A kind of authentication method of RFID system
An authentication method and authentication failure technology, applied in transmission systems, digital transmission systems, user identity/authority verification, etc., can solve the problems of not providing resistance to denial-of-service attacks, blocking, and legal labels cannot be authenticated, and achieve resistance to denial-of-service attacks. effect of attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
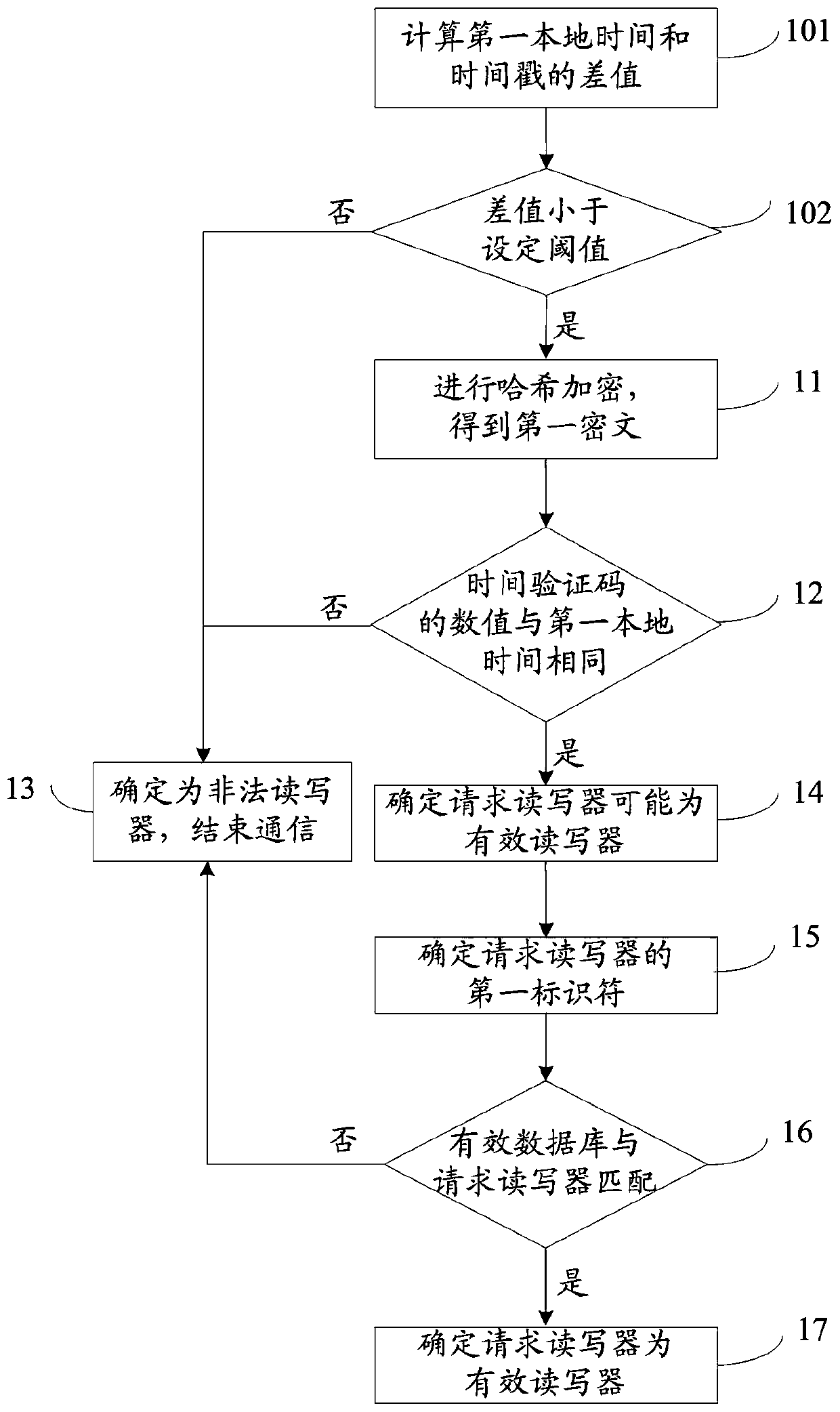
[0069] Such as figure 1 As shown, when the database is an effective database, the authentication methods of the RFID system include:
[0070] Step 11: After receiving the query message sent by the requesting reader, the valid database uses a hash function to perform hash encryption on the string including the timestamp and the first local time of the valid database to obtain the first ciphertext, and convert the first ciphertext to A ciphertext is sent to a valid reader-writer, wherein the requesting reader-writer is divided into a valid reader-writer and an illegal reader-writer. In this embodiment, the timestamp is the second local time read by the requesting reader-writer;
[0071] Step 12: The valid database judges whether the requesting reader has passed the preliminary authentication according to the value of the time verification code sent by the requesting reader and the first local time:
[0072] Step 13: If the value of the time verification code is different from t...
Embodiment 2
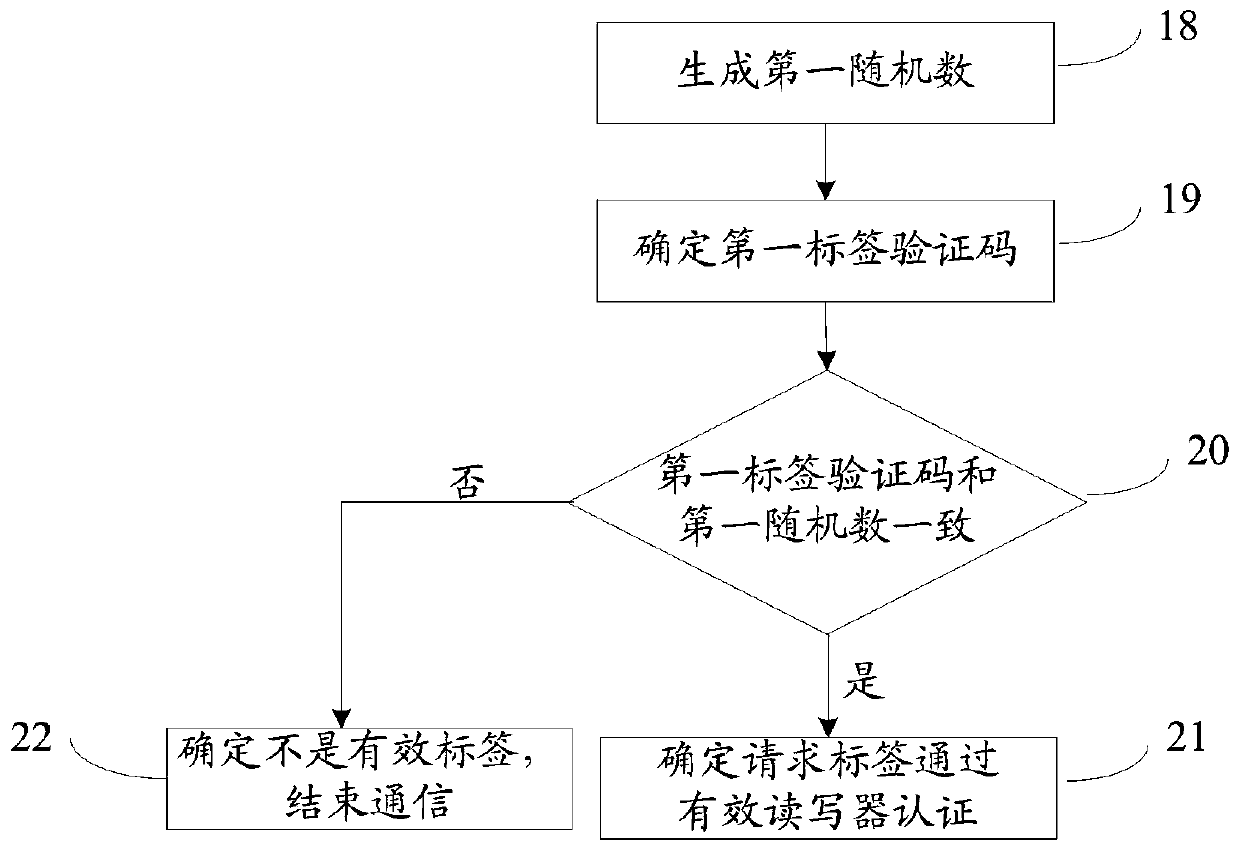
[0124] Such as Figure 6 As shown, when the reader-writer is a valid reader-writer, the authentication method also includes:
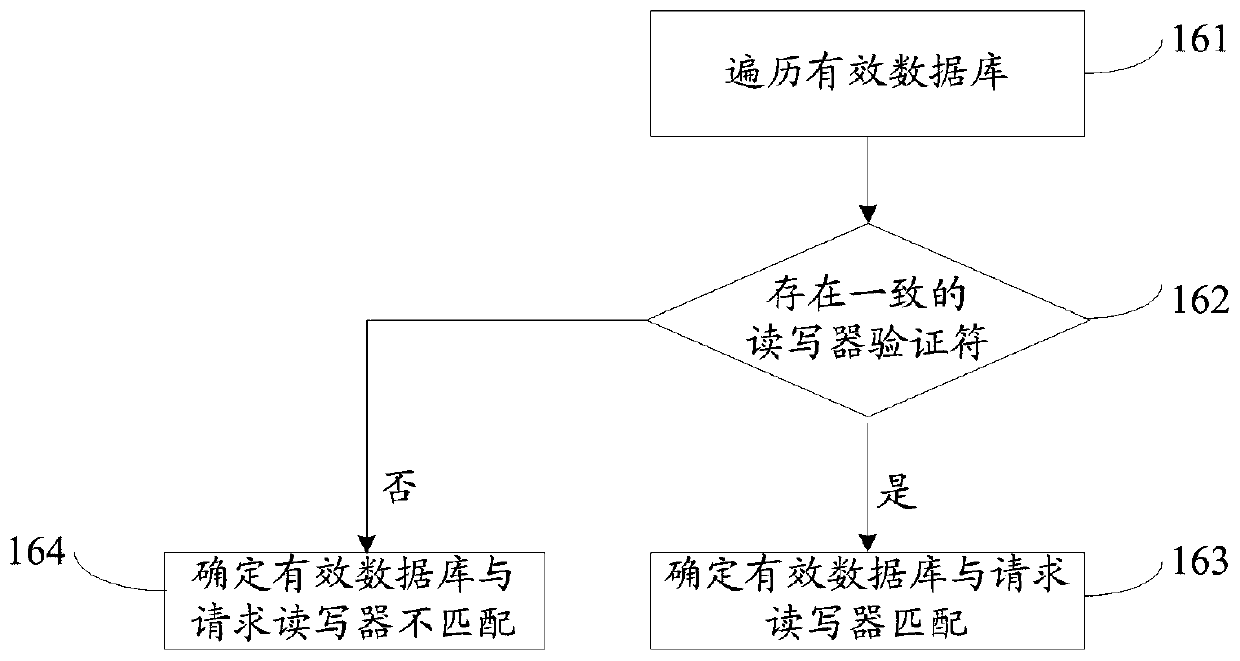
[0125] Step 27: According to the third local time of the valid reader and the verification information of the first database sent by the requesting database, the valid reader determines the reader verifier sent by the requesting database, wherein the valid first database sent by the valid database The verification information is an encrypted character string obtained by the valid database encrypting the string containing the third local time of the valid reader-writer and the identifier of the valid reader-writer using a hash function, that is, valid first database verification information;
[0126] Step 28: judging whether the reader-writer verifier is consistent with the identifier of a valid reader-writer;
[0127] If the reader-writer verifier is consistent with the identifier of the valid reader-writer, perform step 29;
[0128] If the reader-wr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com