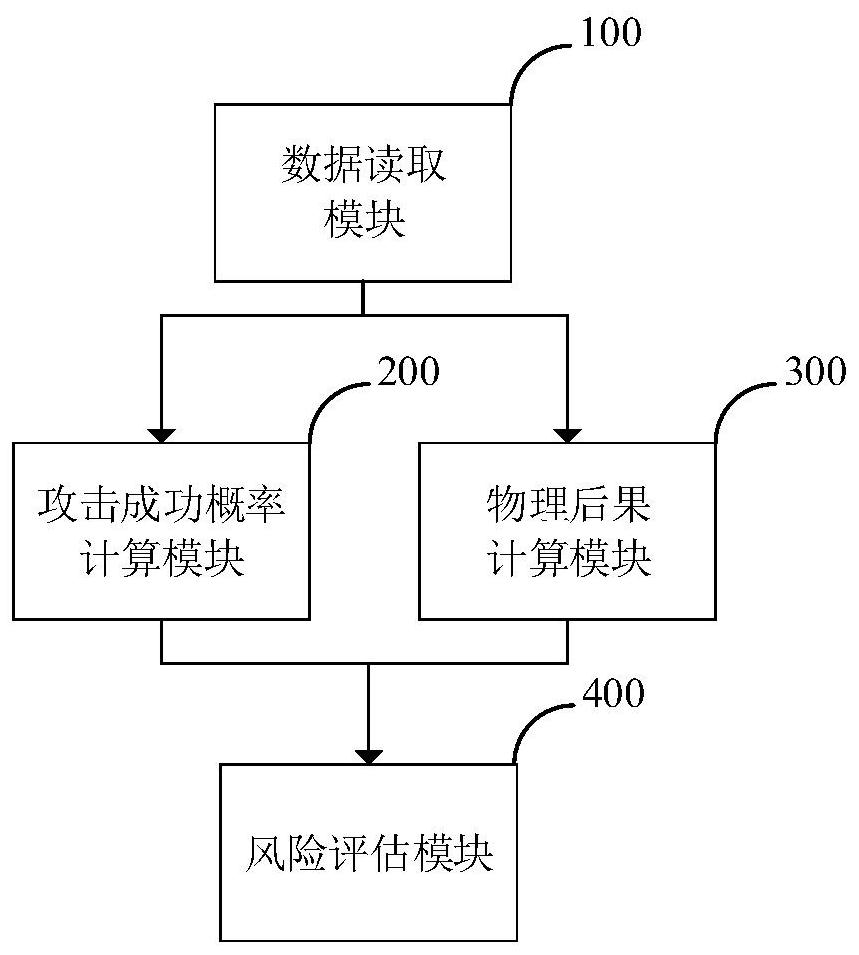
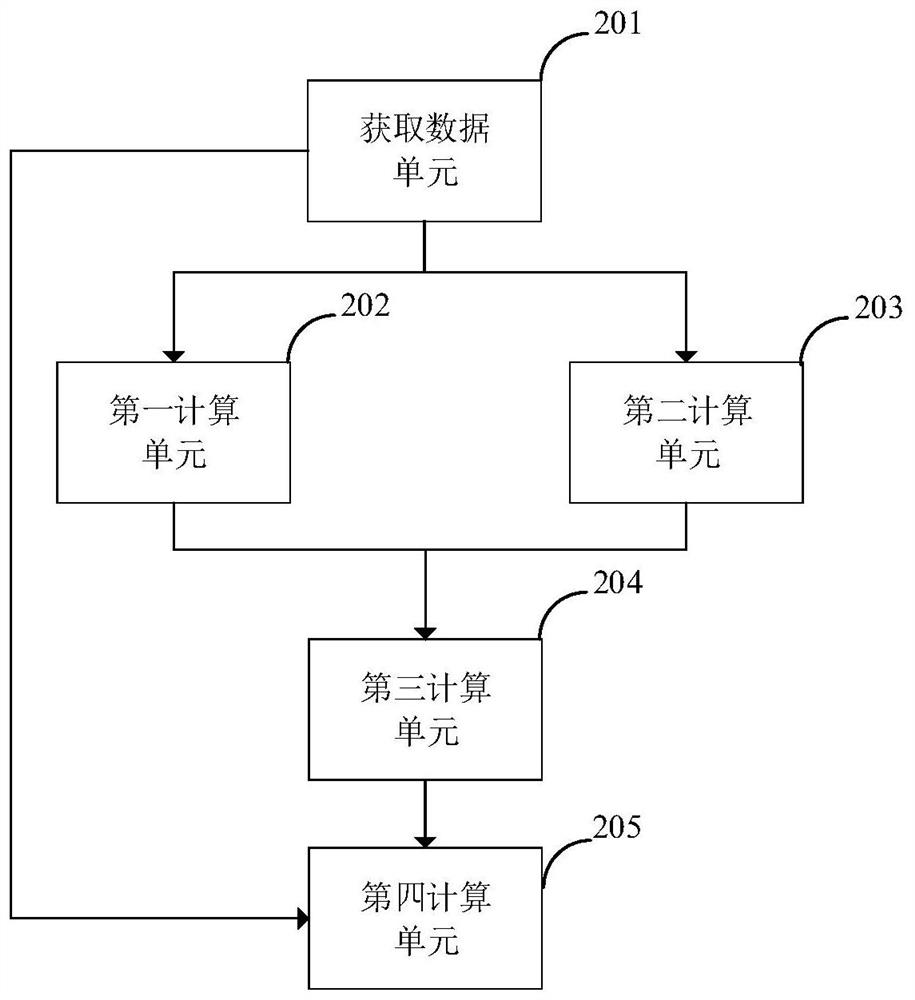
Method, system and power system for assessing hidden dangers of information physical security in electric power network
A technology of power information and information physics, applied in transmission systems, electrical components, data processing applications, etc., can solve the problem of ignoring the probability of security risks, the probability of transmission risks of power information networks, the lack of failure relationship analysis of information equipment and physical components, and the proneness to errors. Reporting and missed reporting, etc., to improve accuracy, overcome the difficulty of dealing with large-scale system risk assessment, and simplify computational complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
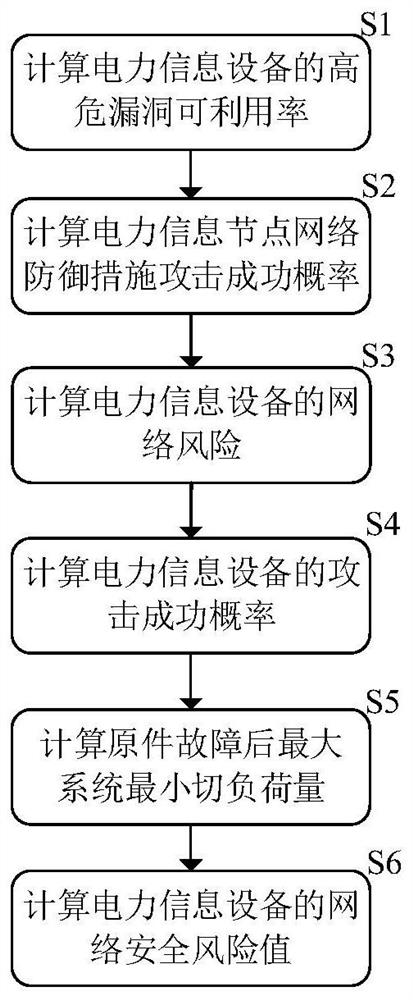
[0077] Further as a preferred embodiment, step S1 includes:
[0078] Step S11: Input the high-risk vulnerability data on each power information device. The basic indicators include vulnerability access method, vulnerability access complexity, and vulnerability access conditions. The time indicator is the vulnerability exposure time. The device host operating system type and the attacker's familiarity with the power system.
[0079] Step S12: According to the basic indicator data in the high-risk vulnerability data on the power information equipment, calculate the basic indicators in the high-risk vulnerability assessment of the power information equipment, the specific formula is as follows:
[0080] Base=AV×AC×AU (3)
[0081] Among them, AV is the vulnerability access method, AC is the vulnerability access complexity, and AU is the vulnerability access condition, and its assignment is provided by the CVSS system.
[0082] Step S13: According to the vulnerability exposure ti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com