Access method and device of Kubernetes cluster in private network, equipment and medium
A technology of private network and access method, applied in the field of computer and cloud computing, can solve the problems of network inaccessibility and inaccessibility, and achieve the effect of reducing the risk of external attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
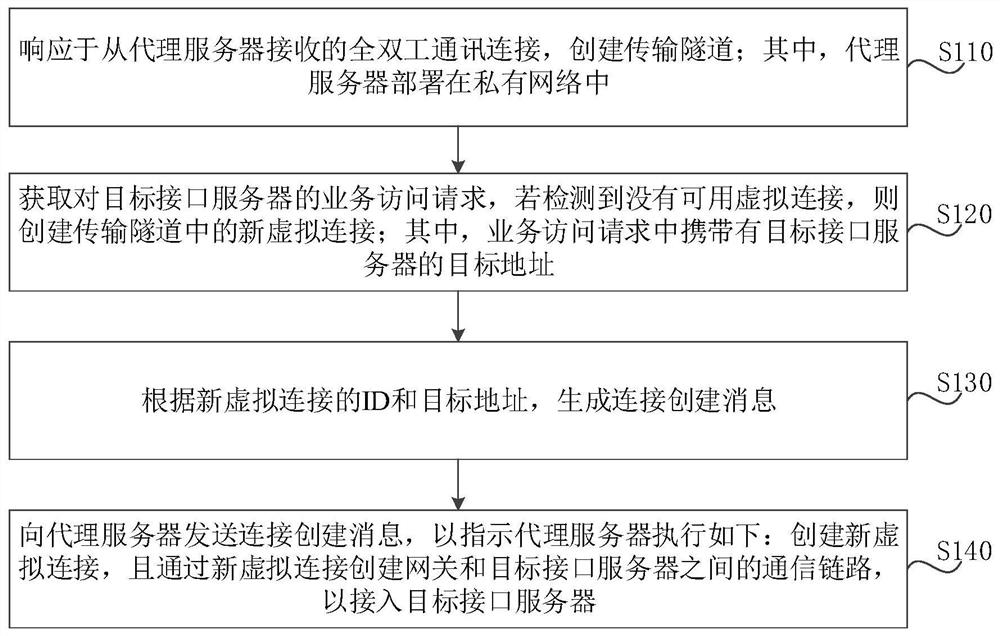
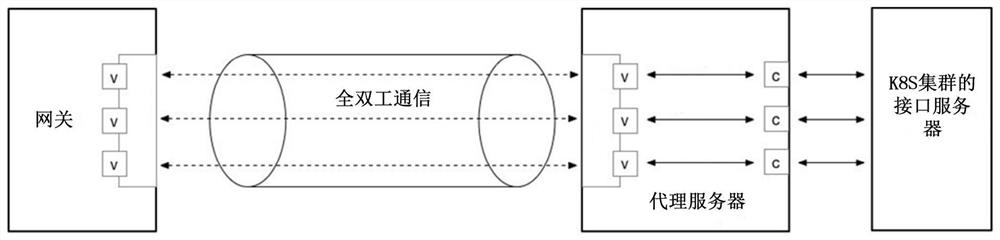
[0069] figure 1 It is a flowchart of a method for accessing a Kubernetes cluster in a private network according to Embodiment 1 of the present application. This embodiment is applicable to the case of connecting a Kubernetes cluster in a private network to a cloud platform in a public network. The method can be executed by the access device of the Kubernetes cluster in the private network, and the device can be implemented in the form of software and / or hardware, and integrated on any electronic device with a network communication function. Wherein, the access method of the Kubernetes cluster in this embodiment may be executed by a gateway deployed in a public network.
[0070] Such as figure 1 As shown, the access method of the Kubernetes cluster in the private network provided in the embodiment of the present application includes the following steps:
[0071] S110. Create a transmission tunnel in response to the full-duplex communication connection received from the proxy ...
Embodiment 2
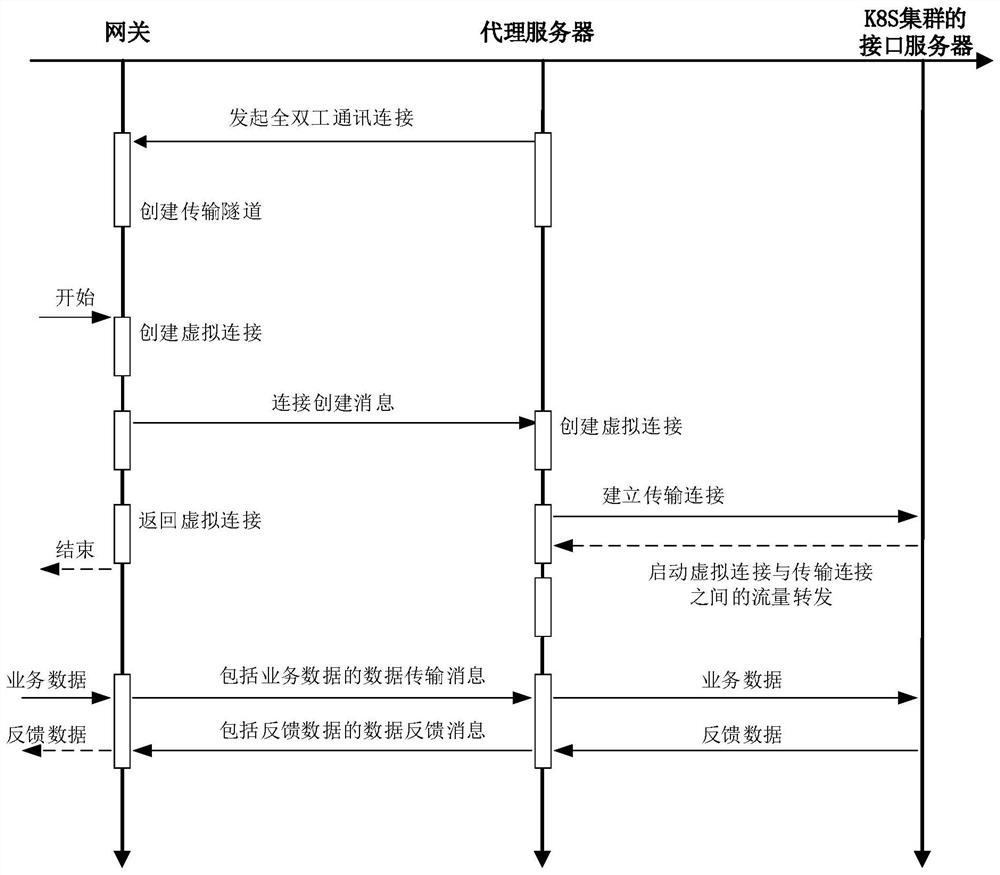
[0098] Figure 4 It is a flowchart of a method for accessing a Kubernetes cluster in a private network according to Embodiment 2 of the present application. The embodiment of the present application is optimized on the basis of the above-mentioned embodiments. The embodiment of the present application can be combined with one or more of the above-mentioned Various optional schemes are combined in the embodiment. The solution of this embodiment is applicable to a situation where a Kubernetes cluster in a private network is connected to a cloud platform in a public network. The method can be executed by the access device of the Kubernetes cluster in the private network, and the device can be implemented in the form of software and / or hardware, and integrated on any electronic device with a network communication function. Wherein, the access method of the Kubernetes cluster in this embodiment may be performed by a proxy server deployed in a private network.
[0099] like Figu...
Embodiment 3
[0115] Figure 5 It is a structural block diagram of an access device for a Kubernetes cluster in a private network for realizing the access method of the Kubernetes cluster in the private network of the embodiment of the present application. This embodiment is applicable to connecting the Kubernetes cluster in the private network to the public The situation of the cloud platform in the network. This method can be carried out by the access device of Kubernetes cluster in the private network, and this device can adopt the mode of software and / or hardware to realize, and be integrated on any electronic equipment with network communication function, the access of the Kubernetes cluster of this embodiment The device is configured in a gateway deployed in a public network.
[0116] Such as Figure 5 As shown, the access device of the Kubernetes cluster in the private network provided in the embodiment of the present application includes: a first tunnel creation module 510 , a fir...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com