A method for user access authentication
An access authentication and user technology, applied in user identity/authority verification, electrical components, transmission systems, etc., can solve problems such as poor user connectivity, different client programs, single-point bottlenecks and failures, and avoid waste, passwords, etc. The effect of delivering security and preventing attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
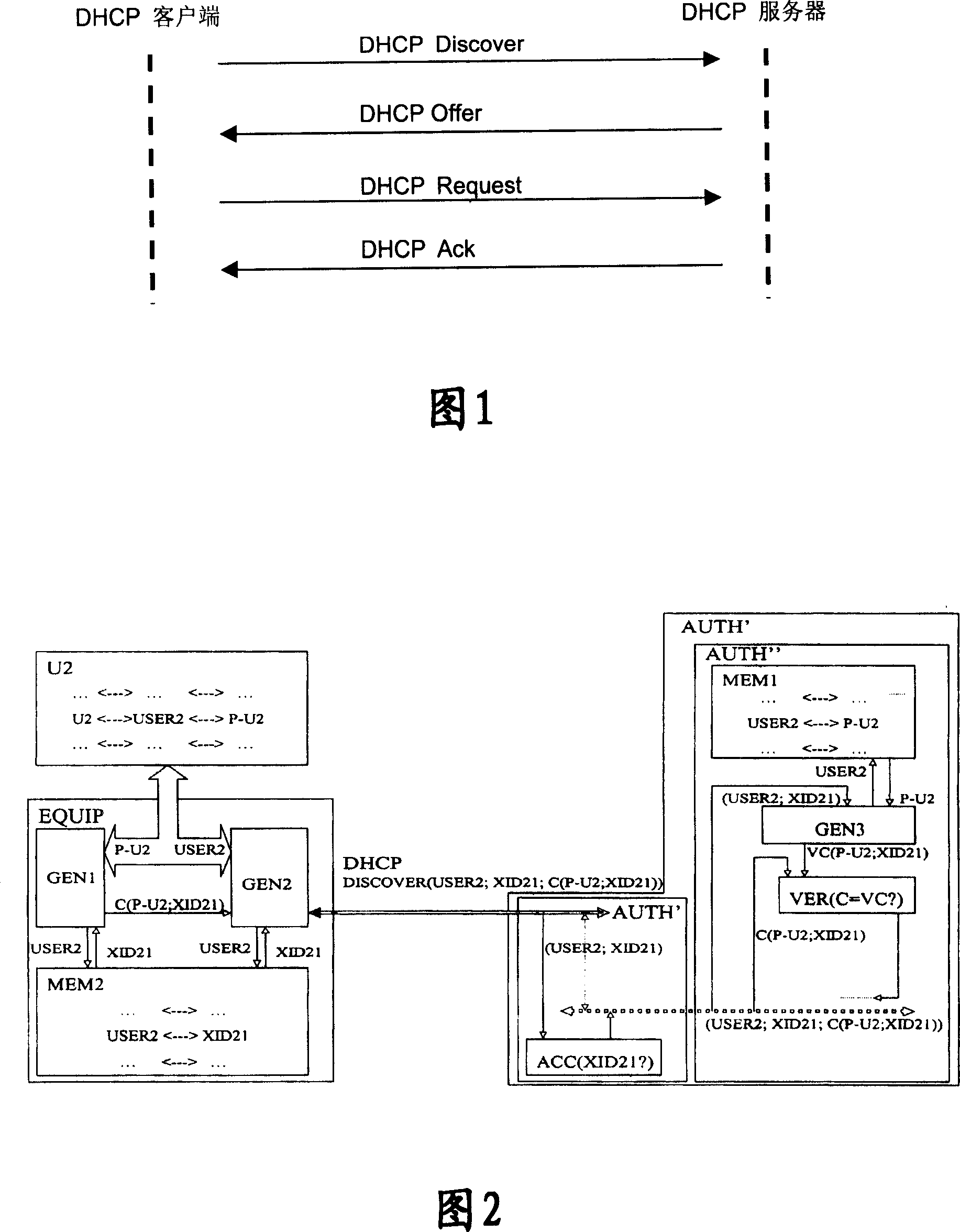
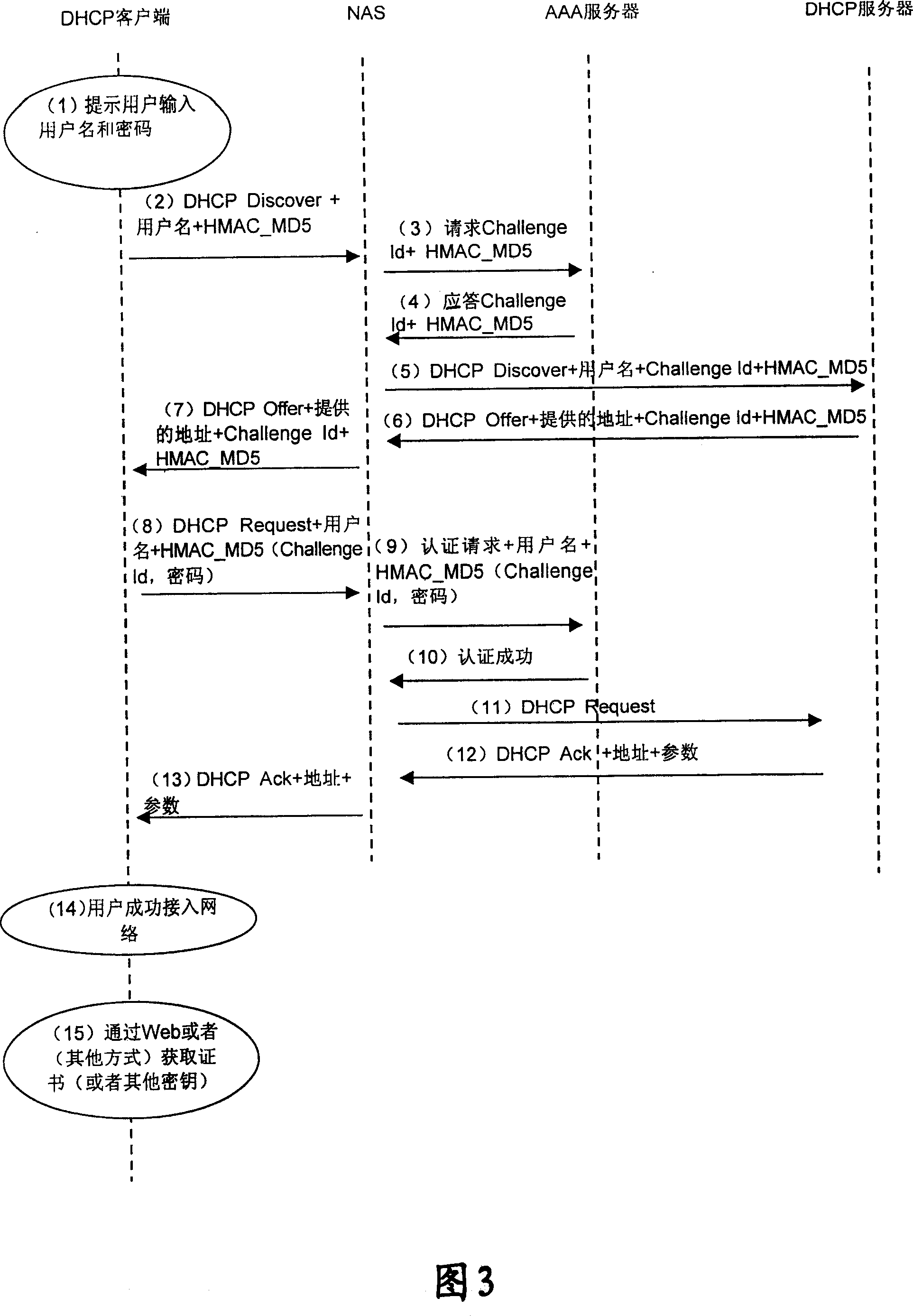
[0117]In order to solve the security problem when transmitting user password (password), specific embodiment 1 of the present invention obtains random number (as challenge word: Challenge ID) from network side when user requests address, and user utilizes random number (Challenge ID) and The user password is encrypted, and the encrypted result is sent to the authentication server on the network side. The authentication server on the network side also uses the above random number and the stored user password to perform the same encryption operation, and compares the user password with the network side. The encrypted result is used to authenticate the user.
[0118] The user password is encrypted by using the random number provided by the network side to the user, and the same random number is also used to encrypt the user password on the network side (such as the authentication server side), and the user can use the network side only after the authentication is successful. The ...
Embodiment 2
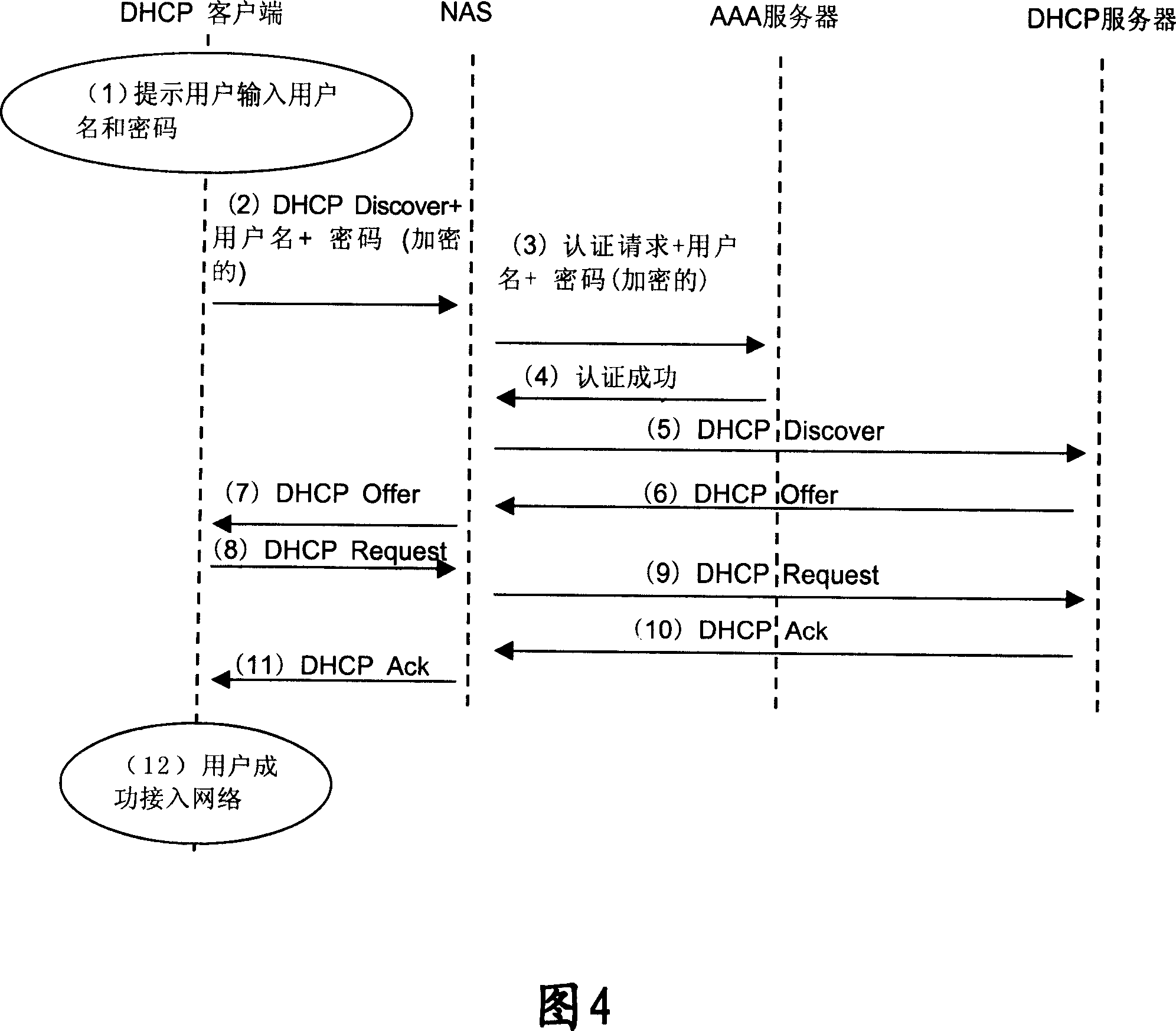
[0147] As shown in Figure 4, the process for a user to perform Layer 3 authentication through DHCP includes:
[0148]1) The user equipment (that is, the DHCP client) obtains the user name and password of the user through user input. For example, a pop-up window can be displayed on the user equipment to prompt the user to input the user name and password. Of course, other alternative methods can also be used.
[0149] 2) The user equipment broadcasts and sends a DHCP Discover message, which carries the user ID and the password encrypted by the key (or certificate).
[0150] The key (or certificate) can be obtained through the network (Web, Ftp, etc.) after the user successfully accesses the network, or can be directly configured (or other out-of-band methods) or the Extensible Authentication Protocol (EAP) before the first startup. Obtained from the network side, the network side establishes the binding relationship between the key (or certificate) and the user while distributi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com