Camera network protocol fuzzy test method based on FSM
A fuzzy test and network protocol technology, applied in the direction of data exchange network, digital transmission system, electrical components, etc., to achieve highly targeted effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
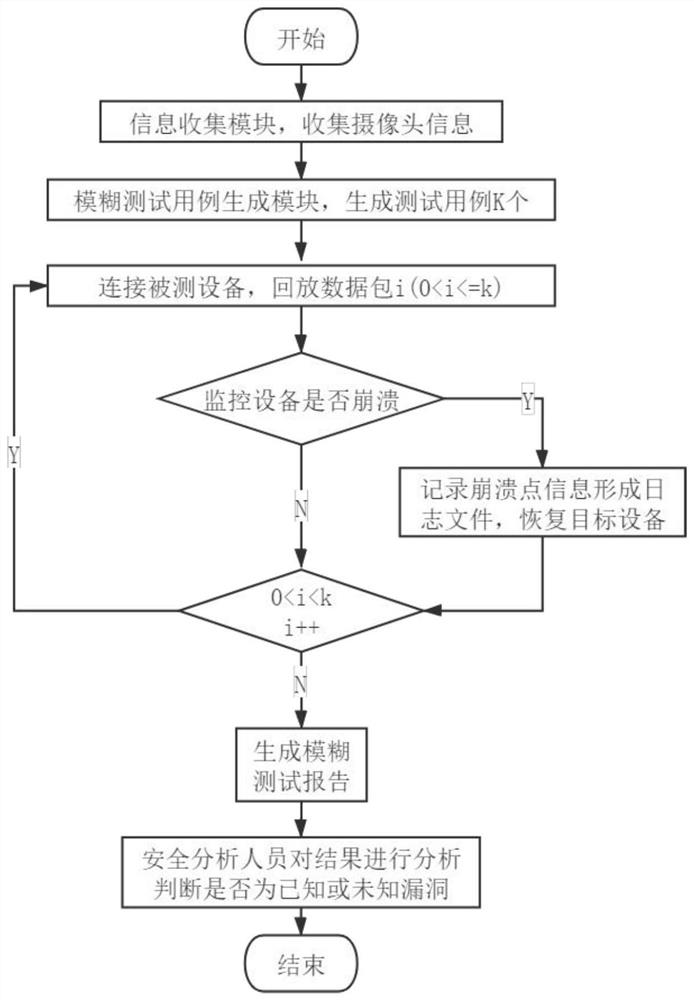
[0048] There are 4 steps in total, such as figure 1 Shown:
[0049] A. Collect camera information;
[0050] B. Use the mutation method to generate fuzzy test cases;
[0051] C. Test the device using fuzz test cases;
[0052] D. Generate a fuzz test report.
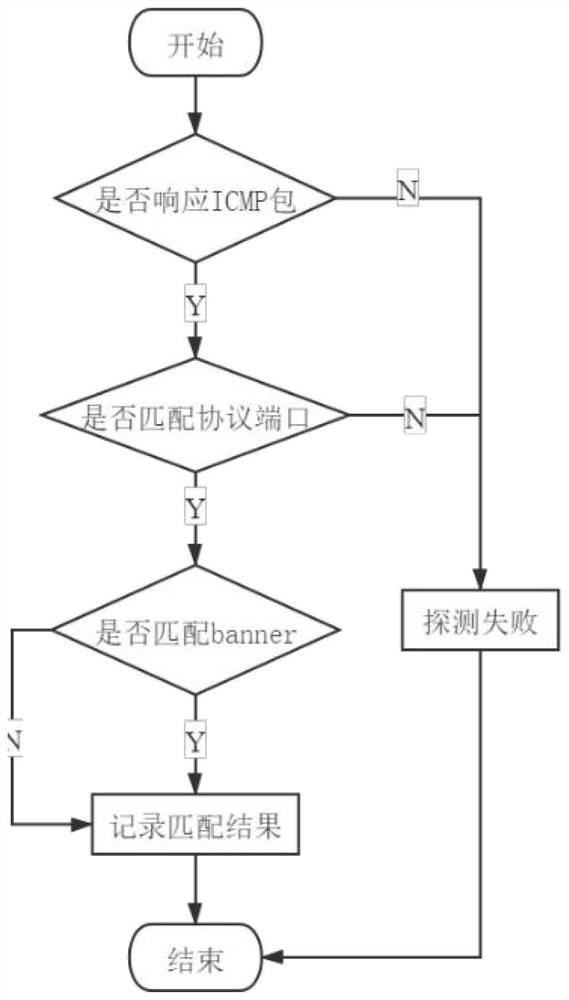
[0053] 1. The collection of camera information is completed by the fingerprint detection module, which will identify the logo of the general networked camera, the model specification of the network camera, and the HTTP protocol information of the camera. The detection process is as follows: figure 2 shown.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com