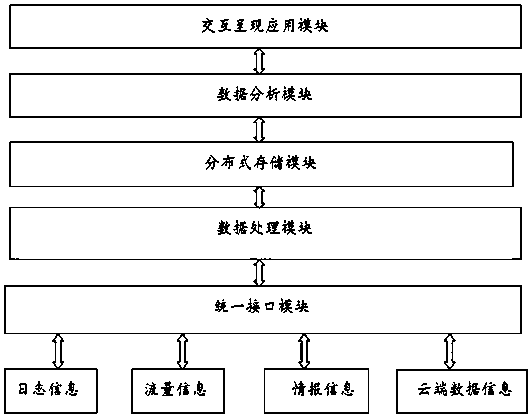
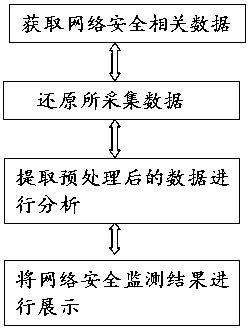
Network space security big data intelligent analysis method and computer readable medium
A network security and cyberspace technology, applied in the field of intelligent analysis of cyberspace security big data and computer readable media, can solve the problem of low effectiveness and accuracy of big data security intelligent analysis, insufficient big data security business presentation and monitoring and early warning forms , single source of big data and other issues, to achieve the effect of protecting the core assets of customers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0073] Example 1: Event Correlation
[0074] Event correlation supports the search of event characteristics, can save and visualize the search track, helps to restore the event attack process, and discover the source of the attack, and at the same time realizes statistics on the characteristics of all security events that have occurred within a certain period of time. The event features include basic features (such as cross-site scripting (XSS) attacks, SQL injection attacks, automated threats), communication features (such as various communication protocols such as http, https, ftp, etc.). Event correlation can be divided into rule-based event correlation, single event correlation, multi-event correlation, event search, event attack process restoration, etc. To be introduced below.
[0075] a. Rule-based event correlation:
[0076]The system has a built-in visual rule editor, and users can define association rules based on logical expressions and statistical conditions, and...
example 2
[0095] Example 2: Sample Association
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com