Big data security visualization interaction analysis system and method
An interactive analysis and big data technology, applied in the field of data security, can solve problems such as data processing stagnation, untimely processing, and meaningless data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
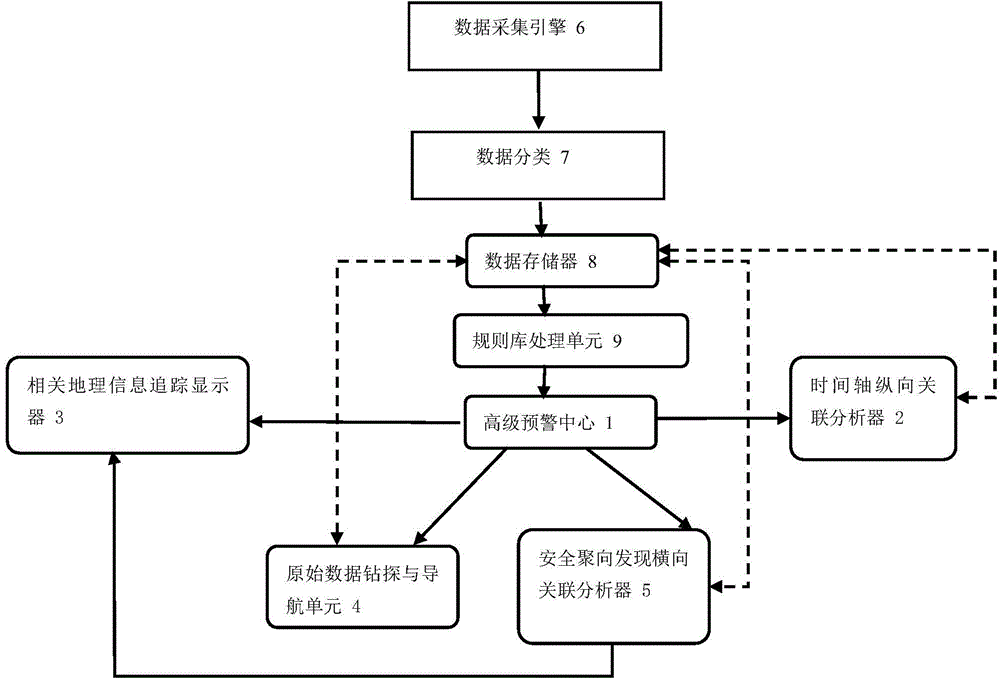
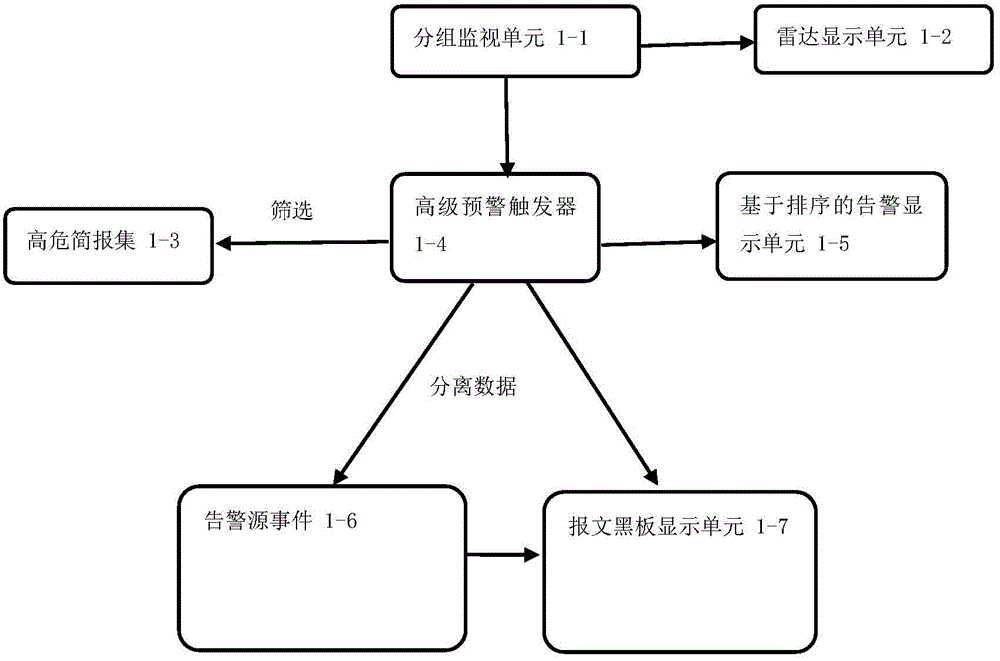
[0119] See figure 1 The present invention discloses a security visualized interactive analysis system and method based on big data. The system includes: advanced warning center module 1, time axis longitudinal correlation analyzer module 2, related geographic information tracking display module 3, raw data drilling and navigation Unit module 4, safe gathering direction discovery horizontal association analyzer module 5, data acquisition engine module 6, data classification module 7, data storage module 8, rule library processing unit module 9.
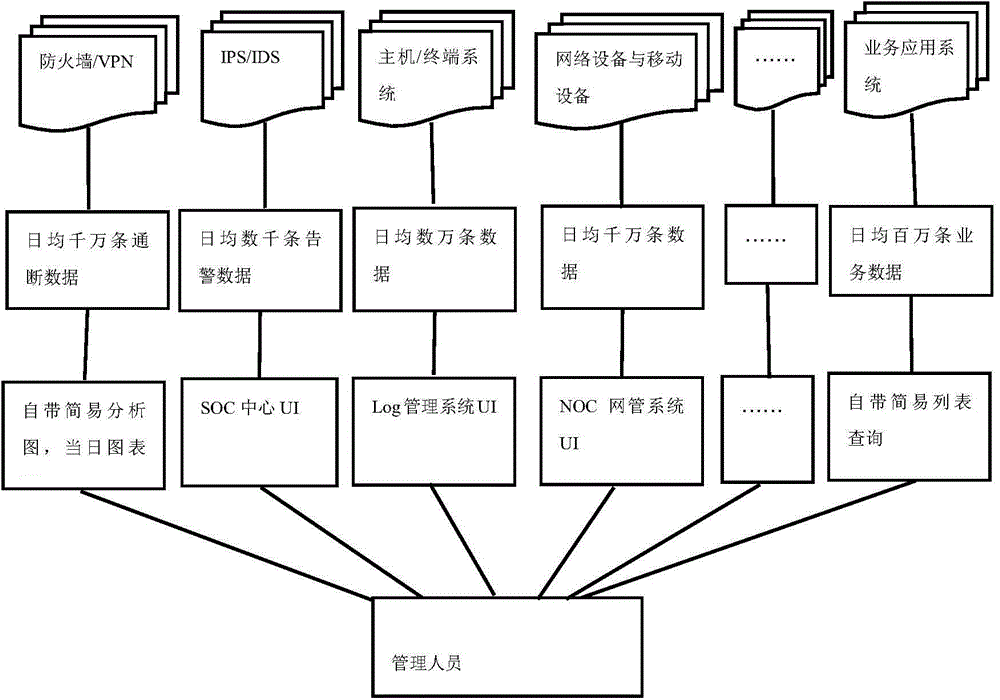
[0120] The data collection engine module 6 includes firewalls, IPS / IDS, switches, servers, audit systems, AV / virus, behavior management, software applications, and other types of data collection sensors used to collect massive security big data from various network objects, classification And collected to the data classification module 7.
[0121] The data storage module 8 is used to collect and classify the big safety data collected from ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com