Method for realizing access authentication and client
A technology of access authentication and implementation method, which is applied in the field of communication, can solve problems such as low success rate of authentication process, and achieve the effect of improving flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
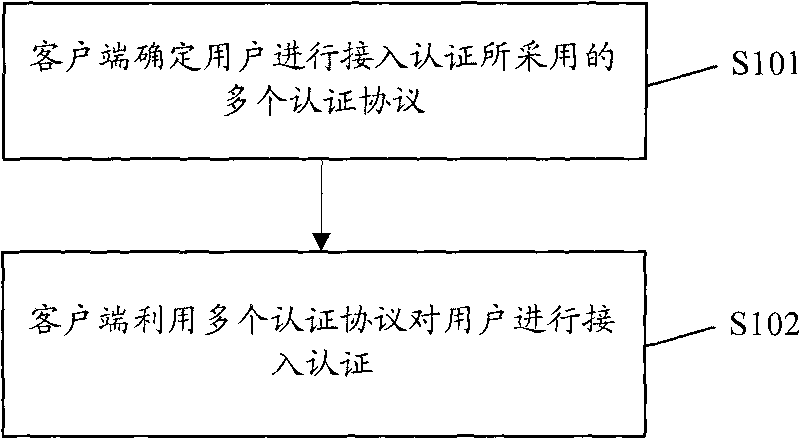
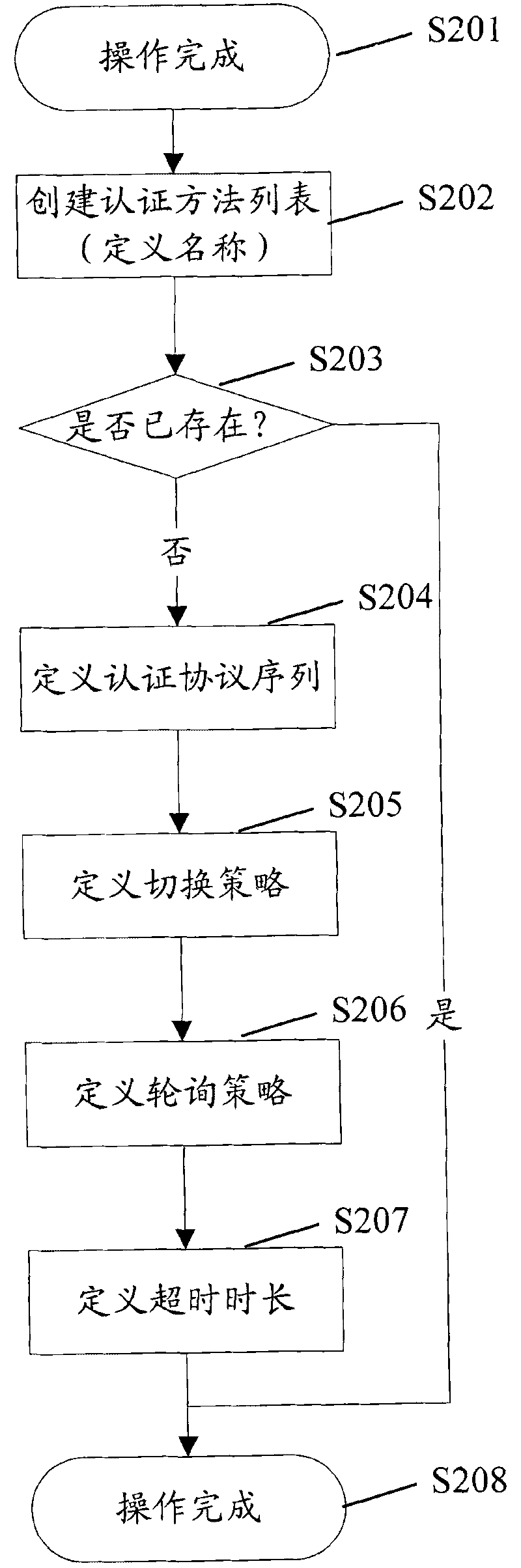
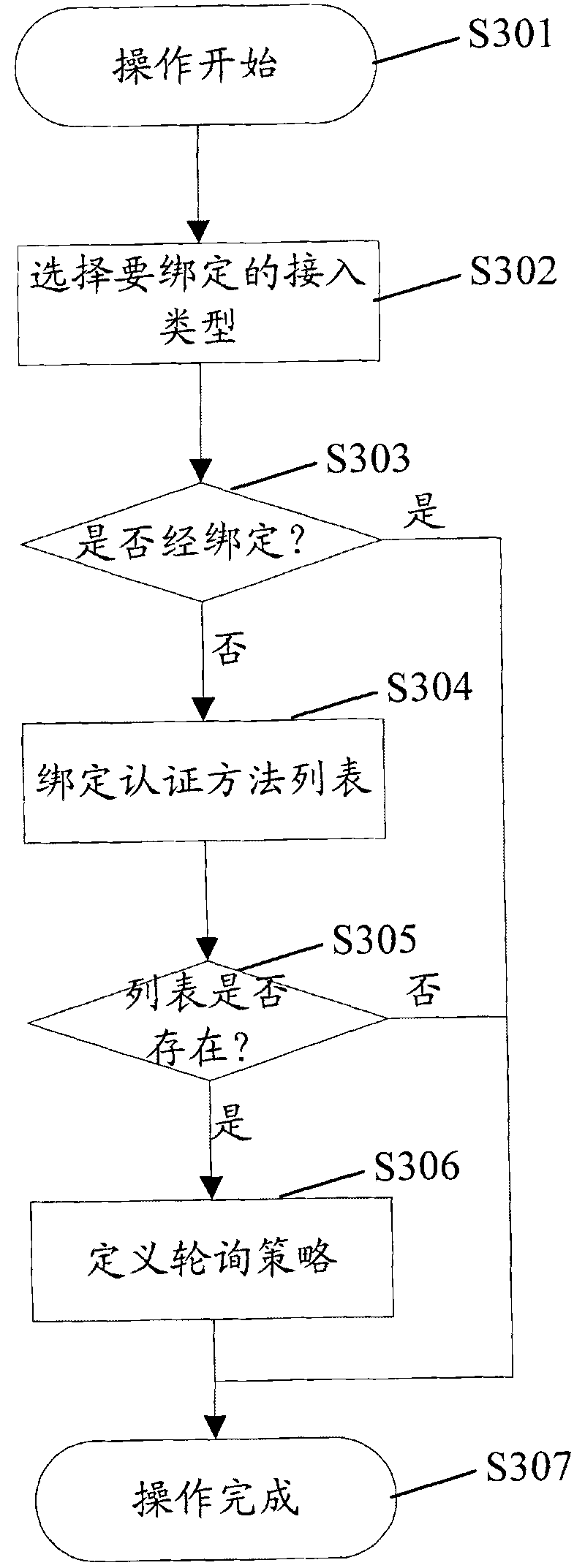
[0039] In related technologies, it usually only involves the interaction between the AAA client and server, and a single server switching mechanism, but only these mechanisms cannot support authentication switching between multiple protocols and methods, resulting in successful authentication. The access may fail due to other reasons, but it cannot try to access in other ways, resulting in a reduction in the success rate of the authentication process. The present invention considers that the access terminal (user) does not care about which authentication method is used for authentication. The authentication method The designation is done by the AAA client. Therefore, the present invention proposes that the AAA client can bind multiple authentication methods and method lists for the access type adopted by the user (access end), and ensure that the authentication method is selected through the protocol selection strategy. Within the minimum range allowed by security, the user's a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com