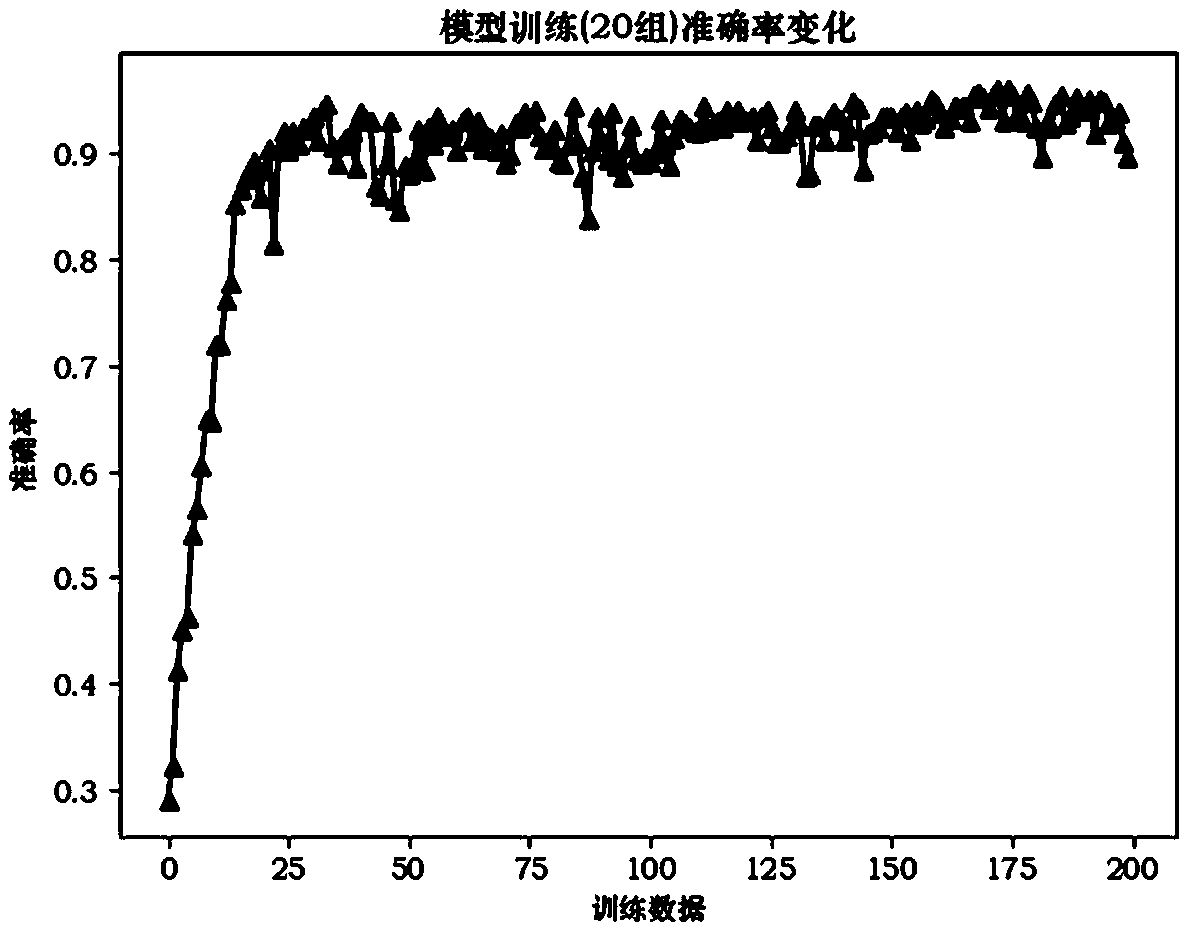
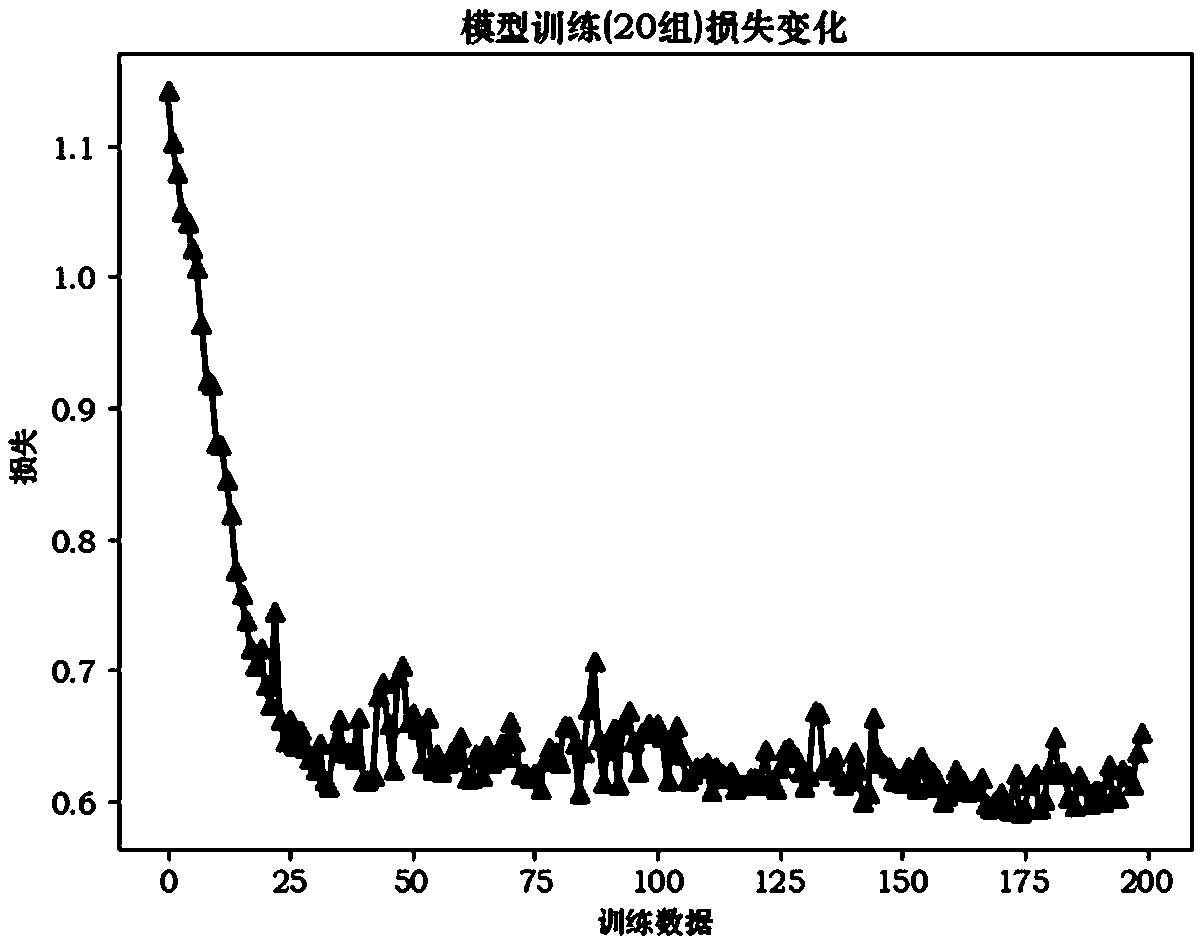
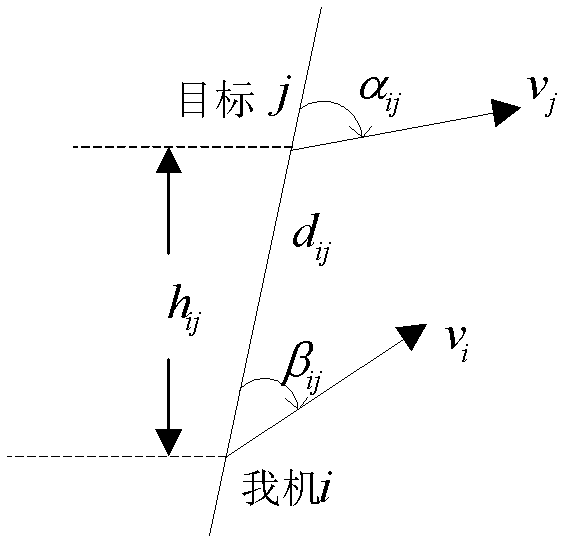
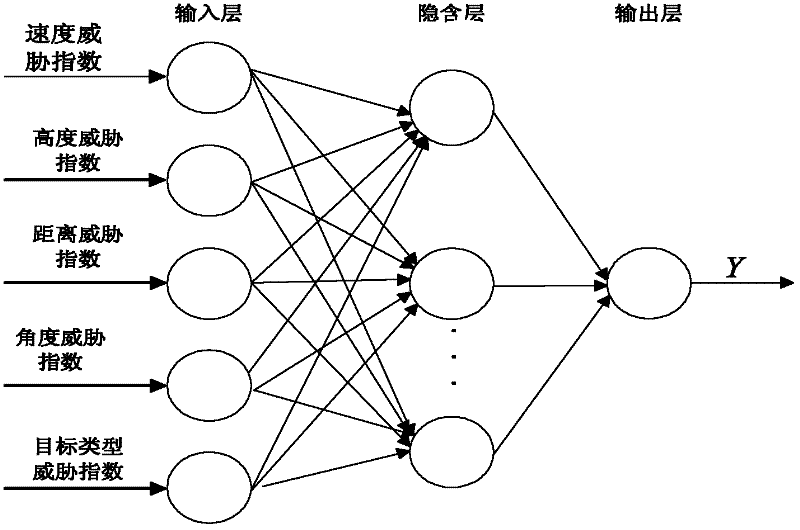
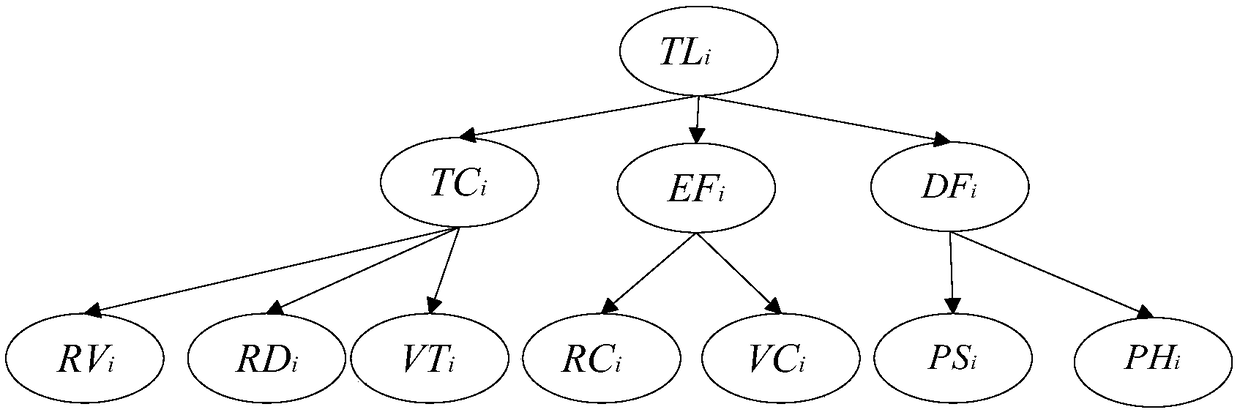
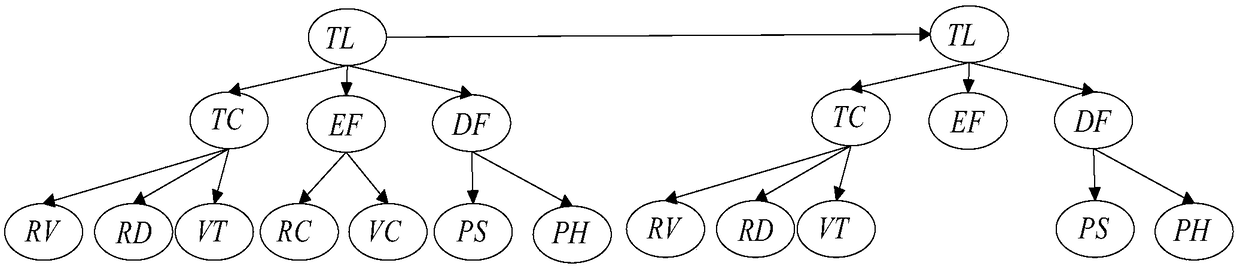
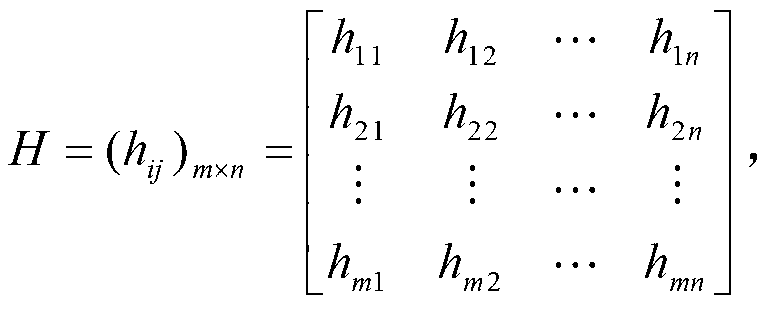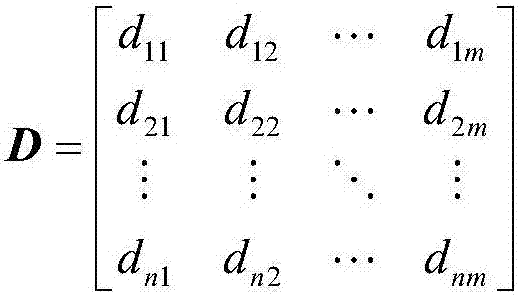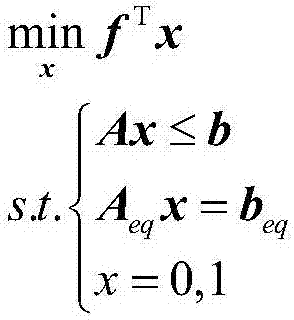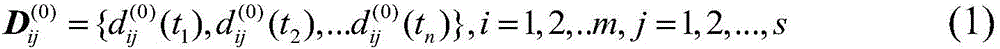Patents
Literature
56 results about "Targeted threat" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Targeted threats are a class of malware destined for one specific organization or industry. A type of crimeware, these threats are of particular concern because they are designed to capture sensitive information. Targeted attacks may include threats delivered via SMTP e-mail, port attacks, zero day attack vulnerability exploits or phishing messages. Government organisations are the most targeted sector. Financial industries are the second most targeted sector, most likely because cybercriminals desire to profit from the confidential, sensitive information the financial industry IT infrastructure houses. Similarly, online brokerage accounts have also been targeted by such attacks.
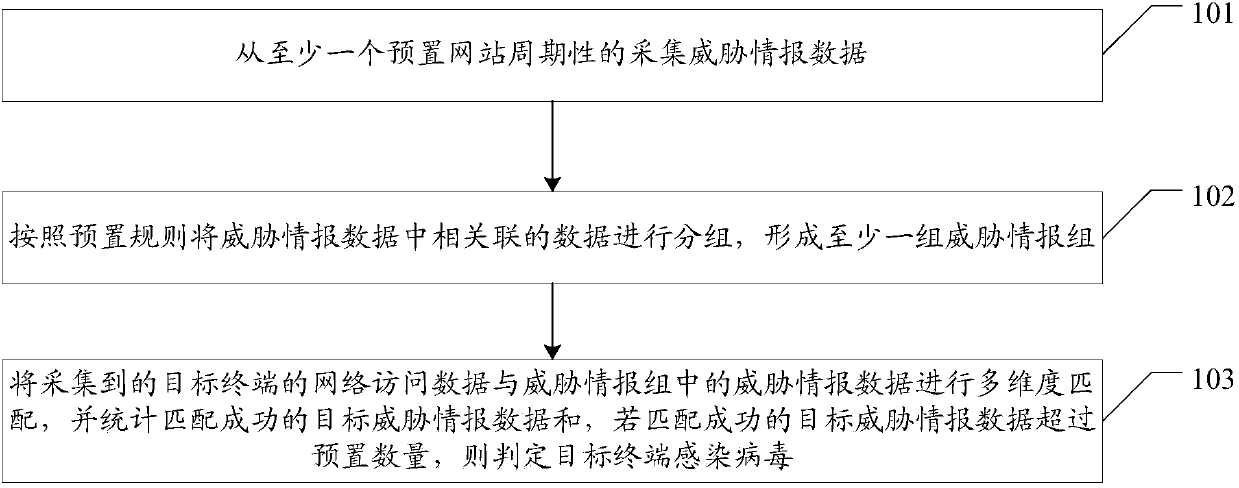
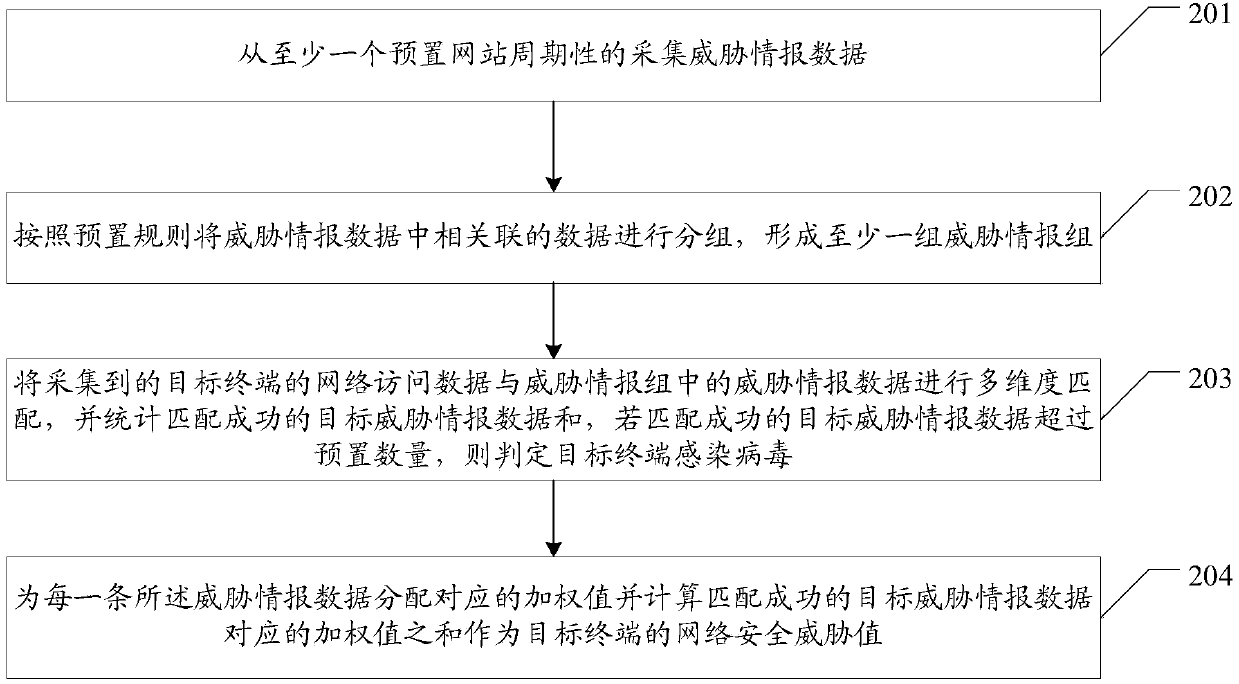
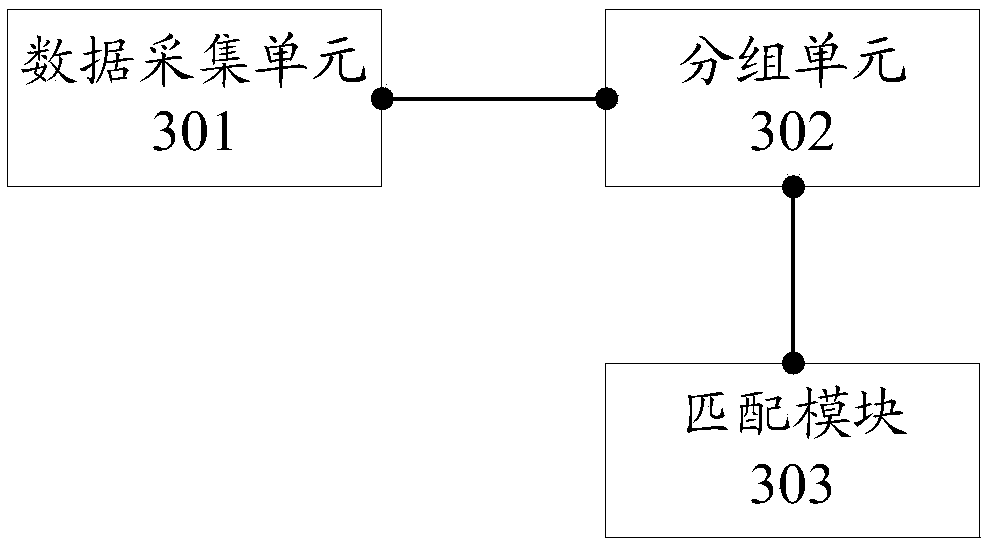
Threat intelligence-based network security detection method and system
The embodiment of the invention provides a threat intelligence-based network security detection method and system, aiming at improving the accuracy of network security detection. The method provided by the embodiment of the invention includes the following steps: periodically acquiring threat intelligence data from at least one preset website; grouping associated data in the threat intelligence data according to a preset rule to form at least one threat intelligence group, wherein the threat intelligence group includes at least one type of the threat intelligence data, and each type of the threat intelligence data includes one or more pieces of data; and performing multidimensional matching on acquired network access data of a target terminal and the threat intelligence data in the threatintelligence group, and calculating target threat intelligence data that is successfully matched, and if the number of the target threat intelligence data that is successfully matched exceeds a presetnumber, determining that the target terminal is infected with a virus.
Owner:SANGFOR TECH INC
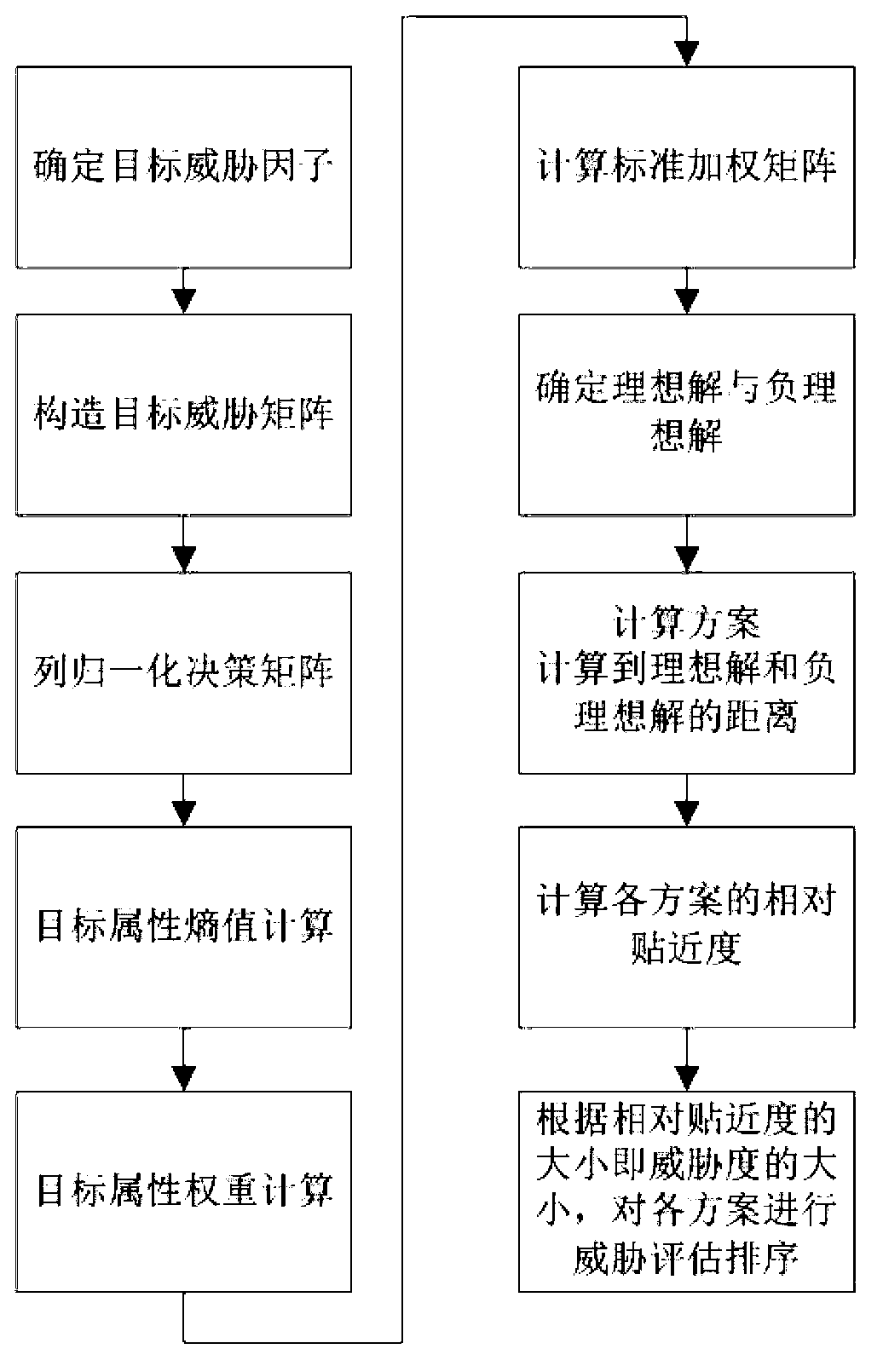
TOPSIS-method multi-target threat ordering method based on information entropy
InactiveCN103246818AAvoid deficienciesImprove accuracySpecial data processing applicationsEntropy weight methodWeight coefficient
The invention provides a TOPSIS-method multi-target threat ordering method based on information entropy. The method includes first building a threat assessment threat factor model, building a target attribute decision matrix according to the threat factor model, adopting an entropy weight method to calculate a target attribute weight vector according to the decision matrix, adopting a TOPSIS method to calculate relative close degree of target schemes according to the weight vector calculated through the entropy weight method and conducting threat assessment ordering on the schemes according to the close degree, namely the threat degree. By means of the method, shortcomings of the traditional ideal solution approaching ordering method in determination of weight coefficients are effectively overcome, and the target threat degree prediction accuracy is improved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
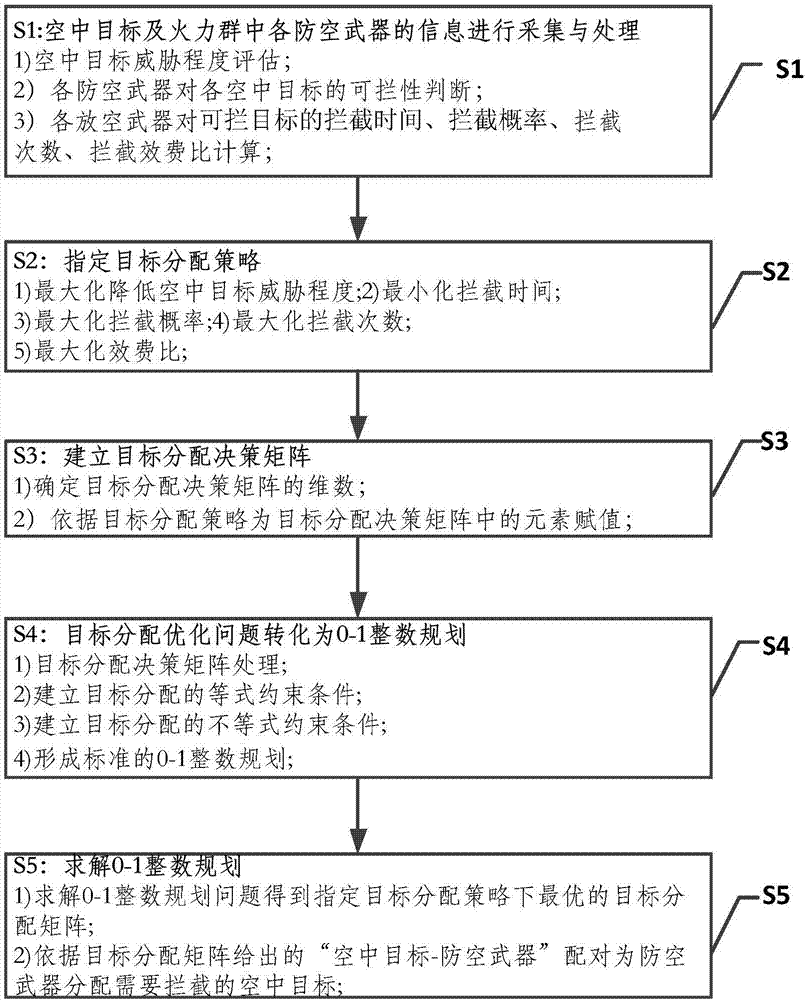
Multi-type air defense weapon mixed firepower group target assignment optimization method
The invention discloses a multi-type air defense weapon mixed firepower group target assignment optimization method. According to the states and the indexes of different types of air defense weapons in the firepower group and the real-time air attack target detection information, the air target threat degree, the interception time, the interception possibility, the interception times, the interception efficiency-cost ratio and the like can be used as optimization indexes, air targets in need of interception are assigned to the air defense weapons in the firepower group, and different optimal interception policies with the maximum reduction of the air target threat degree, the shortest interception time, the largest interception possibility, the maximum interception times, the highest interception efficiency-cost ratio and the like can be realized. The method can be applied to target assignment software design and target assignment simulation model development and the like for a multi-type air defense weapon mixed firepower group tactical command and control system.
Owner:SHANGHAI INST OF ELECTROMECHANICAL ENG
Aerial target threat assessment method based on dynamic TOPSIS
InactiveCN106296031ARealize pre-discriminationAvoid the problem that threat assessment lags behind changes in battlefield situationDesign optimisation/simulationResourcesEntropy weight methodOriginal data
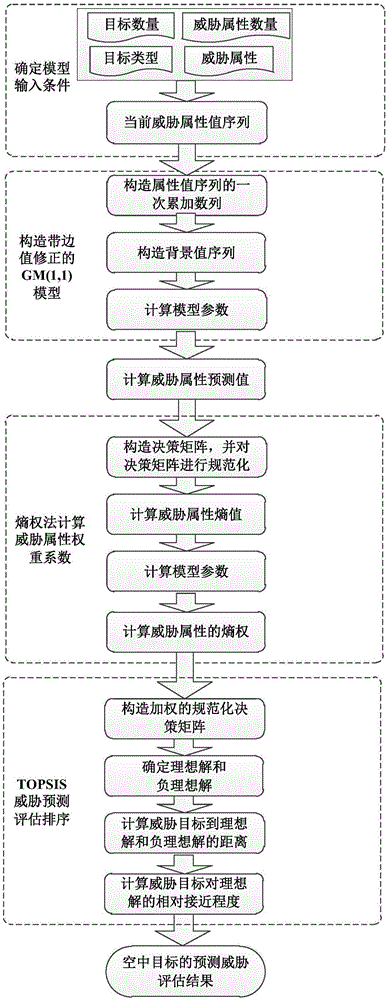
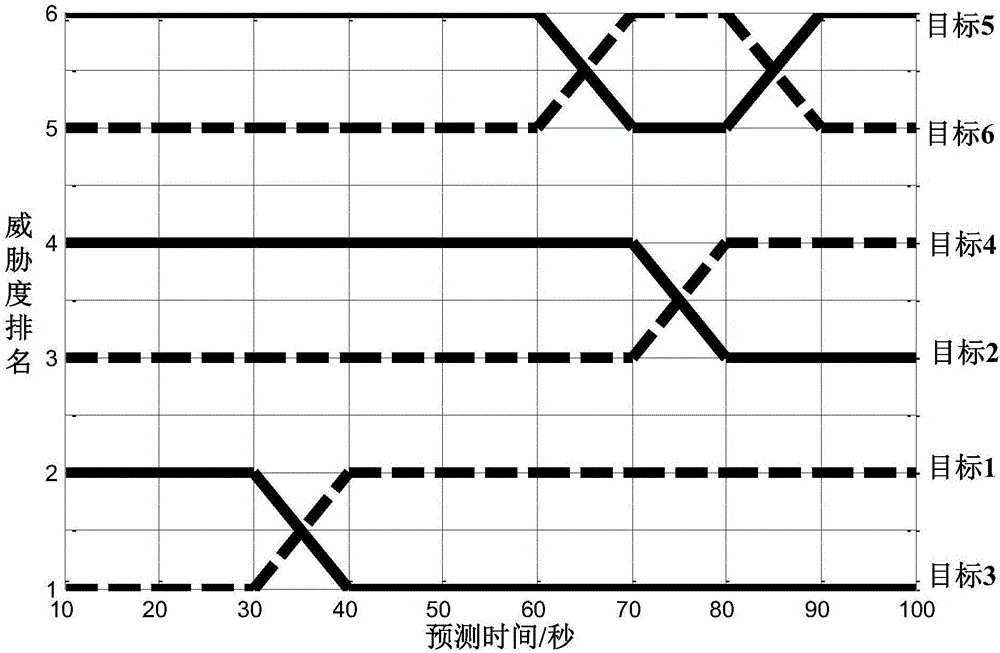
The invention discloses an aerial target threat assessment method based on dynamic TOPSIS, relates to an aerial target threat assessment method, and belongs to the field of threat assessment in data fusion processing. The method comprises the steps: firstly obtaining the sequential value of threat attributes of the aerial target at a discrete time node according to the original data of the aerial target, and predicting the change trend of the sequential value of threat attributes of each target with time through employing a GM(1, 1) model with boundary value correction; carrying out the weight calculation of an obtained dynamic threat attribute value prediction sequence through an entropy weight method, and further constructing a weighted standardized decision matrix; carrying out the assessment of the aerial threats at future time nodes through employing a TOPSIS method, and obtaining the dynamic prediction assessment result of the threat degree of the aerial target. The method can achieve the dynamic prediction assessment of the threat degree of the aerial target in variable environments of battlefields. The method can be used in the field of air defense command, remarkably shorten the reaction time of the air defense command, and meet the requirements for the instantaneity of air defense.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
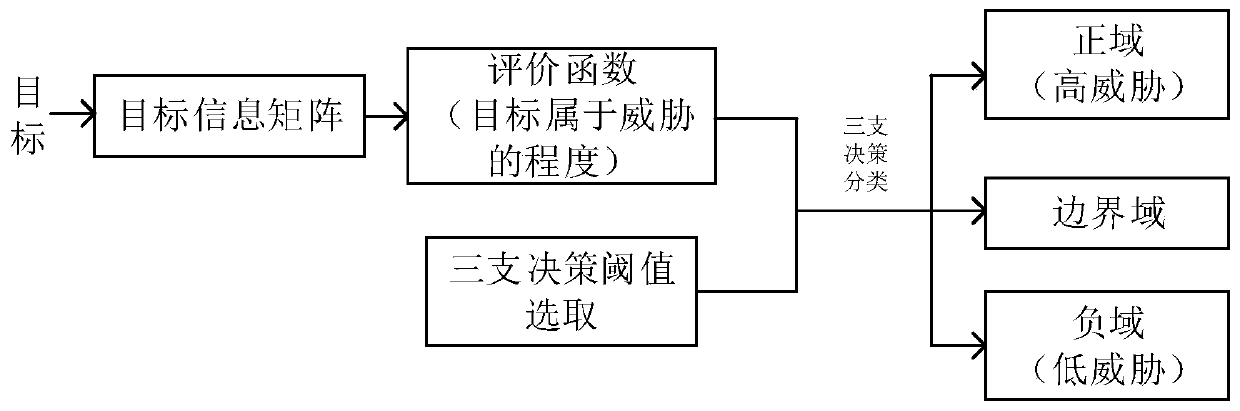
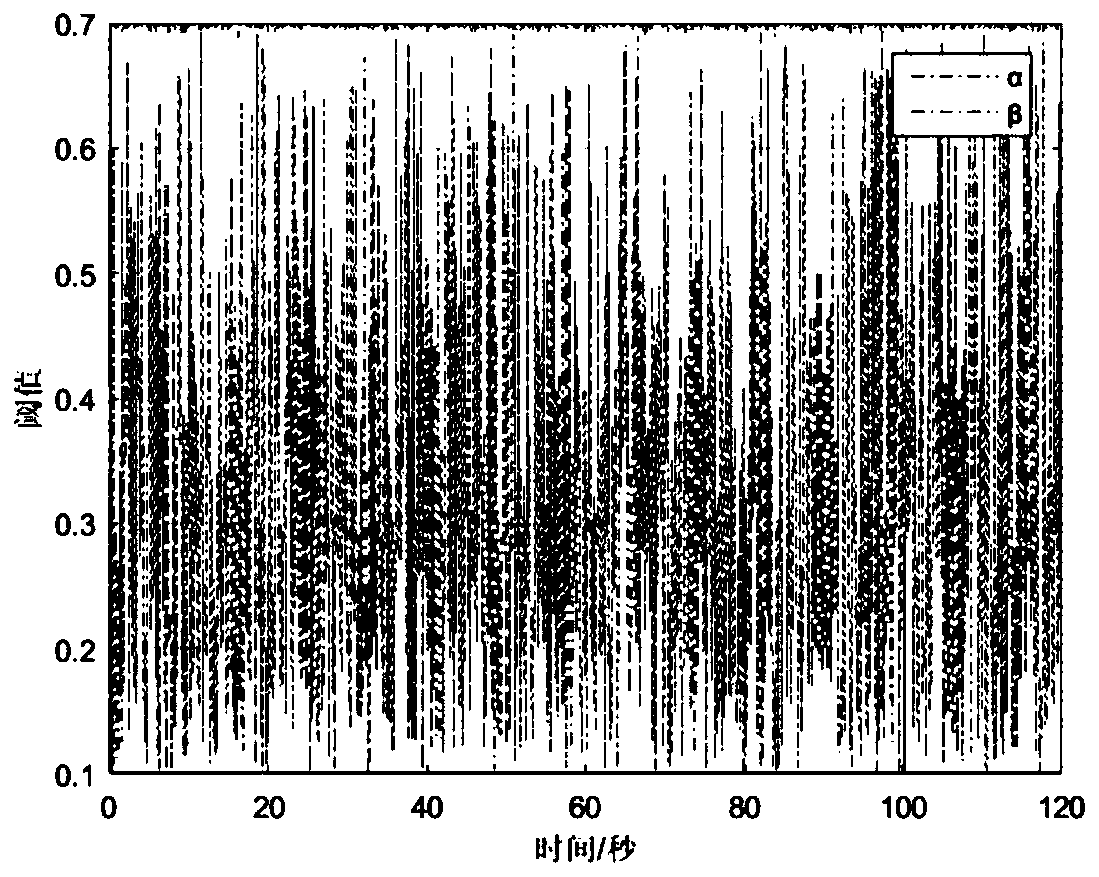
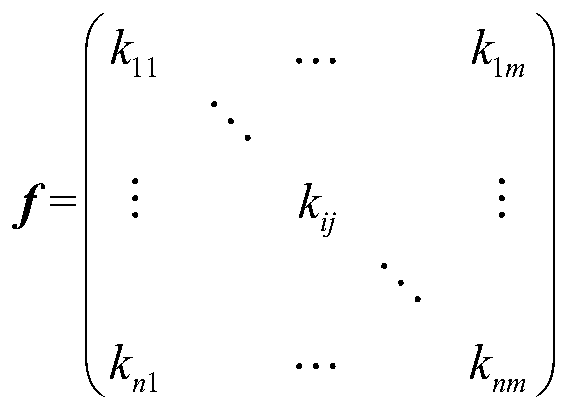
Threat assessment method based on three-way decision
ActiveCN110232518AQuick Command JudgmentReduce the likelihood of wrong decisionsResourcesComplex mathematical operationsDecision makerRadar
The invention provides a threat assessment method based on a three-way decision. The threat assessment method comprises the steps: determining target feature information detected by a radar, obtaininga target information matrix, obtaining a target assessment function in the three-way decision according to the target information, employing a simulated annealing algorithm to select the optimal threshold of the three-way decision, and carrying out three-way decision on the threat degree according to the optimal threshold. According to the threat assessment invention, three decision theories areintroduced into target threat assessment; targets are successfully divided into high threats; and in the three domains, namely the low threat domain, the low threat domain and the boundary domain, a decision maker can make a targeted decision on the target according to the divided three domains, and compared with a traditional method which only sorts the threat degrees of the target, the decisionmaker makes a command and decision, and the decision maker can make a command and judgment more conveniently and rapidly through system classification of the target. Compared with the traditional two-way decision, the introduction of the boundary domain in the three-way decision also reduces the possibility of making an error decision only for the high threat domain and the low threat domain to acertain extent.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
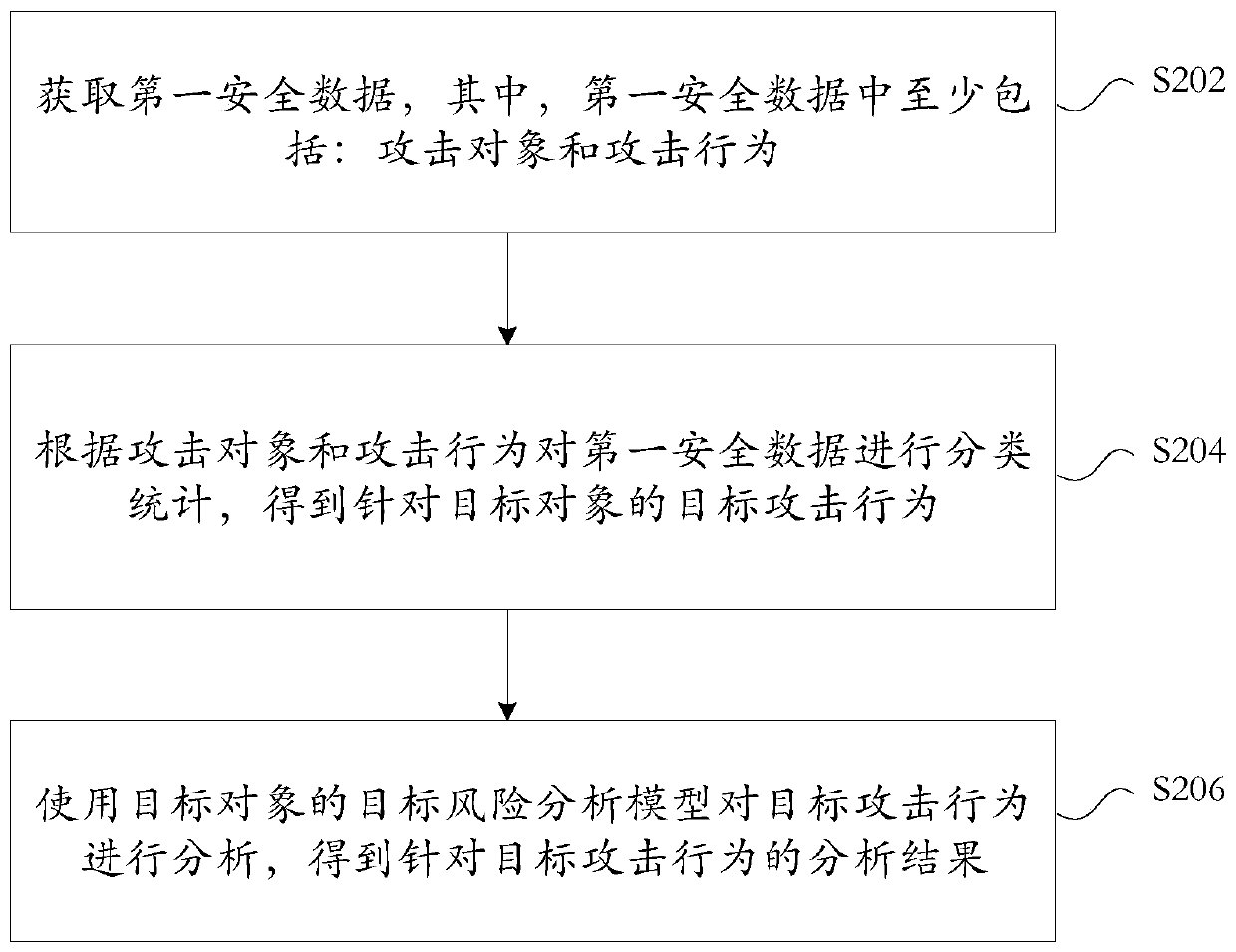
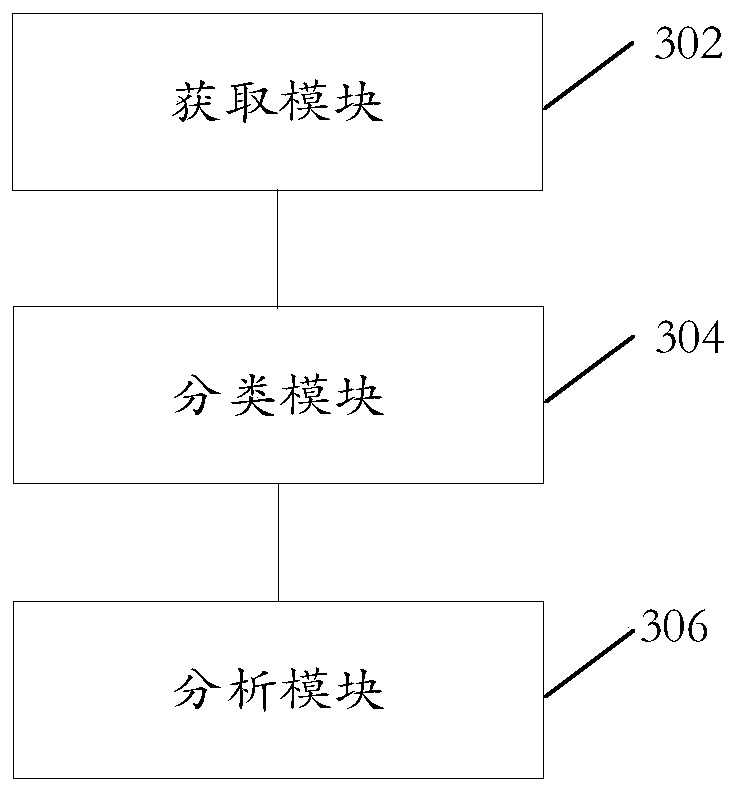
Attack behavior analysis method and device, storage medium and electronic device
ActiveCN110417772ASolve the problem that it is impossible to make targeted threat predictions for specific targetsTransmissionTargeted threatAnalysis method
The embodiment of the invention provides an attack behavior analysis method and device, a storage medium and an electronic device, and the method comprises the steps: obtaining first safety data whichat least comprises an attack object and an attack behavior; performing classification statistics on the first security data according to the attack object and the attack behavior to obtain a target attack behavior for the target object; and analyzing the target attack behavior by using the target risk analysis model of the target object to obtain an analysis result for the target attack behavior.The problem that the network security analysis cannot perform targeted threat prediction on the specific target in the prior art is solved.
Owner:ZHEJIANG DAHUA TECH CO LTD
Phased array beam dwell scheduling method based on scheduling benefit and genetic algorithm
The invention discloses a phased array beam dwell scheduling method based on a scheduling benefit and a genetic algorithm, belongs to the field of phased array radar resource management, and particularly relates to a method for implementing adaptive beam dwell scheduling by utilizing a task priority and a scheduling strategy. According to the invention, firstly, on the basis of a target threat model, target attribute information is expressed with a threat degree function; secondly, a two-dimensional priority list thought is utilized, a two-dimensional priority list is utilized for twice to integrate three parameters of a working mode priority, a deadline and a threat degree into a comprehensive priority in a nonlinear weighting mode, and uniqueness of the comprehensive priority is ensured;then the comprehensive priority is combined with a validity function of task scheduling to form a new scheduling benefit and accordingly, a scheduling optimization model is established, wherein a pulse interleaving technology and time and energy constraint conditions are considered; and finally, such nonlinear optimization problem is solved by the genetic algorithm. According to the phased arraybeam dwell scheduling method based on the new scheduling benefit, which is disclosed by the invention, a loss rate of a task can be effectively reduced, a hit value ratio and a correction value rate are improved, and meanwhile, an execution threat rate and a time utilization rate are also promoted.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Threat information processing method and device, electronic equipment and medium
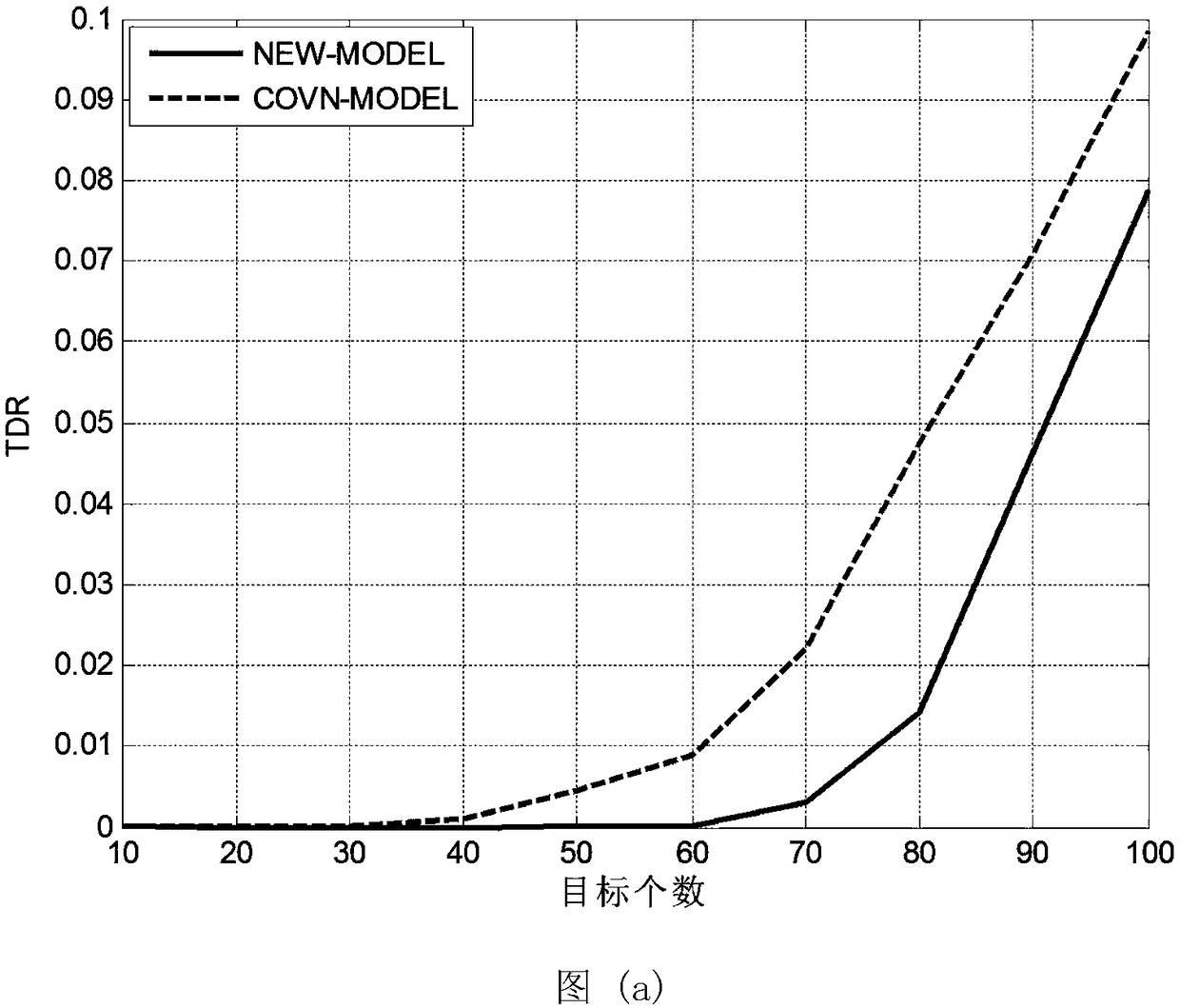
ActiveCN110809010AConvenient statisticsFacilitate targeted threat predictionTransmissionInformation processingAttack
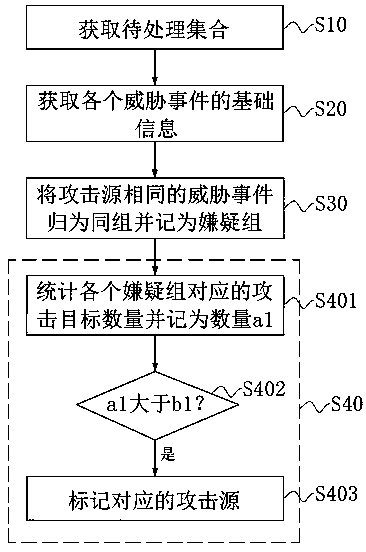
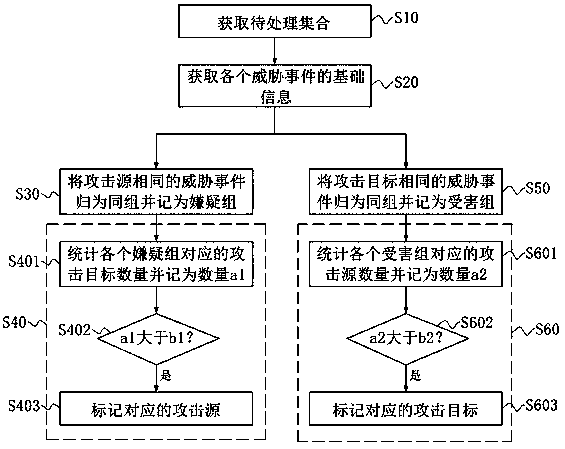
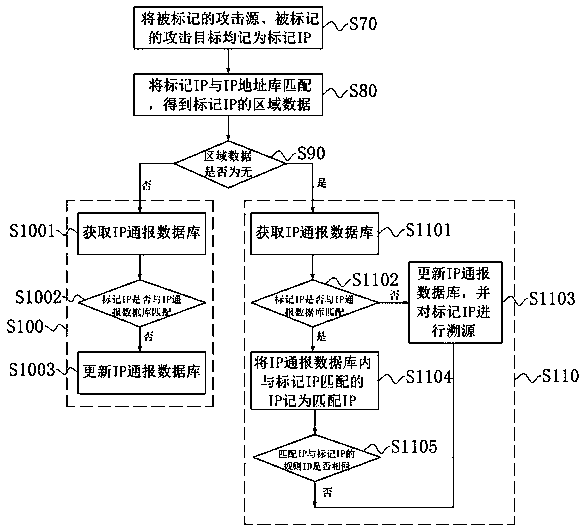
The invention discloses a threat information processing method, and relates to the technical field of information security, and is used for solving the problem that targeted threat prediction is difficult to perform on each attack source, and the method specifically comprises the following steps: obtaining a to-be-processed set, marking events of the to-be-processed set as threat events, and enabling attack types of the threat events to be the same and addresses to be located in a preset region; obtaining basic information of each threat event, wherein the basic information comprises an attacksource and an attack target; classifying the threat events with the same attack source into the same group and marking as a suspect group; counting the number of attack targets of each suspect groupand recording the number as a1, judging whether the number a1 is greater than a preset value b1 or not, and if so, marking a corresponding attack source. The invention further discloses a threat information processing device, electronic equipment and a computer readable medium.
Owner:浙江乾冠信息安全研究院有限公司
Asset vulnerability identification method, device and system
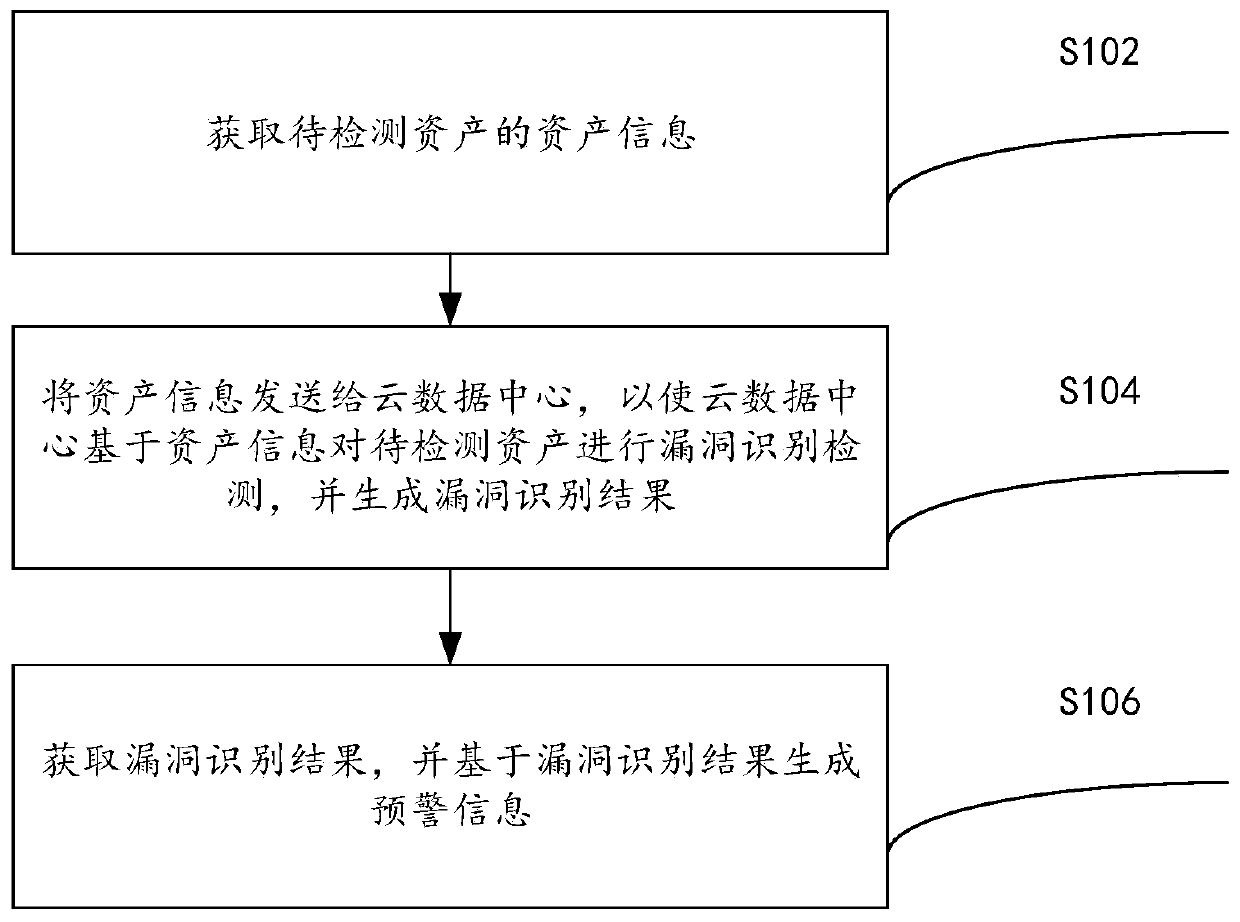
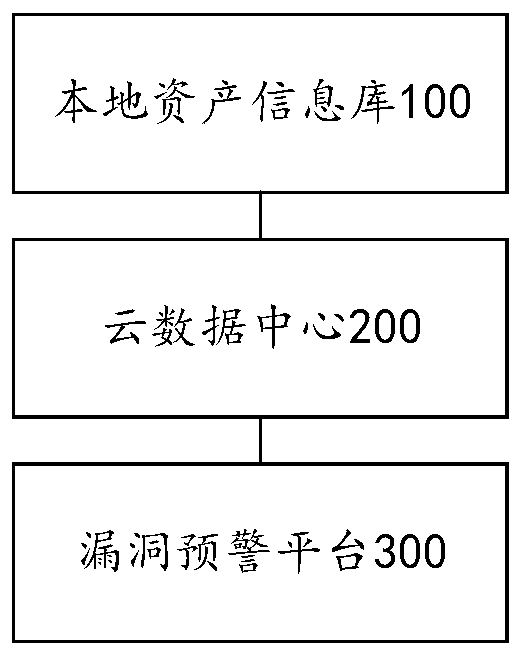
InactiveCN110708315AComprehensive Vulnerability DetectionSolve the relatively simple technical problems of detectionTransmissionCloud data centerTargeted threat
The invention provides an asset vulnerability identification method, device and system, and relates to the technical field of network security, and the method comprises the steps: obtaining the assetinformation of to-be-detected assets; sending the asset information to a cloud data center; the cloud data center performing vulnerability identification detection on the to-be-detected assets based on the asset information and generating a vulnerability identification result; wherein the cloud data center stores target threat intelligence data, and the target threat intelligence data comprises atleast one of threat intelligence data uploaded by a security service provider, threat intelligence data uploaded by a security intelligence organization and threat intelligence data uploaded by an enterprise to which assets to be detected belong; and obtaining the vulnerability identification result, and generating early warning information based on the vulnerability identification result, thereby solving the technical problem that an existing asset vulnerability identification method is relatively single in asset vulnerability detection.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Compression method for early-warning radar track data transmission
InactiveCN105807266AOvercoming the problem of limited communication capacityFully functionalWave based measurement systemsRadarCurve fitting
The invention discloses a transmission compression method for early warning radar track data, and relates to the technical field of radar data transmission methods. The method includes the following steps: the sending end receives the data reported by the radar; the target points of the same batch number have been associated into the track by the radar, and the least square method is used for curve fitting with every 6 points in the track as a unit to obtain The fitting curve parameters of the target track; according to the threat level of the target, upload the fitting curve parameters of the target track and the last point track data in the time period to the receiving end; the receiving end uses the track fitting curve parameters to restore the target track trace. The method makes full use of limited communication capacity to transmit radar intelligence data, and fully utilizes the function of Beidou short messages, so that it can become a means of early warning radar emergency information transmission, which has far-reaching military and strategic significance.
Owner:PEOPLES LIBERATION ARMY ORDNANCE ENG COLLEGE
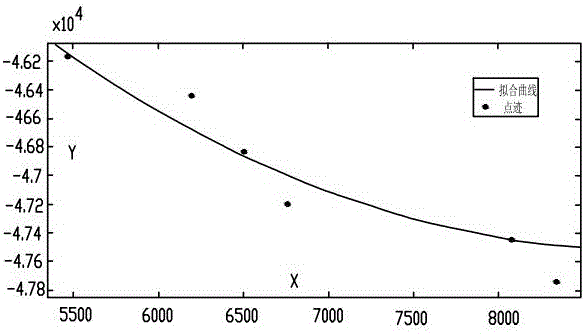
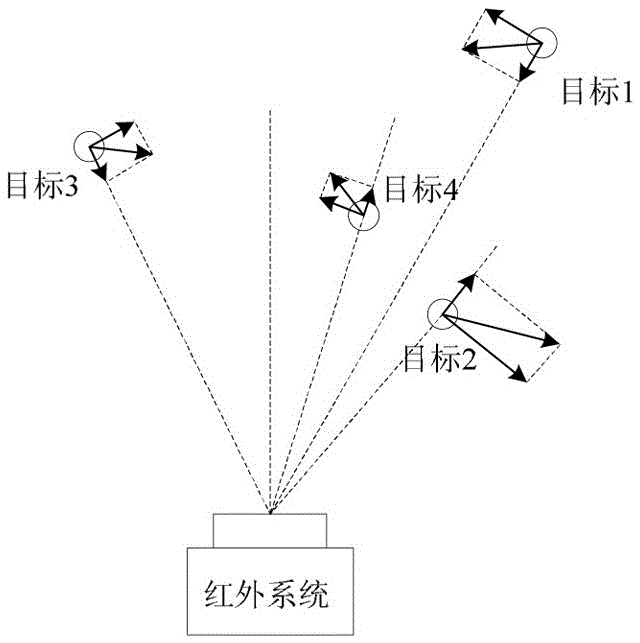
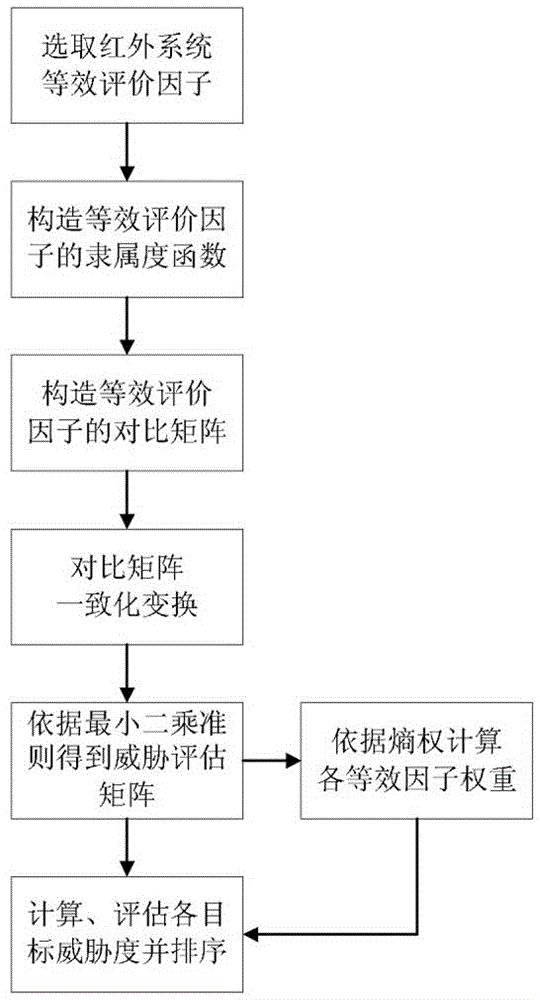
Infrared multi-target threat sequencing method based on equivalent evaluation factors
ActiveCN106650250ARealize threat calculationRealize evaluationRadiation pyrometrySpecial data processing applicationsAlgorithmEvaluation system
The invention relates to an infrared multi-target threat sequencing method based on equivalent evaluation factors. The method comprises the steps that a, threat indexes of targets in an infrared system are selected, and fuzzy membership is calculated; b, a contrast matrix of multiple equivalent evaluation factors is constructed for each target; c, evaluation values of the n equivalent evaluation factors for each target are solved according to the optimal constraint planning principle of least squares; d, an entropy method is utilized to finally determine and calculate entropy weights of all the equivalent evaluation factors in an evaluation system; e, threat degrees of the targets in the threat evaluation system of the infrared system are calculated and evaluated, sequencing is performed, and attention is paid to the targets with higher threat degrees. According to the method, evaluation can be directly performed through actual parameters acquired by the infrared system, and therefore rapidity of target threat evaluation is improved; threat index weights are adjusted according to the motion states of the targets, so that inaccuracy brought by subjective judgment is lowered, and application of the infrared system to extraction, discrimination and other aspects of emphasized targets is further strengthened.
Owner:PEOPLES LIBERATION ARMY ORDNANCE ENG COLLEGE
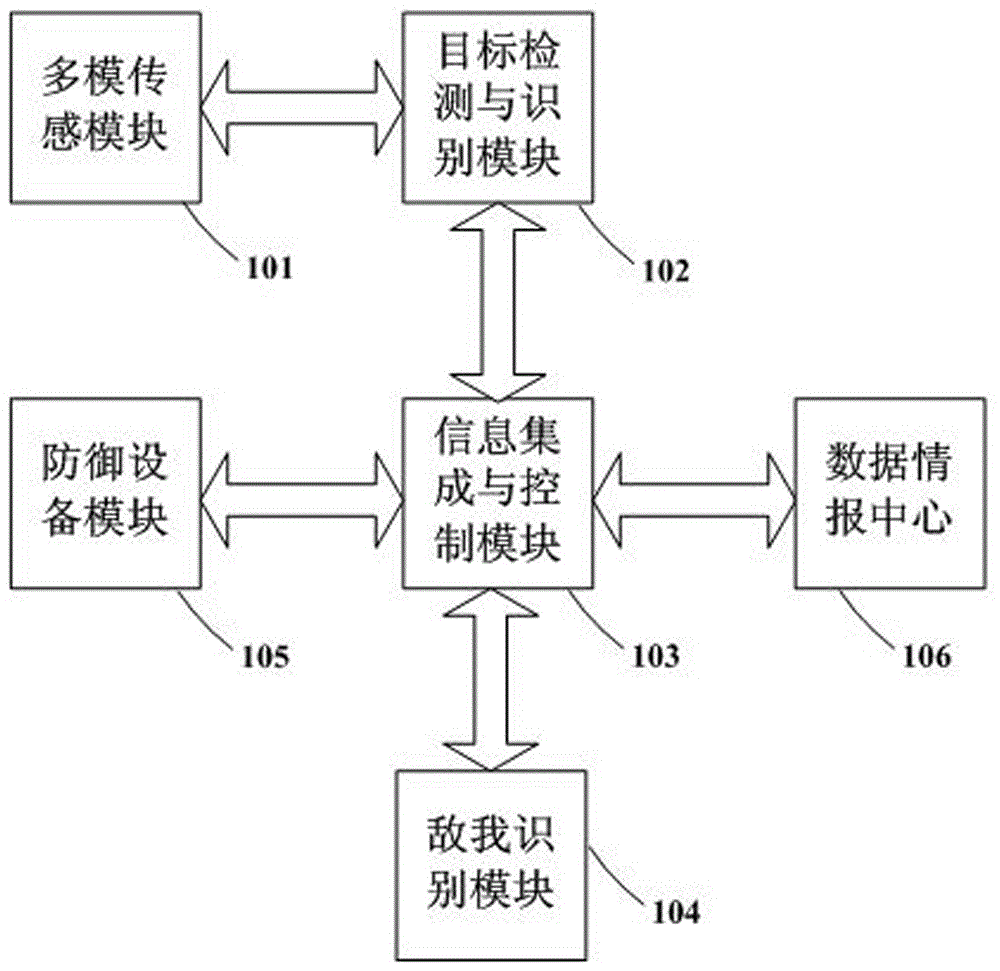
Region monitoring and defending system based on multimode compound sensing mechanism
ActiveCN106643303APortable and convenientQuick Arming CapabilitiesWeapons typesData centerEngineering
The invention relates to a region monitoring and defending system based on a multimode compound sensing mechanism. A result obtained by conducting multi-source sourcing information collection on an open space target through a multimode sensing module is sent to a target detection and identification module for information fusion and analysis; when an analysis result indicates that a target exists in a region, a friend or foe identification module receives target information and feeds a judged result on a target threat level back to an information integration and control module, the information integration and control module can send a control instruction to a defense equipment module in an automatic or manual intervention mode on the basis of pre-designed or set defensive strategies, and corresponding defensive measures are automatically adopted for a ground or aerial target according to the characteristics of comprehensive defense equipment and target properties. By means of an information data center connected to an information integration and control module, a human intervention control interface is provided, and on the basis of multidimensional sensing information collected by the multimode sensing module, continuous updating and property optimization are conducted on the system.
Owner:SHANGHAI RADIO EQUIP RES INST
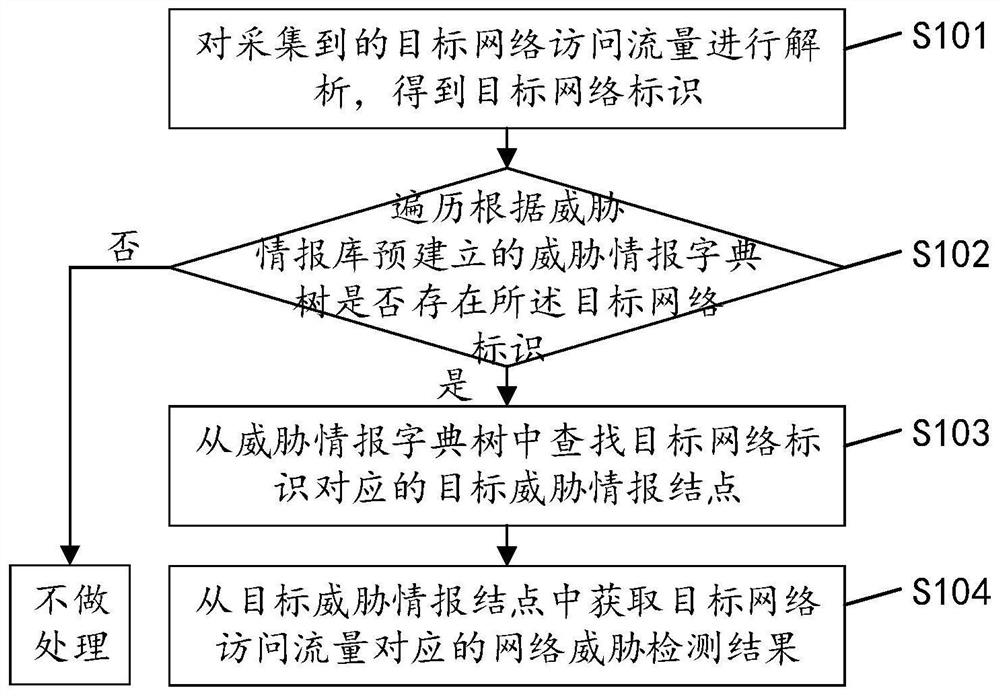
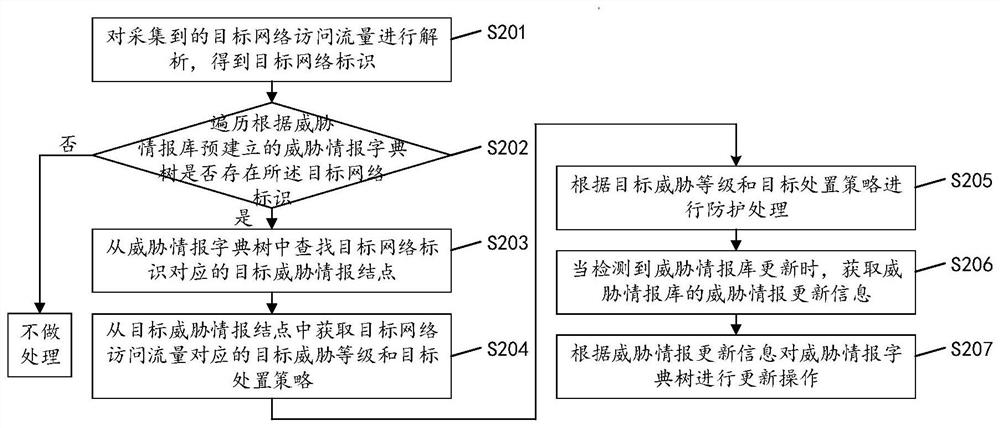
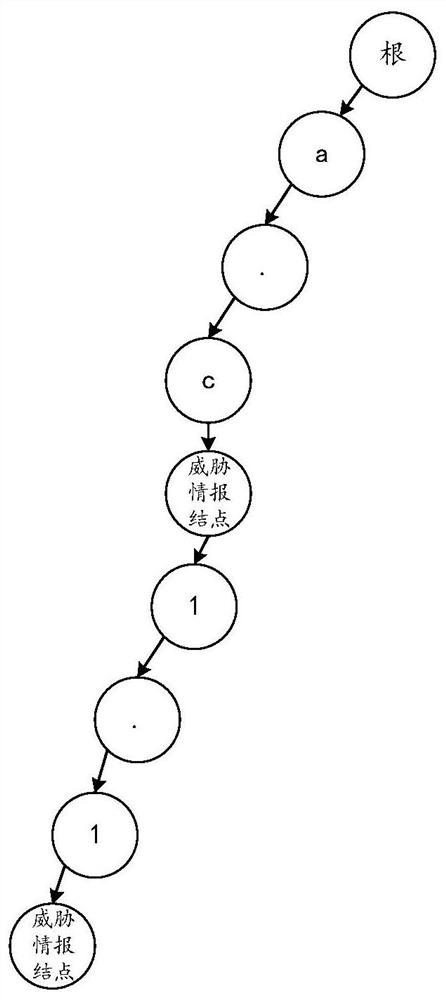
Network threat detection method and device based on dictionary tree, equipment and storage medium
PendingCN112491873AImprove Threat Detection EfficiencyAvoid attackTransmissionCyber threat intelligenceAttack
The invention discloses a network threat detection method based on a dictionary tree, and the method comprises the following steps: carrying out the analysis of collected target network access flow, and obtaining a target network identification; traversing whether a target network identifier exists in a threat information dictionary tree pre-established according to the threat information libraryor not; if so, searching a target threat intelligence node corresponding to the target network identifier from the threat intelligence dictionary tree; and obtaining a network threat detection resultcorresponding to the target network access flow from the target threat information node. By applying the network threat detection method based on the dictionary tree provided by the invention, the influence of the performance of the server on network threat information detection is avoided, the network threat detection efficiency is improved, and attacks can be prevented in time. The invention further discloses a network threat detection device and equipment based on the dictionary tree and a storage medium, and the corresponding technical effects are achieved.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
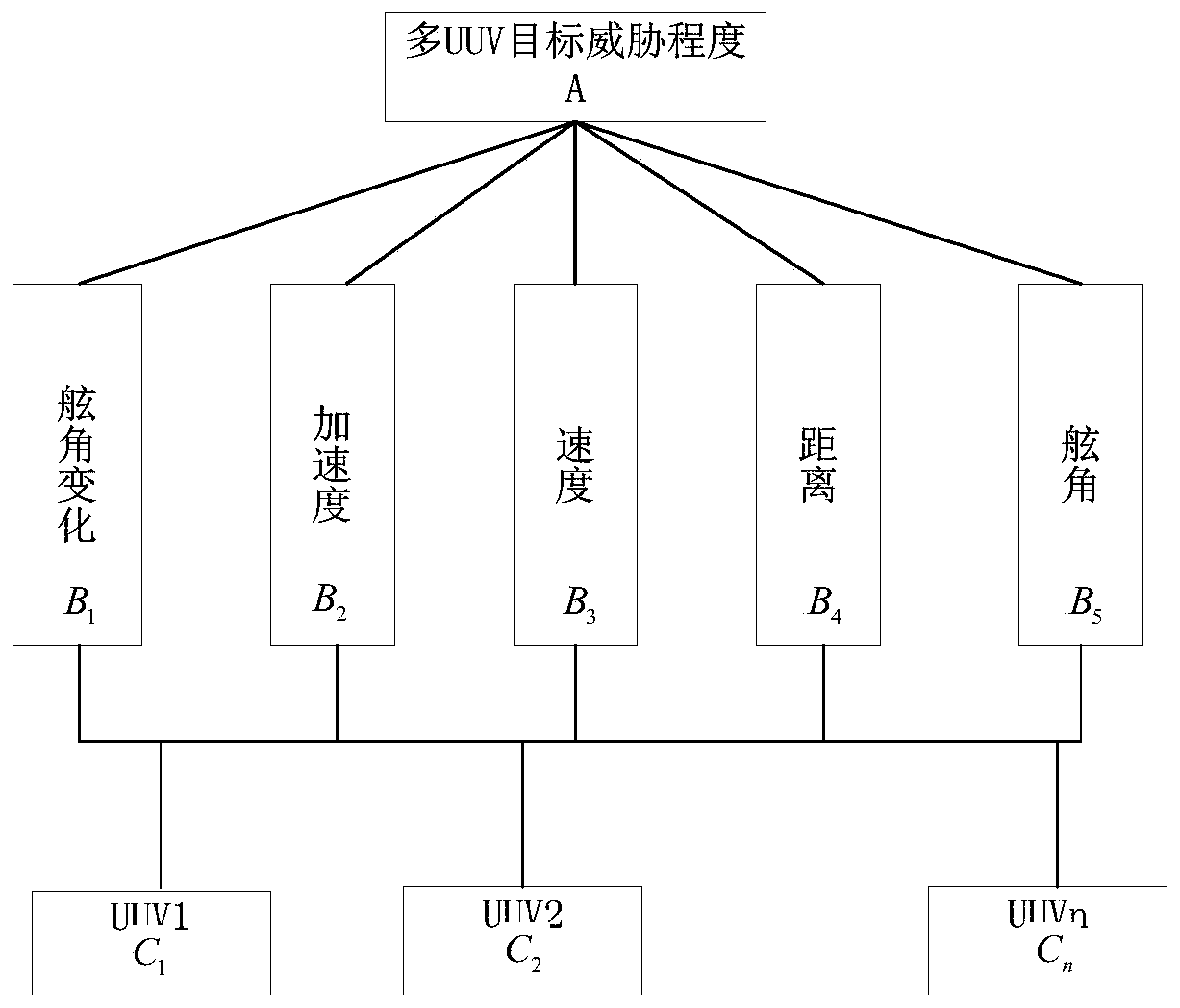
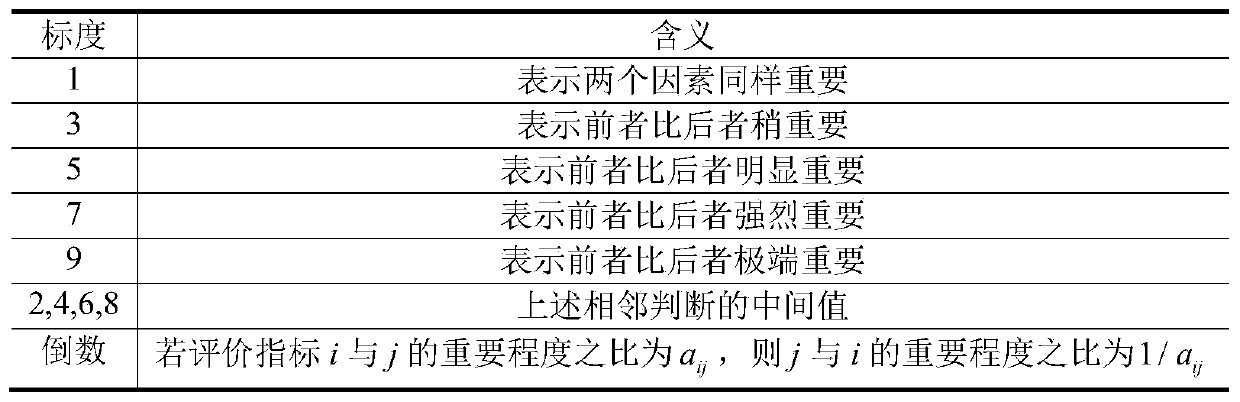
Multi-UUV red and blue party AHP threat assessment method for base attack and defense task
PendingCN110188461AQuantify Threat IntentQuantify Threat CapabilitiesDesign optimisation/simulationResourcesTargeted threatComputer science
The invention provides a multi-UUV red and blue party AHP (Analytic Hierarchy Process) threat assessment method for a base attack and defense task. The multi-UUV red and blue party AHP threat assessment method comprises the steps: 1, building a hierarchical structure model; 2, analyzing the importance degree of each assessment index of the same layer to a certain criterion in the upper layer, comparing every two assessment indexes, and constructing a paired comparison matrix according to a 9-scale method; 3, calculating the relative weight of each assessment index to the criterion; 4, calculating the comprehensive weight of each layer of index to the assessment target, and carrying out hierarchical single sorting and consistency inspection; and 5, carrying out hierarchical total sorting and consistency inspection, sorting the weights of the targets, and selecting the red UUV with the maximum threat degree as the target UUV to carry out priority attack. The invention provides a multi-UUV red and blue party AHP threat assessment method for a base attack and defense task, capable of showing the effectiveness of multi-UUV target threat assessment through simulation cases.
Owner:HARBIN ENG UNIV
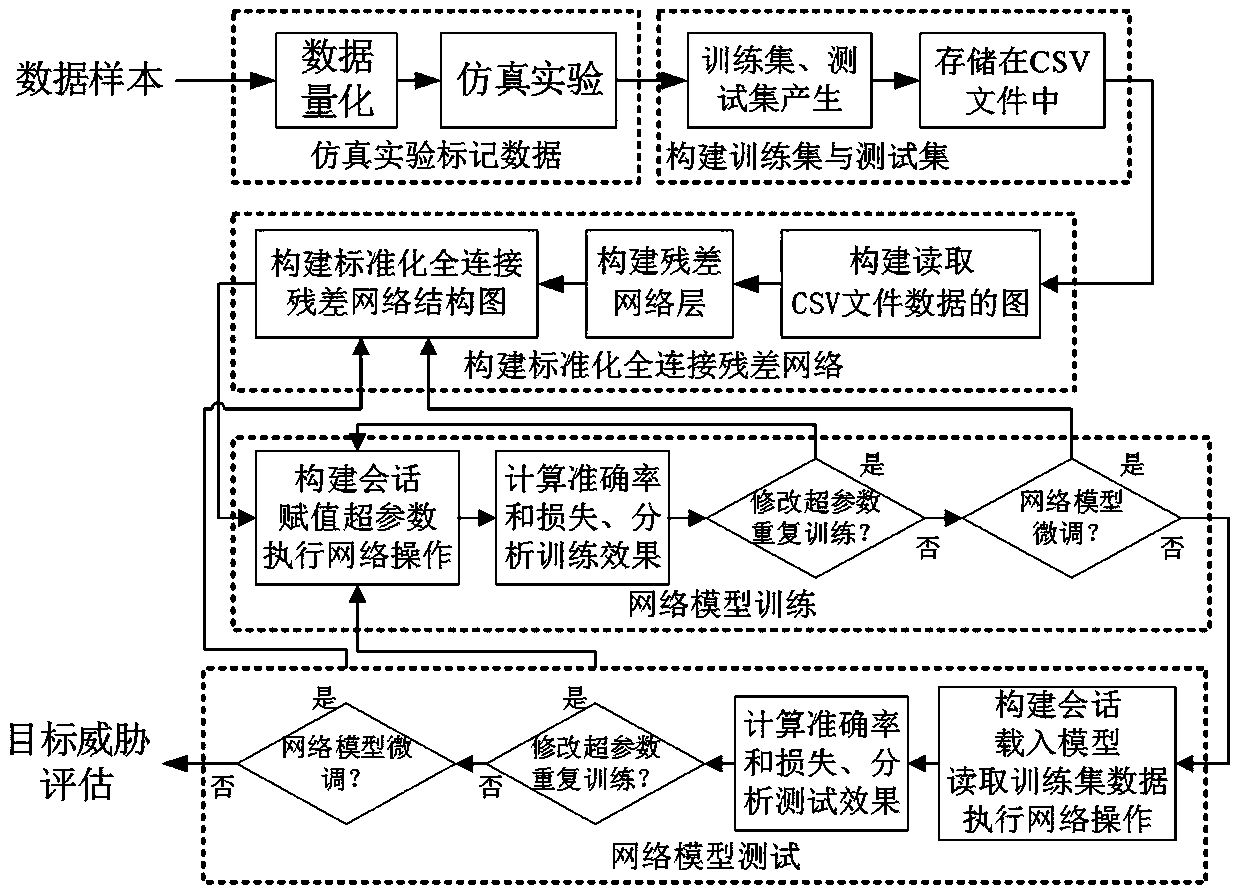
Air combat target threat assessment method based on standardized full-connection residual network
ActiveCN110472296ASolve the problem of inaccurate assessment resultsImprove information processing abilityCharacter and pattern recognitionNeural architecturesNetwork modelTargeted threat
The invention discloses an air combat target threat assessment method based on a standardized full-connection residual network, and belongs to the field of battlefield situation assessment. Firstly, asimulation experiment is carried out to mark data; constructing a training set and a test set and storing the training set and the test set in a CSV file; secondly, constructing a standardized full-connection residual error network under a TensorFlow database, including constructing a graph for reading CSV file data, a residual error network layer and a standardized full-connection residual errornetwork graph, and finally creating a TensorFlow session, training a network model, testing, analyzing network performance and verifying the model. According to the method, the problem of inaccurateevaluation result caused by lack of self-learning reasoning capability for large sample data in other air combat target threat evaluation methods is solved, distribution of input data can be self-learned, rules hidden in the data can be mined, and the trained model can accurately evaluate the air combat target threat. The battlefield situation assessment method is mainly used for (but not limitedto) battlefield situation assessment.
Owner:ZHONGBEI UNIV
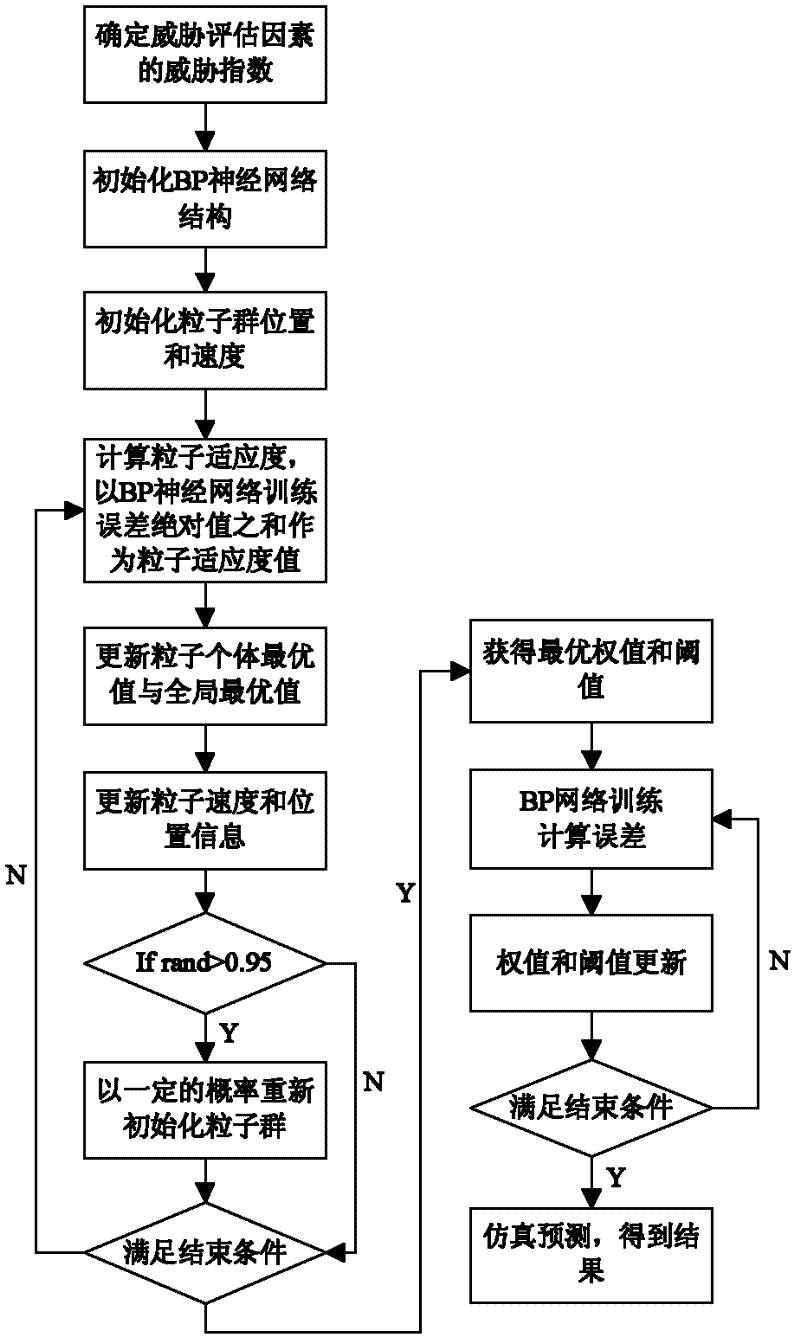
A method for assessing the degree of target threat
InactiveCN102298728AFast convergenceImprove convergence accuracyNeural learning methodsSimulationNetwork structure
The invention belongs to the technical field of data fusion, and discloses a method for evaluating a target threat degree. The method comprises the following steps of: firstly, establishing a threat evaluation quantifying model, and determining a threat index of each threat factor; secondly, initializing a BP (Back Propagation) neural network structure by using the threat index; and lastly, determining an initial weight and threshold value of a BP neural network according to a PSO (Particle Swarm Optimization) algorithm to obtain a threat evaluation degree. In the method, the target threat degree is evaluated by combining the BP neural network with the PSO algorithm, i.e., the initial weight and threshold value of the BP neural network are determined with the PSO algorithm, and then the convergence rate and convergence accuracy of the BP neural network are further accelerated, so that a BP nerve is prevented from being in a local minimum value, and the complexity is lowered on the basis of enhancing the intellectuality.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
Antiaircraft weapon system target threat assessment method
InactiveCN108805406ACalculation method is simpleImprove real-time performanceResourcesInternet privacyTargeted threat
The invention relates to an antiaircraft weapon system target threat assessment method. Factors considered in threat assessment mainly include target possible attack strategic locations, air raid target types and target interception emergency degrees. According to the method, values of all main factors are calculated, target threat degrees are calculated through linear weighting, and then target threat levels are divided according to the threat degrees.
Owner:CNGC INST NO 206 OF CHINA ARMS IND GRP
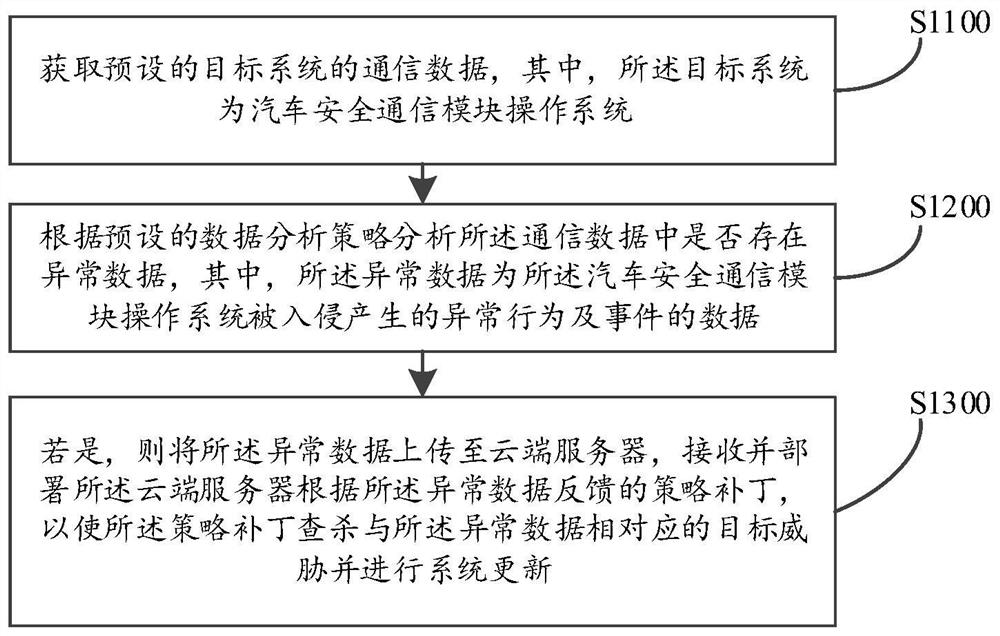
Automobile safety communication control method and device, computer equipment and storage medium
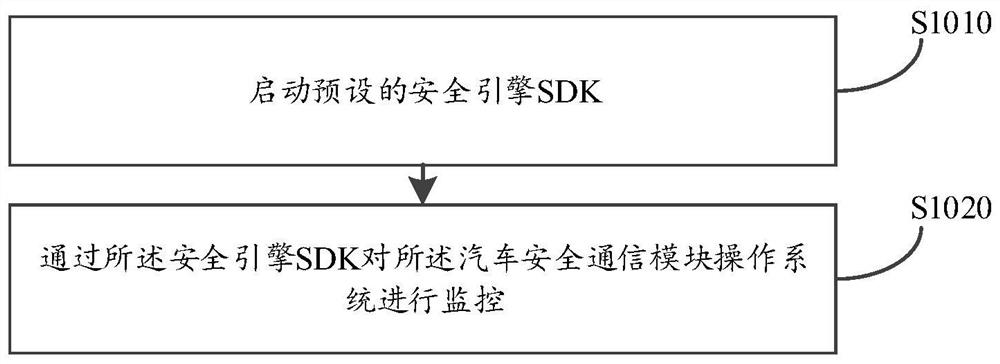
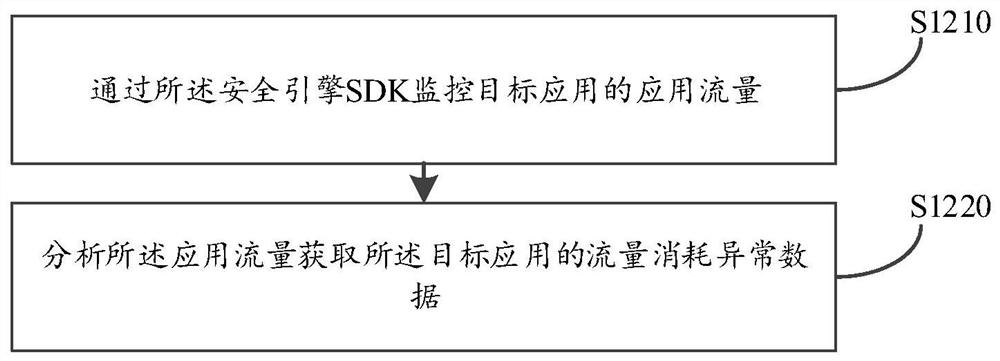
PendingCN112653655AProtection securityPrevent intrusionHardware monitoringPlatform integrity maintainanceOperational systemData information
The embodiment of the invention discloses an automobile safety communication control method and device, computer equipment and a storage medium, and the method comprises the following steps: obtaining the communication data of a preset target system, wherein the target system is an automobile safety communication module operation system; analyzing whether abnormal data exists in the communication data or not according to a preset data analysis strategy, wherein the abnormal data is data of abnormal behaviors and events generated when an automobile safety communication module operating system is invaded; if yes, uploading the abnormal data to a cloud server, and receiving and deploying a strategy patch fed back by the cloud server according to the abnormal data, so that the strategy patch searches and kills a target threat corresponding to the abnormal data and performs system updating. According to the embodiment of the invention, vulnerability repair is carried out on the automobile safety communication module operating system, the target threat updating system is searched and killed, the system safety of the automobile safety communication module operating system is protected, invasion of bad data information is prevented through real-time monitoring, and the safety of various services is ensured.
Owner:深圳市奇虎智能科技有限公司
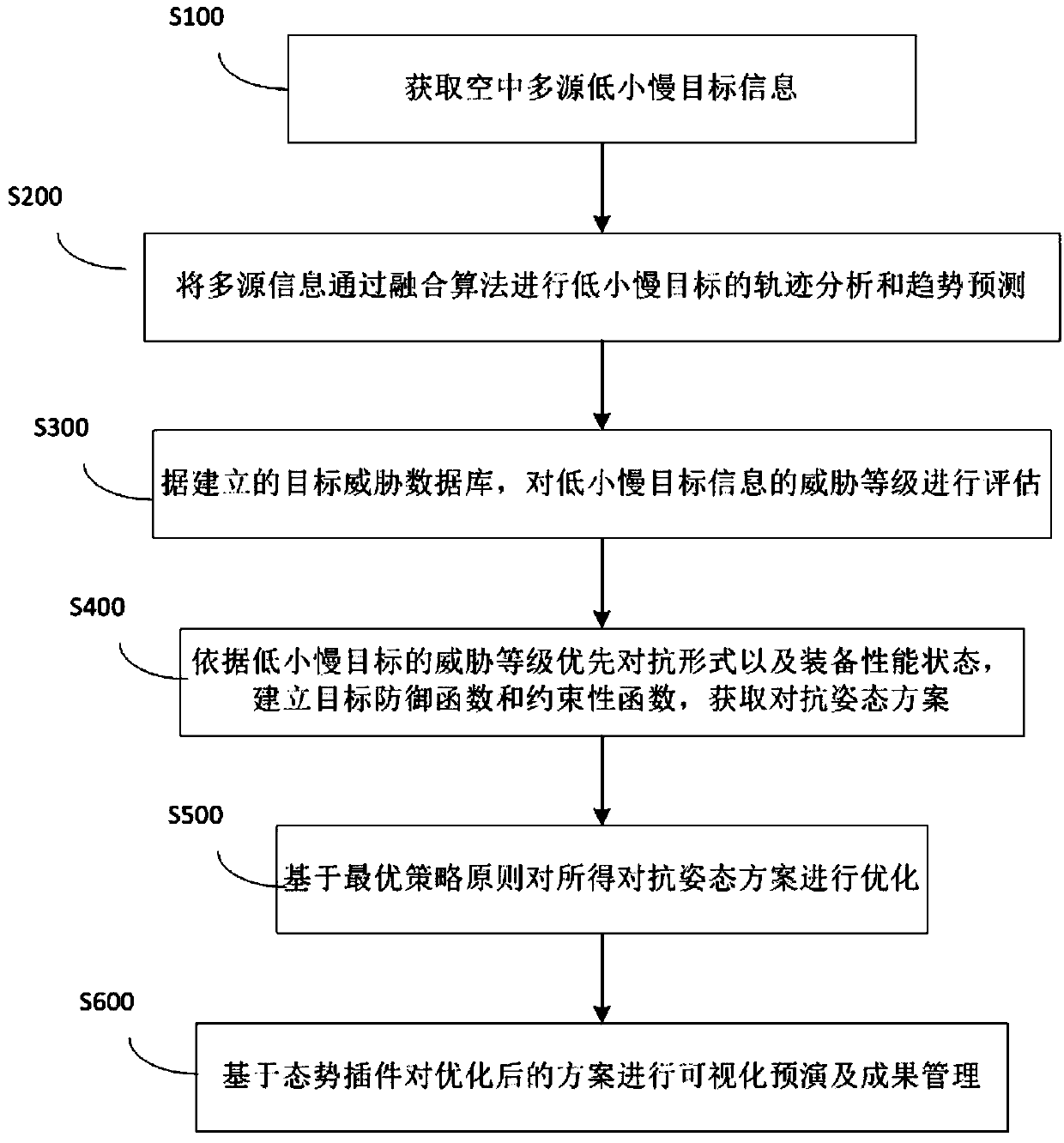
Management and control method of low-alititude low-speed small-target aerial target multi-source information fusion
ActiveCN109613530ARealize visualizationFully automatedRadio wave reradiation/reflectionLow speedTrend prediction
The invention discloses a management and control method of low-alititude low-speed small-target aerial target multi-source information fusion. The management and control method comprises the steps that aerial multi-source low-alititude low-speed small-target target information is obtained; trajectory analysis and trend prediction of a low-alititude low-speed small-target target are carried out through a fusion algorithm by the multi-source information; according to an established target threat database, the threat level of the low-alititude low-speed small-target target information is evaluated; a target defense function and a binding function are established according to the threat level, priority form of confrontation and equipment performance state of the low-alititude low-speed small-target target, and a confrontation attitude scheme is obtained; on the basis of a optimal policy principle, the confrontation attitude scheme is optimized; and visual preview and result management arecarried out on the optimized scheme based on a situation plug-in. According to the management and control method of the low-alititude low-speed small-target aerial target multi-source information fusion, the multi-source information fusion of the aerial low-alititude low-speed small-target target is completed in real time, the multi-party situation visualization display is achieved, and the targetthreat assessment can be quantified; and a plurality of decision-making capabilities are formed, a plurality of action confront schemes are planned, and the full-flow standardization, visualization and automation of the low-alititude safety target defense are realized in real time.
Owner:AEROSPACE SCI & IND MICROELECTRONICS SYST INST CO LTD
Air target sensor management method based on target threat degree
ActiveCN110530424AEasy to useGuaranteed Tracking AccuracyMeasurement devicesTransmissionAir traffic controlInformation gain
The invention discloses an air target sensor management method based on target threat degree. According to the method, after the actual state of the target is measured and obtained, the threat degreeof the target position and the information gain of each sensor on the target measurement are calculated; more sensor resources are required to ensure the tracking precision and the continuous trackingcapability for targets with relatively high threat degree or with abnormal flying tracks; according to the method, the sensor distribution based on threat degree and information gain is achieved, andmore appropriate sensor resources can be distributed to targets with high threat degree according to calculation of multi-target threat degree and information gain, so that the tracking precision ofthe sensor network on a high-threat degree target when multiple targets are tracked is improved, and the sensor network achieves higher use efficiency. The method has great application potential and value in various military and civilian fields such as missile interception, regional target monitoring, air traffic control and the like.
Owner:XI AN JIAOTONG UNIV
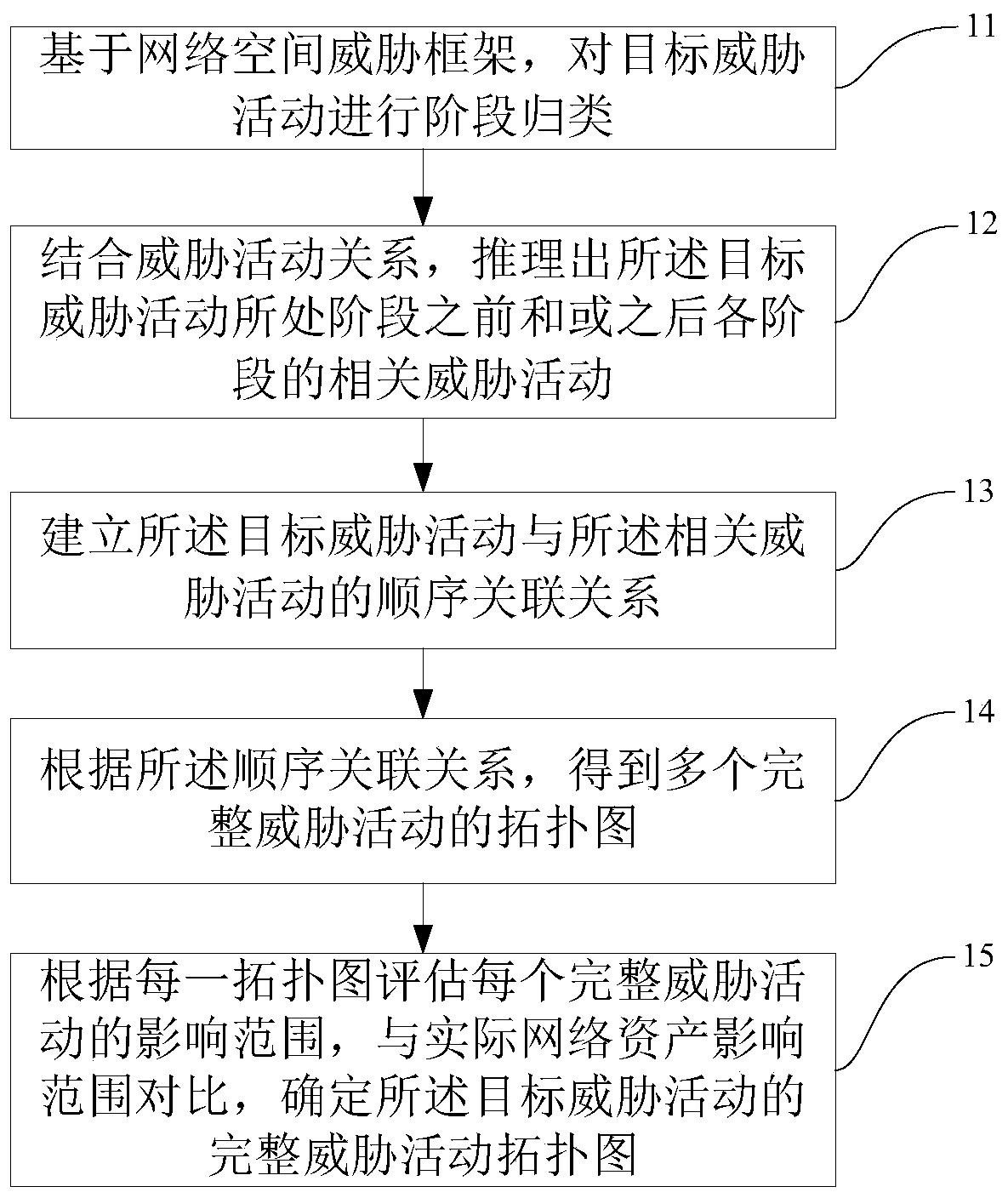
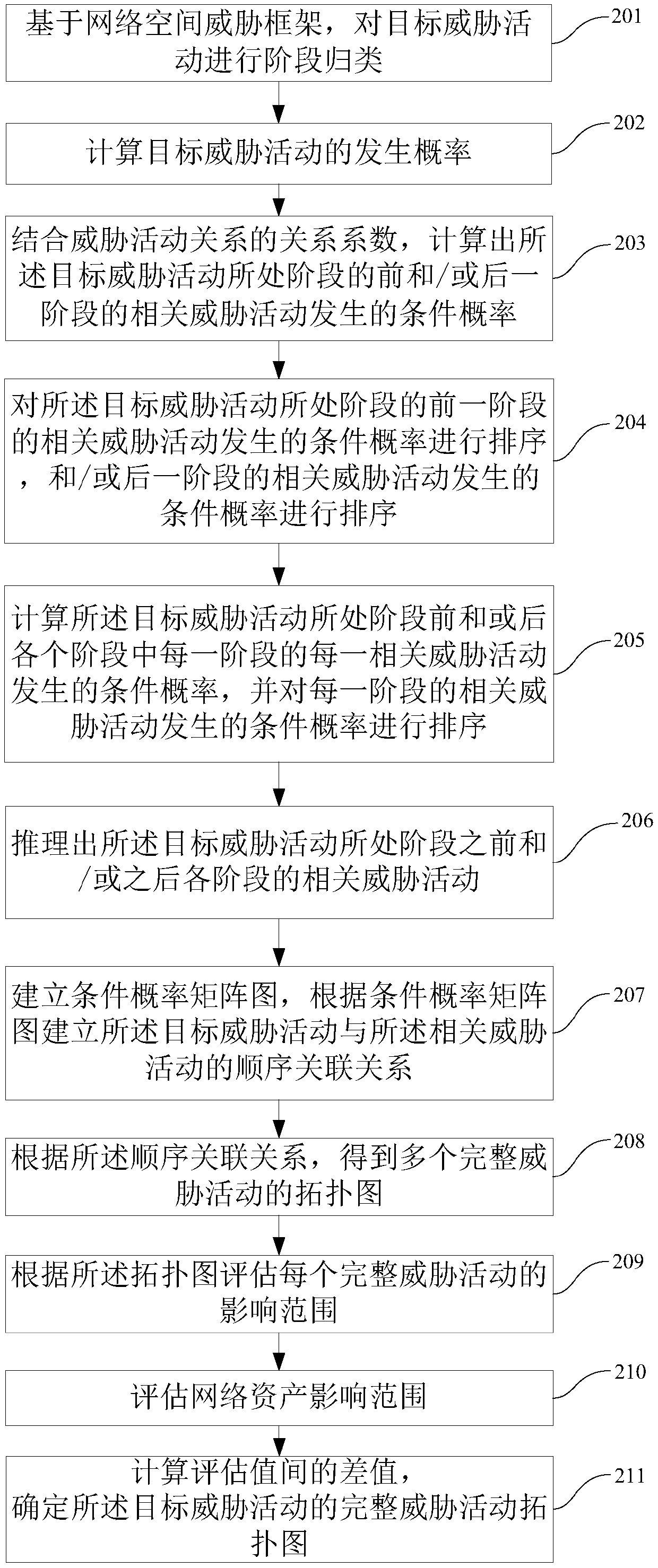
Method and device for establishing threat activity topological graph and storage equipment
The embodiment of the invention discloses a method and a device for establishing a threat activity topological graph and storage equipment. The method and the device are used for solving the problem that the process of threat activity of an attacker cannot be accurately restored due to the fact that analysis on threat activity of a network space stays in fuzzy evaluation based on network assets and an influence range in the prior art. The method comprises the steps of performing stage classification on a target threat activity based on a network space threat framework; in combination with a threat activity relationship, inferring related threat activities of all stages before and / or after the stage where the target threat activity is located; establishing a sequential association relationship between the target threat activity and the related threat activity; obtaining a topological graph of a plurality of complete threatening activities according to the sequential incidence relation;and assessing the influence range of each complete threat activity according to each topological graph, comparing the influence range with the actual network asset influence range, and determining thecomplete threat activity topological graph of the target threat activity.
Owner:HARBIN ANTIY TECH
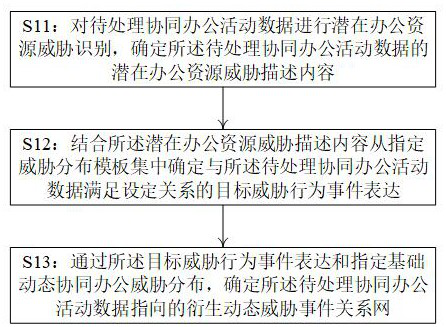
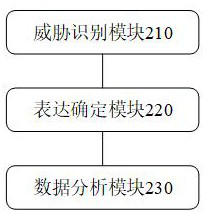
Data processing method and server for coping with cloud computing office threats
ActiveCN114676423AAccurately determineSmall scaleOffice automationPlatform integrity maintainanceEngineeringTargeted threat
According to the data processing method for coping with the cloud computing office threats and the server provided by the invention, when a derivative dynamic threat event relationship network is determined, threat behavior event expressions do not need to be frequently updated, so that the execution complexity is weakened to a certain extent; in combination with the periodic characteristics of the collaborative office staged task description content, the information scale of the specified threat distribution template set determined in advance is relatively small; the data processing server is combined with the potential office resource threat description content of the to-be-processed collaborative office activity data to timely position the target threat behavior event expression from the specified threat distribution template set; and accurately and timely determining a derivative dynamic threat event relationship network which satisfies a set relationship with the to-be-processed collaborative office activity data by means of the target threat behavior event expression and the specified basic collaborative office threat distribution.
Owner:深圳市智联云网科技有限公司
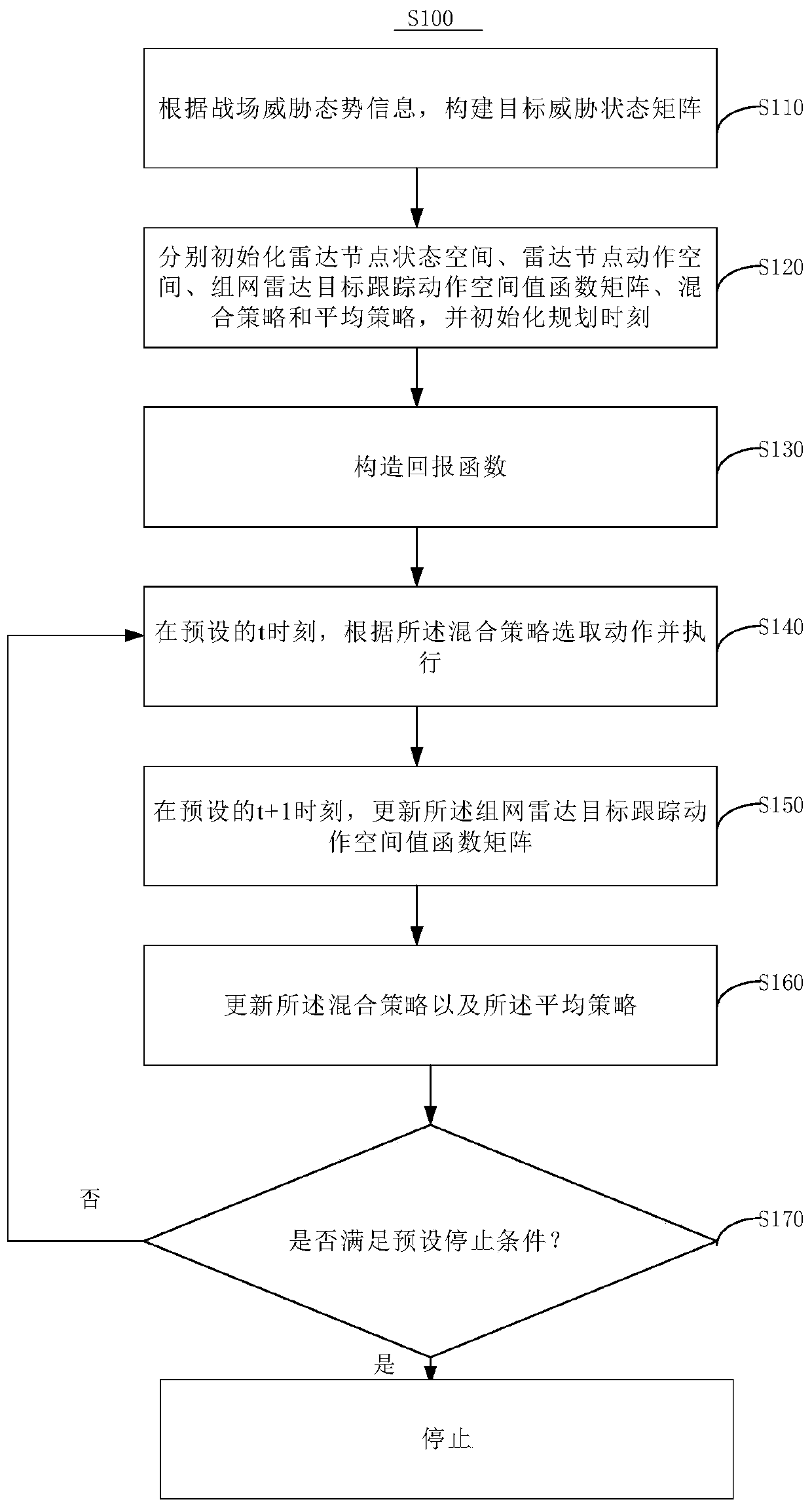
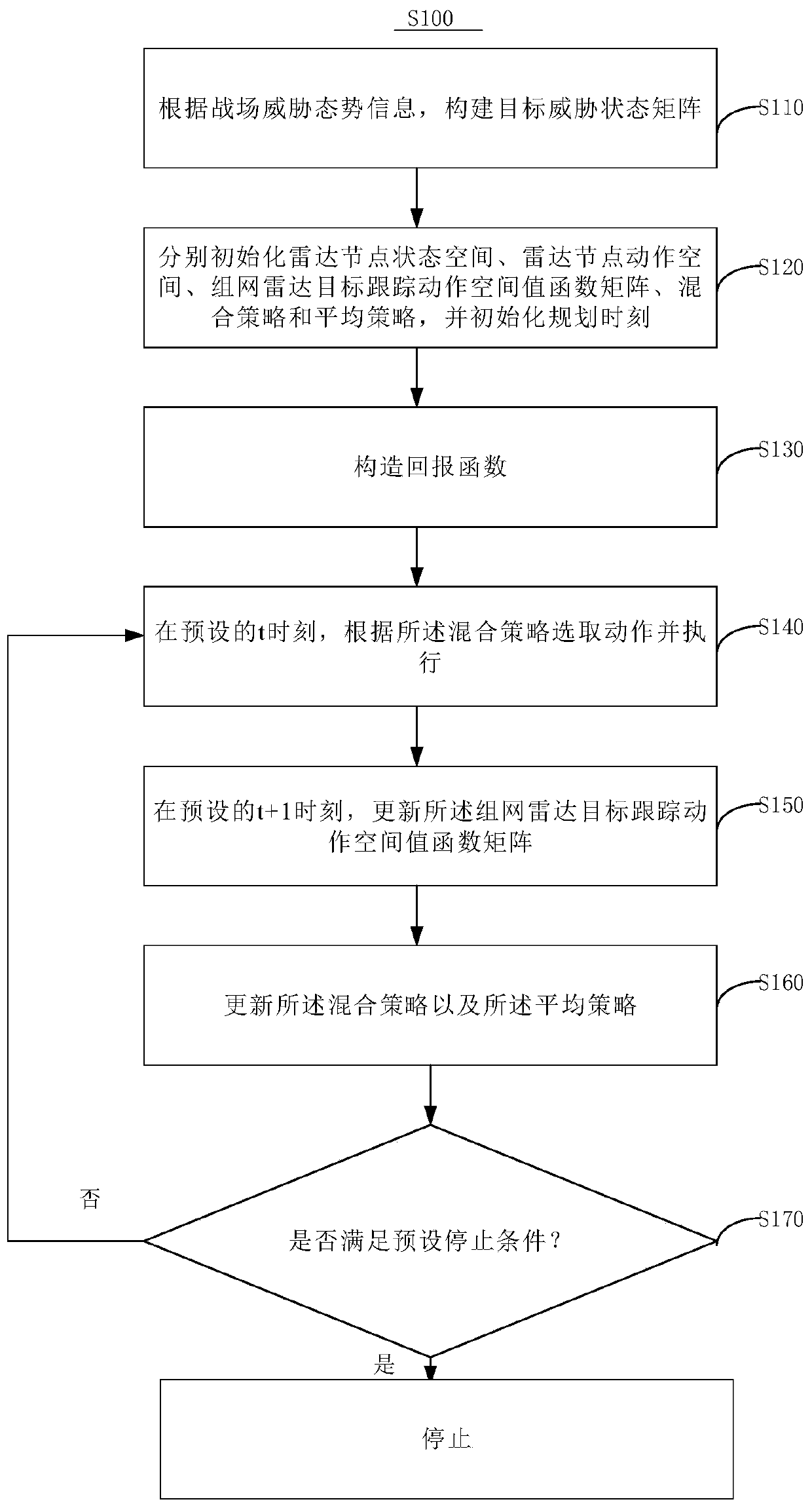
Networked radar resource management and control method and device, and computer readable storage medium
ActiveCN109975800AIncrease autonomyImprove robustnessResource allocationRadio wave reradiation/reflectionRadar systemsState space
The invention discloses a networked radar resource management and control method, a networked radar resource management and control device and a computer readable storage medium. The networked radar resource management and control method comprises the steps of: S110, constructing a target threat state matrix according to battlefield threat situation information; S120, initializing a radar node state space, a radar node action space, a networked radar target tracking action space value functional matrix, a mixed strategy and an average strategy respectively, and initializing a planning moment;S130, constructing a reward function; S140, selecting an action according to the mixed strategy and executing the action at a preset moment t; S150, updating the networked radar target tracking actionspace value functional matrix at a preset moment t+1; S160, updating the mixed strategy and the average strategy; S170, determining whether a preset stopping condition is met, if so, completing networked radar resource management and control, and if not, proceeding to execute the step S140. The networked radar resource management and control method and the networked radar resource management andcontrol device reduce the scale of resource management and control, the radar nodes can autonomously conduct resource management and control decision in a distributed manner, and the autonomy of the networked radar system, the robustness of decision-making and the reliability of the system are improved.
Owner:INFORMATION SCI RES INST OF CETC
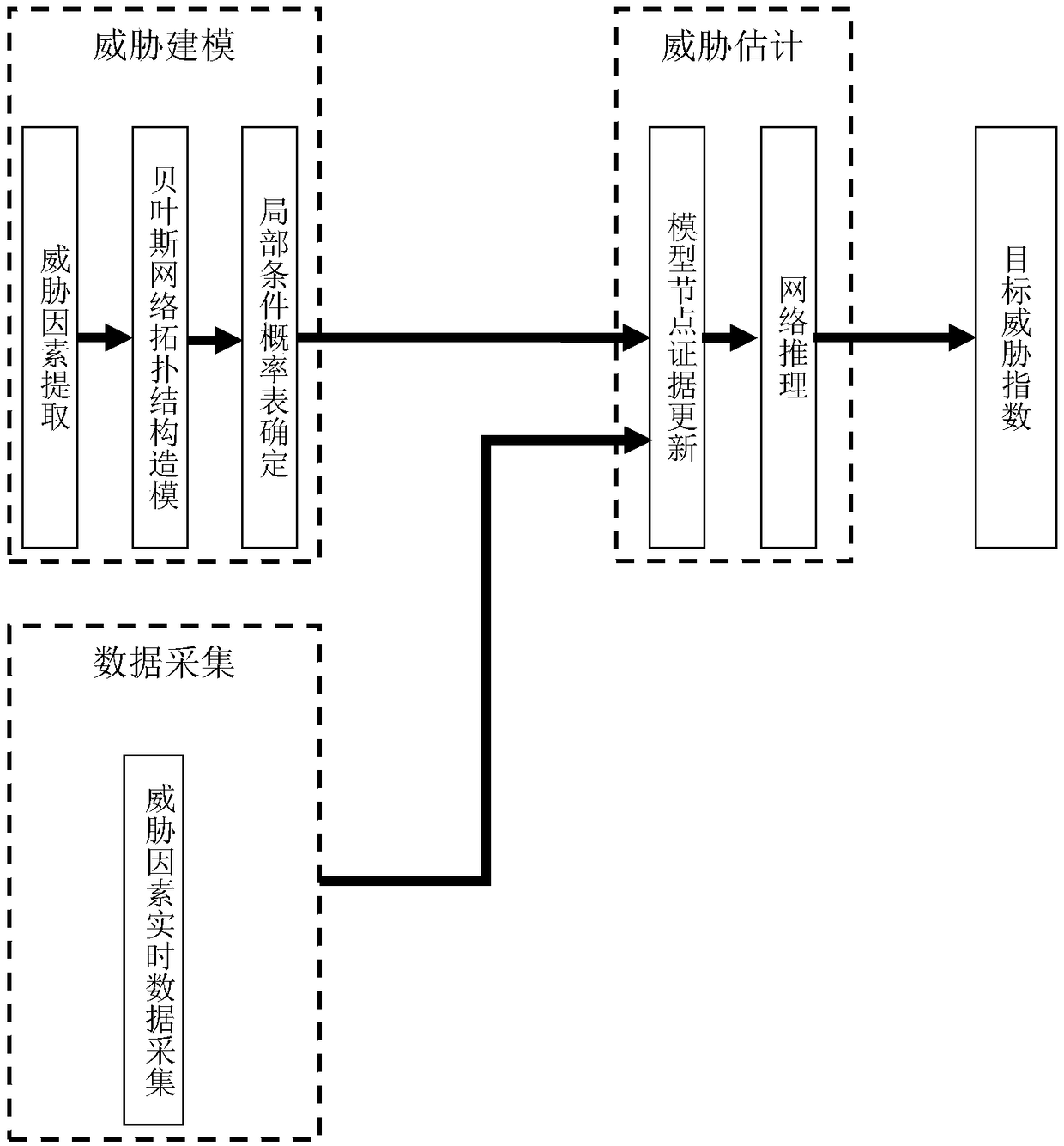
Intelligent vehicle threat estimation system and method based on variable-structure Bayesian network
PendingCN109063940AFully awareEffective cognitionCharacter and pattern recognitionResourcesNODALData acquisition
The invention, which relates to the field of the intelligent vehicle cognitive technology, claims for protection of an intelligent vehicle threat estimation system and method based on a variable-structure Bayesian network thereby evaluating a threat degree of a moving target to a vehicle. The system is composed of a threat modeling module, a data collection module and a threat estimation module. At a threat modeling stage, factors affecting intelligent vehicle threat estimation are determined, wherein the factors include an external environmental factor, a target characteristic factor and a driver factor; a topology of a Bayesian network model is constructed; and then a local condition probability table of the model is determined. During the driving process, the data acquisition module uses sensors to collect real-time data of various influence factors; the threat estimation module reconstructs corresponding variable nodes only for quickly changing factors according to changing rates of all factors to obtain a variable-structure Bayesian network model and then carries out reasoning calculation to obtain a target threat index. Therefore, the performance of intelligent vehicle threatestimation can be improved effectively.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
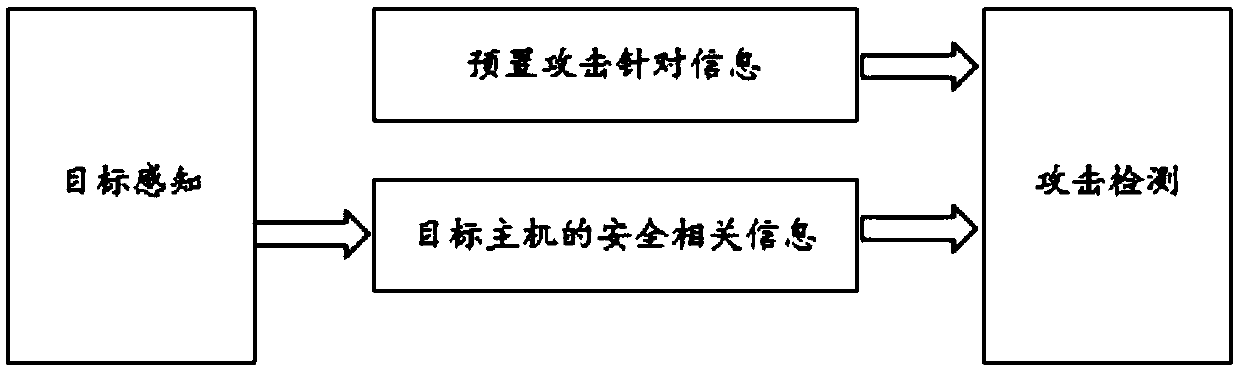
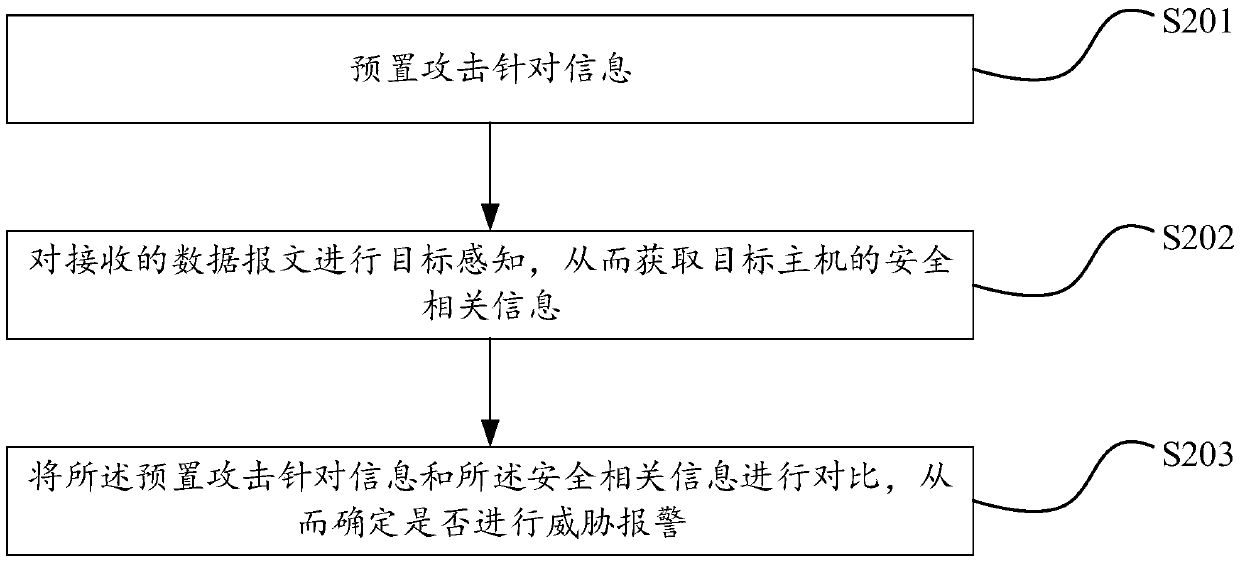
Threat alarm method, device and equipment via target perception
InactiveCN109587120AImprove effectivenessReduce the number of alarmsTransmissionRelevant informationInternet privacy
The invention discloses a threat alarm method, device and equipment via target perception. The method comprises that information aimed at attack is preset; target perception is carried out on a received data message, and security related information of a target host is obtained; and the preset attacked aimed information is compared with the security related information to determine whether to raise threat alarm. The preset attack aimed information is used to senses target threats in the network environment, the attack aimed information is compared with the security related information of target perception, and whether threat alarm is raised is determined according to a comparison result; and thus, alarm is reduced, threat alarm is more effective, possible omission is avoided, a user needsnot to log in the security related information of the protected host manually, instead, possible change of the security related information of the target host is adapted to automatically, and the method is easy to enforce and use and more practical.
Owner:BEIJING TOPSEC NETWORK SECURITY TECH +2
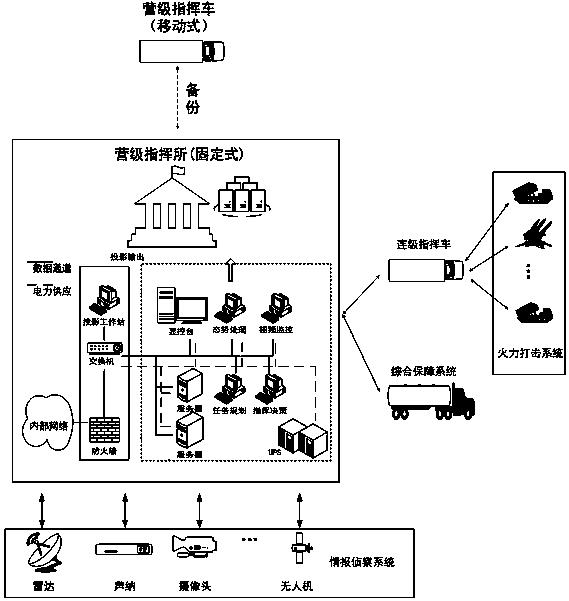
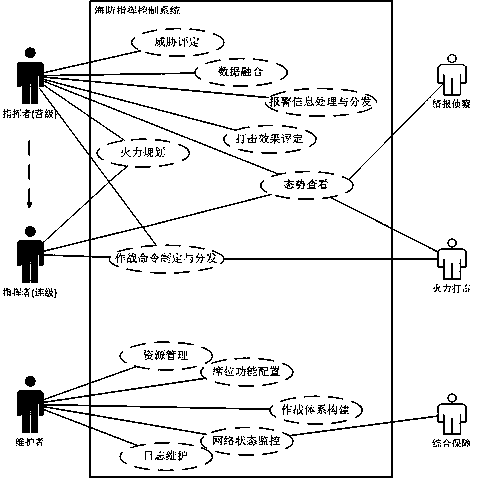
Coastal defense command and control system and method
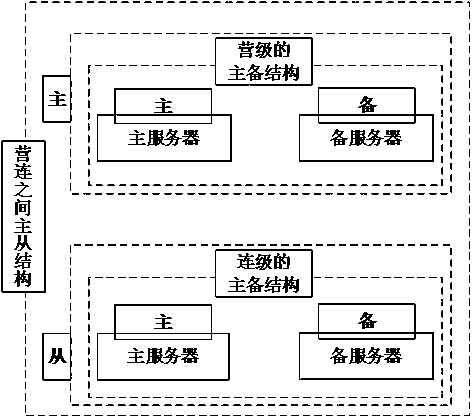
The invention discloses a coastal defense command and control system and method. The coastal defense command and control system comprises a battalion level fixed command post, a battalion level command car, a company level command car, a comprehensive security company, detection equipment and fighting equipment. In peacetime, all kinds of combat units are commanded by the battalion level fixed command post, and the battalion level command car is taken as backup; in wartime, all kinds of combat units are commanded by the battalion level command car; the battalion level fixed command post, the battalion level command car and the company level command vehicle are provided with primary servers and standby servers; a server cluster adopts primary and standby and master and slave architectures;the primary servers are accessed under normal circumstances, when the primary servers fail, the standby servers are started, and the battalion and company command cars constitute master and slave servers, and when the battalion level command car fails, any company level command car can be switched to the battalion level command car. The coastal defense command and control method includes the stepsof data access, data fusion, target threat judgment, alarm information processing and distribution, fire planning, combat order formulation and distribution and strike effect evaluation.
Owner:长沙金信诺防务技术有限公司
Method for judging tuple linguistic model through comprehensive evaluation of target threat level
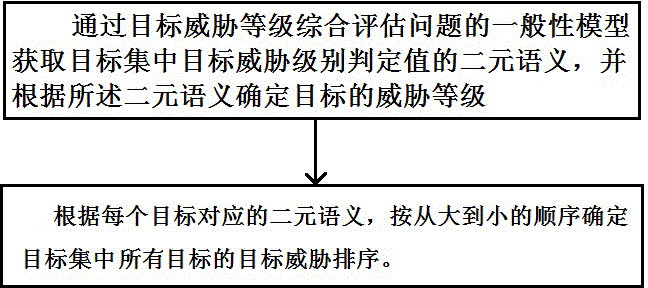
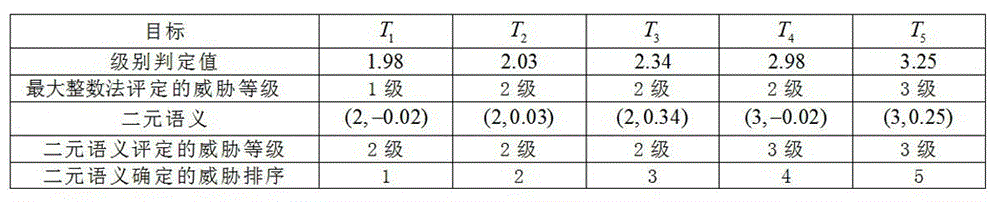
InactiveCN104899450ASure reasonableEasy to implementSpecial data processing applicationsEvaluation resultGuideline
The invention relates to a method for judging a tuple linguistic model through comprehensive evaluation of a target threat level. The method is realized according to the following methods: through uj<[1,h]aT[uj]=(ek, ajk)<Ex[-0.5, 0.5), obtaining a tuple linguistic model (ek, ajk) of a threat level judging value vj of a target Tj in a target set T; according to the tuple linguistic model corresponding to every target, determining the threat level of every target and determining a target threat sequence of all centralized targets according to the order of its tuple linguistic model from big to small. The target thread grade proposed by the invention comprehensively evaluates the grade judging value definition and the tuple linguistic concept, so as to further set up the tuple linguistic judging model and method of the corresponding target threat level comprehensive evaluation, so as to provide theoretical basis for the signifying operation of the target thread level comprehensive evaluation result, facilitate the implementation by computer, and provide the theoretical basis and intelligent support to guide the decision making; moreover, the method can be expanded and applied to multiattribute or rule group classification decision-making issues in economical management, information system management, information security, and other domains.
Owner:FUZHOU UNIV
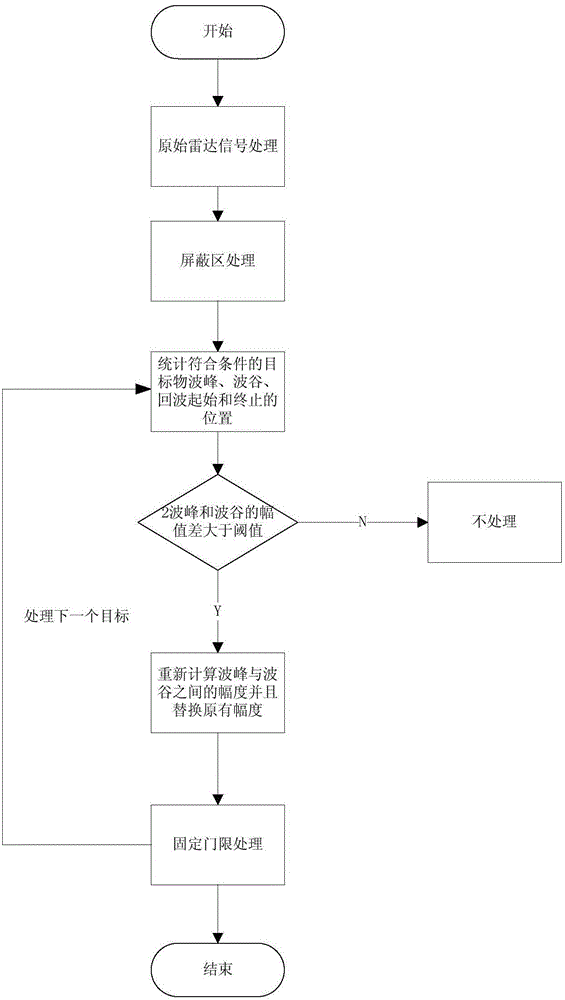
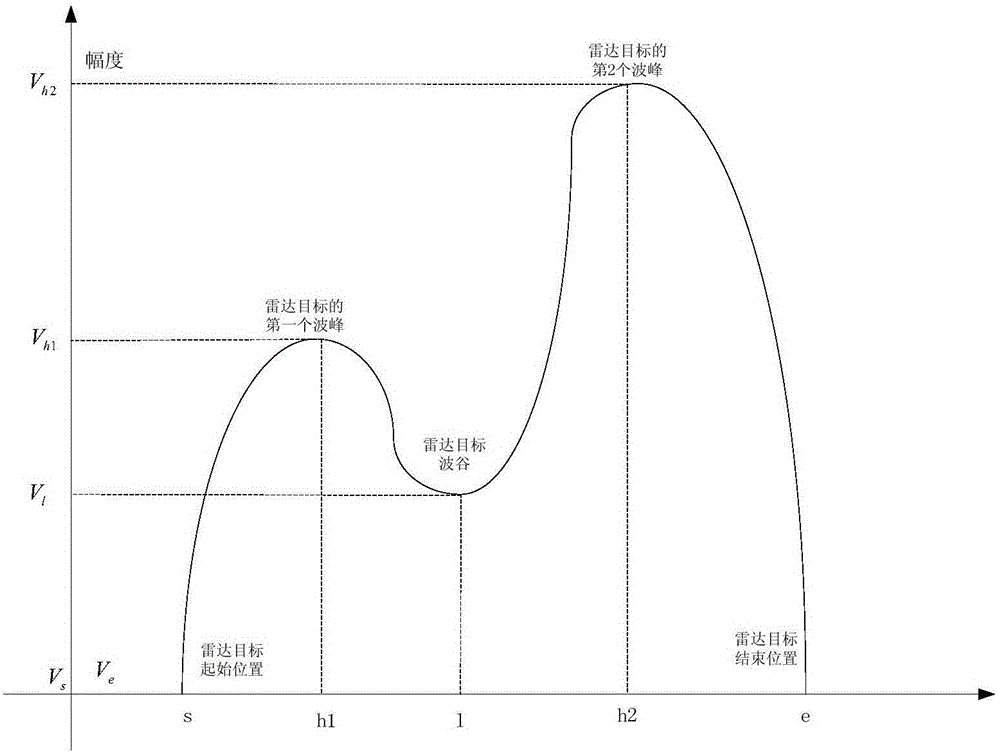
Method for improving VTS radar resolution
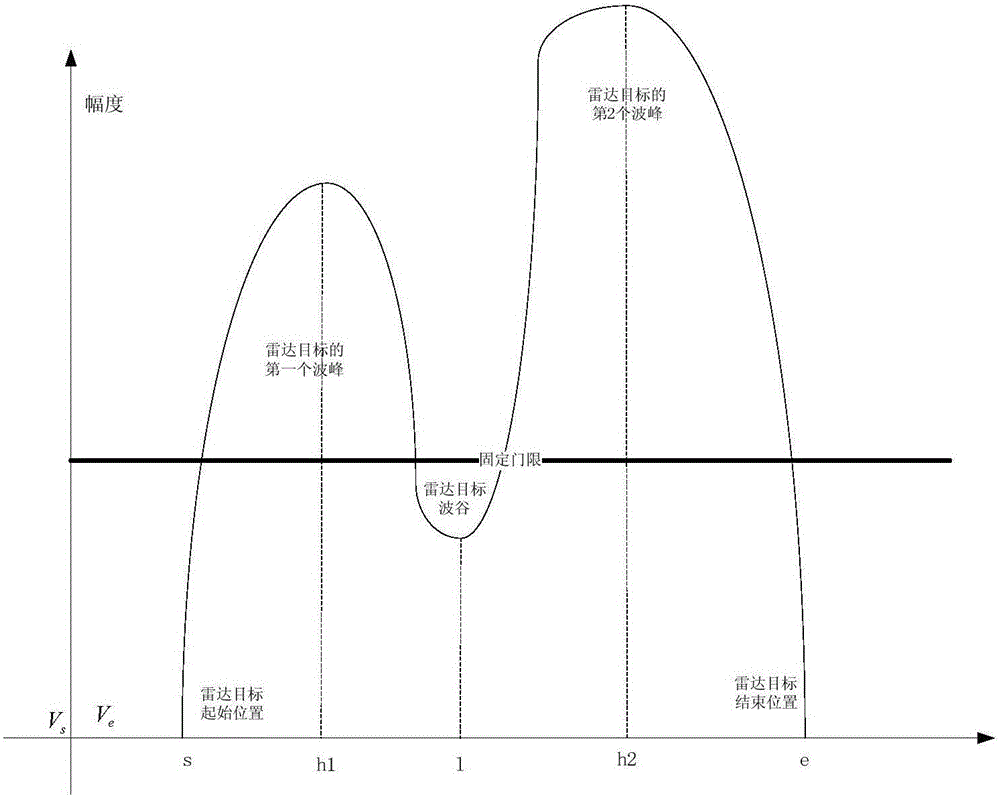
The invention discloses a method for improving VTS radar resolution. The method mainly comprises a step of shielding a radar echo of a non-specially-focused target object; a step of carrying out position finding and recording on two close-range radar targets; a step of calculating amplitude difference between a wave crest and a wave valley; a step of amplifying wave crest amplitude; a step of carrying out pixel amplitude recalculation and substitution; and a step of setting a fixed threshold and the like. Through the method above, when the distance between the two targets is very close, the radar resolution is improved by amplifying the wave crest amplitude of the target object and through a method of filtering an adhesion part echo by utilizing the fixed threshold, so that limit of hardware of the radar itself can be broken through, target object identification capability is improved, and supervision intensity is improved. The method can be applied to the fields of vessel traffic supervision, custom anti-smuggling, coast guard warning, marine fishery and marine environmental protection and the like; and besides, the method has realistic significance in judging target threat level and ship moving posture and the like under a battle condition.
Owner:中船鹏力(南京)大气海洋信息系统有限公司 +3
Work mode deciding method for integrated RF system of unmanned platform
ActiveCN109946687AAvoid demandSimplify reasoningRadio wave reradiation/reflectionDecision-making softwareControl engineering
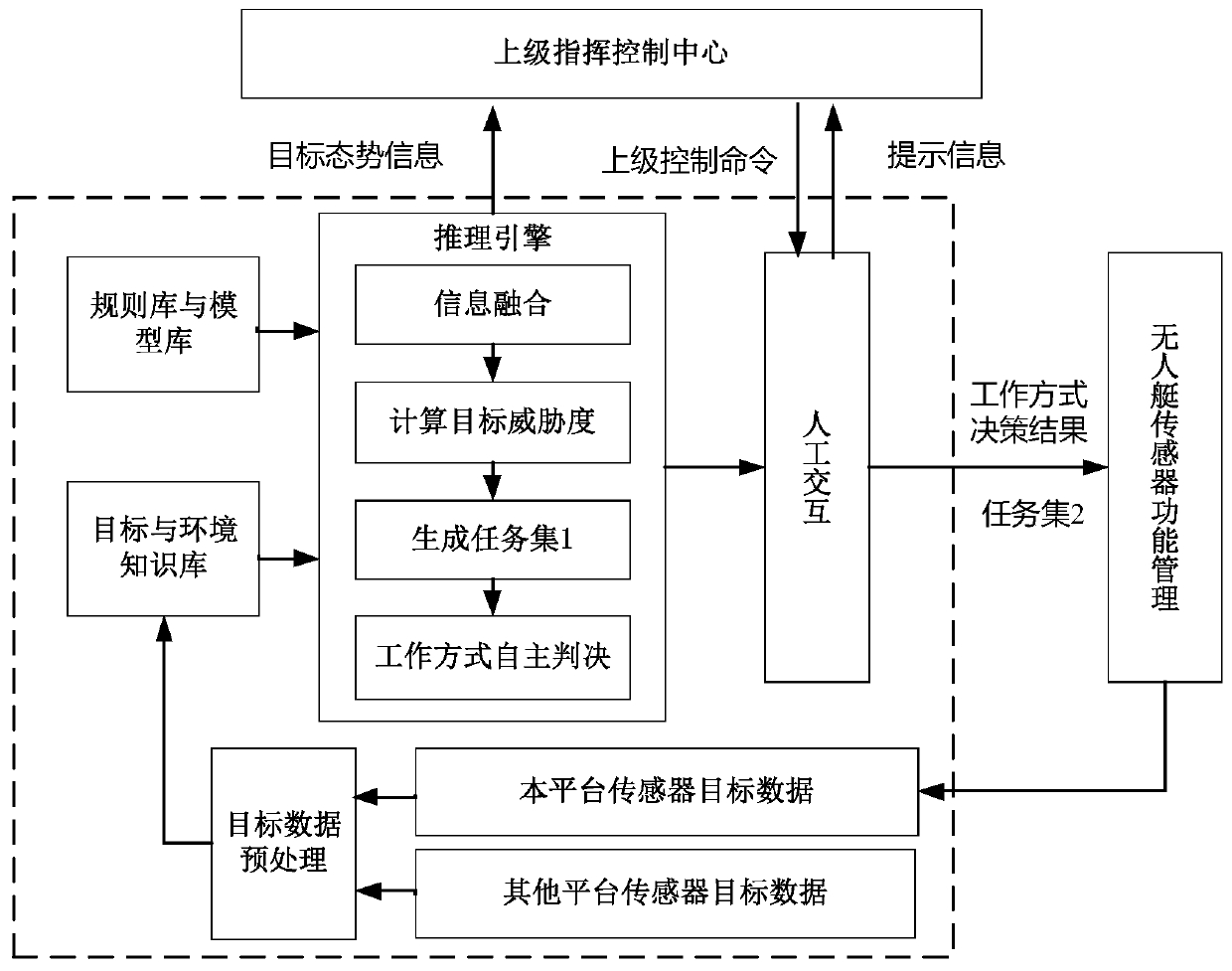
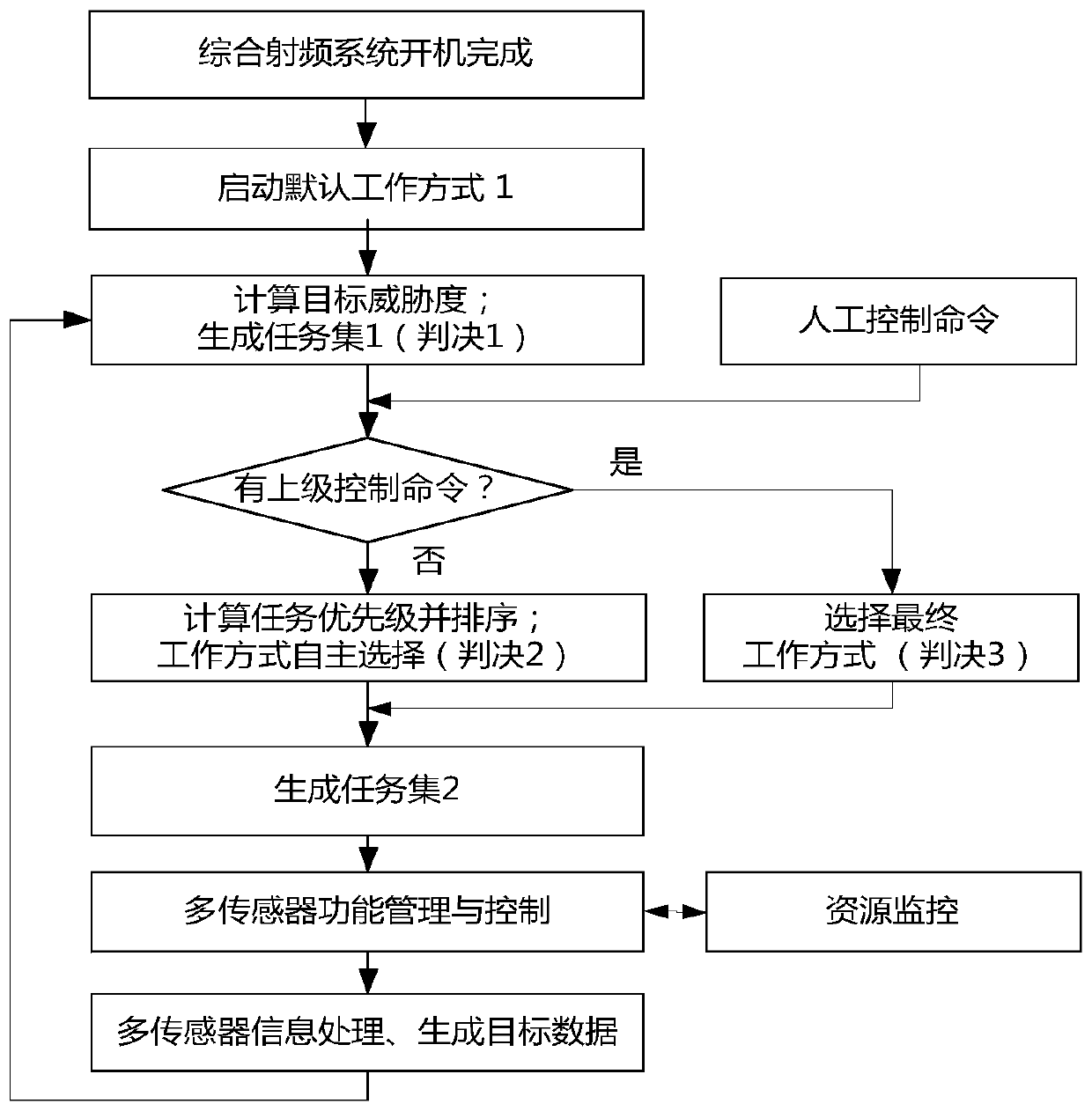
The invention relates to a work mode deciding method for an integrated RF system of an unmanned platform. To meet the demand for work mode decision in present use of the unmanned platform, a typical inference parameter model including an artificial intervention and computer decision support decision software function configuration, a work flow, a target threat degree and a task priority is designed. According to the method, information of a target and environment knowledge library, real-time collection data and sensor using rules is used, a structured inference engine with fewer hierarchies isused for autonomous decision of the integrated RF system in the unmanned-on-duty state, the real-time and light-weight demands of the system are met while functions are ensured, and the requirement for establishing the unmanned platform is satisfied.
Owner:THE 724TH RES INST OF CHINA SHIPBUILDING IND
Weapon platform, anti-frogman weapon system with weapon platform and operation method
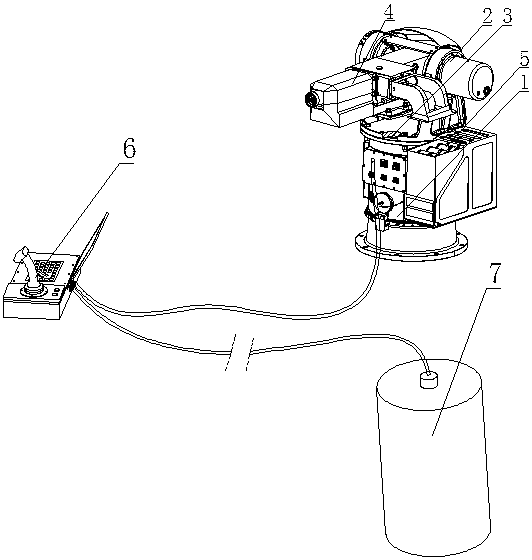
ActiveCN109029123AAdjust direction angleAdjust pitch angleDefence devicesLaunching weaponsSonarInformation processing
The invention discloses a weapon platform, an anti-frogman weapon system with the weapon platform and an operation method. The anti-frogman weapon system comprises a portable fire control box (6), a weapon station and a detection sonar (7). The weapon station comprises a planar rotating mechanism (1), a pitching mechanism (2), a first sealing ring (3), an automatic grenade launcher (4), a cartridge box assembly (5), a main control board, and a motor driver. The operation process includes the following steps that the detection sonar (7) performs real-time monitoring, target identification and tracking, and after it is found that a target invades a defense area, the detection sonar (7) sends out alarm information; detected target data are sent to a fire control computer of the portable firecontrol box (6) through a communication cable; the fire control computer receives target information sent by the detection sonar (7), the target information processing is completed, and the processedtarget information is displayed on a display in real time; and according to movement information of the target, the target threat analysis is carried out, and the system enters into a combat operationmode.
Owner:长沙金信诺防务技术有限公司 +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com