphs and / or application object data that represent application objects in a standardized manner. A mapping graph for an application object may describe a mapping between the application object and its underlying storage objects on a storage system. Application object data may describe a mapping graph in a standardized format. Application object data representing application objects may be received by an application policy manager that manages data policies on the application objects (including virtual applications and virtual storage components) based on the received application object data. Data policies may include policies for backup, service level objectives, recovery, monitoring and / or reporting.
Owner:NETWORK APPLIANCE INC
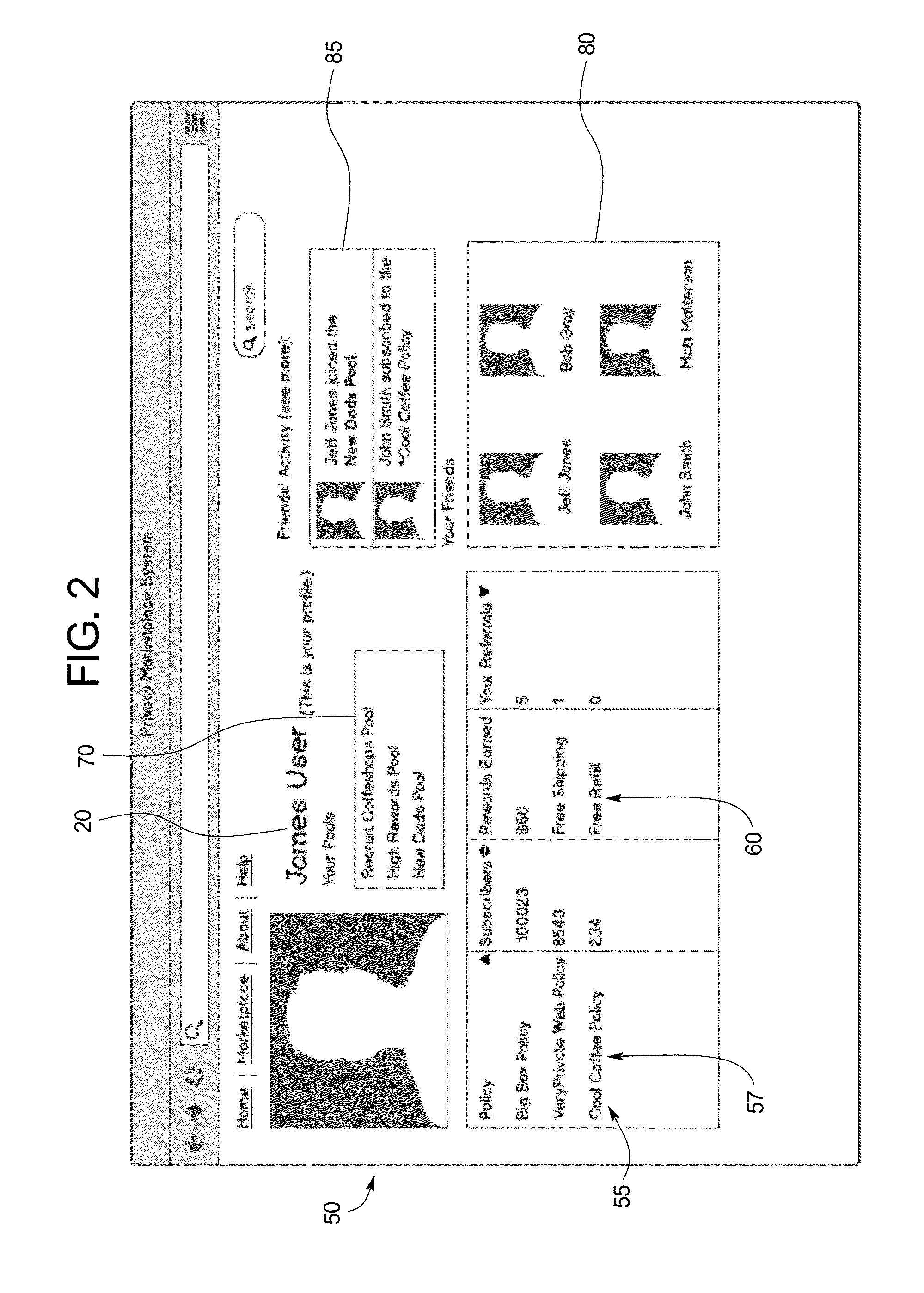
User-controlled centralized privacy marketplace system
ActiveUS20140282852A1Provide mechanismDigital data protectionPlatform integrity maintainanceInternet privacyData access
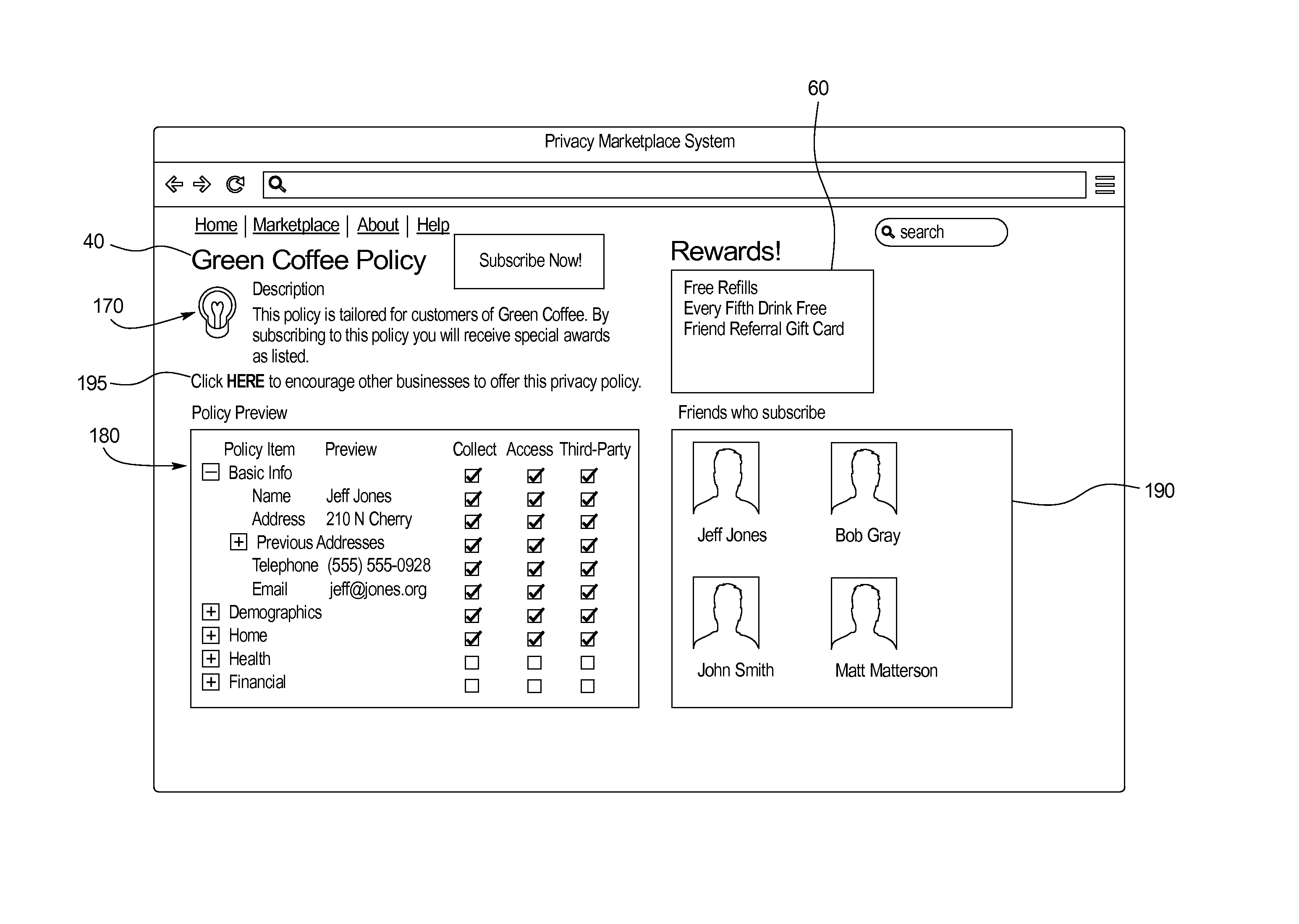
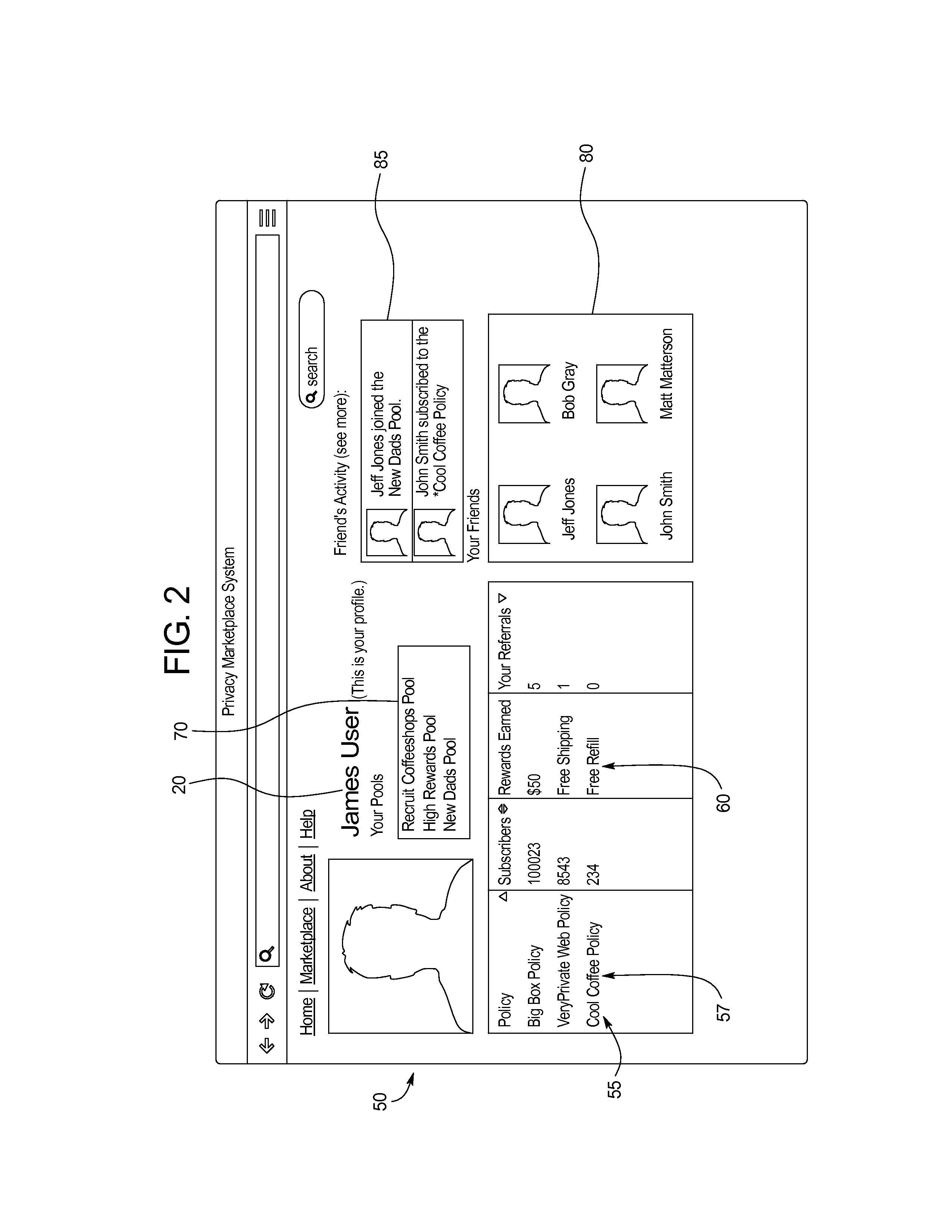
A system for managing personal information of a user includes: a personal information database including personal information records of the user including data associated with the user, wherein a user is associated with a data policy including at least one permission for an accessing party to interact with a personal information record; and a data access module that receives and responds to requests from an accessing party, wherein a request may be one of: a read request specifying a personal information record to be read; and a write request specifying a personal information to be written to a personal information record to be written, wherein in response to a write request, the data access module responds with the a personal information record to be read, or updates the personal information record to be written in the personal information database, if permitted by the personal information record the privacy policy.
Owner:VESTEVICH JACQUELINE K
Transaction workflow and data collection system
A transaction workflow and data collection system including the steps of configuring multiple user profiles and system-wide loan data policies, process the loan transaction using a workflow system during which loan data is collected and validated using the system-wide loan data policies and communicating the validated loan transaction data to third-party systems. This Abstract is provided only for searching purposes as required by the U.S.P.T.O., and is not intended to narrow the scope of the present invention as defined by the attached claims in any way.
Owner:DEVAULT RICKY W
Access files
ActiveUS20160285835A1Memory architecture accessing/allocationKey distribution for secure communicationUser deviceLimited access
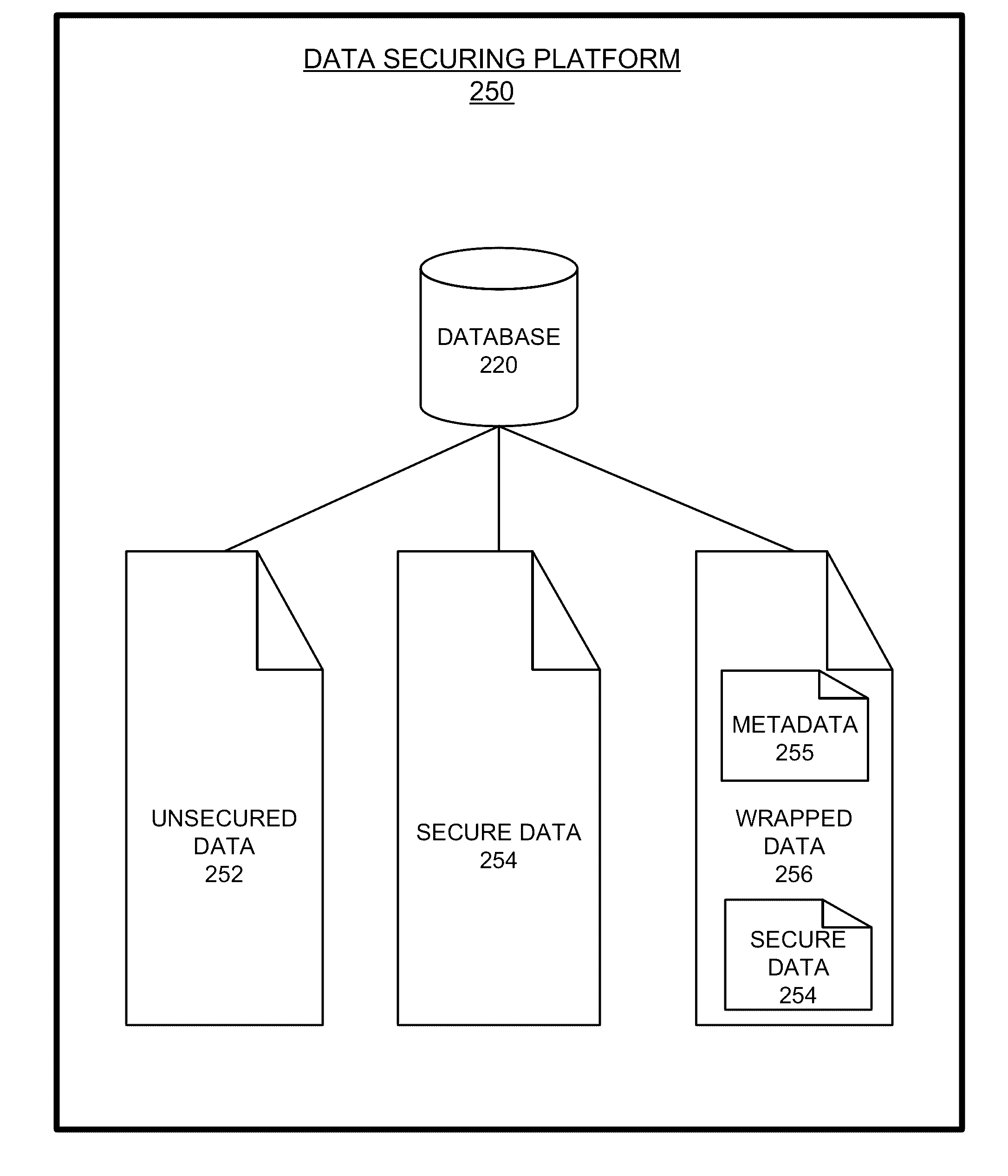
Data security access and management may require a server dedicated to monitoring document access requests and enforcing rules and policies to limit access to those who are not specifically identified as having access to the data. One example of operation may include selecting data to access via a user device, identifying a user profile associated with the user device, retrieving at least one user policy associated with the user profile, determining whether the user policy permits the user device to access the data, matching the user policy to a data policy associated with the data, receiving an encryption key at the user device, applying the encryption key to the data, and unwrapping the data from a wrapped data format to access the data.
Owner:VERA
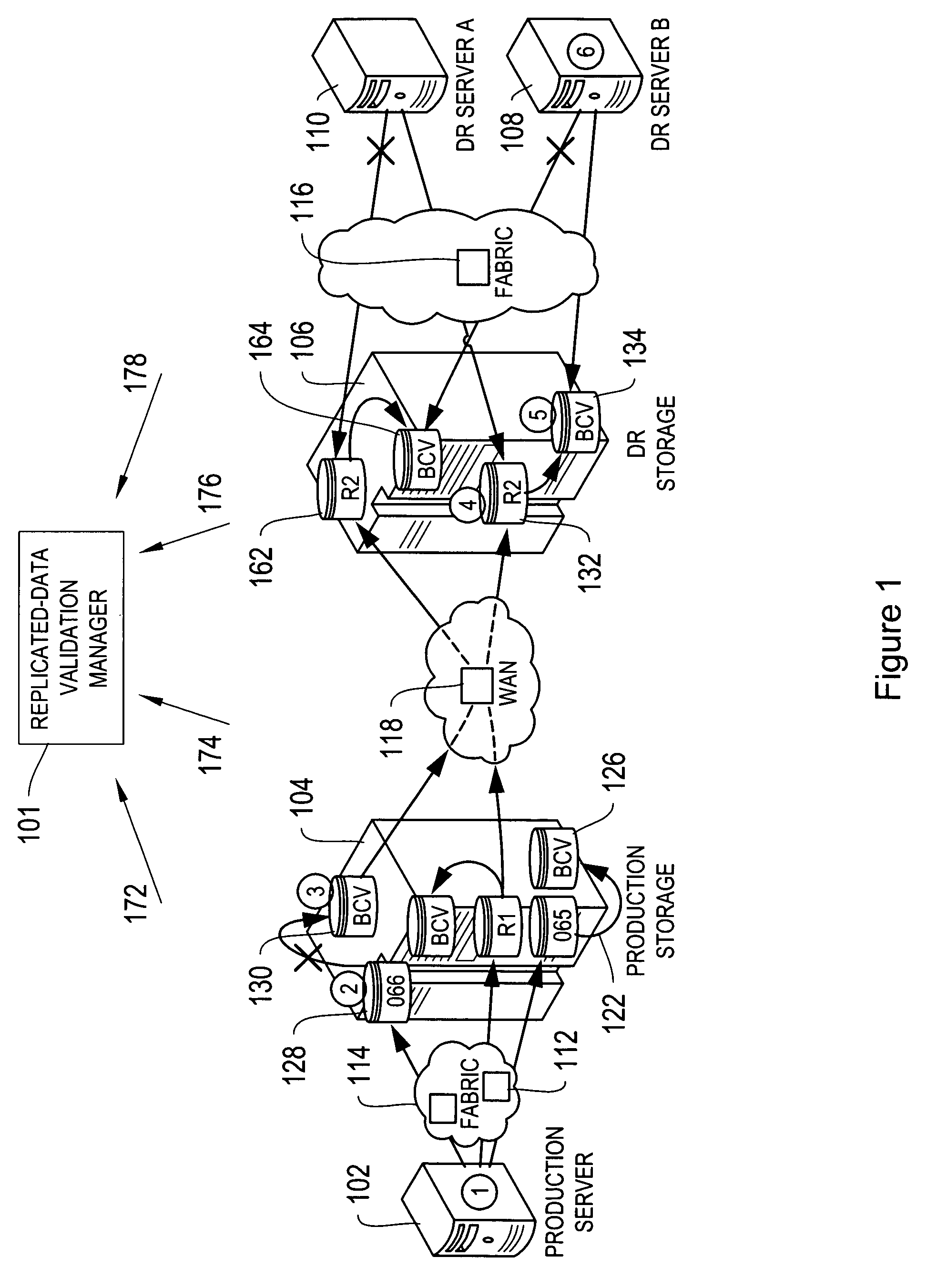
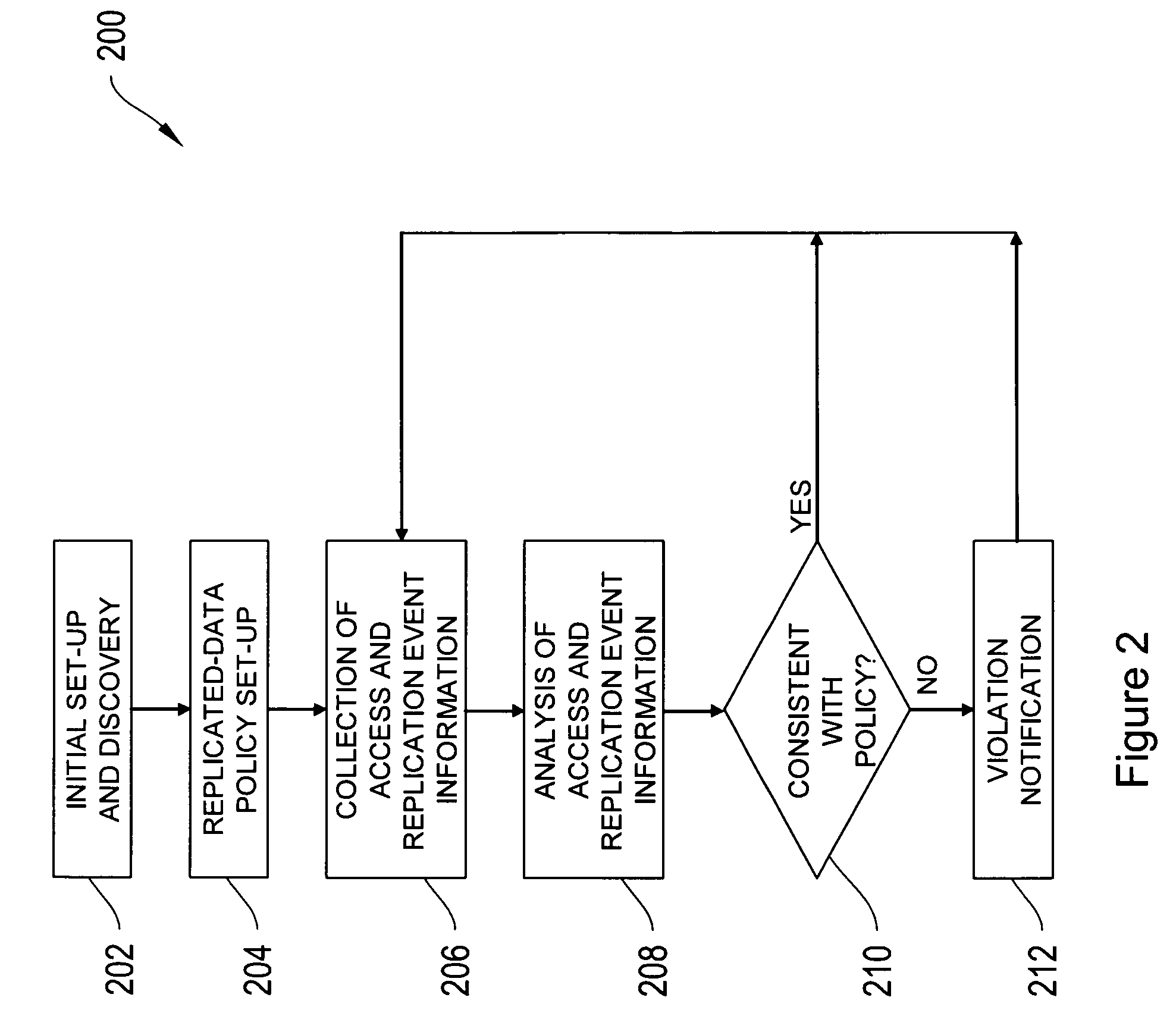
Methods and systems for validating accessibility and currency of replicated data
ActiveUS20070088763A1Digital data information retrievalDigital data processing detailsData systemAccessibility
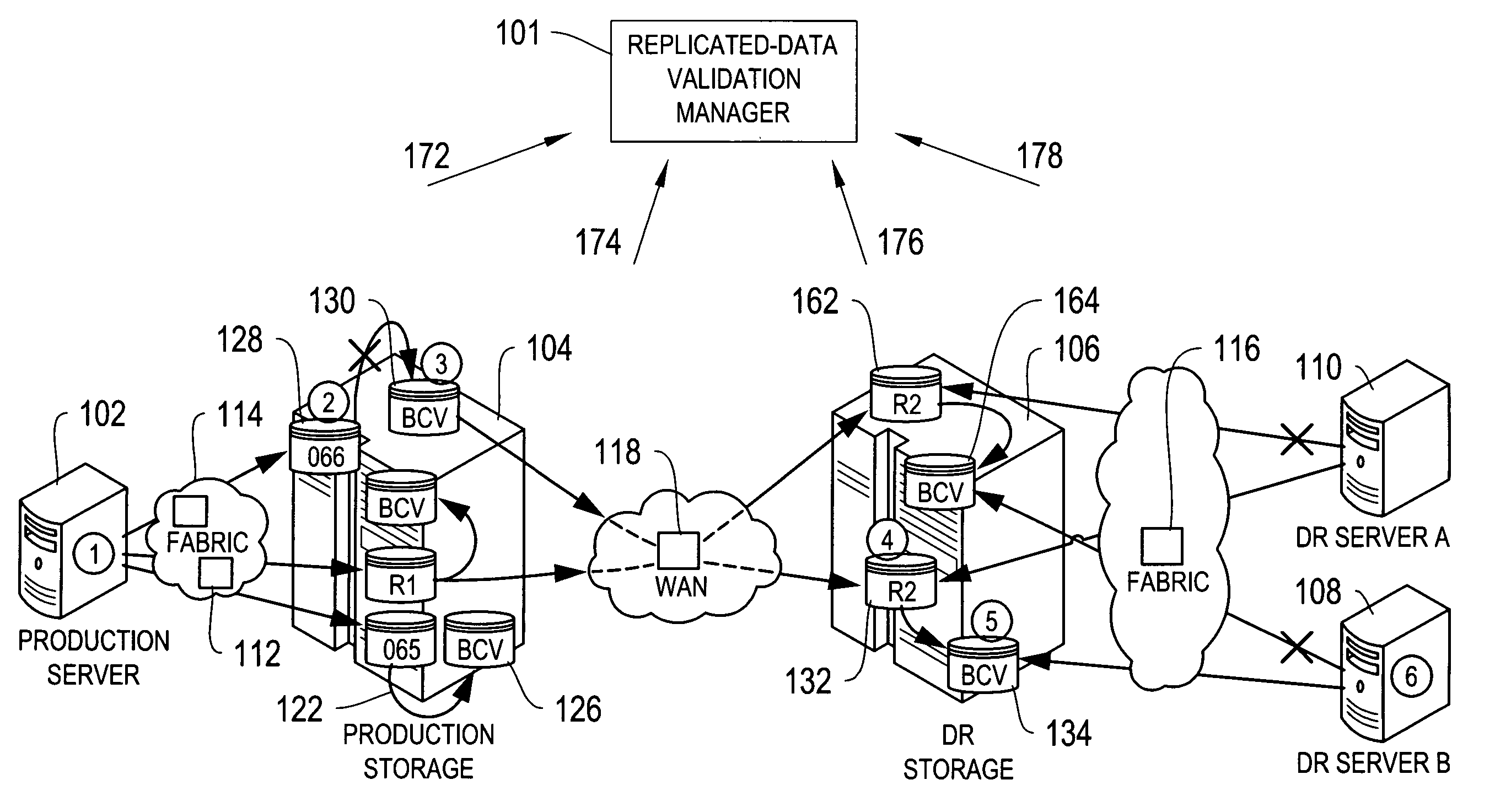
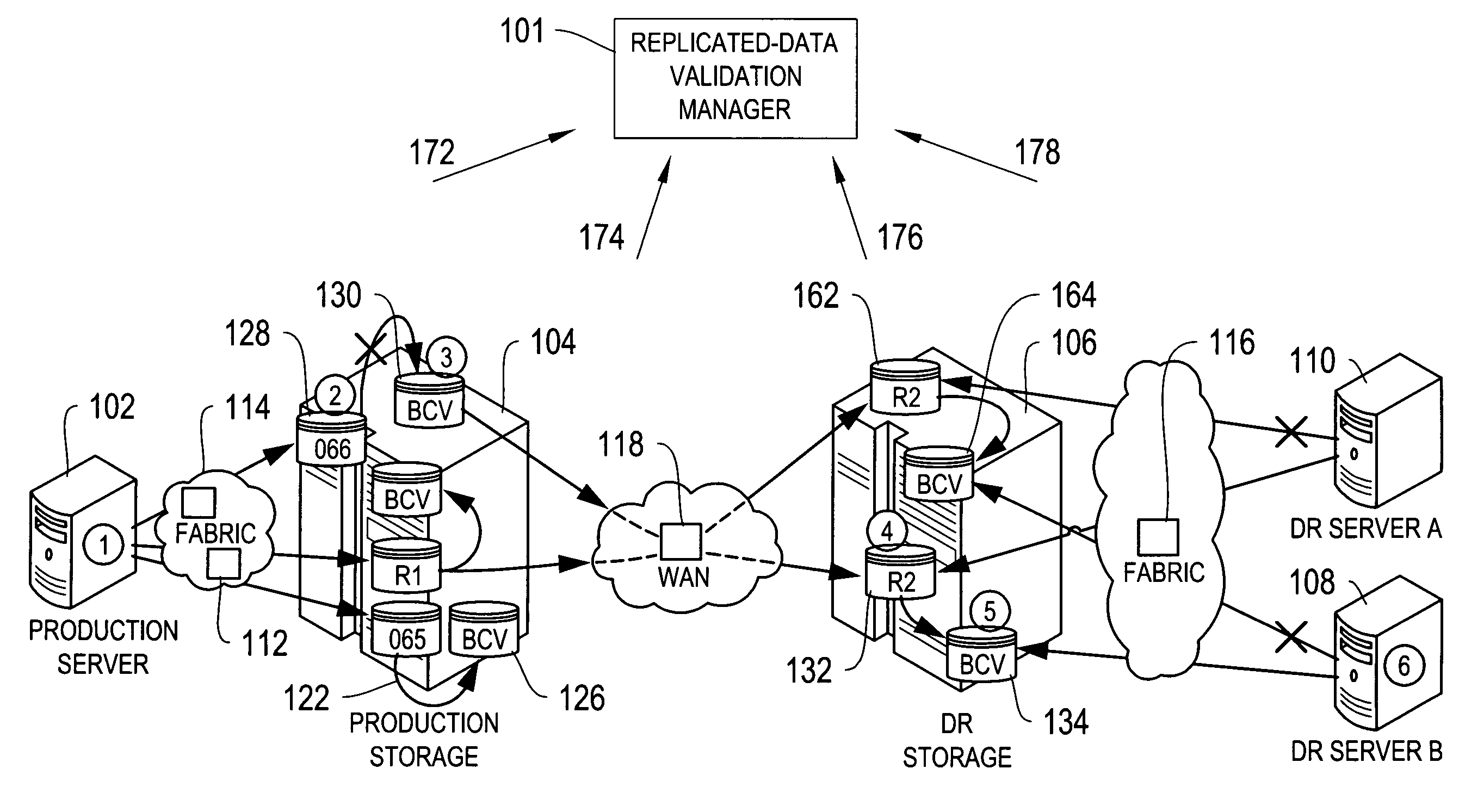
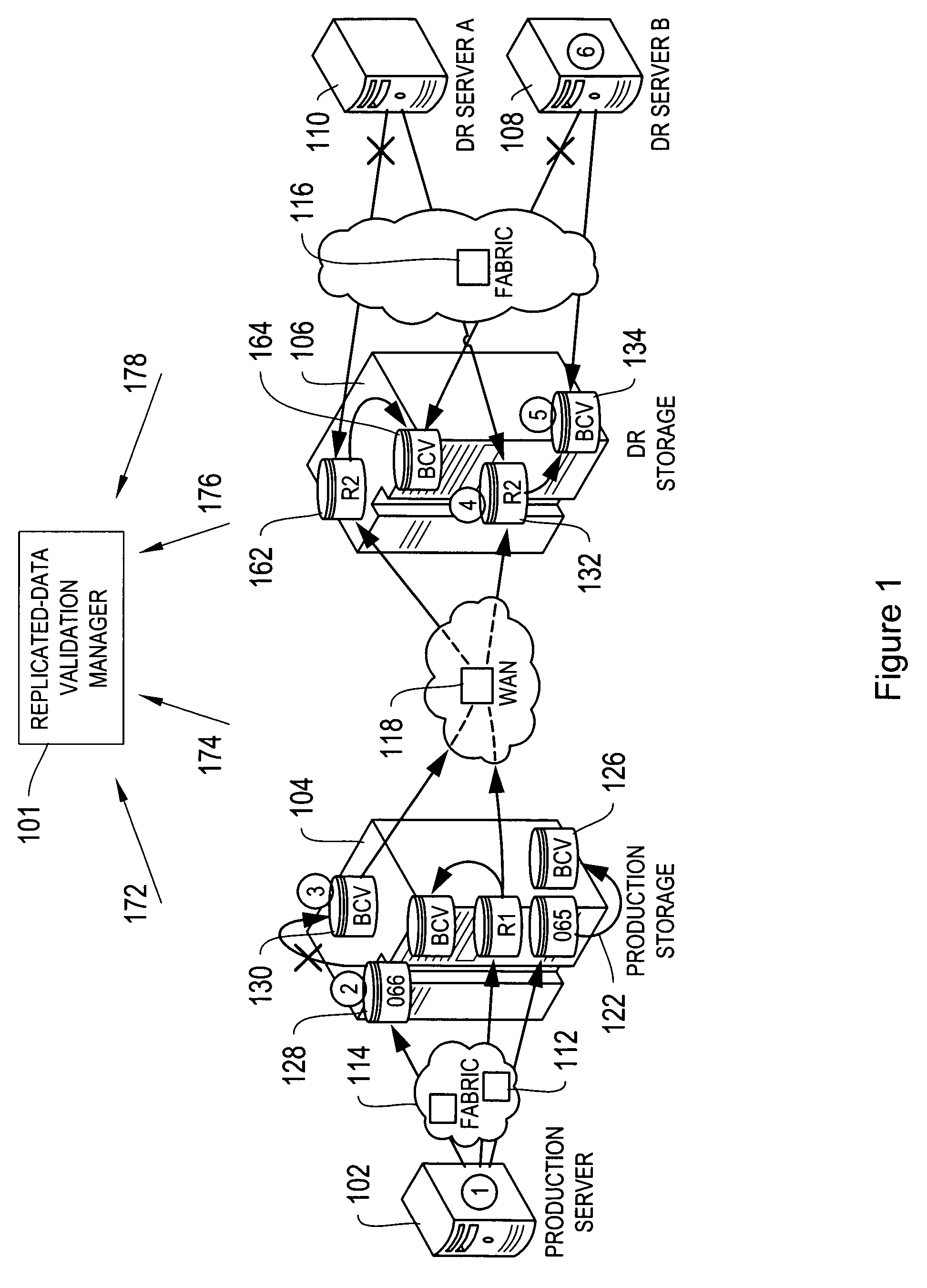
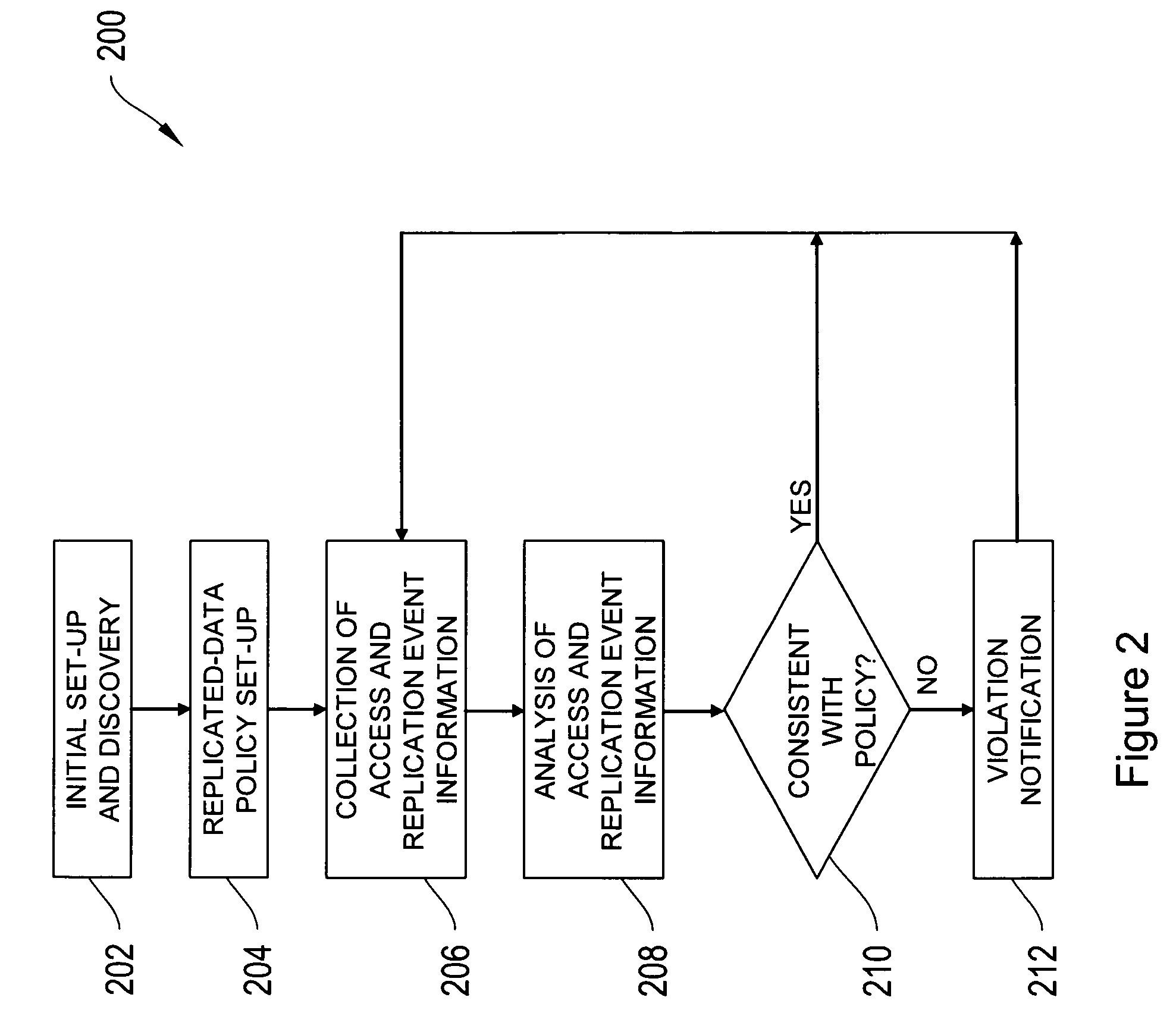
Systems and processes for determining and validating accessibility and currency, i.e., the actual status, of data replicated in a networked environment are disclosed. According to the disclosed process, a replicated-data policy for replicating data is defined, and access paths between network devices or between applications running on the network devices are monitored, for example, by a replicated-data monitor. Also monitored are the data replication activities in the network. The currency, i.e., timeliness, and accessibility of a replica by a network device is then compared with the requirements in the replicated-data policy and discrepancies with the replicated-data policy are identified, optionally accompanied by a notification.
Owner:NETWORK APPLIANCE INC +1
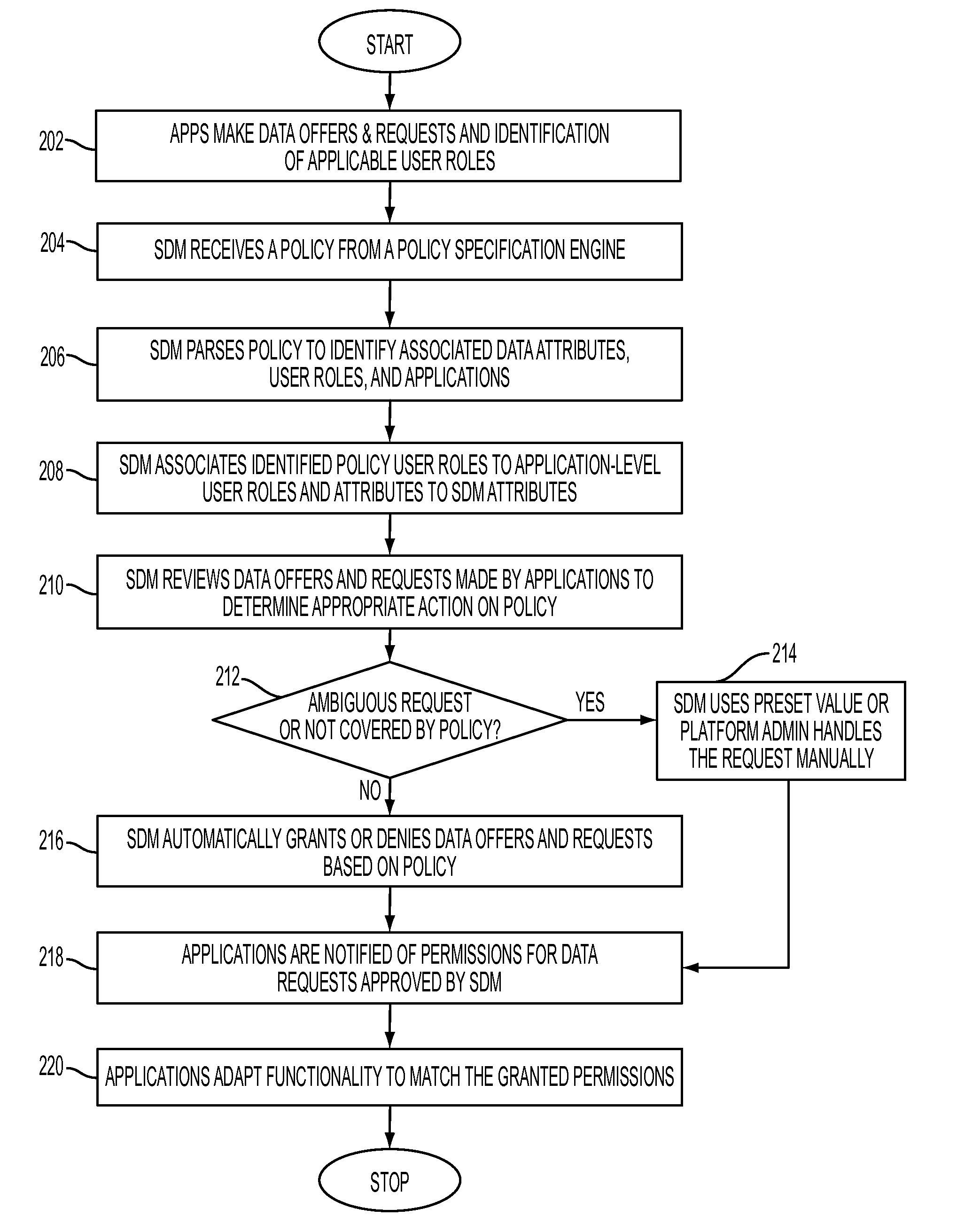
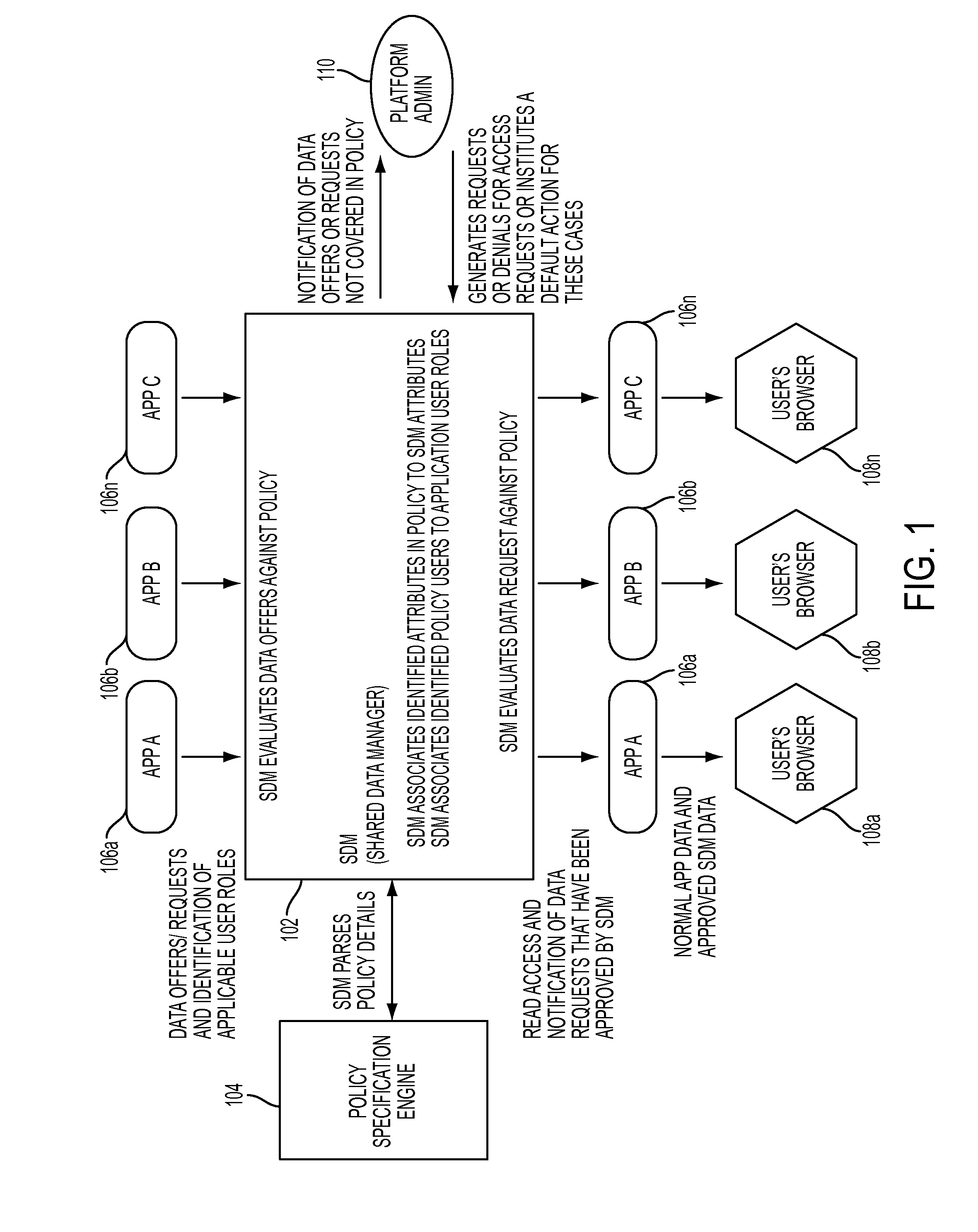
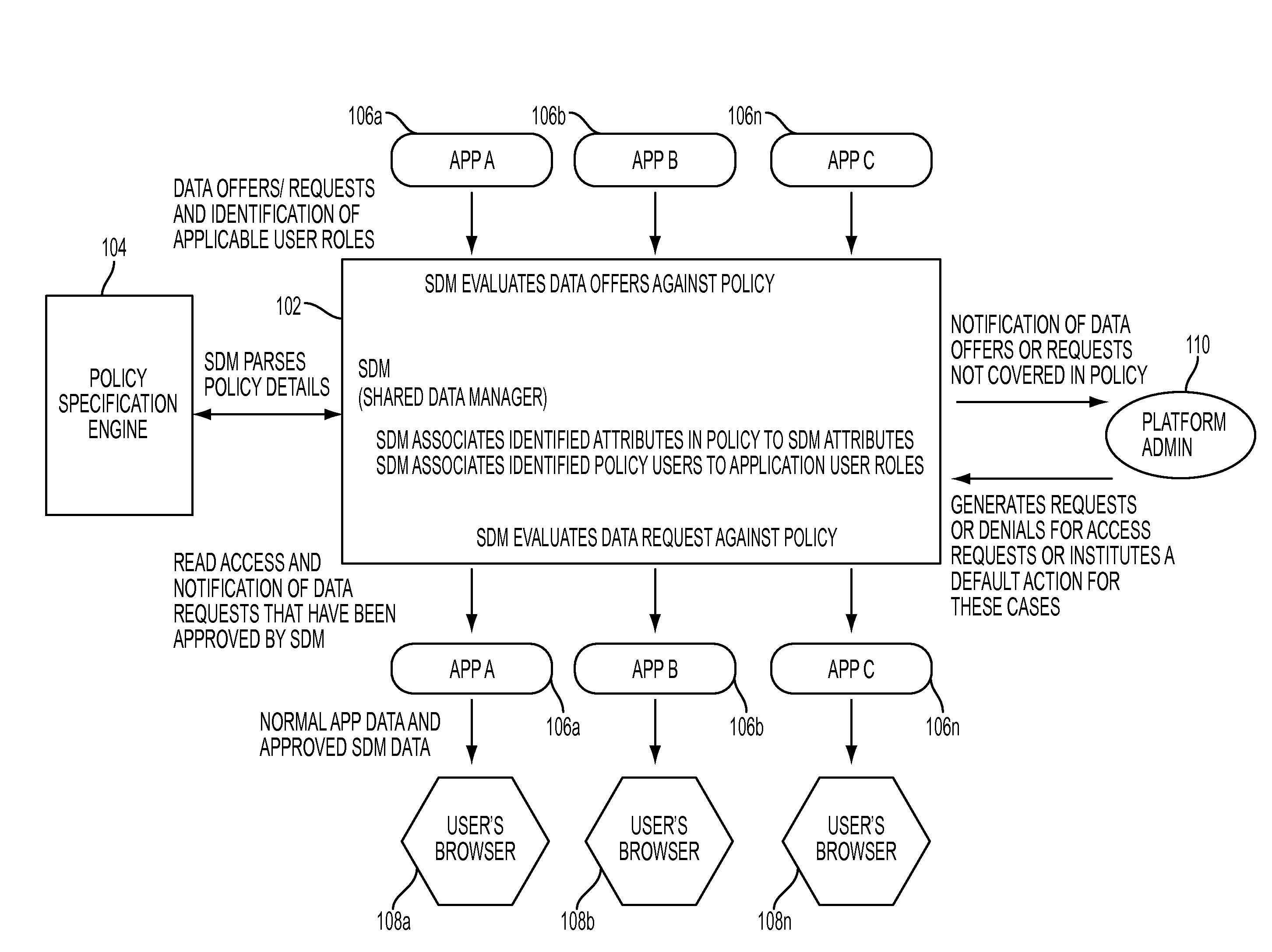
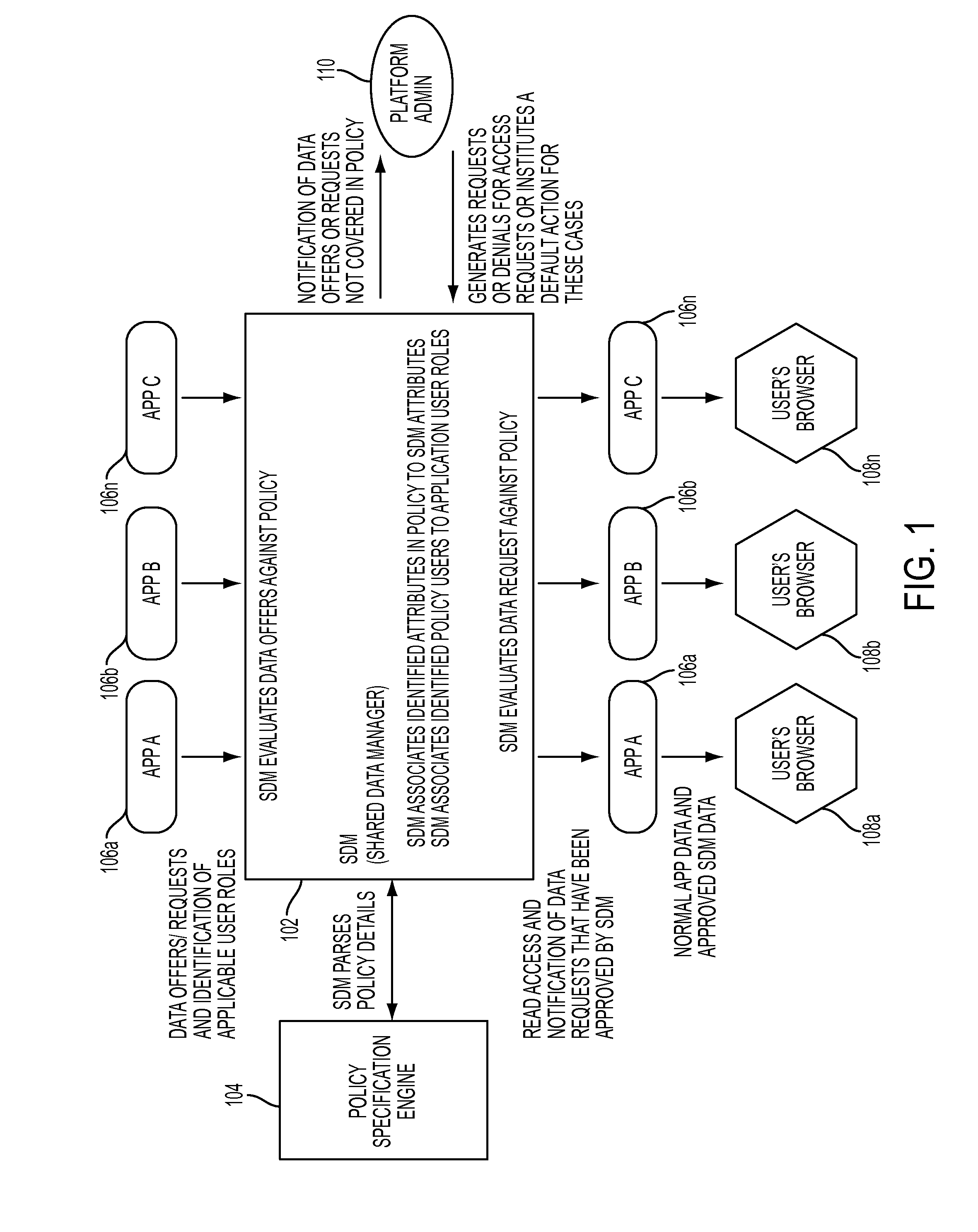
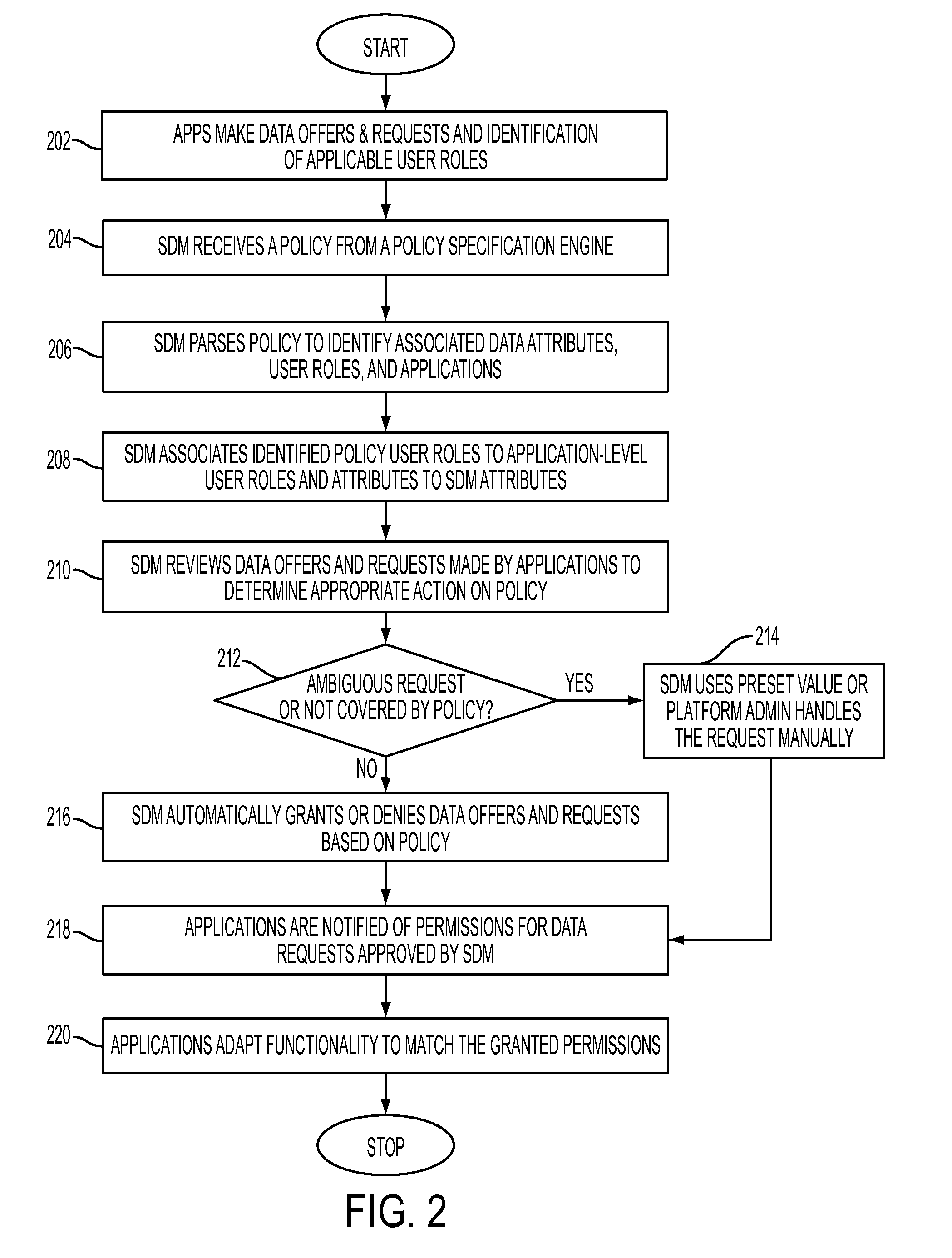
Enforcing data sharing policy through shared data management
InactiveUS8595798B2Digital data processing detailsAnalogue secracy/subscription systemsData accessData domain
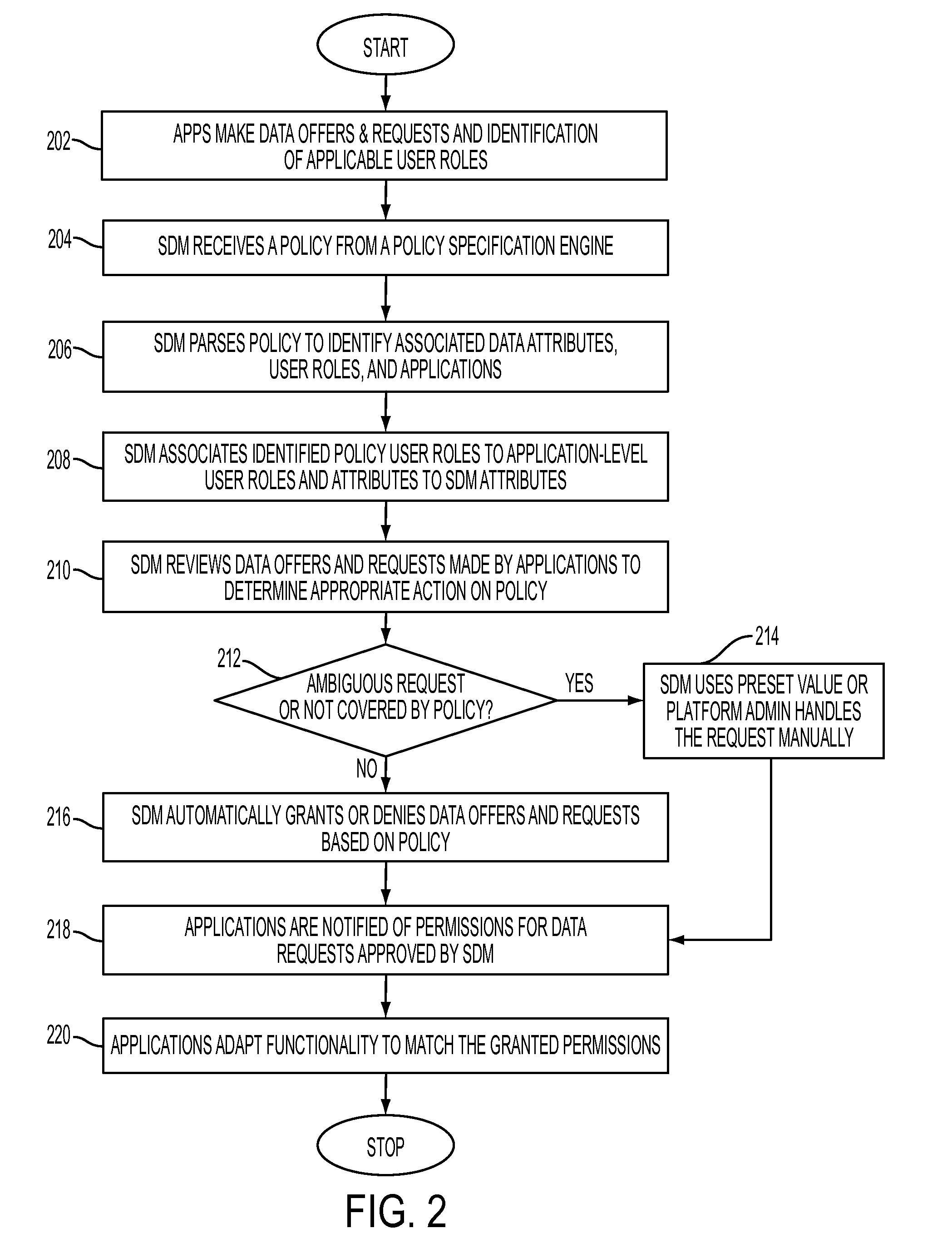
Enforcing data sharing policy through shared data management, in one aspect, may include extracting data access rights from the one or more data policies based on a user role, data purpose, an object set and a constraint identification; extracting a data domain from the one or more data policies based on the data purpose and the object set; associating the data access rights and the data domain with data attributes of the shared data; automatically responding to application-based offers and requests for the shared data within a Software-as-a-Service platform based on the data access rights.
Owner:IBM CORP +1
Methods and systems for validating accessibility and currency of replicated data
ActiveUS7702667B2Digital data information retrievalDigital data processing detailsData systemAccessibility
Systems and processes for determining and validating accessibility and currency, i.e., the actual status, of data replicated in a networked environment are disclosed. According to the disclosed process, a replicated-data policy for replicating data is defined, and access paths between network devices or between applications running on the network devices are monitored, for example, by a replicated-data monitor. Also monitored are the data replication activities in the network. The currency, i.e., timeliness, and accessibility of a replica by a network device is then compared with the requirements in the replicated-data policy and discrepancies with the replicated-data policy are identified, optionally accompanied by a notification.
Owner:NETWORK APPLIANCE INC +1
Enforcing data sharing policy through shared data management
InactiveUS20120324529A1Digital data processing detailsAnalogue secracy/subscription systemsData domainData access
Enforcing data sharing policy through shared data management, in one aspect, may include extracting data access rights from the one or more data policies based on a user role, data purpose, an object set and a constraint identification; extracting a data domain from the one or more data policies based on the data purpose and the object set; associating the data access rights and the data domain with data attributes of the shared data; automatically responding to application-based offers and requests for the shared data within a Software-as-a-Service platform based on the data access rights.
Owner:IBM CORP +1
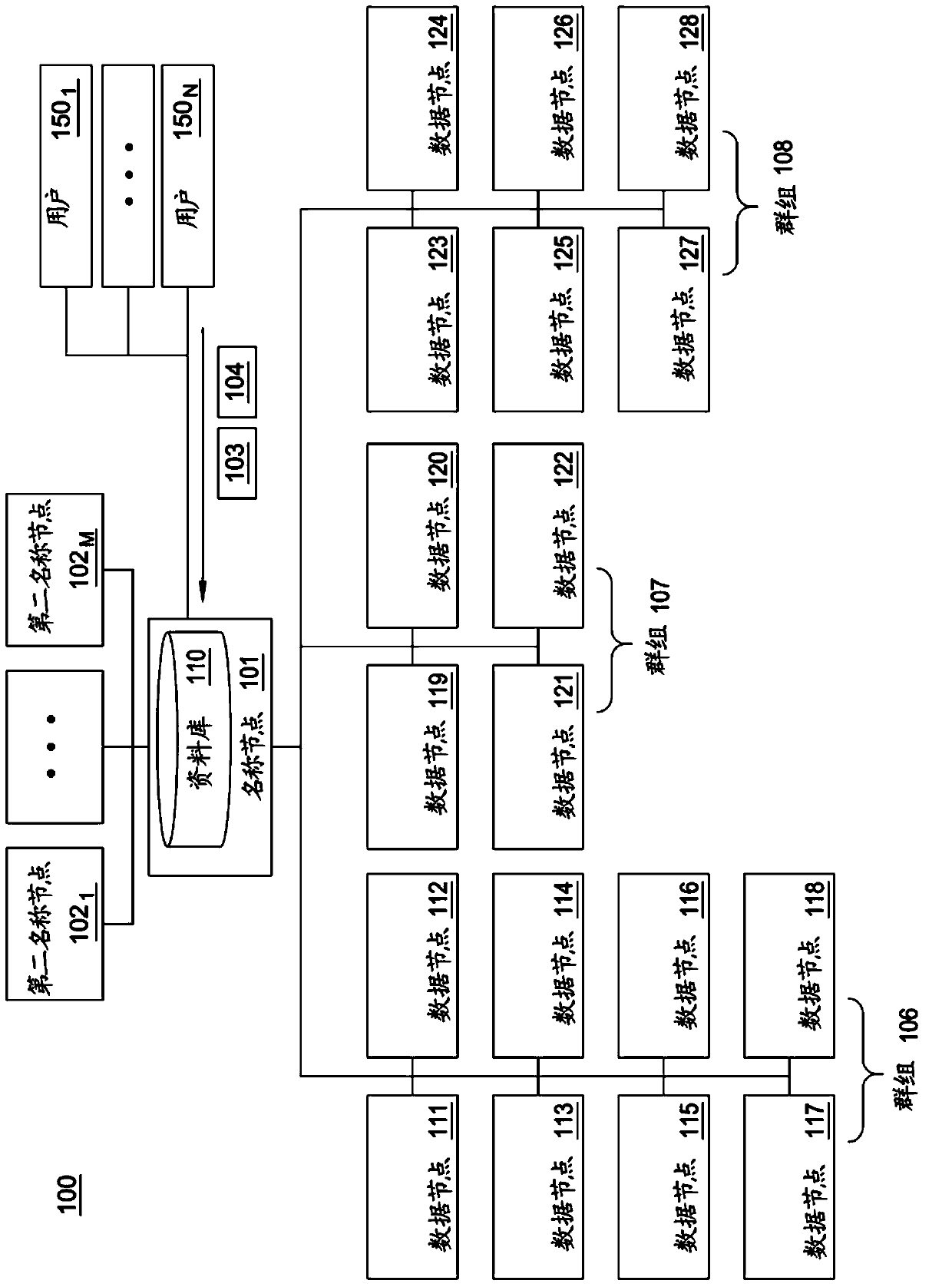
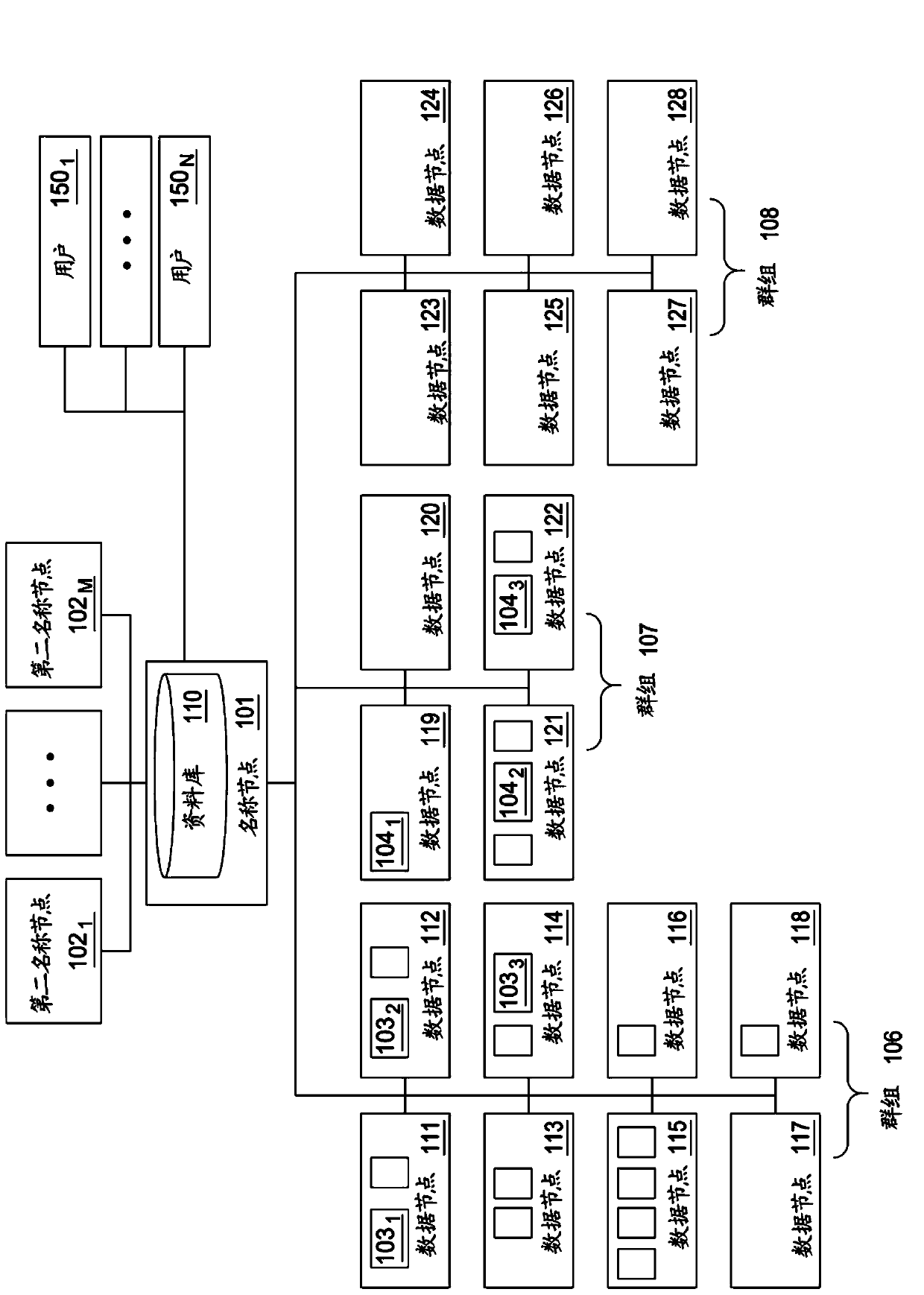
Method and system to select data nodes configured to satisfy a set of requirements
Method, system, and computer program product to select data nodes configured to satisfy a set of requirements for processing client data in a distributed computing environment by providing, for each data node of a plurality of data nodes in the distributed computing environment, nodal data describing the respective data node of the plurality of data nodes, receiving a request to process the client data, the client data being identified in the request, retrieving the set of requirements for processing the client data, and analyzing the retrieved data policy and the nodal data describing at least one of the data nodes, to select a first data node of the plurality of data nodes as a delegation target, the first data node selected based on having a higher suitability level for satisfying the set of requirements than a second data node of the plurality of data nodes.
Owner:IBM CORP
System and method for managing data policies on application objects
ActiveUS8650165B2Digital data processing detailsError detection/correctionData managementApplication software
Described herein are systems and methods for providing data policy management over application objects in a storage system environment. An application object may comprise non-virtual or virtual objects (e.g., non-virtual-based applications, virtual-based applications, or virtual storage components). An application object manager may represent application objects by producing mapping graphs and / or application object data that represent application objects in a standardized manner. A mapping graph for an application object may describe a mapping between the application object and its underlying storage objects on a storage system. Application object data may describe a mapping graph in a standardized format. Application object data representing application objects may be received by an application policy manager that manages data policies on the application objects (including virtual applications and virtual storage components) based on the received application object data. Data policies may include policies for backup, service level objectives, recovery, monitoring and / or reporting.
Owner:NETWORK APPLIANCE INC
Data mining-based real estate client interpretation method and apparatus
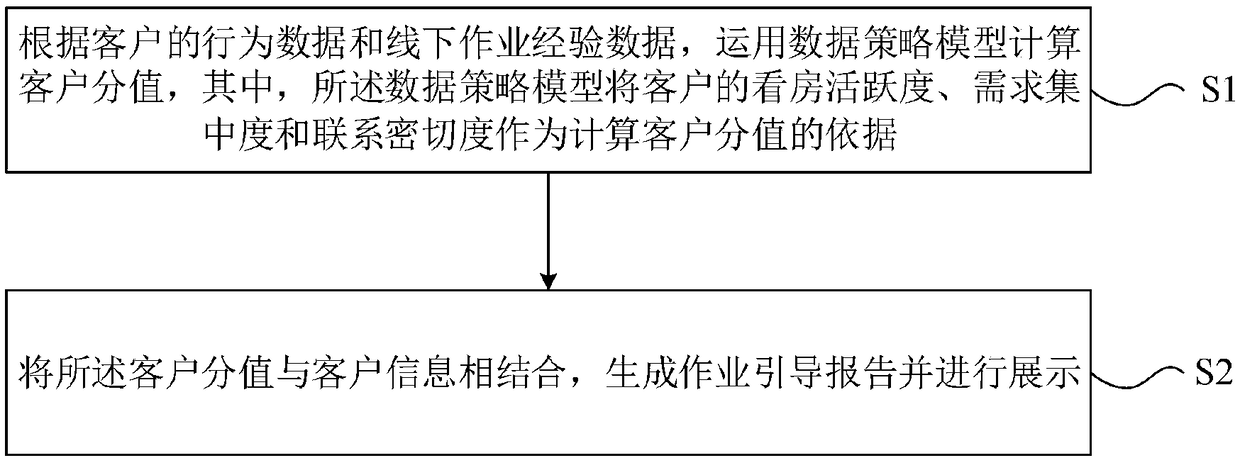
InactiveCN108389068AInterpret data effectivelyEasy to carry outMarket predictionsMarket data gatheringData dredgingData mining
The invention provides a data mining-based real estate client interpretation method and apparatus. The method comprises the steps of S1, according to behavior data and offline job experience data of aclient, calculating a client score by applying a data policy model, wherein the data policy model takes house seeing activeness, demand concentration degree and relationship closeness of the client as bases for calculating the client score; and S2, combining the client score with client information to generate a job guide report, and performing display. The job guide report can be automatically generated according to the client information; effective client interpretation data is provided; a real estate broker is assisted to better carry out related services; and an existing platform takes aneffect of guiding a business job.
Owner:KE COM (BEIJING) TECHNOLOGY CO LTD
Method and device for accurate matching based on policies and client big data
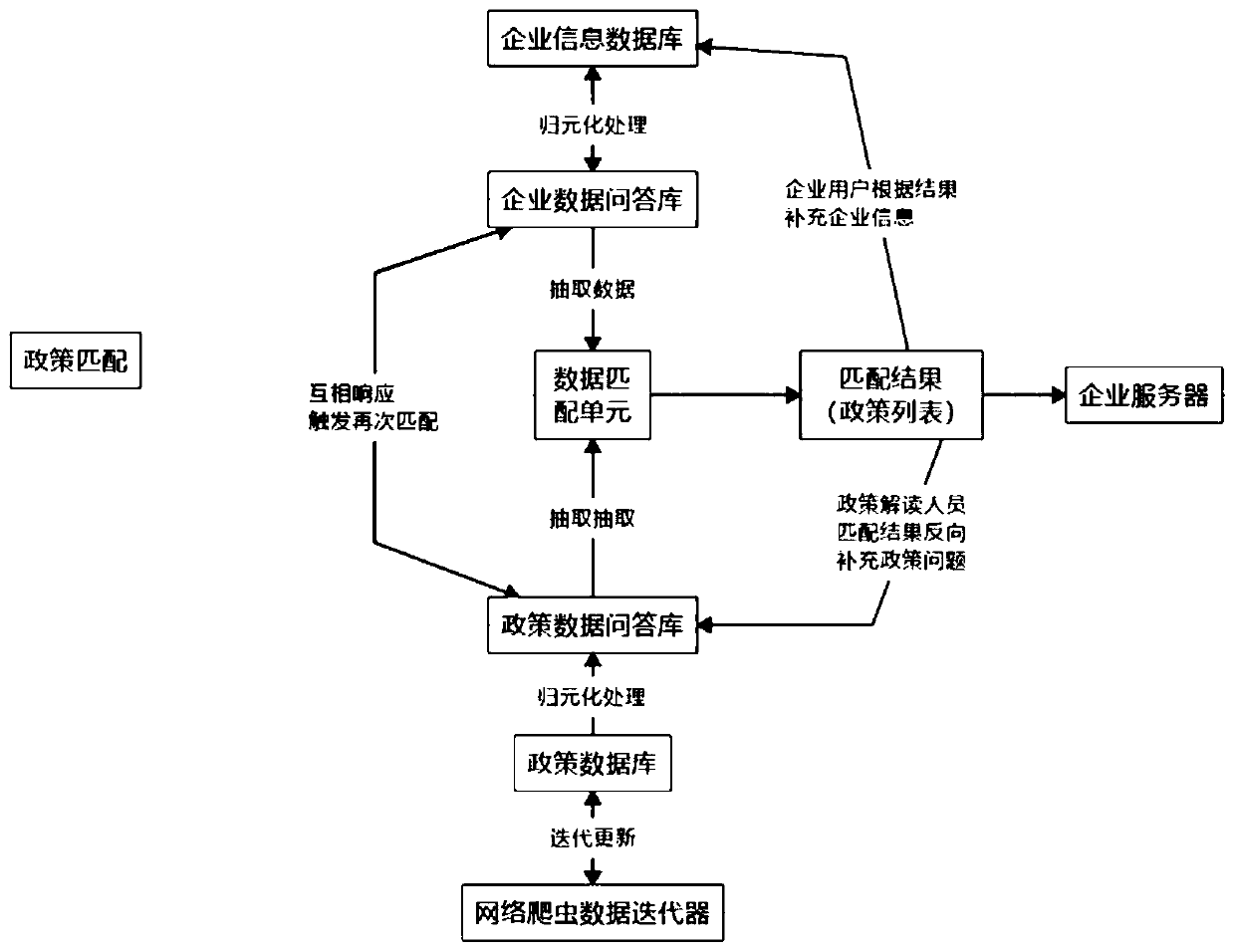
InactiveCN110297892AActive pushPrecise pushText database queryingSpecial data processing applicationsQuestions and answersData policy
The invention provides a method and device for accurate matching based on policies and client big data, and belongs to the technical field of computers, for solving the problem that policies issued bygovernments are asymmetric to policy data digestible by enterprises. The method and device can generate enterprise data question and answer library through enterprise basic information input by an enterprise, and can realize bidirectional interaction and matching with the policy data question and answer library collected according to the system, so that accurate pushing of data policies can be completed according to the condition of the enterprise.
Owner:八戒科技服务有限公司
A data management and control system based on big data
InactiveCN109034532AStandard operation modeTimely responseOffice automationResourcesData controlProcess module
The invention provides a data management and control system based on big data, which comprises a data management and control organization module, an evaluation and assessment module, a management andcontrol process module and a management and control platform. The invention defines the organization structure, roles and responsibilities in the data management and control process, and standardizesthe daily task processing mode of each joint in the process of data management and control. By establishing some qualitative or quantitative data control evaluation indicators, the method evaluates and assesses the performance of the data-related responsible person, the implementation of data control standards and data policies, adopts a special technical platform to support the automation of themanagement process, publishes some relevant standards and specifications formulated by the control organization, and timely reflects some problems existing in the control process.
Owner:江苏网域科技有限公司
User-controlled centralized privacy marketplace system
A system for managing personal information of a user includes: a personal information database including personal information records of the user including data associated with the user, wherein a user is associated with a data policy including at least one permission for an accessing party to interact with a personal information record; and a data access module that receives and responds to requests from an accessing party, wherein a request may be one of: a read request specifying a personal information record to be read; and a write request specifying a personal information to be written to a personal information record to be written, wherein in response to a write request, the data access module responds with the a personal information record to be read, or updates the personal information record to be written in the personal information database, if permitted by the personal information record the privacy policy.
Owner:VESTEVICH JACQUELINE K
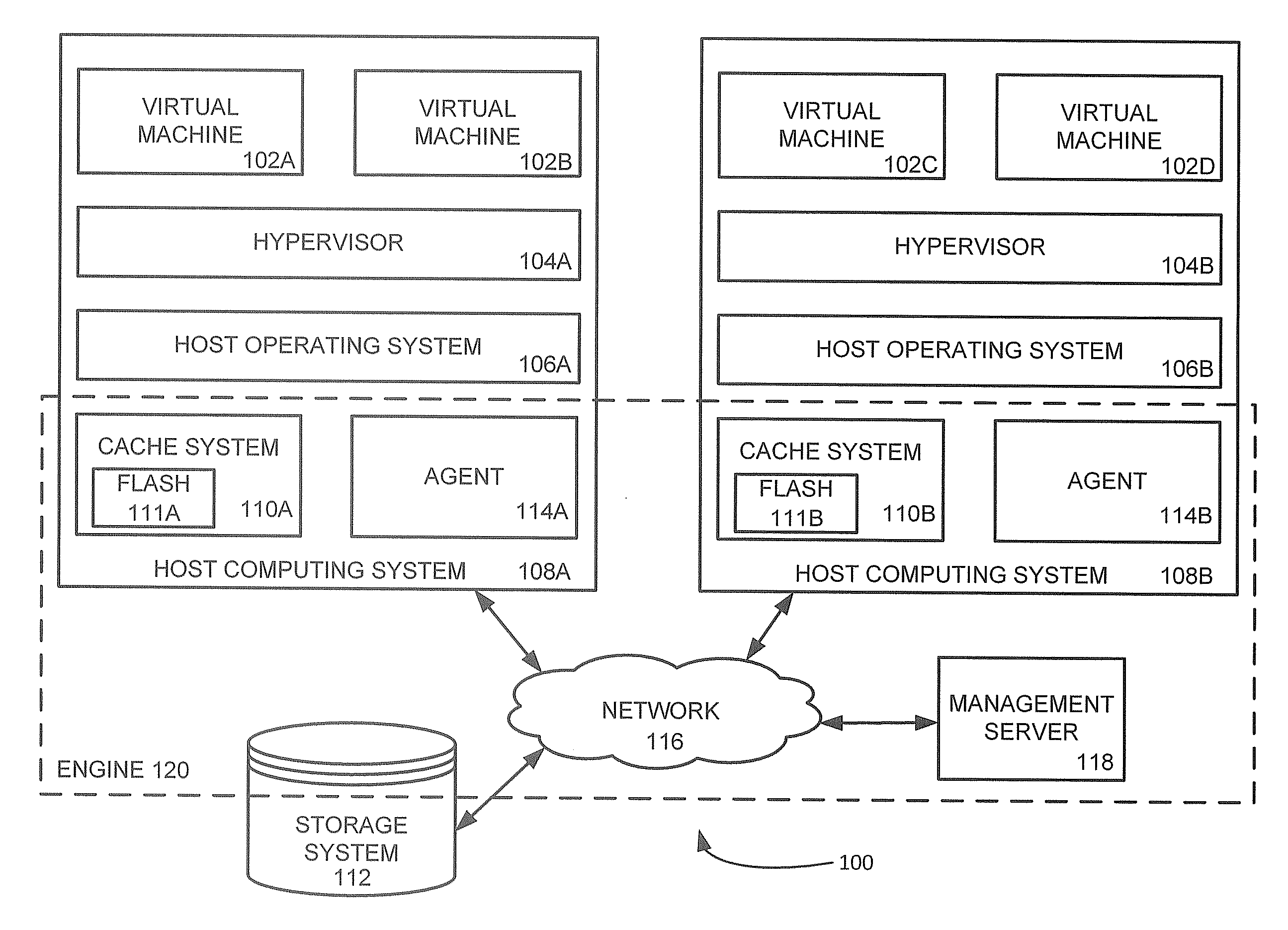
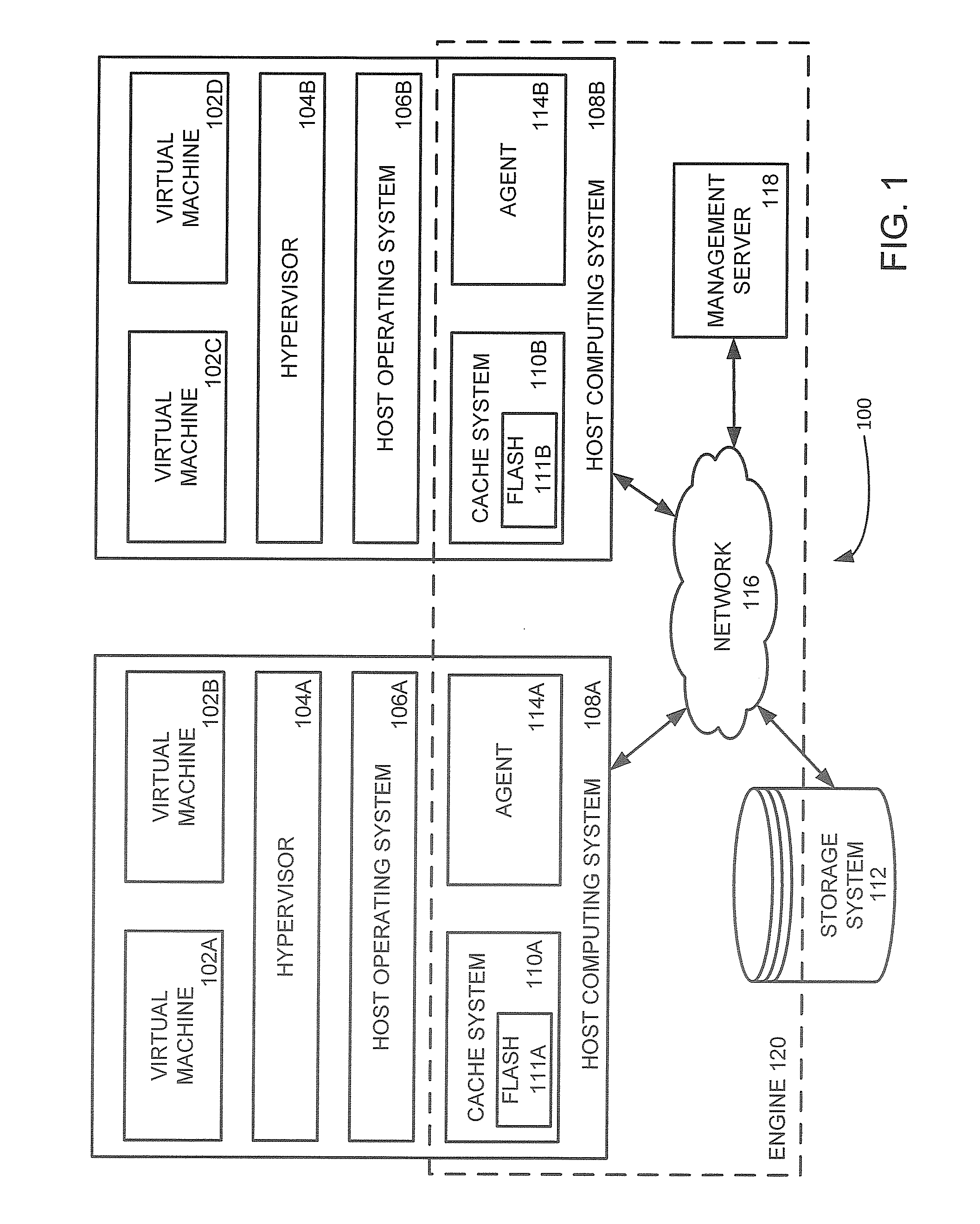
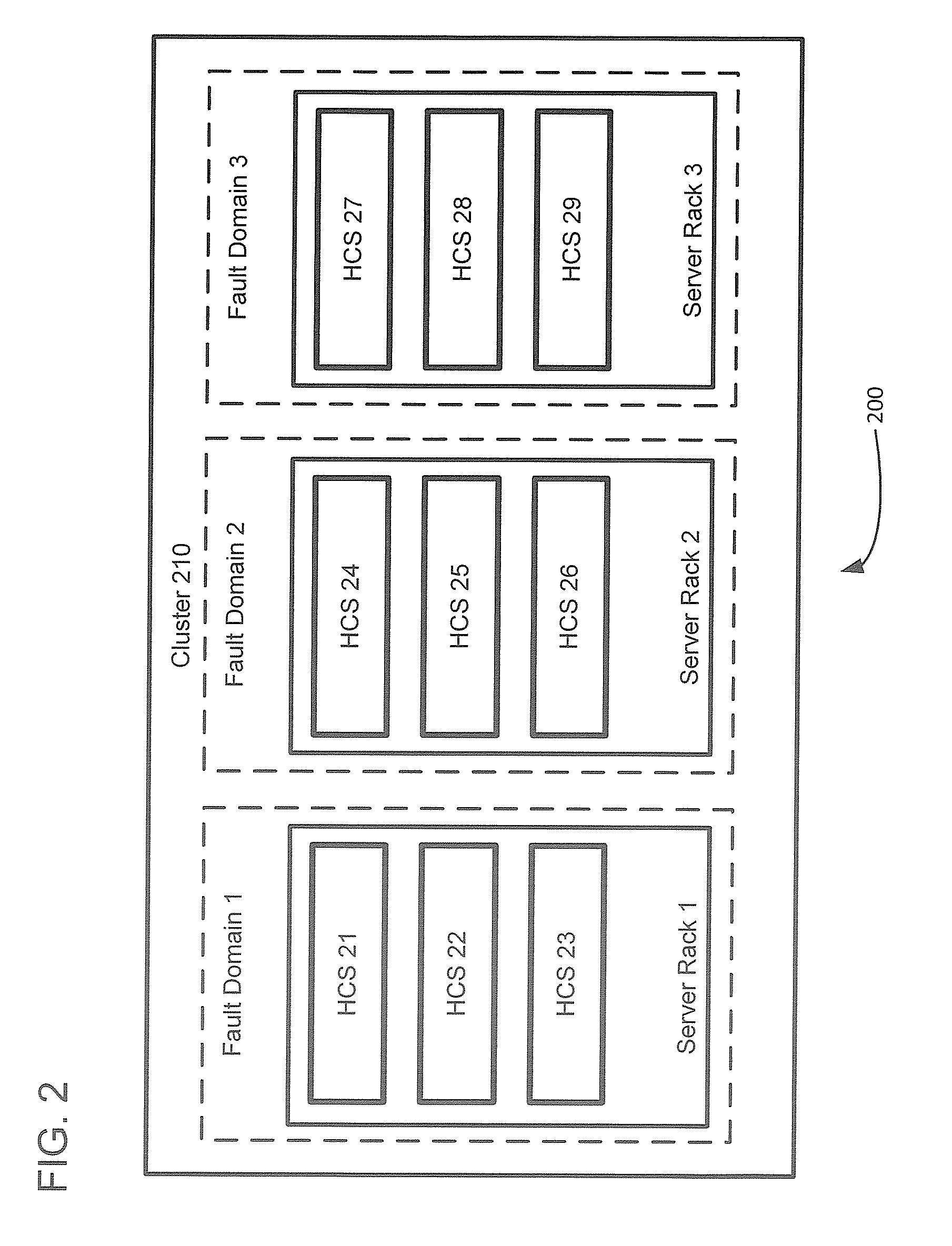
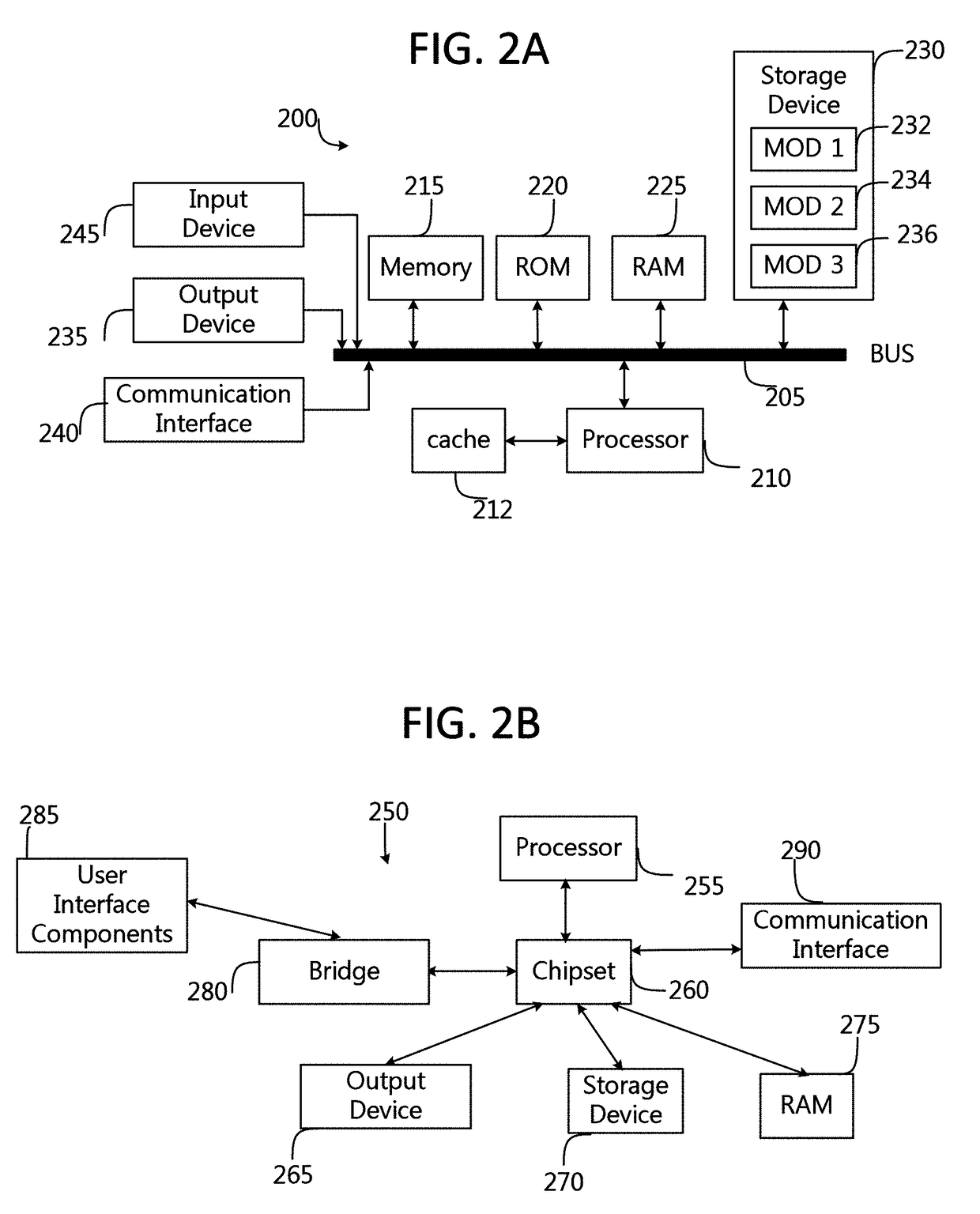
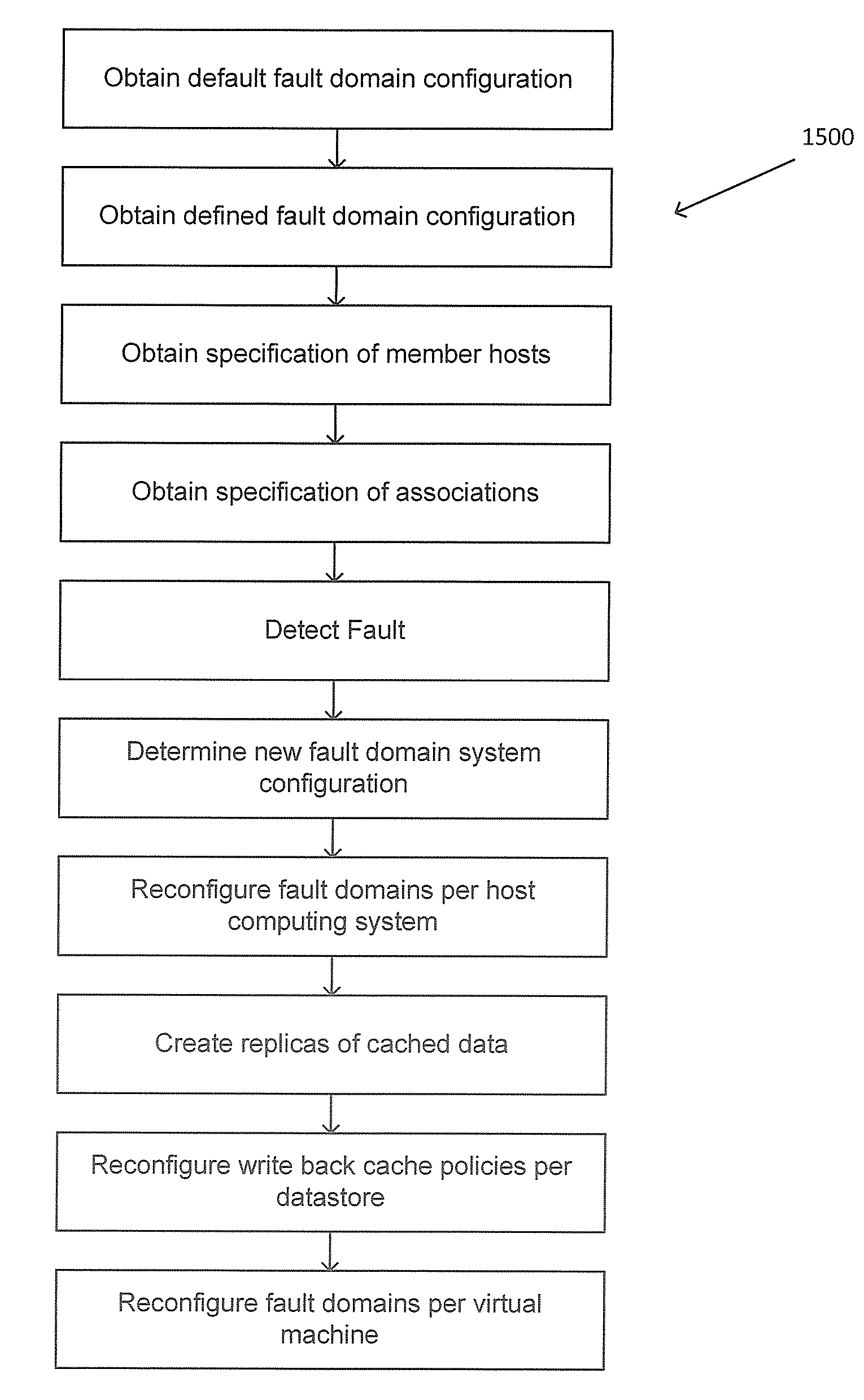
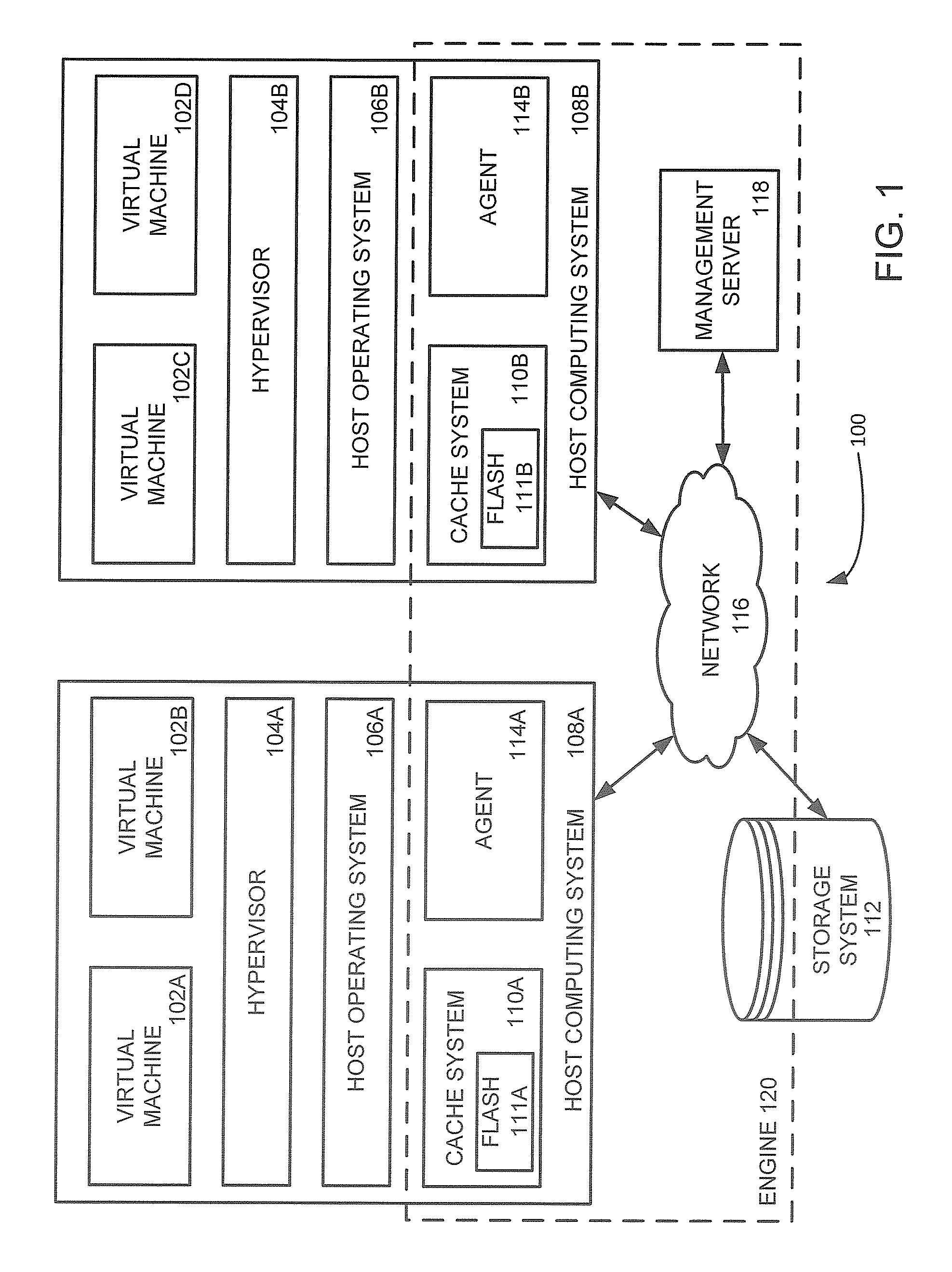
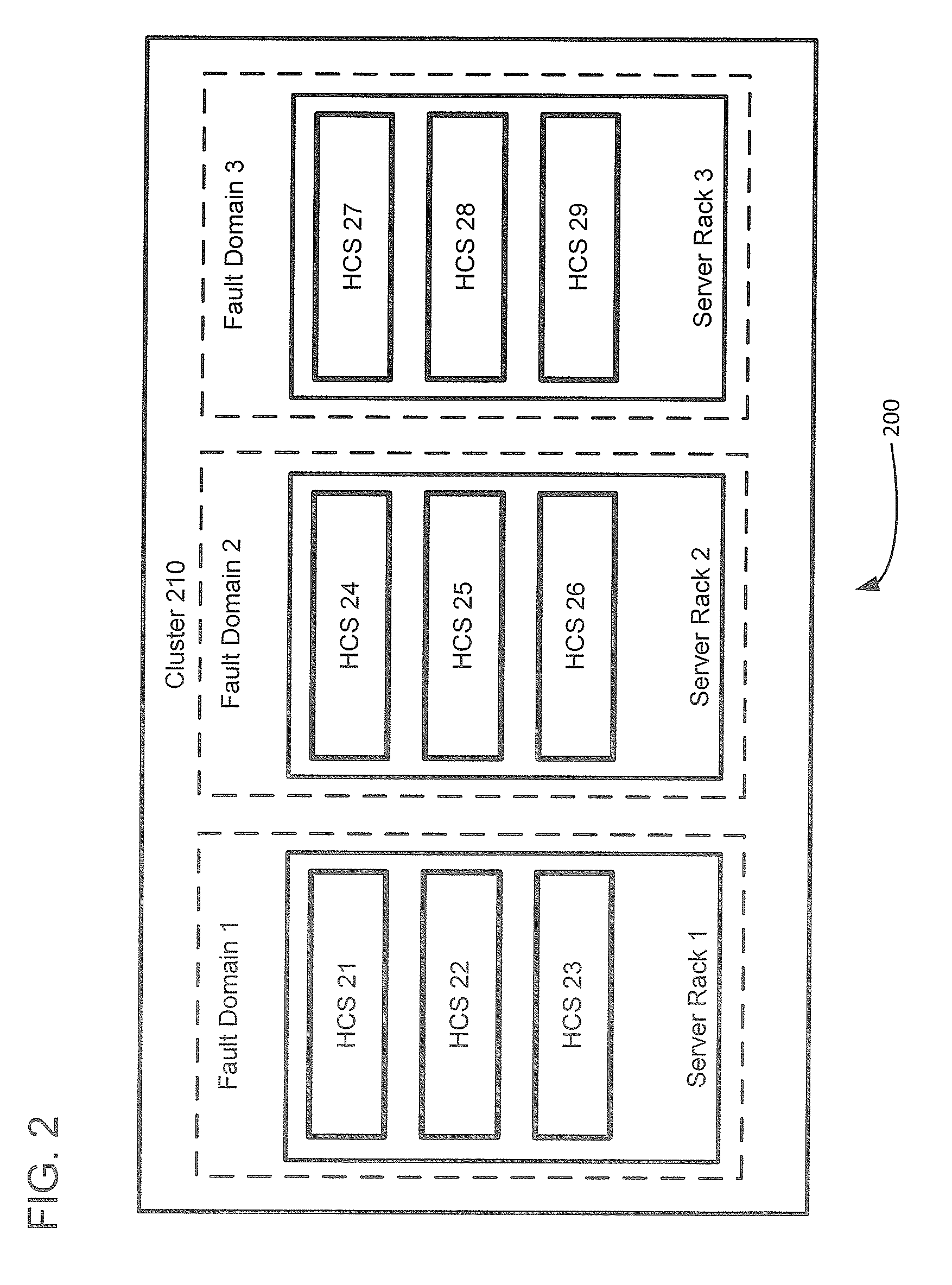
Management and utilization of fault domains in distributed cache systems
ActiveUS20160314051A1Memory architecture accessing/allocationMemory adressing/allocation/relocationReplication methodDistributed cache
Fault domains are defined which reflect, either physically or virtually, the topology of a networked computing environment. These defined fault domains are then used to control where cached data is replicated when running in a write back cache mode. Unlike known replication approaches, the present approach replicates such data according to a user's defined data policy and based on the defined fault domains thereby avoiding the user having to keep track of changes in computing system configurations or update their data policy when virtual machines migrate from one host computing system to another.
Owner:PERNIXDATA
Symmetric bi-directional policy based redirect of traffic flows
Disclosed are systems, methods, and computer-readable storage media for guaranteeing symmetric bi-directional policy based redirect of traffic flows. A first switch connected to a first endpoint can receive a first data packet transmitted by the first endpoint to a second endpoint connected to a second switch. The first switch can enforce an ingress data policy to the first data packet by applying a hashing algorithm to a Source Internet Protocol (SIP) value and a Destination Internet Protocol (DIP) value of the first data packet, resulting in a hash value of the first data packet. The first switch can then route the first data packet to a first service node based on the hash value of the first data packet.
Owner:CISCO TECH INC
Management and utilization of fault domains in distributed cache systems
ActiveUS9588855B2Memory architecture accessing/allocationMemory adressing/allocation/relocationReplication methodDistributed cache
Fault domains are defined which reflect, either physically or virtually, the topology of a networked computing environment. These defined fault domains are then used to control where cached data is replicated when running in a write back cache mode. Unlike known replication approaches, the present approach replicates such data according to a user's defined data policy and based on the defined fault domains thereby avoiding the user having to keep track of changes in computing system configurations or update their data policy when virtual machines migrate from one host computing system to another.
Owner:PERNIXDATA
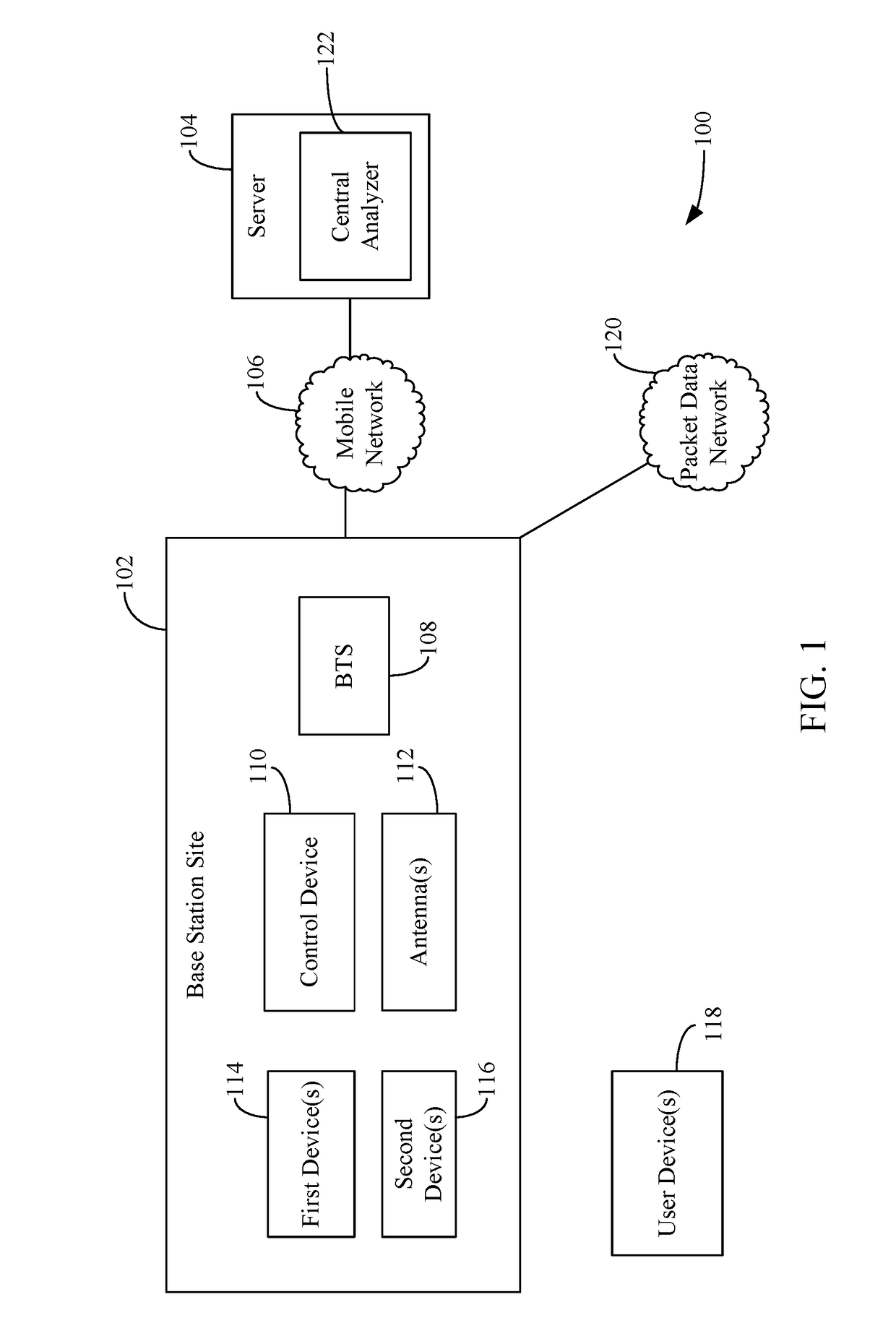
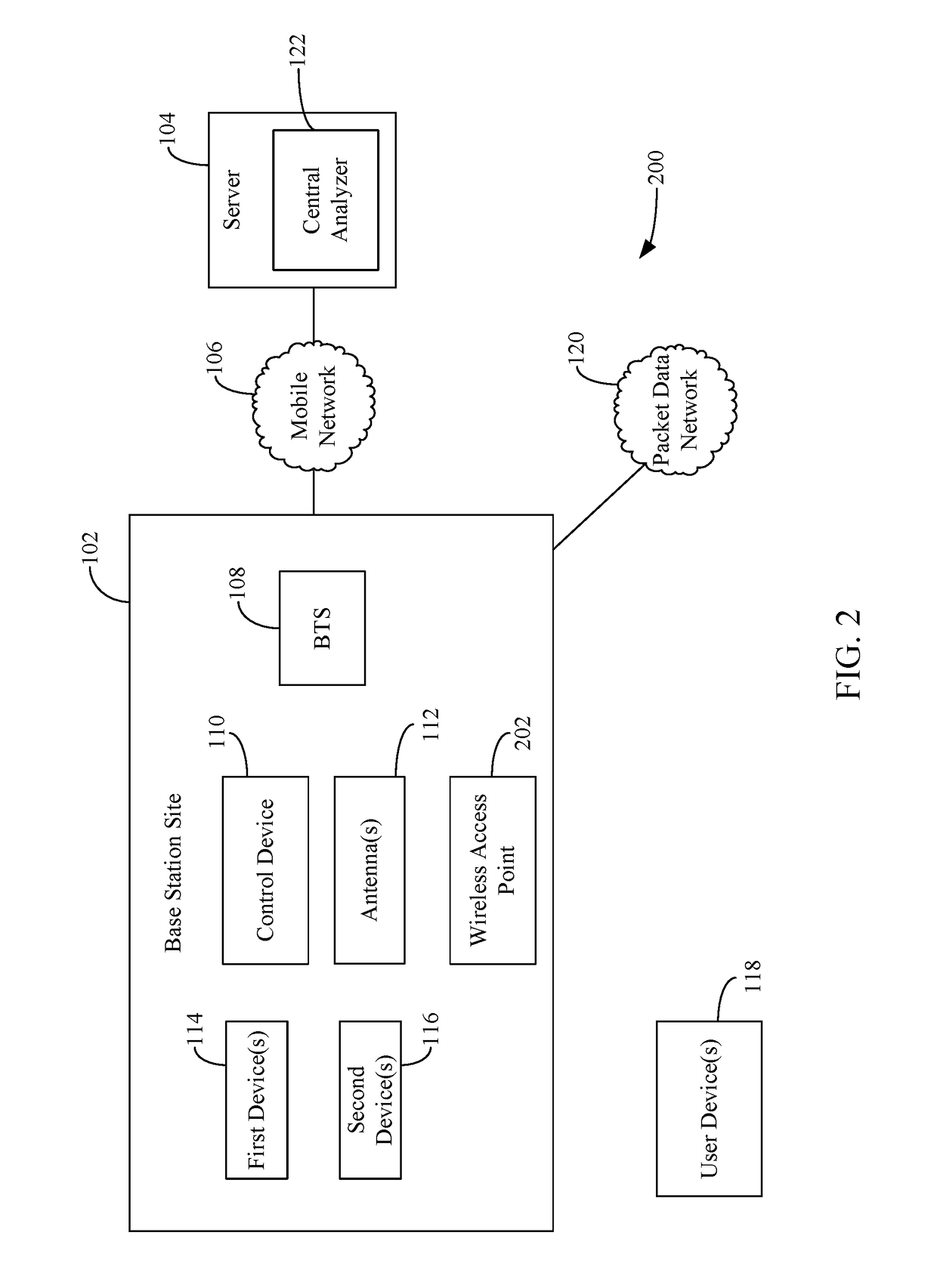
Remote management of base stations and/or the functions performed thereby
InactiveUS20180376358A1Data switching networksWireless communicationUser deviceWireless access point
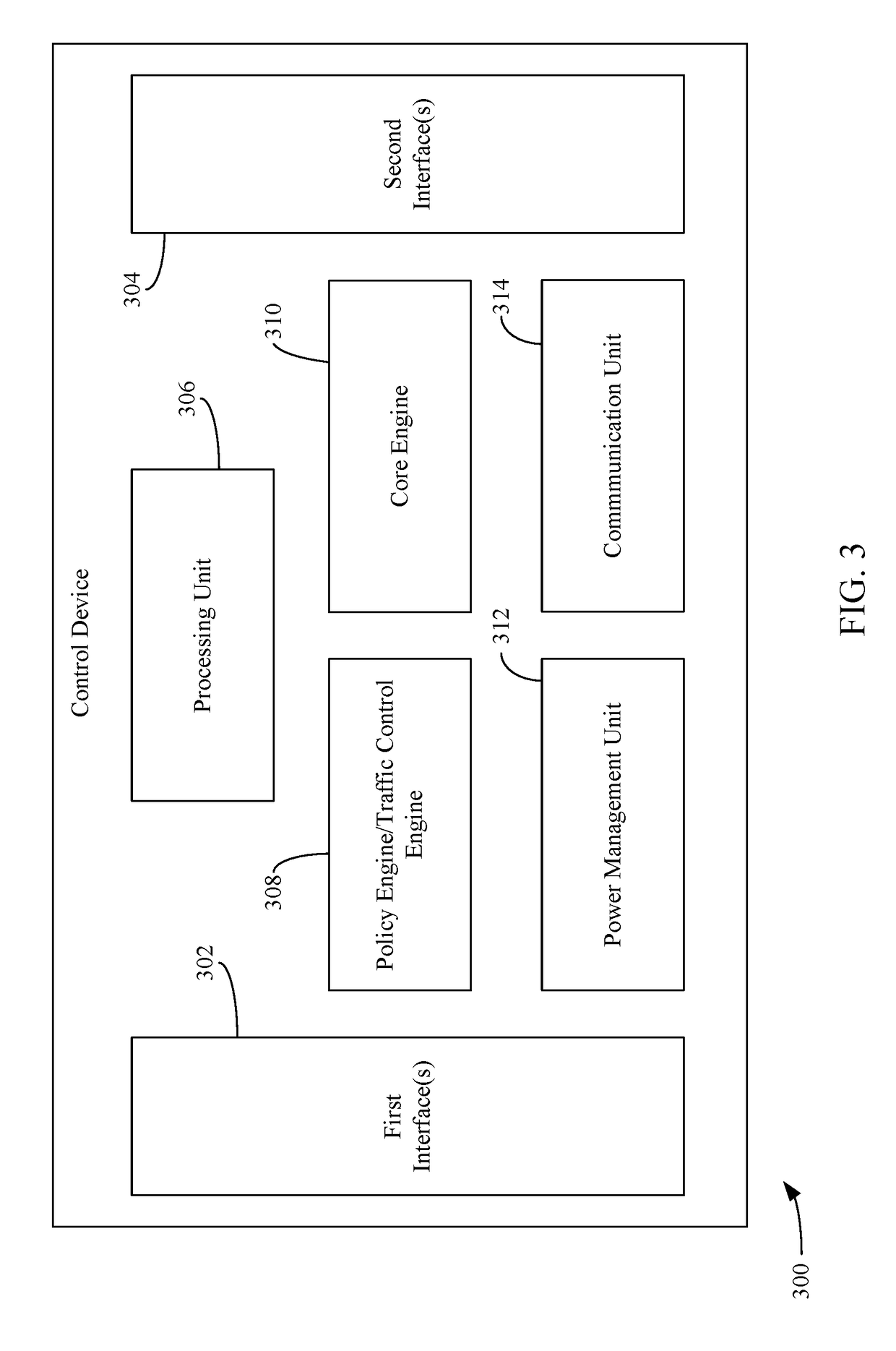
Embodiments described herein are directed to a control device that is configured to monitor parameter(s) associated with device(s) located at a site. The control device performs action(s) based on the monitored parameter(s). The control device sends command(s) to the device(s) that cause the device(s) to perform a certain function or operation based on the monitored parameter(s). The control device may also provide the parameters and / or other information provided by the device(s) to a centralized server for further monitoring and / or processing. The centralized server receives information from a plurality of control devices located at a plurality of different sites and provide commands to the control devices based on the received information. In addition, the control device determines whether a user device is connected to a base station or a wireless access point located at the site and provide / receive data in accordance with a data policy enforceable by the control device.
Owner:TAMBORA SYST SINGAPORE PTE LTD
Apparatus and method for establishing seamless secure communications between components in an industrial control and automation system
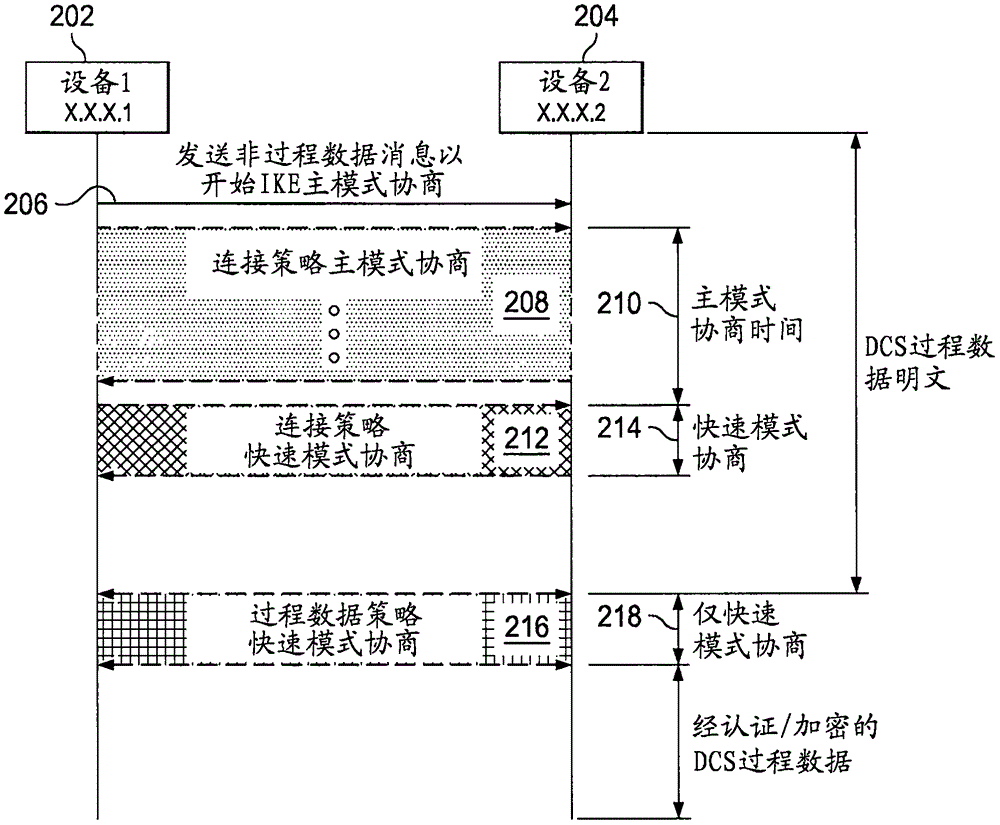
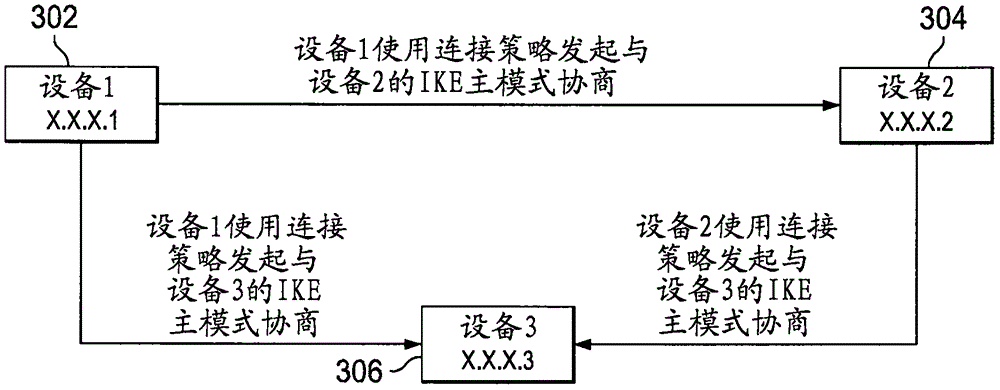
A method includes establishing (408), using a connection policy at a first device (202, 204, 302, 304, 306), a security association with a second device (202, 204, 302, 304, 306) of an industrial process control and automation system (100). The method also includes, once the security association is established, activating a process data policy at the first device. The security association is established during first and second types of negotiations (406). The process data policy is activated during the second type of negotiation (412) without the first type of negotiation. The second type of negotiation is faster than the first type of negotiation. The connection policy defines a communication channel between the devices using a non-process communication port of the first device. The process data policy defines a communication channel between the devices for real-time industrial process data. The first type of negotiation could include an IKE main mode negotiation, and the second type of negotiation could include an IKE quick mode negotiation.
Owner:HONEYWELL INT INC
Privacy protection method for big data in cloud computing
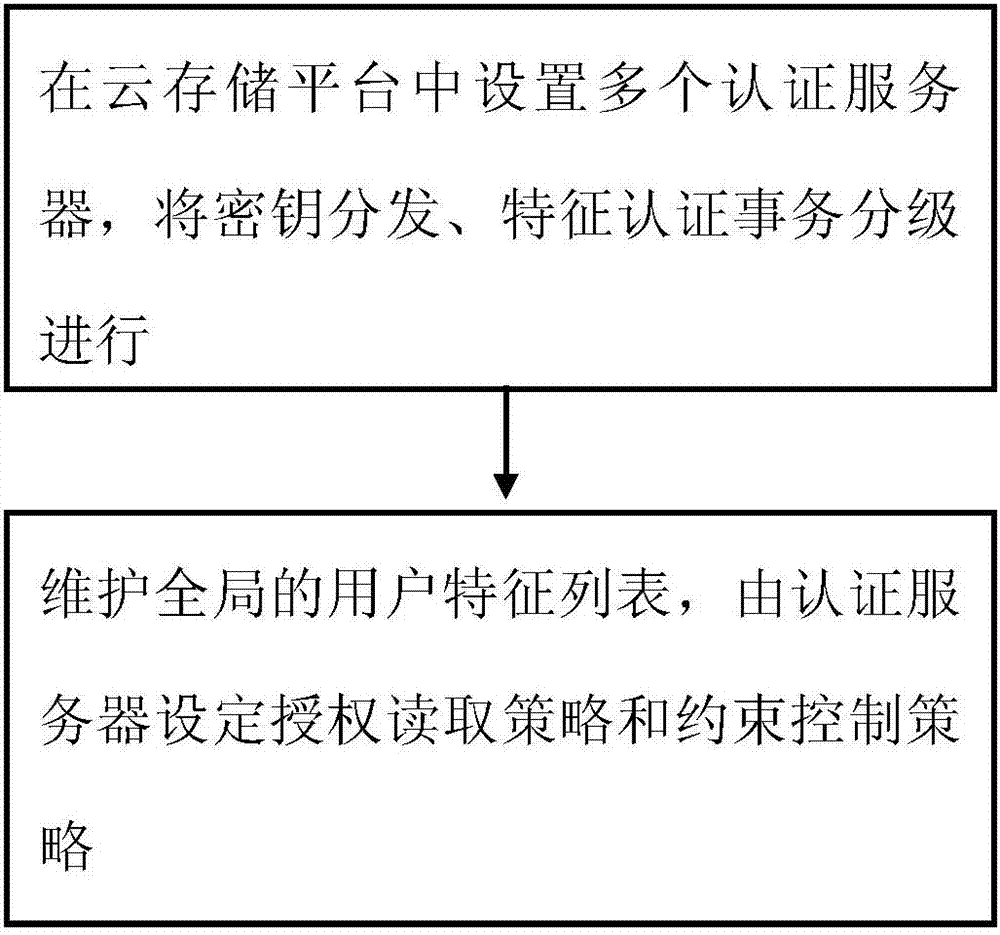
InactiveCN107483200AReduce computational costMeet application needsKey distribution for secure communicationPrivacy protectionConstraint control
The invention provides a privacy protection method for big data in cloud computing. The method includes the steps of setting a plurality of authentication servers in a cloud storage platform, and conducting secret key distribution and character authentication transaction processing by class; maintaining a global user character list, wherein the authentication servers set an authorization reading policy and a constraint control policy. The privacy protection method for the big data in the cloud computing enhances safe reading policy control of environment and policy constraints, reduces computing costs of writing users on the premise of ensuring safety, and meets application demands of various cross-cloud cross-class data policies.
Owner:CHENGDU DINGZHIHUI TECH
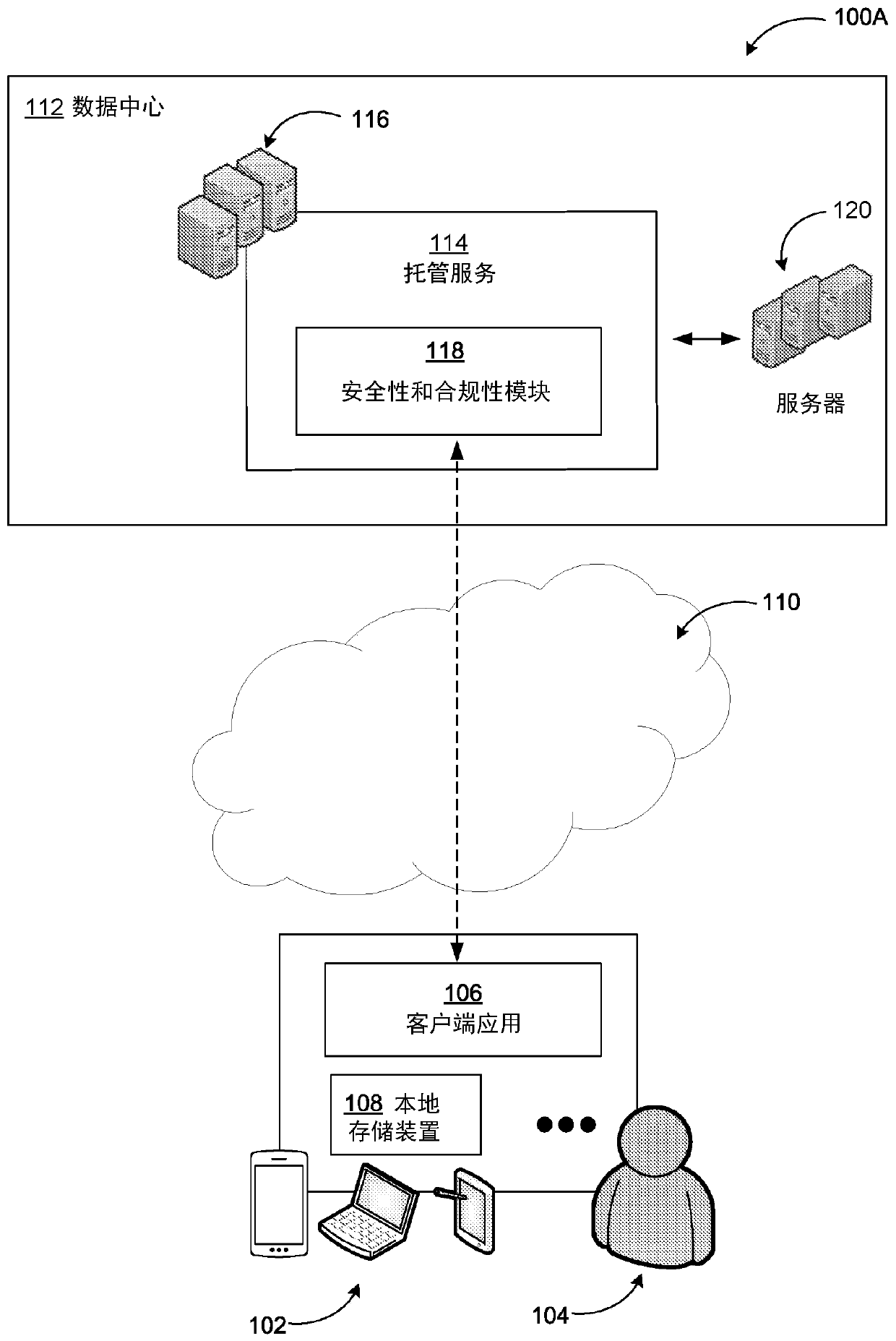
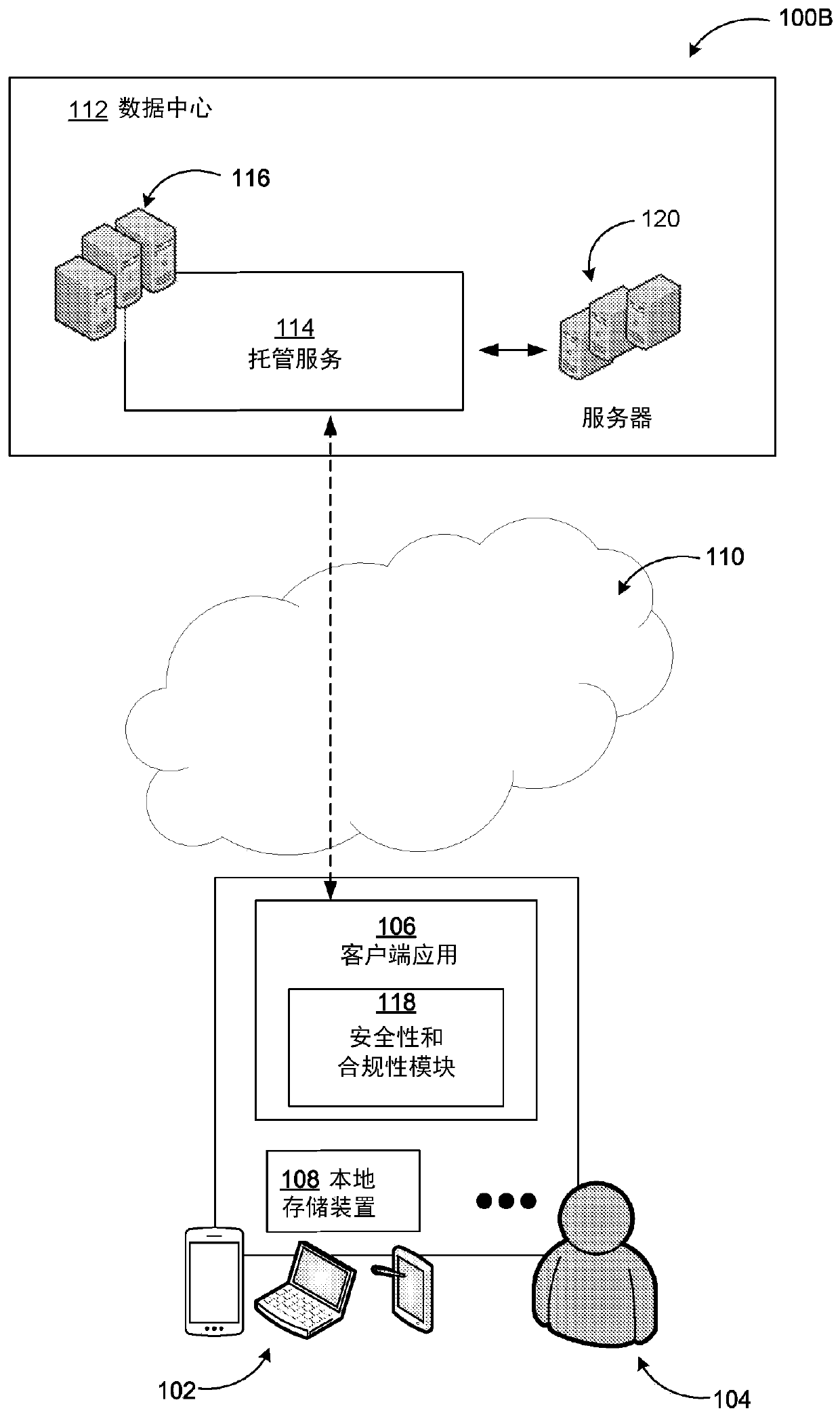
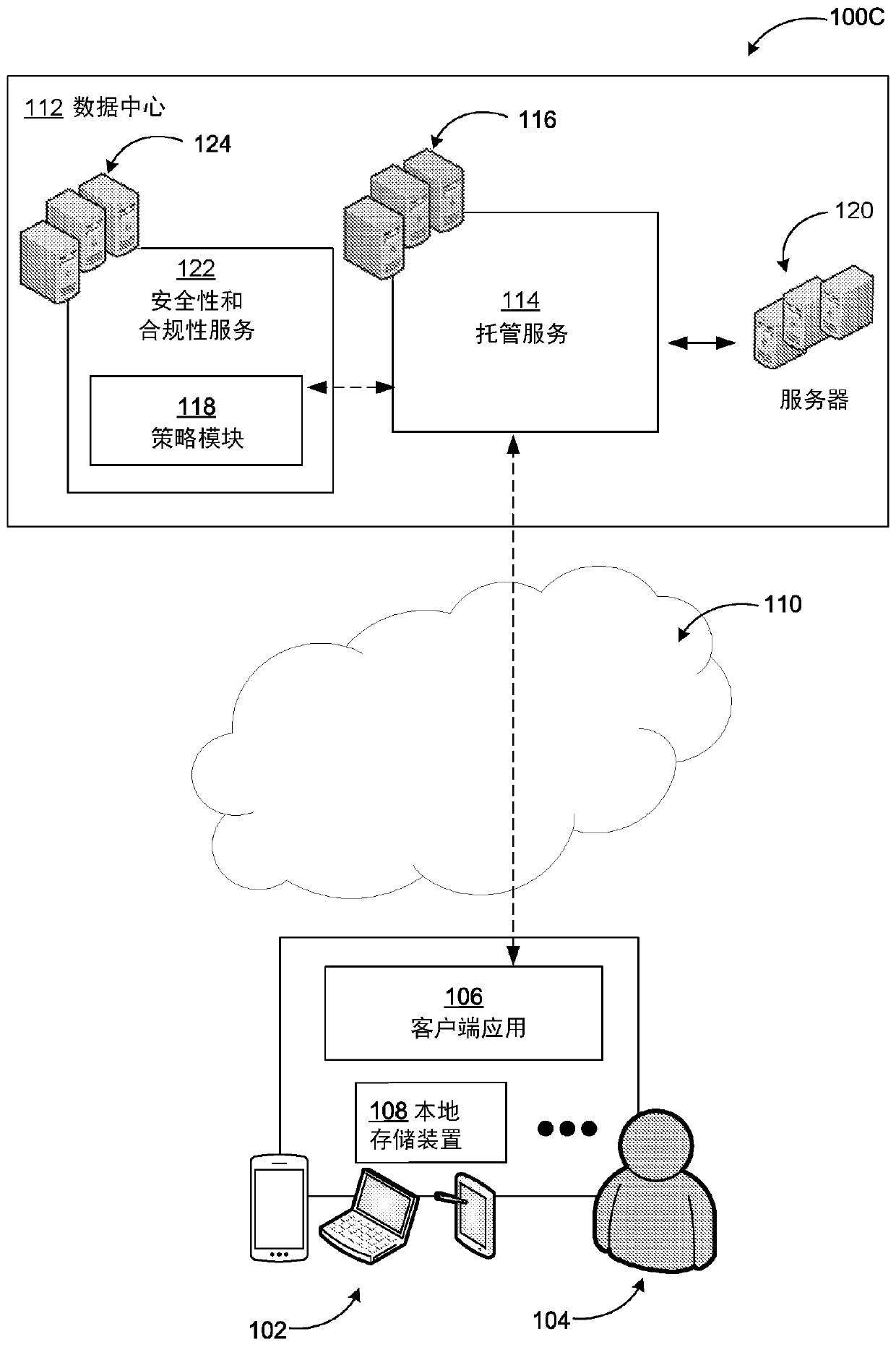
Policies based on classification of groups, teams, and sites
Information technology use policies based on classification of groups, teams, and sites is provided. Example systems may enable information technology administrators to specify which policies may apply based on manual or automatic classification of groups, teams and sites. This may include the ability to specify associated membership, sharing, and access policies, data storage and sharing locations, retention policies for different types of content, and application of various information governance and protection options / requirements. Information technology administrators, who inherently understand the data and information management needs of organizations and members, may define a reasonable set of simplified classification options that information workers can use. Thus, information workers may no longer need to learn the details of data policies. They can simply select the proper data classification, and the security and compliance service may automatically configure the associated groups, teams, sites, and associated data.
Owner:MICROSOFT TECH LICENSING LLC
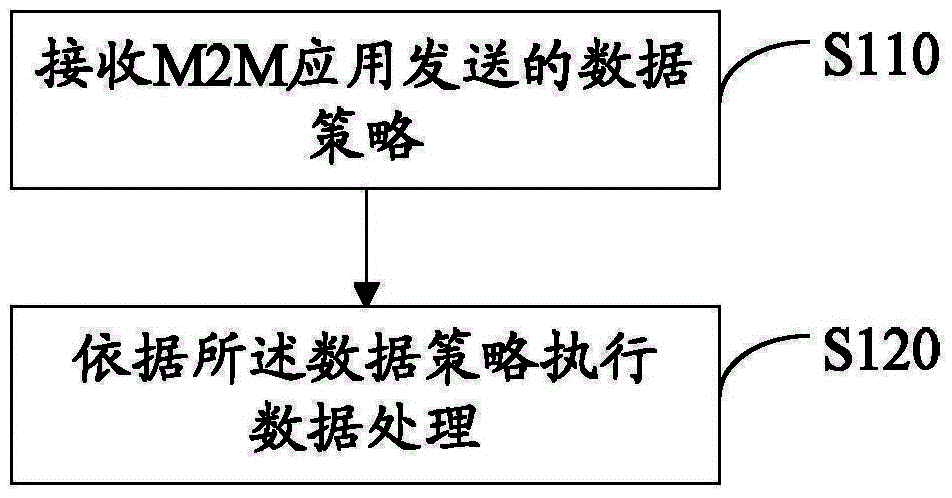
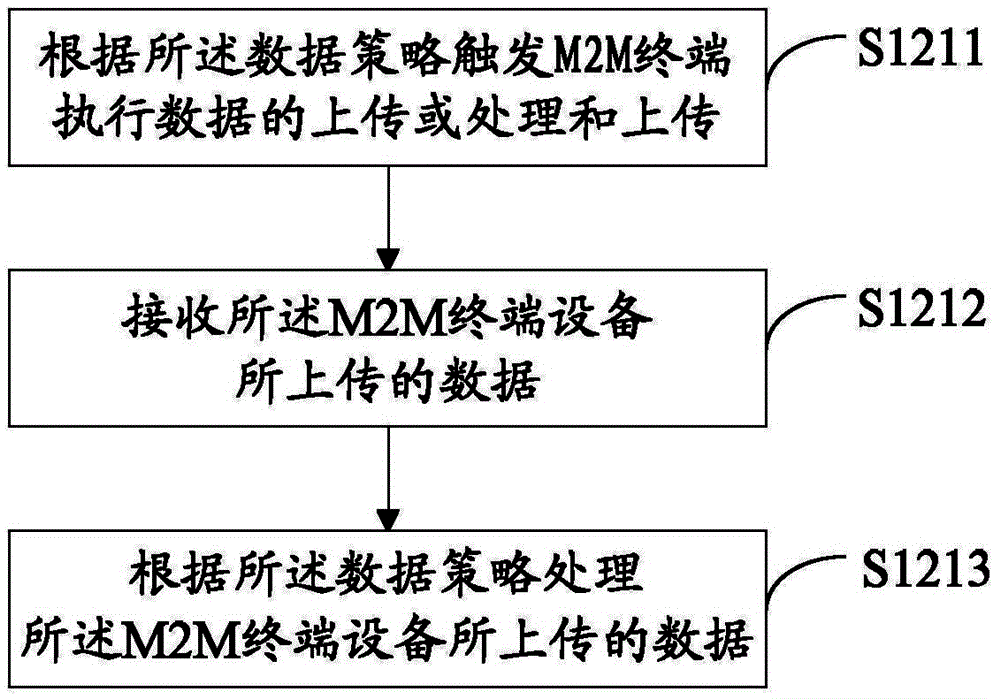
Method, device and system for processing M2M system data
InactiveCN104796844AAvoid processing disorderImprove satisfactionNetwork traffic/resource managementWireless commuication servicesComputer scienceData policy
A data processing method, an apparatus and a system for an M2M system, which relates to the field of data processing. The data processing method for an M2M system comprises: receiving a data policy sent by an M2M application, and performing data processing according to the data policy. Also disclosed are a mobile terminal and a computer storage medium. Further disclosed is a computer storage medium in which a computer executable instruction is stored.
Owner:ZTE CORP
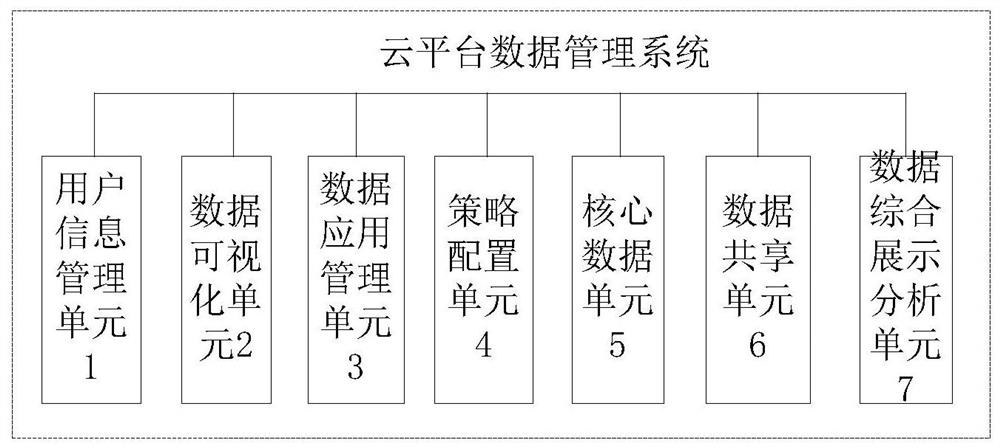
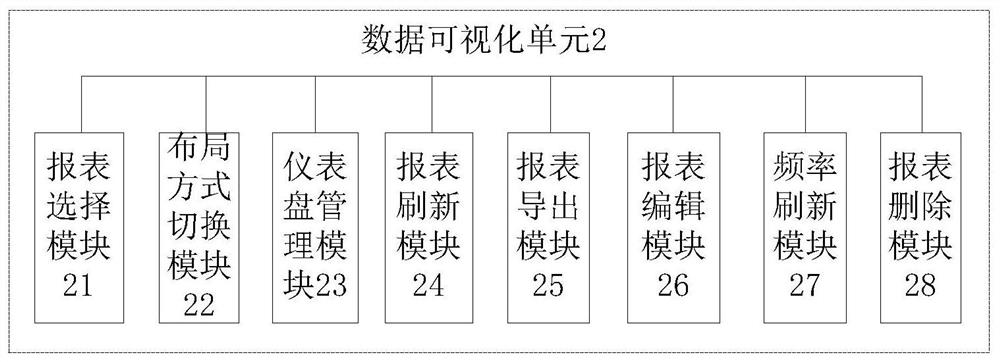
Cloud platform data management system
Owner:广州市友达电子科技有限公司
A mobile substation monitoring and alarm system and method
ActiveCN111509863BFully automatedImprove real-time efficiencyCircuit arrangementsInformation technology support systemInteraction interfaceMonitoring system
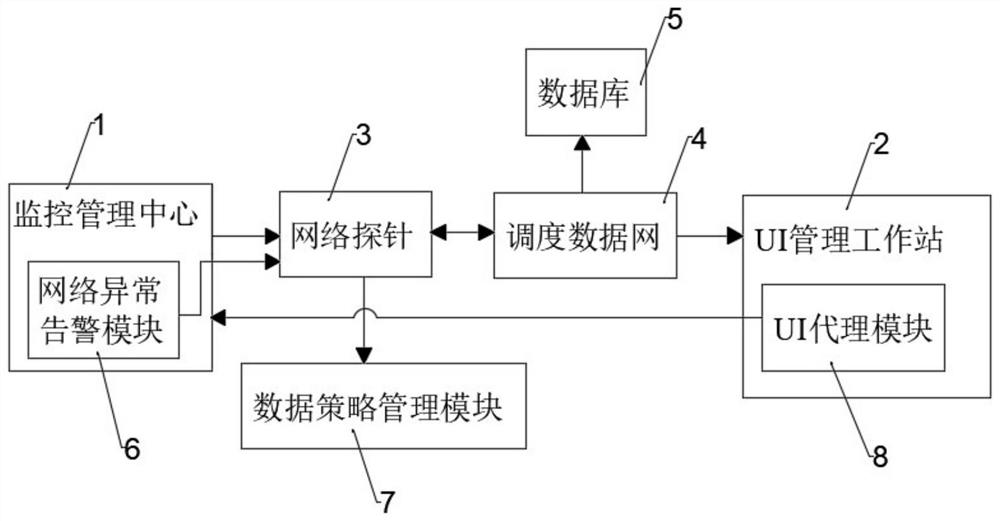
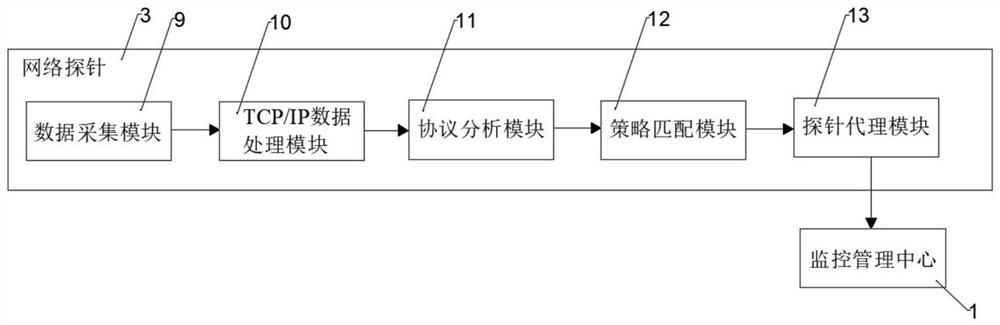
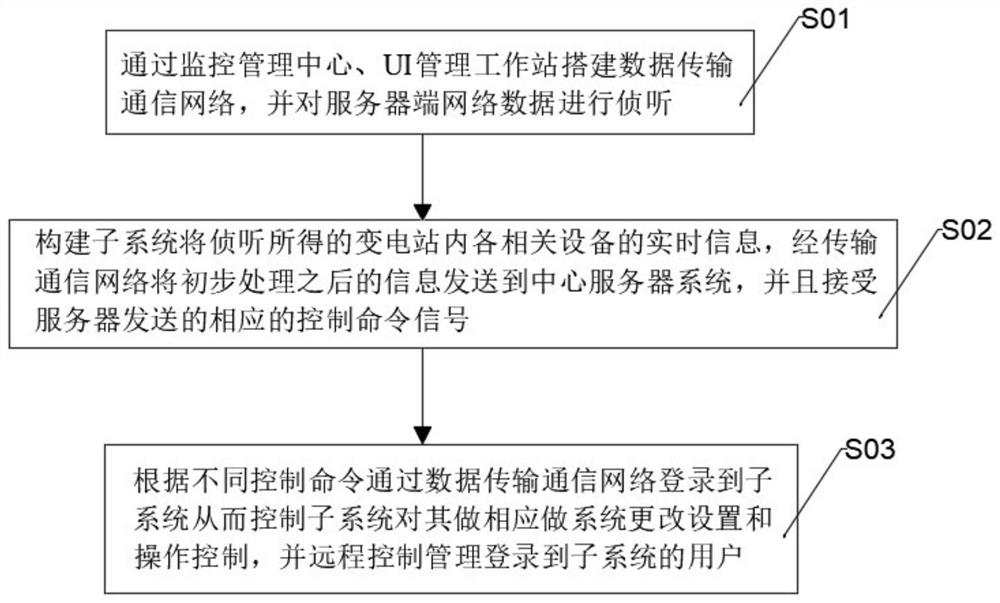
The embodiment of the present invention discloses a mobile substation monitoring and alarming system and method, including a monitoring management center and a UI management workstation. The monitoring management center adopts a B / S technology architecture mode to conduct a unified analysis of the substation network communication data information through a network probe and management, the network probe interacts and communicates with the UI management workstation through the scheduling data network, the UI management workstation obtains data from the monitoring management center and provides a human-computer interaction interface in the form of WEB, and the monitoring management center A network abnormality alarm module is set inside, and the network abnormality alarm module is connected with a data strategy management module through a network probe. The system can realize the automation of the entire power monitoring system, so that faults can be discovered as early as possible and solved accordingly. Improve the real-time efficiency of system troubleshooting.
Owner:GUANGDONG POWER GRID CO LTD +1
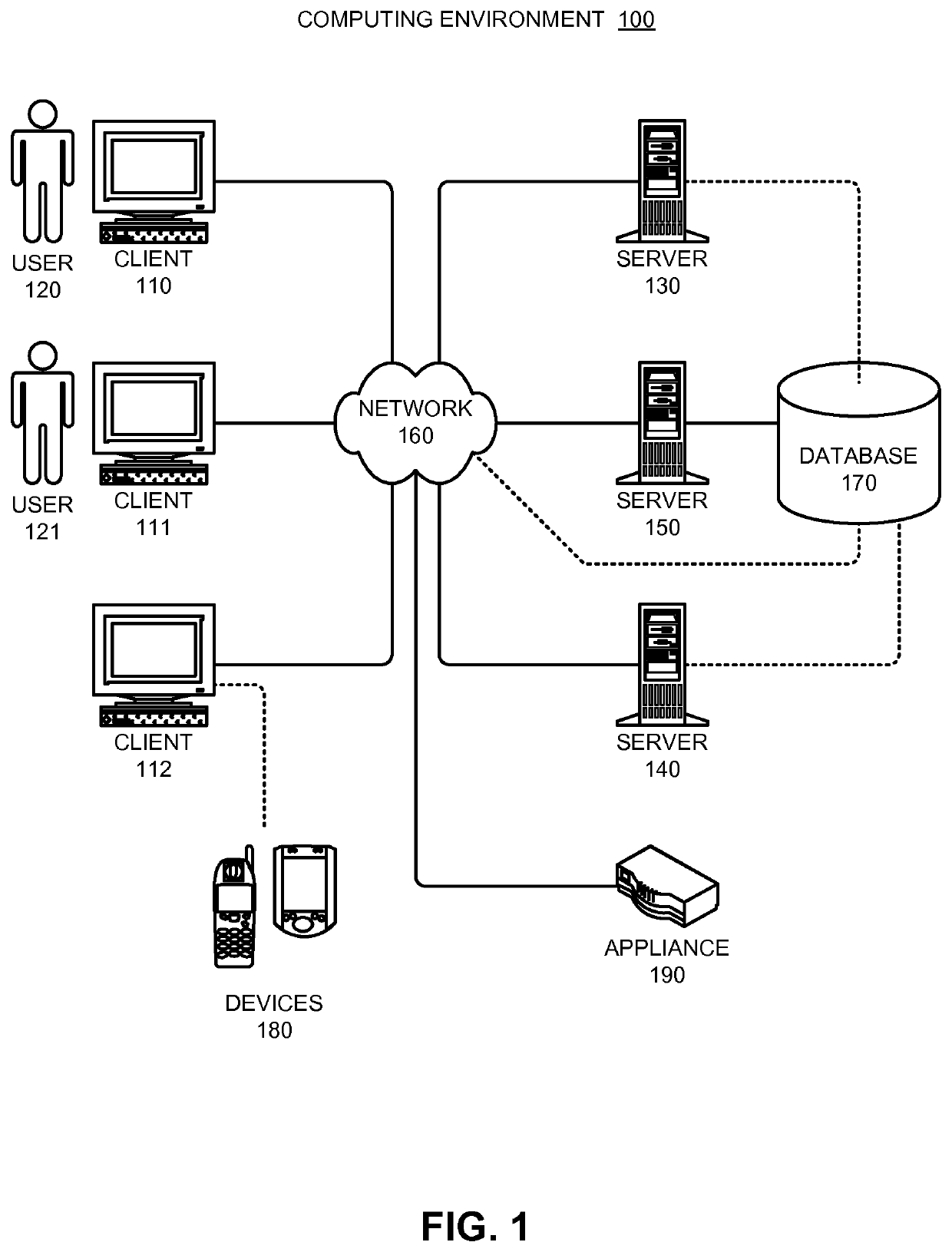
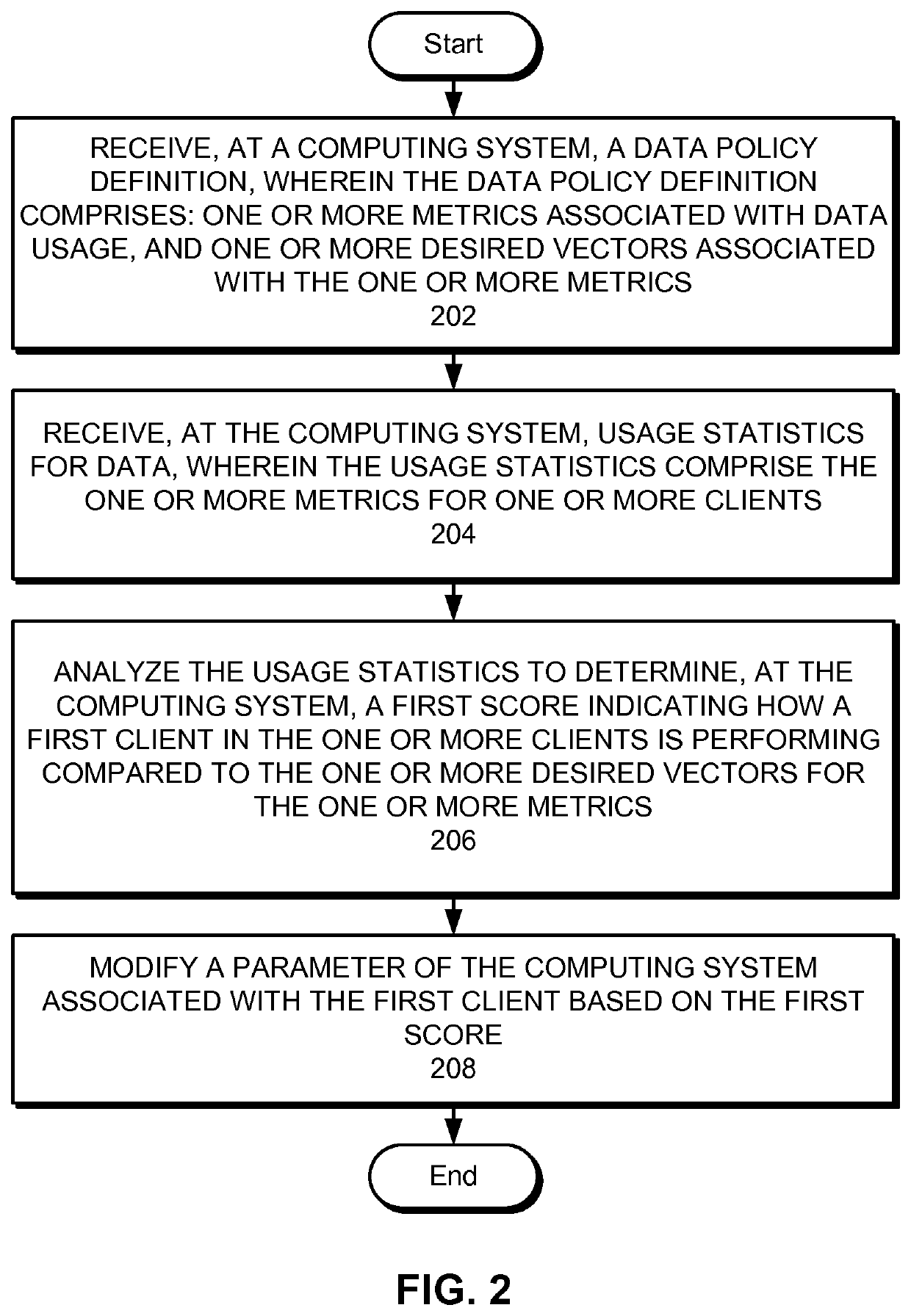
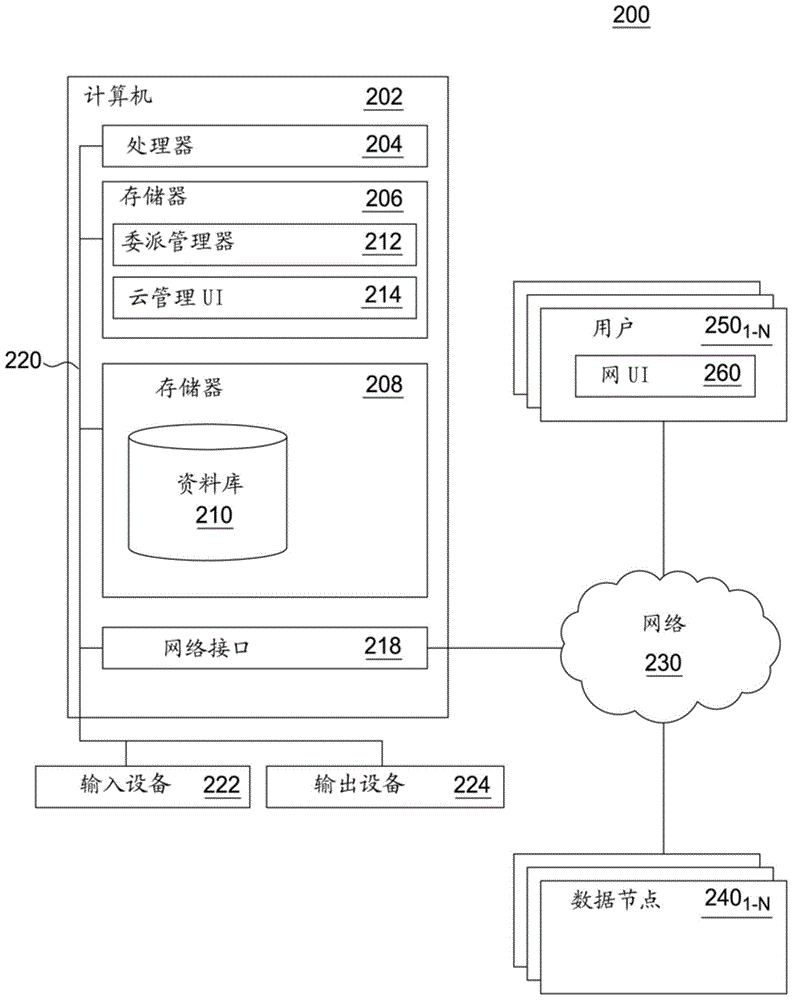
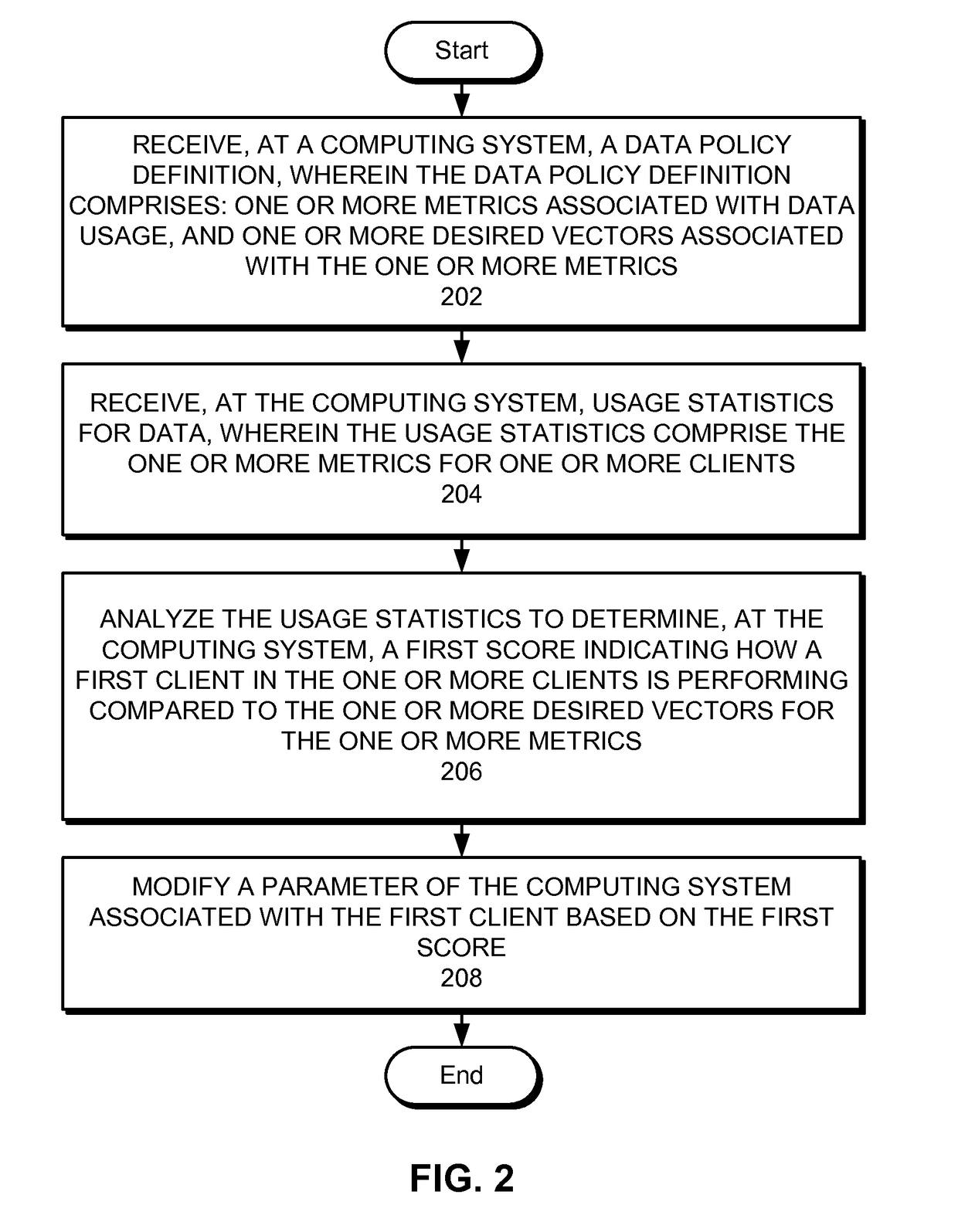
Automatically modifying computer parameters as an incentive for complying with data policies
One embodiment of the present invention provides a system for automatically modifying computer parameters as an incentive for complying with data policies. During operation, the system receives, at a computing system, a data policy definition, wherein the data policy definition comprises: one or more metrics associated with data usage, and one or more desired vectors associated with the one or more metrics. Next, the system receives, at the computing system, usage statistics for data, wherein the usage statistics comprise the one or more metrics for one or more clients. The system then analyzes the usage statistics to determine, at the computing system, a first score indicating how a first client in the one or more clients is performing compared to the one or more desired vectors for the one or more metrics. Finally, the system automatically modifies a parameter of the computing system associated with the first client based on the first score.
Owner:INTUIT INC
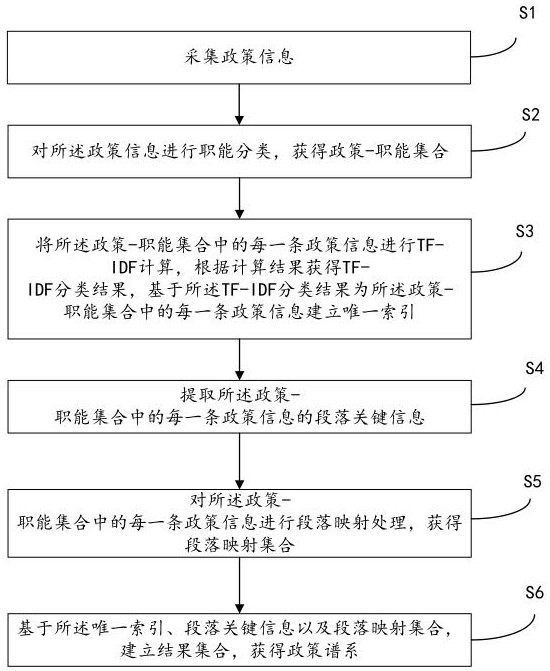
Policy pedigree construction method and device and electronic equipment
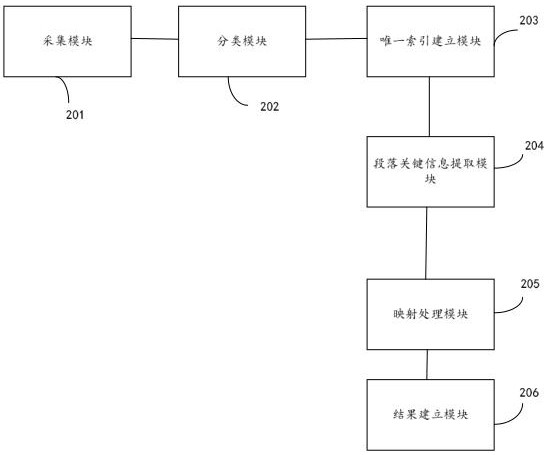
ActiveCN112800246AImplement automatic buildAchieve horizontal comparisonNatural language data processingText database indexingEngineeringResult set
The invention discloses a policy pedigree construction method and apparatus, and electronic equipment. The method comprises: collecting policy information; performing function classification on the policy information to obtain a policy-function set; performing TF-IDF calculation on each piece of policy information in the policy-function set, obtaining a TF-IDF classification result according to a calculation result, and establishing a unique index for each piece of policy information in the policy-function set based on the TF-IDF classification result; extracting paragraph key information of each piece of policy information in the policy-function set; performing paragraph mapping processing on each piece of policy information in the policy-function set to obtain a paragraph mapping set; and, based on the unique index, the paragraph key information and the paragraph mapping set, establishing a result set, and obtaining a policy pedigree. The method can realize automatic construction of a large amount of policy information data policy pedigree, and is high in efficiency and accuracy.
Owner:北京智源人工智能研究院
Method and system for selecting data nodes configured to meet a set of requirements
Owner:INT BUSINESS MASCH CORP
Automatically modifying computer parameters as an incentive for complying with data policies
One embodiment of the present invention provides a system for automatically modifying computer parameters as an incentive for complying with data policies. During operation, the system receives, at a computing system, a data policy definition, wherein the data policy definition comprises: one or more metrics associated with data usage, and one or more desired vectors associated with the one or more metrics. Next, the system receives, at the computing system, usage statistics for data, wherein the usage statistics comprise the one or more metrics for one or more clients. The system then analyzes the usage statistics to determine, at the computing system, a first score indicating how a first client in the one or more clients is performing compared to the one or more desired vectors for the one or more metrics. Finally, the system automatically modifies a parameter of the computing system associated with the first client based on the first score.
Owner:INTUIT INC
Access files
ActiveUS9921976B2Memory architecture accessing/allocationKey distribution for secure communicationLimited accessUser device
Data security access and management may require a server dedicated to monitoring document access requests and enforcing rules and policies to limit access to those who are not specifically identified as having access to the data. One example of operation may include selecting data to access via a user device, identifying a user profile associated with the user device, retrieving at least one user policy associated with the user profile, determining whether the user policy permits the user device to access the data, matching the user policy to a data policy associated with the data, receiving an encryption key at the user device, applying the encryption key to the data, and unwrapping the data from a wrapped data format to access the data.
Owner:VERA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com