Enterprise security operation center (SOC) Bot
A safe and enterprise technology, applied in the field of network security, can solve problems such as missed attacks, and achieve the effect of reducing labor intensity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
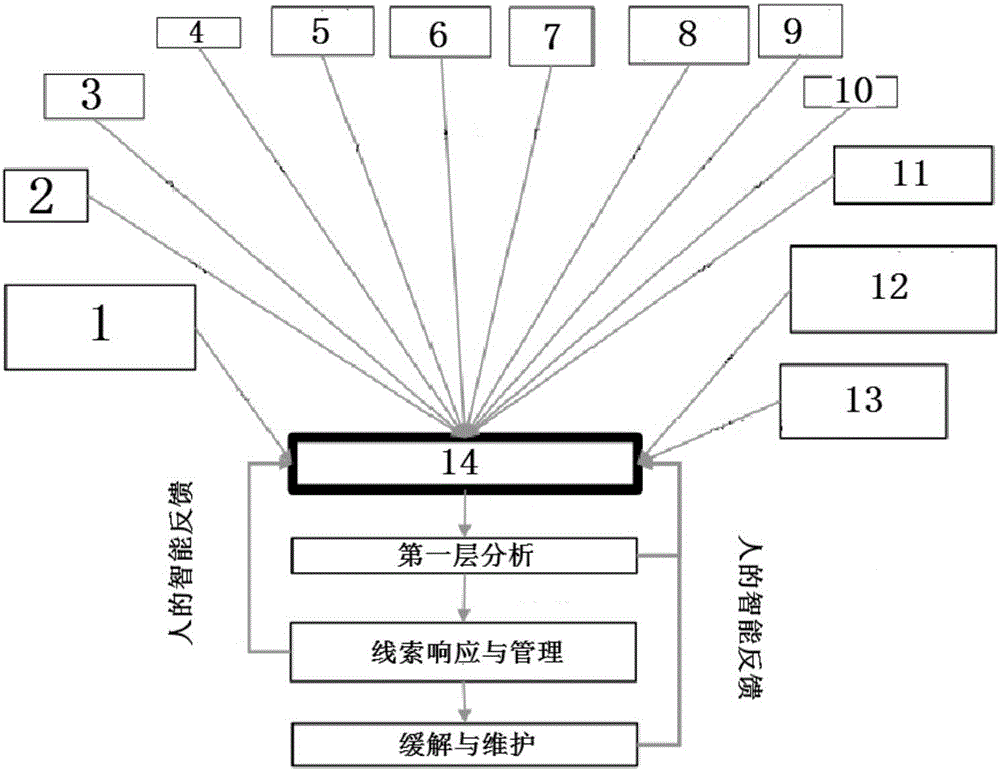
[0058] An enterprise security operation center Bot, including data collection, data identification, data processing, data integration, machine learning, marking and alarming, command execution, etc. Flagging, security threat alerts, and security protection and repair functions. Provide analysis clues for SOC security analysts and perform tasks assigned by security analysts.
[0059] The data collection section is capable of collecting various security event data from across the enterprise, and these data sources include the following:
[0060] · Preventive security technology data, such as AD logs, firewalls, IDS / IPS, DHCP, VPN, Windows event logs, DLP logs, endpoint protection logs, file sharing and synchronization logs, such as BOX or Dropbox, http traffic logs.
[0061] · Threat intelligence;
[0062] · Manual reports, emails, voicemails, text messages;
[0063] Physical security data, such as mark collection data at the entrance of the company or key places, such as fin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com