Identity identifying method and device
A technology of identity recognition and user identity recognition, applied in the field of identity recognition methods and devices, can solve the problems of embezzlement of funds, illegal personnel embezzlement of funds, lack of efficient and reliable control implementation methods, etc., and achieve the effect of high uniqueness and friendly interaction process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
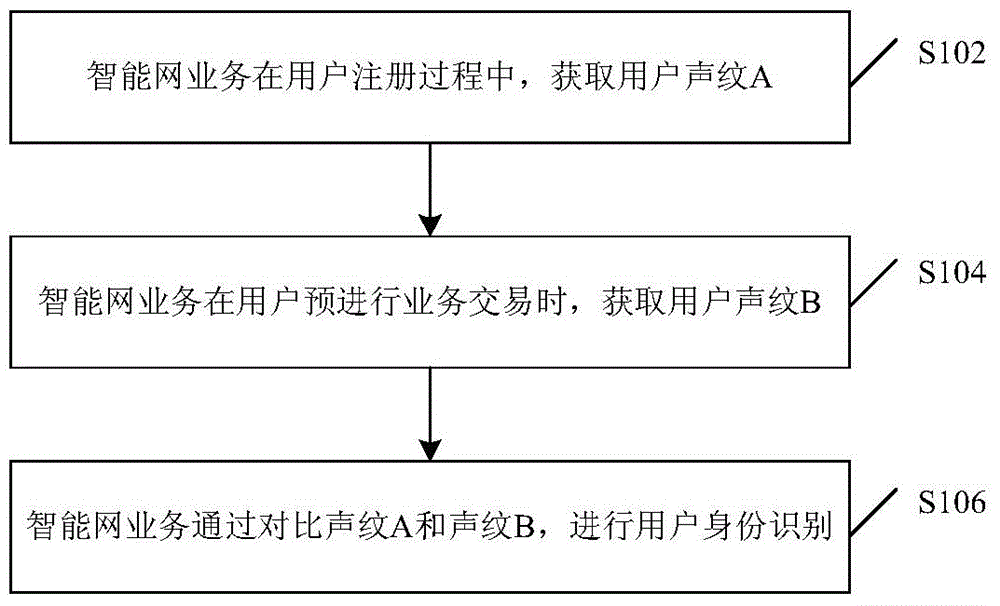
[0042] In order to solve the transaction security defects in the current mobile network, the embodiment of the present invention provides an IVR process in the broadband intelligent network to complete the voiceprint collection and identity recognition control from the terminal to the operator to the server, and use the terminal's business application and broadband business The IVR operation is described as an example. The service of the terminal may be a payment application or a banking application.
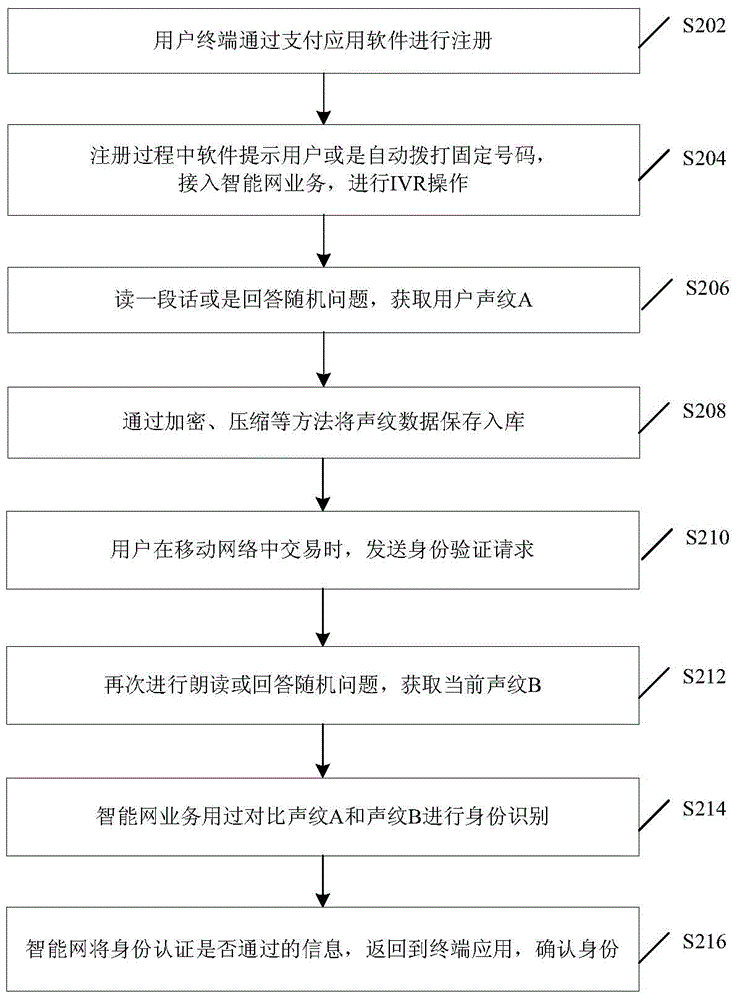
[0043] figure 2 It is a flow chart of broadband intelligent network voiceprint recognition according to Embodiment 1 of the present invention, such as figure 2 As shown, the process includes but is not limited to the following implementation steps:
[0044] Step S202, the user terminal registers through the payment application software.
[0045] Step S204, during the registration process, the software prompts the user or automatically dials a fixed number to access the inte...
Embodiment 2
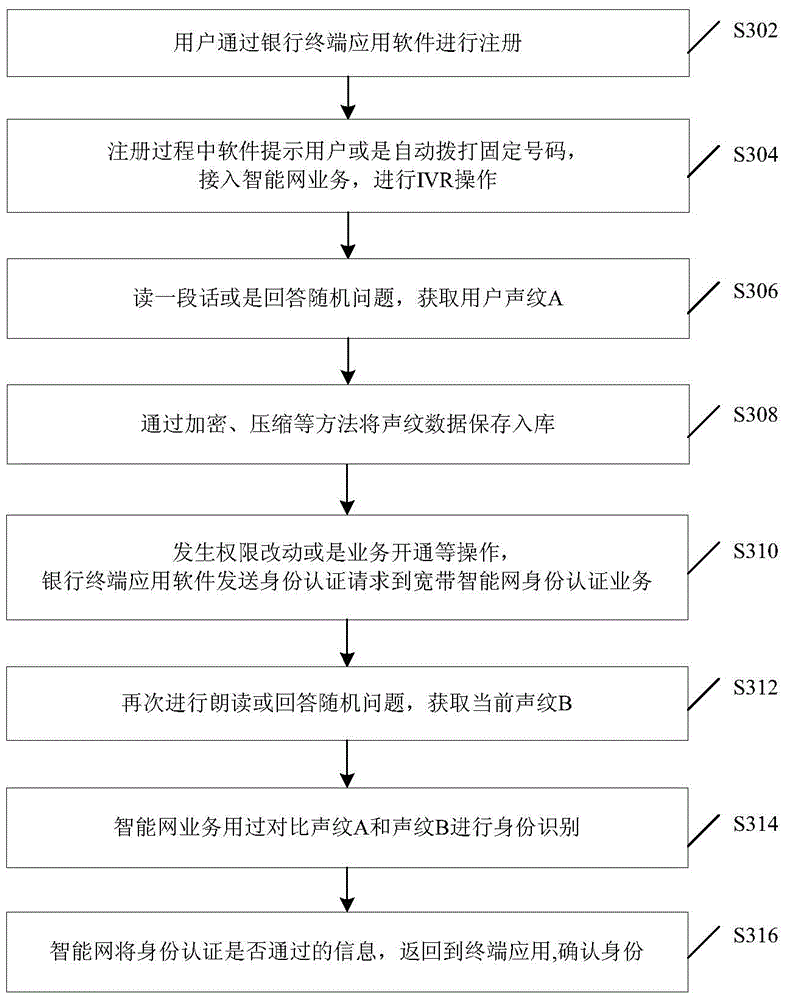
[0053] image 3 It is a flow chart of voiceprint recognition in a broadband intelligent network according to Embodiment 2 of the present invention, as image 3 As shown, the process includes but is not limited to the following implementation steps:
[0054] Step S302, the user registers through the bank terminal application software.
[0055] Step S304, during the registration process, the software prompts the user or automatically dials a fixed number to access the intelligent network service and perform IVR operation.
[0056] Step S306, the IVR operation requests the user to read a paragraph or answer random questions according to the operation voice prompt, and obtain the user's voiceprint A.
[0057] In step S308, the voiceprint data is stored in storage through methods such as encryption and compression.
[0058] Step S310, when the user performs operations such as authority modification or service activation in the bank terminal application software, the bank termina...
Embodiment 3
[0063] Figure 4 It is a flow chart of broadband intelligent network voiceprint recognition according to Embodiment 3 of the present invention, as Figure 4 As shown, the process includes but is not limited to the following implementation steps:
[0064] Step S402, the user registers through the bank terminal application software.
[0065] Step S404, during the registration process, the software prompts the user or automatically dials a fixed number to access the intelligent network service and perform the IVR operation.
[0066] Step S406, the IVR operation requests the user to read a paragraph or answer random questions according to the operation voice prompt, and obtain the user's voiceprint A.
[0067] In step S408, the voiceprint data is stored in a database by means of encryption and compression.
[0068] Step S410, when the user performs operations such as permission modification or service activation in the self-service voice service provided by the bank, the bank's...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com