Patents
Literature
85results about How to "Safe interaction" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
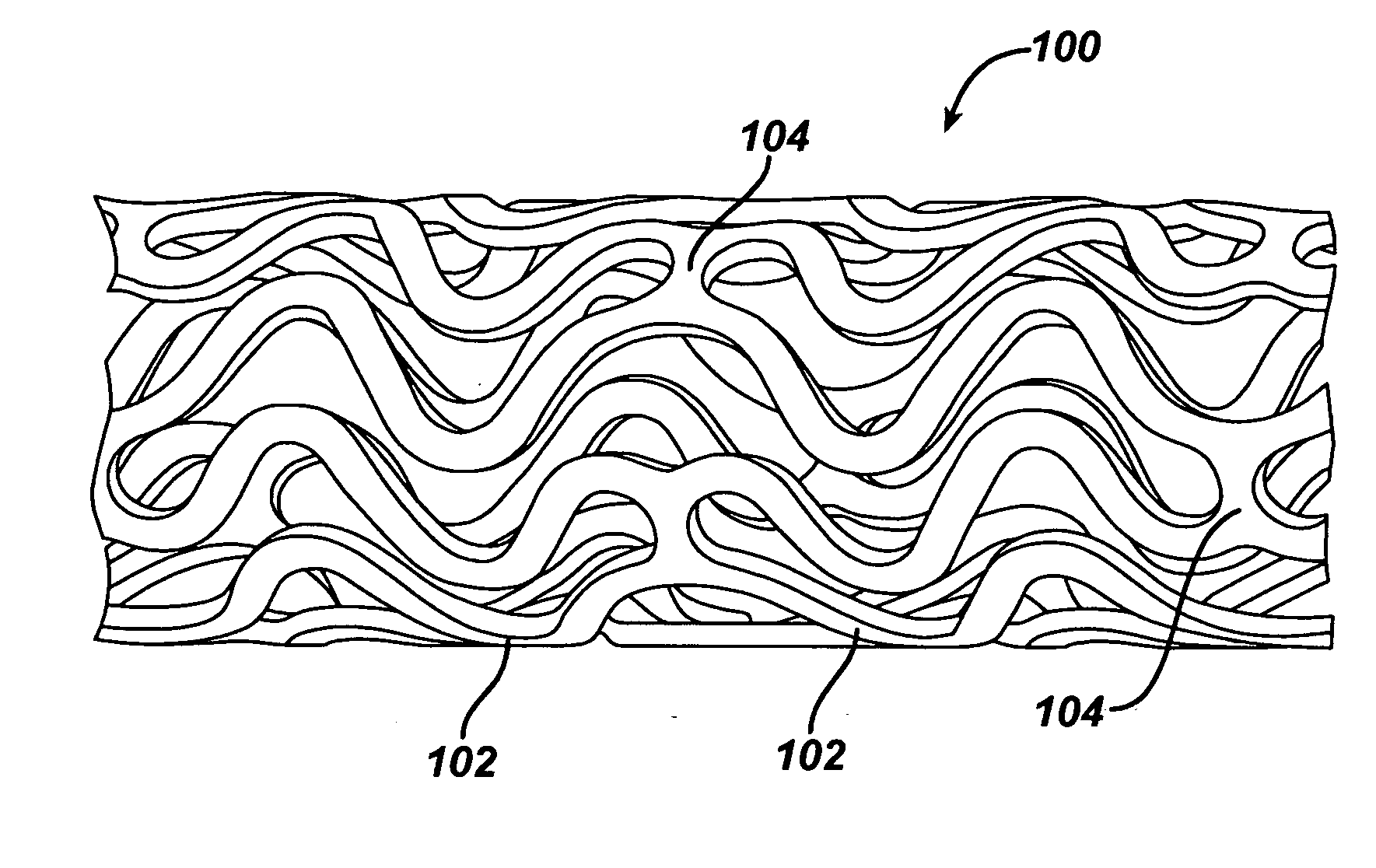
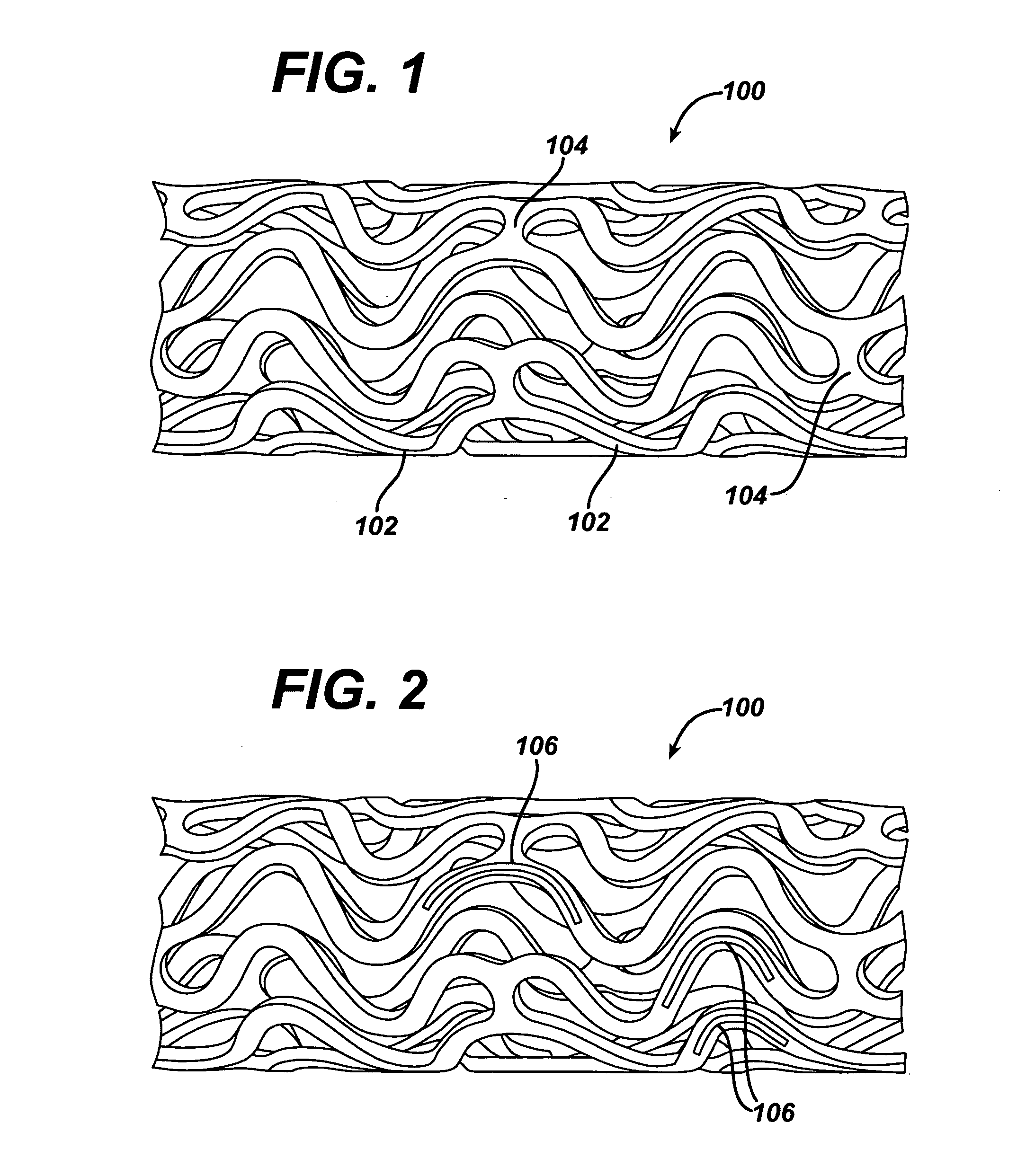
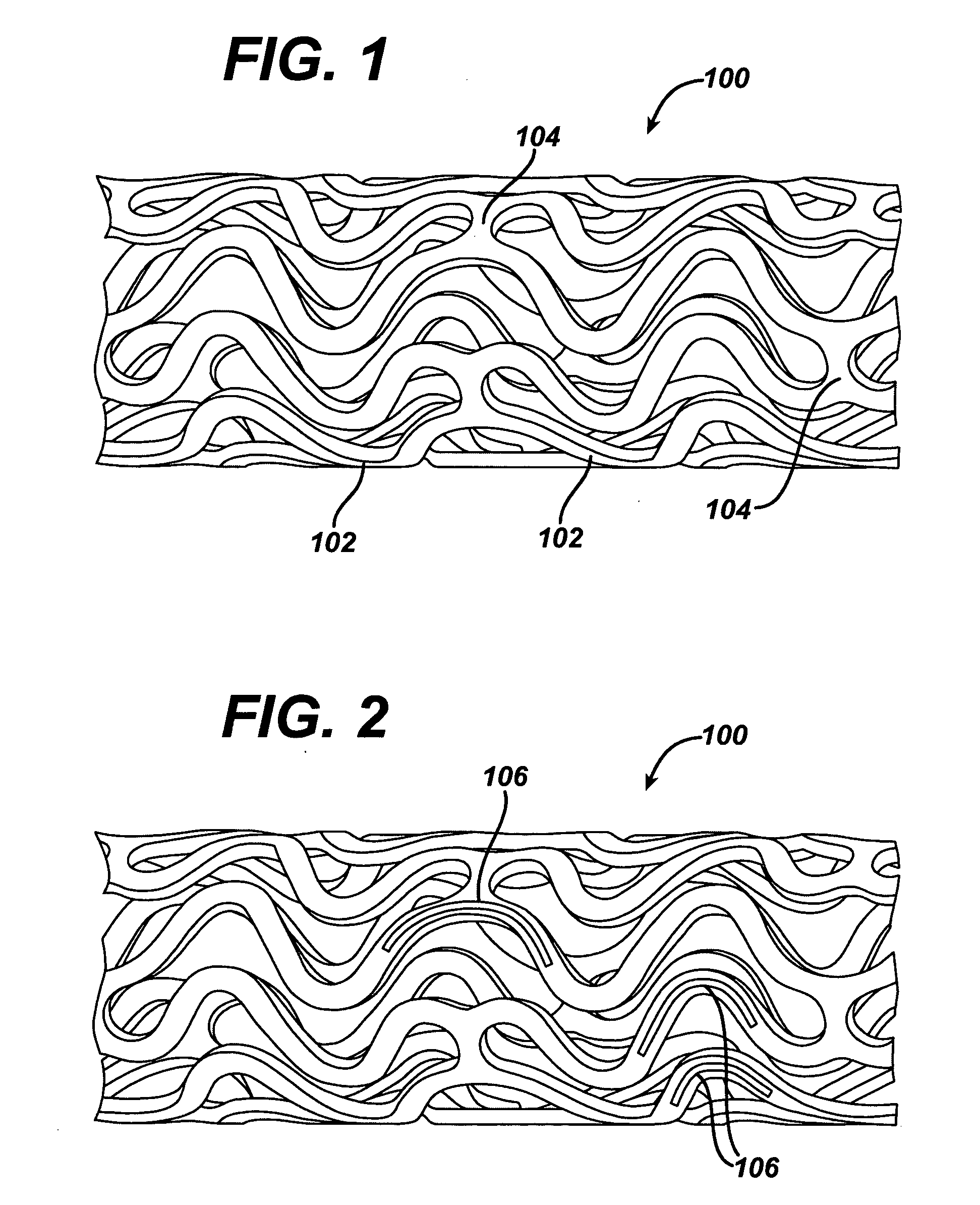
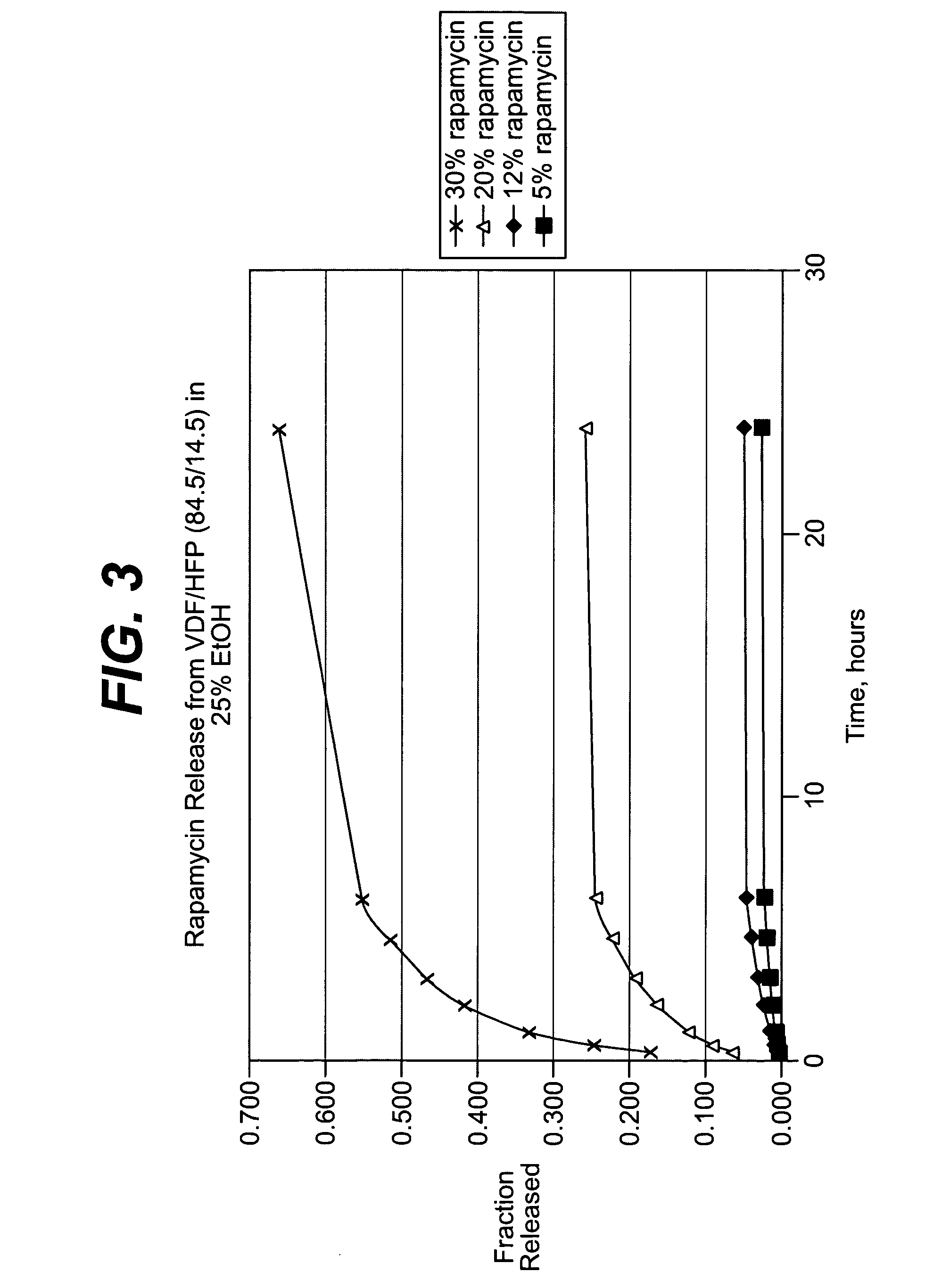
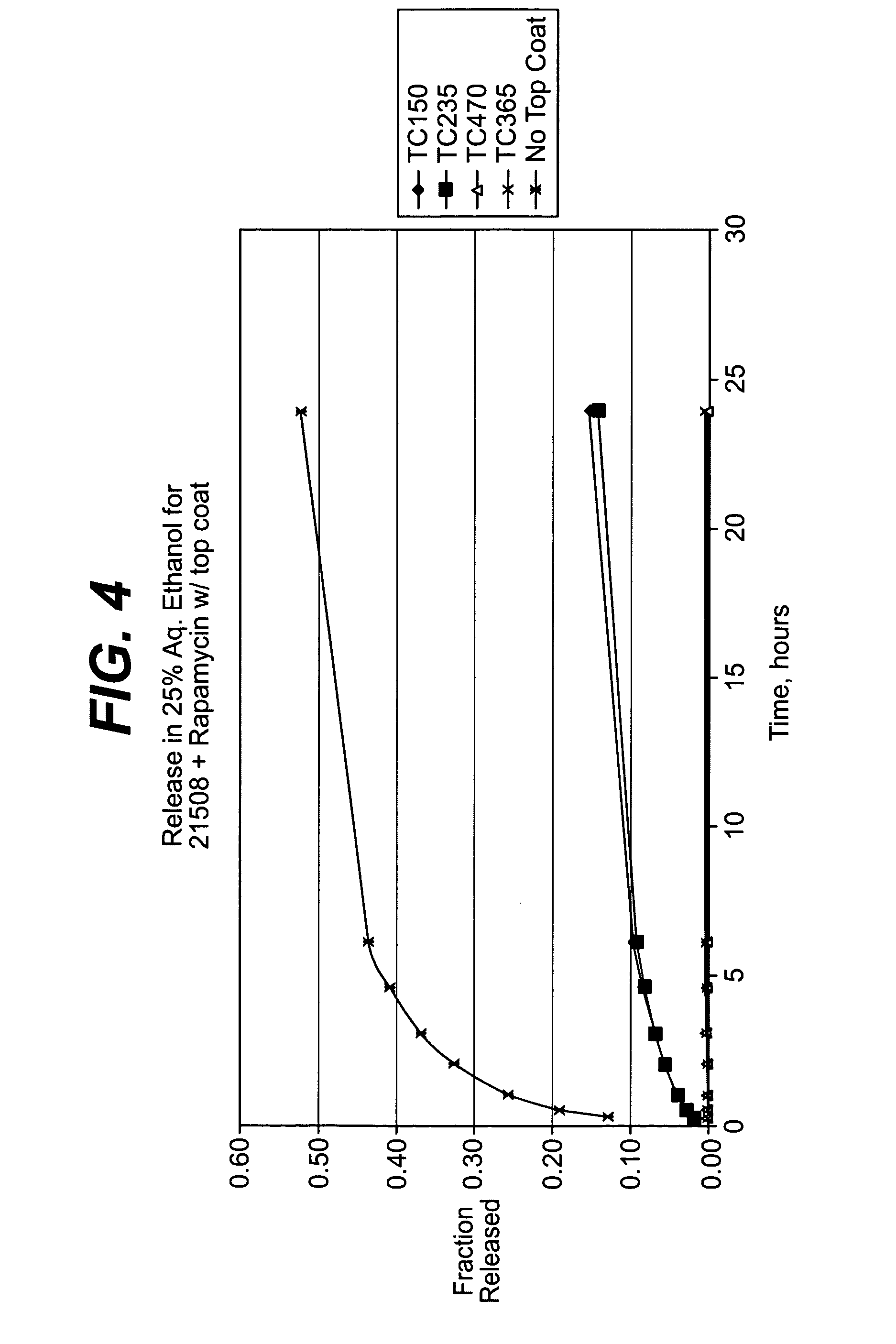
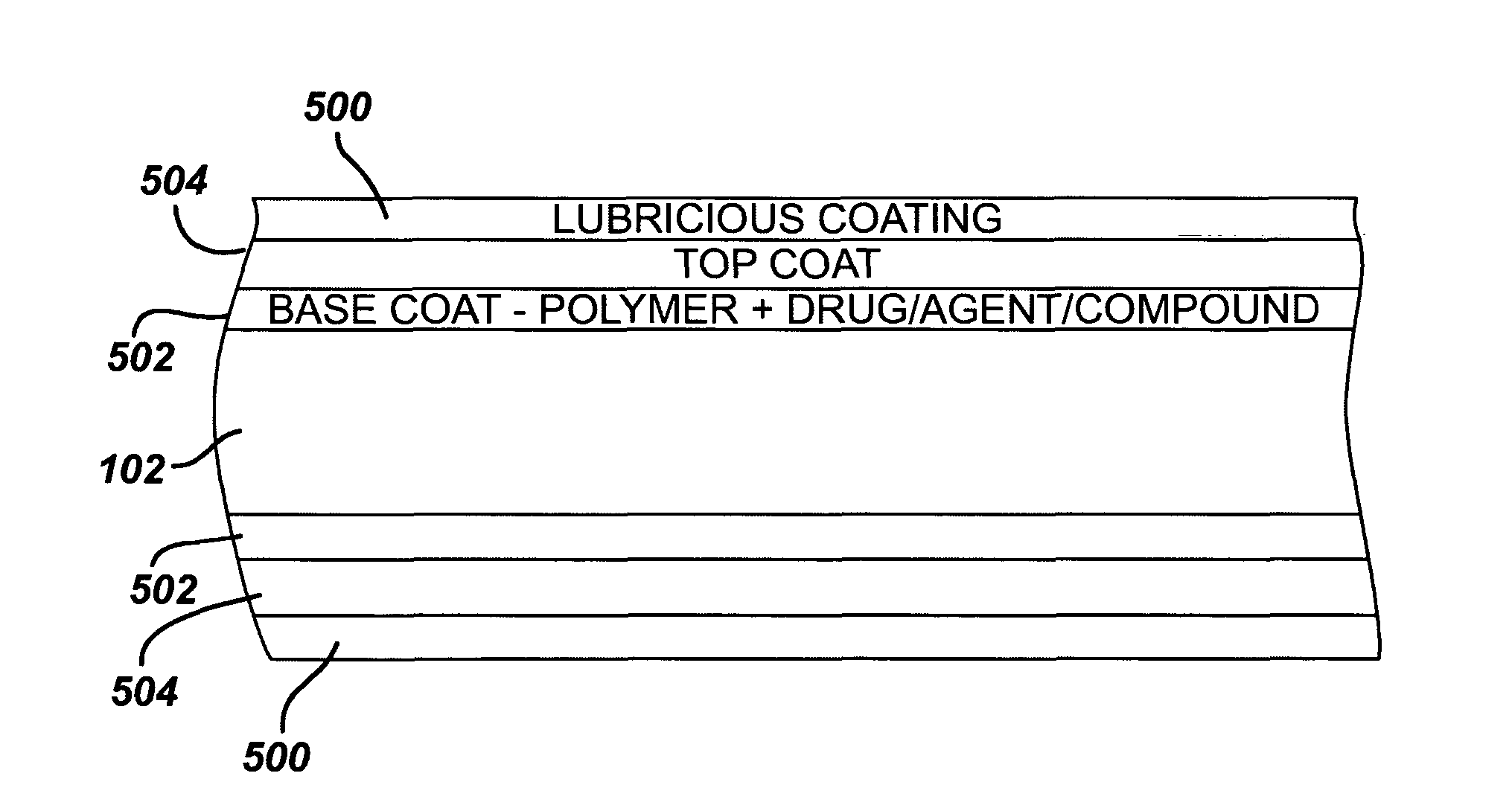
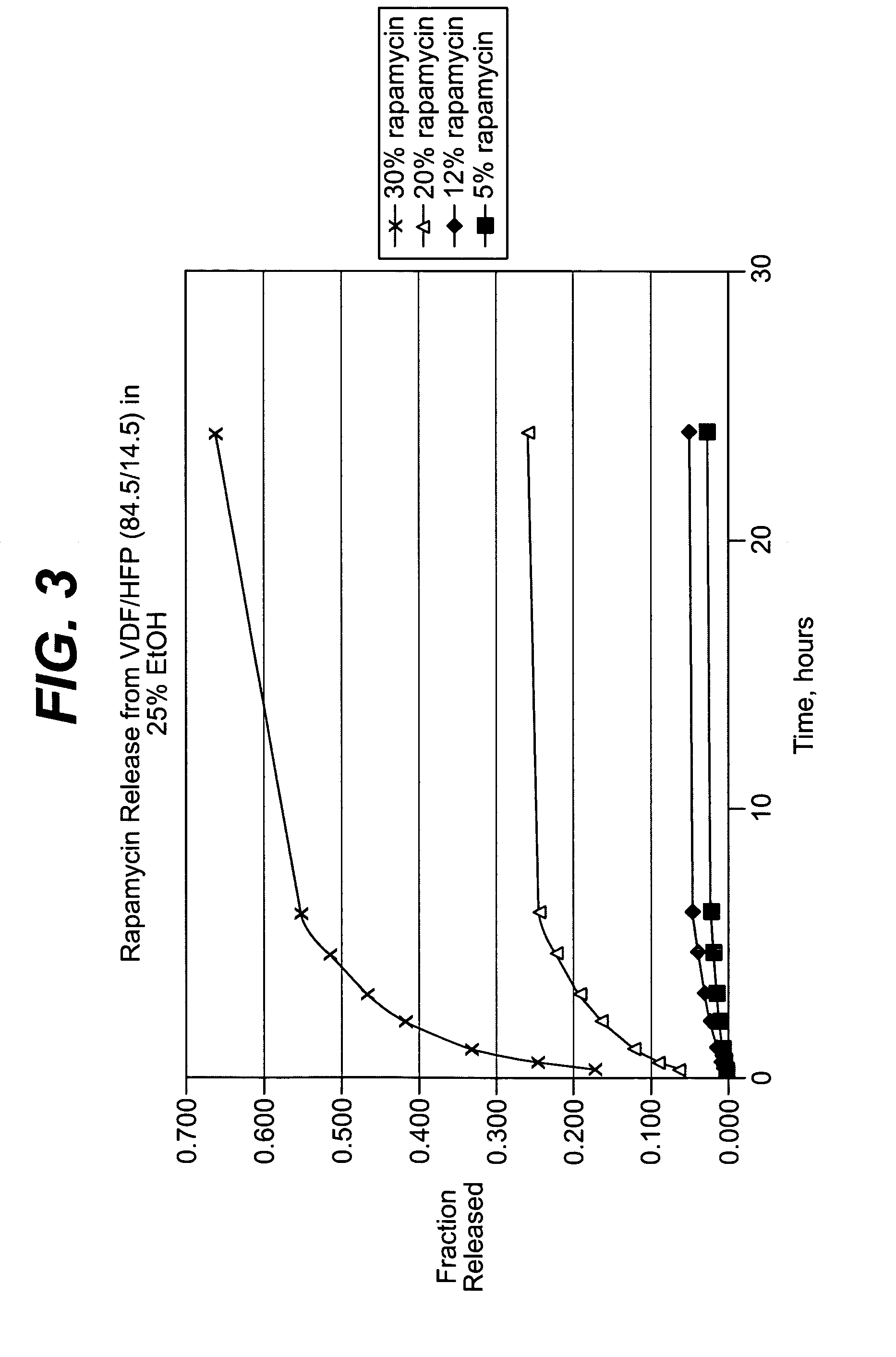
Heparin barrier coating for controlled drug release
ActiveUS20050004663A1Reduce frictional forceReduce forceSuture equipmentsStentsCompound (substance)Antioxidant
Medical devices, and in particular implantable medical devices, may be coated to minimize or substantially eliminate a biological organism's reaction to the introduction of the medical device to the organism. The medical devices may be coated with any number of biocompatible materials. Therapeutic drugs, agents or compounds may be mixed with the biocompatible materials and affixed to at least a portion of the medical device. These therapeutic drugs, agents or compounds may also further reduce a biological organism's reaction to the introduction of the medical device to the organism. In addition, these therapeutic drugs, agents and / or compounds may be utilized to promote healing, including the formation of blood clots. The drugs, agents, and / or compounds may also be utilized to treat specific diseases, including vulnerable plaque. Therapeutic agents may also be delivered to the region of a disease site. In regional delivery, liquid formulations may be desirable to increase the efficacy and deliverability of the particular drug. Also, the devices may be modified to promote endothelialization. Various materials and coating methodologies may be utilized to maintain the drugs, agents or compounds on the medical device until delivered and positioned. In addition, the devices utilized to deliver the implantable medical devices may be modified to reduce the potential for damaging the implantable medical device during deployment. Medical devices include stents, grafts, anastomotic devices, perivascular wraps, sutures and staples. In addition, various polymer combinations as well as other therapeutic agents may be utilized to control the elution rates of the therapeutic drugs, agents and / or compounds from the implantable medical devices. In each of these instances, antioxidants are utilized to prolong product integrity.
Owner:WYETH
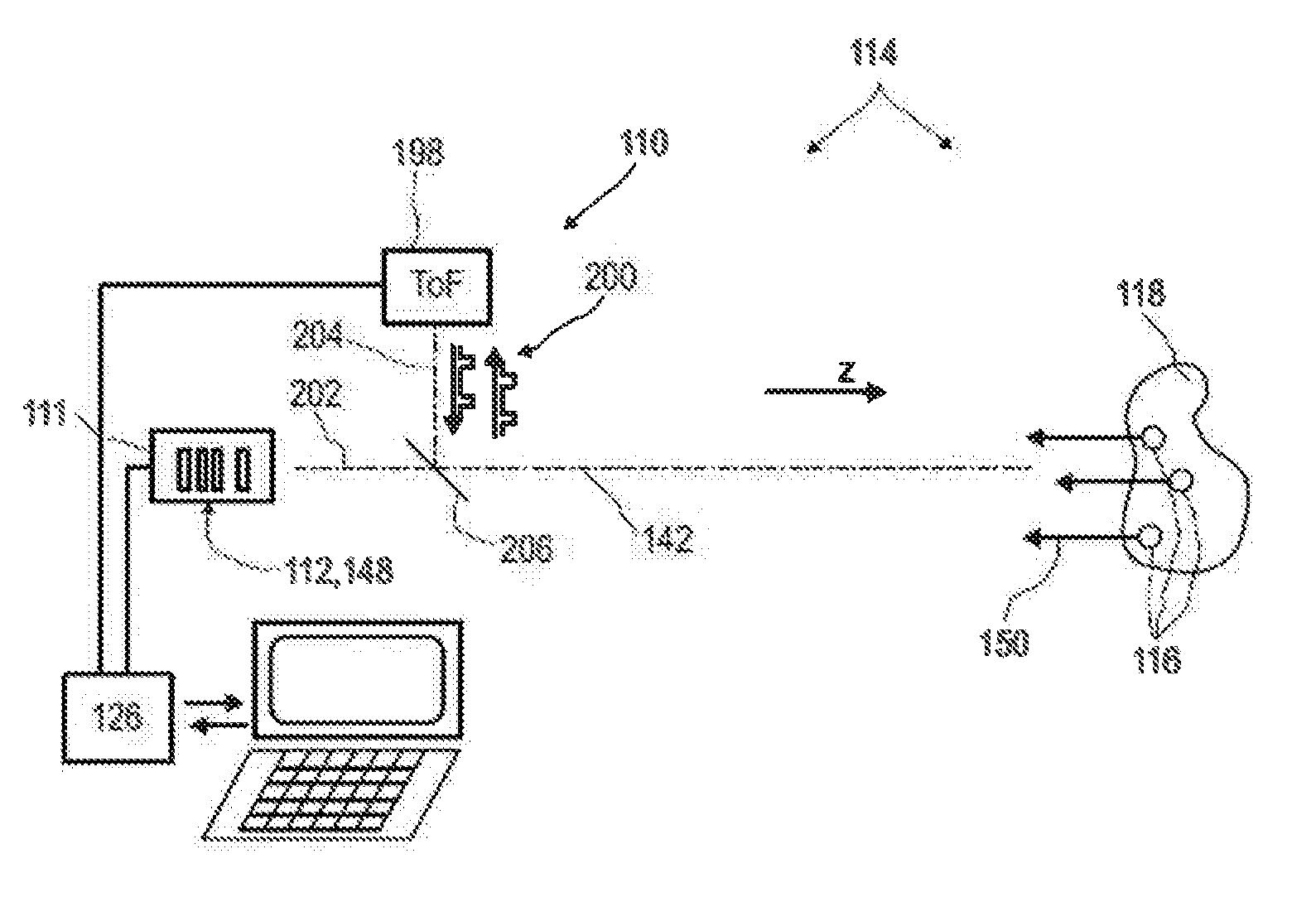
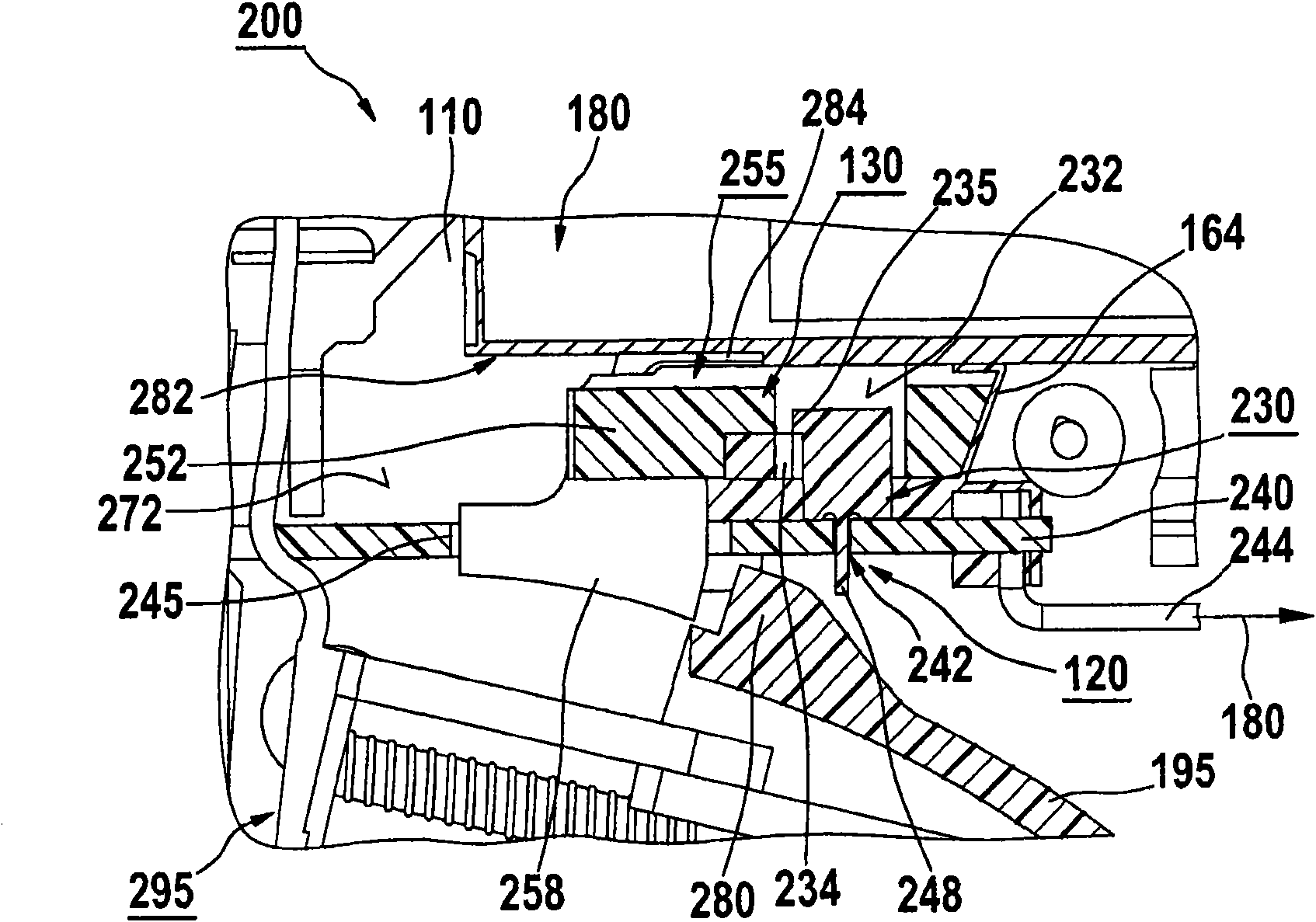
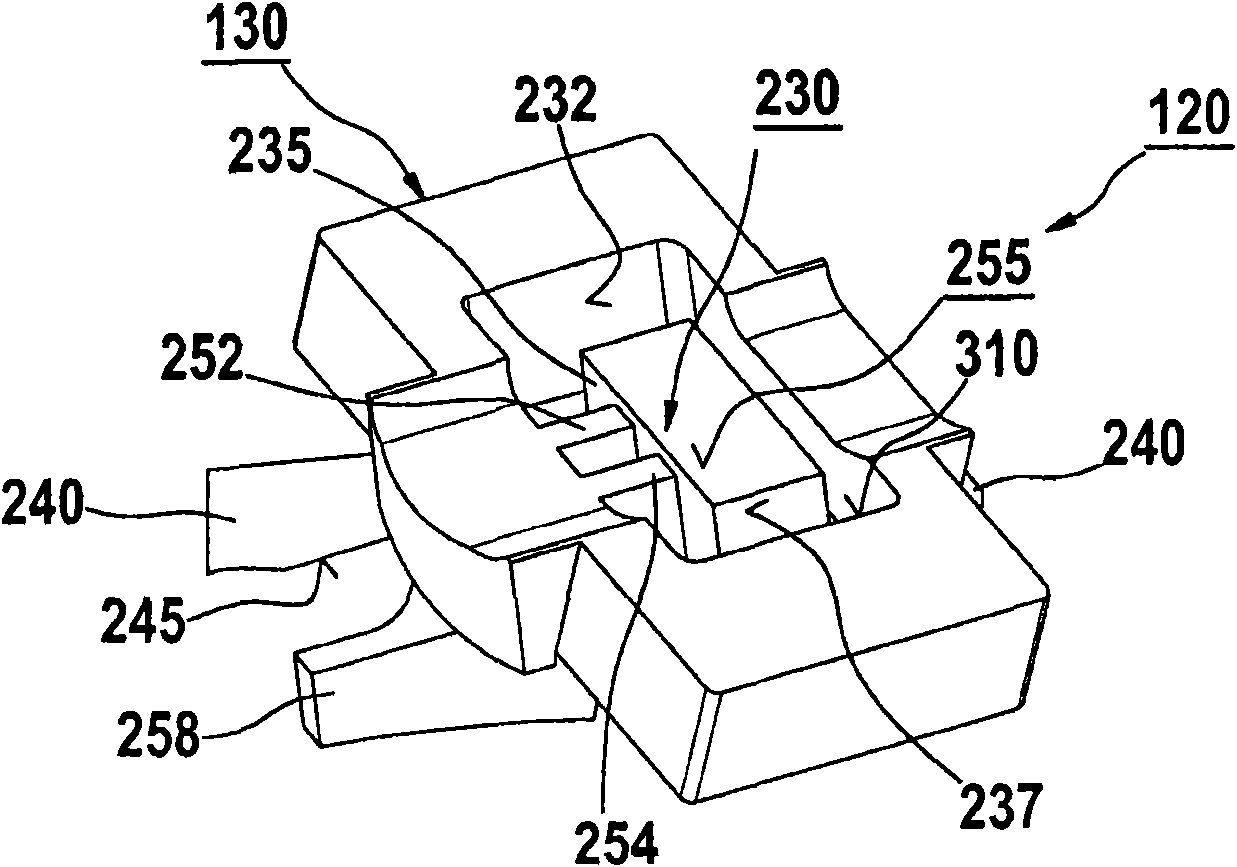
Detector for optically detecting at least one object
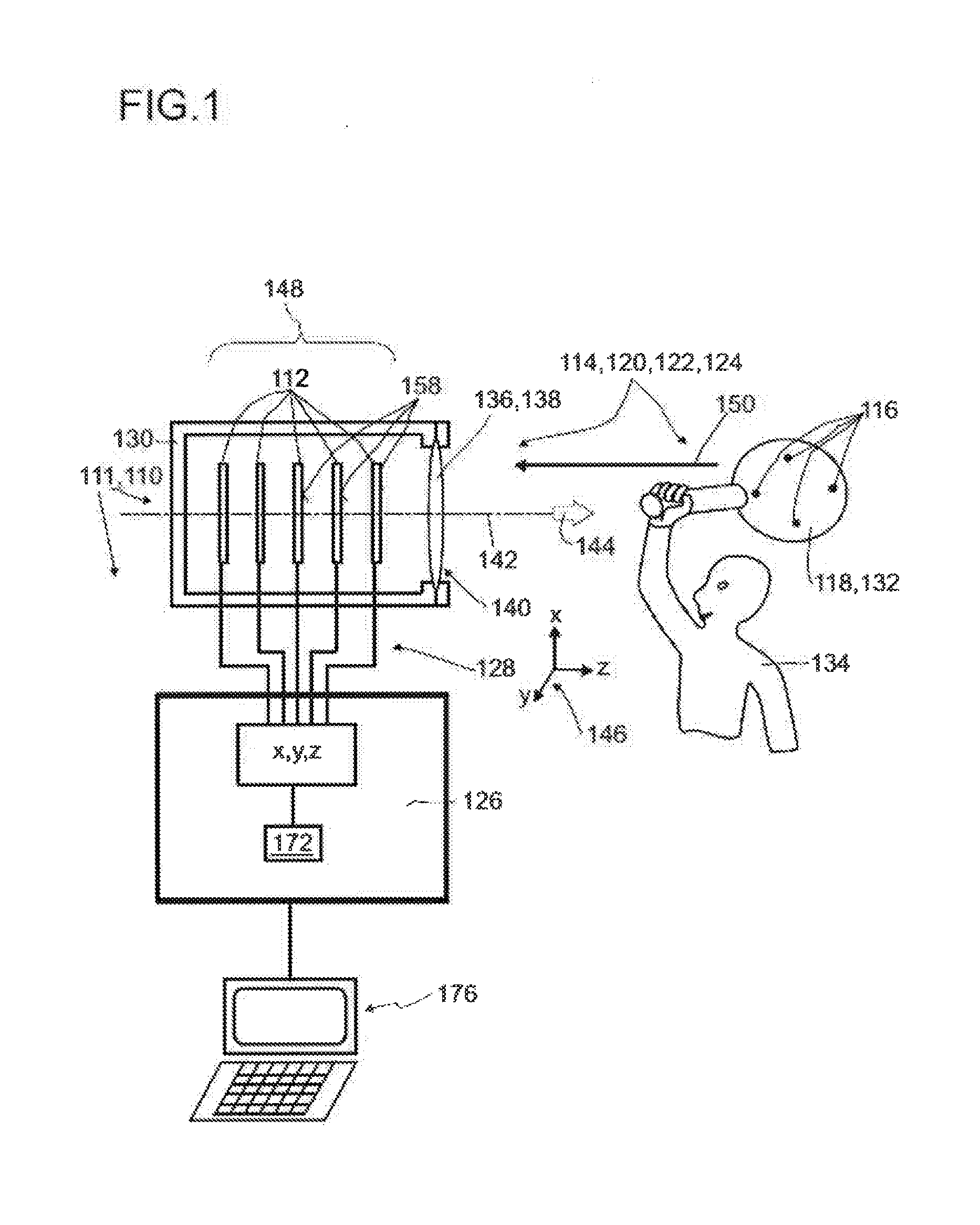
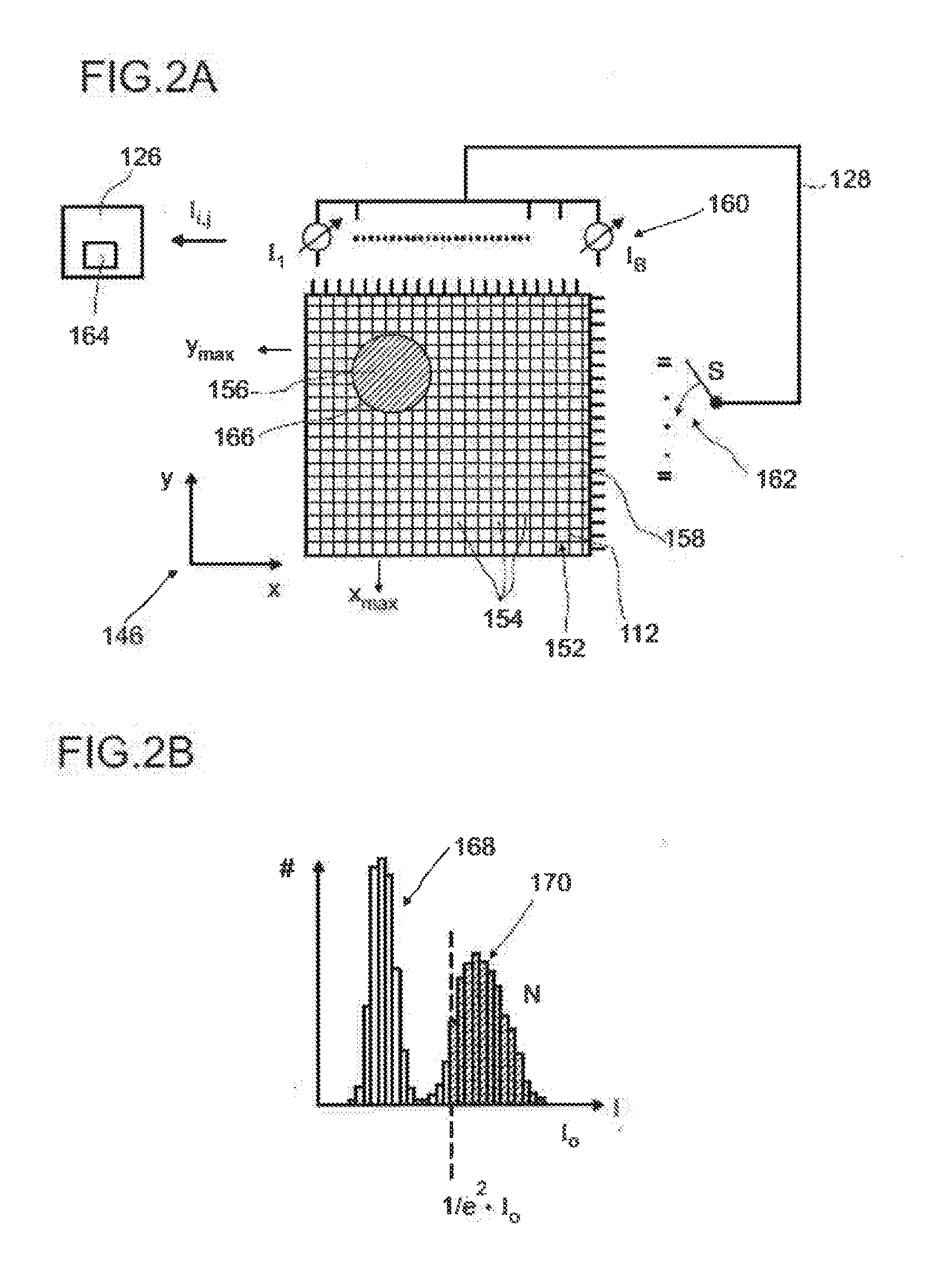
ActiveUS20160127664A1Safe and direct interactionSafe interactionTelevision system detailsOptical rangefindersOpticsPhysics
A detector (110) for determining a position of at least one object (118) is disclosed. The detector (110) comprises:at least one optical sensor (112), the optical sensor (112) being adapted to detect a light beam (150) traveling from the object (118) towards the detector (110), the optical sensor (112) having at least one matrix (152) of pixels (154); andat least one evaluation device (126), the evaluation device (126) being adapted to determine a number N of pixels (154) of the optical sensor (112) which are illuminated by the light beam (150), the evaluation device (126) further being adapted to determine at least one longitudinal coordinate of the object (118) by using the number N of pixels (154) which are illuminated by the light beam (150).
Owner:BASF AG
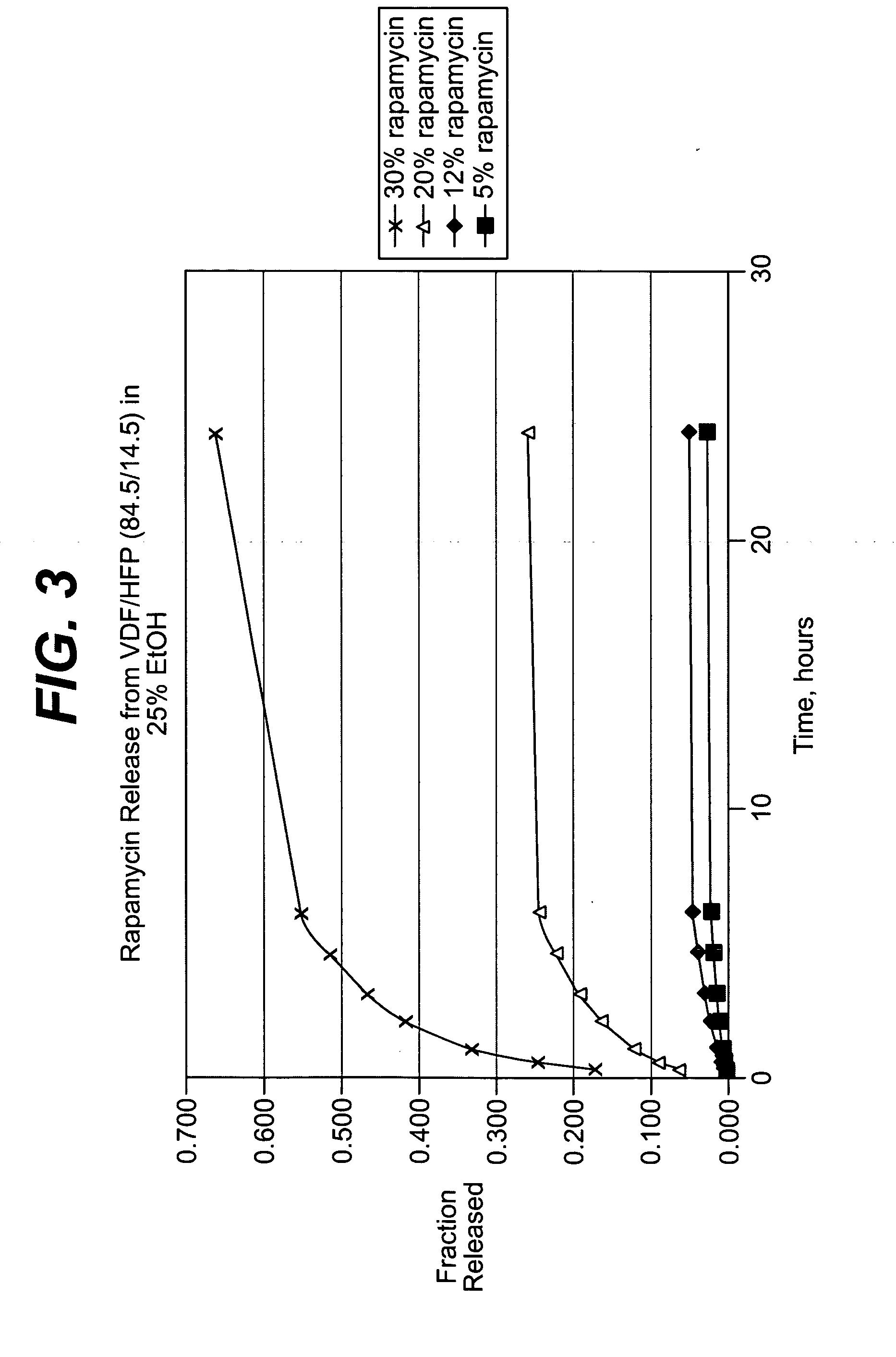
Injectable formulations of taxanes for cad treatment
InactiveUS20050272806A1Minimize potential risk of damageReduce frictionBiocideOrganic active ingredientsAntioxidantBlood vessel
Medical devices, and in particular implantable medical devices, may be coated to minimize or substantially eliminate a biological organism's reaction to the introduction of the medical device to the organism. The medical devices may be coated with any number of biocompatible materials. Therapeutic drugs, agents or compounds may be mixed with the biocompatible materials and affixed to at least a portion of the medical device. These therapeutic drugs, agents or compounds may also further reduce a biological organism's reaction to the introduction of the medical device to the organism. In addition, these therapeutic drugs, agents and / or compounds may be utilized to promote healing, including the formation of blood clots. The drugs, agents, and / or compounds may also be utilized to treat specific diseases, including vulnerable plaque. Therapeutic agents may also be delivered to the region of a disease site. In regional delivery, liquid formulations may be desirable to increase the efficacy and deliverability of the particular drug. Also, the devices may be modified to promote endothelialization. Various materials and coating methodologies may be utilized to maintain the drugs, agents or compounds on the medical device until delivered and positioned. In addition, the devices utilized to deliver the implantable medical devices may be modified to reduce the potential for damaging the implantable medical device during deployment. Medical devices include stents, grafts, anastomotic devices, perivascular wraps, sutures and staples. In addition, various polymer combinations may be utilized to control the elution rates of the therapeutic drugs, agents and / or compounds from the implantable medical devices. Liquid formulations, including solutions and suspensions of the various drugs, agents and / or compounds, may be locally or regionally delivered. In each of these instances, antioxidants are utilized to prolong product integrity.
Owner:CARDINAL HEALTH SWITZERLAND 515 GMBH
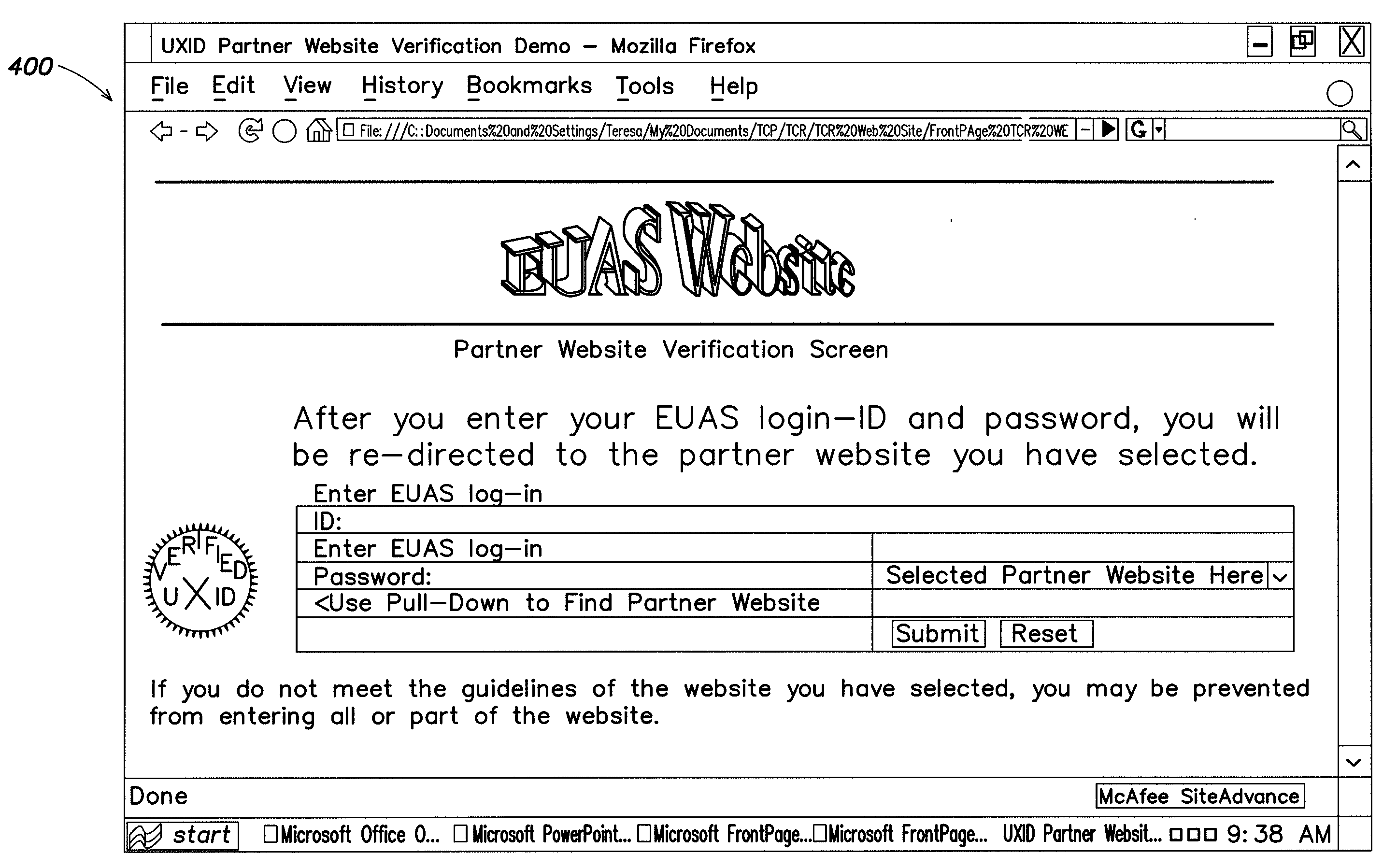
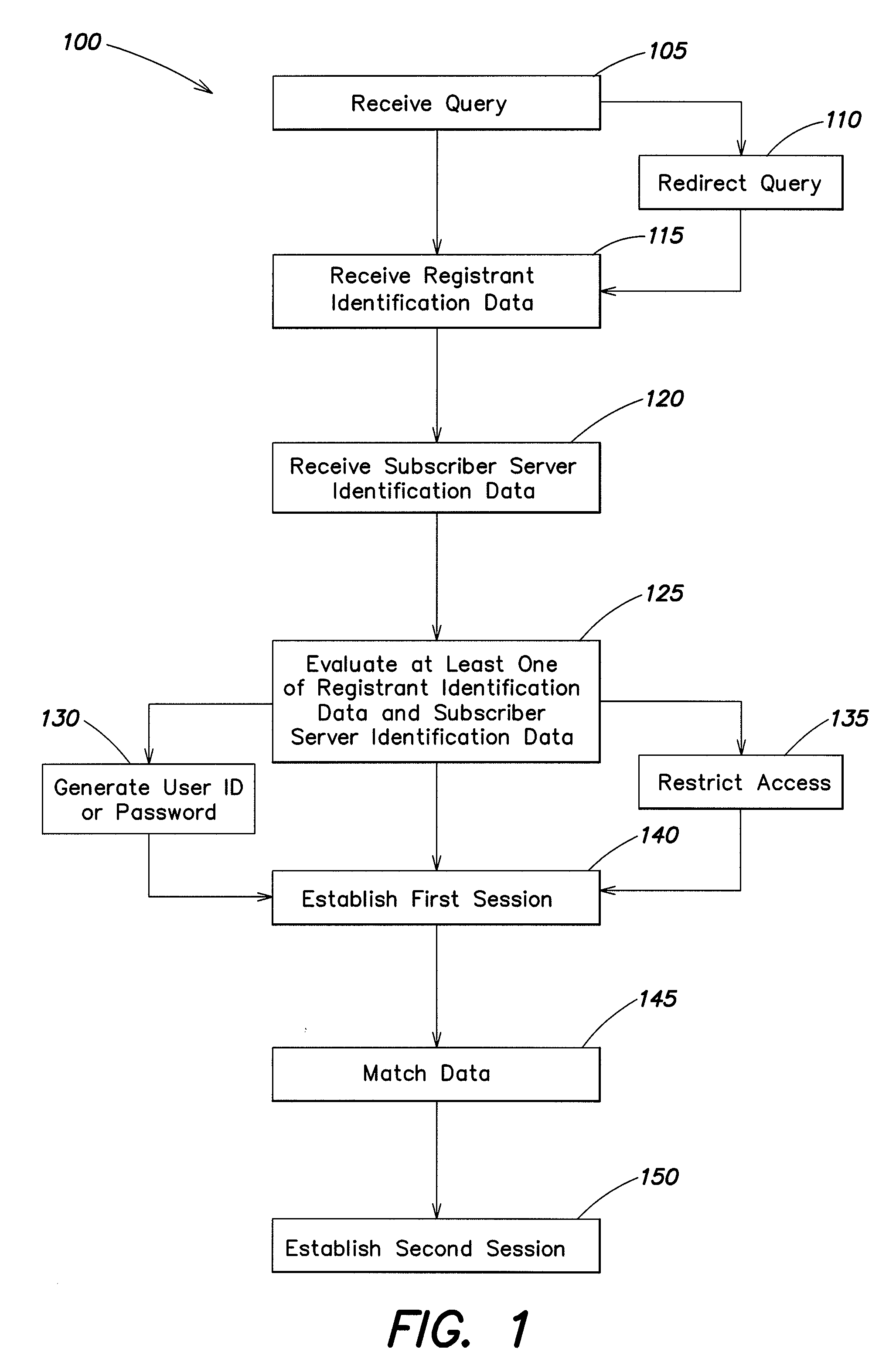
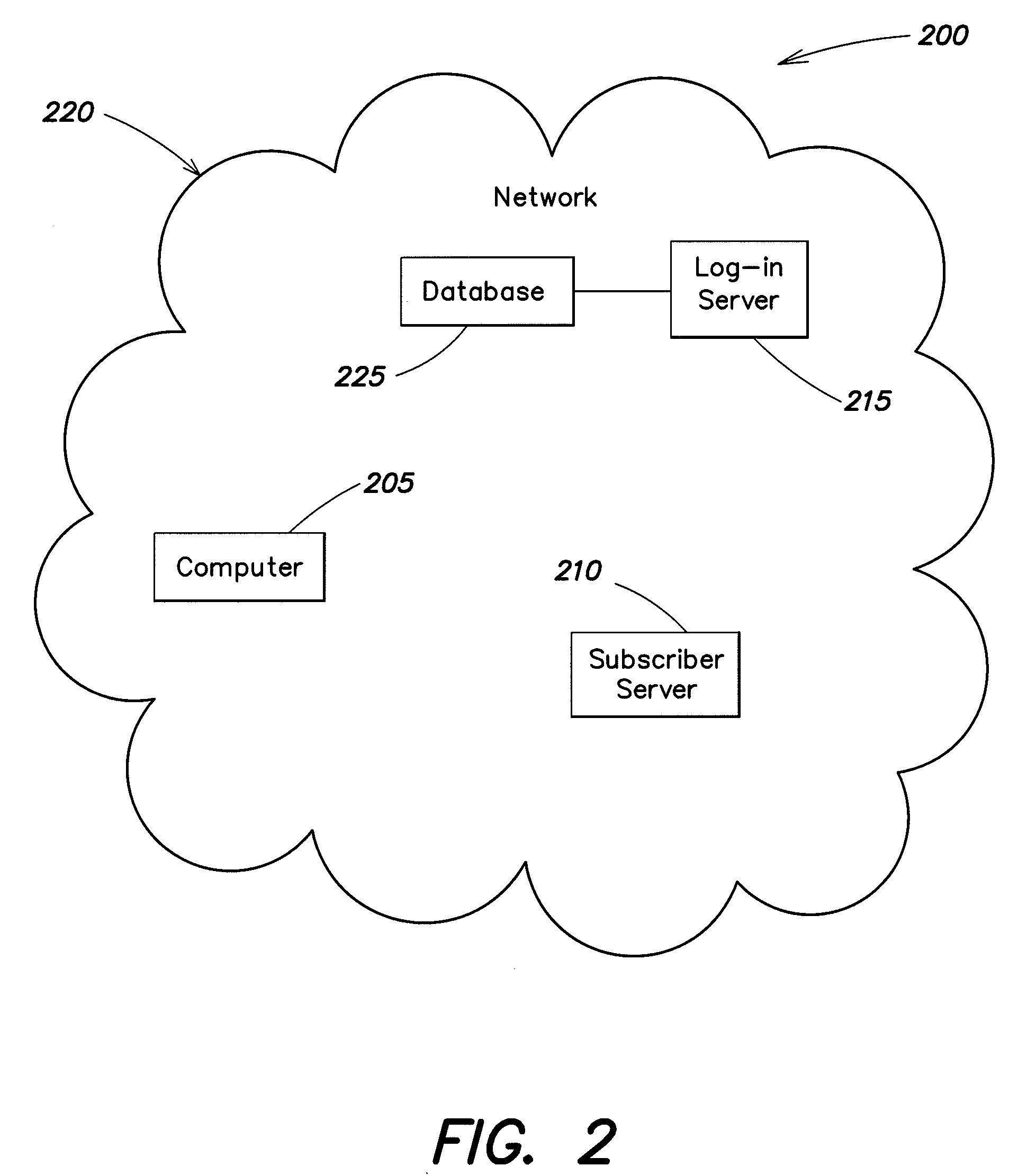
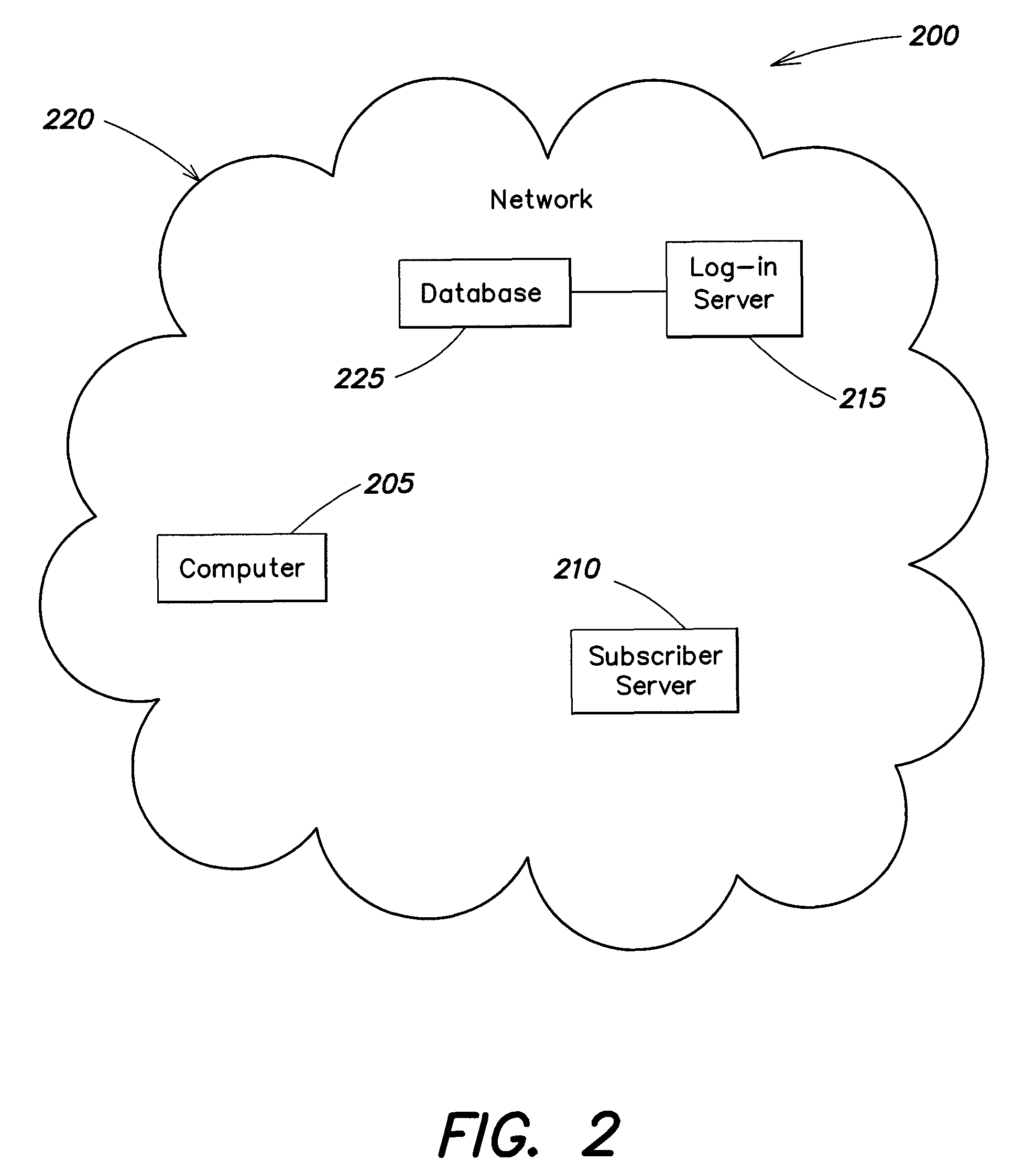
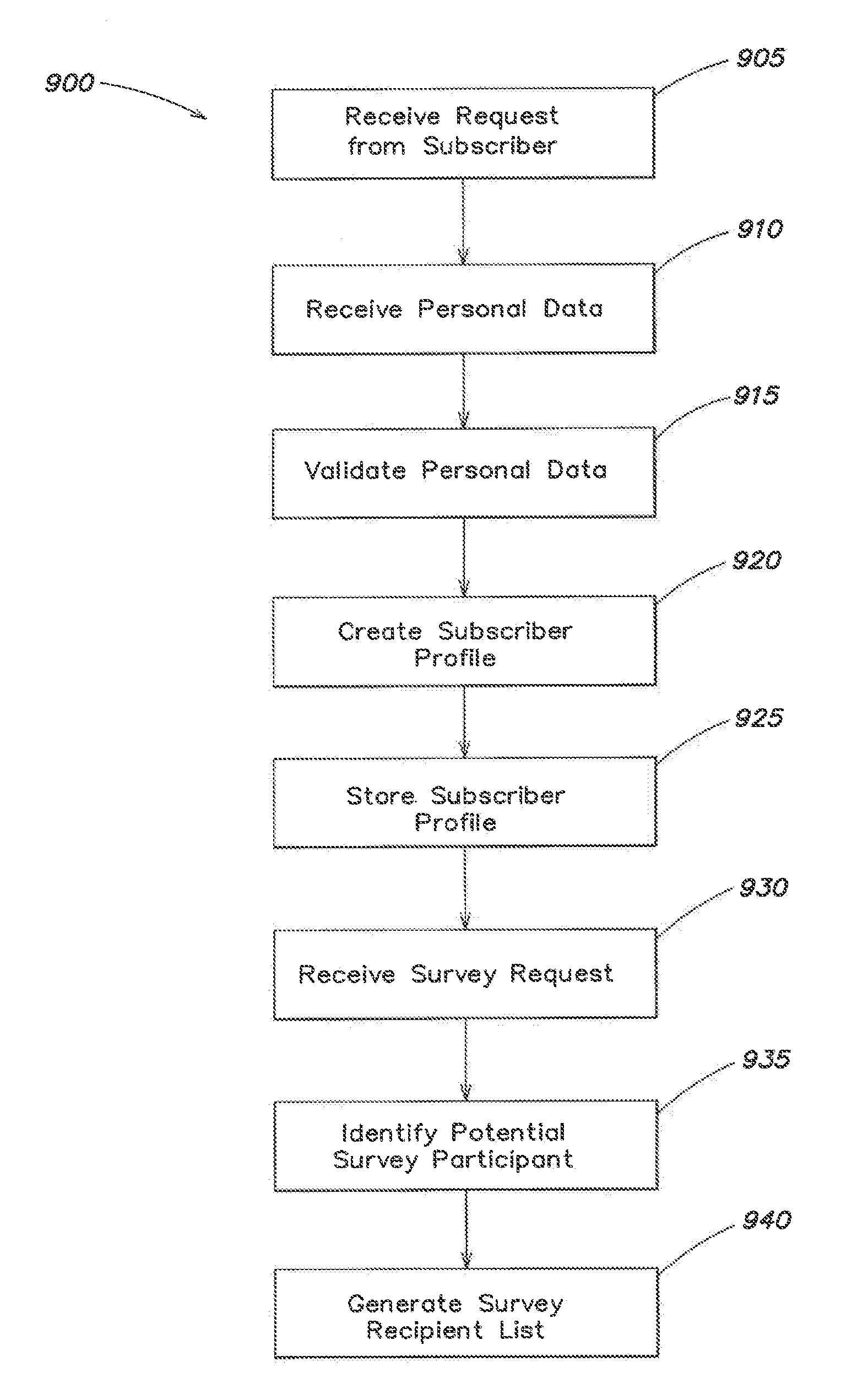
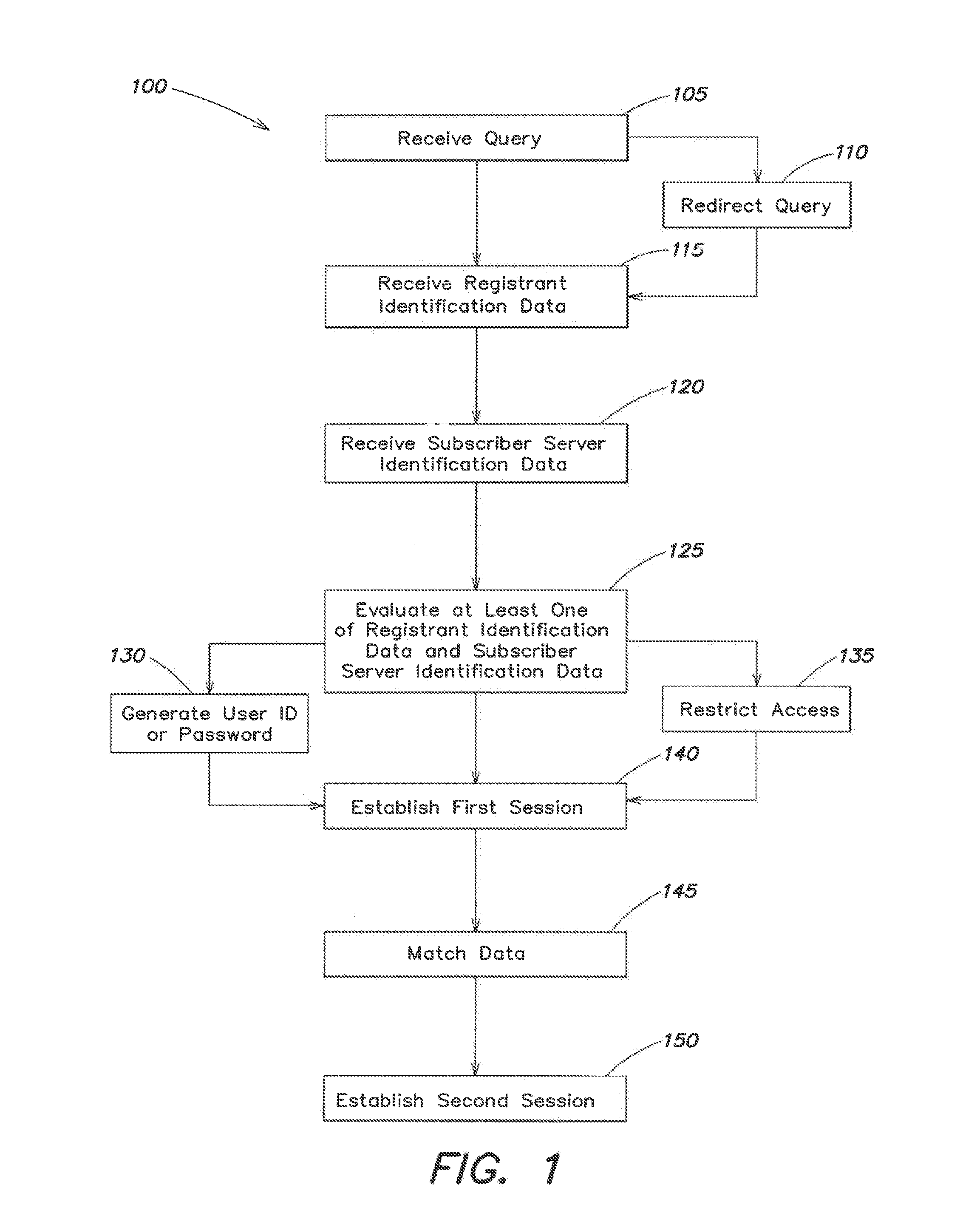
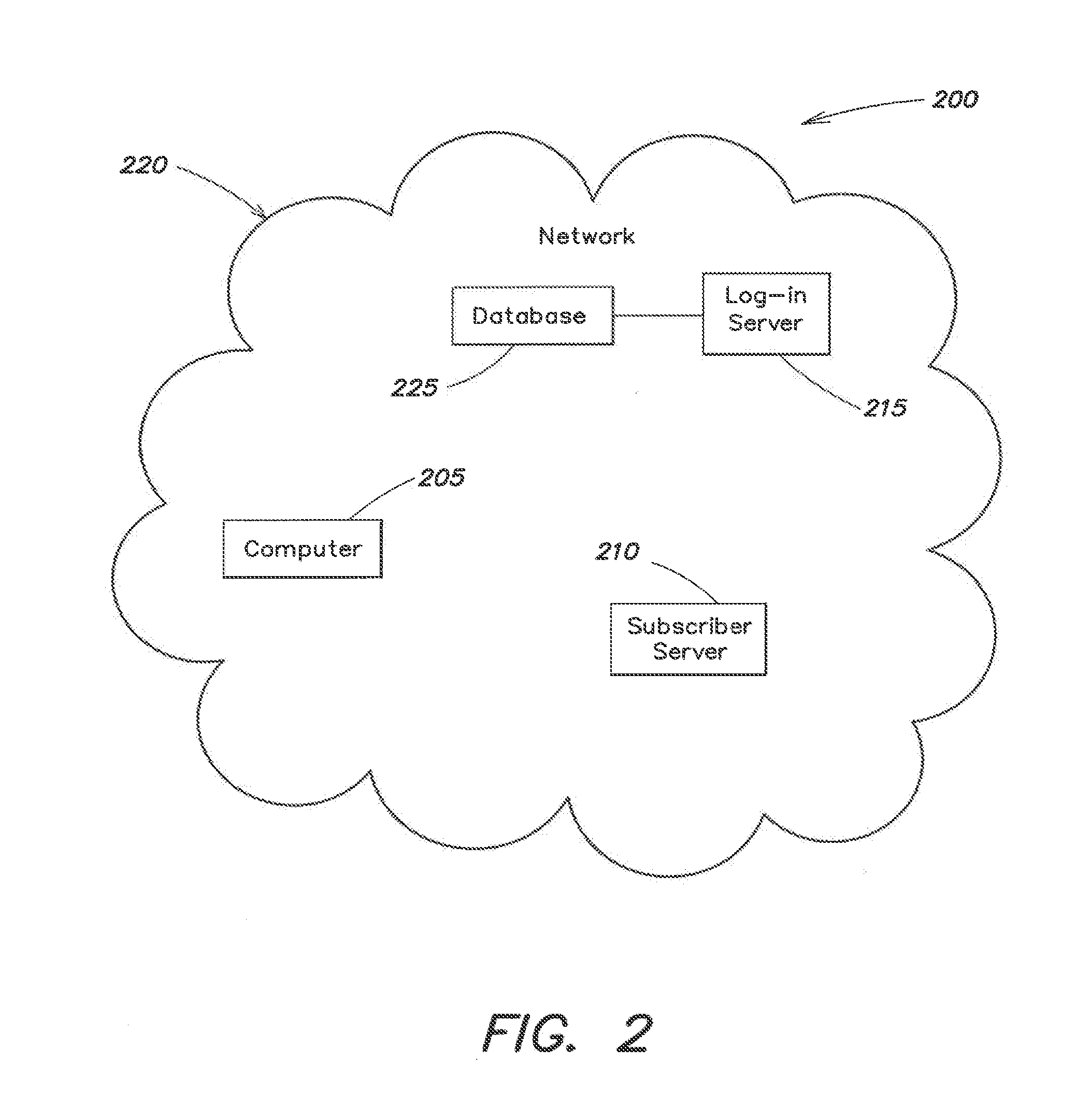
Systems and methods for universal enhanced log-in, identity document verification, and dedicated survey participation
ActiveUS20090055915A1Improve efficiencySafe interactionMarket predictionsDiscounts/incentivesPasswordNetwork connection
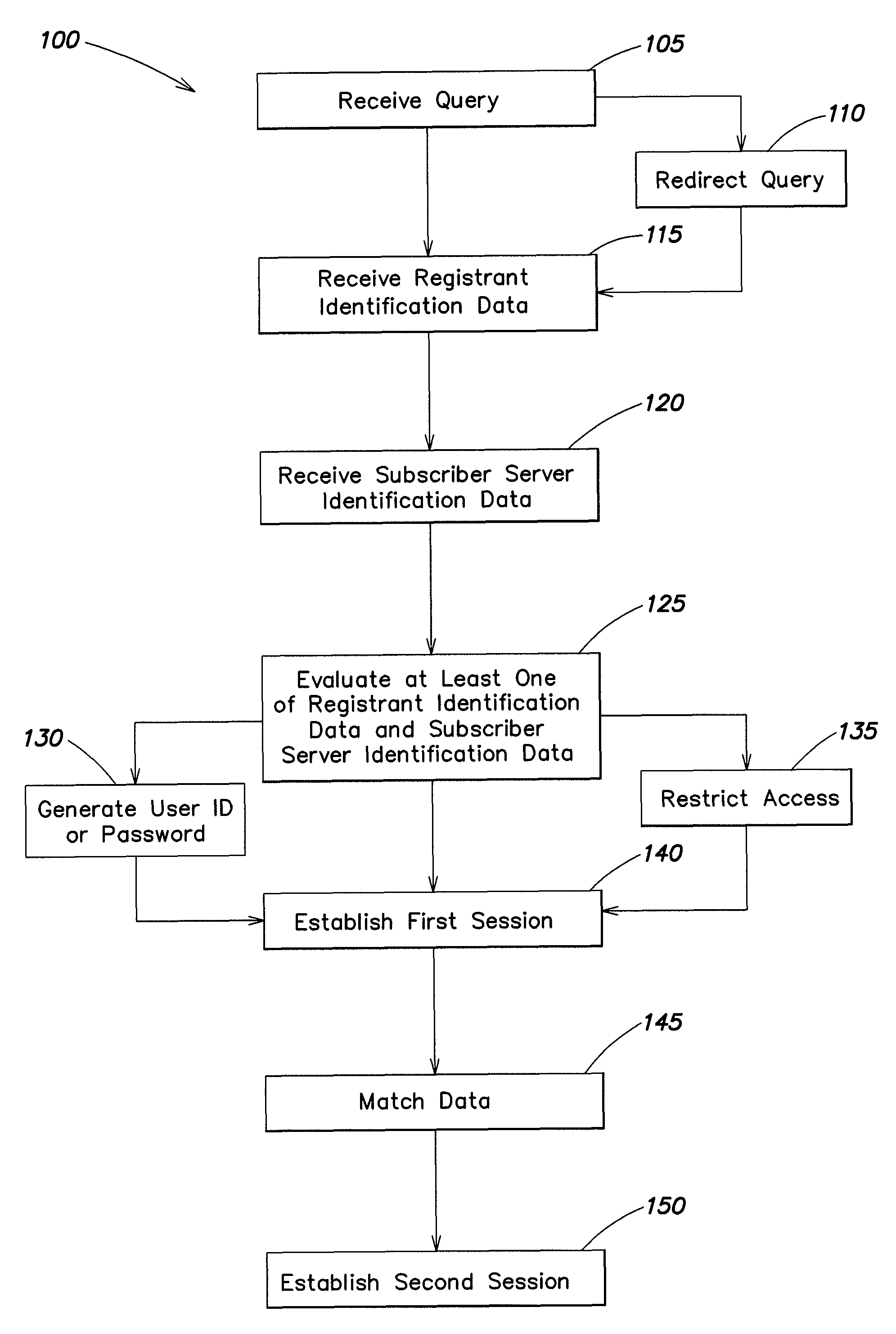
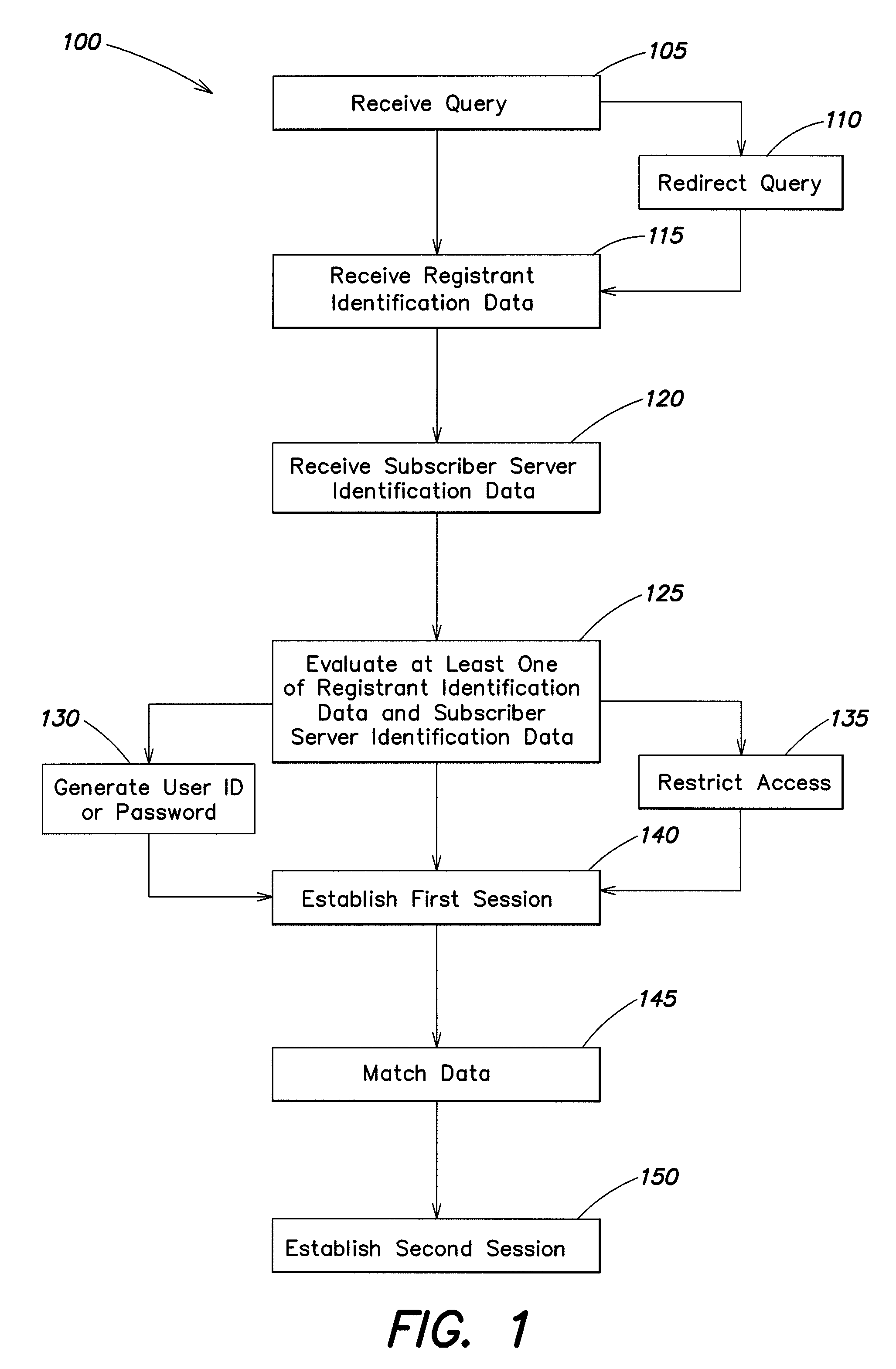
Systems and methods are provided for controlling access via a computer network to a subscriber server. A log-in server receives a query to connect through the computer network to the subscriber server, and the log-in server receives registrant identification data. A first session is established between the log-in server and the subscriber server to validate the registrant identification data, and to generate a session password. A second session is established between the log-in server and the subscriber server. The second session is configured to authorize, based in part on the registrant identification data, access to at least a portion of a website associated with the subscriber server.
Owner:PILIOURAS TERESA C
Method and device for generating secret key
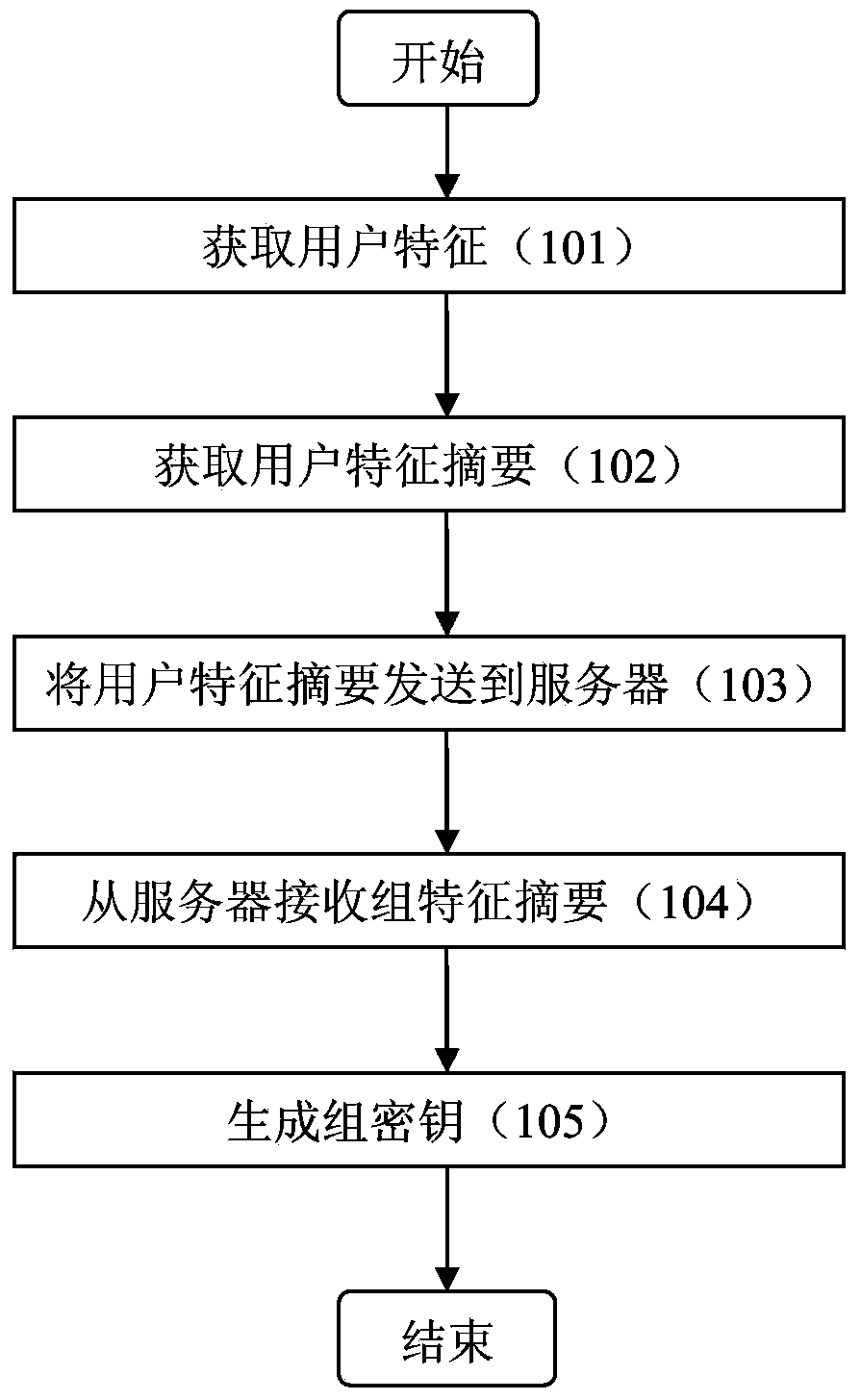
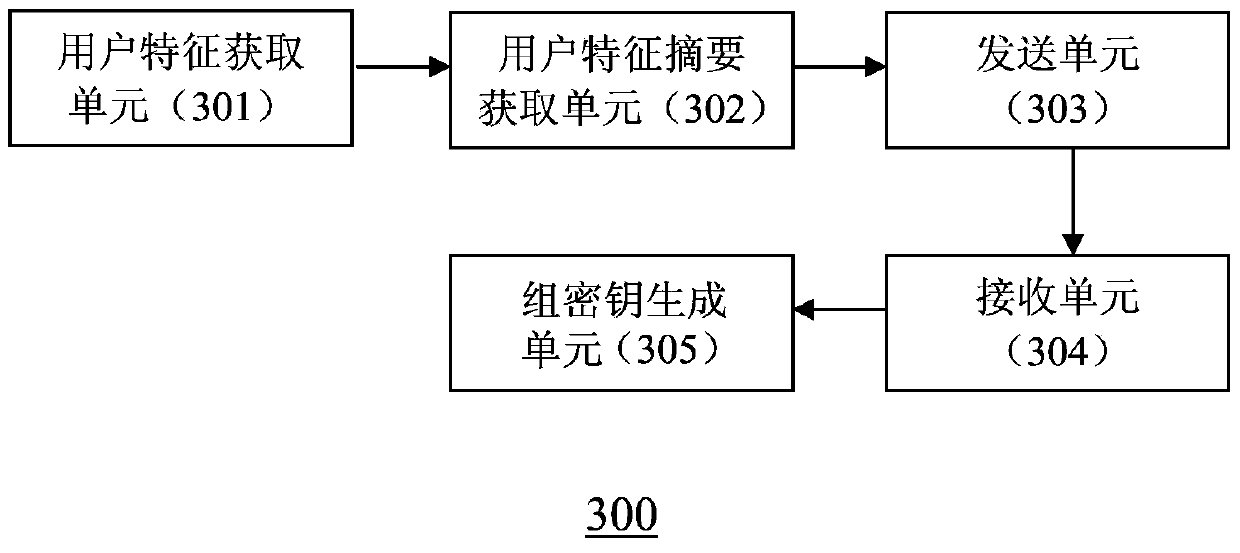
ActiveCN103731258AImprove securityPrevent leakageKey distribution for secure communicationFeature generationComputer security
The invention discloses a method and device for generating a secret key. The method includes the following steps that at least one user characteristic of an electronic terminal is obtained; irreversible abstract generalization is performed on the obtained user characteristic so as to obtain a user characteristic abstract of the electronic terminal; the user characteristic abstract of the electronic terminal is sent to a server; a group characteristic abstract of a group where the electronic terminal exists is received from the server, wherein the group characteristic abstract is determined based on the user characteristic abstract of the electronic terminal; a group secret key of the group where the electronic terminal exists is generated based on the group characteristic abstract of the group where the electronic terminal exists and the user characteristic of the electronic terminal.
Owner:SAMSUNG ELECTRONICS CHINA R&D CENT +1
Systems and methods for universal enhanced log-in, identity document verification, and dedicated survey participation
ActiveUS8056118B2Improve efficiencySafe interactionMarket predictionsDiscounts/incentivesPasswordCipher
Systems and methods are provided for controlling access via a computer network to a subscriber server. A log-in server receives a query to connect through the computer network to the subscriber server, and the log-in server receives registrant identification data. A first session is established between the log-in server and the subscriber server to validate the registrant identification data, and to generate a session password. A second session is established between the log-in server and the subscriber server. The second session is configured to authorize, based in part on the registrant identification data, access to at least a portion of a website associated with the subscriber server.
Owner:PILIOURAS TERESA C
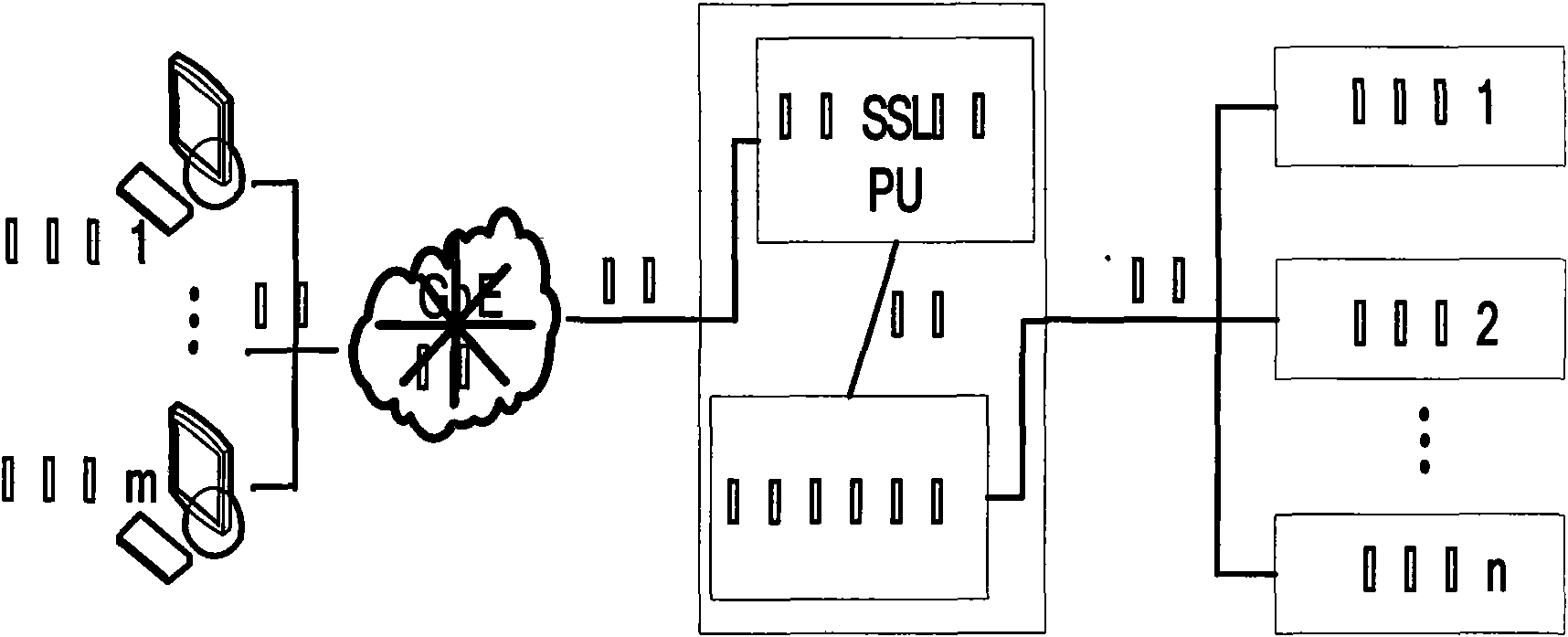
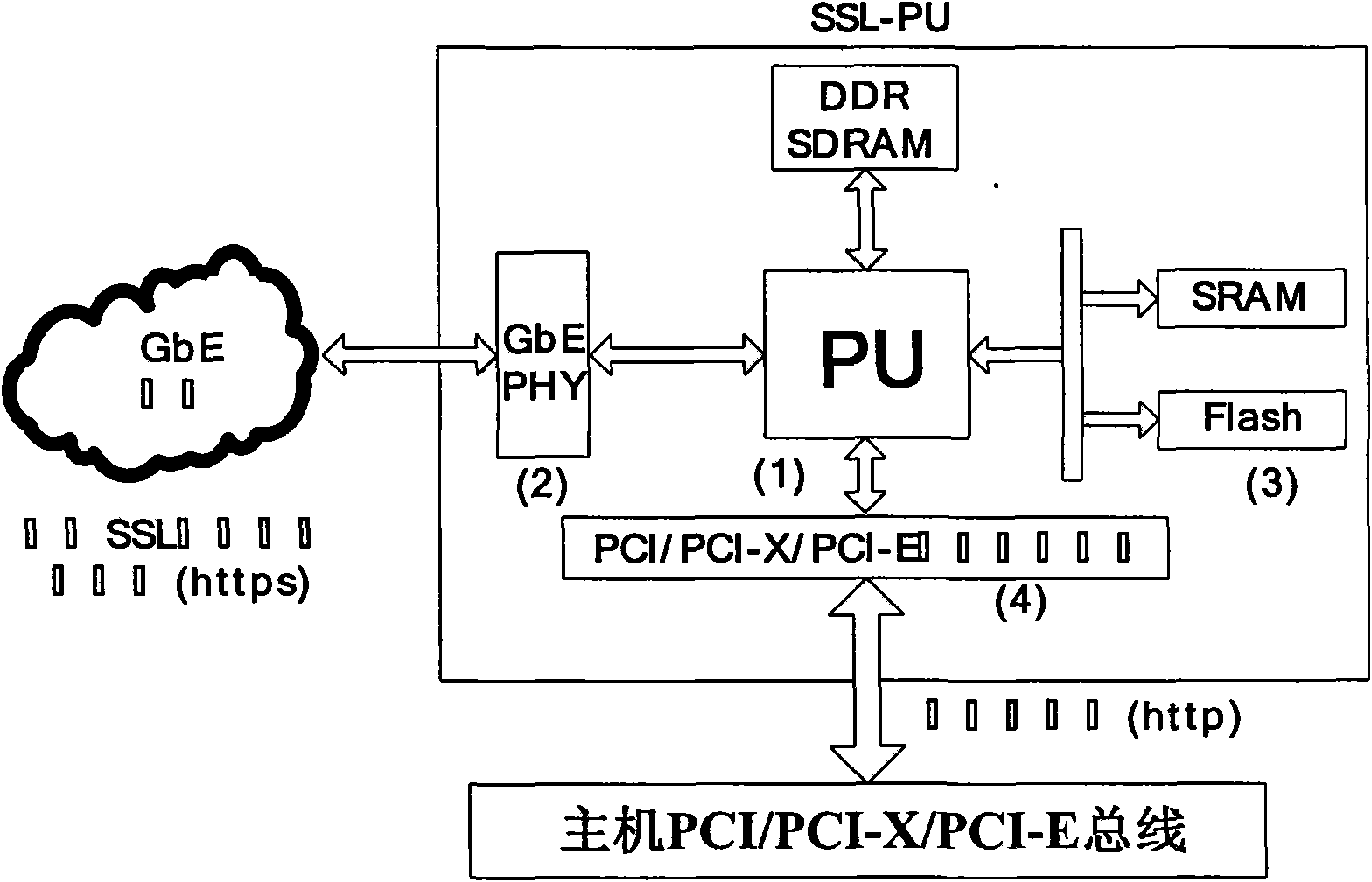
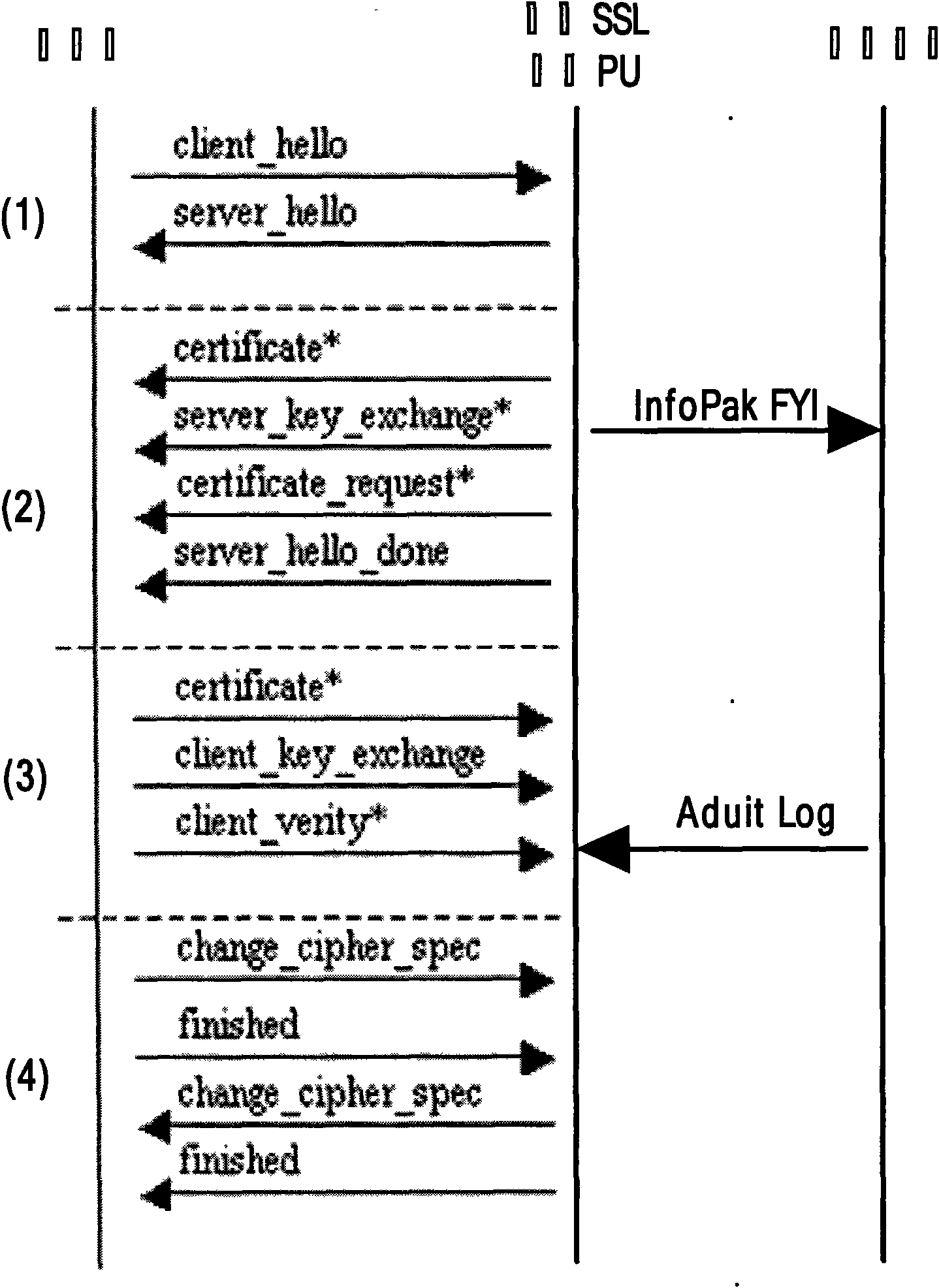
Design architecture and method for secure load balancing by utilizing SSL communication protocol
The invention discloses design architecture and a method for secure load balancing by utilizing SSL communication protocol, in particular to provide secure and reliable data communication for client and load balancing equipment by introducing SSL (Security Socket Layer) communication protocol. The invention mainly designs a processor SSL-PU based on SSL encryption, wherein, the processor SSL-PU is loaded in a load balancer and comprises a processing unit (PU), a memory cell (Flash, SRAM, DDR SDRAM, etc.), an Ethernet network controller (PCI, PCI-X, PCI-E) and GbE PHY (RJ45 interface). SSL-PU well solves the security problem caused by traditional load-balancing equipment and client clear text and the problem that traditional SSL encryption technology based on software excessively occupies system CPU and memory resources, thereby saving server bandwidth, increasing throughput and improving flexibility and availability of network; the processor well realizes the security data interaction with the client, and delivers data in the form of clear text to a load-balancing module; the load balancing module locates a request to a corresponding server according to load balancing algorithm; the server transmits data to the load balancing equipment; and the load balancer with an SSL-PU module transmits encrypted security data to the client, thereby completing secure data interactive access. The invention is particularly suitable for secure load-balancing scheduling of load balancing equipment of which the back end is a cluster system.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
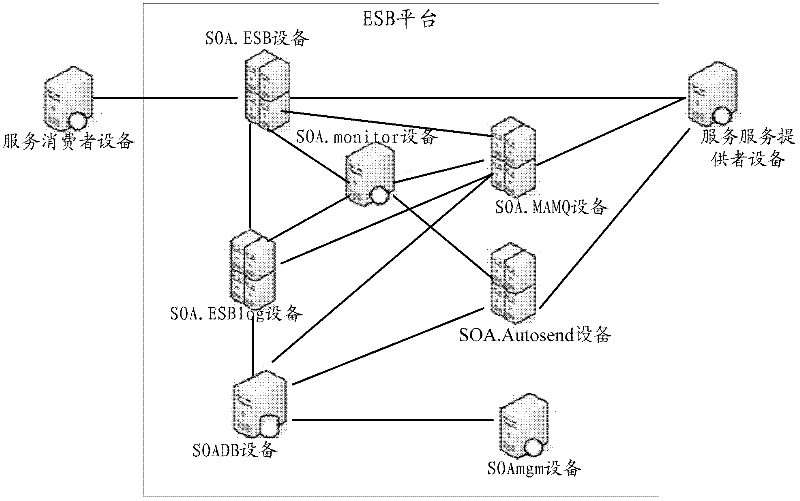
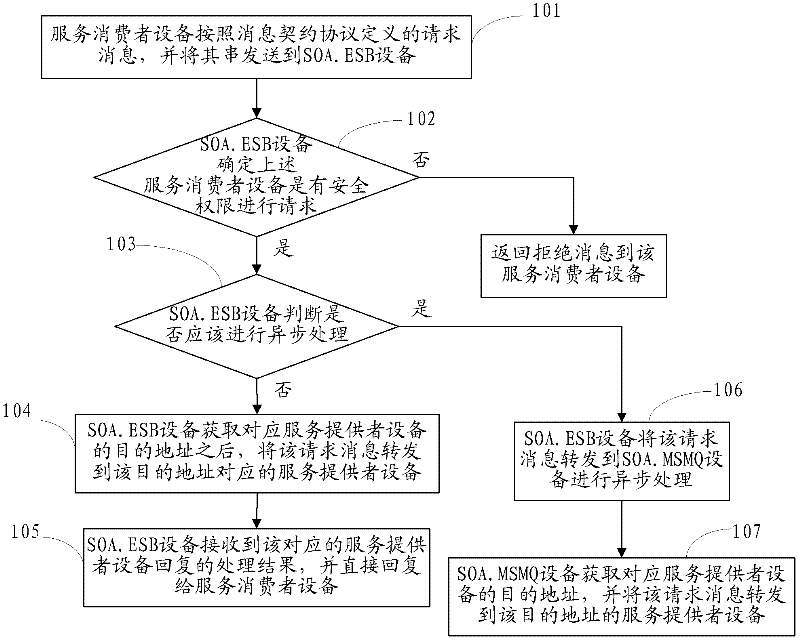
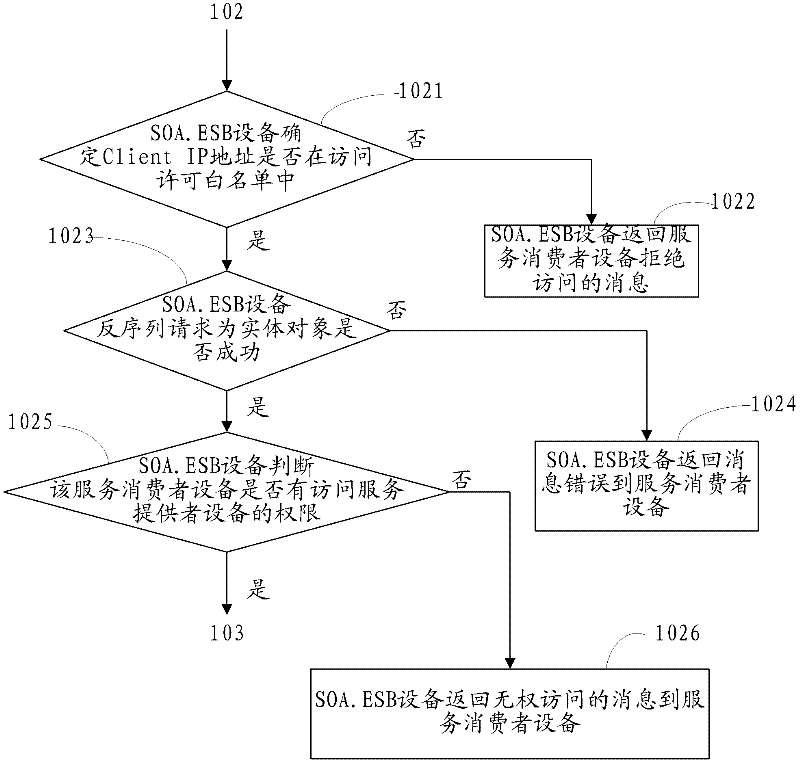
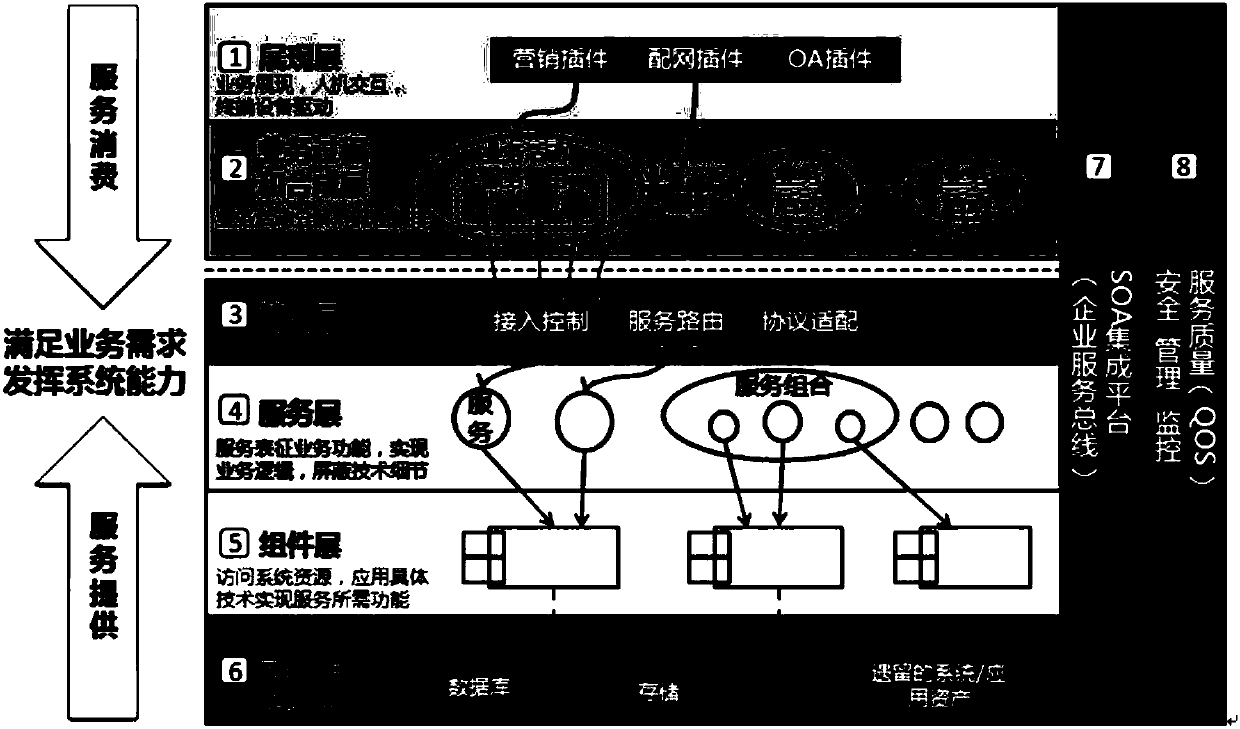
Realization method and equipment for enterprise service bus and corresponding platform
InactiveCN102364921ASafe interactionSimplify the interaction processTransmissionInstrumentsInteraction technologyUser identifier
The invention provides a realization method and realization equipment for an enterprise service bus and a corresponding platform, which relate to an enterprise application system interaction technology and solve the technical problem that the realization method for the enterprise service bus (ESB) in the prior art is excessively heavy for a system. The method provided by the invention mainly comprises that: service-oriented architecture ESB (SOA.ESB) equipment receives a request message which is defined according to a request message protocol from service consumer equipment; the SOA.ESB equipment determines whether the service consumer equipment has security right over requesting or not according to a user identifier carried by the request message; and if the service consumer equipment has the security right over the requesting, the SOA.ESB equipment forwards the request message to corresponding service provider equipment when a message parameter carried by the request message indicates synchronization processing. The method, the equipment and the platform are mainly used for intra-enterprise interaction.
Owner:CTRIP COMP TECH SHANGHAI
Session message processing method and device
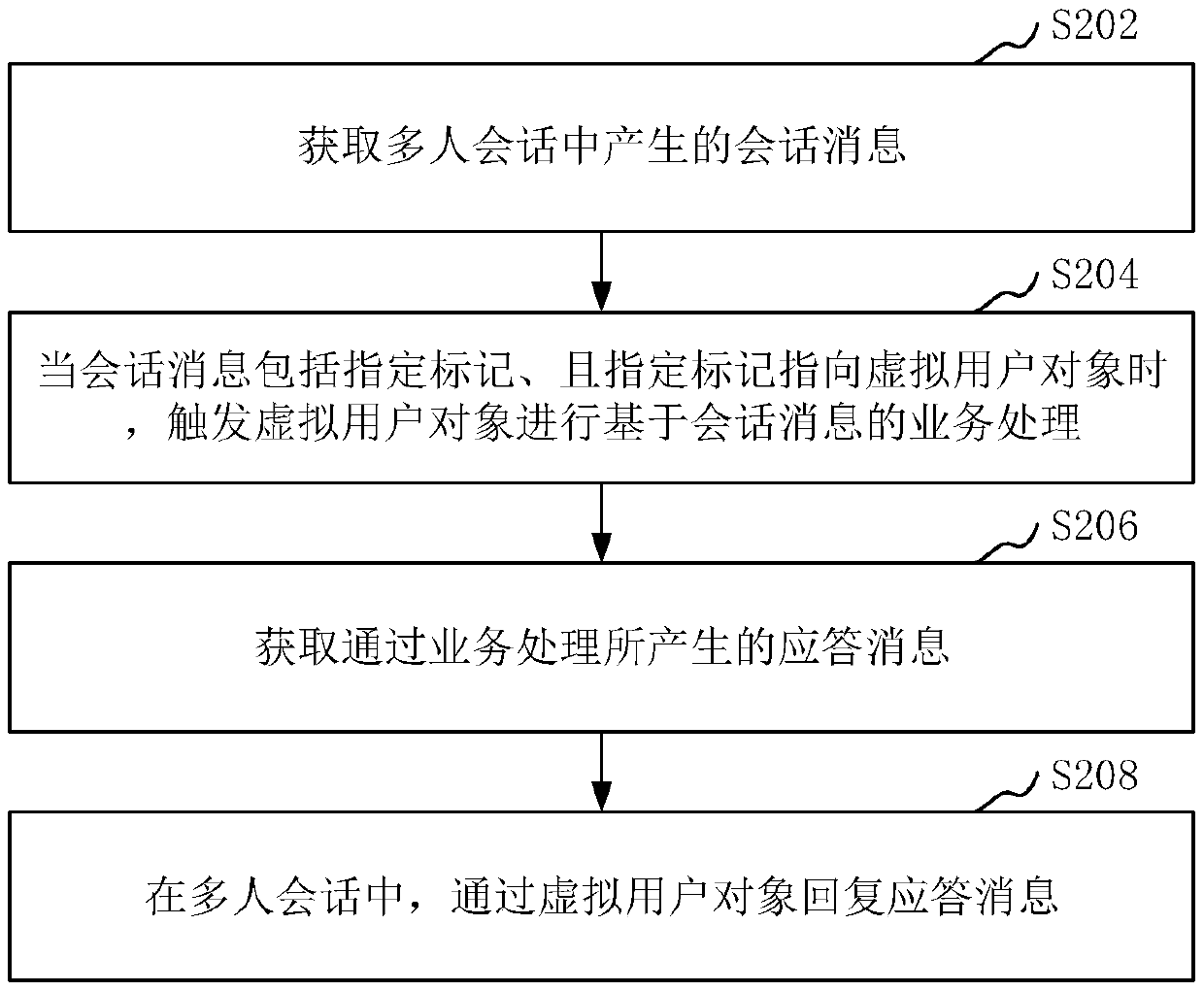
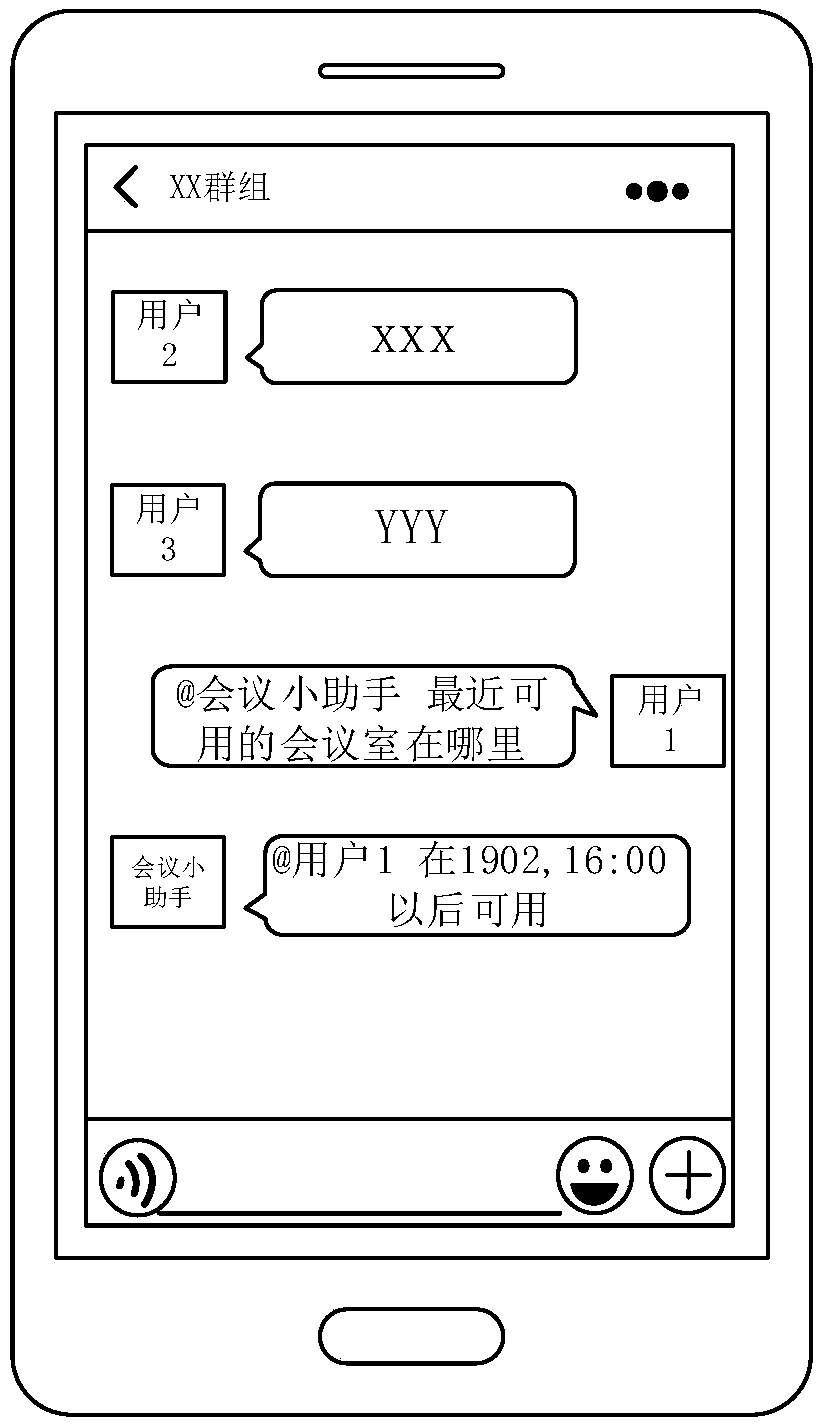
ActiveCN109639828AFlexible and intelligent interactionSafe interactionTransmissionVirtual userMessage processing
The invention relates to a session message processing method and device, computer readable storage medium and computer equipment. The method comprises the steps of acquiring a session message generated in a multi-user session; when the session message comprises a specified mark, and the specified mark points to a virtual user object, triggering the virtual user object to perform business treatmentbased on the session message; acquiring a response message generated via the business treatment; and in the multi-user session, replying to the response message via the virtual user object. Accordingto the scheme provided by the invention, the flexibility of interaction with the virtual user object can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
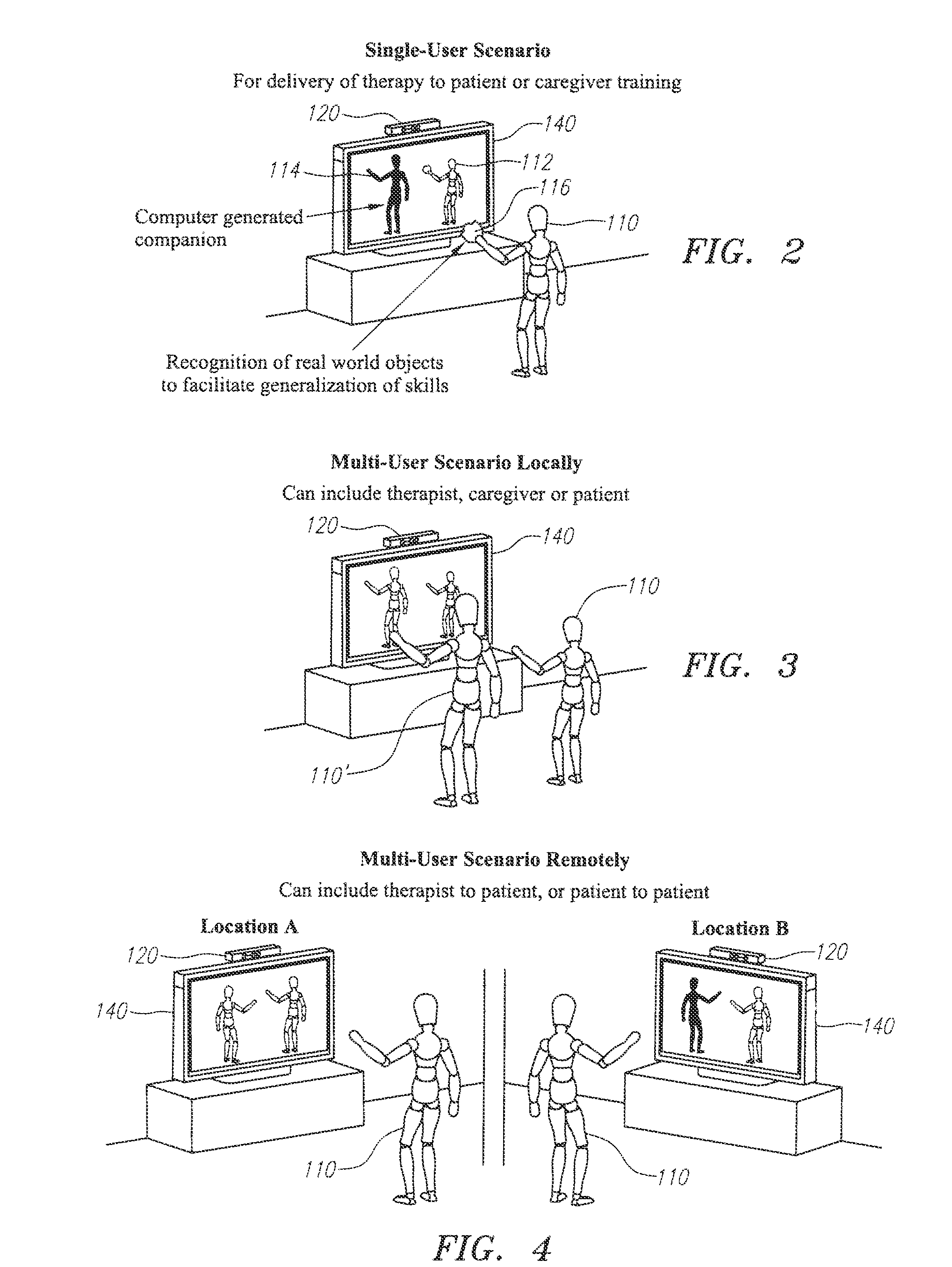
Systems, apparatus and methods for delivery and augmentation of behavior modification therapy and teaching
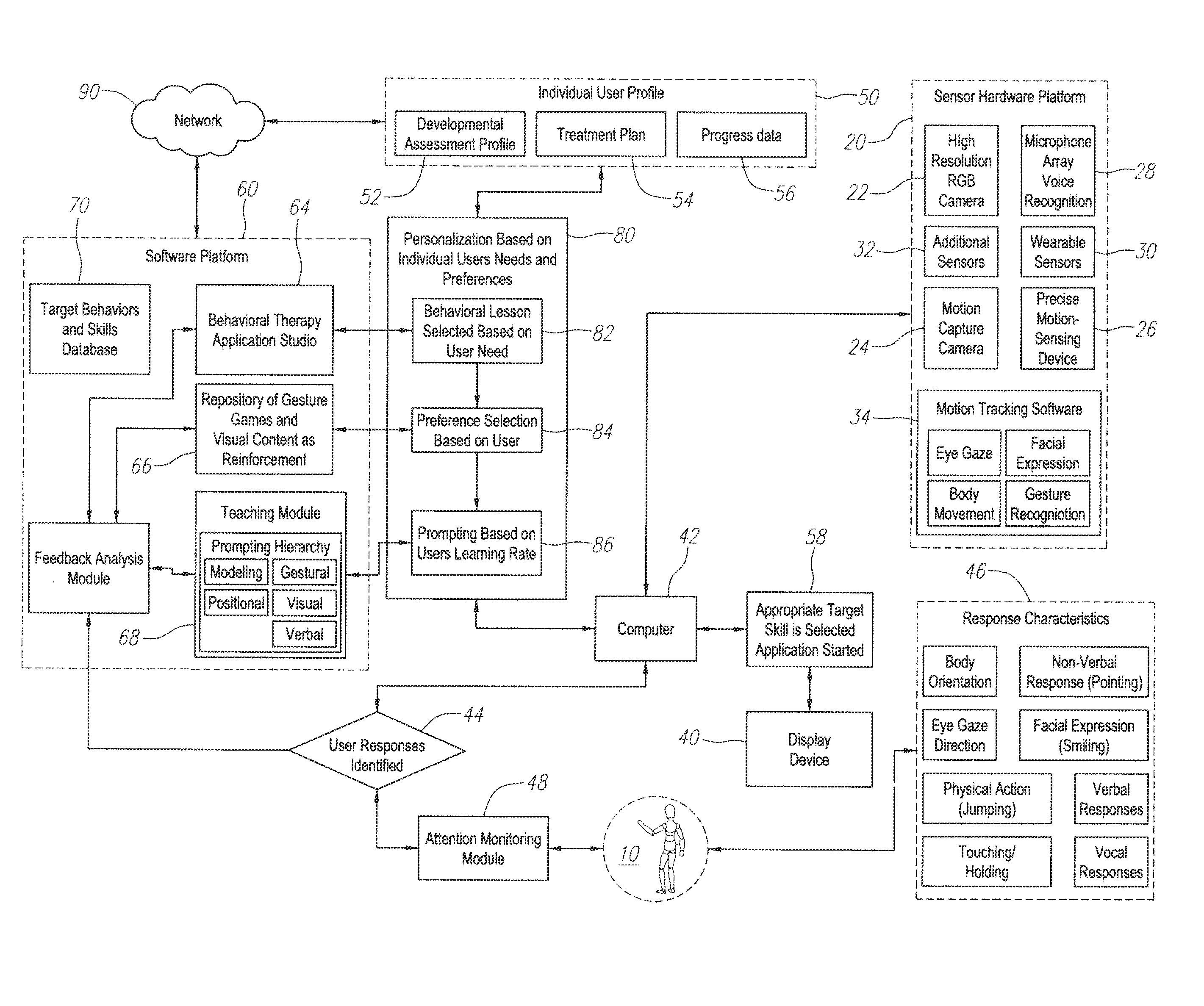
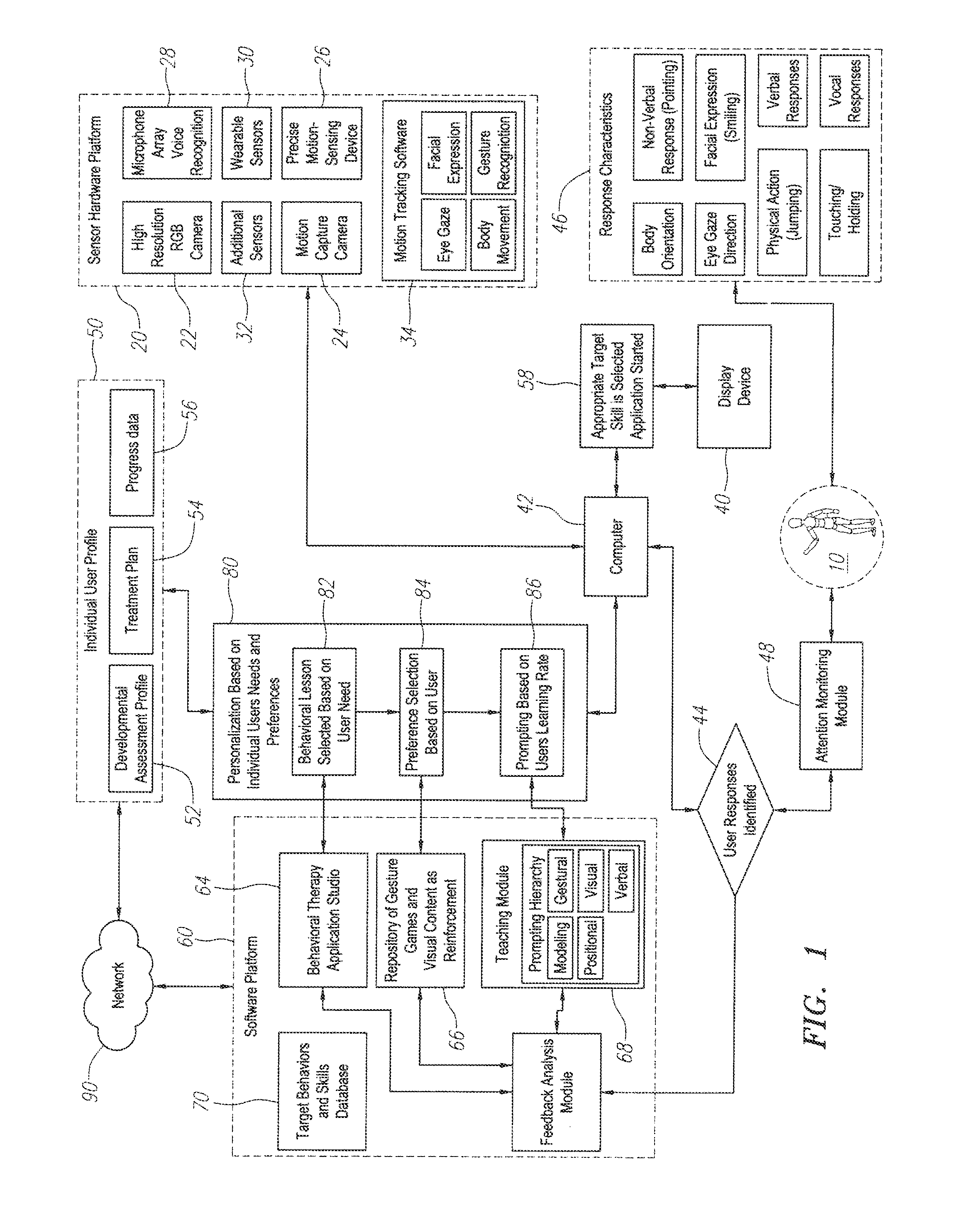
ActiveUS20140370470A1Easy to learnEasy to trackMechanical/radiation/invasive therapiesDiagnostics using lightDisplay deviceUser profile
A system, apparatus and method are provide for a lesson to a user of the system. The lesson may be a behavioral lesson or a teaching lesson, such as where knowledge or skill is being imparted to the user. In one aspect, the inventions include a sensor apparatus, the sensor apparatus generating an output indicative of a user's actions. Memory is provided for storing an individual user profile including at least a plan. and a display. A processor and associated storage comprising a computing platform to generate user feedback
Owner:NORTHEASTERN UNIV
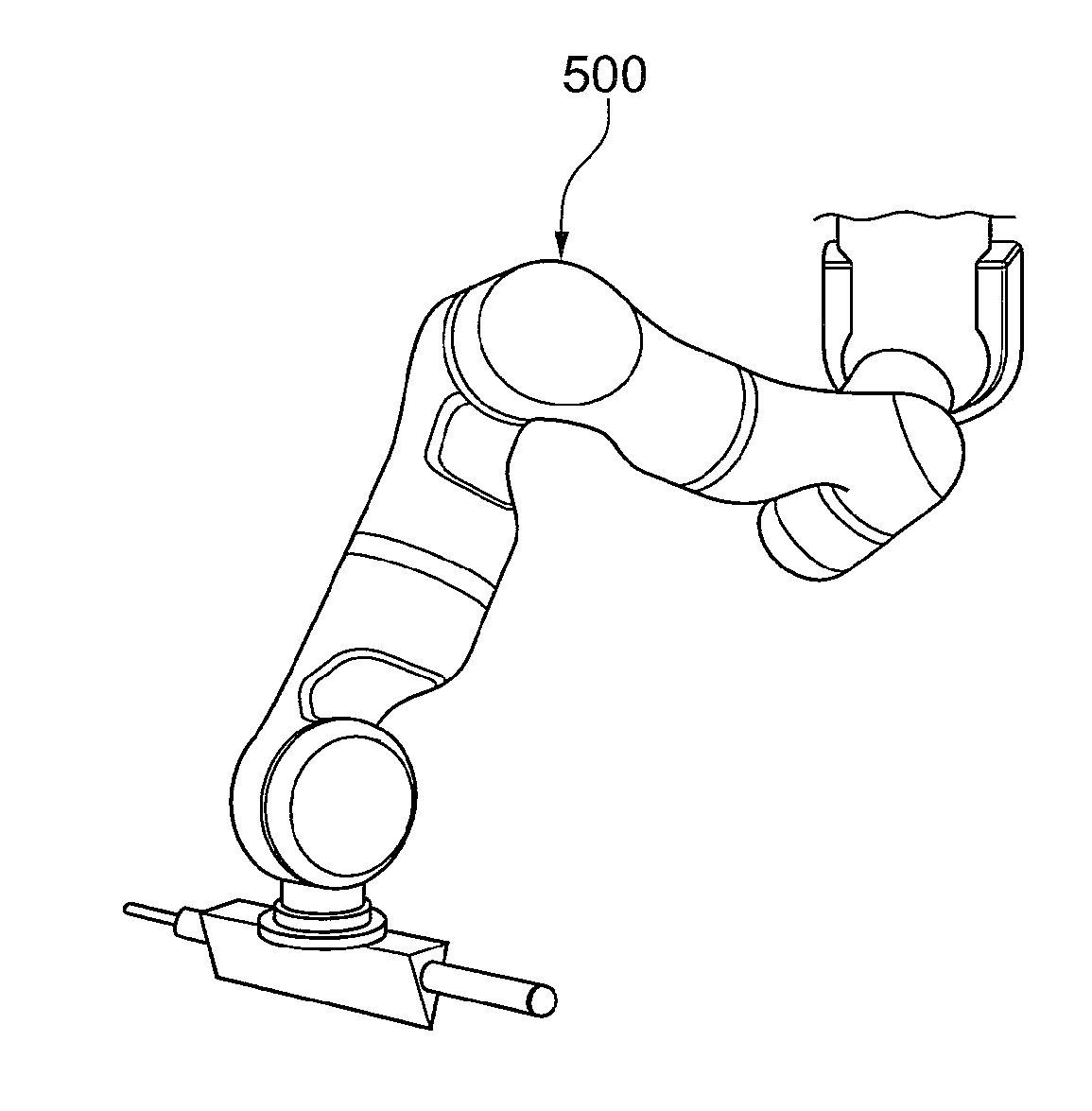
Method for controlling a robot device, robot device and computer program product
ActiveUS20150239124A1Reduce risk of injurySafe interactionProgramme-controlled manipulatorComputer controlManipulatorComputer program
A method for controlling a robot device (500) having a movable manipulator and / or effector (400), according to which method a speed and / or direction of movement of the manipulator and / or effector (400) is monitored and adjusted as appropriate, taking into consideration medical parameters for injury and robot dynamics is provided. A robot device (500) for implementing such a method and to a computer program product for executing such a method.
Owner:DEUTSCHES ZENTRUM FUER LUFT & RAUMFAHRT EV
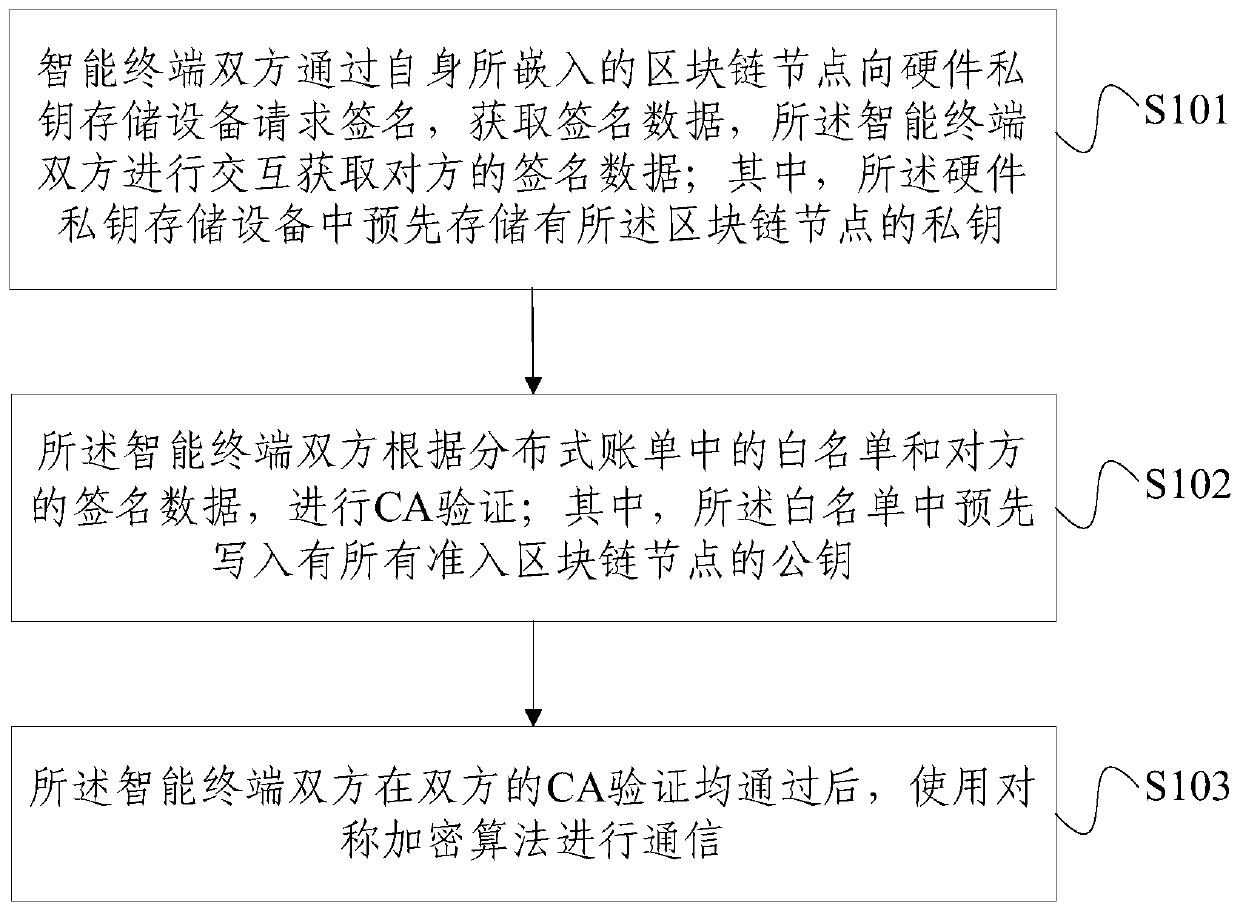
Intelligent terminal safety communication method based on block chain
ActiveCN110581854ASafe interactionReduce complexityUser identity/authority verificationCommunication complexitySecure communication
The invention provides an intelligent terminal safety communication method based on a block chain, which comprises the following steps that: both intelligent terminals request a signature from hardware private key storage equipment through embedded block chain nodes to obtain signature data, and the both intelligent terminals interact to obtain the signature data of the other intelligent terminals, wherein a private key of the blockchain node is pre-stored in the hardware private key storage device; both intelligent terminals perform CA verification according to the white list in the distributed bill and the signature data of the opposite side, wherein public keys of all admission blockchain nodes are written into the white list in advance; after CA verification is passed, both intelligentterminals communicate by using a symmetric encryption algorithm, wherein the blockchain node achieves consensus through a consensus algorithm, and adjusts the topology and the member list of the blockchain network through a distributed identity identification method. According to the invention, the communication complexity is reduced, and the lightweight secure communication is realized; under the condition that resources are limited, safe and credible interaction of data and services between the intelligent terminals is achieved.
Owner:北京笔新互联网科技有限公司
Variable-stiffness three-finger soft-bodied robot
ActiveCN108858269AImprove applicabilityLow processing and manufacturing costsGripping headsMesh gridElectrical and Electronics engineering
The invention discloses a variable-stiffness three-finger soft-bodied robot. Each soft-bodied finger is driven by a gas to produce a bending variable-stiffness effect and mainly comprises a driving layer, an inextensible layer and a variable-stiffness layer, wherein the driving layer consists of a plurality of gas bags communicating with one another and can be bent under a positive pressure; the inextensible layer mainly comprises a silica gel substrate with gridding cloth embedded therein and can limit tensile deformation of the corresponding soft-bodied finger during bending deformation; artificial scales which are sequentially distributed in a stacked manner are arranged in the variable-stiffness layer, and the variable-stiffness layer can be pressed under the positive pressure to achieve a soft-to-stiff effect; and the soft-bodied fingers are mainly formed by die casting, and part of structures can be manufactured by means of the 3D printing technology. The variable-stiffness three-finger soft-bodied robot realizes non-destructive grabbing of a produced object while guaranteeing the grabbing speed.
Owner:TIANJIN UNIV
Human-machine cooperation oriented bionic lightweight mechanical arm
PendingCN110202559AGuaranteed symmetryIncrease stiffnessProgramme-controlled manipulatorEngineeringDrive motor
The invention discloses a human-machine cooperation oriented bionic lightweight mechanical arm comprising a first machine arm, a second machine arm, a wrist joint, an elbow joint and a shoulder joint.The first machine arm is arranged between the shoulder joint and the elbow joint, the second machine arm is arranged between the elbow joint and the wrist joint, the wrist joint is a three-degree-of-freedom motion pair, the wrist joint includes a two-degree-of-freedom parallel mechanism connected with a single-degree-of-freedom Hook hinge mechanism in series, the elbow joint is a single-degree-of-freedom rotational joint, and the shoulder joint is a three-degree-of-freedom parallel ball joint mechanism; and the mechanical arm further comprises an elbow joint drive motor and three wrist jointdrive motors, and the elbow joint drive motor arranged at the end, close to the shoulder joint, of the second machine arm and the wrist joint drive motors control the elbow joint and the wrist joint through rope drive transmission. By means of the mechanical arm, the collision inertia is reduced, and therefore the safety of human-computer interaction is improved.
Owner:SOUTH CHINA UNIV OF TECH
Multi-functional reconfigurable pet enrichment system
ActiveUS20160286761A1Safe interactionProvide spaceAnimal housingTaming and training devicesFastenerEngineering
A reconfigurable pet enrichment system designed to help pets fulfill their natural behaviors is provided. The system is arranged to facilitate an environment that helps stimulate, entertain, and exercise a pet, and also provides a defensible space for napping, resting, or sleeping. The system is constructed from two separate pieces of pliable material. A base component is fashioned with a non-slip element. A top-covering component is attached to the base component, by means of semi-permanent fasteners, to create a variety of forms such as ripples, nooks and tunnels. The top component contains a plurality of differing sized openings. Openings appeal to a pet's predatory nature, as the openings provide a source of stimulation and interaction. The pet enrichment system may be formed of any desired material, so as to be safe for pet interaction. The system may also be configured with a plurality of members attached via semi-permanent fasteners.
Owner:RUCKEL FREDERICK W +1
Heparin barrier coating for controlled drug release
ActiveUS8182527B2Good curative effectReduce in quantitySuture equipmentsOrganic active ingredientsDrug releasePolymer
Medical devices, and in particular implantable medical devices, may be coated to minimize or substantially eliminate a biological organism's reaction to the introduction of the medical device to the organism. The medical devices may be coated with any number of biocompatible materials. Therapeutic drugs, agents or compounds may be mixed with the biocompatible materials and affixed to at least a portion of the medical device. In addition, various polymer combinations as well as other therapeutic agents may be utilized to control the elution rates of the therapeutic drugs, agents and / or compounds from the implantable medical devices.
Owner:WYETH LLC
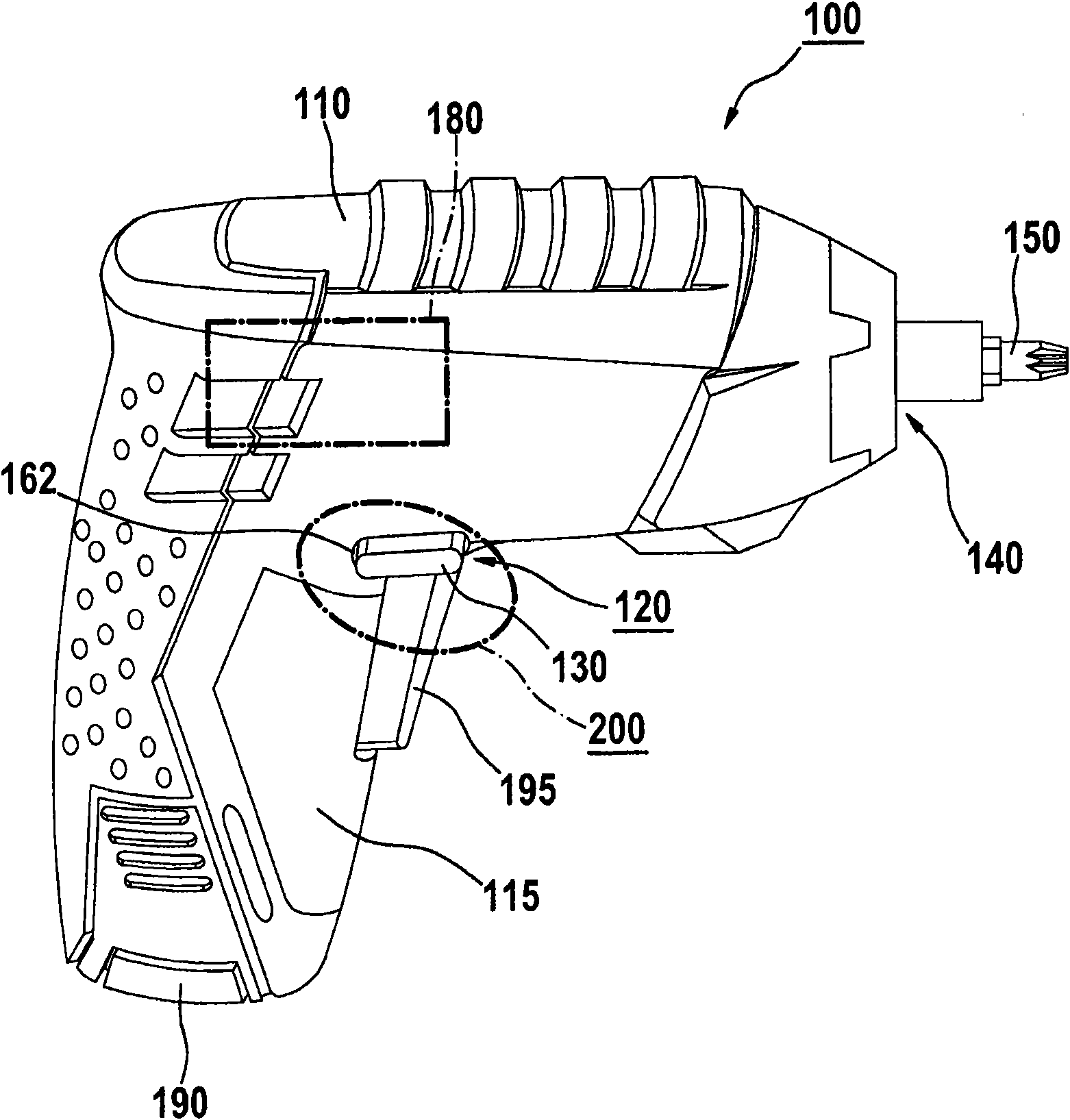
Hand-held power tool
ActiveCN101954635ASave construction spaceCompact structureElectric switchesPortable power-driven toolsHand heldDrive motor
The invention relates to a hand-held power tool, which has a device (120) for presetting a selected rotation direction of a drive motor (180) that is associated with the power tool and contained in a tool housing (110). The device (120) is equipped with an actuating element (130) accessible from outside the tool housing (110) for mechanically actuating a switch element (110), which is situated inside the tool housing (110) and is at least embodied for electrically switching between a first and second rotation direction of the drive motor (180), the switch element (230) is situated in the vicinity of the actuating element (130).
Owner:ROBERT BOSCH GMBH
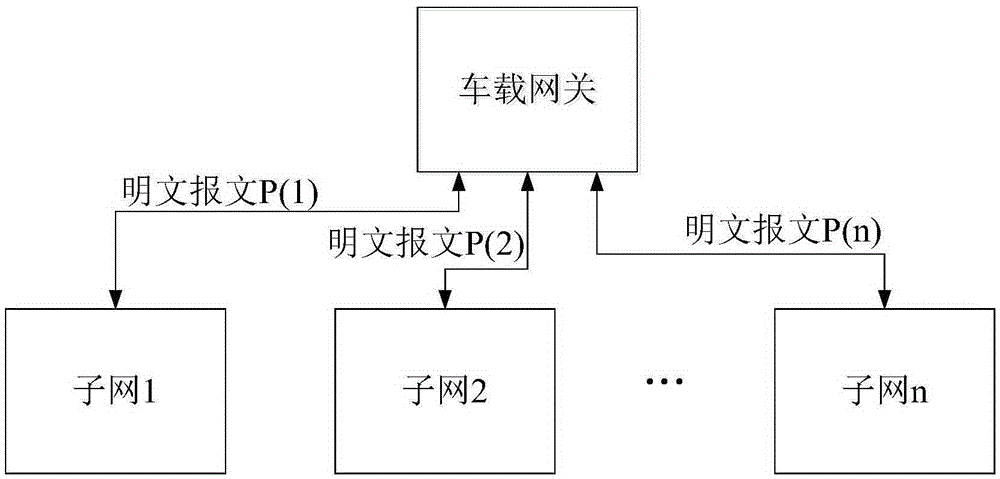
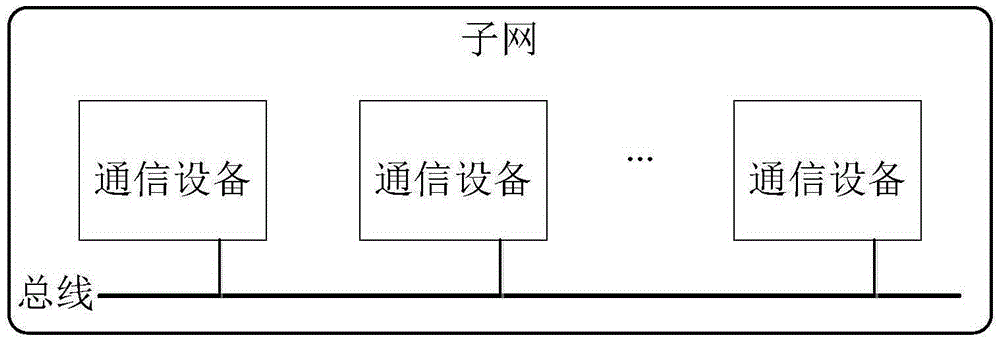
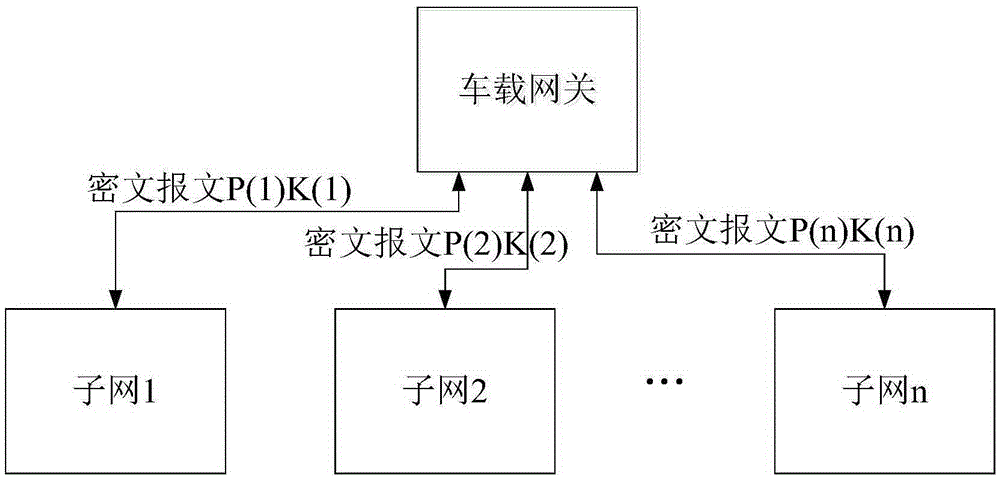
Data communication method and system and gateway applied to in-vehicle network comprising multiple sub-networks
InactiveCN105897819AEnsure safetyGuaranteed stabilityData stream serial/continuous modificationMultiple keys/algorithms usageCiphertextIn vehicle
An embodiment of the application provides a data communication method and system and a gateway applied to an in-vehicle network comprising multiple sub-networks. The data communication method applied to the in-vehicle network comprising the multiple sub-networks comprises the following steps: first encrypted message sent to a second sub-network from a communication device of a first sub-network is obtained; the first encrypted message is decoded via a predetermined first sub-network safe secret key, and first message data is obtained; the first message data is converted into second message data that conforms with a second sub-network communication protocol, the second message data is encrypted via a predetermined second sub-network safe secret key, and a second encrypted message is obtained; the second encrypted message is sent to a corresponding communication device in the second sub-network. Via use of the data communication method and system and the gateway applied to the in-vehicle network comprising the multiple sub-networks, messages transmitted among the sub-networks can be sent in forms of cryptographs, and in-vehicle network security can be improved.
Owner:FAFA AUTOMOBILE (CHINA) CO LTD
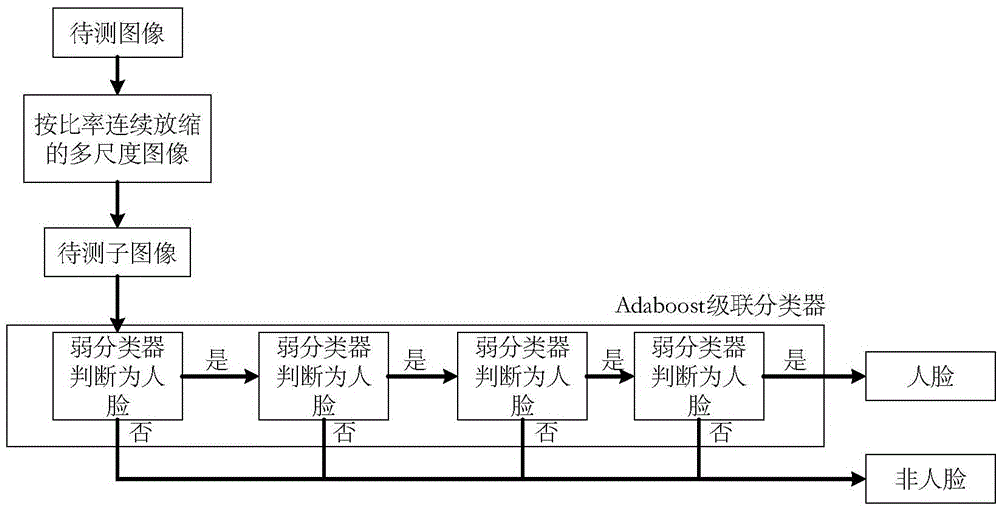
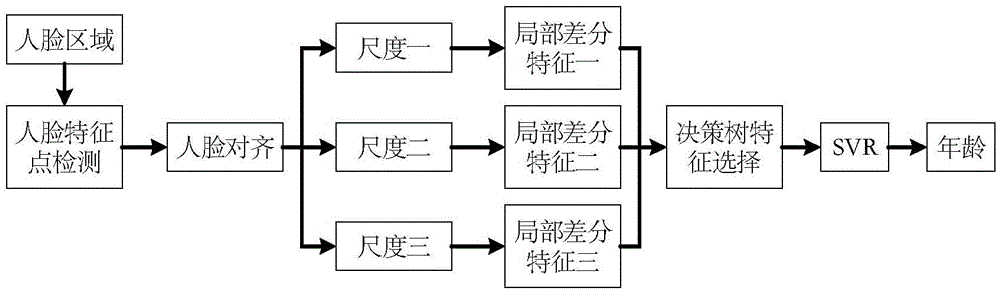
Age estimation method and system based on multi-scale linear differential textural features
ActiveCN105550641AInteractive humanitySafe interactionCharacter and pattern recognitionCharacteristic spaceEuclidean vector
The invention discloses an age estimation method and system based on multi-scale linear differential textural features. The method includes the steps of: first, using Haar-like features and an Adaboost classifier algorithm to detect a face in a picture to be detected, and cutting out a face region; then extracting textural features based on multi-scale linear differential features from the face region that is cut out, using a decision-making tree to perform feature selection, and reducing feature vector dimensionality; and finally training an SVR model in a feature space after the feature vector dimensionality is reduced, and using the SVR model to perform age prediction of the face picture. Since RBF kernel-based nonlinear support vector regression is used as a classifier model to perform age estimation, the age estimation is relatively accurate, and in addition, the age estimation is performed through the face picture, thereby enabling human-computer interaction to be relatively humanized and safe.
Owner:KONKA GROUP
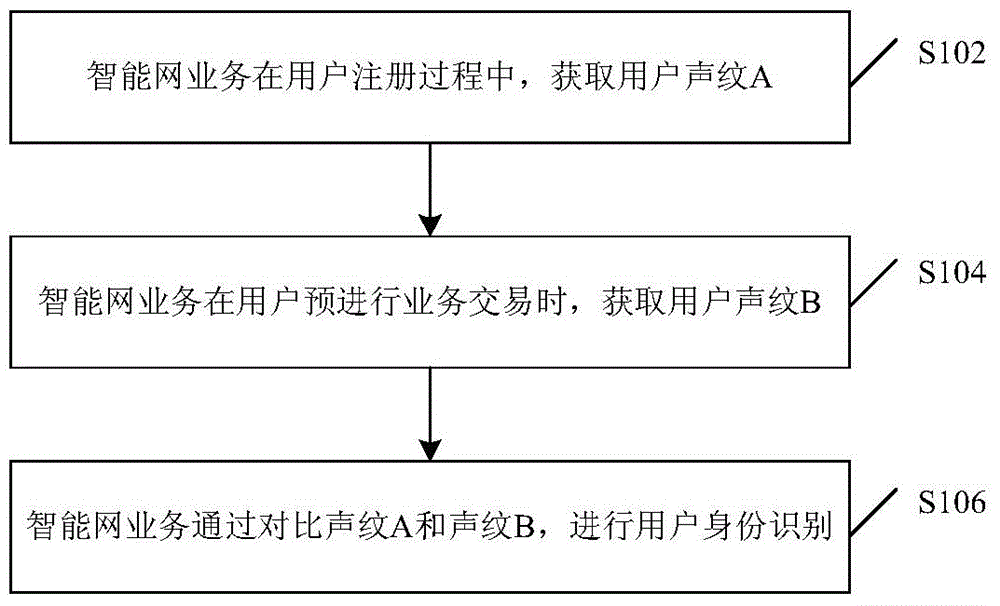
Identity identifying method and device
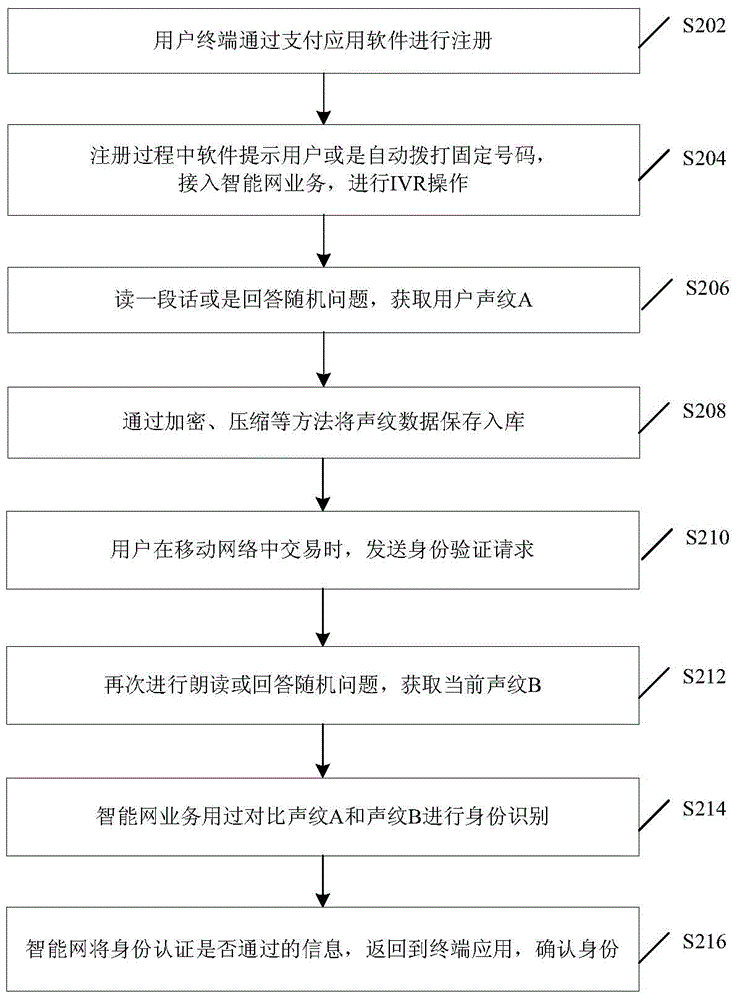
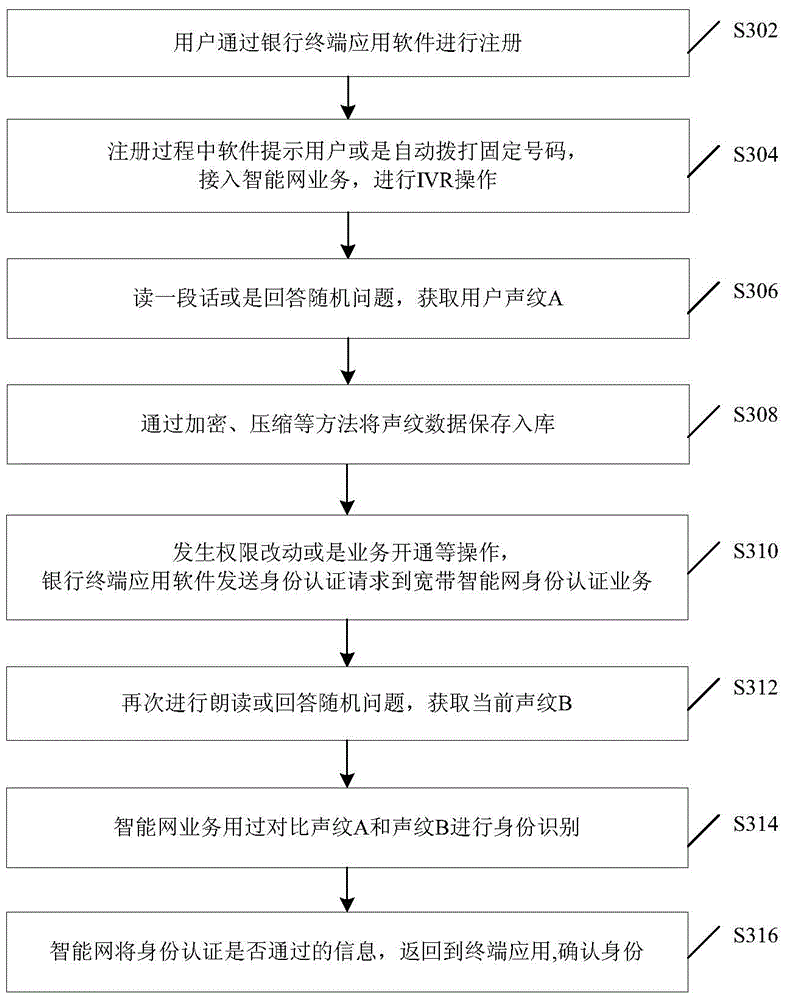
InactiveCN105096954AAvoid illegal acquisitionSolve problems with efficient and reliable control implementation methodsInterconnection arrangementsSpeech analysisIdentity recognitionData acquisition
Disclosed are an identity recognition method and apparatus, and a storage medium. The method is applied to an intelligent network, and comprises: obtaining a user voiceprint A during registration of a user; obtaining a user voiceprint B when the user intends to perform a business transaction; and recognizing an identity of the user by comparing the voiceprint A with the voiceprint B. By using a service of performing identity recognition through a voiceprint based on a broadband intelligent network, the problem in the prior art that a voiceprint recognition technology lacks an efficient and reliable control implementation method in the mobile payment field is solved. Control and data collection from a terminal to a server can be effectively implemented by using a call, and an operator's intelligent service and the terminal's transactional APP software are combined, so that a phishing website and viruses are prevented from illegally obtaining user information, thereby providing a reliable identity authentication environment for high-value transactions in the mobile Internet. In addition, more reliable and unique identity authentication is provided through the voiceprint recognition.
Owner:ZTE CORP
Power demand side management platform
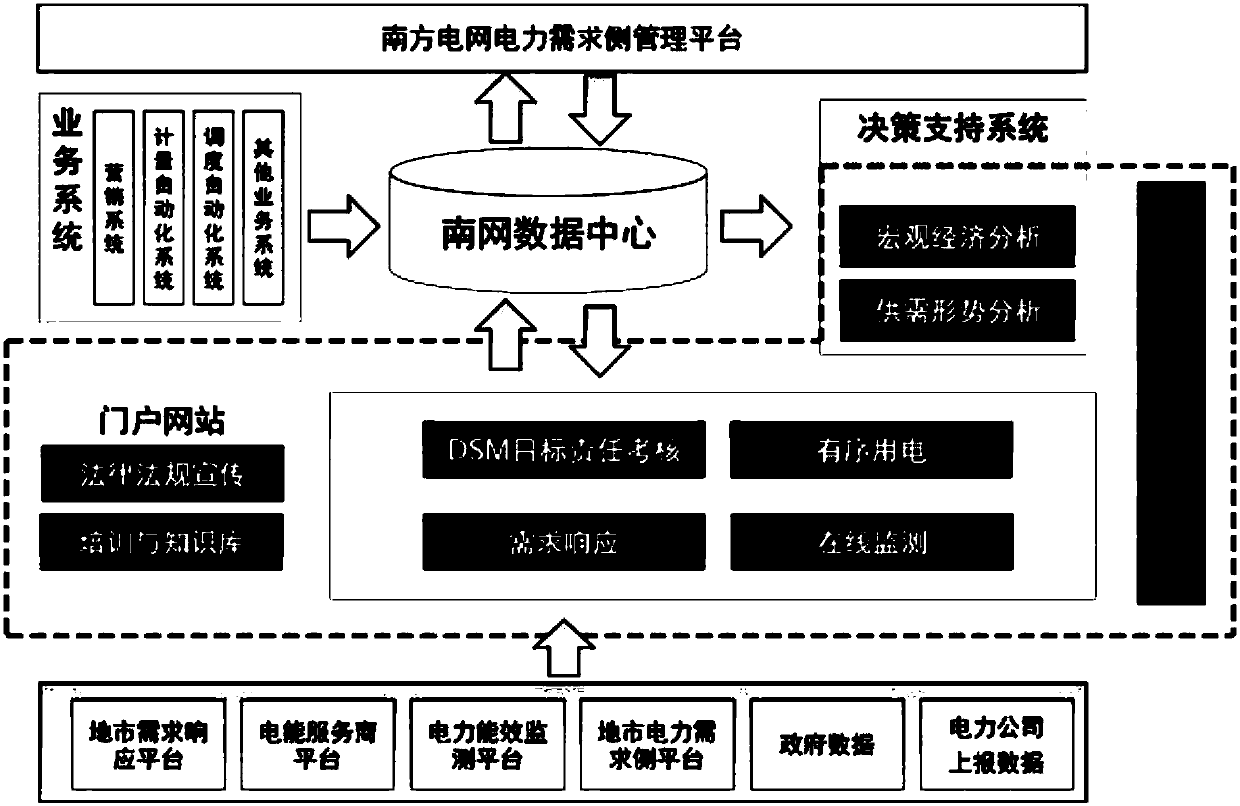
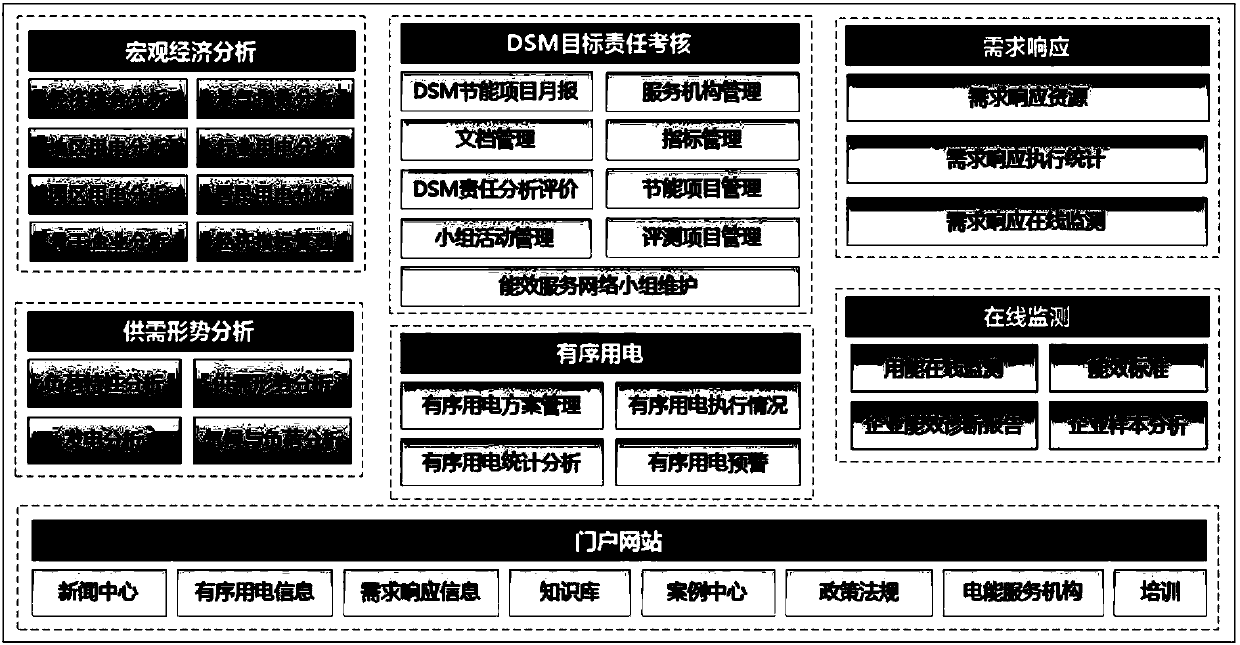
InactiveCN107657389AImprove the level of work informationHigh-speed integrated managementTechnology managementResourcesManagement toolElectric power system
The present invention discloses a power demand side management platform for solving a technical problem that a scientific, reasonable and efficient power demand side management tool is urgently neededat present to help power demand side management departments and personnel to arrange limited demand-side resources as efficient and reasonable as possible. The present invention focuses on the business needs of a power system and provides unified external interface service, the service integration with other systems such as a marketing system, a metering automation system and a dispatching automation system is realized, the platform is designed from seven aspects of macroeconomic analysis, supply and demand situation analysis, DSM target responsibility assessment, ordered power consumption, demand response, on-line monitoring and a portal web, and the integrated management of high-speed, secure and reliable interaction of power system service and data quality supervision is realized frommany aspects.
Owner:ELECTRIC POWER RES INST OF GUANGDONG POWER GRID
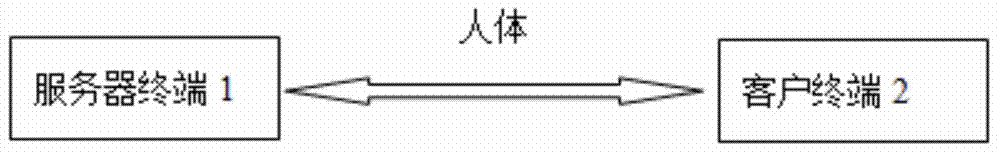
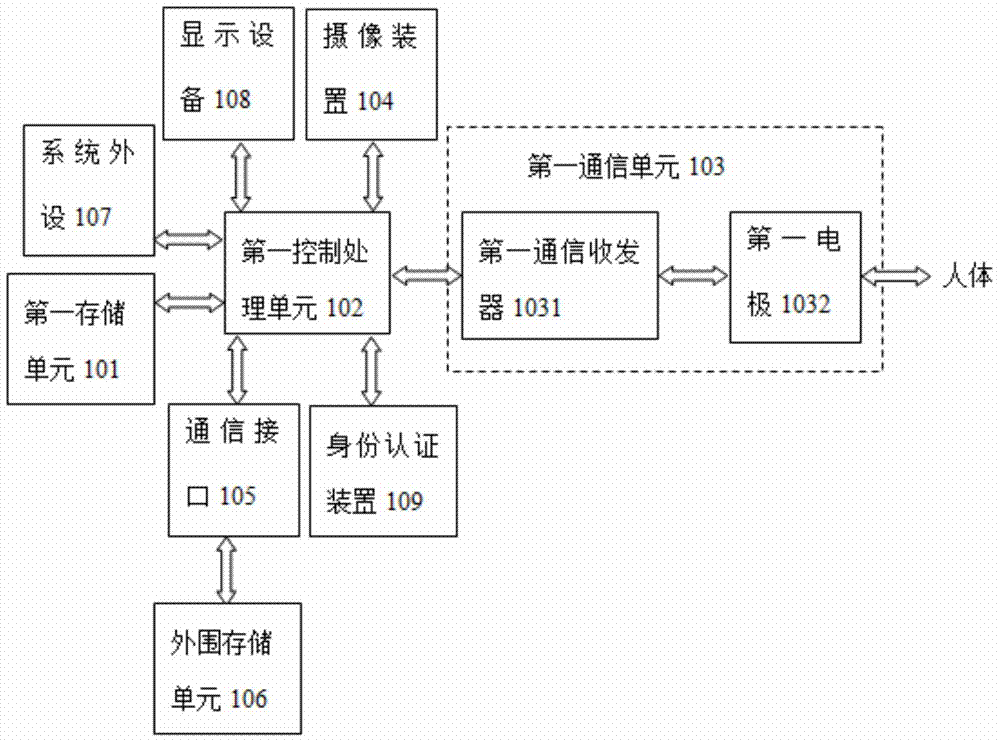
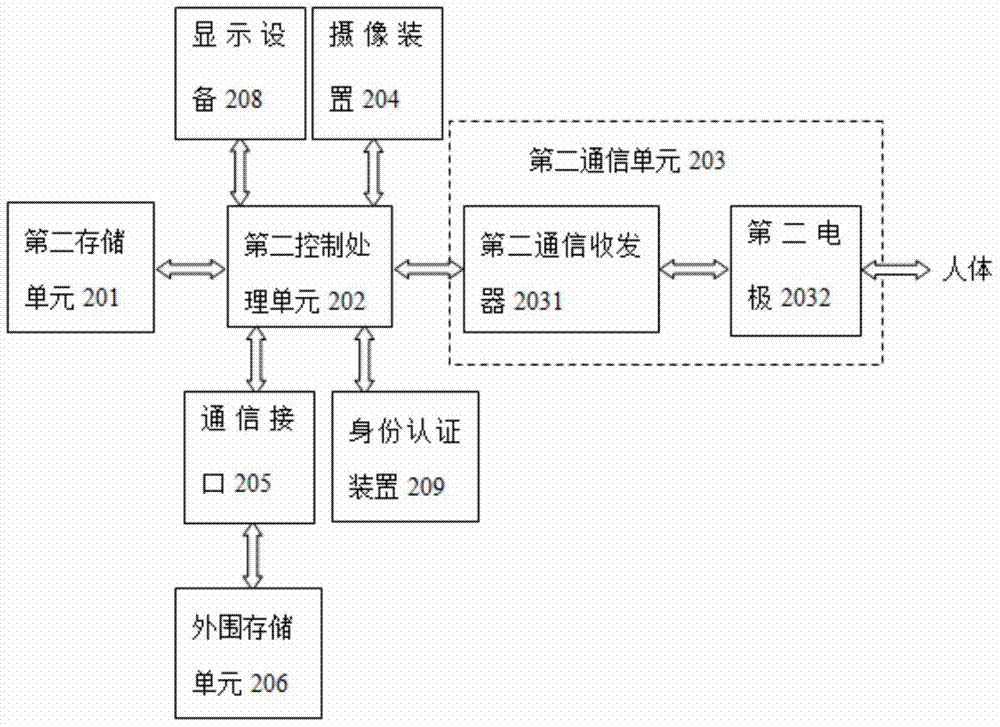
Server terminal for information interaction, client terminal and information interaction system
ActiveCN103944649AConvenient and fast interactive dataLow costTransmissionInteraction systemsCommunication unit
The invention discloses an information interaction system which comprises a server terminal and a client terminal. The server terminal comprises a first storage unit, a first processing control unit and a first communication unit. The first storage unit is used for storing service information and received data information, and the first communication unit is controlled by the first processing control unit and used for sending the service information or receiving the data information. The client terminal can be worn on a human body, and the client terminal comprises a second storage unit, a second processing control unit and a second communication unit. The second storage unit is used for storing the data information of a client and the received service information, and the second communication unit is controlled by the second processing control unit and used for sending the data information or the received service information. The server terminal and the client terminal achieve information interaction through the first communication unit and the second communication unit.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
Systems and methods for universal enhanced log-in, identity document verification, and dedicated survey participation
ActiveUS20120010924A1Improve efficiencySafe interactionMarket predictionsDiscounts/incentivesPasswordNetwork connection
Owner:PILIOURAS TERESA C
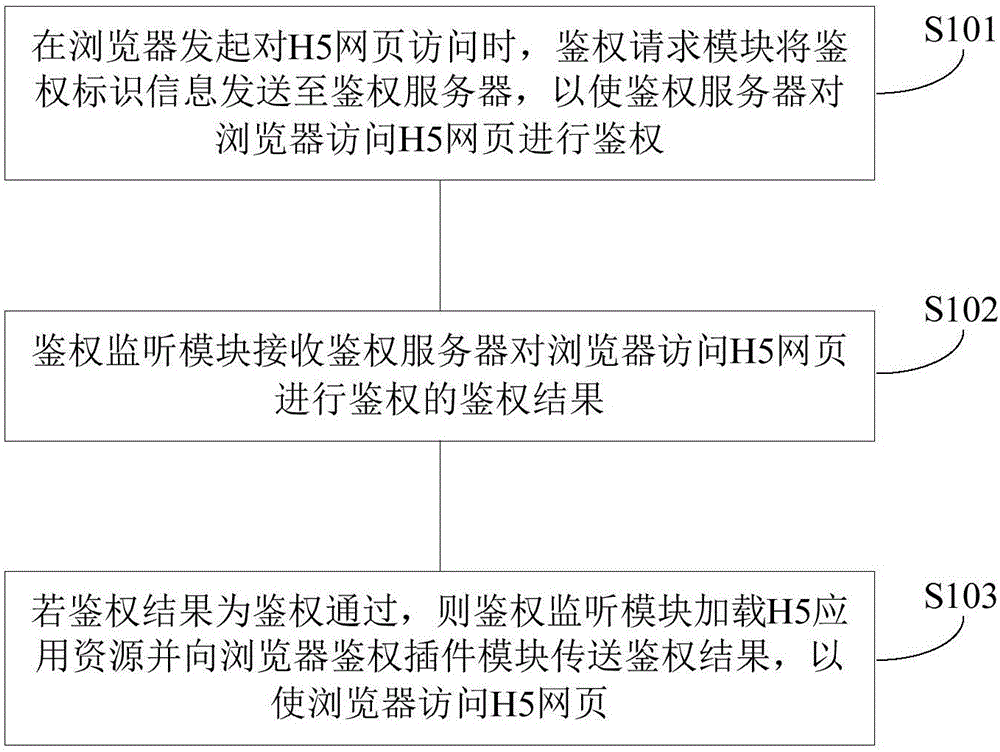
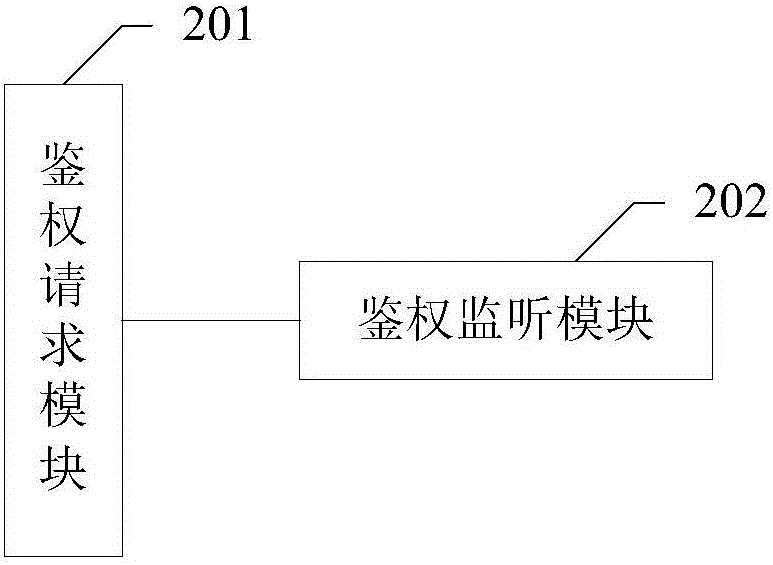
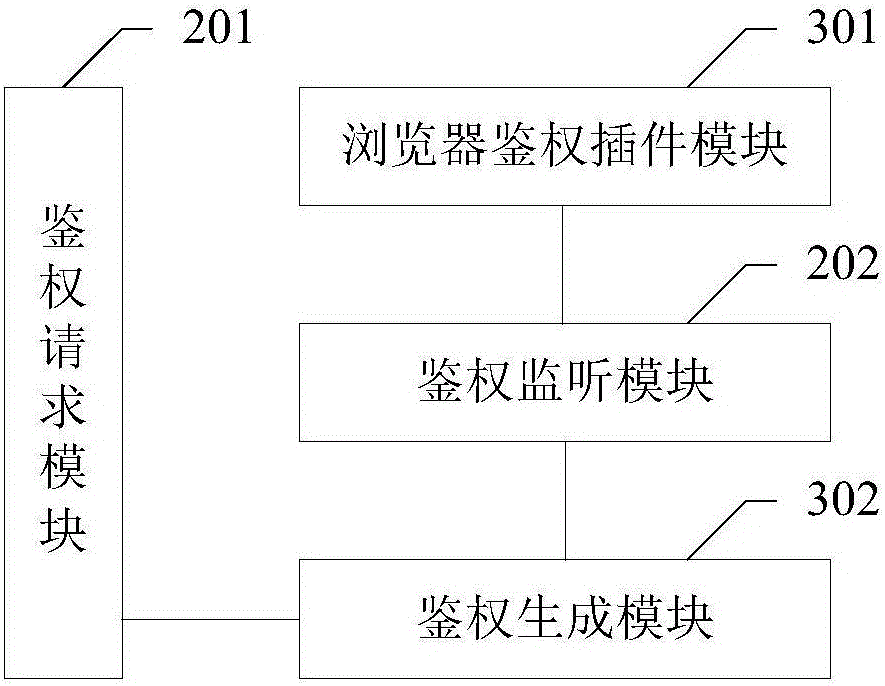
Application authentication method, device and system
InactiveCN106101127ASafe interactionTransmissionSecurity arrangementThe InternetAuthentication server
The invention provides an application authentication method, device and system, and aims at improving the safety of interaction between an application and an intelligent household electrical appliance. The application is embedded with a browser; and the method comprises that when the browser initiates webpage access, an authentication request module sends authentication identification information to an authentication server, so that the authentication server authenticates webpage access by the browser; an authentication monitoring module receives an authentication result; and if the authentication result shows that authentication passes, the authentication monitoring module loads resources of the application and transmits the authentication result to an authentication plug-in module of the browser, so that the browser accesses the webpage. Compared with the prior art in which data is only encrypted in the data transmission process after that the browser accesses the webpage, according to the method of the invention, authentication is carried out at the very beginning and the browser cannot access the webpage unless authentication passes, and thus, interaction between the application and the intelligent household electrical appliance is safer in the Internet of things.
Owner:TCL CORPORATION
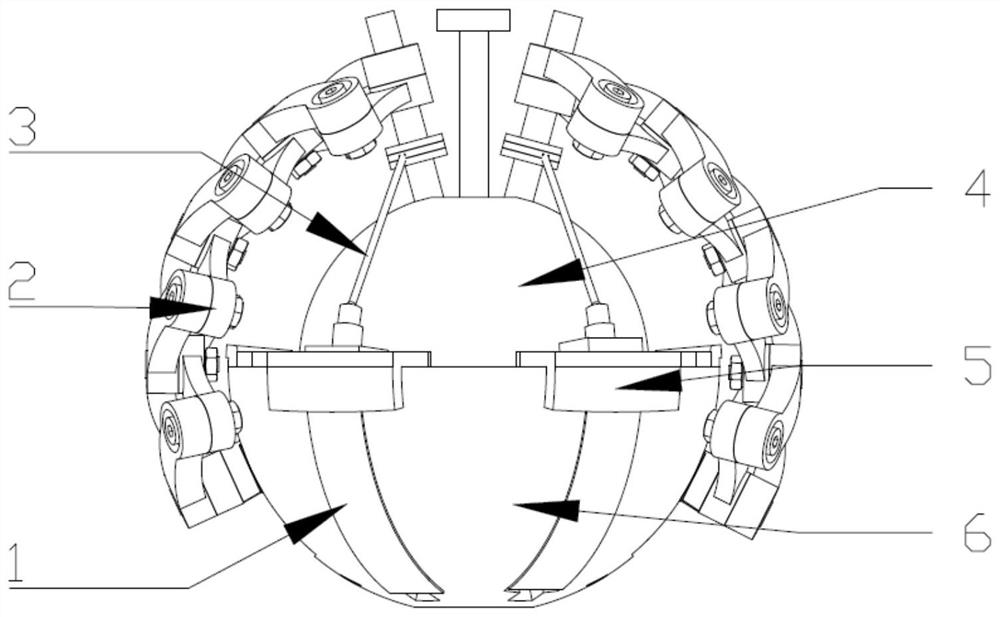
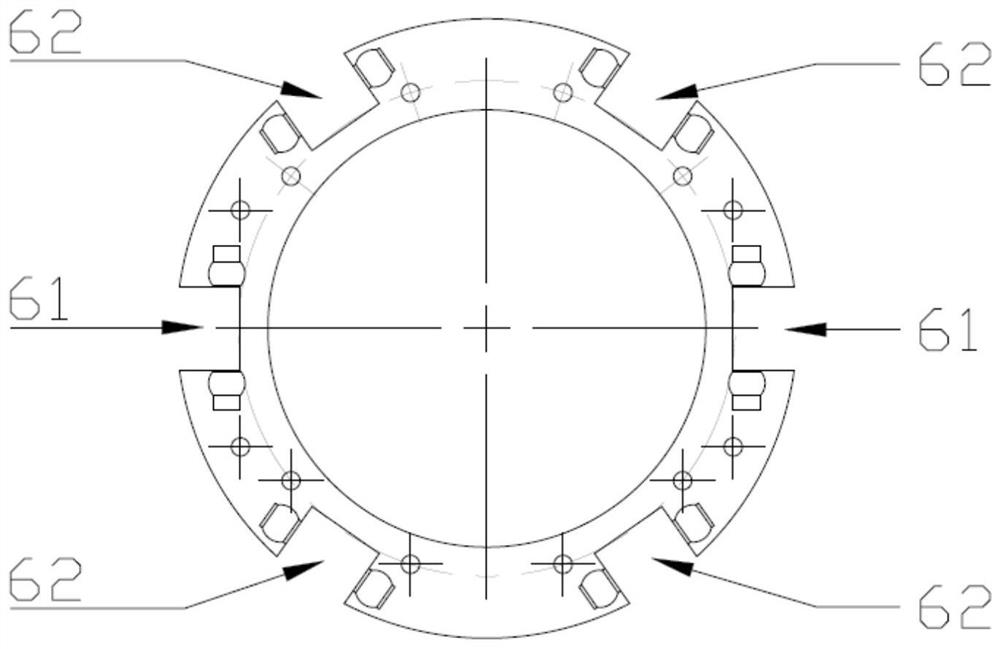
Rope-driven large-motion-range flexible bionic ball socket joint
The invention discloses a rope-driven large-motion-range flexible bionic ball socket joint, and belongs to the technical field of robots. A ball head can rotate in a ball socket in a three-degree-of-freedom manner, two offset driving rods are symmetrically arranged at the ball head, two flexible sliding grooves are symmetrically formed in the ball socket, one ends of spherical shear fork mechanisms are connected with the offset rods, the other ends of the spherical shear fork mechanisms are connected with flexible sliding blocks, the flexible sliding blocks can slide along the flexible slidinggrooves, and springs are installed between the sliding grooves and the sliding blocks. The structure simulates the human ligament to limit the joint. A muscle driving manner of the human body is simulated, four rope driving structures are symmetrically arranged in the driving sliding grooves in the ball socket in pairs, each rope driving structure is an expandable mechanism and can be expanded only under single-direction pulling force, one end of each rope is connected to a driving rod of the ball head, and the other end of each rope is wound around the interior of the corresponding rope driving structure and extends out of the lower side of the ball socket to be then connected with a driver, and the three rotational degrees of freedom of the ball socket joint can be controlled. The jointhas high compactness, and the deflection range can reach 120 degrees.
Owner:BEIJING JIAOTONG UNIV
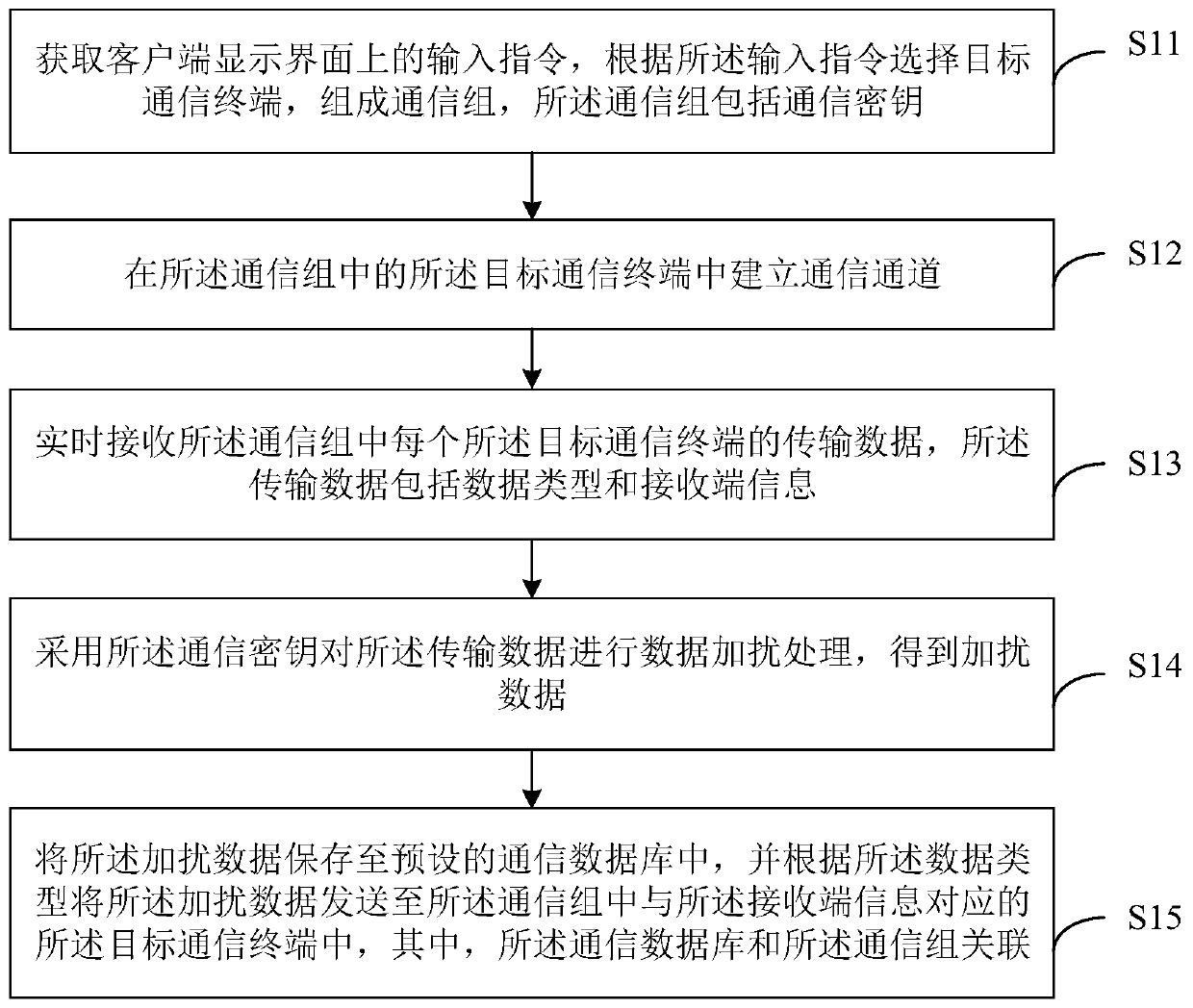
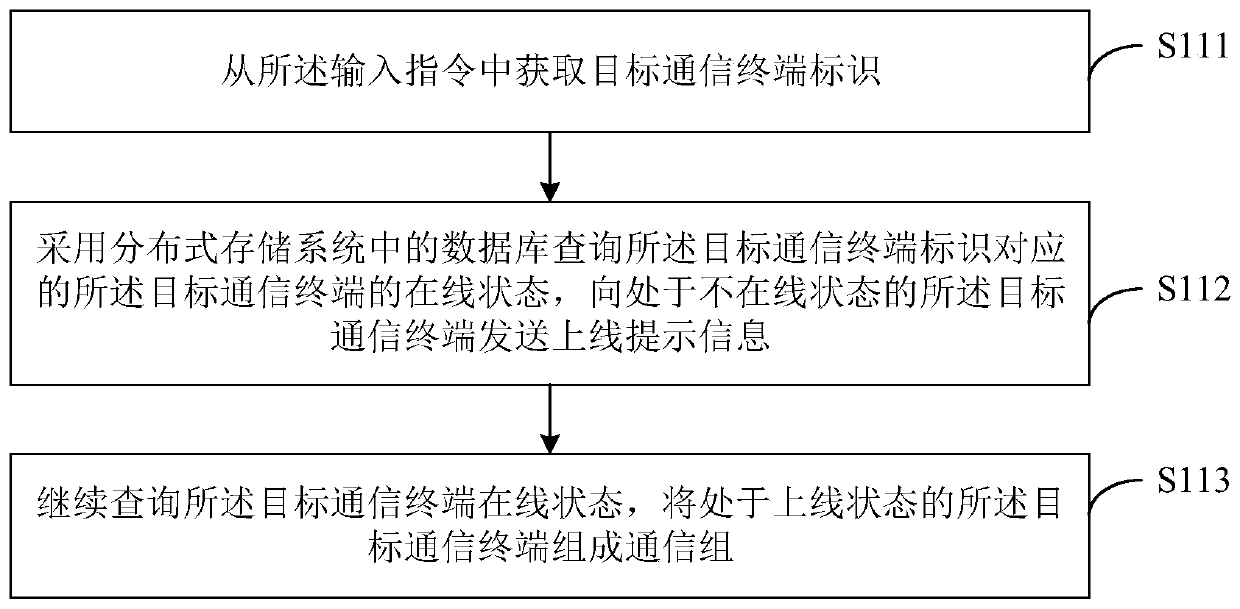
Communication group establishing method and device, computer equipment and storage medium
ActiveCN110943849AEnhanced interactionSafe interactionSpecial service provision for substationData classComputer network
The invention discloses a communication group establishing method and device, computer equipment and a storage medium. The method comprises the steps of acquiring an input instruction on a display interface of a client, selecting a target communication terminal according to the input instruction to form a communication group, and the communication group comprising a communication key; establishinga communication channel in a target communication terminal in the communication group; receiving transmission data of each target communication terminal in the communication group in real time, wherein the transmission data comprises a data type and receiving end information; performing data scrambling processing on the transmission data by adopting the communication key to obtain scrambled data;and storing the scrambled data in a preset communication database, and sending the scrambled data to a target communication terminal corresponding to the receiving end information in the communication group according to the data type. According to the technical scheme, mutual communication and cooperation of salesmen are facilitated, the message privacy is ensured, and the exhibition cost is reduced.
Owner:CHINA PING AN PROPERTY INSURANCE CO LTD
Interaction method of browser application and system platform and display equipment
PendingCN112199064ASafe interactionAvoid security issuesWebsite content managementSpecial data processing applicationsHuman–computer interactionNetwork service
The invention discloses an interaction method of a browser application and a system platform and display equipment, which are used for enabling the browser application to quickly and safely interact with the system platform. The method comprises the following steps: in response to an interaction instruction of the browser application and the system platform, the interaction instruction is sent toa network server side through a network client side, so that the network server side is in butt joint with the system platform, and feedback information of the system platform is sent to the network client side; and the feedback information is sent to the browser application through the network client side.
Owner:VIDAA美国公司 +1
Cross-network interaction system and cross-network interaction method
ActiveCN110933291ASafe interactionReal-time security callTelevision system detailsElectric signal transmission systemsControl signalTarget signal
The invention provides a cross-network interaction system. The cross-network interaction system comprises an interaction computer, first conversion equipment, one-way transmission equipment and secondconversion equipment in each sub-network; the interactive computer is used for sending a control command for one signal source to the first conversion equipment through a network; the first conversion equipment receives the control command, and converts the control command in the network signal form into a proper form suitable for being transmitted to second conversion equipment in a subnet wherethe signal source is located through the one-way transmission equipment, and the control command in the proper form is transmitted to the second conversion equipment through the one-way transmissionequipment; and the second conversion equipment receives the control command in the proper form, converts the control command into a control command in a network signal form again, and sends the control command to the targeted signal source through the subnet so as to control the signal source. According to the invention, real-time and safe calling of the network cameras in the plurality of subnetsand safe interaction of the network cameras can be realized.
Owner:北京仁光科技有限公司
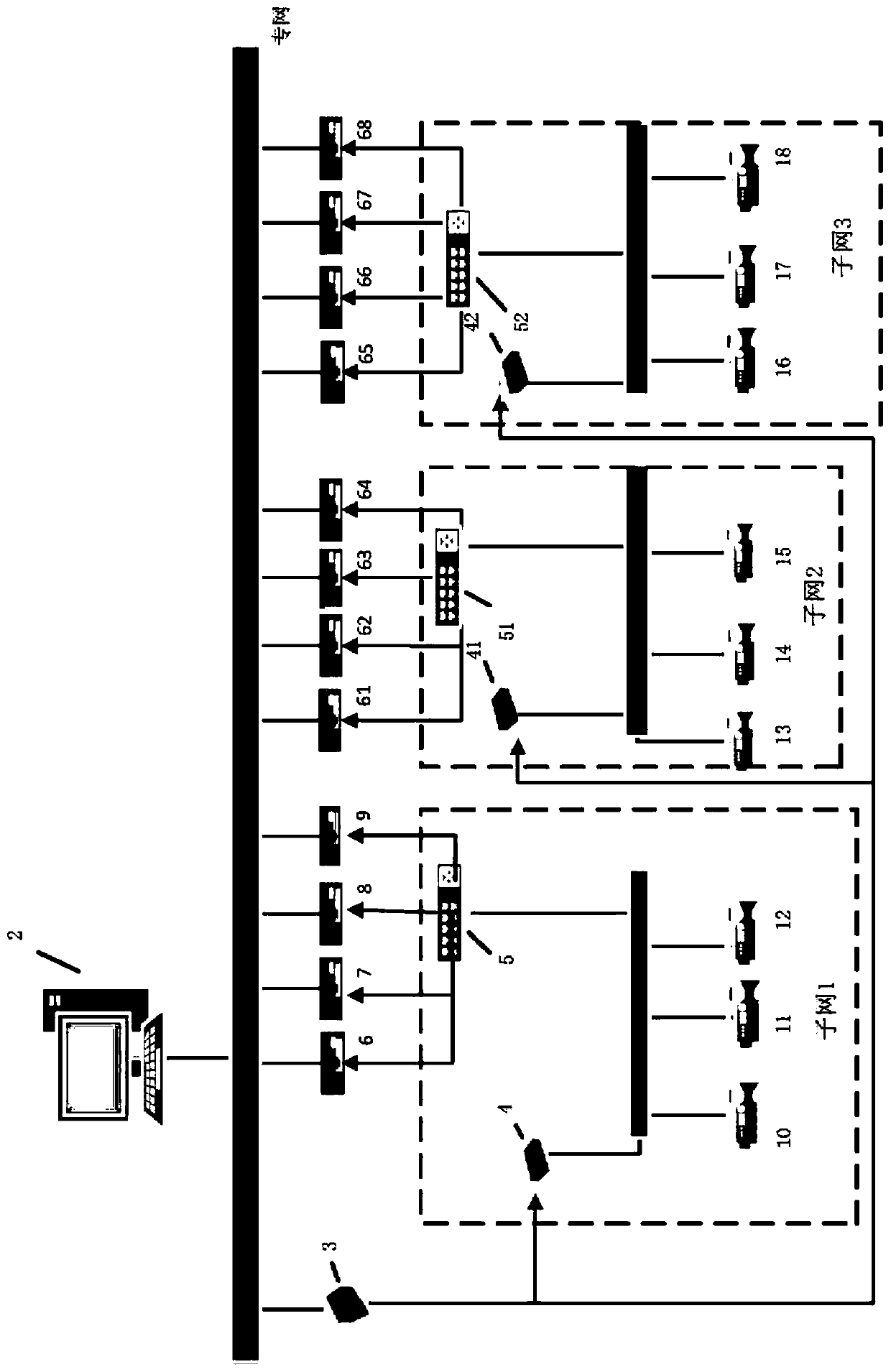
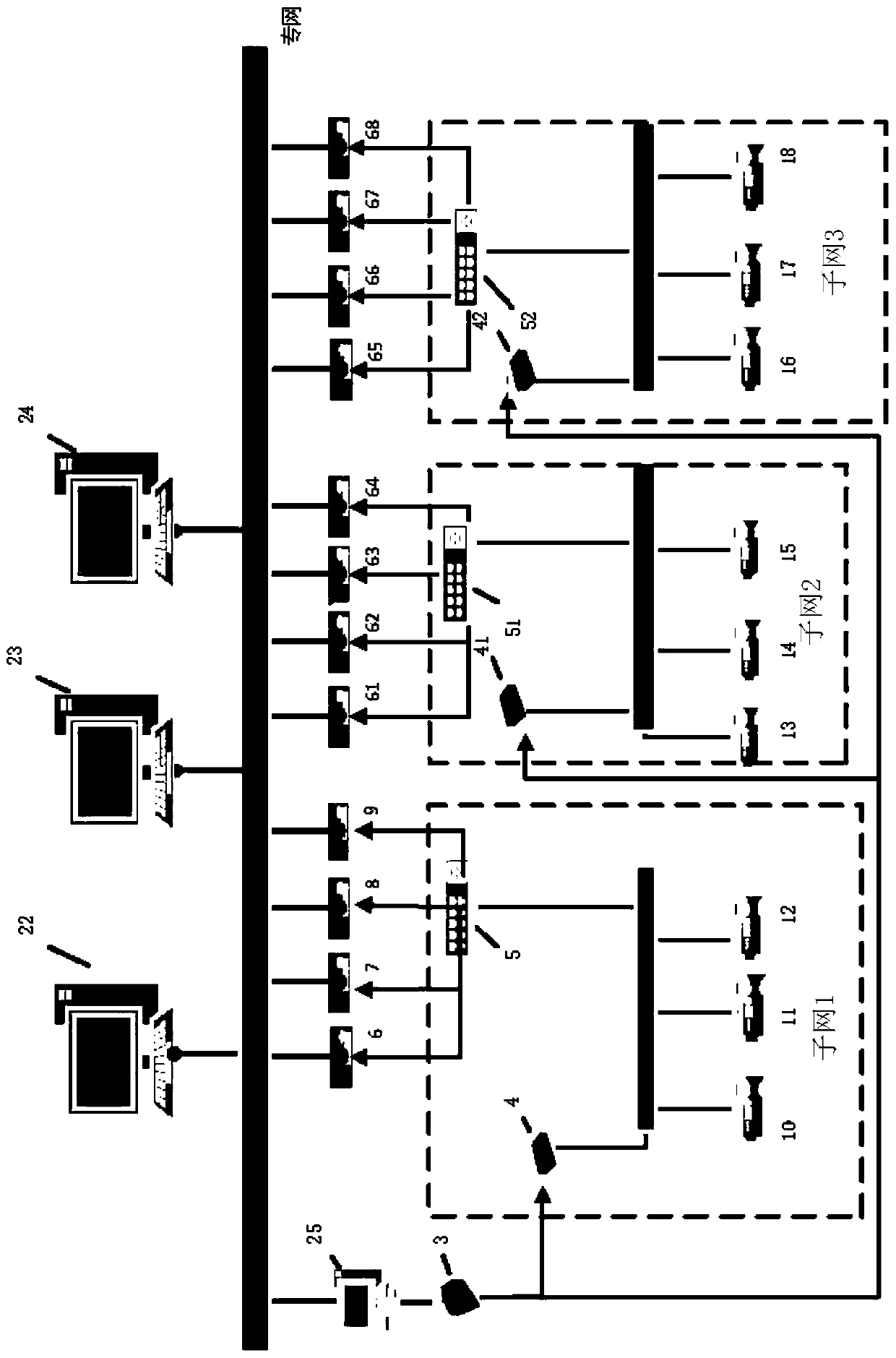
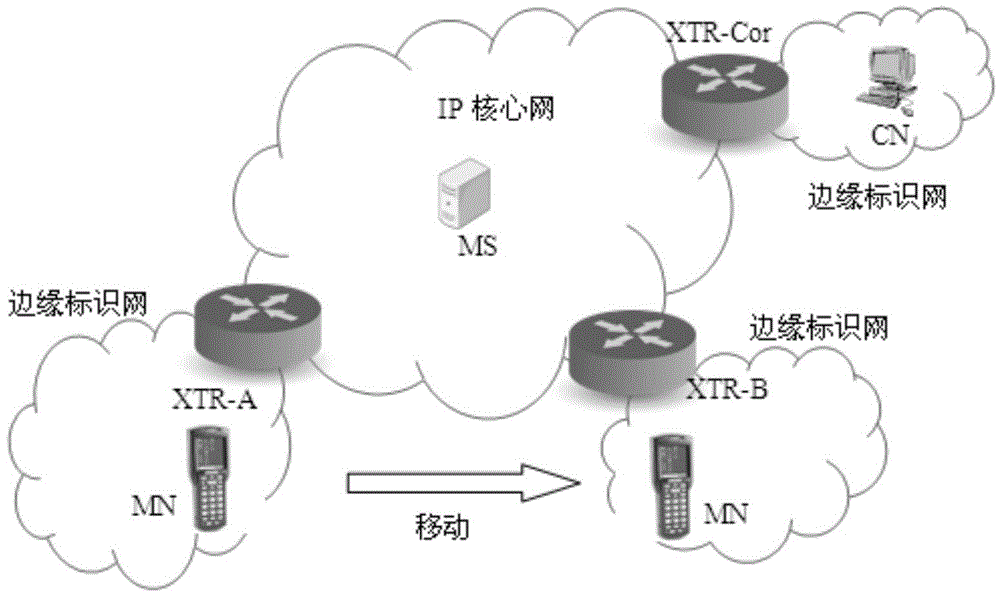
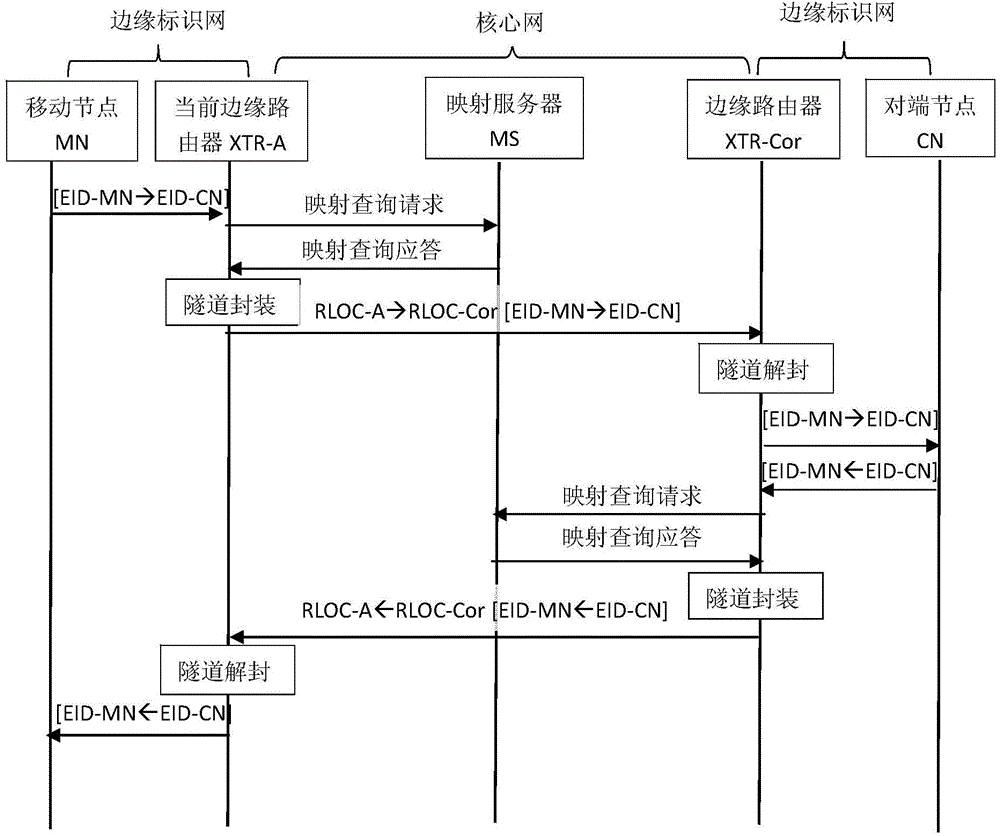
Marked net mobile access method
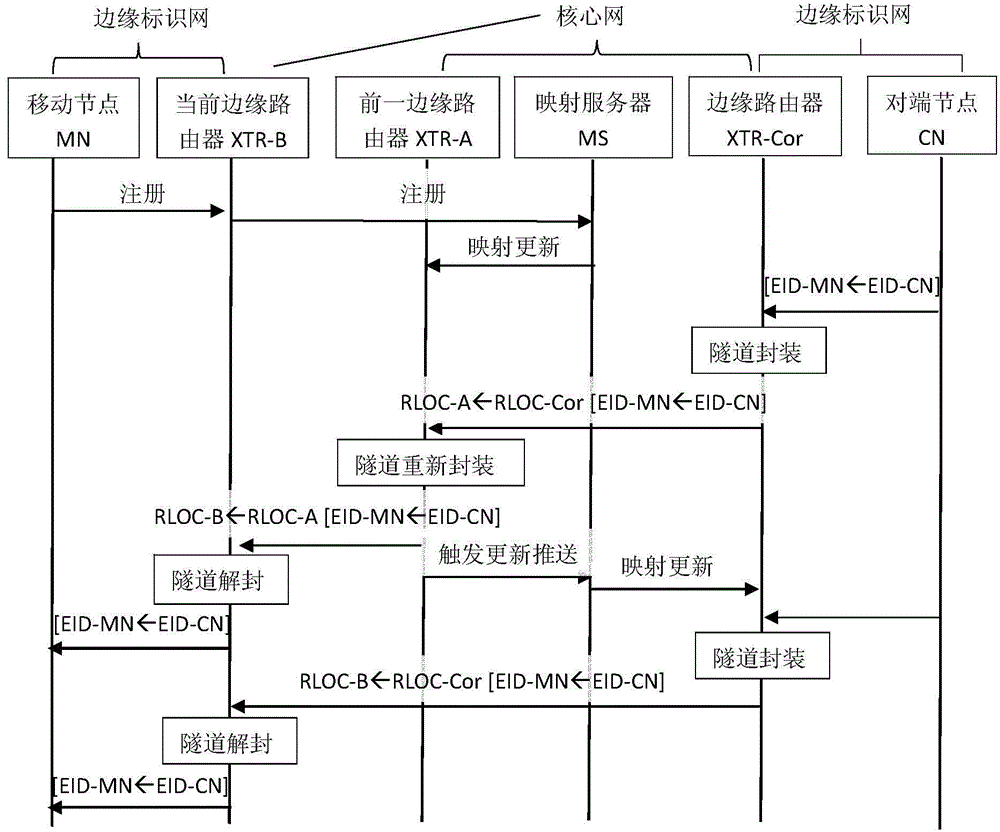
InactiveCN104980916AReduce overheadAvoid triangular routingNetwork data managementAccess methodEncapsulated data
The invention discloses a marked net mobile access method. The method comprises the following steps that: a mobile node judges whether or not movement occurs through router notice information of an edge router; if movement occurs, the mobile node initiates registration to the edge router, and the edge router assists the mobile node in registering to a mapping server as an agent; the mapping server pushes new mapping information to a previous edge router of the mobile node; data transmitted to the mobile node by an opposite-end communication node through the edge router to which the opposite-end communication node accesses is transmitted to a previous edge router of the mobile node, and the previous edge router re-encapsulates the data and forwards the re-encapsulated data to a current edge router of the mobile node; the previous edge router pushes the new mapping information of the mobile node to an edge router where the opposite-end communication node is positioned through the mapping server; data subsequently transmitted by the opposite-end communication node is directly transmitted to the current edge router in the edge router of the opposite-end communication node according to the new mapping information; and data transmitted to the opposite-end communication node by the mobile node is transmitted normally through the accessed edge router.
Owner:SOUTHEAST UNIV
Access method and device of Kubernetes cluster in private network, equipment and medium
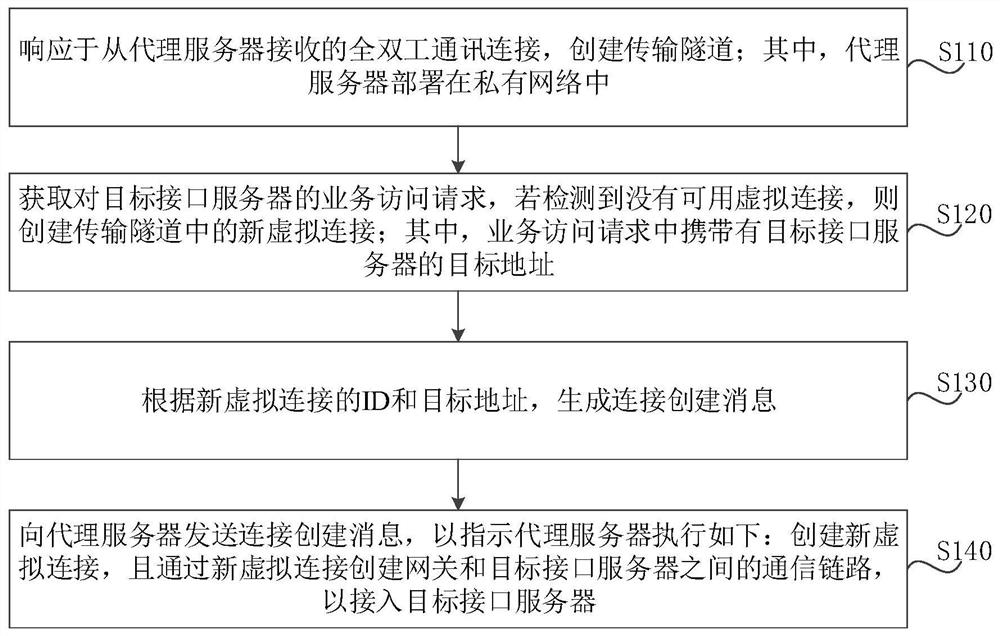
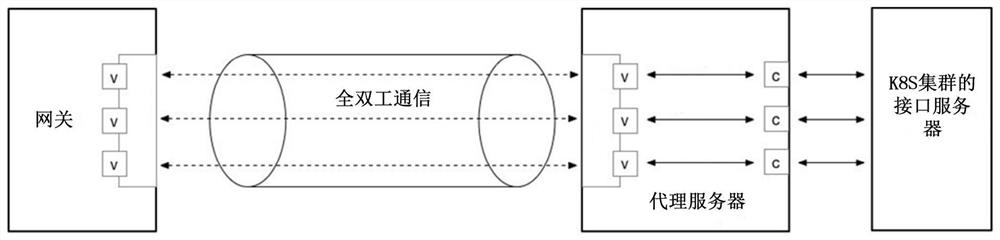
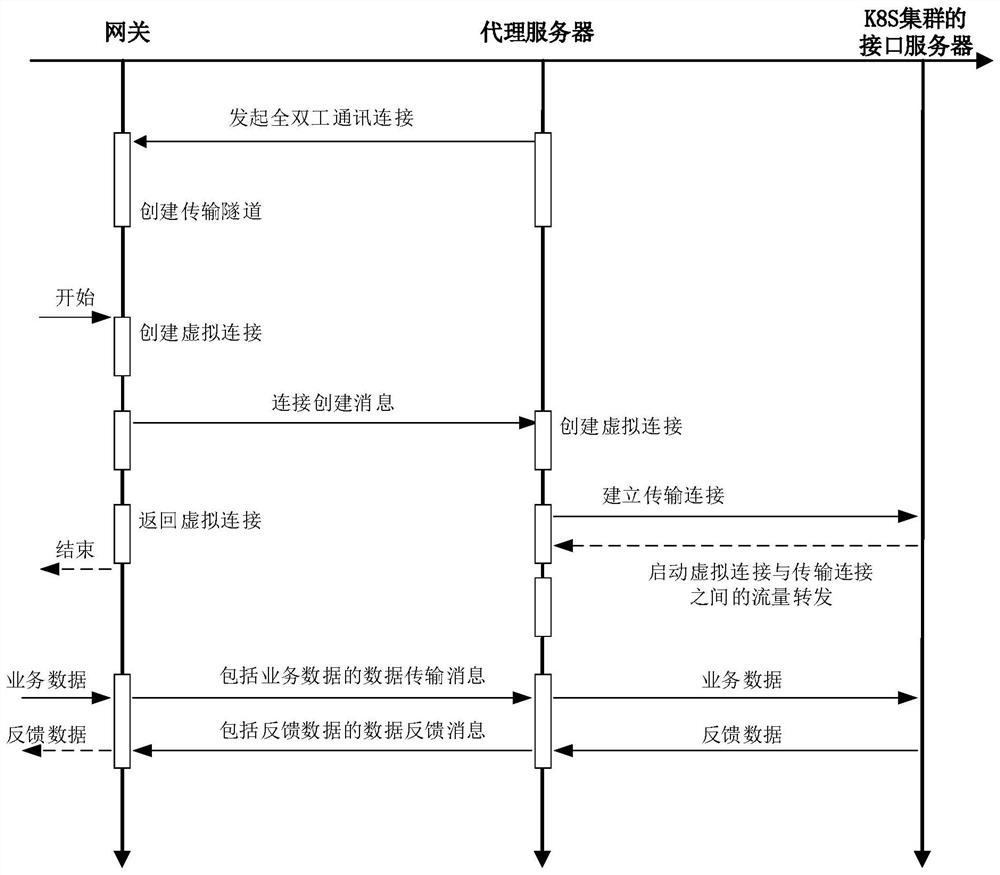
ActiveCN113141386ASafe interactionReduce the risk of external attacksNetworks interconnectionNetwork connectionsCloud computingTelecommunications link
The invention discloses an access method and device of a Kubernetes cluster in a private network, equipment and a medium, and relates to the technical field of computers, in particular to the technical field of cloud computing. The specific implementation scheme is as follows: in response to full duplex communication connection received from a proxy server, creating a transmission tunnel; acquiring a service access request for a target interface server, and if no available virtual connection is detected, creating a new virtual connection in the transmission tunnel; generating a connection creation message according to the ID and the target address of the new virtual connection; sending a connection creation message to the proxy server to instruct the proxy server to execute the following steps: creating a new virtual connection, and creating a communication link between the gateway and the target interface server through the new virtual connection to access the target interface server. By adopting the scheme provided by the invention, the K8S cluster in the private network can be accessed to the cloud platform in the public network, and the public network IP is not needed, so the risk that the K8S cluster is subjected to external attacks can be greatly reduced.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com