Mail attachment threat detection method and system
A threat detection and attachment technology, applied in the field of email attachment threat detection, can solve the problems of increasing traffic processing delay, unable to continue processing subsequent traffic quickly, and reducing threat detection efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
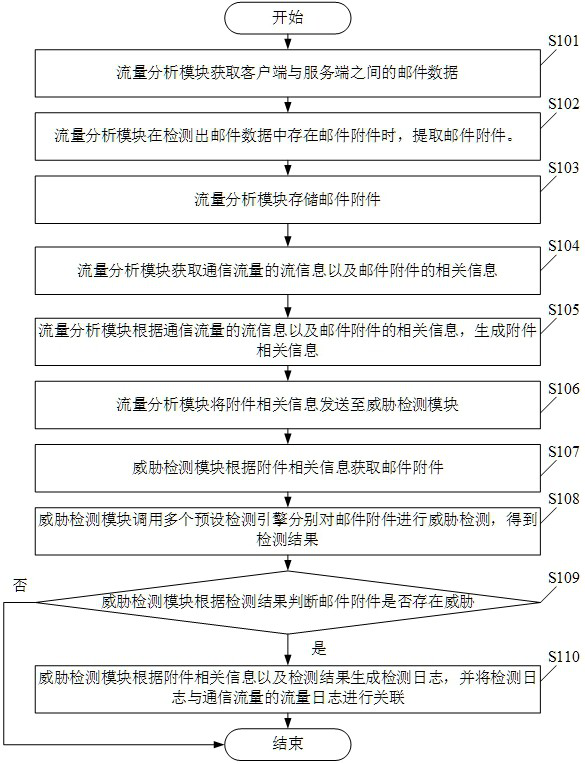
[0044] Please see figure 1 , figure 1 A schematic flow chart of a method for detecting threats of email attachments is provided for the embodiment of the present application. Wherein, the email attachment threat detection method is applied to an email attachment threat detection system, and the email attachment threat detection system includes a traffic analysis module and a threat detection module, including:
[0045] S101. The traffic analysis module acquires email data between the client and the server.
[0046] As an optional implementation, the traffic analysis module obtains email data between the client and the server, including:
[0047] The traffic analysis module obtains the communication traffic between the client and the server;
[0048] The traffic analysis module identifies the mail protocol of the communication traffic to obtain the mail data.
[0049] In the above implementation manner, the communication traffic between the client and the server may specifi...
Embodiment 2
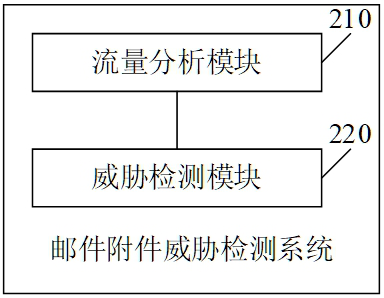
[0086] Please see figure 2 , figure 2 It is a schematic structural diagram of an email attachment threat detection system provided by the embodiment of the present application. Such as figure 2 As shown, the email attachment threat detection system traffic analysis module 210 and threat detection module 220 .
[0087] The traffic analysis module is used to obtain the email data between the client and the server; and analyze the email data to obtain attachment-related information; and send the attachment-related information to the threat detection module.
[0088] The threat detection module is configured to perform threat detection on email attachments according to attachment-related information to obtain detection results; and generate detection logs according to the detection results.
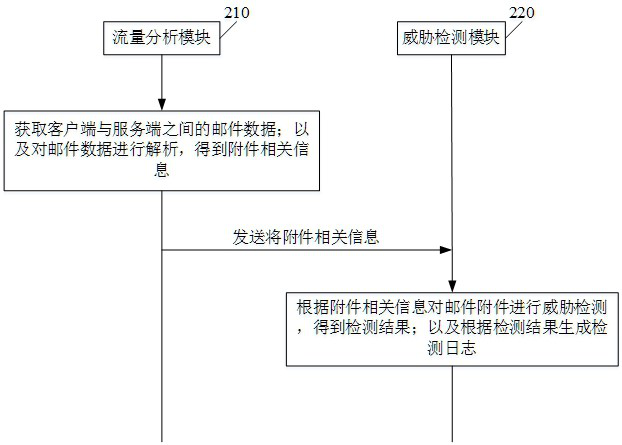
[0089] Please also refer to Figure 5 , Figure 5 It is a schematic diagram of information interaction between modules of an email attachment threat detection system provided by the e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com