Method and device for generating secret key
A technology for generating keys and devices, which is applied in the field of information security, can solve problems such as unfavorable data confidentiality and exposure of private data of users of electronic terminals, and achieve the effects of improving security, safe data sharing, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] Embodiments of the invention will now be described in detail, examples of which are illustrated in the accompanying drawings, wherein like reference numerals refer to like parts throughout. The embodiments are described below in order to explain the present invention by referring to the figures.
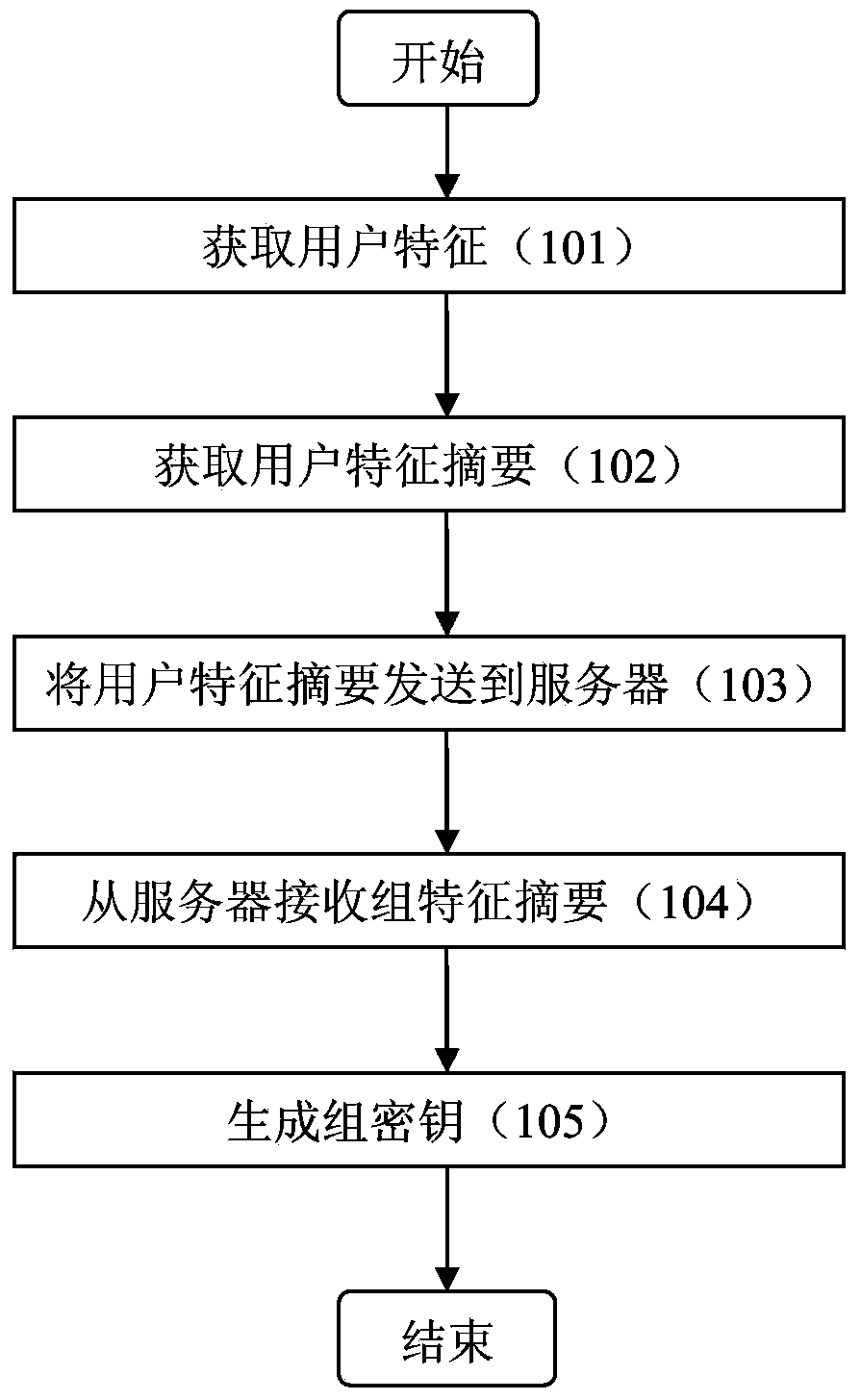
[0041] figure 1 A flowchart showing a method for generating a key at an electronic terminal according to an embodiment of the present invention.
[0042] In step 101, at least one user feature of an electronic terminal is acquired. User features are features that can characterize user interests. For example, the user feature may be tags of TV programs that the user often watches (type of program, keyword of the program, director, actor, etc.). User characteristics can be acquired in various ways. For example, the user characteristics of the electronic terminal may be acquired by receiving the user characteristics input by the user on the electronic terminal, or the user ch...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com