Security process and security tower controlling coming vehicles at checkpoint
A technology of safety procedures and checkpoints, which is applied in traffic control systems of road vehicles, traffic control systems, character and pattern recognition, etc. The effect of improving situational awareness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
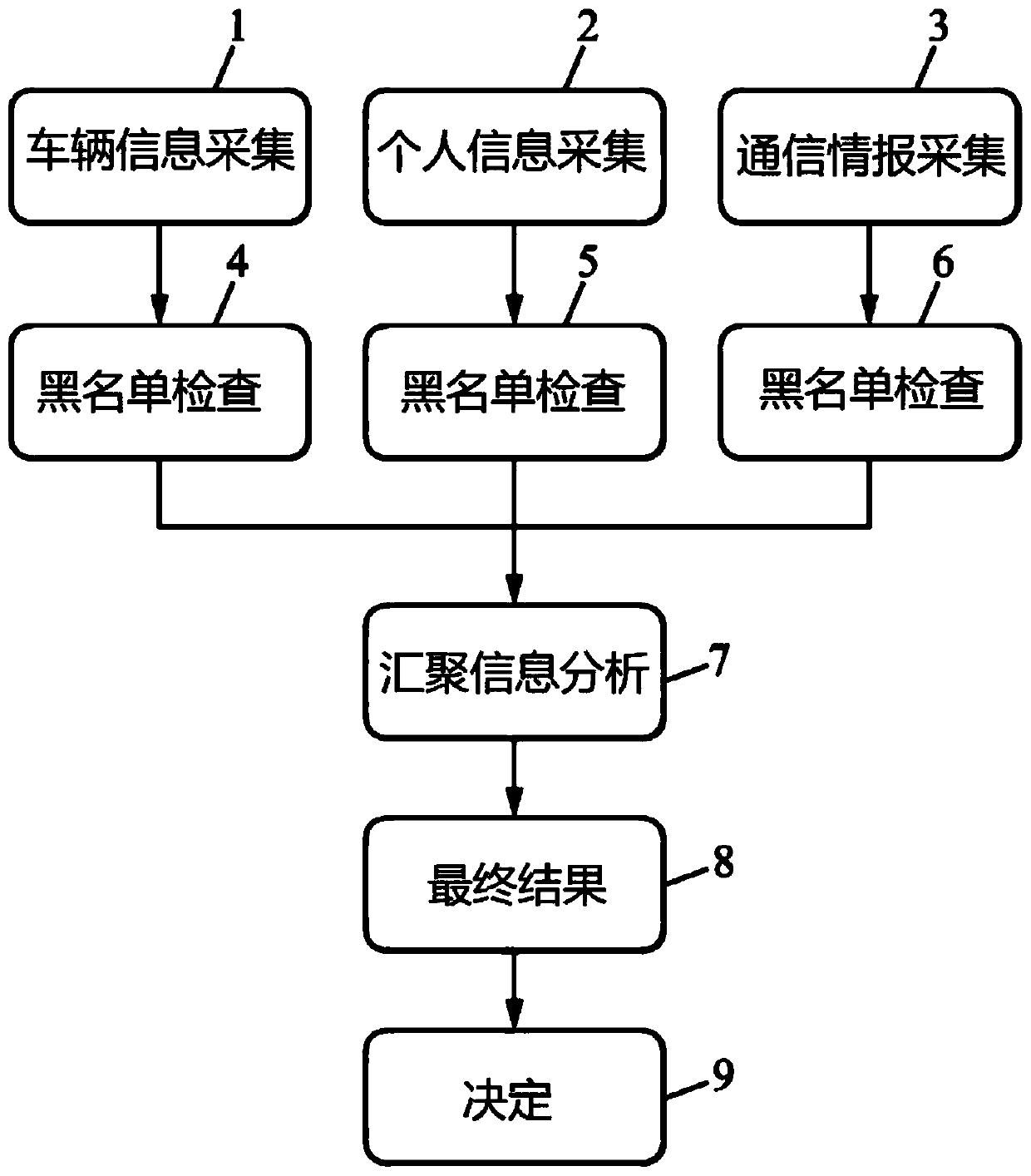
[0044] figure 1 An example of a security program according to an embodiment of the present invention is shown.
[0045] The security program first executes three collection steps at the same time, vehicle information collection step 1, personal information collection step 2, and mobile phone information collection step 3.
[0046] In the vehicle information collection step 1, the collected vehicle information includes: vehicle license plate, vehicle type, vehicle color, vehicle brand, vehicle size and vehicle shape.
[0047] In personal information collection step 2, the collected personal information includes: the number of people entering the vehicle, the facial recognition of the driver entering the vehicle, and the facial recognition of all passengers entering the vehicle, including the driver entering the vehicle.
[0048] In mobile phone information collection step 3, the collected mobile phone information includes: the number of mobile phones entering the vehicle, the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com