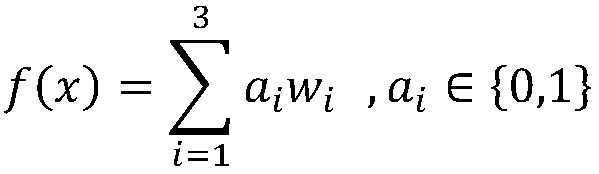Network threat intelligence credibility identification method
An identification method and reliability technology, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve the problems of the increase in the amount of intelligence, the impact of threat intelligence utilization efficiency, and the inability to measure threat intelligence indicators.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0012] In order to enable those skilled in the art to better understand the technical solutions in the embodiments of the present invention, and to make the purpose, features and advantages of the present invention more obvious and comprehensible, the technical core of the present invention will be further described in detail below in conjunction with examples.
[0013] In the present invention, a method for reputation measurement of network threat indicators is proposed.
[0014] The steps of this method include:
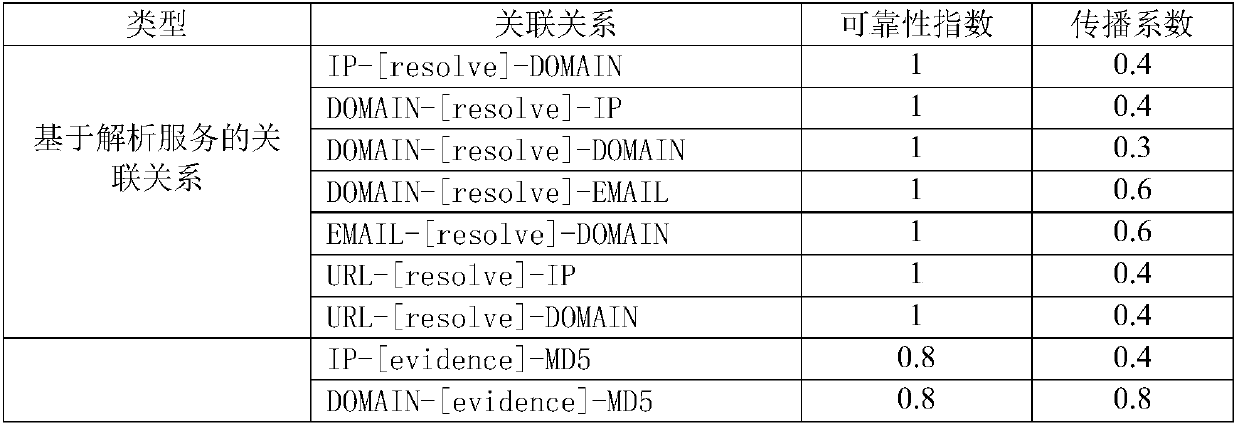
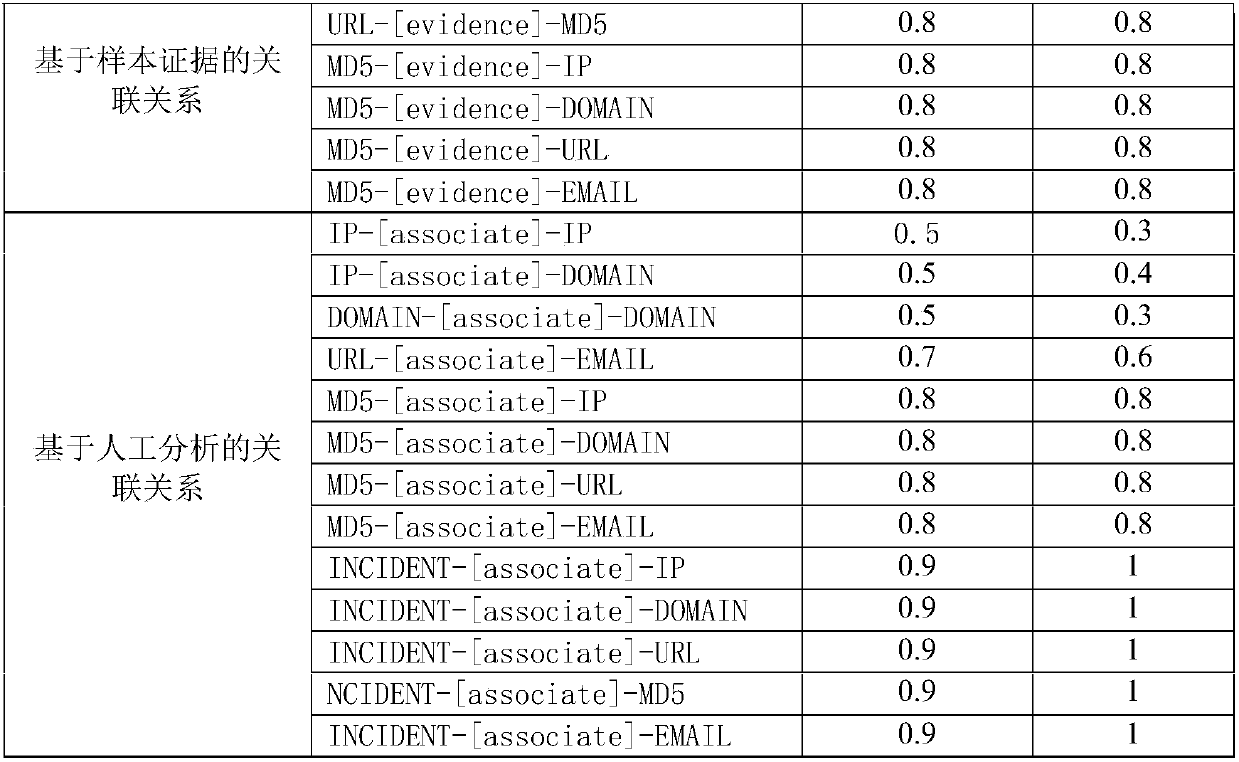
[0015] Step 1. Construct the correlation graph model of network threat intelligence. This module builds a network graph of threat intelligence relationships. The network graph of threat intelligence correlation is composed of nodes and edges, each node represents a network threat indicator, and the node types include IP, URL, Domain, Email, Incident, and MD5. The edge types are designed into three categories. Including associations based on analytical services, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com