A Network Threat Intelligence Sharing Model
An intelligence and network technology, applied in the field of cyber threat intelligence sharing model, can solve problems such as low sharing efficiency, low intelligence sharing efficiency, lack of unified norms, etc. effect of ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
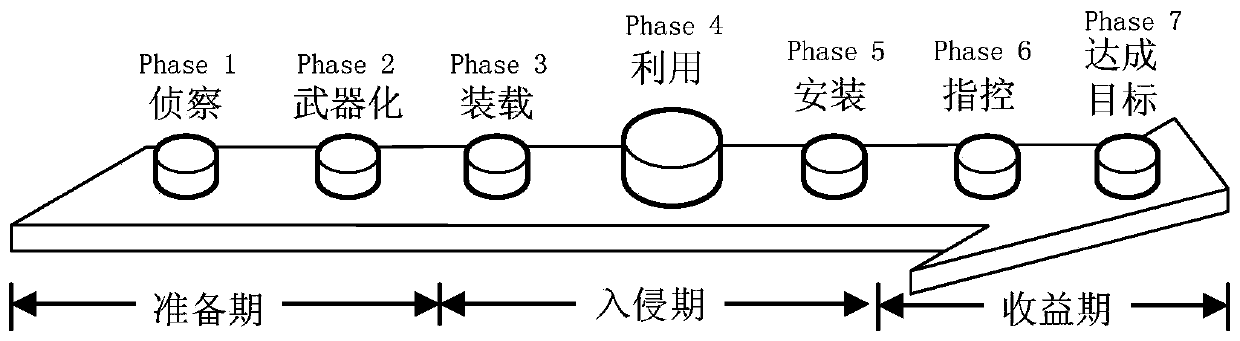
[0019] A typical network attack process is as follows: figure 1 As shown, it generally includes the preparation period, the invasion period and the benefit period, which are subdivided into the following seven stages:
[0020] (1) Two phases of the preparation period:
[0021] Phase 1—Reconnaissance: The attacker studies, identifies and selects the target. Typical methods include using Internet crawlers to collect information such as meeting minutes, email addresses, social relations, or using special methods to collect information;
[0022] Stage 2—Weaponization: The attacker uses automated tools to modify the remote Trojan horse containing vulnerabilities and implants it into a specific carrier, such as data file formats such as PDF or office commonly used by clients;
[0023] (2) Three phases of the invasion period:
[0024] Phase 3—Loading: Transfer of the weaponized vehicle into the target environment. According to the Lockheed-Martin Computer Incident Response Team (L...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com