Patents
Literature
72 results about "Scoring Engine" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
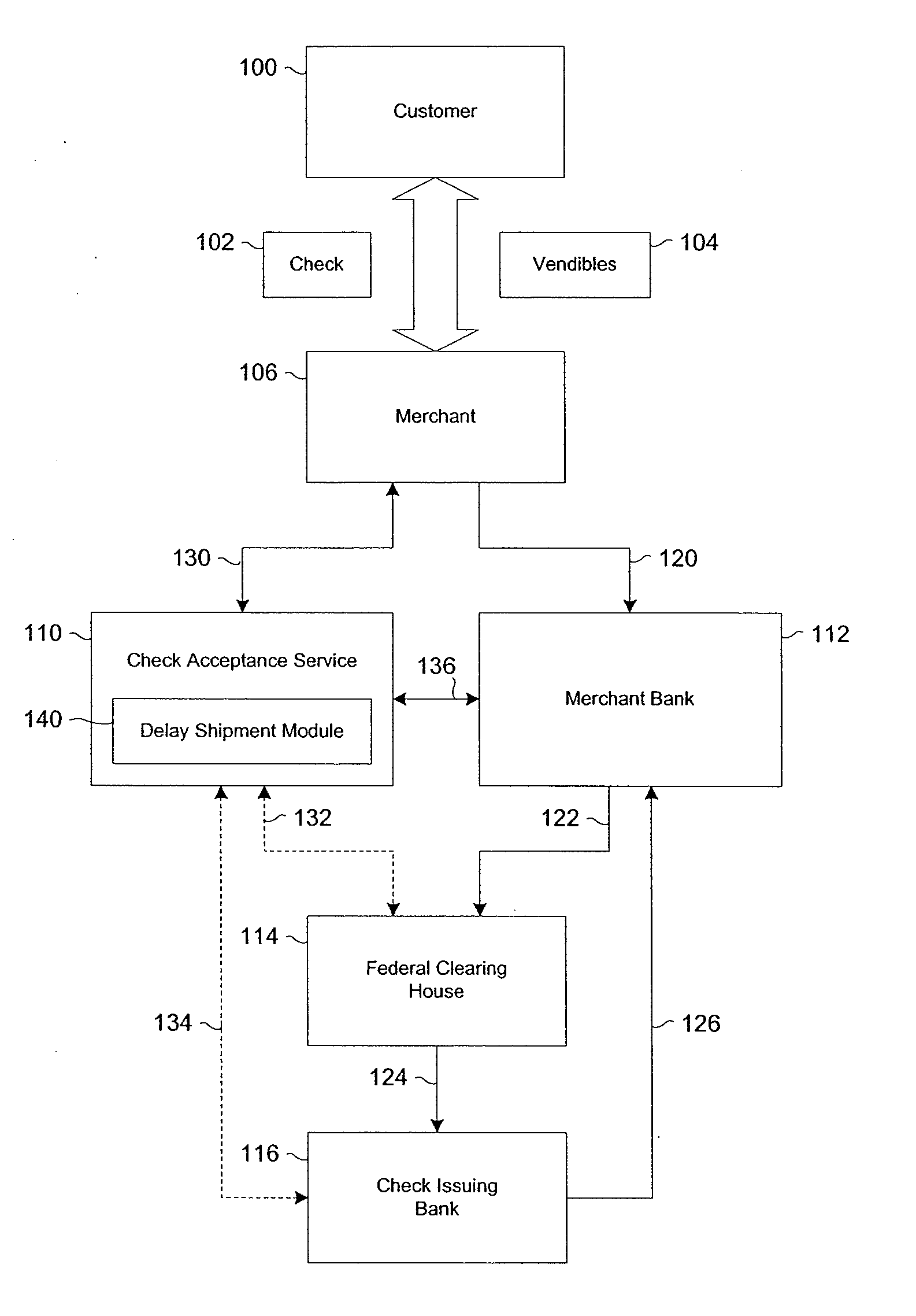
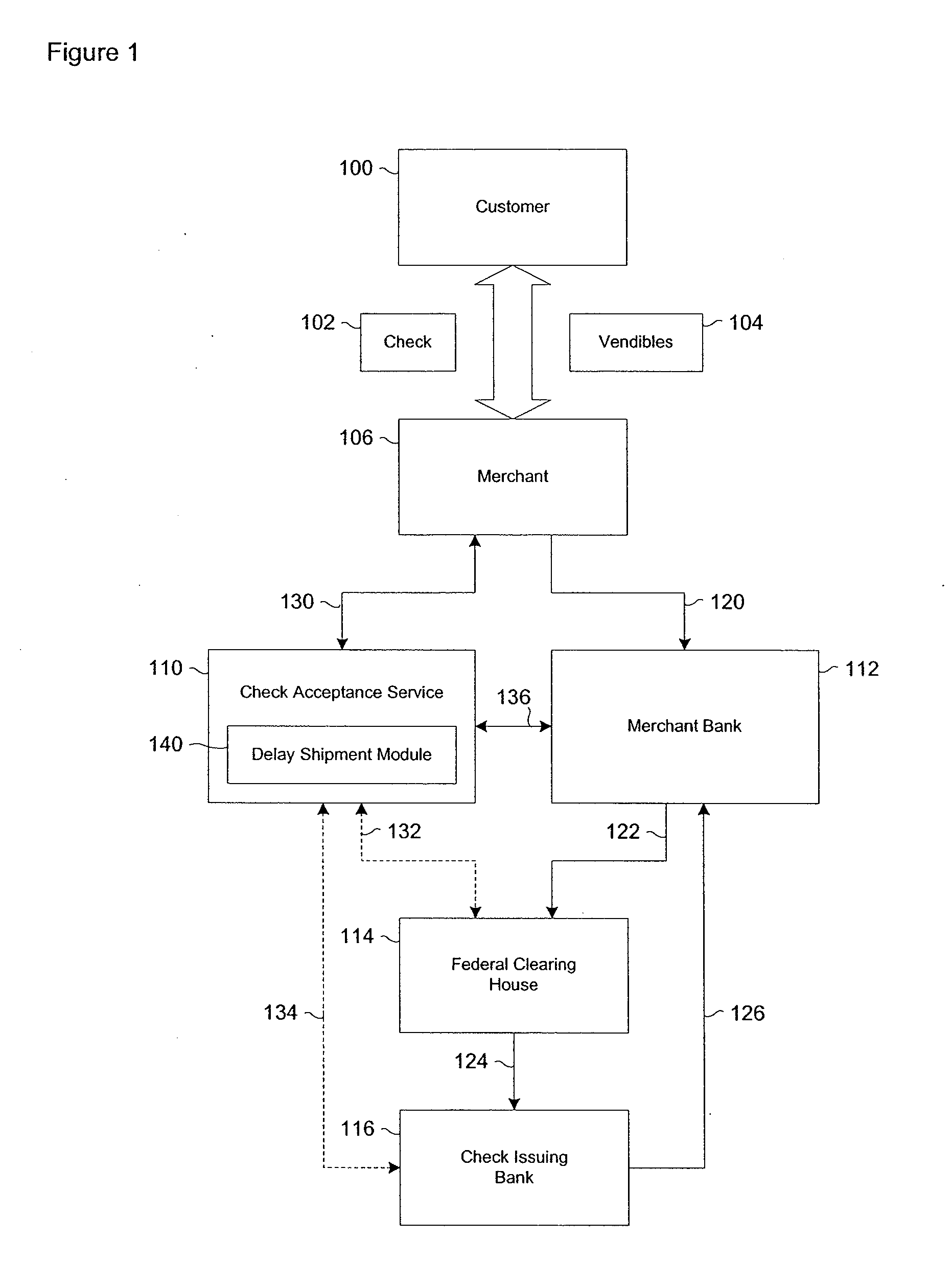
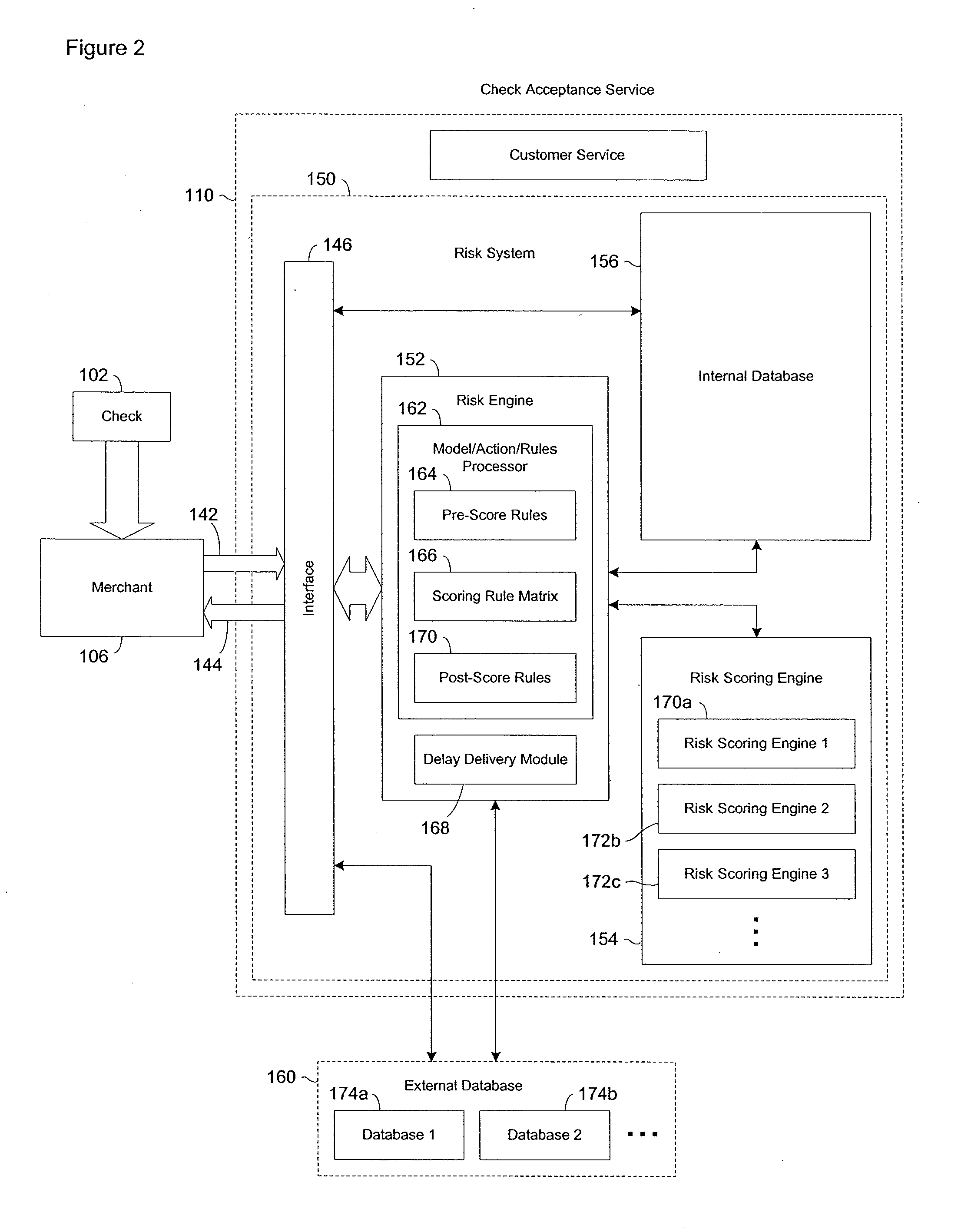
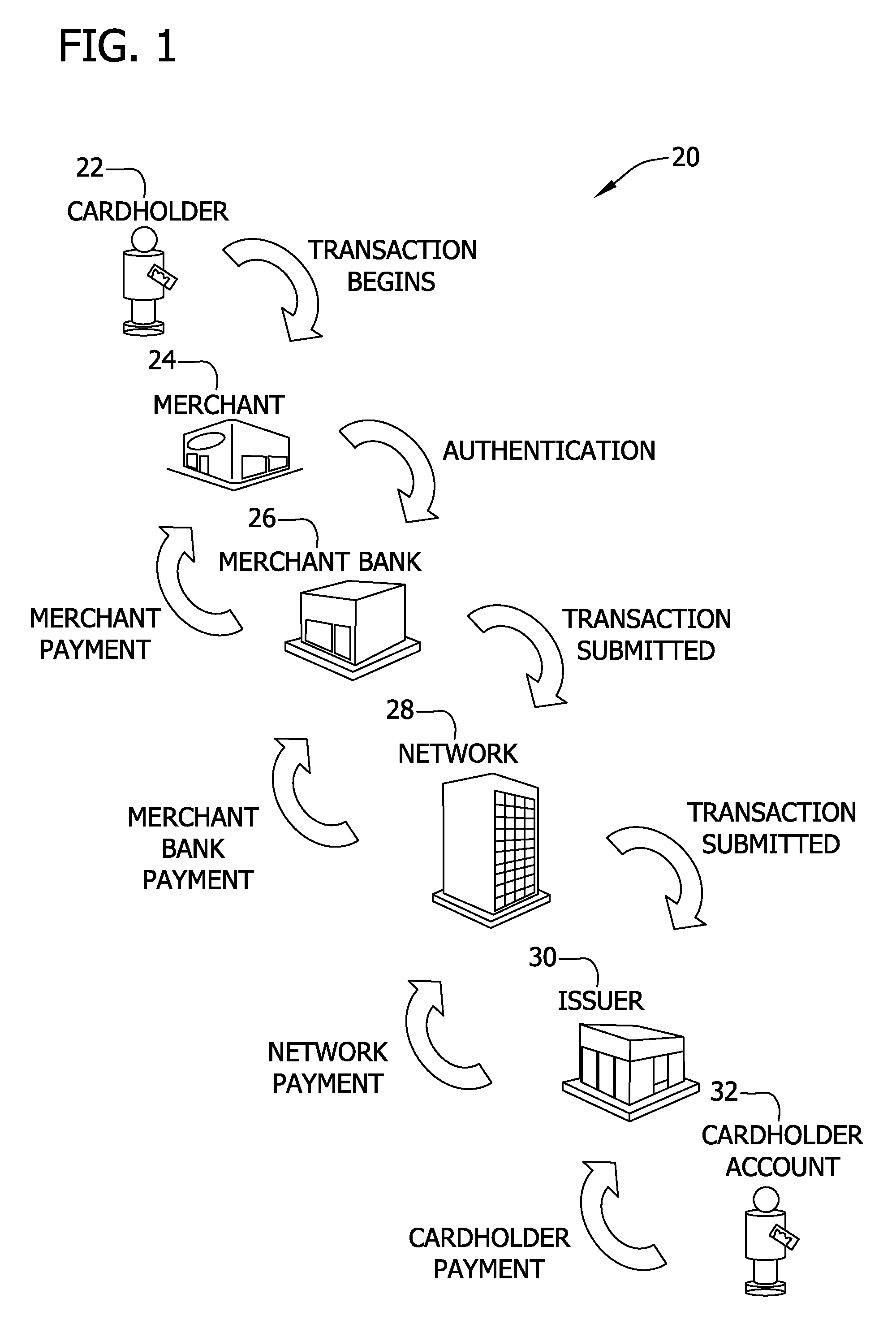
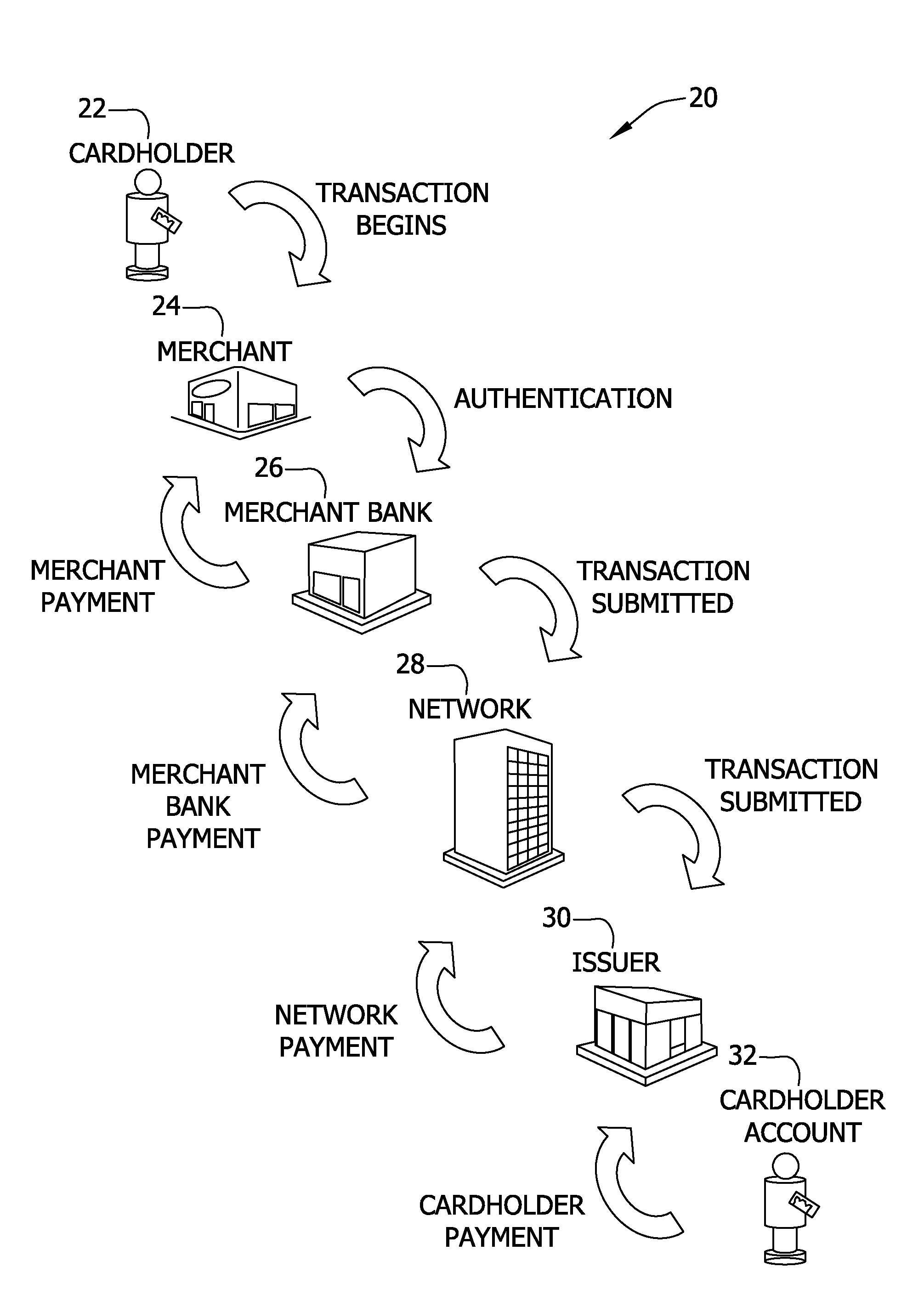
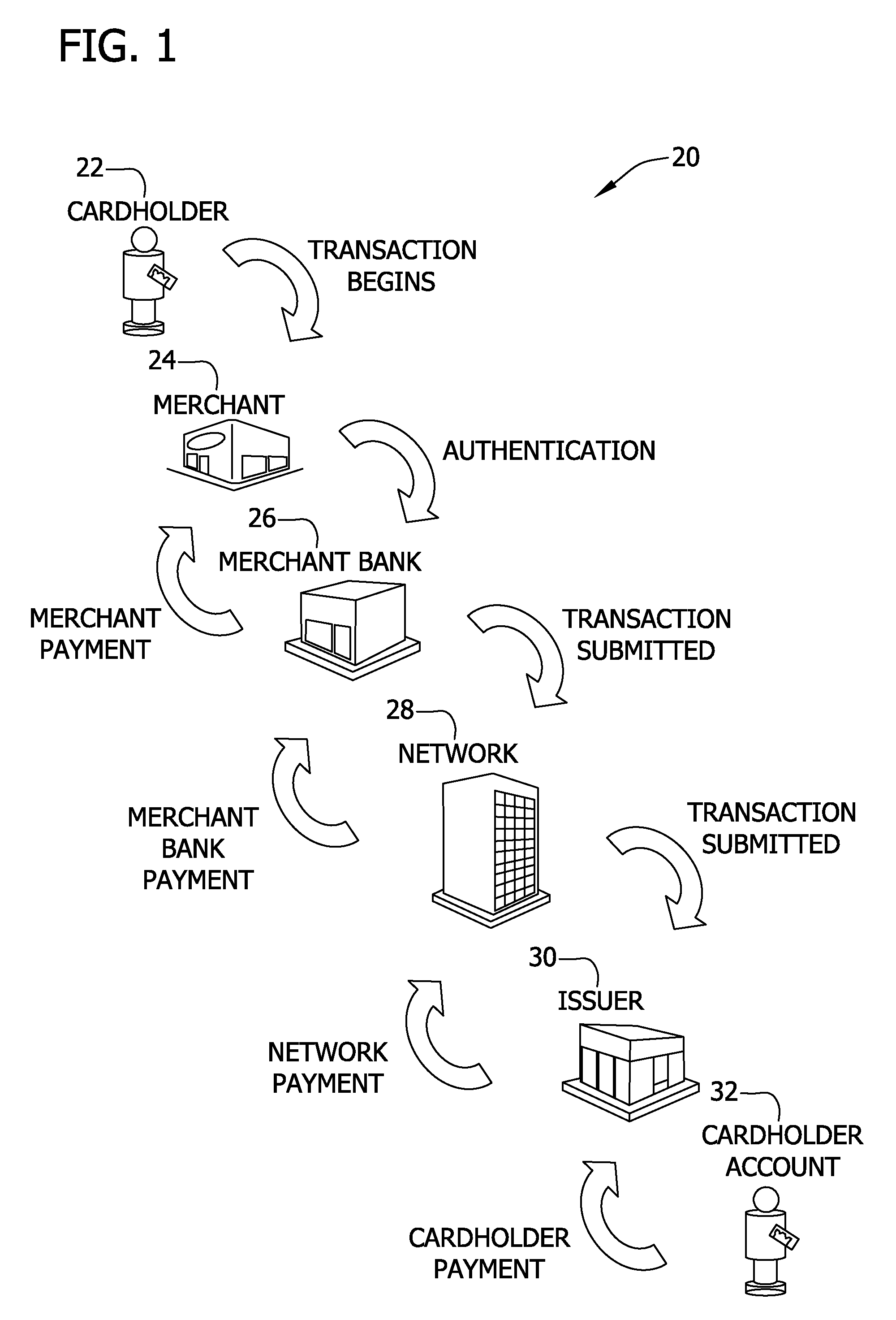
Systems and methods for selectively delaying financial transactions
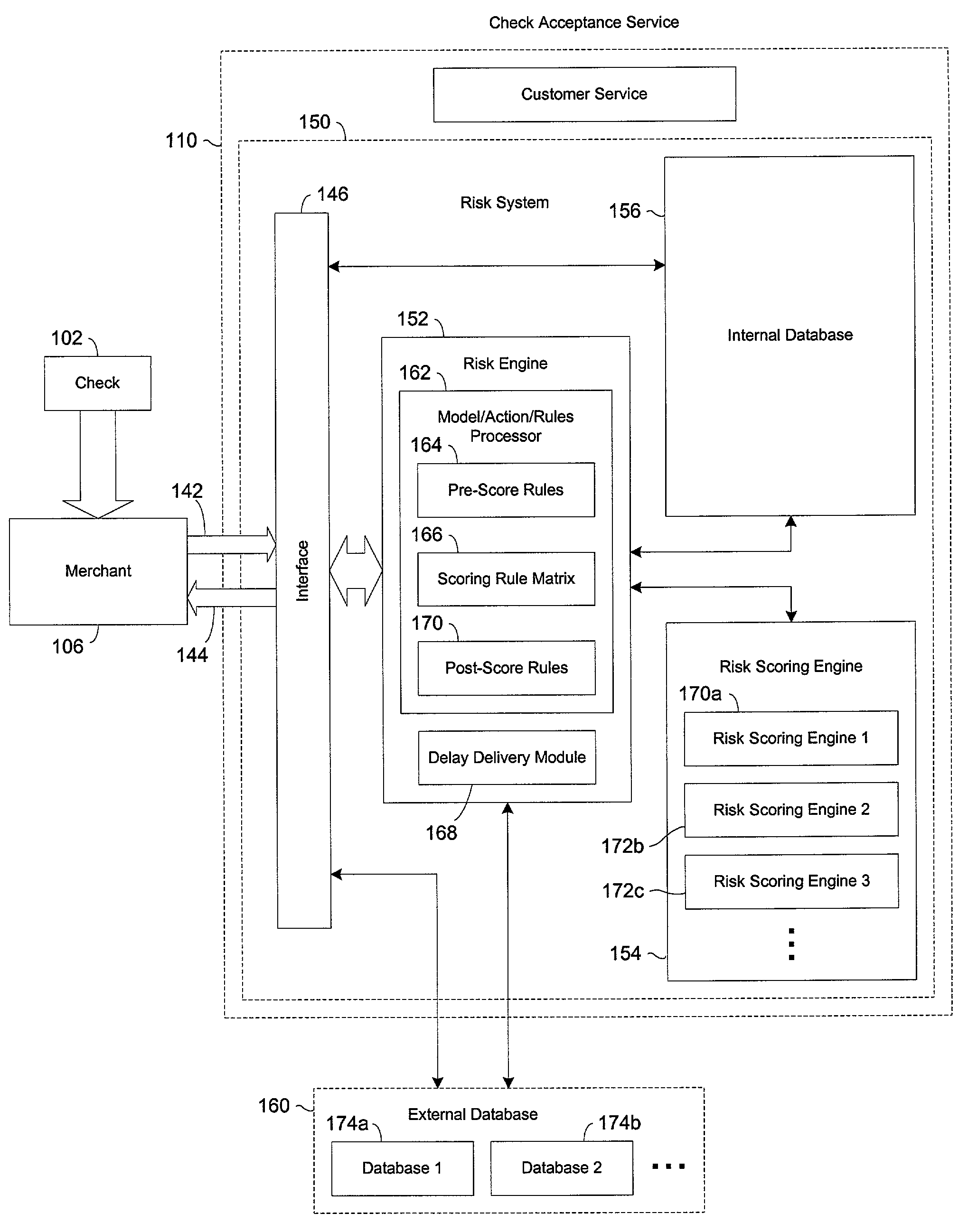
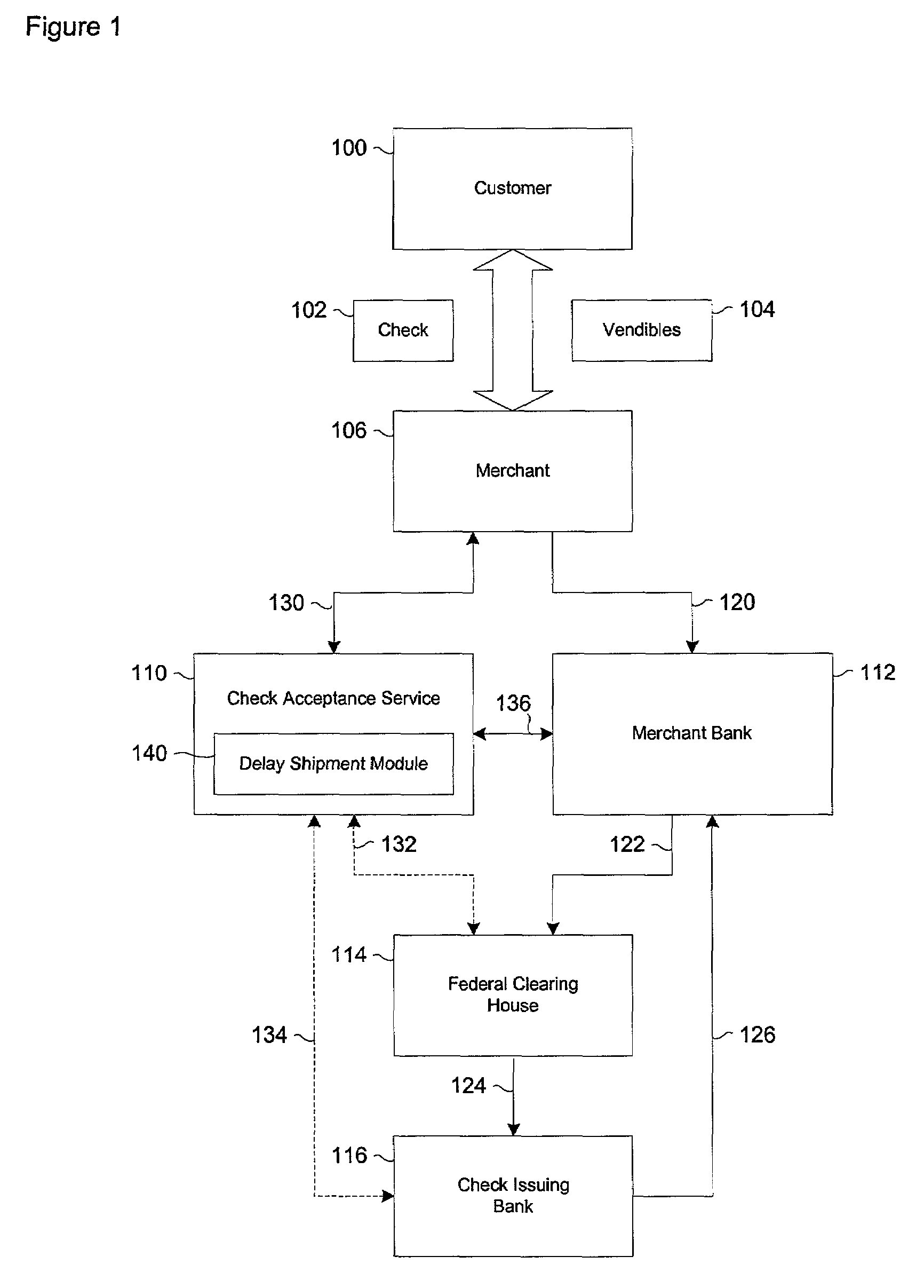
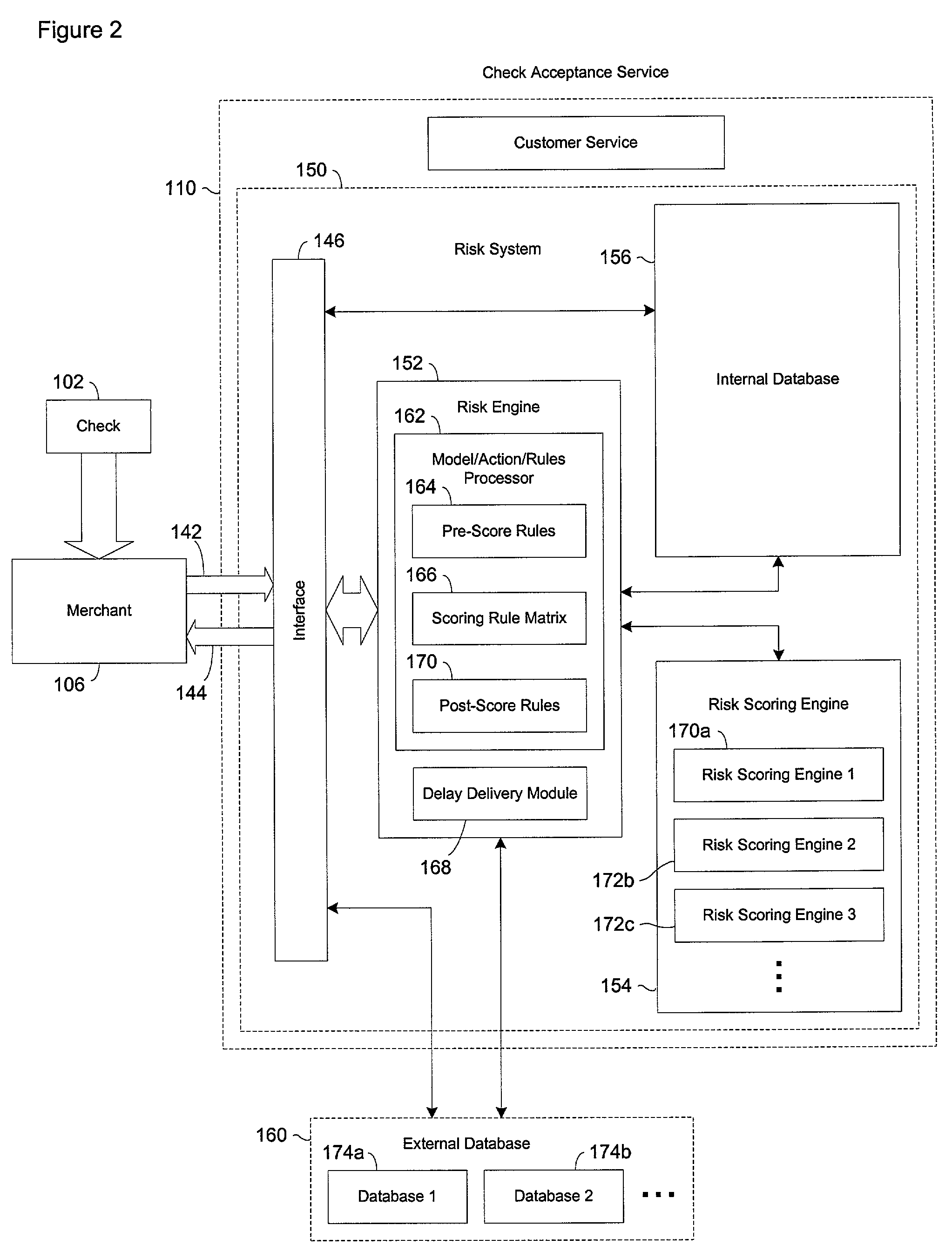
A risk system that performs a risk assessment of a financial transaction to obtain an initial risk score. Based on the initial risk score, the risk system performs at least one post-score assessment by selectively utilizing various scoring engines and databases. The at least one post-score risk assessment may include delaying the shipment of merchandise in financial transactions that are of marginal risk to thereby provide a check acceptance service with more time to further evaluate the financial transaction risks. Thus, marginally risky financial transactions that are likely to benefit the check acceptance service and a merchant that subscribes to the check acceptance service are authorized for increased profitability and customer satisfaction. Furthermore, the post-score risk assessment may approve or authorize financial transactions that generally fail standard risk assessments that use a cut-off risk score to divide the financial transactions into either approved or declined groups. As a result, the post-score assessment process efficiently re-evaluates some of the borderline exception cases for the purpose of securing beneficial financial transactions.
Owner:FIRST DATA
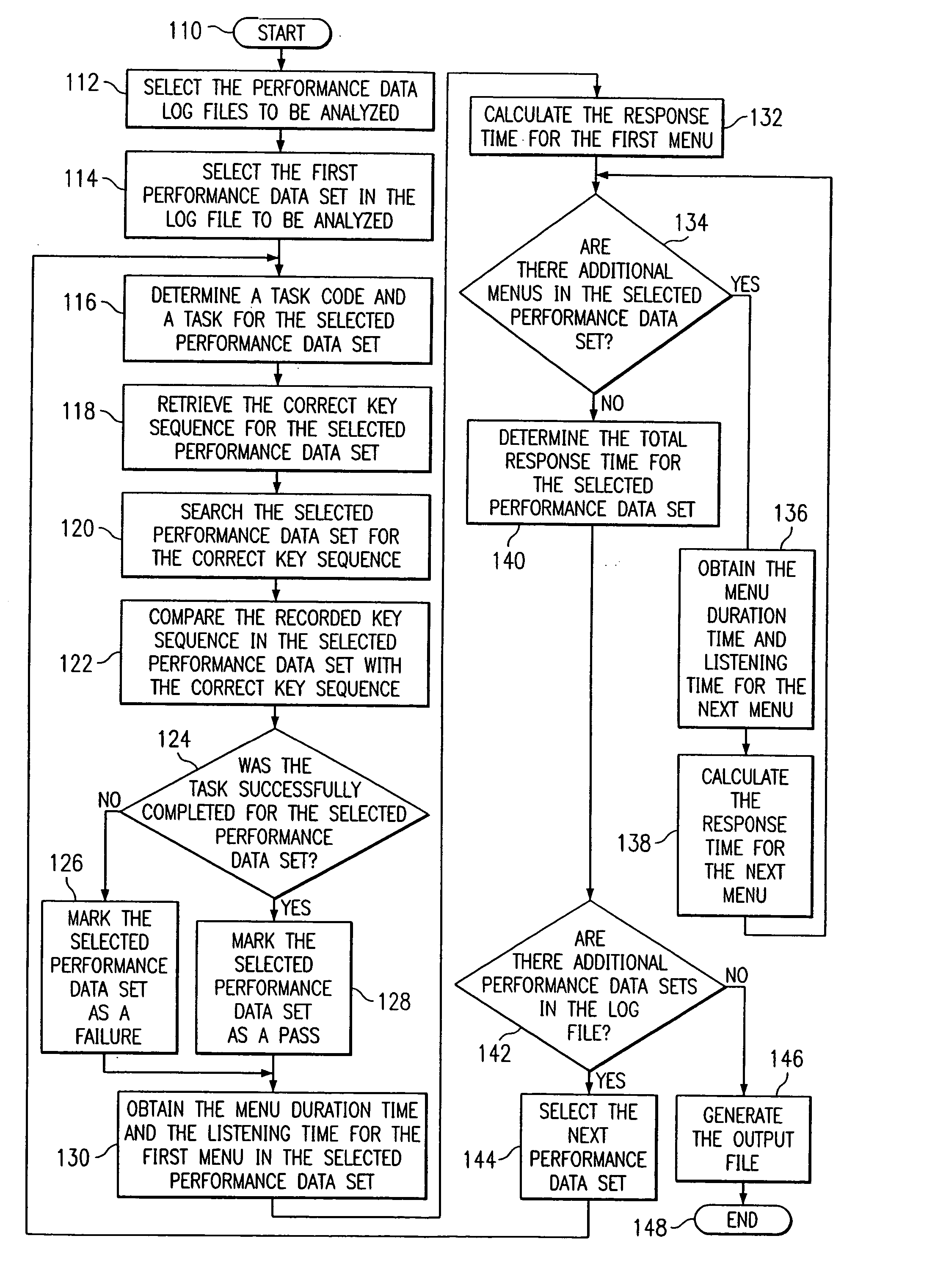
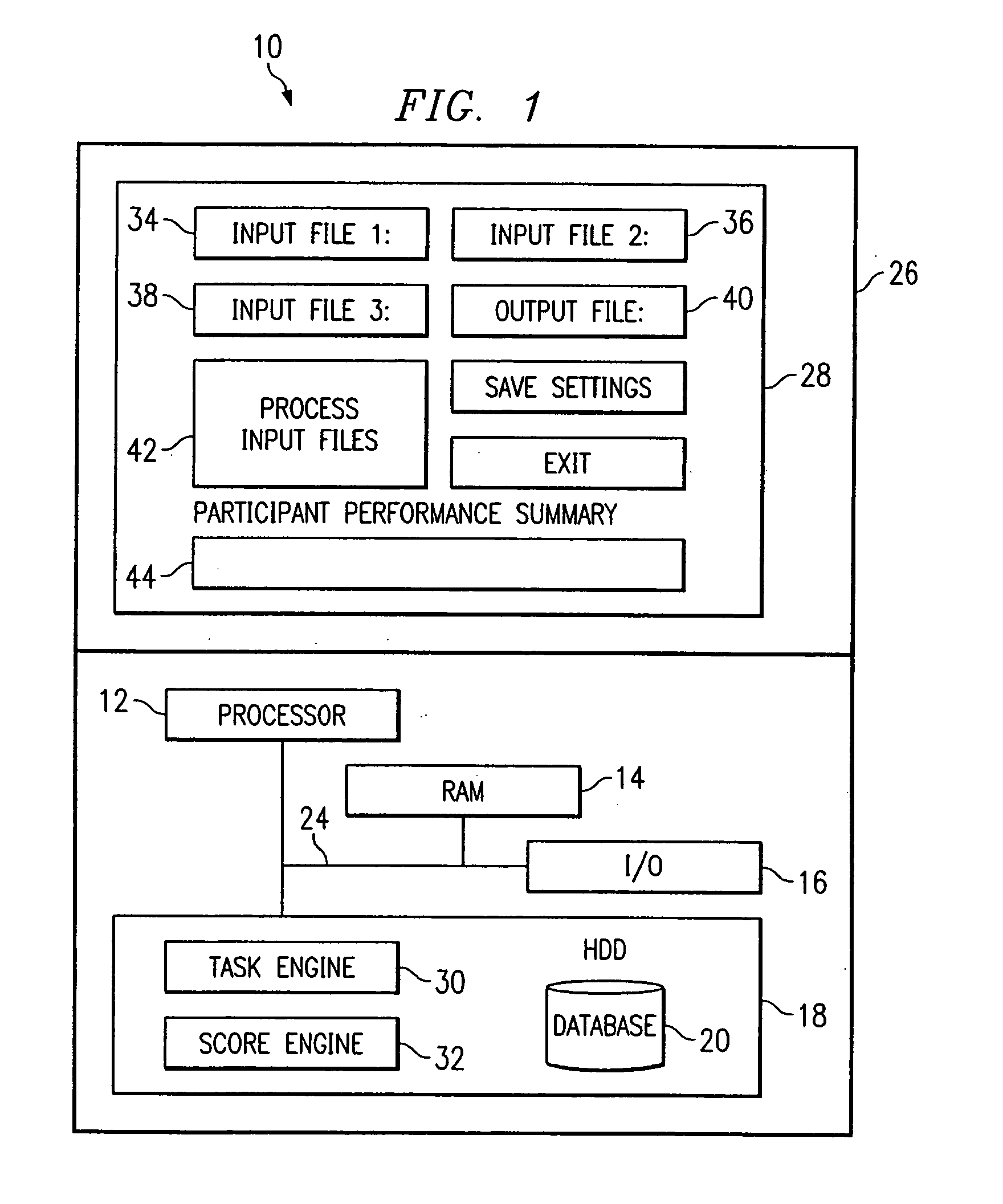
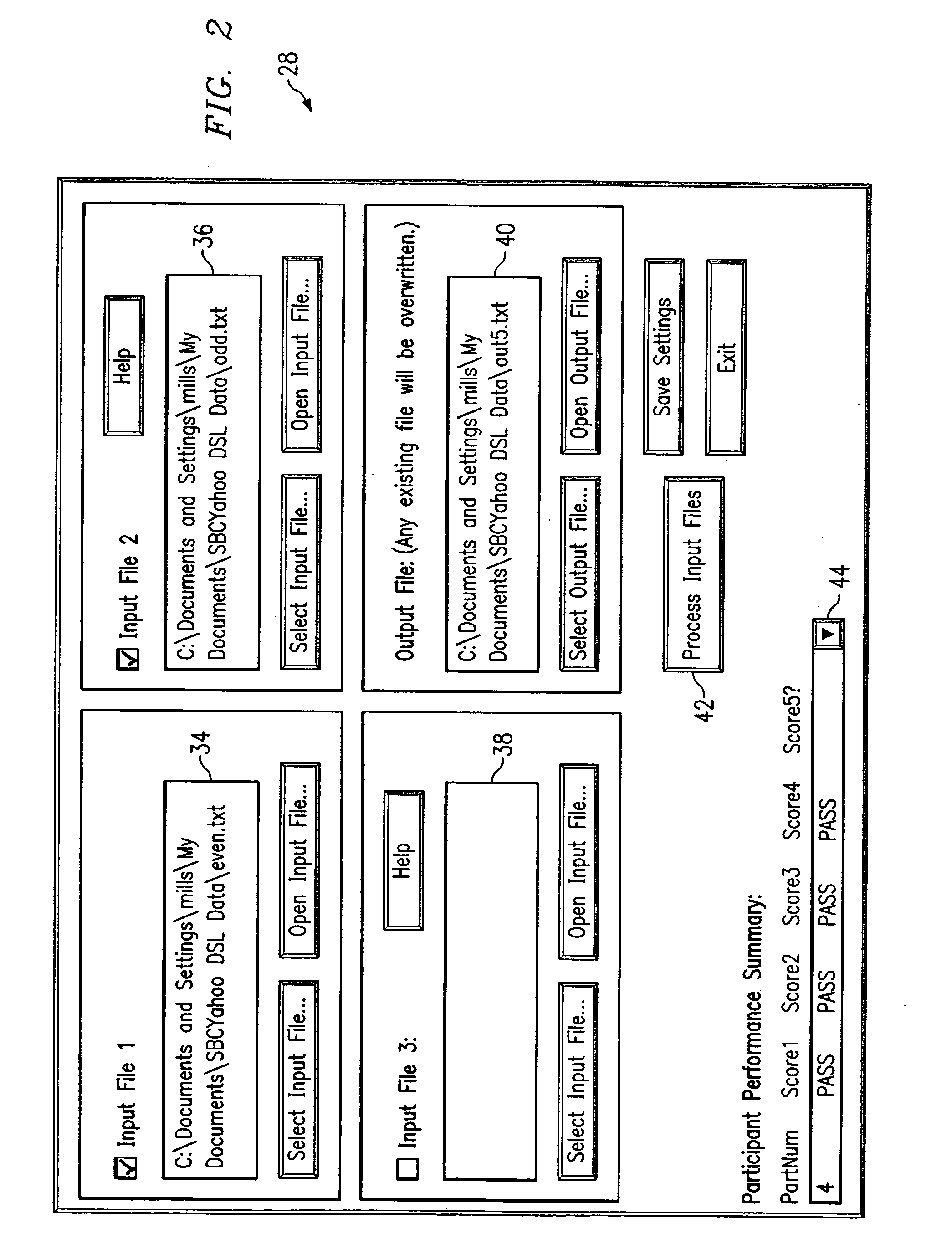
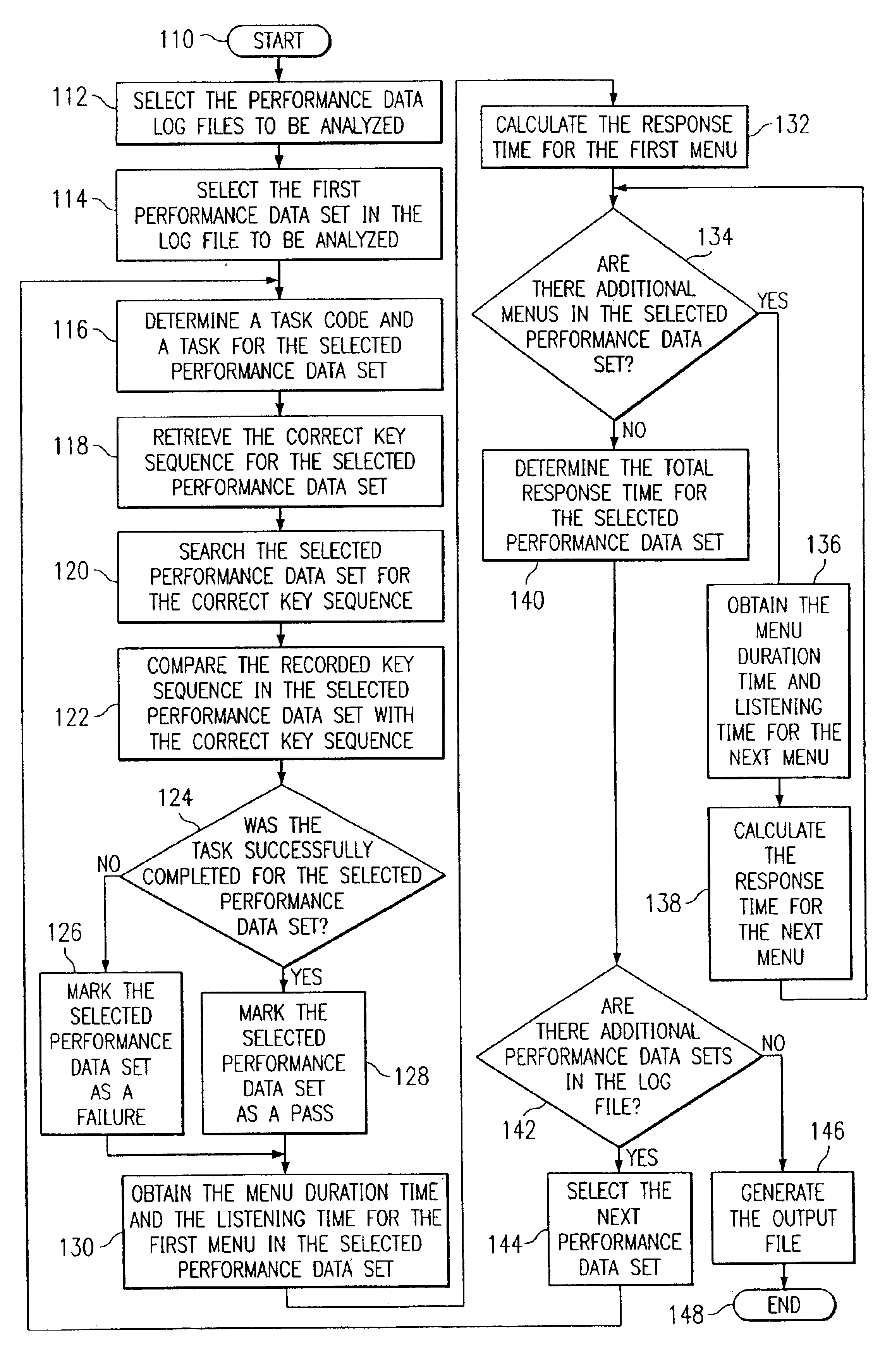
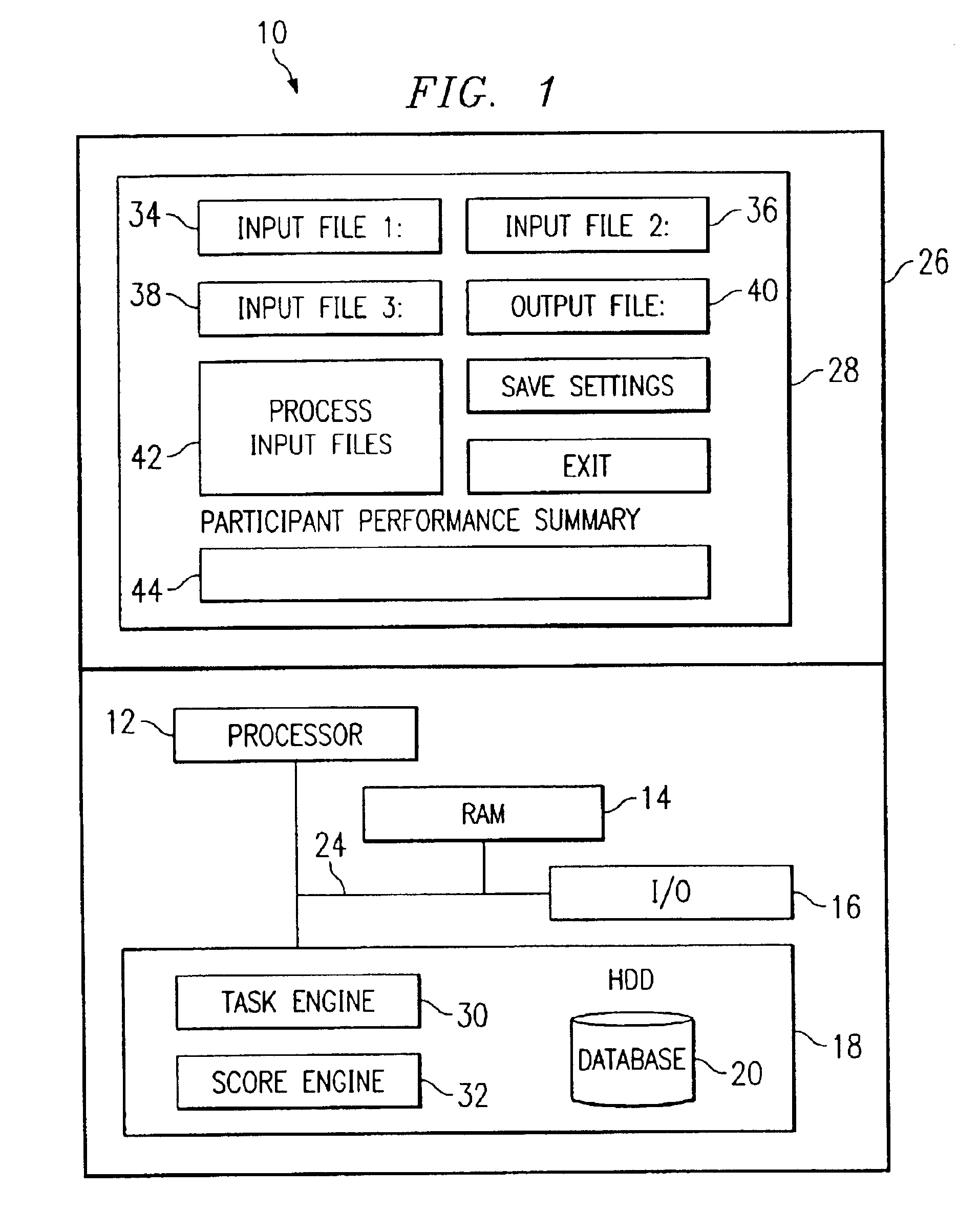
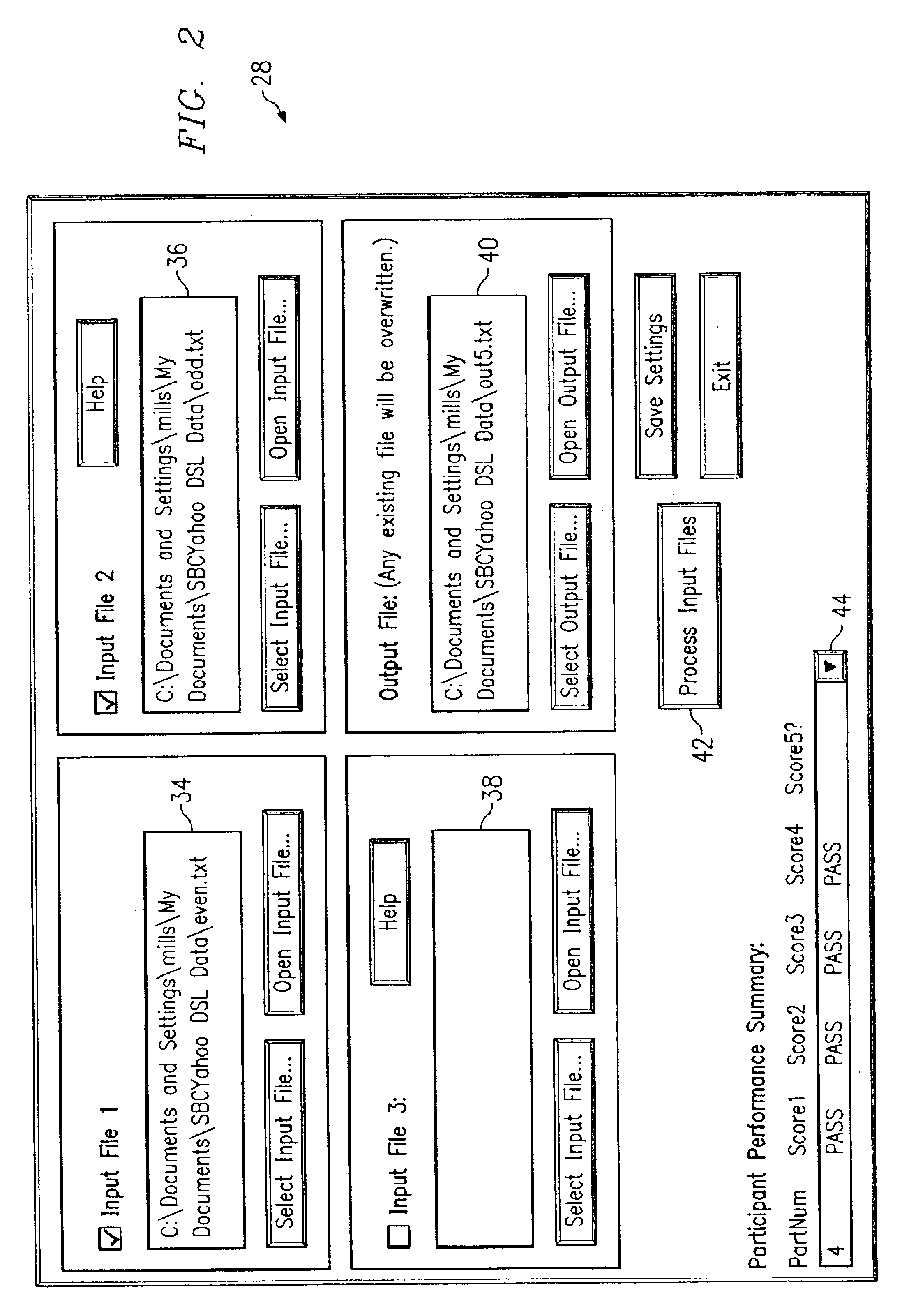
System and method for the automated analysis of performance data
ActiveUS20050078805A1Automatic call-answering/message-recording/conversation-recordingSupervisory/monitoring/testing arrangementsData setCost savings
A method and system for automating the analysis of performance data includes an analysis system automatically analyzing a plurality of performance data sets, a task engine, and a score engine. The task engine allows for the matching of each performance data set with an assigned task for each performance data set and the retrieval of a correct key sequence for each performance data set. The score engine compares the correct key sequence with a recorded key sequence of the performance data set to determine if the assigned task is successfully accomplished. The score engine further calculates one or more response times for each performance data set. The automated analysis of performance data allows for a cost savings, more efficient use of time, and more reliable and consistent performance data analysis results.
Owner:SBC KNOWLEDGE VENTURES LP
System and method for the automated analysis of performance data
InactiveUS6842504B2Automatic call-answering/message-recording/conversation-recordingSupervisory/monitoring/testing arrangementsData setCost savings
A method and system for automating the analysis of performance data includes an analysis system automatically analyzing a plurality of performance data sets, a task engine, and a score engine. The task engine allows for the matching of each performance data set with an assigned task for each performance data set and the retrieval of a correct key sequence for each performance data set. The score engine compares the correct key sequence with a recorded key sequence of the performance data set to determine if the assigned task is successfully accomplished. The score engine further calculates one or more response times for each performance data set. The automated analysis of performance data allows for a cost savings, more efficient use of time, and more reliable and consistent performance data analysis results.
Owner:SBC PROPERTIES
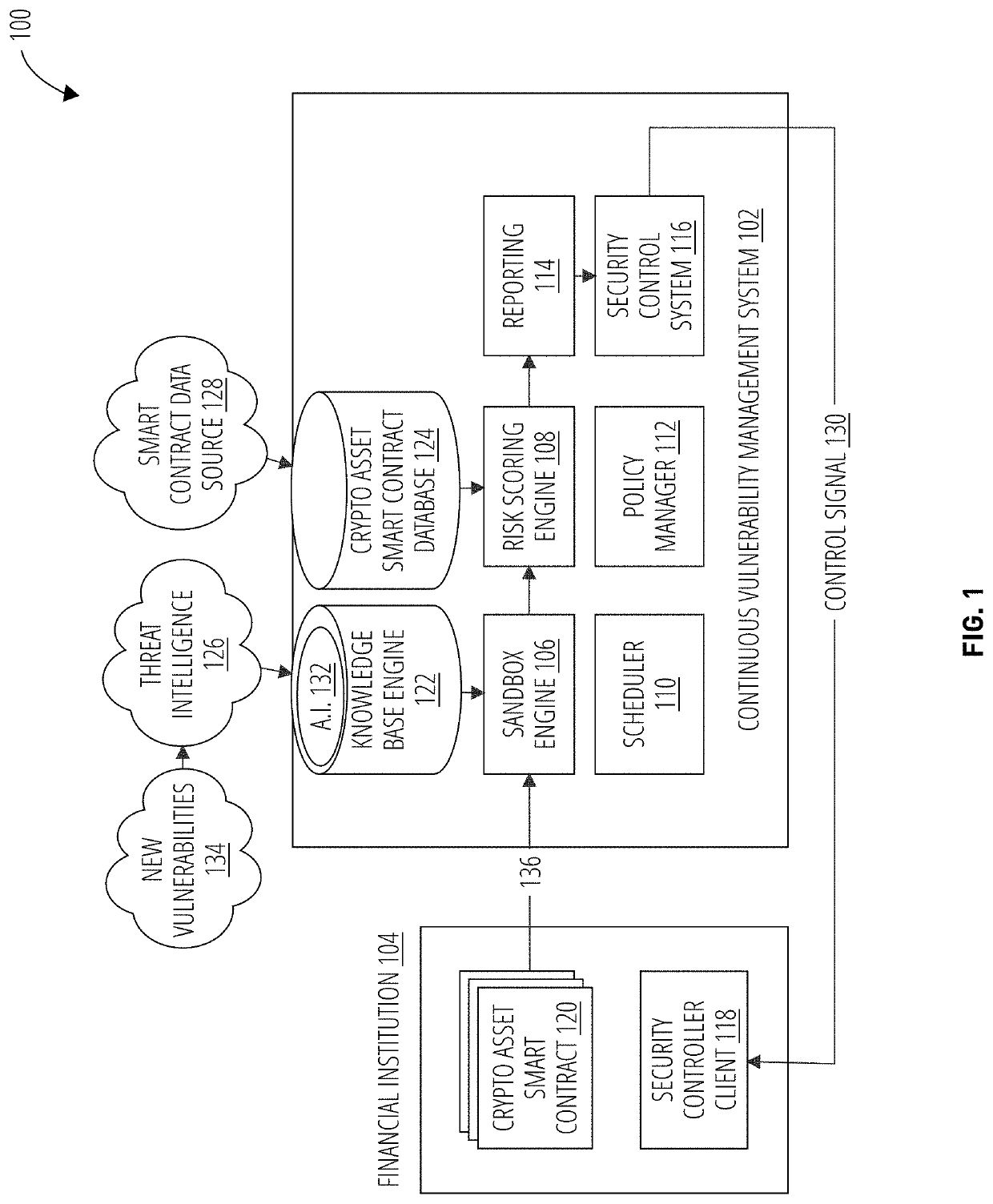
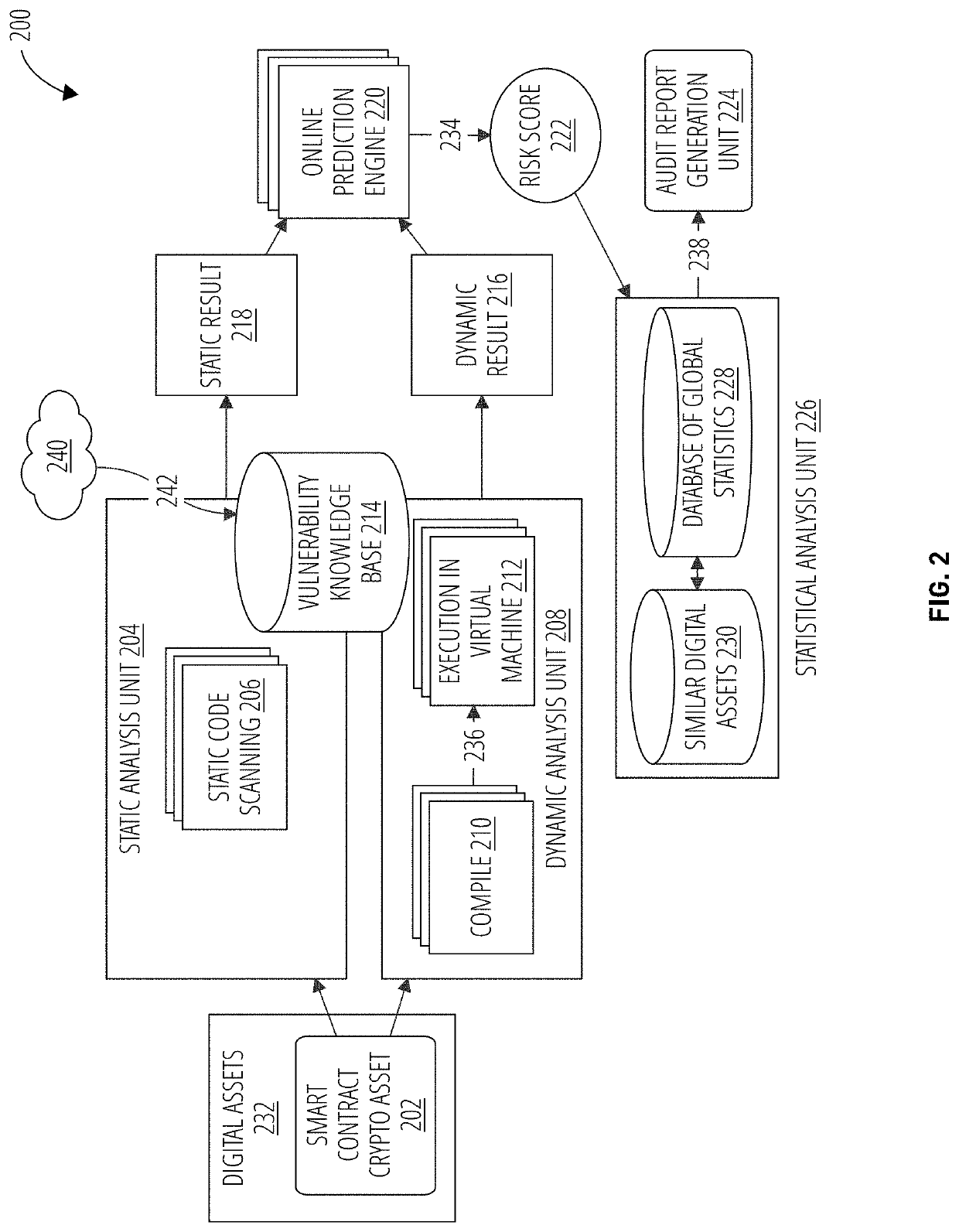
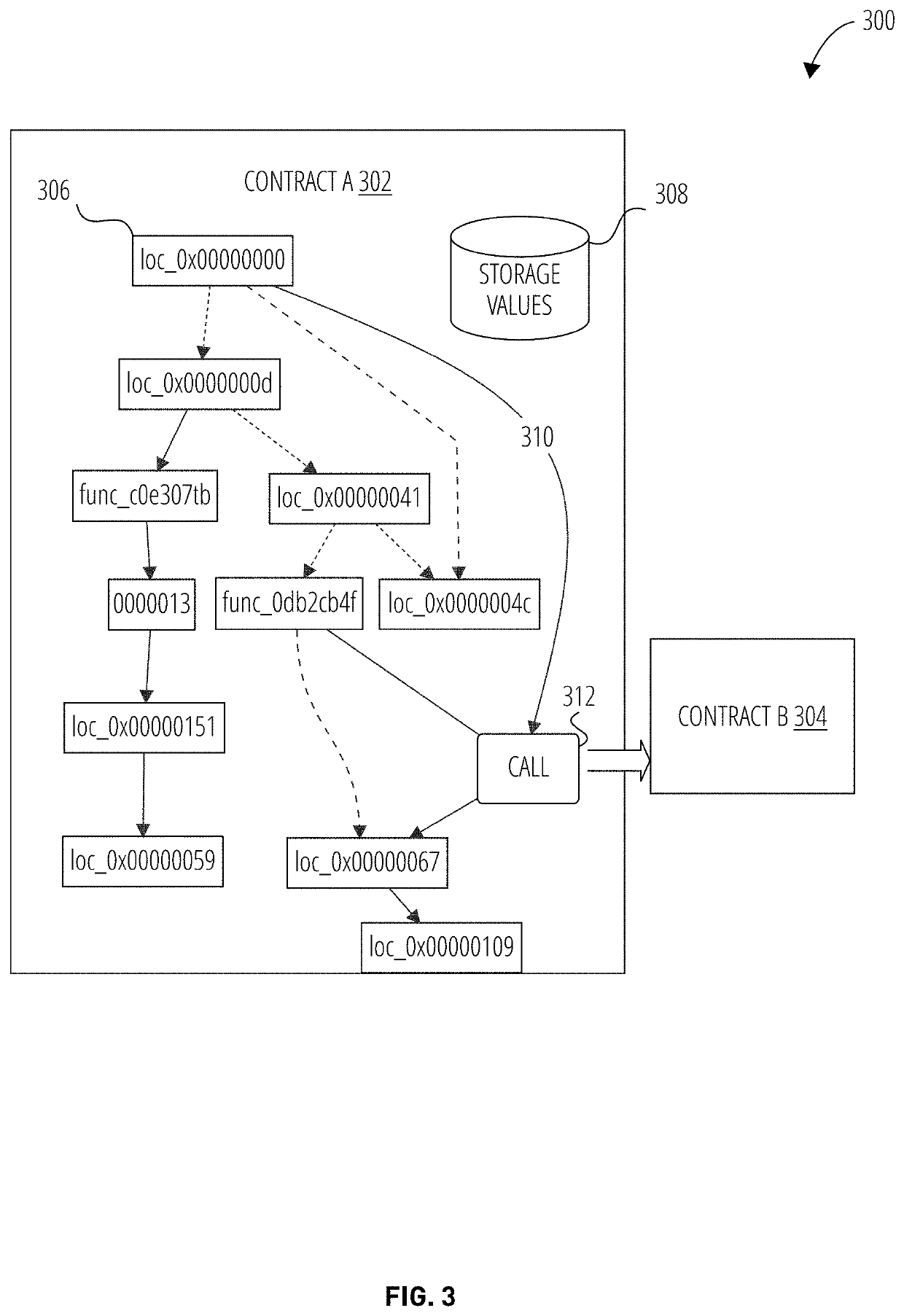
Continuous vulnerability management system for blockchain smart contract based digital asset using sandbox and artificial intelligence
ActiveUS20210110047A1Database distribution/replicationPayment protocolsStatistical analysisReliability engineering
A continuous vulnerability management system for identifying, analyzing, protecting, and reporting on digital assets is disclosed. The continuous vulnerability management system comprises a sandbox engine configured to scan digital assets for vulnerabilities, including a static analysis unit for static code scanning, a dynamic analysis unit for analyzing compiled code, and a statistical analysis unit for processing a risk score and generating an audit report. A knowledge base is also disclosed, including a knowledge base engine configured to acquire information related to new vulnerabilities to digital assets. A risk scoring engine is configured to analyze sandbox engine outcomes and assign a risk score to each vulnerable asset. A security control system is configured to act on an identified vulnerable asset based on the risk score assigned to the identified vulnerable asset.
Owner:ANCHAIN AI INC
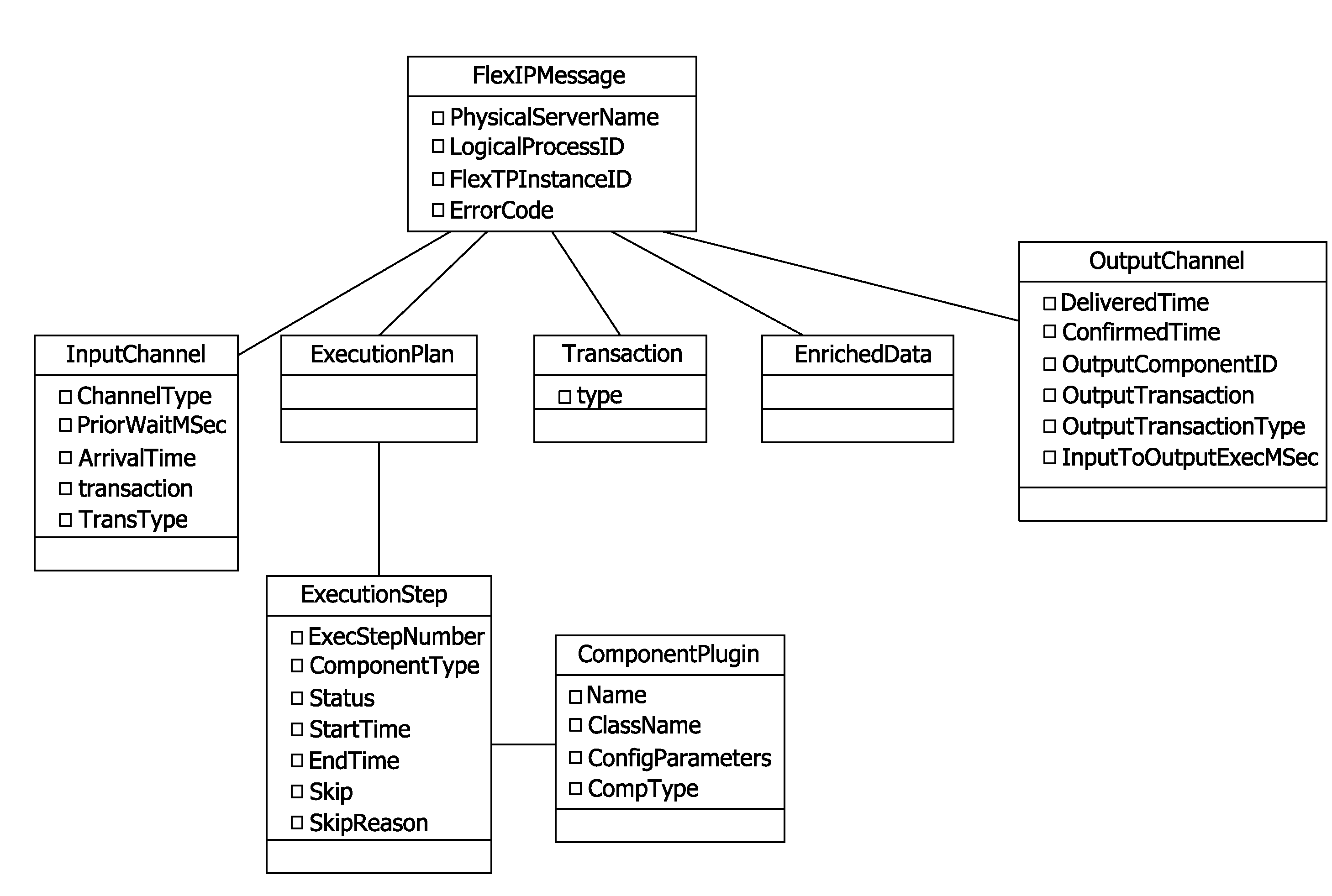
Methods and systems for providing a decision making platform
A method for enriching the data associated with financial transaction card transactions using a computer system is described. The method includes receiving financial transaction data from a plurality of input channels, each input channel associated with a financial transaction data format, converting the received financial transaction data into a common data format, enriching the converted financial transaction data by scoring the converted financial transaction data across a plurality of scoring engines, converting the plurality of scores relating to the financial transaction data from the scoring engines into output data, and transmitting the output data using an output manager, the output manager operable to provide the data into a format appropriate for each intended recipient.
Owner:MASTERCARD INT INC
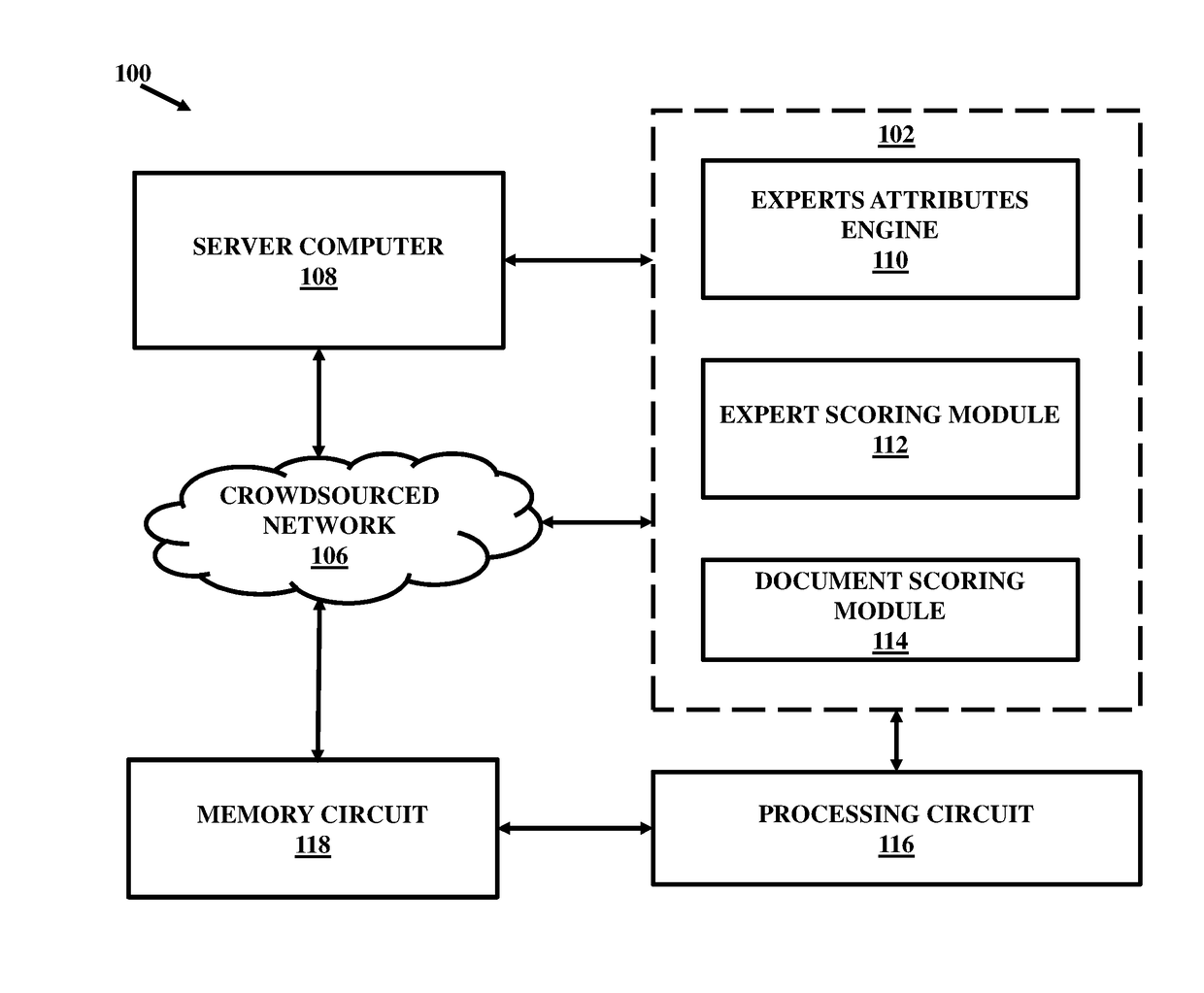
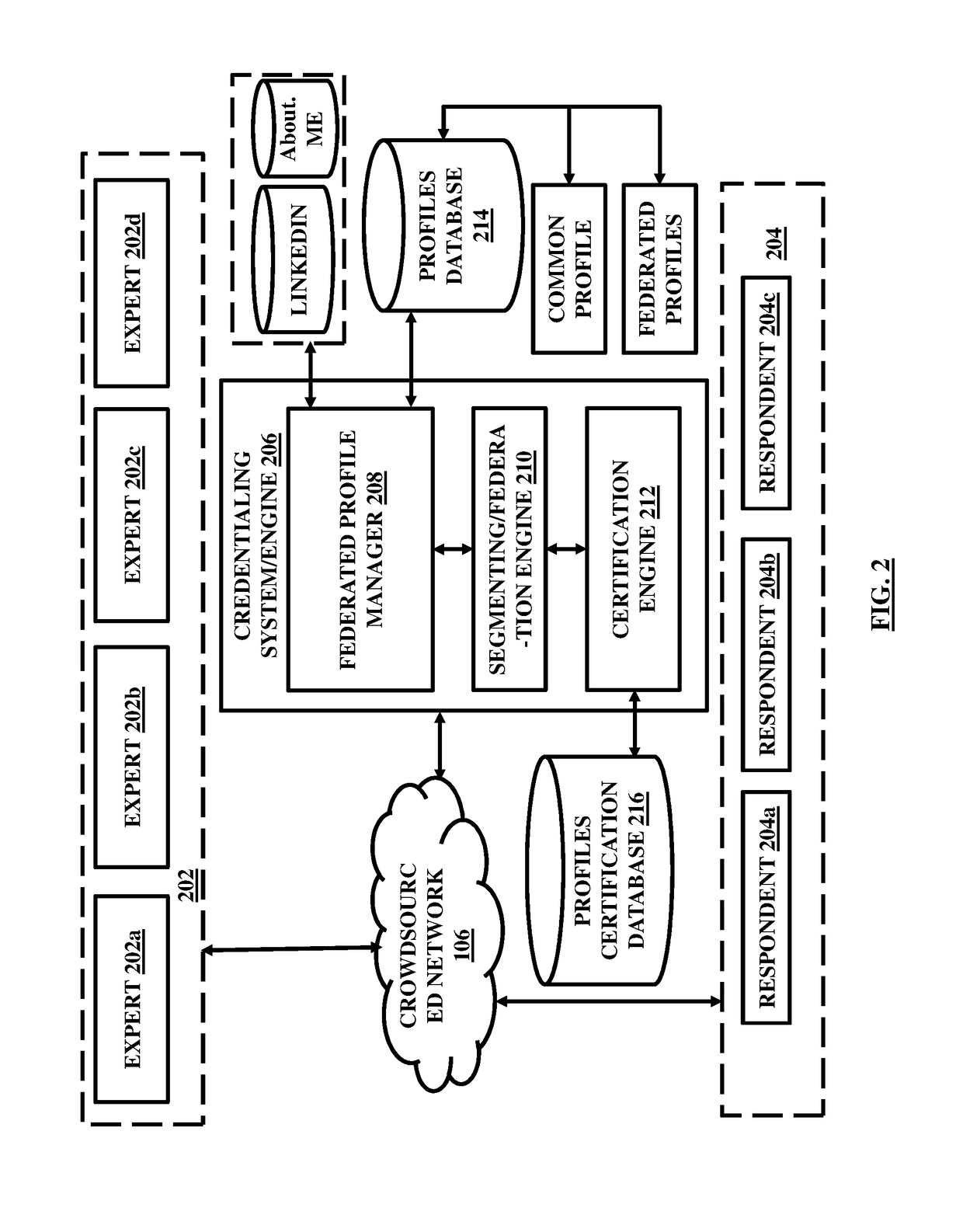
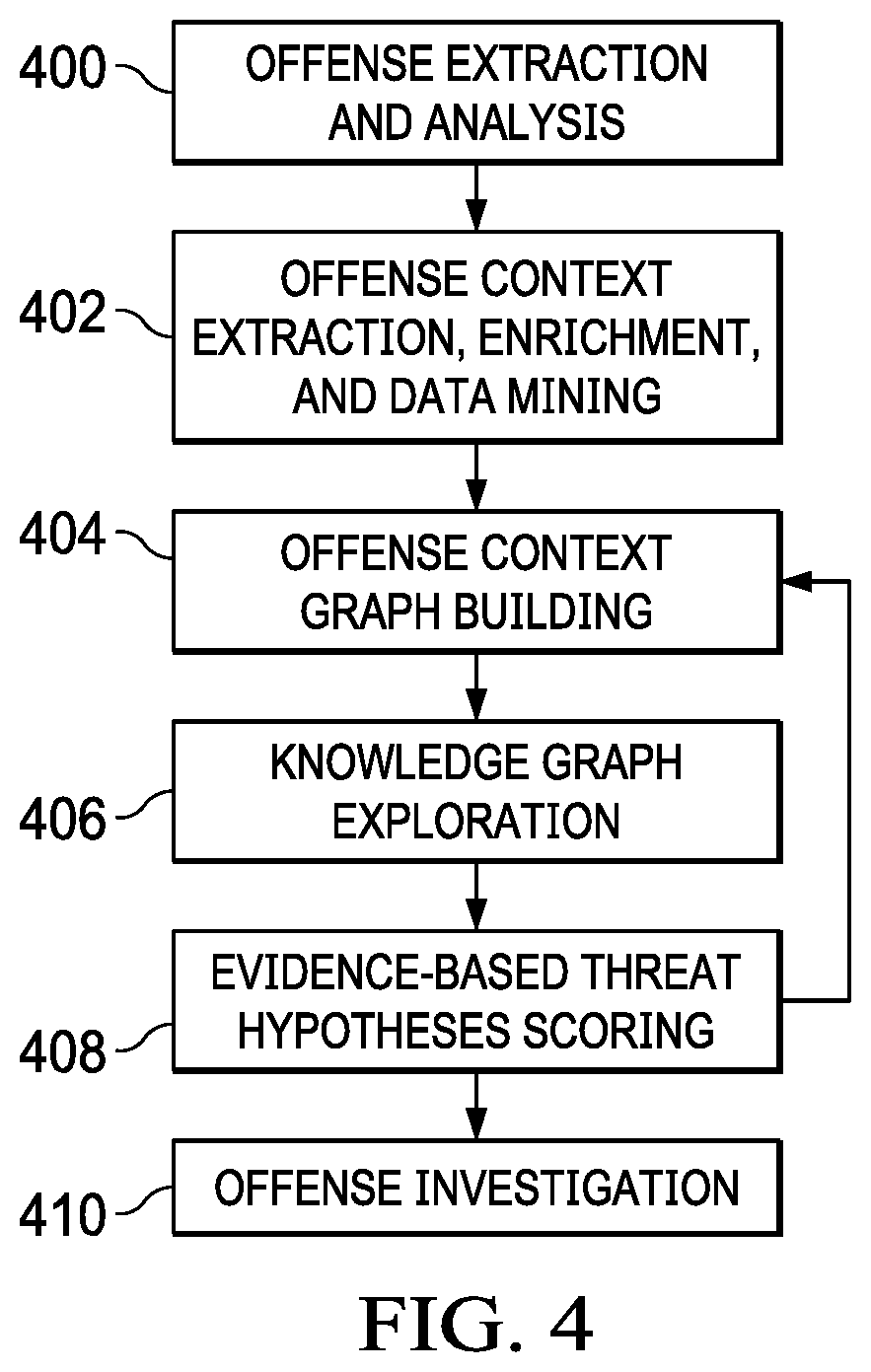
Distributed electronic document review in a blockchain system and computerized scoring based on textual and visual feedback
ActiveUS20170103472A1Increase the number ofEncryption apparatus with shift registers/memoriesSemantic analysisElectronic documentDocumentation procedure
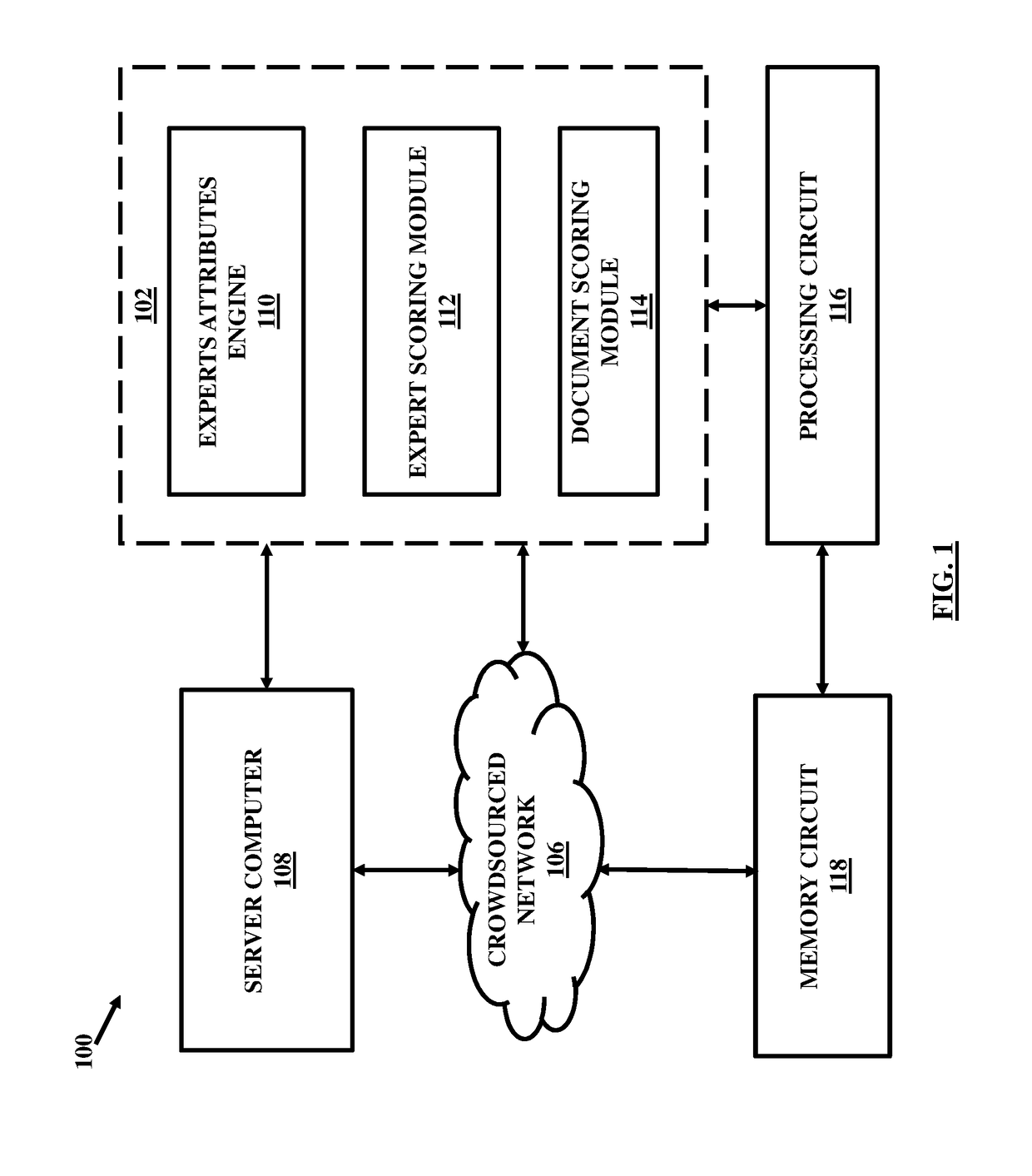
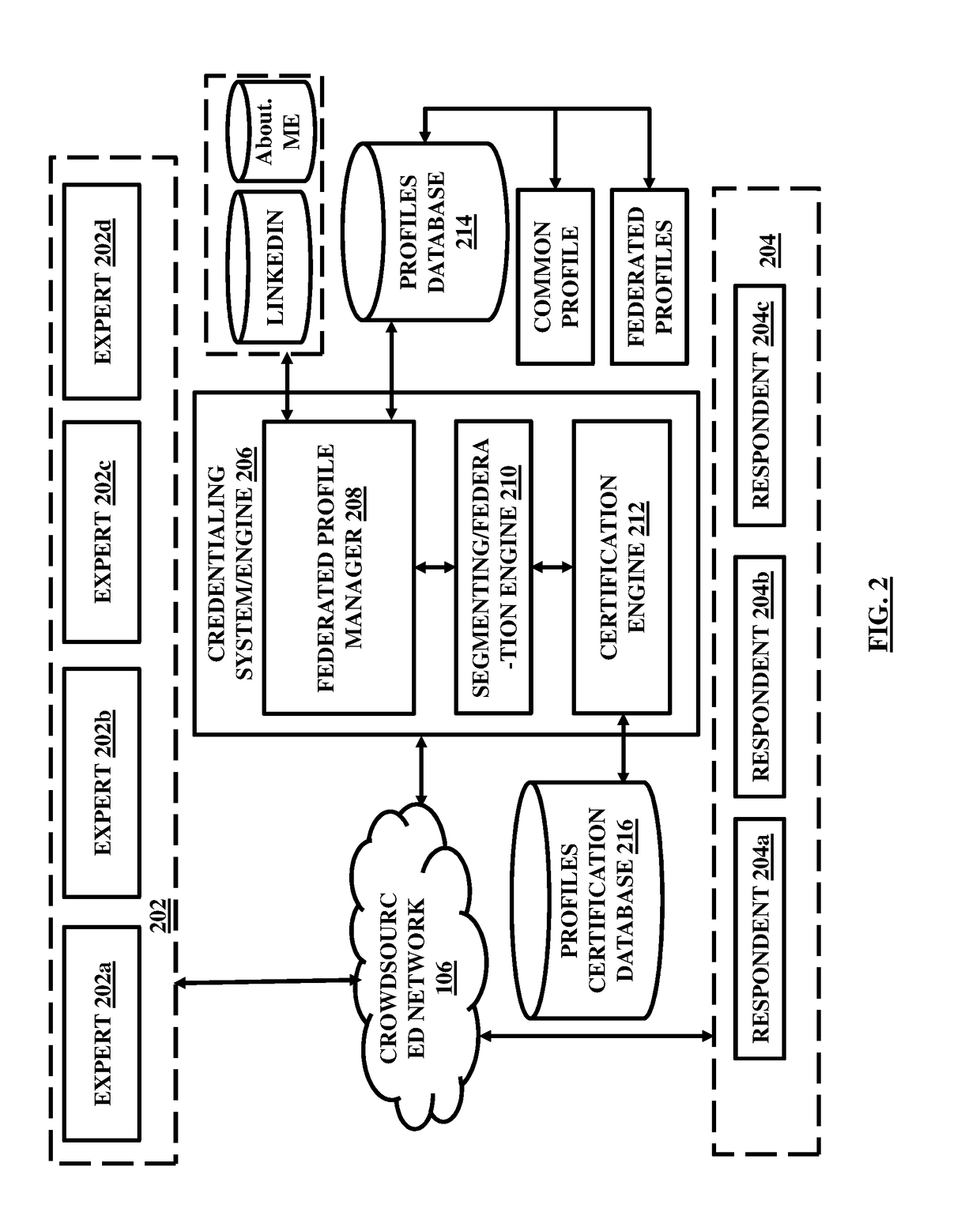
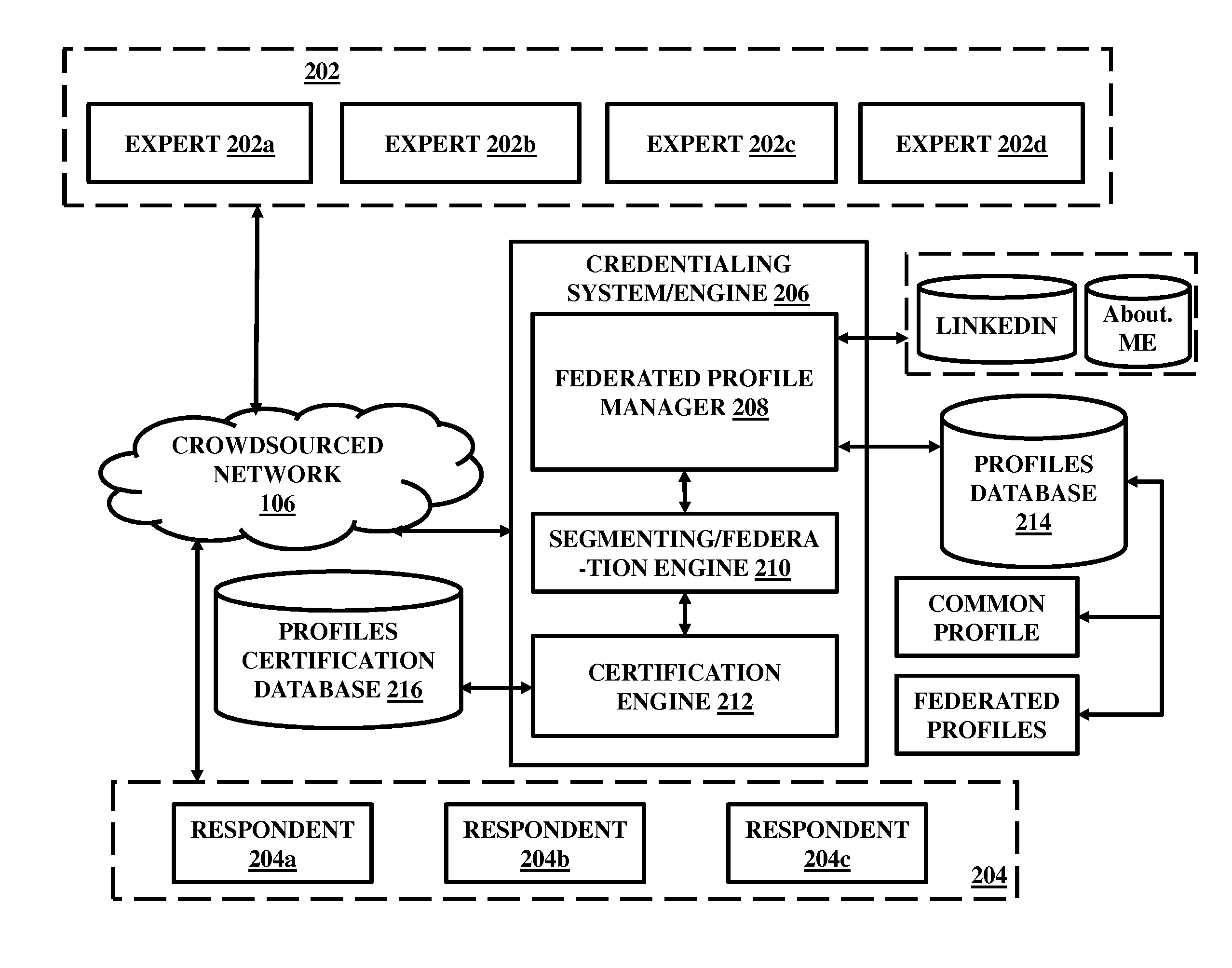
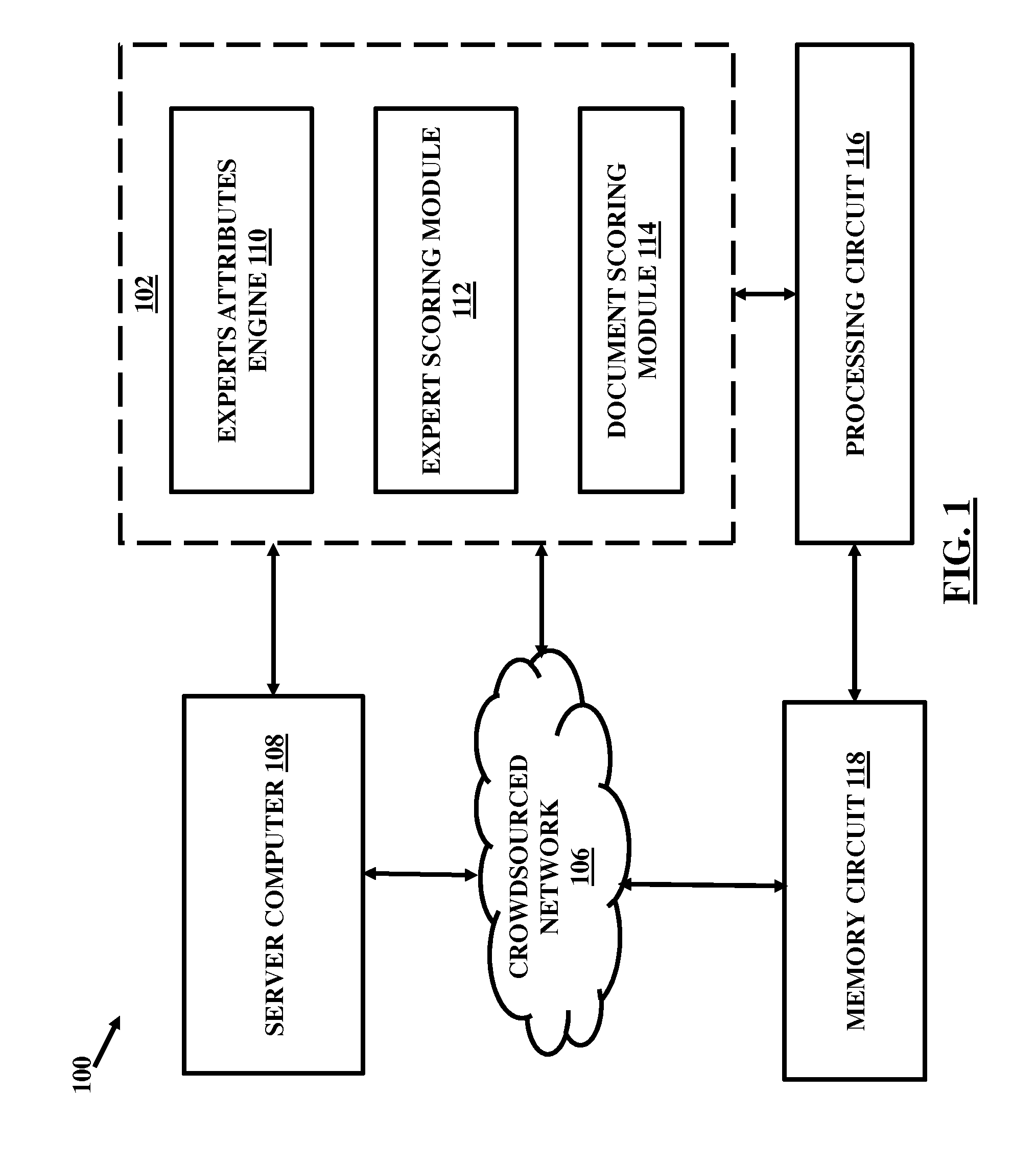
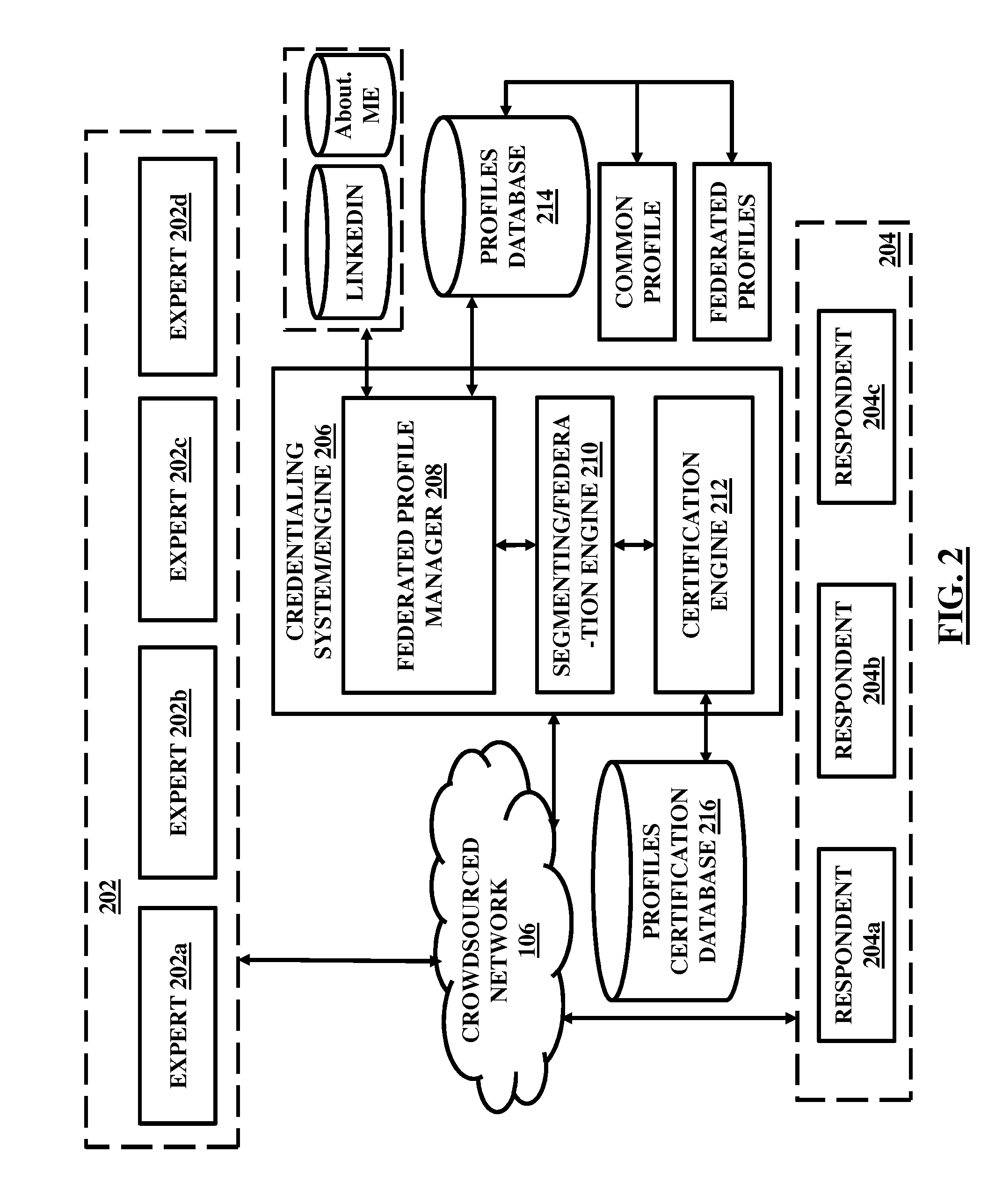
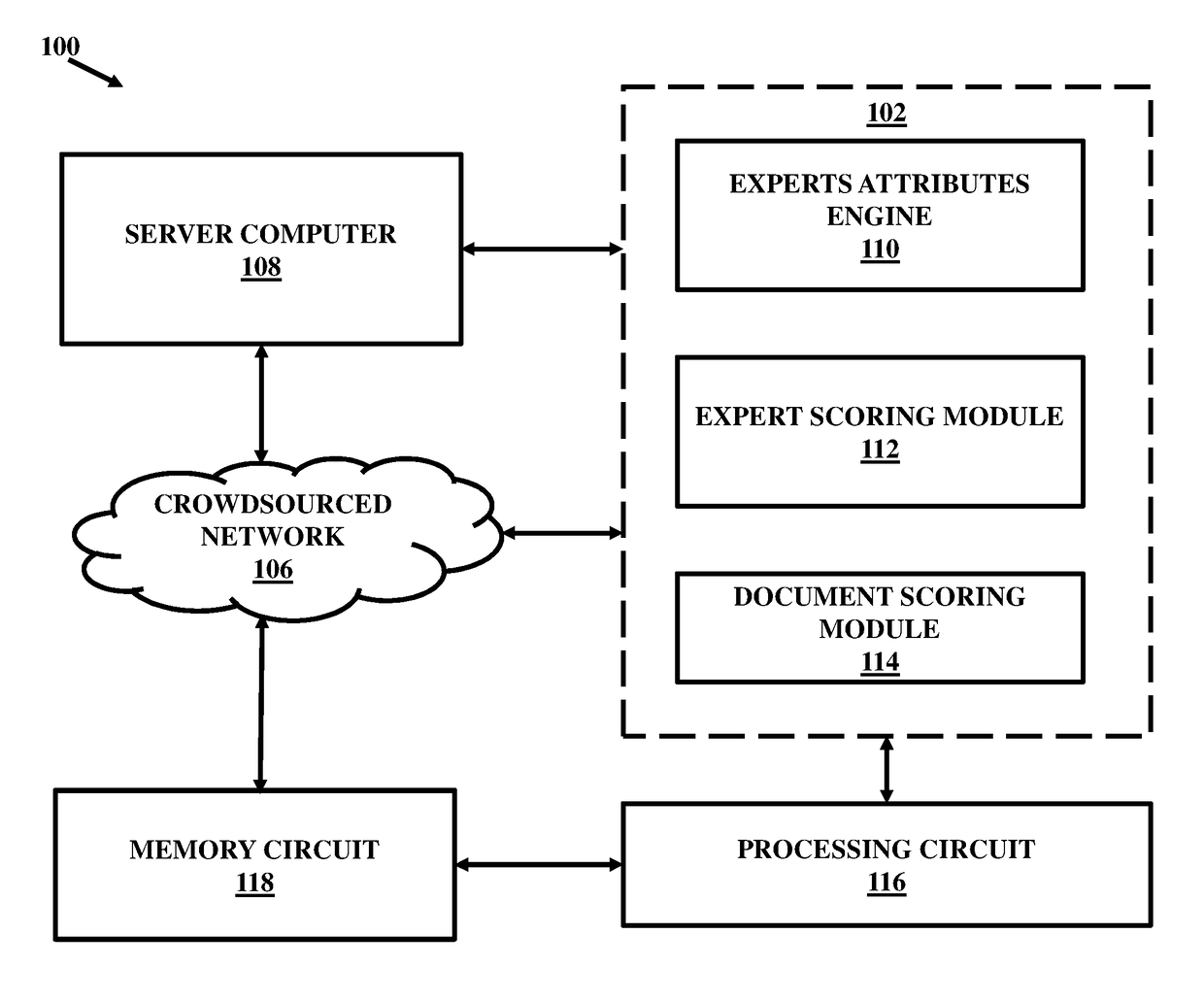
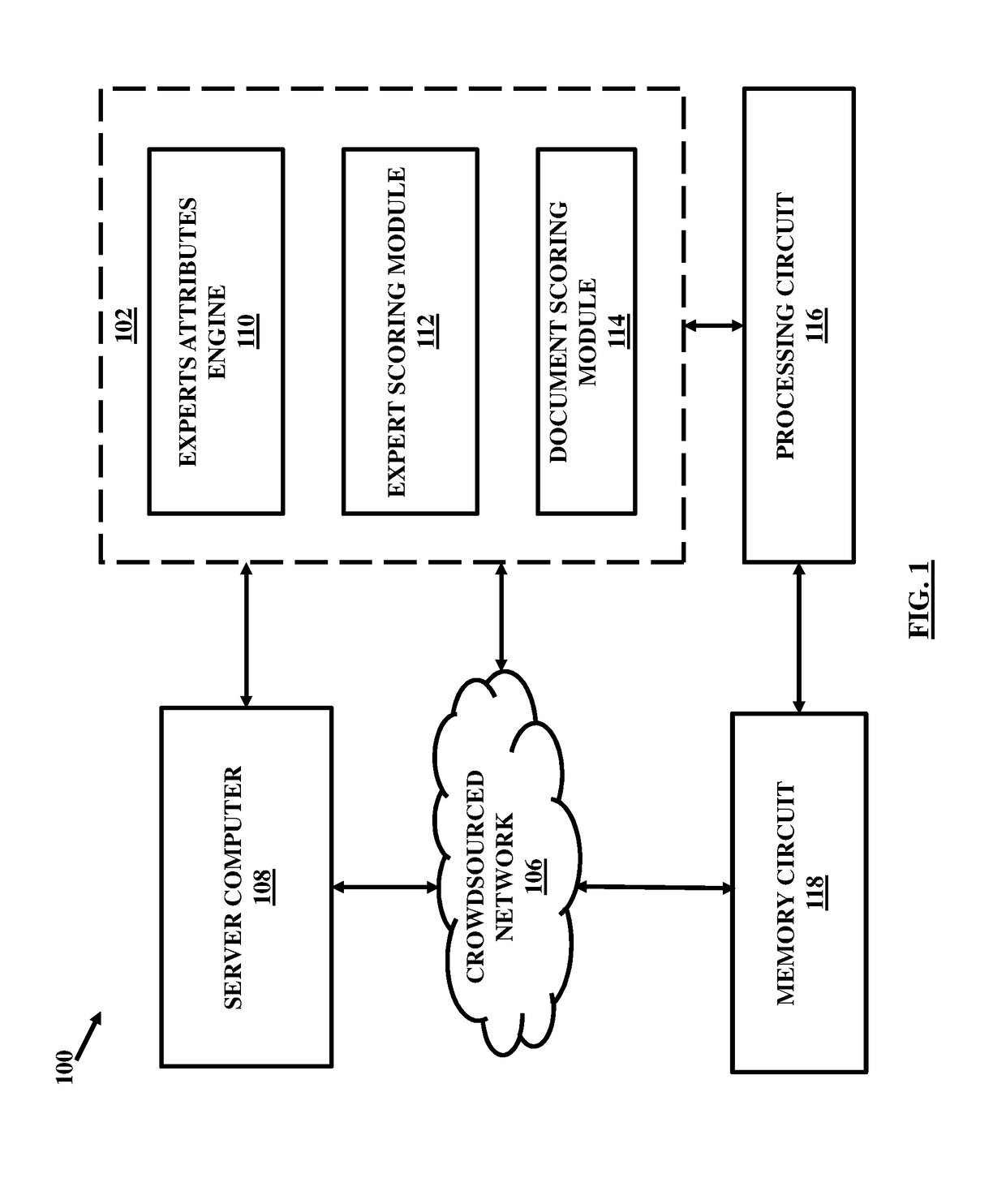
A blockchain configured system and a method for facilitating an expertise driven review and scoring of electronic documents in a crowdsourced environment. The system includes a server computer, a memory circuit and a processing circuit. The processing circuit is coupled to the memory circuit and includes or is coupled to a credentialing engine. The system further includes an expert scoring module. The system further includes a document reviewing and scoring engine coupled to the processing circuit. The document review and scoring module associates an aggregate score to the electronic document based on aggregation of the review ratings by crowdsourced experts and aggregate scores of each of the crowdsourced experts based on the set of attributes including one or more of the credentialed expertise, reputation of the expert, and the officiality.
Owner:NETSPECTIVE COMM
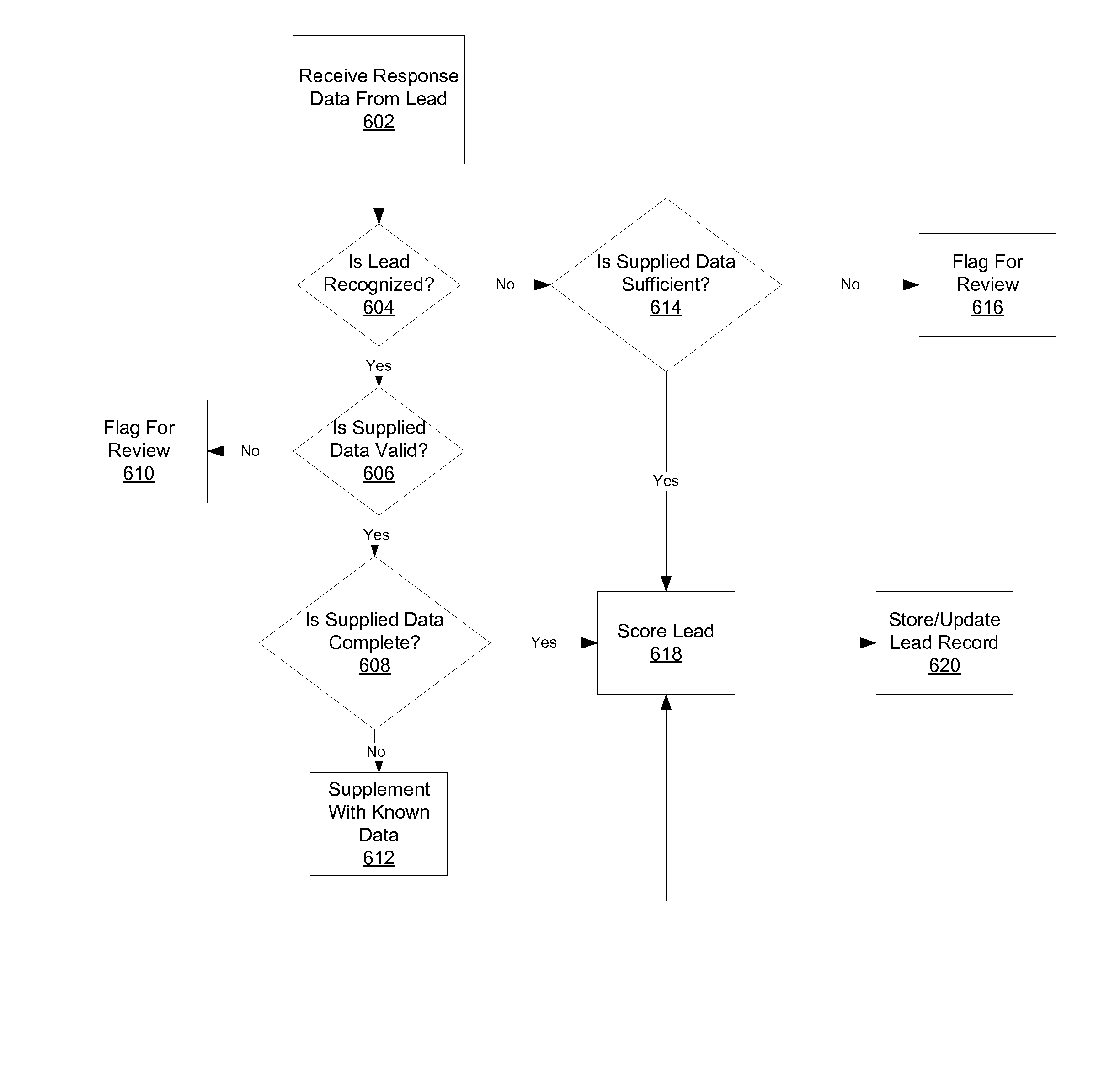
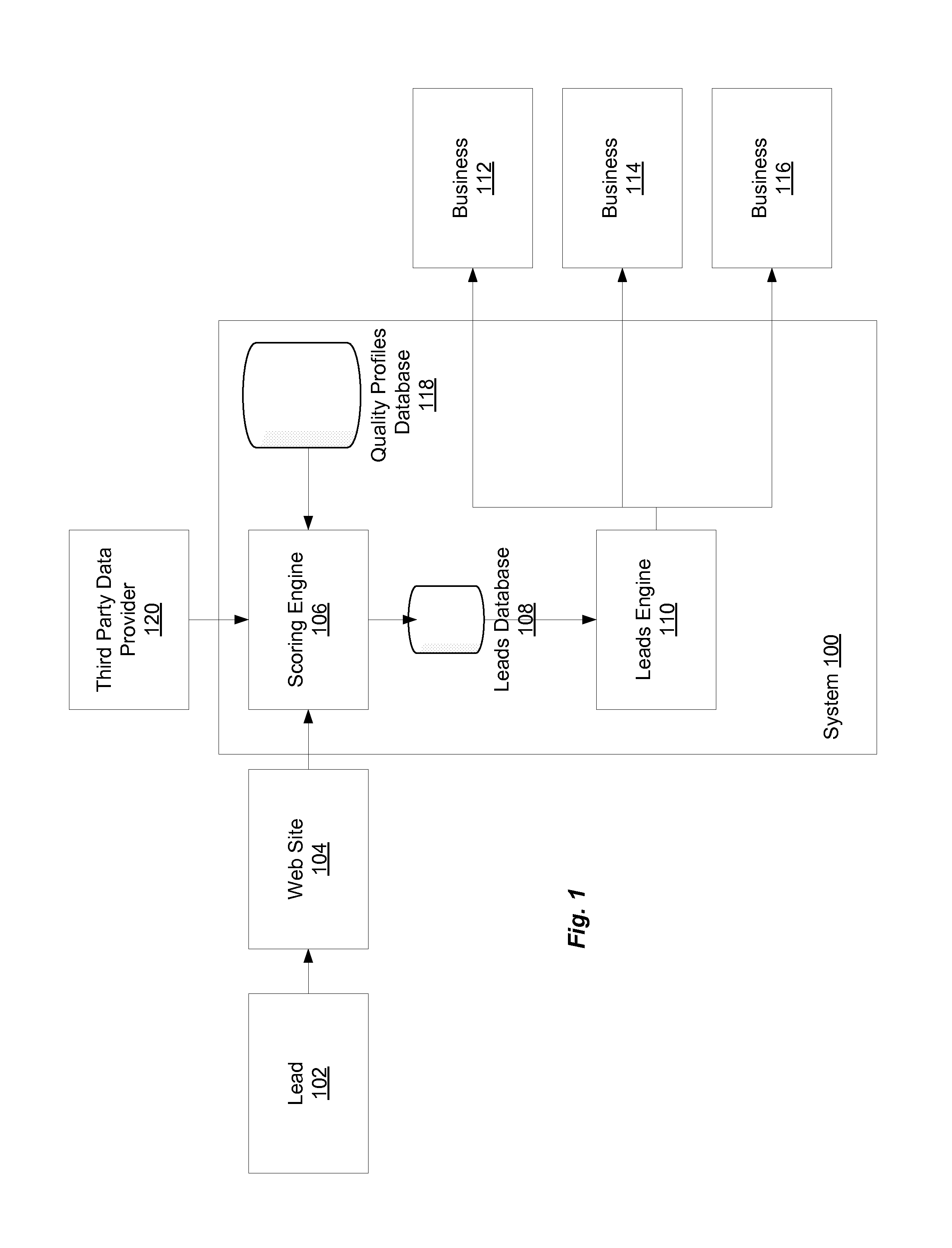
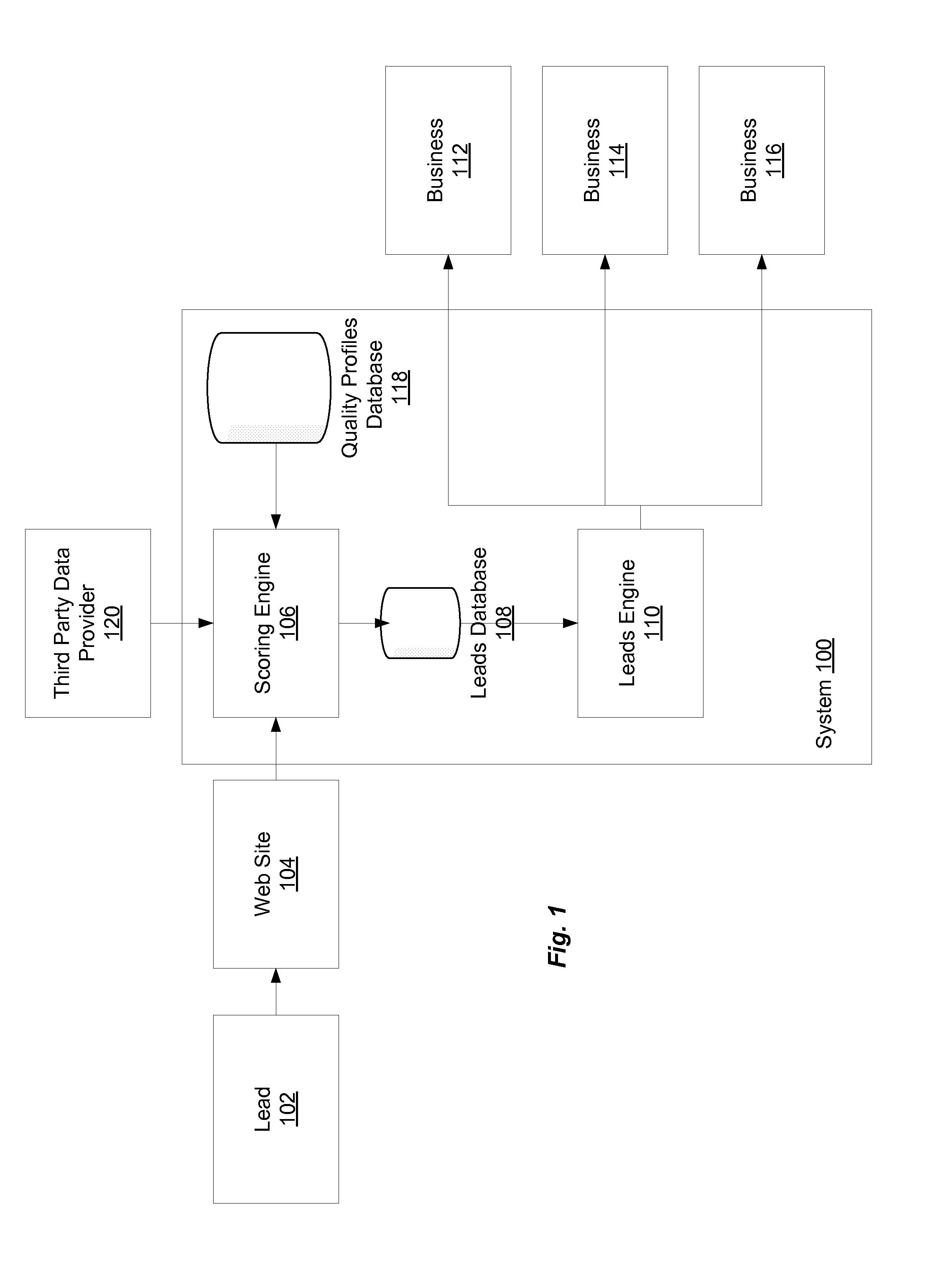
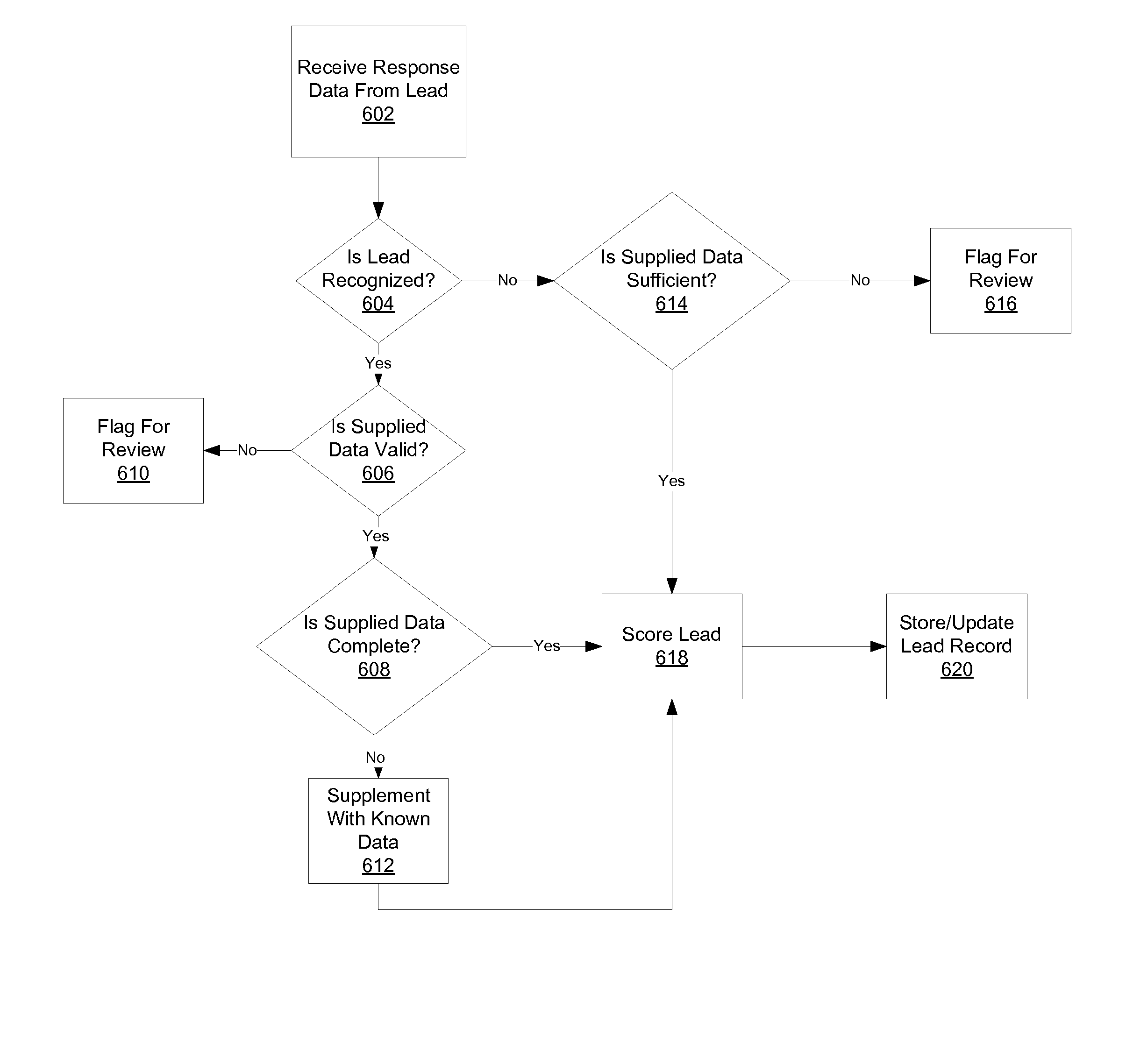
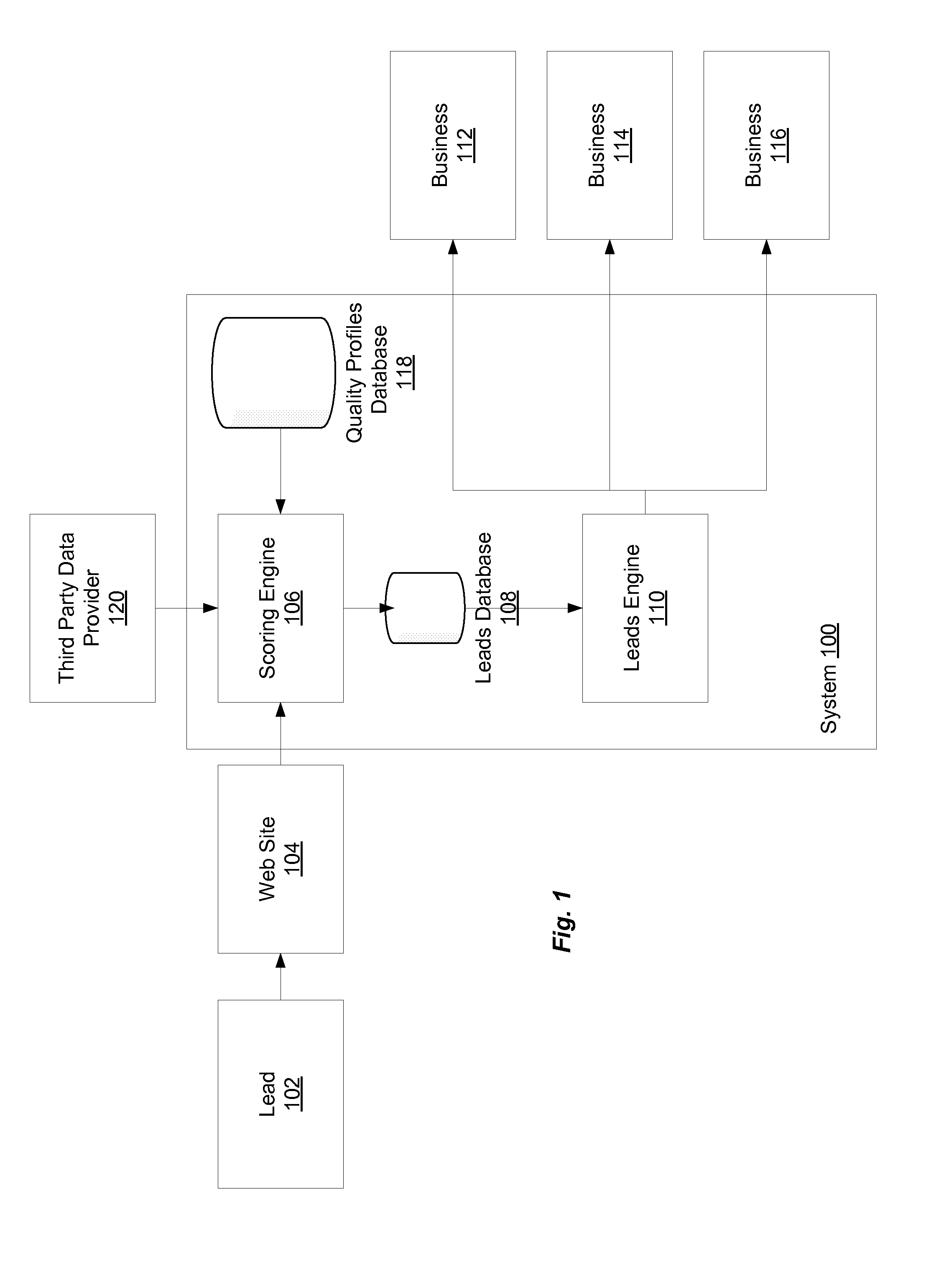
Automated Lead Scoring
Effective acquisition of high-quality sales leads is provided. Businesses provide scoring criteria, representing the relative importance of a potential customer's attributes, such as sales revenue, number of employees, industry, geographic location, etc. A scoring engine determines a score for the combination of a potential customer and one or more businesses by applying the criteria in the business' quality profile to the attribute values provided by the potential customer. If the score exceeds a threshold, information about the potential customer is provided to the business at a customized price. The business can then purchase contact information for the potential customer. If the business does not pursue the potential customer, the lead may be offered to additional businesses in a secondary marketplace. A business that agrees to have rejected leads contributed to the secondary marketplace can be issued a credit against past or future leads purchases.
Owner:DEMANDBASE
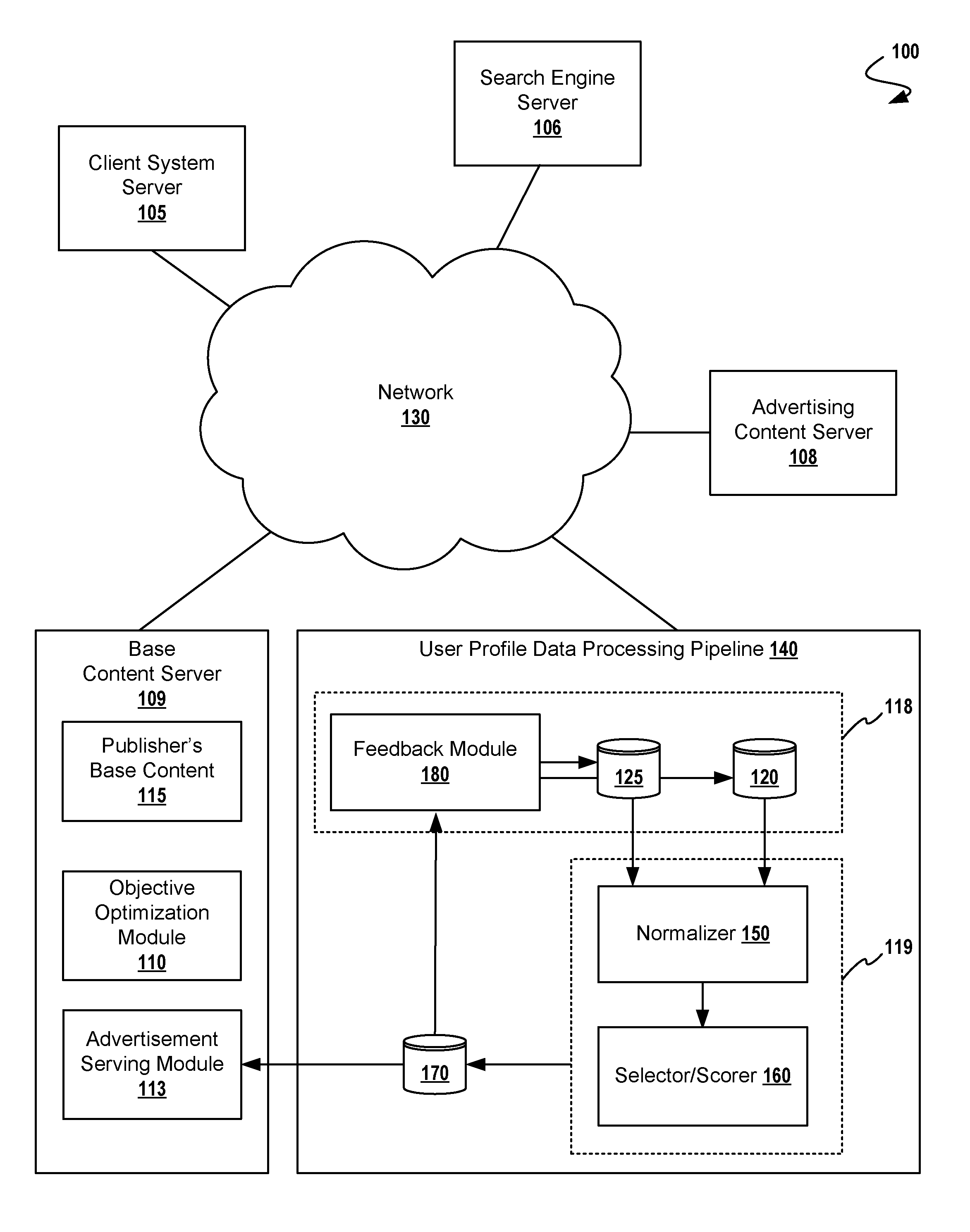
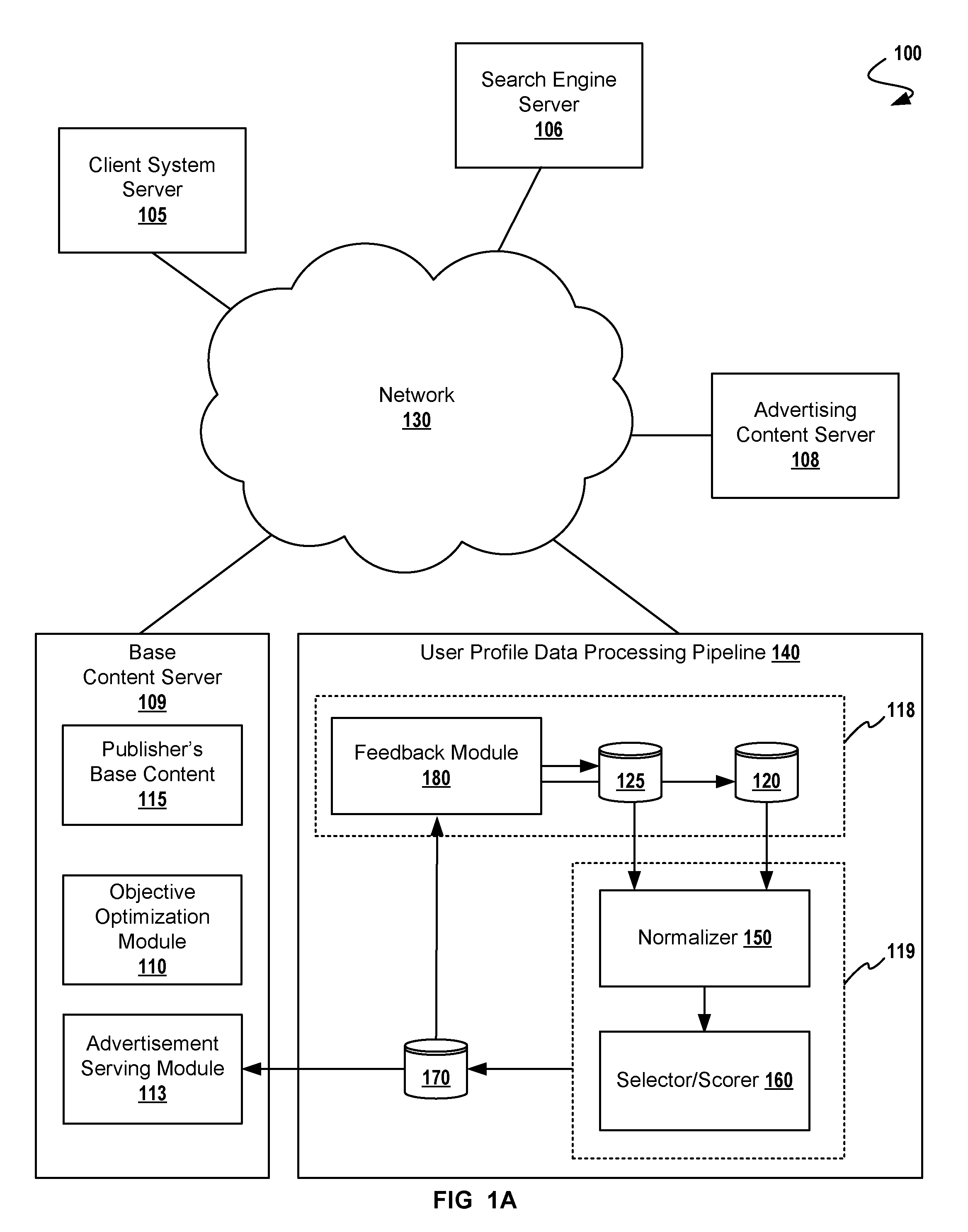
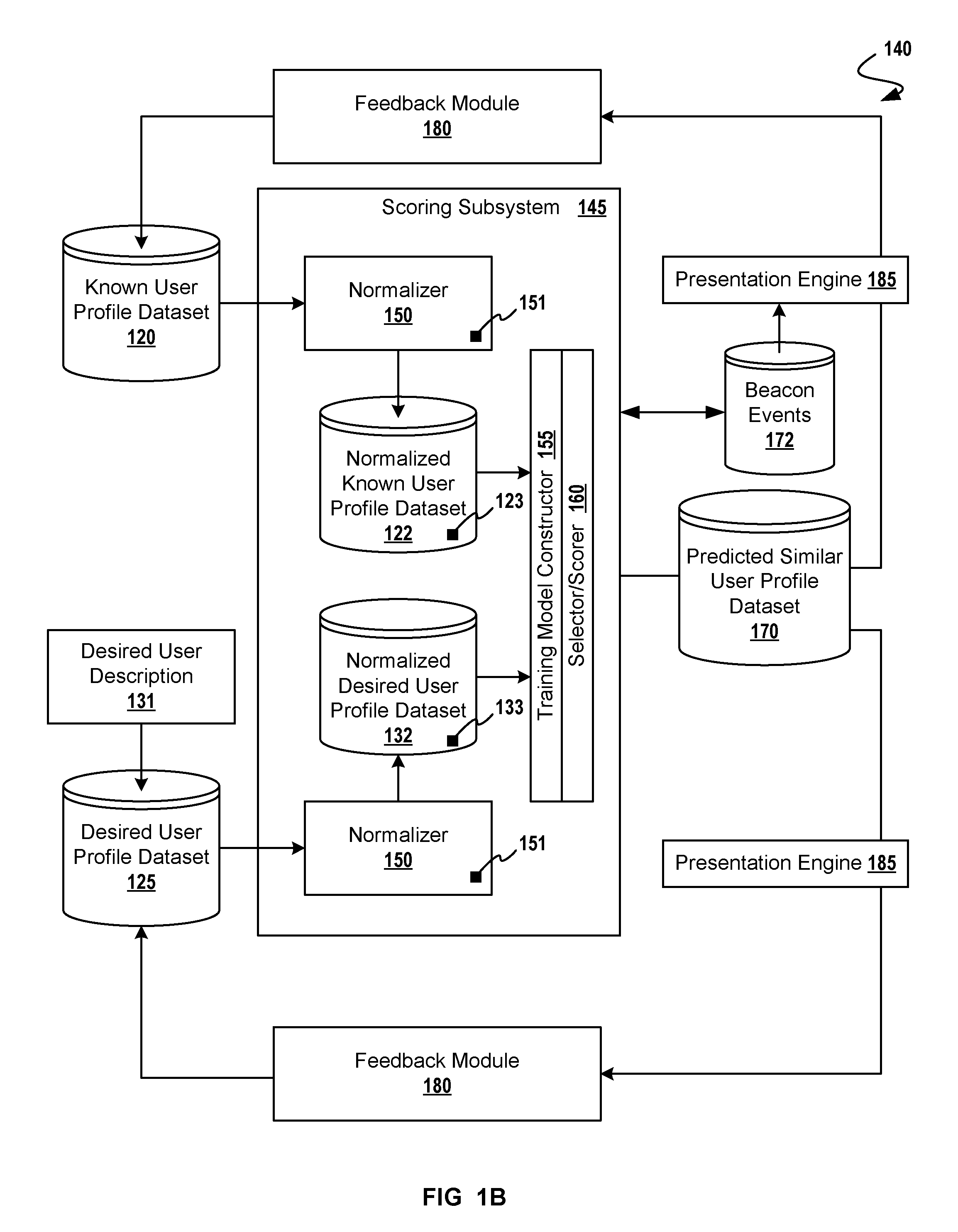
Adaptive Targeting for Finding Look-Alike Users
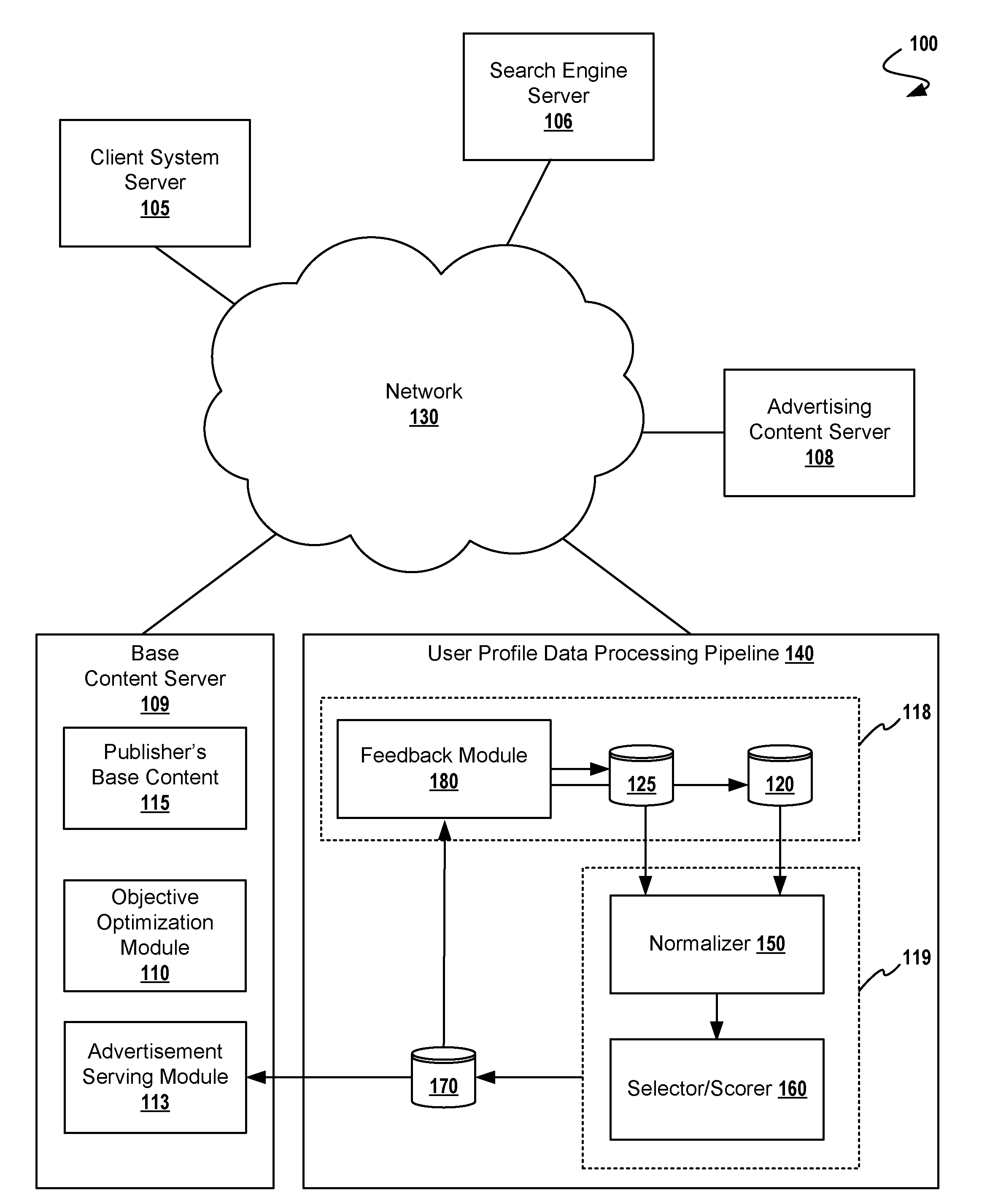
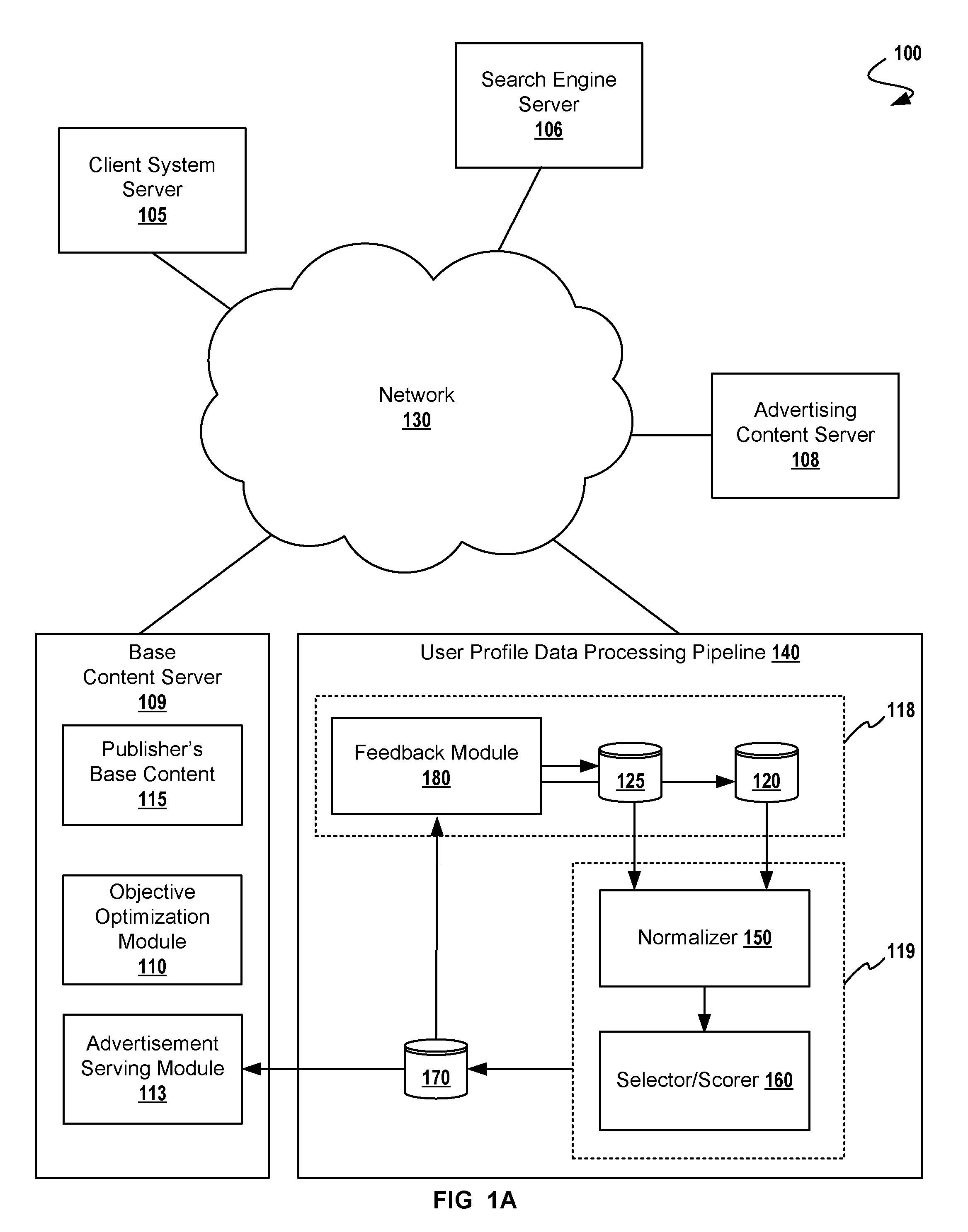
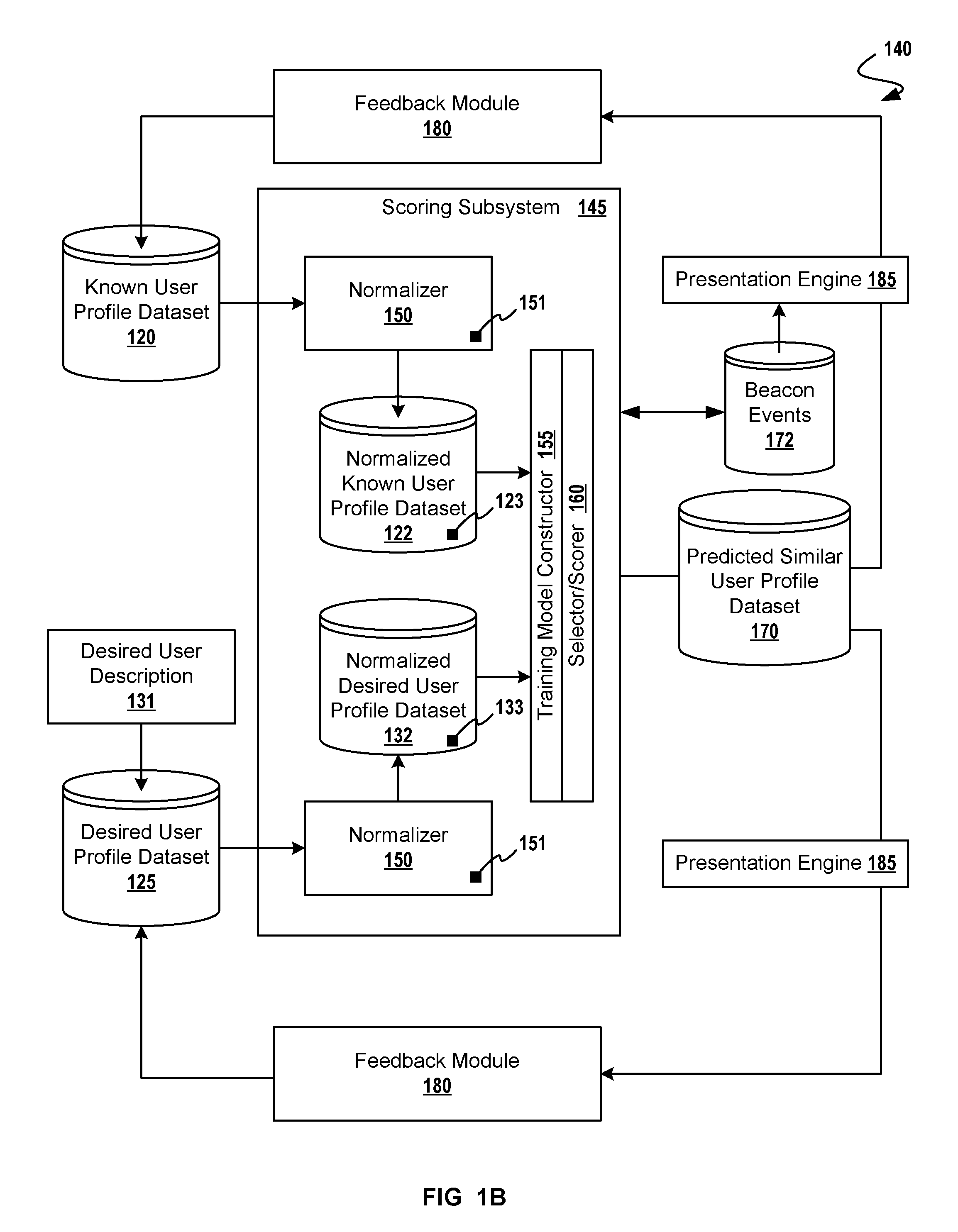
A method for adaptive display of internet advertisements to look-alike users using a desired user profile dataset as a seed to machine learning modules. Upon availability of a desired user profile, that user profile is mapped other look-alike users (from a larger database of users). The method proceeds to normalize the desired user profile object, proceeds to normalize known user profile objects, then seeding a machine-learning training model with the normalized desired user profile object. A scoring engine uses the normalized user profiles for matching based on extracted features (i.e. extracted from the normalized user profile objects). Once look-alike users have been identified, the internet display system may serve advertisements to the look-alike users, and analyze look-alike users' behaviors for storing the predicted similar user profile objects into the desired user profile object dataset, thus adapting to changing user behavior.
Owner:R2 SOLUTIONS
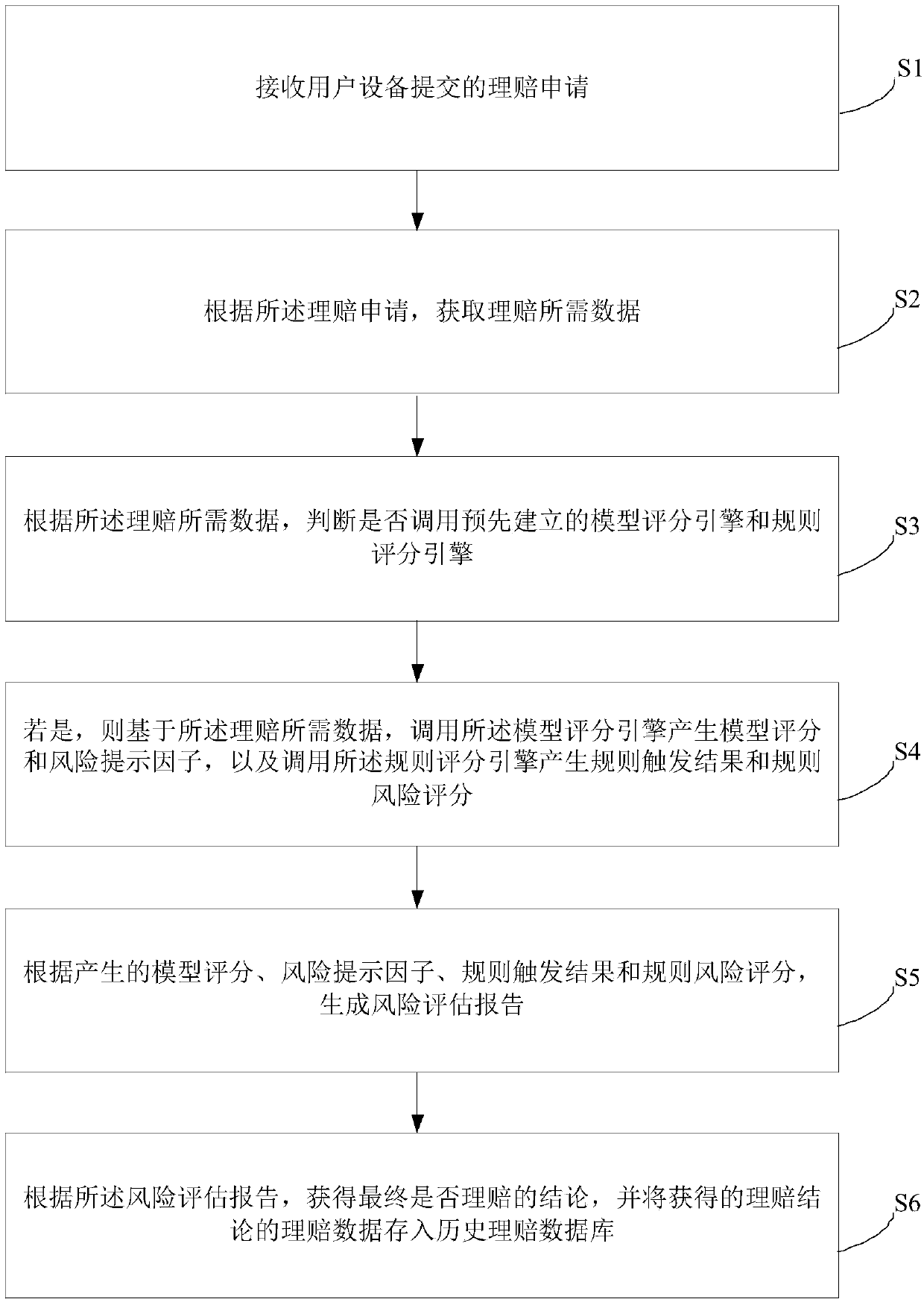
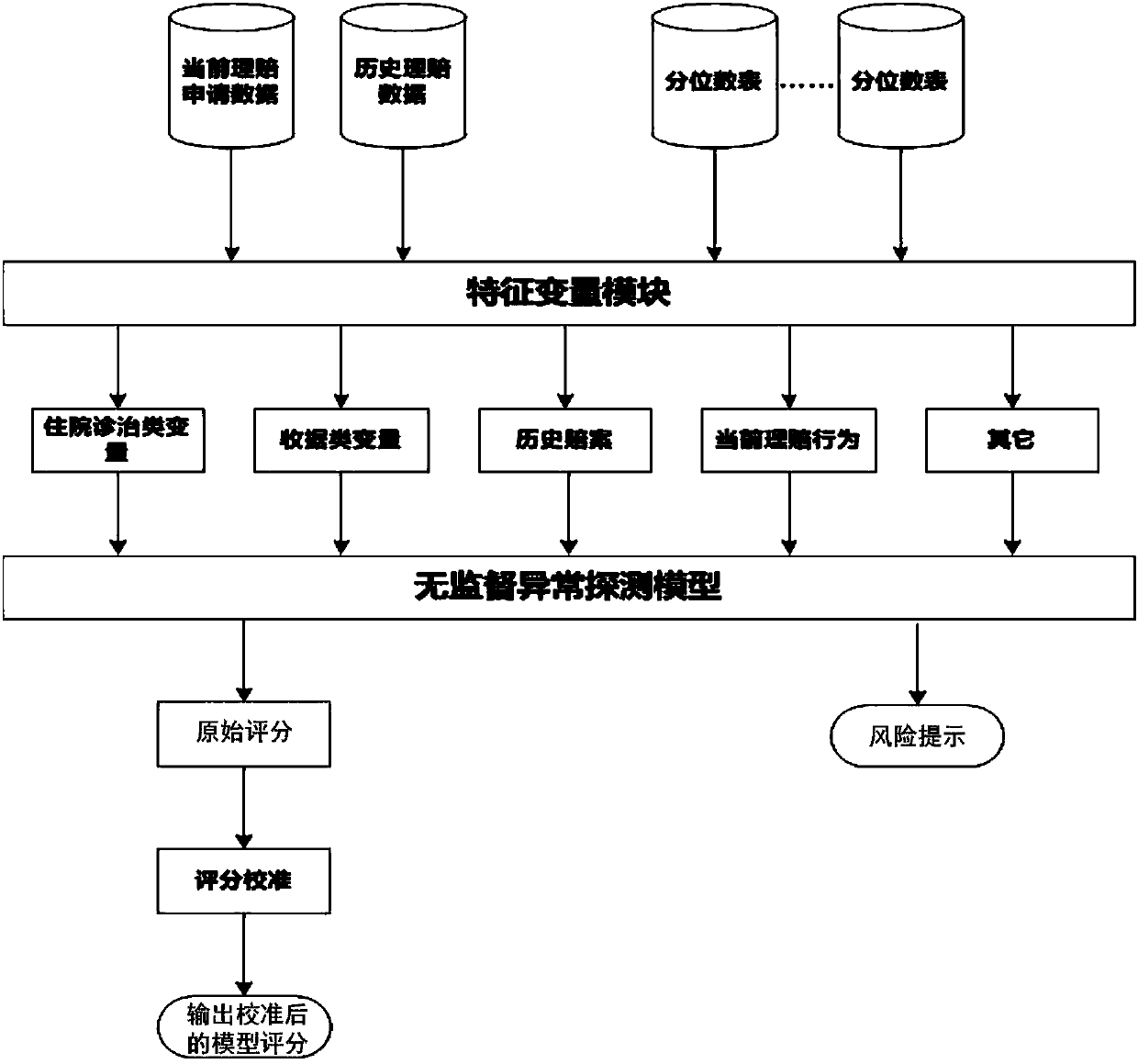
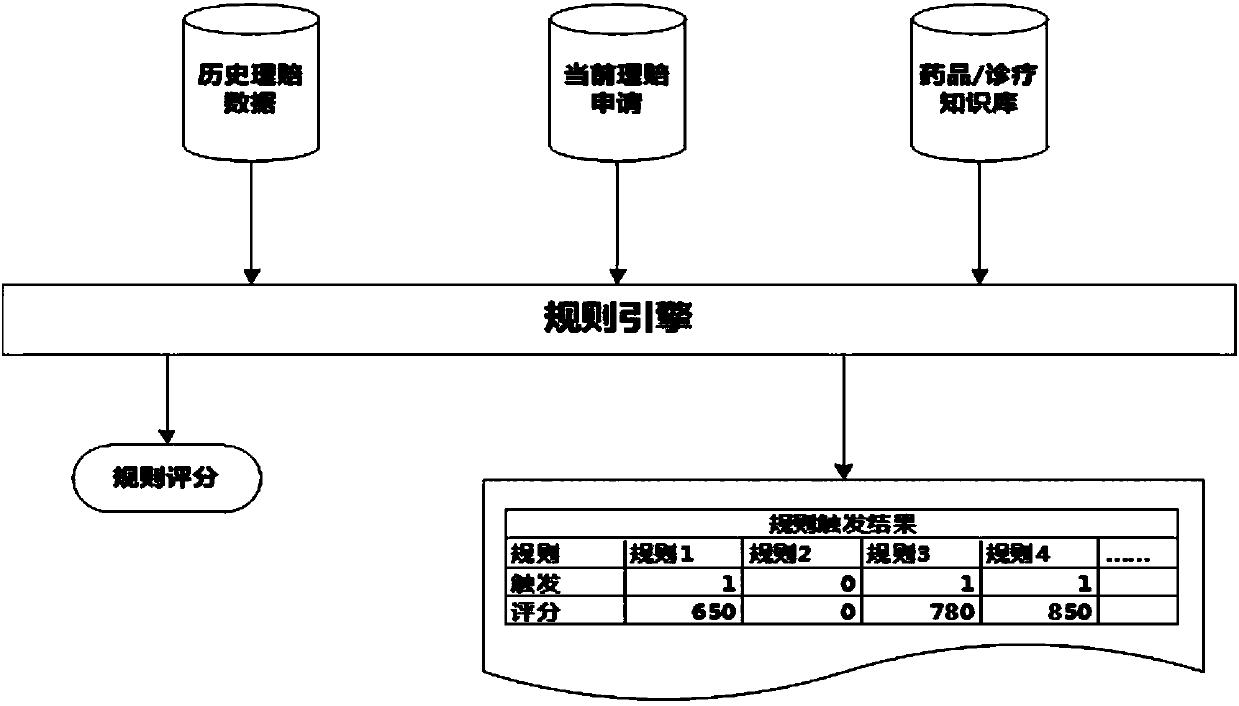
Detection method and system of health insurance compensation fraud and abuse
The embodiment of the invention discloses a detection method and system of health insurance compensation fraud and abuse. The method includes: receiving a claim application submitted by user equipment; acquiring data, which are required for a claim, according to the claim application; according to the data required for the claim, judging whether a pre-established model scoring engine and rule scoring engine are called; If yes, calling the model scoring engine on the basis of the data, which are required for the claim, to generate a model score and a risk prompting factor, and calling the rulescoring engine to generate rule triggering results and rule risk scores; generating a risk evaluation report according to the generated model score, risk prompting factor, rule triggering results andrule risk scores; and according to the risk evaluation report, obtaining a conclusion of whether the claim is finally settled, and storing claim data of the obtained claim conclusion into a historicalclaim database. According to the embodiment of the invention, detection on health insurance compensation fraud and abuse can be realized, and accuracy and efficiency of detection are greatly improved.
Owner:太平洋健康保险股份有限公司
Acquiring Leads Using Scoring
Effective acquisition of high-quality sales leads is provided. Businesses provide scoring criteria, representing the relative importance of a potential customer's attributes, such as sales revenue, number of employees, industry, geographic location, etc. A scoring engine determines a score for the combination of a potential customer and one or more businesses by applying the criteria in the business' quality profile to the attribute values provided by the potential customer. If the score exceeds a threshold, information about the potential customer is provided to the business at a customized price. The business can then purchase contact information for the potential customer. If the business does not pursue the potential customer, the lead may be offered to additional businesses in a secondary marketplace. A business that agrees to have rejected leads contributed to the secondary marketplace can be issued a credit against past or future leads purchases.
Owner:DEMANDBASE
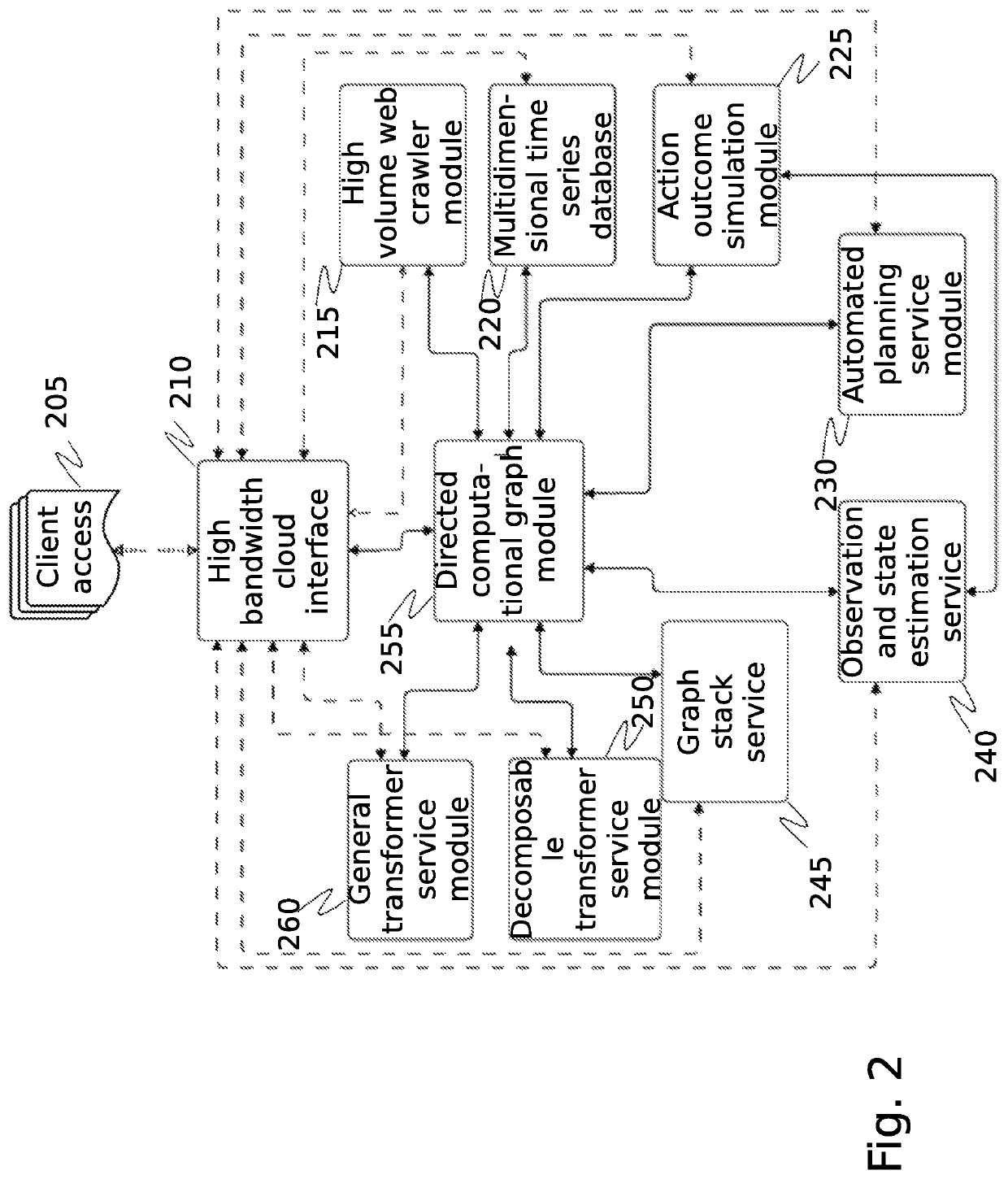
System and method for cybersecurity analysis and score generation for insurance purposes
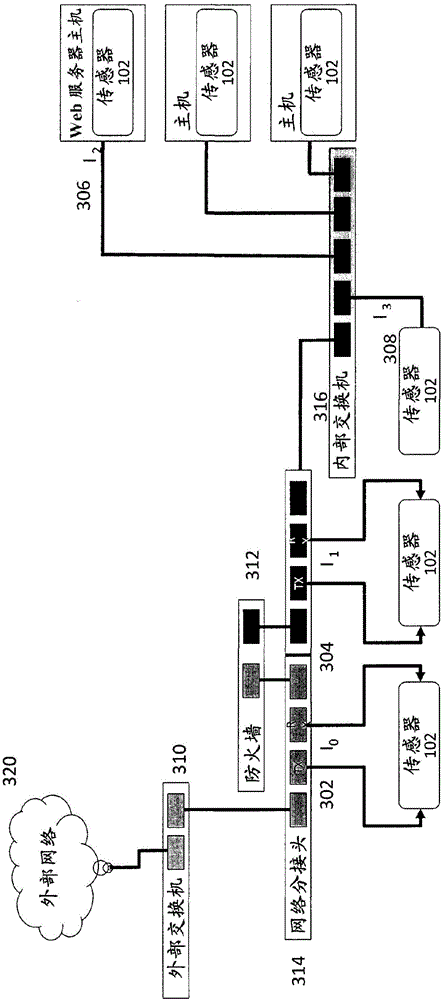
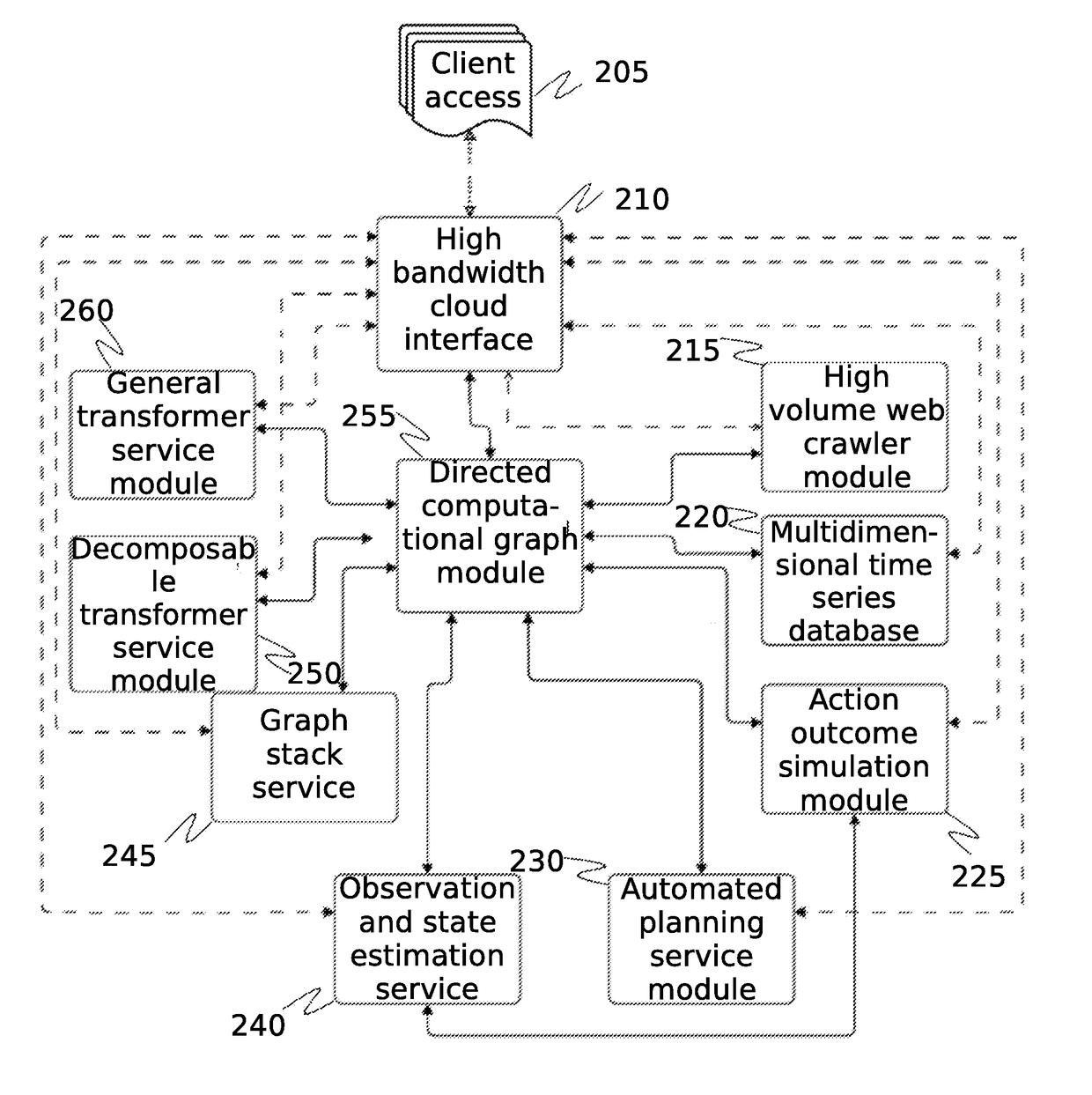
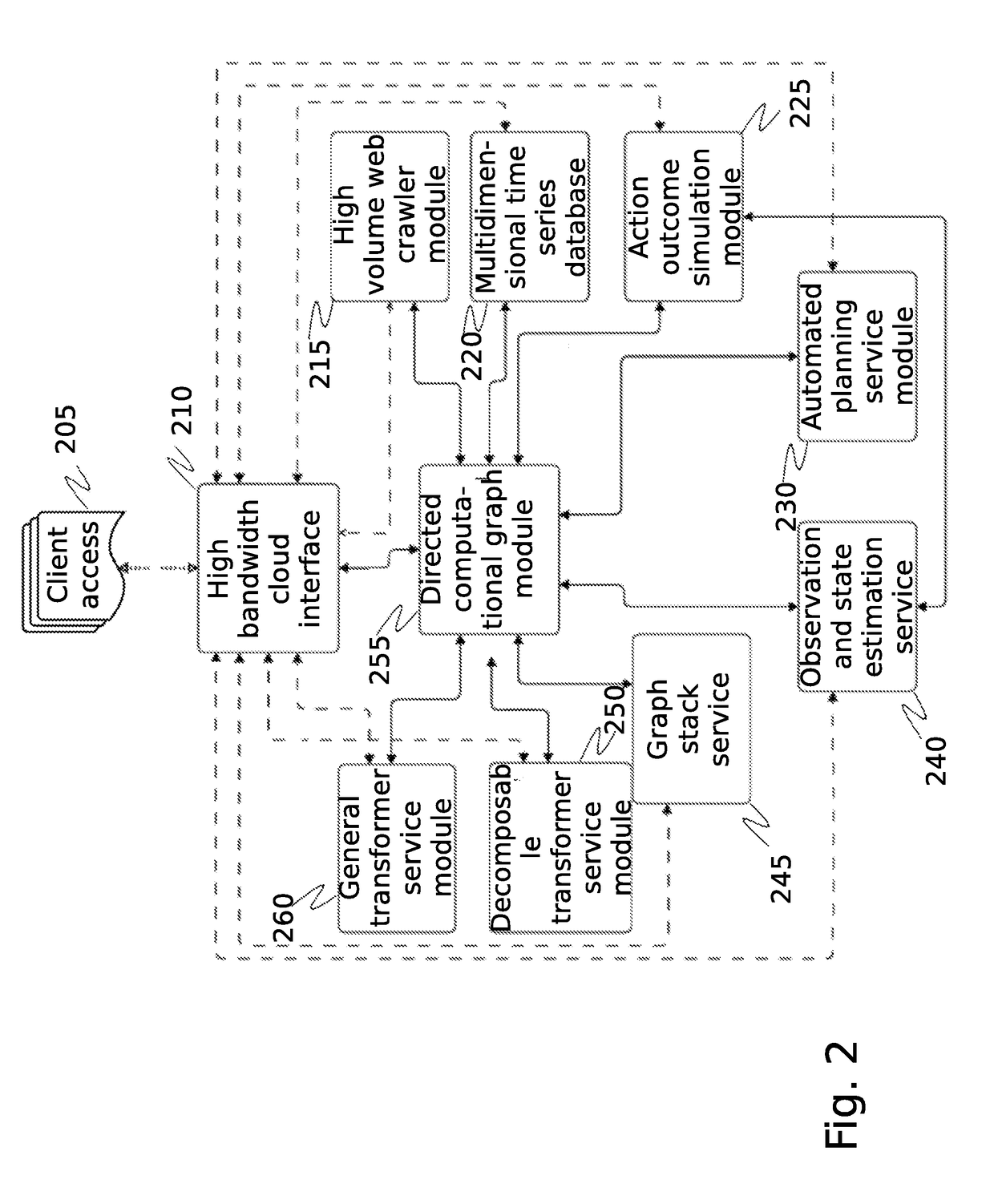
A system for comprehensive cybersecurity analysis and rating based on heterogeneous data and reconnaissance is which uses a high volume web crawler directed by an automated planning service module to establish a scope of cybersecurity analysis for a target network, perform reconnaissance of the target network, and assign scores for several types of reconnaissance, and uses a cybersecurity scoring engine to generate an aggregated cybersecurity rating from the assigned scores.
Owner:QOMPLX LLC
Systems and methods for selectively delaying financial transactions
A risk system that performs a risk assessment of a financial transaction to obtain an initial risk score. Based on the initial risk score, the risk system performs at least one post-score assessment by selectively utilizing various scoring engines and databases. The at least one post-score risk assessment may include delaying the shipment of merchandise in financial transactions that are of marginal risk to thereby provide a check acceptance service with more time to further evaluate the financial transaction risks. Thus, marginally risky financial transactions that are likely to benefit the check acceptance service and a merchant that subscribes to the check acceptance service are authorized for increased profitability and customer satisfaction. Furthermore, the post-score risk assessment may approve or authorize financial transactions that generally fail standard risk assessments that use a cut-off risk score to divide the financial transactions into either approved or declined groups. As a result, the post-score assessment process efficiently re-evaluates some of the borderline exception cases for the purpose of securing beneficial financial transactions.
Owner:FIRST DATA
Crowdsourced electronic documents review and scoring
InactiveUS20150074033A1Knowledge representationSpecial data processing applicationsElectronic documentDocumentation procedure
A system and a method for facilitating an expertise driven review and scoring of electronic documents in a crowdsourced environment. The system includes a server computer, a memory circuit and a processing circuit. The processing circuit is coupled to the memory circuit and includes or is coupled to a credentialing engine. The system further includes an expert scoring module. The system further includes a document reviewing and scoring engine coupled to the processing circuit. The document review and scoring module associates an aggregate score to the electronic document based on aggregation of the review ratings by crowdsourced experts and aggregate scores of each of the crowdsourced experts based on the set of attributes including one or more of the credentialed expertise, reputation of the expert, and the officiality.
Owner:NETSPECTIVE COMM
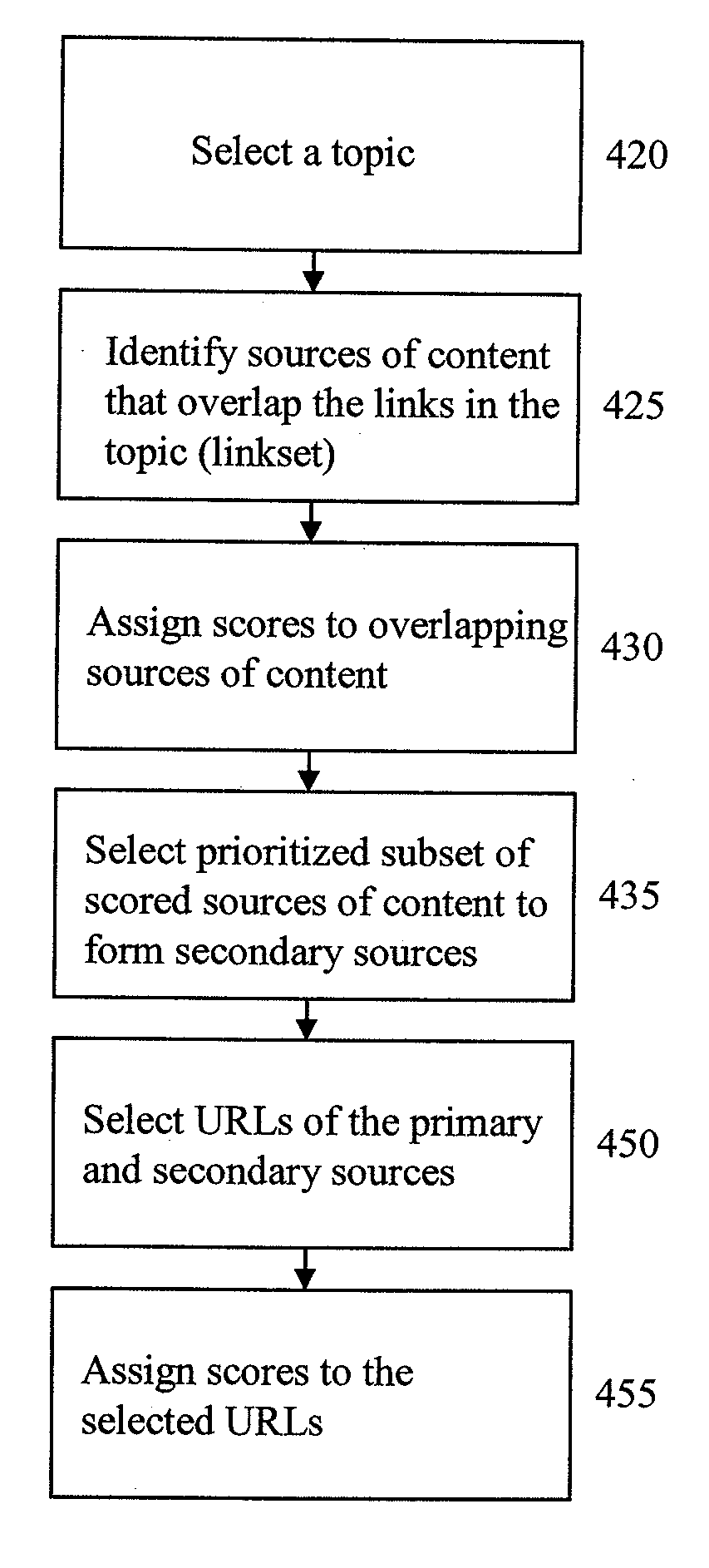
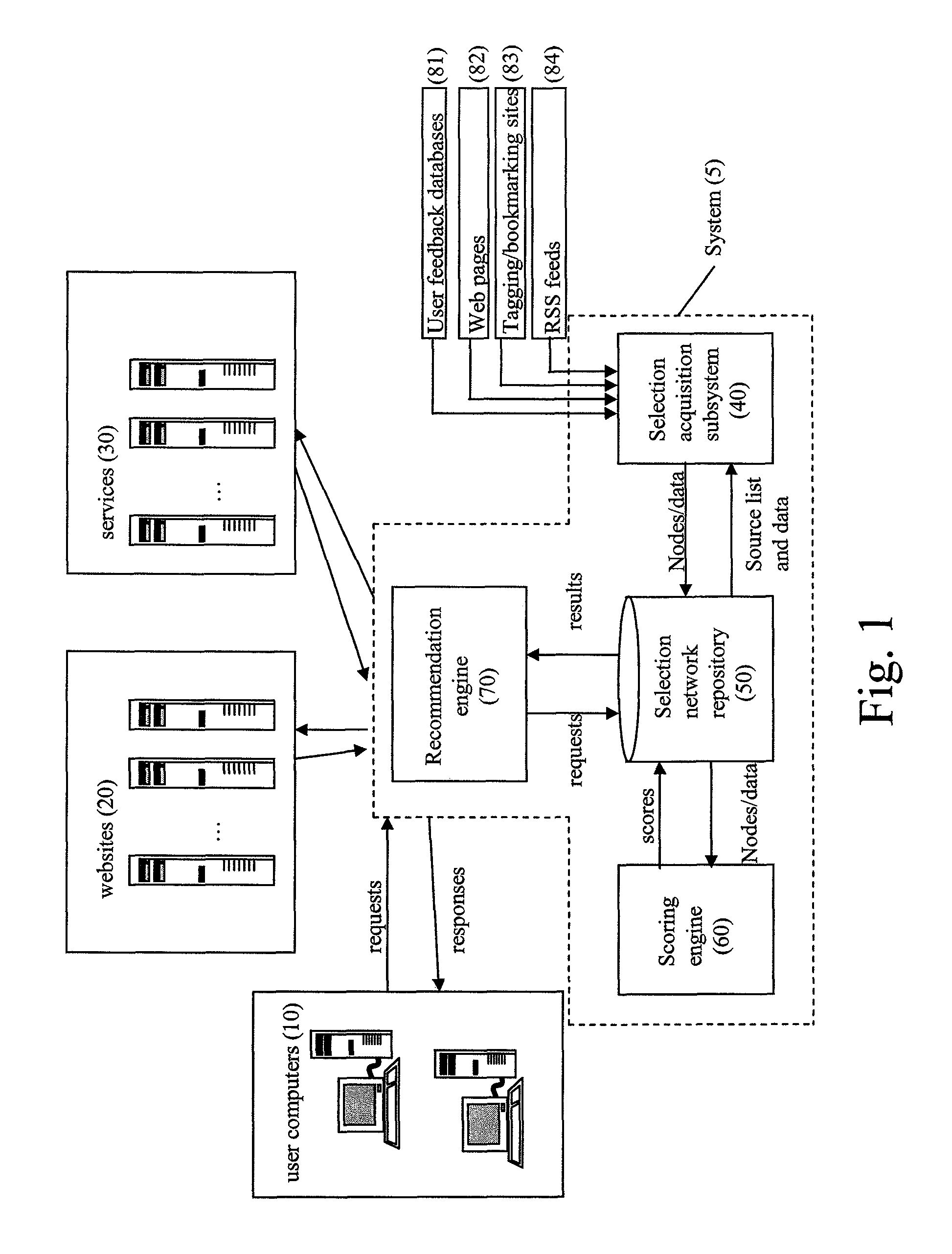
System and method for indexing a network of interrelated elements
ActiveUS7761423B1Digital data processing detailsDigital computer detailsSystem identificationInformation retrieval
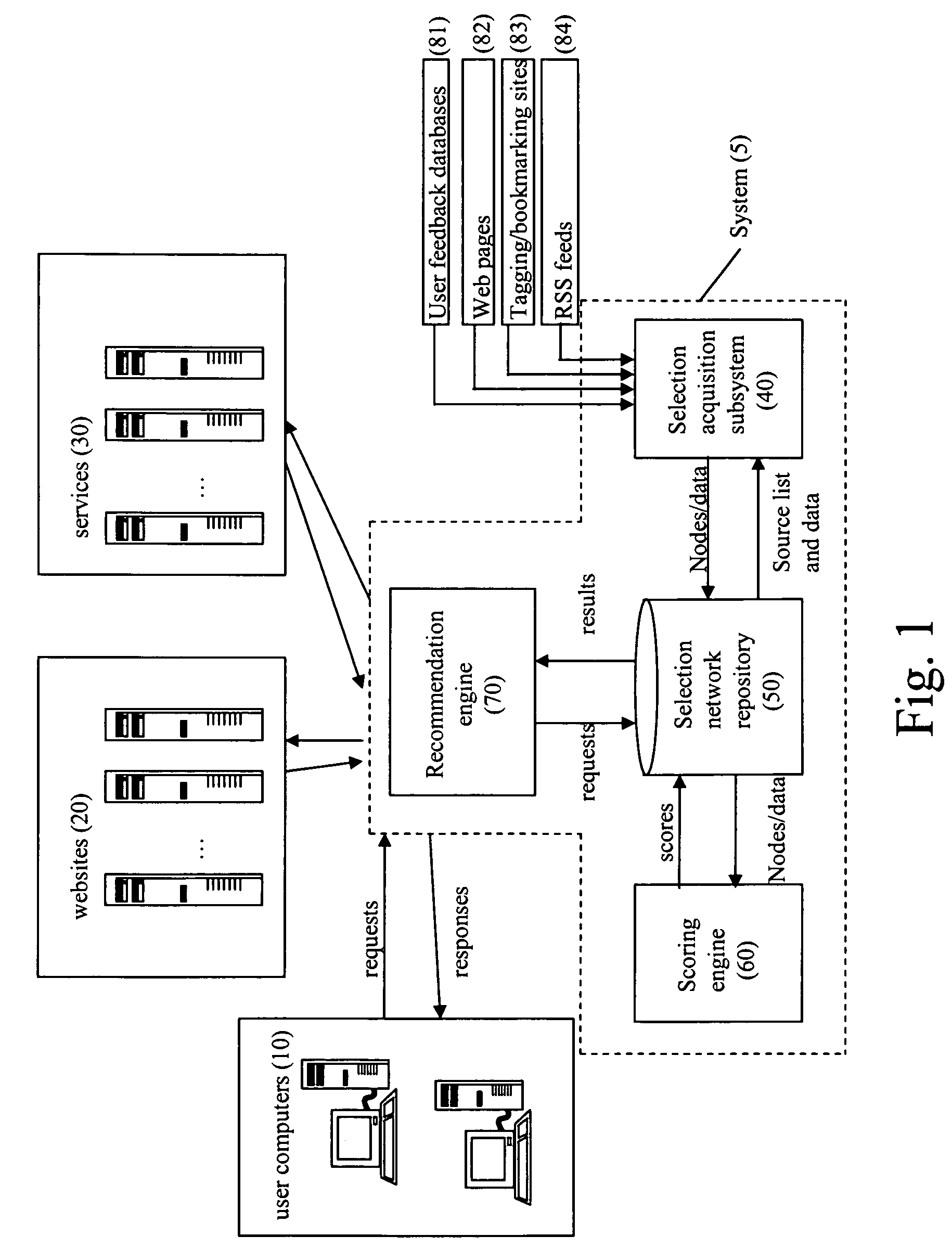
The system provides a technique for finding relevant content and content sources based on the aggregation and analysis of individual indications of relevance. The system identifies and provides selections of relevant content. It may comprise a selection acquisition subsystem, a selection network repository subsystem, a scoring engine, and a recommendation engine, and is used to generate sources of content comprising sets of prioritized links directed to a topic or community of interest.
Owner:ESW HLDG INC
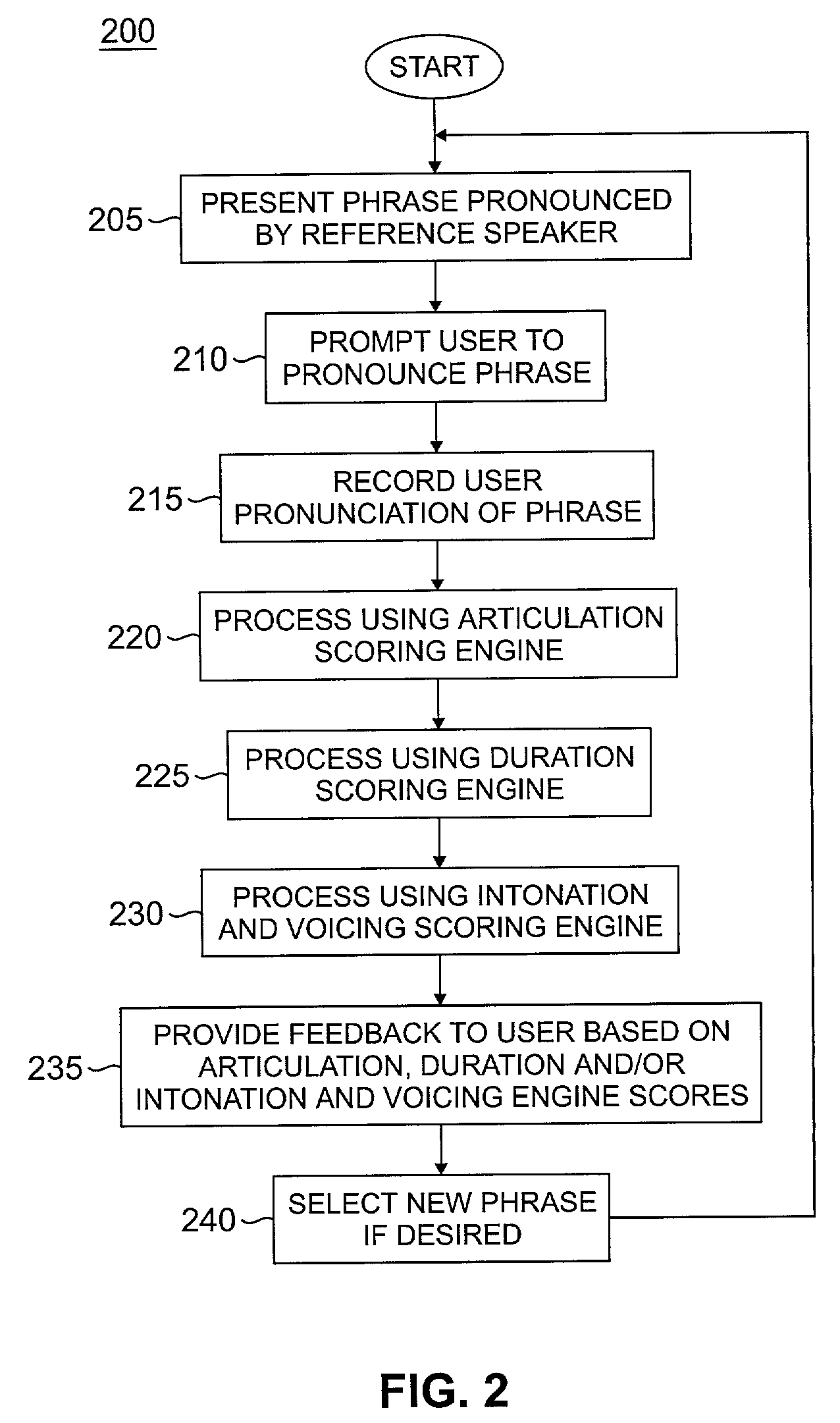
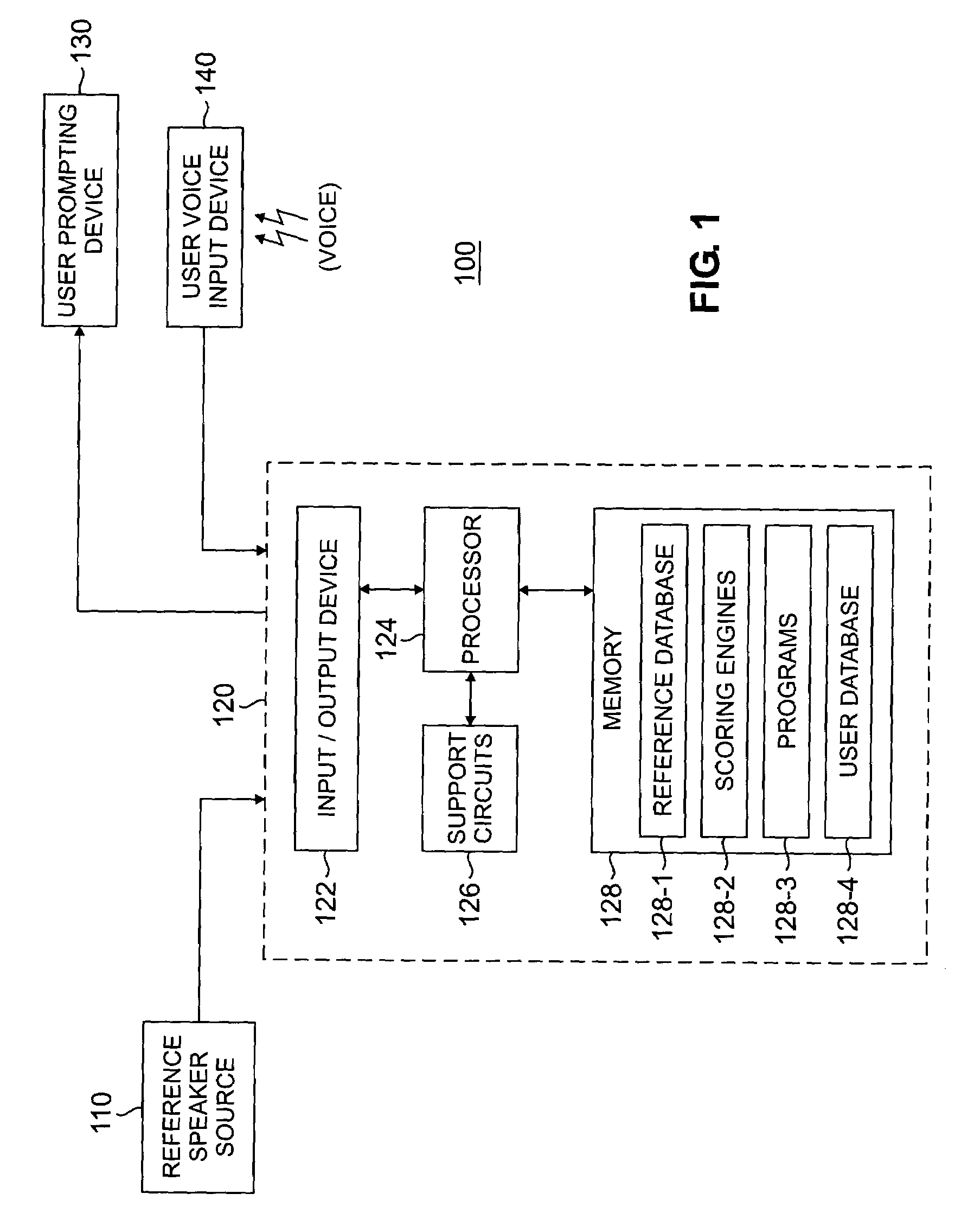
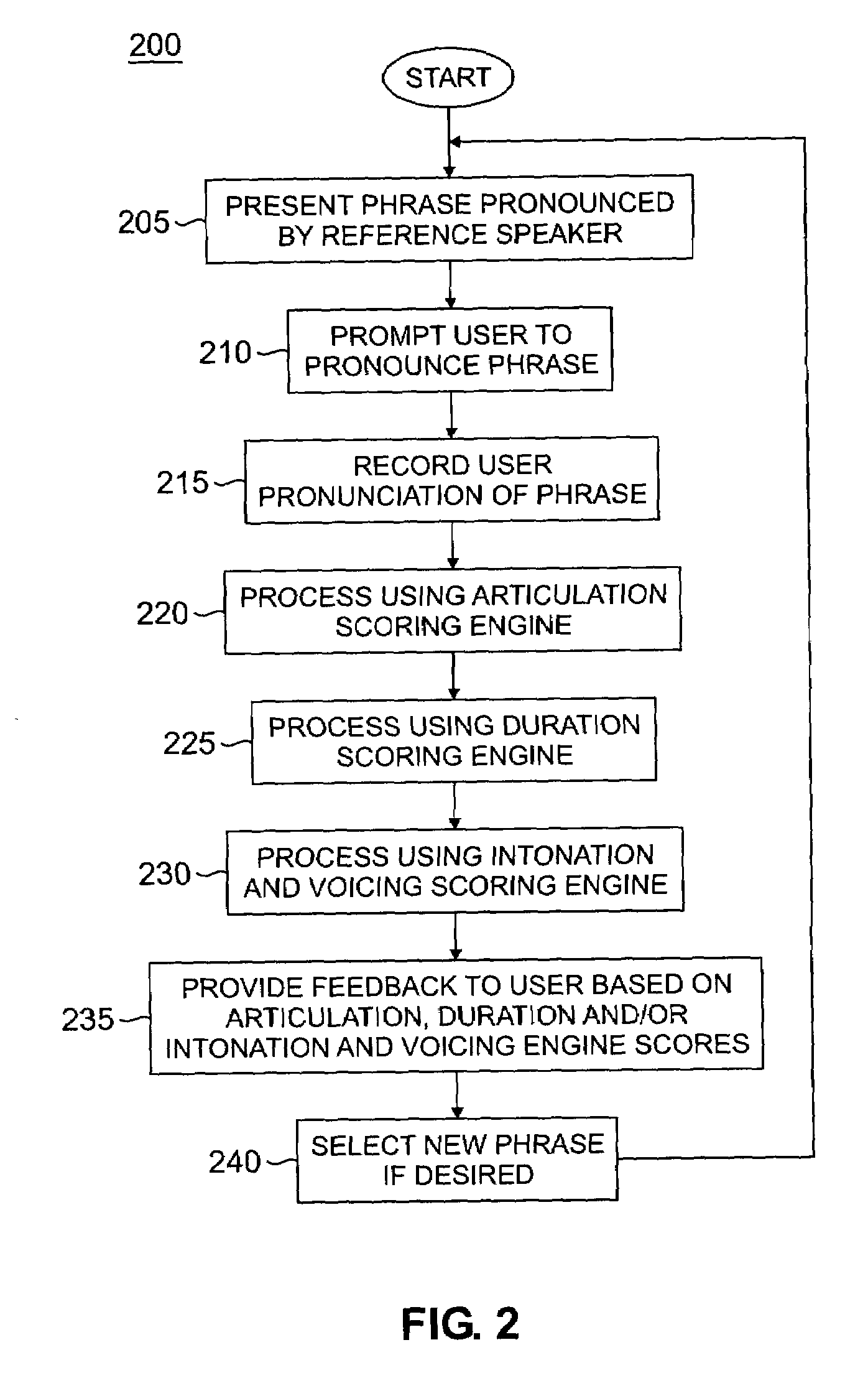
Automatic pronunciation scoring for language learning
InactiveUS7219059B2Meaningful feedbackFocusSpeech recognitionTeaching apparatusArticulation scoreVerbal learning
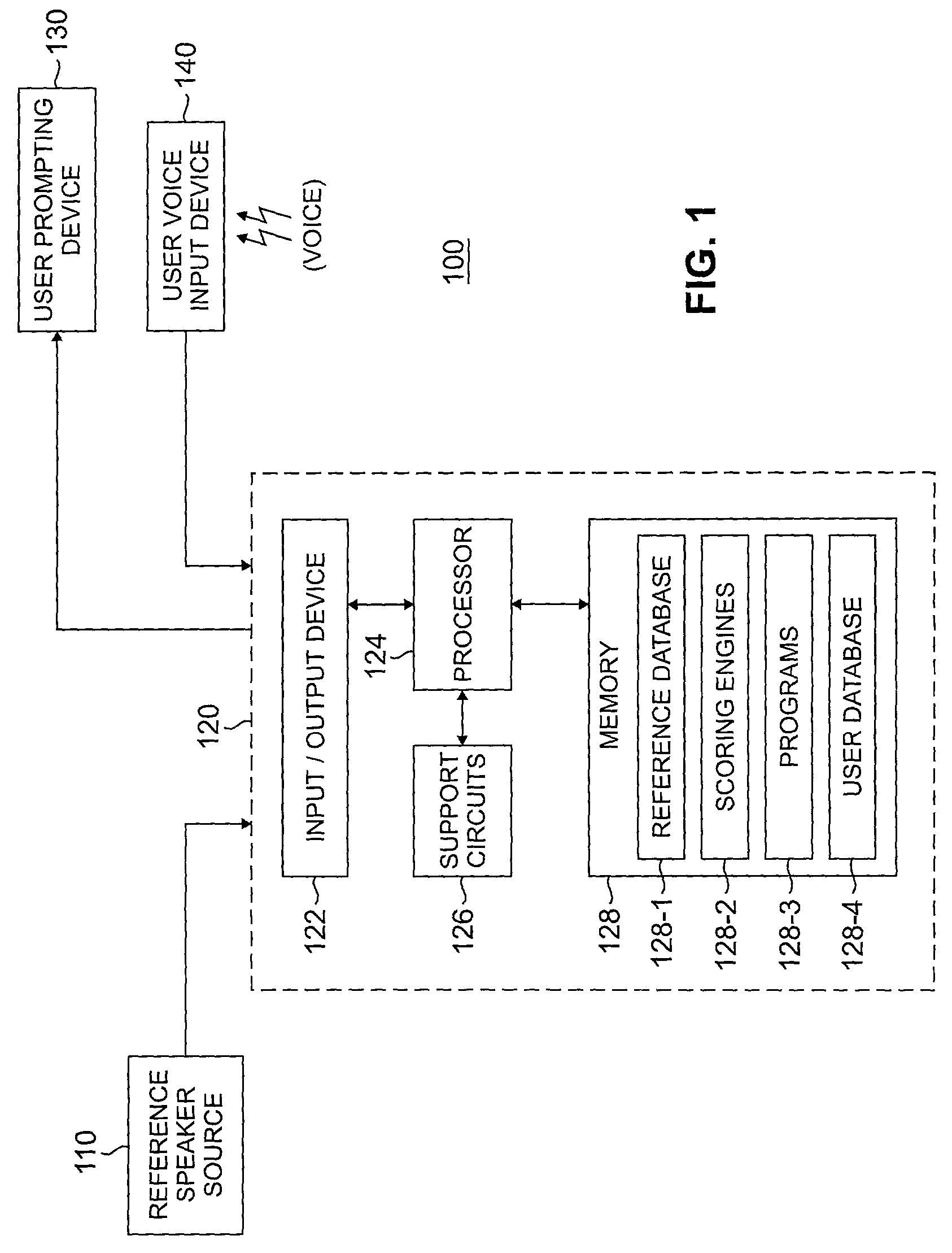
A method and apparatus for generating a pronunciation score by receiving a user phrase intended to conform to a reference phrase and processing the user phrase in accordance with at least one of an articulation-scoring engine, a duration scoring engine and an intonation-scoring engine to derive thereby the pronunciation score.
Owner:WSOU INVESTMENTS LLC +1
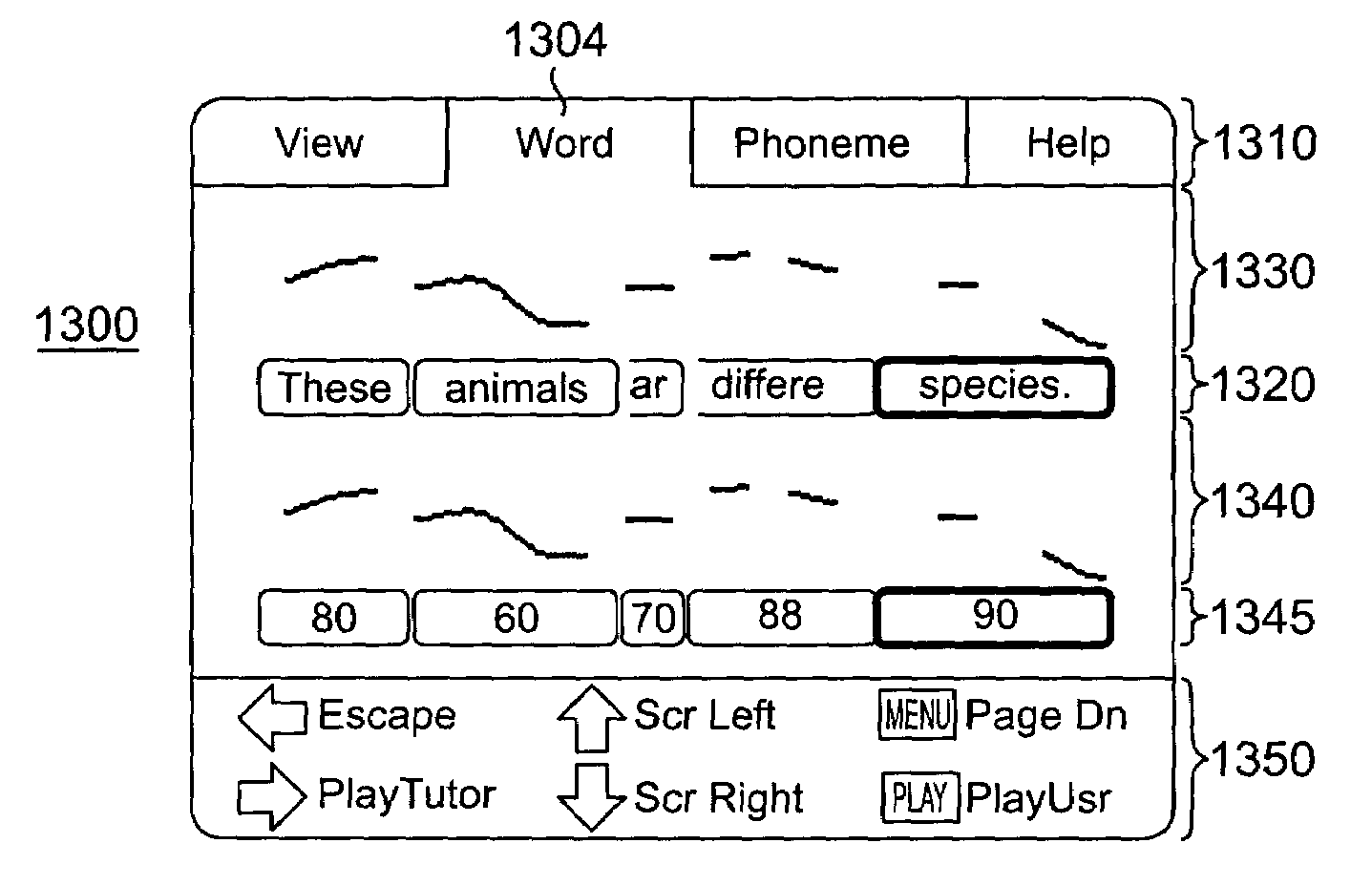
Method and apparatus for providing an interactive language tutor
InactiveUS7299188B2Meaningful feedbackFocusNatural language translationDigital computer detailsDigital feedbackRemedial action
A method and apparatus for generating a pronunciation score by receiving a user phrase intended to conform to a reference phrase and processing the user phrase in accordance with at least one of an articulation-scoring engine, a duration scoring engine and an intonation-scoring engine to derive thereby the pronunciation score. The scores provided by the various scoring engines are adapted to provide a visual and / or numerical feedback that provides information pertaining to correctness or incorrectness in one or more speech-features such as intonation, articulation, voicing, phoneme error and relative word duration. Such useful interactive feedback will allow a user to quickly identify the problem area and take remedial action in reciting “tutor” sentences or phrases.
Owner:LUCENT TECH INC +1
Distributed electronic document review in a blockchain system and computerized scoring based on textual and visual feedback
ActiveUS9870591B2Encryption apparatus with shift registers/memoriesSemantic analysisElectronic documentDocumentation procedure
A blockchain configured system and a method for facilitating an expertise driven review and scoring of electronic documents in a crowdsourced environment. The system includes a server computer, a memory circuit and a processing circuit. The processing circuit is coupled to the memory circuit and includes or is coupled to a credentialing engine. The system further includes an expert scoring module. The system further includes a document reviewing and scoring engine coupled to the processing circuit. The document review and scoring module associates an aggregate score to the electronic document based on aggregation of the review ratings by crowdsourced experts and aggregate scores of each of the crowdsourced experts based on the set of attributes including one or more of the credentialed expertise, reputation of the expert, and the officiality.
Owner:INTELLECTUAL FRONTIERS LLC
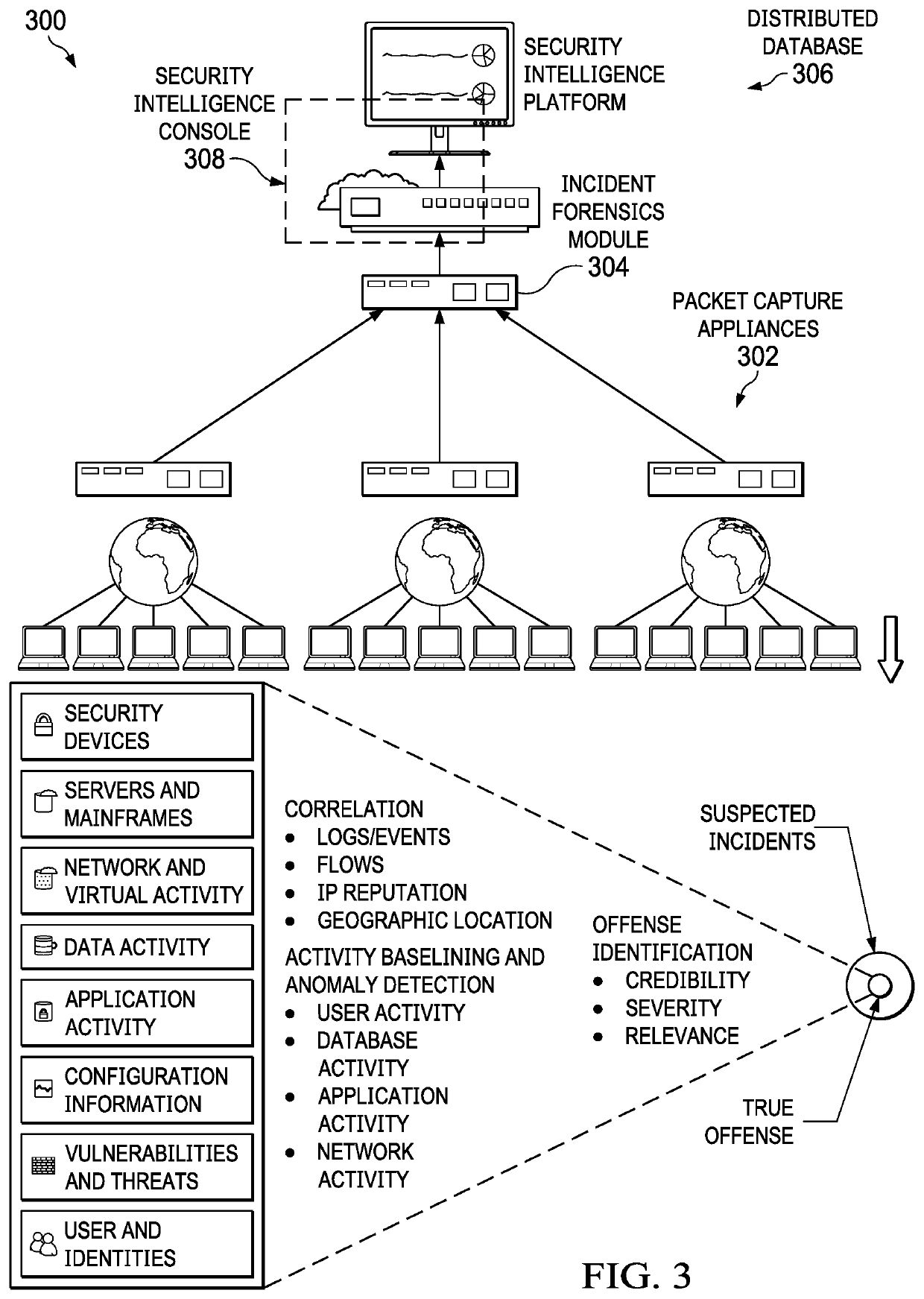
Affectedness scoring engine for cyber threat intelligence services
ActiveUS20200327223A1Digital data information retrievalPlatform integrity maintainanceManaged security serviceCyber threat intelligence
A network-accessible cyber-threat security analytics service is configured to characterize and respond to a description that includes threat indicators (e.g., IOCs), and an initial severity. Enterprises register with the service by providing identifying information, such as industry, geographies, and the like. For each threat indicator, a query is sent to each of a set of one or more security knowledge bases, and at least some of the queries are scoped by the enterprise industry / geo information specified. The knowledge bases may vary but typically include: a managed security service, a cyber threat intelligence service, and a federated search engine that searches across one or more enterprise-connected data sources. Responses to the queries are collected. A response provides an indication whether the threat indicator identified in the query has been sighted in the knowledge base and the frequency. The system then adjusts the initial severity to reflect the indications returned from querying the security knowledge bases.
Owner:IBM CORP
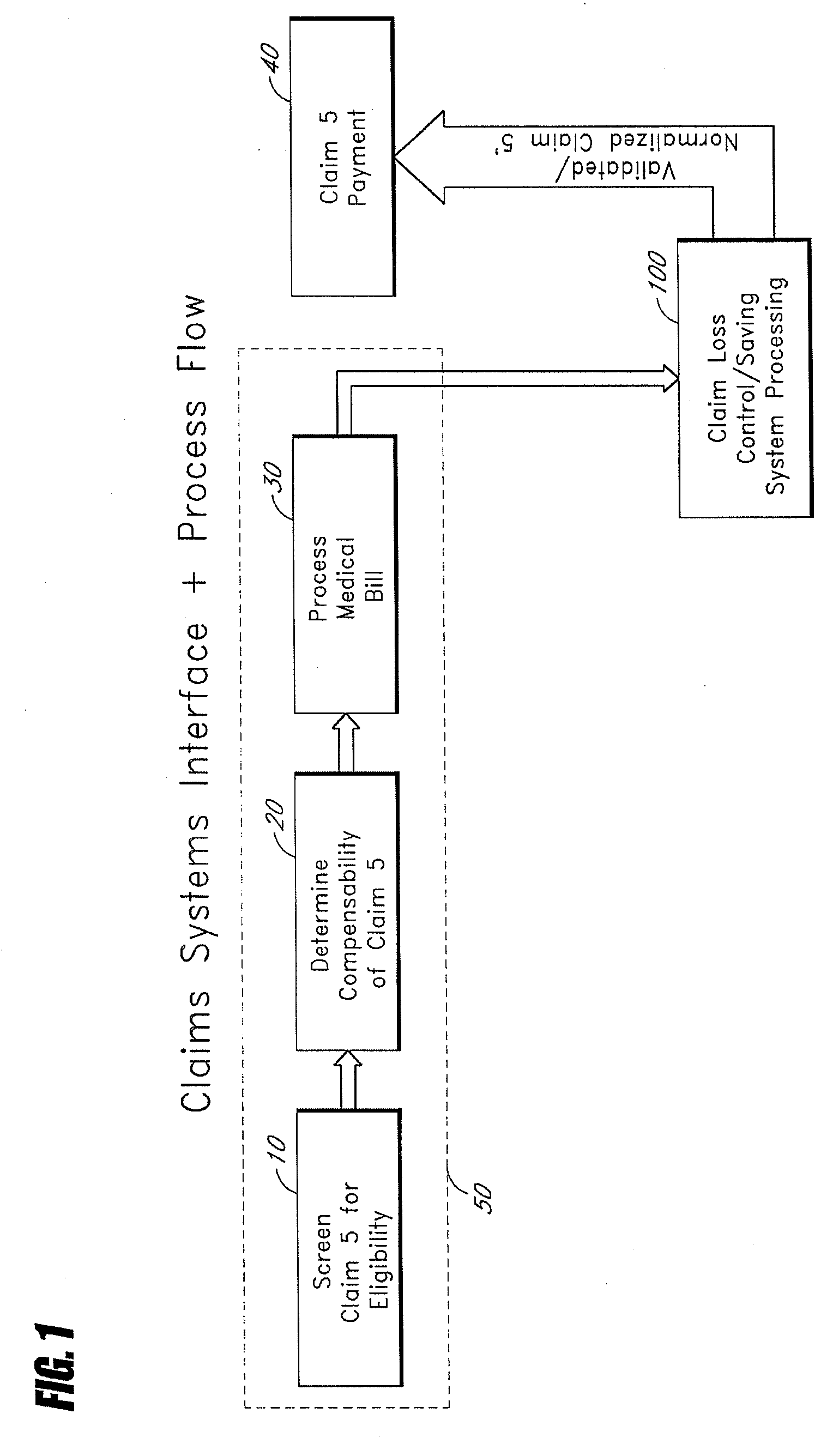
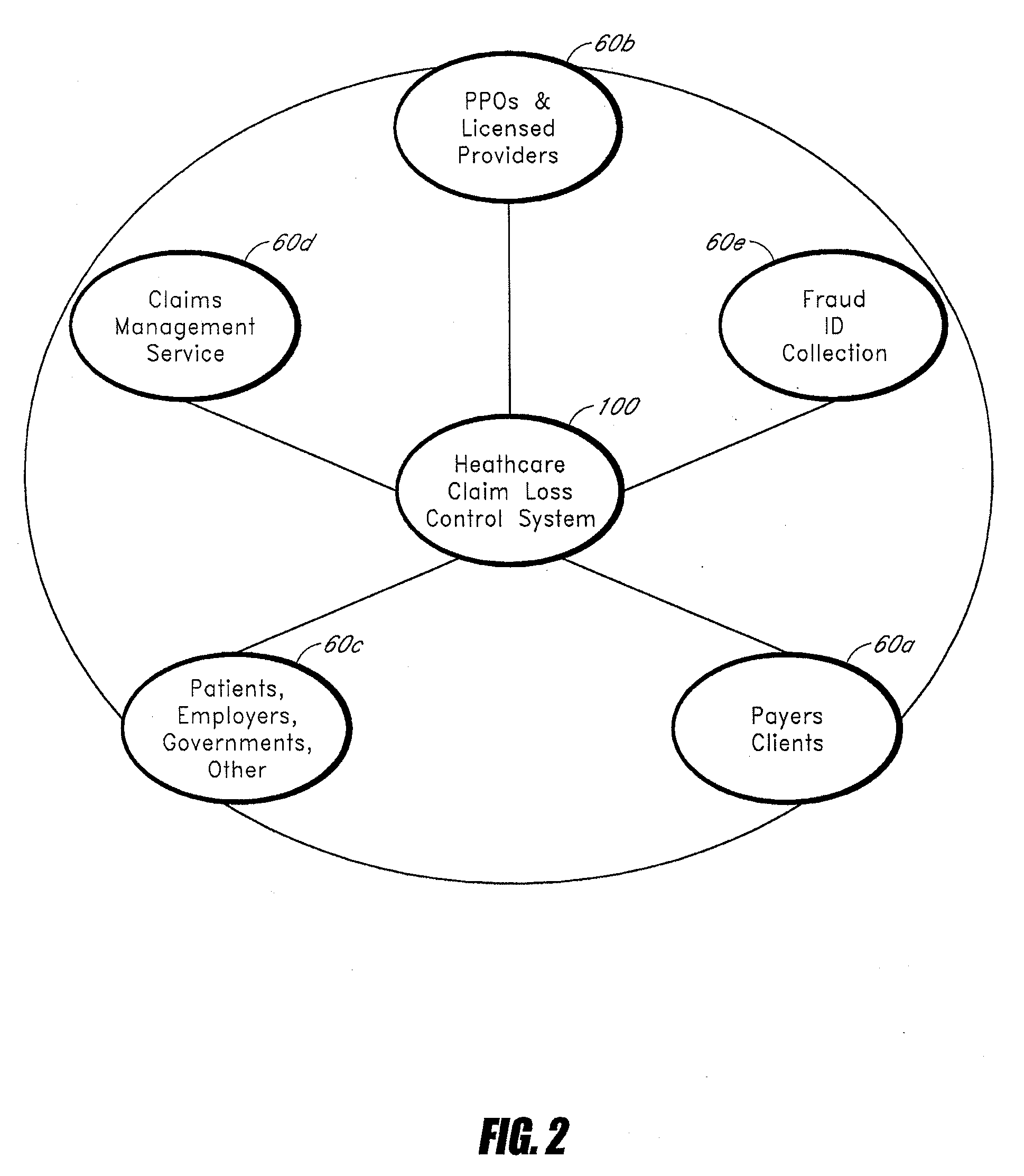
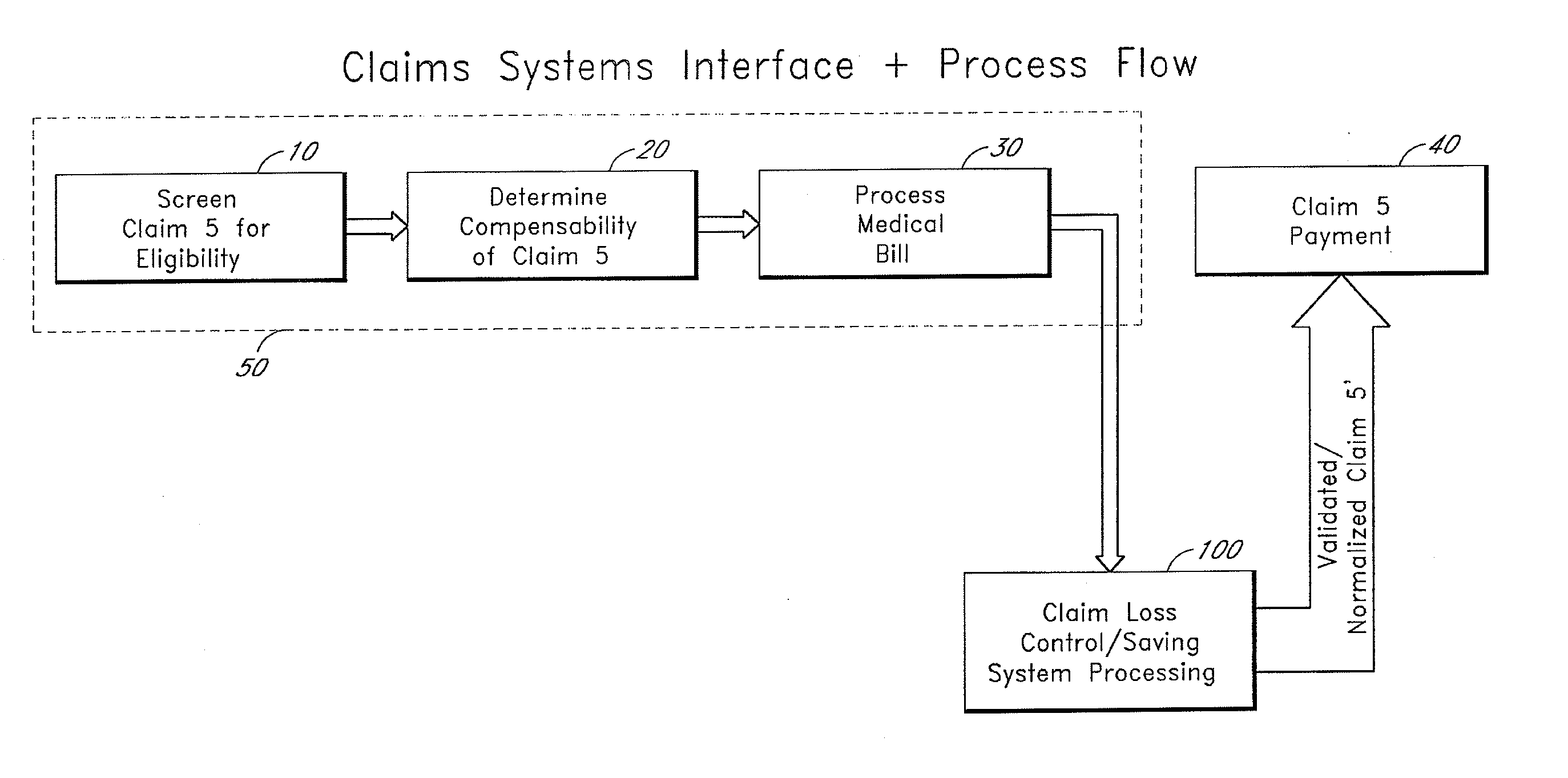
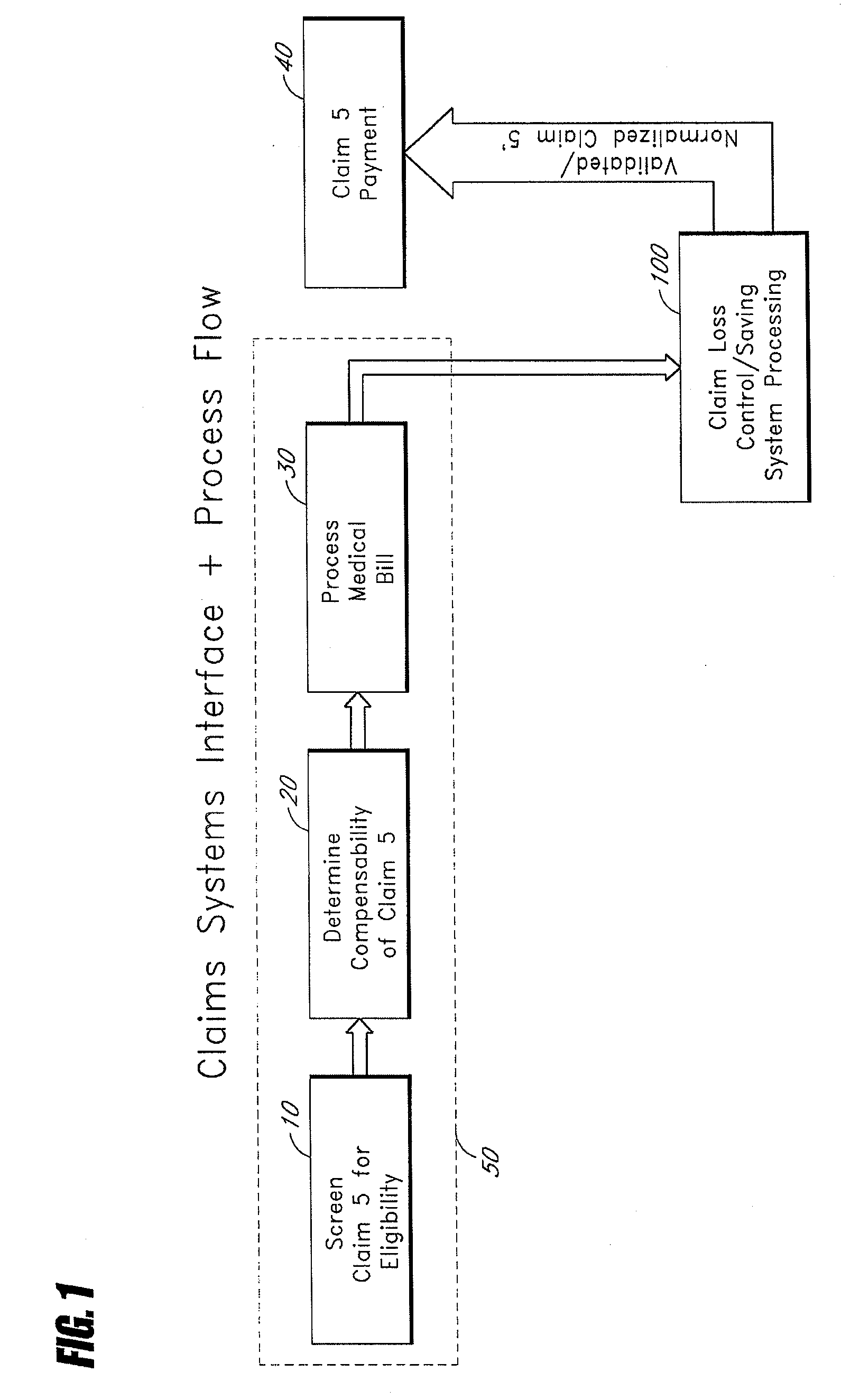
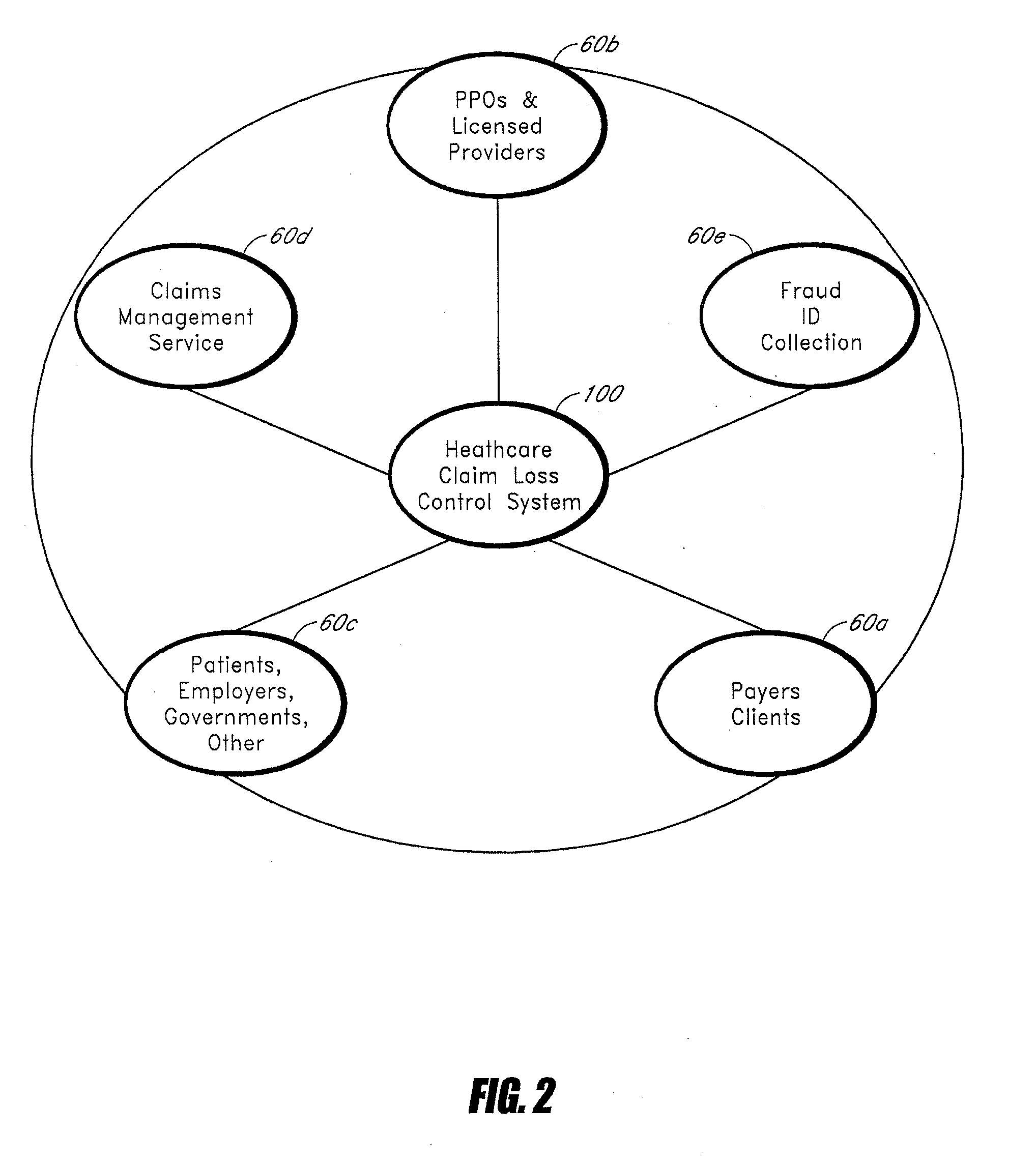
Systems and methods for determining indications of fraud in healthcare claims
InactiveUS20070011032A1Efficient executionSafeguard and improve integrityFinancePayment architecturePaymentControl system
A method of controlling healthcare claim payment losses including accessing information about a claim after a payer is prepared to pay, but prior to payment, applying at least one rule to the information, wherein the at least one rule is adapted to determine indications of fraud and if fraud is indicated, flagging the claim, else recommending payment, wherein flagging of the claim or recommending payment occurs prior to payment. Also, a healthcare claim loss control system including a database having data related to healthcare claims and a loss control engine in communication with the database wherein the loss control engine accesses data corresponding to a healthcare claim when the claim is ready for payment, but before payment of the claim occurs and wherein the claim scoring engine applies at least one rule adapted to identify fraud and flags the claim for any indicated fraud before payment of the claim.
Owner:TC3 HEALTH
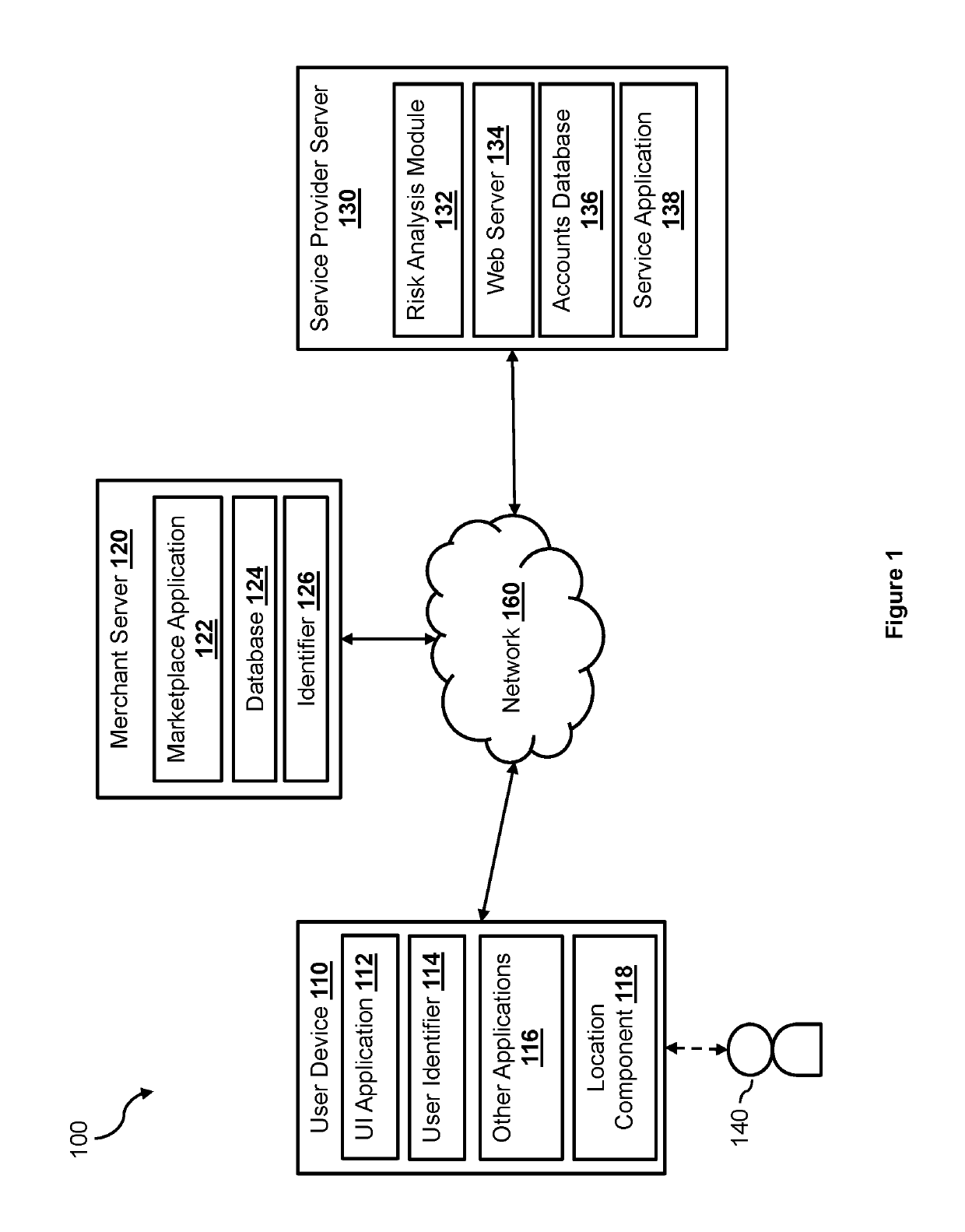
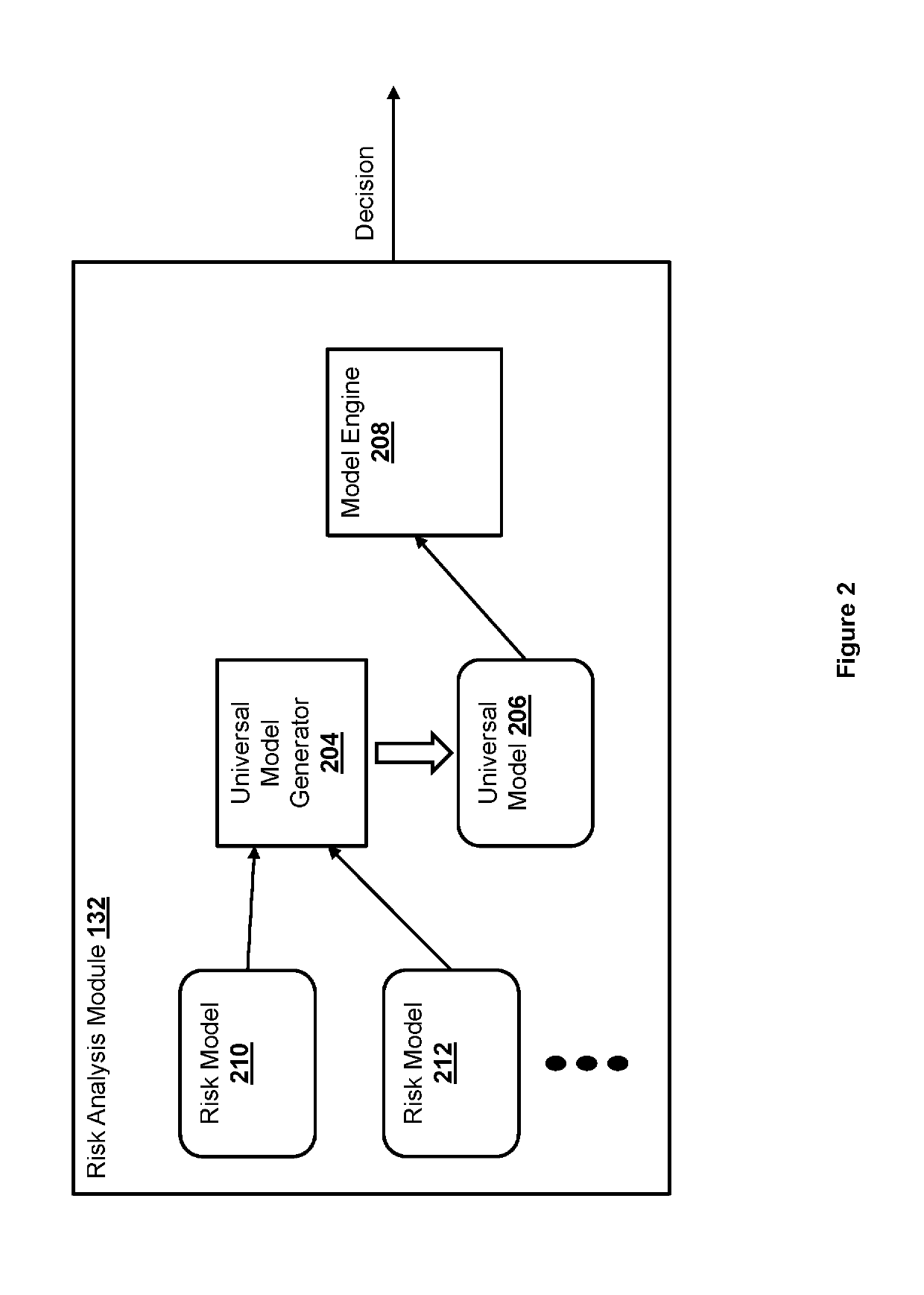
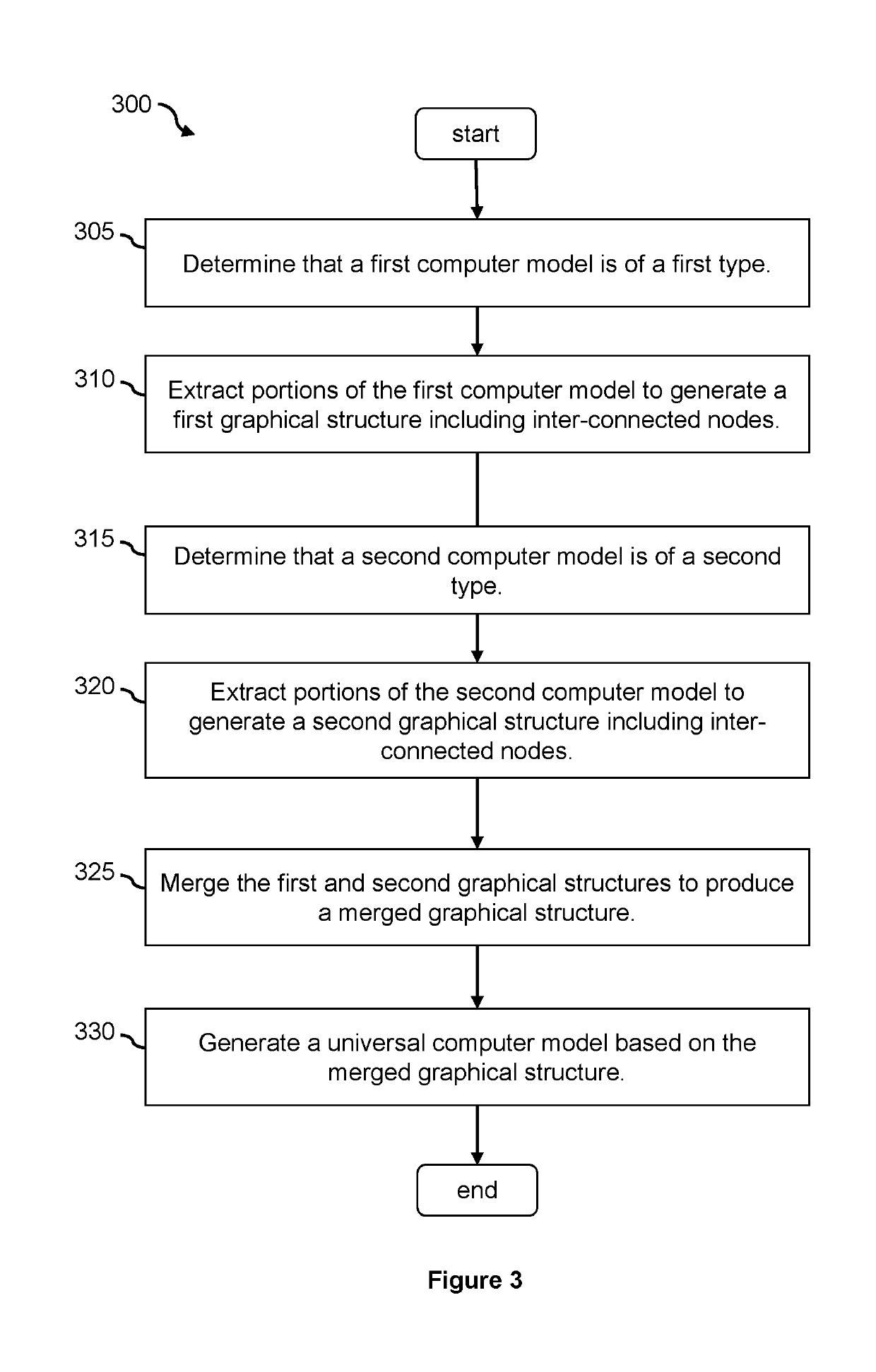
Universal model scoring engine
Methods and systems for generating a universal computer model for assessing a risk in an electronic transaction based on one or more risk assessment models are presented. The one or more risk assessment models may be incompatible with each other. Different portions of a risk assessment models may be extracted from the risk assessment models. A node structure is generated for each risk assessment model based on the portions extracted from a corresponding risk assessment model. The node structures generated based on the risk assessment models are merged to produce a merged node structure. The universal computer model is generated based on the merged node structure.
Owner:PAYPAL INC
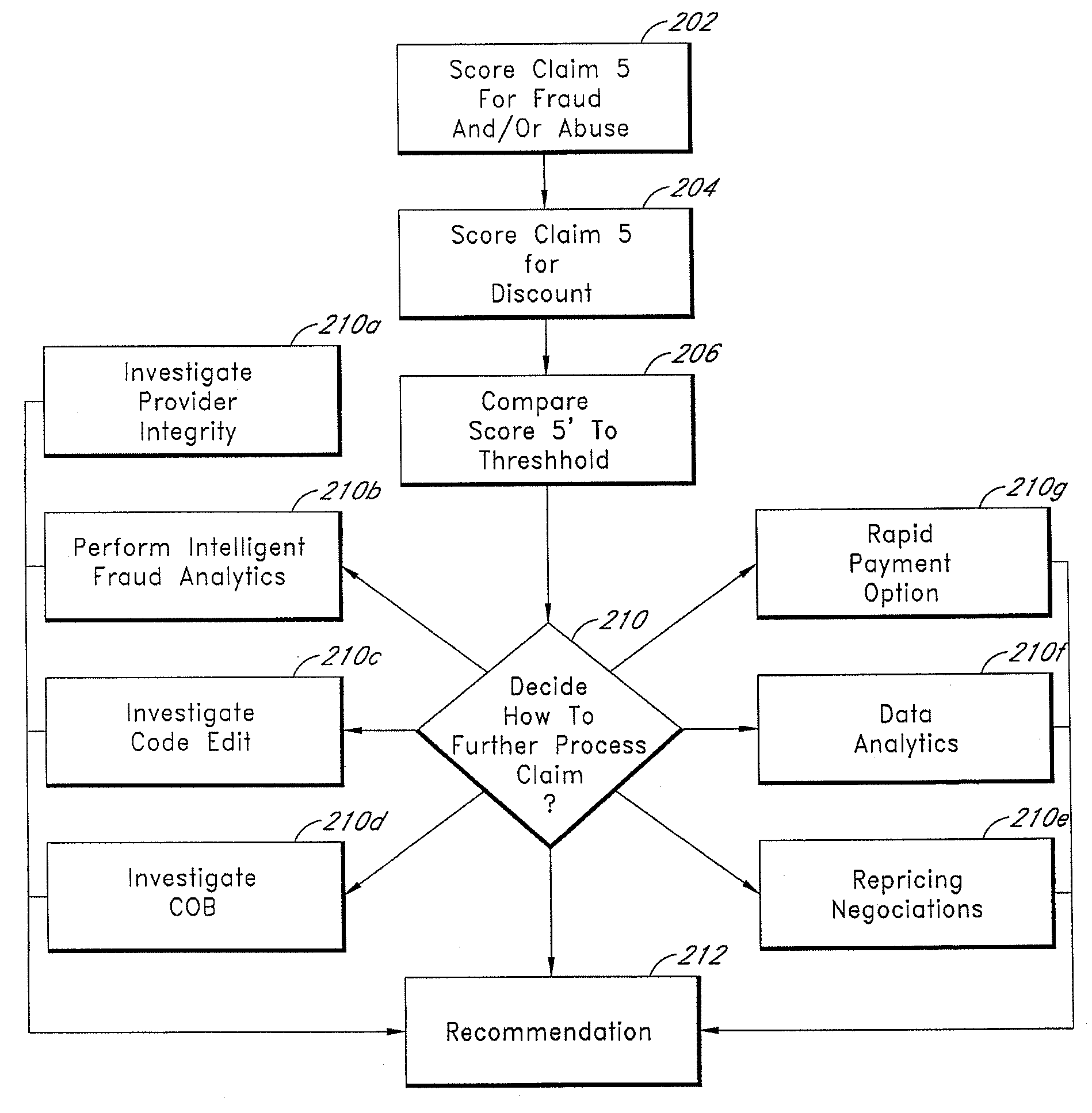
Systems and methods for scoring loss control opportunities in healthcare claims
InactiveUS20070011030A1Efficient executionSafeguard and improve integrityFinancePayment architecturePaymentControl system
A method of controlling healthcare claim payment losses including accessing claim information after a payer is prepared to pay the claim, but prior to payment, evaluating the information and developing a score indicative of loss control opportunities and if the score exceeds a threshold, flagging the claim to the payer for loss control opportunities else, recommending payment, wherein flagging of the claim or recommending payment of the claim occurs prior to payment. A healthcare claim loss control system including a database having data related to claims and a scoring engine in communication with the database wherein the scoring engine accesses data corresponding to a claim when the claim is ready for payment, but before payment occurs and wherein the scoring engine evaluates the claim for loss control opportunities and generates at least one score for the claim corresponding to the evaluated loss control opportunities before payment.
Owner:TC3 HEALTH
System and method for generating sources of prioritized content
ActiveUS8484205B1Digital data processing detailsSpecial data processing applicationsSystem identificationScoring Engine
The system provides a technique for finding relevant content and content sources based on the aggregation and analysis of individual indications of relevance. The system identifies and provides selections of relevant content. It may comprise a selection acquisition subsystem, a selection network repository subsystem, a scoring engine, and a recommendation engine, and is used to generate sources of content comprising sets of prioritized links directed to a topic or community of interest.
Owner:ESW HLDG INC
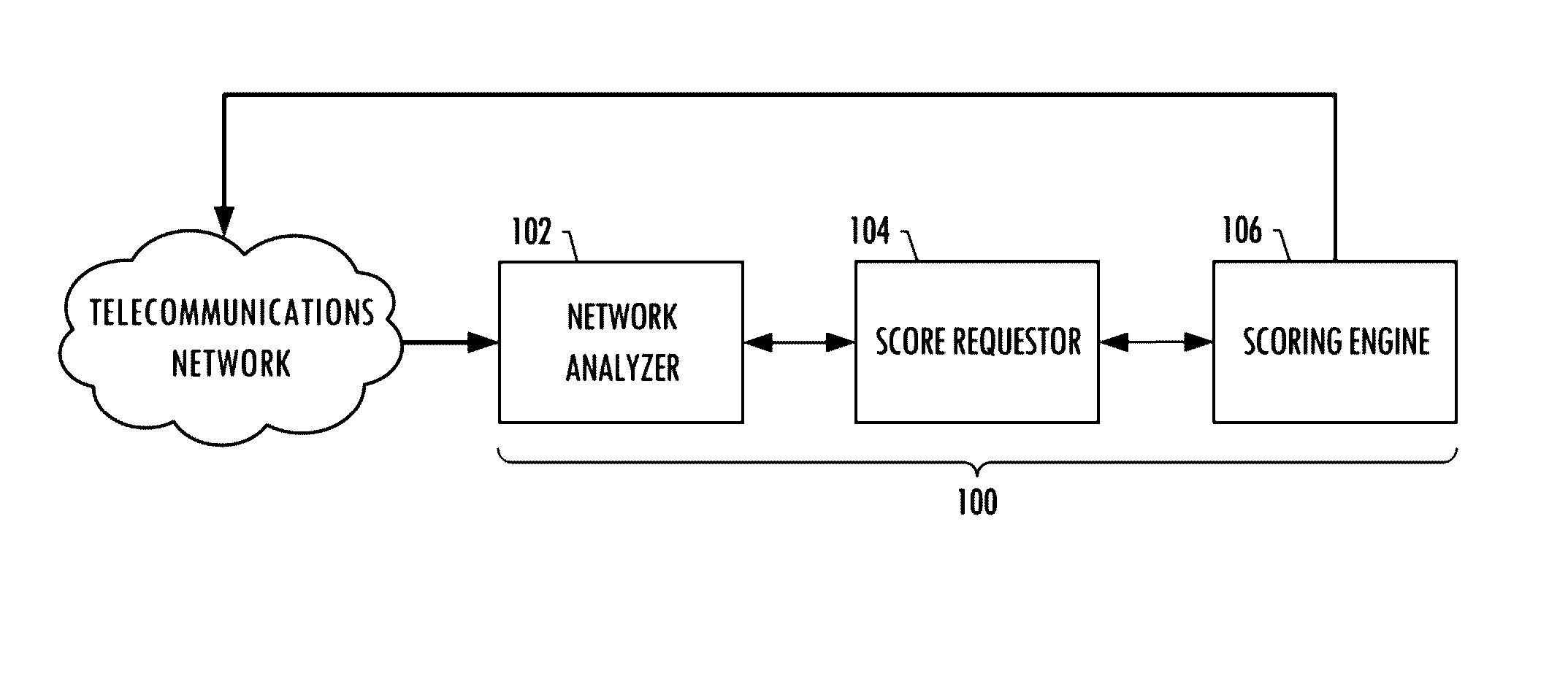
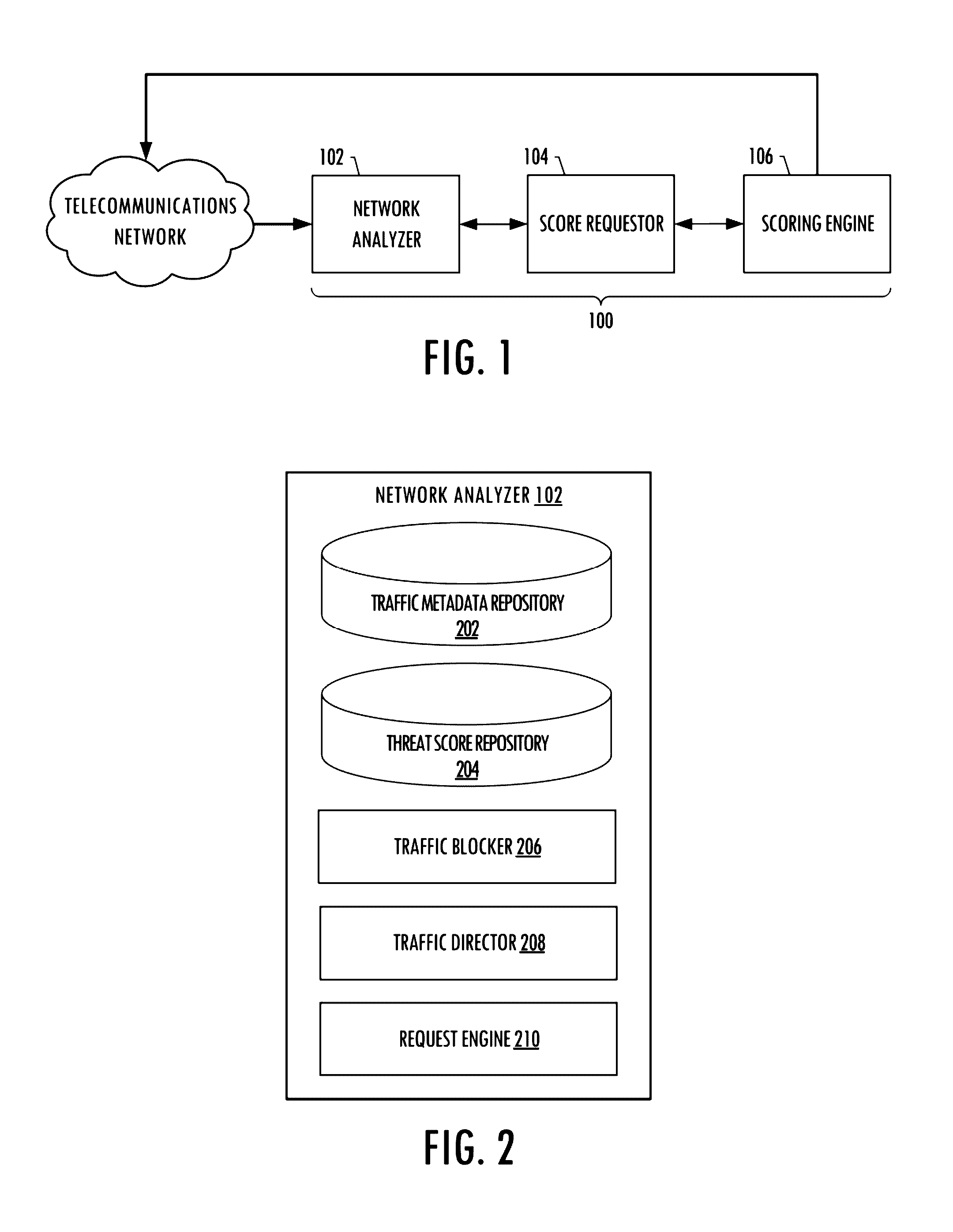
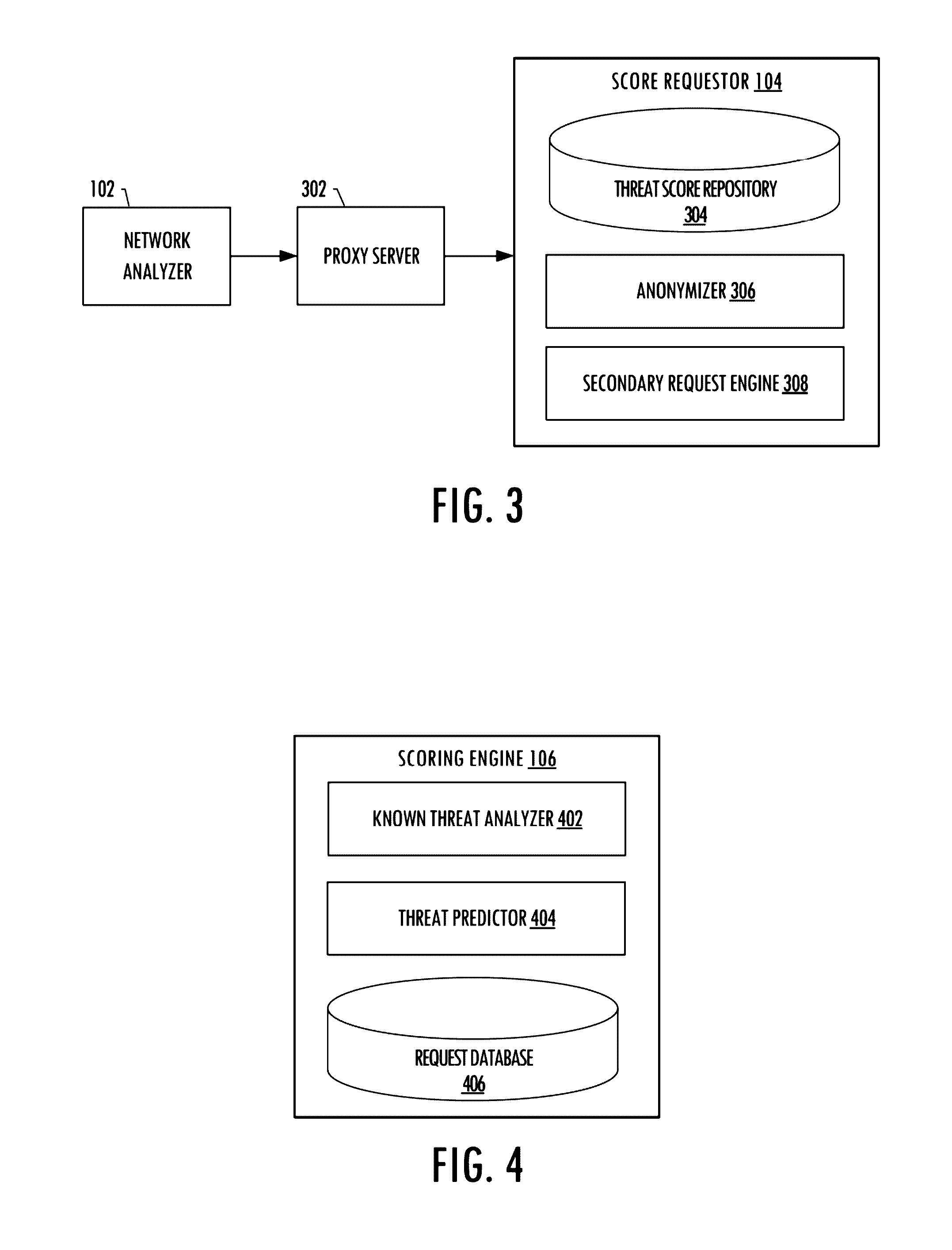
System for anonymously detecting and blocking threats within a telecommunications network
A system is provided for anonymously detecting and blocking threats within a telecommunications network. A network analyzer of the system may intercept traffic, or receive log files, related to traffic that passes over the network, collect metadata that includes values of data attributes associated with the traffic, interpret the metadata and therefrom generate and transmit a request for an associated threat score for the value of a data attribute, and receive the associated threat score and based thereon initiate a block or redirection of the traffic. A score requestor of the system may receive and serve the request by either returning the score from local storage or otherwise, generating and transmitting a secondary request to a scoring engine configured to calculate the associated threat score and the associated threat score to the score requestor to return to the network analyzer.
Owner:CELERIUM INC
Adaptive targeting for finding look-alike users
A method for adaptive display of internet advertisements to look-alike users using a desired user profile dataset as a seed to machine learning modules. Upon availability of a desired user profile, that user profile is mapped other look-alike users (from a larger database of users). The method proceeds to normalize the desired user profile object, proceeds to normalize known user profile objects, then seeding a machine-learning training model with the normalized desired user profile object. A scoring engine uses the normalized user profiles for matching based on extracted features (i.e. extracted from the normalized user profile objects). Once look-alike users have been identified, the internet display system may serve advertisements to the look-alike users, and analyze look-alike users' behaviors for storing the predicted similar user profile objects into the desired user profile object dataset, thus adapting to changing user behavior.
Owner:R2 SOLUTIONS
Methods and systems for providing a decision making platform
A method for enriching the data associated with financial transaction card transactions using a computer system is described. The method includes receiving financial transaction data from a plurality of input channels, each input channel associated with a financial transaction data format, converting the received financial transaction data into a common data format, enriching the converted financial transaction data by scoring the converted financial transaction data across a plurality of scoring engines, converting the plurality of scores relating to the financial transaction data from the scoring engines into output data, and transmitting the output data using an output manager, the output manager operable to provide the data into a format appropriate for each intended recipient.
Owner:MASTERCARD INT INC
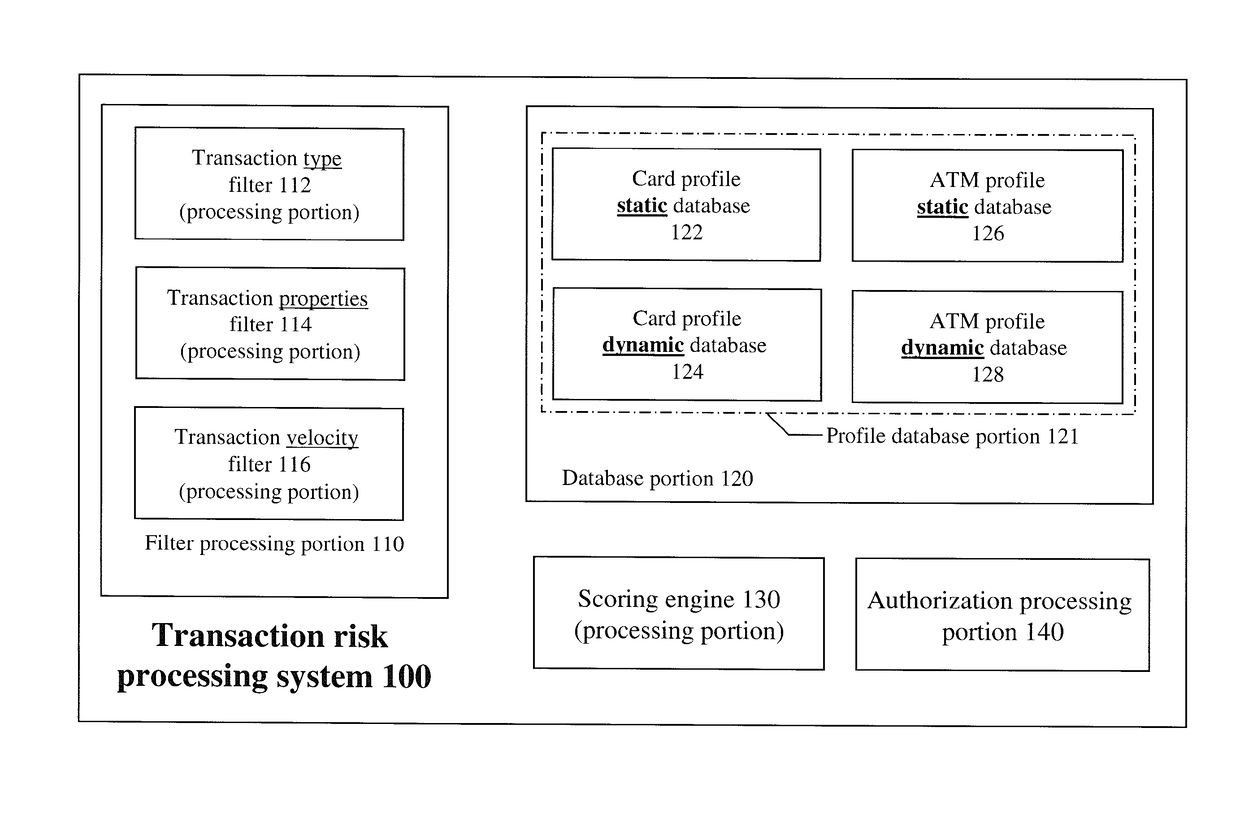
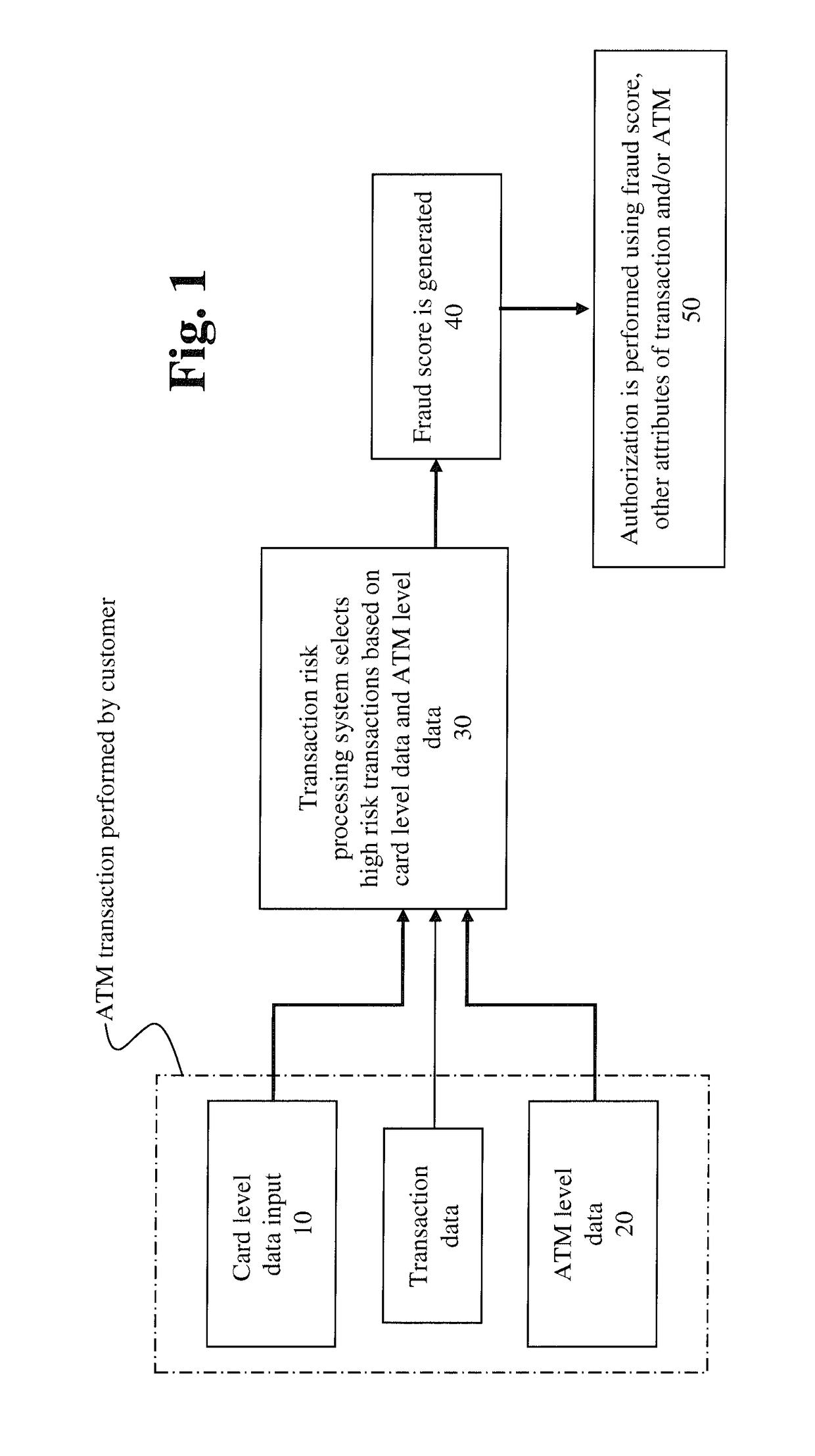
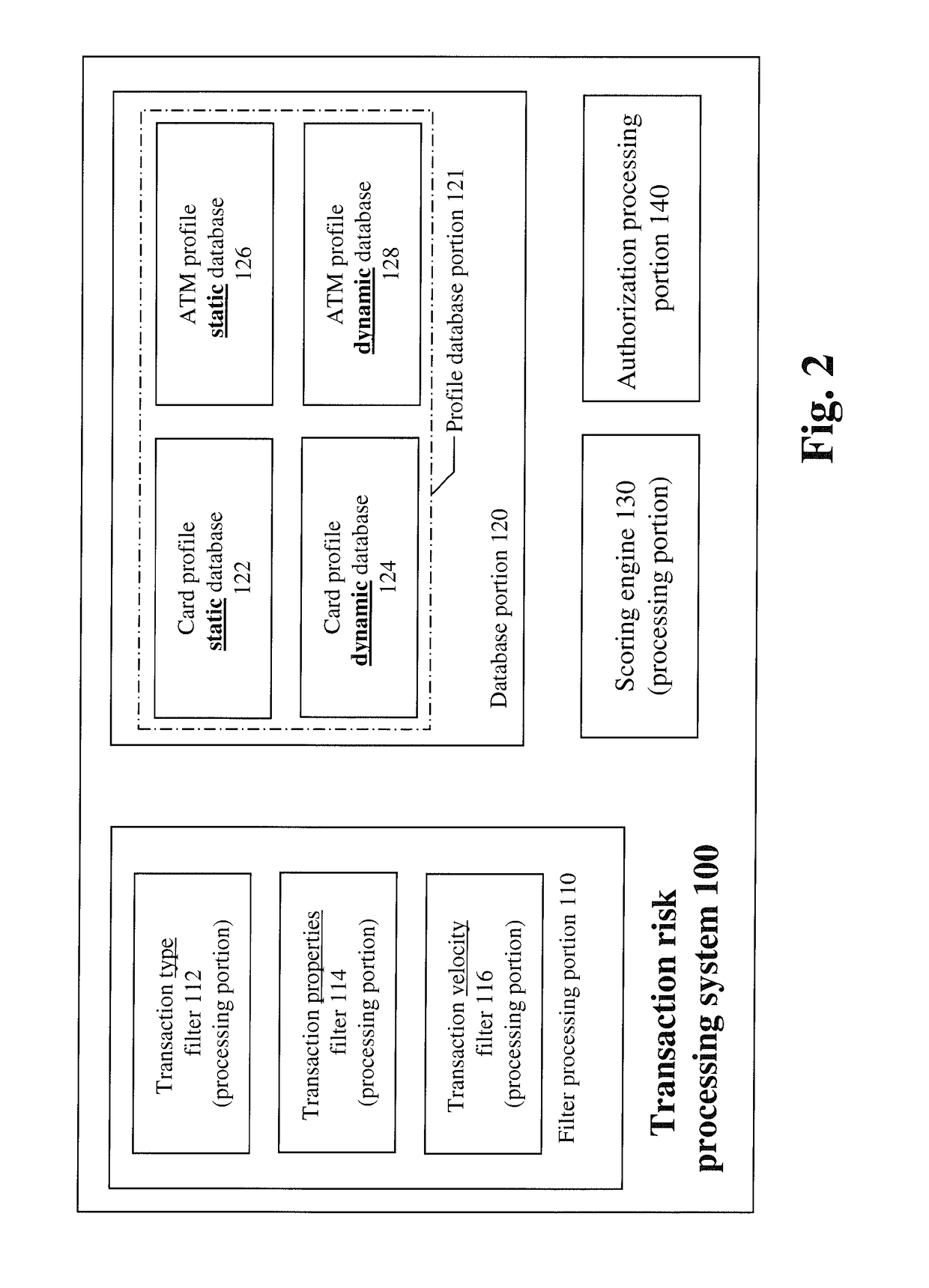
Systems and methods for fraud detection
The invention provides systems and methods for identifying fraud in an ATM transaction and in other financial processing environments. The system, tangibly embodied in the form of a computer processer includes a profile database, a filter processing portion, a scoring engine, and an authorization processing portion. The profile database contains card profiles and ATM profiles. The filter processing portion inputs transaction data generated from a requested ATM transaction. The filter processing portion includes a plurality of filters that filter high risk transactions, and outputs customer related data and ATM related data to the profile database. The scoring engine assesses risk of the high risk transaction based on attributes of the transaction, data in at least one card profile, and data in at least one ATM profile. The authorization processing portion determines whether the requested transaction should be approved or declined based on the fraud score and transaction data.
Owner:JPMORGAN CHASE BANK NA
System and methods for sandboxed malware analysis and automated patch development, deployment and validation
A system and methods for sandboxed malware analysis and automated patch development, deployment and validation, comprising a business operating system, vulnerability scoring engine, binary translation engine, sandbox simulation engine, at least one network endpoint, at least one database, a network, and a combination of machine learning and vulnerability probing techniques, to analyze software, locate any vulnerabilities or malicious behavior, and attempt to patch and prevent undesired behavior from occurring, autonomously.
Owner:QOMPLX INC
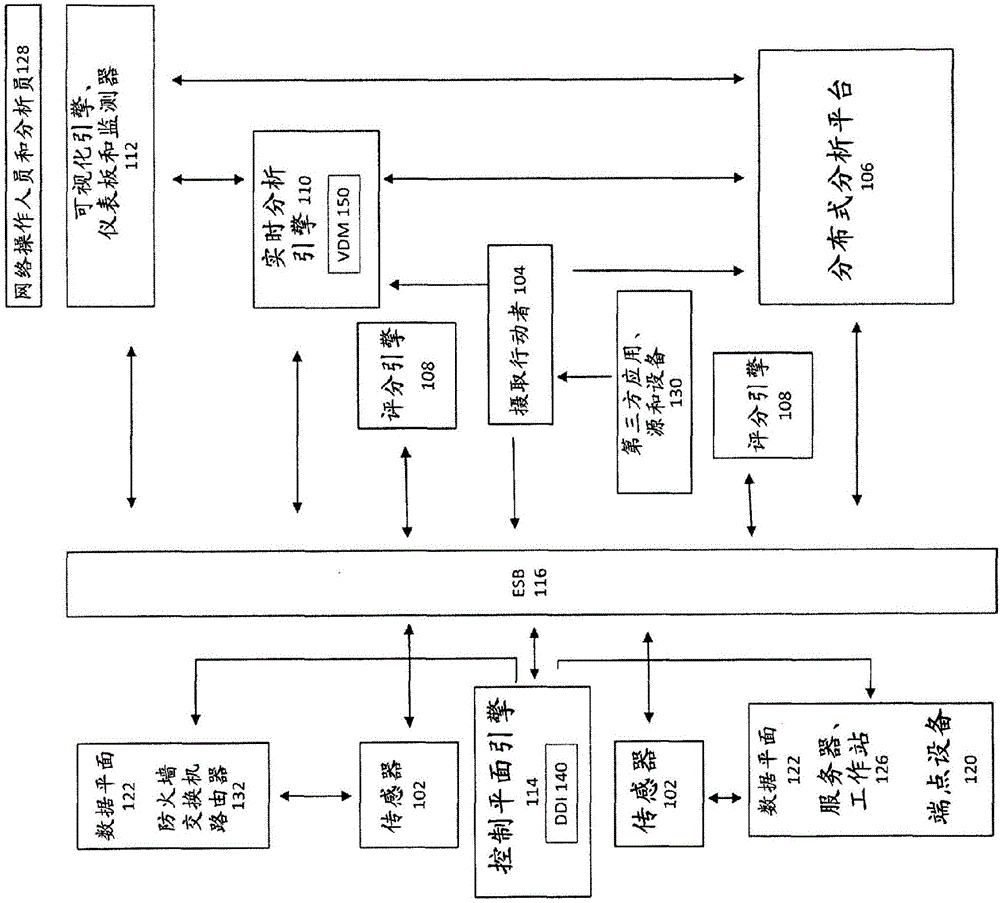
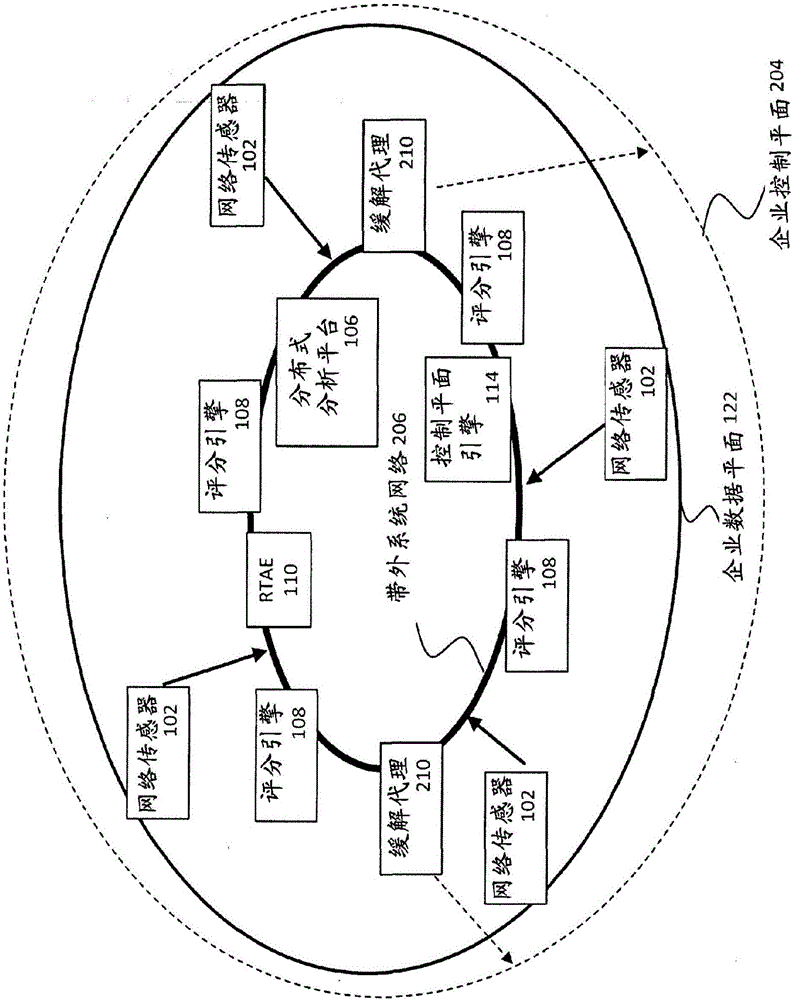
Cybersecurity system
A cybersecurity system for processing events to produce scores, alerts, and mitigation actions is provided. The system includes sensors for receiving and processing data to form events, distributed analytic platform for processing events to form analytic workflows, and scoring engines for processing events using analytic workflows to produce scoring engine messages. The system also includes real time analytic engine for processing scoring engine messages and distributed analytic platform messages by using the analytic workflows and analytic workflow and event processing rules to form and transmit a threat intelligence message. Threat intelligence messages include broadcast messages, mitigation messages, and model update messages. The system also includes logical segments which associate an analytic model, a set of analytic models, or an analytic workflow; one or more sources of inputs about activity within the logical segment, and a set of actions for mitigating an impact of the anomalous activity occurring within the logical segment.
Owner:IRONNET CYBERSECURITY INC
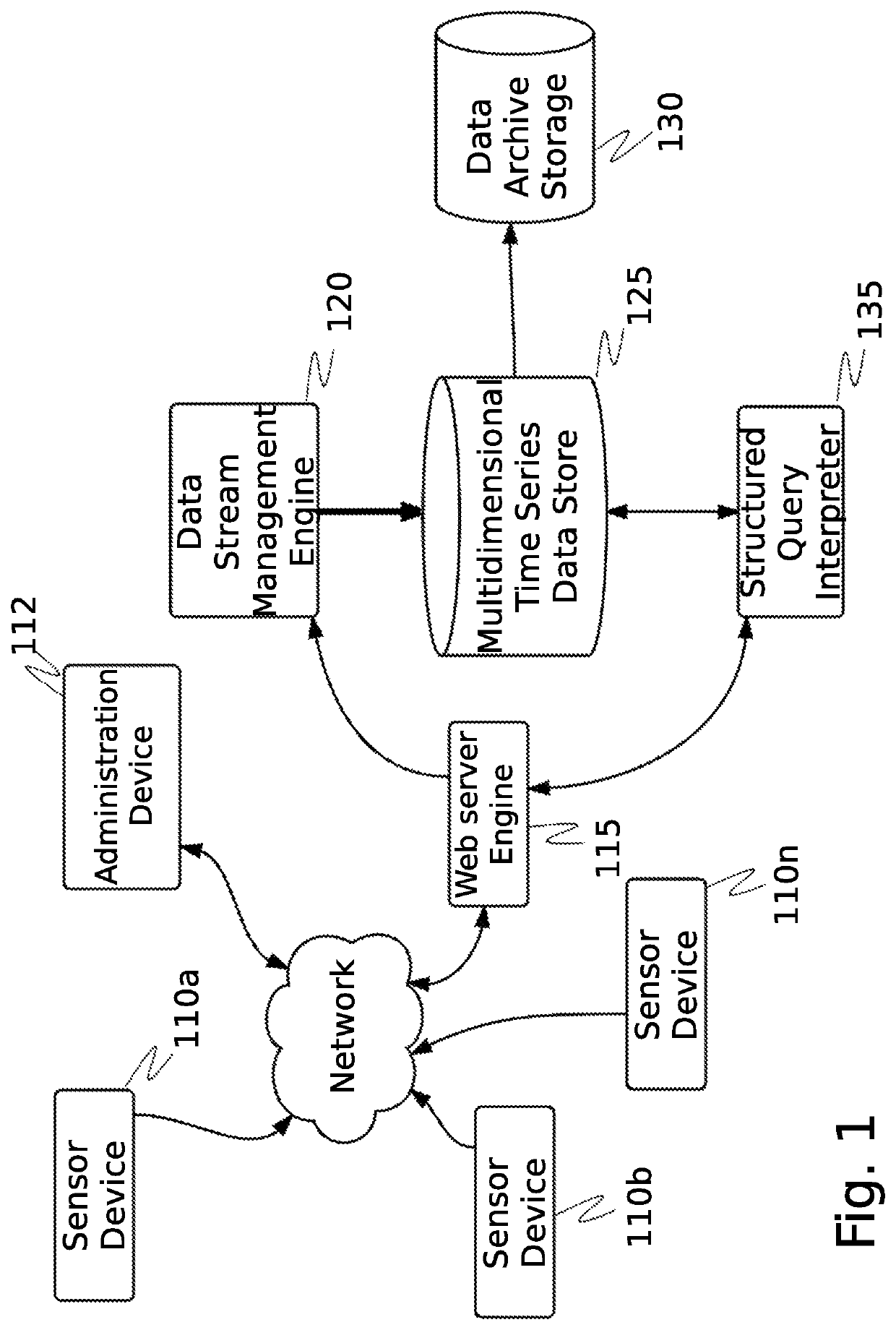
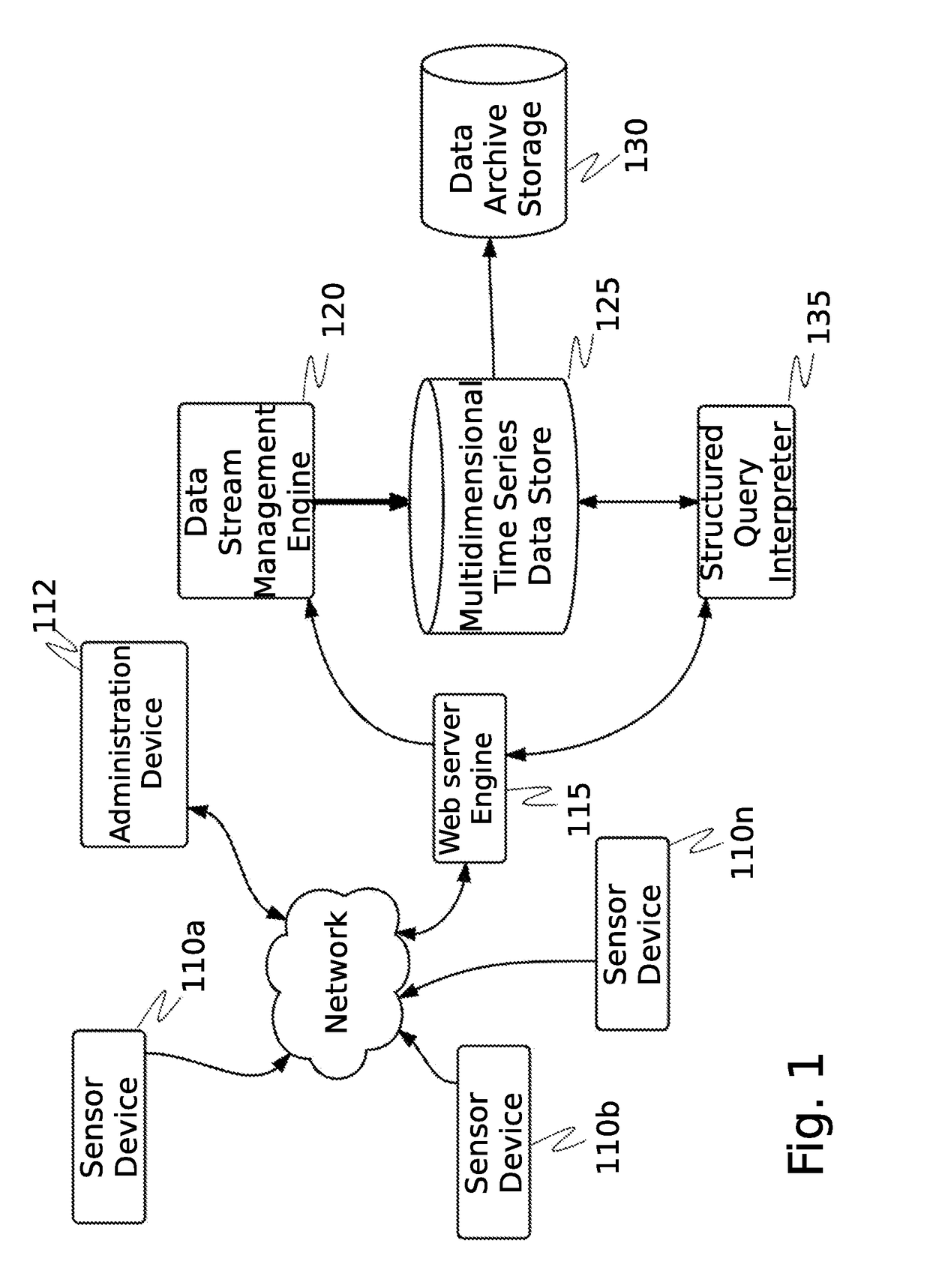
System and method for cybersecurity analysis and score generation for insurance purposes
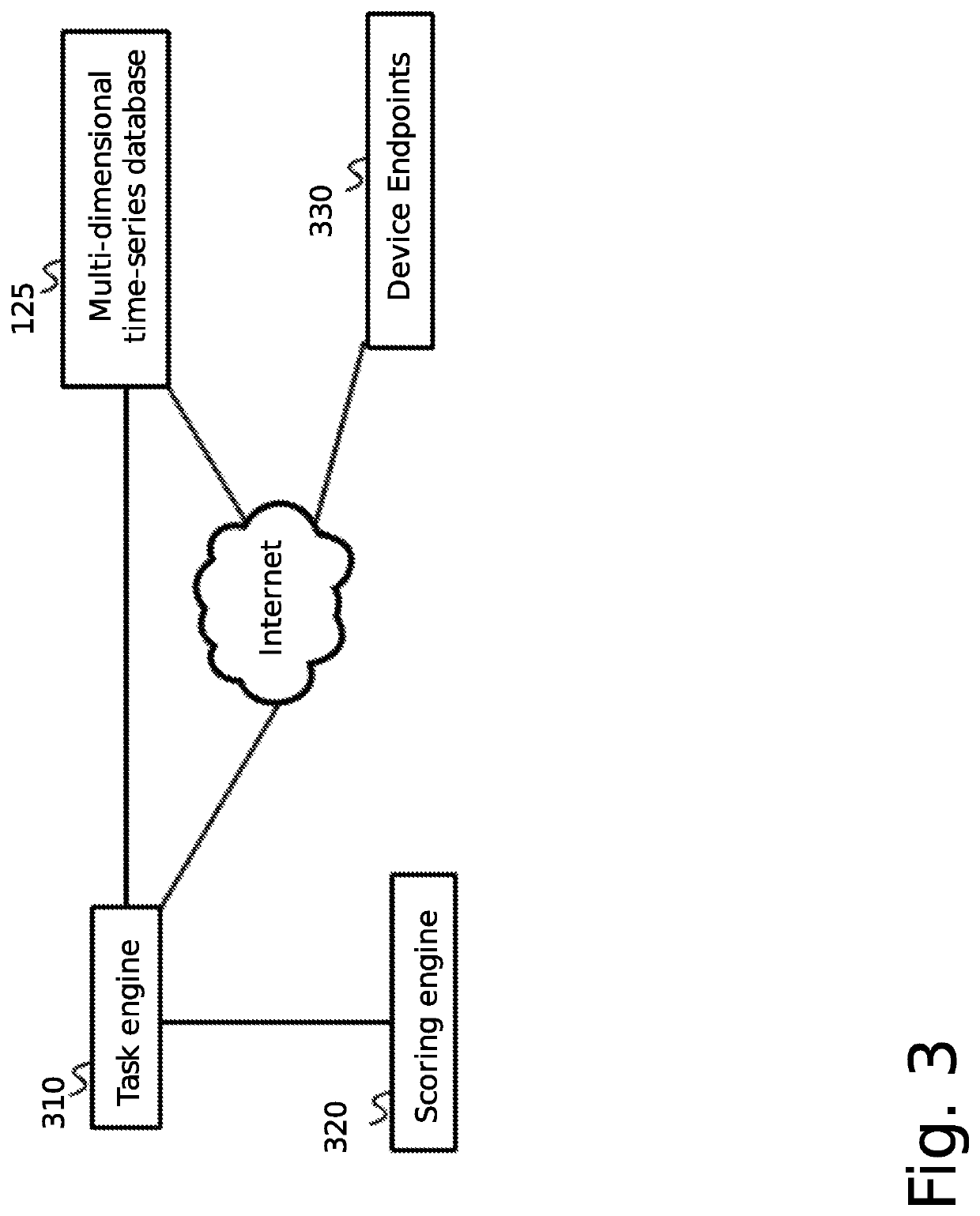
A system for comprehensive cybersecurity analysis and rating based on heterogeneous data and reconnaissance is provided, comprising a multidimensional time-series data server configured to create a dataset with at least time-series data gathered from passive network reconnaissance of a client; and a cybersecurity scoring engine configured to retrieve the dataset from the multidimensional time-series data server, process the dataset using at least computational graph analysis, and generate an aggregated cybersecurity score based at least on results of processing the dataset.
Owner:QOMPLX INC
Secondary Marketplace For Leads
Effective acquisition of high-quality sales leads is provided. Businesses provide scoring criteria, representing the relative importance of a potential customer's attributes, such as sales revenue, number of employees, industry, geographic location, etc. A scoring engine determines a score for the combination of a potential customer and one or more businesses by applying the criteria in the business' quality profile to the attribute values provided by the potential customer. If the score exceeds a threshold, information about the potential customer is provided to the business at a customized price. The business can then purchase contact information for the potential customer. If the business does not pursue the potential customer, the lead may be offered to additional businesses in a secondary marketplace. A business that agrees to have rejected leads contributed to the secondary marketplace can be issued a credit against past or future leads purchases.
Owner:DEMANDBASE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com