Network threat detection method and device based on dictionary tree, equipment and storage medium
A threat detection and dictionary technology, applied in the field of network security, can solve the problem of missing the best time to prevent attacks, and achieve the effect of preventing attacks in time and improving the efficiency of network threat detection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
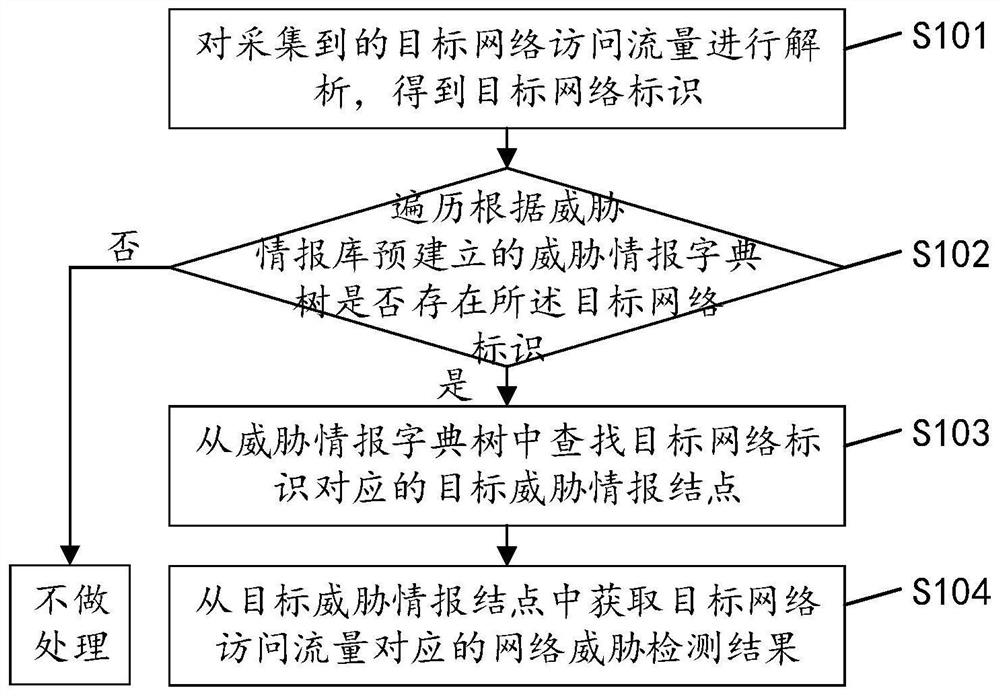
[0045] see figure 1 , figure 1 It is an implementation flowchart of a network threat detection method based on a dictionary tree in an embodiment of the present invention, and the method may include the following steps:
[0046] S101: Analyze the collected target network access traffic to obtain a target network identifier.
[0047] When the target network access traffic is collected, the collected target network access traffic is analyzed to obtain the target network identifier. The target network identifier may include domain name information, IP address information, etc. of the network to be visited.
[0048] S102: Traverse the threat intelligence dictionary tree pre-established according to the threat intelligence database to see if there is a target network identifier, if yes, perform step S103, if not, do not process.
[0049] A threat intelligence library is pre-established, which stores pre-collected threat intelligence information, and each threat intelligence info...
Embodiment 2
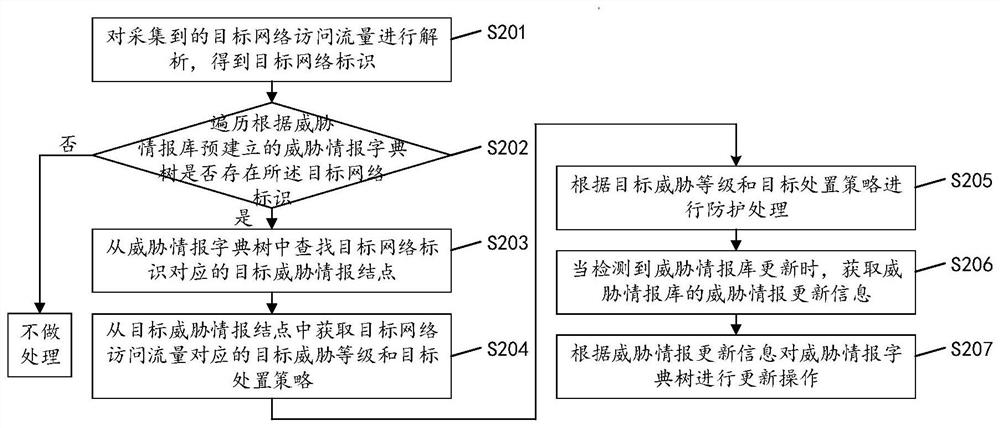
[0057] see figure 2 , figure 2 It is another implementation flowchart of a network threat detection method based on a dictionary tree in an embodiment of the present invention, and the method includes the following steps:
[0058] S201: Analyze the collected target network access traffic to obtain a target network identifier.
[0059] S202: Traverse the threat intelligence dictionary tree pre-established according to the threat intelligence database to see if there is a target network identifier, if yes, perform step S203, if not, do not process.
[0060] S203: Find a target threat intelligence node corresponding to the target network identifier from the threat intelligence dictionary tree.
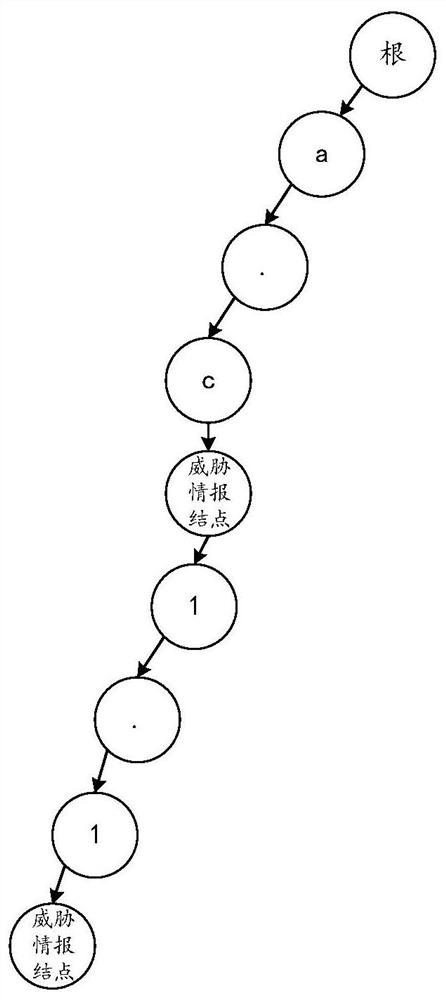
[0061] see image 3 and Figure 4 , image 3 It is a structural diagram of a threat intelligence dictionary tree in an embodiment of the present invention, Figure 4 It is a structure diagram of another threat intelligence dictionary tree in the embodiment of the present invention...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com