A method for generating and protecting real-name system network identity
A technology of network identity and network identity identification, which is applied in the field of real-name system network identity generation and protection, can solve the problem of personal privacy of users who cannot truly realize the "identity of witnesses", and achieve the effect of avoiding widespread dissemination and ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
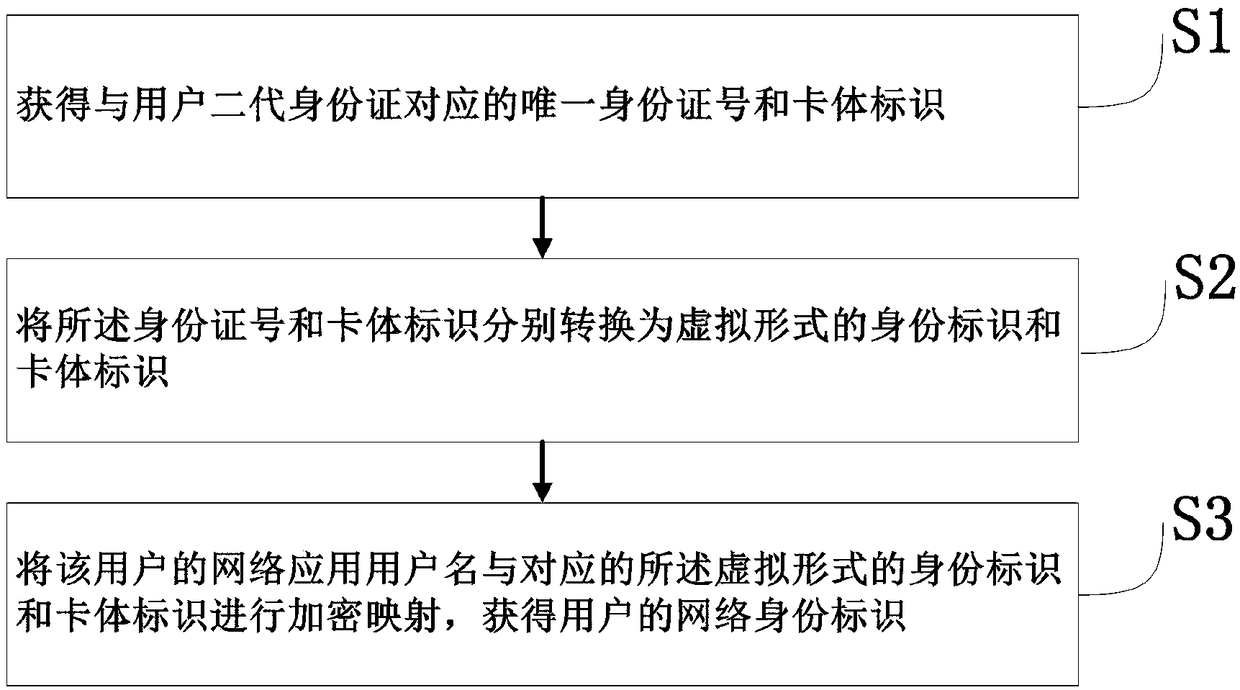
[0055] Such as figure 1 As shown, a specific embodiment of the present invention discloses a method for generating and protecting a real-name network identity, including the following steps:
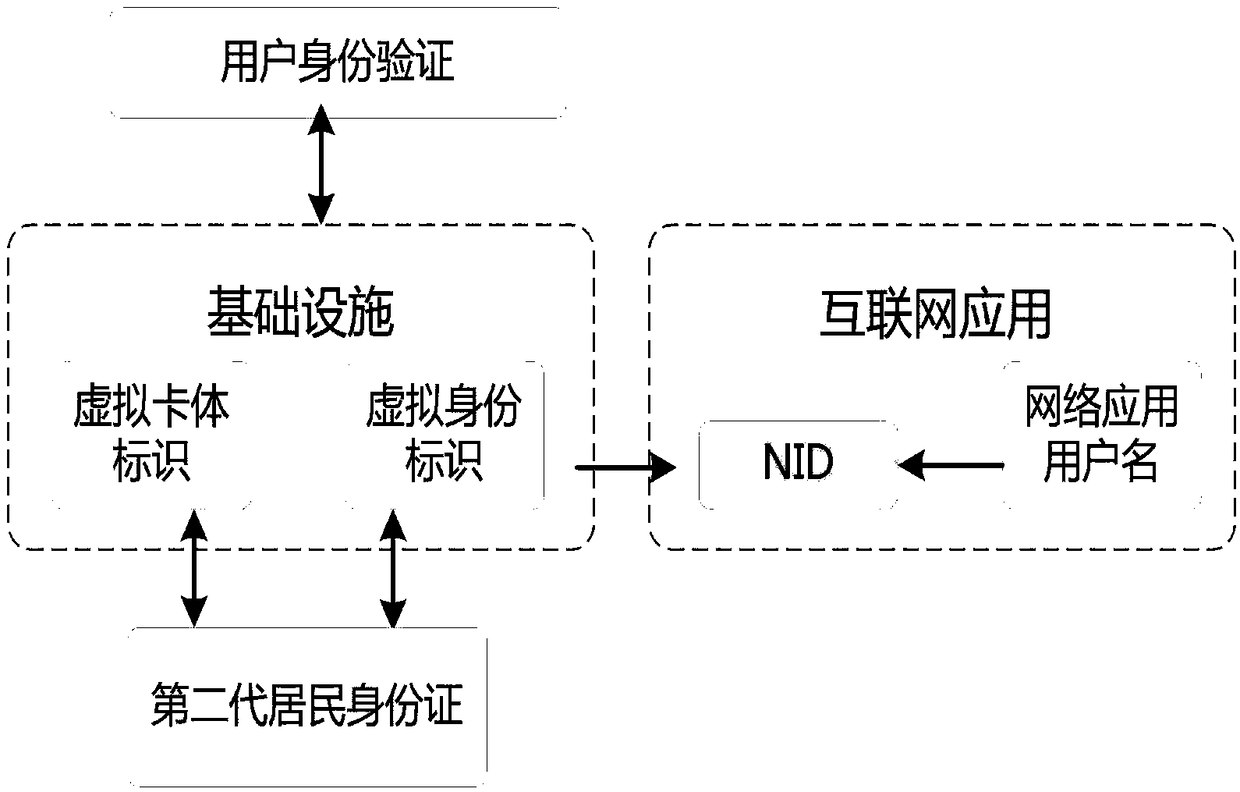
[0056] S1. Obtain the unique ID number and card body identification corresponding to the user's second-generation ID card by manually entering, using a card reader or NFC device, such as figure 2 shown.
[0057] S2. In the infrastructure, the ID number and the card body identification are respectively converted into a virtual form of identity identification and card body identification according to a preset algorithm, such as figure 2 shown. The infrastructure includes computers, which may include multiple computers. The preset algorithm is a data encryption algorithm agreed upon in advance by the infrastructure manufacturer and the public security. Using the existing algorithm, those skilled in the art can understand that the virtual form of the identity mark and the card body mark...
Embodiment 2
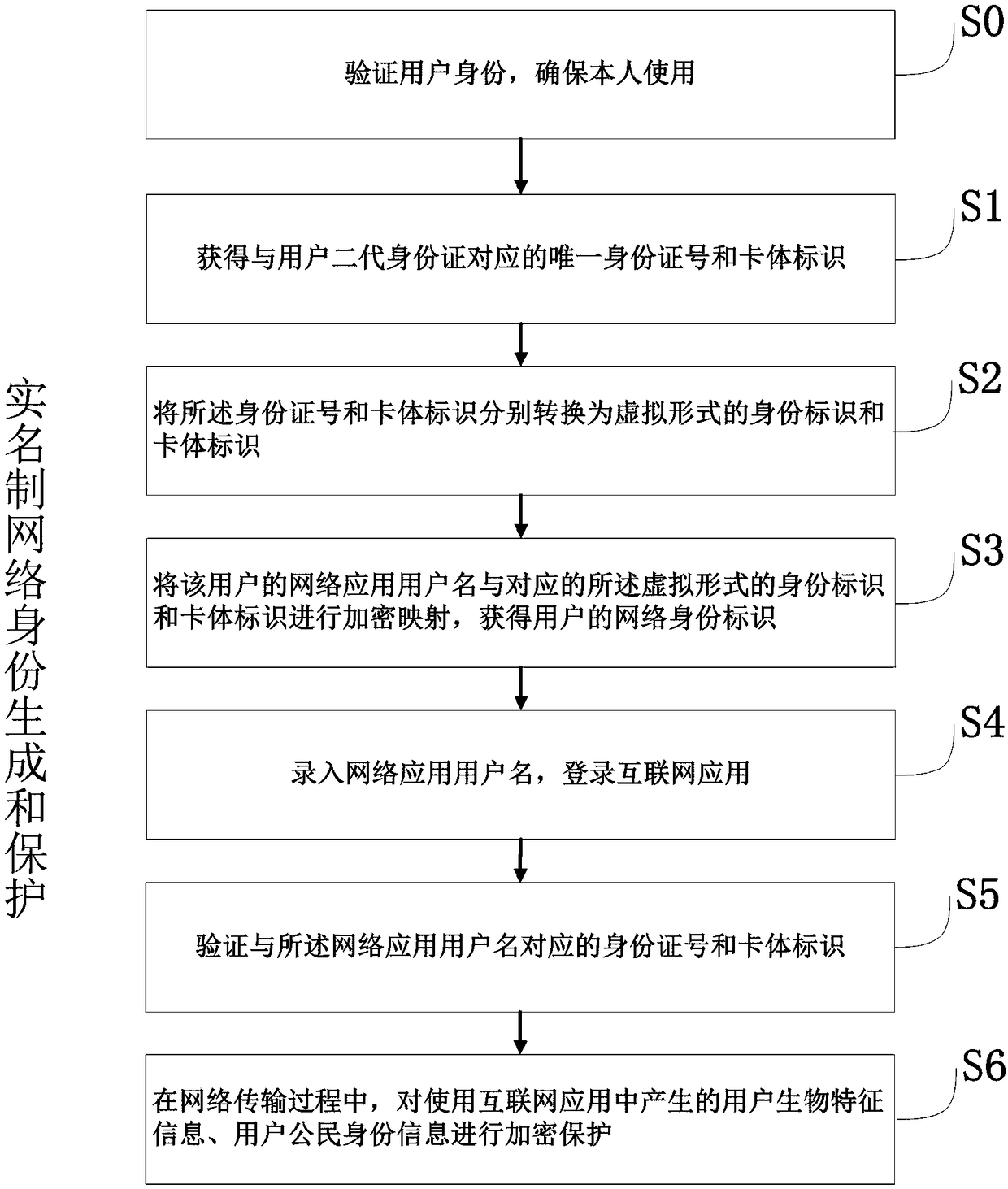
[0061] Such as image 3 As shown, optimization is carried out on the basis of the above-mentioned embodiment, and before obtaining the unique ID number corresponding to the user's second-generation ID card and the card body identification, the step S0 of verifying the user's identity is also included:
[0062] S0. Through at least one method of fingerprint recognition, portrait recognition, retinal recognition, voice recognition, and PIN code verification, or through on-site user identity verification by public security organs.
[0063] The user identity verification step S0 is generally carried out through on-site collection to ensure the identity of witnesses. The identity of the citizen identity information and the user can be effectively verified through user identity verification, so the citizen identity information (identity card information) is not easy to be fraudulently used. In addition, before logging into the Internet application, a user identity verification step...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com