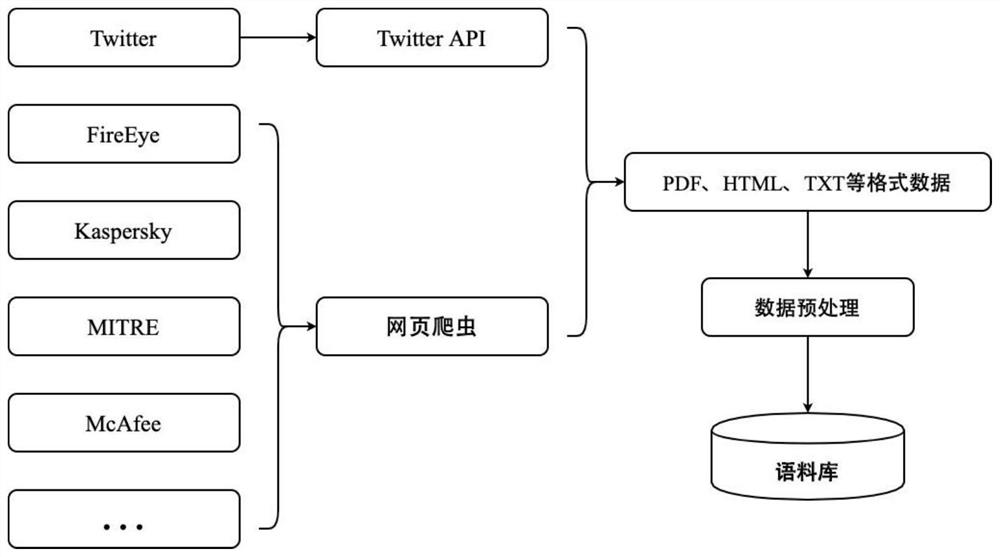
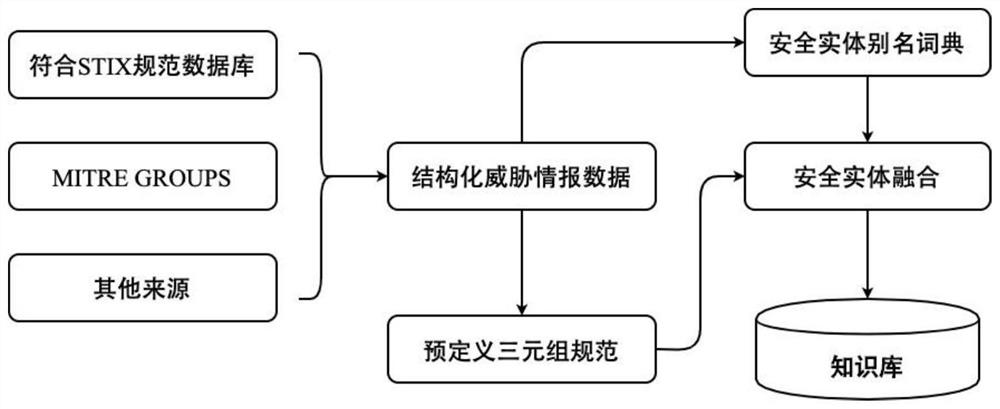
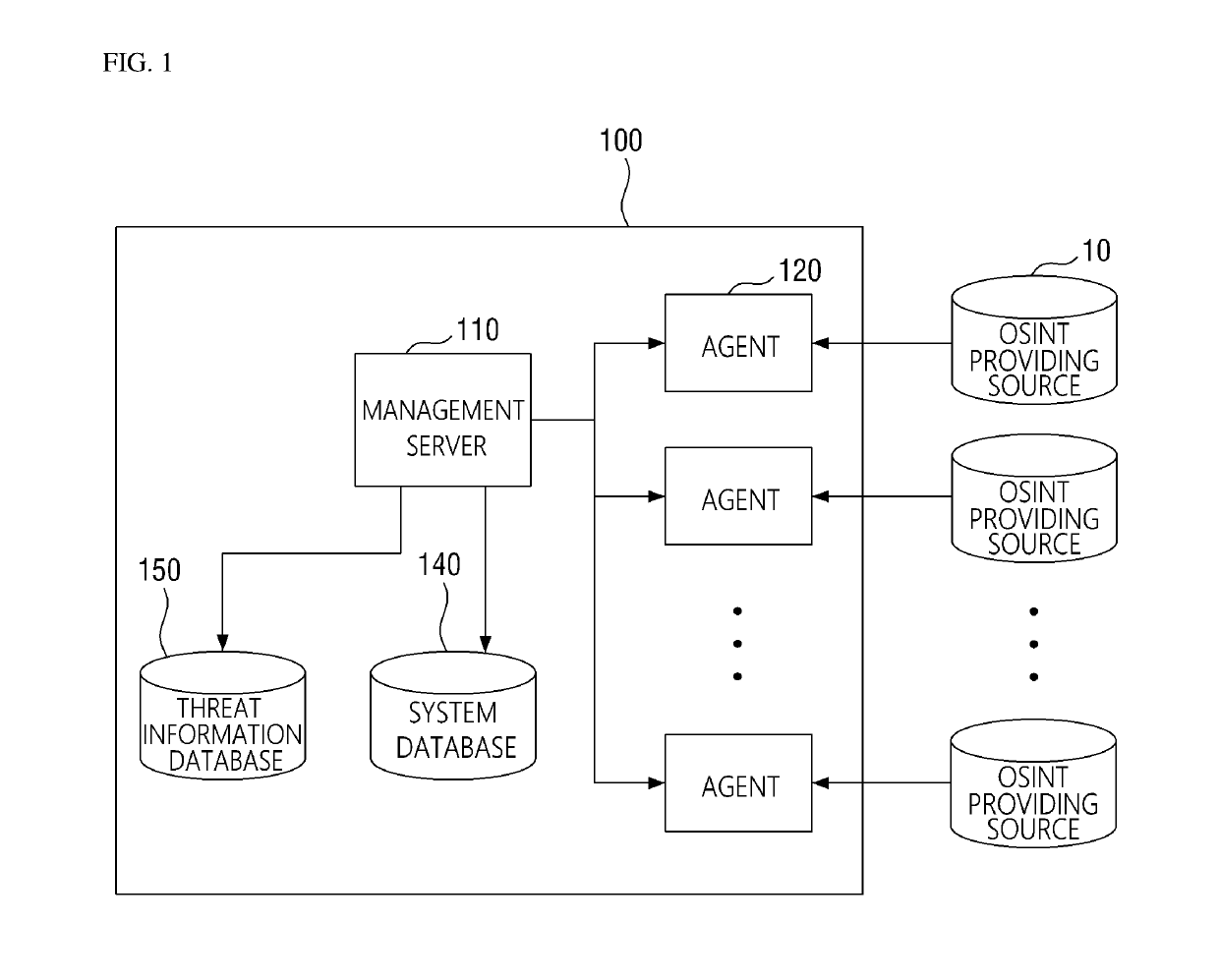
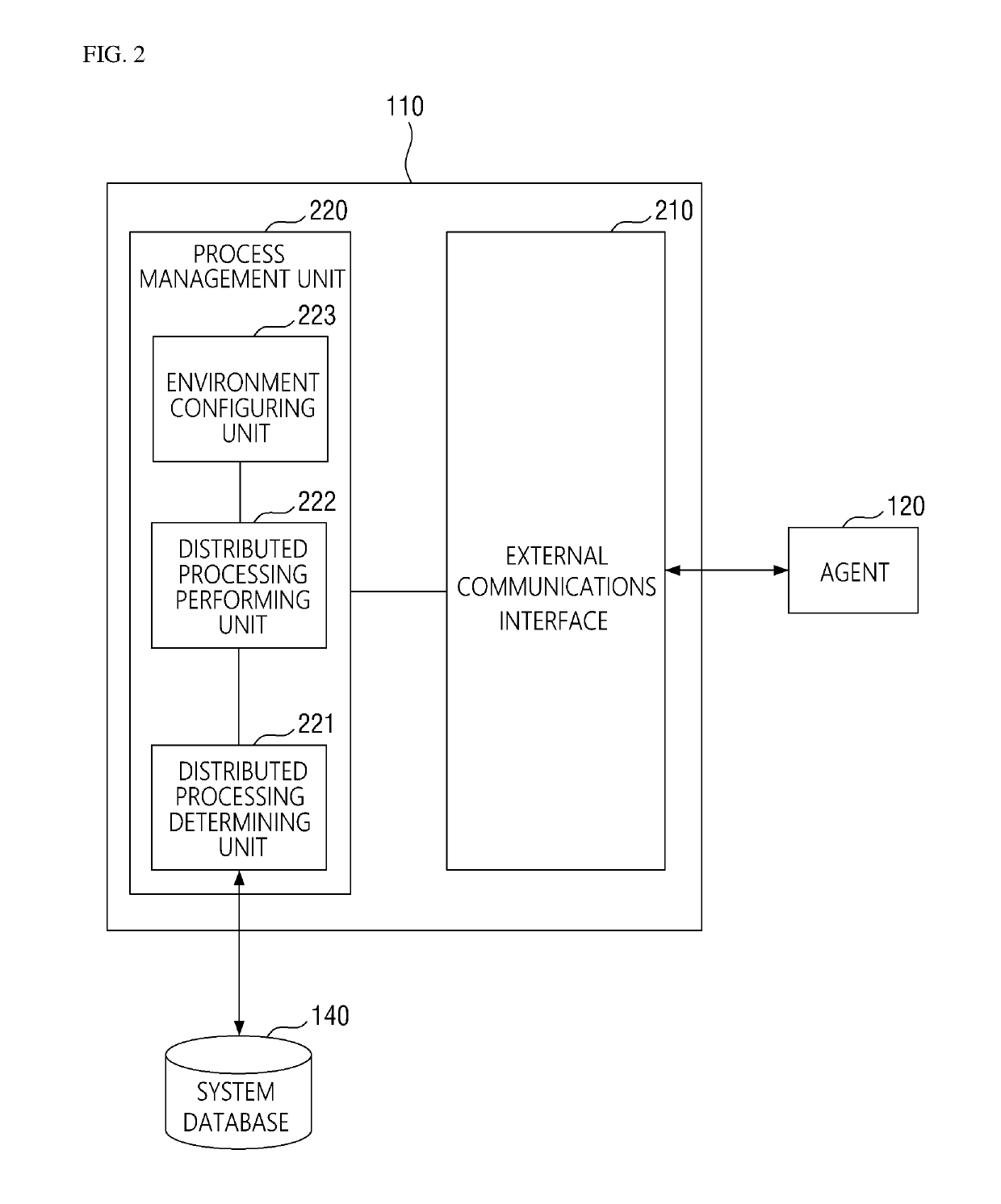
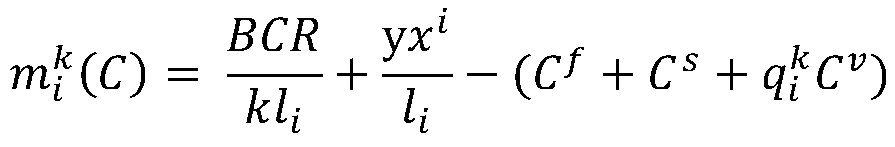Patents
Literature
36 results about "Cyber threat intelligence" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
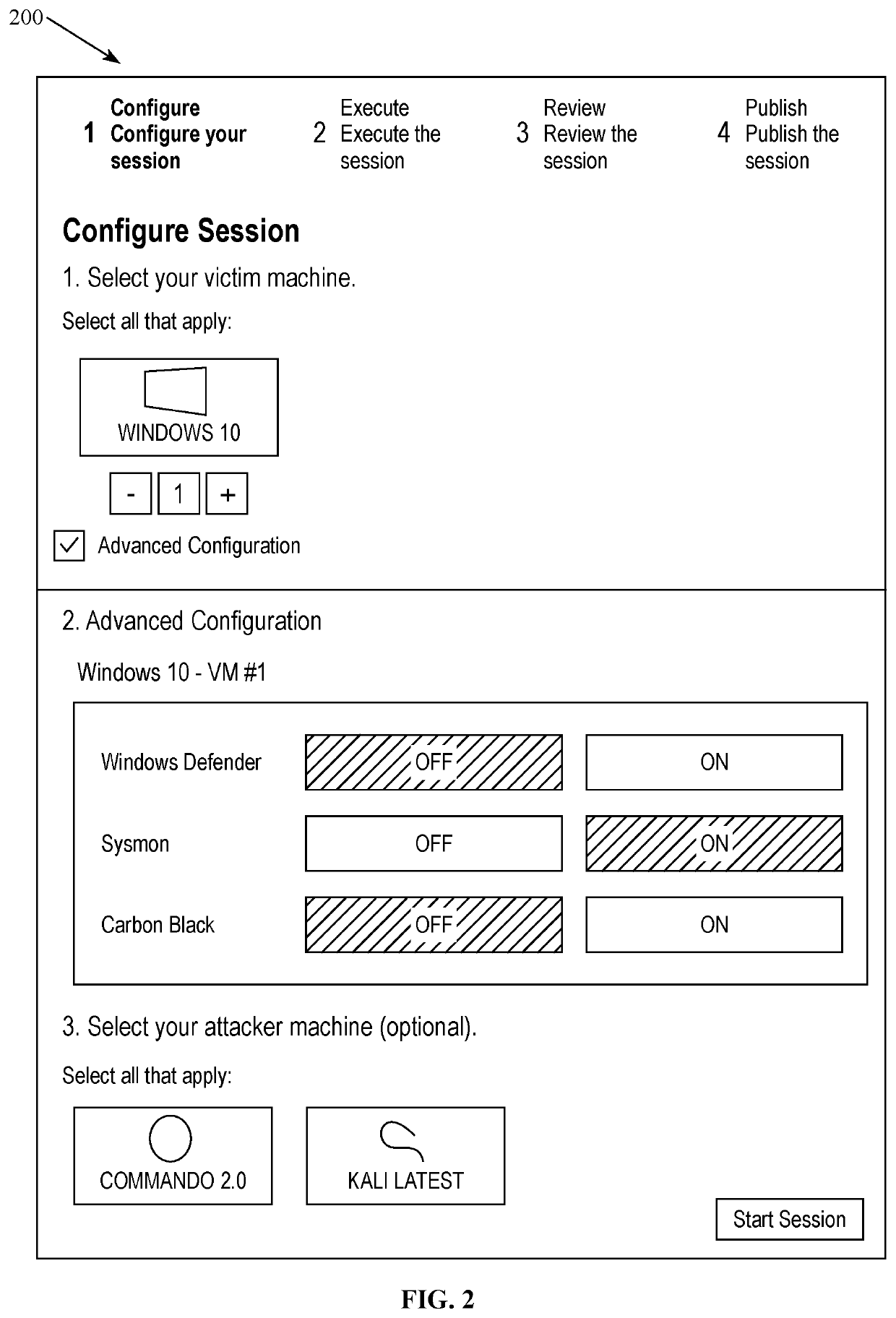
Affectedness scoring engine for cyber threat intelligence services
ActiveUS20200327223A1Digital data information retrievalPlatform integrity maintainanceManaged security serviceCyber threat intelligence
A network-accessible cyber-threat security analytics service is configured to characterize and respond to a description that includes threat indicators (e.g., IOCs), and an initial severity. Enterprises register with the service by providing identifying information, such as industry, geographies, and the like. For each threat indicator, a query is sent to each of a set of one or more security knowledge bases, and at least some of the queries are scoped by the enterprise industry / geo information specified. The knowledge bases may vary but typically include: a managed security service, a cyber threat intelligence service, and a federated search engine that searches across one or more enterprise-connected data sources. Responses to the queries are collected. A response provides an indication whether the threat indicator identified in the query has been sighted in the knowledge base and the frequency. The system then adjusts the initial severity to reflect the indications returned from querying the security knowledge bases.
Owner:IBM CORP
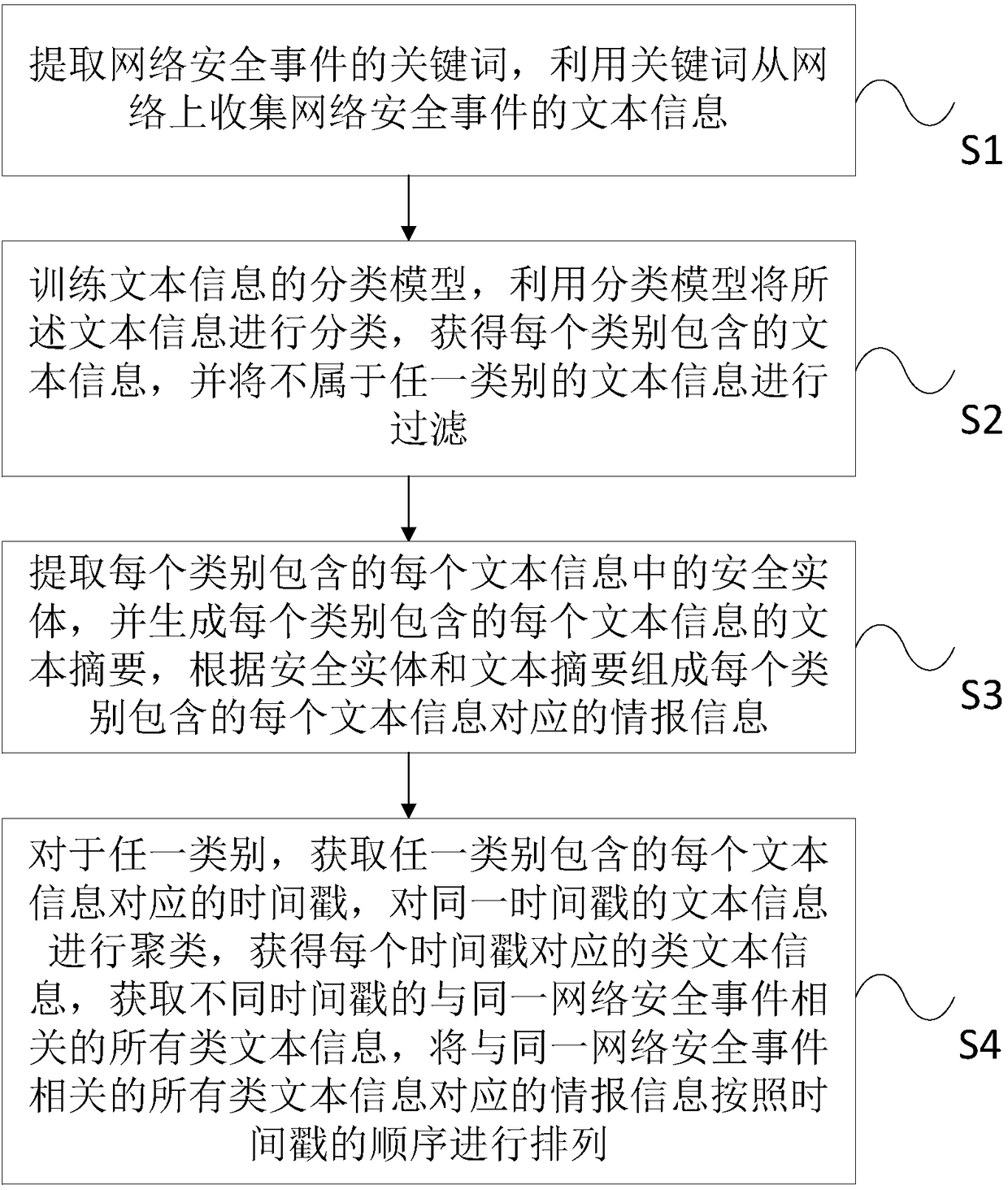
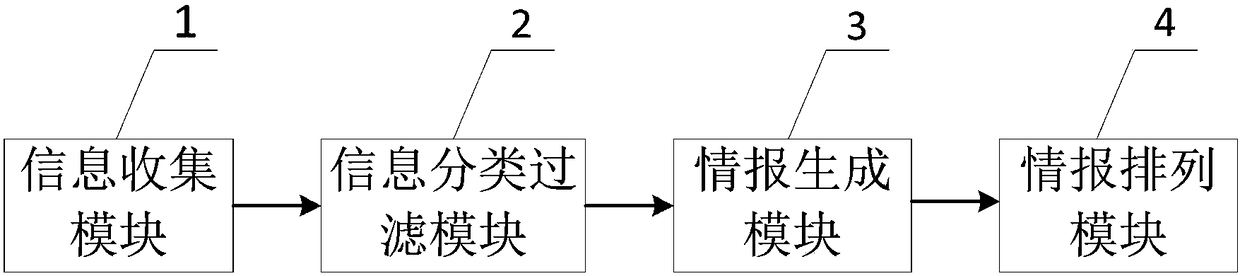
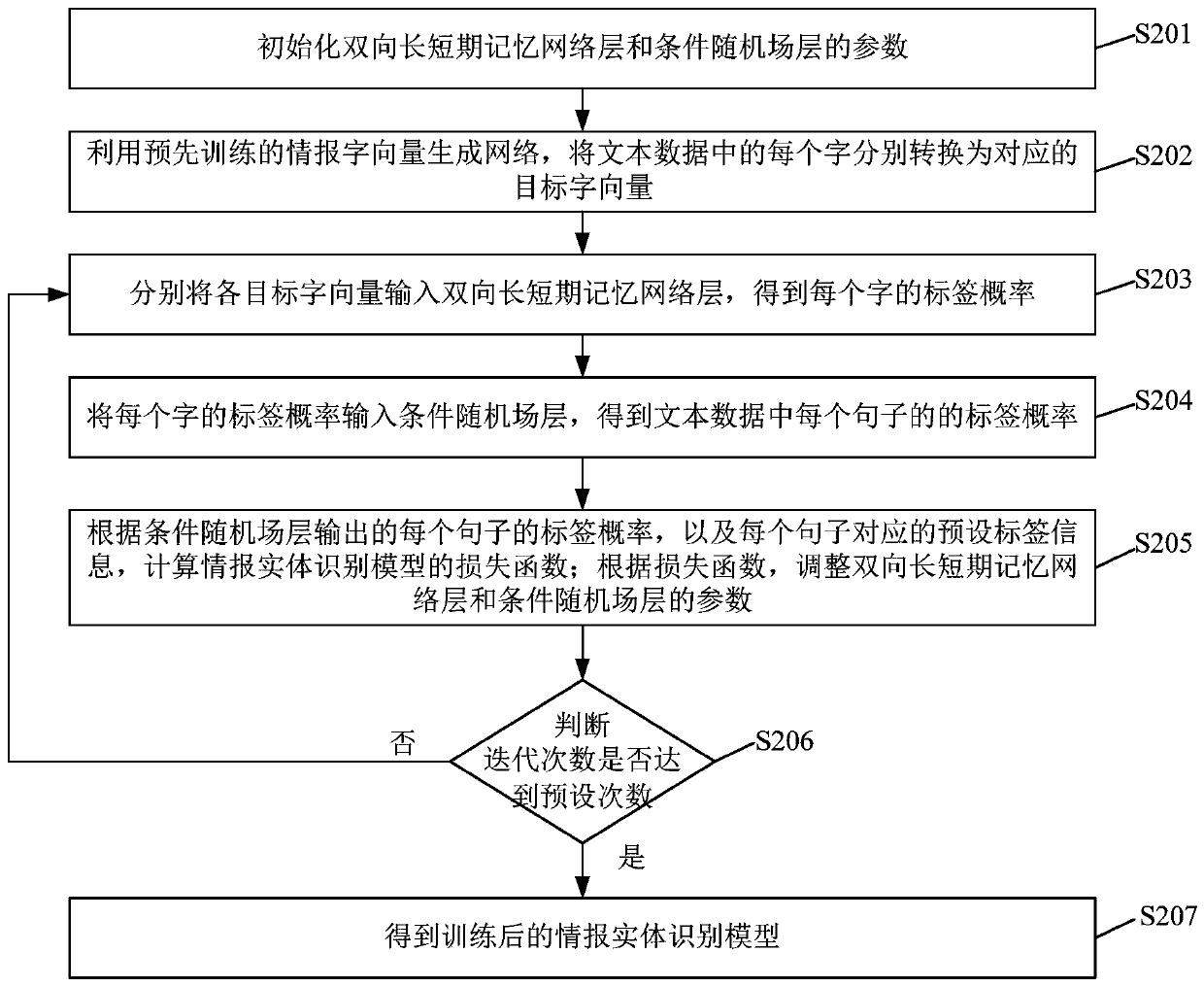
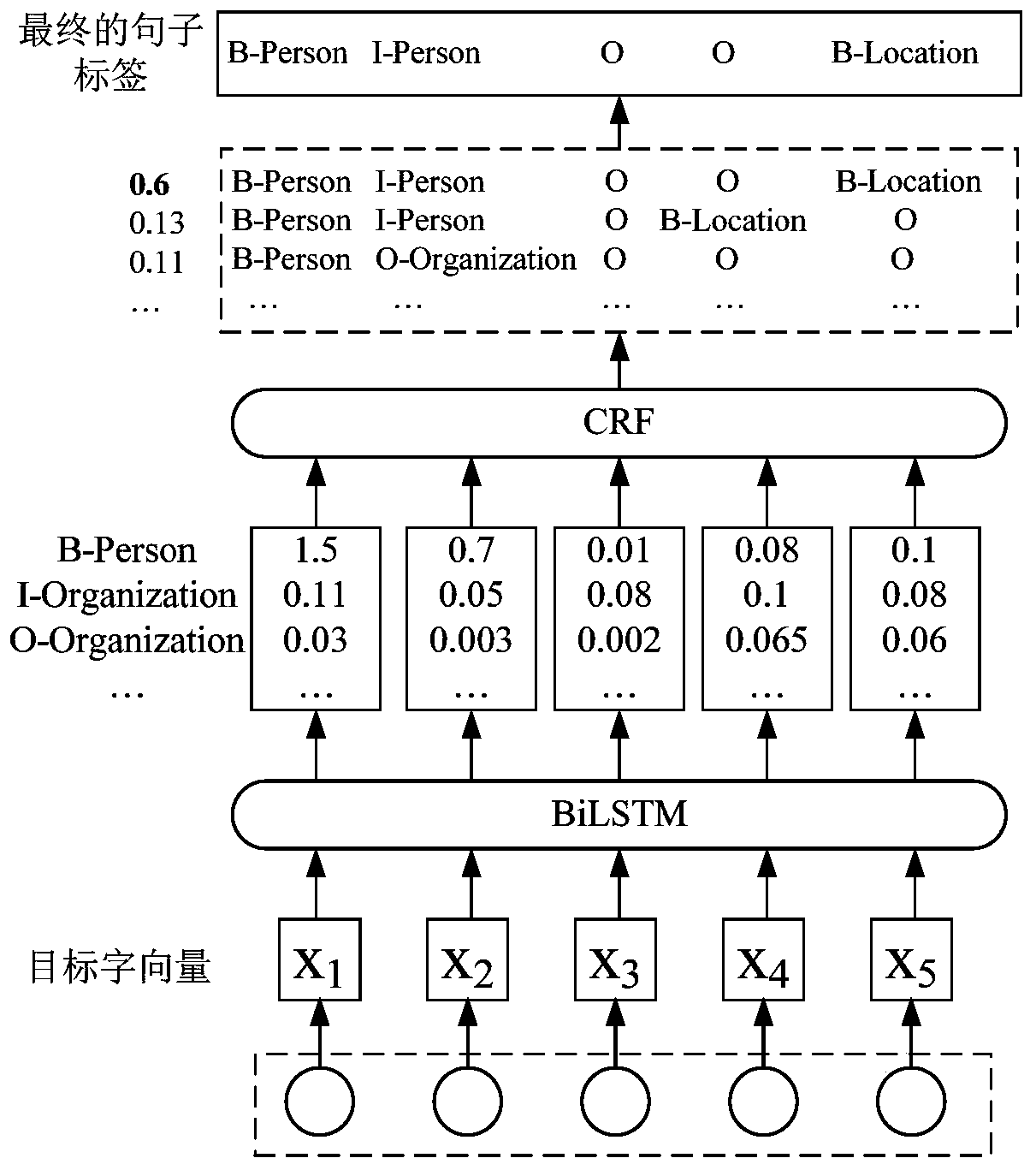
Cyber threat intelligence generation method and system
InactiveCN108399194AQuick understandingEasy to track in real timeSpecial data processing applicationsText database clustering/classificationTimestampCyber threat intelligence
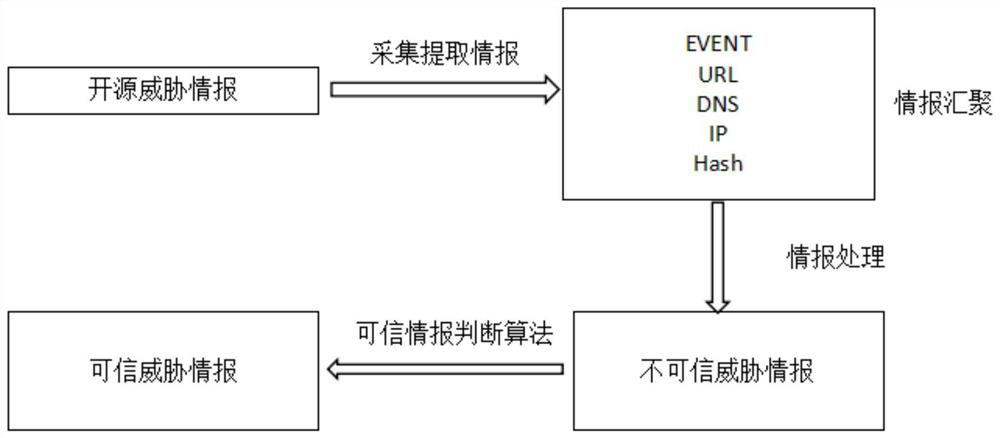
The invention provides a cyber threat intelligence generation method and system. The method comprises the steps of collecting text information of a network security event from a network by utilizing akeyword; classifying the text information by utilizing a classification model, and filtering the text information not belonging to any category; extracting a security entity in each piece of the textinformation comprised in each category, and generating a text abstract of each piece of the text information comprised in each category, and according to the security entities and the text abstracts,forming intelligence information; and clustering the text information with the same timestamps, obtaining class text information corresponding to the timestamps, obtaining all class text information,related to the same network security event, of different timestamps, and sorting the intelligence information corresponding to all the class text information related to the same network security event according to a timestamp sequence. An intelligence tracking system taking an event chain as a presentation form is formed, so that security personnel can track the security event in real time, and the manpower resource cost of intelligence collection is reduced.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Network threat intelligence credibility identification method
InactiveCN109672674AEase of evaluationAchieve quantificationData switching networksCyber threat intelligenceThreat intelligence
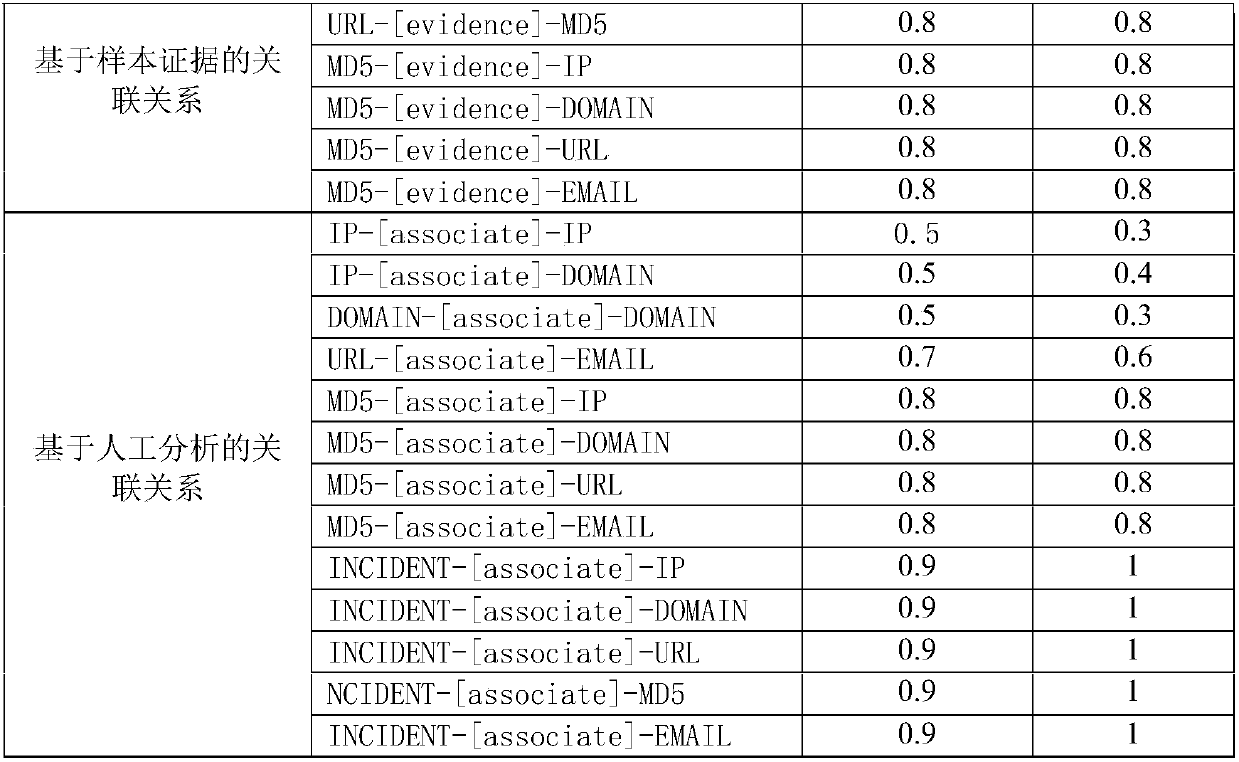
The invention discloses a network threat intelligence credibility identification method. The method disclosed by the invention comprises the following steps: 1) constructing an association diagram model of network threat intelligence, wherein a node on the diagram is a network threat indicator; 2) each network threat indicator has an initial reputation value, calculating the initial reputation value of each network threat indicator to serve as a part of a final threat reputation value of the indicator; 3) calculating a weight for each edge in the association diagram model; 4) designing a threat propagation algorithm via the idea of a diagram propagation algorithm, so that the threat reputation value is propagated step by step among the nodes and neighboring nodes, and then combining the threat reputation value with the initial reputation value of each network threat indicator to calculate a final reputation value; and 5) determining the network threat intelligence credibility accordingto the final reputation value of the network threat indicator. By adoption of the network threat intelligence credibility identification method disclosed by the invention, the quality of network threat intelligence can be better evaluated.
Owner:INST OF INFORMATION ENG CAS
Network threat intelligence sharing platform based on blockchain smart contract
PendingCN112543196AImprove satisfactionReduce false alarm rateTransmissionComputer networkCyber threat intelligence
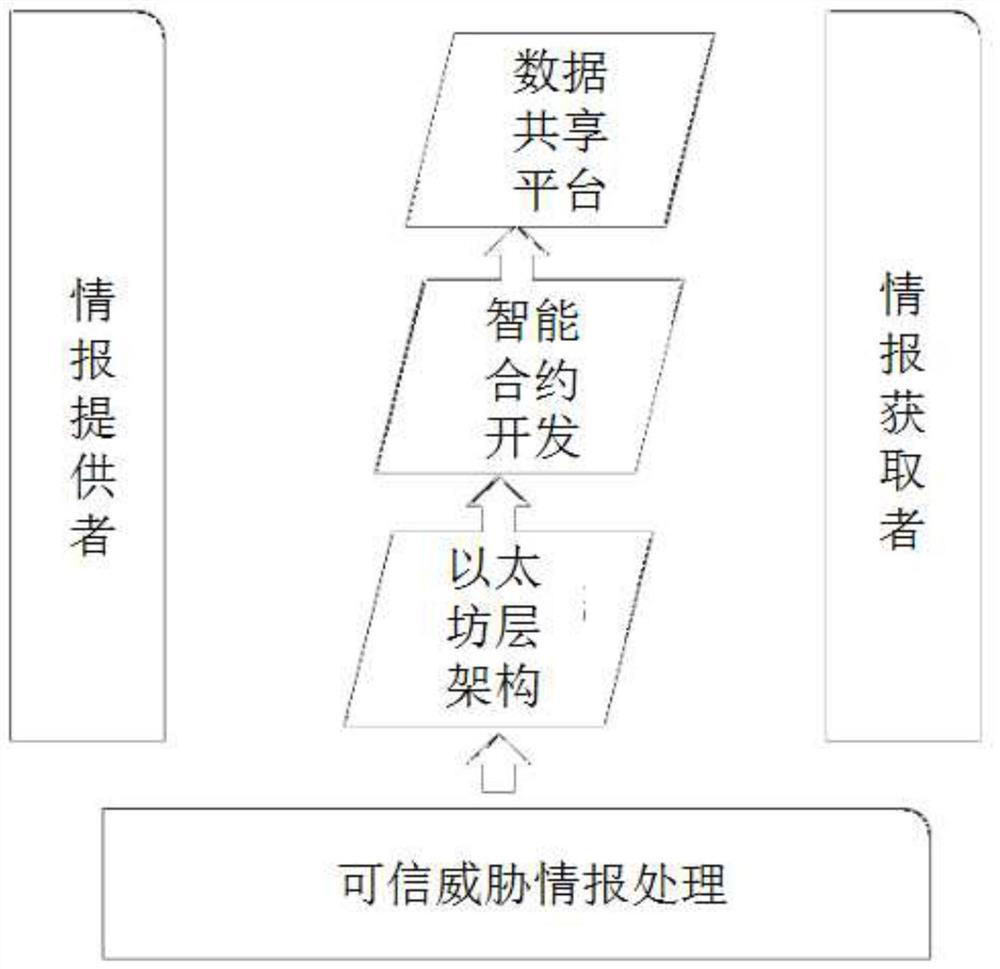
The invention provides a network threat intelligence sharing platform based on a blockchain smart contract, which is based on an Ethereum underlying architecture, takes network threat intelligence data as data assets, processes the network threat intelligence data through a trustworthy threat intelligence processing module, and with distributed data storage of a blockchain system, through intelligent contract development and design, intelligence sharing of network threat intelligence data on an autonomous peer-to-peer data platform by a data provider and a data purchaser is realized. Threat intelligence credibility evaluation in a unified security sharing network space of network threat intelligence data is realized, the problem of low multi-source data integration quality faced by threatintelligence sharing in the prior art is solved, the satisfaction degree of sharing platform users is increased, and the false alarm rate of threat intelligence security application is reduced.
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY +1
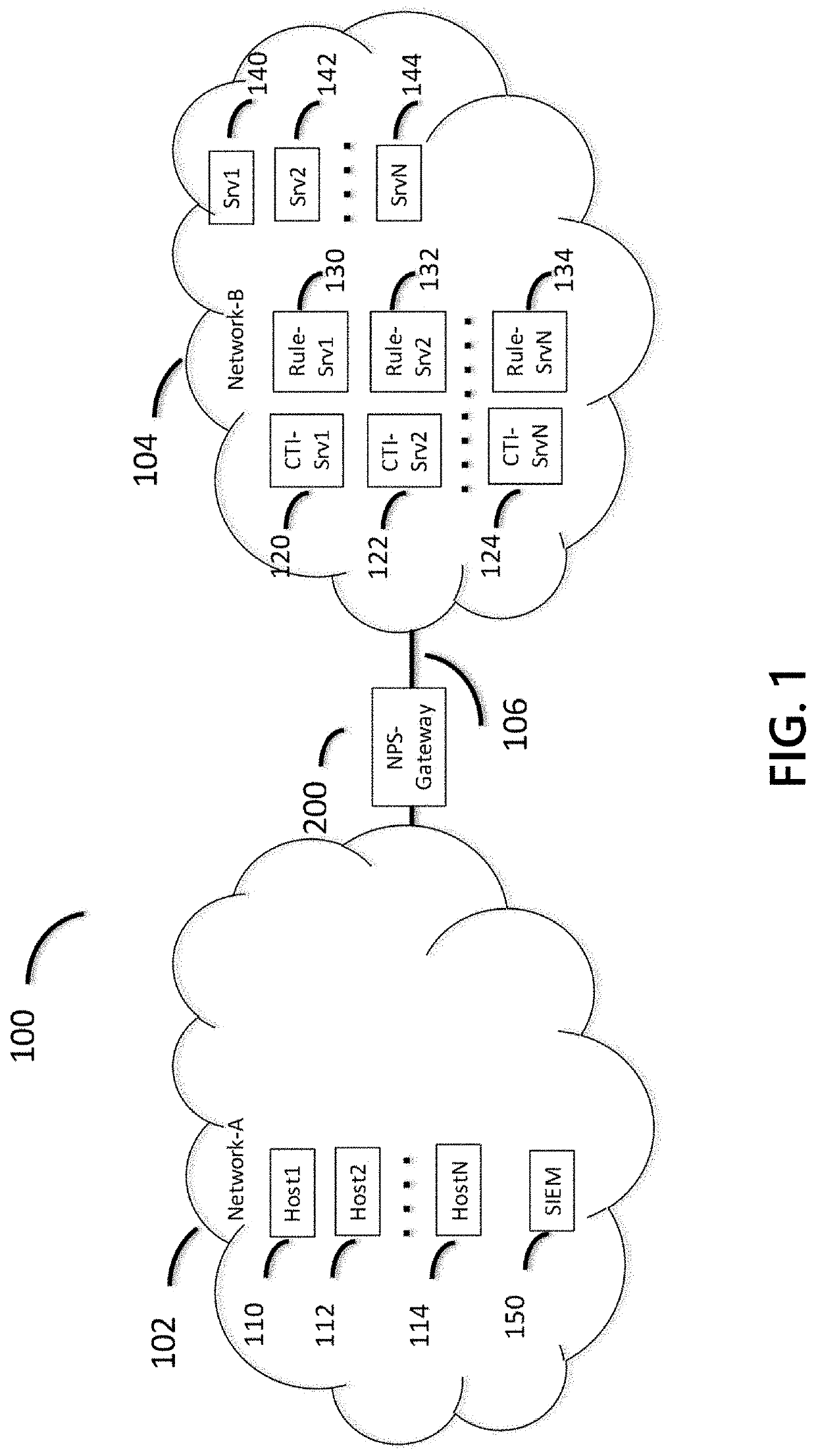
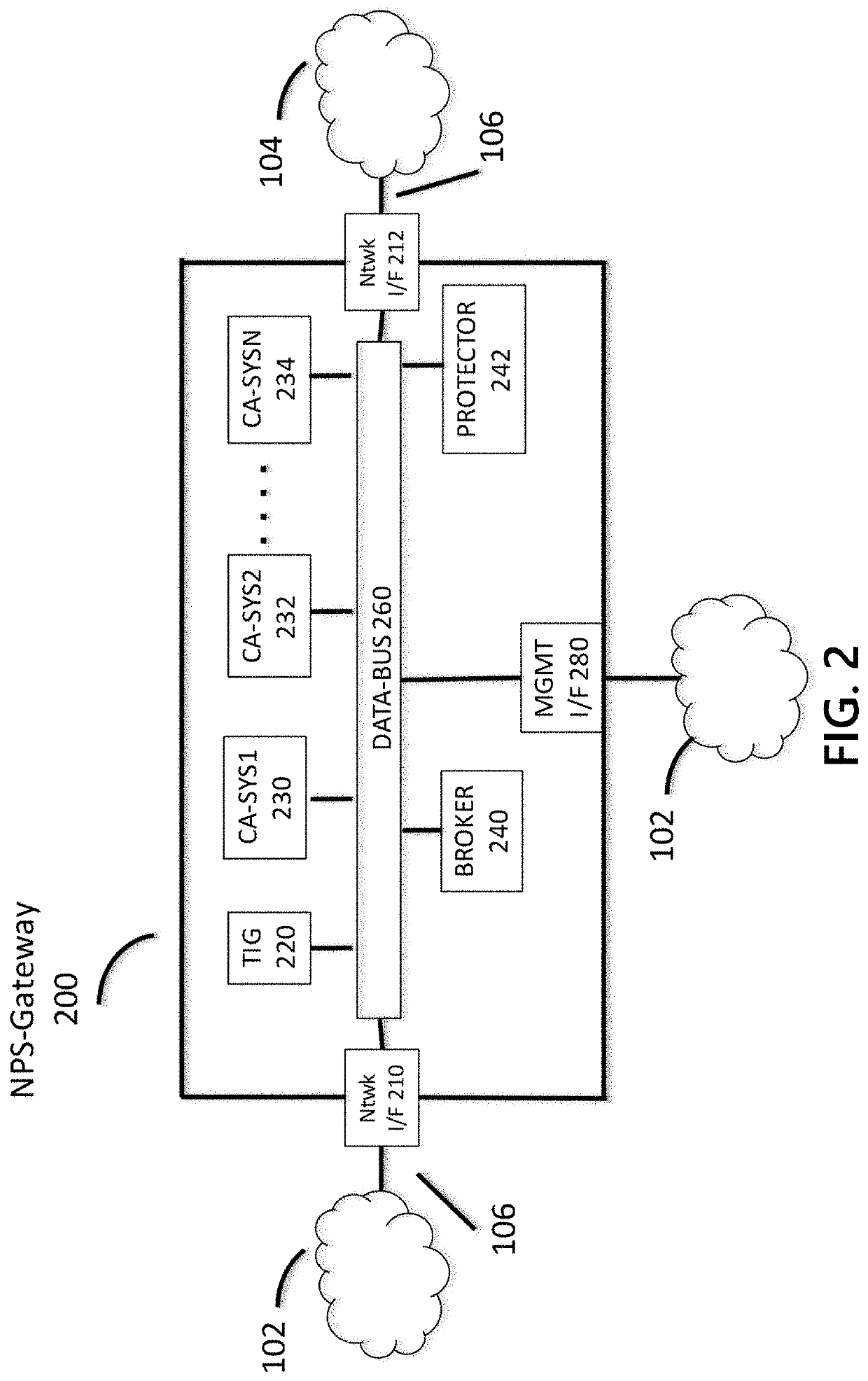
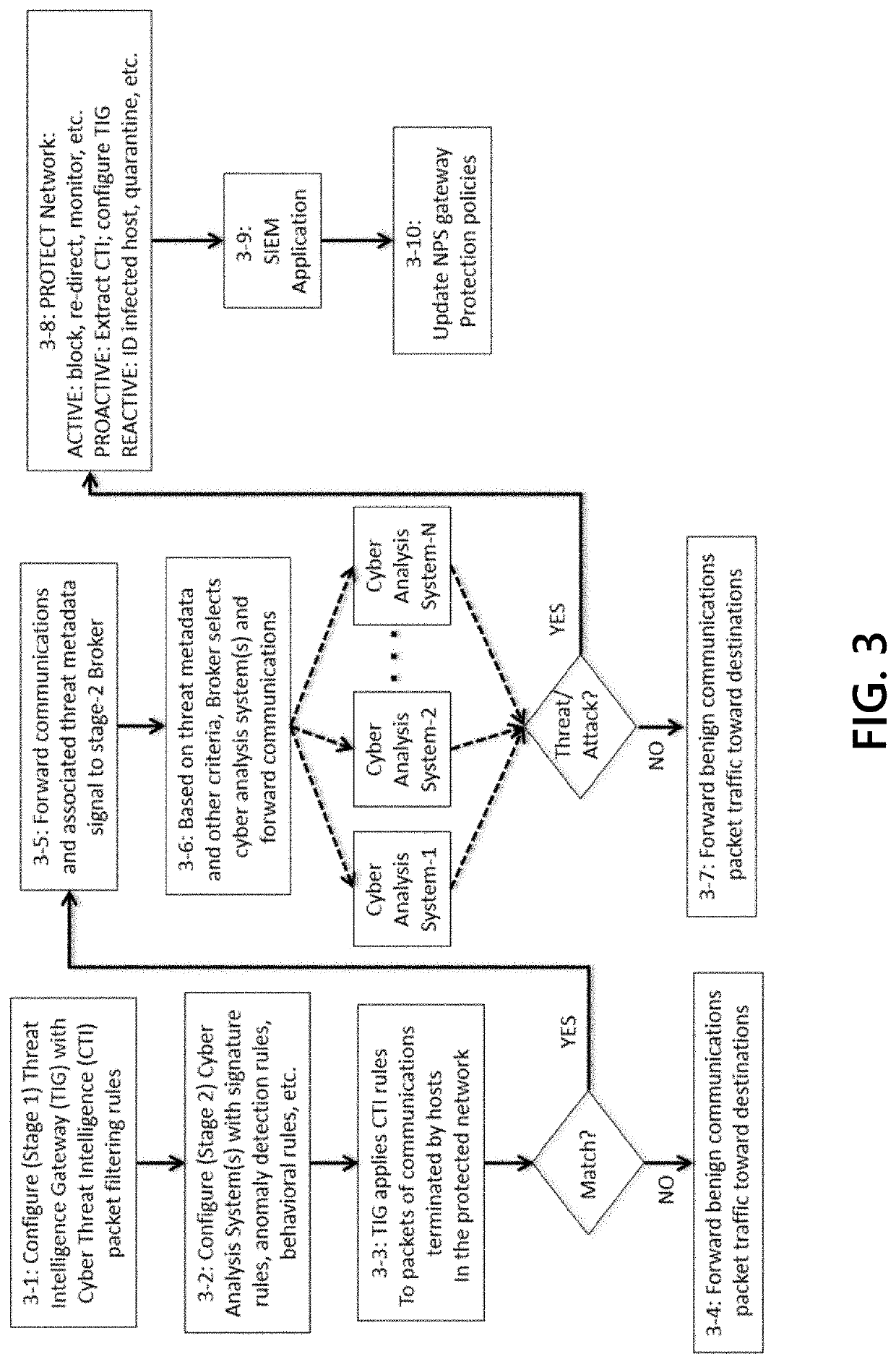
Methods and systems for efficient network protection
ActiveUS10333898B1Improve efficiencyImprove performanceData switching networksCyber threat intelligencePassive networks
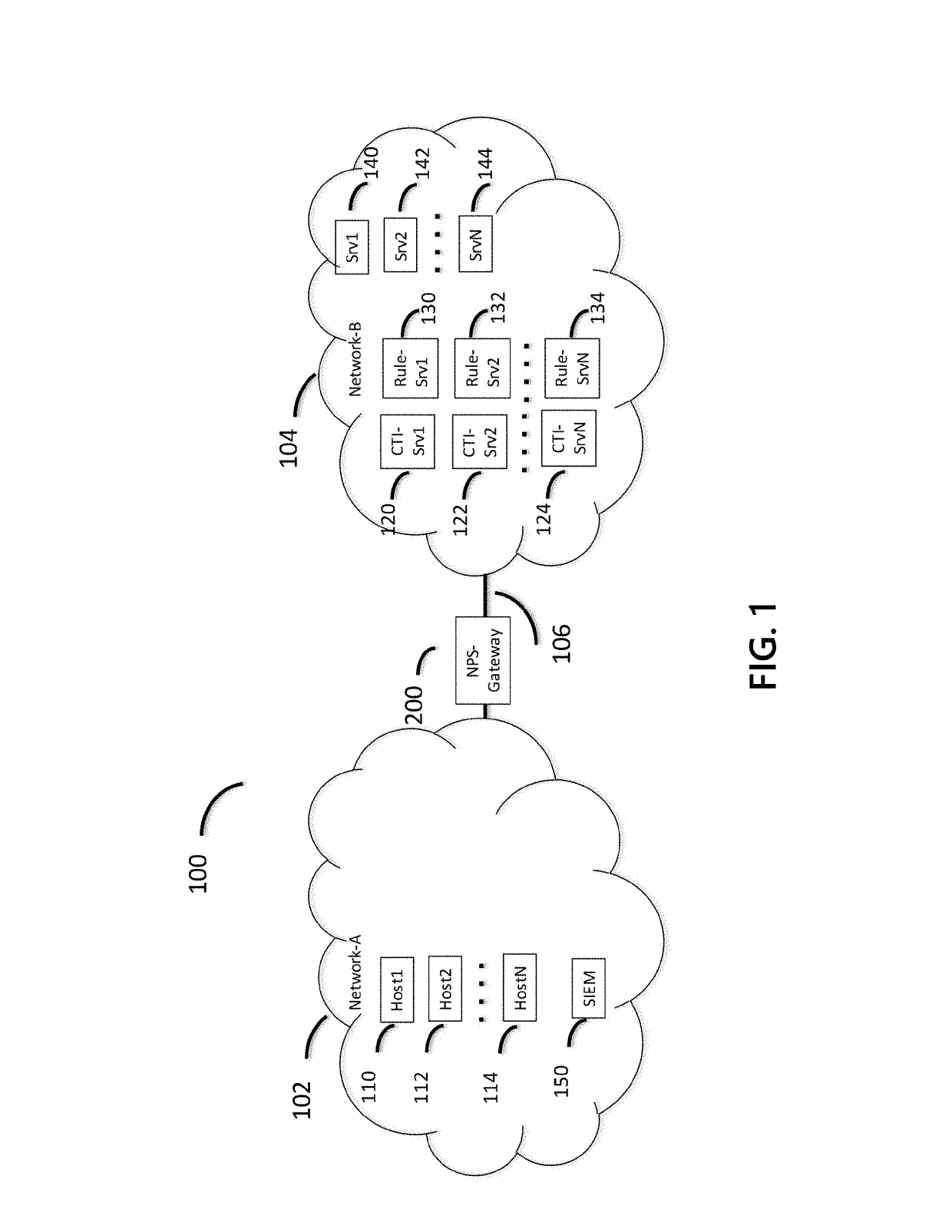
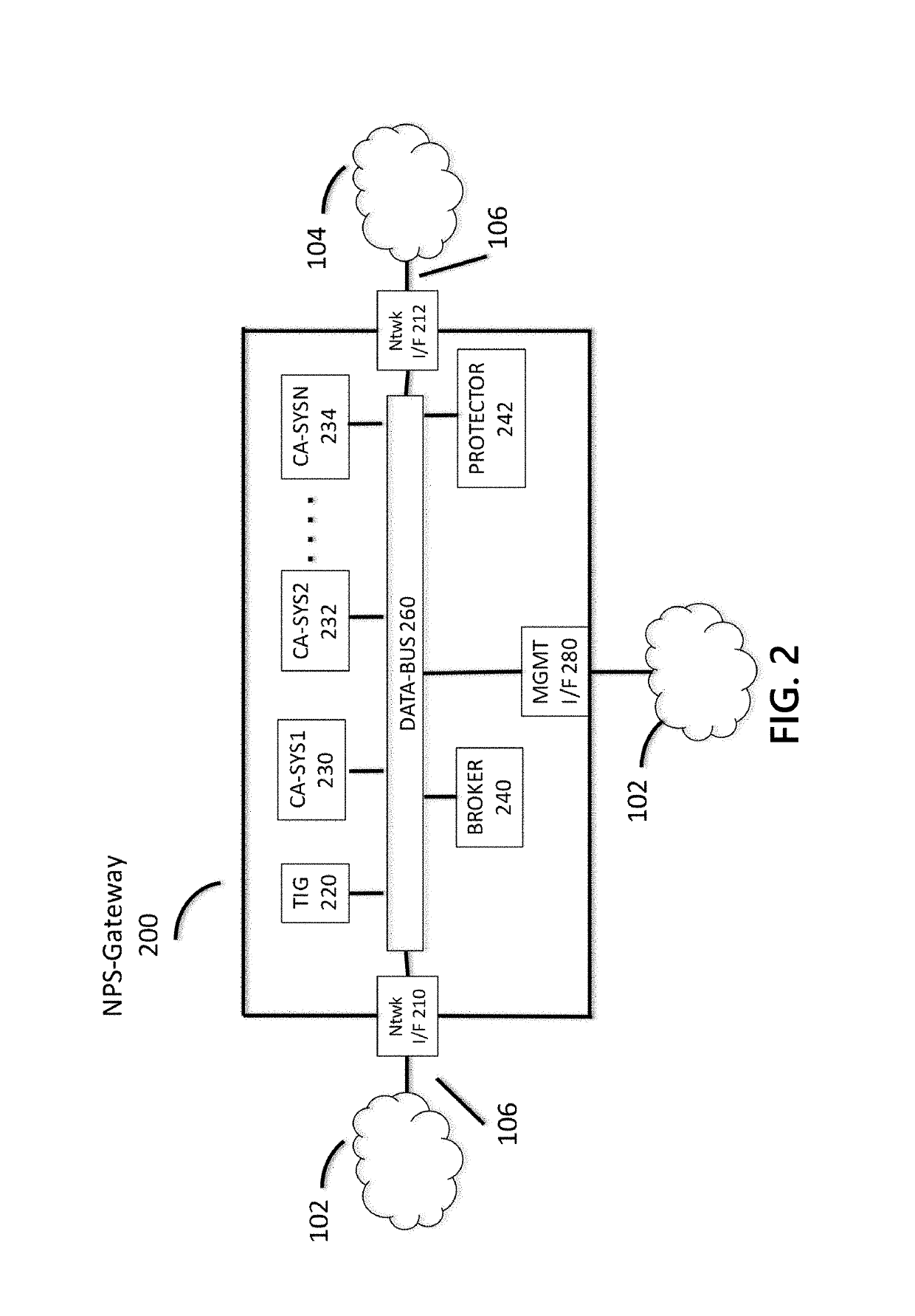
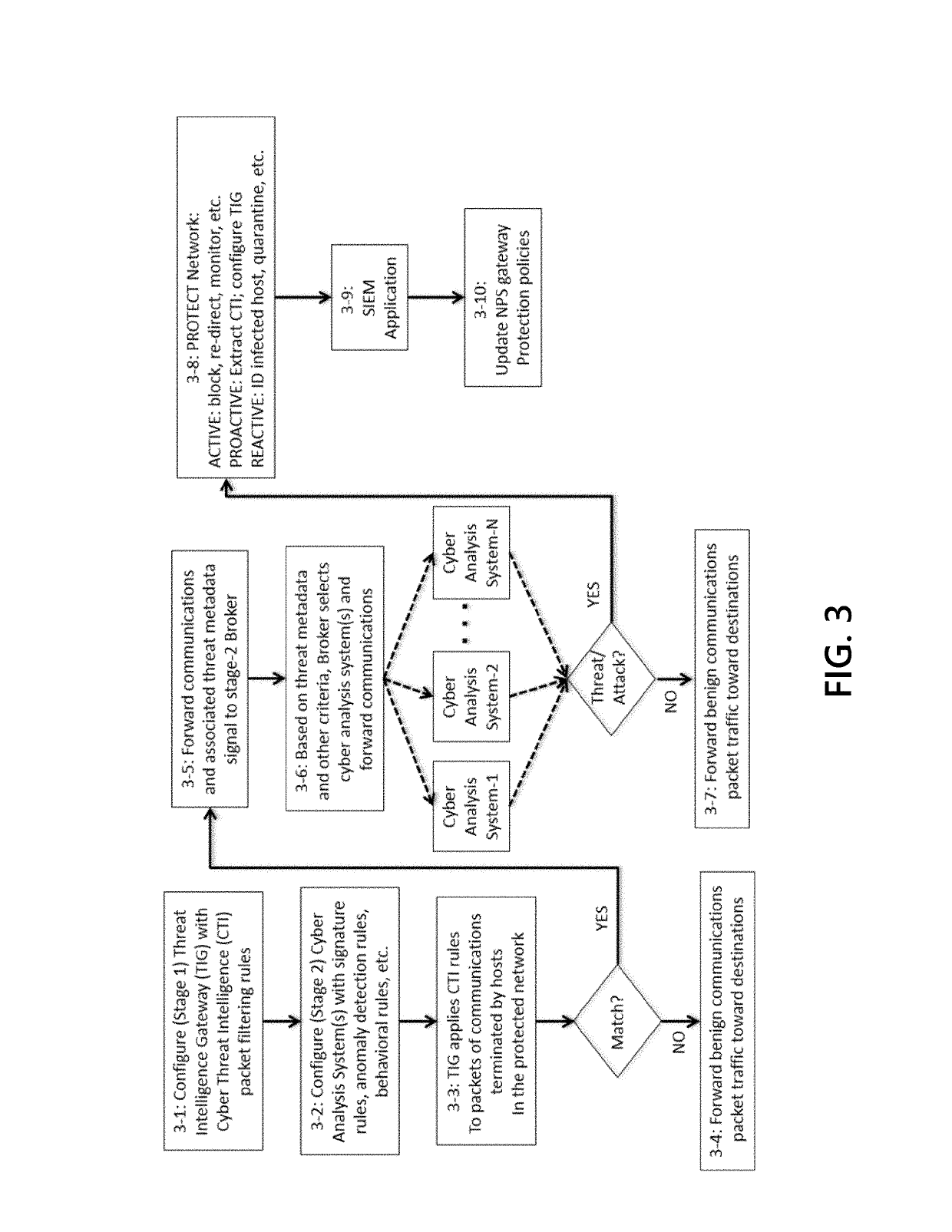
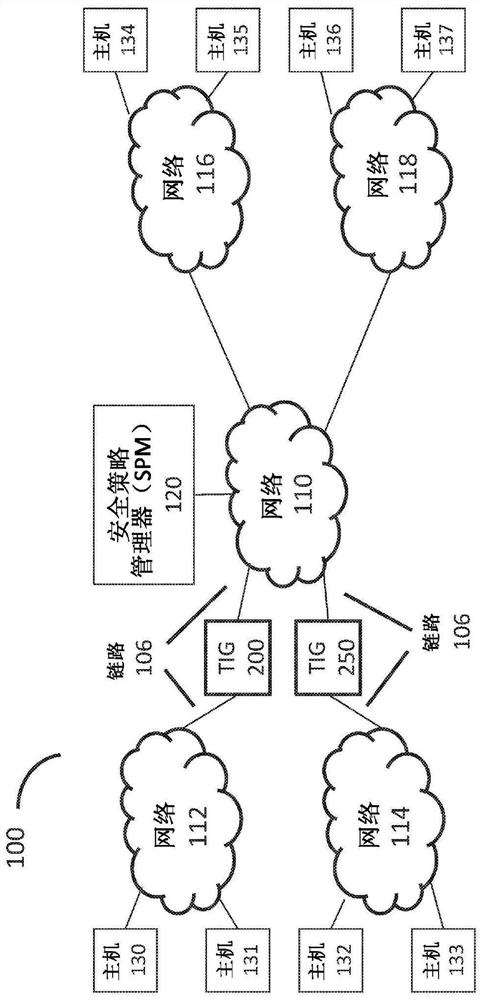
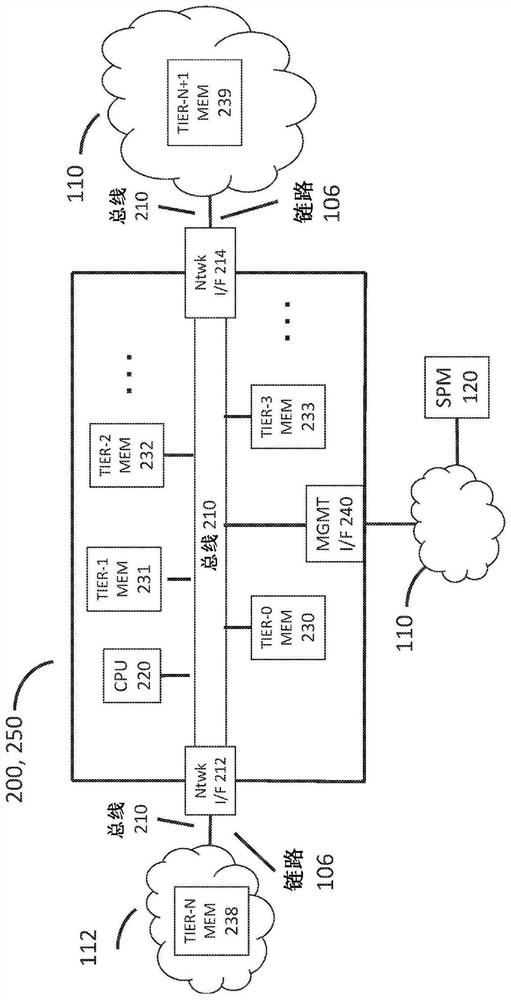
Methods and systems are disclosed for integrating cyber threat intelligence (CTI), threat metadata, and threat intelligence gateways with analysis systems to form efficient and effective system for active, proactive, and reactive network protection. A network gateway may be composed of multiple stages. A first stage may include a threat intelligence gateway (TIG). A second stage may include one or more cyber analysis systems that ingest TIG-filtered communications and associated threat metadata signals. A third stage may include network protection logic that determines which protective actions. The gateway may be provisioned and configured with rules that specify the network protection policies to be enforced. The gateway may ingest all communications flowing between the protected network and the unprotected network.
Owner:CENTRIPETAL NETWORKS LLC
Network threat intelligence automatic extraction method based on deep learning
PendingCN111552855AReduce out-of-order resultsImprove accuracyWeb data indexingNeural architecturesCyber threat intelligenceEngineering
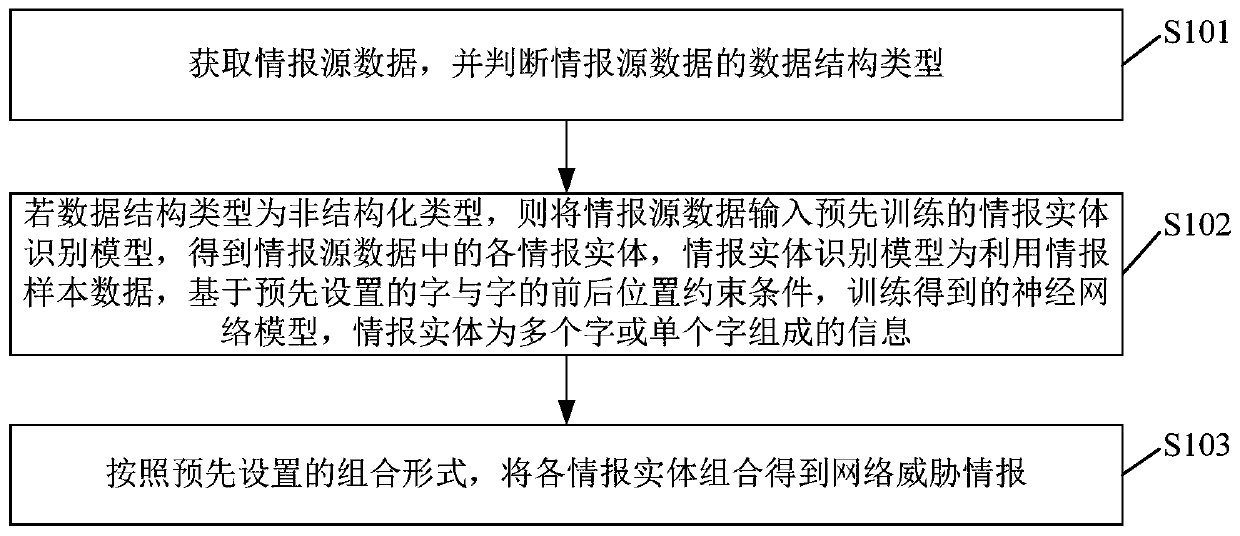
The embodiment of the invention provides a network threat intelligence automatic extraction method based on deep learning, which can obtain intelligence source data and judge the data structure type of the intelligence source data. If the data structure type is an unstructured type, inputting the intelligence source data into a pre-trained intelligence entity identification model to obtain each intelligence entity in the intelligence source data, the intelligence entity identification model being a neural network model obtained by training based on preset characters and front and back positionconstraint conditions of the characters by using the intelligence sample data; and according to a preset combination form, combining the information entities to obtain the network threat information.According to the invention, a pre-trained information entity identification model can be used to carry out automatic extraction of network threat information; and the position constraint conditions introduced by the information entity identification model during training limit the front-back position relationship of the characters in the information entity, so that the out-of-order result of theinformation entity is reduced, and the accuracy of network threat information identification is improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
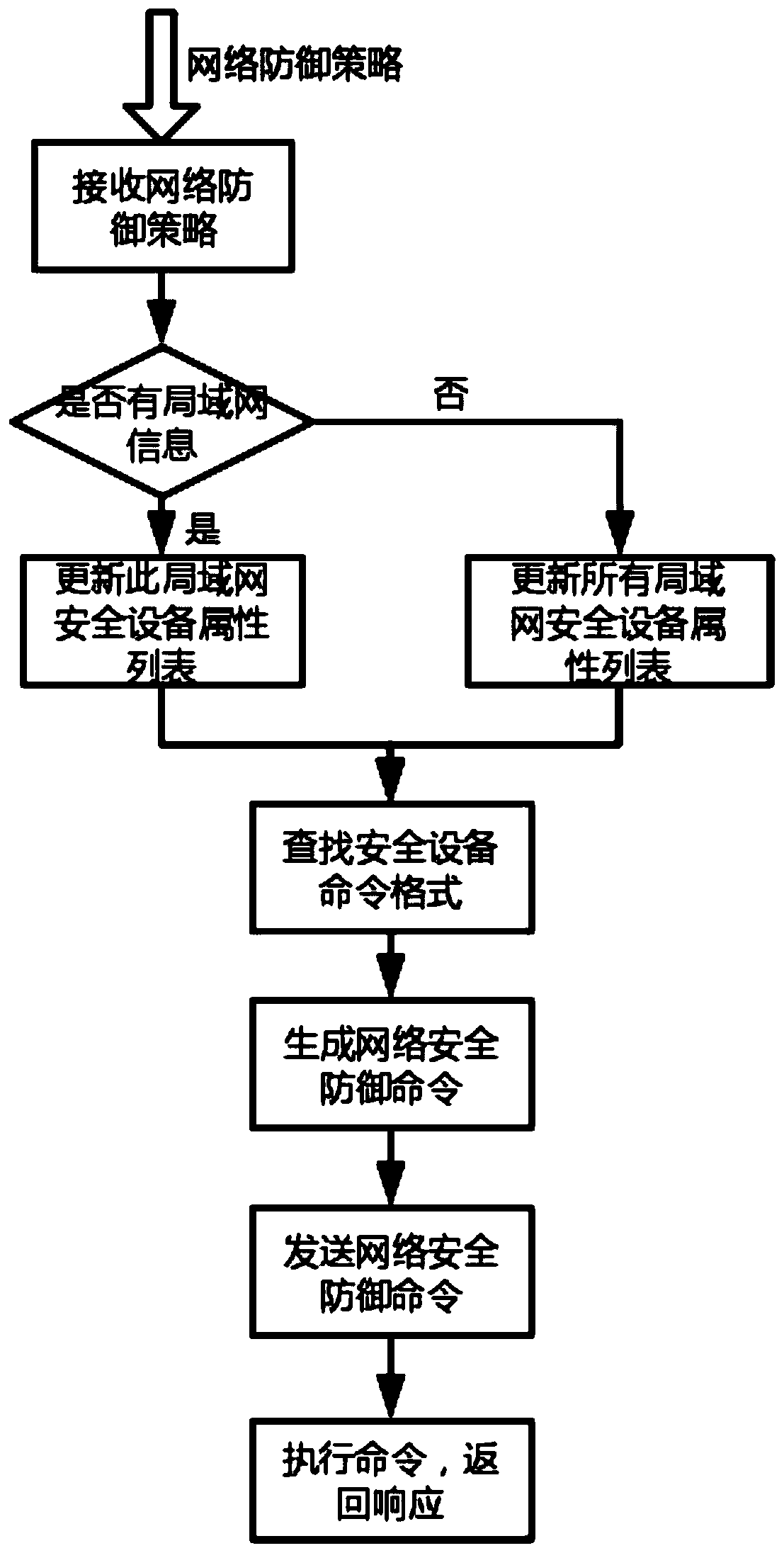
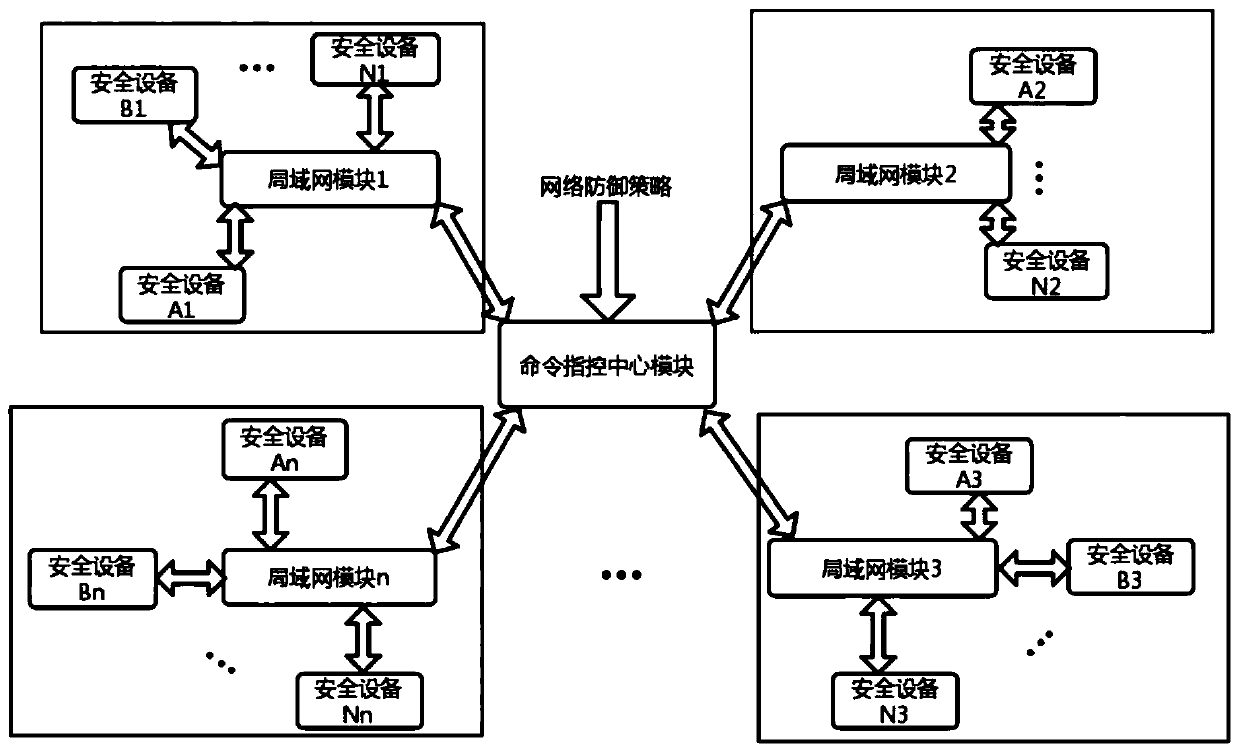
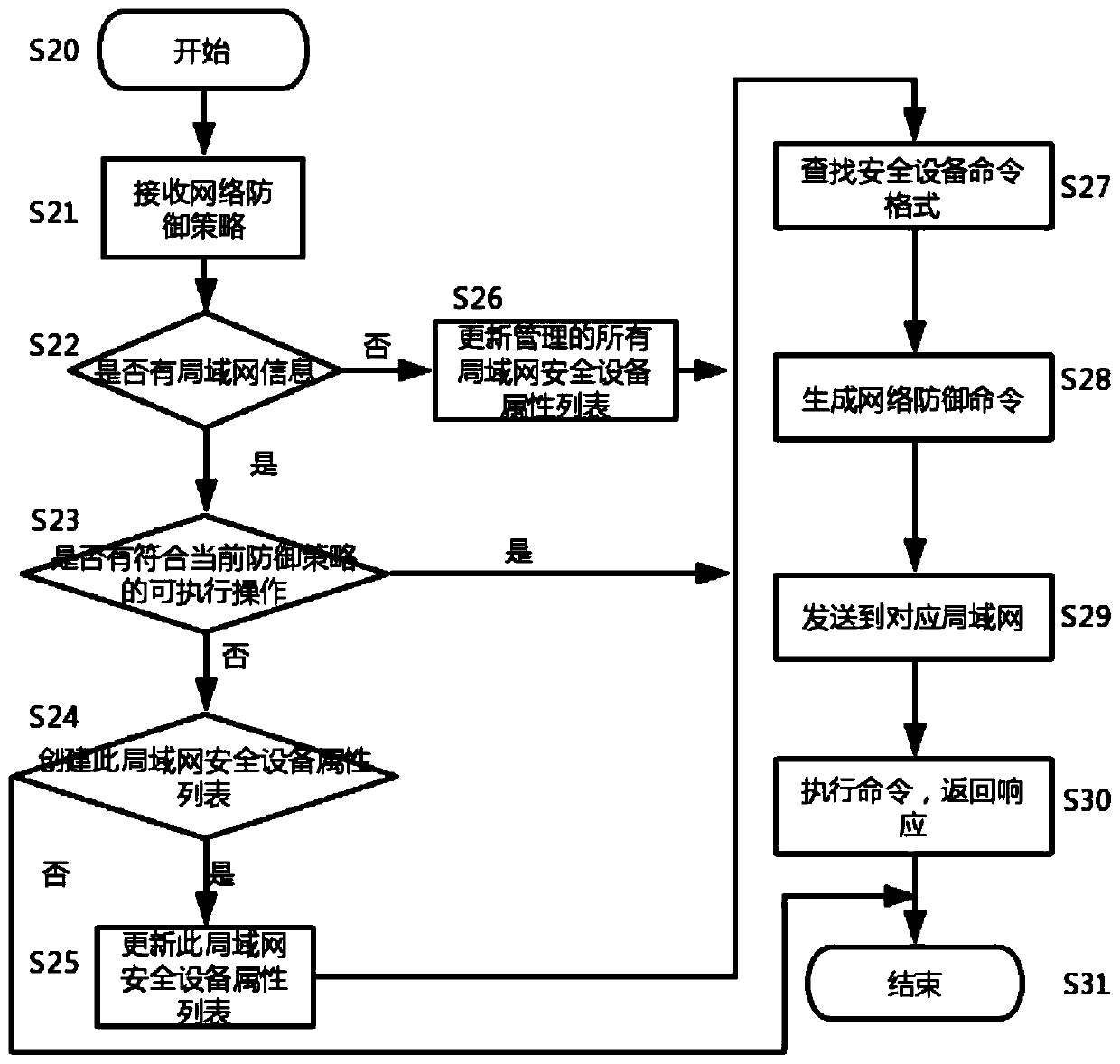
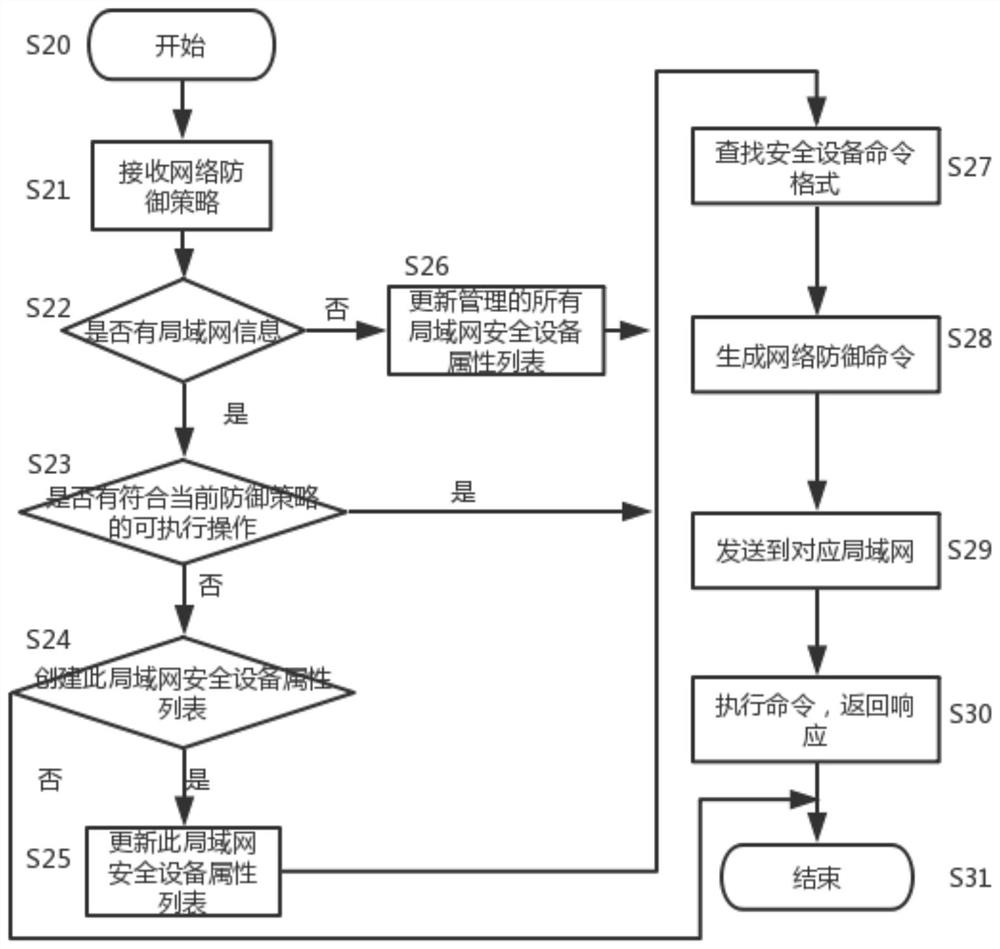
Unified control method and system for network security equipment
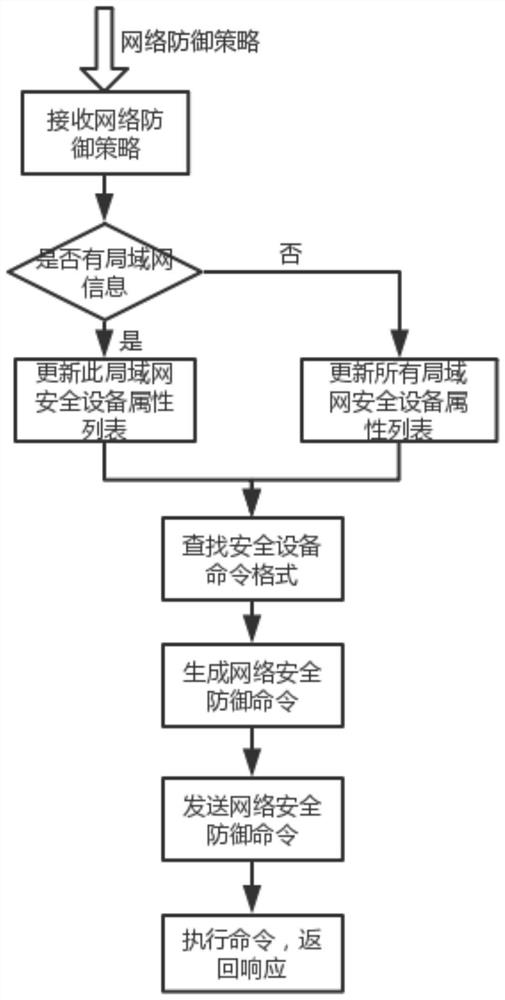
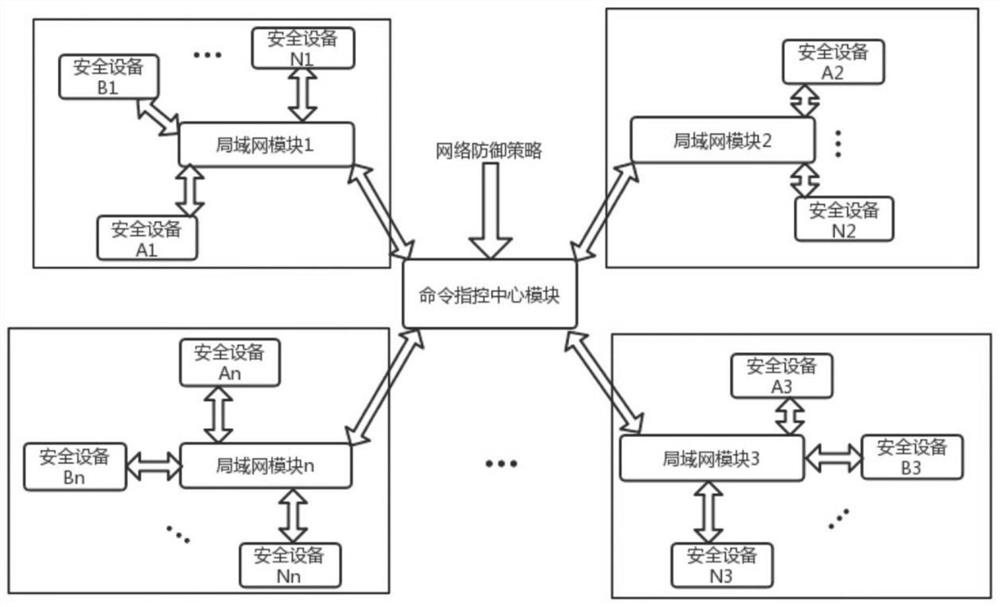
The invention belongs to the technical field of network security, and particularly relates to a unified control method and system for network security equipment, and the method comprises the followingsteps: generating a network defense strategy according to a received network threat information; judging whether the generated network defense strategy contains local area network information or not,commanding a command and control center to send a request to all the local area network managers, and updating an attribute list of all the managed local area network security devices; generating a corresponding network defense command through security equipment and a command format file thereof specified in the network defense strategy, and sending the network defense command to the local area network security equipment; and using the local area network security device to execute the network defense command and return a response to the command and control center. Various kinds of safety equipment are dynamically and uniformly controlled, the safety equipment comprises an intrusion detection system, a virtual private network and a safety gateway, and rapid defense can be carried out.
Owner:HARBIN ENG UNIV
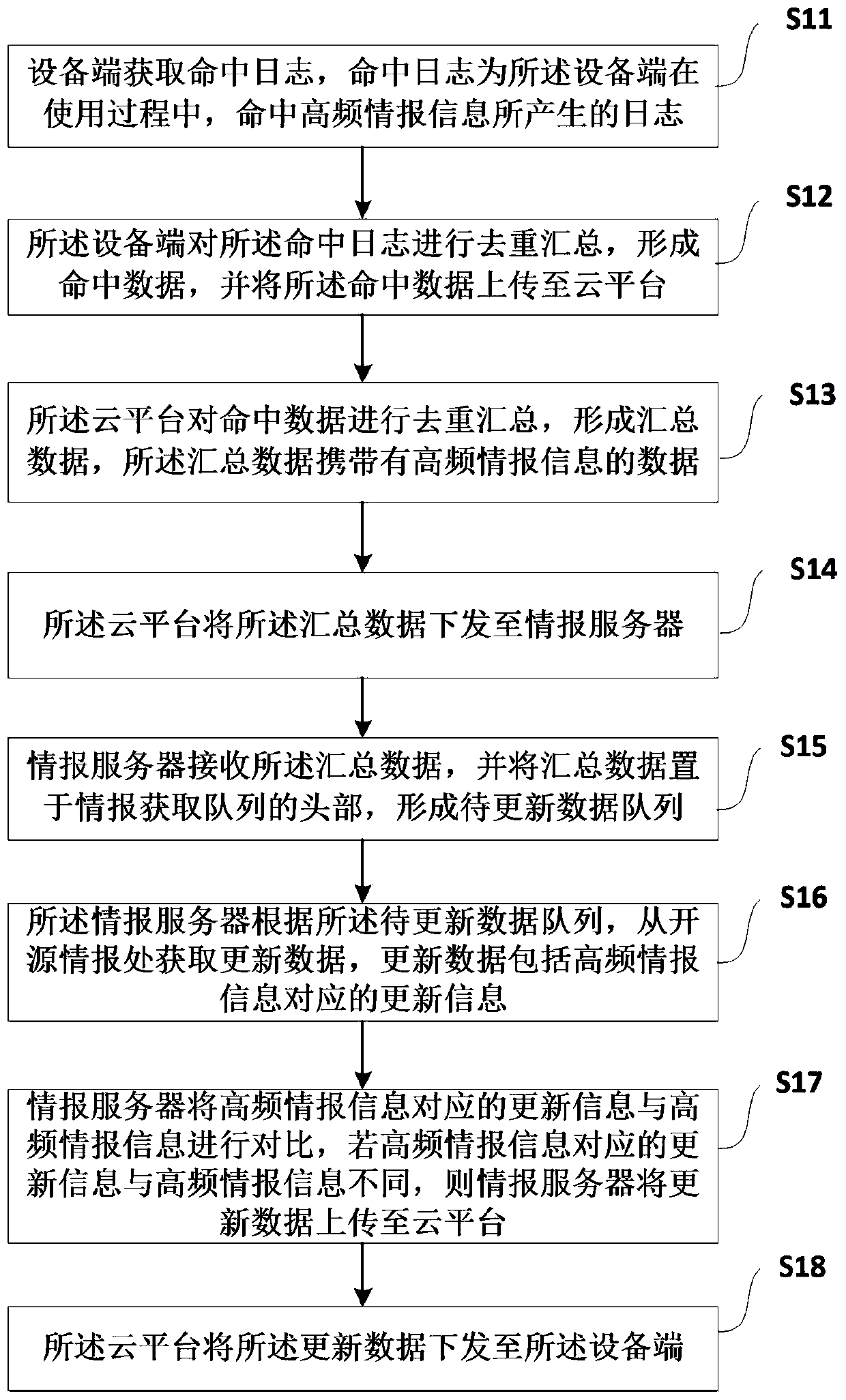
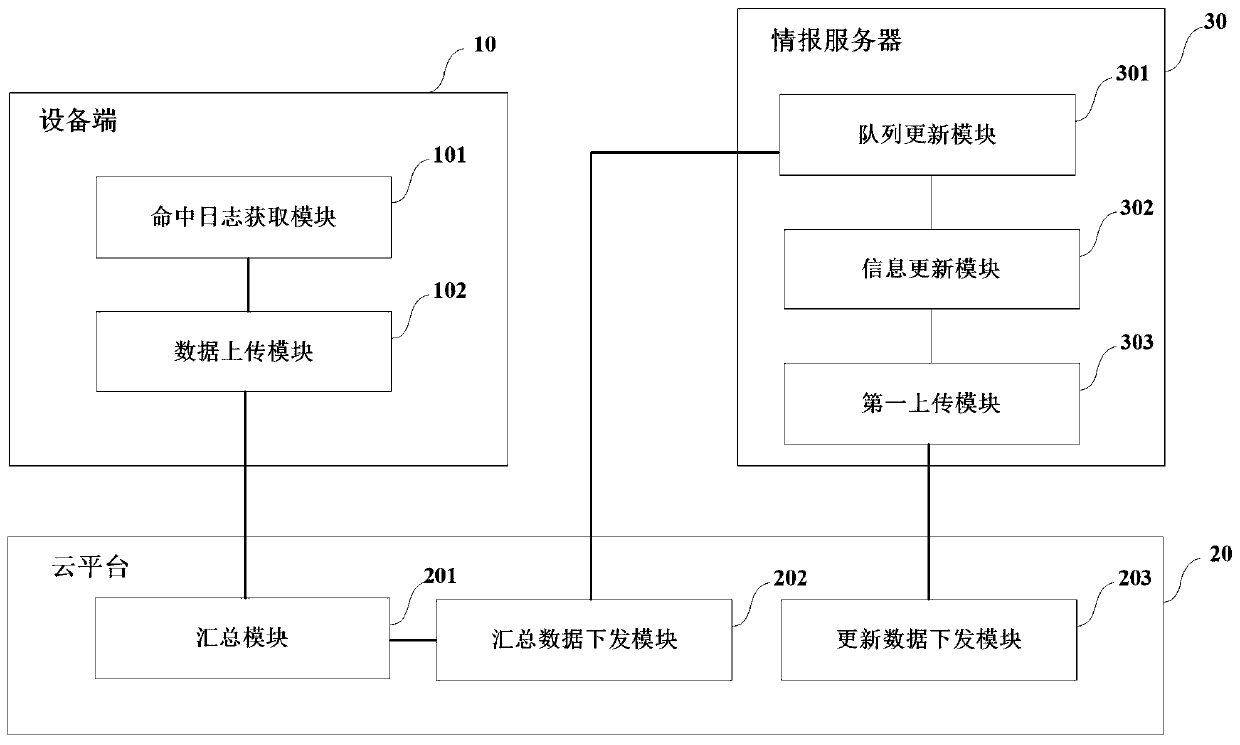
Method and system for updating network threat information
The invention discloses a method and a system for updating network threat information. In the method, a log generated by hitting the high-frequency information in the equipment end is processed to form the summary data, the summary data is fed back to the information server through the cloud platform, and the information server places the summary data in the information acquisition queue accordingto the fed back summary data, so that when the basic information is acquired from the open source information, the updating information corresponding to the high-frequency information can be preferentially acquired according to the summary data. Updating information corresponding to the acquired high-frequency information is compared with the original high-frequency information; according to themethod, whether the high-frequency information is updated or not can be judged, and if yes, the updating information corresponding to the high-frequency information is sent to the equipment end through the cloud platform, so that the equipment end can update the high-frequency information in time in a targeted manner.
Owner:武汉思普崚技术有限公司
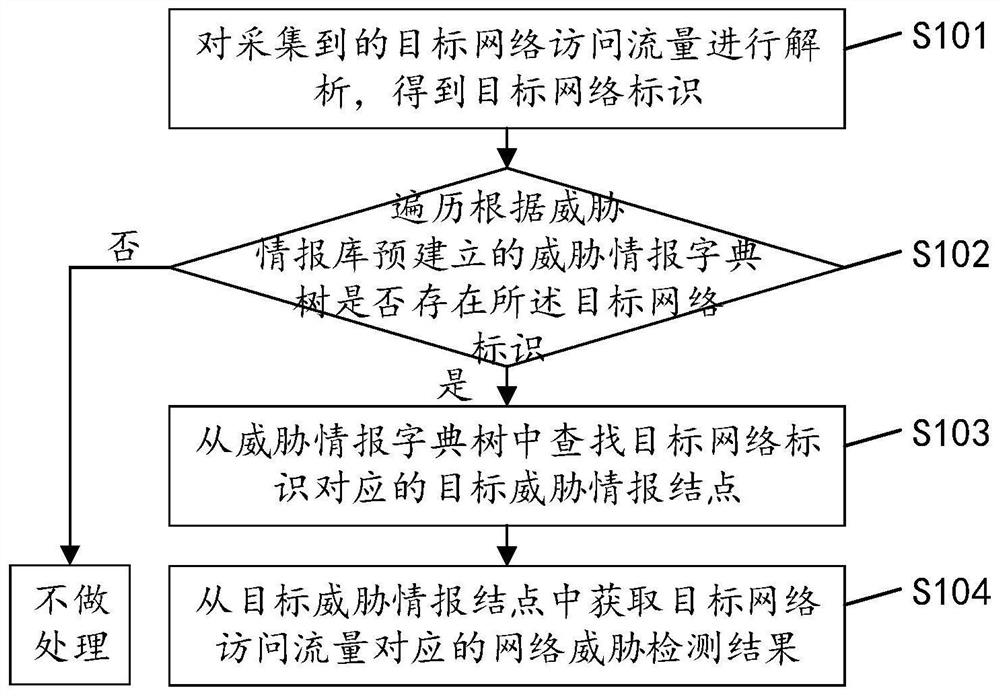
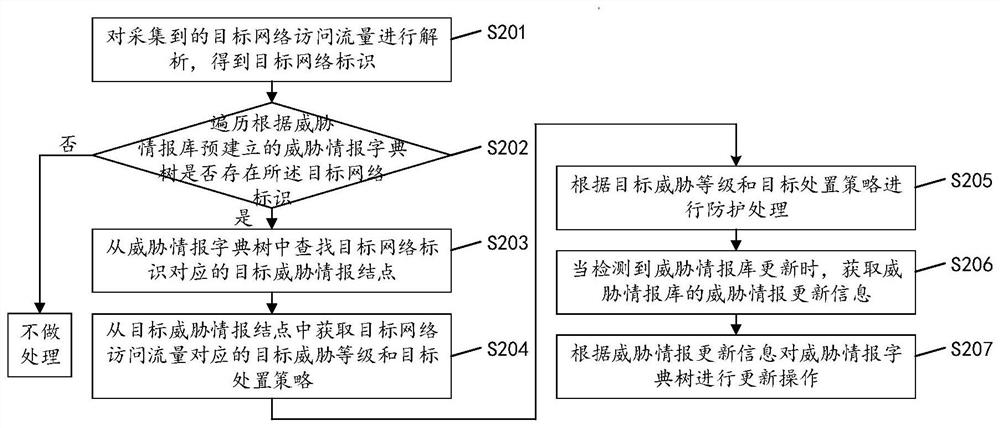
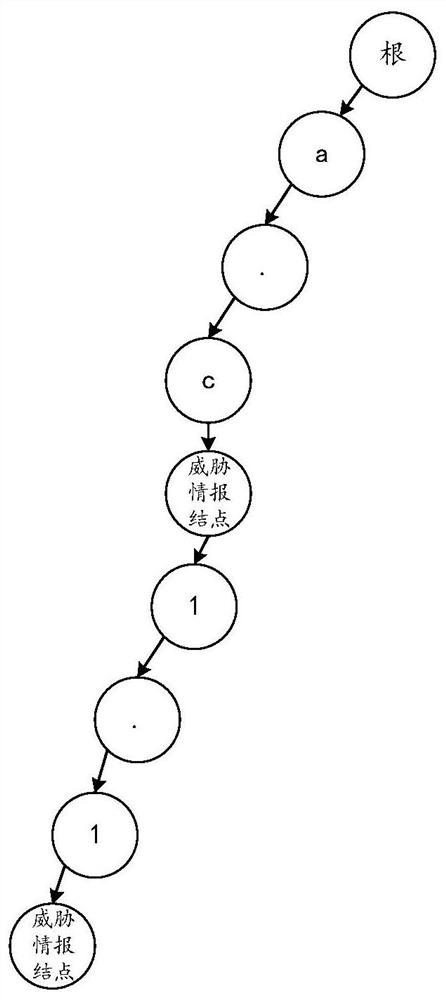
Network threat detection method and device based on dictionary tree, equipment and storage medium
PendingCN112491873AImprove Threat Detection EfficiencyAvoid attackTransmissionCyber threat intelligenceAttack
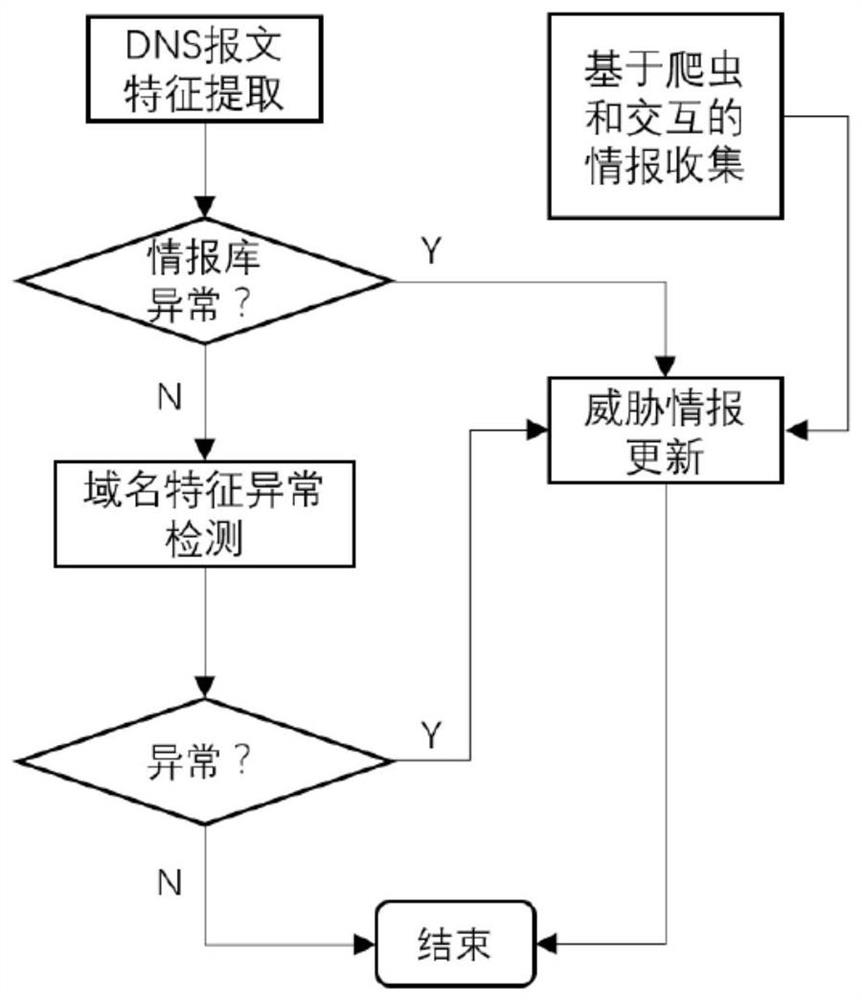
The invention discloses a network threat detection method based on a dictionary tree, and the method comprises the following steps: carrying out the analysis of collected target network access flow, and obtaining a target network identification; traversing whether a target network identifier exists in a threat information dictionary tree pre-established according to the threat information libraryor not; if so, searching a target threat intelligence node corresponding to the target network identifier from the threat intelligence dictionary tree; and obtaining a network threat detection resultcorresponding to the target network access flow from the target threat information node. By applying the network threat detection method based on the dictionary tree provided by the invention, the influence of the performance of the server on network threat information detection is avoided, the network threat detection efficiency is improved, and attacks can be prevented in time. The invention further discloses a network threat detection device and equipment based on the dictionary tree and a storage medium, and the corresponding technical effects are achieved.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
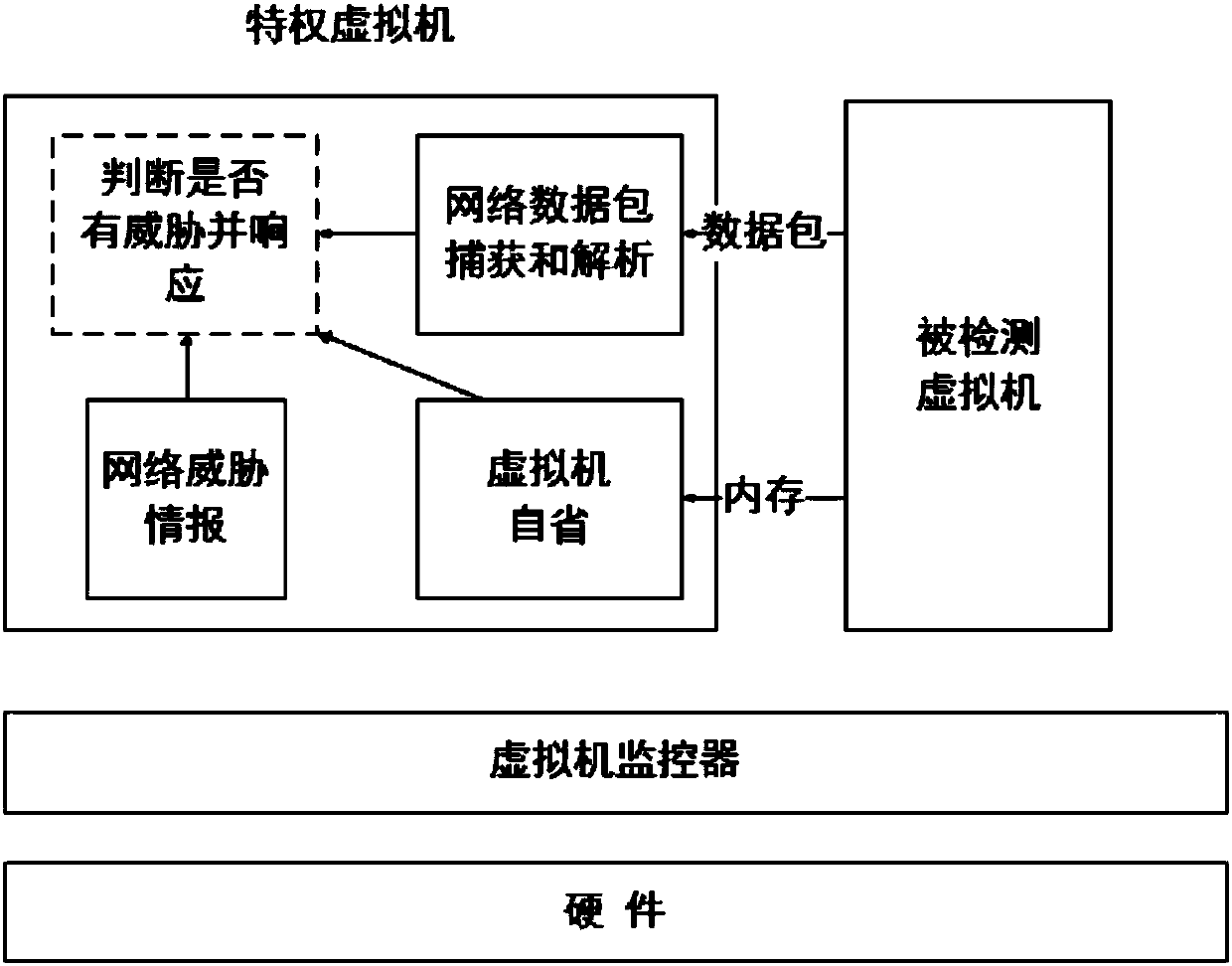
Threat intelligence response and disposal method and system based on virtual machine introspection
ActiveCN107608752AEasy maintenanceAvoid attackPlatform integrity maintainanceSoftware simulation/interpretation/emulationCyber threat intelligenceNetwork packet
The invention relates to a threat intelligence response and disposal method and system based on virtual machine introspection. A threat detection and response module is deployed on a privilege virtualmachine except a detected virtual machine; a virtual machine introspection technology is used for obtaining a port number-transmission layer network protocol-process corresponding relationship in thedetected virtual machine which carries out network communication; the network data package of virtual machine communication is captured and analyzed; a network threat intelligence database is used for judging whether the data package has threats or not; and if the data package has threats, a thread alarm is given, and the obtained corresponding relationship is used for positioning and threateningthe virtual machine process of thread source communication so as to block the process or the port and the like. By use of the method and the system, the threat detection and response module is deployed on the outer part of the detected virtual machine, the detection and response module is effectively protected, meanwhile, process-level network threat detection and response can be finished, existing cloud architecture does not need to be changed, and the method and the system can be conveniently applied to a server of a cloud service provider.
Owner:INST OF INFORMATION ENG CAS
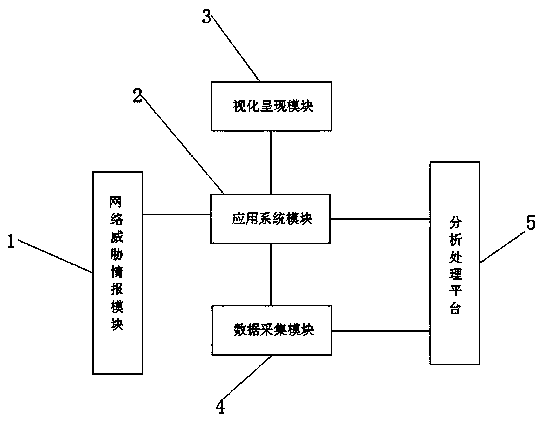
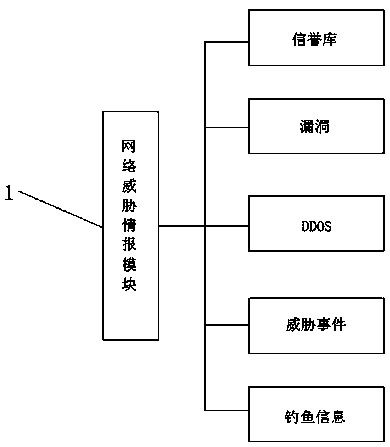
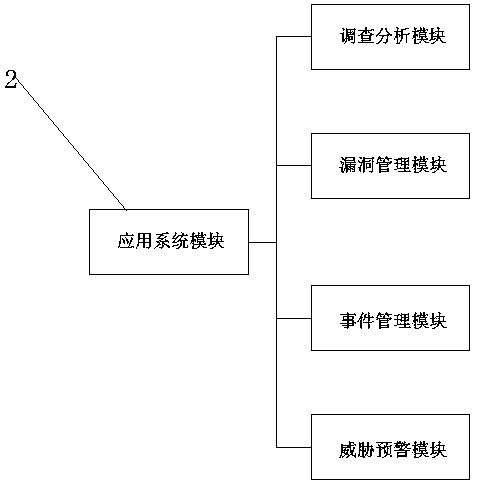
Computer network security situation awareness platform architecture
InactiveCN110247888AImplement asset managementImplement Vulnerability ManagementTransmissionCyber threat intelligenceData platform
The invention discloses a computer network security situation awareness platform architecture. The computer network security situation awareness platform architecture comprises a network threat information module, an application system module, a data acquisition module and an analysis processing platform, wherein the network threat information module is connected with the application system module; the application system module is connected with the data acquisition module; the application system module and the data acquisition module are respectively connected with the analysis processing platform; and the analysis processing platform extracts the network threat information acquired by the data acquisition module. The computer network security situation awareness platform architecture has the advantages that information network related data are comprehensively collected; threat intelligence is fused for safety management and safety analysis based on a big data platform, asset management, vulnerability management, event management, threat alarm, investigation and analysis, emergency response and other service functions are achieved; and technical support is provided for safety operation (management, analysis and response) teams.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY +1
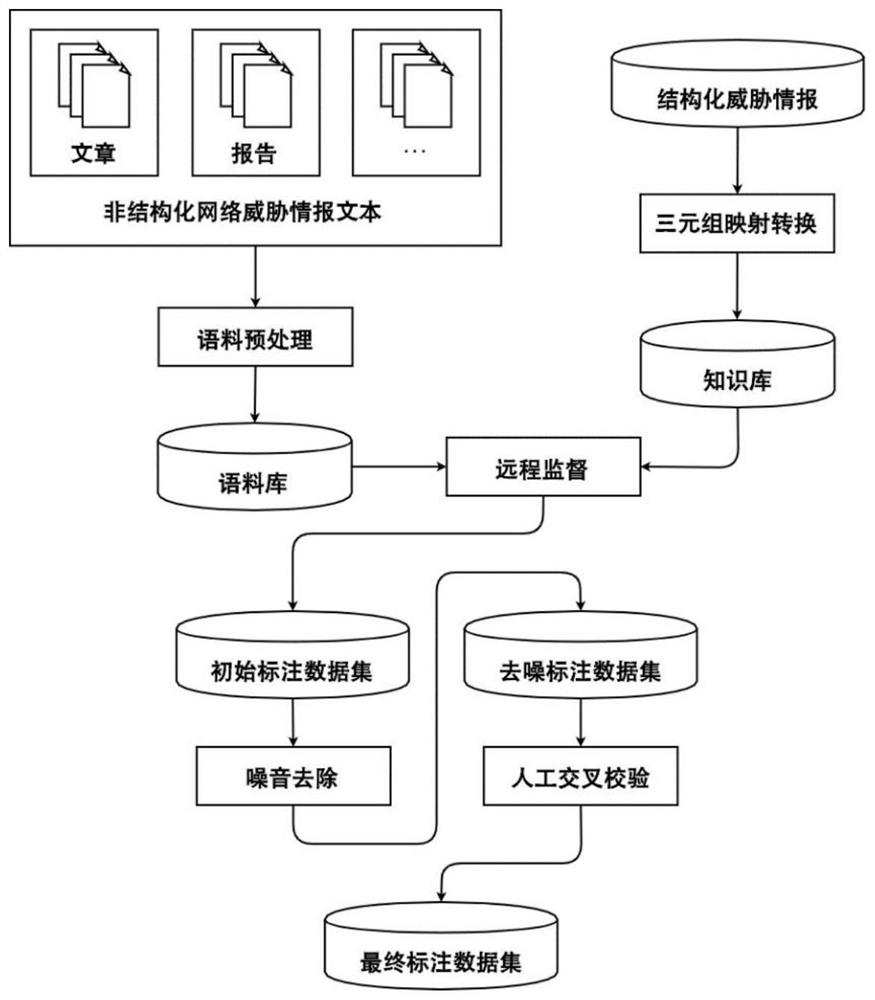
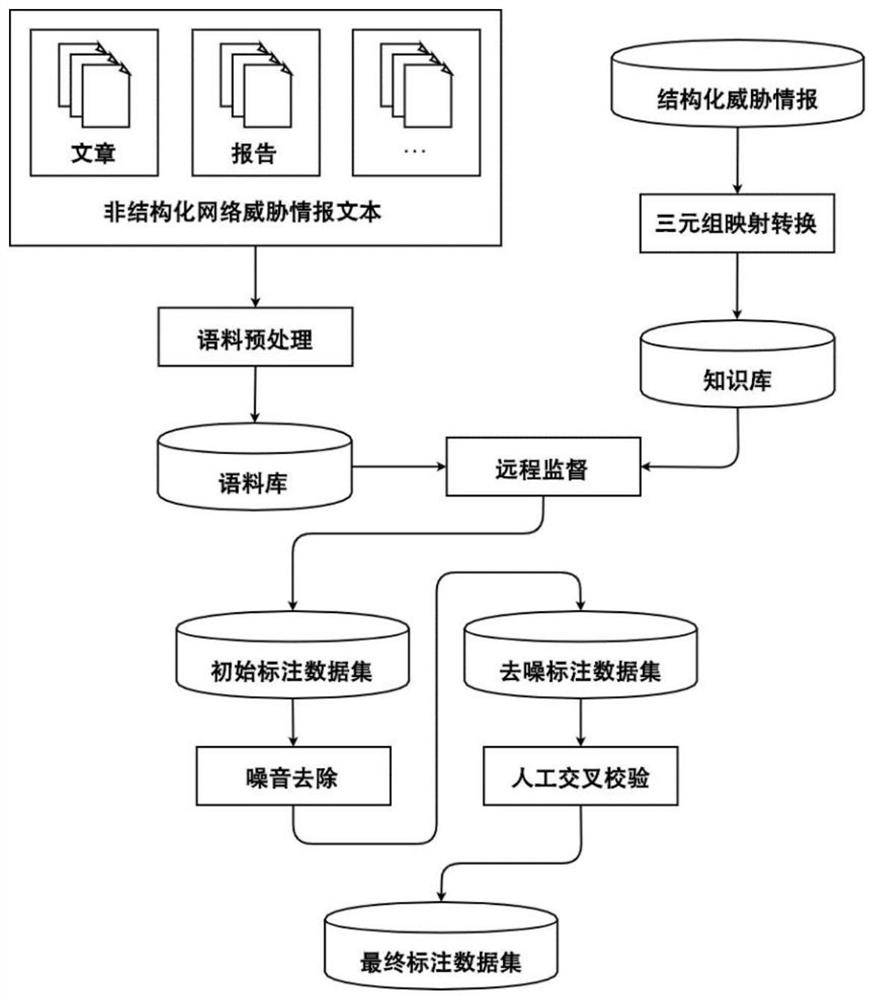
Network threat intelligence-oriented annotation corpus generation method and electronic device
ActiveCN111859966ASolve the problem of noisy dataRealize semi-automatic generationNatural language data processingSpecial data processing applicationsCyber threat intelligenceData set
The invention provides a network threat intelligence-oriented annotation corpus generation method and an electronic device, and the method comprises the steps of extracting a safety entity in a structured threat intelligence data training set, mapping each piece of structured threat intelligence data into a (head entity, relation type and tail entity) triple, and obtaining a head entity set and atail entity set; extracting security entities in the to-be-labeled text, and obtaining sentences containing at least one security entity belonging to the head entity set and at least one security entity belonging to the tail entity set; judging a relationship type contained in the sentence; annotating each (head entity, relationship type and tail entity) triple of all sentences to obtain an initial annotation data set, and then obtaining a denoised annotation data set. According to a remote supervision theory, existing structured network threat intelligence data is utilized to label unlabeledcorpora, large-scale training corpora are generated, and an automatic denoising and cross validation method is provided to solve the problem that noise data exists in the labeled corpora.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
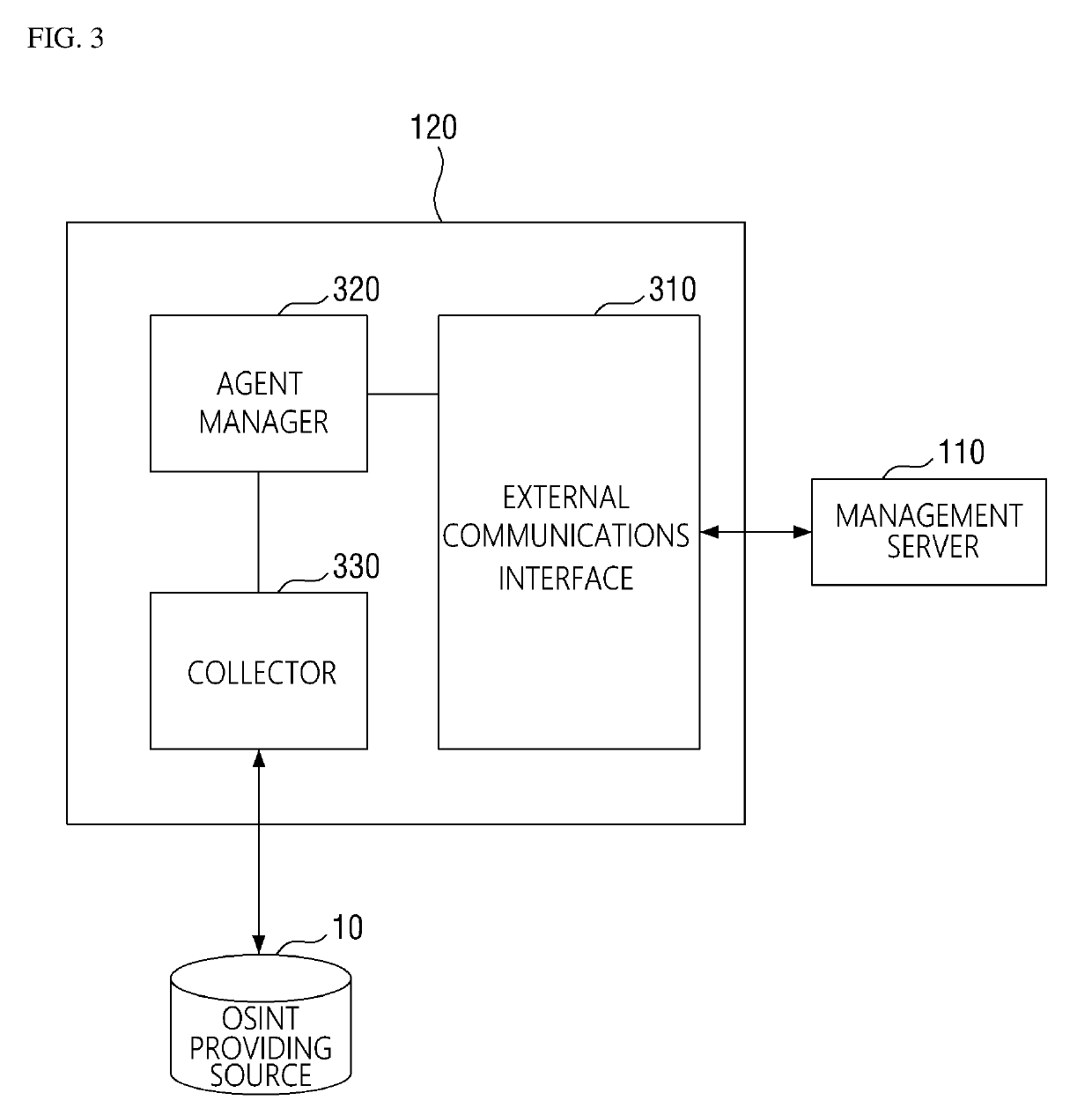
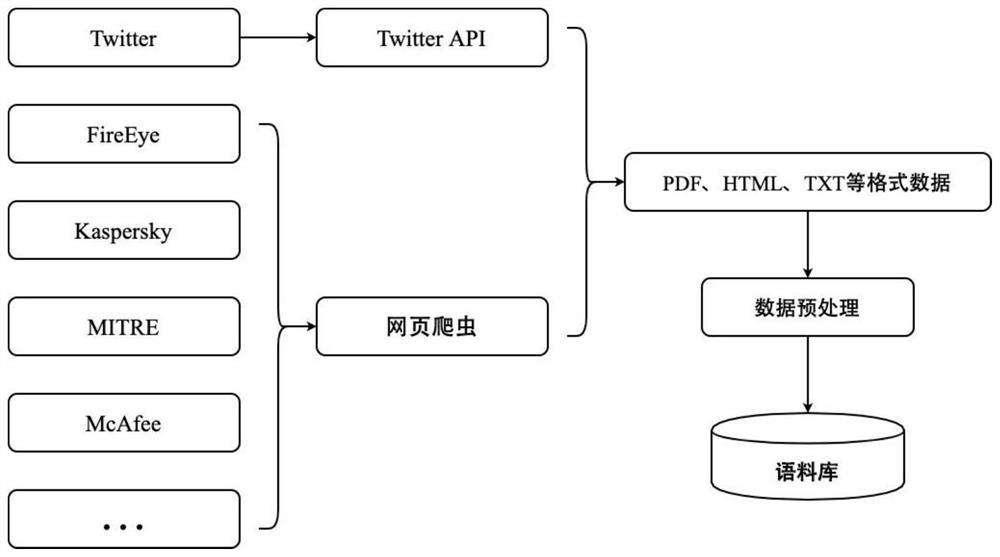
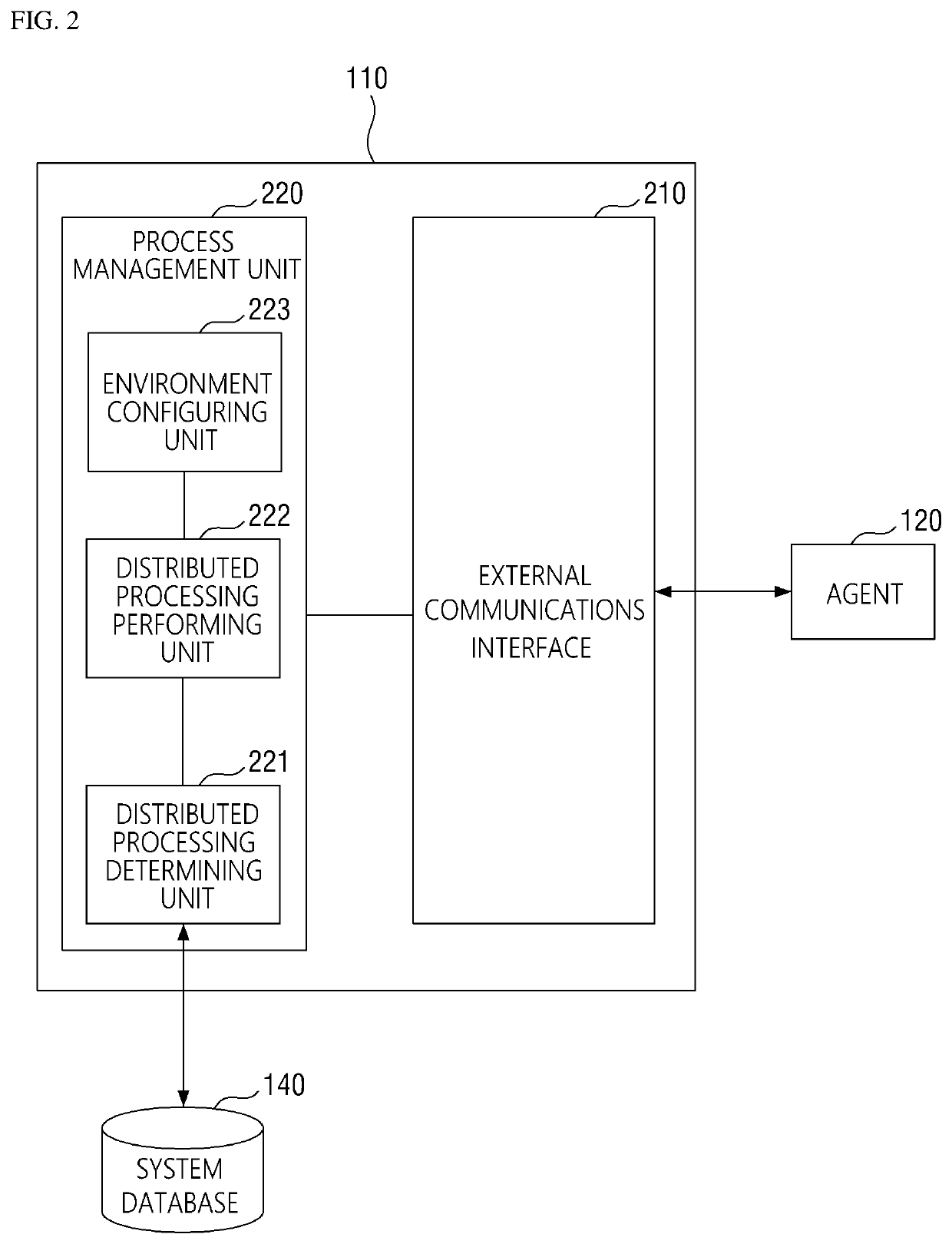
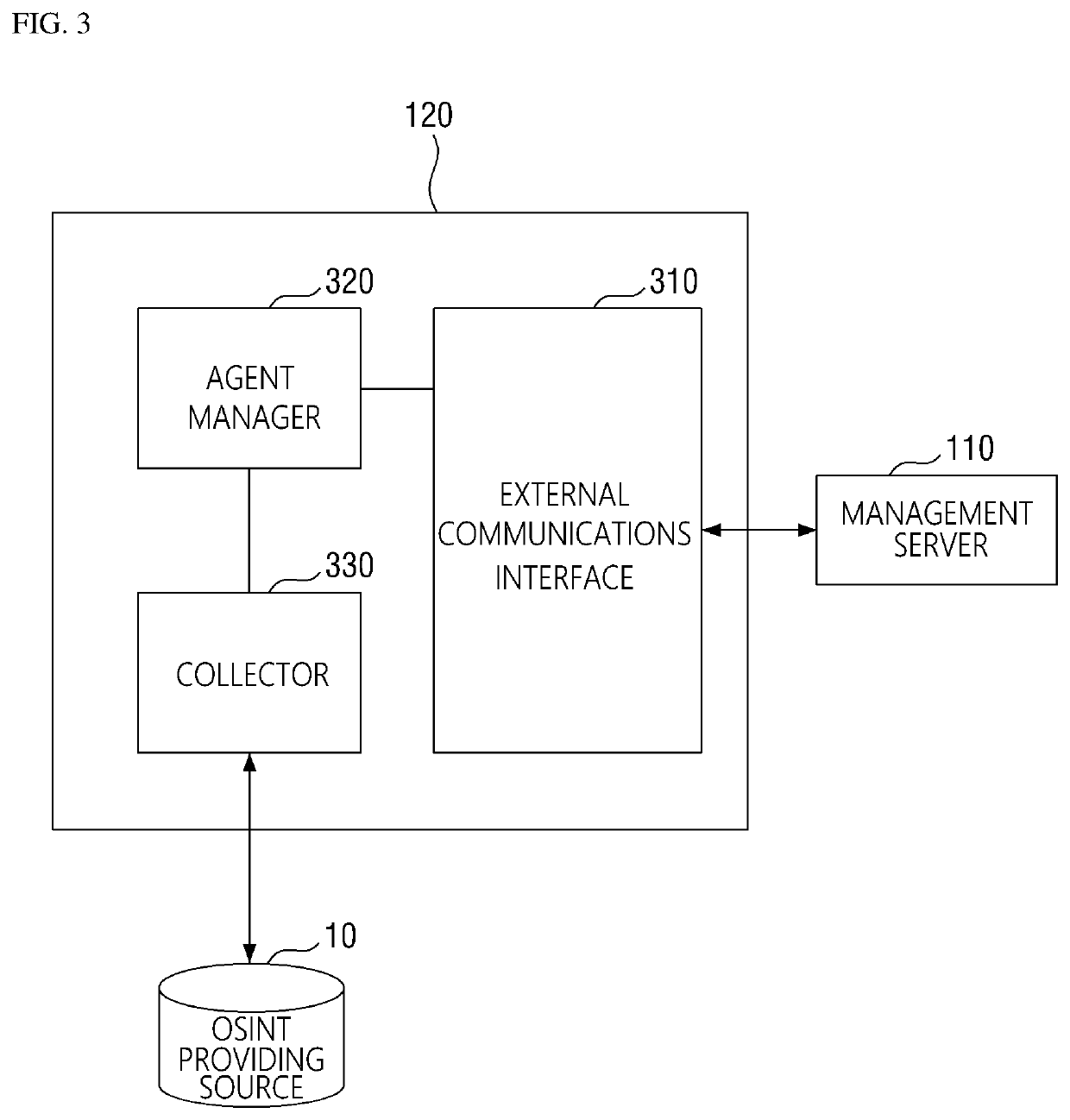
Method for collecting cyber threat intelligence data and system thereof
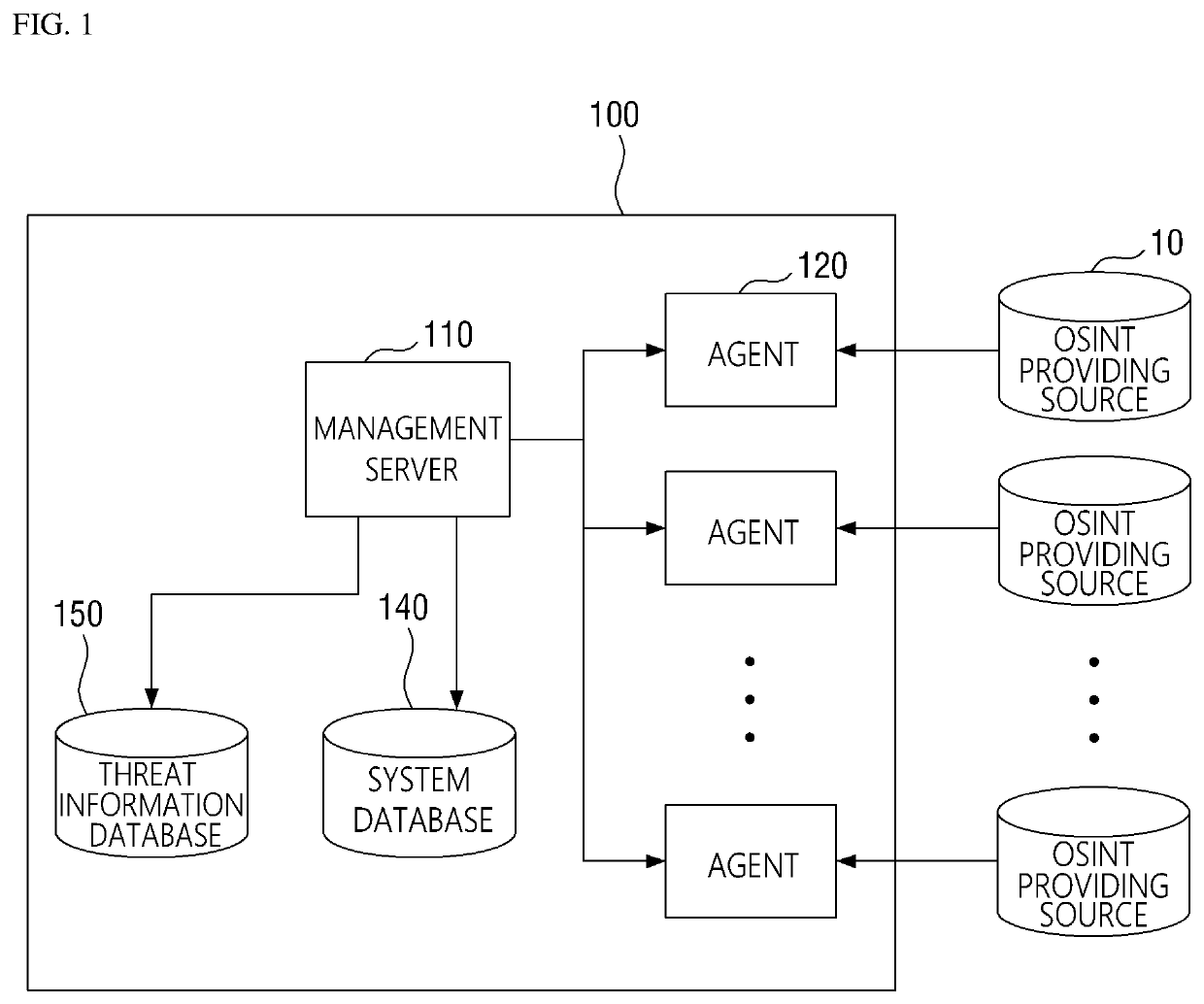
ActiveUS20190166143A1More system resourceEfficient use ofPlatform integrity maintainanceData switching networksCyber threat intelligenceDatabase
Disclosed herein are a method and system for collecting cyber threat intelligence (CTI) data. The system includes a management server that determines agent configuration values associated with an OSINT providing source, an agent that receives the agent configuration values from the management server, performs a data collection task for collecting the CTI data based on the agent configuration values, and transmits the CTI data and data collection status information to the management server, a threat information database where which the CTI data is logged, and a system database where the data collection status information is logged.
Owner:KOREA INTERNET & SECURITY AGENCY
Methods and Systems for Efficient Network Protection
ActiveUS20200106742A1Improve efficiencyImprove performanceData switching networksComputer networkCyber threat intelligence
Methods and systems are disclosed for integrating cyber threat intelligence (CTI), threat metadata, and threat intelligence gateways with analysis systems to form efficient and effective system for active, proactive, and reactive network protection. A network gateway may be composed of multiple stages. A first stage may include a threat intelligence gateway (TIG). A second stage may include one or more cyber analysis systems that ingest TIG-filtered communications and associated threat metadata signals. A third stage may include network protection logic that determines which protective actions. The gateway may be provisioned and configured with rules that specify the network protection policies to be enforced. The gateway may ingest all communications flowing between the protected network and the unprotected network.
Owner:CENTRIPETAL NETWORKS LLC
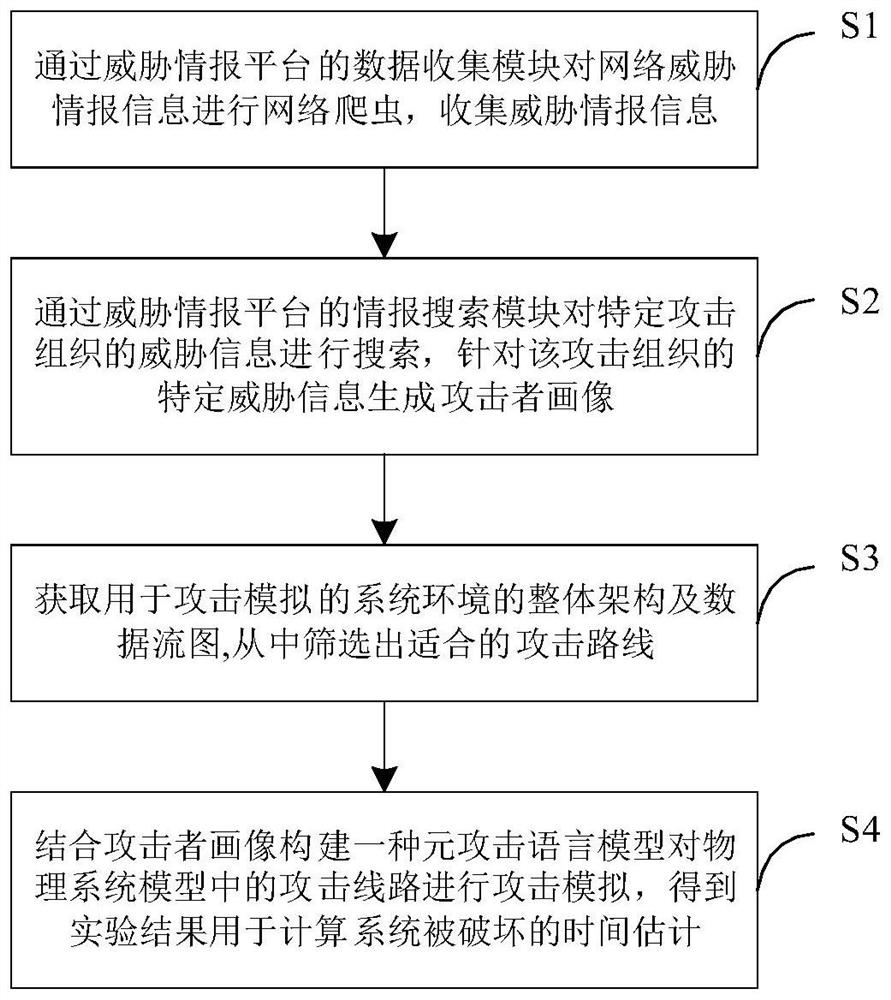
Attack simulation method based on network threat intelligence in industrial Internet of Things
PendingCN114547415ASolve the problem of low integrationComprehensive and effective graspWeb data indexingSemantic analysisCyber threat intelligenceData stream
The invention provides an attack simulation method based on network threat intelligence in an industrial internet of things, which comprises the following steps of: threat intelligence collection: carrying out web crawler on network threat intelligence information through a threat intelligence platform, and collecting the threat intelligence information; generating an attacker portrait: searching threat information of the attack organization, and generating the attacker portrait according to the threat information; acquiring an attack route: acquiring an overall architecture and a data flow diagram of a system environment for attack simulation, and screening out a suitable attack route; and attack simulation: constructing a meta-attack language model in combination with an attacker portrait, performing attack simulation on an attack line, and obtaining an experimental result for calculating time estimation of system damage. According to the invention, the problem of low integration level of threat intelligence and attack simulation technology is solved, and specific threats can be automatically evaluated, so that security personnel can quickly take positive measures, and the threat response capability and attack resistance capability of an industrial Internet of Things system are improved.
Owner:ZHONGYUAN ENGINEERING COLLEGE
Transaction promotion method of threat intelligence transaction alliance chain based on benefit distribution
ActiveCN111522884APromote healthy developmentFinanceDatabase distribution/replicationCyber threat intelligenceFinancial transaction
The invention belongs to the technical field of benefit allocation-based transaction promotion in a network threat intelligence transaction alliance chain, and particularly relates to a transaction promotion method for a threat intelligence transaction alliance chain based on benefit distribution. Aiming to solve the problem of identity privacy protection of a transaction endorsement user in a threat intelligence transaction alliance chain transaction process, on the basis of a fragmentation mechanism of an alliance chain, a game strategy of nodes under a unified benefit distribution and fairbenefit distribution mechanism is analyzed by combining a game theory method, cooperation equilibrium conditions of the nodes are studied, and a benefit distribution mechanism based on fragmentation fair distribution is provided under the cooperation equilibrium conditions of the fair benefit distribution mechanism. According to the invention, the effect of attracting more users to participate intransaction cooperation can be achieved, and the goal of threatening benign development of intelligence transactions is achieved.
Owner:HARBIN ENG UNIV
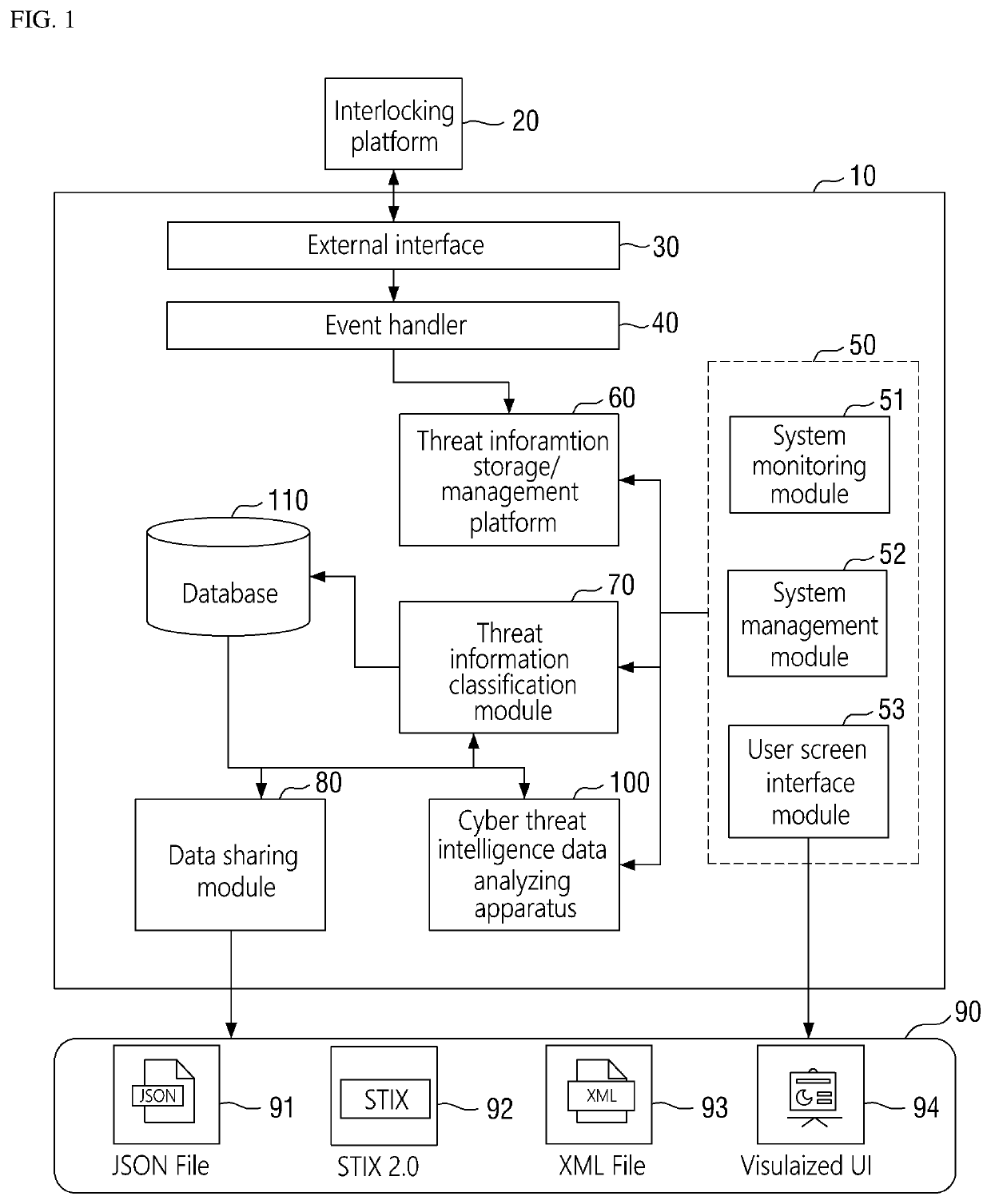
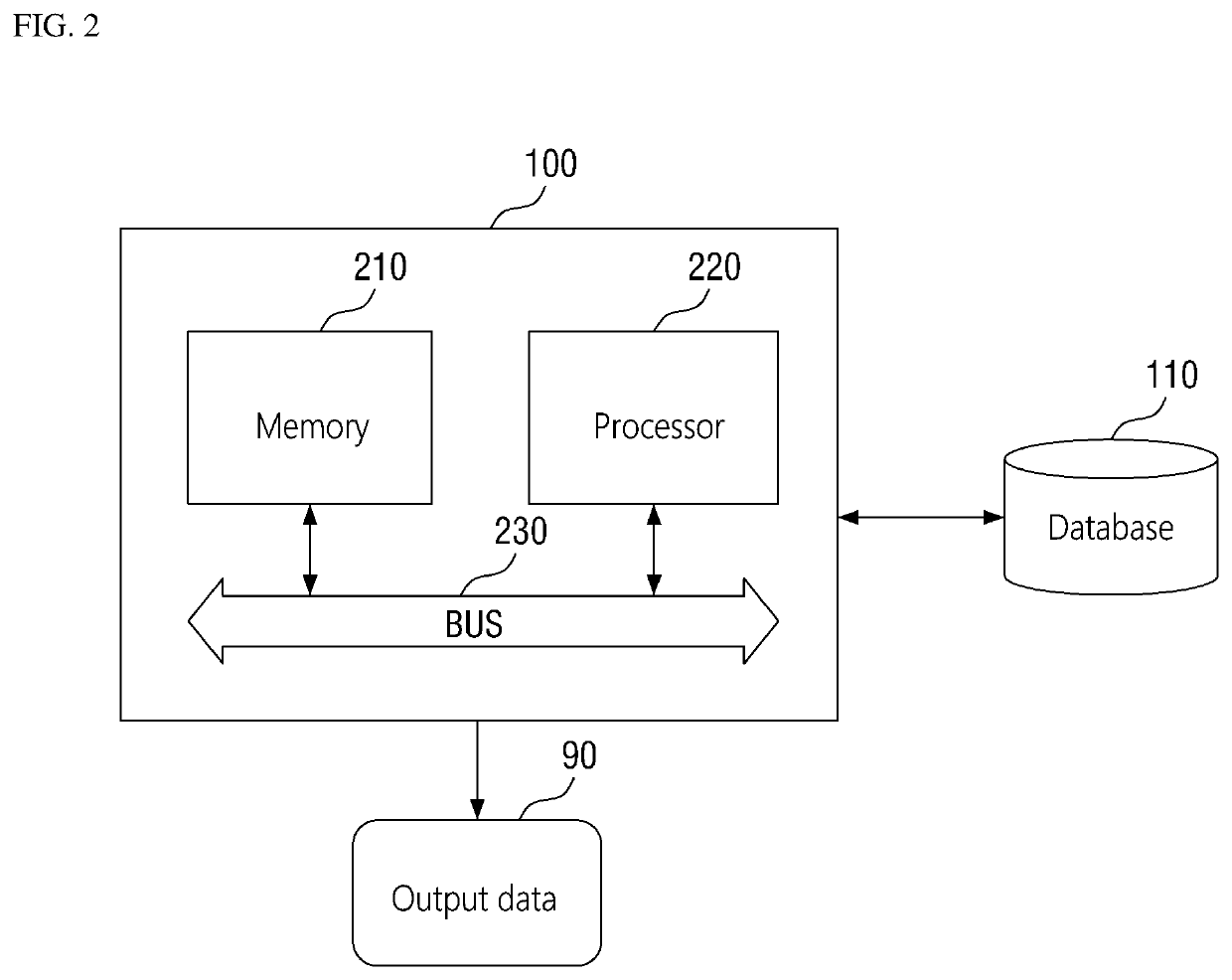
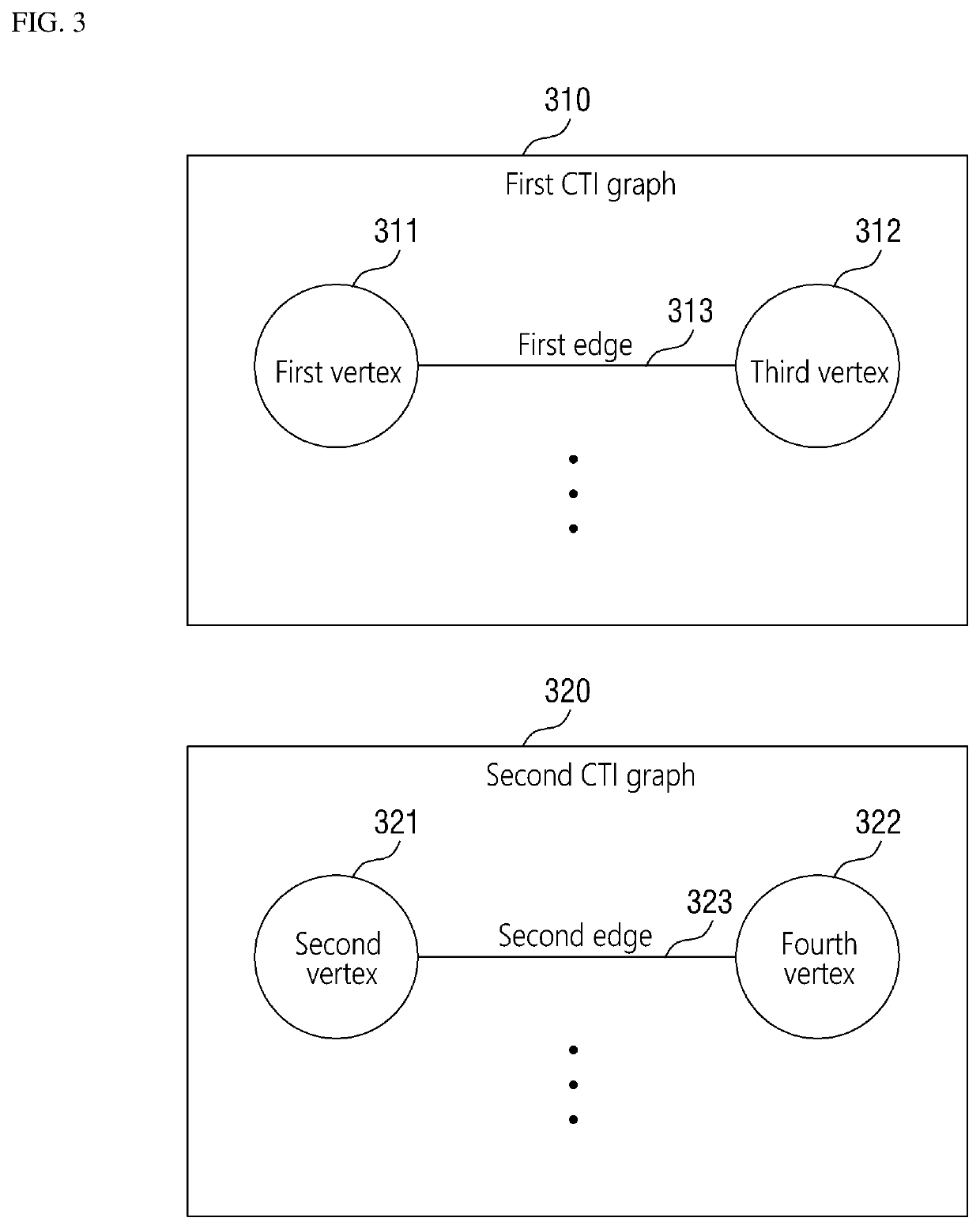
Method for analyzing cyber threat intelligence data and apparatus thereof
ActiveUS11005869B2Easy to useRelational databasesOther databases indexingCyber threat intelligenceTheoretical computer science
A method and apparatus for analyzing cyber threat intelligence data. The method includes: acquiring first and second CTI graphs including first and second CTI data, respectively, classified based on a first classification item; classifying the first CTI data and the second CTI data based on a second classification item determined depending on the first classification item; outputting a graph similarity of the first and second CTI graphs determined based on a first CTI similarity between the first and second CTI data when the first and second CTI data belong to the same classification as a result of the classification; setting the first CTI graph and the second CTI graph to be included in one group when the graph similarity is equal to or greater than a threshold value; and outputting CTI information including the first and second CTI data for each group.
Owner:KOREA INTERNET & SECURITY AGENCY
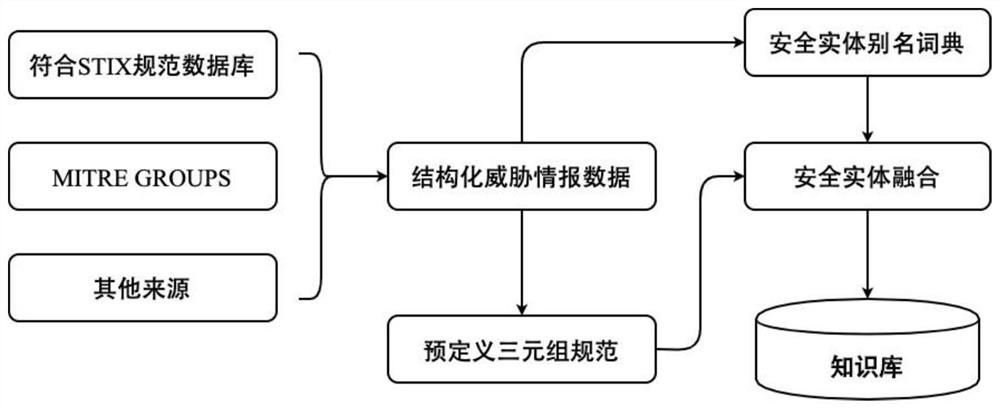
Method and system for fusing network threat intelligence metadata
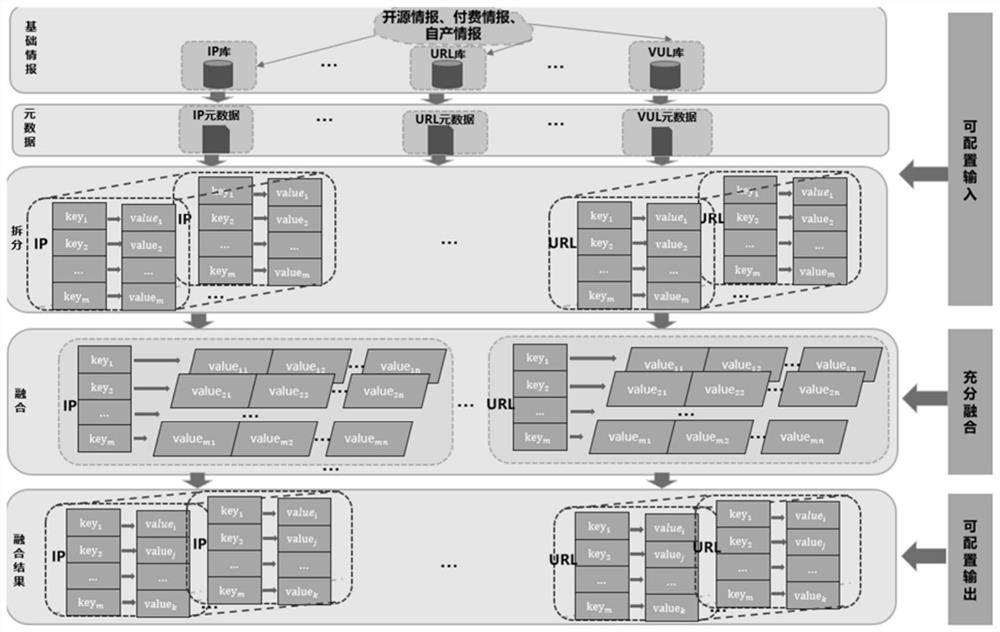
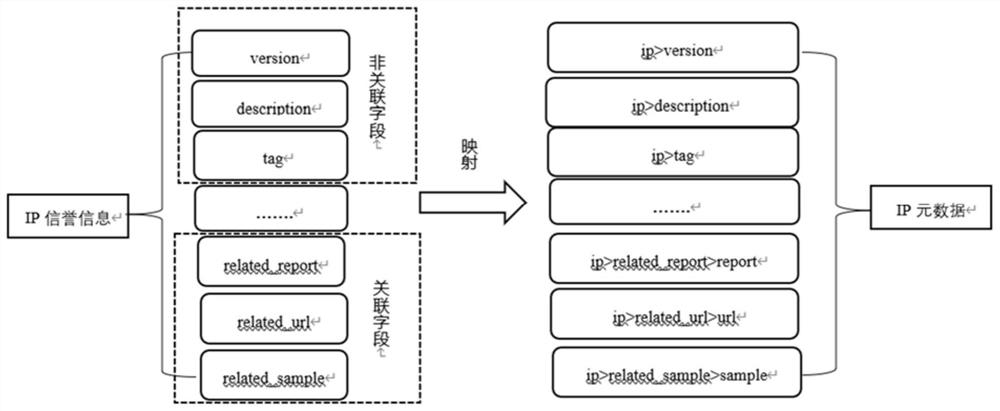
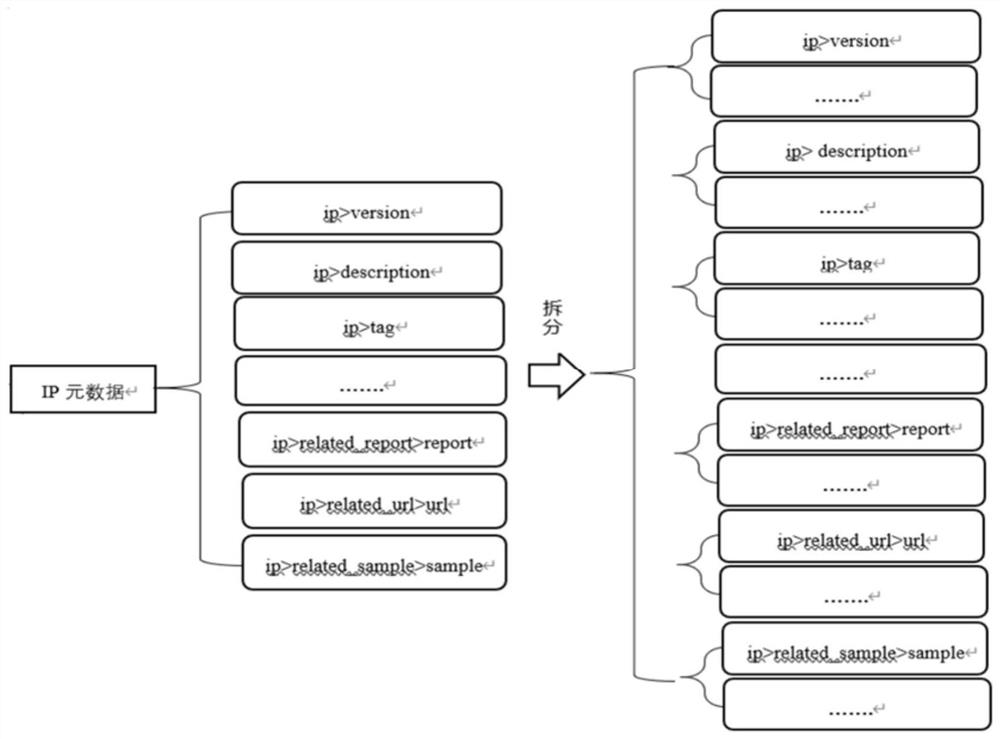
PendingCN112667766AImprove experienceCharacter and pattern recognitionTransmissionCyber threat intelligenceEngineering
The invention designs a method and system for fusing network threat intelligence metadata, which are used for solving multi-source heterogeneous network threat intelligence conflicts. The method comprises the following steps: converting unstructured network threat intelligence data into structured network threat intelligence; mapping the structured network threat intelligence data and metadata; splitting the network threat intelligence metadata; fusing the network threat intelligence metadata; and providing the fused metadata for network security threat intelligence analysts in an interface form through a customized output template. According to the invention, the network threat intelligence data can be fused in a finer-grained manner, and the fused result is automatically configured.
Owner:INST OF INFORMATION ENG CAS
Method and system for analyzing cybersecurity threats and improving defensive intelligence
ActiveUS20220217163A1Mathematical modelsPlatform integrity maintainanceCyber-attackCyber threat intelligence
Owner:THREATOLOGY INC
Affectedness scoring engine for cyber threat intelligence services
ActiveUS11194905B2Digital data information retrievalPlatform integrity maintainanceManaged security serviceCyber threat intelligence
A network-accessible cyber-threat security analytics service is configured to characterize and respond to a description that includes threat indicators (e.g., IOCs), and an initial severity. Enterprises register with the service by providing identifying information, such as industry, geographies, and the like. For each threat indicator, a query is sent to each of a set of one or more security knowledge bases, and at least some of the queries are scoped by the enterprise industry / geo information specified. The knowledge bases may vary but typically include: a managed security service, a cyber threat intelligence service, and a federated search engine that searches across one or more enterprise-connected data sources. Responses to the queries are collected. A response provides an indication whether the threat indicator identified in the query has been sighted in the knowledge base and the frequency. The system then adjusts the initial severity to reflect the indications returned from querying the security knowledge bases.
Owner:INT BUSINESS MASCH CORP
Ring signature method applied to threat intelligence transaction alliance chain
ActiveCN111698090AProtect identity privacyAnonymityUser identity/authority verificationCyber threat intelligenceInternet privacy
The invention belongs to the technical field of ring signature applied to a network threat intelligence transaction alliance chain, and particularly relates to a ring signature method applied to a threat intelligence transaction alliance chain. Aiming at the problem of identity privacy protection of a transaction endorsement user in a threat intelligence transaction alliance chain, the method is used for identity privacy encryption of the endorsement user in the threat intelligence transaction alliance chain. The method has anonymity, security and unforgeability, and can be used for threatening the identity anonymization of the transaction endorsement user in the intelligence transaction alliance chain to protect the identity privacy of the transaction endorsement user in the alliance chain.
Owner:HARBIN ENG UNIV
A unified accusation method and system for network security equipment
The invention belongs to the technical field of network security, and in particular relates to a unified accusation method and system for network security equipment, comprising the following steps: generating a network defense strategy according to received network threat intelligence; judging whether the generated network defense strategy contains local area network information , command the command center to send a request to all LAN managers to update the attribute lists of all managed LAN security devices; generate corresponding network defense commands through the security devices specified in the network defense policy and their command format files, and send them to The aforementioned LAN security device; the LAN security device executes the network defense command and returns a response to the command command center. The present invention dynamically and uniformly instructs various security devices, and the security devices include an intrusion detection system, a virtual private network, and a security gateway, and can perform rapid defense.
Owner:HARBIN ENG UNIV
Annotated corpus generation method and electronic device for network threat intelligence
ActiveCN111859966BSolve the problem of noisy dataRealize semi-automatic generationNatural language data processingSpecial data processing applicationsData setCyber threat intelligence
The present invention provides a method and electronic device for generating tagged corpus oriented to network threat intelligence, including: extracting security entities in a training set of structured threat intelligence data, and mapping each structured threat intelligence data into <头实体、关系类型、尾实体>Triple group, get the head entity set and tail entity set; extract the security entity in the text to be marked, and obtain the sentence containing at least one security entity belonging to the head entity set and at least one security entity belonging to the tail entity set; judge whether the sentence contains relation type; for all sentences <头实体、关系类型、尾实体>The triplets are labeled to obtain the initial labeled data set, and then the denoised labeled data set. According to the remote supervision theory, the present invention uses existing structured network threat intelligence data to mark unmarked corpus to generate large-scale training corpus, and proposes automatic denoising and cross-checking methods to solve the problem of noise data in the marked corpus.< / 头实体、关系类型、尾实体>
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Method and device for extracting entity relationship from network threat intelligence document
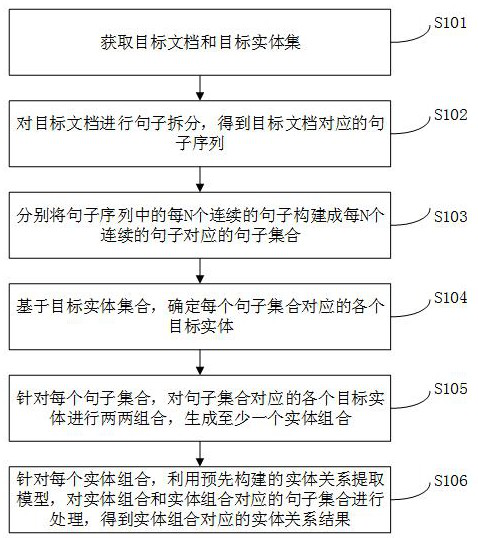
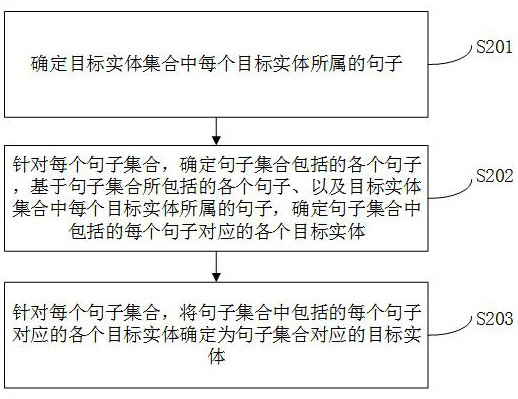
ActiveCN113515598BAddress effectivenessImprove threat analysis capabilitiesNatural language data processingText database queryingCyber threat intelligenceSentence pair
This application provides a method and device for extracting entity relations of network threat intelligence documents, which can obtain target documents and target entity sets; perform sentence splitting on target documents to obtain sentence sequences corresponding to target documents; Consecutive sentences are constructed into a sentence set corresponding to every N consecutive sentences; based on the target entity set, each target entity corresponding to each sentence set is determined; for each sentence set, each target entity corresponding to the sentence set is combined in pairs , generate at least one entity combination; for each entity combination, use the pre-built entity relationship extraction model to process the entity combination and the sentence set corresponding to the entity combination, and obtain the entity relationship result corresponding to the entity combination, realizing the network threat The entity relationship extraction at the intelligence document level solves the problem that the threat intelligence text is too long to effectively extract key relationships, and improves the blockchain network threat analysis capability.
Owner:STATE GRID E COMMERCE CO LTD +2
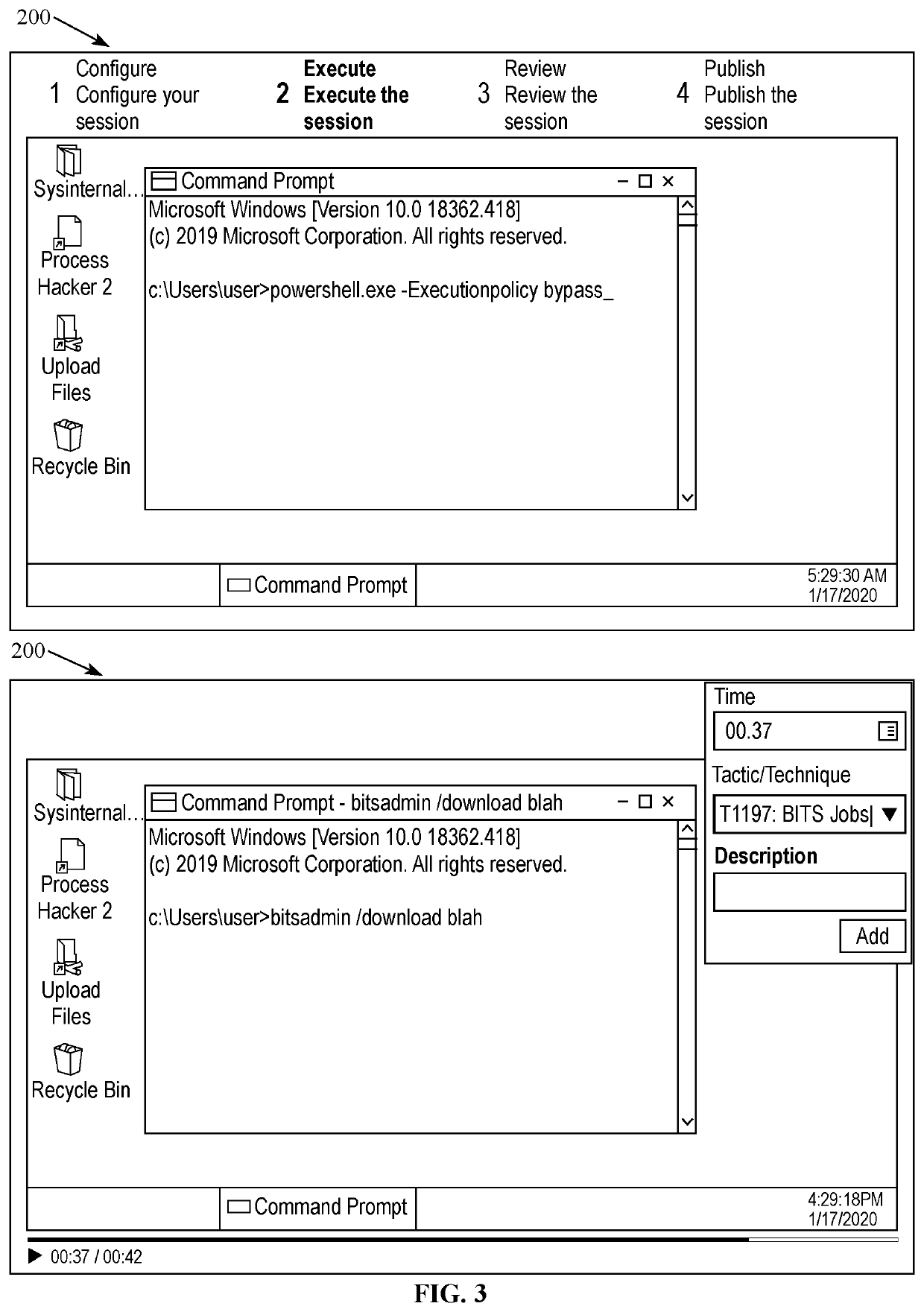
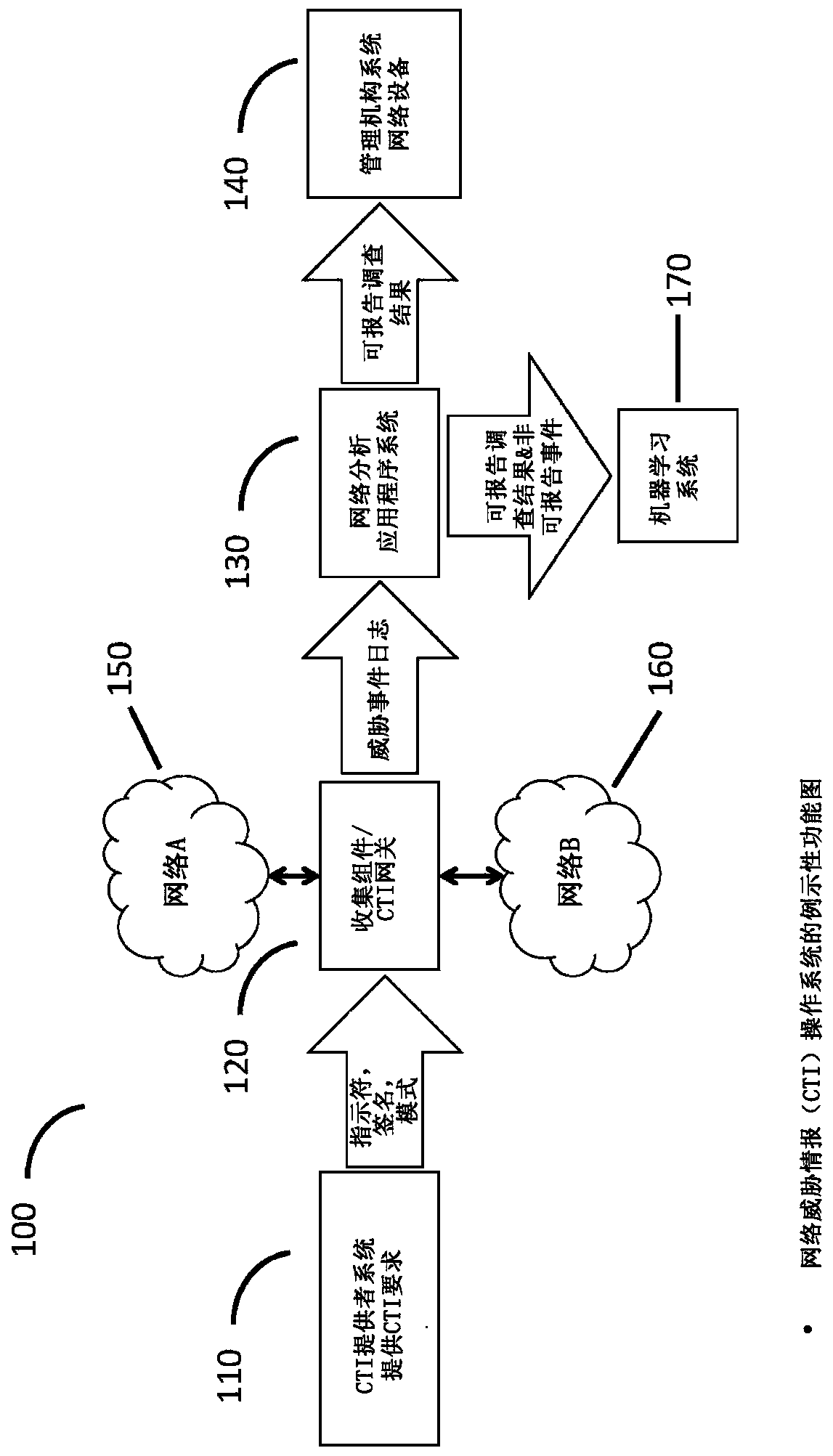
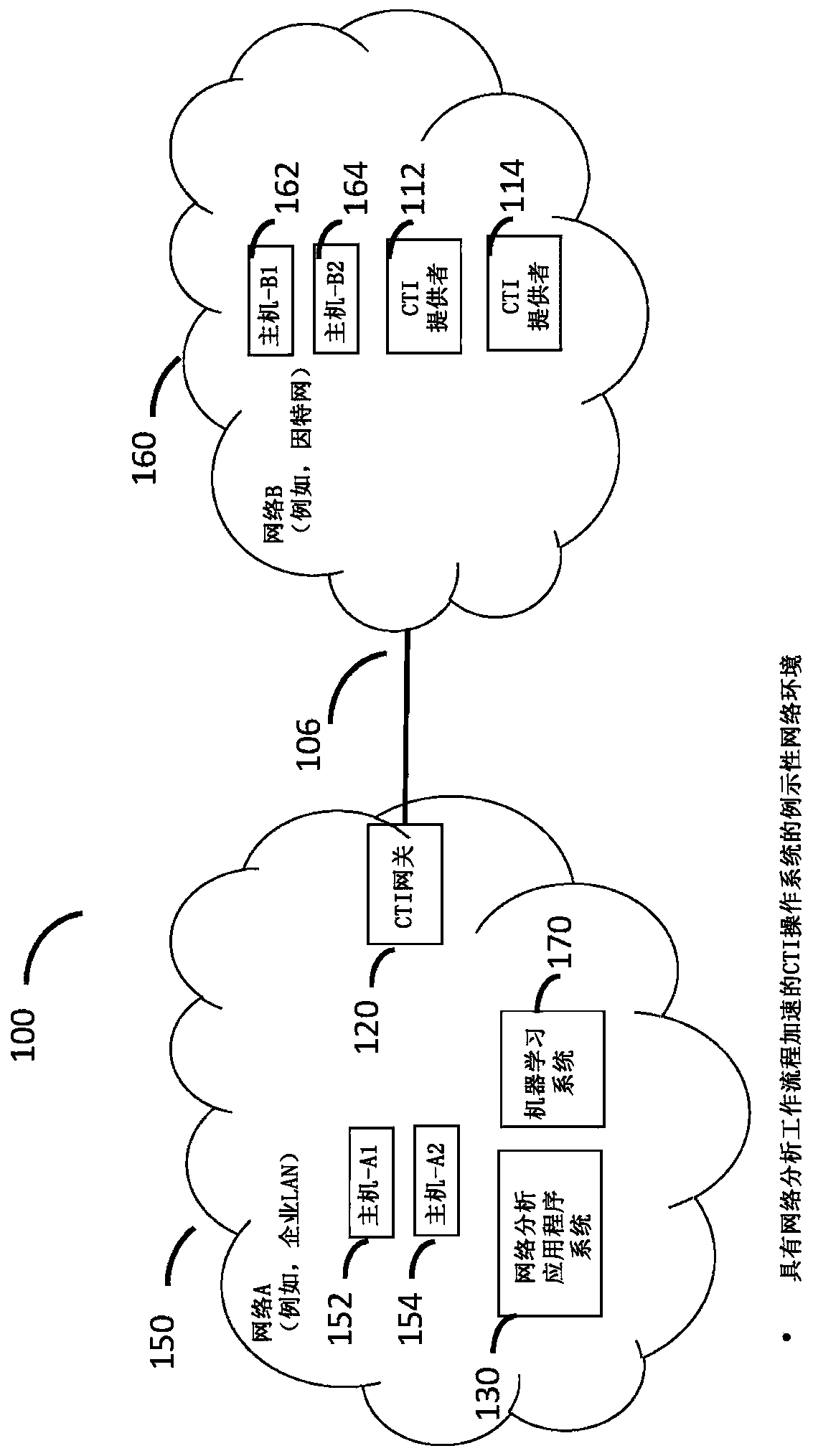
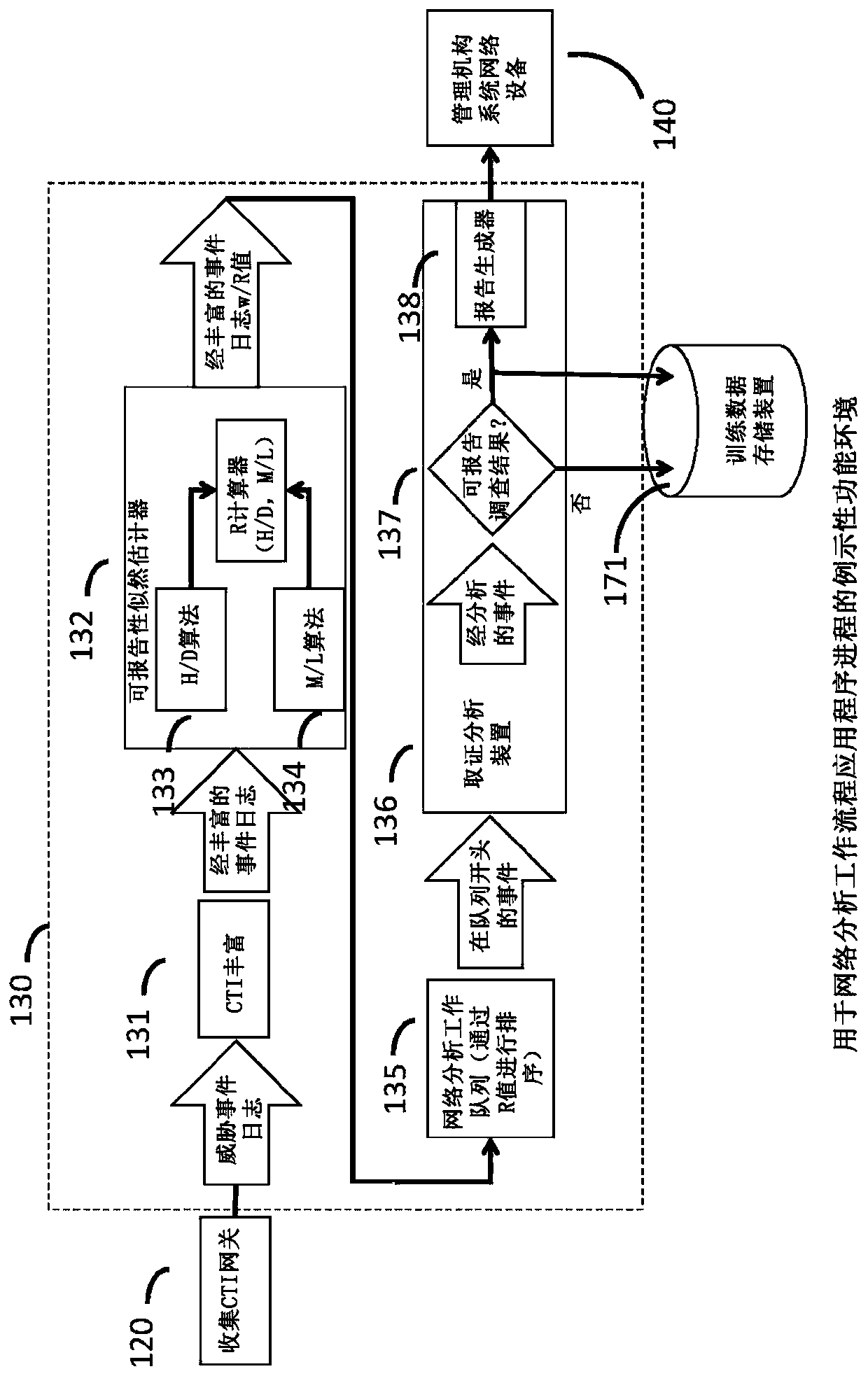
Cyberanalysis workflow acceleration
A cyber threat intelligence (CTI) gateway device may receive rules for filtering TCP / IP packet communications events that are configured to cause the CTI gateway device to identify communications corresponding to indicators, signatures, and behavioral patterns of network threats. The CTI gateway device may receive packets that compose endpoint-to-endpoint communication events and, for each event,may determine that the event corresponds to criteria specified by a filtering rule. The criteria may correspond to one or more of the network threat indicators, signatures, and behavioral patterns. The CTI gateway may create a log of the threat event and forward the threat event log to a task queue managed by a cyberanalysis workflow application. Human cyberanalysts use the cyberanalysis workflowapplication to service the task queue by removing the task at the front of the queue, investigating the threat event, and deciding whether the event is a reportable finding that should be reported tothe proper authorities. In order to improve the efficiency of the workflow process, tasks in the queue are ordered by the likelihood, or probability, that cyberanalysts will determine the associated threat events to be reportable findings; thus, high-likelihood events are investigated first. Likelihoods are computed using human-designed algorithms and machine-learned algorithms that are applied tocharacteristics of the events. Low-likelihood events may be dropped from the work queue to further improve efficiency.
Owner:向心有限公司
A Network Threat Intelligence Sharing Model
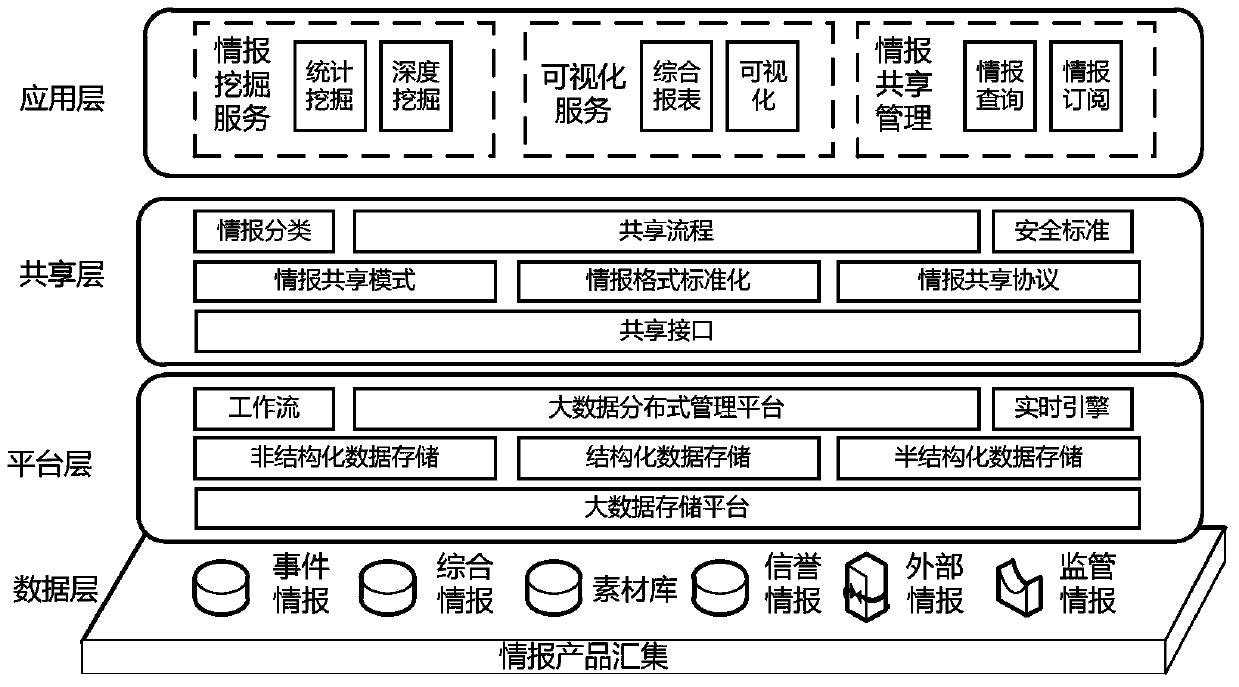
ActiveCN106060018BFast deliveryImprove responsivenessTransmissionCyber threat intelligenceInformation sharing
The invention discloses a network threat information sharing model which comprises a data layer, a platform layer, a sharing layer and an application layer which longitudinally pass through threat information sharing. The network threat information sharing model aims to solve the problems that unified standards are absent between existing network threat information automatic processing and cross-department information sharing, the information sharing efficiency is low, and the leakage risk is caused by sharing. In order to provided the unified specifications and standards for cross-department information sharing, the network threat information sharing model comprises data sharing type standards, sharing protocol standards and the like; for the problem that the sharing efficiency is low, a mixed sharing technology is provided, and that is to say, the requirements of different information sharing applications are met by the modes such as concentrated sharing and point-to-point sharing; and for the leakage risk caused by sharing, an information sharing level classification method is provided, the sharing range of information is limited by different categories, and the leakage risk caused by excessive sharing is lowered.
Owner:CHINA ELECTRONICS TECH CYBER SECURITY CO LTD
Network threat intelligence text key information extraction method based on weak supervised learning
ActiveCN114138966ALiberation character level labeling pressureImprove interpretabilitySemantic analysisNeural architecturesCyber threat intelligenceEngineering
The invention discloses a network threat intelligence text key information extraction method based on weak supervised learning, and the method comprises the steps: converting information extraction into a feature data space mapping task, combining a knowledge representation learning method, adopting an attention mechanism based on a local sequence, and utilizing a text theme label to extract key information of a network threat intelligence text; key information extraction of a weak supervised learning text is realized, the quality of the extracted information is verified by using a manual evaluation and confidence evaluation mode, and the information is ensured to be real, reliable and credible. The method comprises the following steps: training a more accurate, comparative and basis key information extraction model for a text, and hoping that the key information formed by the extraction model can reflect the actual semantic value of a sequence tag rationally; through a weak supervised learning strategy and two evaluation methods defined by the method, through end-to-end network training, the complexity and time cost of information extraction are reduced, and the accuracy and recall rate of key information extracted by the method in label classification are improved.
Owner:SICHUAN UNIV
Method and system for efficient packet filtering
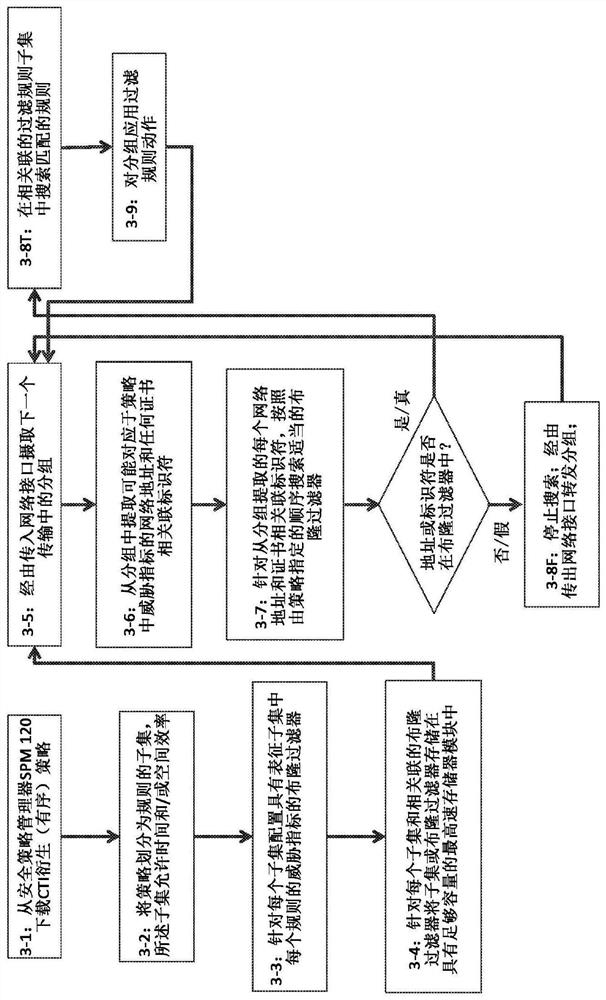
PendingCN114514727AHigh false positive rateSecuring communicationCyber threat intelligenceInternet traffic
The packet gateway may protect the TCP / IP network by enforcing security policies on in-transit packets across network boundaries. The policy may include network threat intelligence (CTI) derived packet filtering rules. The rapid increase of the CTI amount and the size of the associated CTI derivation strategy, and the continuously increased network link speed and network flow may stop the cost of enough computing resources. To efficiently process packets, a packet gateway may be provided with at least one probabilistic data structure, such as a Bloom filter, for testing packets to determine whether packet data may match packet filtering rules. The packet filtering rules may be grouped into subsets of rules, and a data structure may be provided for determining a subset of matching rules associated with a particular packet.
Owner:向心有限公司
Method for collecting cyber threat intelligence data and system thereof
ActiveUS10986112B2More system resourceEfficient use ofPlatform integrity maintainanceData switching networksCyber threat intelligenceEngineering
Disclosed herein are a method and system for collecting cyber threat intelligence (CTI) data. The system includes a management server that determines agent configuration values associated with an OSINT providing source, an agent that receives the agent configuration values from the management server, performs a data collection task for collecting the CTI data based on the agent configuration values, and transmits the CTI data and data collection status information to the management server, a threat information database where which the CTI data is logged, and a system database where the data collection status information is logged.
Owner:KOREA INTERNET & SECURITY AGENCY
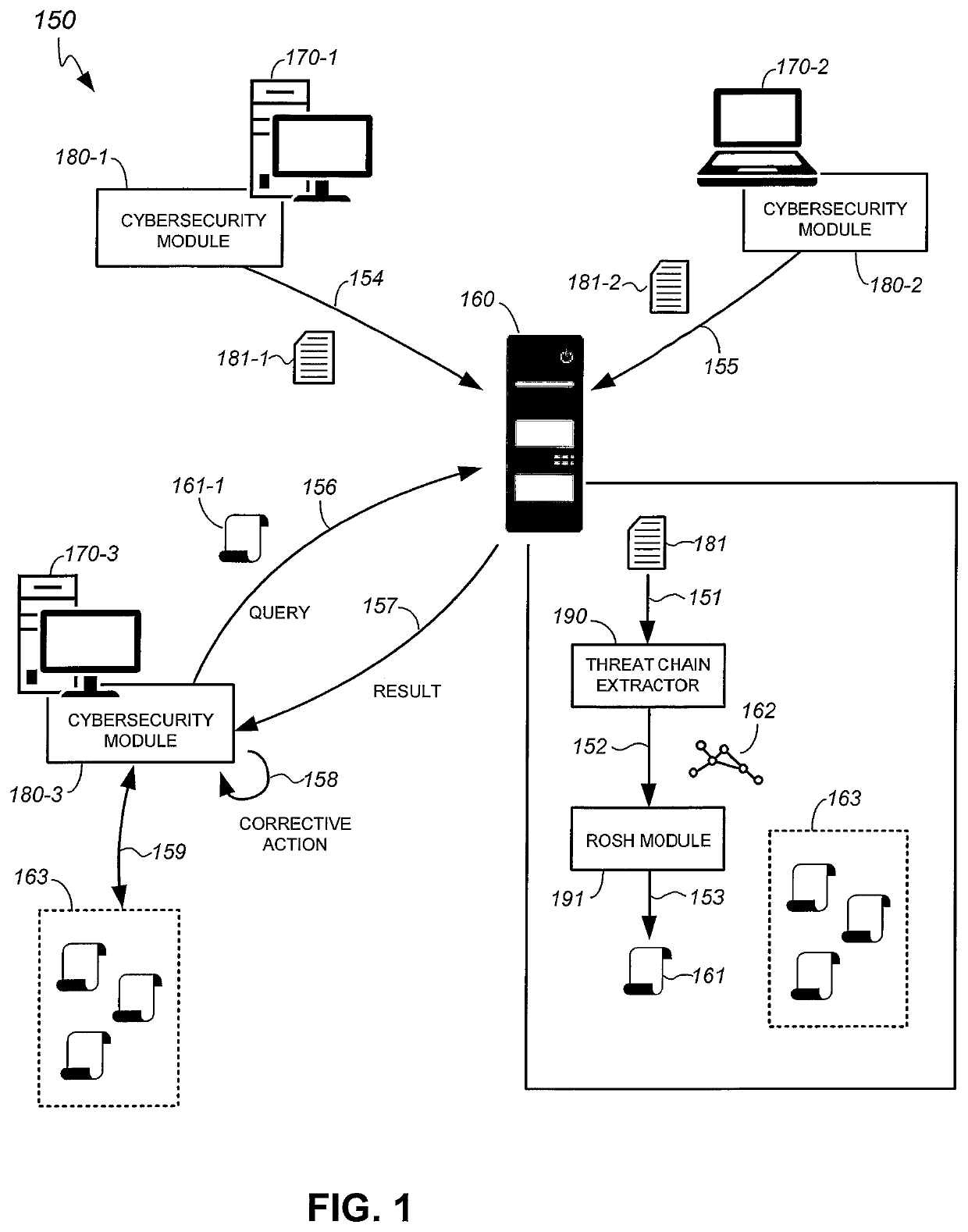
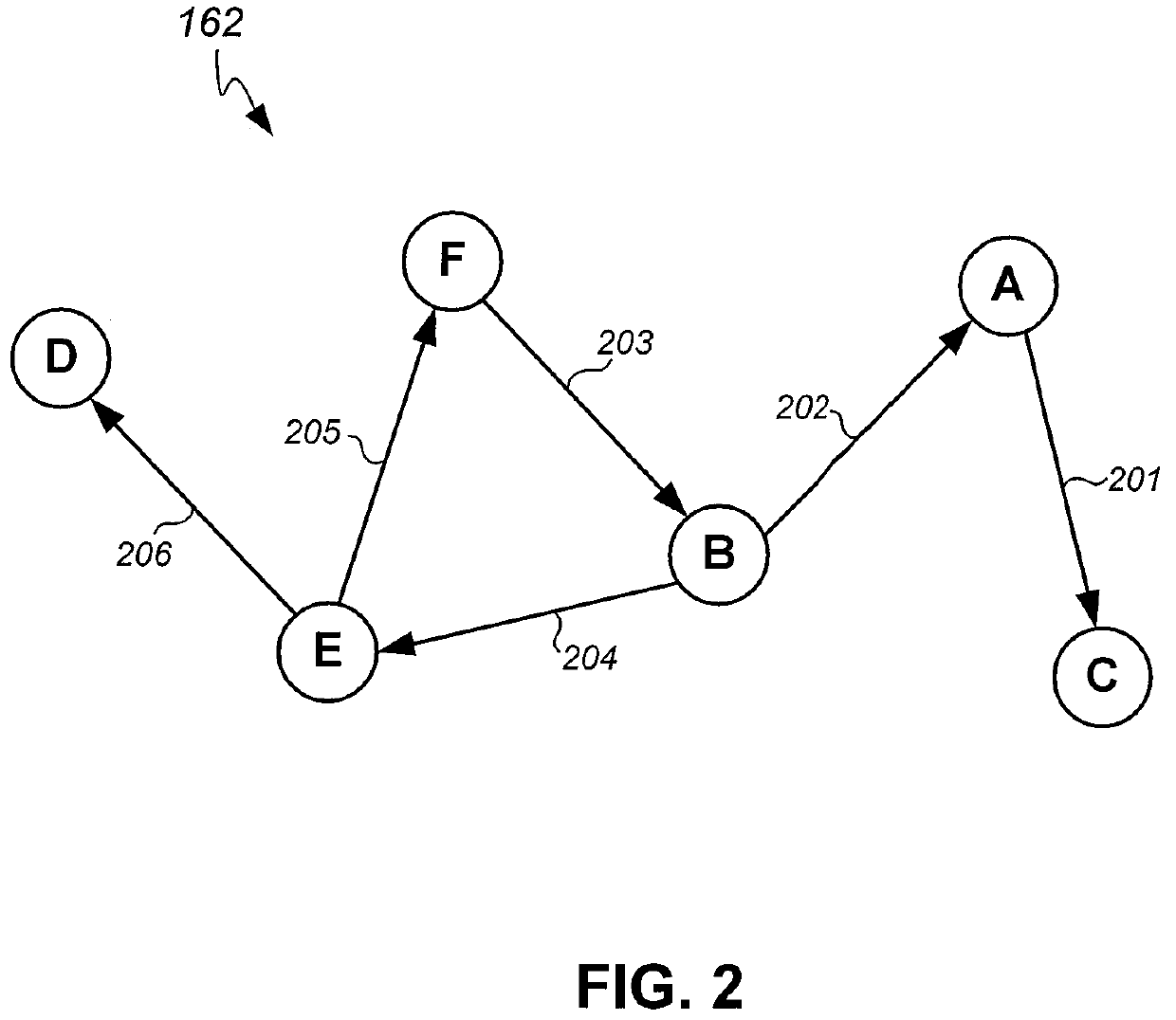
Methods and system for combating cyber threats using a related object sequence hash
ActiveUS11296868B1Encryption apparatus with shift registers/memoriesUser identity/authority verificationCyber threat intelligenceTheoretical computer science
A cyber threat intelligence of a cyber threat includes a threat chain that describes objects involved in the cyber threat and relationships between the objects. A related object hash of an object is calculated by calculating a hash of one or more objects that are linked to the object as indicated in the cyber threat intelligence. A related object sequence hash of the threat chain is generated by calculating a total of the related object hashes. The related object sequence hash of the threat chain is compared to a related object sequence hash of another threat chain to detect cyber threats.
Owner:TREND MICRO INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com