A unified accusation method and system for network security equipment
A security device and network security technology, applied in the field of network security, can solve the problems of lack of collaborative defense of LAN, single network defense, network threat intelligence and defense strategies cannot be better utilized, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The present invention will be further described below in conjunction with the accompanying drawings.
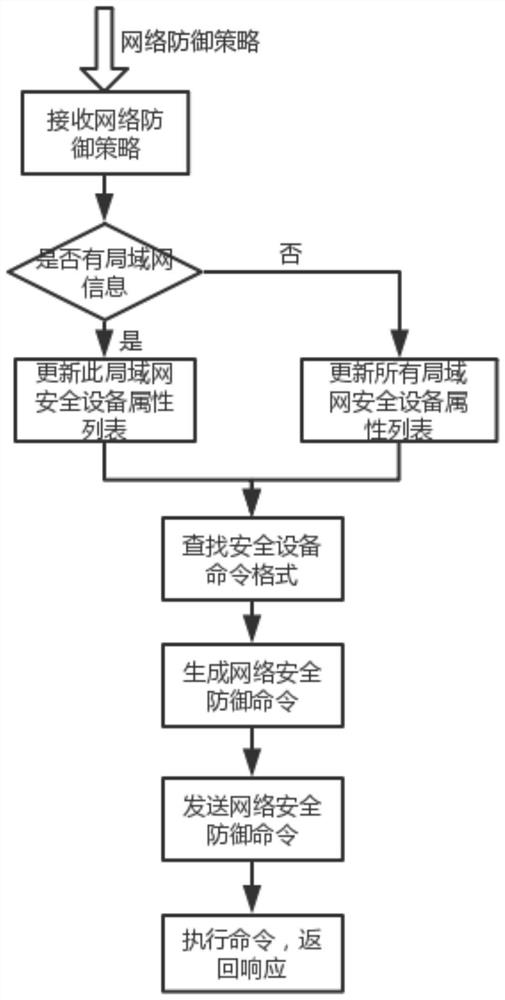
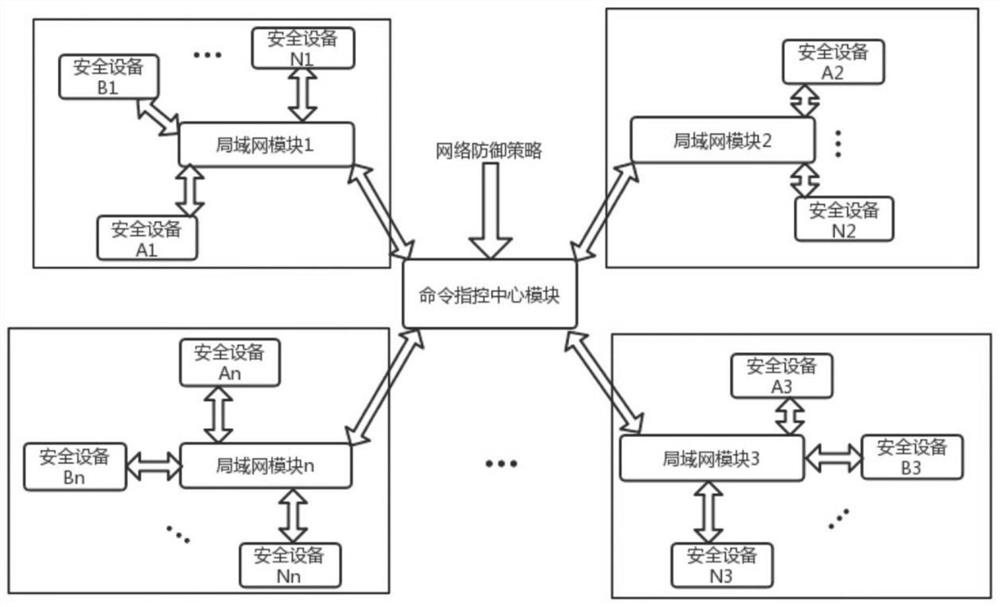
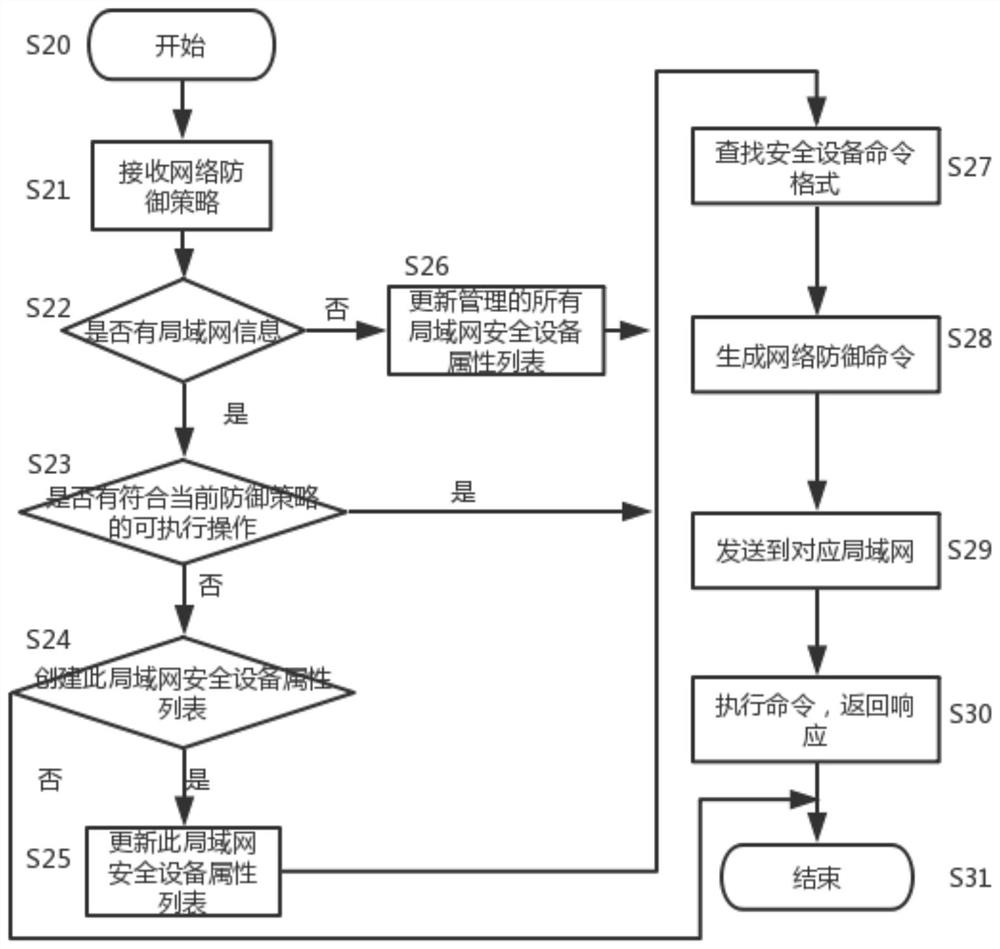
[0026] The invention discloses a unified accusation method and system for network security equipment, and relates to the technical field of network security. The method includes, according to the network defense strategy formed by the network threat intelligence, if the network defense strategy includes LAN information, ordering the command and control center to send a request to the LAN manager, updating the attribute list of the LAN security device, and generating a network defense command, and It is sent to the LAN security device; if the network defense strategy does not contain LAN information, the command center will send a request to all LAN managers, update the property list of all managed LAN security devices, and generate a network defense command, and send it to all For the same type of security equipment, the final LAN security equipment executes the networ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com