Service safety analysis method and system thereof
A security analysis and business technology, applied in transmission systems, digital transmission systems, electrical components, etc., can solve problems such as high cost, inability to effectively detect internal network security threats, and inability to cope with large-scale network data traffic
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] In order to facilitate the understanding of those skilled in the art, the present invention will be further described below in conjunction with the accompanying drawings, which cannot be used to limit the protection scope of the present invention.
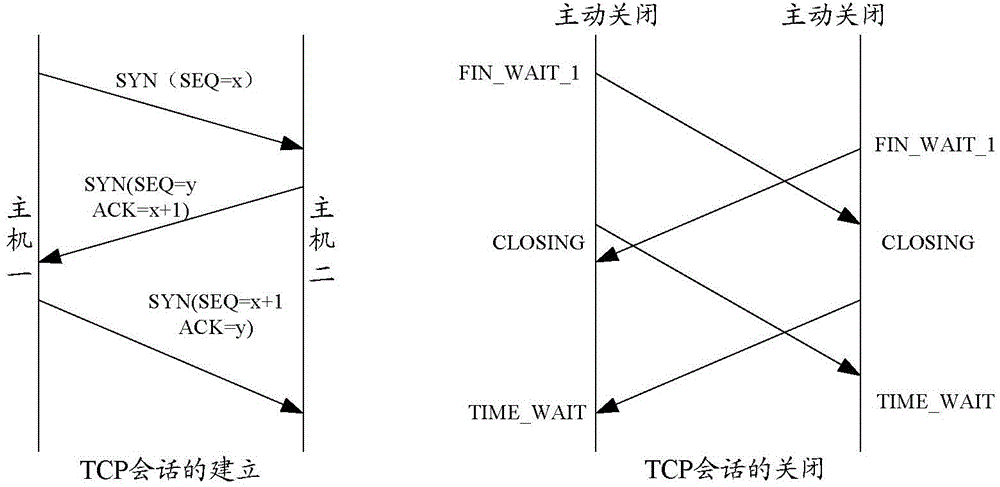
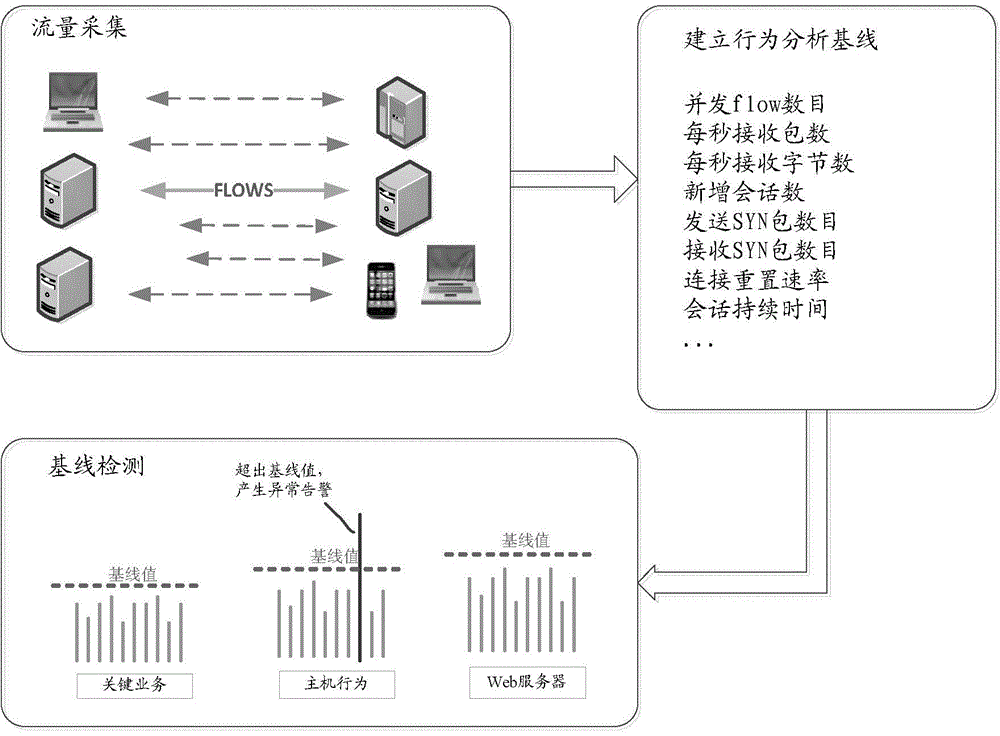
[0050] Aiming at many deficiencies in threat detection of traditional security detection equipment such as firewalls and intrusion detection systems (IDS), security analysis technology based on network flow Netflow technology, combined with big data statistics, anomaly detection and other technologies, can provide more timely effective solution.
[0051] Netflow technology was first invented by Cisco in 1996. It is applied to Cisco routers and switches to record end-to-end access information. It is a technical means to analyze and measure the characteristics of IP data flows passing through network devices.
[0052] However, the traditional Netflow technology based on Cisco's patent is usually applied to network performance ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com