Method, device and system for preventing services from being attacked
A technology of being attacked and server, which is applied in the field of information security, can solve problems such as dangerous loopholes, excessive consumption, and high consumption, and achieve the effect of preventing malicious attacks, avoiding dangerous loopholes, and preventing services from being attacked
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
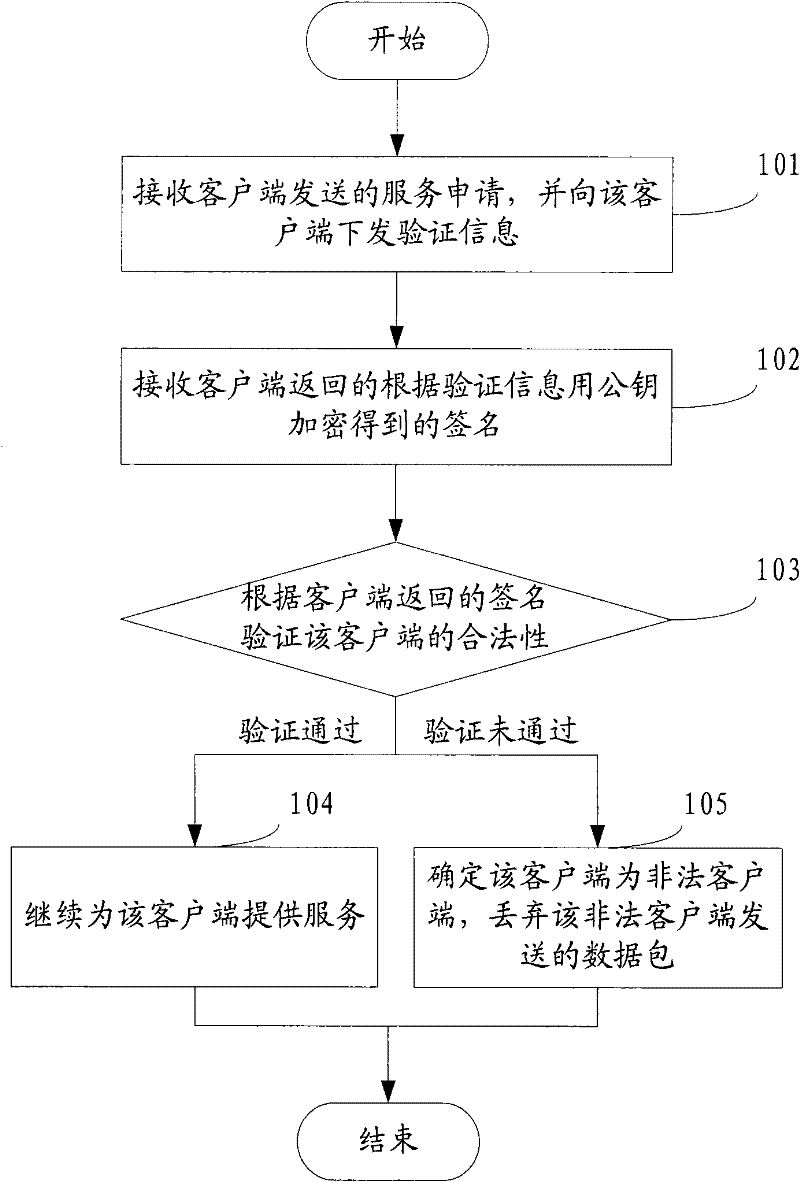
[0056] see figure 1 , this embodiment provides a method for preventing services from being attacked, and the method flow is as follows:
[0057] 101: Receive the service application sent by the client, and send verification information to the client;
[0058] Among them, the verification information includes at least randomly generated plaintext and user identification encrypted with a private key;
[0059] 102: Receive the signature encrypted with the public key according to the verification information returned by the client;
[0060] 103: Verify the legitimacy of the client according to the signature returned by the client. If the verification is passed, execute 104; if the verification fails, execute 105;
[0061] 104: continue to serve the client, and the process ends;
[0062] 105: Determine that the client is an illegal client, discard the data packets sent by the illegal client, and the process ends.
[0063] In the method provided by this embodiment, before provid...
Embodiment 2
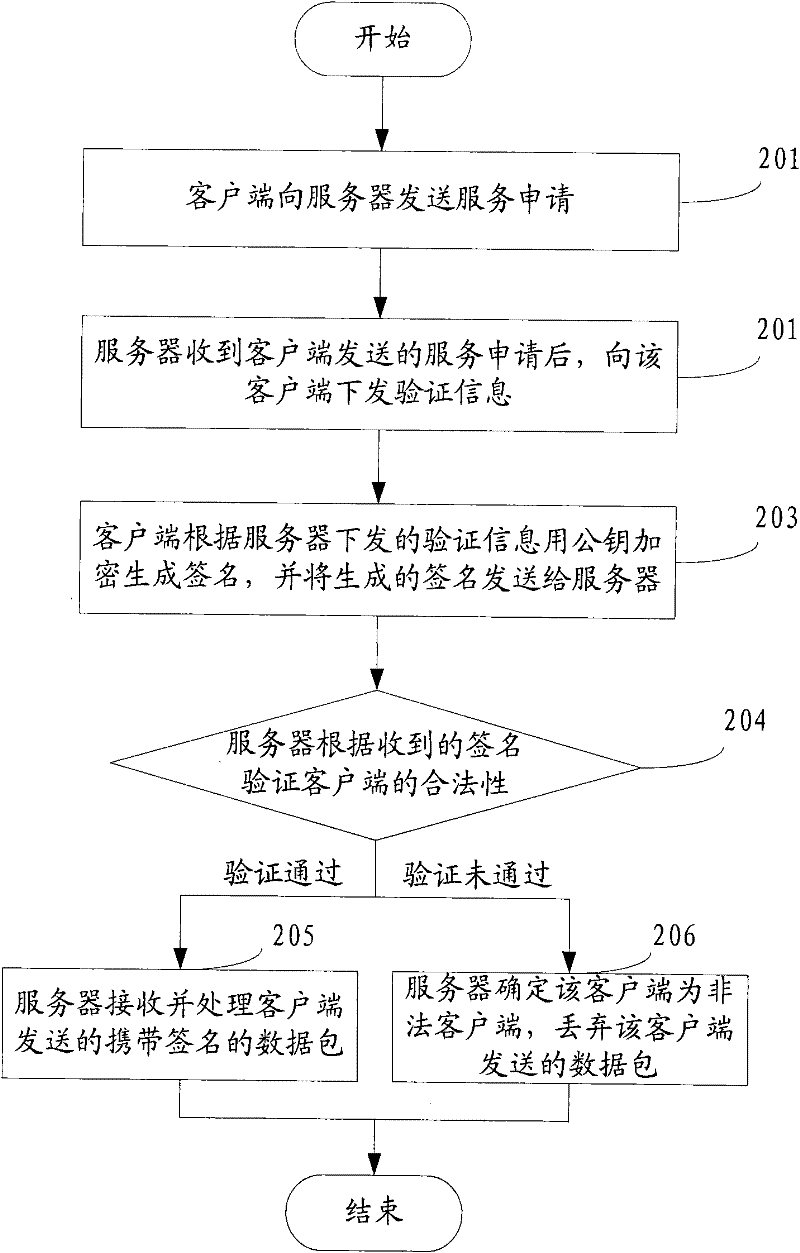
[0065] This embodiment provides a method for preventing services from being attacked. In this method, before providing services to the client, the server first verifies the legitimacy of the client, and after confirming that the client is an illegal client, discards the data packets, so as to achieve the effect of preventing the service from being attacked. see figure 2 , the method flow is as follows:
[0066] 201: The client sends a service application to the server;
[0067] For this step, in order to prevent the service of the server from being attacked, the client needs to submit a service application to the server before accepting the service of the server, so that the server can verify the legitimacy of the client submitting the service application, thereby preventing the service of the server from being attacked .
[0068] 202: After receiving the service application sent by the client, the server sends verification information to the client;
[0069] Among them, ...
Embodiment 3
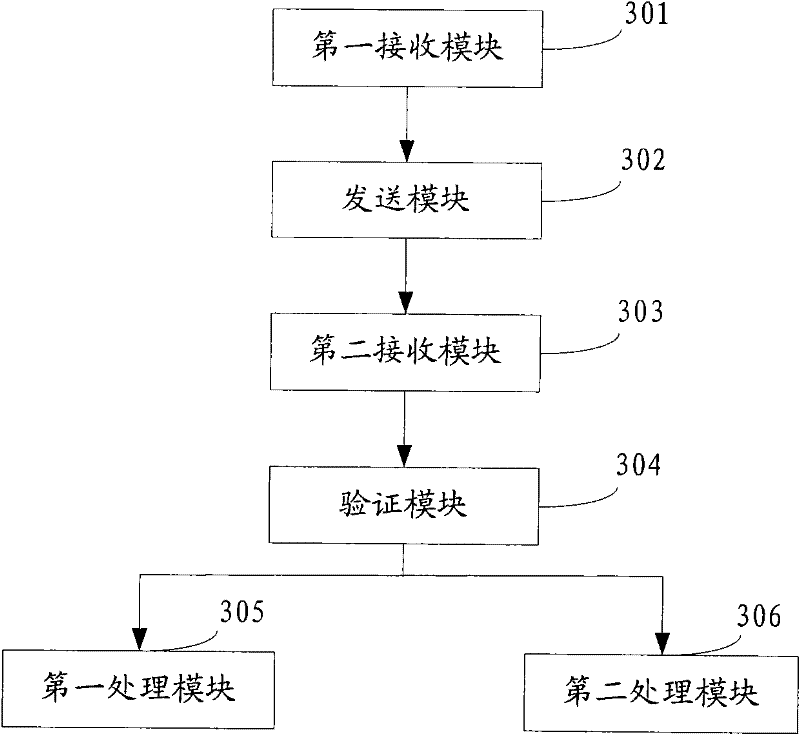
[0082] see image 3 , this embodiment provides a server, the server includes:
[0083] The first receiving module 301 is configured to receive the service application sent by the client;
[0084] The sending module 302 is configured to send verification information to the client after the first receiving module 301 receives the service application sent by the client, and the verification information includes at least randomly generated plaintext and a user ID encrypted with a private key;
[0085] The second receiving module 303 is used to receive the signature obtained by encrypting the verification information sent by the sending module 302 with a public key returned by the client;
[0086] The verification module 304 is configured to verify the legitimacy of the client according to the signature returned by the client received by the second receiving module 303;
[0087] The first processing module 305 is configured to continue serving the client after the client passes t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com