A network attack defense method based on system events
A system event and network attack technology, applied in the field of defense against remote vulnerability exploit attacks, can solve the problems of slow detection speed, high false negative rate, encryption, obfuscation and other problems of intrusion detection methods, and achieve good scalability and flexibility, The effect of good compatibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
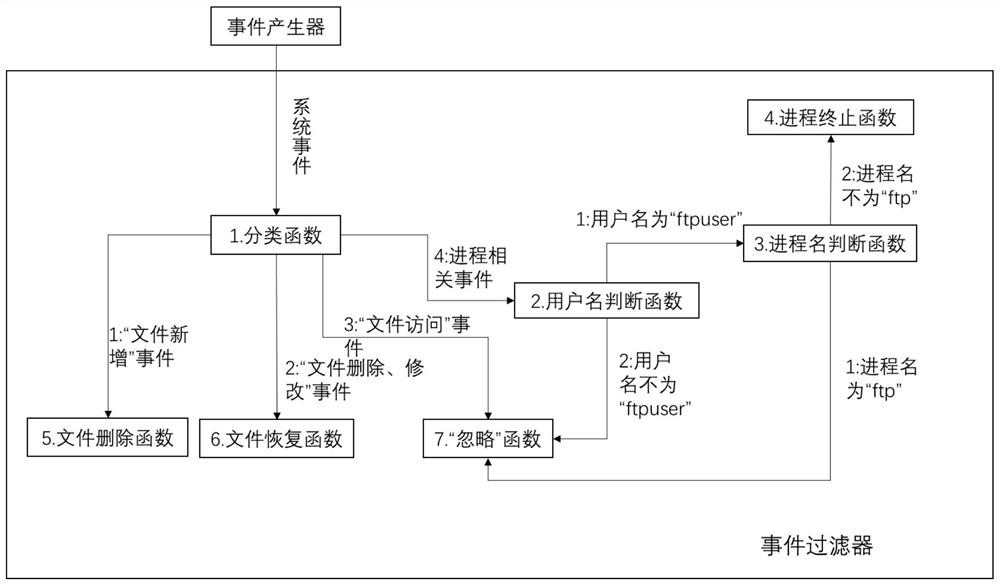
[0053] In order to make those skilled in the art better understand the technical scheme of the present invention, take the FTP service in the Linux operating system protected by the present invention as an example. Run for the user of "ftpuser", only use the folder whose path is " / var / ftp / ", and there is only a file named "test" under this folder. The present invention will be further described in detail below in conjunction with the accompanying drawings.
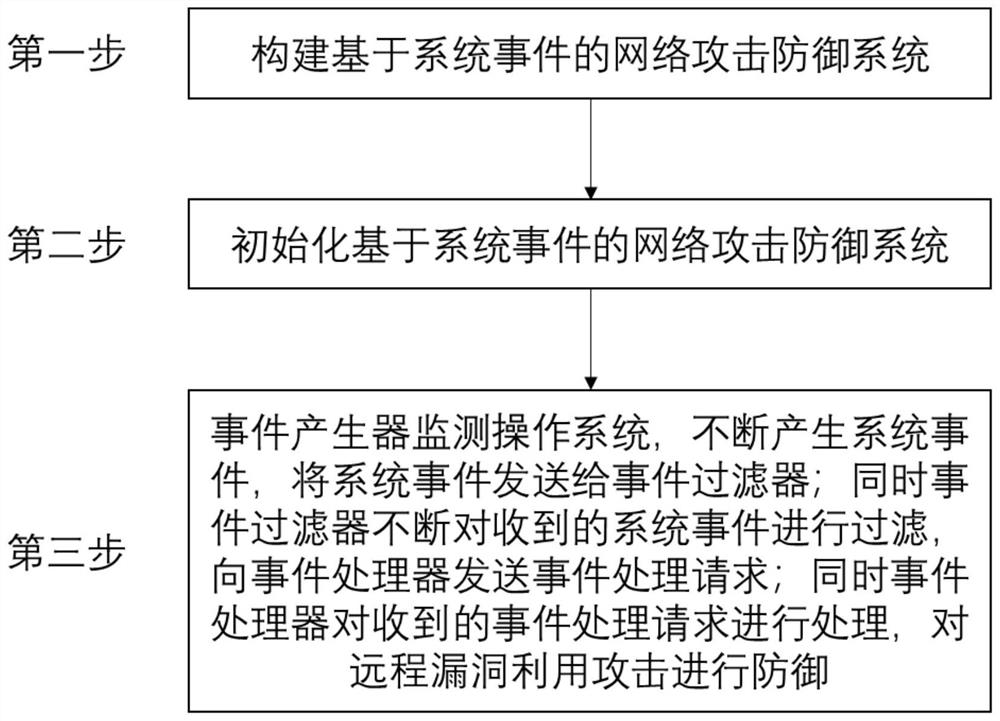
[0054] like figure 2 Shown, the present invention comprises the steps:
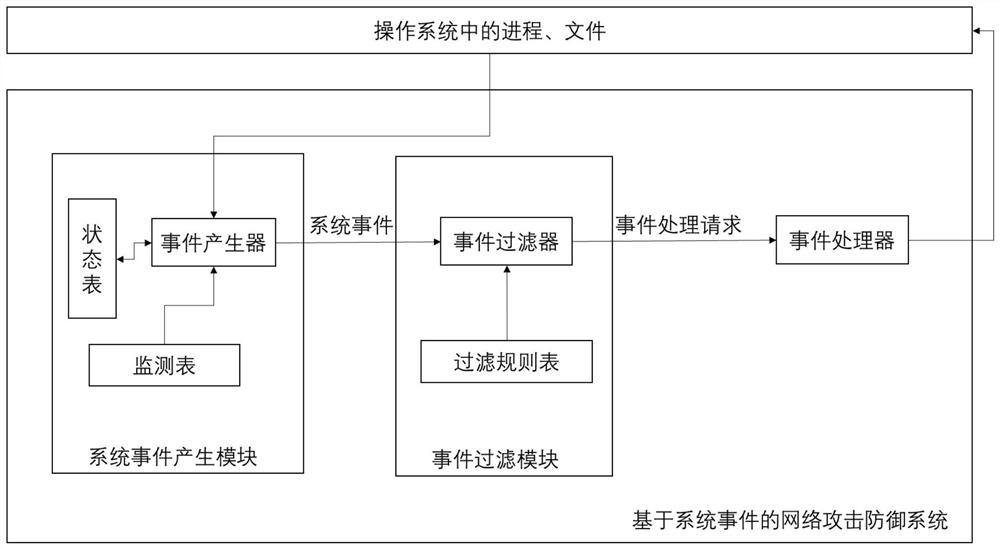
[0055] The first step is to build a network attack defense system based on system events. The system as figure 1 As shown, it consists of system event generation module, event filter module and event processor. The system event generation module is connected with the event filtering module and the operating system, and the system event generation module monitors key changes in the operating system (including the addition, deletion, access, and mod...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com