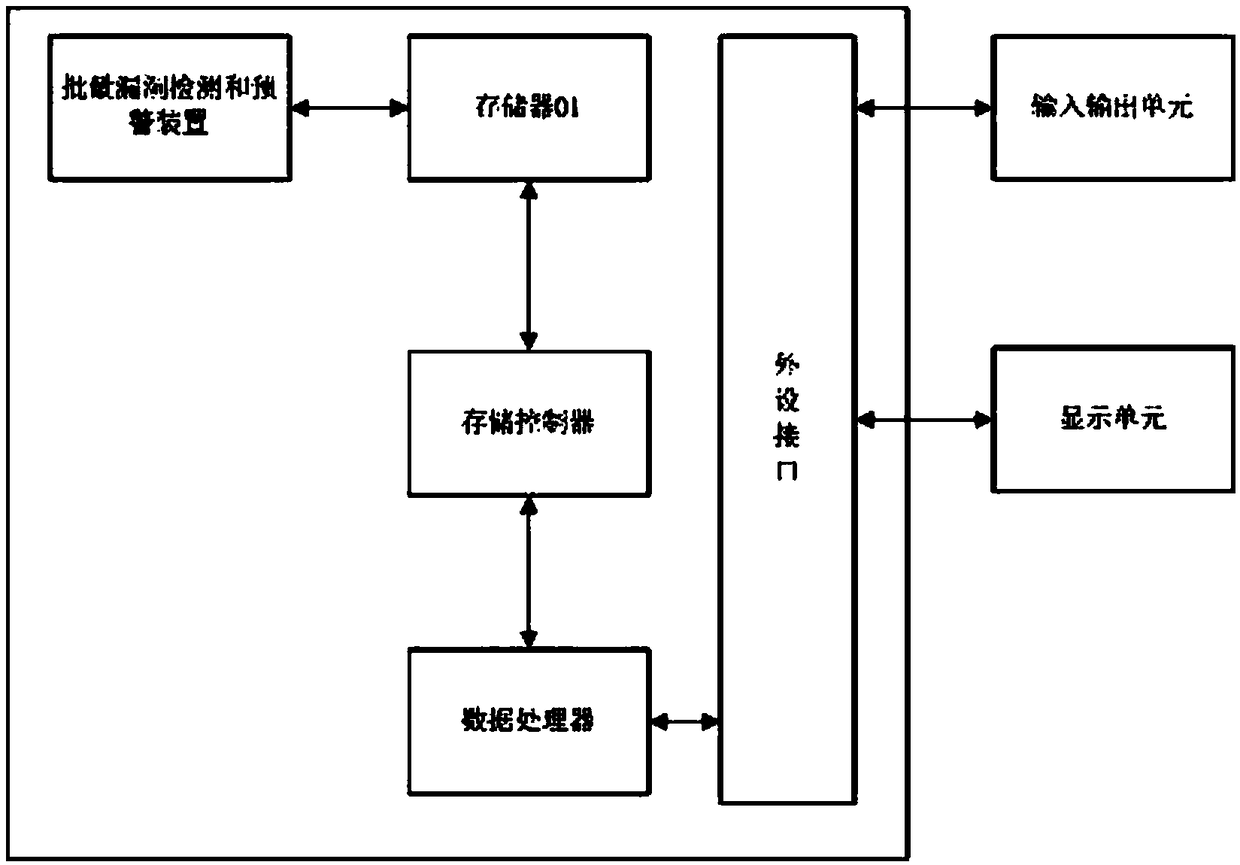
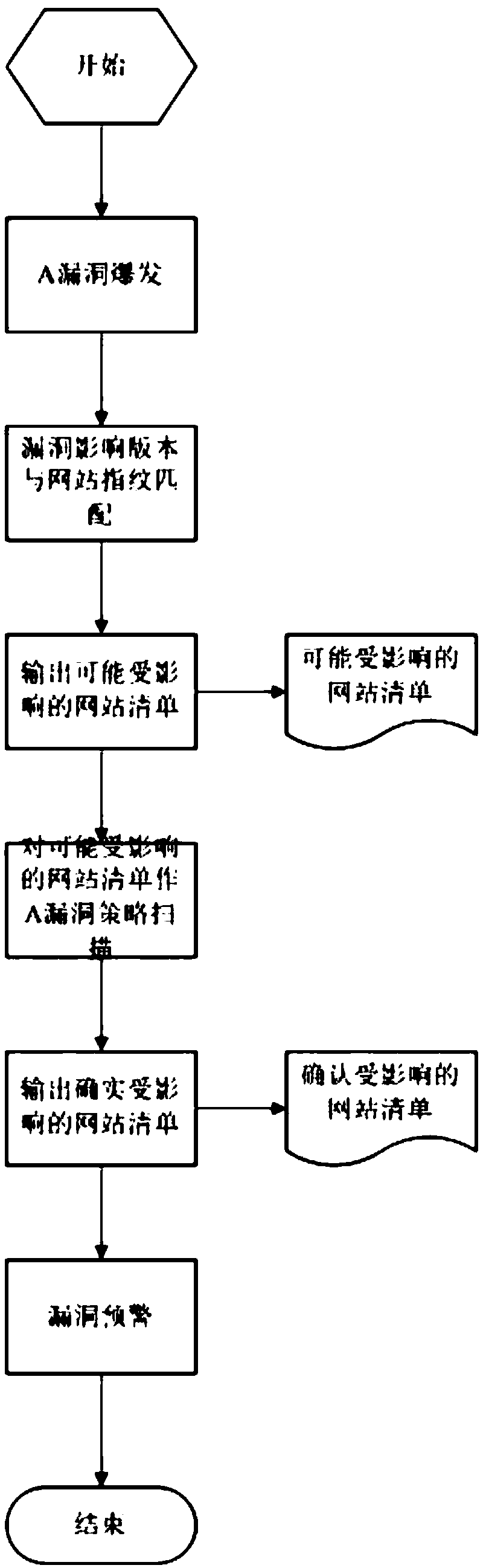
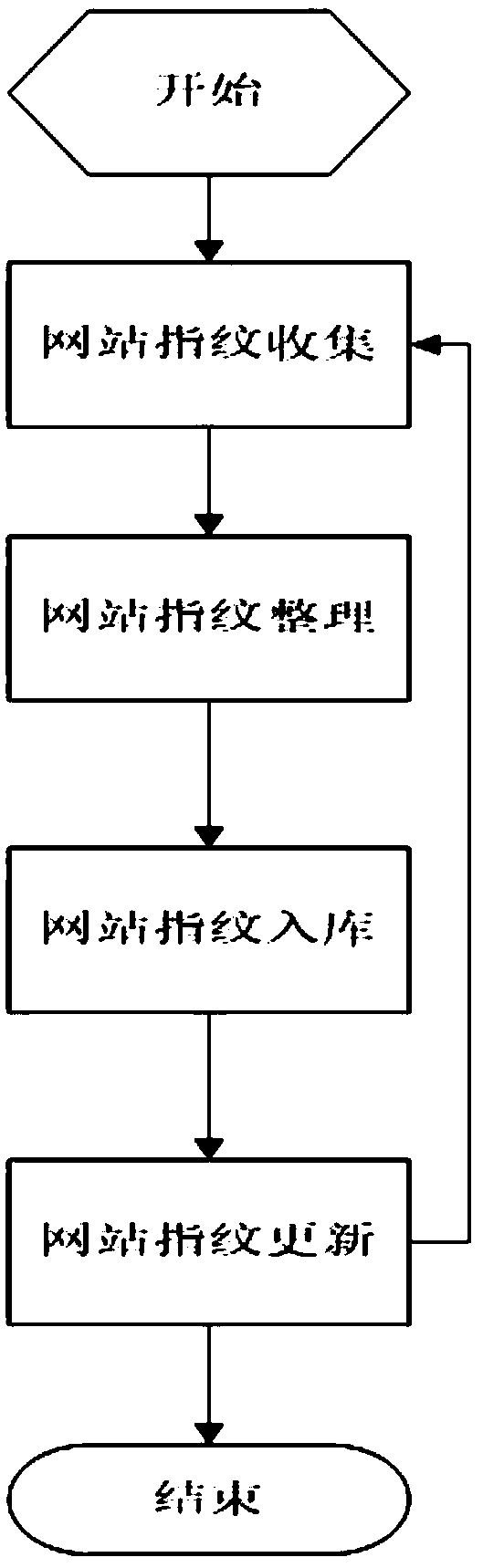
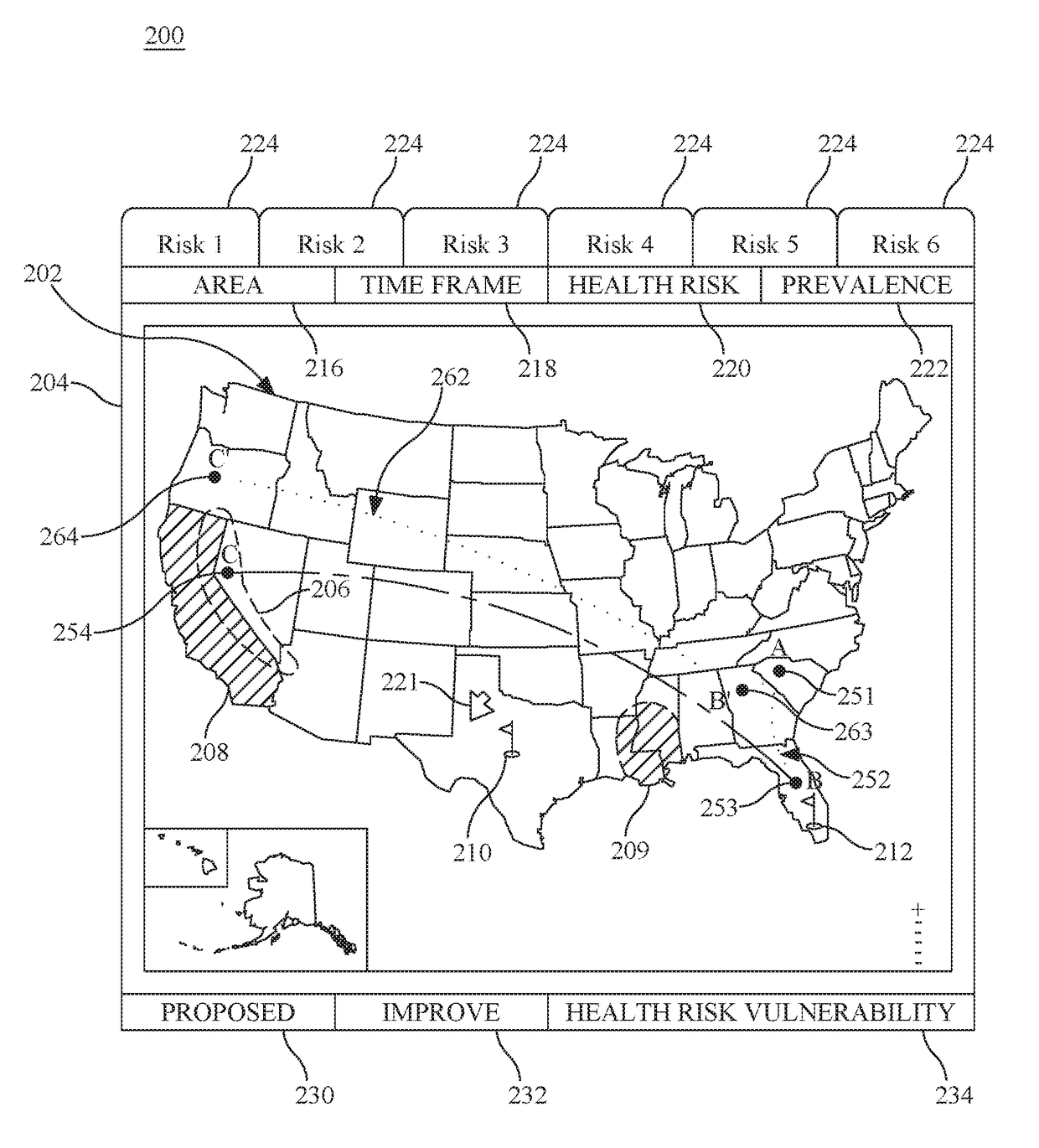
Patents
Literature
31 results about "Risk vulnerability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A vulnerability is a weakness or gap in our protection efforts. Risk – The potential for loss, damage or destruction of an asset as a result of a threat exploiting a vulnerability. ... Risk is a function of threats exploiting vulnerabilities to obtain, damage or destroy assets. Thus, threats (actual, conceptual, or inherent) may exist, but if there are no vulnerabilities then there is little/no risk.
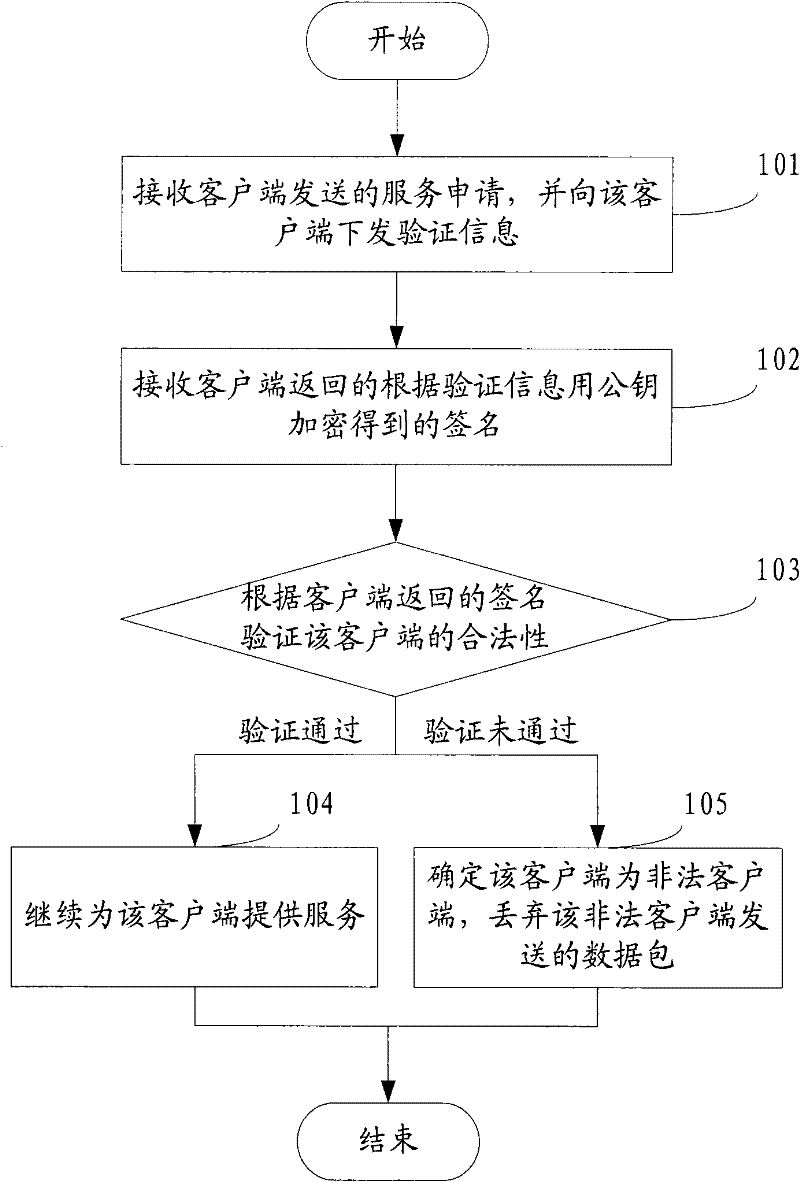
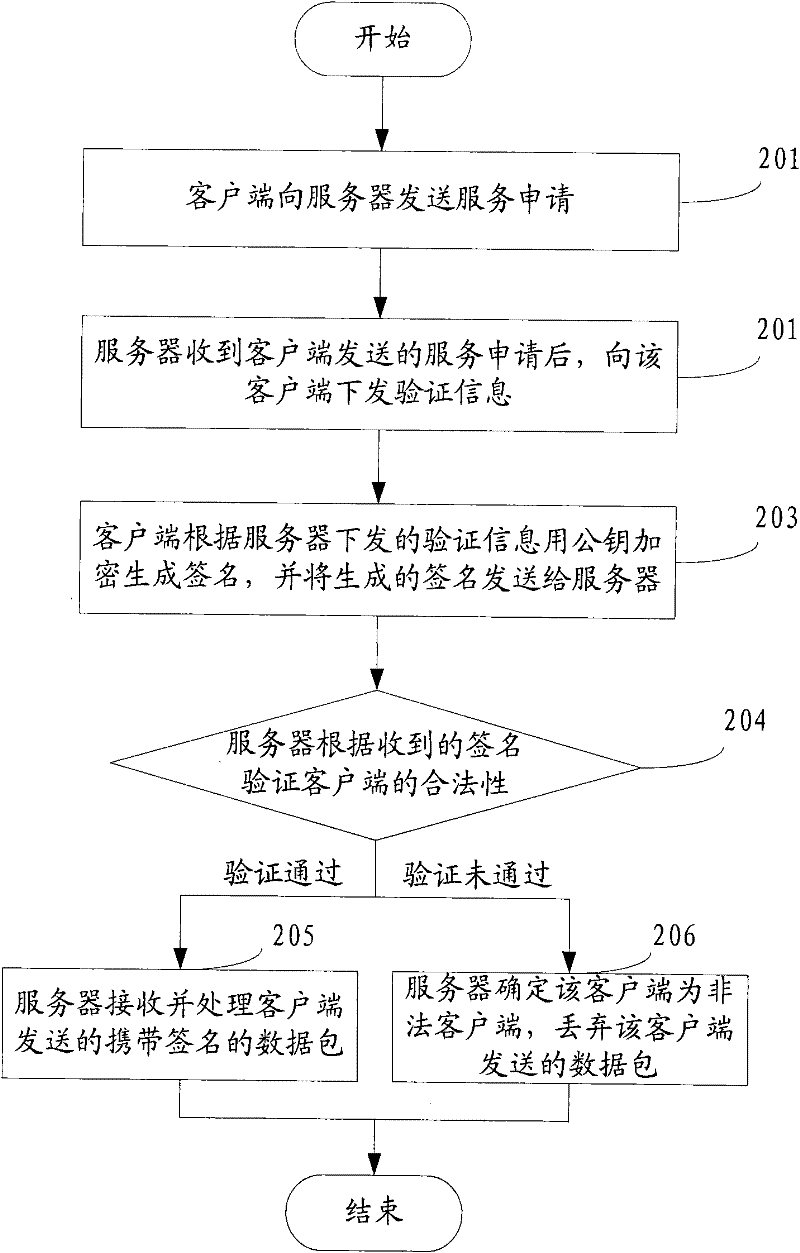
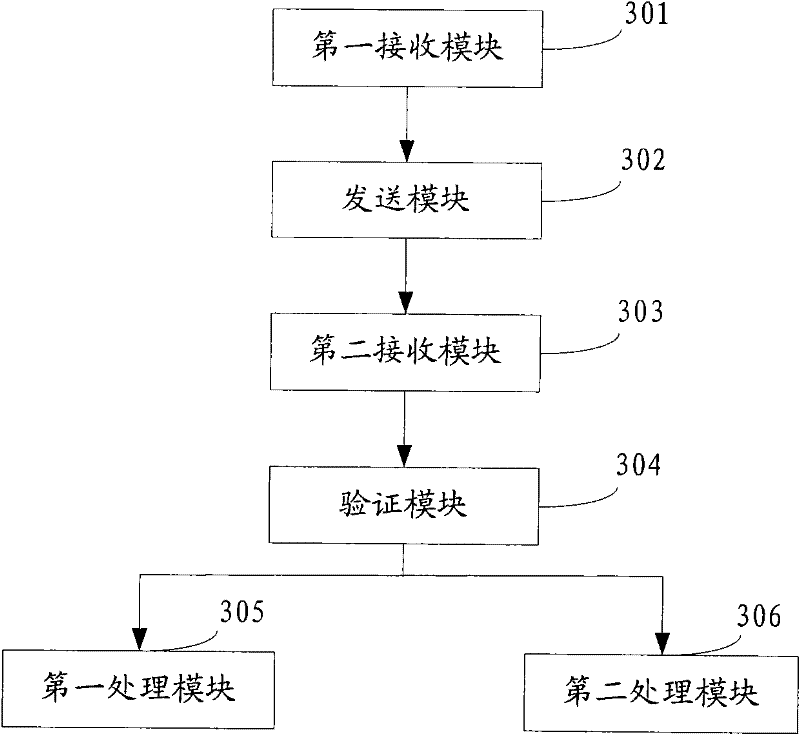
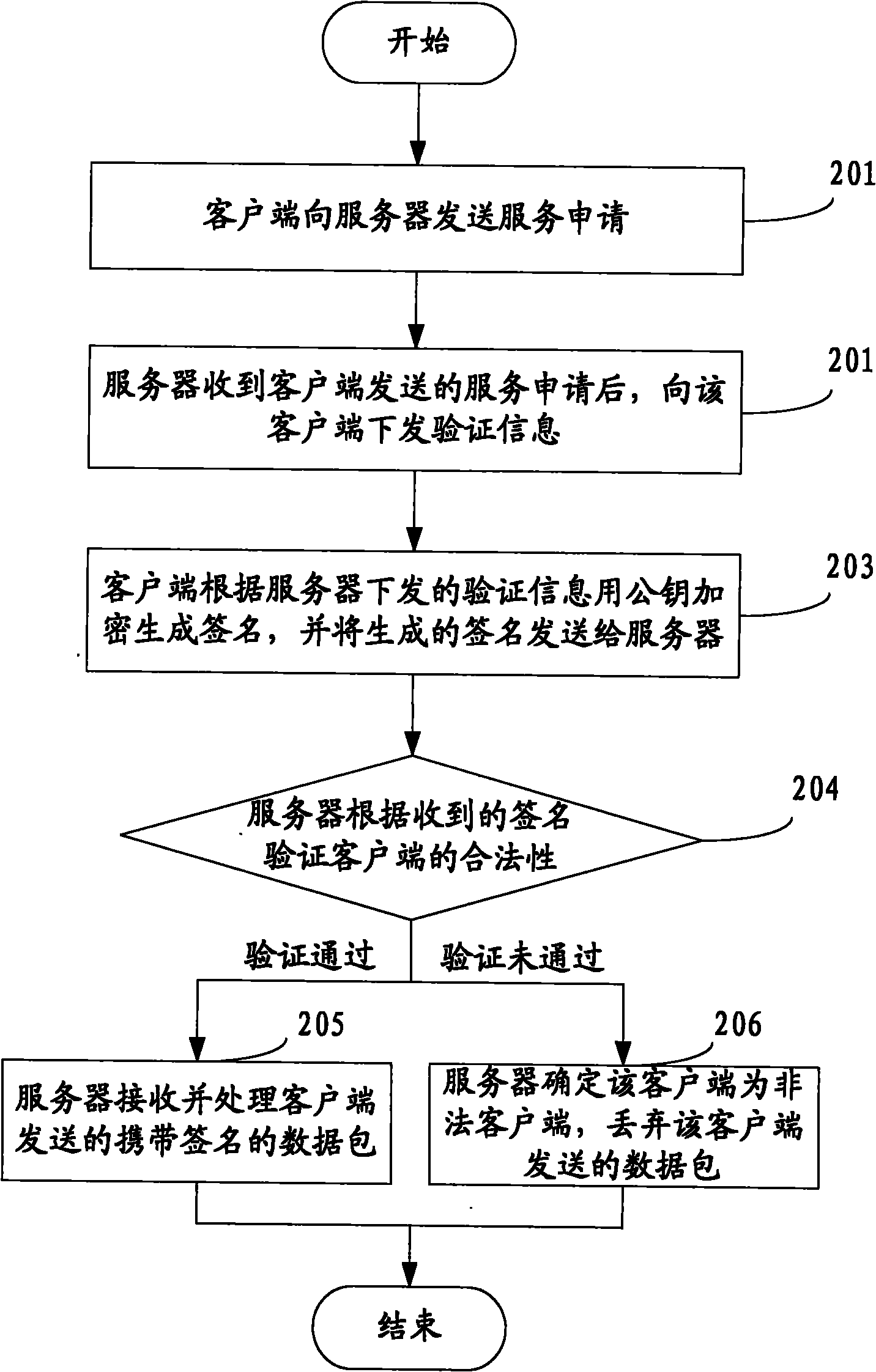
Method, device and system for preventing services from being attacked
ActiveCN102164033AAvoid attackLimit Malicious AttacksMultiple keys/algorithms usageUser identity/authority verificationPlaintextNetwork packet
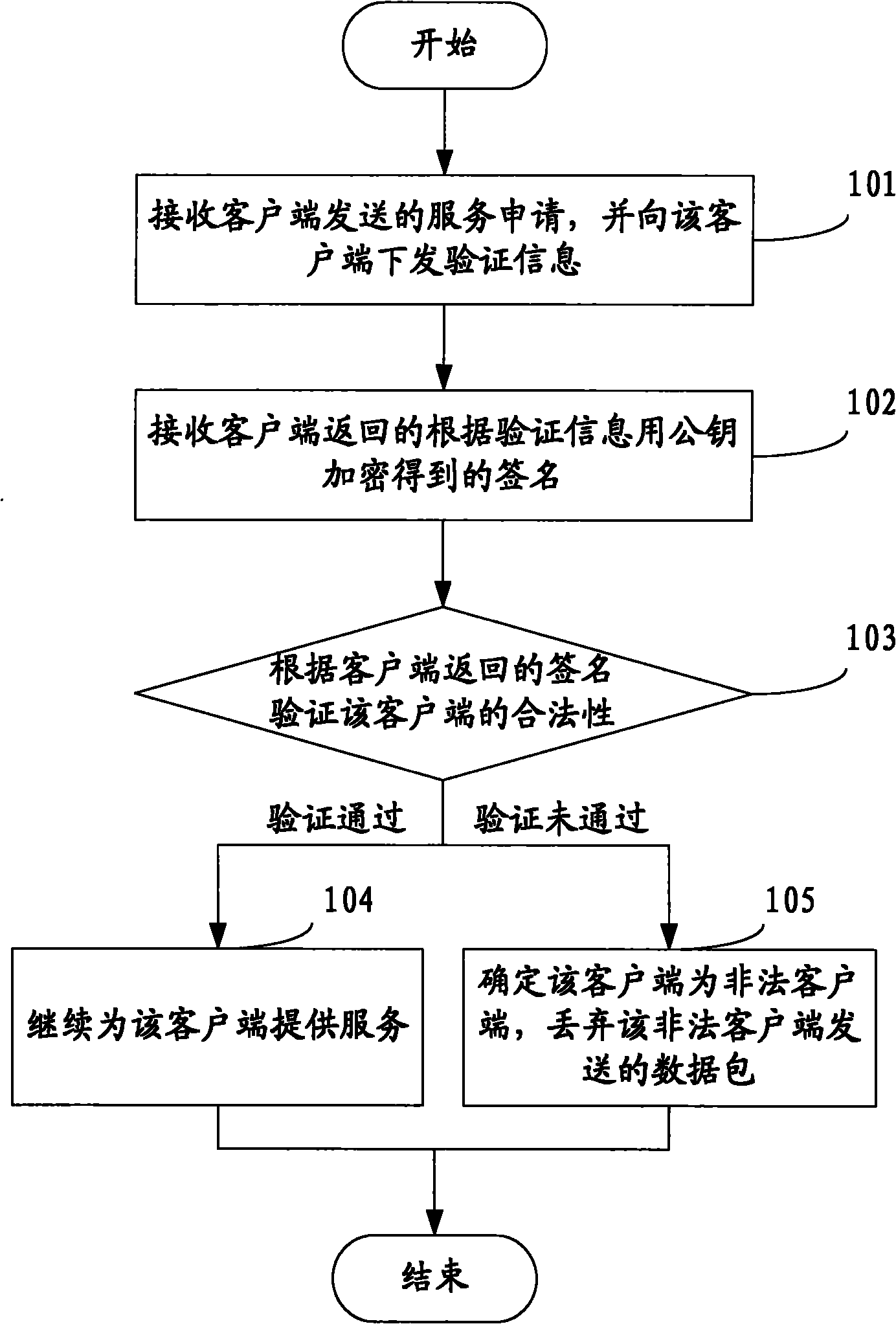
The invention discloses a method, device and system for preventing services from being attacked, which belong to the technical field of information security. The method comprises the following steps: receiving a service request sent by a client, and issuing verification information to the client, wherein the verification information at least comprises plaintexts generated randomly and user identifications encrypted by private keys; receiving a signature which is returned by the client and encrypted by a public key for verification information; and verifying the legality of the client according to the signature returned by the client, if passing the verification, continuing to serve the client, otherwise, determining that the client is an illegal client, and discarding a data packet sent by the illegal client. The method, device and system disclosed by the invention have the advantages that because the client is subjected to legality verification before being provided with services, no excessive spending is added in the process of verification, and the secret key interaction between a server and a client is not required, the risk vulnerabilities existing in secret key interaction can be avoided, and then the effect of preventing services from being attacked can be achieved.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
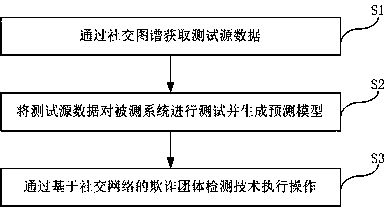
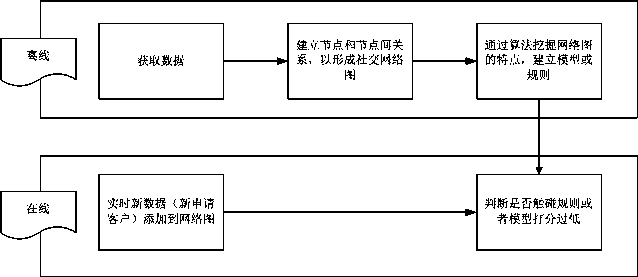
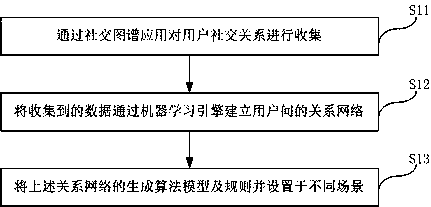
Social network-based fraud group detection method and system
InactiveCN107943879AImprove global risk identification capabilitiesAvoid risk loopholesForecastingResourcesSocial graphRisk identification
The invention discloses a social network-based fraud group detection method and system. The method comprises the following steps of S1, obtaining test source data through a social graph; S2, testing atested system by the test source data and generating a prediction model; and S3, executing operation through a social network-based fraud group detection technology. According to the social network-based fraud group detection method and system provided by the invention, through the social network-based fraud group detection technology, a user can mine potential group fraud according to a social relationship and predict fraud groups, so that global risk identification capability of a network can be improved and unnecessary risk vulnerabilities are avoided.
Owner:上海维信荟智金融科技有限公司
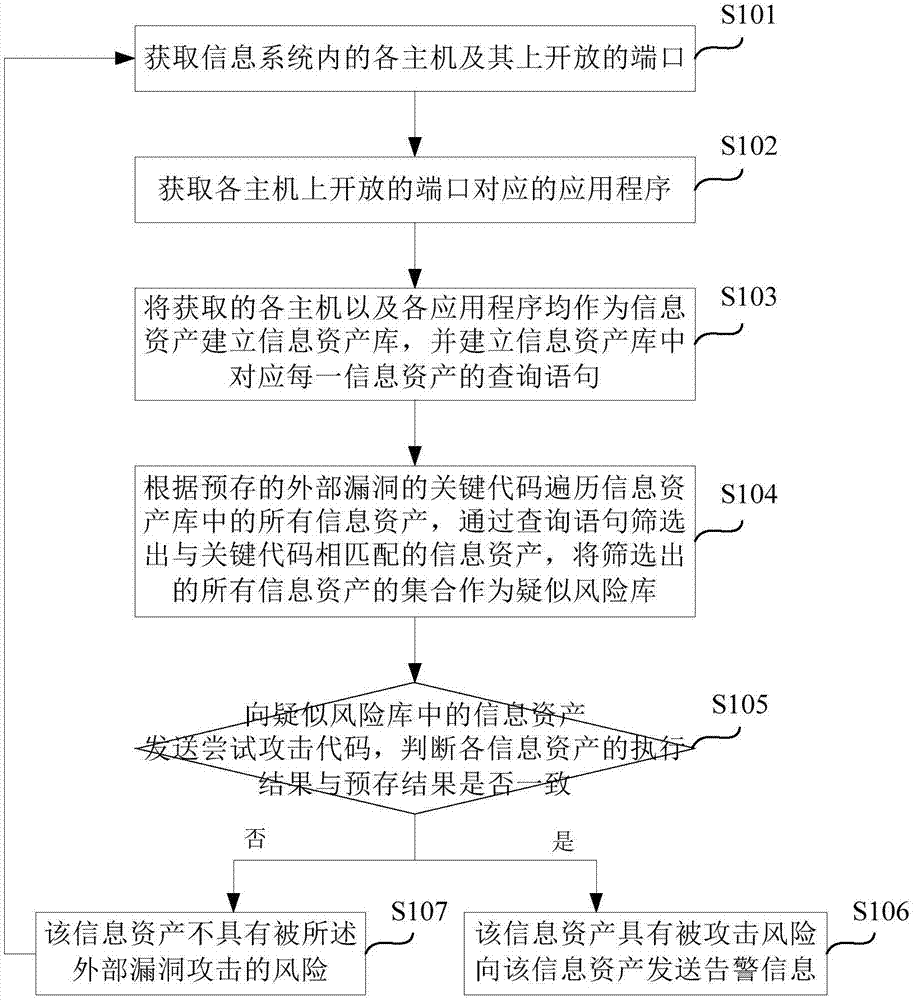
Vulnerability detection method and system for information system, storage medium and electronic equipment
ActiveCN107577947AShorten emergency response timeImprove resource utilization efficiencyPlatform integrity maintainanceApplication softwareInformation system
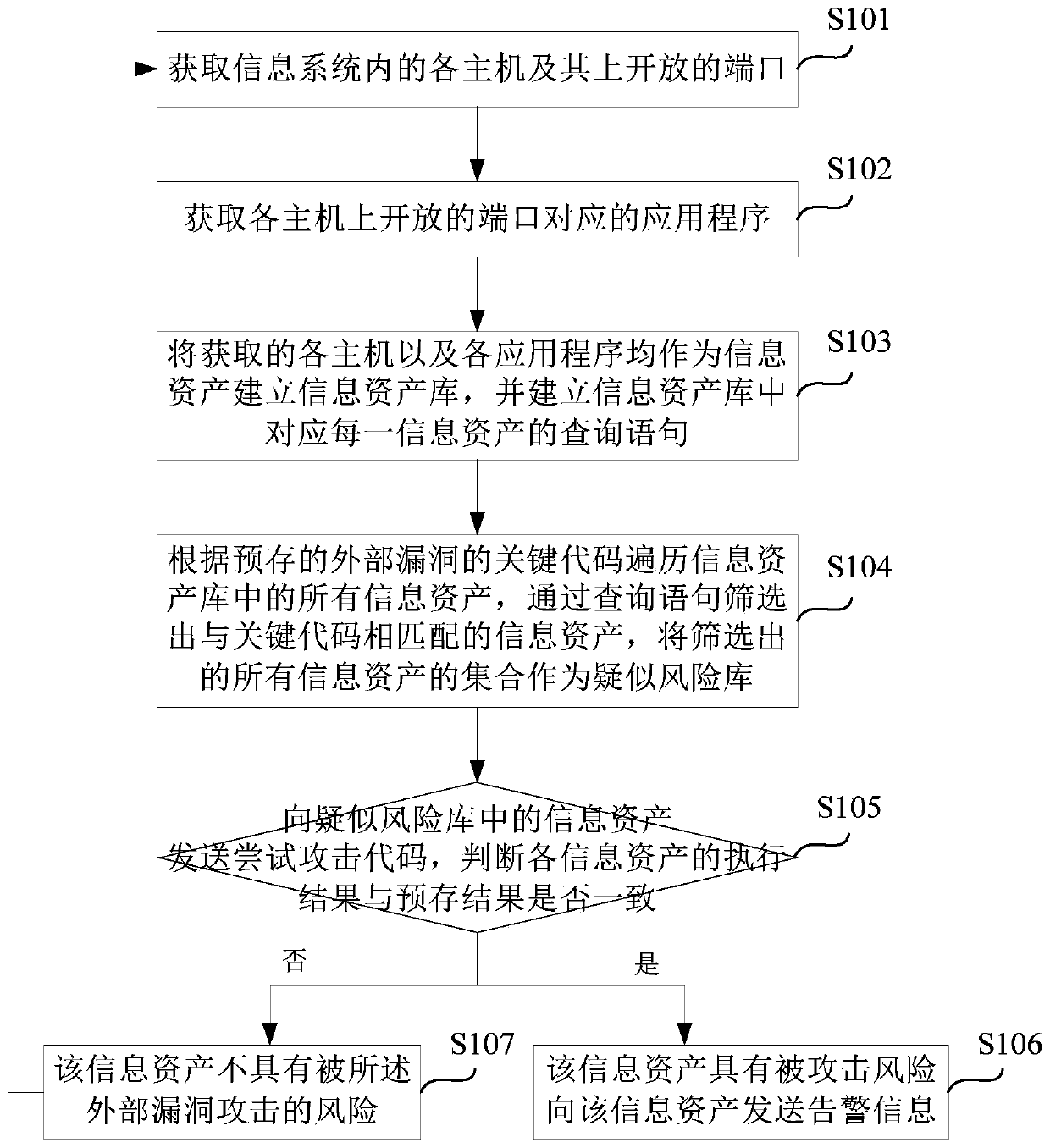
The invention provides a vulnerability detection method and system for an information system, a storage medium and electronic equipment. The method comprises the steps that all hosts in the information system and ports open in all the hosts are acquired; application programs corresponding to the ports open in all the hosts are acquired; all the hosts and all the application programs are used as information assets to establish an information asset library; the information asset library is traversed according to a key code of an external vulnerability, and information assets matched with the keycode are screened out to serve as a suspected risk library; an attempt attack code is sent to the information assets in the suspected risk library according to an attack code of the external vulnerability; whether execution results returned by all the information assets after the attempt attack code is executed are consistent with a pre-stored result is judged; and if yes, alarm information is sent to the hosts where the information assets are located. When a high-risk vulnerability is reported externally, by use of the vulnerability detection method and system, the position with a risk can be found at the first time in an intranet environment, the vulnerability is automatically verified, and the influenced hosts or applications are output.
Owner:携程旅游信息技术(上海)有限公司
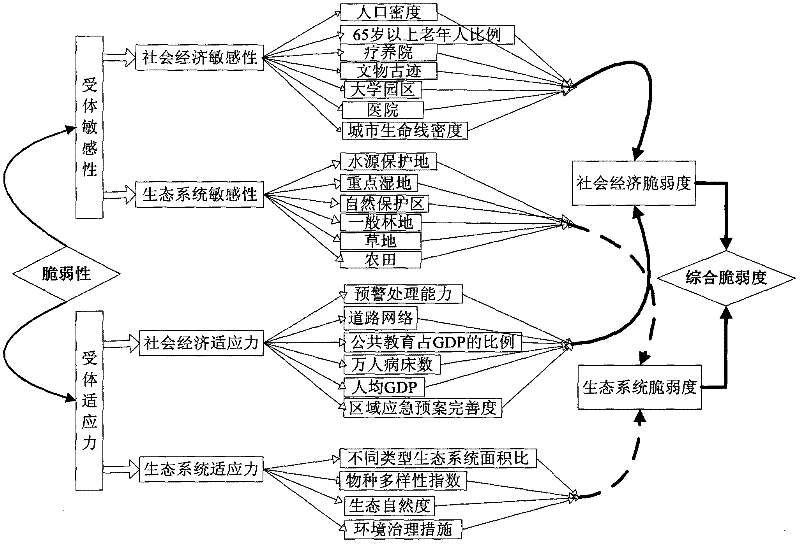
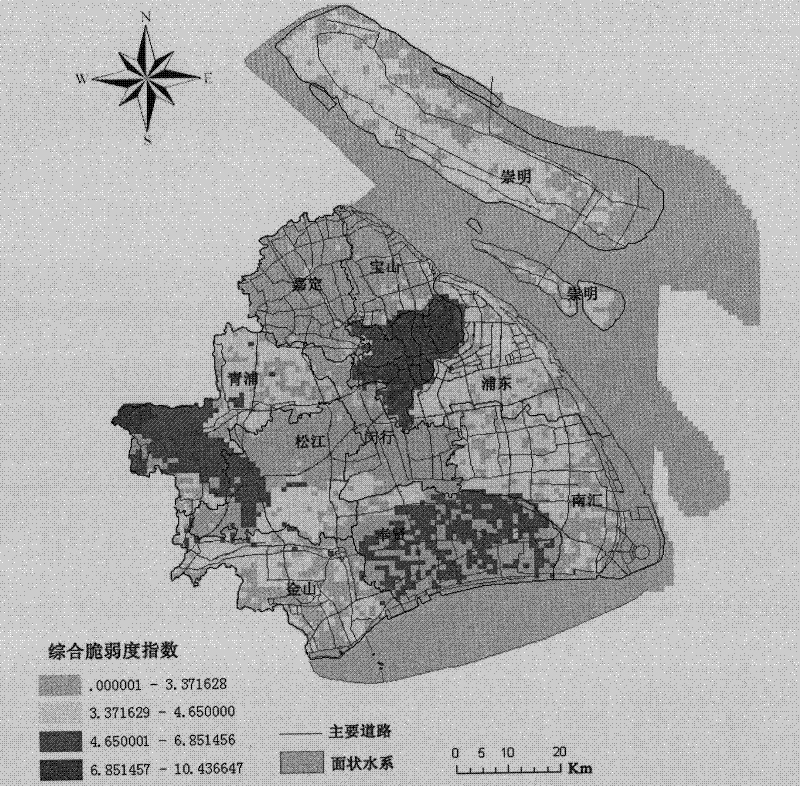
A Vulnerability Assessment Method for Regional Environmental Risk Receptors
InactiveCN102270325AComprehensive evaluationEvaluation is scientific and comprehensiveInstrumentsFragilityEnvironment of Albania
Owner:BEIJING NORMAL UNIVERSITY
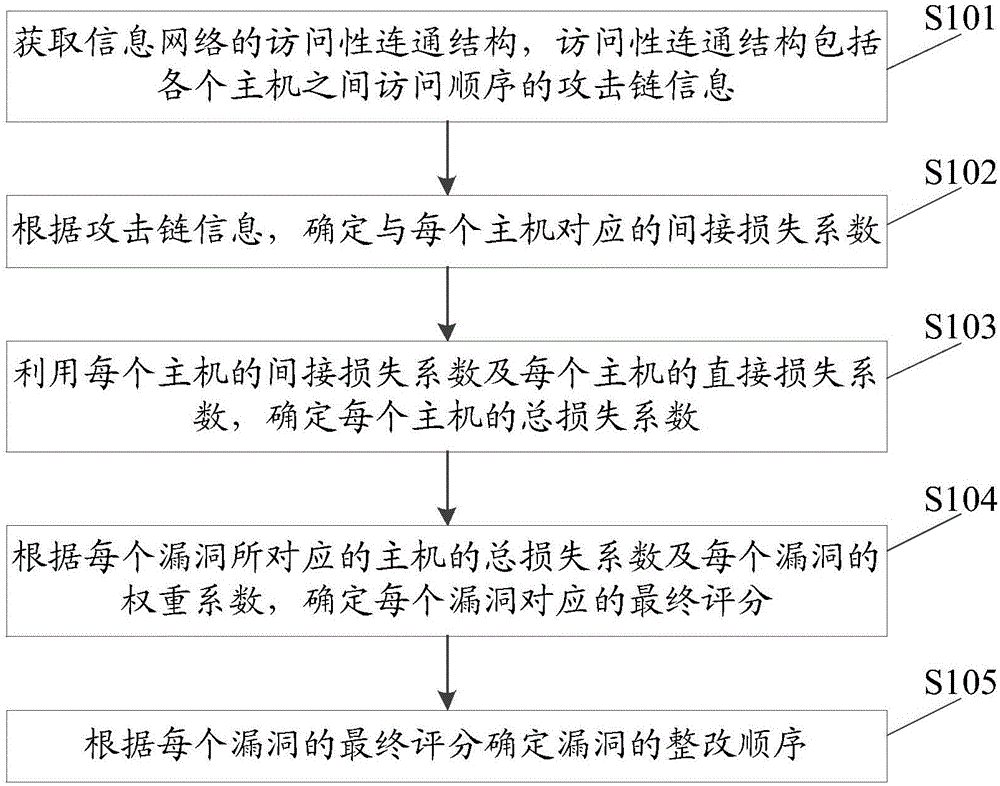
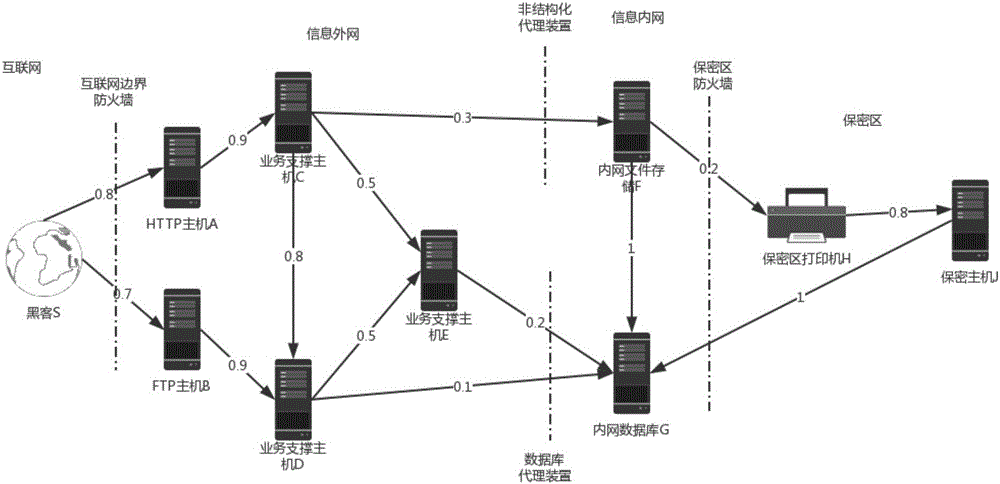
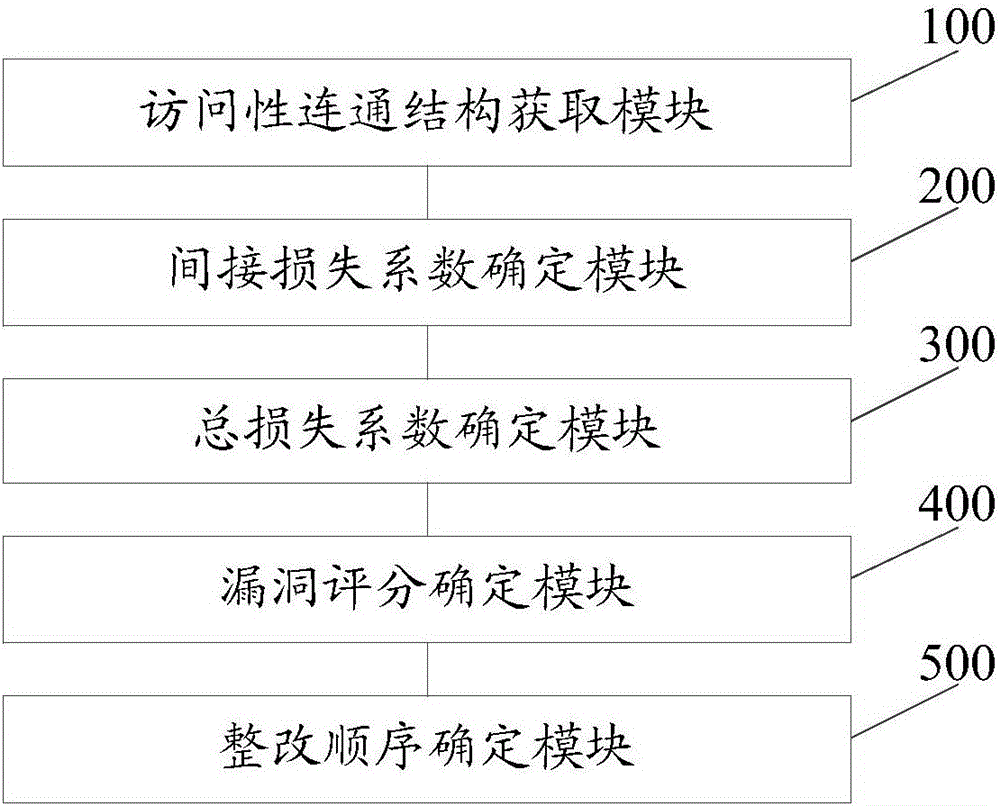
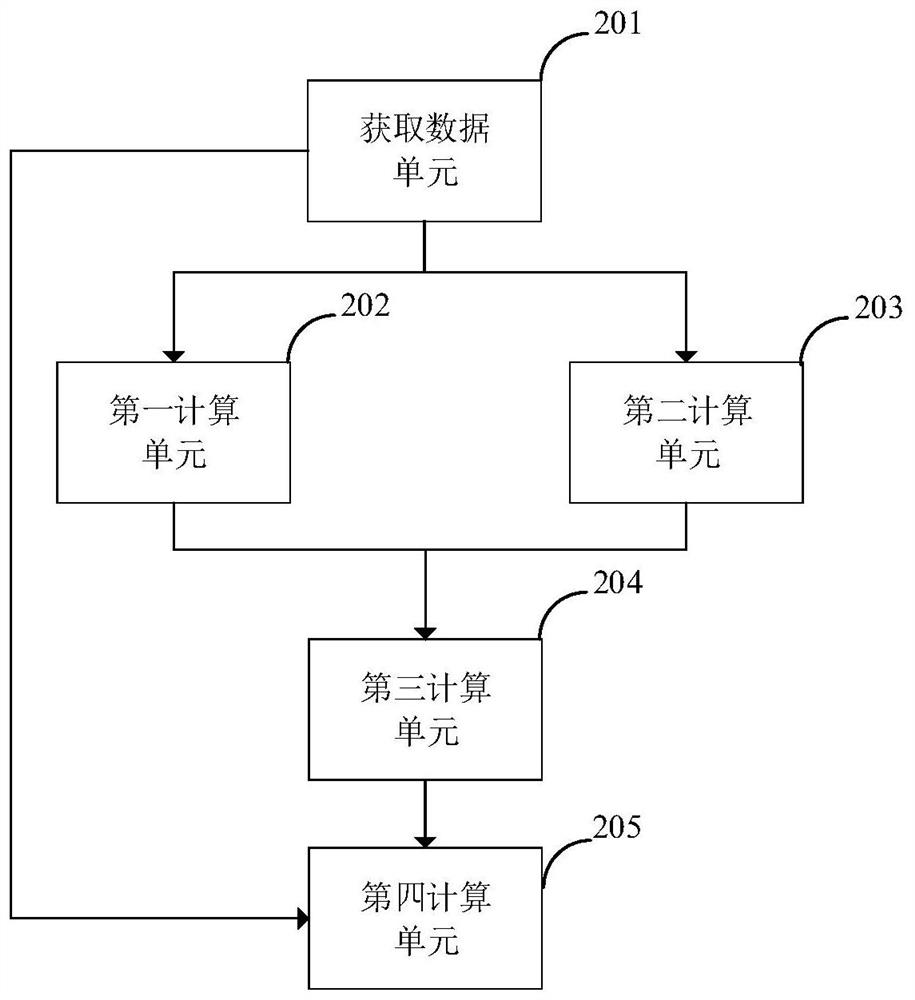
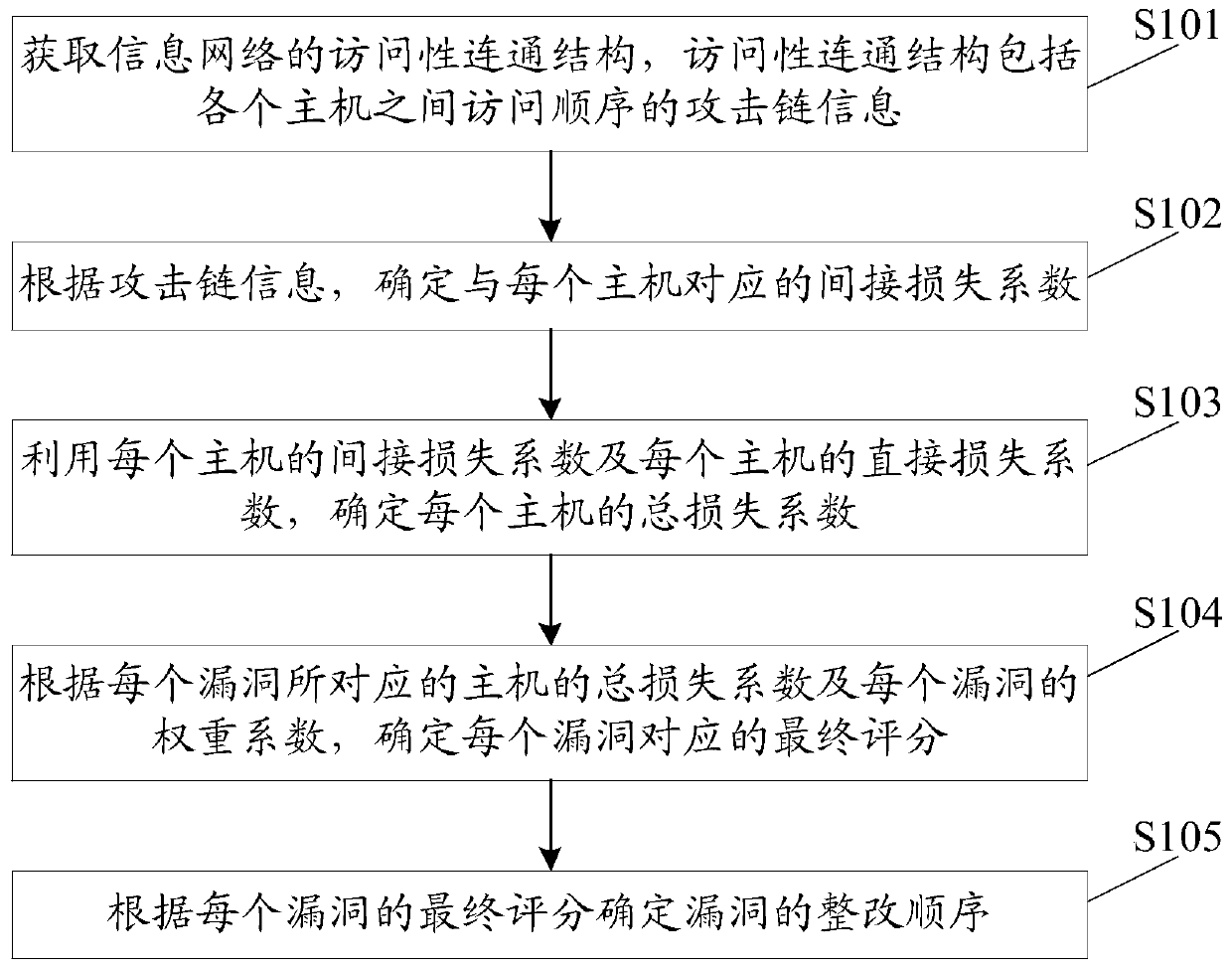
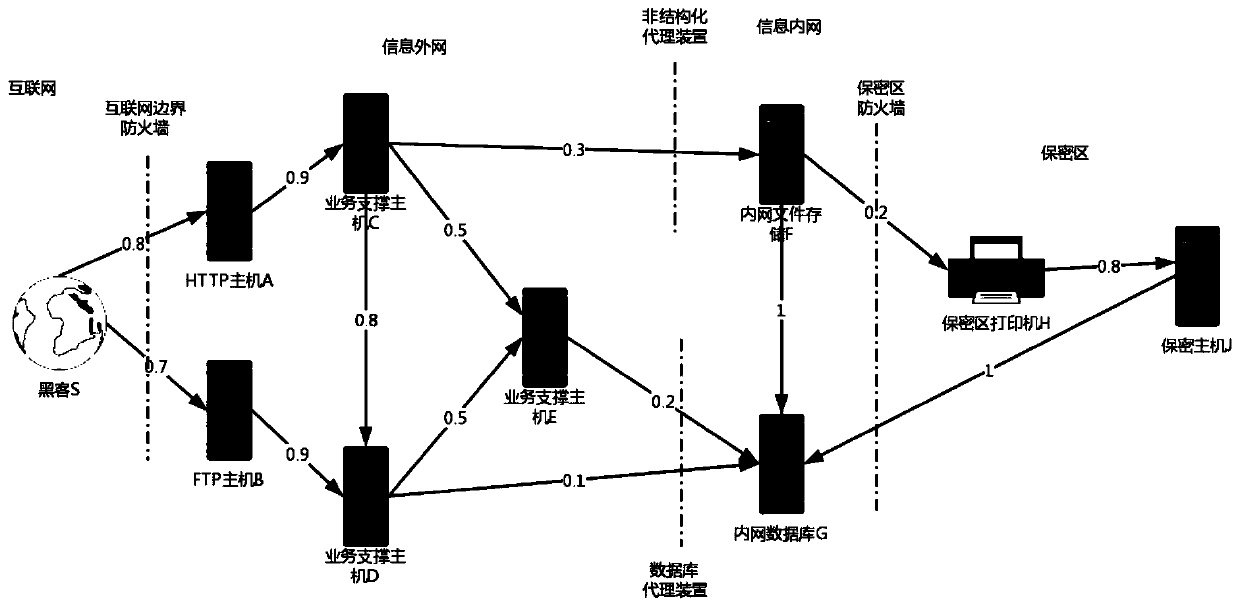
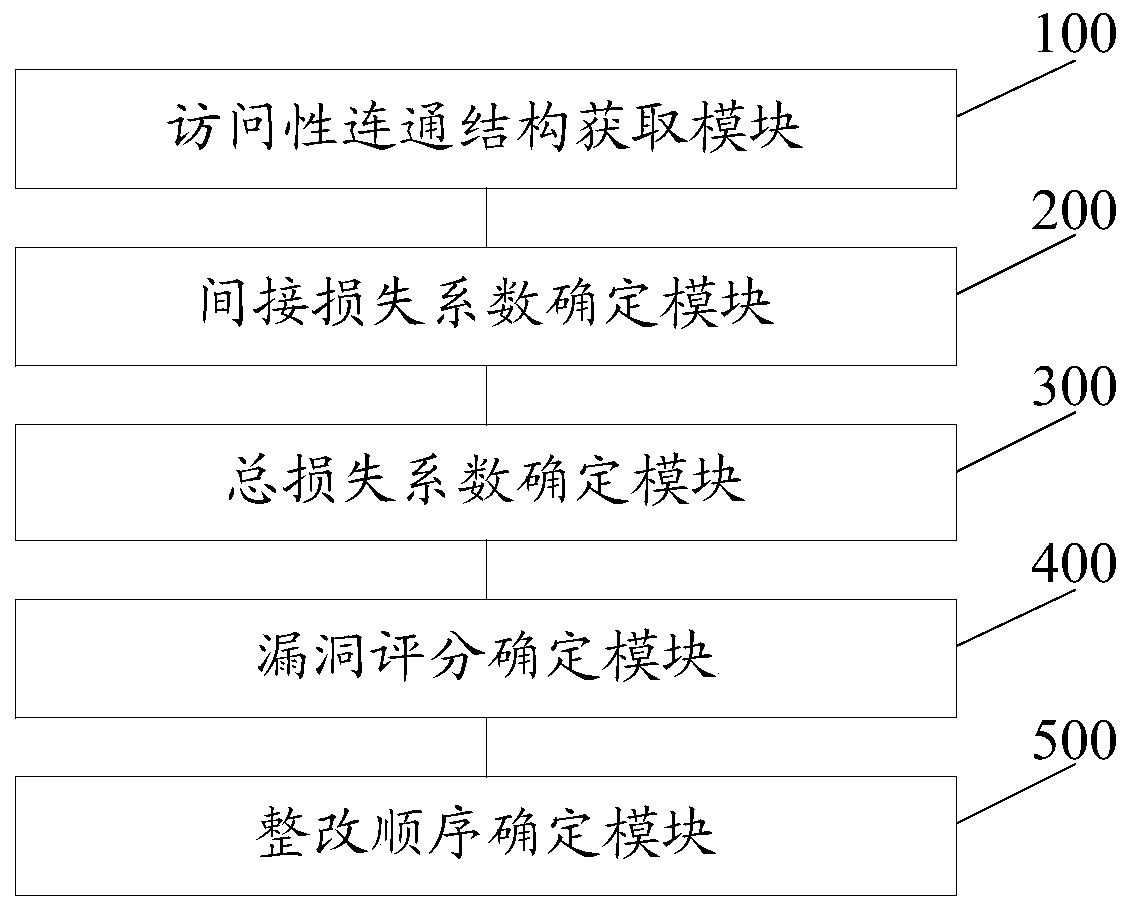
Vulnerability restructuring sequence determining method and system based on attack links
The invention discloses a vulnerability restructuring sequence determining method and system based on attack links. The method comprises the steps of determining an indirect loss coefficient corresponding to each host according to attack link information of an access connection structure; through utilization of the indirect loss coefficient of each host and the direct loss coefficient of each host, determining a total loss coefficient of each host; and determining a final score and a vulnerability restructuring sequence corresponding to each vulnerability according to the total loss coefficient of each host corresponding to each vulnerability and a weight coefficient of each vulnerability. Visibly, different vulnerabilities are scored through combination of the attack link information of an information network; the harmfulness scores of the vulnerabilities and the hosts can be calculated according to the harmfulness of the vulnerabilities themselves and a topological structure, so under the condition that the manpower is limited, the vulnerabilities and hosts badly in need of restoration are distinguished, the operation and maintenance personnel are prevented from excessively paying close attention to the internal network high-risk vulnerabilities hardly possible to be used, while the external network high-risk vulnerabilities with higher risk are ignored.
Owner:STATE GRID CORP OF CHINA +1
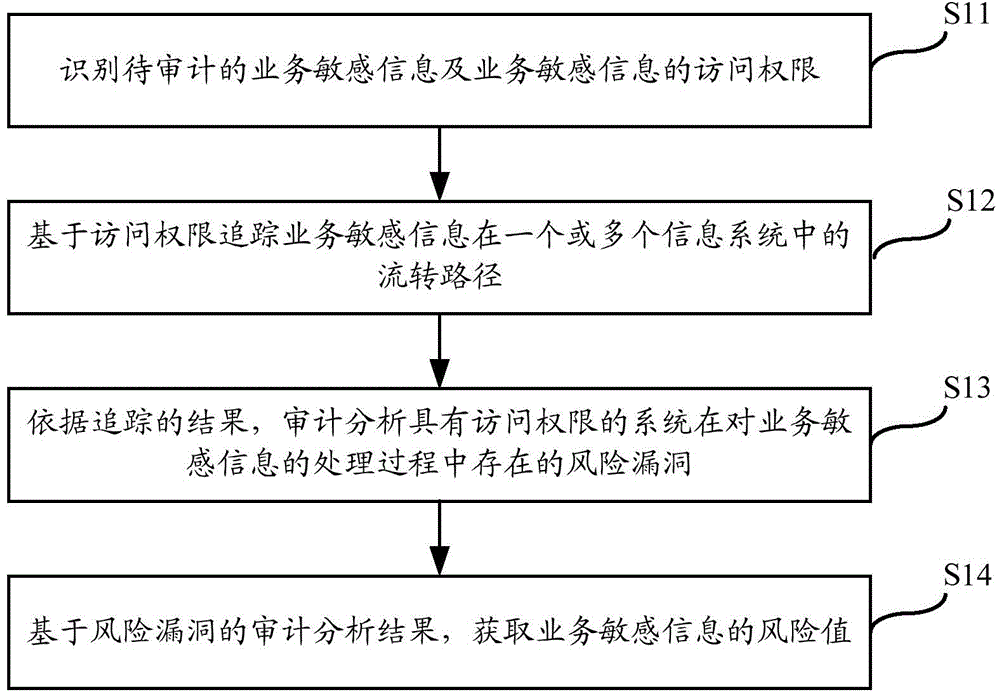
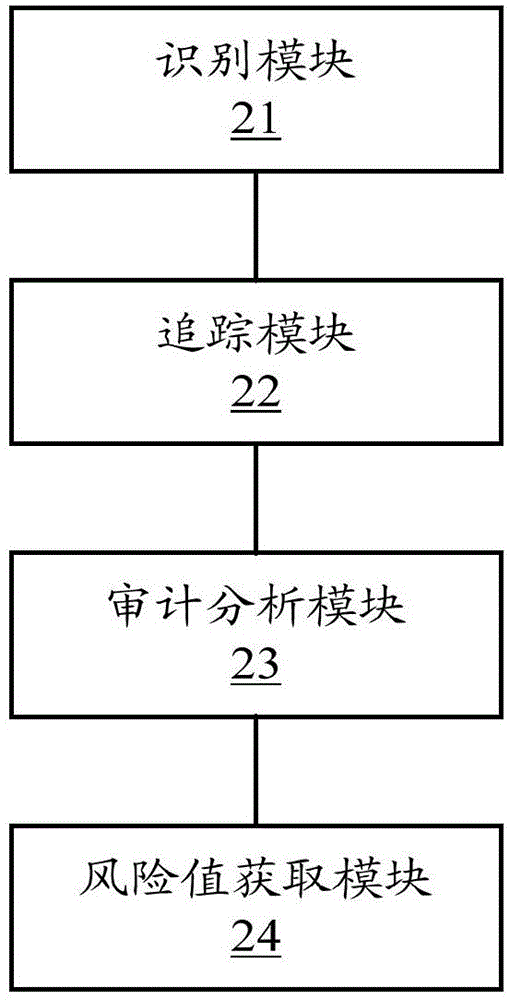
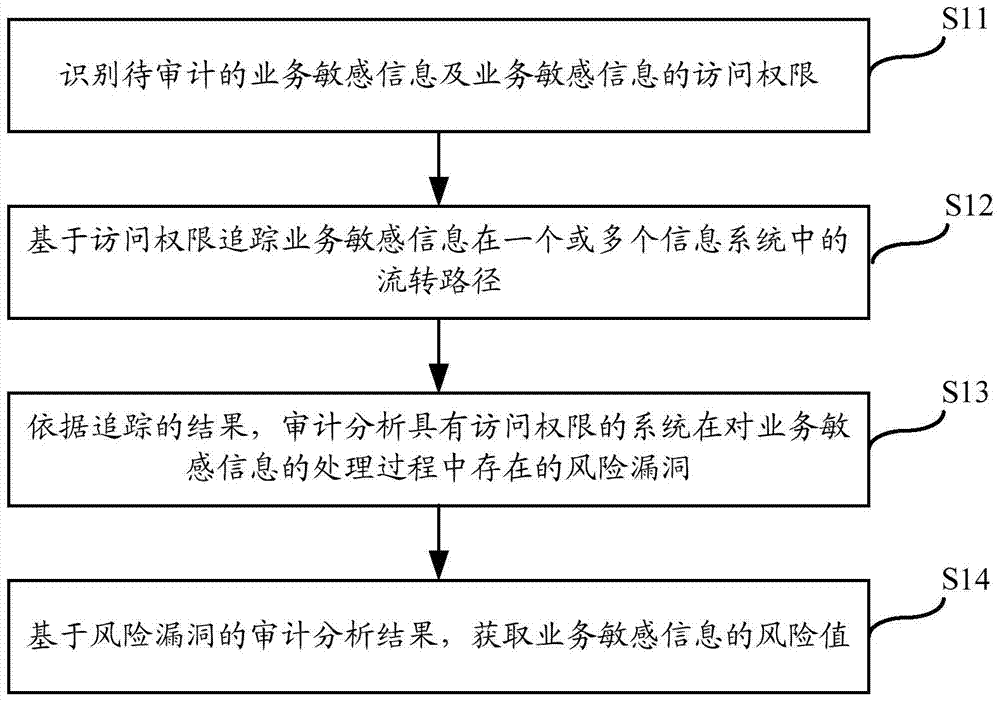
Walk-through test technique based information security audit implementation method and system
InactiveCN104462988ADigital data protectionPlatform integrity maintainanceInternet privacyInformation security audit
The invention relates to the technical field of information monitoring, in particular to a walk-through test technique based information security audit implementation method and system. The method includes: recognizing business sensitive information waiting for audit and access right of the business sensitive information; tracking flow paths of the business sensitive information in one or more information systems based on the access right; performing audit analysis on risk vulnerabilities existing in the process that the systems with access right process the business sensitive information according to tracking results; based on audit analysis results of the risk vulnerabilities, acquiring a risk value of the business sensitive information. By the method and system, risks existing in the process that the sensitive information flows in full life circles of the multiple information systems can be monitored.
Owner:STATE GRID CORP OF CHINA +2
A method and a system for fast detection of bulk site vulnerabilities based on web fingerprints
InactiveCN109190380ARealize risk detectionEarly warningPlatform integrity maintainanceTransmissionData miningFingerprint
The invention relates to network security and provides a method and a system for rapid detection of bulk site vulnerabilities based on web fingerprints. The method for quickly detecting bulk site security vulnerabilities based on web fingerprints comprises the following steps: collecting and classifying target group fingerprints; matching vulnerabilities and the fingerprints, and screening out thesites which may have current vulnerabilities in the target site group; conducting site vulnerability detection to confirm the existence of the vulnerabilities. The method firstly quickly matches thecomponents and versions that are affected by the vulnerability and then carries out targeted vulnerability strategy scanning on the batch of possibly affected sites, thereby rapidly realizing site vulnerability risk detection, realizing site vulnerability early warning and safety response, and reducing the safety risk caused by site vulnerabilities.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
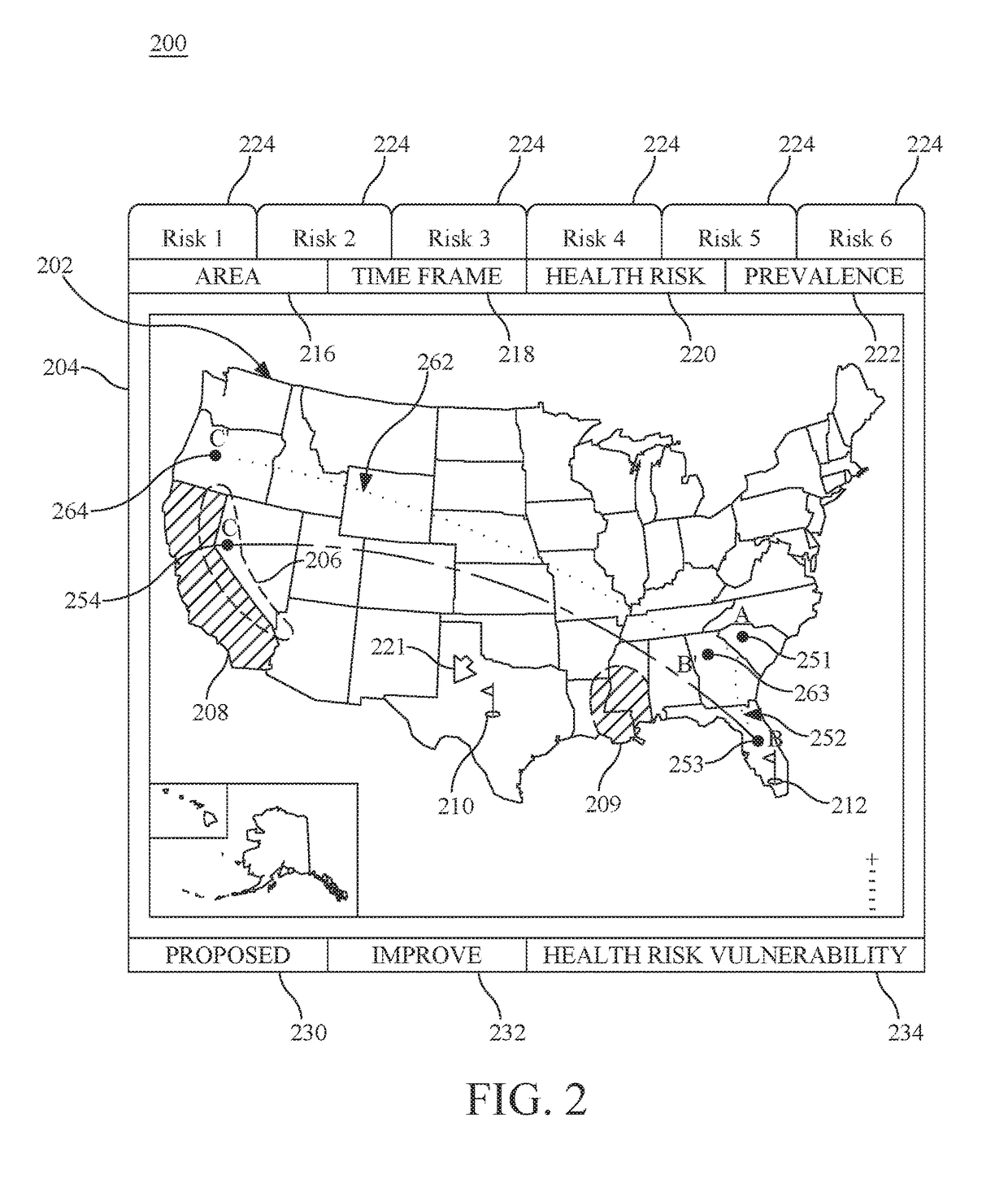
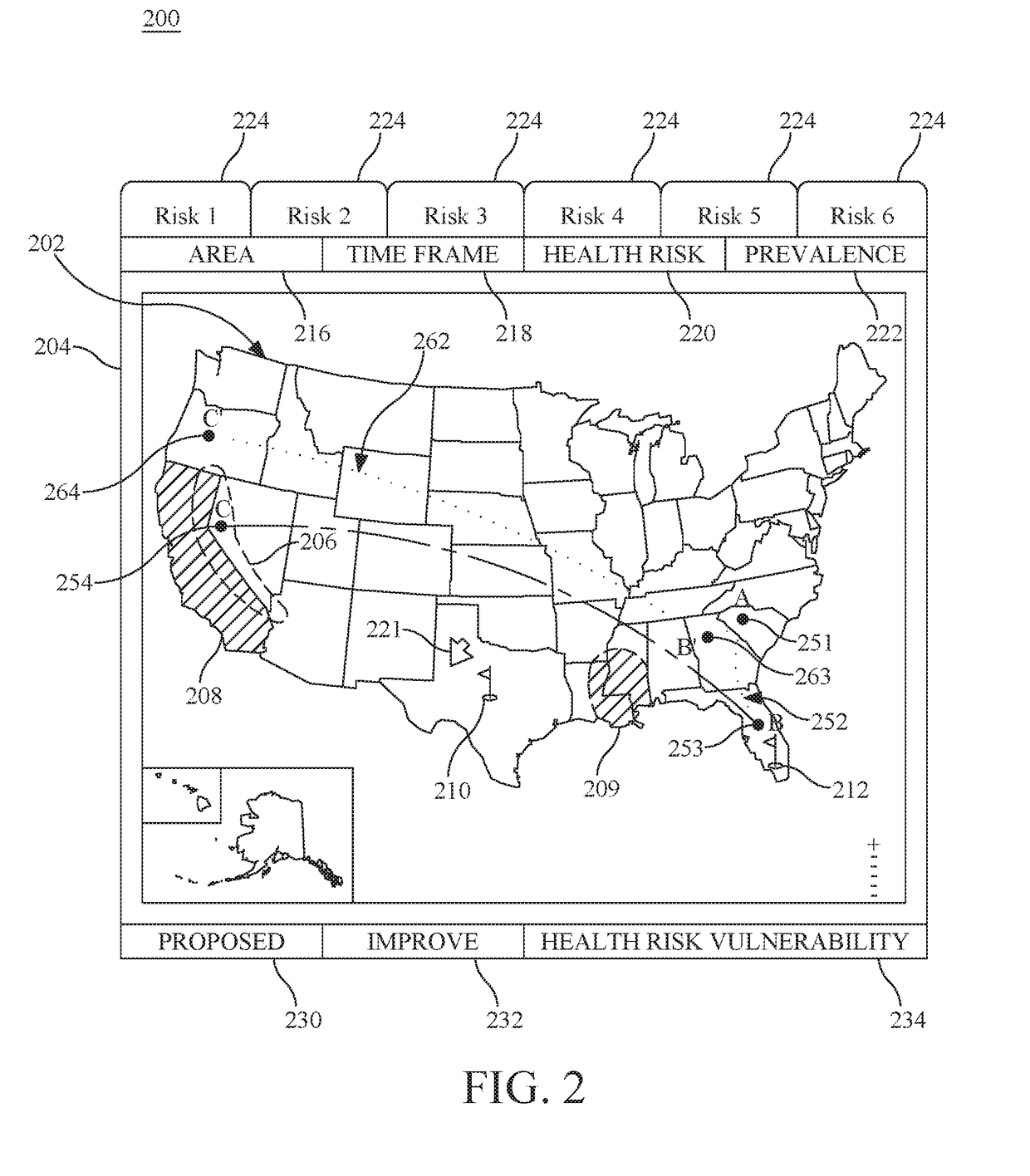
Personal travel health vulnerability navigator
InactiveUS20170351833A1Minimize health vulnerability of individualIncrease the itineraryData processing applicationsHealth-index calculationHealth riskLevel data
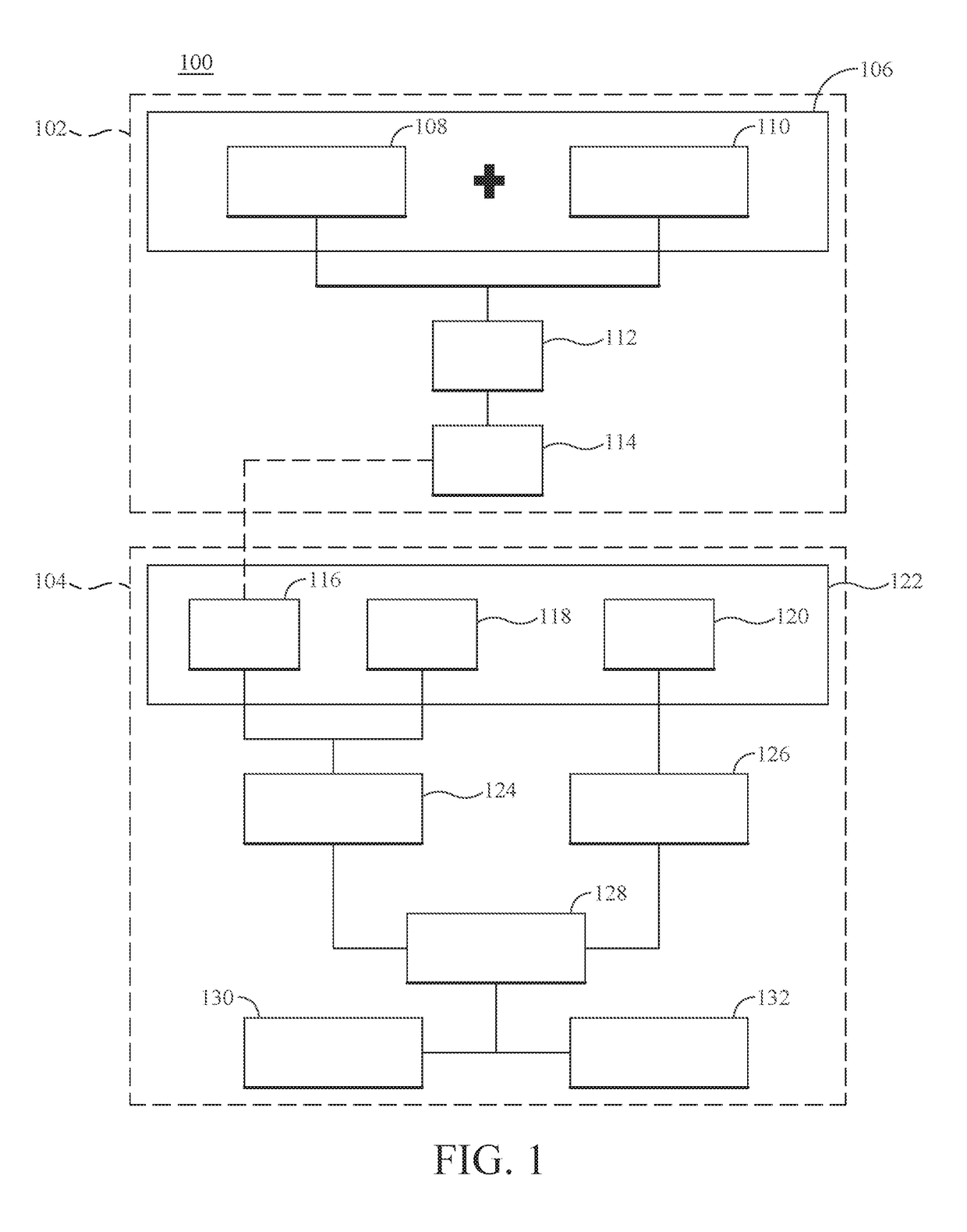
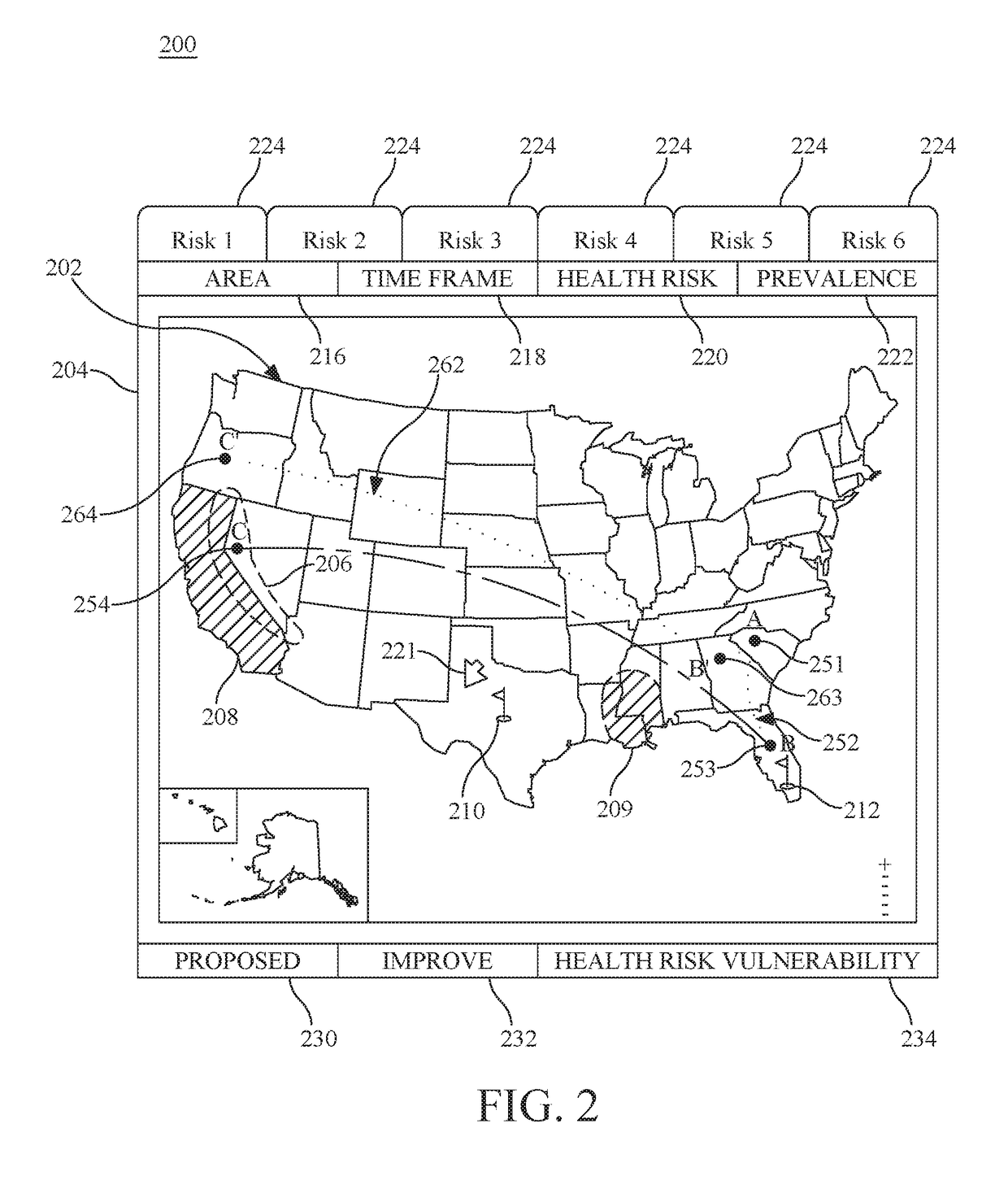
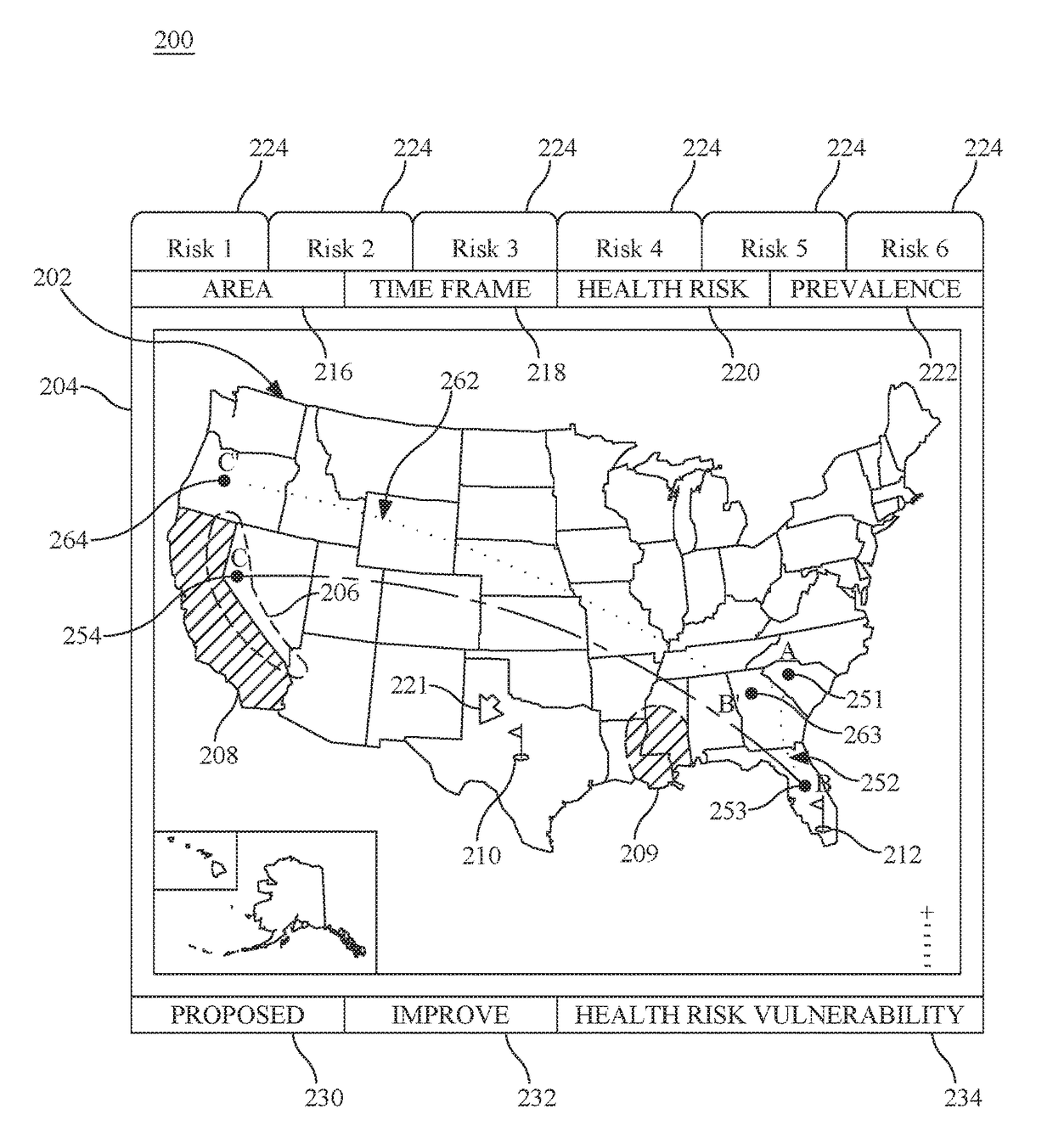
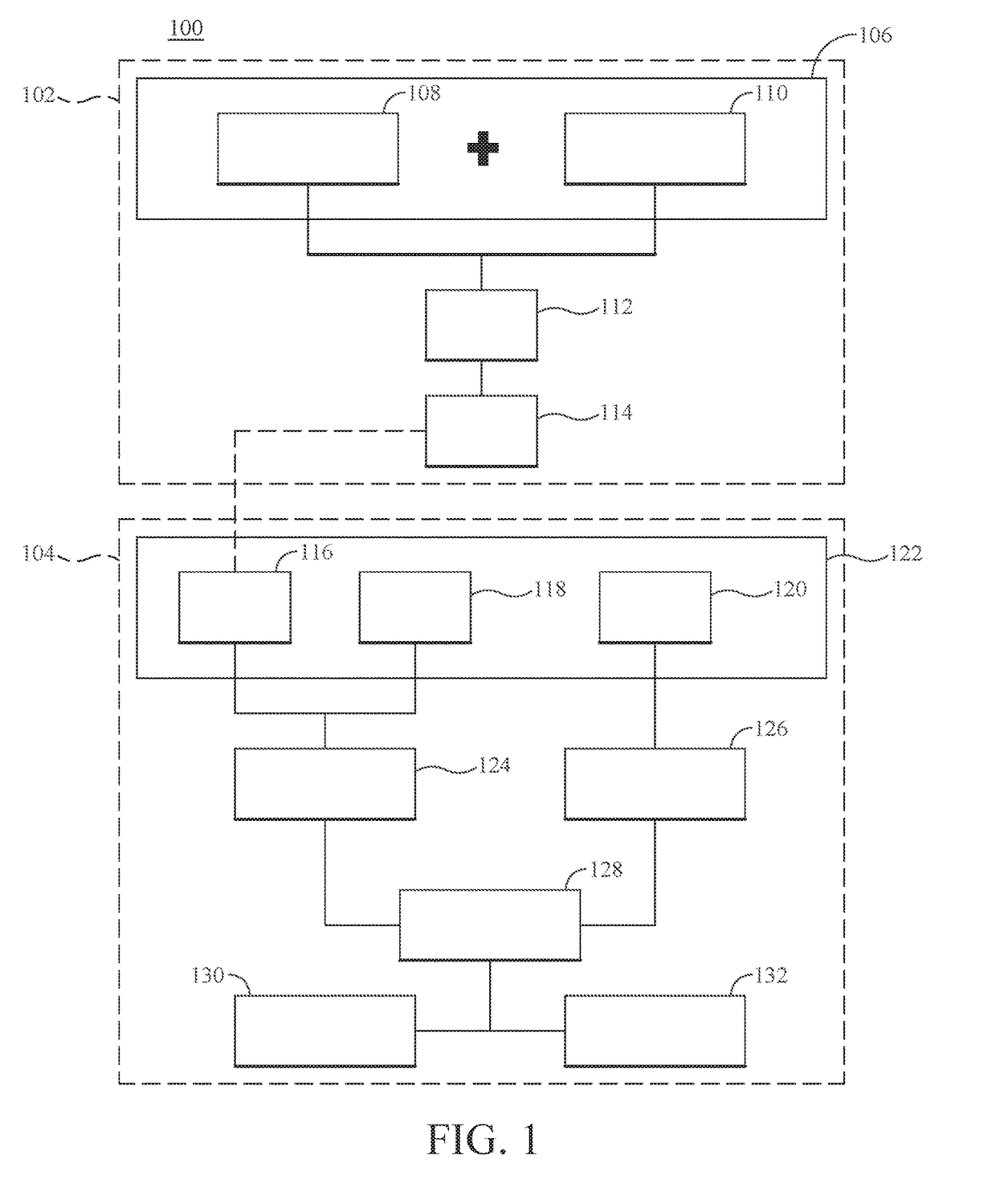
Individual health vulnerability is assessed by obtaining health risk prevalence level data containing health risk prevalence levels for one or more health risks over a given geographical area. The health risk prevalence level data to generate for each health risk a prevalence level forecast as a function of time and location. A health risk prevalence level map is generated for the given geographical area illustrating current and future health risk prevalence levels for each health risk at a plurality of locations within the given geographical area. Personal health status data are obtained for a given individual along with a proposed travel itinerary f covering at least a portion of the geographical area over a given time duration. The personal health status data, travel itinerary and map generate a personal health risk vulnerability model containing a quantification of vulnerability to the one or more health risks resulting from the travel itinerary.
Owner:IBM CORP
Personal travel health vulnerability navigator
InactiveUS20170351834A1Minimize health vulnerability of individualIncrease the itineraryMedical simulationData processing applicationsHealth riskLevel data
Individual health vulnerability is assessed by obtaining health risk prevalence level data containing health risk prevalence levels for one or more health risks over a given geographical area. The health risk prevalence level data to generate for each health risk a prevalence level forecast as a function of time and location. A health risk prevalence level map is generated for the given geographical area illustrating current and future health risk prevalence levels for each health risk at a plurality of locations within the given geographical area. Personal health status data are obtained for a given individual along with a proposed travel itinerary f covering at least a portion of the geographical area over a given time duration. The personal health status data, travel itinerary and map generate a personal health risk vulnerability model containing a quantification of vulnerability to the one or more health risks resulting from the travel itinerary.
Owner:IBM CORP
Personal travel health vulnerability navigator
InactiveUS20170351831A1Minimize health vulnerability of individualIncrease the itineraryData processing applicationsHealth-index calculationHealth riskLevel data
Individual health vulnerability is assessed by obtaining health risk prevalence level data containing health risk prevalence levels for one or more health risks over a given geographical area. The health risk prevalence level data to generate for each health risk a prevalence level forecast as a function of time and location. A health risk prevalence level map is generated for the given geographical area illustrating current and future health risk prevalence levels for each health risk at a plurality of locations within the given geographical area. Personal health status data are obtained for a given individual along with a proposed travel itinerary f covering at least a portion of the geographical area over a given time duration. The personal health status data, travel itinerary and map generate a personal health risk vulnerability model containing a quantification of vulnerability to the one or more health risks resulting from the travel itinerary.
Owner:IBM CORP
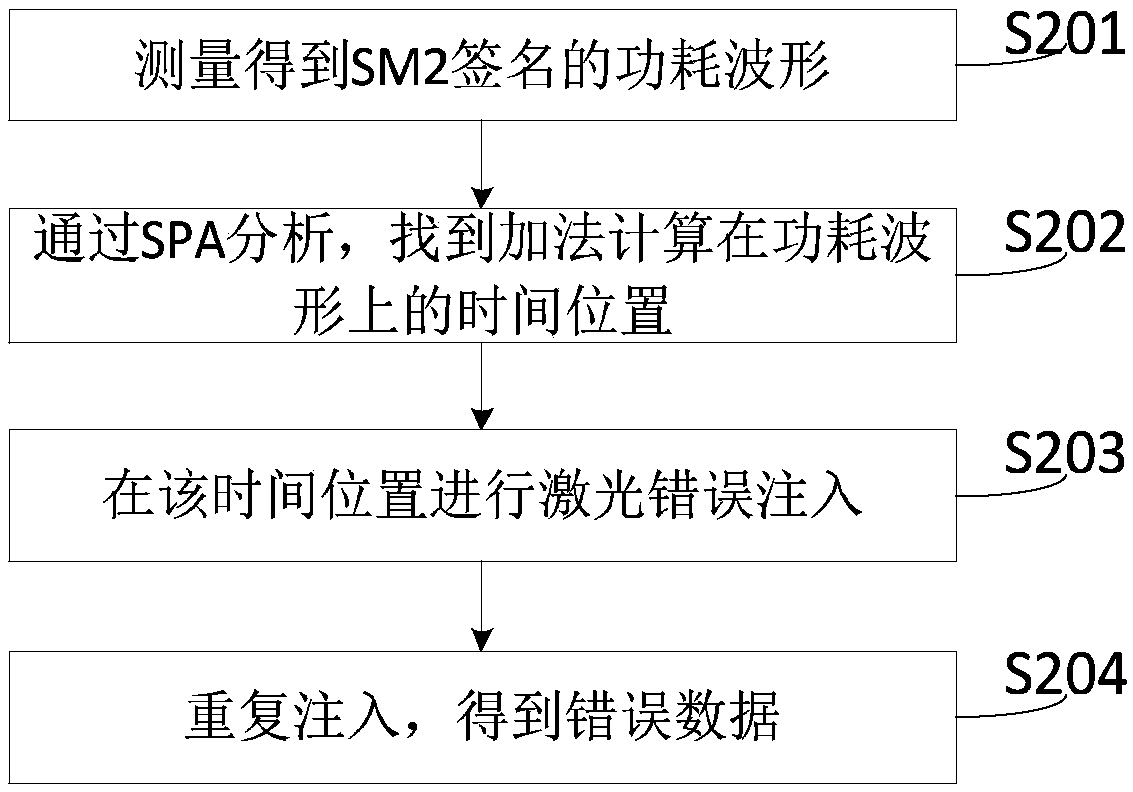
Attack verification and protection method and device for SM2 signature algorithm
ActiveCN109600232AImprove encryption securityKey distribution for secure communicationUser identity/authority verificationValidation methodsInjection attacks
The invention discloses an attack verification and protection method and device for an SM2 signature algorithm. According to the attack verification method, an error injection attack is carried out atan addition position of an SM2 signature algorithm, and the protection method protects an addition and subtraction process in which a random number k participates. The attack verification device forthe SM2 signature algorithm comprises an attack module, and a protection device for the SM2 signature algorithm comprises a protection module. The invention discovers that the protection measures in the prior art ignore the protection of the random number k when s is calculated, regardless of the original formula k-r*dA, or a deformed r + k, an addition and subtraction process in which a random number k participates exists. The existing protection technology does not protect this, so that the existing SM2 encryption algorithm has certain risk vulnerabilities, and the protection method providedby the invention can effectively resist corresponding attack means and prevent information leakage.
Owner:北京智慧云测科技有限公司 +1
Big data-based security interception rule updating method and artificial intelligence security system
InactiveCN113239065AImprove matchImprove the effectiveness of bug fixesDatabase updatingPlatform integrity maintainanceAlgorithmArtificial intelligence
The embodiment of the invention provides a big data-based security interception rule updating method and an artificial intelligence security system, and the method comprises the steps: carrying out the matching of a security interception rule cluster of an information security operation framework for intercepting an application service according to a service risk vulnerability; and screening a plurality of target screening security interception rule clusters for the service risk vulnerability according to the security interception service interval of each security interception rule in the security interception rule clusters, and performing vulnerability pre-repair according to the target screening security interception rule clusters. According to the technical scheme, the security interception rule characteristics of the information security operation framework for intercepting the application service are considered, and the security interception service interval of the security interception rule is also considered, so that the matching degree with the intercepted application service can be improved during vulnerability pre-repair, and the vulnerability repair effect can be improved.
Owner:深圳市合美鑫精密电子有限公司
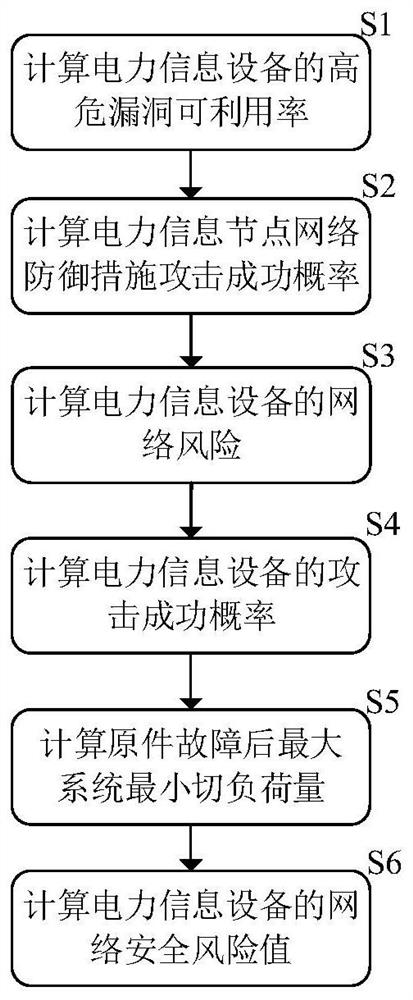
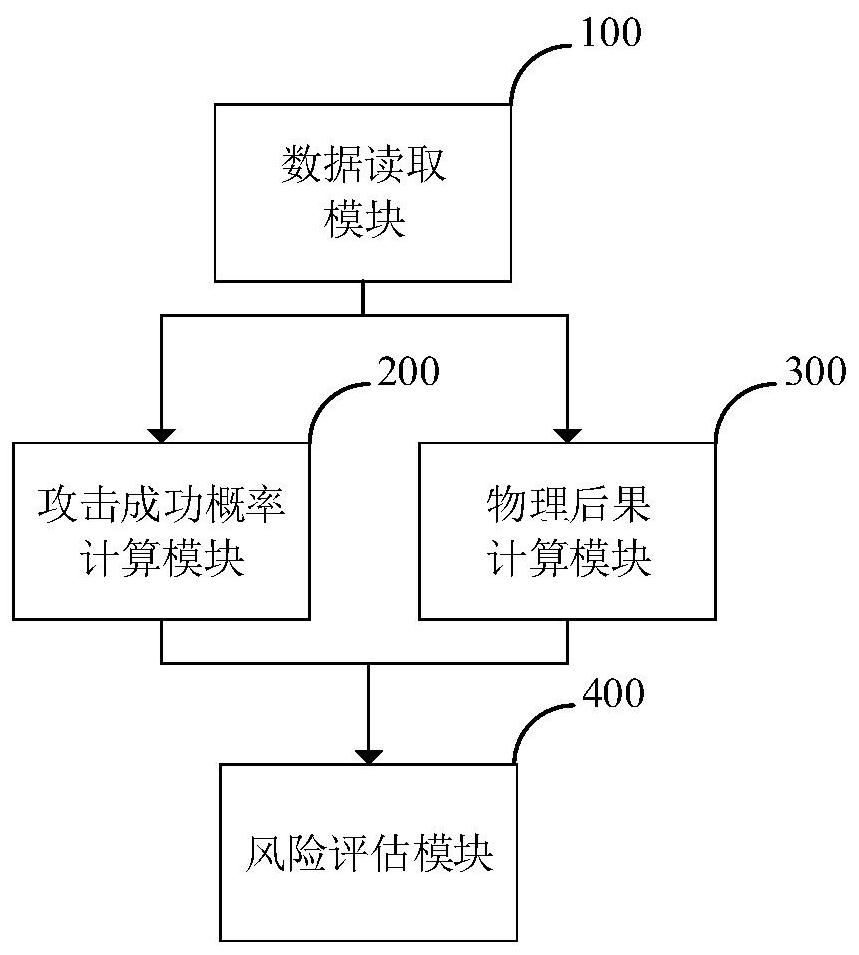
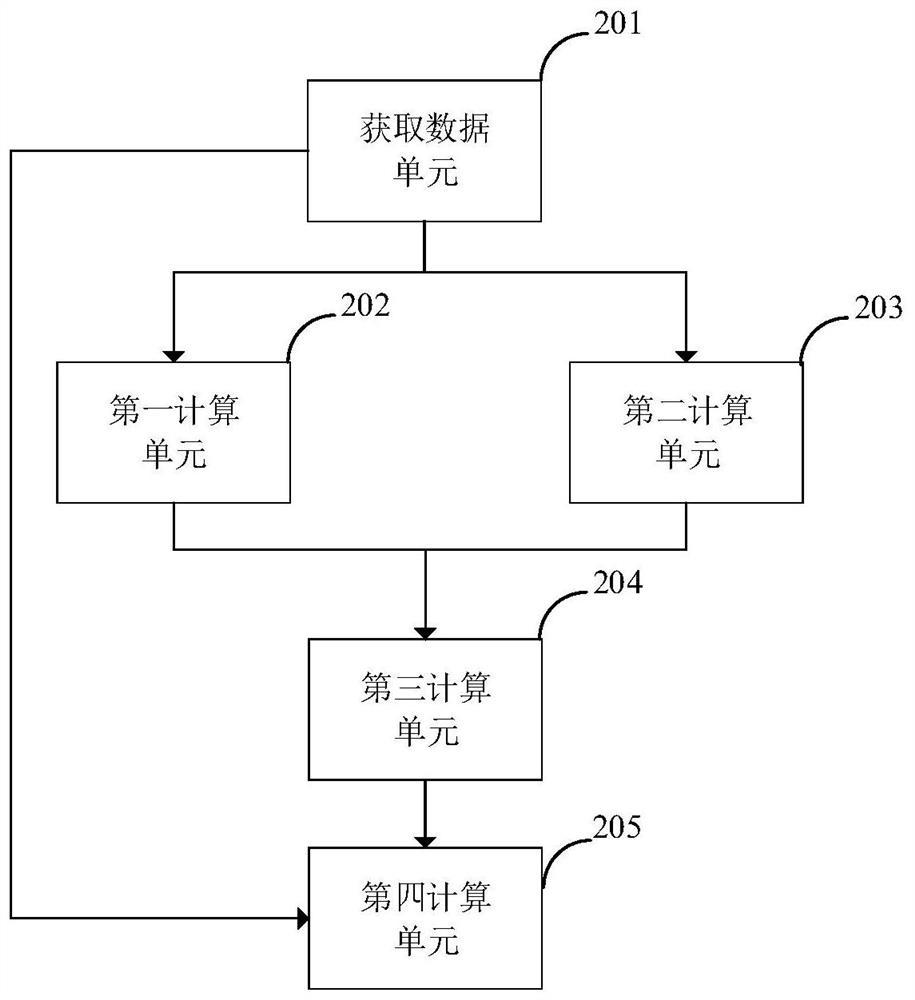
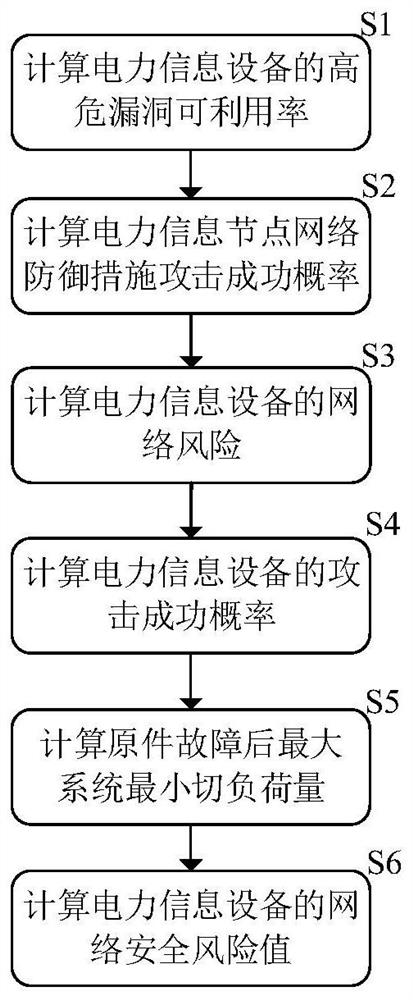
Power network information physical potential safety hazard assessment method and system, and power system
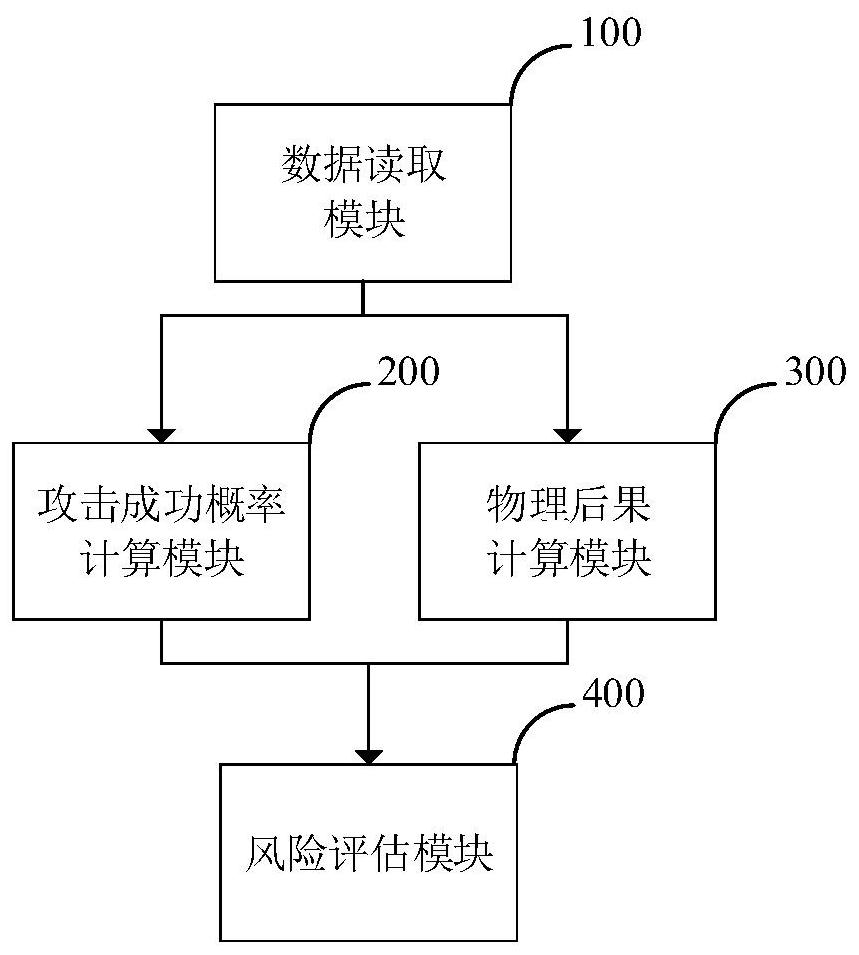
ActiveCN111641596AOvercoming the shortcomings of static analysisImprove accuracyResourcesTransmissionAttackNetwork attack
The invention discloses a power network information physical potential safety hazard assessment method, a power network information physical potential safety hazard assessment system and a power system. The power network information physical potential safety hazard assessment method comprises the steps of: comprehensively considering a basic index, a time index and a network attack capability index, and calculating high-risk vulnerability availability of power information equipment; establishing a power information equipment network security vulnerability assessment model, and calculating an attack success probability of defense measures of the power information equipment; establishing a network attack graph model according to the high-risk vulnerability availability of the power information equipment and the attack success probability of the defense measures of the power information equipment, and calculating an attack success probability of the power information equipment; and establishing a power information equipment-physical element failure association model, and assessing physical consequences caused by network attacks on the power information equipment. The power network information physical potential safety hazard assessment method overcomes the defects that an existing method is insufficient in attack behavior analysis and lacks consideration of power business features, and improves the accuracy and credibility of power network potential safety hazard risk assessment.
Owner:HUNAN UNIV
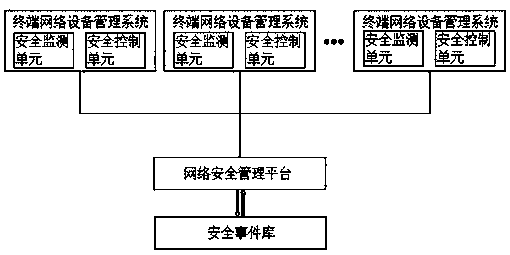
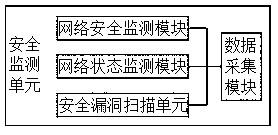
Special network security event management system for enterprise
ActiveCN111147521ARealize acquisitionRealize scanningTransmissionPrivate networkInformation acquisition
The invention discloses a special network security event management system for an enterprise. The system comprises a plurality of terminal network equipment management systems, a network security management platform and a security event library, and is characterized in that the plurality of terminal network equipment management systems are connected with the network security management platform. In the present invention, through a security vulnerability scanning unit, risk vulnerabilities in the terminal network equipment systems as well as software installed in terminal network equipment arescanned; meanwhile, risk vulnerability scanning is carried out on a system server, a router and a switch associated with the terminal network equipment; when network security monitoring and information acquisition are carried out, the security status data of network connected with the terminal network equipment is acquired in time, information acquisition of the terminal network equipment is realized, and security scanning of associated equipment of the terminal network equipment is also realized, so that the acquired information is more comprehensive, and comprehensive and effective network security management is realized.
Owner:深圳市高德信通信股份有限公司
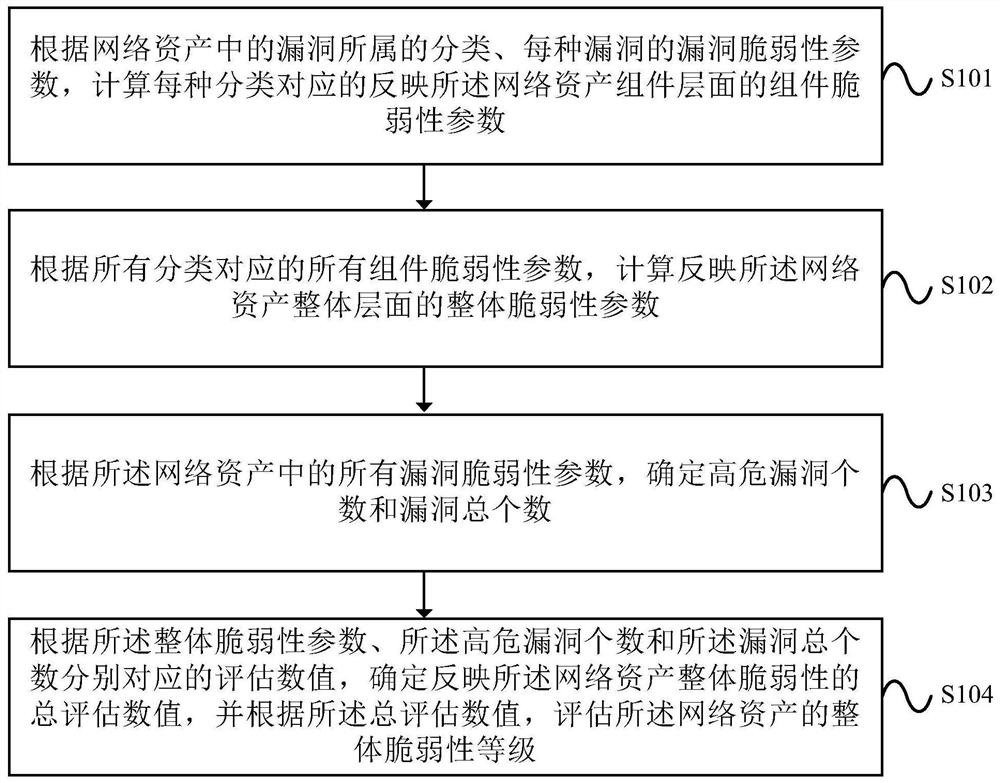
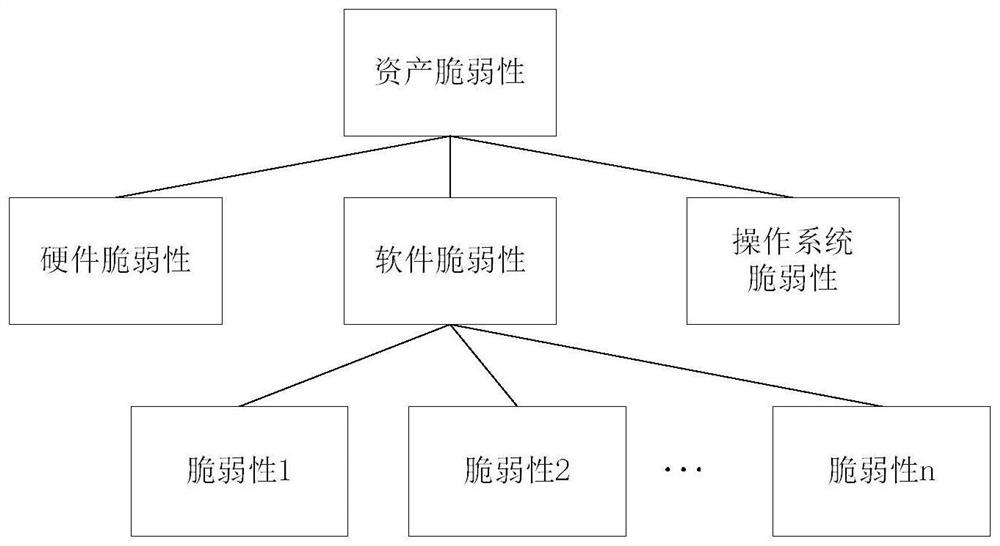
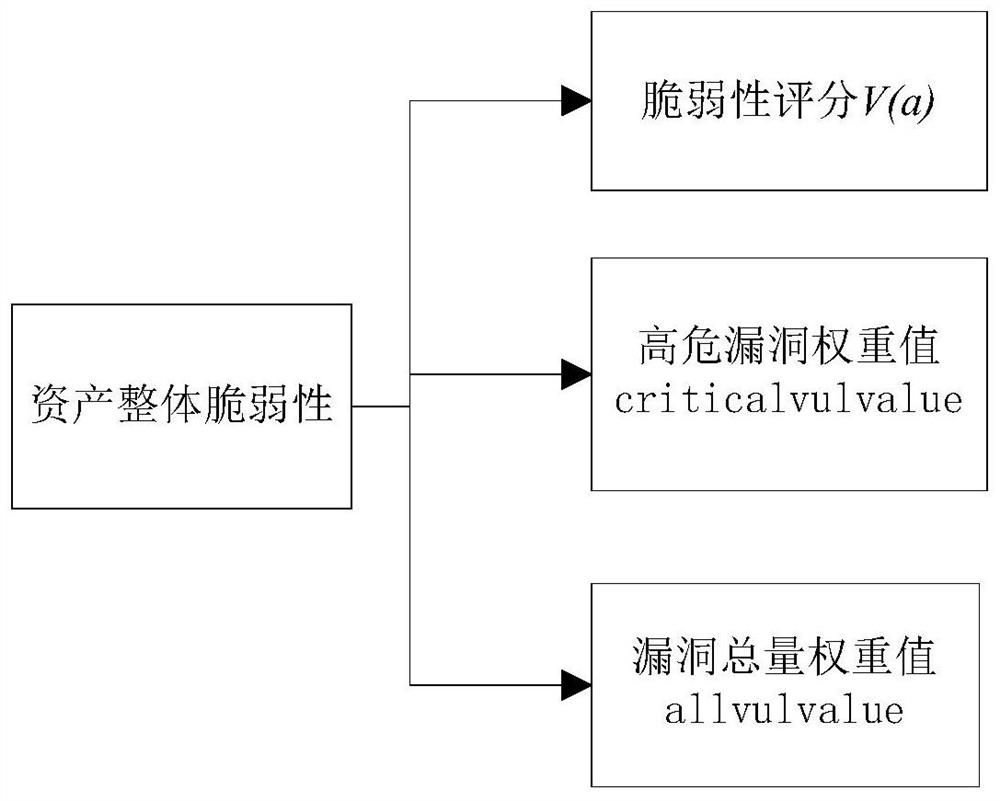
Method and device for evaluating network assets
InactiveCN112087408AAccurate assessmentComprehensive assessmentPlatform integrity maintainanceTransmissionComputer networkReliability engineering
The embodiment of the invention provides a method and a device for evaluating network assets, and the method comprises the steps: calculating a component vulnerability parameter, reflecting a networkasset component level, corresponding to each classification according to the classification of vulnerabilities in the network assets and the vulnerability parameter of each vulnerability; according toall the component vulnerability parameters corresponding to all the classifications, calculating overall vulnerability parameters reflecting the overall level of the network assets; determining the number of high-risk vulnerabilities and the total number of vulnerabilities according to all vulnerability parameters in the network assets; and determining a total evaluation value reflecting the overall vulnerability of the network assets according to the overall vulnerability parameters, the number of the high-risk vulnerabilities and the evaluation values corresponding to the total number of the vulnerabilities, and evaluating the overall vulnerability level of the network assets according to the total evaluation value. The device executes the method. According to the method and the deviceprovided by the embodiment of the invention, the vulnerability of the network assets can be accurately and comprehensively evaluated.
Owner:POTEVIO INFORMATION TECH
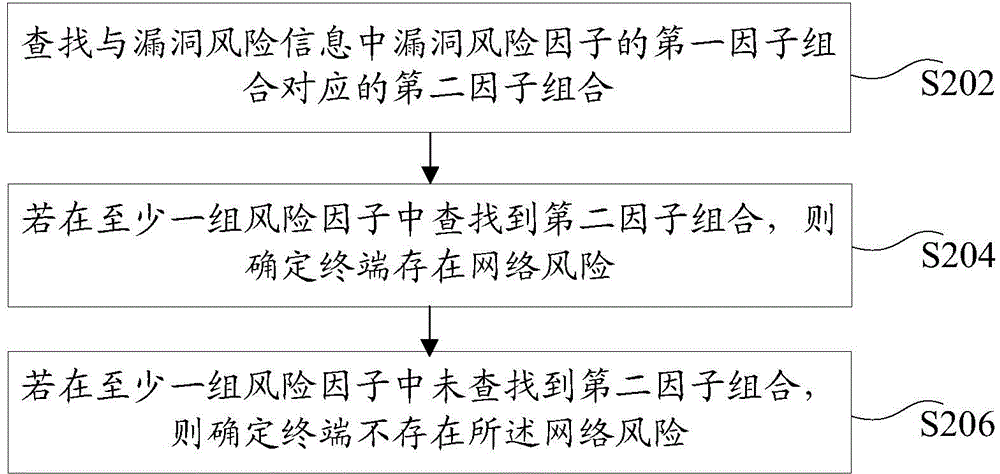
Processing method and device of vulnerability risks of automatic information system
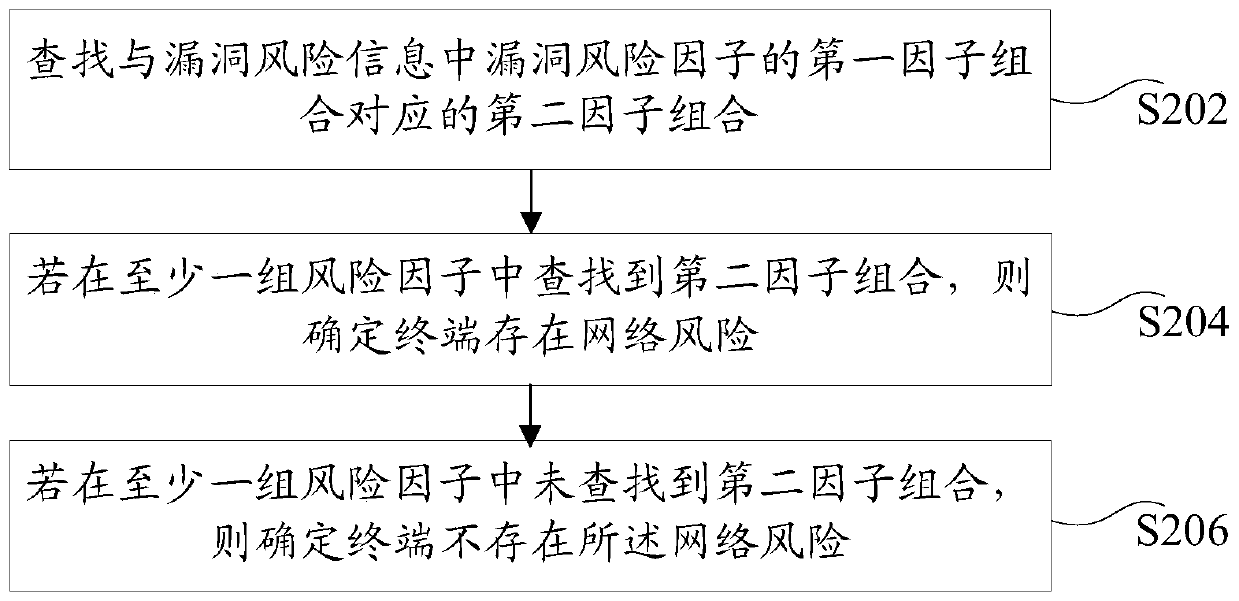
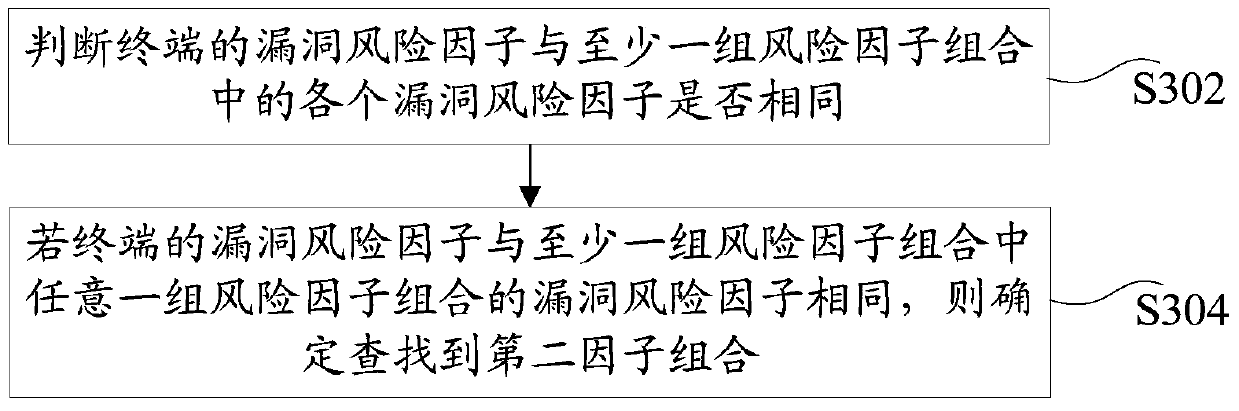
ActiveCN106156627AIncrease diversityImprove accuracyPlatform integrity maintainanceRisk levelComputer science
The invention discloses a processing method and device of vulnerability risks of an automatic information system. The method includes the steps of issuing detecting scripts to all terminals in the information system; obtaining vulnerability risk information of all the terminals, wherein all the terminals execute the detecting scripts to obtain the risk information, and the vulnerability risk information is used for depicting one or more vulnerability risk factors of all the terminals; determining whether network risks exist in the terminals on the basis of the vulnerability risk factors; if yes, obtaining the risk levels of the terminals; generating the prompting information of the risk levels of the terminals. The technical problem that in the prior art, the risk vulnerability of a desktop computer can not be effectively evaluated, so troubleshooting is difficult after the desktop computer fails is solved, and the effect of improving the failure troubleshooting efficiency of the desktop computer is achieved.
Owner:SEMICON MFG INT (SHANGHAI) CORP
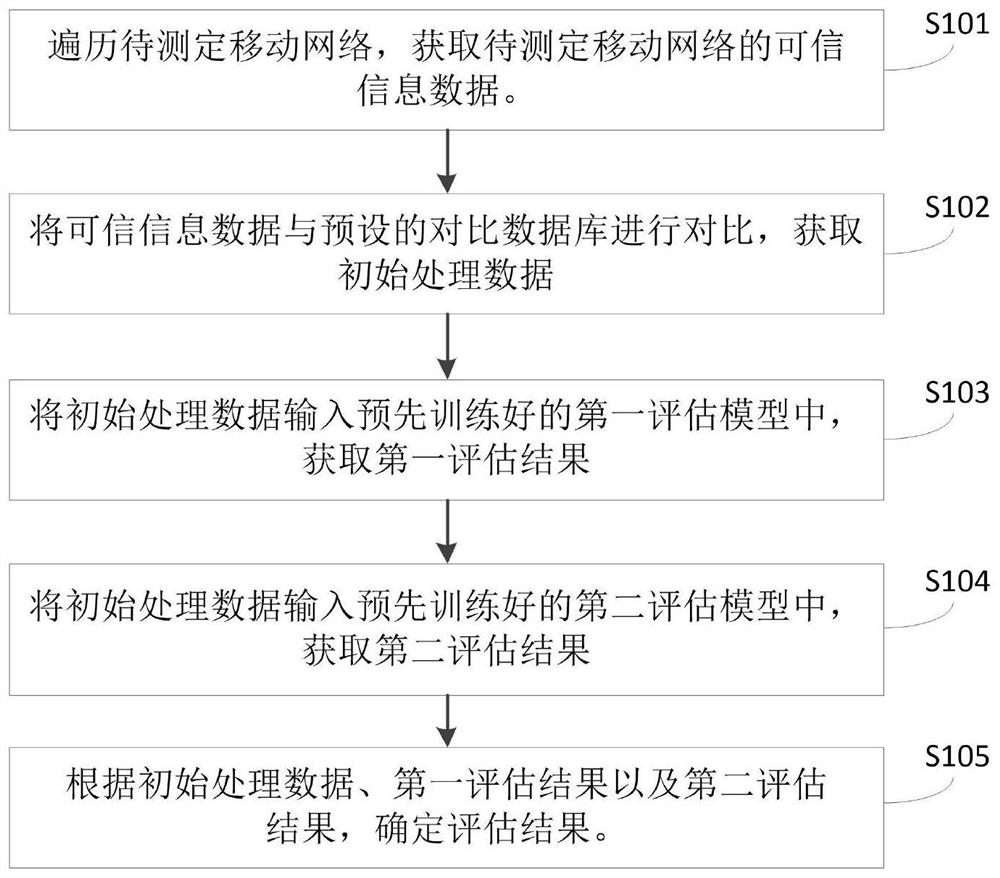
Method and device for evaluating risk vulnerability of mobile network
PendingCN113378158AConform to the characteristicsTargetedPlatform integrity maintainanceNeural architecturesEvaluation resultData mining
The invention provides a method and device for evaluating risk vulnerability of mobile network. The method provided by the invention comprises the steps of traversing a to-be-evaluated mobile network, and obtaining basic information data of the to-be-evaluated mobile network; comparing the basic information data with a preset comparison database to obtain initial processing data, wherein the comparison database is established according to historical information data and historical determination results of experts; inputting the initial processing data into a pre-trained first evaluation model to obtain a first evaluation result; inputting the initial processing data into a pre-trained second evaluation model to obtain a second evaluation result, wherein the second evaluation model comprises a corresponding relationship between the initial processing data and the evaluation result; and determining an evaluation result according to the initial processing data, the first evaluation result and the second evaluation result. According to the embodiment of the invention, the comparison database is adopted, and subjective factors are introduced in a mobile network risk assessment process, so that the evaluation process is more targeted.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
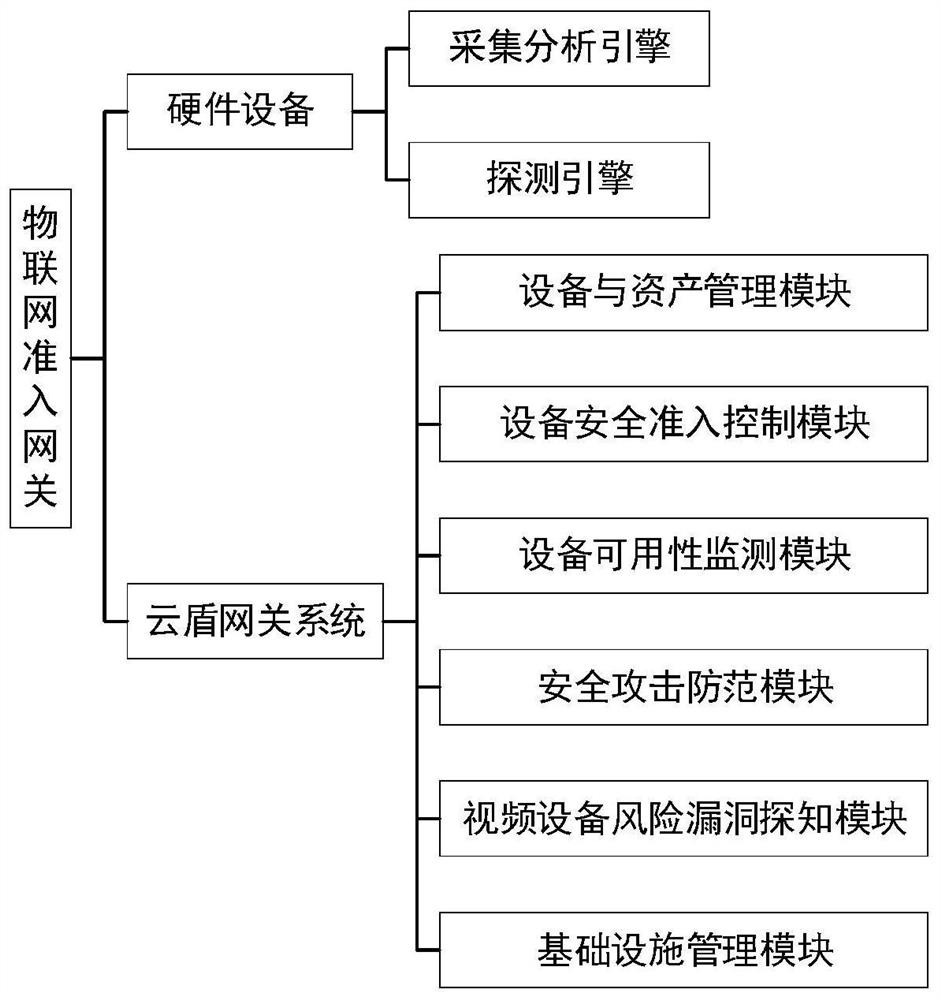
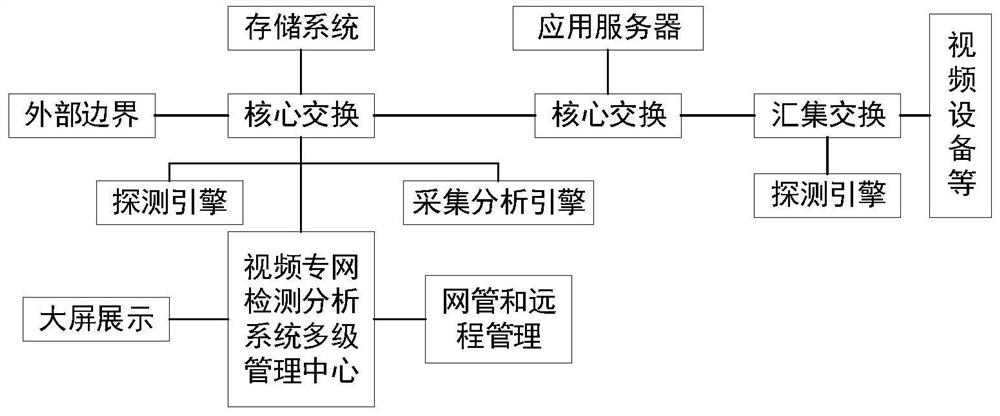
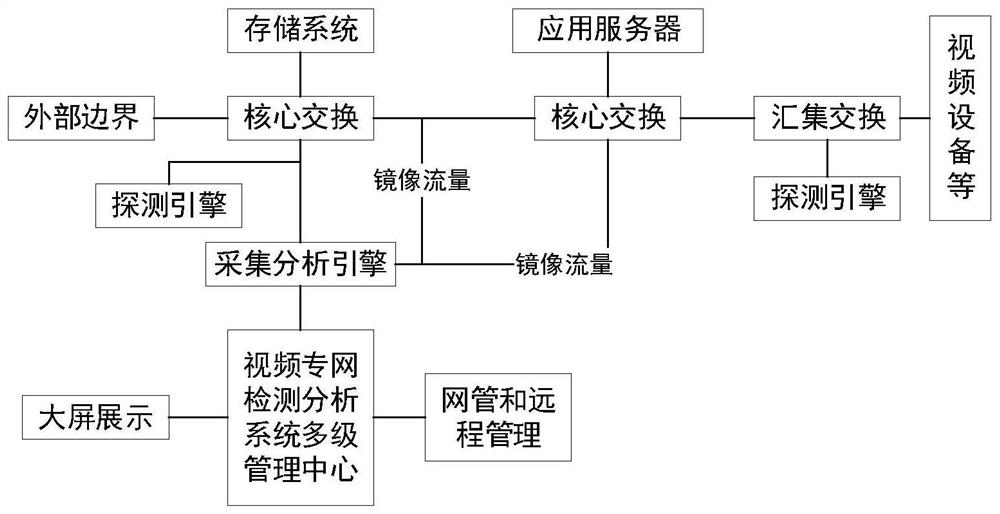
Internet of Things admission gateway for video network system
PendingCN112565202AEfficient managementGuaranteed closureCharacter and pattern recognitionTransmissionPrivate networkThe Internet
The invention discloses an Internet of Things admission gateway for a video network system. The Internet of Things admission gateway comprises hardware equipment and a cloud shield gateway system, wherein the hardware equipment comprises an acquisition and analysis engine and a detection engine; the cloud shield gateway system comprises a device and asset management module, a device security admission control module, a device availability monitoring module, a security attack prevention module, a video device risk vulnerability detection module and an infrastructure management module. The system integrates the functions of equipment management, security admission, availability monitoring, attack prevention, vulnerability detection, equipment automatic discovery, equipment state detection, vulnerability automatic detection, access automatic discrimination, behavior automatic analysis, violation automatic blocking and the like, three-dimensional monitoring is formed from boundaries to core data, deep defense is established, security operation management is enhanced, functions of clear assets in the video private network at a glance, real-time alarm of equipment faults, real-time control of safety risks, timely blocking of illegal invasion and the like are realized, and the problem of safe operation of the video private network is solved.
Owner:INFORMATION & COMMNUNICATION BRANCH STATE GRID JIANGXI ELECTRIC POWER CO +1
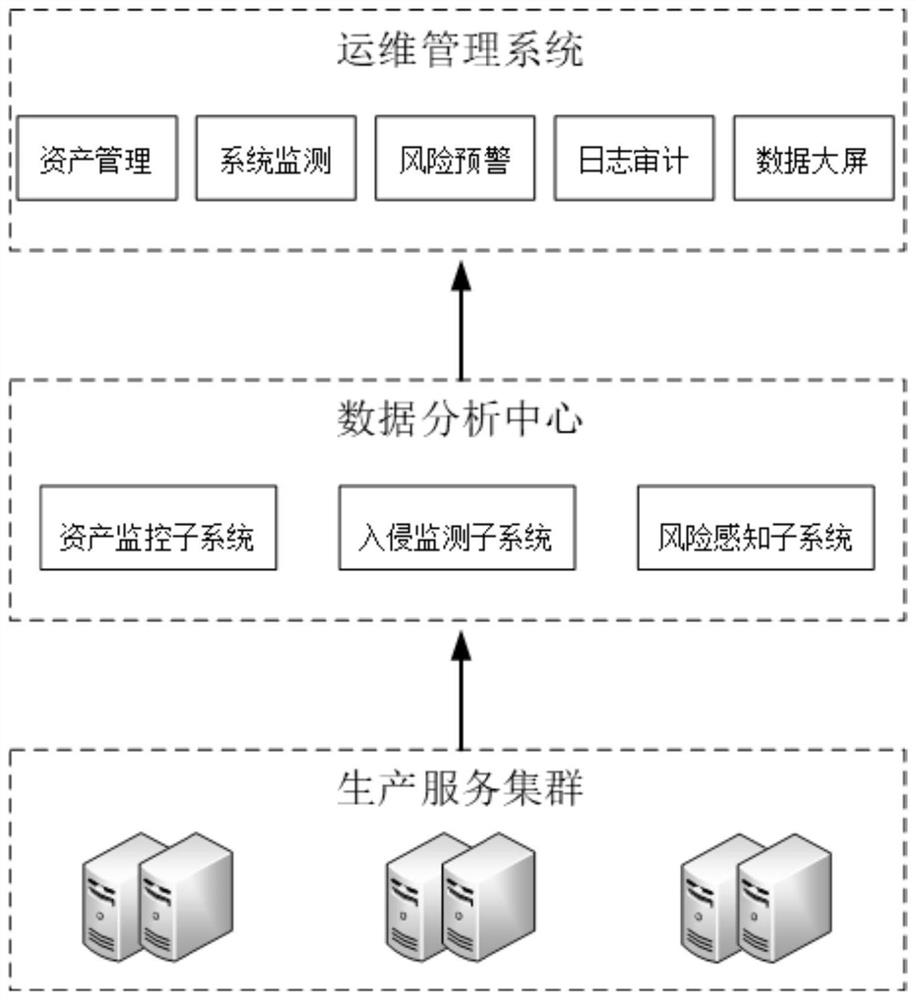
Server asset management system based on integrated monitoring
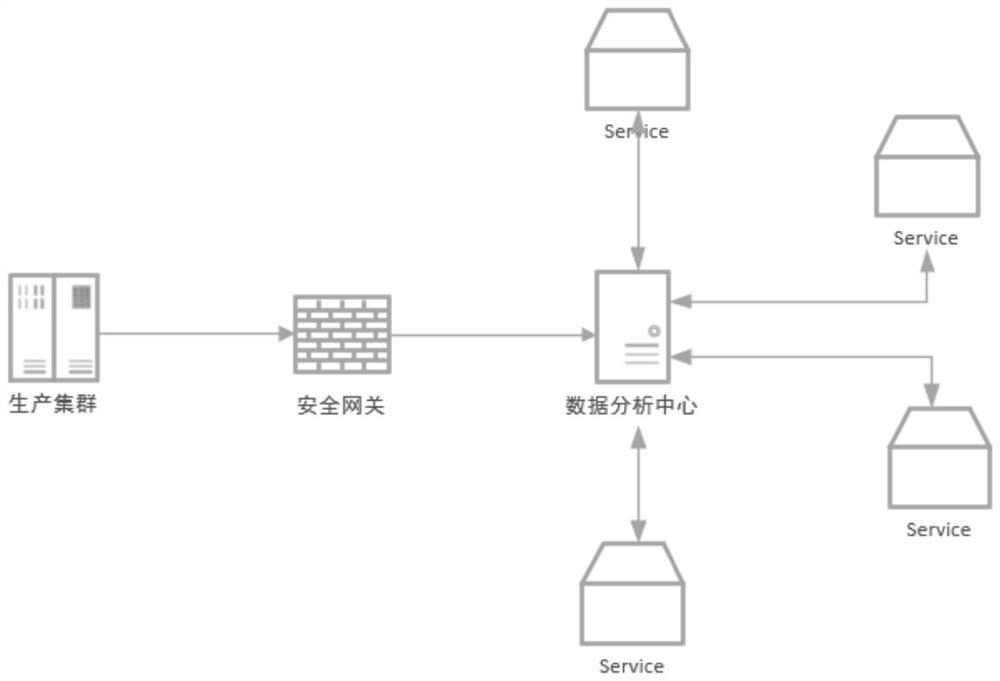
PendingCN113556348ATo achieve the purpose of increasing revenue and reducing expenditureHardware monitoringPlatform integrity maintainanceData classIntegrated monitoring
The invention provides a server asset management system based on integrated monitoring. The server asset management system comprises a production service cluster, a data analysis center and an operation and maintenance management system, wherein the production service cluster is composed of a plurality of independent servers and collects data through service nodes and data nodes; after receiving the data, the data analysis center distributes the data to an asset monitoring subsystem, an intrusion monitoring subsystem and a risk perception subsystem for processing according to data types, and sends a processing result to the operation and maintenance management system; the asset monitoring subsystem judges whether the server has the problem of performance excess or performance shortage; the intrusion monitoring subsystem mainly aims at network access flow data, and judges whether an intrusion risk exists or not according to a network access behavior; the risk perception subsystem mainly aims at network flow data and risk vulnerabilities of the server; and the operation and maintenance management system allocates the processing results to different management subsystems according to the types of the processing results, and gives corresponding management prompts and operations.
Owner:中能融合智慧科技有限公司
Data export security detection method and detection system
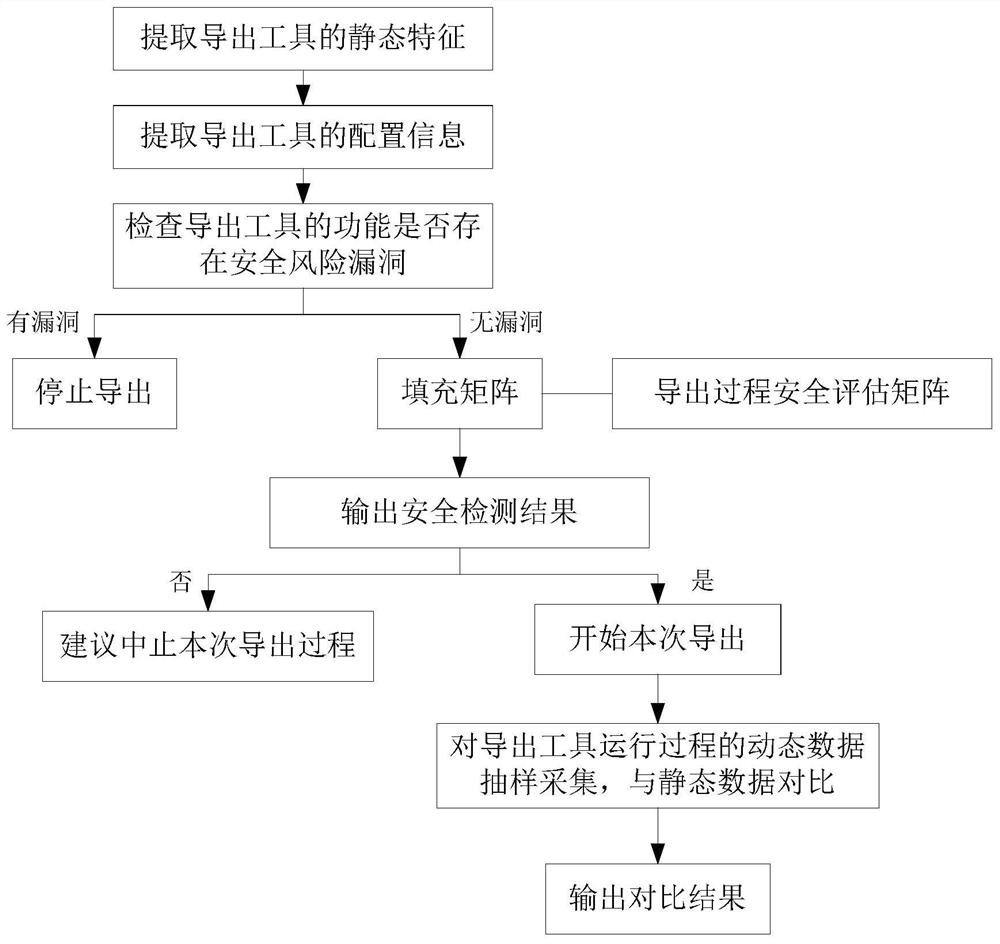
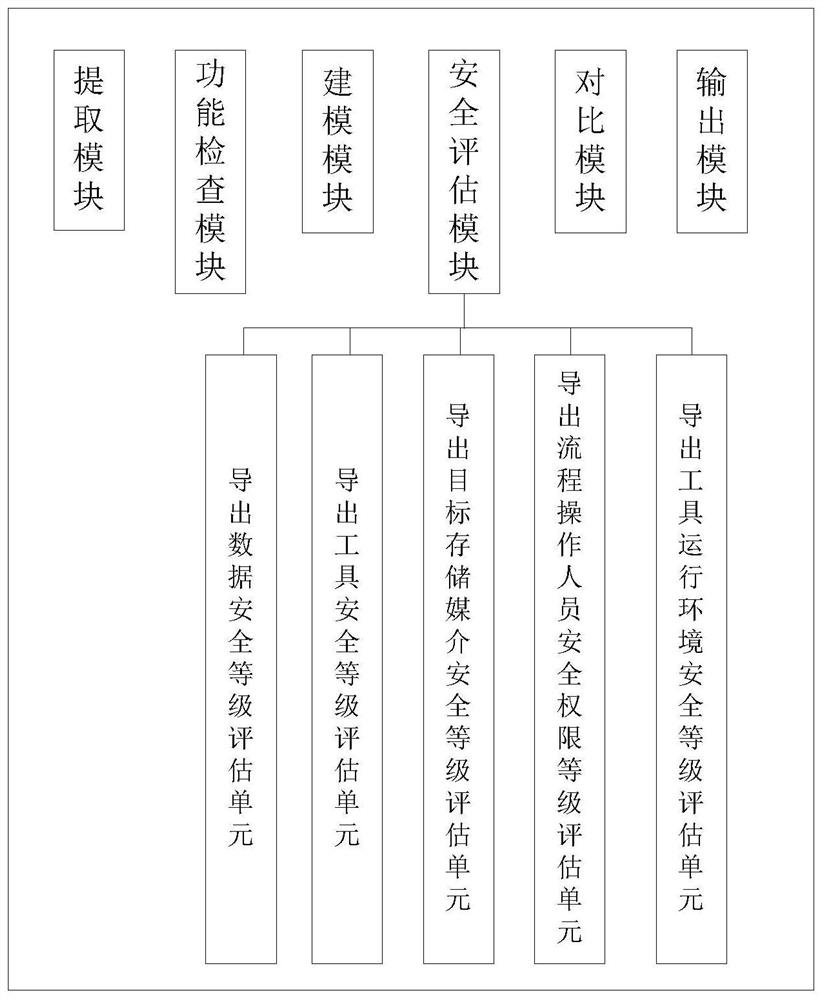
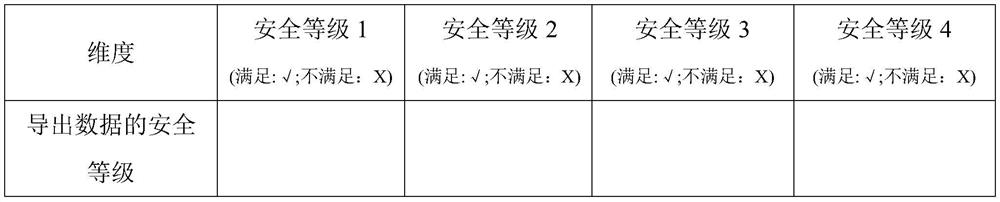
ActiveCN112861141AAddress leak risksReduce risk of leakageDatabase management systemsPlatform integrity maintainanceData miningDynamic data
The invention discloses a data export security detection method and system, and the method comprises the steps: extracting static features and configuration information of an export tool, checking whether the function of the export tool has security risk vulnerabilities or not, filling an export process security evaluation matrix, and outputting a security detection result based on the filled export process security evaluation matrix; sampling and collecting dynamic data in the operation process of the exporting tool in the exporting process, and comparing a sampling and collecting result with static data of the exporting tool. The invention aims to provide the data export security detection method and detection system, so as to solve the problem of data leakage risk in the data export process in the prior art, and achieve the purposes of improving the security and controllability of the data export process and reducing the leakage risk in the data export process.
Owner:湖北宸威玺链信息技术有限公司
Method for actively discovering distributed self-built system and scanning security vulnerabilities
PendingCN112364355ACurbing "Blowout" GrowthReliable data supportWebsite content managementPlatform integrity maintainanceInformatizationEngineering
Owner:BC P INC CHINA NAT PETROLEUM CORP +1
Method, device and system for preventing services from being attacked
ActiveCN102164033BAvoid attackLimit Malicious AttacksMultiple keys/algorithms usageUser identity/authority verificationPlaintextNetwork packet
The invention discloses a method, device and system for preventing services from being attacked, which belong to the technical field of information security. The method comprises the following steps: receiving a service request sent by a client, and issuing verification information to the client, wherein the verification information at least comprises plaintexts generated randomly and user identifications encrypted by private keys; receiving a signature which is returned by the client and encrypted by a public key for verification information; and verifying the legality of the client according to the signature returned by the client, if passing the verification, continuing to serve the client, otherwise, determining that the client is an illegal client, and discarding a data packet sent by the illegal client. The method, device and system disclosed by the invention have the advantages that because the client is subjected to legality verification before being provided with services, no excessive spending is added in the process of verification, and the secret key interaction between a server and a client is not required, the risk vulnerabilities existing in secret key interaction can be avoided, and then the effect of preventing services from being attacked can be achieved.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
Method and system for implementing information security audit based on walk-through test technology
InactiveCN104462988BDigital data protectionPlatform integrity maintainanceGlobal information systemInternet privacy
The invention relates to the technical field of information monitoring, in particular to a walk-through test technique based information security audit implementation method and system. The method includes: recognizing business sensitive information waiting for audit and access right of the business sensitive information; tracking flow paths of the business sensitive information in one or more information systems based on the access right; performing audit analysis on risk vulnerabilities existing in the process that the systems with access right process the business sensitive information according to tracking results; based on audit analysis results of the risk vulnerabilities, acquiring a risk value of the business sensitive information. By the method and system, risks existing in the process that the sensitive information flows in full life circles of the multiple information systems can be monitored.
Owner:STATE GRID CORP OF CHINA +2
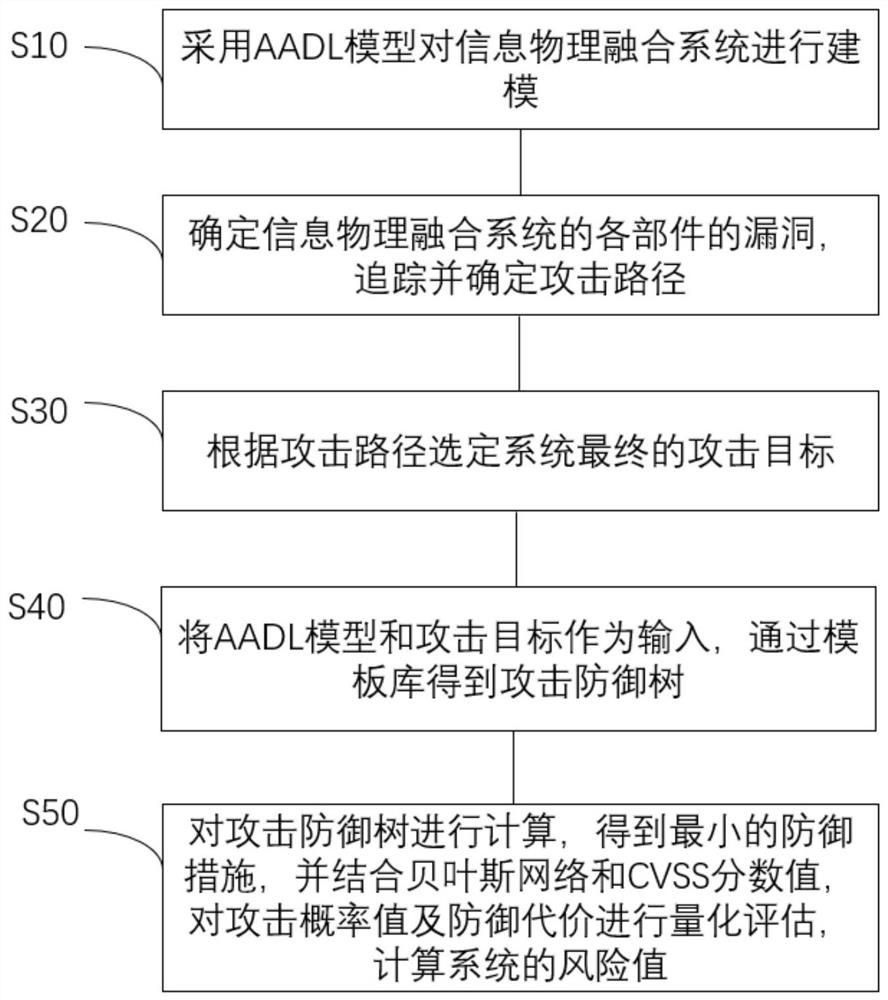
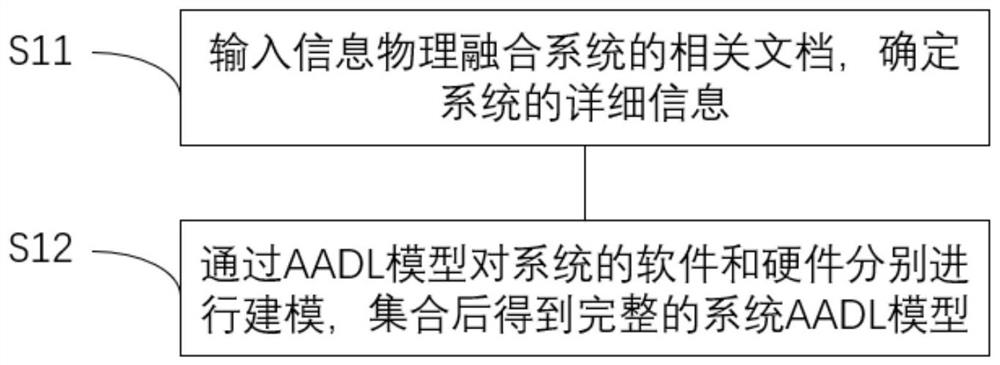
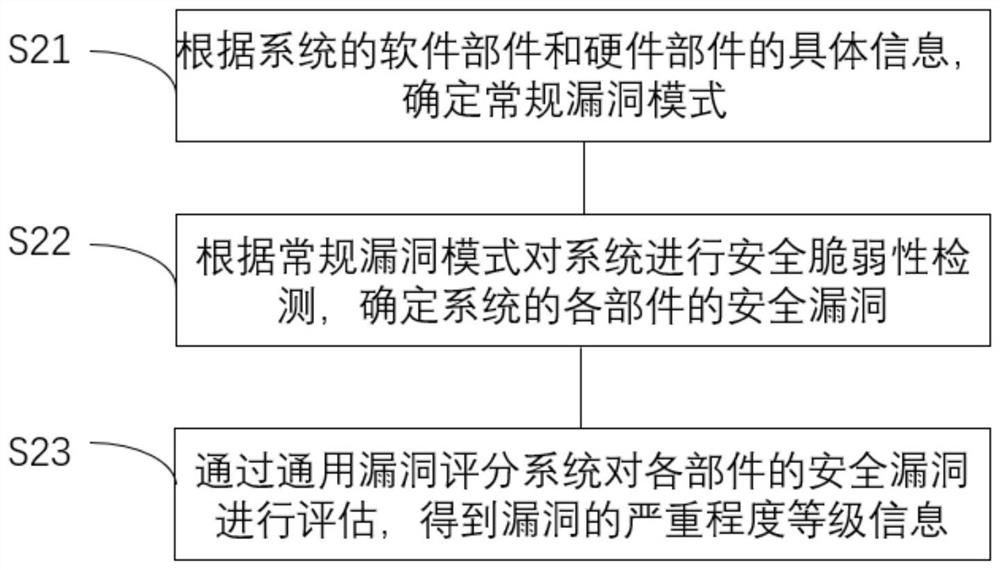
AADL-based automatic generation method of attack defense tree
The invention discloses an AADL-based automatic generation method of an attack defense tree. The method comprises the following steps: modeling an information physical fusion system by adopting an AADL model; determining vulnerabilities of each component of the cyber-physical fusion system, and tracking and determining an attack path; selecting a final attack target of the system according to the attack path; taking the AADL model and an attack target as input, and obtaining an attack defense tree through a template library; and calculating the attack defense tree to obtain a minimum defense measure, performing quantitative evaluation on an attack probability value and a defense cost by combining a Bayesian network and a CVSS score value, and calculating a risk value of the system. The problems that a complex system is difficult to model, and risk vulnerabilities in the system are difficult to determine, track and solve, including the influence of network attacks on a physical system and an information system, are solved.
Owner:NANJING FORESTRY UNIV
Method, system and power system for assessing hidden dangers of information physical security in electric power network
ActiveCN111641596BOvercoming the shortcomings of static analysisImprove accuracyResourcesTransmissionPhysical securityAttack
Owner:HUNAN UNIV
A method and system for determining the sequence of vulnerability rectification based on attack chain
The invention discloses a vulnerability restructuring sequence determining method and system based on attack links. The method comprises the steps of determining an indirect loss coefficient corresponding to each host according to attack link information of an access connection structure; through utilization of the indirect loss coefficient of each host and the direct loss coefficient of each host, determining a total loss coefficient of each host; and determining a final score and a vulnerability restructuring sequence corresponding to each vulnerability according to the total loss coefficient of each host corresponding to each vulnerability and a weight coefficient of each vulnerability. Visibly, different vulnerabilities are scored through combination of the attack link information of an information network; the harmfulness scores of the vulnerabilities and the hosts can be calculated according to the harmfulness of the vulnerabilities themselves and a topological structure, so under the condition that the manpower is limited, the vulnerabilities and hosts badly in need of restoration are distinguished, the operation and maintenance personnel are prevented from excessively paying close attention to the internal network high-risk vulnerabilities hardly possible to be used, while the external network high-risk vulnerabilities with higher risk are ignored.
Owner:STATE GRID CORP OF CHINA +1
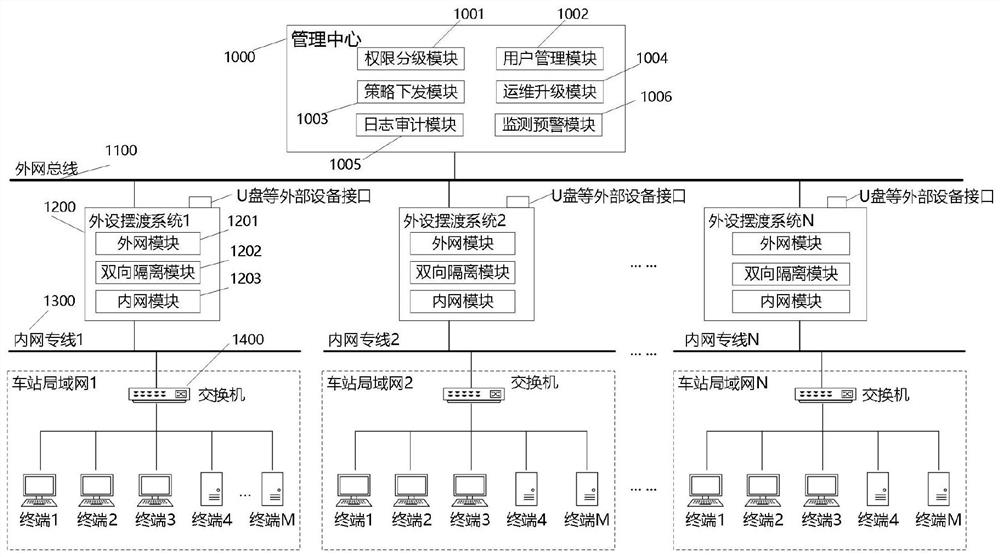
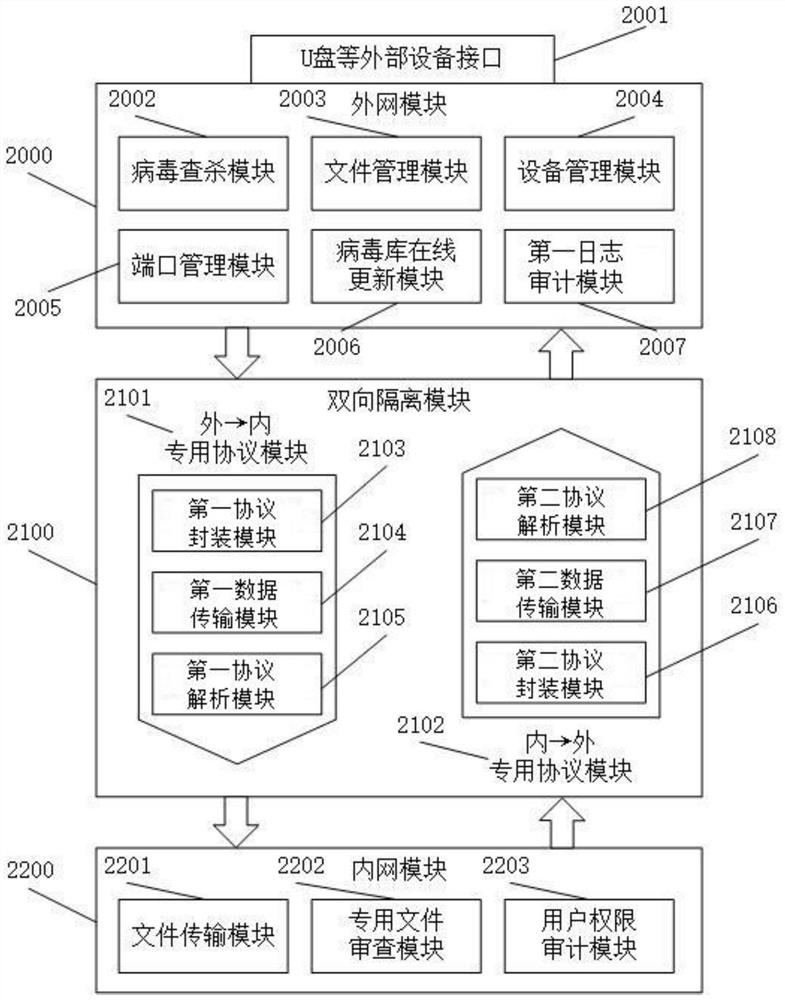
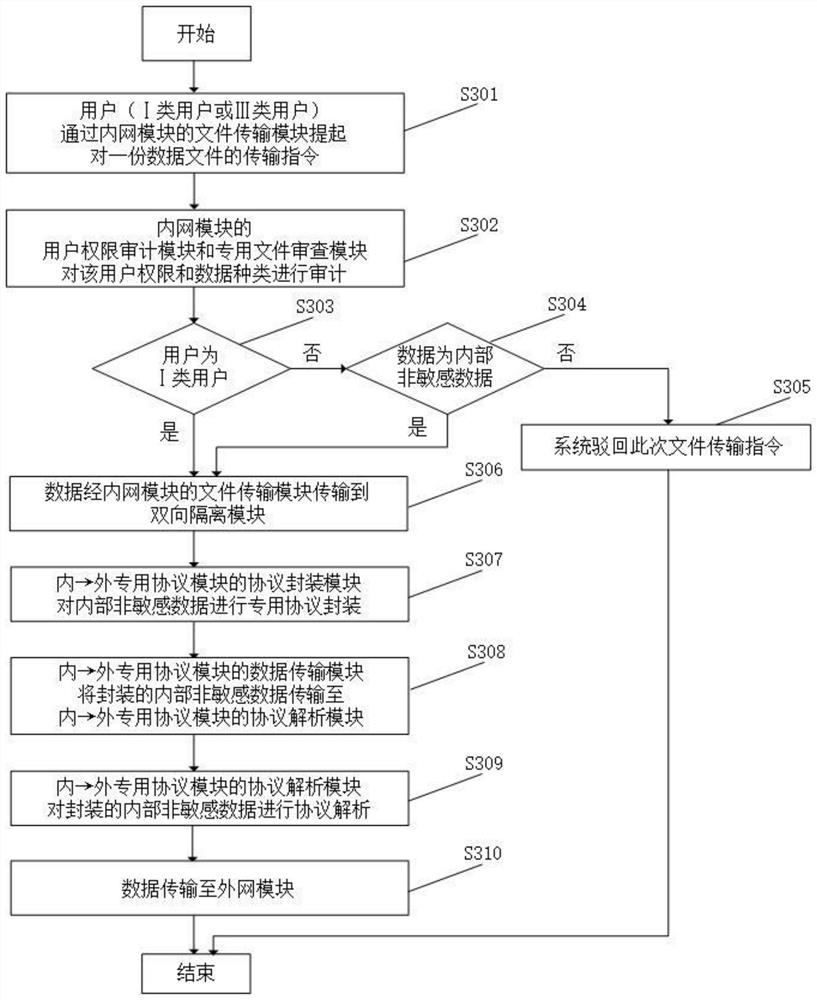
Audit-based data secure transmission method and system from inside to outside, and electronic equipment
PendingCN114710360ACompensate for the risks of complex structuresAvoid outbound risk vulnerabilitiesSecuring communicationData informationEngineering
The invention provides an audit-based secure data transmission method and system from inside to outside and electronic equipment, and the method comprises the steps that an intranet module receives an internal data transmission instruction lifted by a user, and audits user information and internal data information; if the audit is passed, the intranet module transmits internal data; and if the audit is not passed, rejecting the internal data transmission instruction, and ending the operation. According to the data security transmission method, the risk vulnerability that sensitive data in the rail transit system is transmitted outwards can be avoided, so that the risk caused by the complex system structure of the rail transit system is effectively made up, and a technical support is provided for establishing and perfecting a data security migration protection system based on the rail transit system.
Owner:CRSC RESEARCH & DESIGN INSTITUTE GROUP CO LTD
Information processing method based on fingerprint attendance system and fingerprint attendance service system
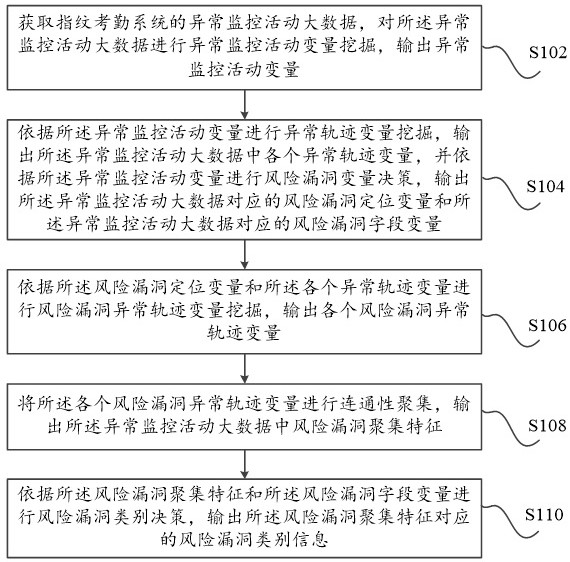
ActiveCN114697143AHigh precisionRegistering/indicating time of eventsCharacter and pattern recognitionInformation processingCategory recognition
The embodiment of the invention discloses an information processing method based on a fingerprint attendance system and a fingerprint attendance service system, and the method comprises the steps: carrying out the abnormal monitoring activity variable mining of abnormal monitoring activity big data, and outputting an abnormal monitoring activity variable; outputting each abnormal trajectory variable in the abnormal monitoring activity big data and a corresponding risk vulnerability positioning variable and a risk vulnerability field variable according to the abnormal monitoring activity variable, and outputting each risk vulnerability abnormal trajectory variable according to the risk vulnerability positioning variable and each abnormal trajectory variable, and performing connectivity aggregation on each risk vulnerability abnormal trajectory variable, and outputting risk vulnerability aggregation features in the abnormal monitoring activity big data, thereby performing comprehensive analysis of risk vulnerability categories by combining the aggregation dimension of the abnormal trajectory of the risk vulnerability and the risk vulnerability field dimension. Compared with a traditional scheme in which analysis is carried out only based on risk vulnerability field variables, the method can improve the accuracy of risk vulnerability category identification.
Owner:苏州英博特力信息科技有限公司
Method and device for processing vulnerability risk of automated information system
ActiveCN106156627BIncrease diversityImprove accuracyPlatform integrity maintainanceRisk levelComputer terminal
The invention discloses a processing method and device of vulnerability risks of an automatic information system. The method includes the steps of issuing detecting scripts to all terminals in the information system; obtaining vulnerability risk information of all the terminals, wherein all the terminals execute the detecting scripts to obtain the risk information, and the vulnerability risk information is used for depicting one or more vulnerability risk factors of all the terminals; determining whether network risks exist in the terminals on the basis of the vulnerability risk factors; if yes, obtaining the risk levels of the terminals; generating the prompting information of the risk levels of the terminals. The technical problem that in the prior art, the risk vulnerability of a desktop computer can not be effectively evaluated, so troubleshooting is difficult after the desktop computer fails is solved, and the effect of improving the failure troubleshooting efficiency of the desktop computer is achieved.
Owner:SEMICON MFG INT (SHANGHAI) CORP
Vulnerability detection method, system, storage medium and electronic equipment of information system
ActiveCN107577947BShorten emergency response timeImprove resource utilization efficiencyPlatform integrity maintainanceAttackInformation system
The invention provides a vulnerability detection method and system for an information system, a storage medium and electronic equipment. The method comprises the steps that all hosts in the information system and ports open in all the hosts are acquired; application programs corresponding to the ports open in all the hosts are acquired; all the hosts and all the application programs are used as information assets to establish an information asset library; the information asset library is traversed according to a key code of an external vulnerability, and information assets matched with the keycode are screened out to serve as a suspected risk library; an attempt attack code is sent to the information assets in the suspected risk library according to an attack code of the external vulnerability; whether execution results returned by all the information assets after the attempt attack code is executed are consistent with a pre-stored result is judged; and if yes, alarm information is sent to the hosts where the information assets are located. When a high-risk vulnerability is reported externally, by use of the vulnerability detection method and system, the position with a risk can be found at the first time in an intranet environment, the vulnerability is automatically verified, and the influenced hosts or applications are output.
Owner:携程旅游信息技术(上海)有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com