Threat alarm method, device and equipment via target perception
A target and target host technology, applied in the field of network security, can solve the problems of not knowing the security-related information of the protected host, not knowing the protected host, misjudgment and omission, etc., to achieve easy implementation and use, reduce the number of alarms, and improve effect of effectiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
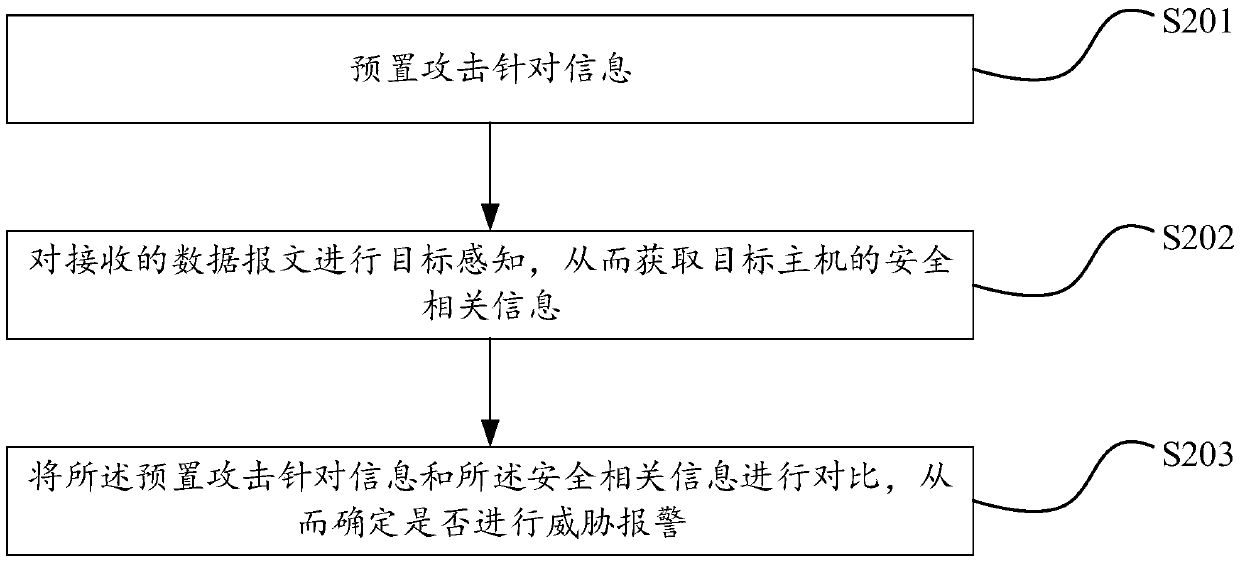
[0059] The embodiment of the present invention provides a method for threat alarm through target perception, such as figure 2 shown, including:
[0060] Step S201: preset attack target information;
[0061] Attack detection devices or systems are usually preset with a large number of known threat fingerprints to discover attack events. For each threat, there is usually descriptive text information, such as threat name, detailed description, risk level, target system, workarounds and more. However, these text messages only help users recognize threats and guide defense measures, and have no technical significance for detection itself.
[0062] The preset attack-targeted information is to reorganize the applicable environment and target for each threat, and define and solidify it with a program-identifiable information structure, so that this information can be used for attack detection. The preset attack targeting information and the preset threat fingerprint feature are up...
Embodiment 2
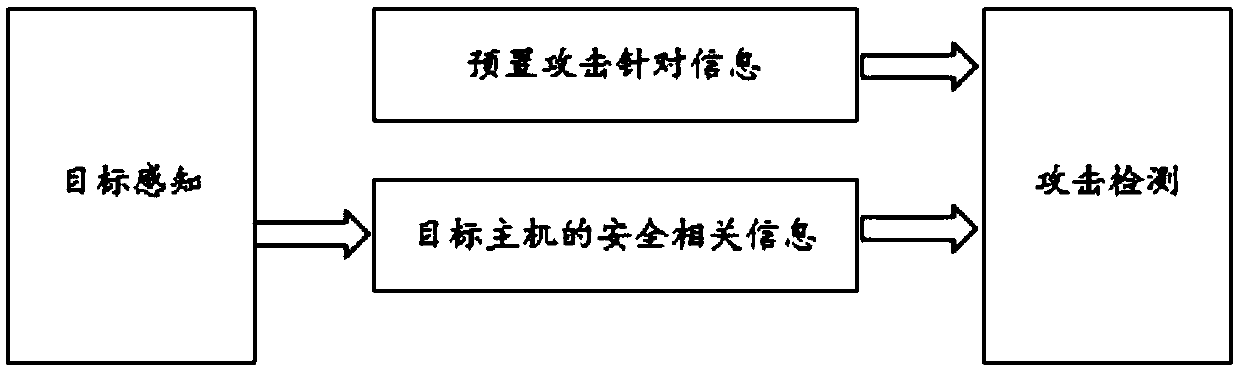
[0121] The implementation of the present invention provides a device for threat alarm through target perception, such as Figure 8 shown, including:
[0122] Presetting module 801: used to preset attack target information;
[0123] Perception module 802: used to perform target perception on the received data message, so as to obtain security-related information of the target host;
[0124] Comparison module 803: used to compare the preset attack target information with the security-related information, so as to determine whether to issue a threat alarm.
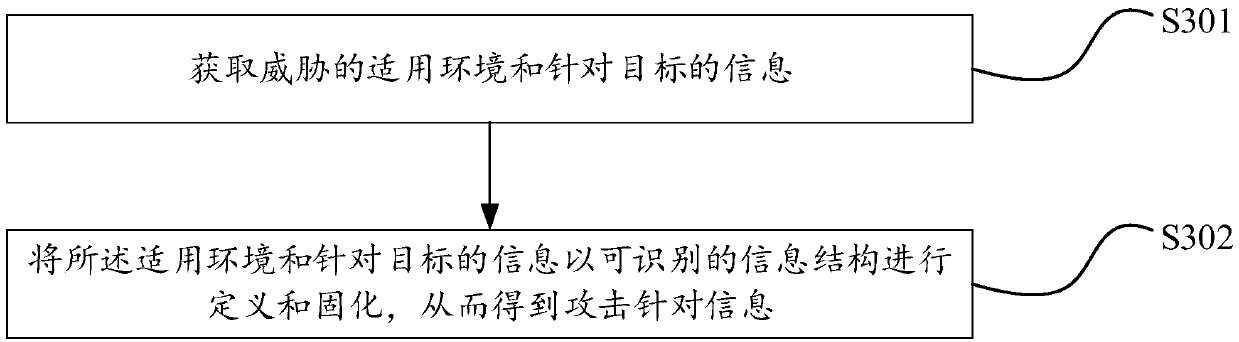
[0125] As a specific implementation of the present invention, as Figure 9 As shown, the preset module 801 includes:
[0126] Information acquisition module 901: used to acquire the applicable environment of the threat and information on the target;
[0127] Definition module 902: used to define and solidify the applicable environment and target-targeted information in an identifiable information structure, so as to obtai...
Embodiment 3
[0153] An embodiment of the present invention provides an electronic device, the electronic device includes: a memory, a processor, and a computer program stored on the memory and executable on the processor, the computer program being executed by the processor When executed, the method steps of Embodiment 1 are implemented.
[0154] The processor may be a general-purpose processor, such as a central processing unit (Central Processing Unit, CPU), or a digital signal processor (Digital Signal Processor, DSP), an application specific integrated circuit (Application Specific Integrated Circuit, ASIC), or configured form one or more integrated circuits implementing embodiments of the invention. Wherein, the memory is used for storing executable instructions of the processor; the memory is used for storing program codes and transmitting the program codes to the processor. The memory may include volatile memory (Volatile Memory), such as random access memory (Random Access Memory,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com