Transaction promotion method of threat intelligence transaction alliance chain based on benefit distribution
A benefit distribution and transaction technology, applied in the direction of database distribution/replication, structured data retrieval, transmission system, etc., can solve the problem of low participation enthusiasm of nodes, and achieve the effect of promoting healthy development
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be further described below in conjunction with the accompanying drawings.
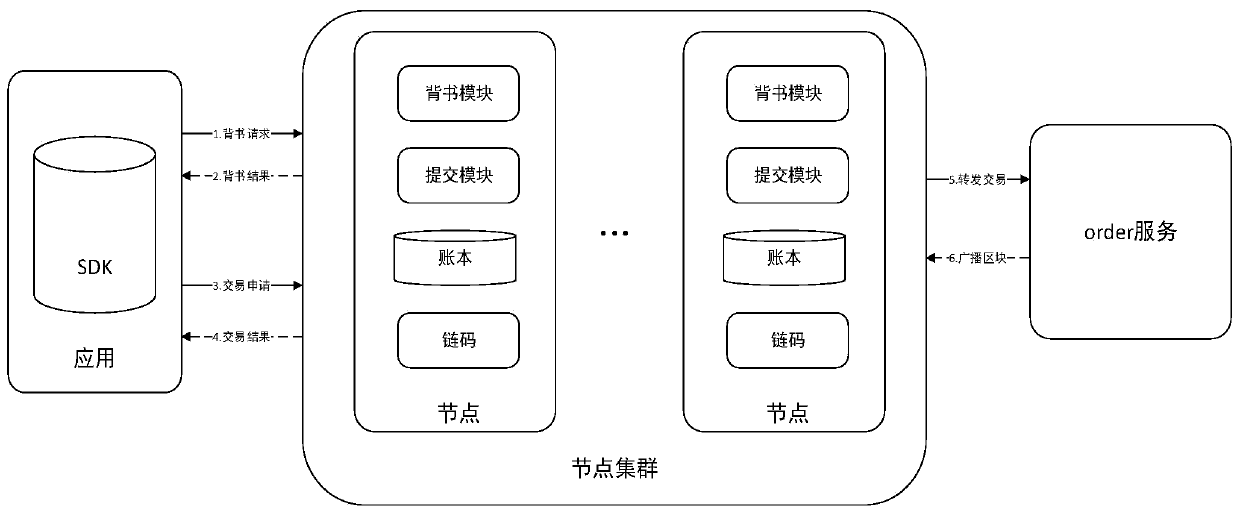
[0030] The present invention proposes a transaction promotion method of a threat intelligence transaction alliance chain based on benefit distribution, and the specific steps are as follows:
[0031] (1) Fragment formation and master node election phase processing method: each node determines the shard to which it belongs, and then uses the voting mechanism to elect the master node in this shard.
[0032] (2) Processing method for initiating a transaction and determining the number of transactions: At the beginning of the transaction cycle, the transaction initiation node creates and initiates the transaction, and the transaction application is sent to all shard master nodes.
[0033] (3) Determine the list of cooperative nodes and the processing method of the threshold stage: each node in the shard is verified, and initially decides whether to participate in the trans...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com