Patents
Literature
51 results about "Security analyst" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
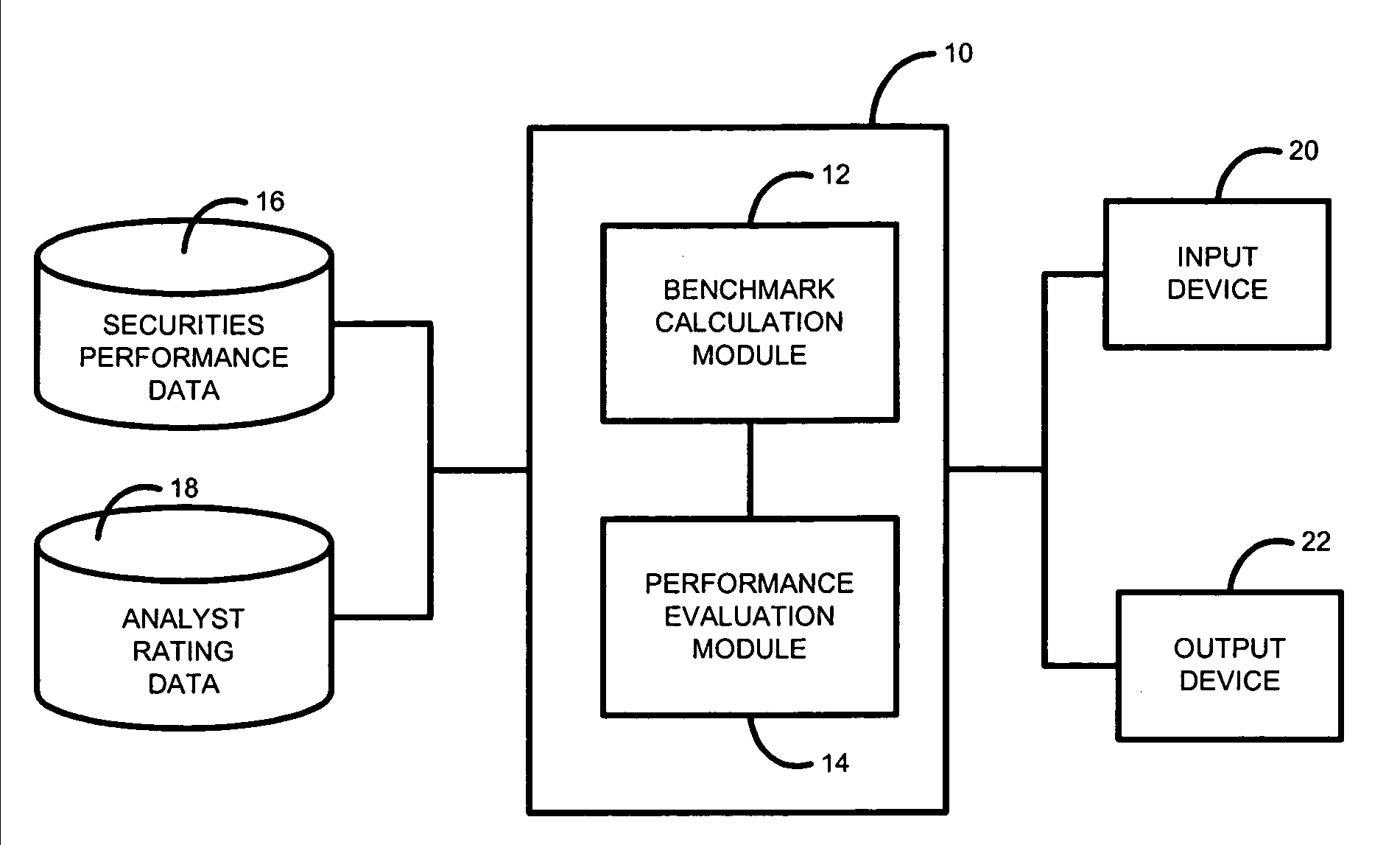
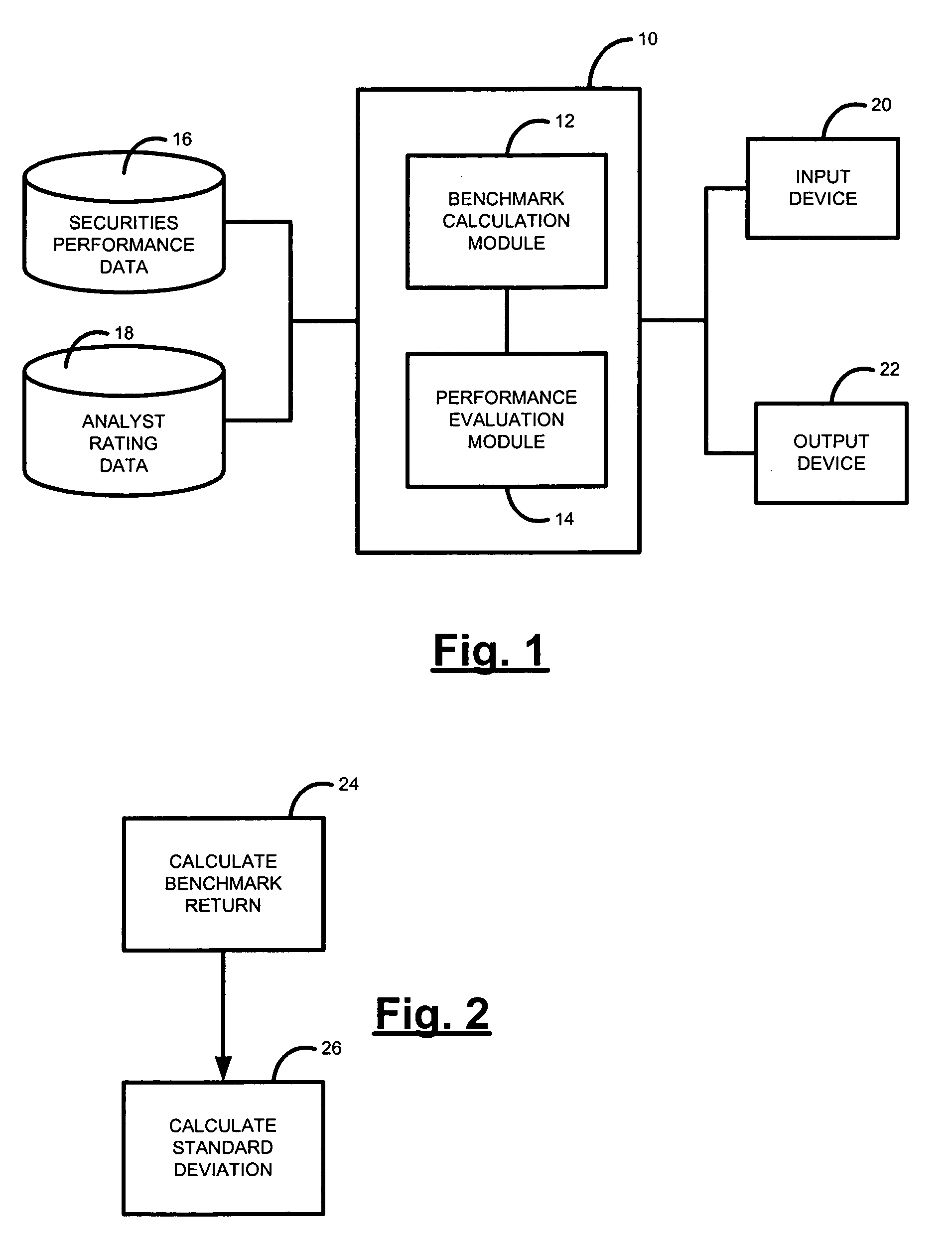
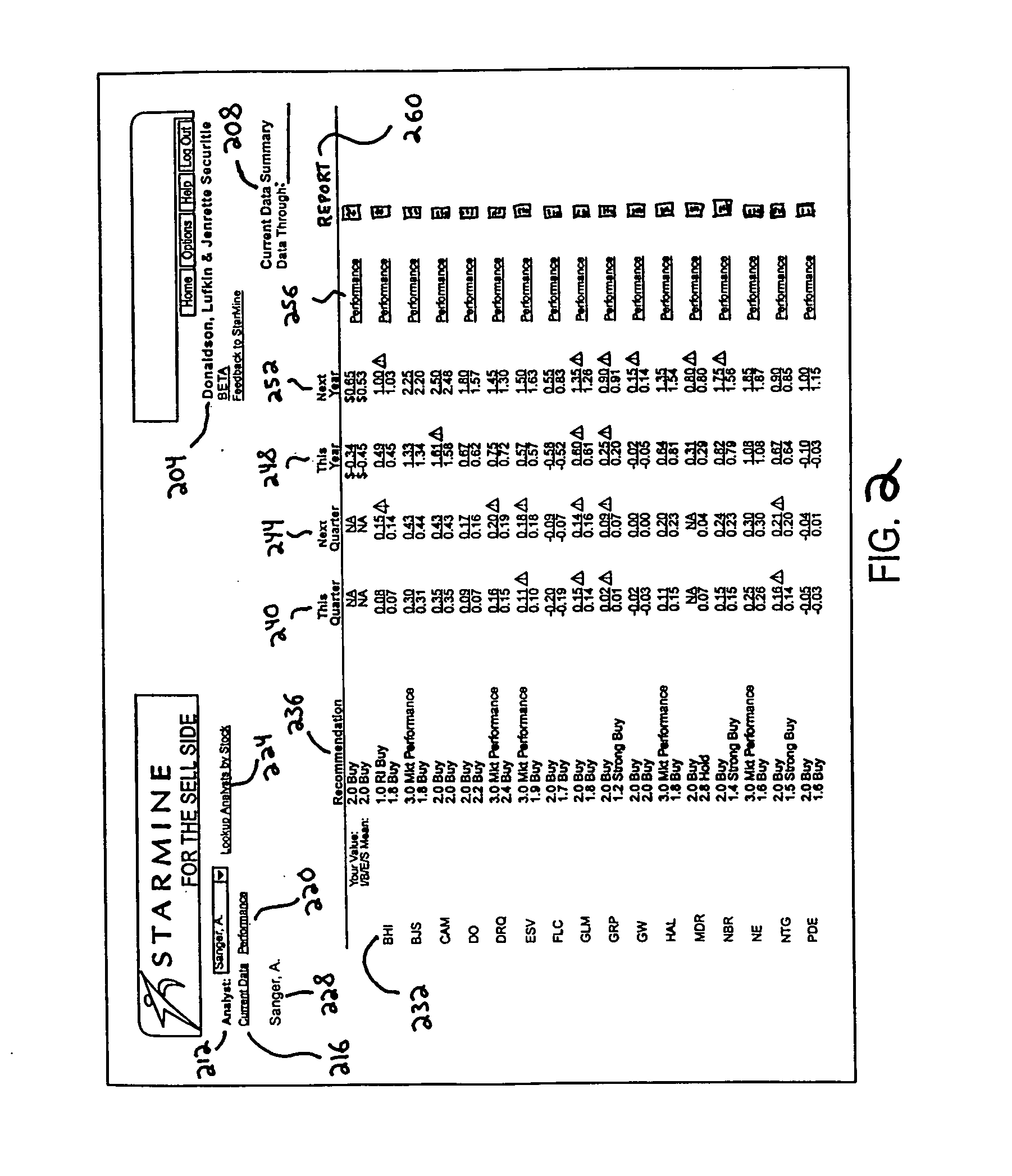
Security analyst performance tracking and analysis system and method
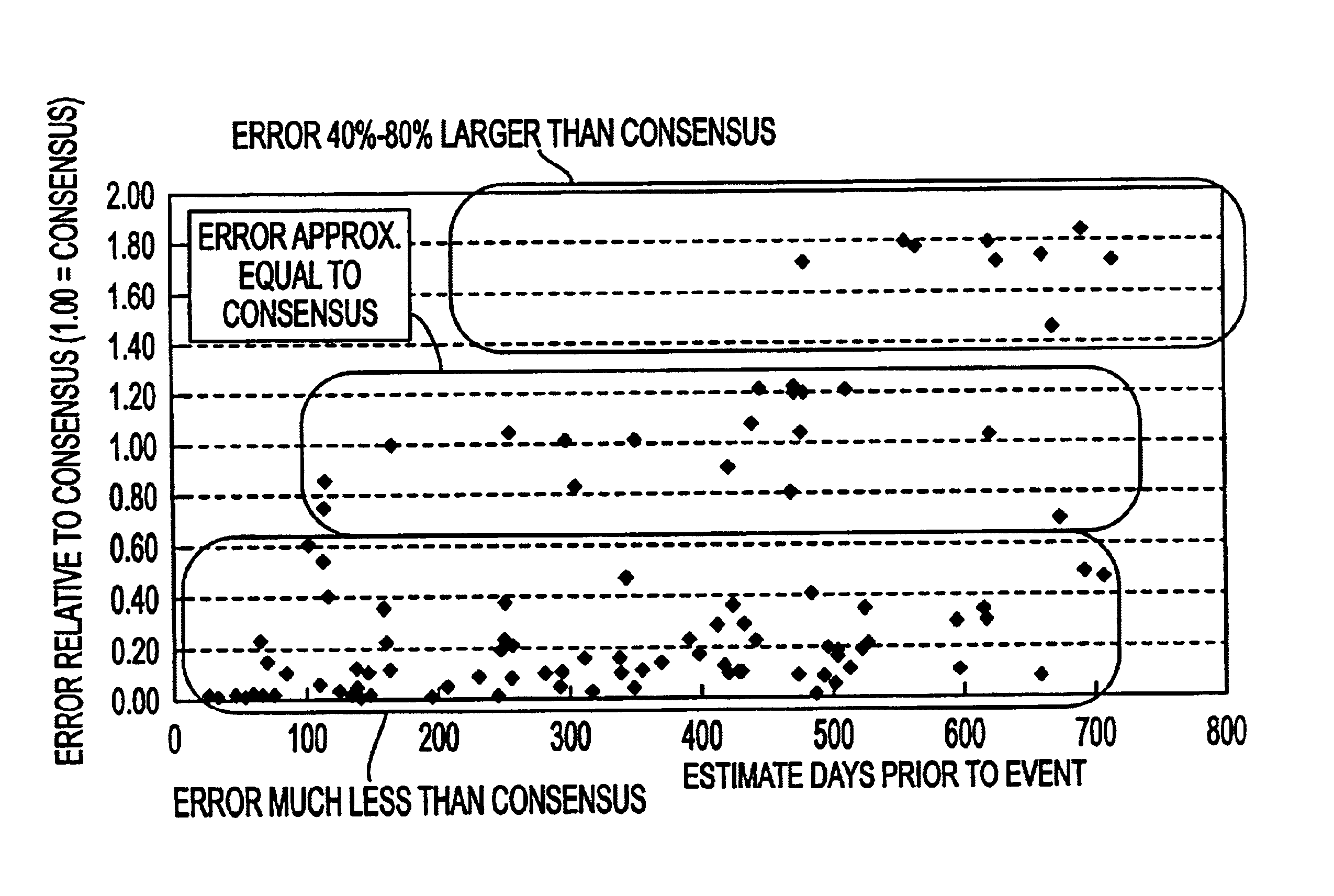
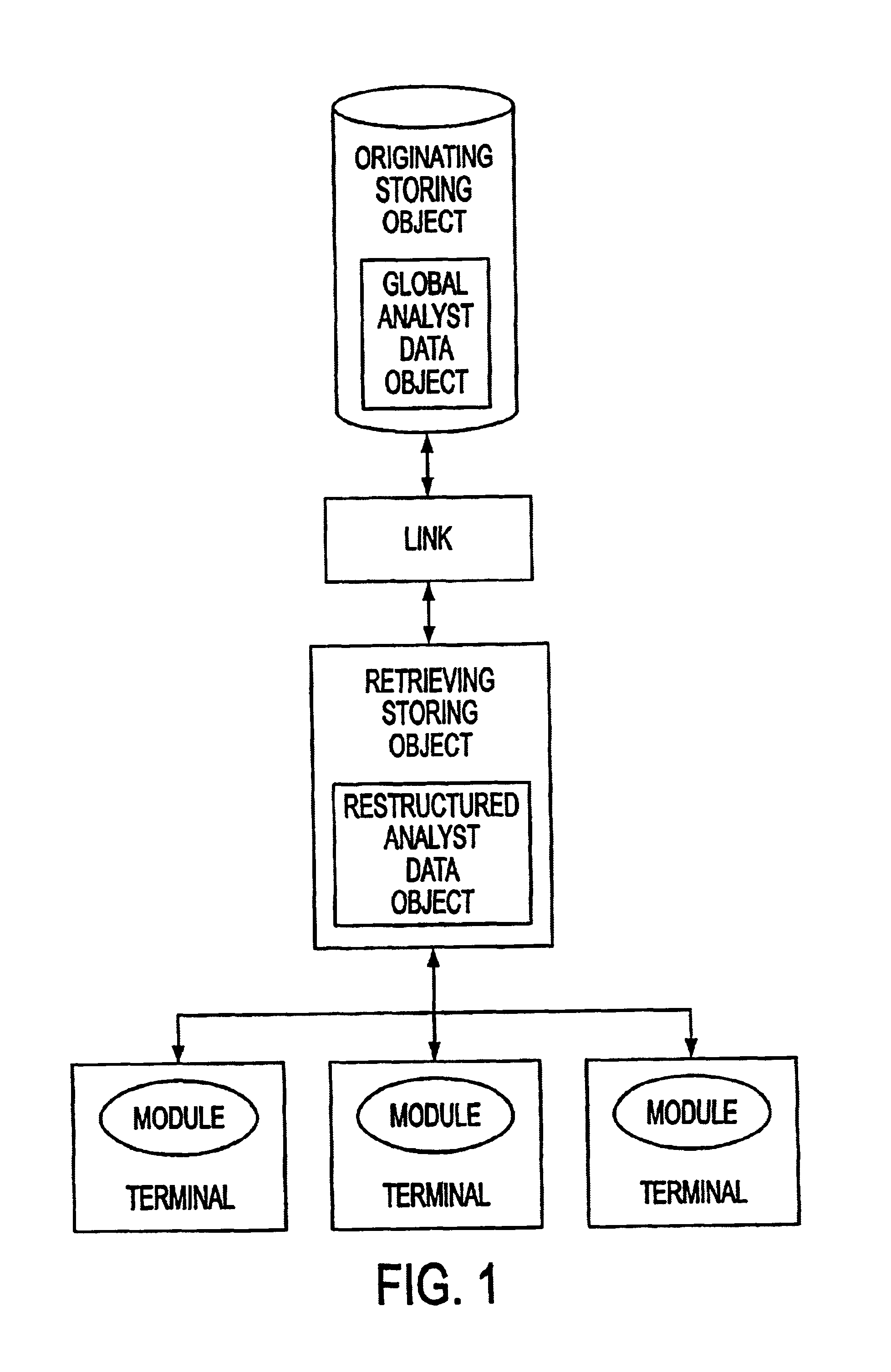
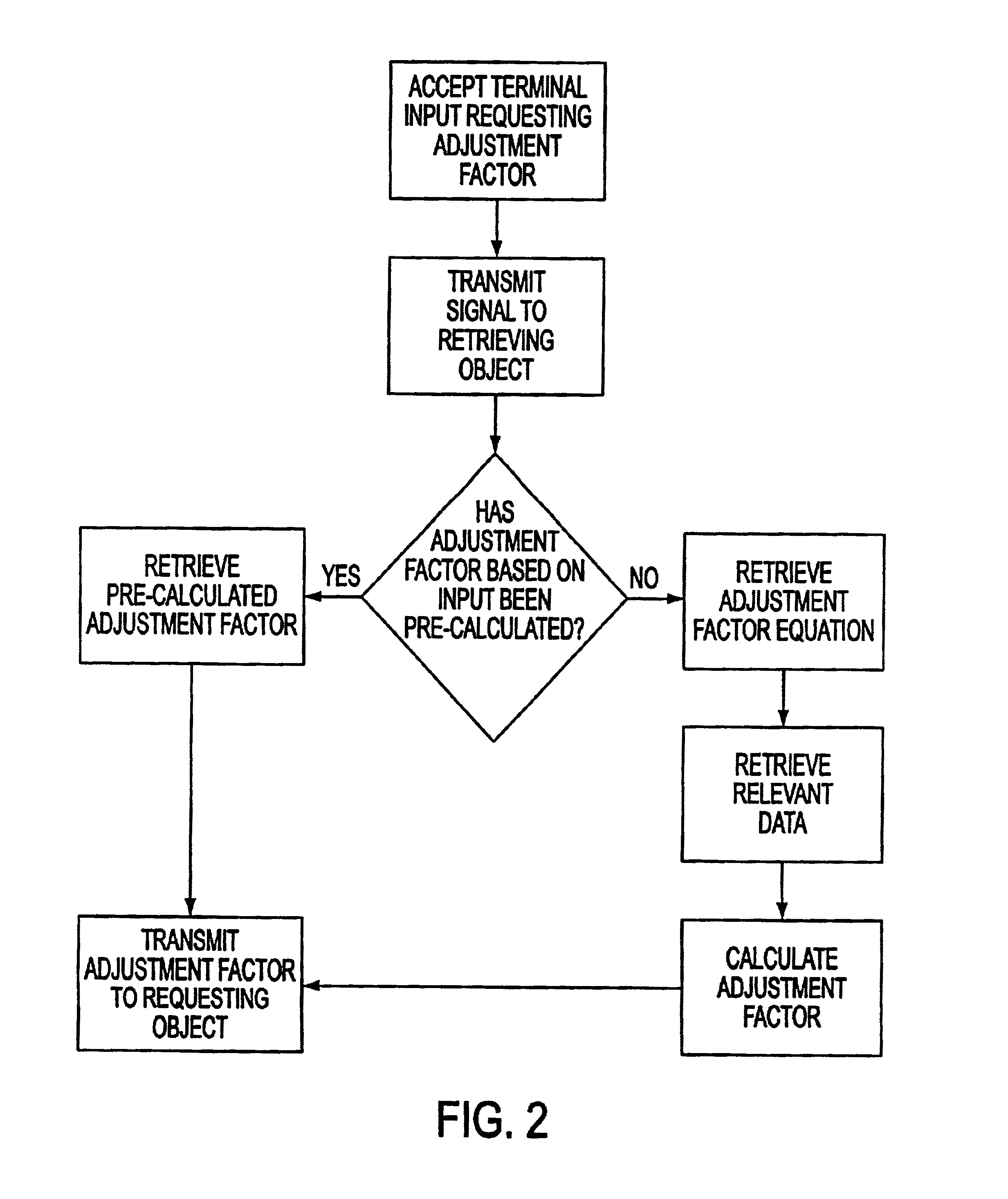
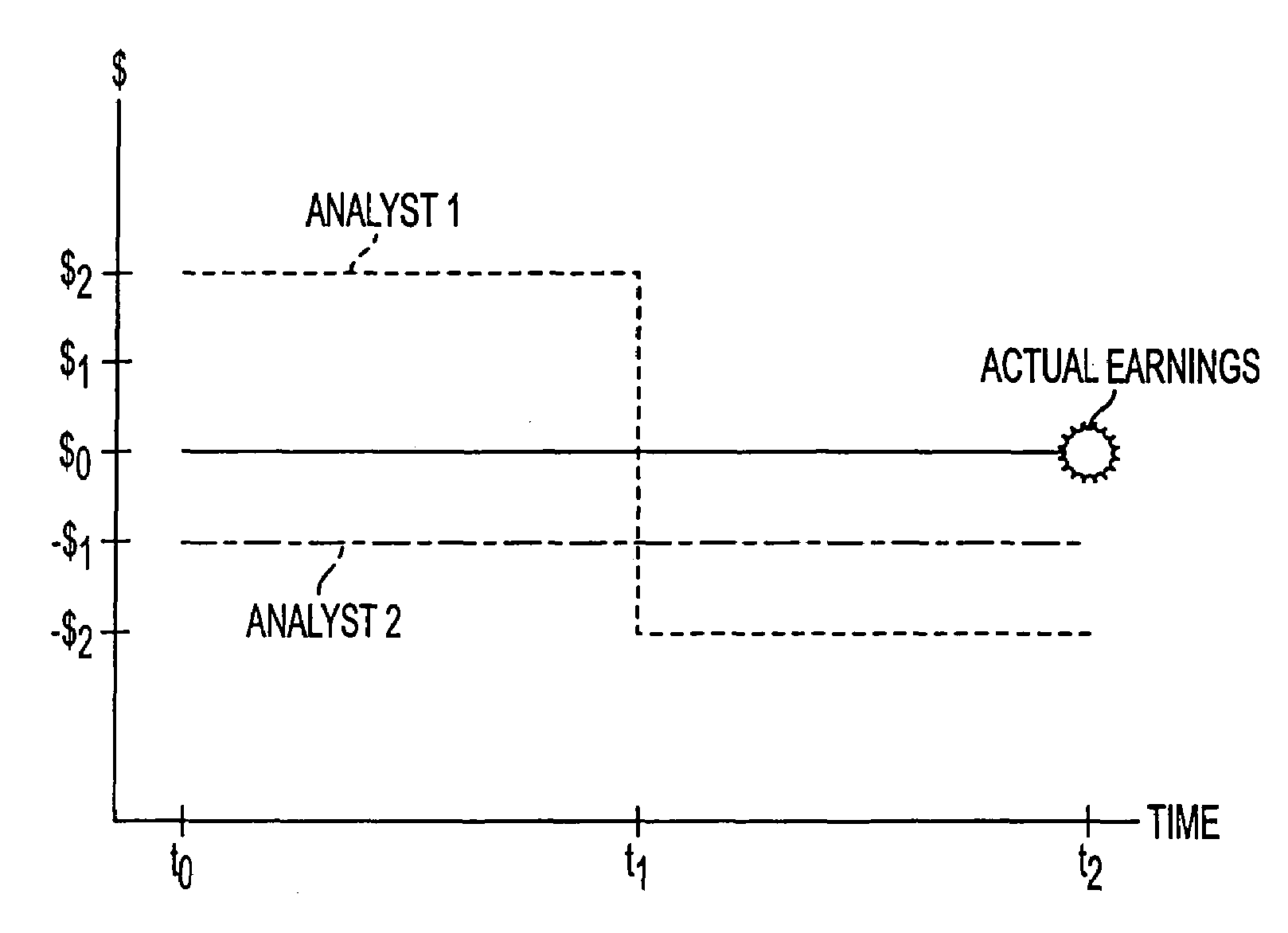
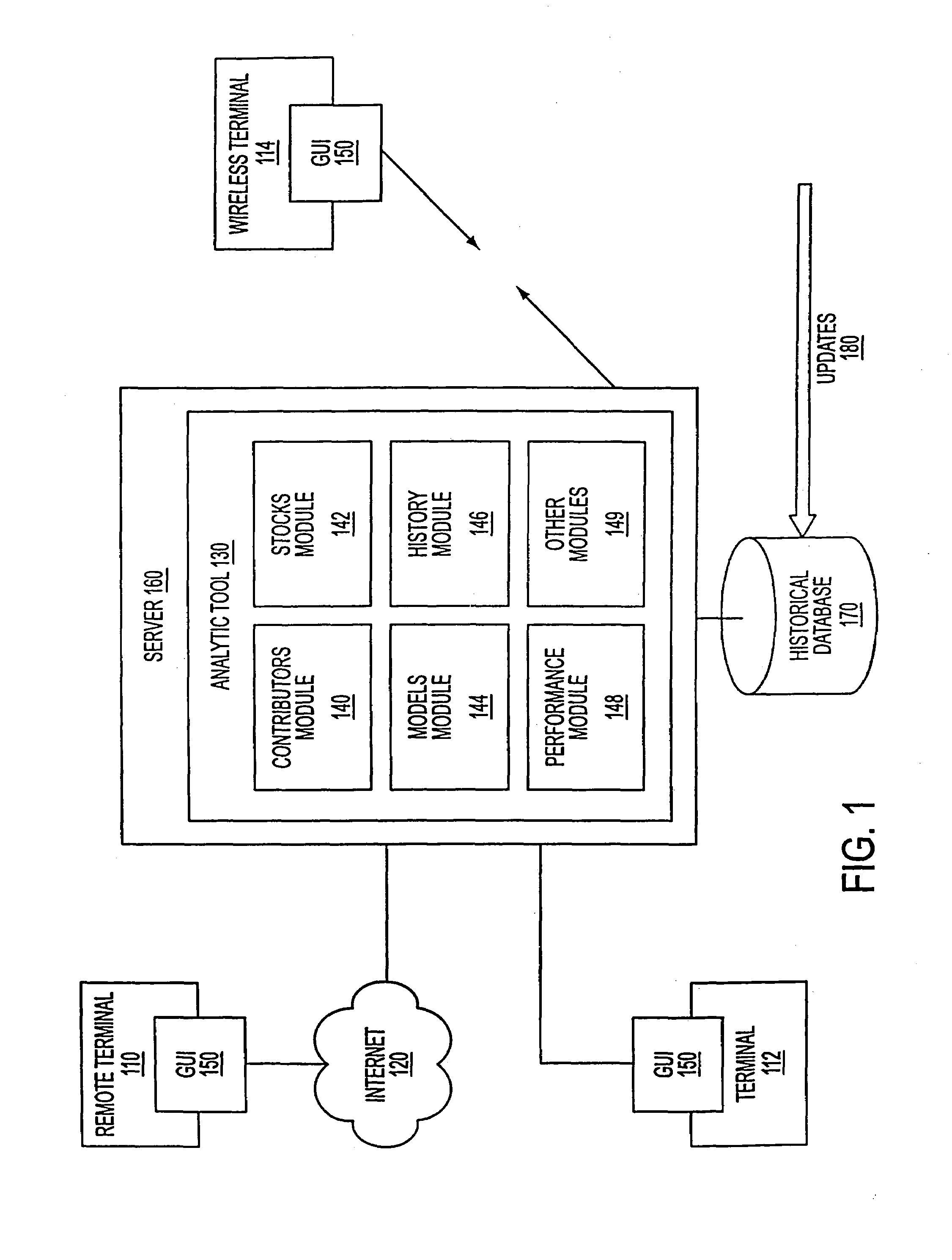
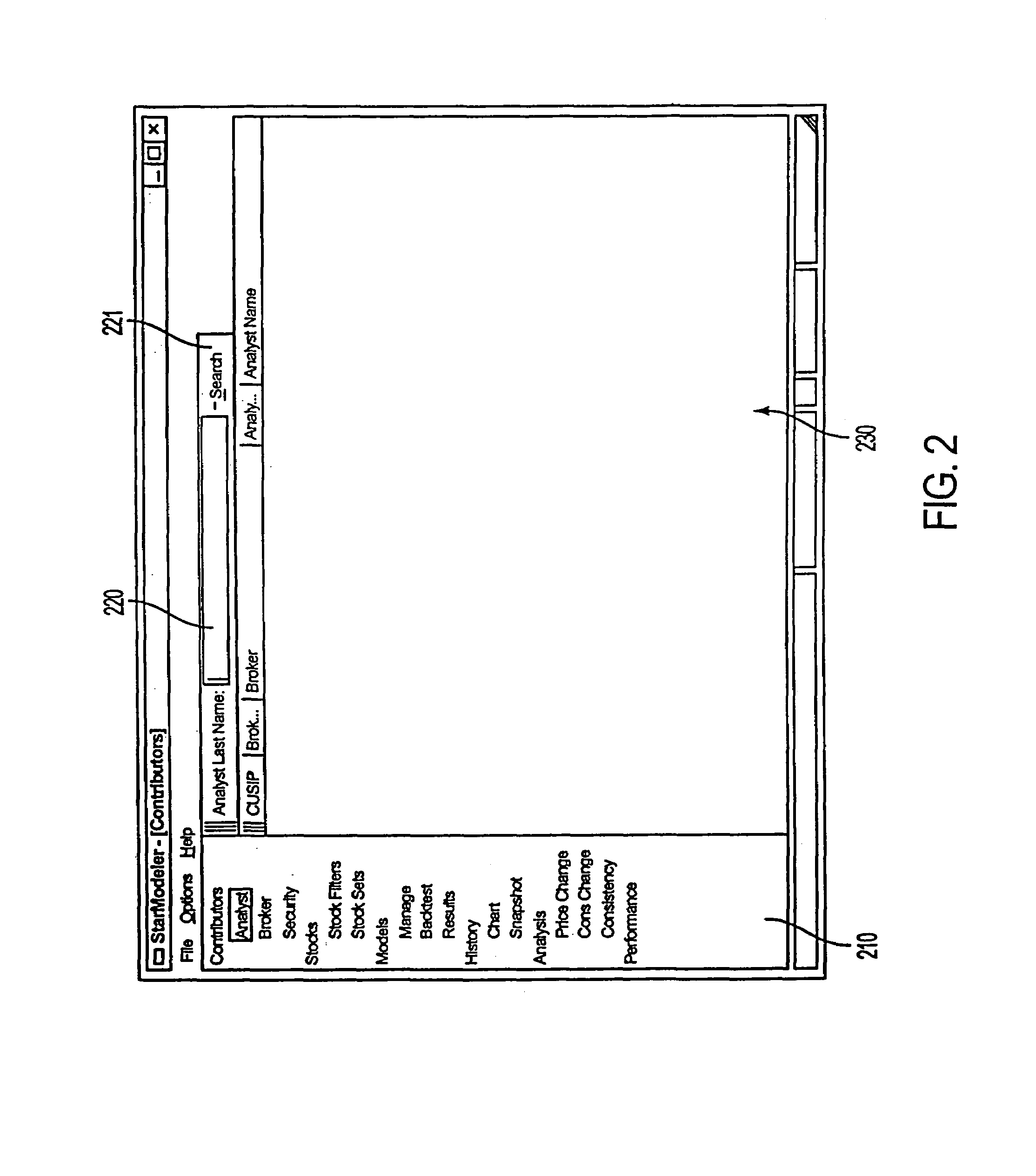
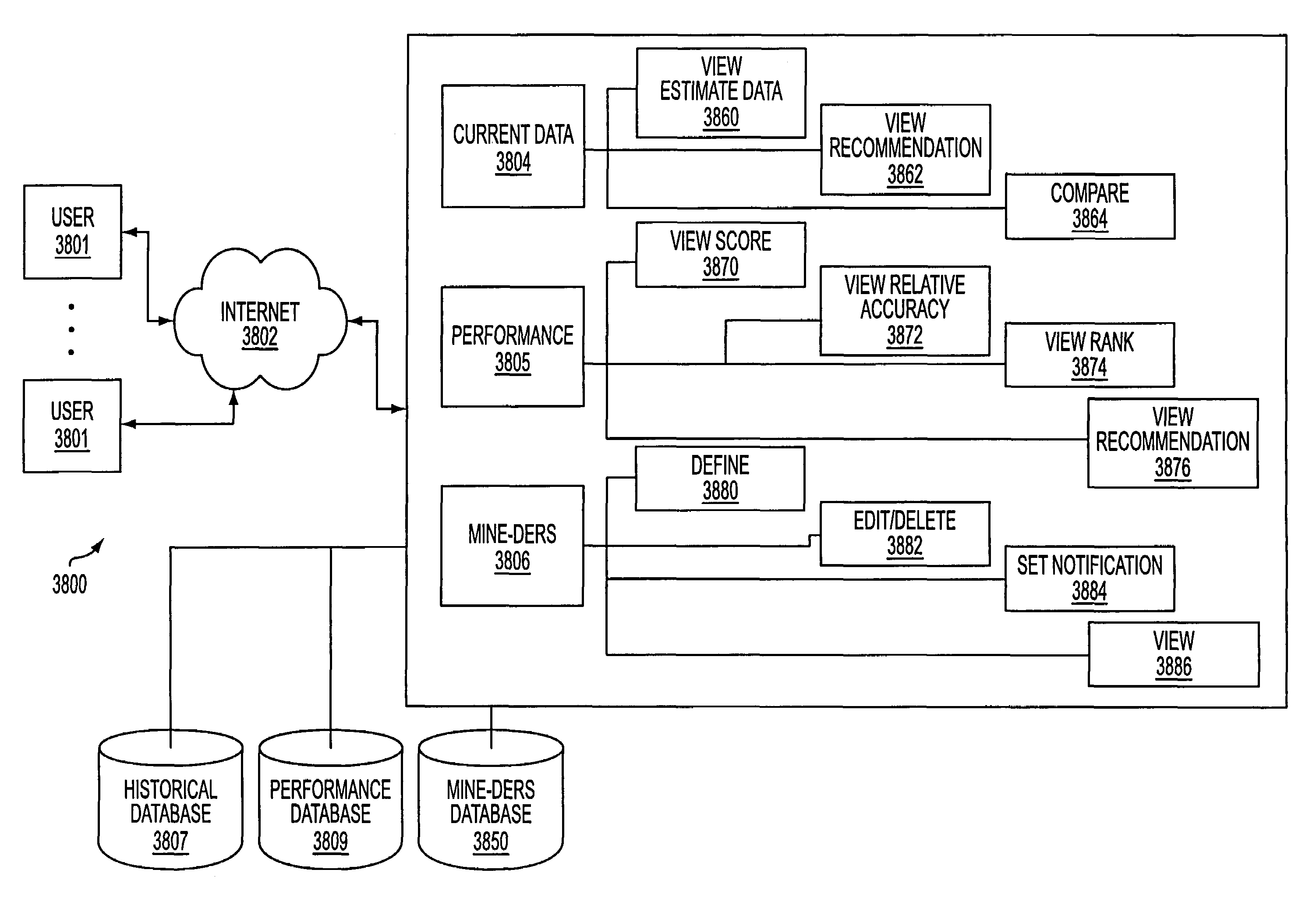
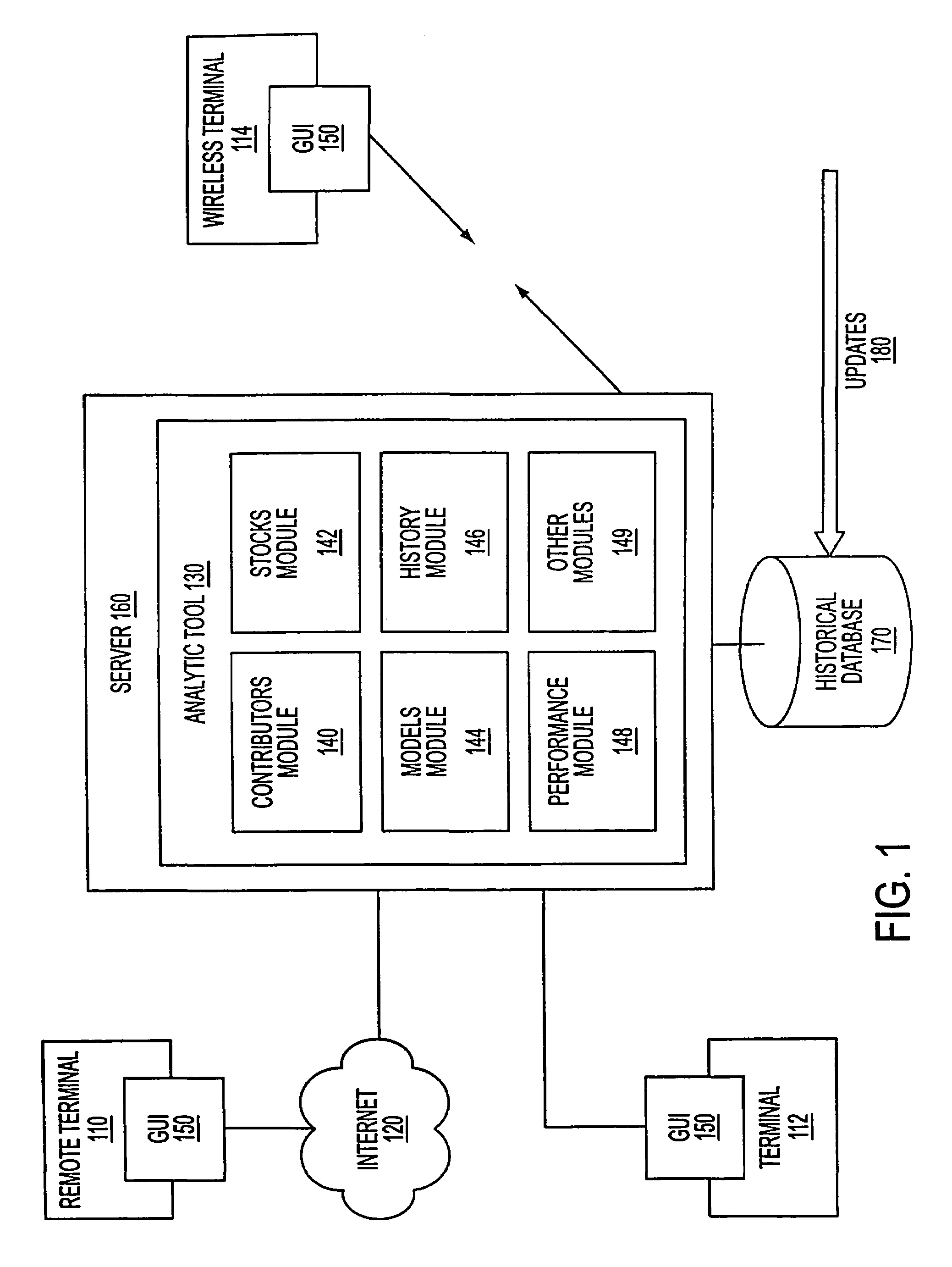
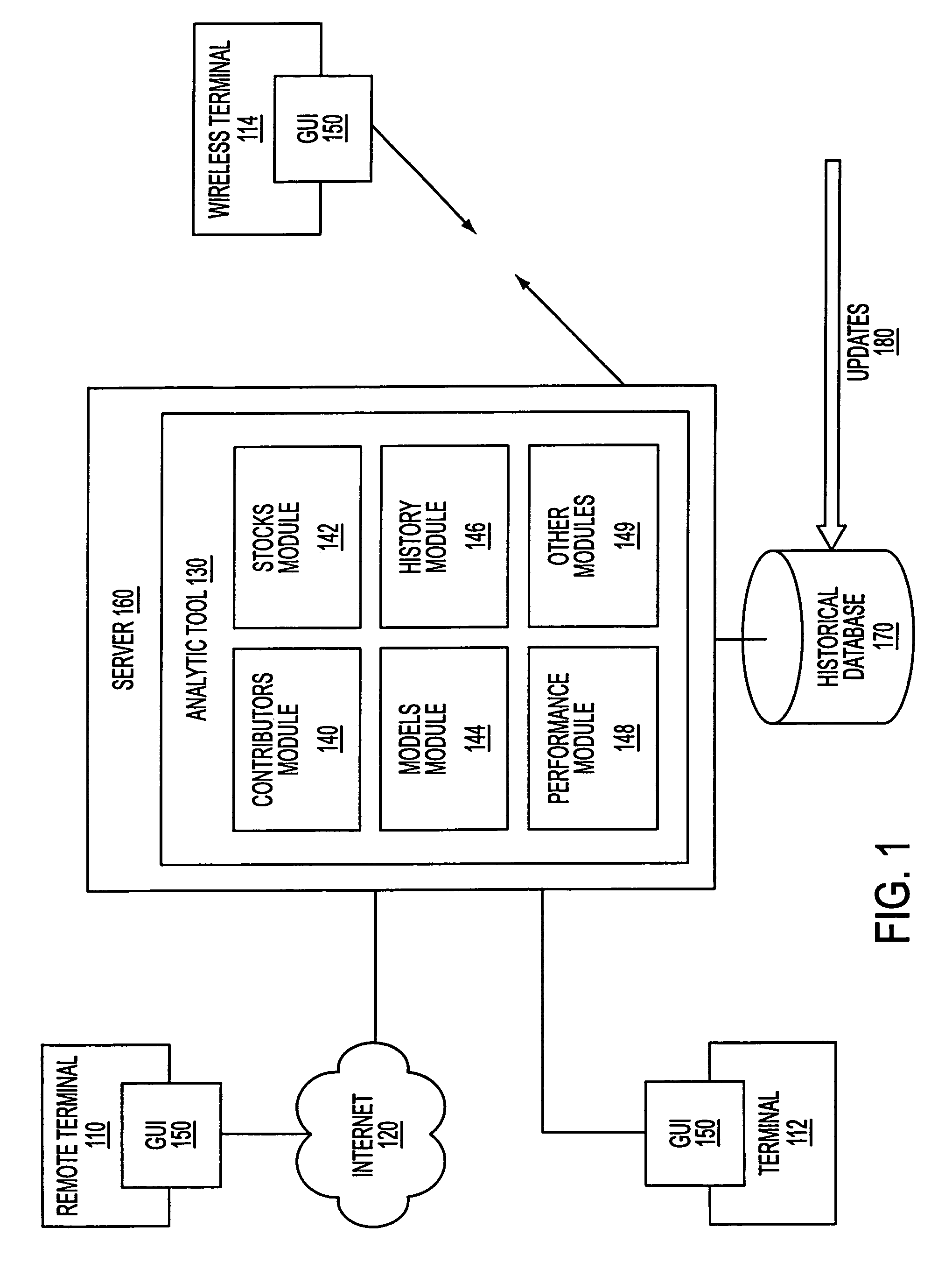
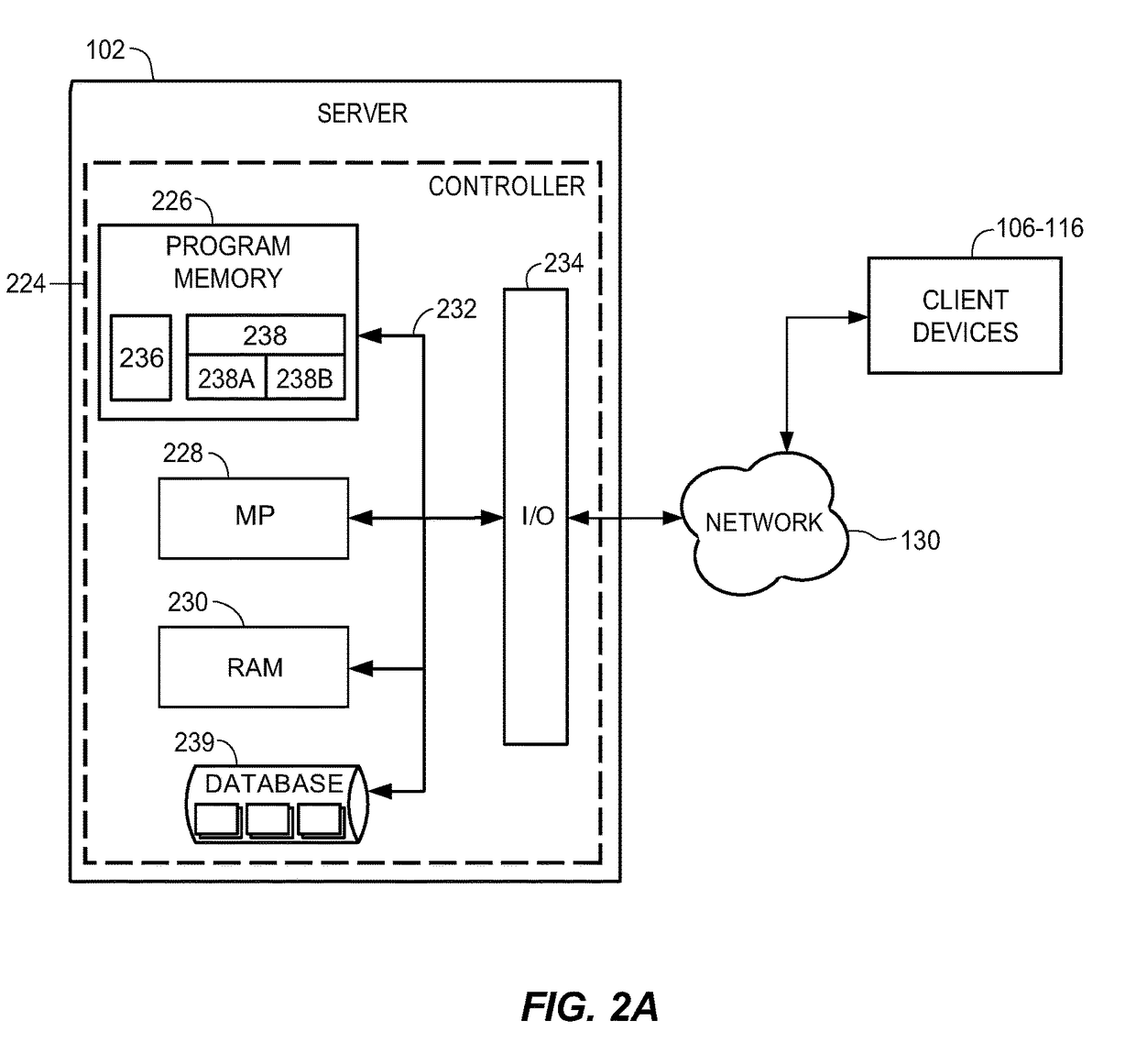
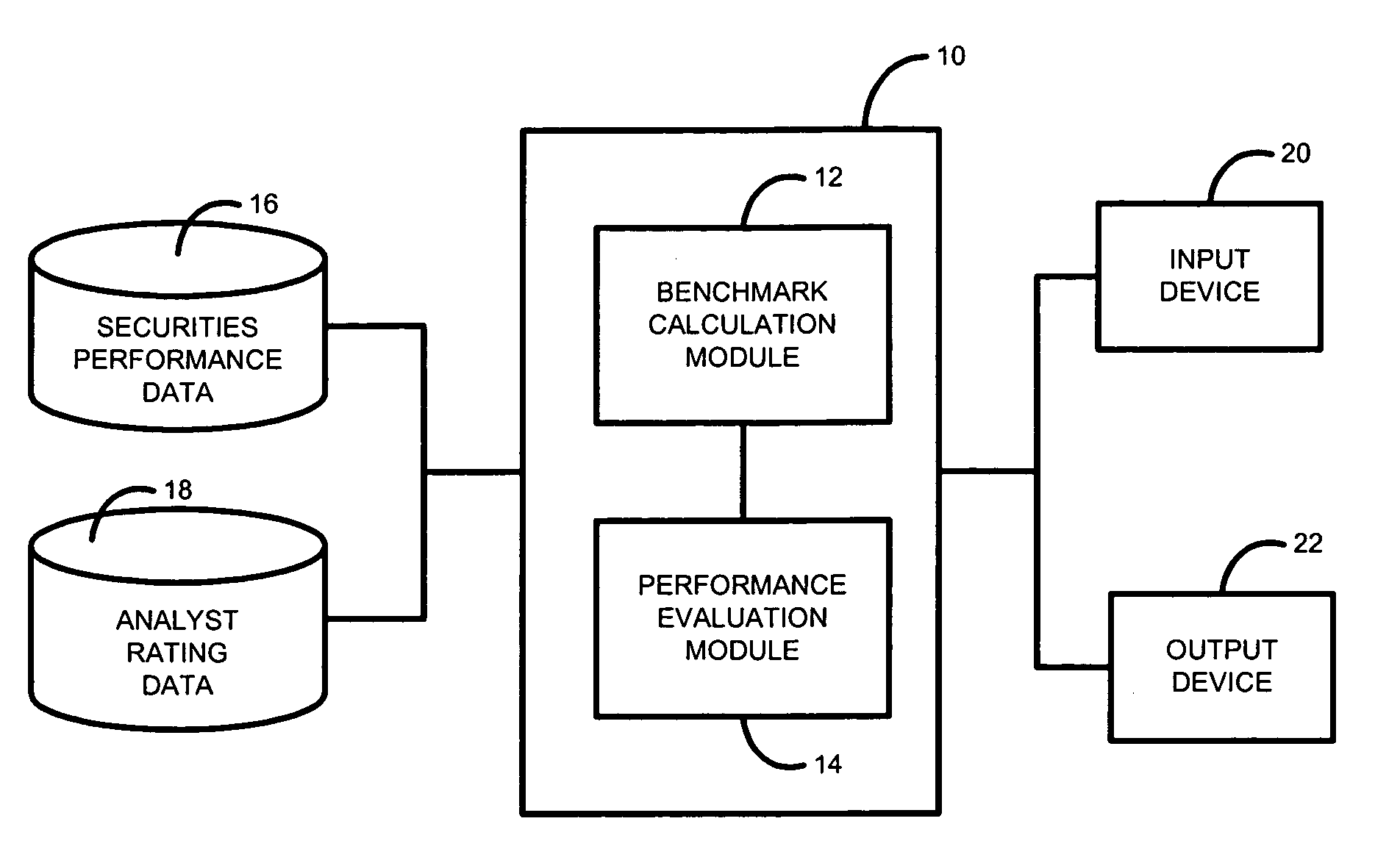
A system and method for measuring, analyzing, and tracking the past performance of security analysts' earnings estimates and recommendations. A database containing historical information pertaining to analyst earnings estimates and recommendations is downloaded into the system. Pre-calculated data values are also added to the database including adjustment factors a single or set of analysts based upon their historical earnings estimates as compared to actual earnings estimates over time, and other user-defined performance analysis set parameters and metrics. A weighting factor may also be calculated for a set of analysts based upon factors such as the recency of an analyst's earnings estimates. Using these adjustment and weighting factors and each analyst's actual earnings estimate, a custom composite estimate may be derived. A front-end graphical user interface (GUI) is used to view analyst historical data either as raw data or, by using a data visualization technique, as a graph or chart.
Owner:REFINITIV US ORG LLC
Security analyst estimates performance viewing system and method
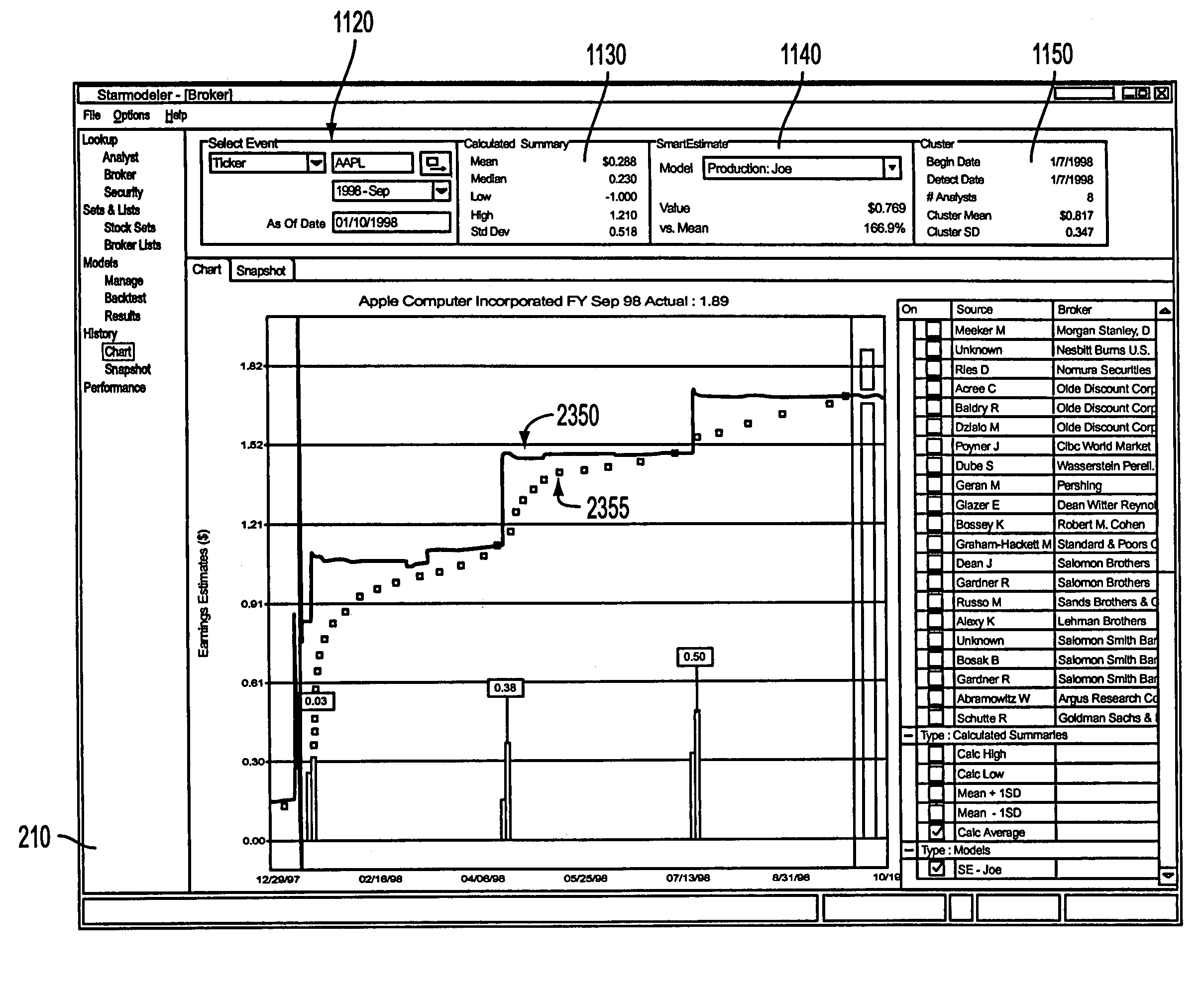
A system and method for measuring, analyzing, and tracking the past performance of security analysts' earnings estimates and recommendations. The present invention provides a database of historical data relating to security analyst earnings estimate predictions wherein a historical model enables users to view the historical data as a time series of earnings estimates for each analyst selected, for a selected period of time, for a predetermined earnings event. Users may define a model to automatically create enhanced composite estimates wherein an improved prediction of the quantity being estimated, such as company earnings, revenue or cash flow is obtained. Users may view performance screens and historical performance data for a particular contributor or various contributors for a given security. Other views may be available.
Owner:REFINITIV US ORG LLC
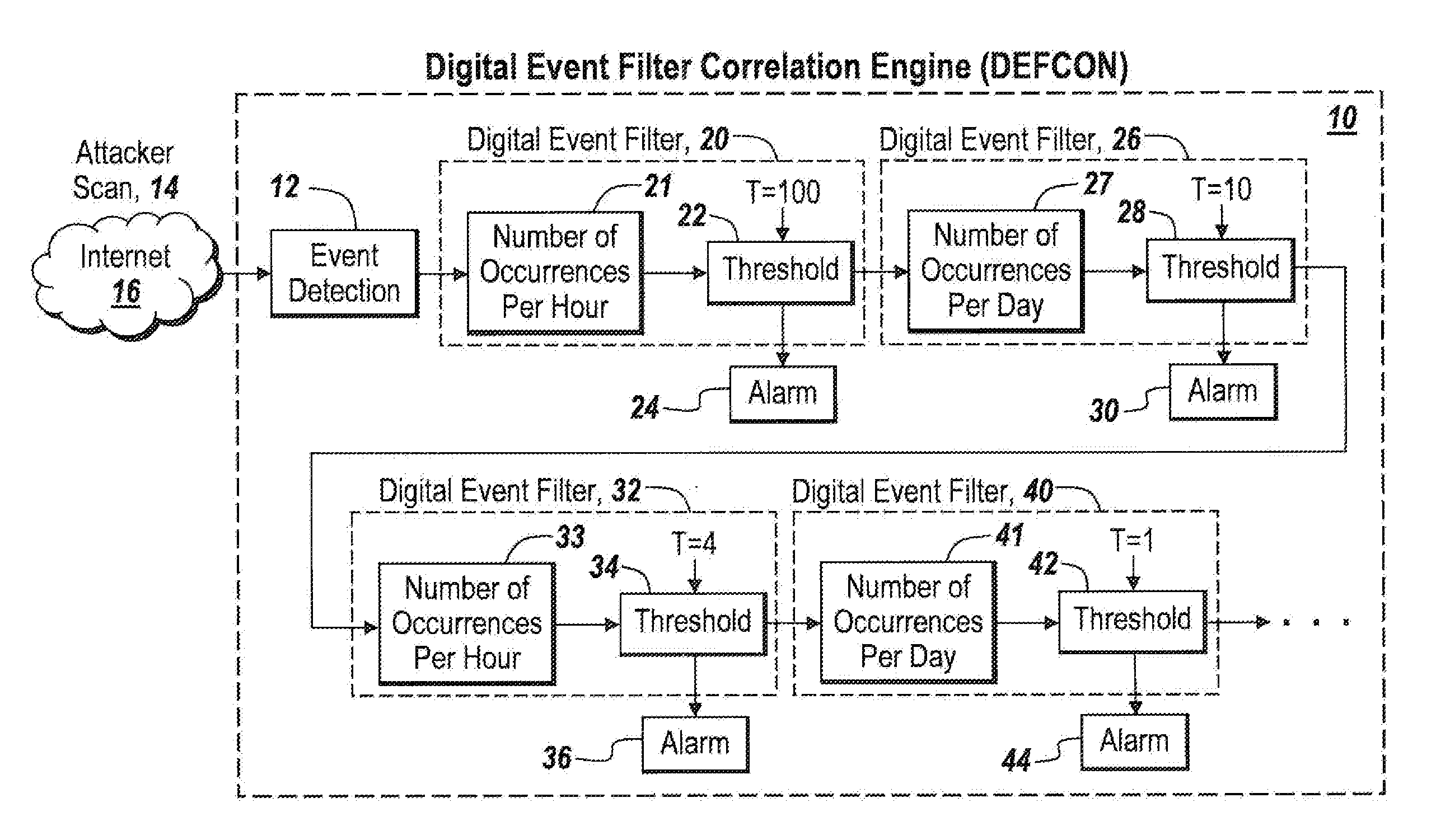
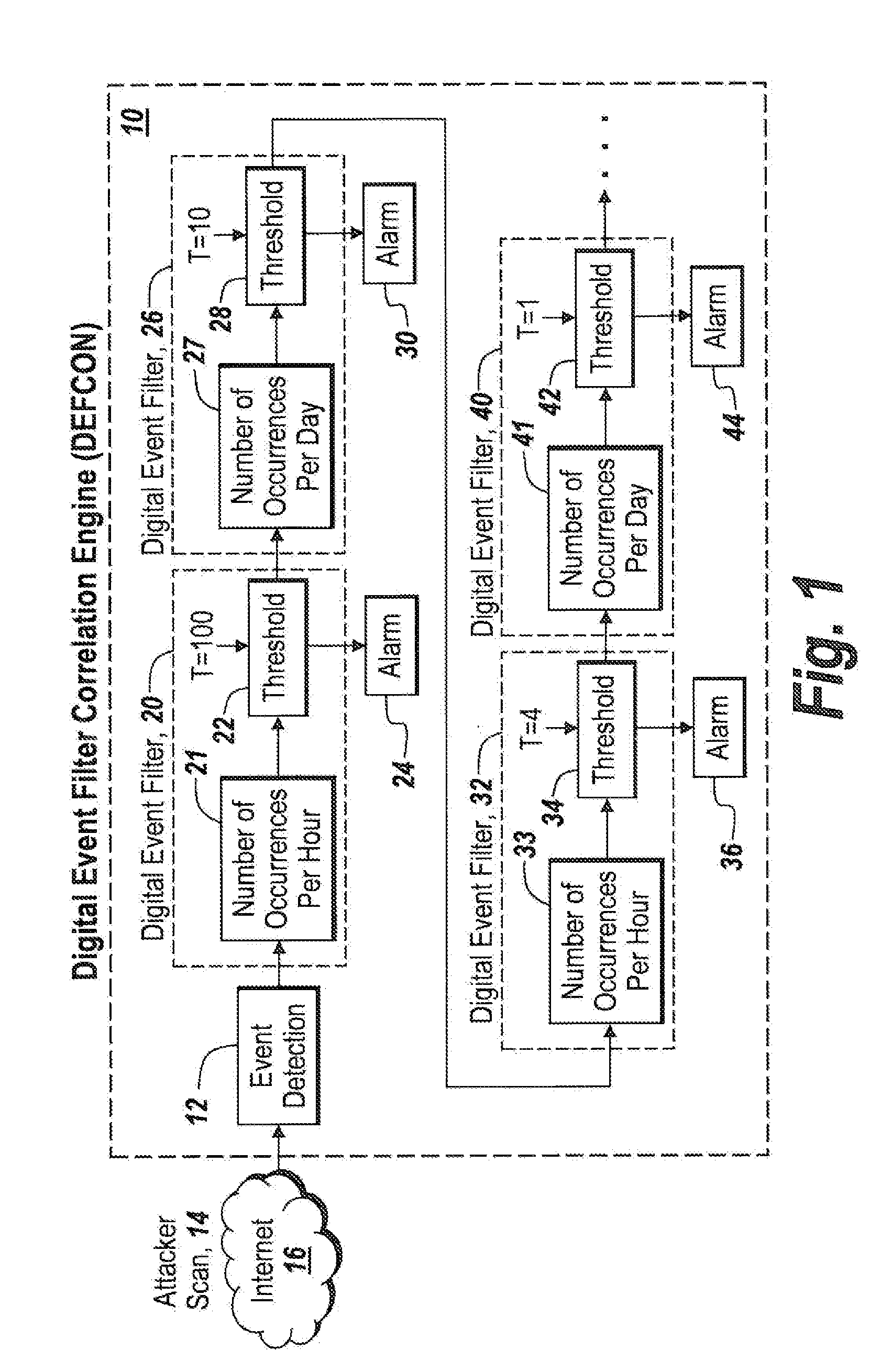
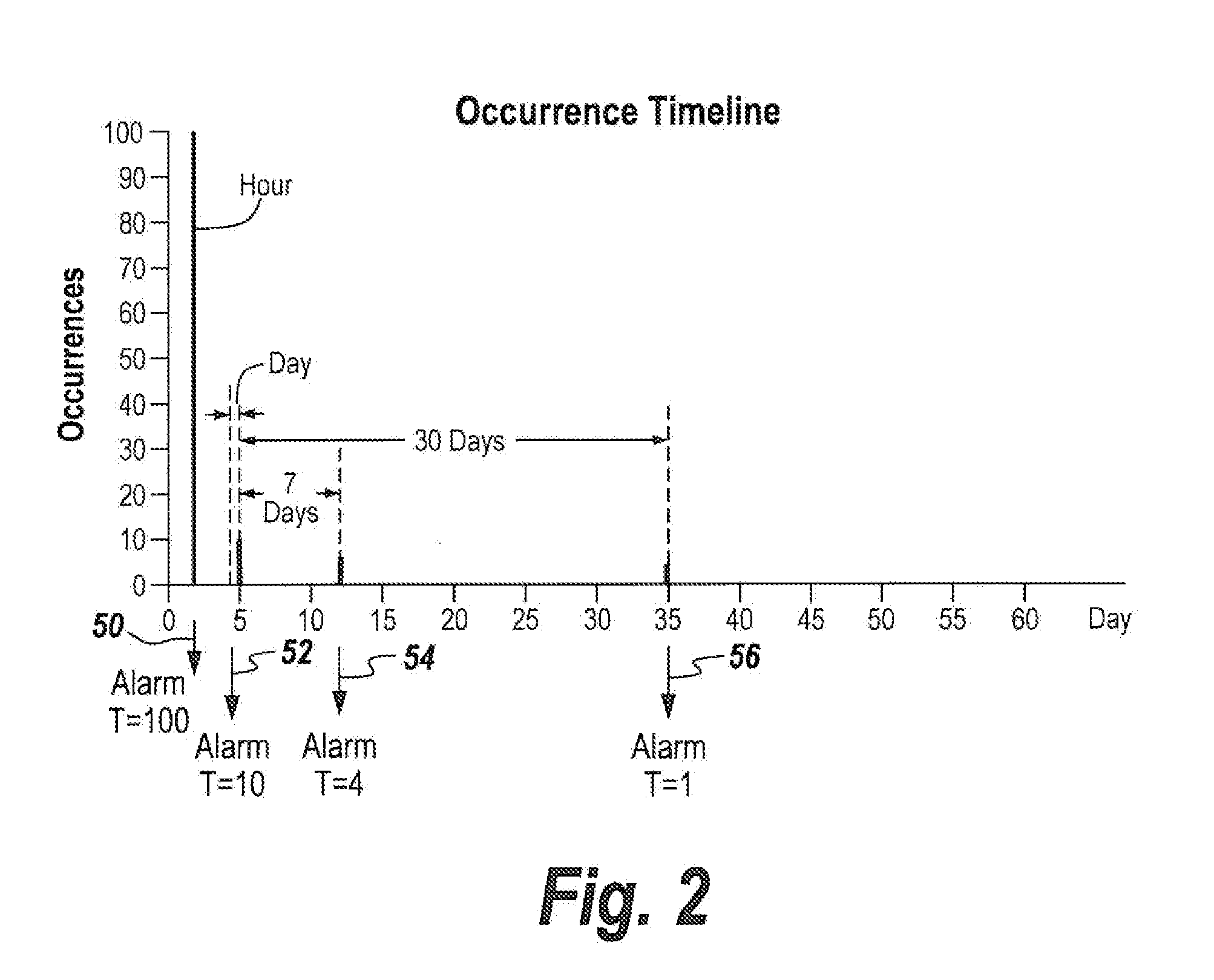
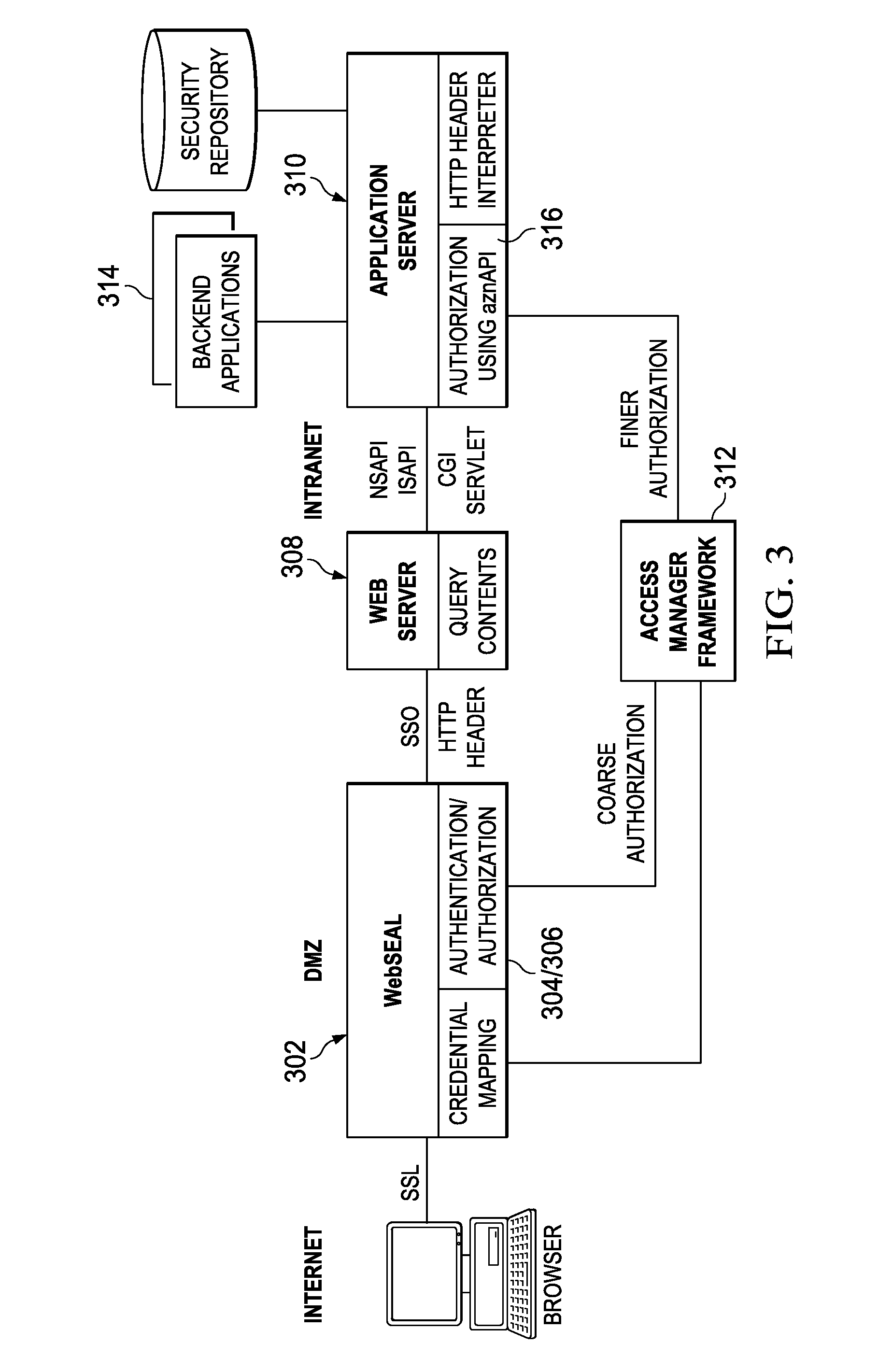
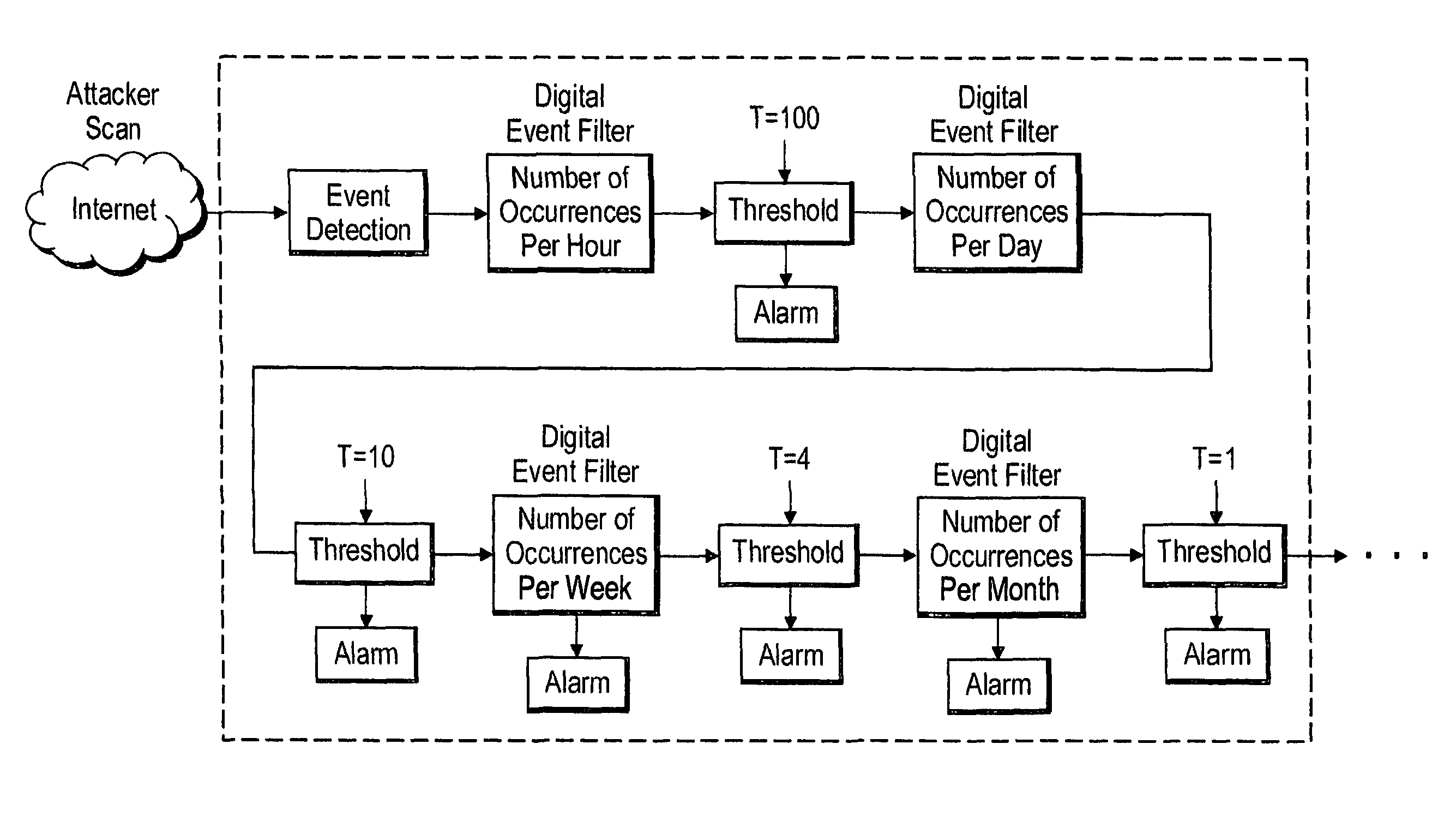
Method and apparatus for detecting ssh login attacks
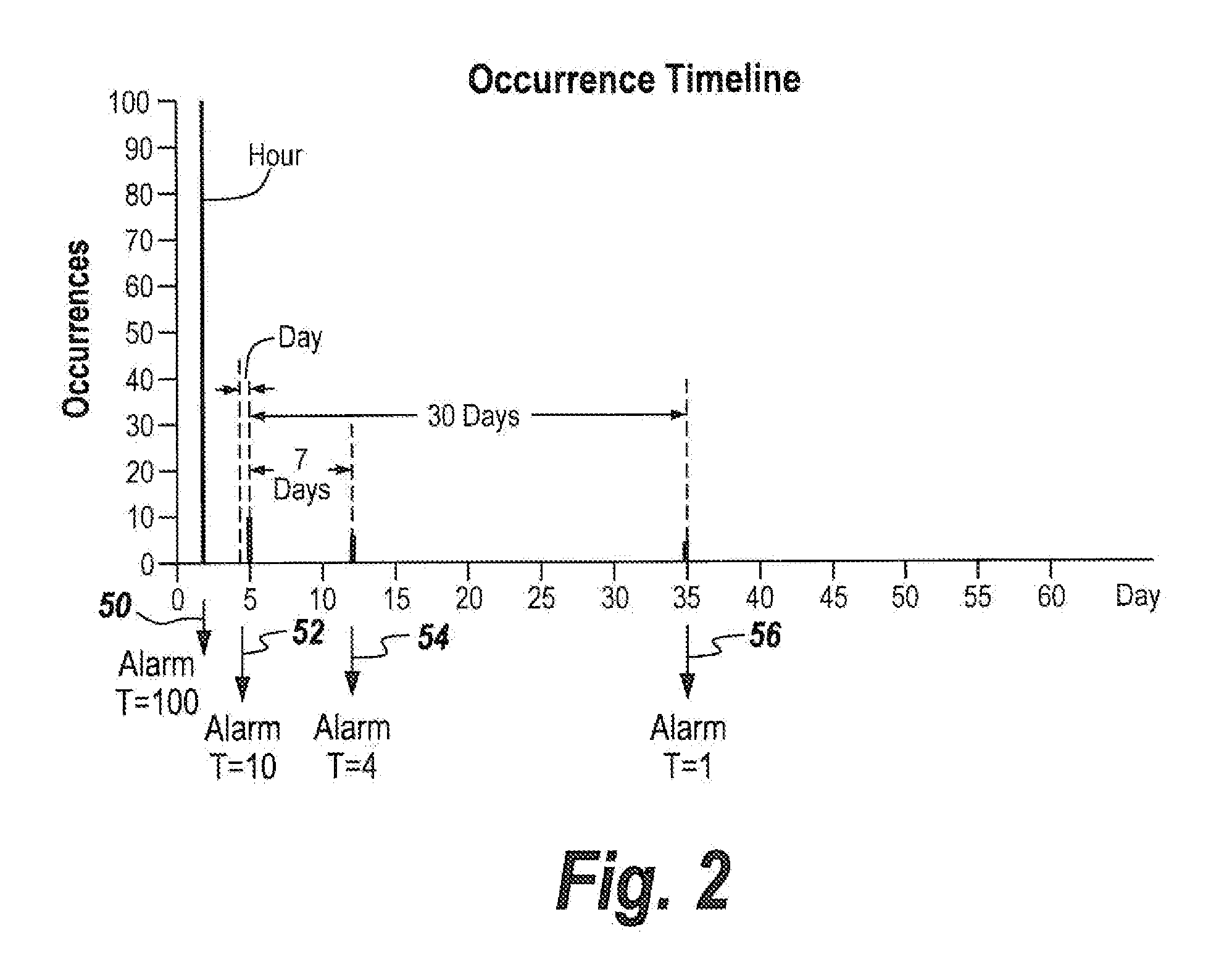
ActiveUS20110185419A1Remove noise causedWork lessMemory loss protectionError detection/correctionDigital filterSecurity analyst
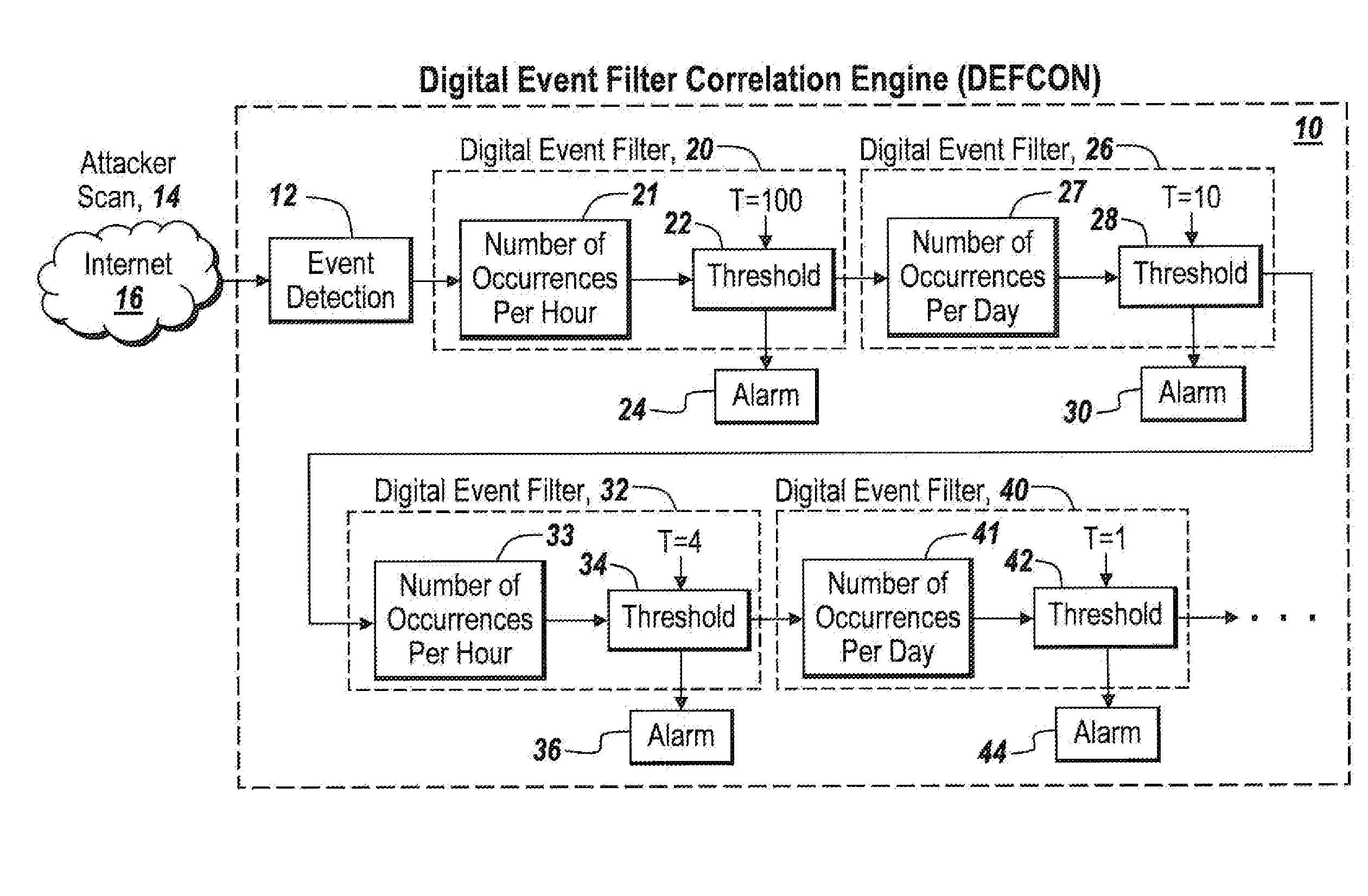
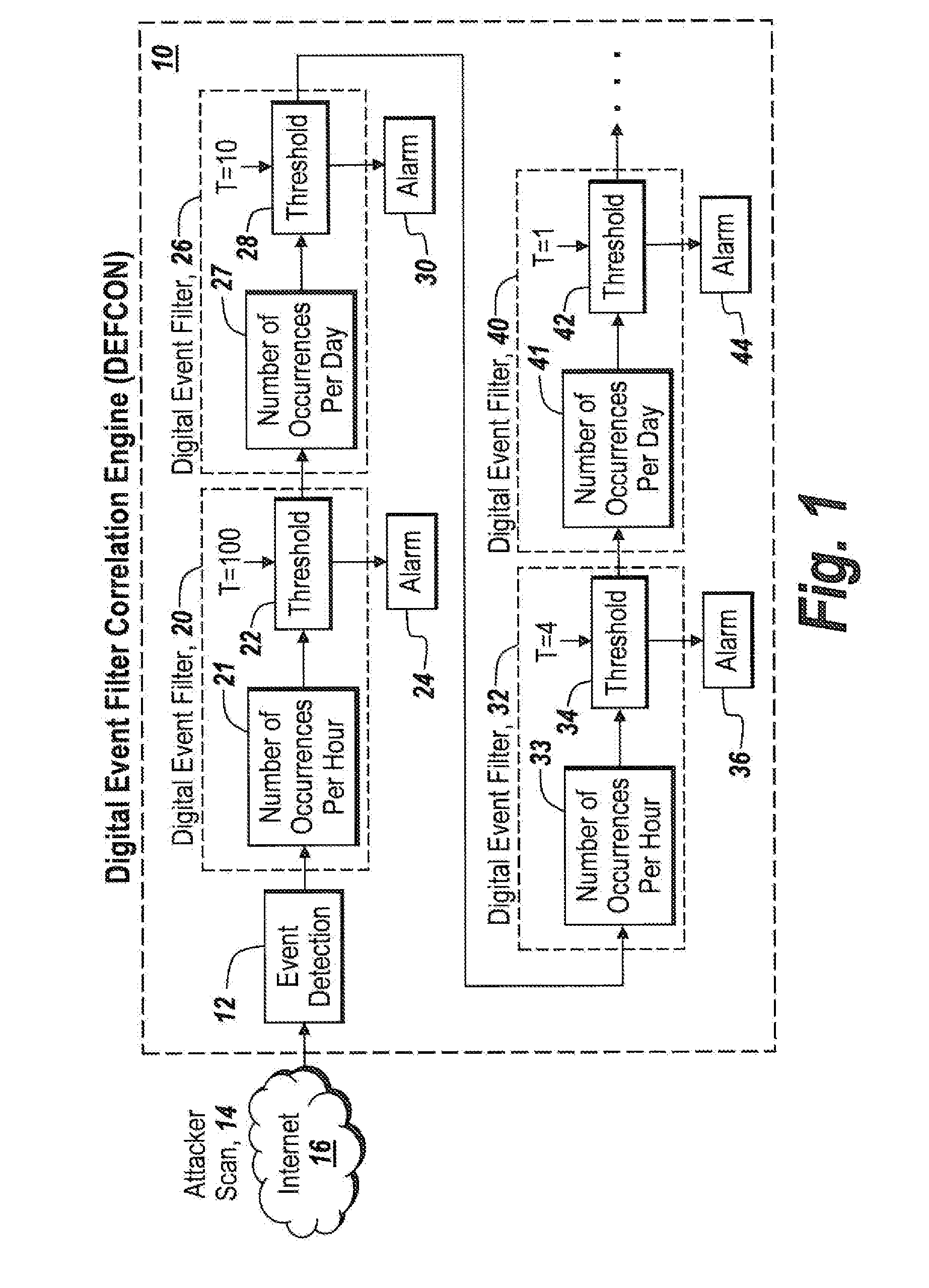
A digital filter correlation engine, wherein the correlation engine combines N arbitrary digital filter states based on the weights and along with a threshold generate a network incident. This network incident in turn can be feedback to another digital filter. This multi-layering capability allows the creation of higher level event detections that are time-based for a cyber security analyst to analyze, thereby reducing the amount of manual work the analyst has to do in inspecting behaviors within the network.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTERGRATION INC
Detection method and system for HTTP malicious traffic
ActiveCN109960729AEasy to detectReduce false positivesNatural language data processingTransmissionTraffic capacityCluster algorithm
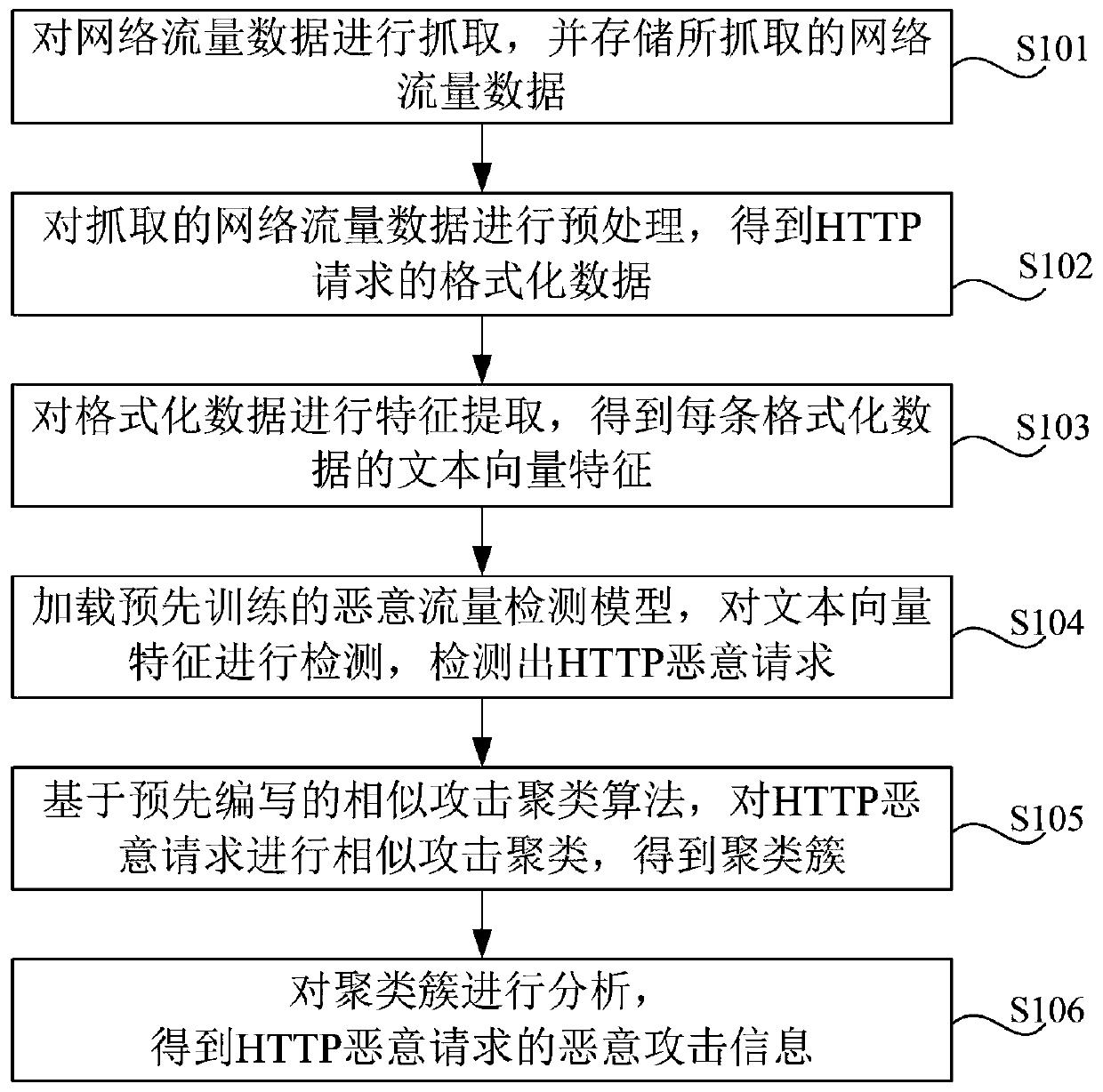
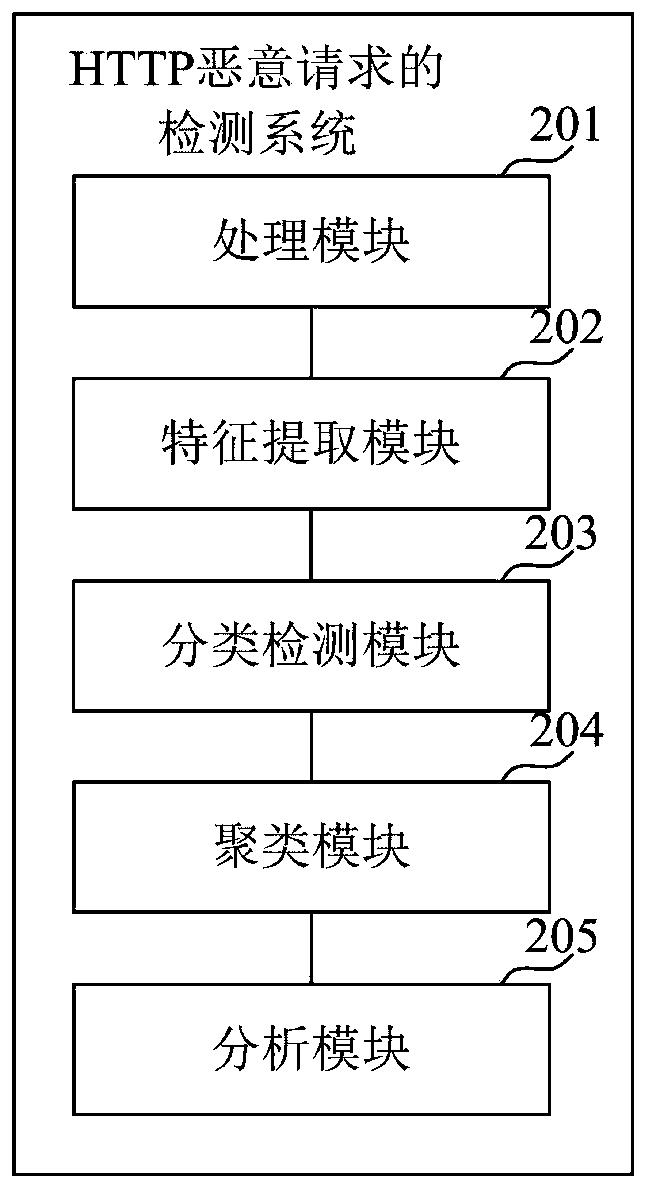
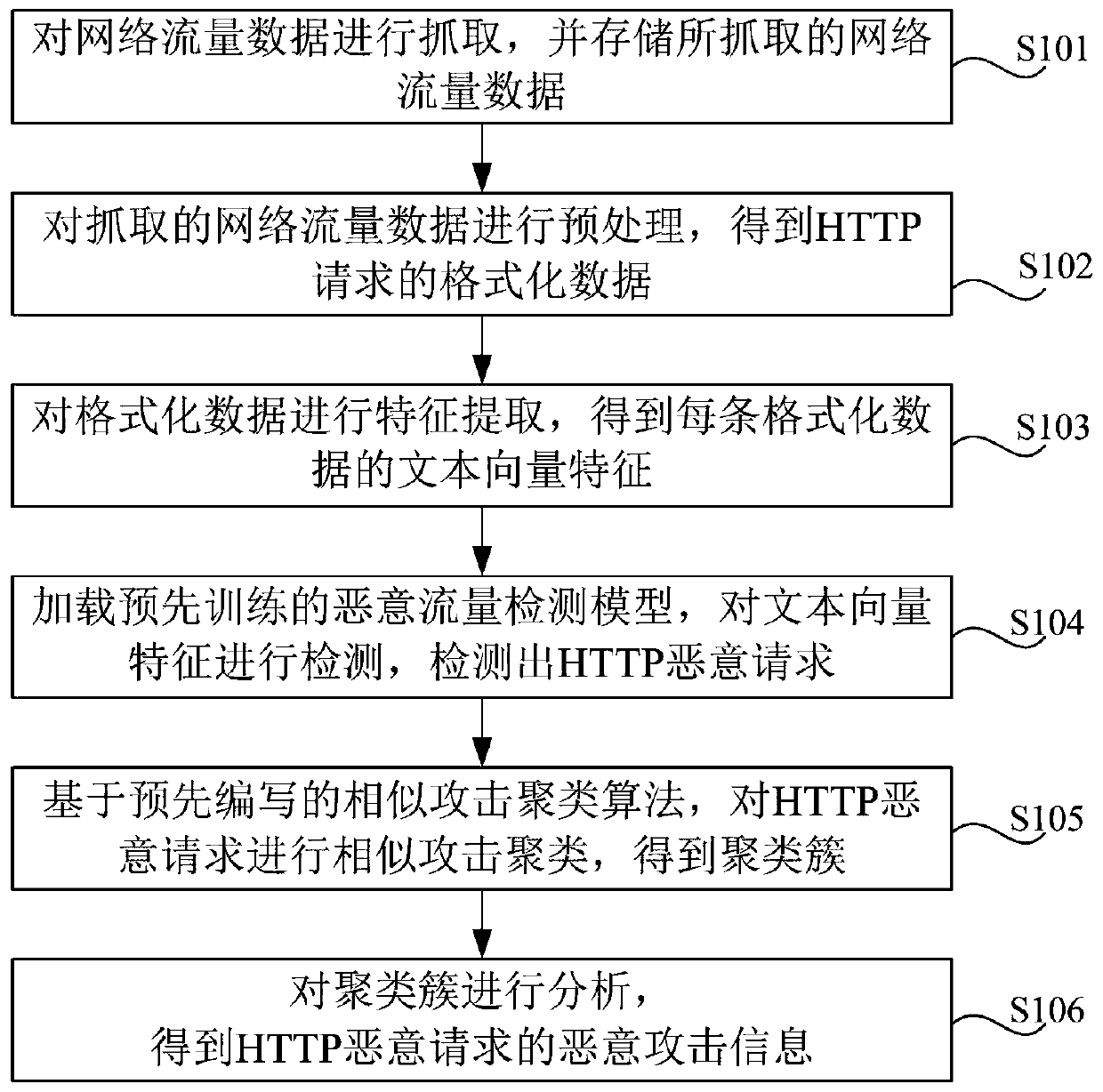
The invention discloses a detection method and system for HTTP malicious traffic, and the method comprises the steps: capturing network traffic data, carrying out the preprocessing of the network traffic data, and obtaining formatted data corresponding to each HTTP request; performing feature extraction on the formatted data to obtain text vector features of each piece of formatted data; performing classification detection on the text vector characteristics based on a pre-trained malicious flow detection model to detect an HTTP malicious request; performing similar attack clustering on the HTTP malicious request based on a similar attack clustering algorithm to obtain a cluster; and performing analysis based on the cluster to obtain malicious attack information of the HTTP malicious request. According to the method, the Spark big data analysis engine is used for carrying out feature extraction and conversion on the flow data, and the machine learning and clustering algorithm is used for mining the malicious flow, so that the detection accuracy of the network malicious flow is improved, and the flow analysis time cost of security analysts is reduced.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT
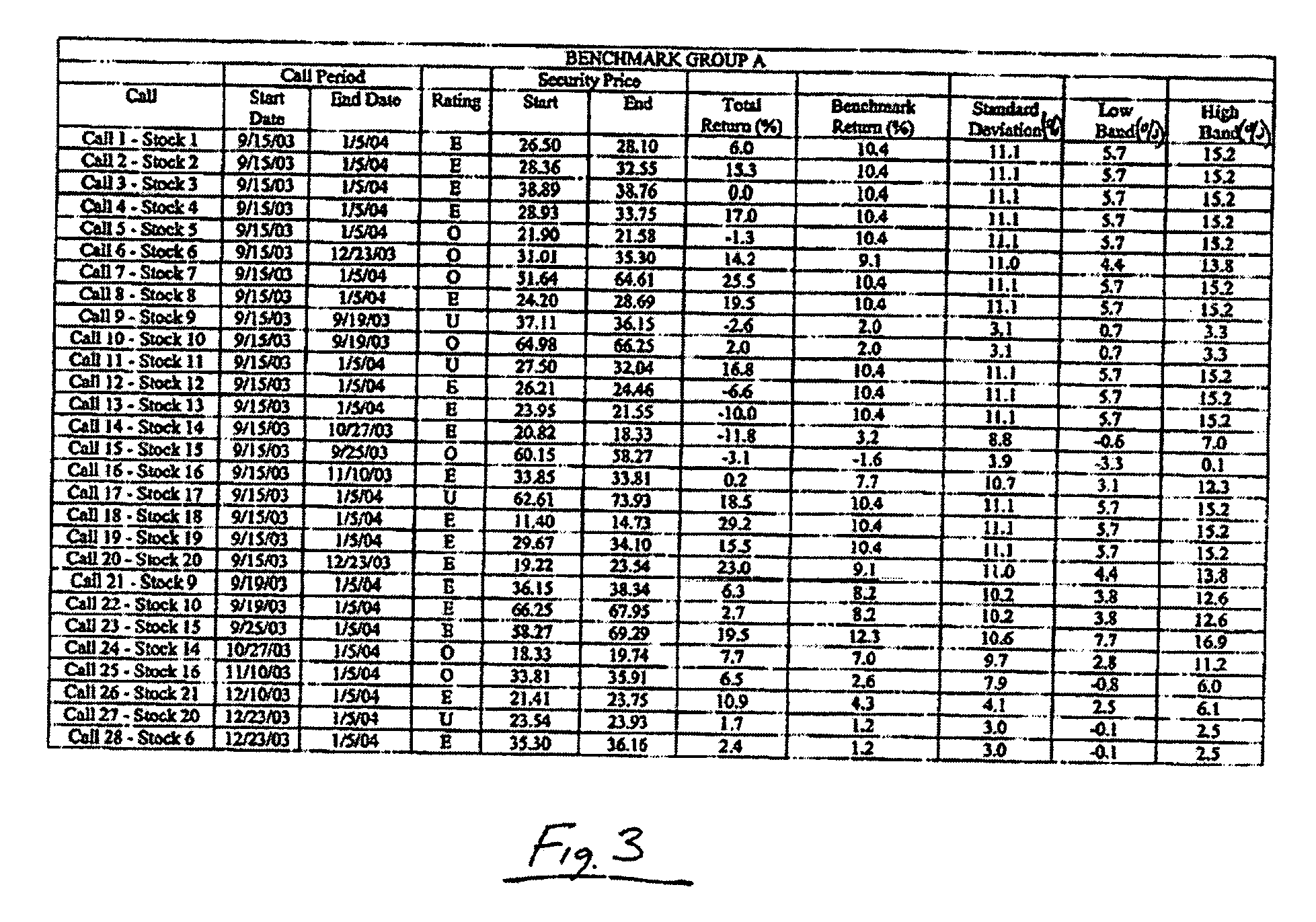
Method and system for evaluating the investment ratings of a securities analyst
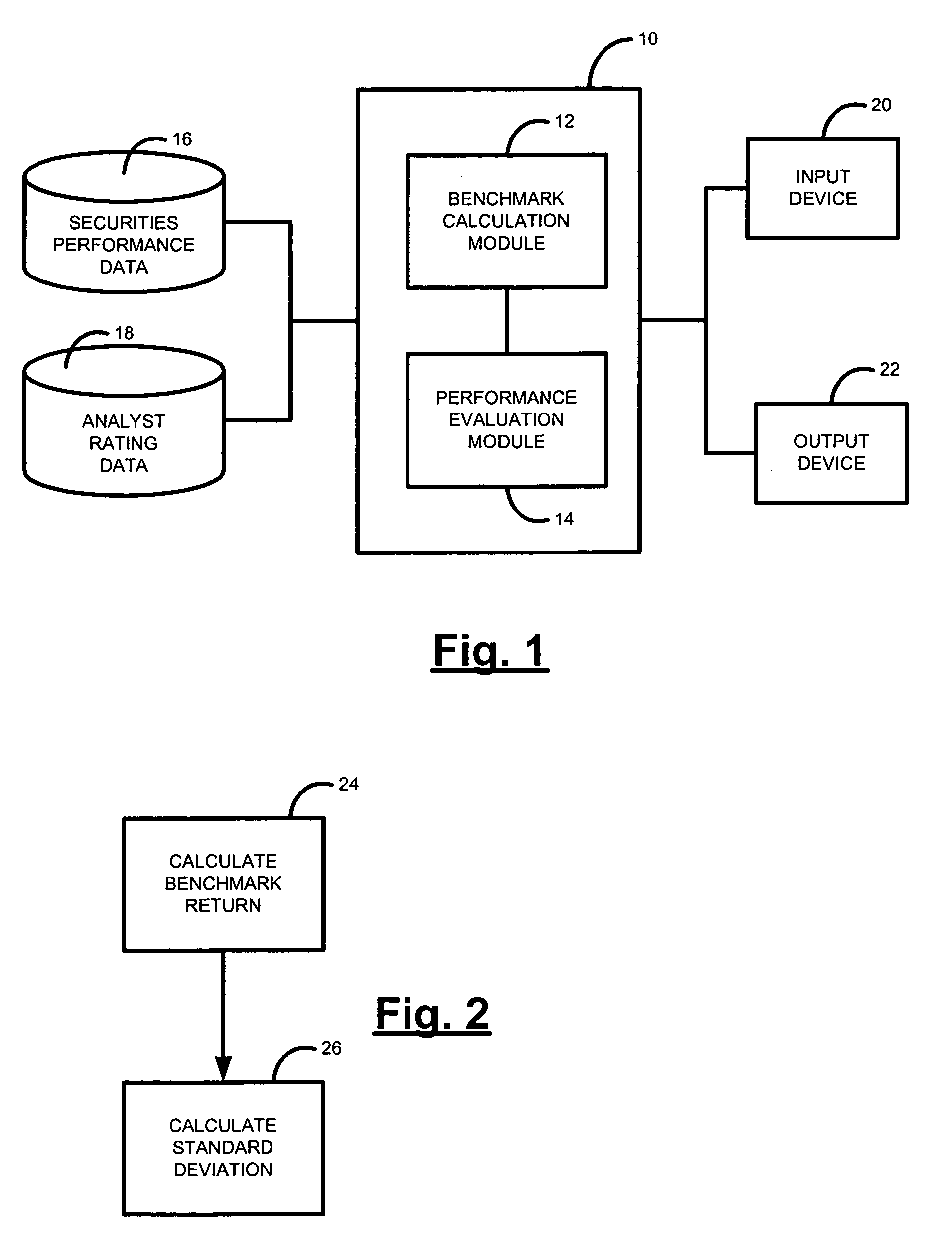
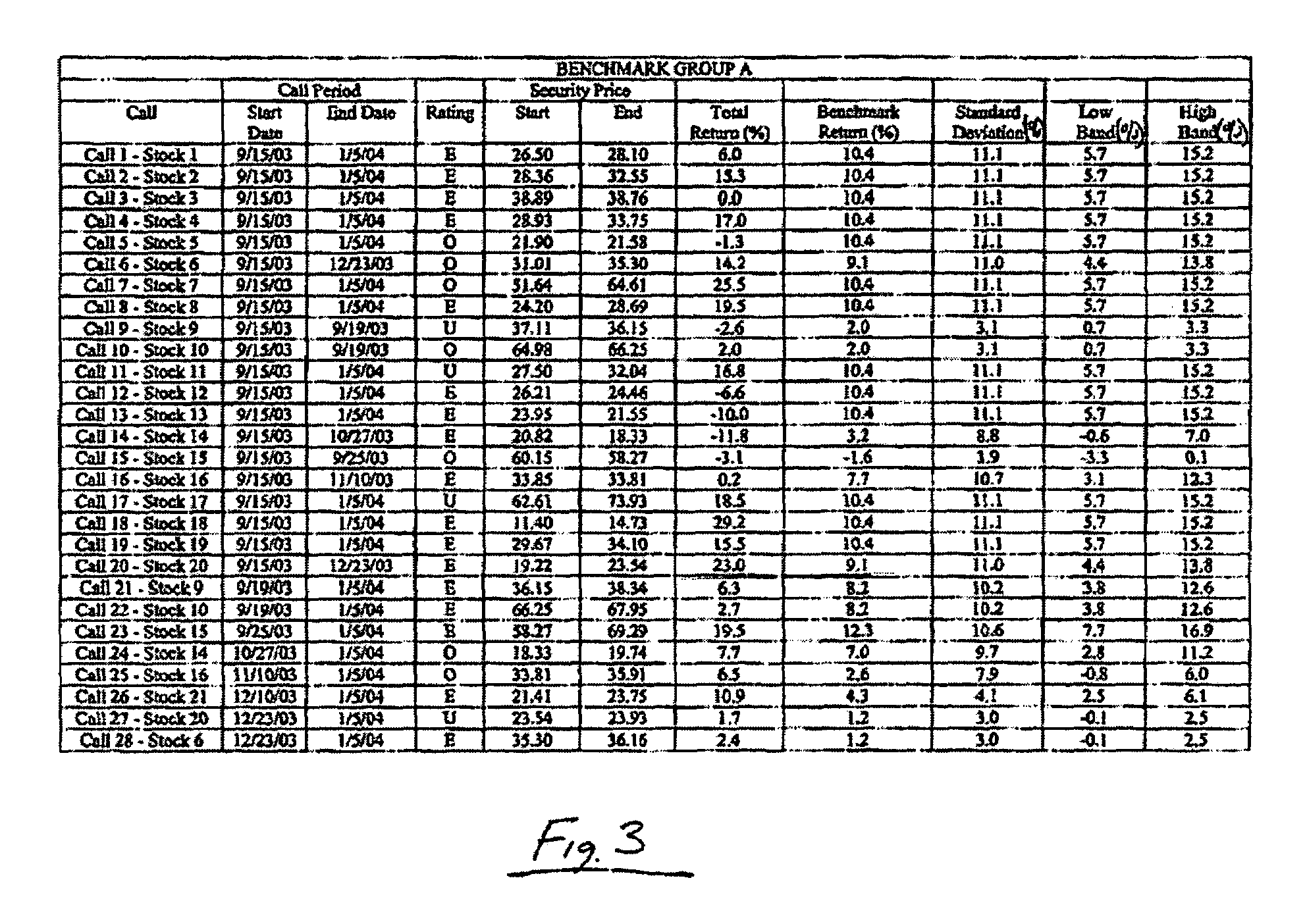
Systems and methods for measuring the performance of calls on securities by a securities analyst during an evaluation period are disclosed. According to various embodiments, the system may include a performance evaluation module. The performance evaluation module is for determining a value (called the “hit ratio”) indicative of the success of the calls by the analyst for securities within a benchmark group of securities within an industry covered by the analyst relative to a benchmark return for the benchmark group for the corresponding call periods of the calls. The hit ratio may be computed as the ratio of the sum of the actual excess returns to the sum of the total available excess returns for each call by the analyst over the call evaluation period. The contributions to the hit ratio by each call may be equally weighted or weighted according to market capitalization of the rated security.
Owner:MORGAN STANLEY
Feedback-based prioritized cognitive analysis
ActiveUS20180367549A1Easy to analyzeDigital data information retrievalMachine learningEvent dataGraph Node
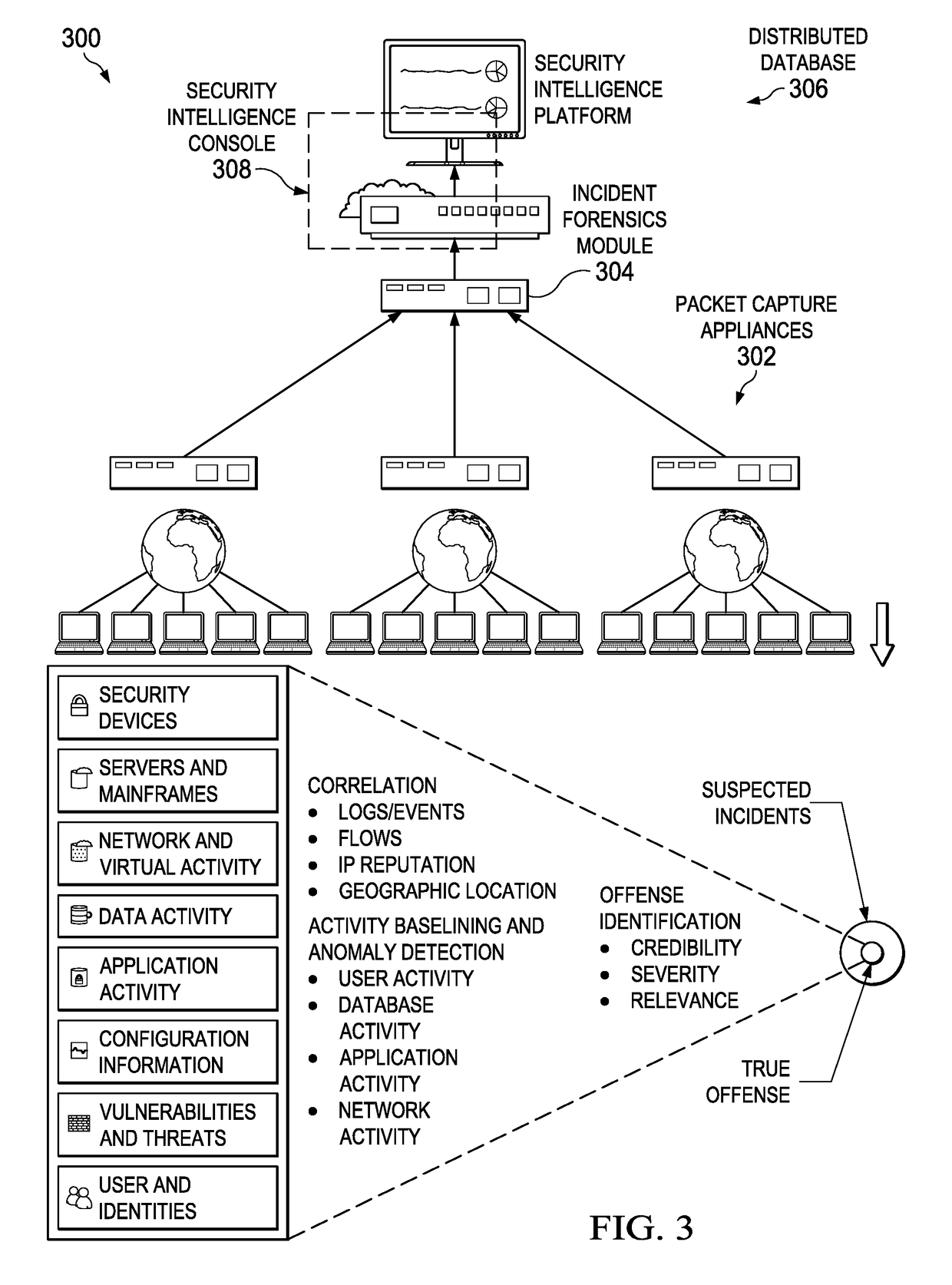
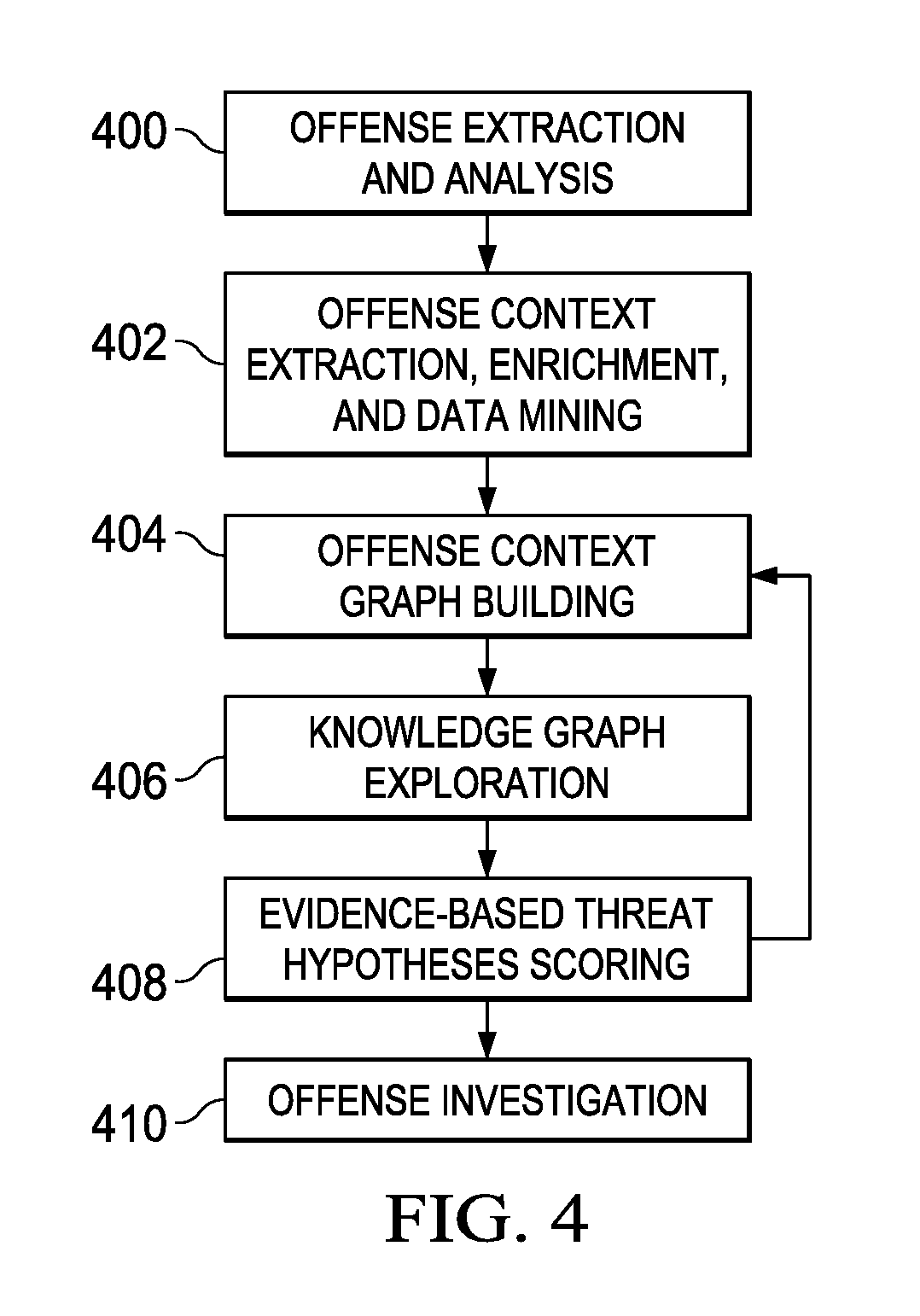
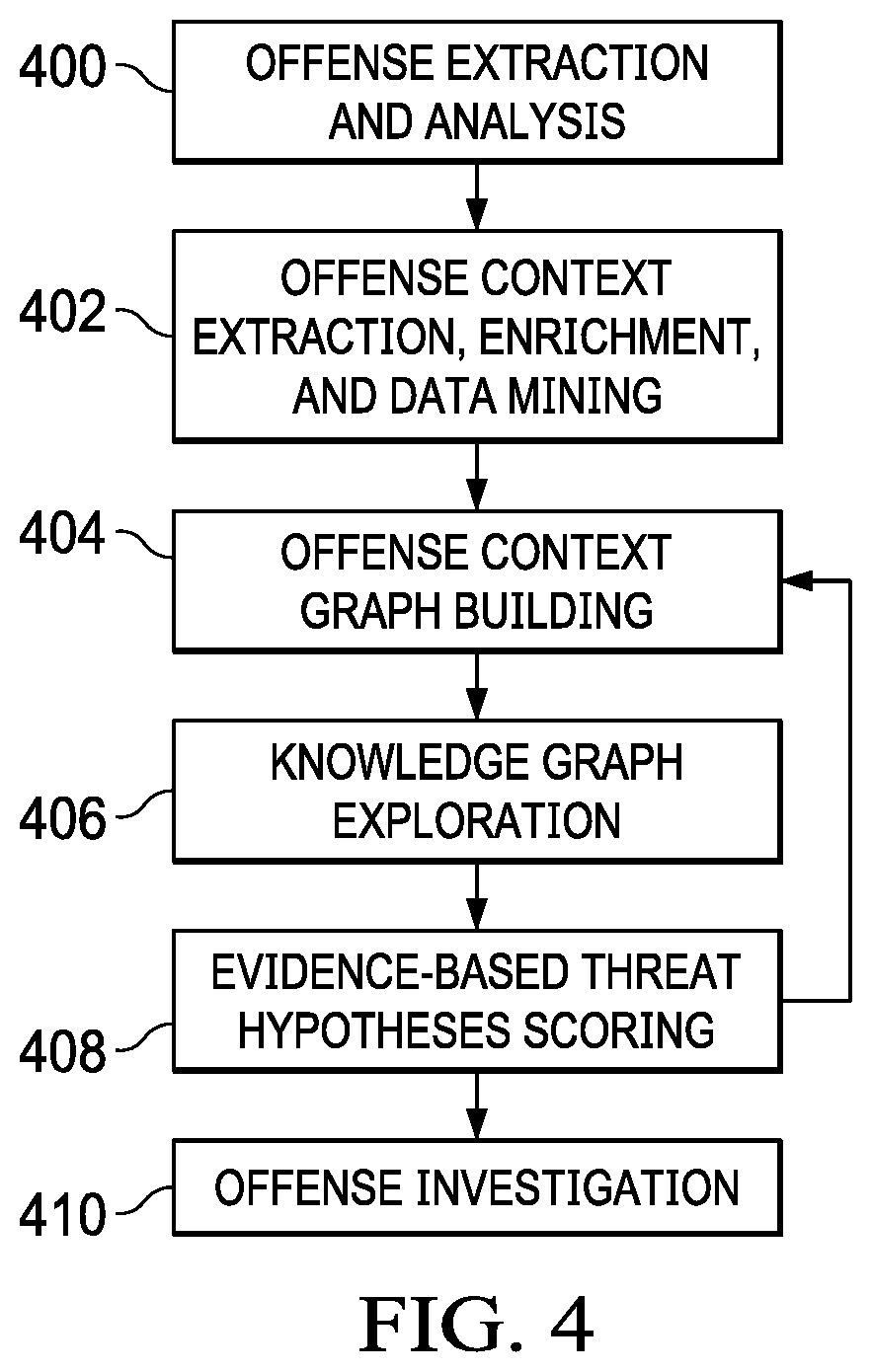
An automated method for processing security event data in association with a cybersecurity knowledge graph having nodes and edges. It begins by receiving from a security system (e.g., a SIEM) information representing an offense. An offense context graph is built. Thereafter, and to enhance the offense context graph, given nodes and edges of the knowledge graph are prioritized for traversal based on an encoding captured from a security analyst workflow. This prioritization is defined in a set of weights associated to the graph nodes and edges, and these weights may be derived using machine learning. The offense context graph is then refined by traversing the nodes and edges of the knowledge graph according to a prioritization tailored at least in part by the encoding. In addition to using security analyst workflow to augment generation of weights, preferably the machine learning system provides recommendations back to the security analysts to thereby influence their workflow.
Owner:IBM CORP
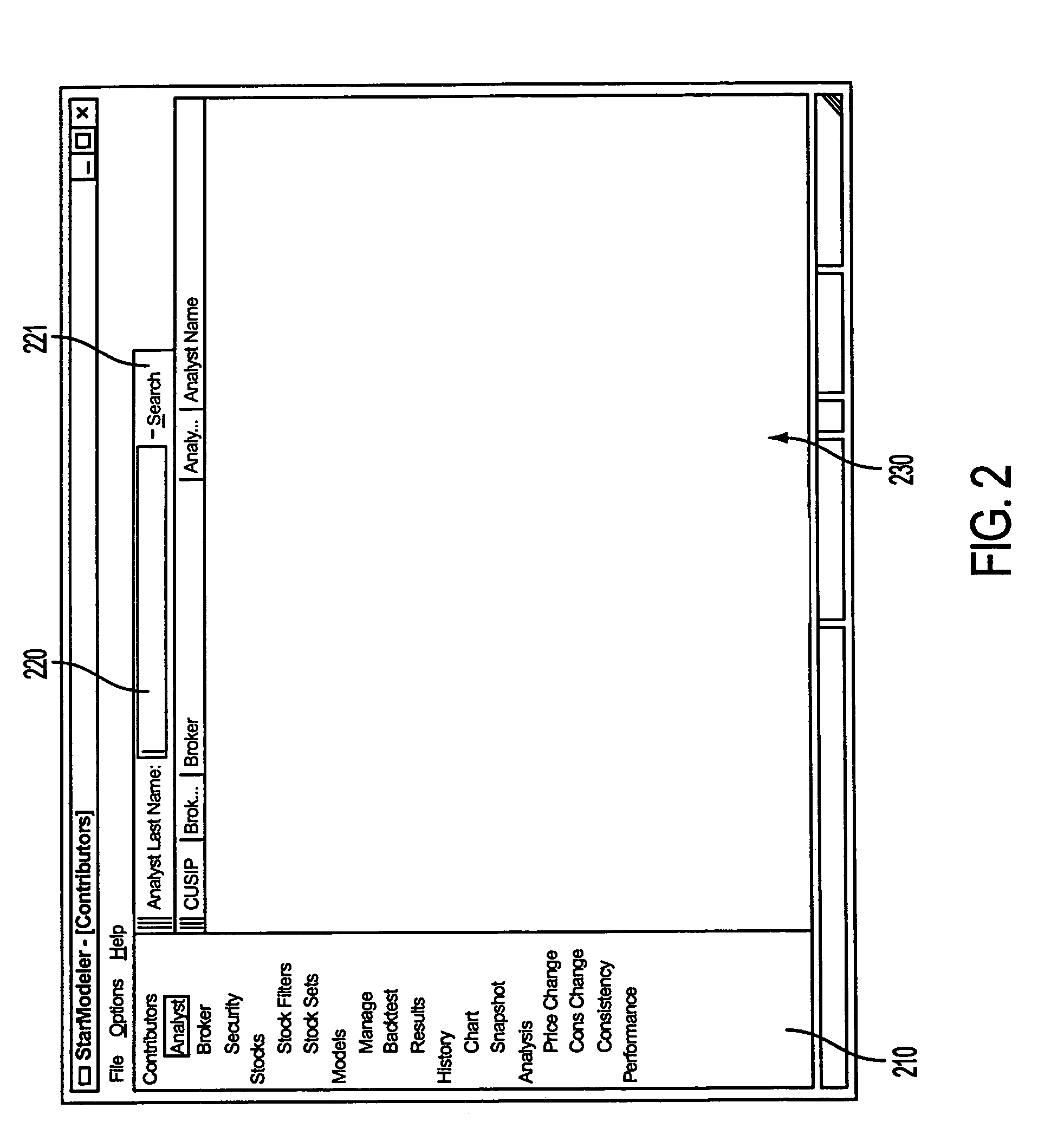
System and method for facilitating the selection of security analyst research reports
InactiveUS20050080695A1Convenient researchAvoiding unnecessary expenditure of resourceFinanceBuying/selling/leasing transactionsGraphicsGraphical user interface
A system and method for facilitating the selection of security analyst research reports is provided. Investors (or other users) seeking to efficiently target and access only those security analyst research reports most likely to assist in an investment-related decision may access an application. The application may enables users to simultaneously view (e.g., via a graphical user interface) current predictions of security analysts (or other contributors), research report objects associated with the predictions, and data, metrics, or other information corresponding to the historical performance of predictions made by the analysts. By simultaneously displaying historical performance data for contributors, along with their current predictions and research report objects associated with their current predictions, users are provided with objective criteria by which to guide their selection of research reports.
Owner:THOMSON REUTERS MARKETAB
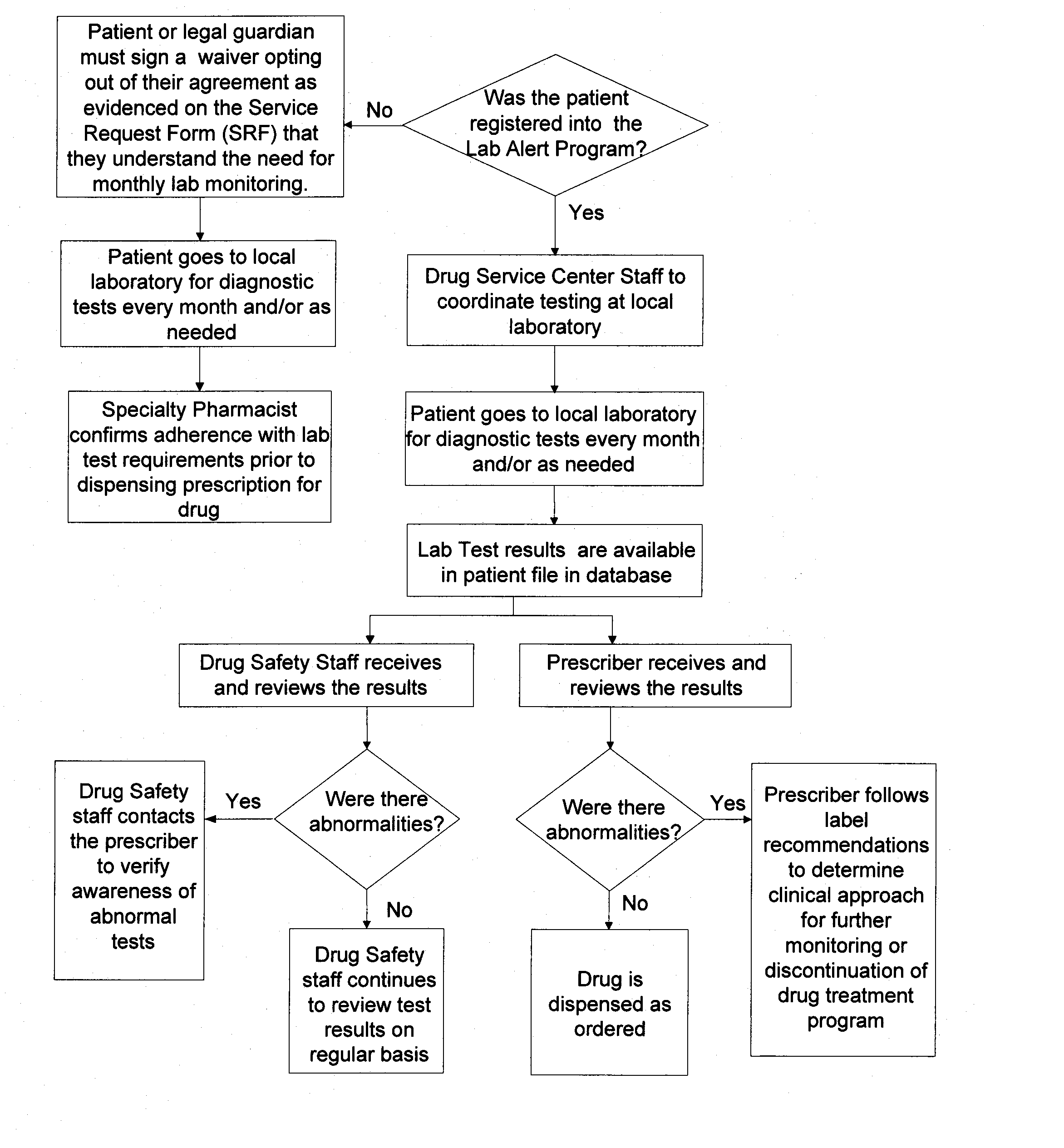
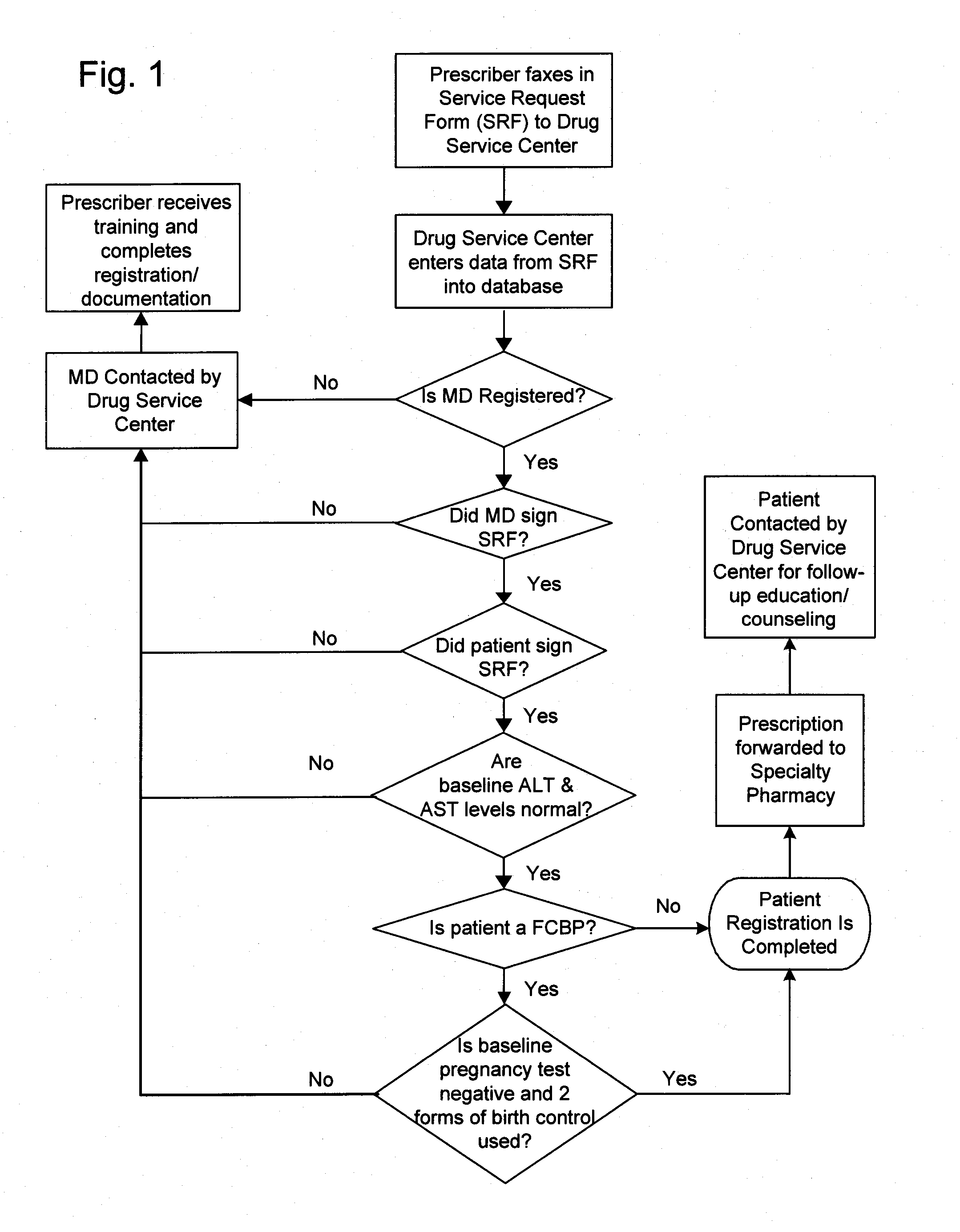
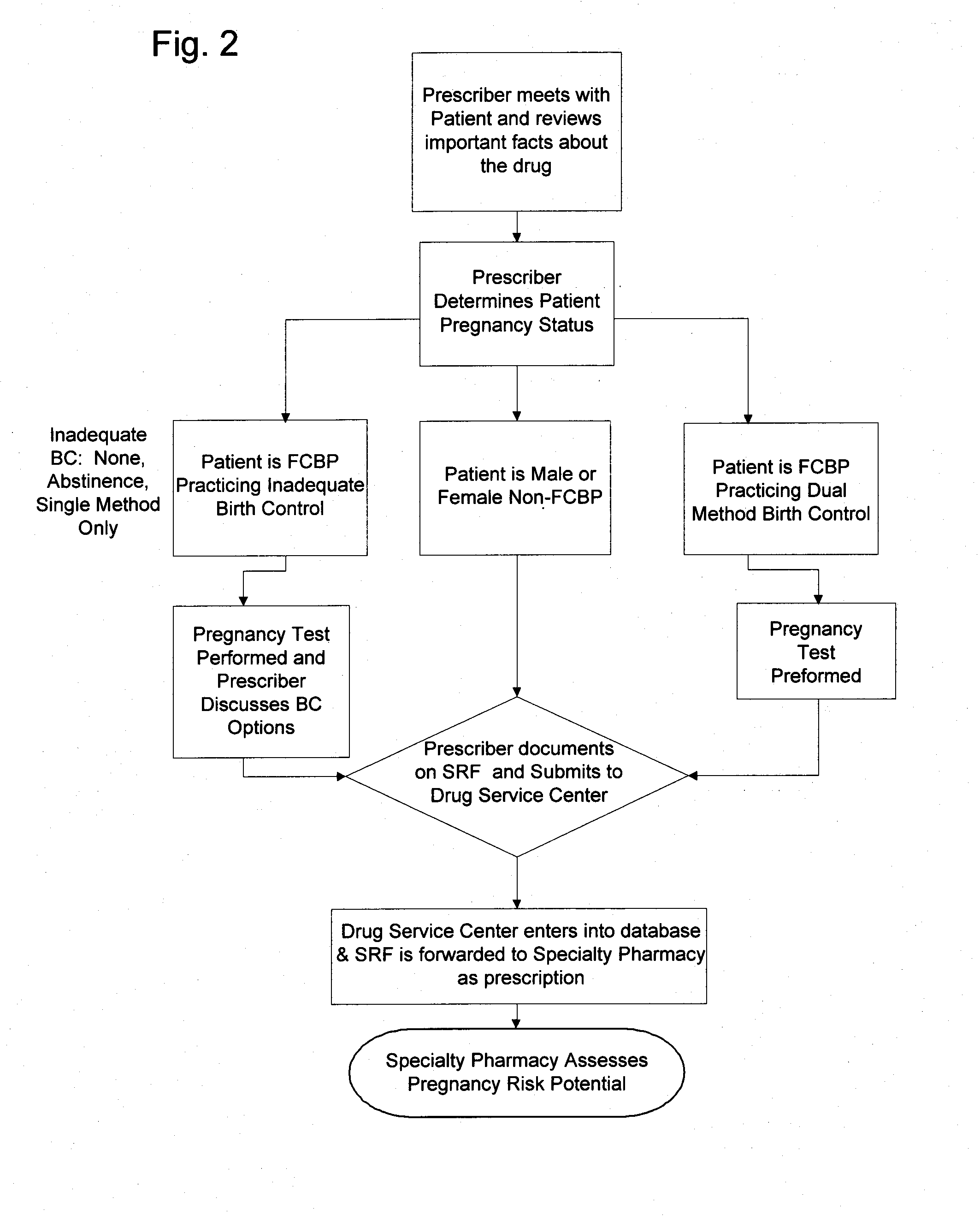
Method of managing and reducing side effects associated with exposure to a drug
InactiveUS20070219825A1Minimize occurrenceData processing applicationsHealth-index calculationHealth related informationPharmacy
A method for restricted distribution of a drug to a patient while minimizing the occurrence of adverse side effects. The method restricts access to the drug by preventing distribution to certain patients for whom the drug may be contraindicated. The method permits a prescription to be filled by a pharmacy only after the pharmacy has received an approval for release of the prescription. Generation of the prescription approval depends on registration of a prescriber, pharmacy and patient in a central database, and the determination that the risk is acceptable that the patient will experience an adverse side effect. The database contains a patient profile that may include additional patient-specific health-related information that is probative of the risk that an adverse side effect is likely to occur if the patient is exposed to the drug. Based in part on the information in the patient profile, the registered prescriber makes a determination as to the patient's risk of adverse side effects. If the registered prescriber determines that the risk is acceptable, a prescription request is generated. At the time that the prescription is to be dispensed to the patient, the pharmacy also makes a determination as to the patient's risk of adverse side effects. If the pharmacy determines that the risk is acceptable, the drug is dispensed to the patient. Additional steps may be taken to ensure compliance with the drug delivery method, such as education, oversight by a drug safety analyst, and / or regular contact with a representative.
Owner:ENCYSIVE PHARMA INC
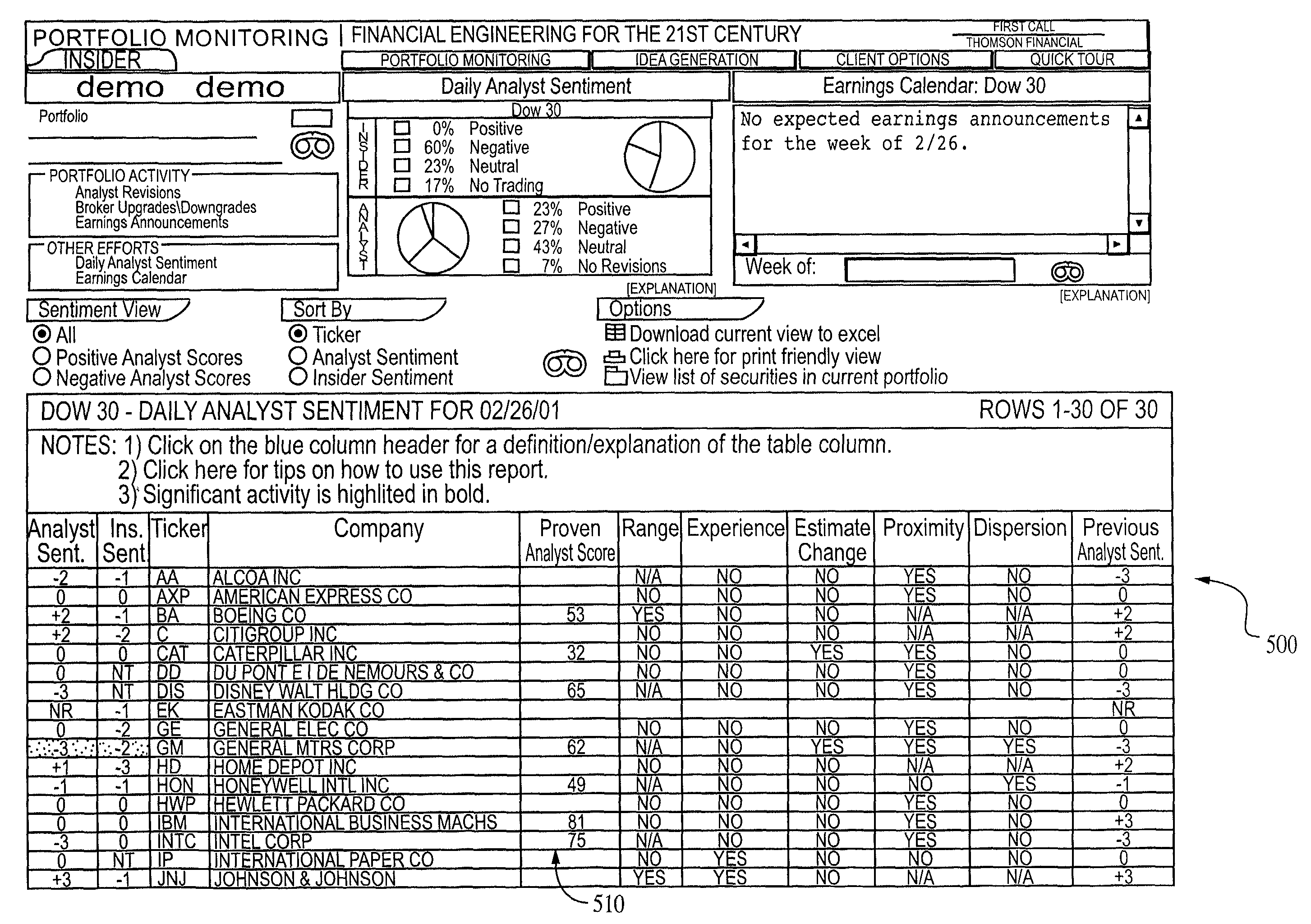
Security analyst estimates performance viewing system and method
A method and system are provided for simultaneously displaying historical accuracy indicators for an analyst and the analyst's estimate for a future event, on an analyst by analyst basis, for a selected one or more analysts, wherein the historical accuracy indicators and analyst's estimate for a future event may involve one or more securities. Other information for simultaneous display may include one or more of historical performance indicators, analyst recommendation data, model information, and other current data, performance data and historical data, on an analyst by analyst basis, for a selected one or more analysts. Various display options may be available, such as displaying those analysts that have current estimates for a user selected security. Other viewing options may involve displaying data for a group of analysts for a current estimate for a user selected security. Other viewing options may be available and other information may be displayed.
Owner:REFINITIV US ORG LLC
Security analyst estimates performance viewing system and method
A system and method for measuring, analyzing, and tracking the past performance of security analysts' earnings estimates and recommendations. The present invention provides a database of historical data relating to security analyst earnings estimate predictions wherein a historical model enables users to view the historical data as a time series of earnings estimates for each analyst selected, for a selected period of time, for a predetermined earnings event. Users may define a model to automatically create enhanced composite estimates wherein an improved prediction of the quantity being estimated, such as company earnings, revenue or cash flow is obtained. Users may view performance screens and historical performance data for a particular contributor or various contributors for a given security. Other views may be available.
Owner:REFINITIV US ORG LLC
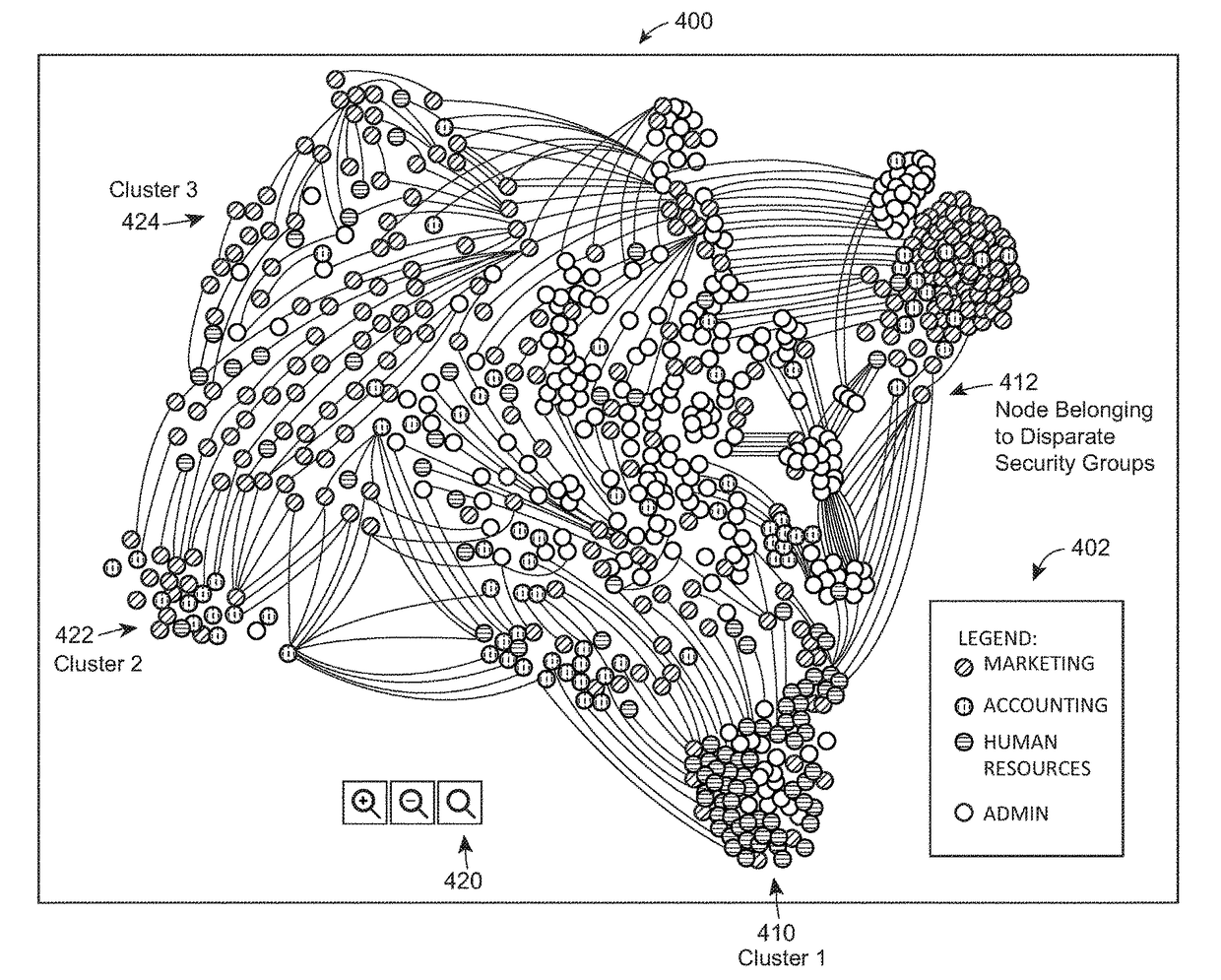
Method and system for identifying security risks using graph analysis
ActiveUS9819685B1Increase in sizeEasy to identifyDigital data processing detailsTransmissionGraphicsInternet privacy
Methods, systems, apparatus, and non-transitory computer readable media are described for identifying users who are likely to have unauthorized access to secure data files in an organizational network. Various aspects may include presenting the identified users on a display for a system administrator and / or security analyst to resolve. For example, the display may include a graph data structure with users represented as nodes and connections between users represented as edges. Each connection may be a pair of users belonging to a same security group. The graph data structure display may be organized and color coded in such a manner, that a system administrator and / or security analyst may quickly and easily view the users who are most likely to have unauthorized access to secure data files. The authorized access may then be remedied or taken away.
Owner:STATE FARM MUTUAL AUTOMOBILE INSURANCE
Methods and systems for measuring performance of a security analyst
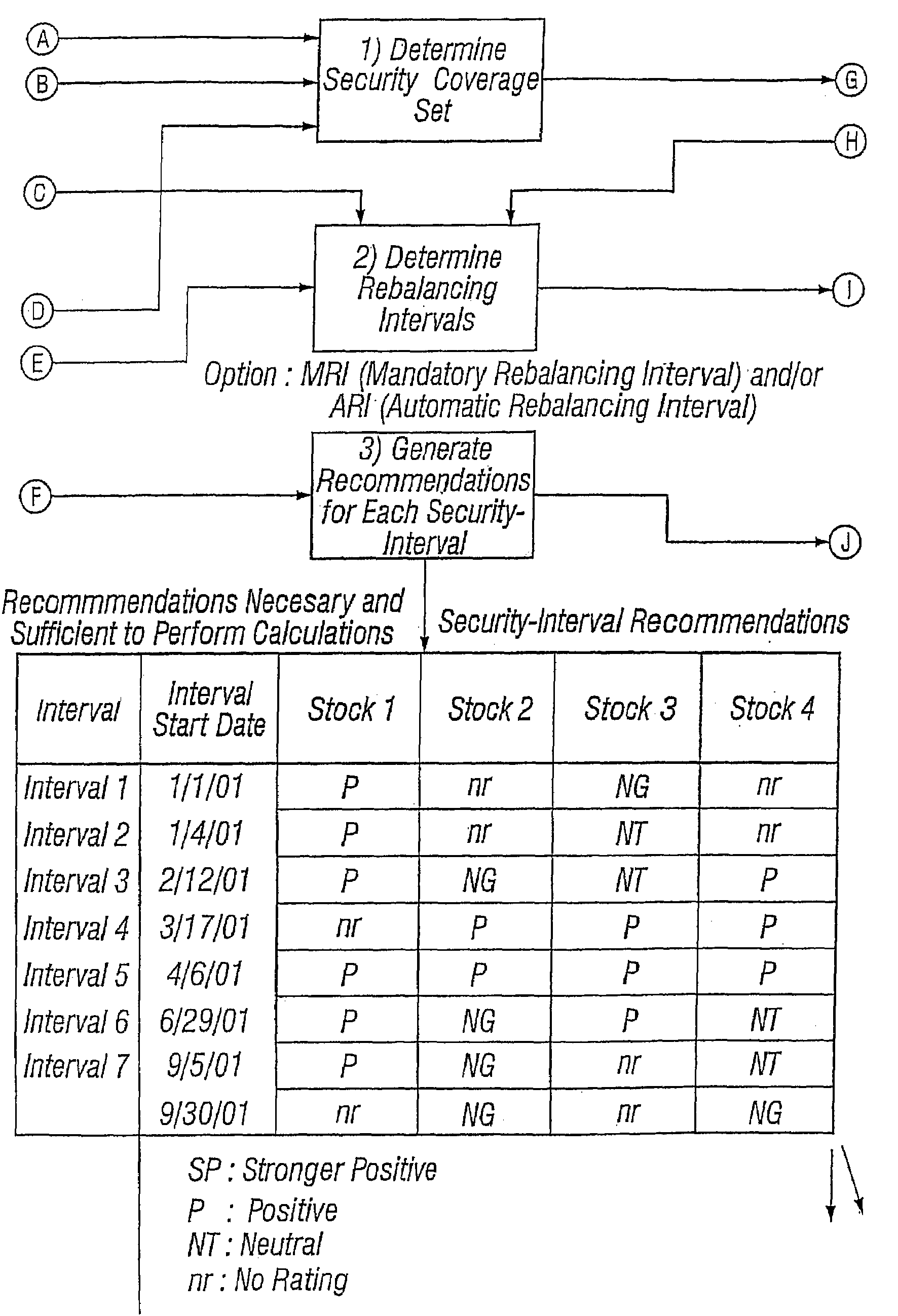
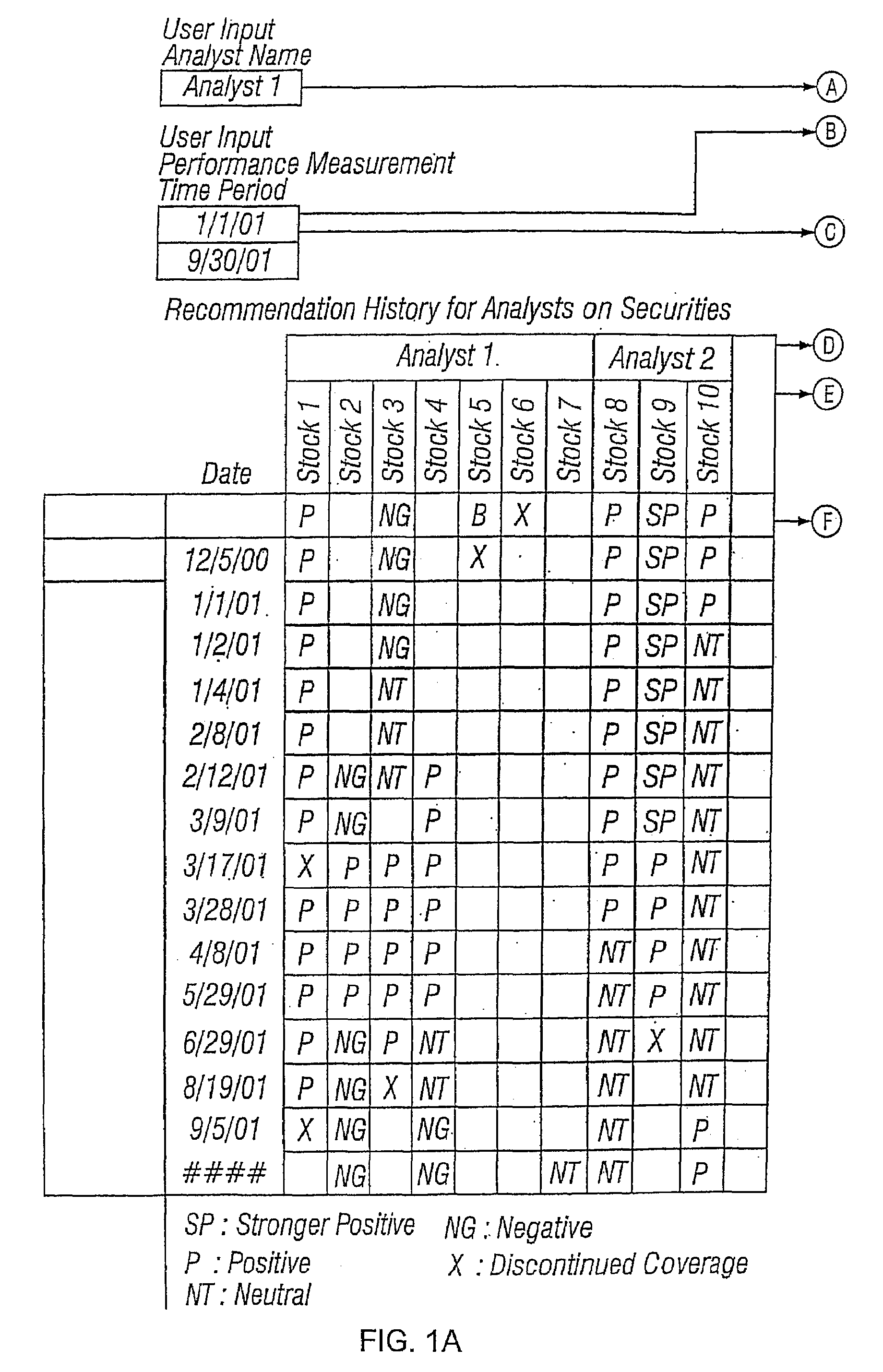
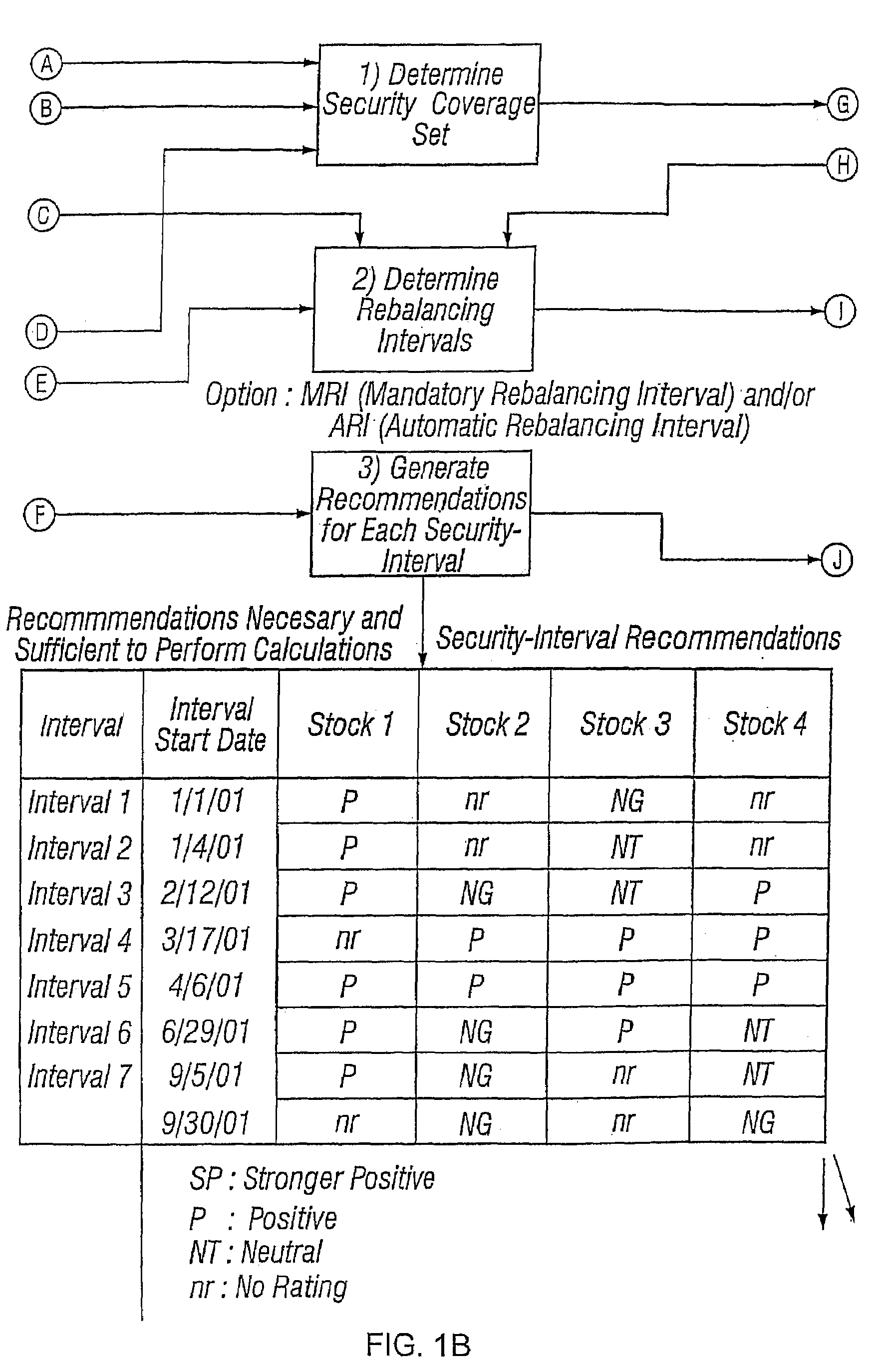
A method of measuring performance of a security analyst includes selecting an analyst that covers a set of securities, and a performance measurement time period. A value add is created by subtracting a return of a benchmark portfolio from a return of a simulated portfolio. The return of the benchmark portfolio is derived exclusively from a selected set of securities that are included in the set of securities covered by the analyst. The simulated portfolio has constituents and weights that are a function of the analyst's recommendations on the securities in the selected set.
Owner:REFINITIV US ORG LLC
Digital filter correlation engine
ActiveUS20110185418A1Reduce the amount requiredCancel noiseMemory loss protectionError detection/correctionEngineeringDigital filter
A digital filter correlation engine, wherein the correlation engine combines N arbitrary digital filter states based on the weights and along with a threshold generate a network incident. This network incident in turn can be feedback to another digital filter. This multi-layering capability allows the creation of higher level event detections that are time-based for a cyber security analyst to analyze, thereby reducing the amount of manual work the analyst has to do in inspecting behaviors within the network.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTERGRATION INC
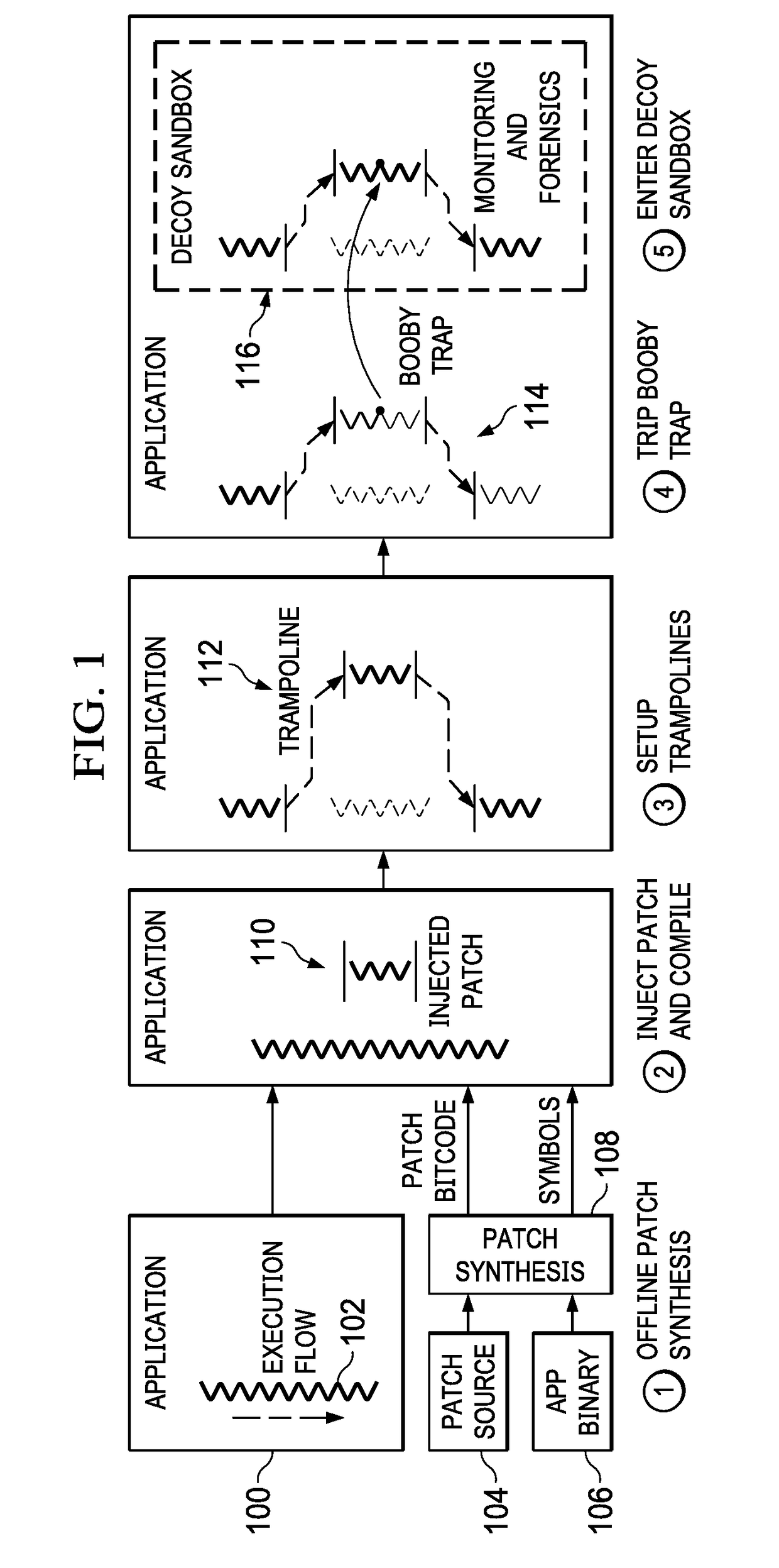
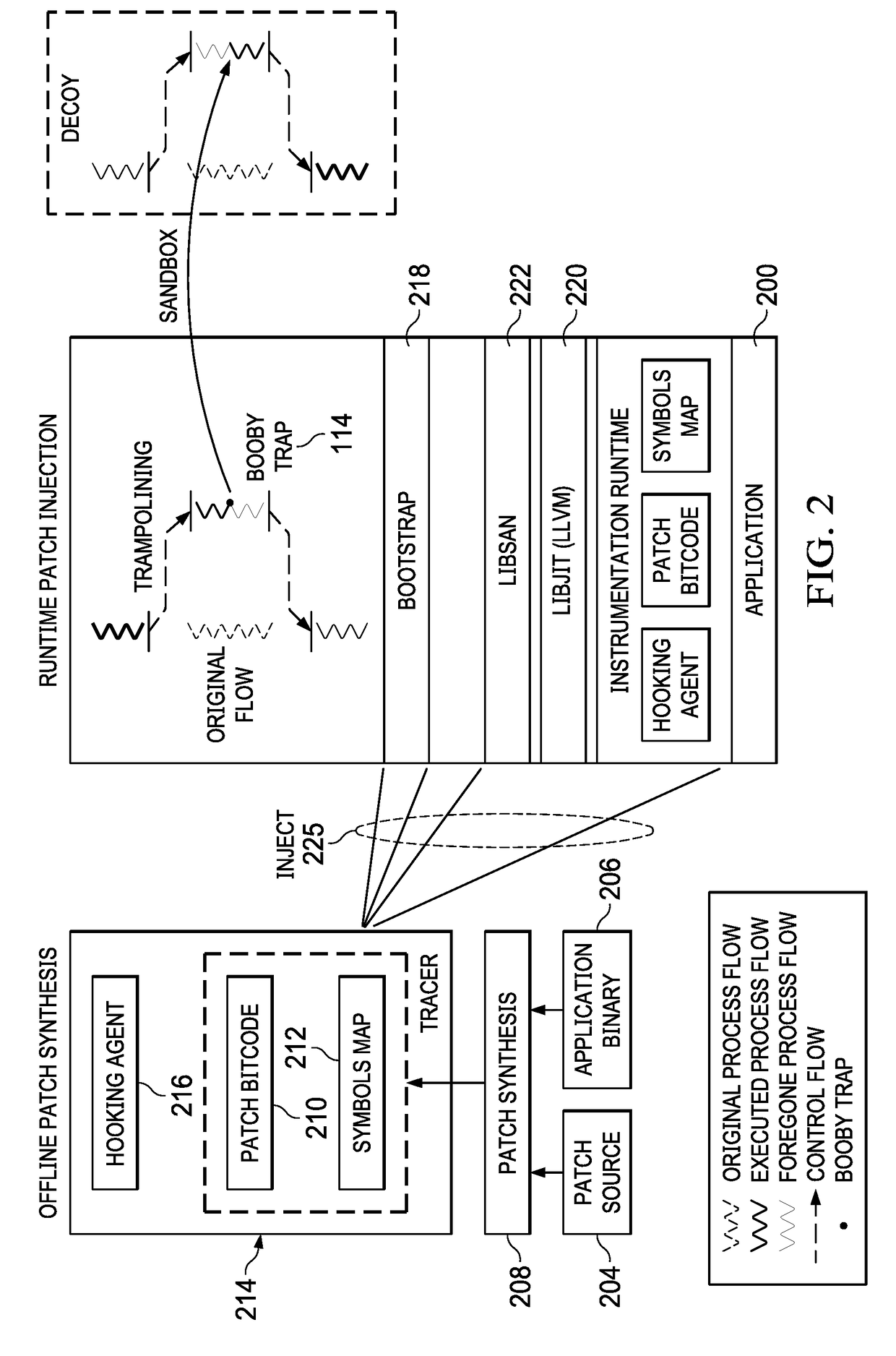
On-demand injection of software booby traps in live processes
ActiveUS20190068640A1Minimal performance overheadRapid deploymentTransformation of program codePlatform integrity maintainanceDecoyDowntime
This disclosure provides for rapid deployments of application-level deceptions (i.e., booby traps) to implant cyber deceptions into running legacy applications both on production and decoy systems, with no downtime and minimal performance overhead compared with the original application. An application-level booby trap is a piece of code injected into an application, and which provides an active defense or deception in response to an attack. A booby trap does not influence program execution under normal operation, and preferably elicits a response that can be defined by a security analyst. In operation, a booby trap is compiled into a bitcode using a patch synthesis process, and it is then injected into a running application, where it is compiled further into machine code, and linked directly with the existing application constructs. The original function also is modified with a function trampoline, and subsequent calls to the original function are then directed to the new function. As easily as a deception (provided by the booby trap) can be deployed, it can be removed easily, thereby leaving no trace in the application.
Owner:IBM CORP
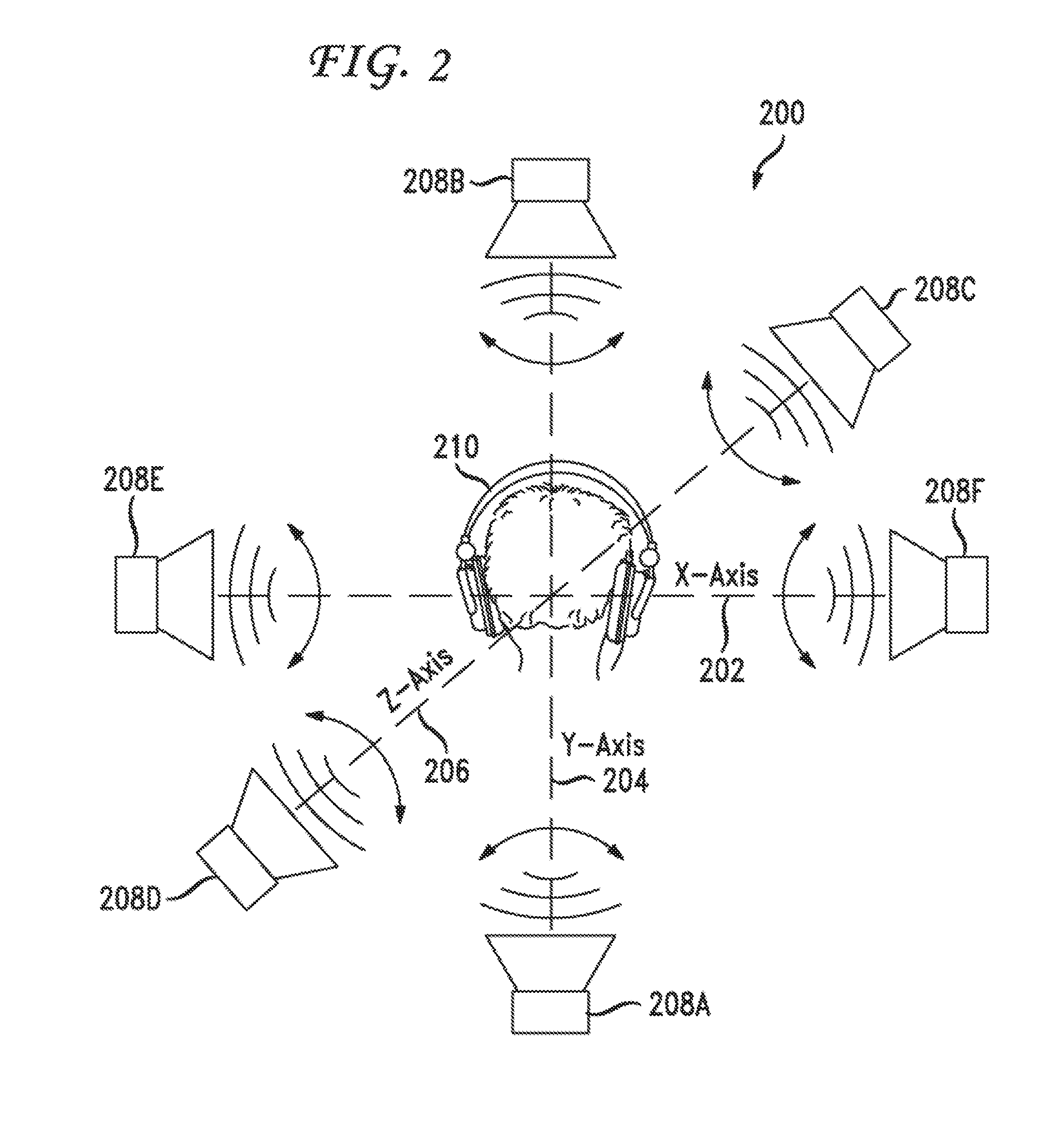
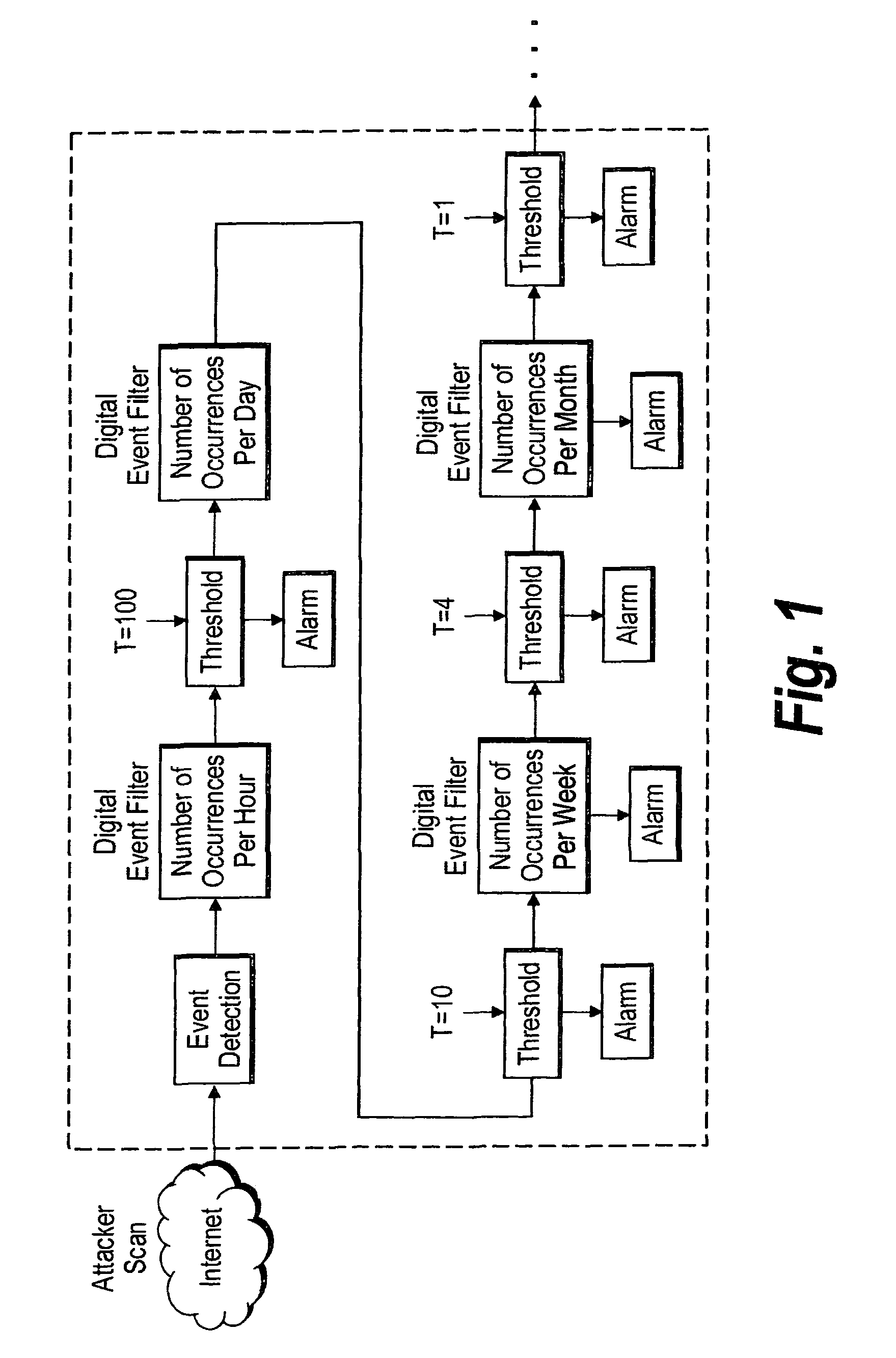
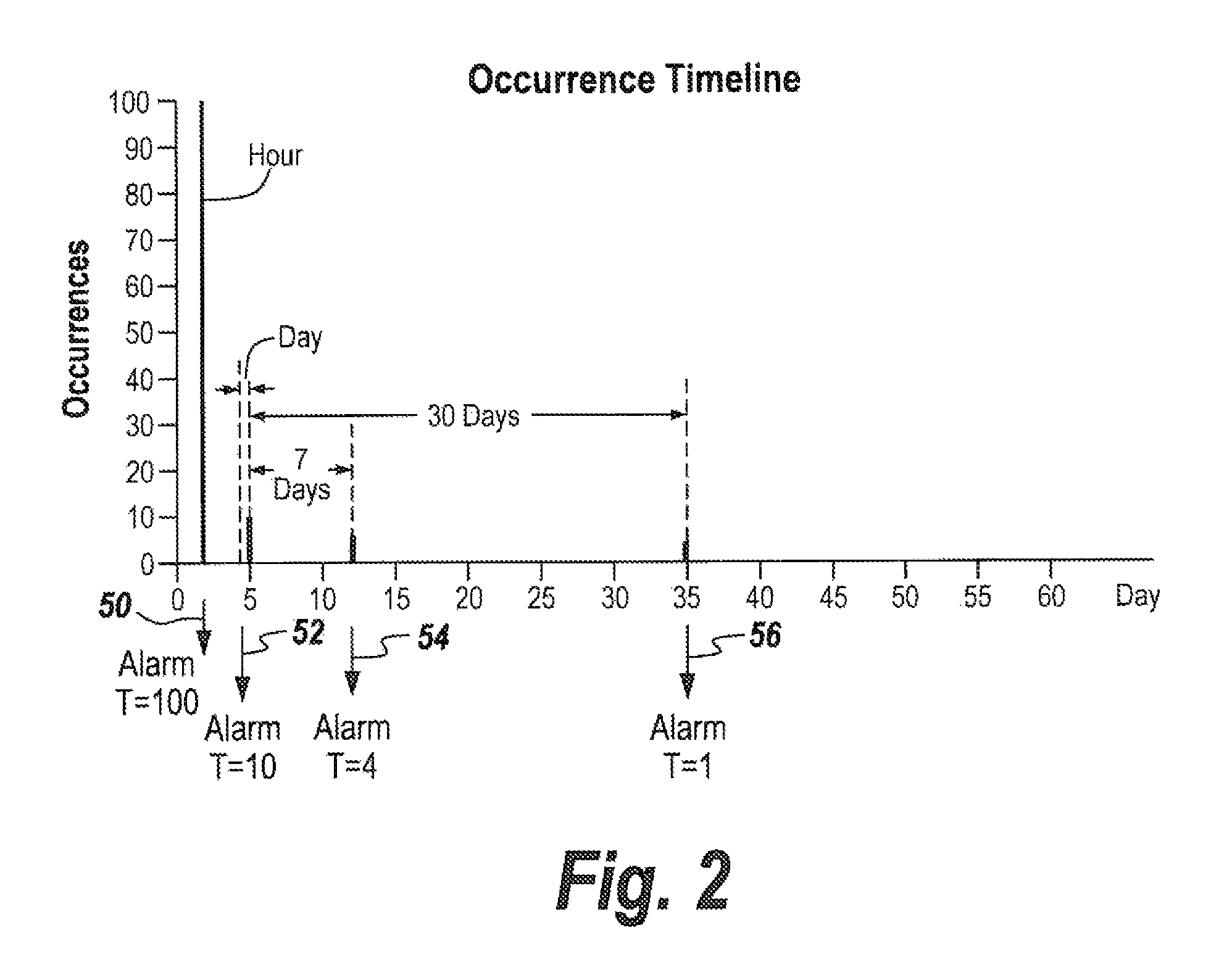
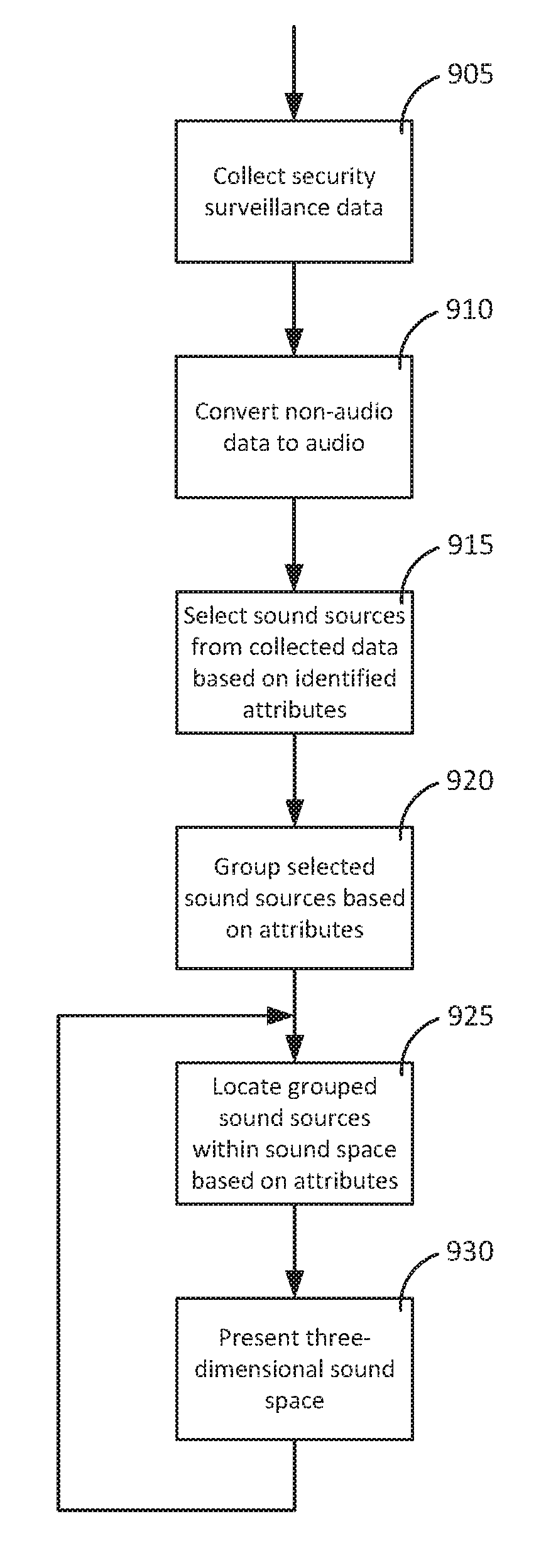
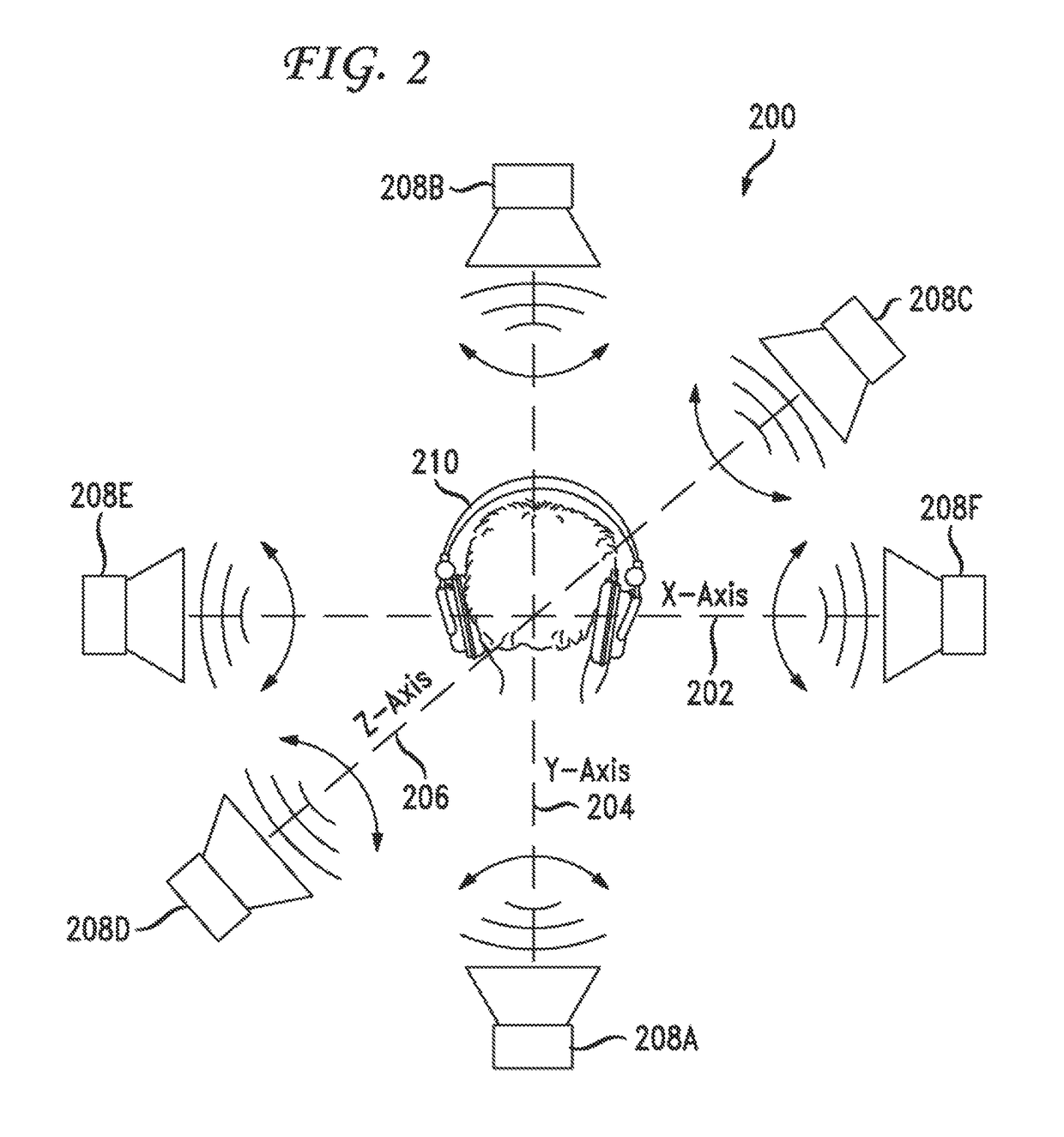
Security surveillance via three-dimensional audio space presentation
ActiveUS20170040028A1Augment and simplify sound spaceEfficiently navigatePublic address systemsSpeech recognitionSound sourcesThree-dimensional space
Owner:AVAYA INC
Systems and methods of responding to cyber security threats
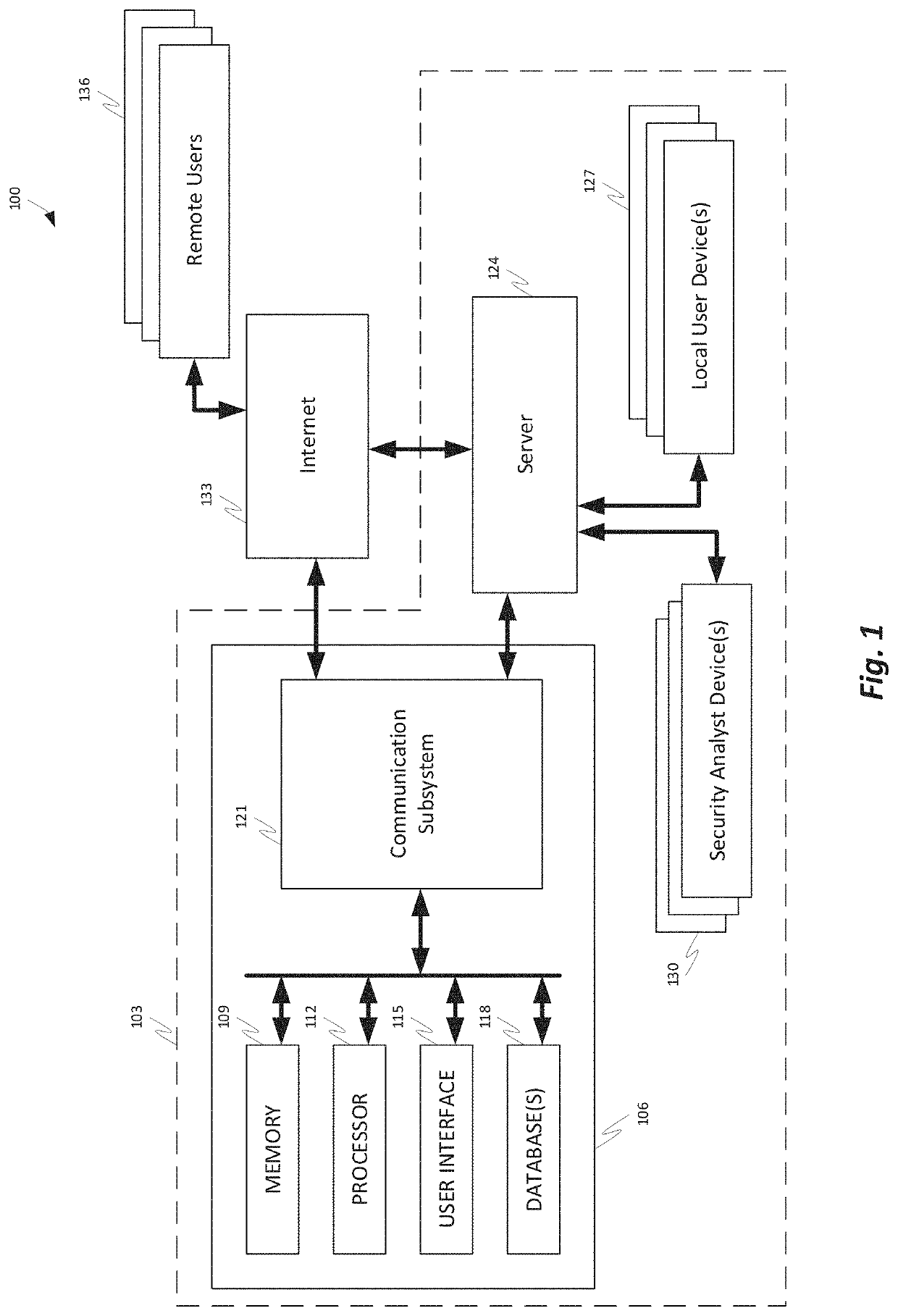
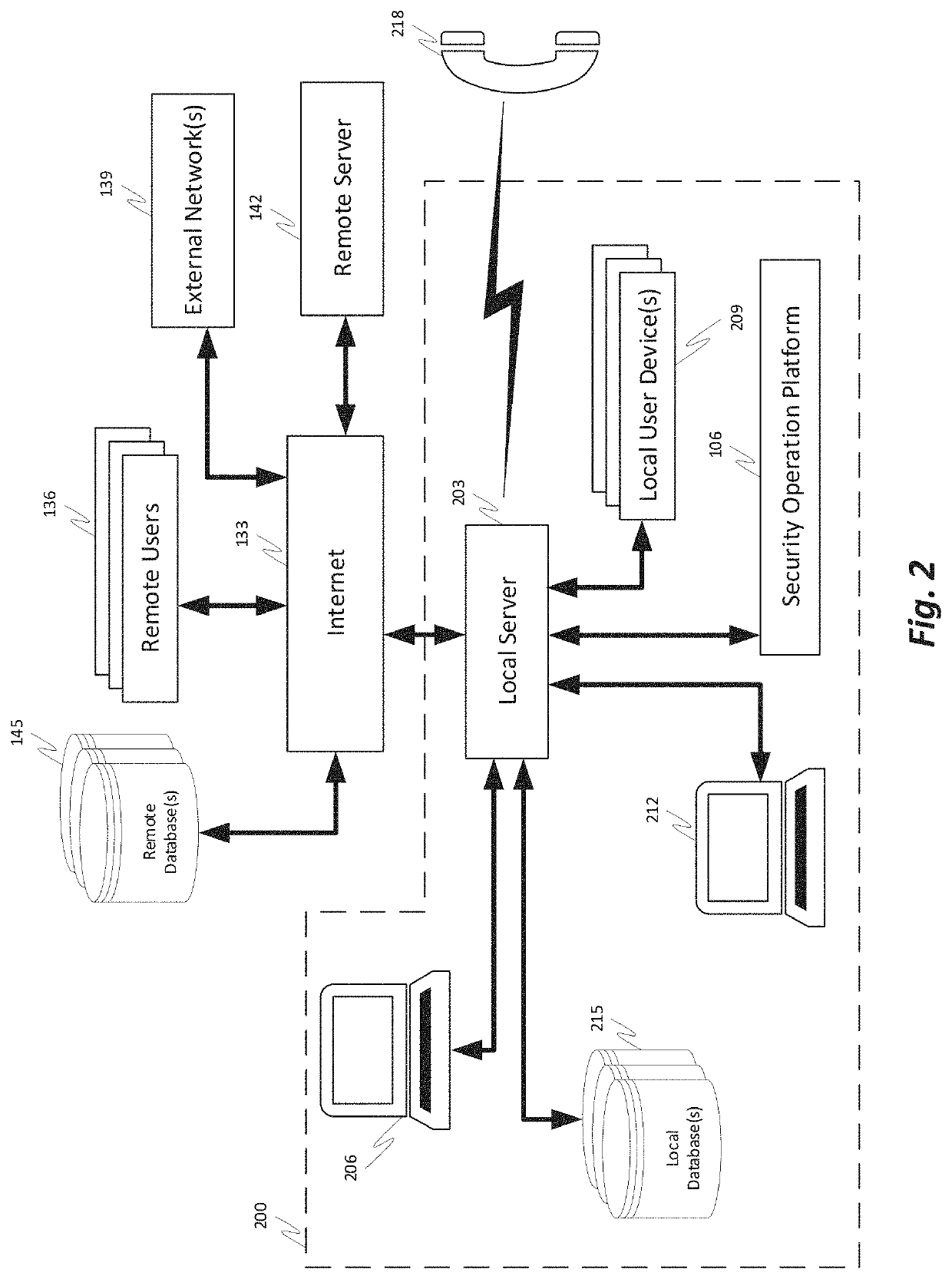
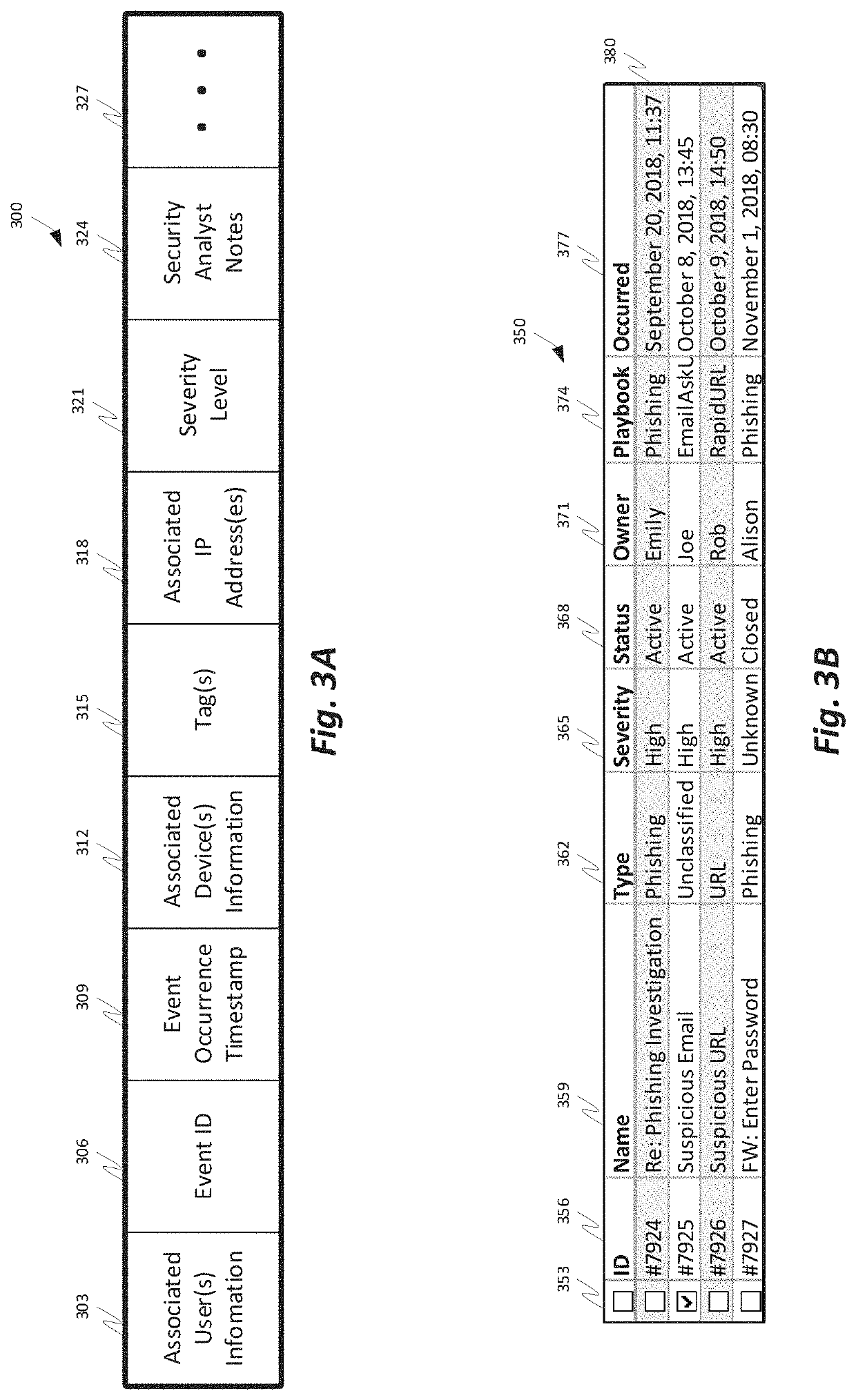
A comprehensive security operation platform with artificial intelligence capabilities which may collaborate and / or automate tasks, including complex and / or redundant security tasks. An automated system may assist security analysts and security operations center managers in discovering security incidents. A comprehensive security operations platform may combine intelligent automation scale and collaborative human social learning, wisdom and experience. An automated system may empower security analysts to resolve incidents faster and reduce redundancy through collaboration with peers in virtual war rooms. An automated system may automate security analyst work by executing tasks from the war room or by following playbooks defined by the security analysts.
Owner:PALO ALTO NETWORKS INC
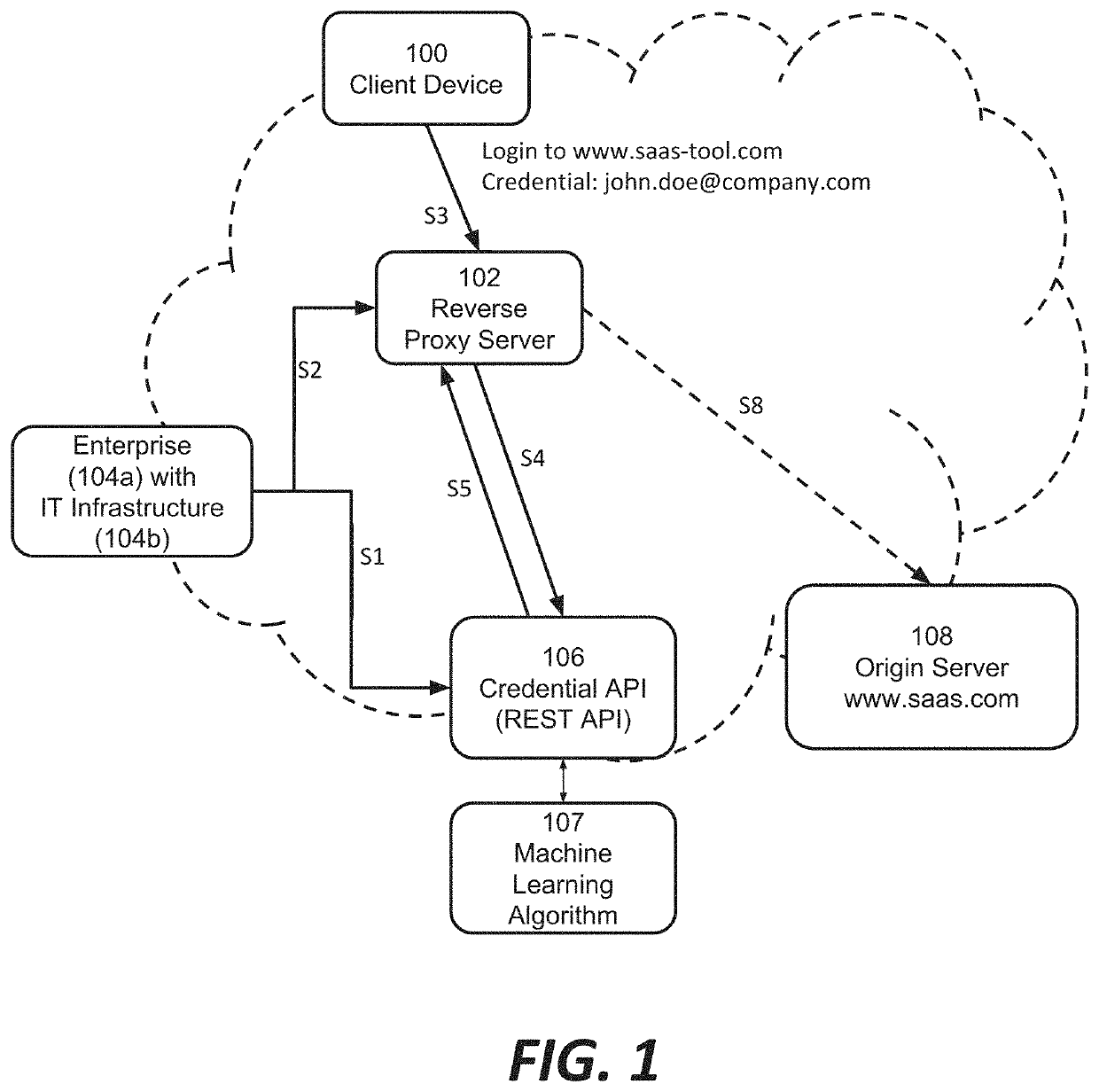
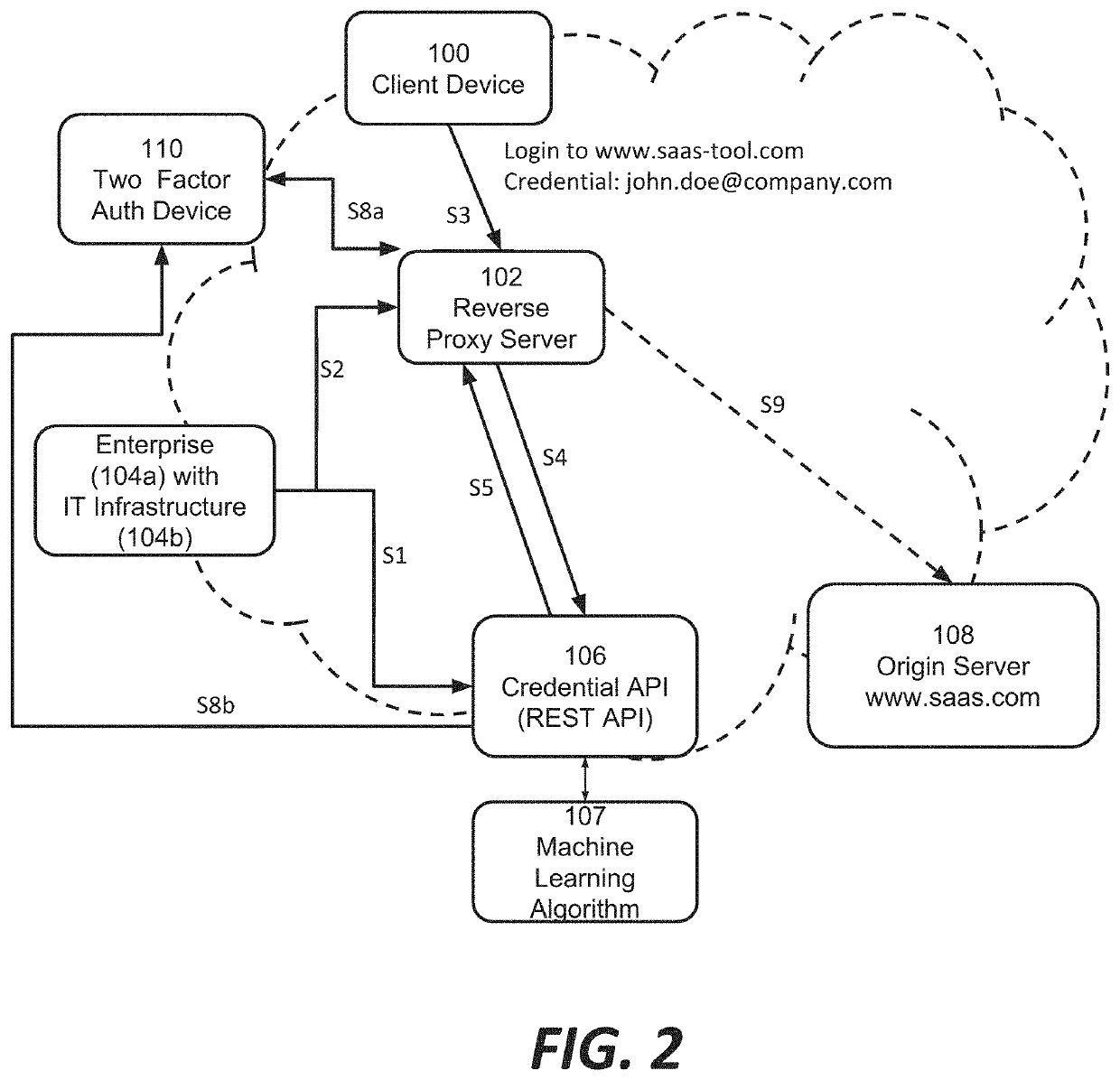
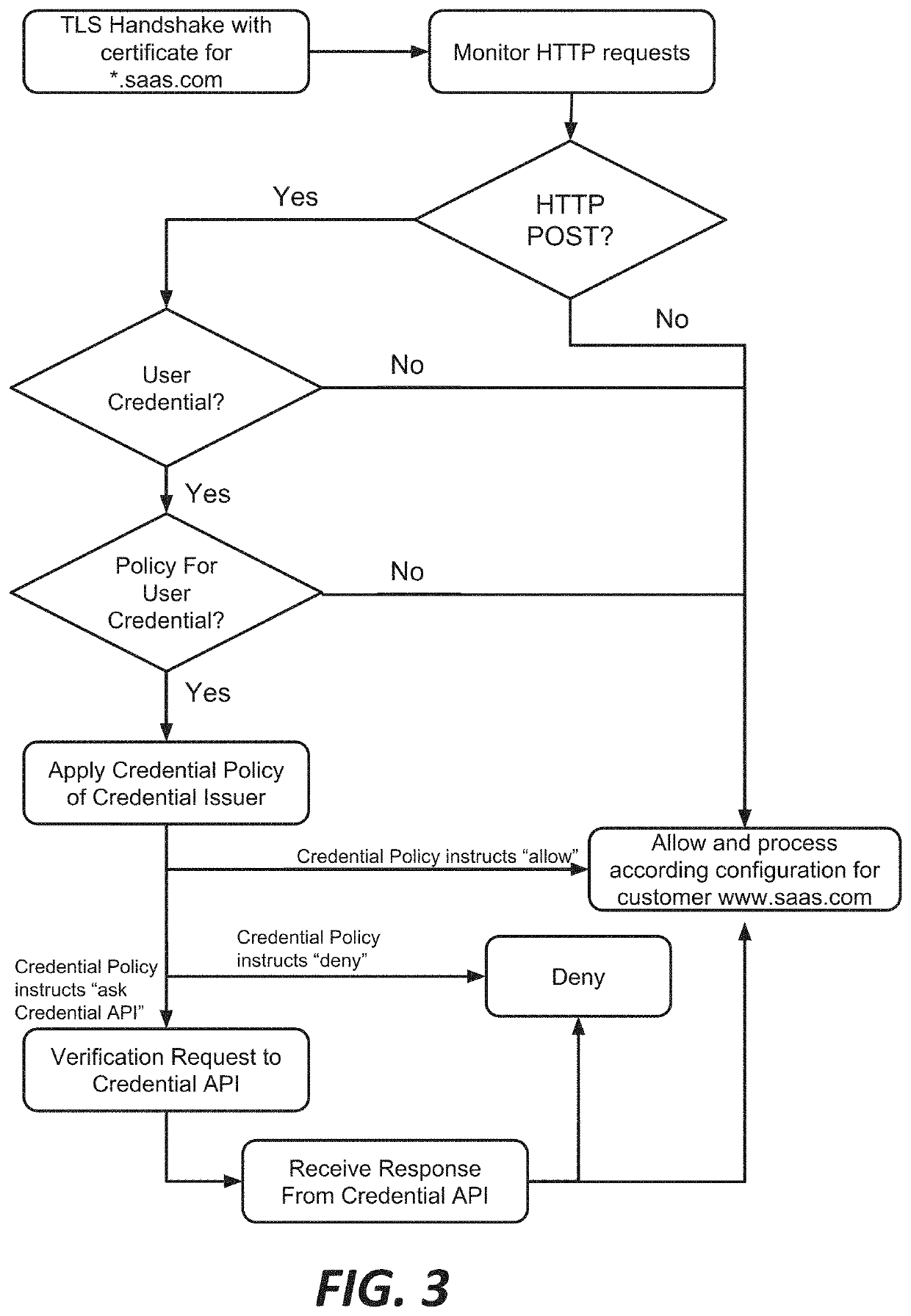
Systems and methods for internet-wide monitoring and protection of user credentials
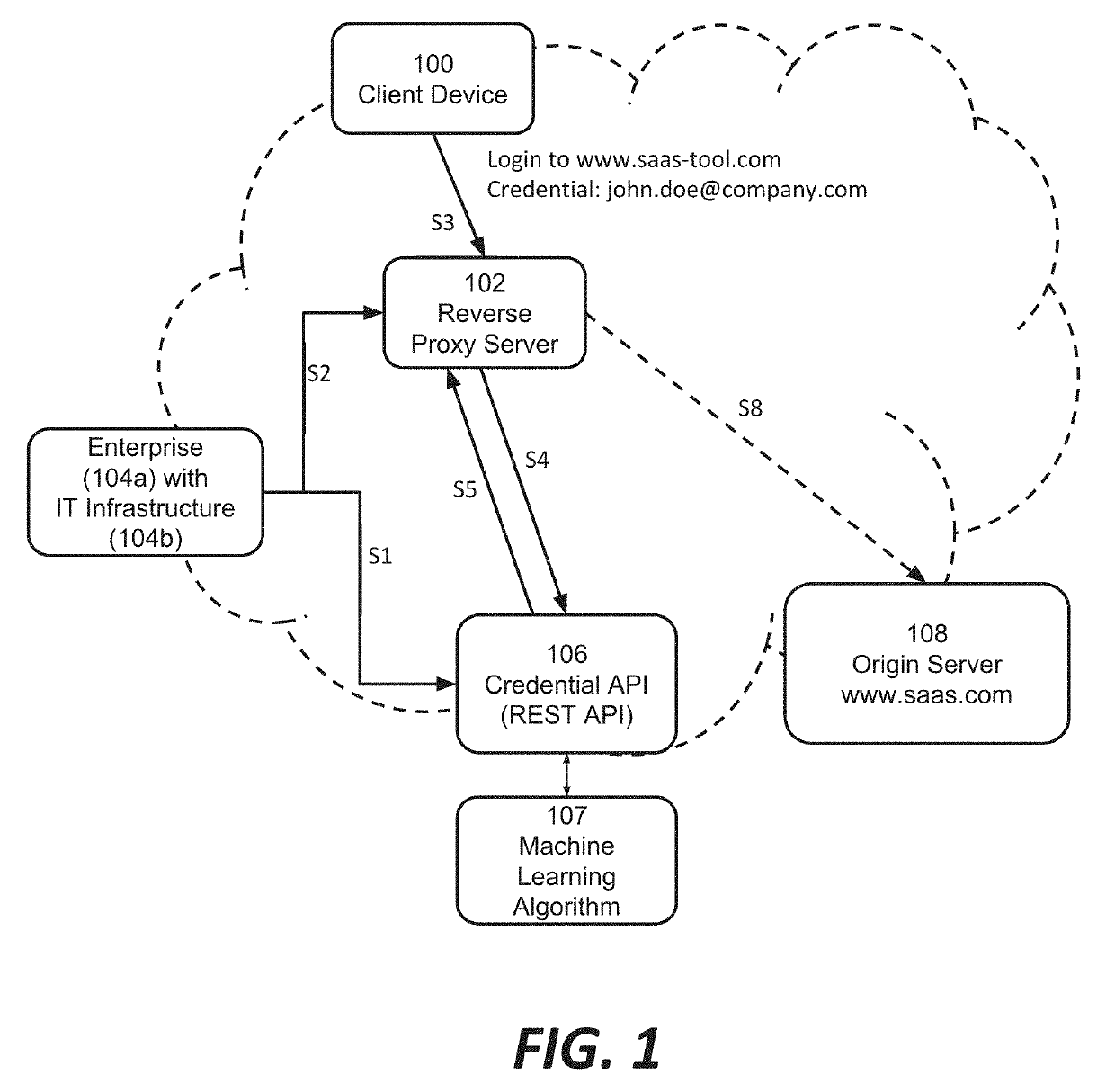
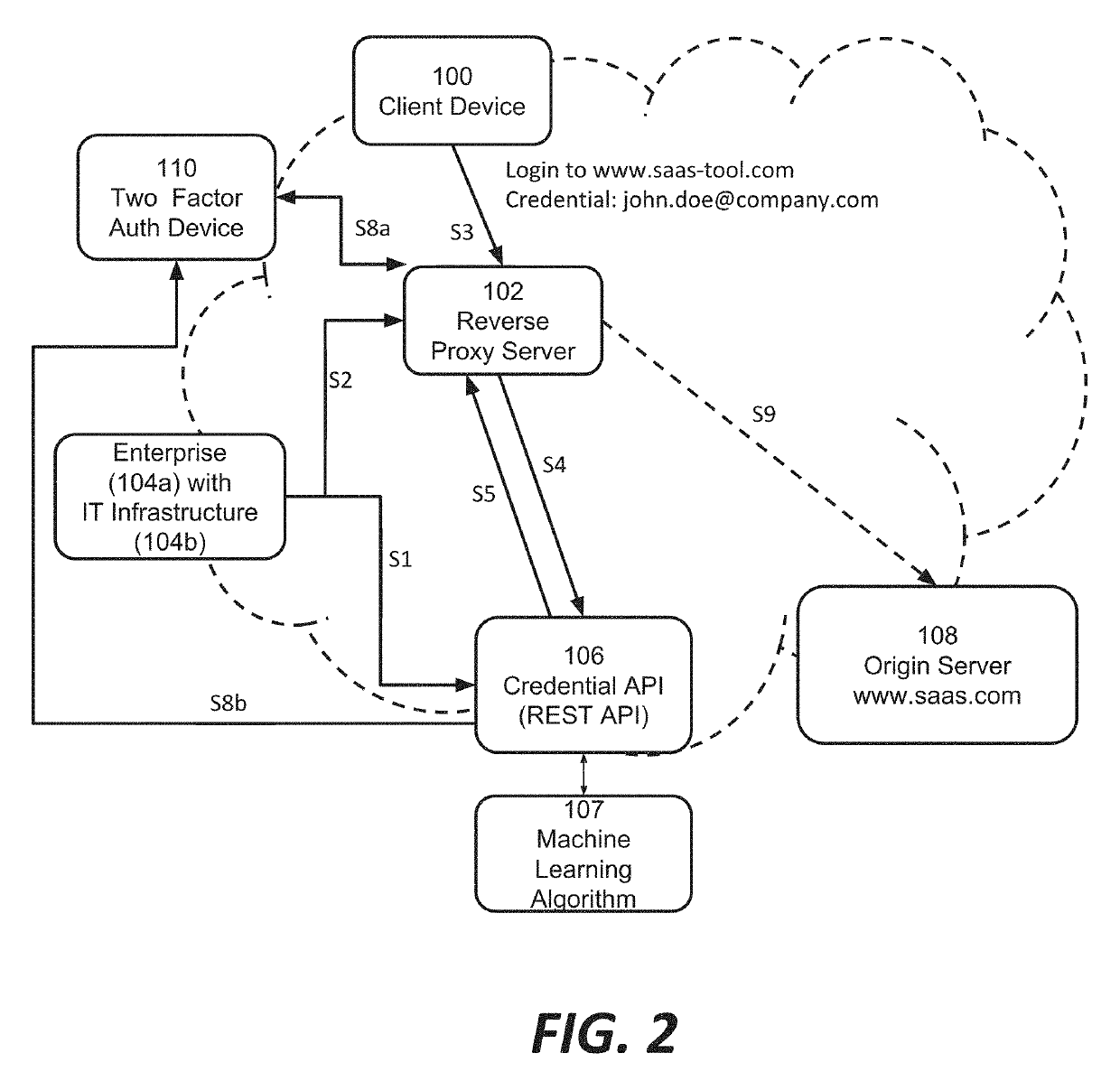
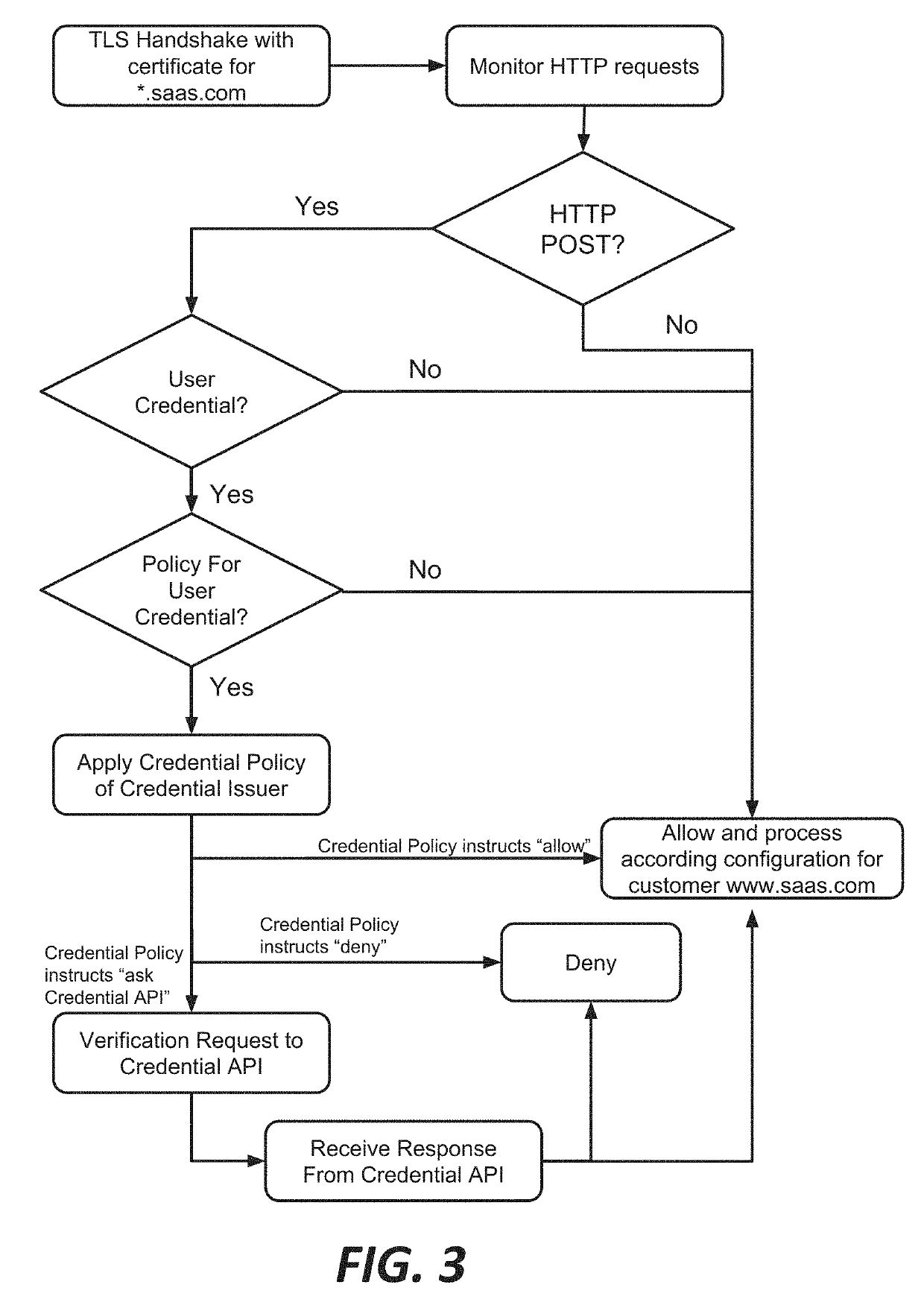
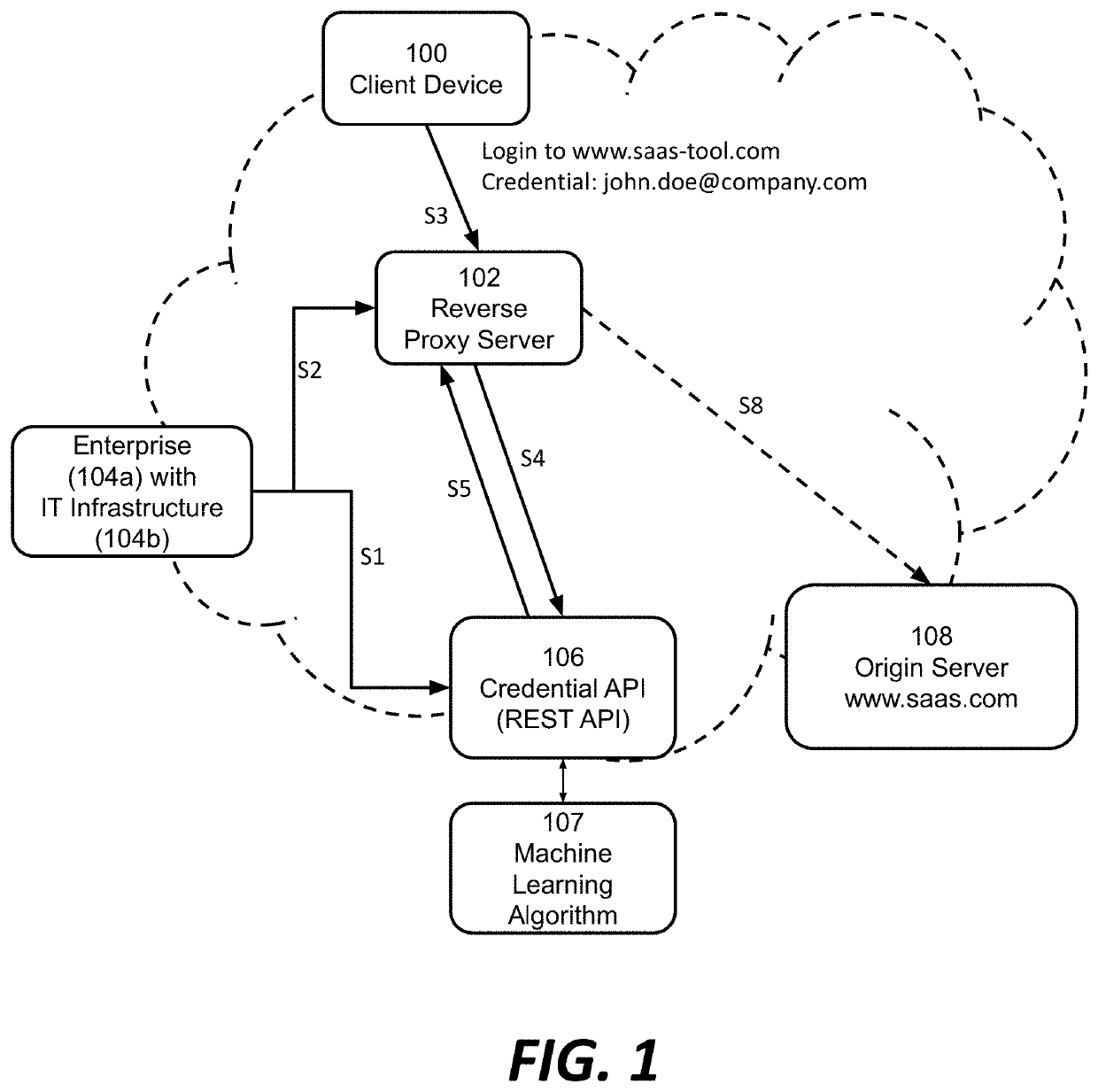
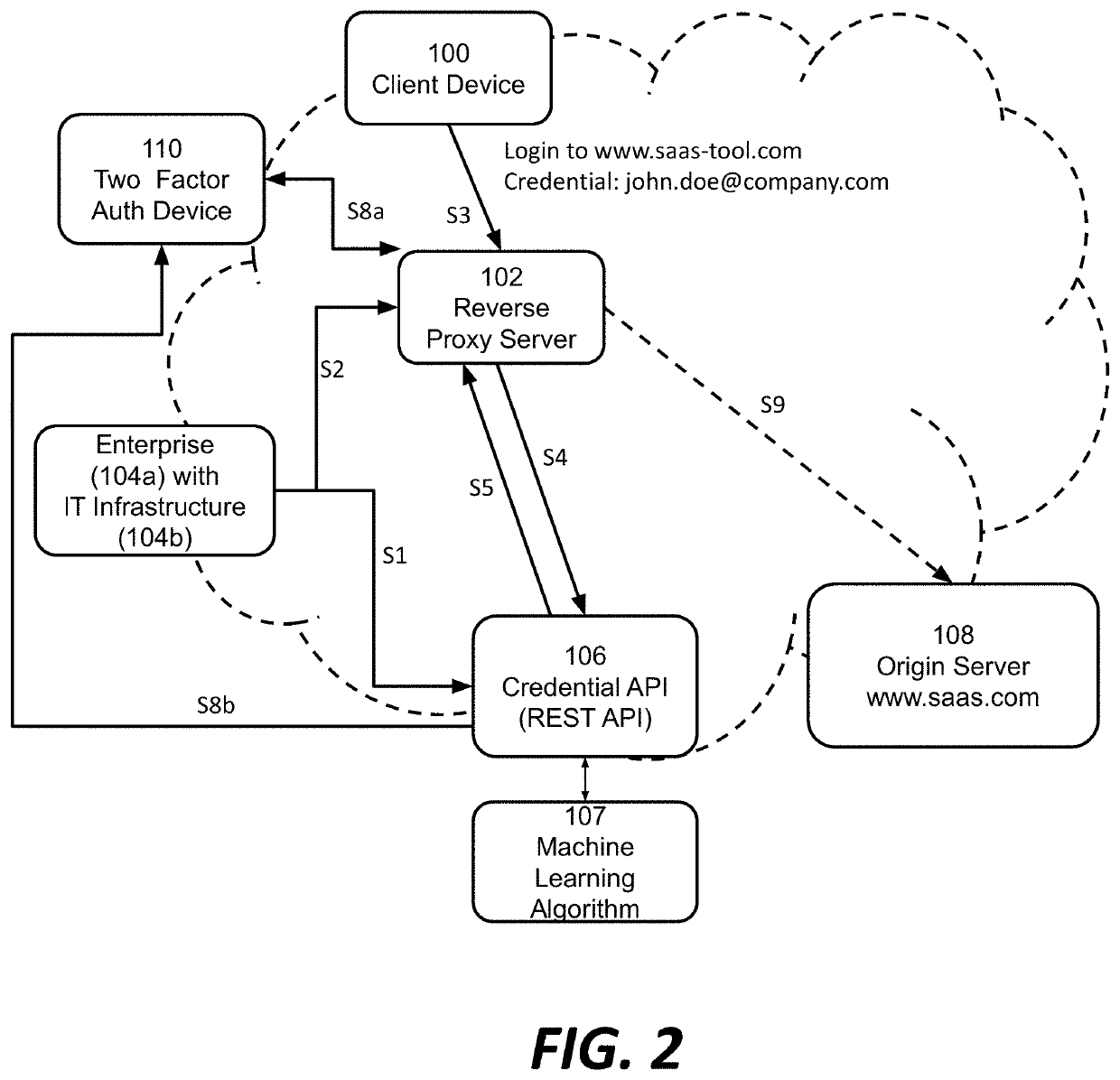
ActiveUS20190297079A1Enhances security analysts' tactical comprehensionComputer security arrangementsTransmissionReverse proxyThe Internet
Among other things, this document describes systems, methods, and apparatus for monitoring and protecting a user credential issued by an organization when that credential is used outside that organization's network security perimeter. For example, a reverse proxy server (RPS) receives a client request directed to a content provider's site. The RPS initiates a process that involves parsing the request message and extracting a user credential. The RPS locates a credential policy from the credential owner based on the user credential. The RPS can issue an API request to a credential service that is authoritative for the credential. That credential service may return a directive to the RPS specifying how to handle the client request message. Preferably, the operation is transparent to the content provider whose site was the target of the client's request message. Activity records can be presented in visualizations that enhance security analysts' tactical comprehension at a glance.
Owner:AKAMAI TECH INC
Method and system for evaluating the investment ratings of a securities analyst
Systems and methods for measuring the performance of calls on securities by a securities analyst during an evaluation period are disclosed. According to various embodiments, the system may include a performance evaluation module. The performance evaluation module is for determining a value (called the “hit ratio”) indicative of the success of the calls by the analyst for securities within a benchmark group of securities within an industry covered by the analyst relative to a benchmark return for the benchmark group for the corresponding call periods of the calls. The hit ratio may be computed as the ratio of the sum of the actual excess returns to the sum of the total available excess returns for each call by the analyst over the call evaluation period. The contributions to the hit ratio by each call may be equally weighted or weighted according to market capitalization of the rated security.
Owner:MORGAN STANLEY
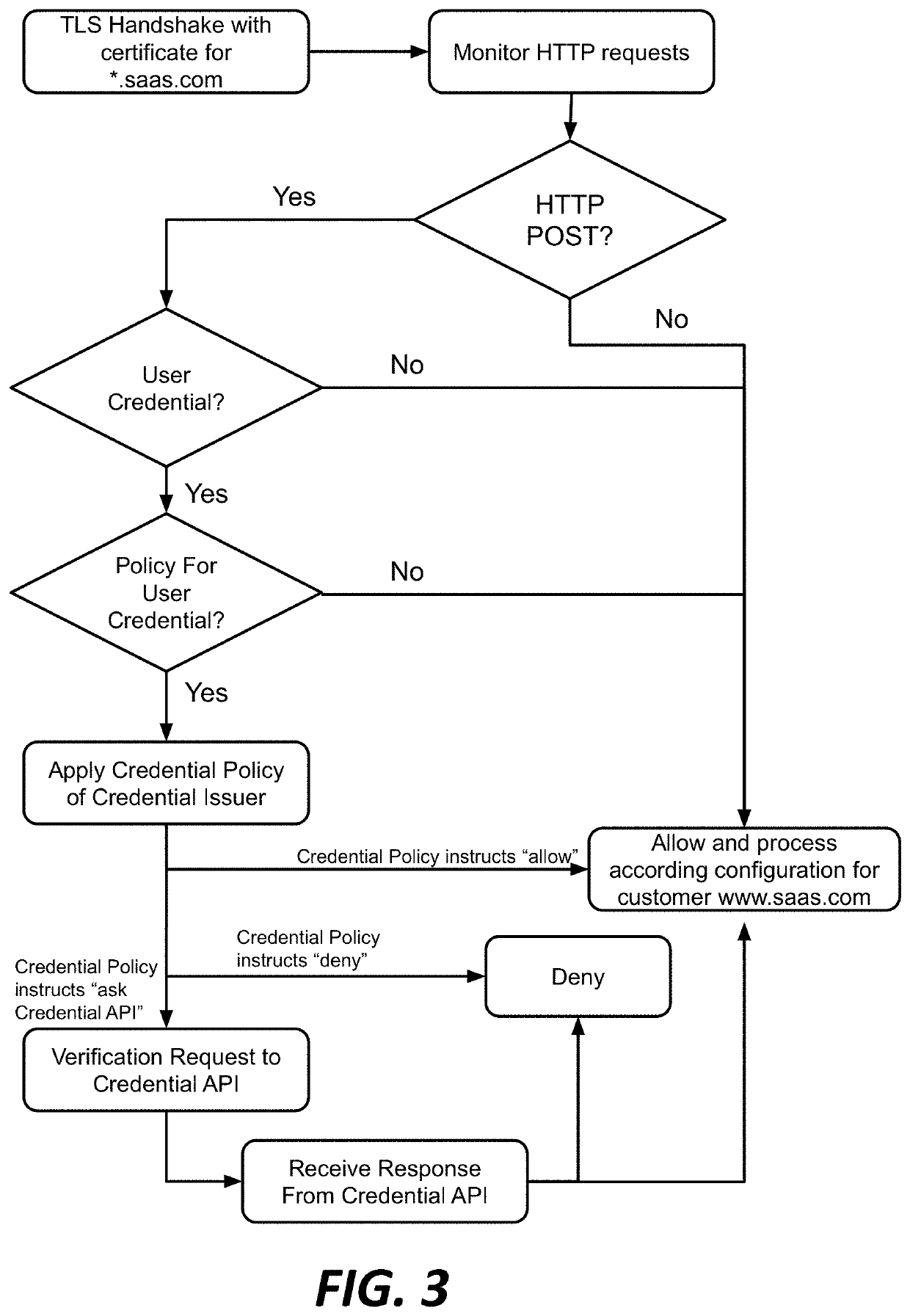
Auto-detection of web-based application characteristics for reverse proxy enablement
ActiveUS20160080324A1Eliminate needTransmissionSpecial data processing applicationsReverse proxyEvent data
This disclosure describes an automated process of discovering characteristics needed to integrate a web-based application to a web portal, such as a reverse proxy. This process eliminates the need for application owners and security analysts to manually discover the information needed for the on-boarding process. To this end, application-specific information is determined by monitoring network traffic flows in and out of the application, user authentication and authorization event data, and the like. An application discovery engine analyzes the discovered data, preferably against a set of patterns and heuristic-based rules, to discover or identify the one or more application characteristics. A set of configuration data is then generated, and this configuration data is then used to integrate the application into the web reverse proxy and, in particular, by specifying the configuration needed to “board” the application. Preferably, the monitoring and application characterization determination functions occur in an automated manner.
Owner:IBM CORP
System, method and computer readable medium containing instructions for evaluating and disseminating securities analyst performance information
An analyst's performance is evaluated by utilizing information pertaining to at least one revision issued by the analyst involving at least one investment. This evaluation includes determining a conditional performance score indicative of the analyst's performance relative to other investors. The performance score is determined at least in part by considering an average historical performance of the investment, following the revision. In addition, the performance score is also determined using a historical consistency of the analyst's performances with respect to revisions involving the investment, and a number of revisions made by the analyst. Then, the performance score may be adjusted according to one or more adjustments, including adjustments for accentuating a number of issued revisions and a return amount, to generate a final performance score.
Owner:REFINITIV US ORG LLC
Systems and methods for internet-wide monitoring and protection of user credentials
ActiveUS10958649B2Enhances security analysts' tactical comprehensionComputer security arrangementsTransmissionReverse proxyInternet privacy
Among other things, this document describes systems, methods, and apparatus for monitoring and protecting a user credential issued by an organization when that credential is used outside that organization's network security perimeter. For example, a reverse proxy server (RPS) receives a client request directed to a content provider's site. The RPS initiates a process that involves parsing the request message and extracting a user credential. The RPS locates a credential policy from the credential owner based on the user credential. The RPS can issue an API request to a credential service that is authoritative for the credential. That credential service may return a directive to the RPS specifying how to handle the client request message. Preferably, the operation is transparent to the content provider whose site was the target of the client's request message. Activity records can be presented in visualizations that enhance security analysts' tactical comprehension at a glance.
Owner:AKAMAI TECH INC
Enterprise security operation center (SOC) Bot
InactiveCN106850293AAccurate identificationImprove detection efficiencyData switching networksSecurity operations centerEnterprise networking
The invention discloses a security operation center (SOC) Bot for assisting an SOC analyst in detecting, surveying and recovering various events in enterprise network security. The SOC Bot comprises the parts of data collection, data identification, data processing, data integration, machine learning, marking and alarming, command execution and the like, and the parts cooperate to finish the functions of enterprise security clue collection, security event monitoring and marking, security threat alarming, and security protection and recovery, provide analysis clues for the SOC security analyst, and execute tasks issued by the security analyst. Through the Bot, the labor intensity of the analyst can be relieved greatly, and the efficiency and automation and intelligence levels of enterprise security detection and maintenance work are increased and raised greatly.
Owner:浙江航芯智控科技有限公司
Systems and methods of network-based intelligent cyber-security
A comprehensive security operation platform with artificial intelligence capabilities which may collaborate and / or automate tasks, including complex and / or redundant security tasks. An automated system may assist security analysts and security operations center managers in discovering security incidents. A comprehensive security operations platform may combine intelligent automation scale and collaborative human social learning, wisdom and experience. An automated system may empower security analysts to resolve incidents faster and reduce redundancy through collaboration with peers in virtual war rooms. An automated system may automate security analyst work by executing tasks from the war room or by following playbooks defined by the security analysts.
Owner:PALO ALTO NETWORKS INC
Method and apparatus for detecting SSH login attacks
ActiveUS8776226B2Remove noise causedWork lessMemory loss protectionError detection/correctionDigital filterSecurity analyst
A digital filter correlation engine, wherein the correlation engine combines N arbitrary digital filter states based on the weights and along with a threshold generate a network incident. This network incident in turn can be feedback to another digital filter. This multi-layering capability allows the creation of higher level event detections that are time-based for a cyber security analyst to analyze, thereby reducing the amount of manual work the analyst has to do in inspecting behaviors within the network.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTERGRATION INC
Security surveillance via three-dimensional audio space presentation
ActiveUS9892743B2Efficiently navigateEfficient identificationPublic address systemsSpeech recognitionSound sourcesThree-dimensional space
Embodiments are directed to using a three-dimensional sound space to analyze security surveillance information. According to one embodiment, the three-dimensional sound space can comprise part of a security surveillance system in which sound sources related to security surveillance information can be presented and a user can efficiently navigate even a large number of sound sources in the three-dimensional sound space. Effective audio surveillance relies on the ability of the surveillance personnel to efficiently identify calls that need further analysis and calls that need no further analysis without introducing too many false negative or false positive conditions. Utilization of three-dimensional space described herein can increase the ease with which security analysts review audio content and identify relevant audio content that requires further analysis.
Owner:AVAYA INC
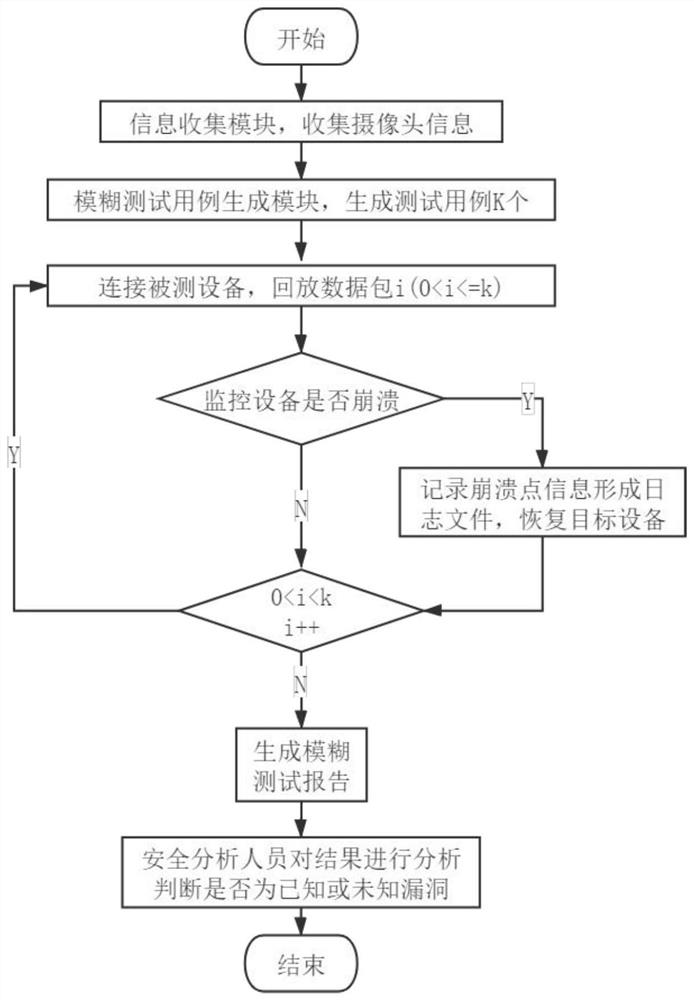
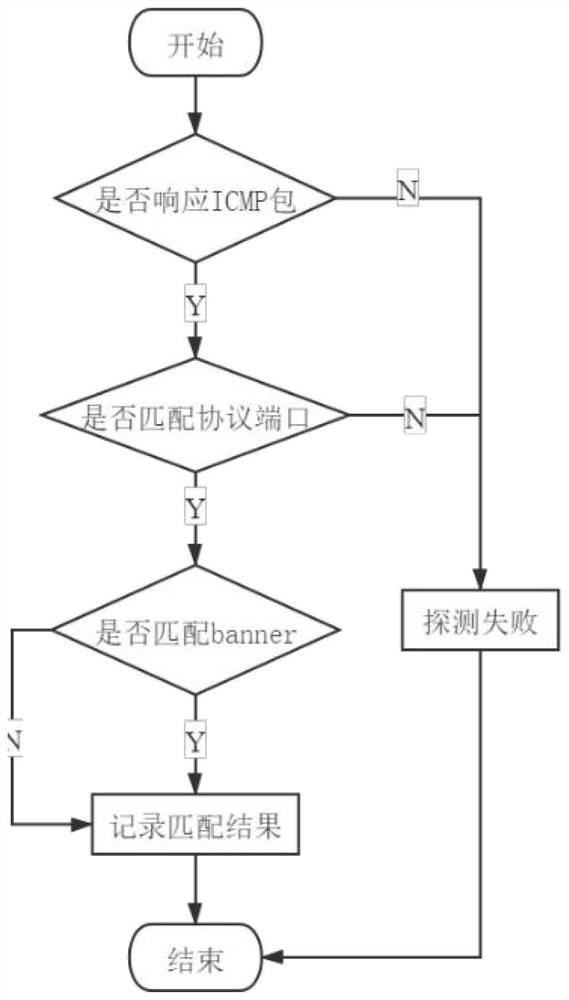
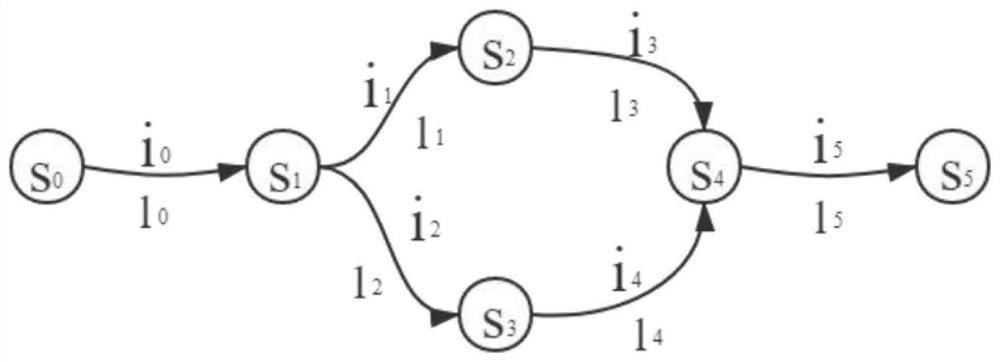
Camera network protocol fuzzy test method based on FSM
InactiveCN112235161AOvercome more loopholesOvercome methodData switching networksNetworking protocolOriginal data
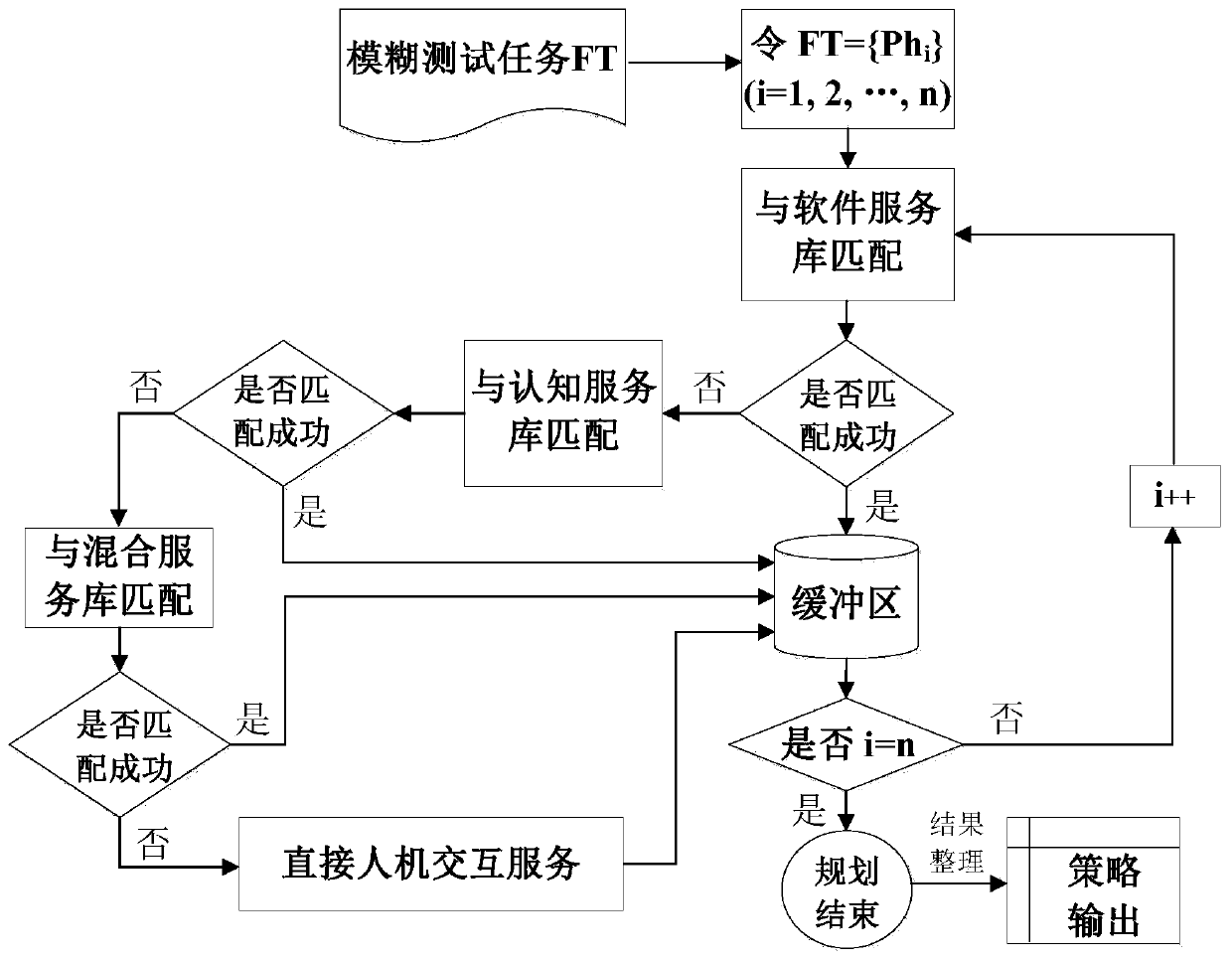
The invention belongs to the technical field of network protocol vulnerability mining, and particularly relates to a camera network protocol fuzzy test method based on an FSM. According to the invention, the problems of more network protocol vulnerabilities and immature fuzzy test method of the current camera are overcome, and the protocol vulnerabilities can be effectively detected. The originaldata can be automatically generated, and the state transition diagram is automatically generated according to the state transition form. According to the method, the pertinence is higher, vulnerability information of SIP and RTSP protocols can be provided, and security analysts are helped to complete subsequent work.
Owner:HARBIN ENG UNIV
Corroborating threat assertions by consolidating security and threat intelligence with kinetics data
A cognitive security analytics platform is enhanced by providing a computationally- and storage-efficient data mining technique to improve the confidence and support for one or more hypotheses presented to a security analyst. The approach herein enables the security analyst to more readily validate a hypothesis and thereby corroborate threat assertions to identify the true causes of a security offense or alert. The data mining technique is entirely automated but involves an efficient search strategy that significantly reduces the number of data queries to be made against a data store of historical data. To this end, the algorithm makes use of maliciousness information attached to each hypothesis, and it uses a confidence schema to sequentially test indicators of a given hypothesis to generate a rank-ordered (by confidence) list of hypotheses to be presented for analysis and response by the security analyst.
Owner:INT BUSINESS MASCH CORP
Software vulnerability fuzzy test method based on man-machine cooperation
ActiveCN111367815AImprove fuzz testing performanceFlexible switchingSoftware testing/debuggingTest efficiencyTest sample
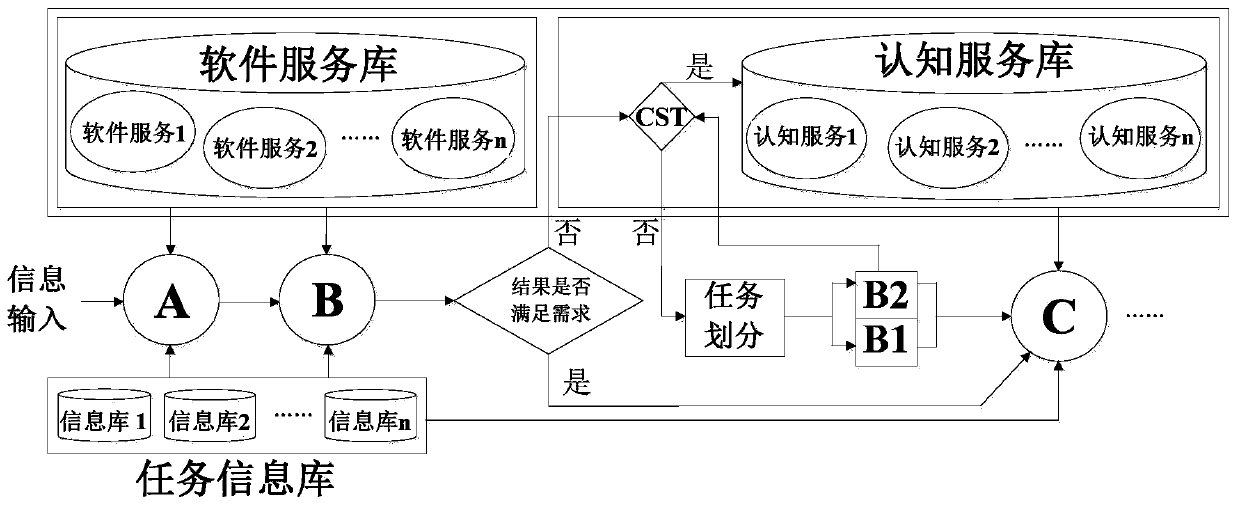
The invention relates to the technical field of software vulnerability fuzzy test, and discloses a software vulnerability fuzzy test method based on man-machine cooperation, which utilizes an automatic service matching and assembling technology to provide cognitive competence of software security analysts as cognitive service for a software vulnerability fuzzy test process. According to the method, the cognitive ability of a person participating in the software vulnerability fuzzy test is used as a component of the system, namely cognitive service, and is immersed into the whole software vulnerability fuzzy test task solution. According to the method, the software service and the cognitive service are fused into a unified framework to achieve man-machine cooperation, flexible switching between the software service and the cognitive service can be achieved, and the purpose of improving the software vulnerability fuzzy test efficiency can be achieved. According to the method, the experience of people is solidified as a service form in the test sample generation link, so that the problem that time is extremely wasted when test cases are artificially generated in the previous fuzzy test process is solved to a certain extent, and the efficiency of the whole fuzzy test is greatly improved.
Owner:CHINA ELECTRONICS TECH CYBER SECURITY CO LTD
Report generation information processing method and device for securities analyst system
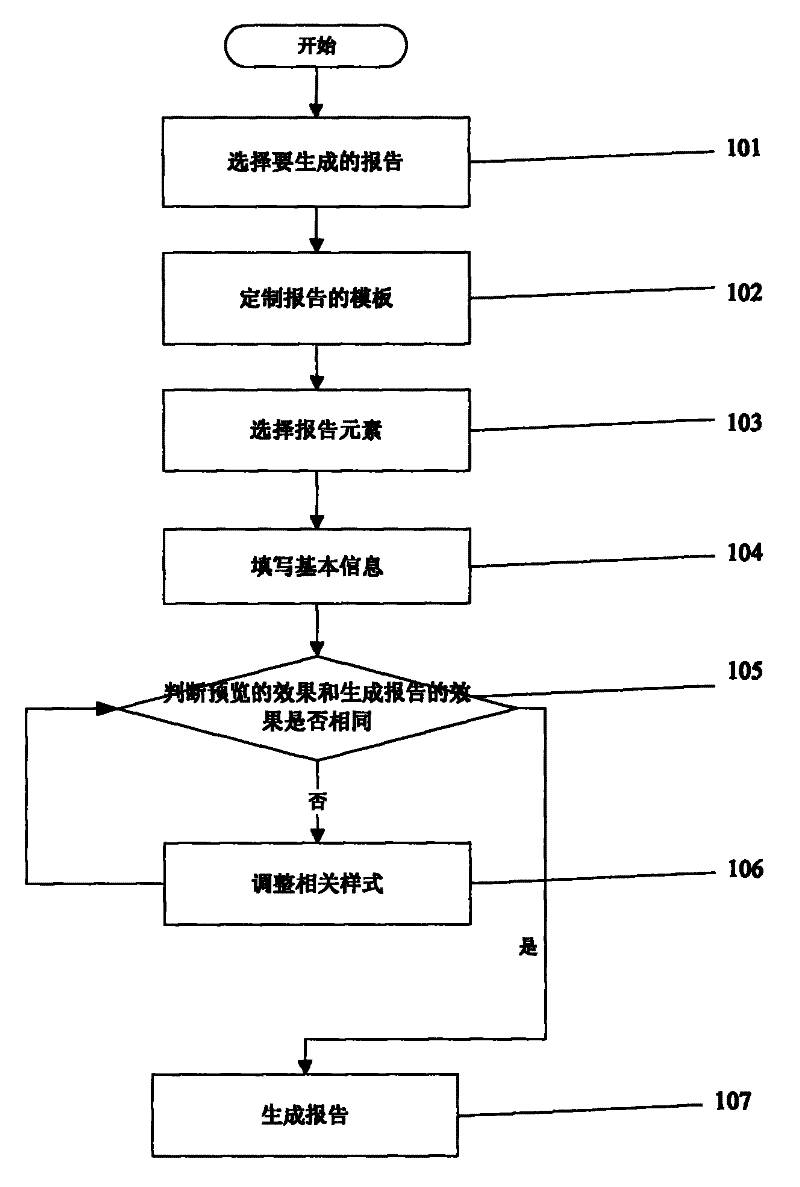
InactiveCN102411570AEasy to customizePromote generationSpecial data processing applicationsInformation processingLow complexity
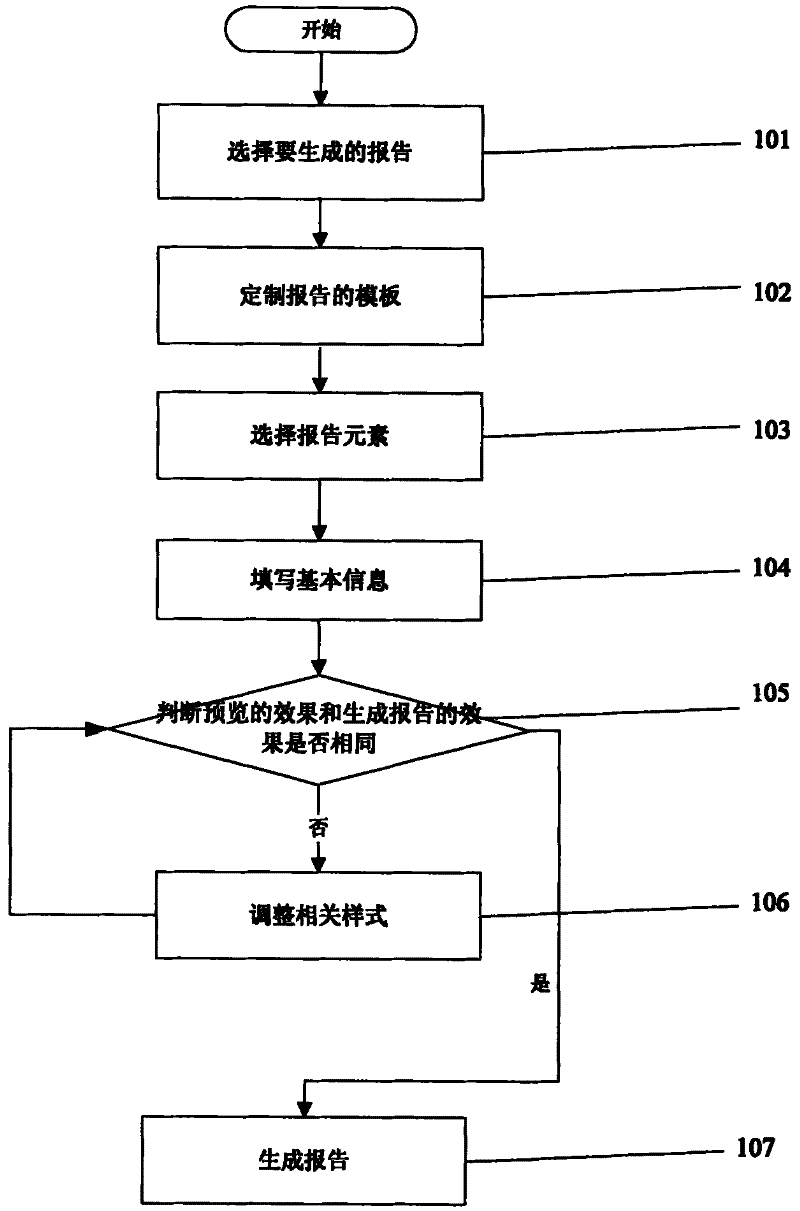
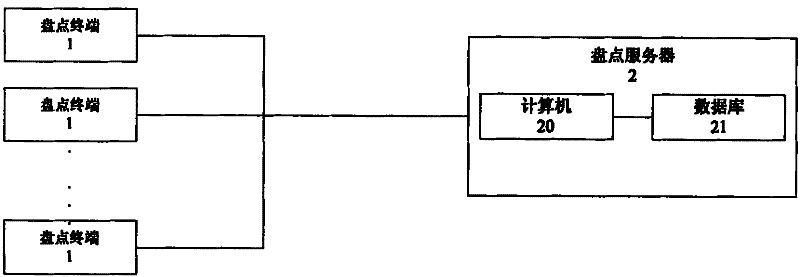
The invention relates to a report generation information processing method for a securities analyst system. The method comprises the following steps of: 1) selecting the type of a report to be generated according to the request information of an inventorying terminal by using an inventorying server; 2) entering a template customization page, and starting customizing a template by using the inventorying server; 3) selecting elements corresponding to columns of the template, and selecting the elements according to the template by using the inventorying server; 4) entering a basic information filling page, and importing the basic information of the report; 5) entering a previewing interface, judging whether previewed effects are the same as the effects of the generated report or not, executing a step 7) if the previewed effects are the same as the effects of the generated report, and executing a step 6) if the previewed effects are different from the effects of the generated report; 6) regulating a related pattern, and returning to the step 5); and 7) generating the report, storing the generated report in the data of the inventorying server, and simultaneously transmitting the generated report to the inventorying terminal. Compared with the prior art, the method has the advantages of low cost, low complexity and the like.
Owner:上海众融信息技术有限公司
Systems and methods for internet-wide monitoring and protection of user credentials
PendingUS20210400041A1Enhances security analysts' tactical comprehensionComputer security arrangementsTransmissionReverse proxyInternet privacy
Among other things, this document describes systems, methods, and apparatus for monitoring and protecting a user credential issued by an organization when that credential is used outside that organization's network security perimeter. For example, a reverse proxy server (RPS) receives a client request directed to a content provider's site. The RPS initiates a process that involves parsing the request message and extracting a user credential. The RPS locates a credential policy from the credential owner based on the user credential. The RPS can issue an API request to a credential service that is authoritative for the credential. That credential service may return a directive to the RPS specifying how to handle the client request message. Preferably, the operation is transparent to the content provider whose site was the target of the client's request message. Activity records can be presented in visualizations that enhance security analysts' tactical comprehension at a glance.
Owner:AKAMAI TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com