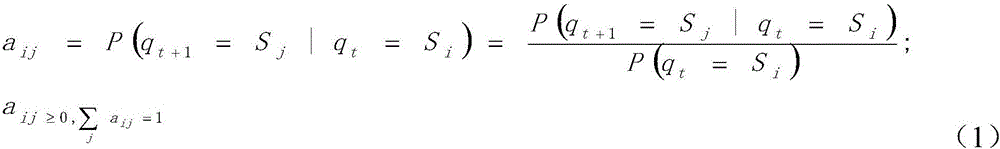Patents
Literature
55results about How to "Eliminate attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
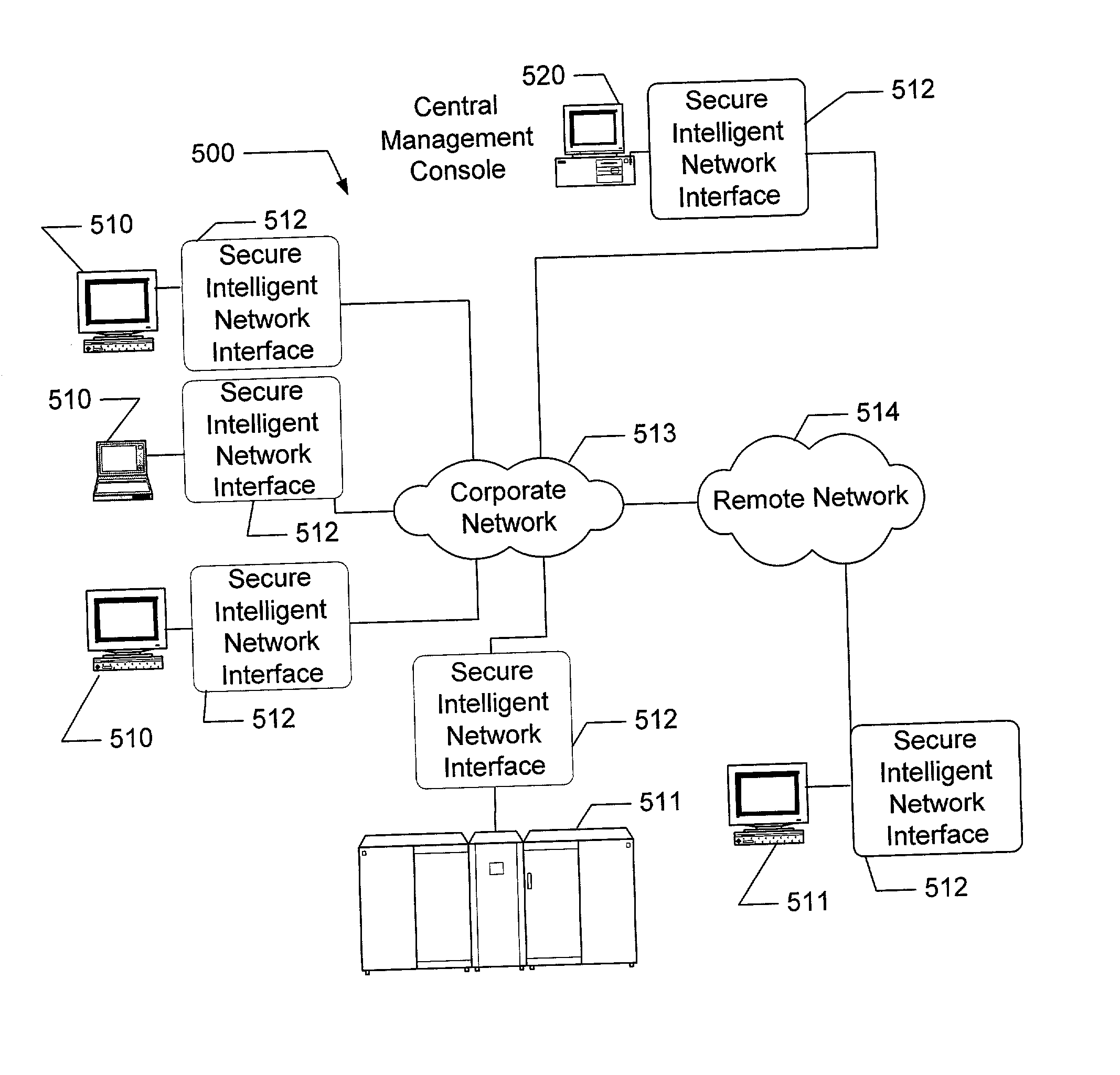
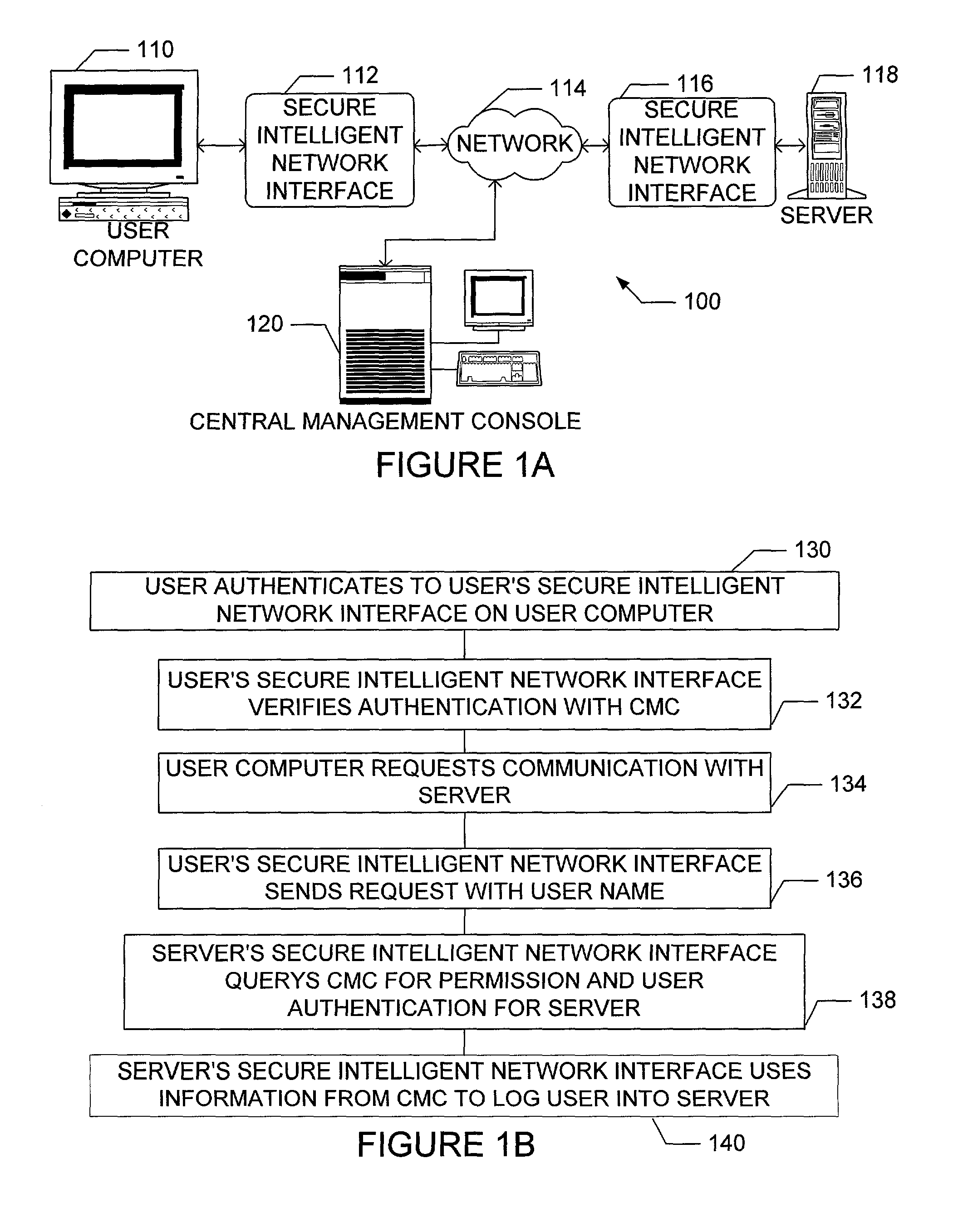
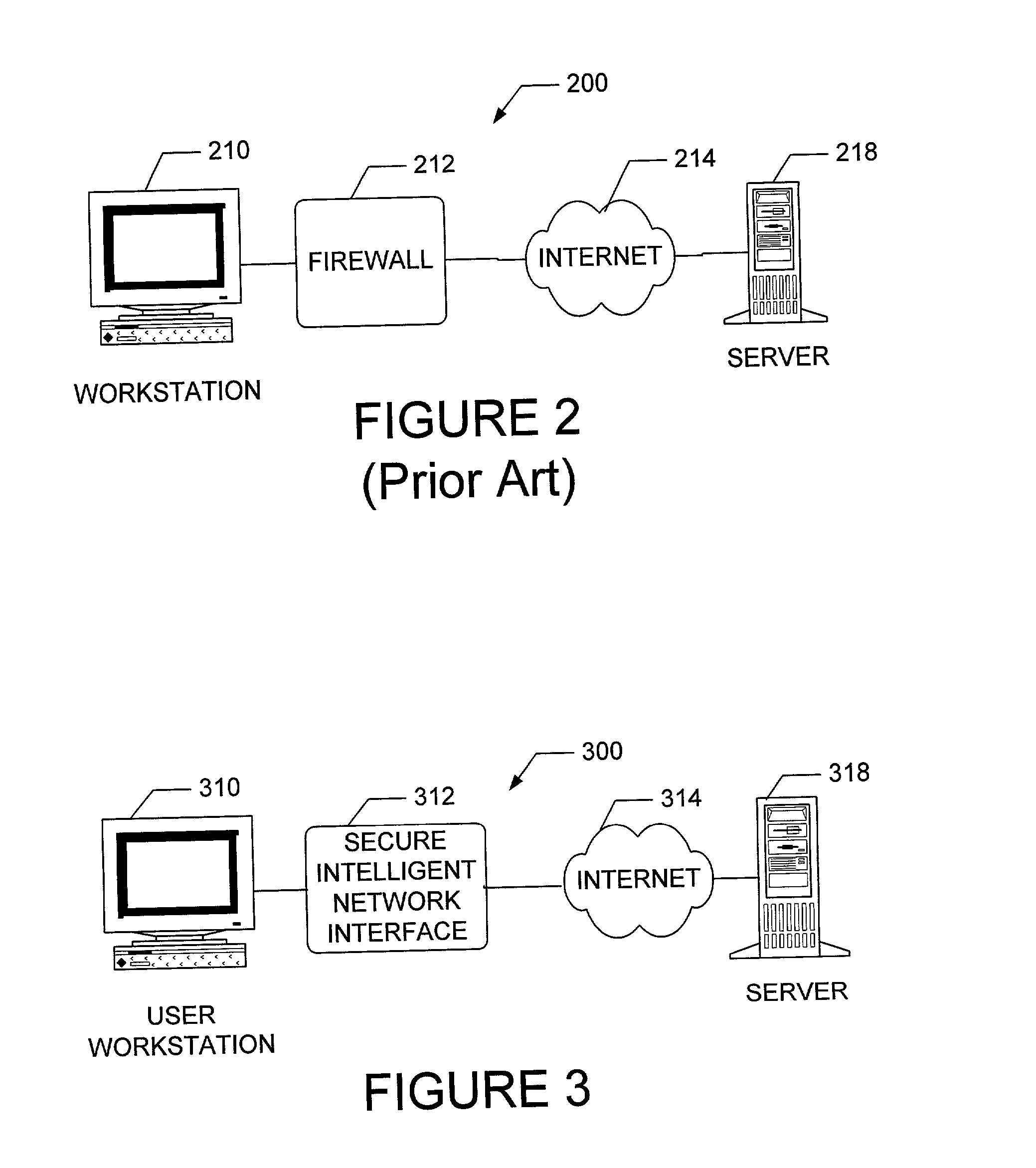
Apparatus and method for providing secure network communication
InactiveUS20020162026A1Eliminate attackEliminate needData taking preventionDigital data processing detailsFault toleranceIntelligent Network
The present invention is drawn to an apparatus and method for providing secure network communication. Each node or computer on the network has a secure, intelligent network interface with a coprocessor that handles all network communication. The intelligent network interface can be built into a network interface card (NIC) or be a separate box between each machine and the network. The intelligent network interface encrypts outgoing packets and decrypts incoming packets from the network based on a key and algorithm managed by a centralized management console (CMC) on the network. The intelligent network interface can also be configured by the CMC with dynamically distributed code to perform authentication functions, protocol translations, single sign-on functions, multi-level firewall functions, distinguished-name based firewall functions, centralized user management functions, machine diagnostics, proxy functions, fault tolerance functions, centralized patching functions, Web-filtering functions, virus-scanning functions, auditing functions, and gateway intrusion detection functions.
Owner:NEUMAN MICHAEL +1
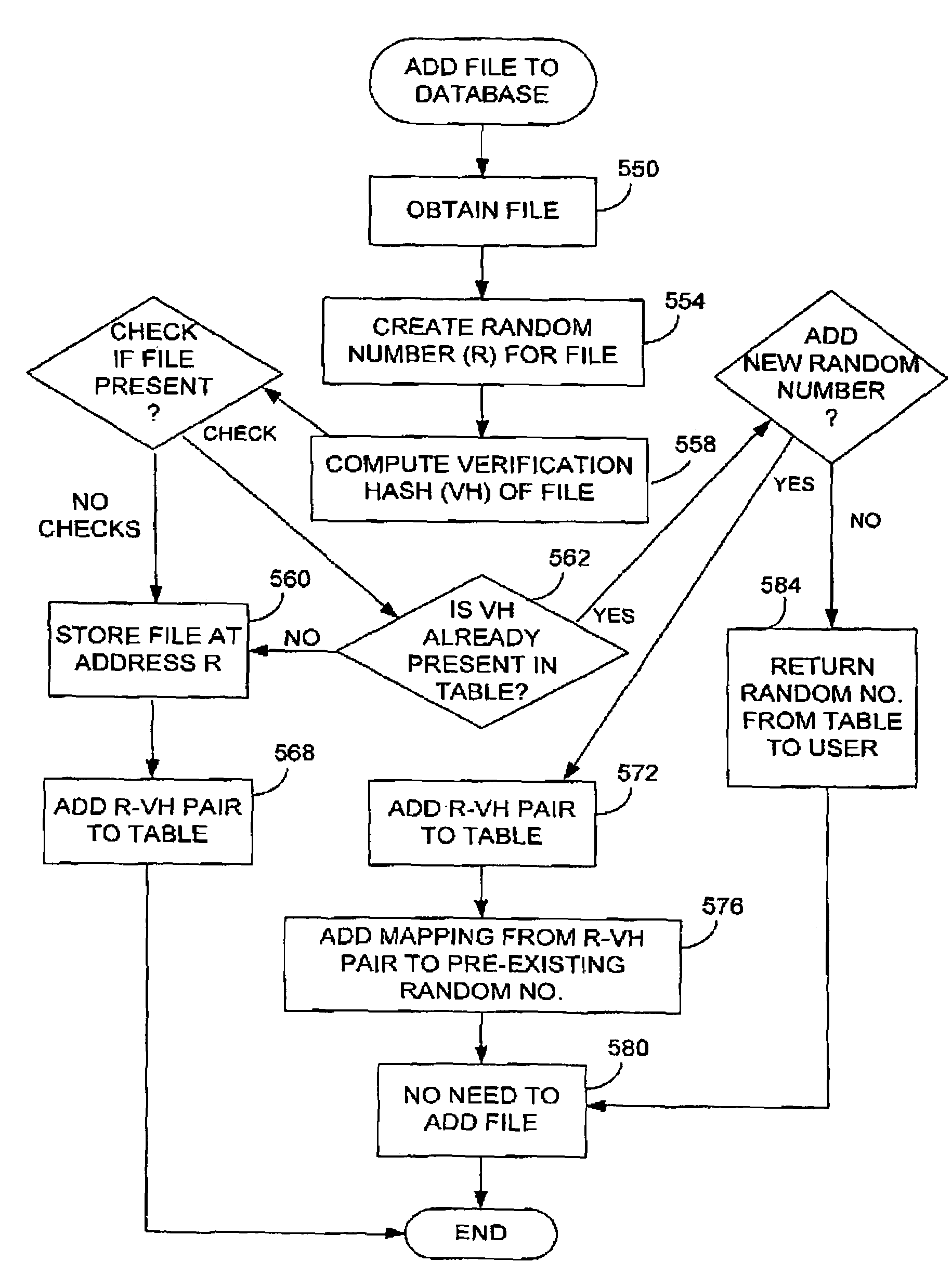
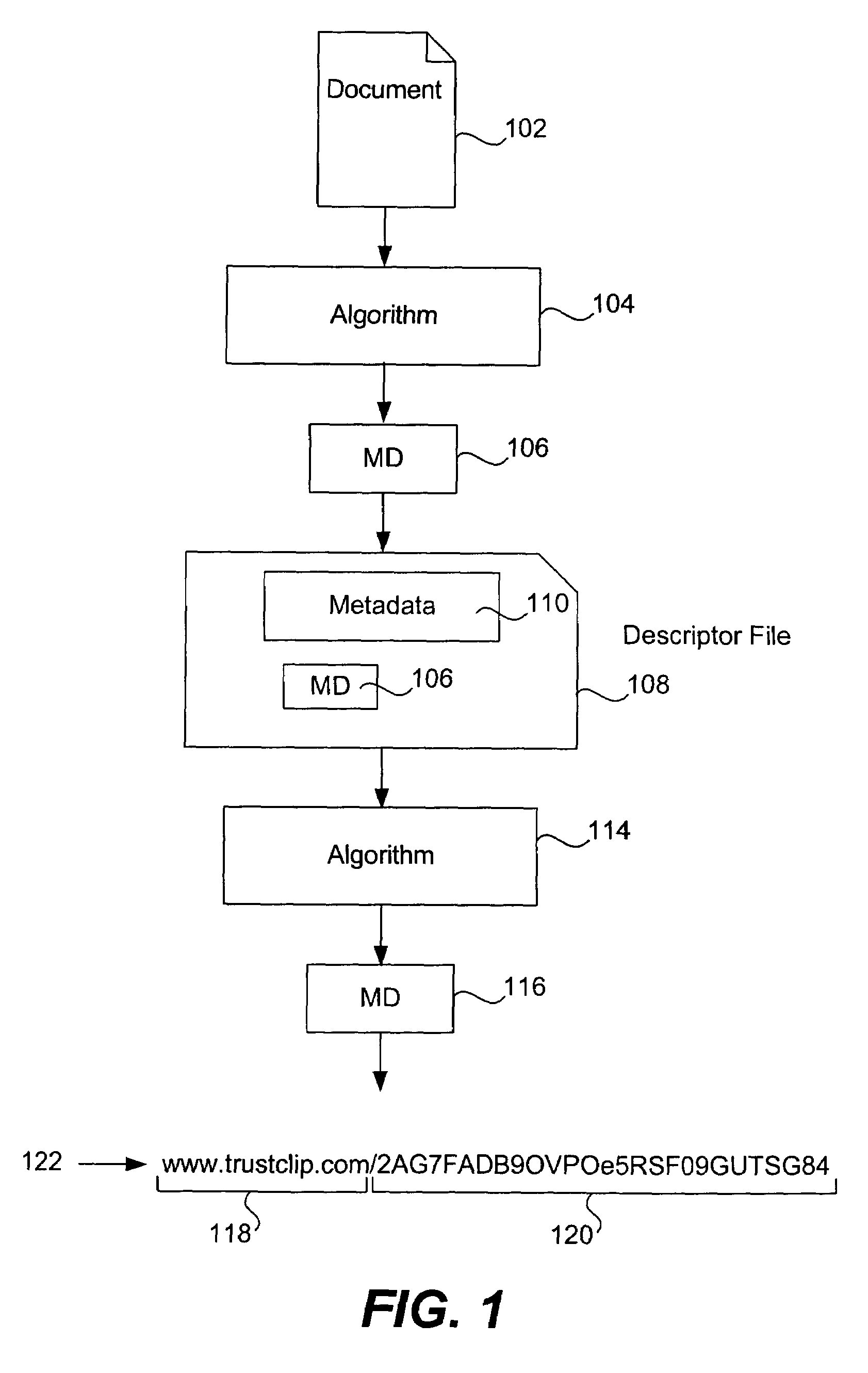
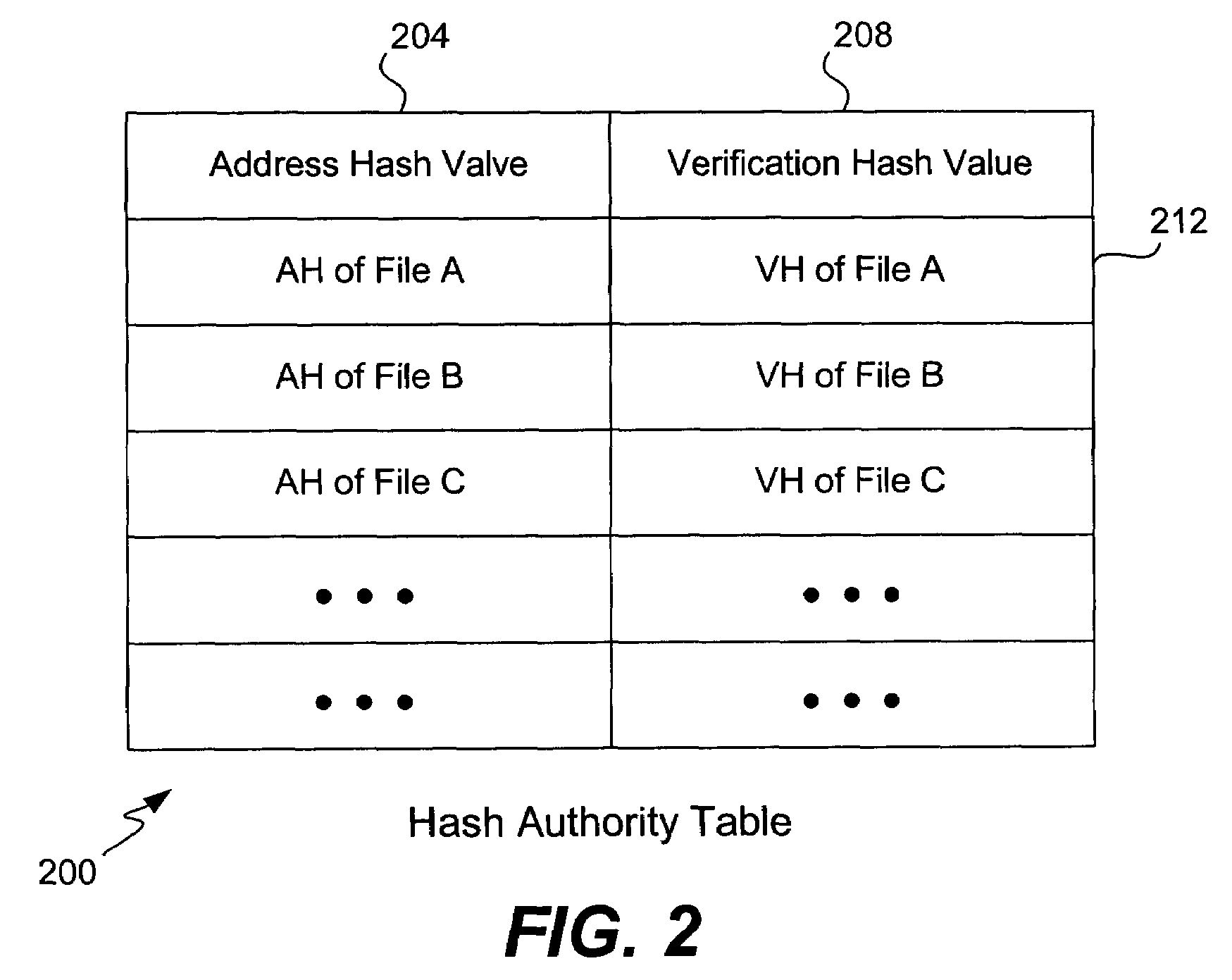
Additional hash functions in content-based addressing
ActiveUS7373345B2Eliminate malicious hash attackEliminate attackData processing applicationsDigital data information retrievalComputer hardwareHash function
A hash function used for content addressing is different from the hash function used for content verification. Adding a file to a database involves storing both hash function values in a table as pair. Verifying the integrity of a file believed to be a duplicate in a database, or when retrieving a file, makes use of the verification hash function. Files can be continuously checked. A multi-level database can be used. A second hash function can be added to an existing system. A verification hash function can be upgraded and more than one content verification hash function can be used. In a variation, a random number generator is used instead of a hash function for content addressing; the verification hash function is also used. Files addressed using a random number are added or retrieved from a database and their verification hash values are checked. Time stamps and digital signatures are used for security.
Owner:DATACORE SOFTWARE
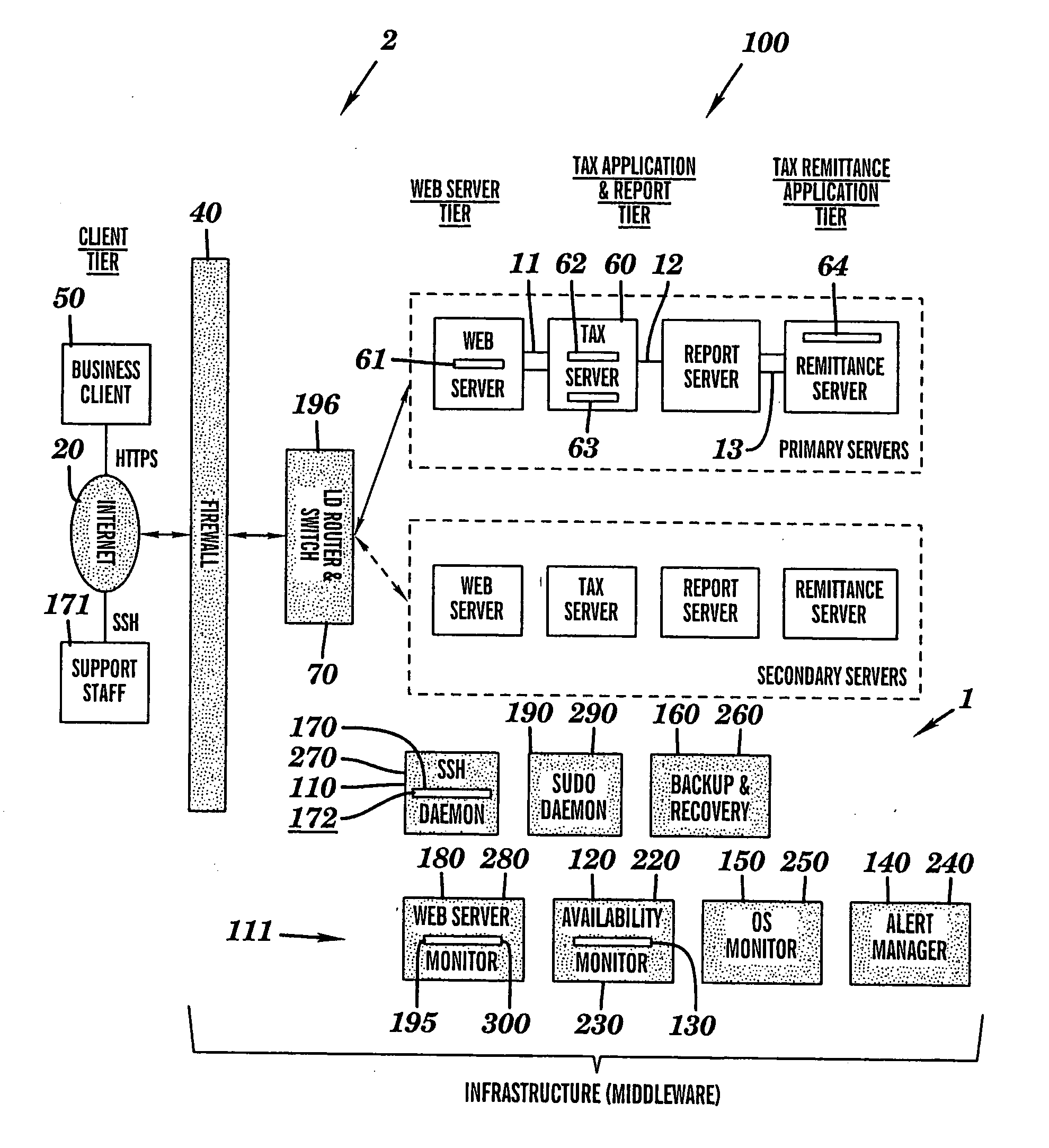
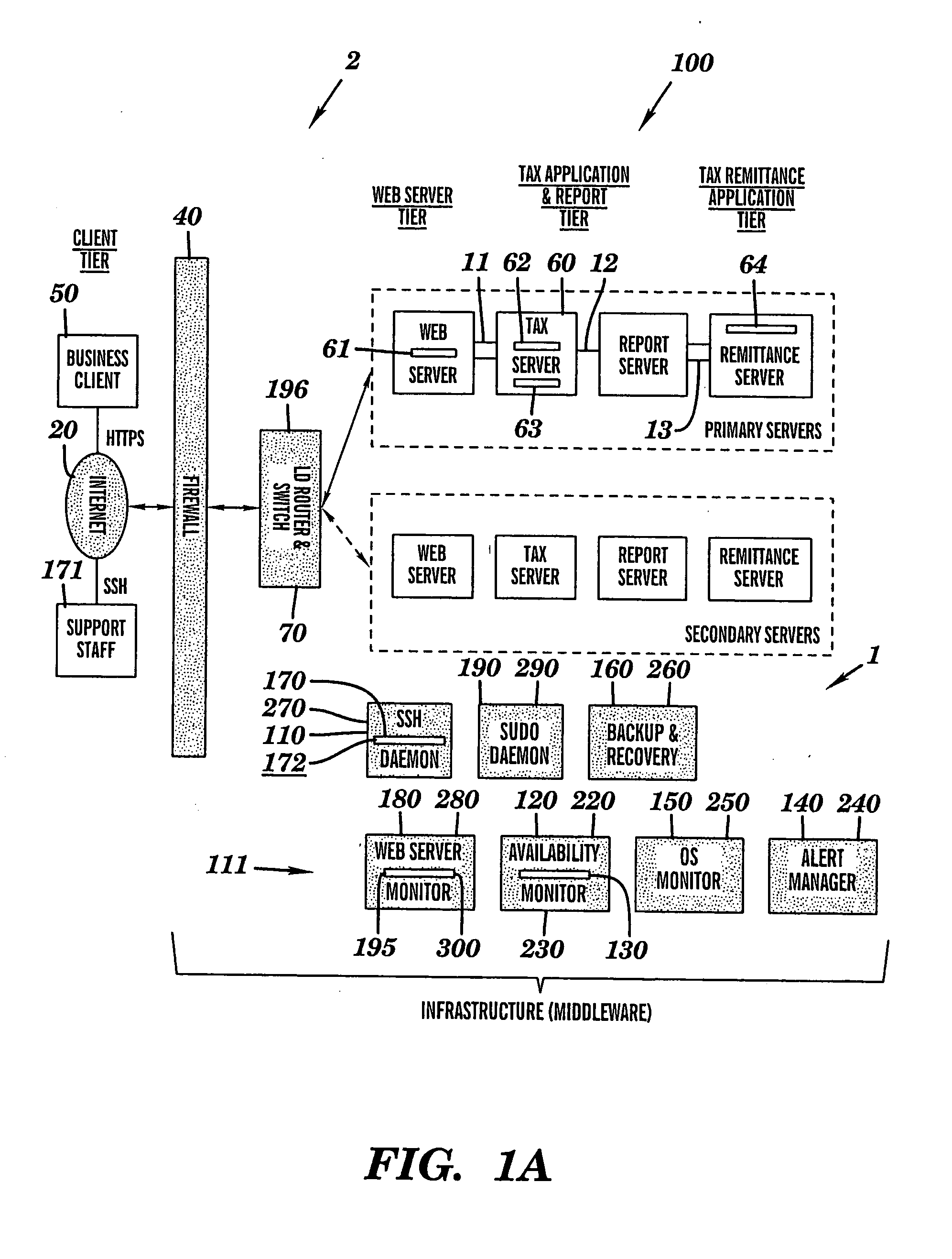
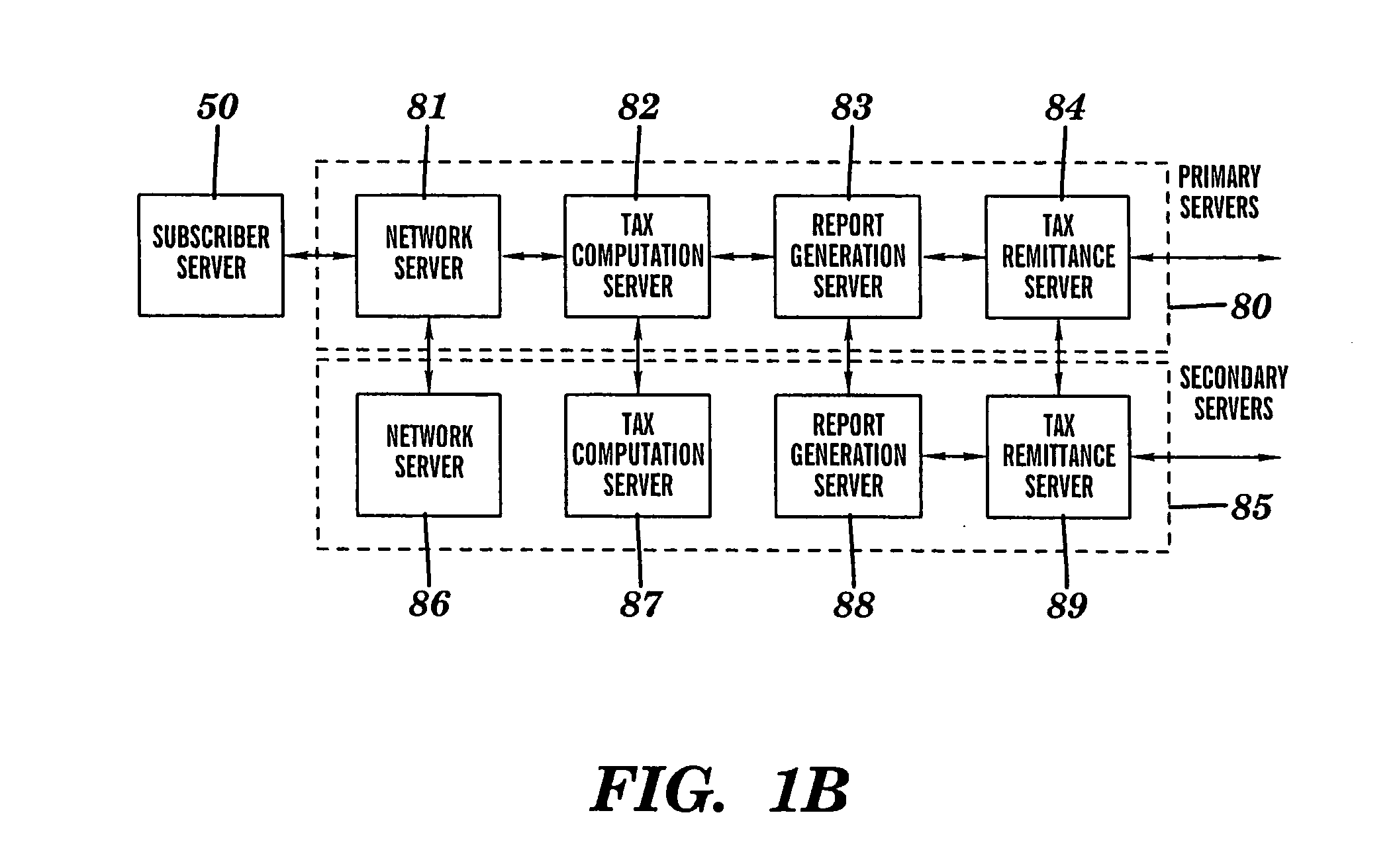
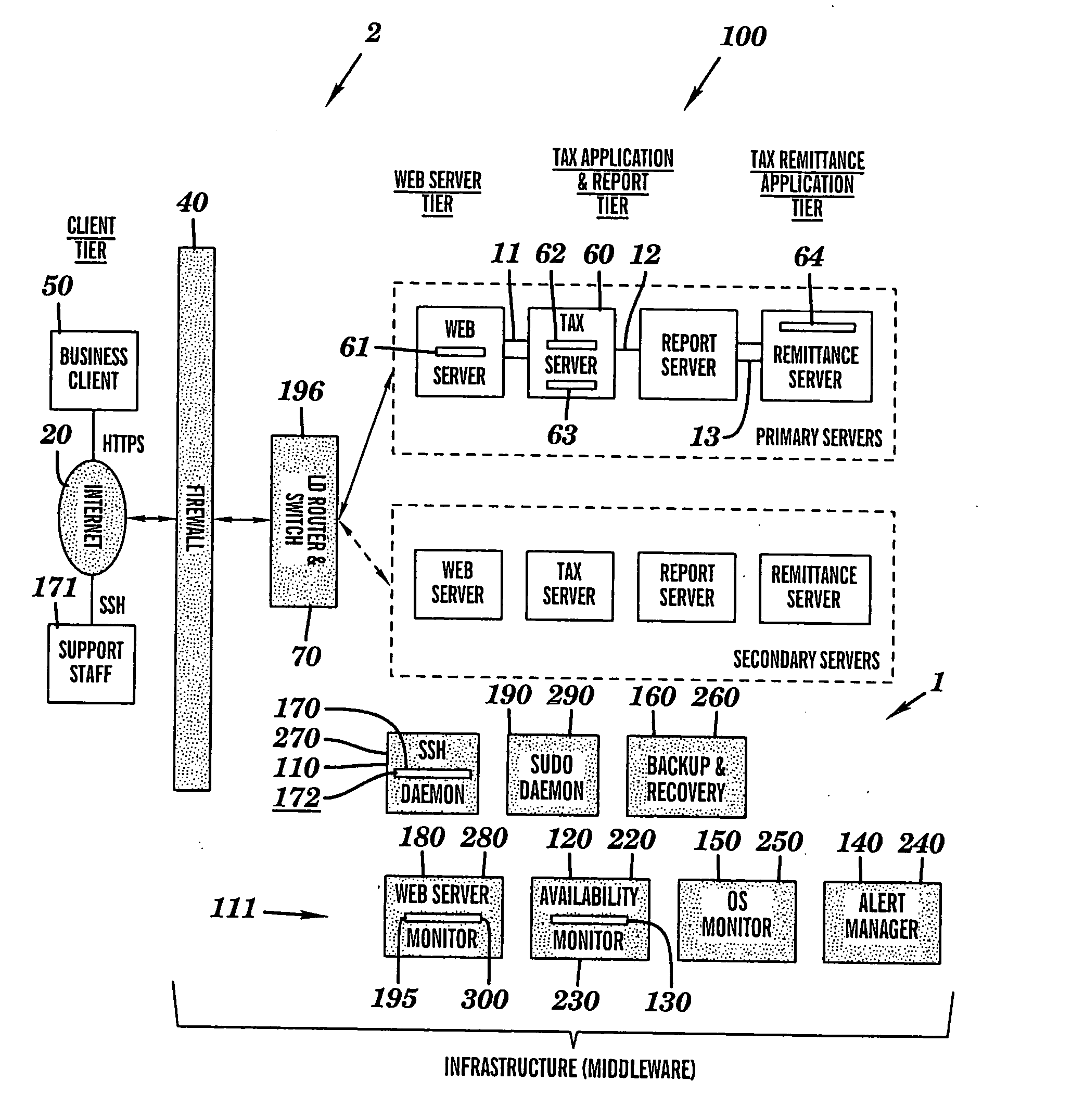
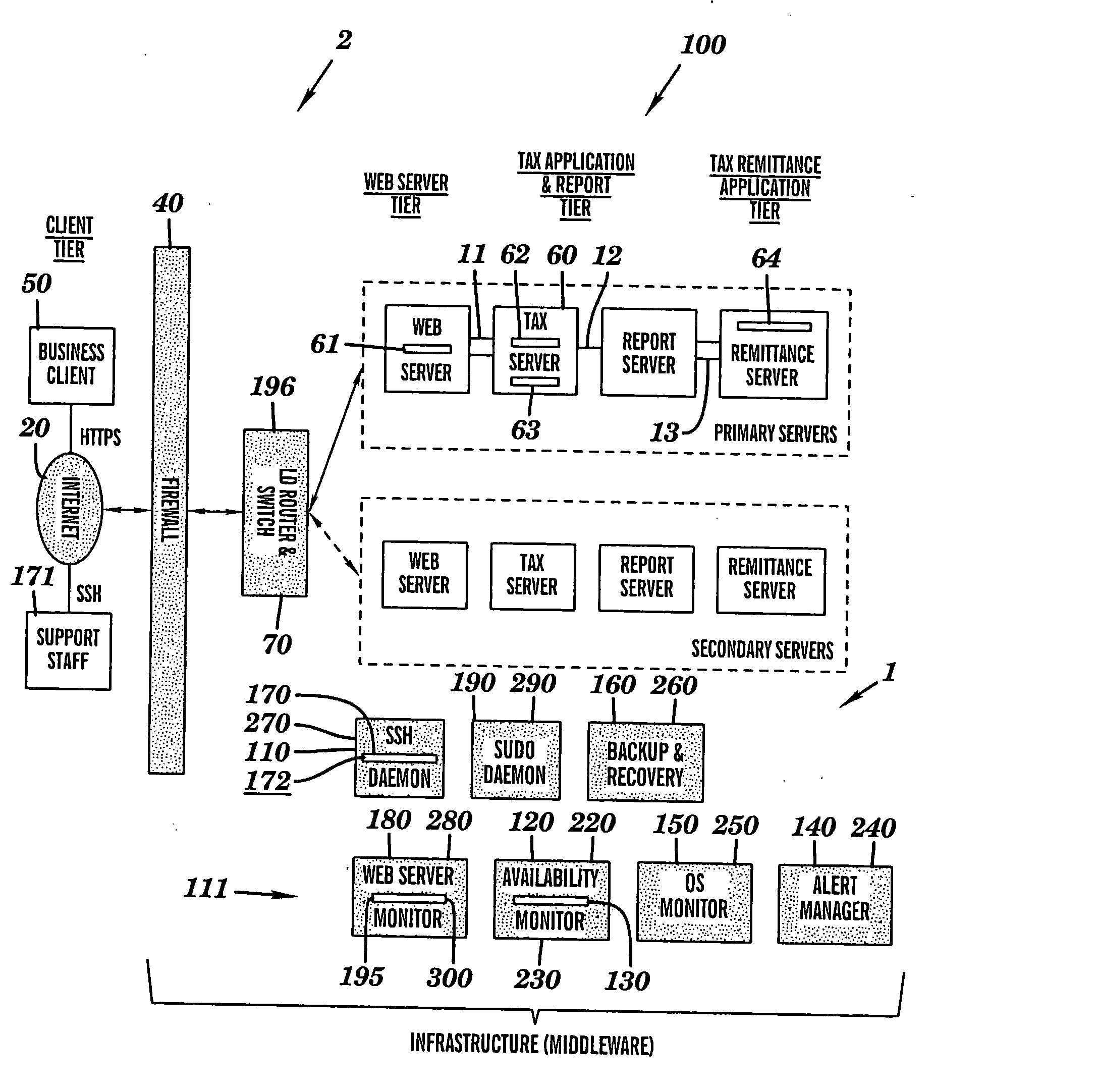
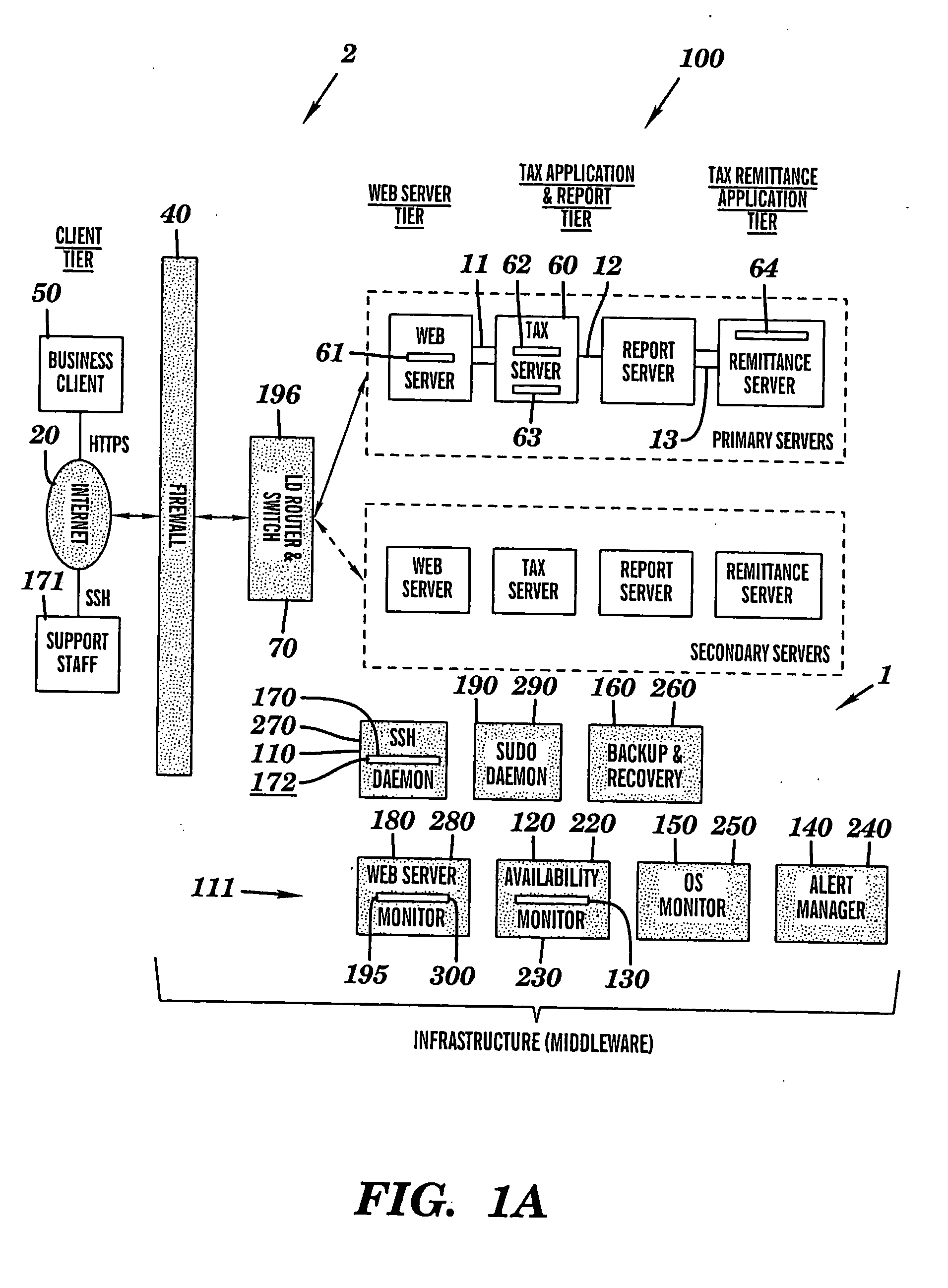
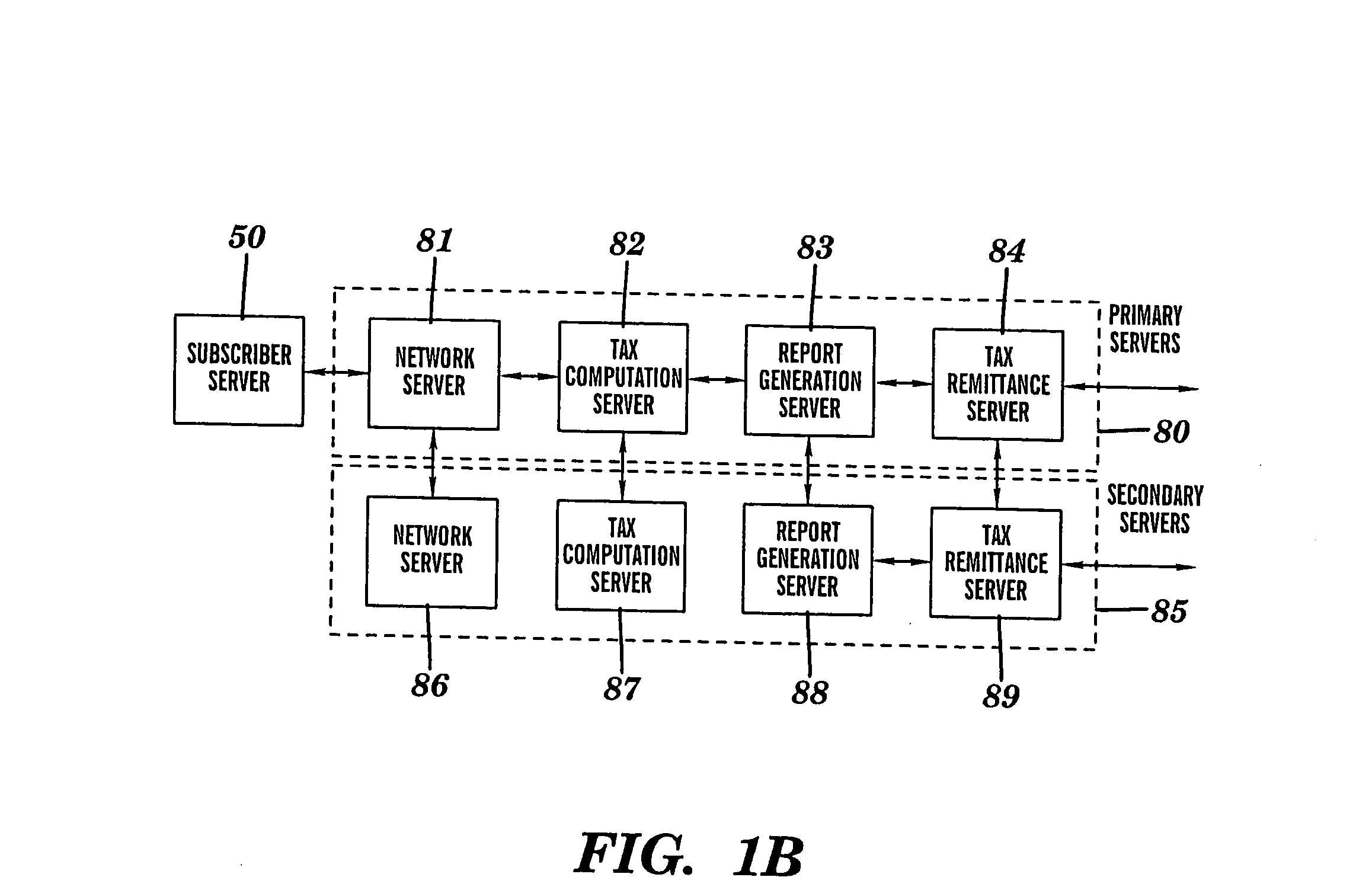
Intelligent system infrastructure for financial data computation, report remittance and funds transfer over an interactive communications network
InactiveUS20050119955A1Eliminate eavesdroppingEliminate connection hijackingComplete banking machinesFinanceExtensibilityProtection system
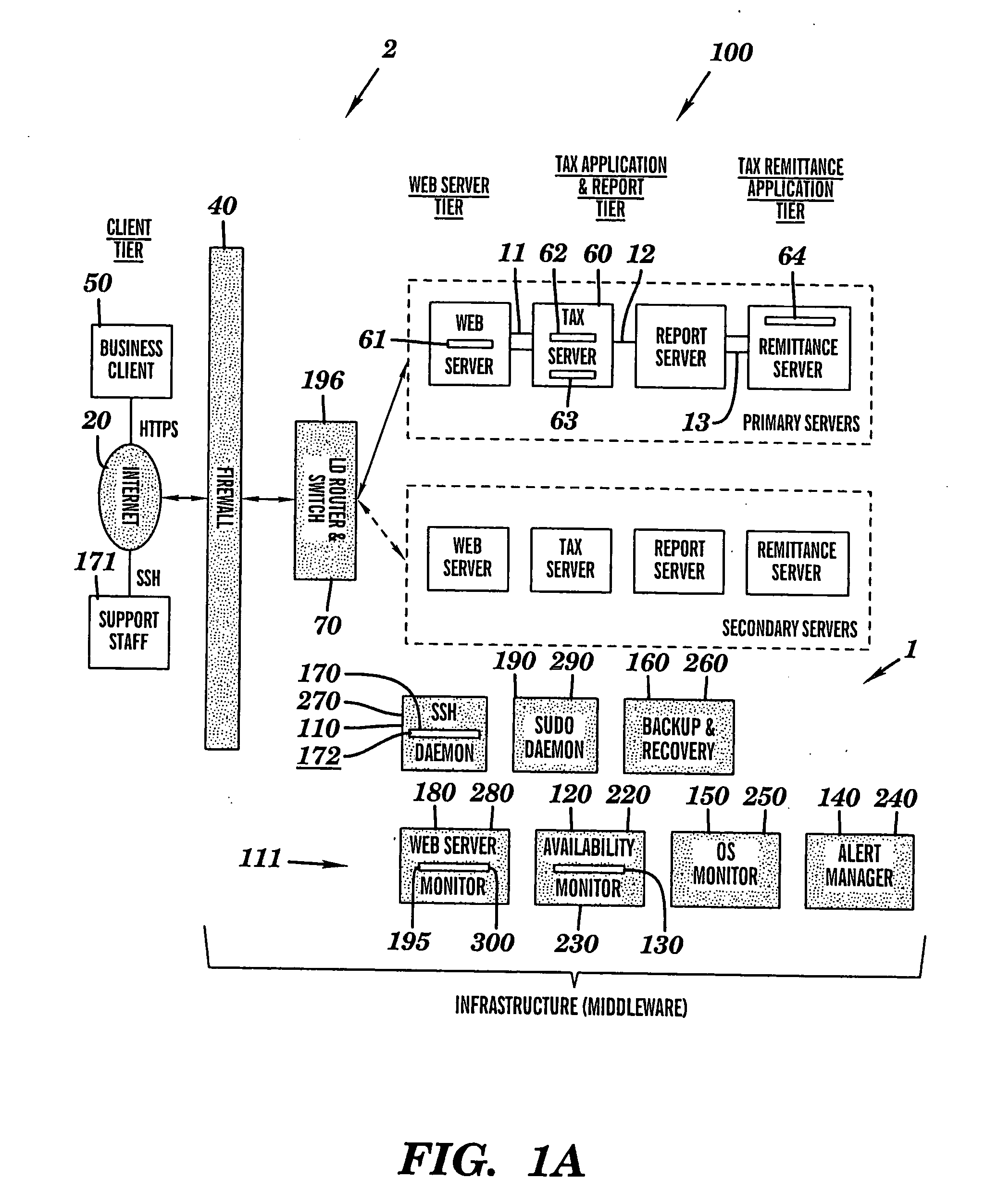
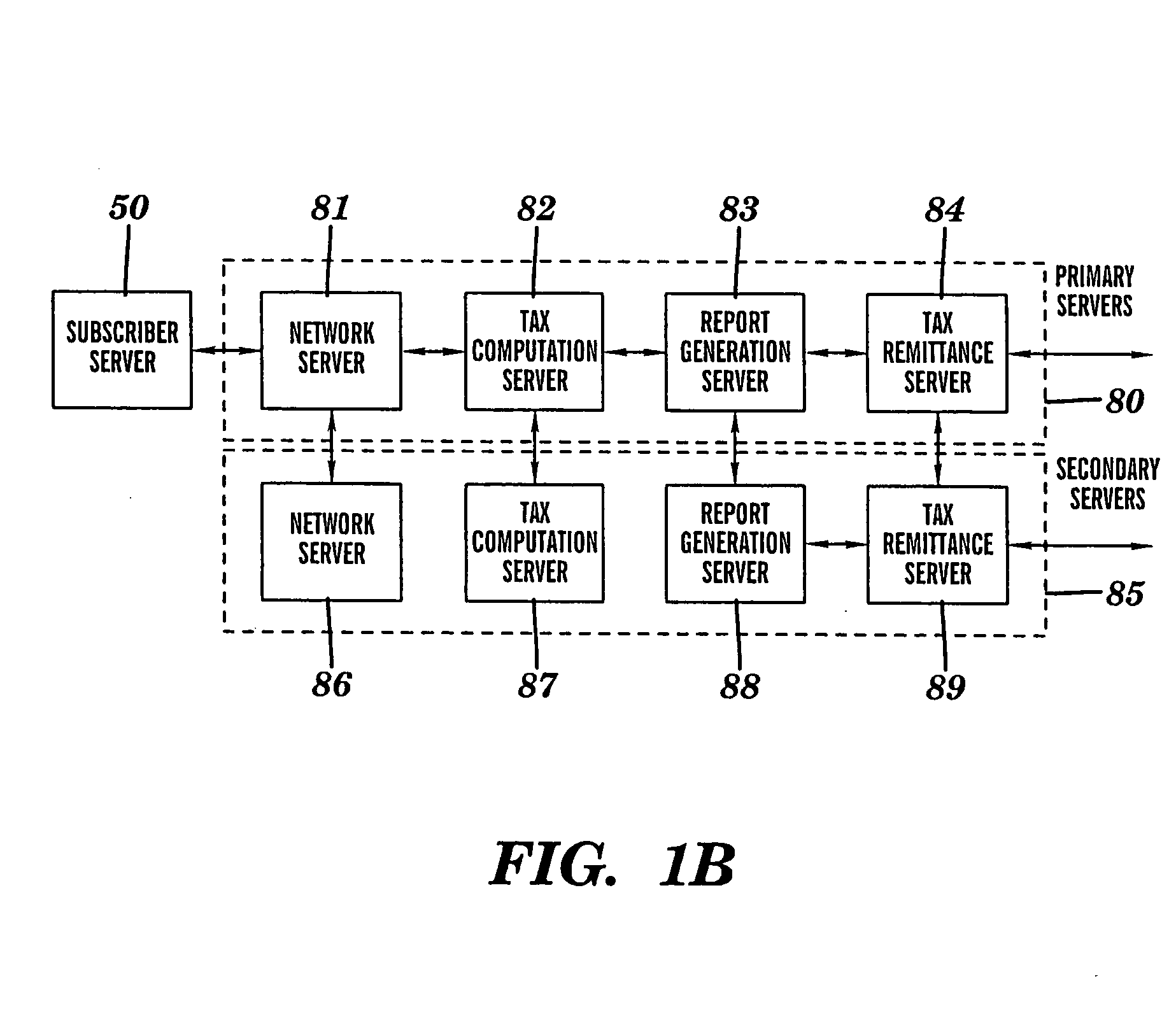
This disclosure relates to a specific, illustrative multilayer architecture for a program controlled system for providing services relating to financial data computation, report remittance and funds transfer services over an interactive communications network. The system comprises a subscriber server for hosting a virtual portal having at least one application for providing e-content to end users, the application including a network browser for accessing, displaying and transmitting data over the network. A first service provider server allows a system administrator to access the system remotely. A first security system for protecting the system from entry of unwanted data during data transfer over the network between the subscriber and service provider servers and the interactive communications network level. Also provided are plurality of primary servers including a primary network server, a primary tax computation server, a primary report generation server and a primary tax remittance server. The network server receives a tax computation transaction request from the subscriber server, transmits the request to the primary tax computation server, and returns data processed by the tax computation server to the subscriber server. In addition, the system has a plurality of secondary servers redundant to the first. The secondary servers include a secondary network server, a secondary tax computation server, a secondary report generation server and a secondary tax remittance server. A load balancing and scalability system is utilized for load directing, routing and switching functions during data transfer from utilization of at least one function at one of the primary servers to a corresponding function at a secondary server for optimum management of system resources.
Owner:DANG HONG M +3
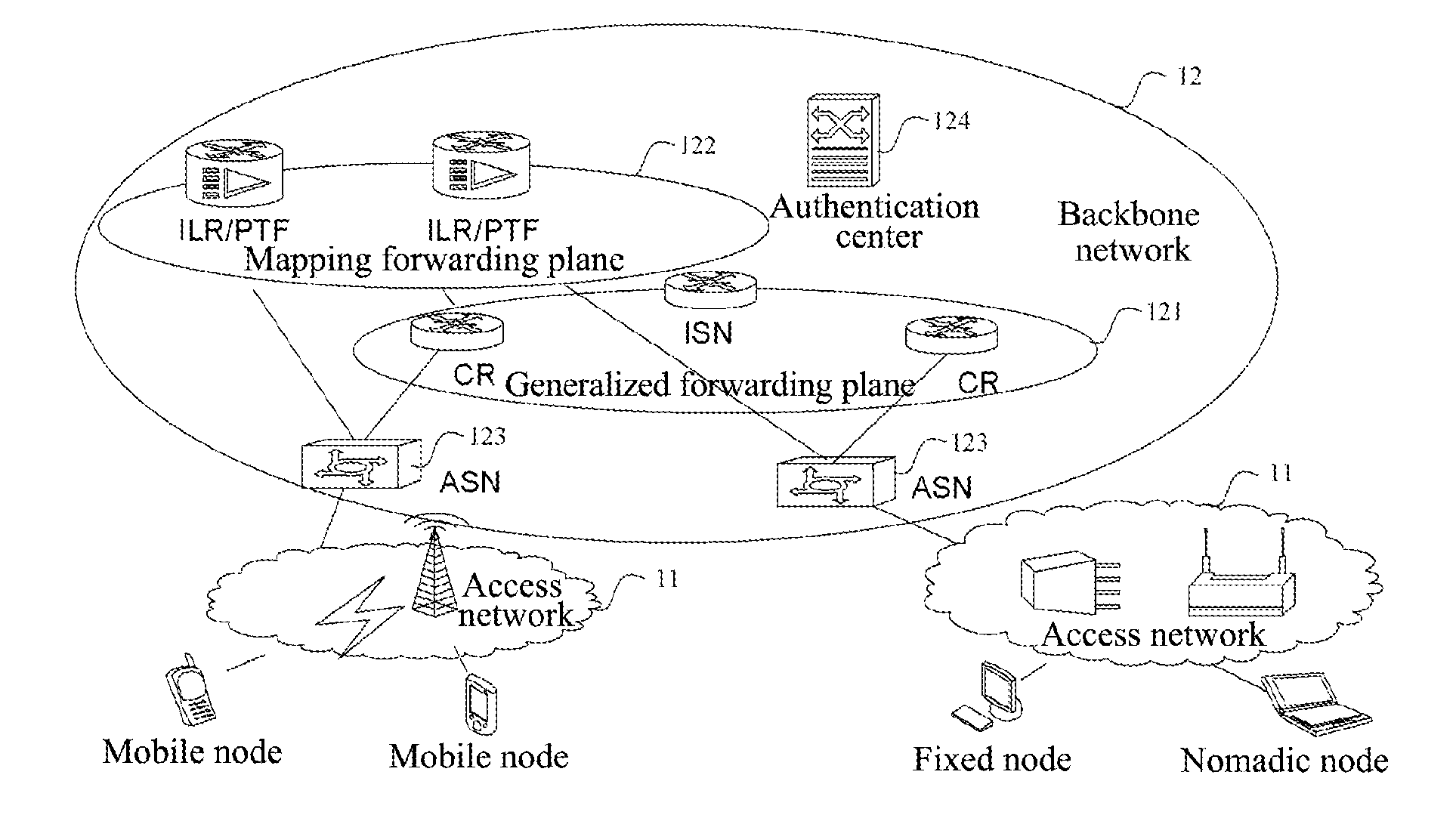
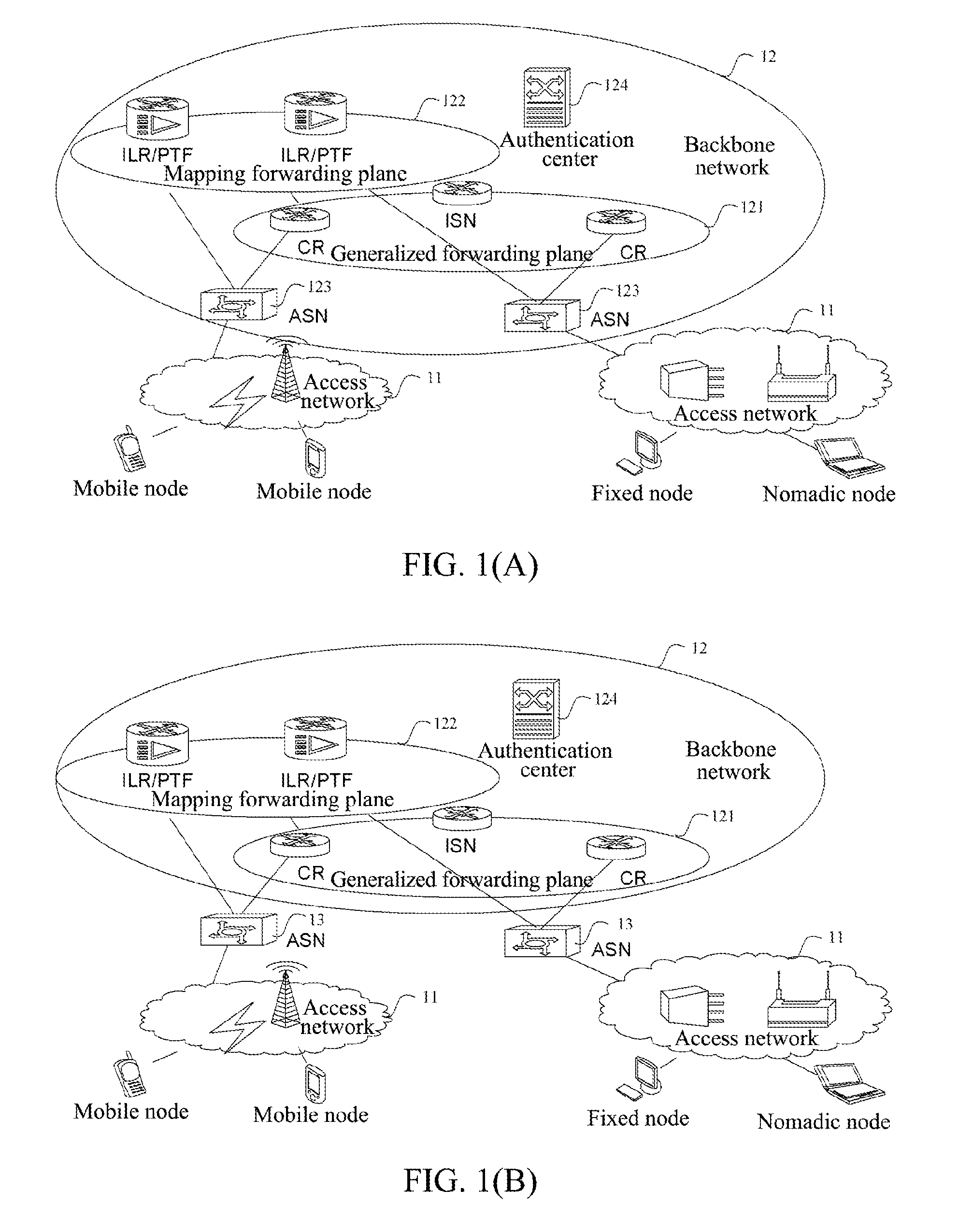
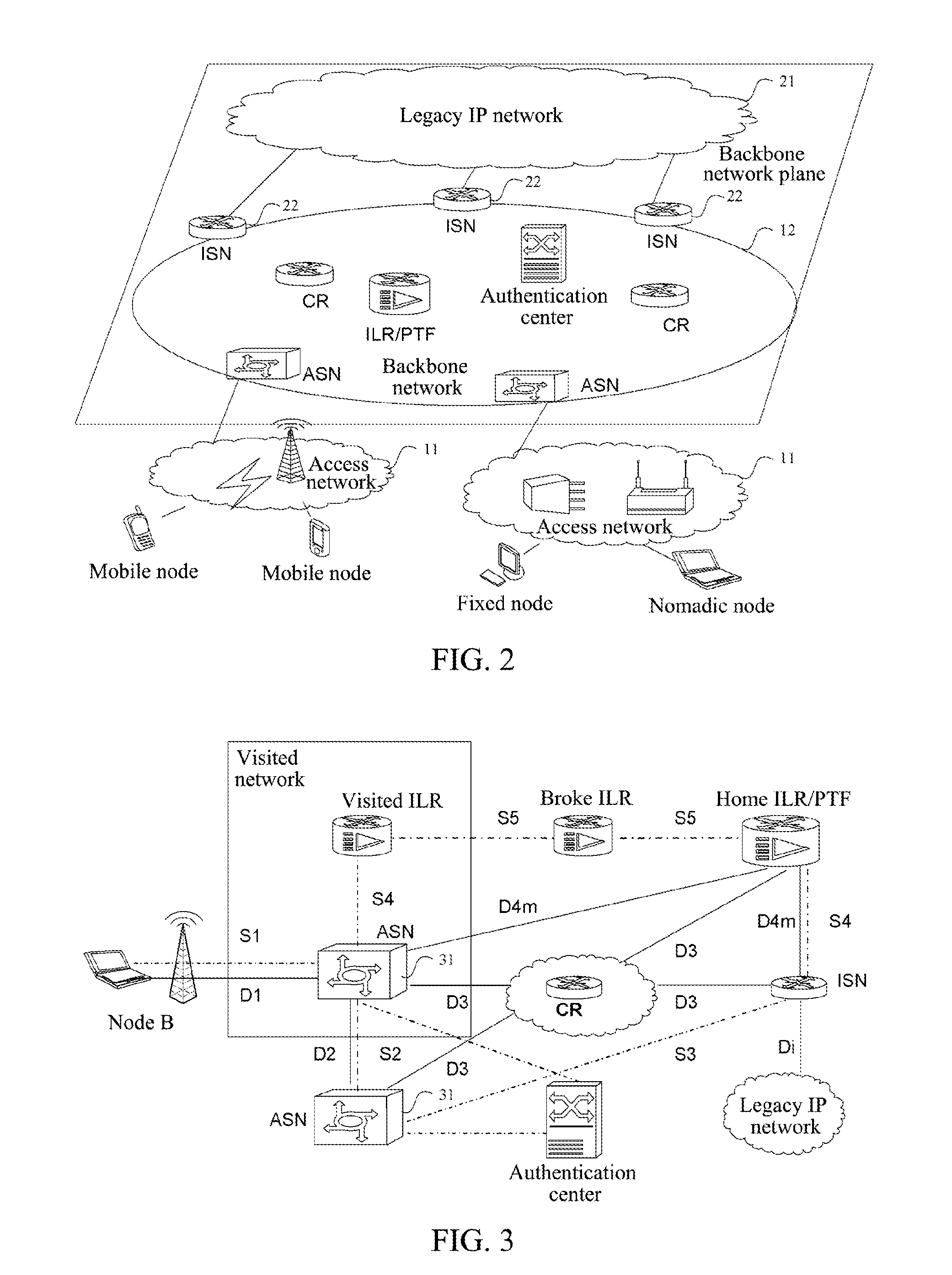
Network based on identity identifier and location separation architecture backbone network, and network element thereof
ActiveUS20120176936A1Improve scalabilityUser privacy is enhancedData switching by path configurationNetwork data managementAccess networkNetwork element
The present invention provides a network based on identity identifier and location separation architecture and each component in the network. The network based on identity identifier and location identifier separation architecture includes access networks and a backbone network, and the access networks and the backbone network have no overlap in topology relation, wherein, the access network is located at an edge of the backbone network, and is set to achieve endpoint access in the access network; the backbone network is set to achieve routing and forwarding of data messages between the endpoints which access via the access networks; in the network, an access identifier (AID) is taken as an identity identifier of an endpoint user, and a routing identifier (RID) is used as a location identifier of the endpoint. The present invention achieves the identity identifier and location separation based on the network.
Owner:ZTE CORP
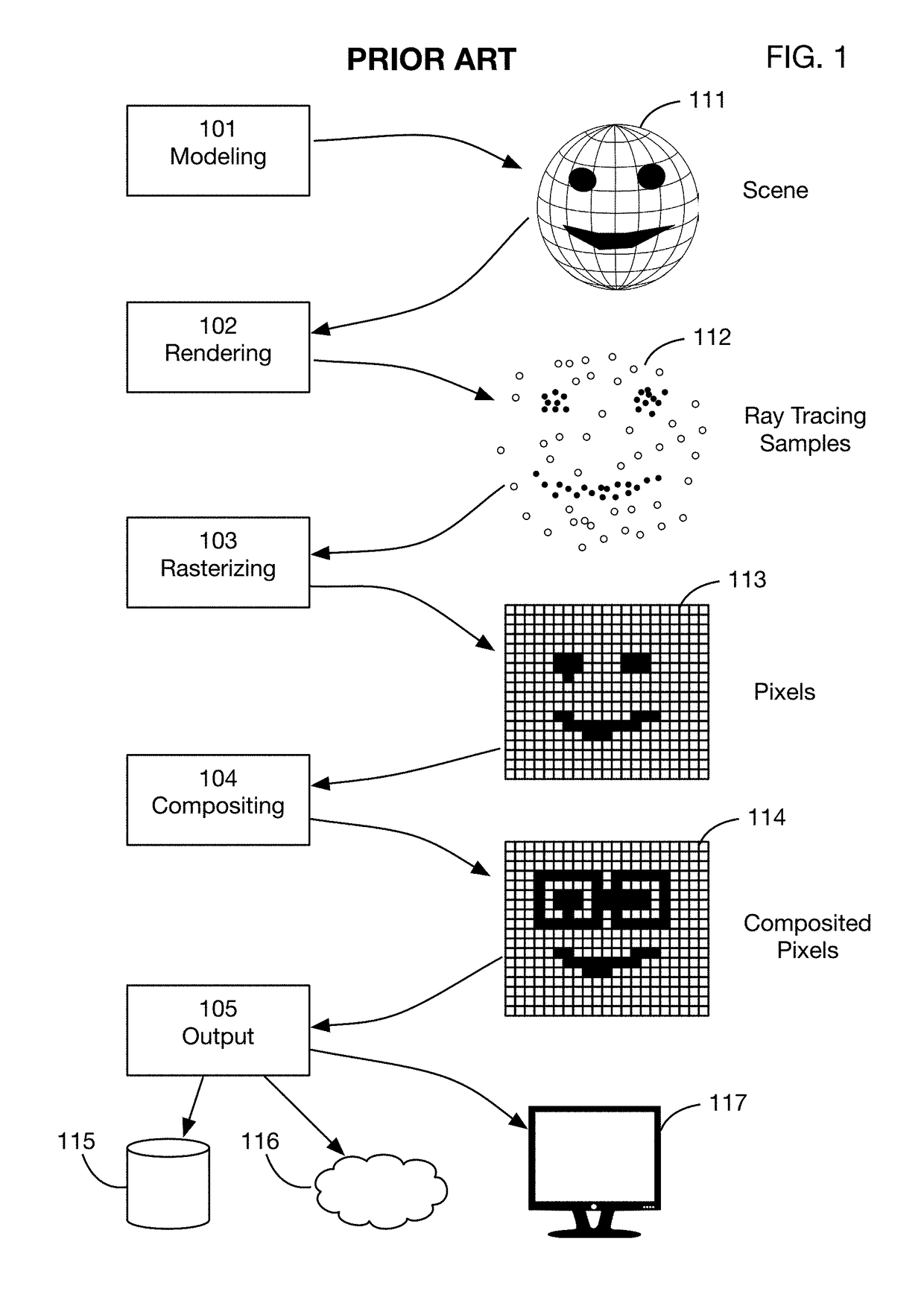
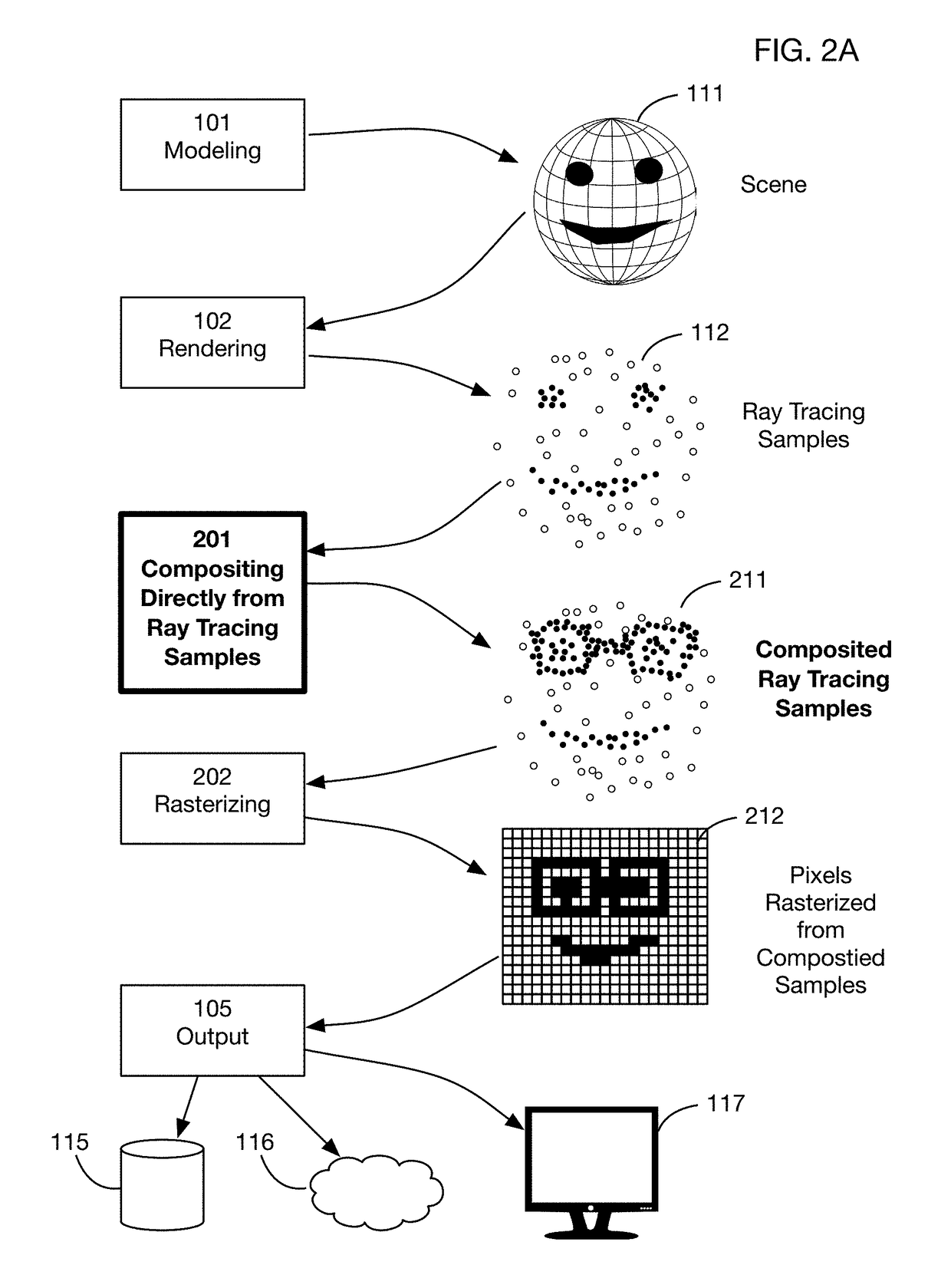
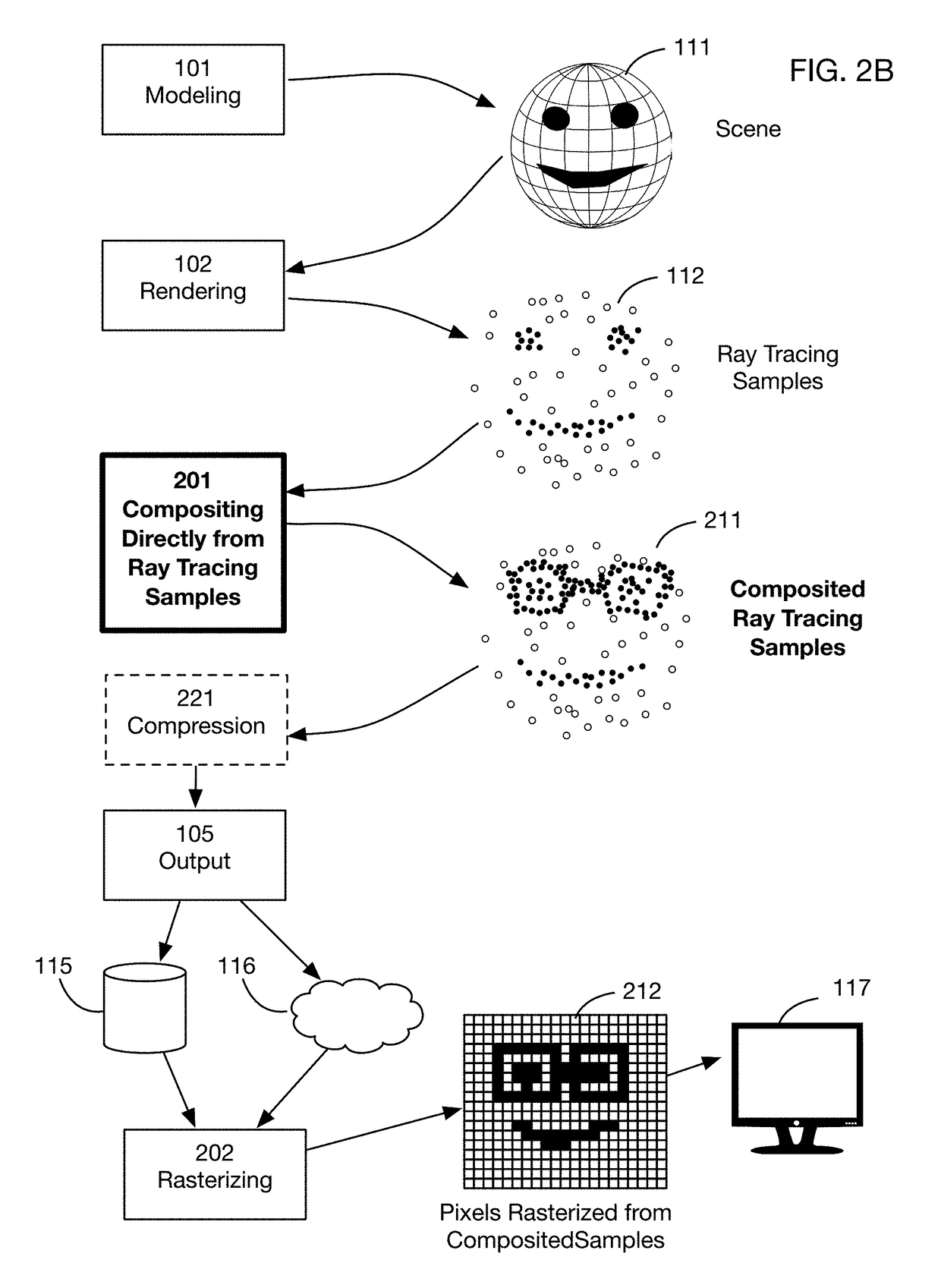
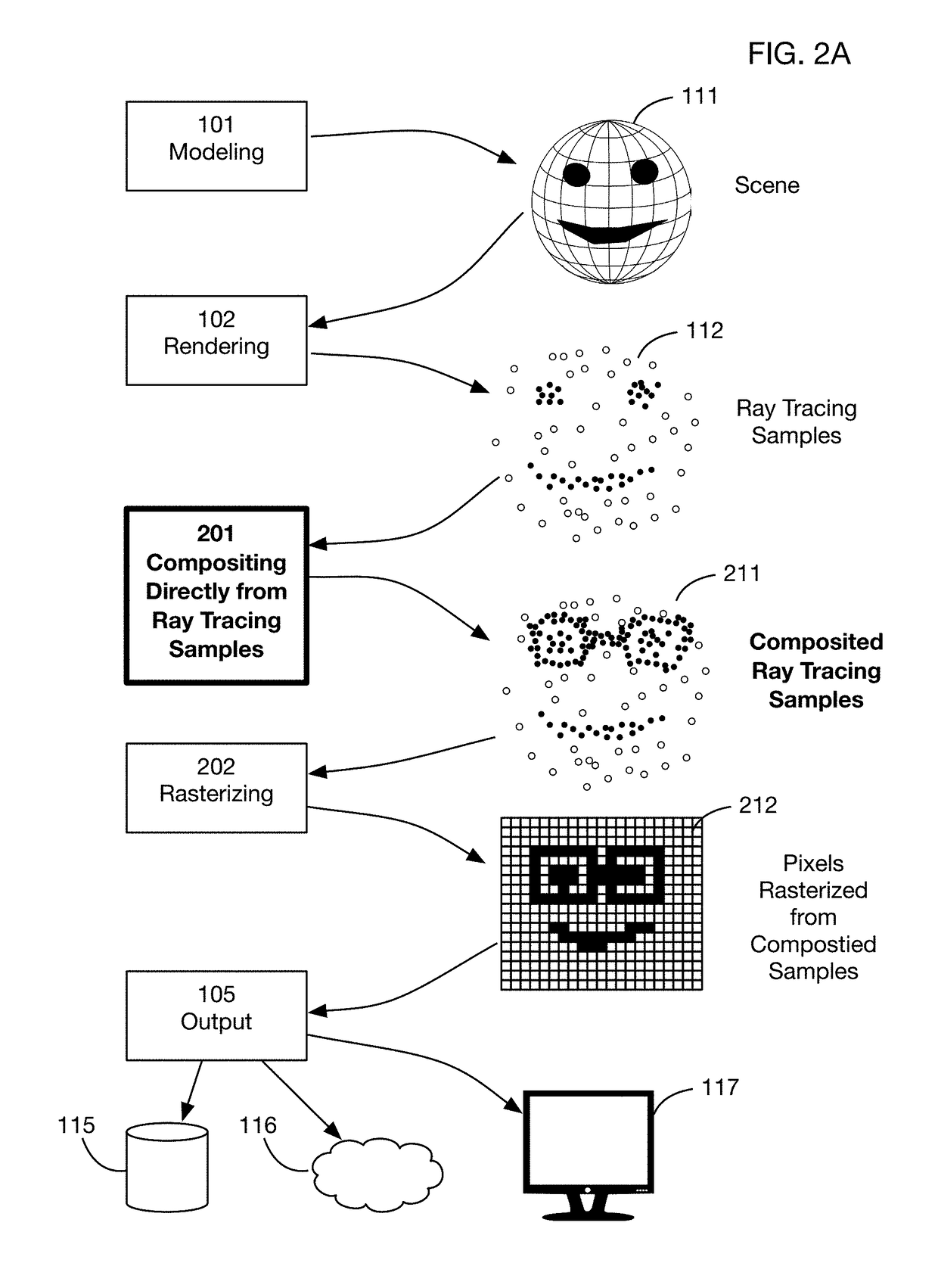
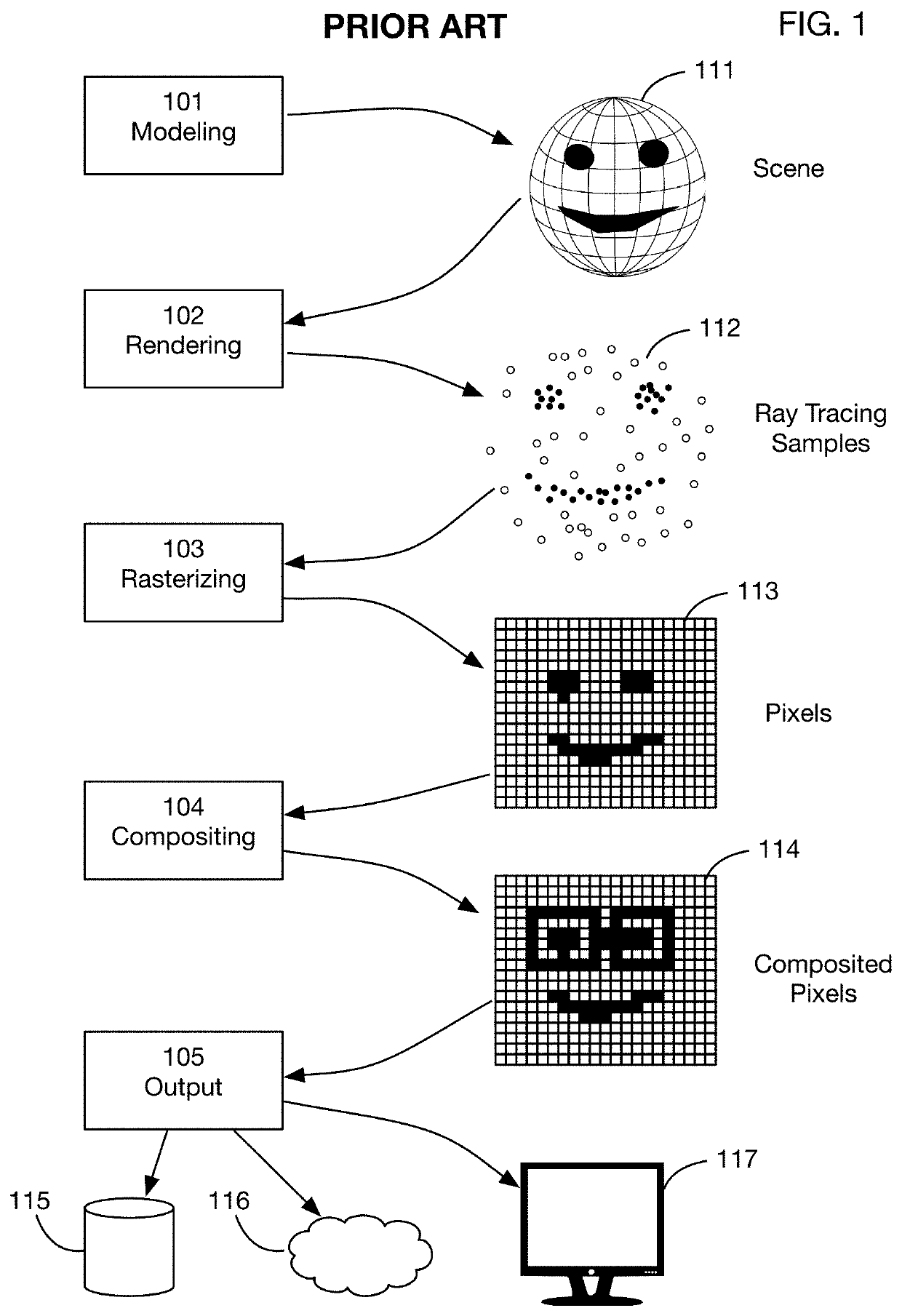
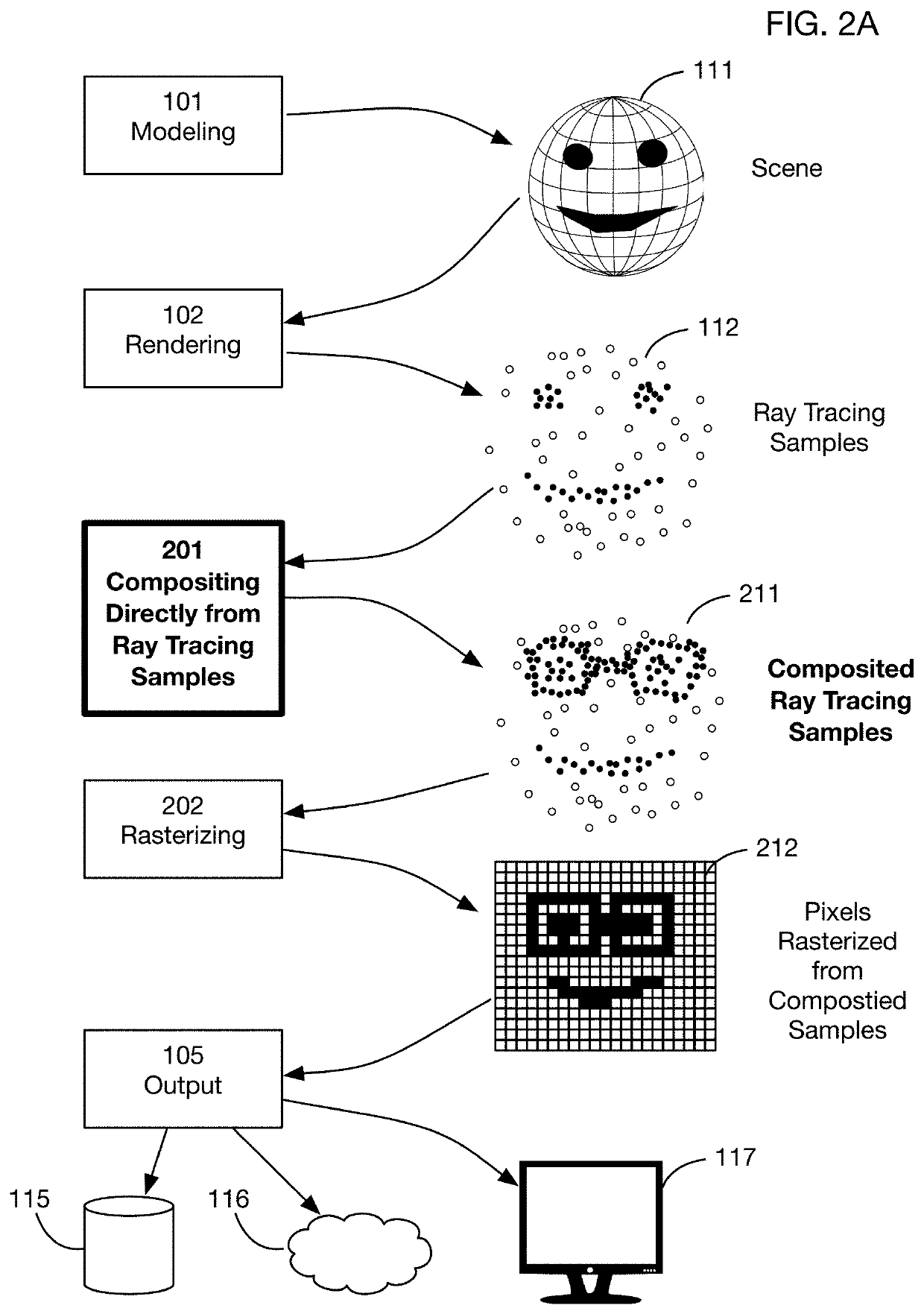
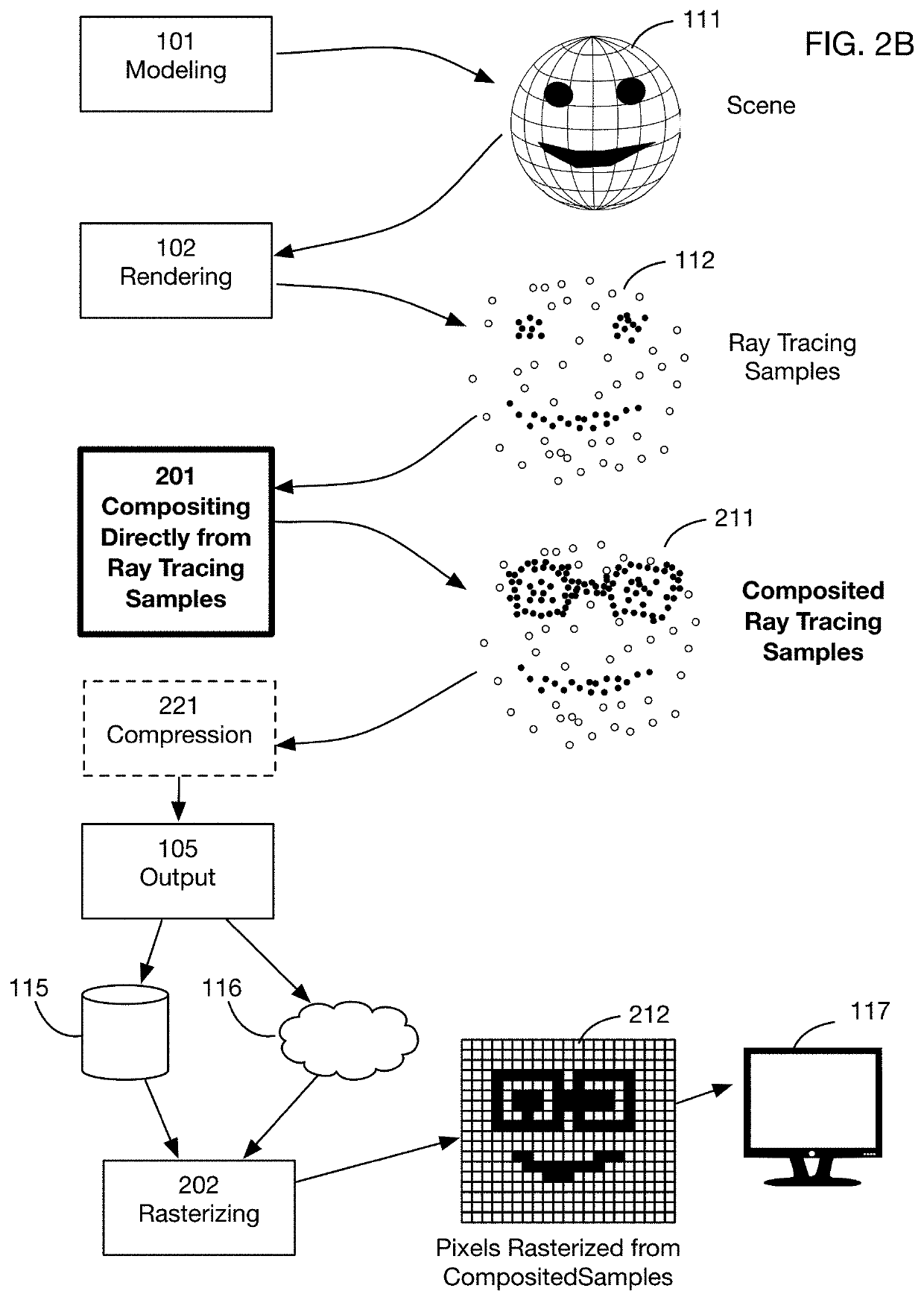
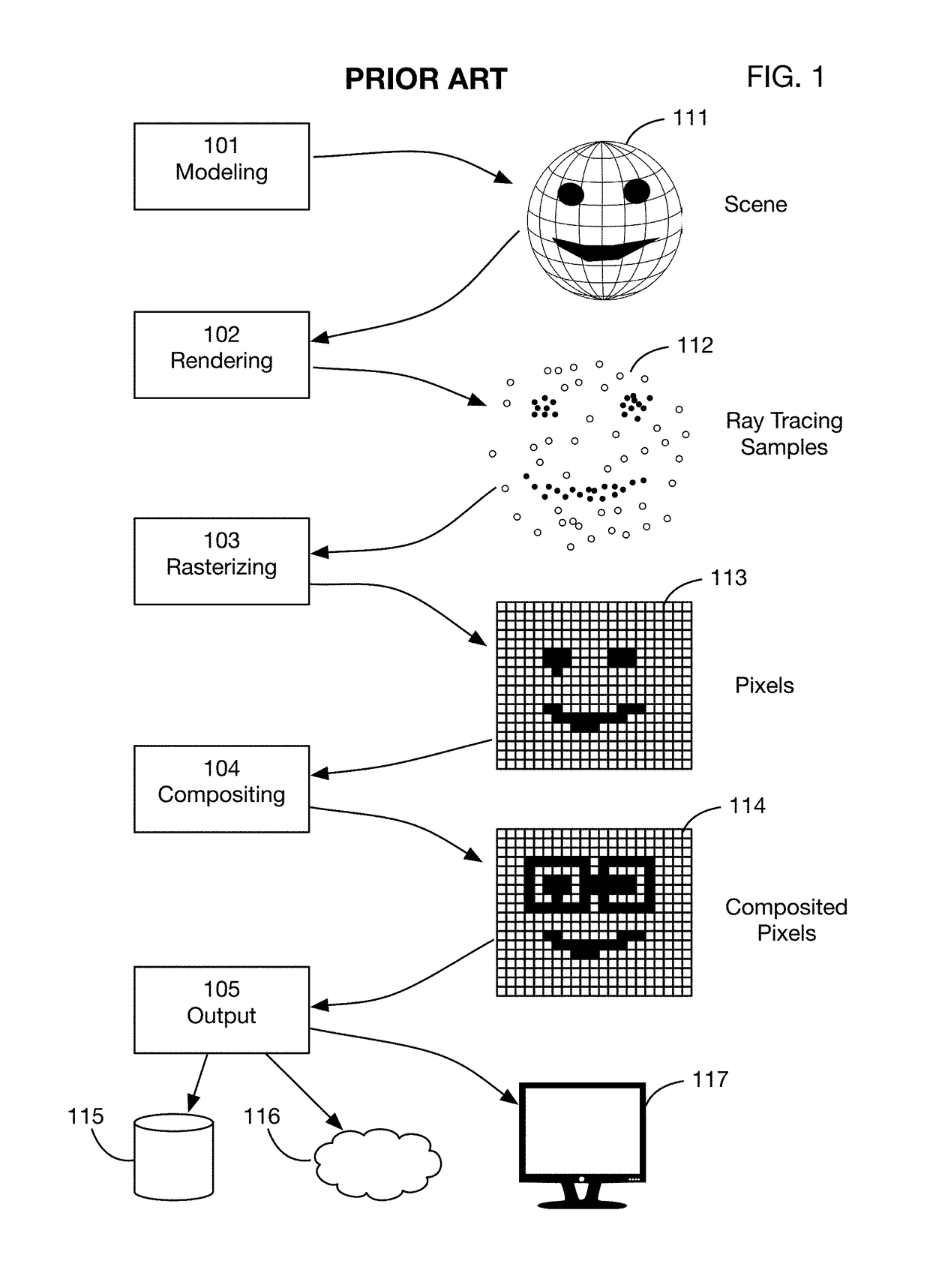
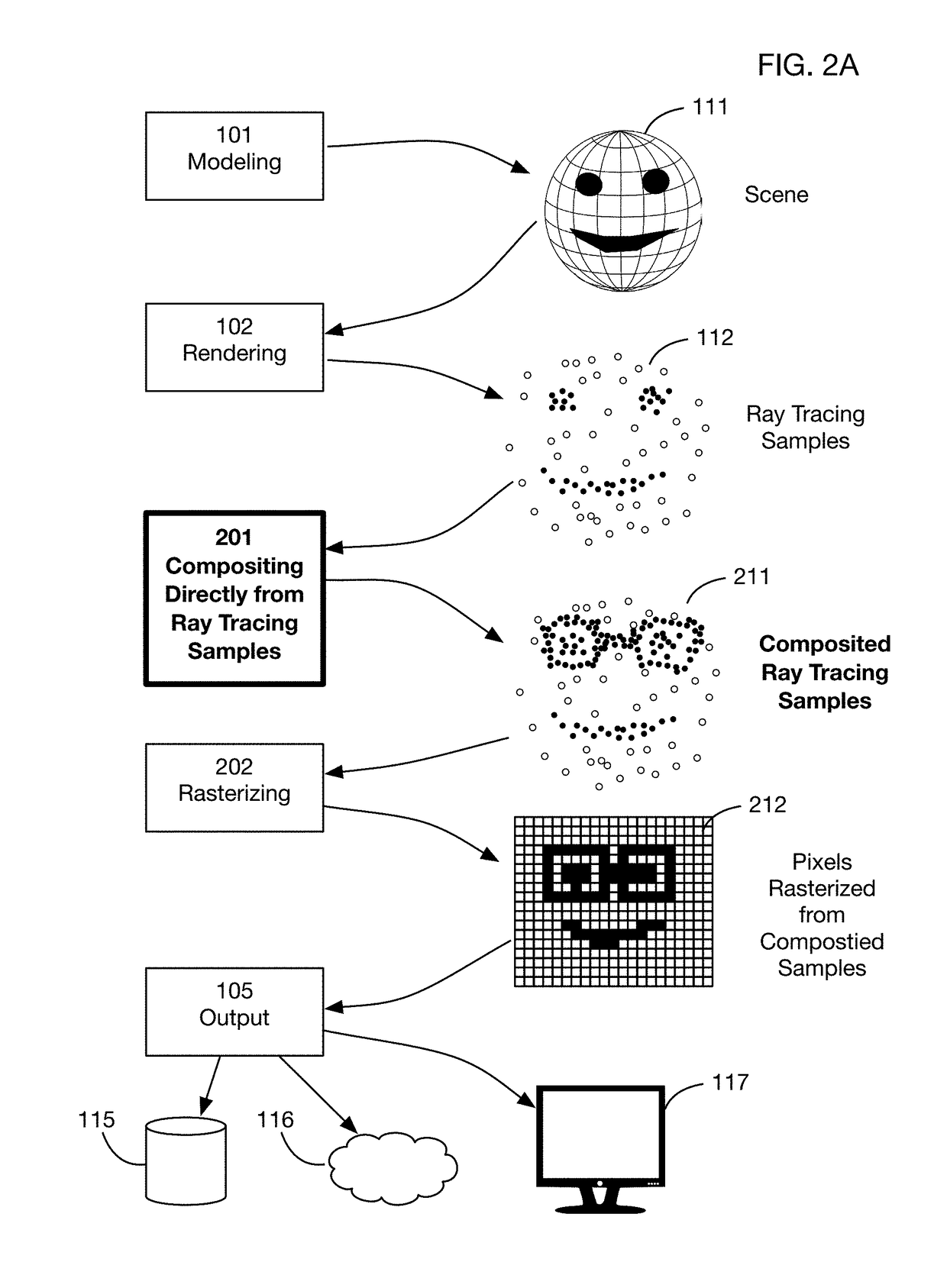
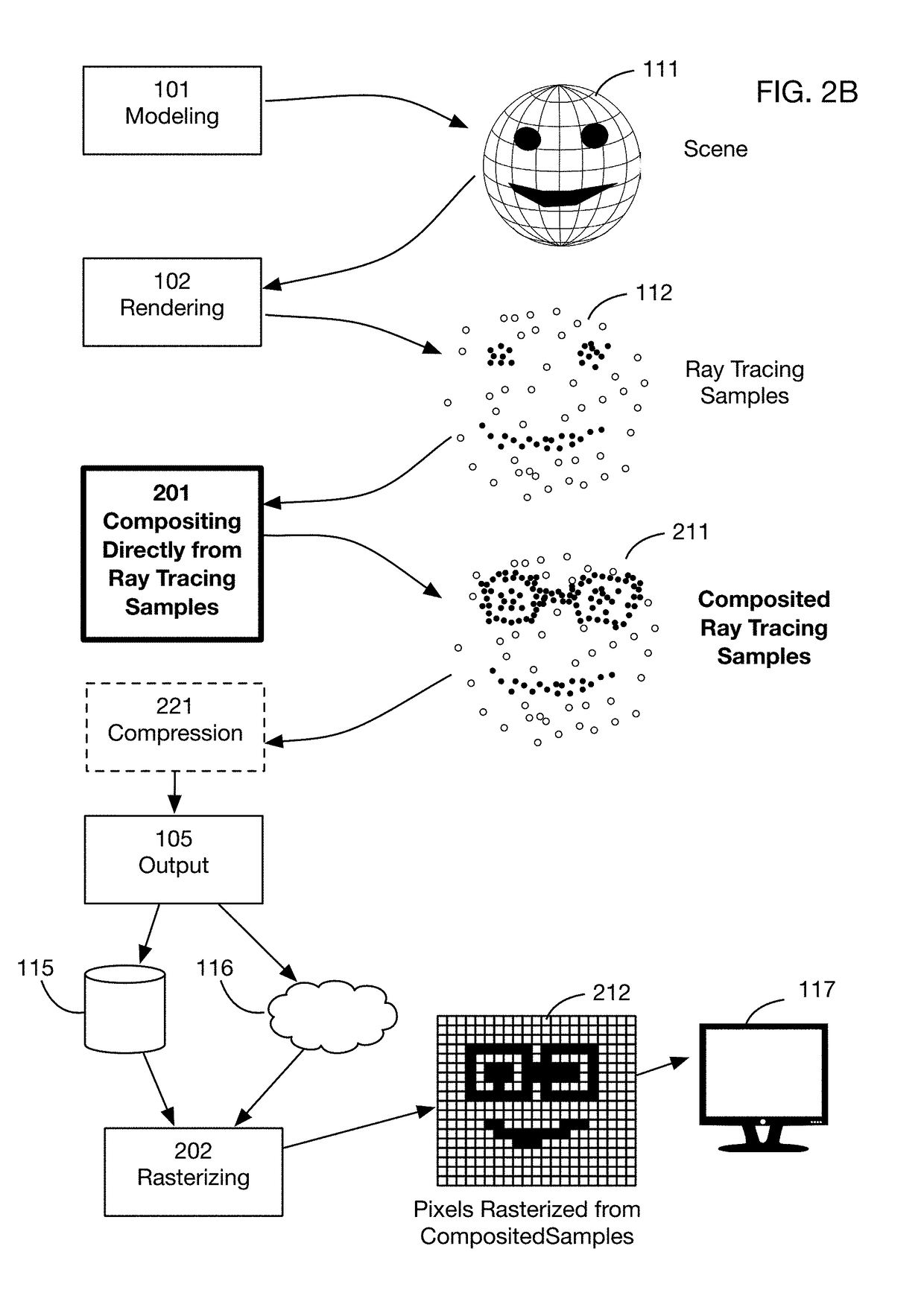
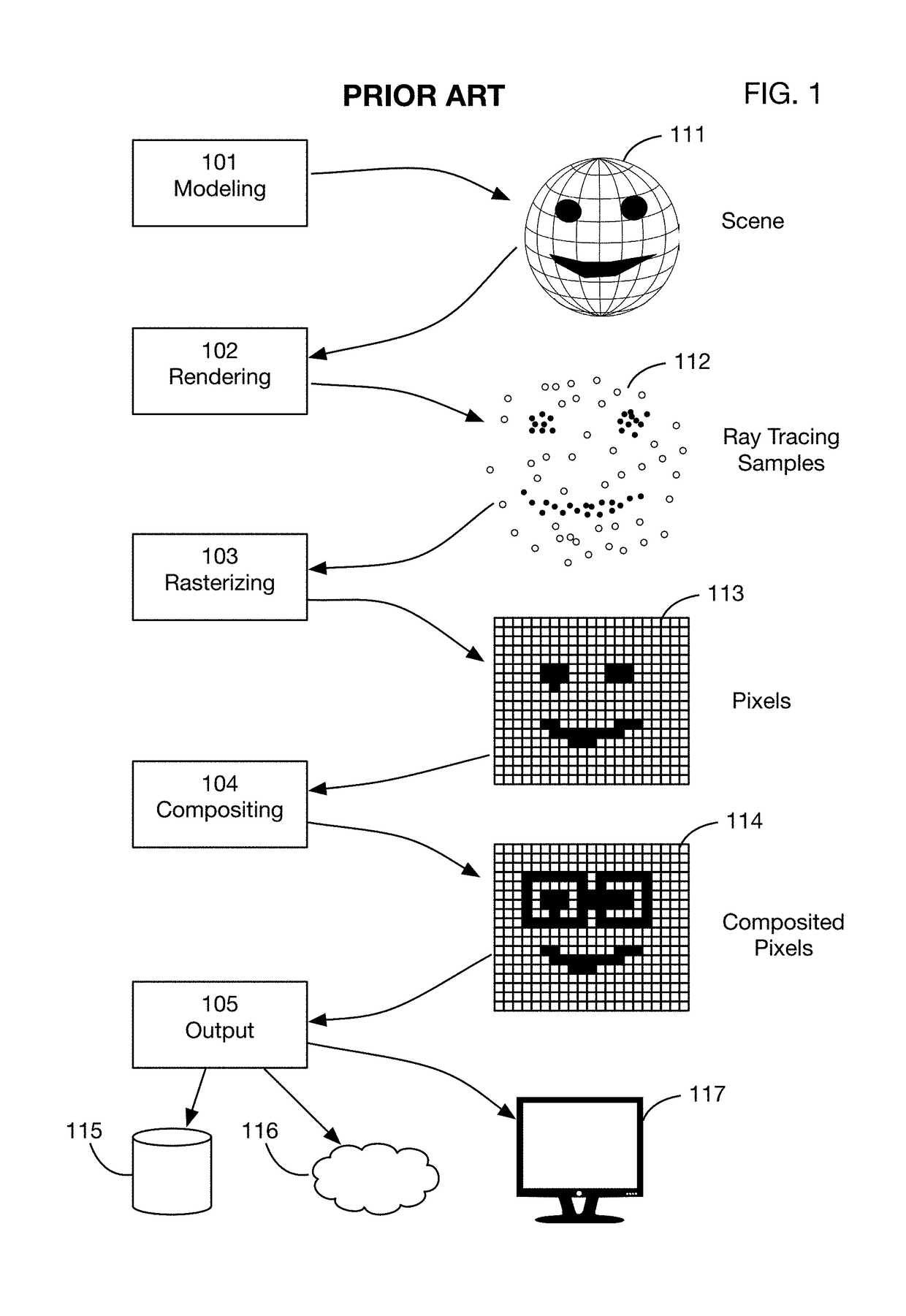
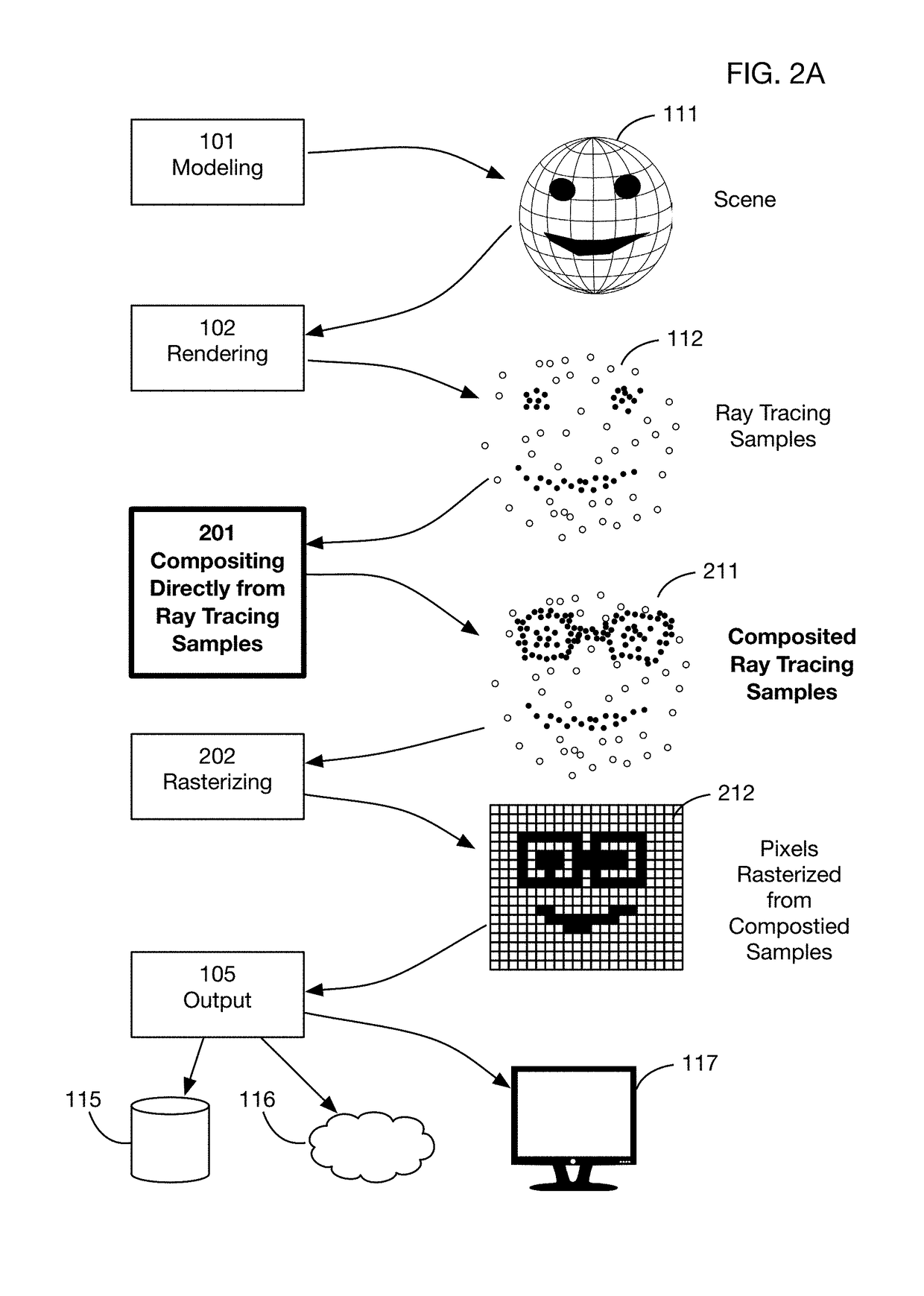
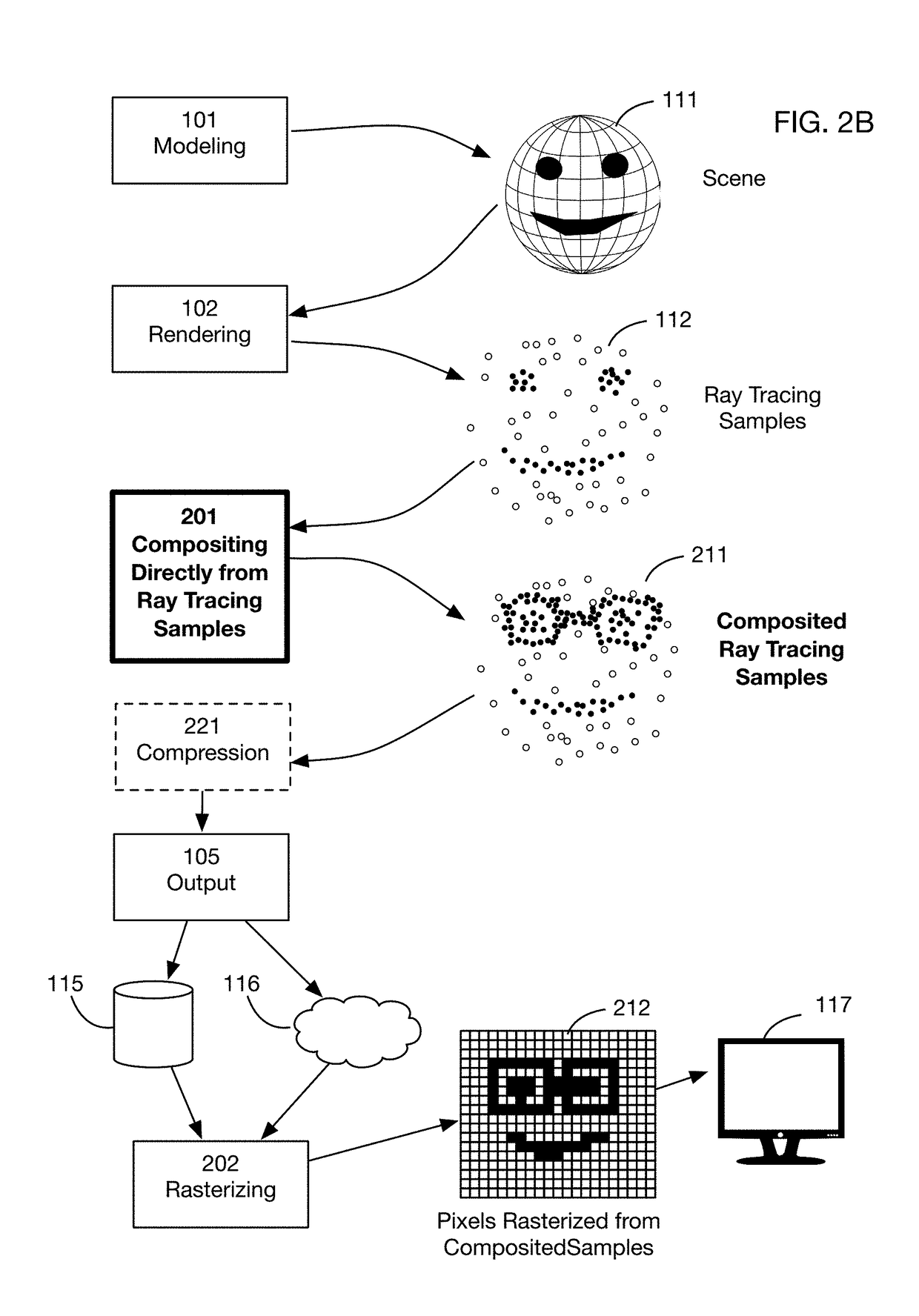
Method of modifying ray tracing samples after rendering and before rasterizing
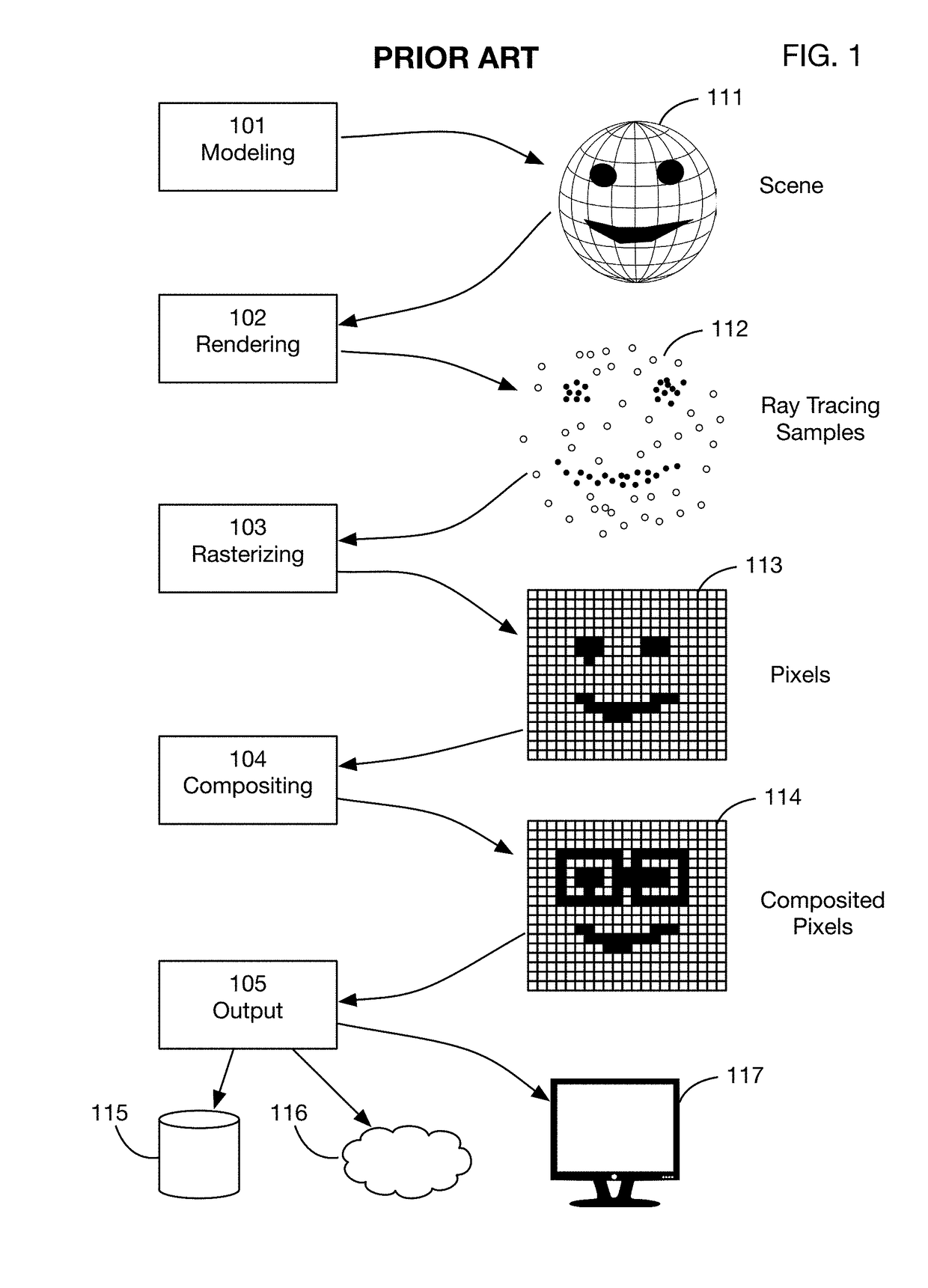
ActiveUS20190066391A1Prevent and mitigate piracyLower potentialKey distribution for secure communicationStill image data indexingImage resolutionUser input
A method of directly modifying ray tracing samples generated by a ray tracing renderer. Modifications to samples may be made after rendering and before rasterizing, in contrast to typical compositing workflows that manipulate pixels of a rasterized image. Modifications may be based on user input. Rasterization may be performed afterwards at any desired resolutions, for example to adapt to different displays. Samples may be tagged with object identities, facilitating object selection without the need for object masks. Pseudo-random ray patterns typically used by renderers may be supported directly. Many operations may be performed directly on samples, including color changes, object repositioning, and merging of samples from different scenes. Secure samples with scrambled ray directions may be modified directly. Modified samples may be compressed for storage or transmission, and may be streamed to receiving devices that rasterize the samples for display, possibly after decompressing or decrypting the received streams.
Owner:GO GHOST LLC
Method of etching structures into an etching body using a plasma
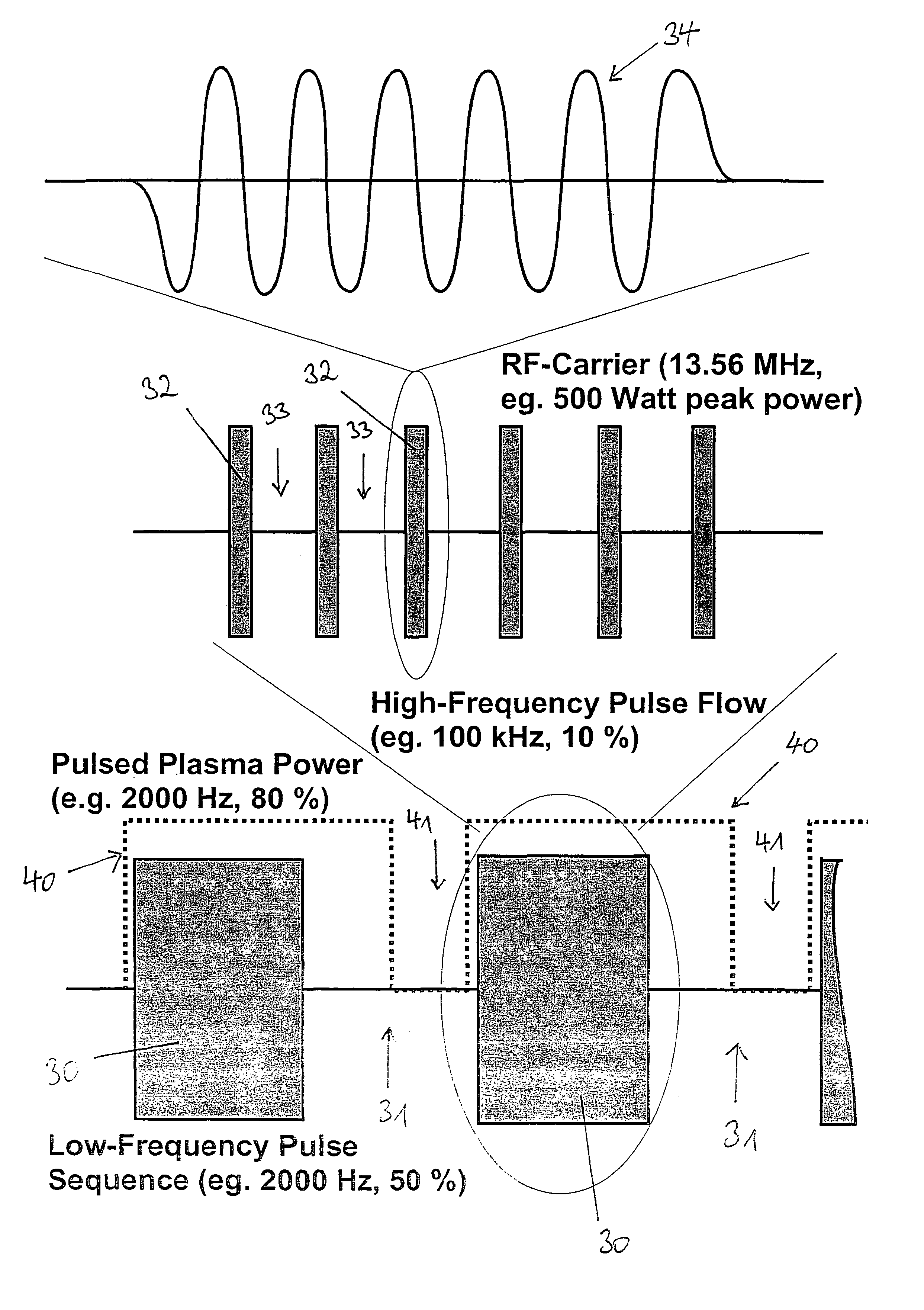
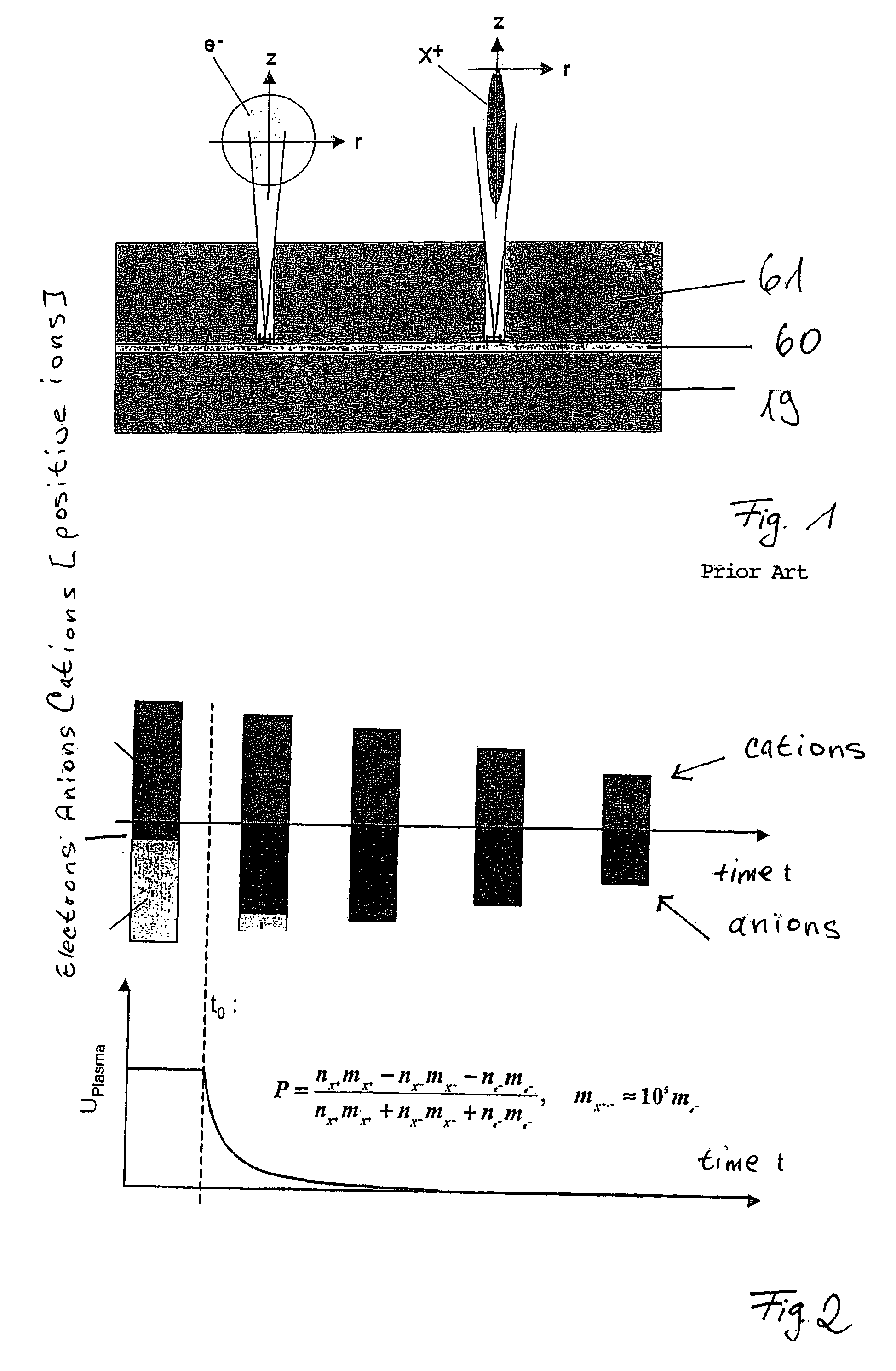
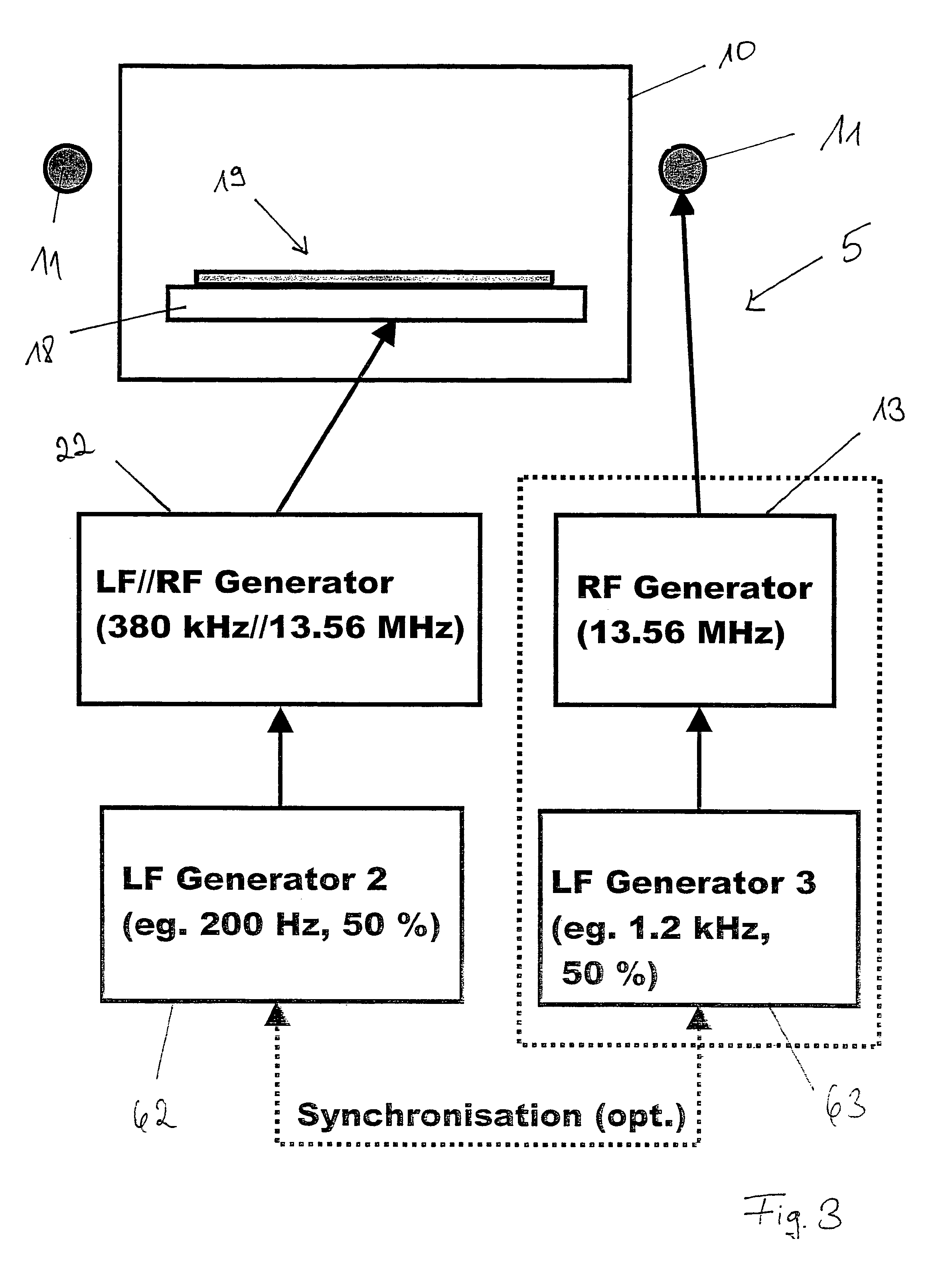
InactiveUS7785486B2Improve stabilityConvenient timeMolten spray coatingElectric discharge tubesEtchingDielectric layer
Additional variants of the method of etching structures into an etching body, in particular recesses in a silicon body that are laterally defined in a precise manner by an etching mask, using a plasma, is described. In addition, the use of this method in the introduction of structures, in particular trenches having a high aspect ratio, into a dielectric layer or a dielectric base body and in a layer of silicon is described, isotropic underetching and / or isotropic, sacrificial-layer etching, in particular using fluorine radicals or a highly oxidizing fluorine compound such as ClF3, being performed after the production of the structures in at least some areas in the case of the layer made of silicon.
Owner:ROBERT BOSCH GMBH
Preparation method for jasmine puer snake gall tea
InactiveCN107173502AHighlight substantiveSignificant progressPre-extraction tea treatmentDigestive systemJasminum tortuosumLost Weight
The invention relates to a preparation method for jasmine puer snake gall tea. The preparation method is characterized by comprising the following steps: (1) taking snake galls from snakes, cleaning, placing in a shade place, shielding light, and naturally drying for later use; (2) taking the dried snake galls, soaking in cold water for 30-40min or soaking in hot water for 4-5min at 100 DEG C, and taking out the snake galls after swelling for later use; (3) preparing jasmine puer tea at the ratio of one snake gall to 10-50g tea leaves for later use; placing the swelling snake galls acquired in the step (2) above the jasmine tea leaves and puncturing, and uniformly dropping the outflow gall into the jasmine puer tea prepared at the appointed ratio in the step (3); uniformly stirring and then standing for 2-3 hours; and adopting a drying machine for drying for 15-20min, packaging in stereoscopic tea bags, sealing, bagging according to the specification quantity of external packing, and putting into a box, thereby acquiring the jasmine puer snake gall tea. The jasmine puer snake gall tea has blackish green appearance, color and luster, has pure and lasting fragrance and has the effects of decreasing lipid, losing weight, reducing pressure, relieving nerves and resisting against aging.
Owner:广西小燕蛇业有限公司
Secure access for B2B applications
PendingUS20210136041A1Reduce attack surfaceReduce operationKey distribution for secure communicationMultiple keys/algorithms usageComputer securityMultiple applications
Owner:ZSCALER INC
Selenium rich paddy rice planting method
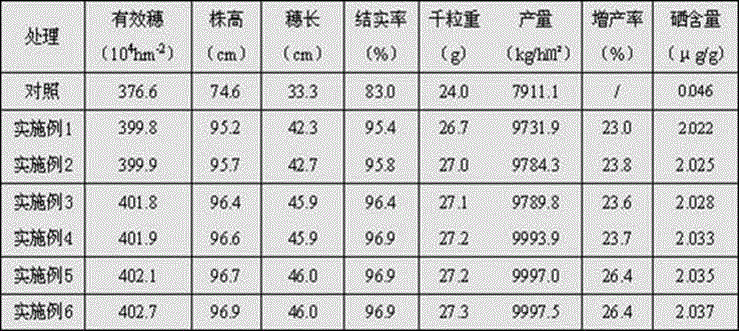
InactiveCN106561369ARapid activation of growth and development performanceResistant to decompositionCalcareous fertilisersMagnesium fertilisersRice plantsTrace element
The invention provides a selenium rich paddy rice planting method. The selenium rich paddy rice planting method includes the steps: seed soaking and processing, transplanting, topdressing, field management, harvesting and other steps. Paddy rice seeds are soaked in selenium liquid, and is fertilized by selenium rich compound fertilizer for four times during the planting process, and the selenium rich compound fertilizer contains rich selenium. The selenium rich paddy rice planting method utilizes the compound fertilizer with rich selenium, high nitrogen content, high-quality humic acid, and organic trace element to improve the fertility of soil and increase growth speed of paddy rice plants, thus improving the utilization rate of fertilizer, reducing loss of fertilizer, and significantly improving paddy rice yields. So that the selenium rich paddy rice obtained through the method has high quality, and is healthy to eat and is nutrient-rich.
Owner:陈海林
Secure rendering system that generates ray tracing samples with obfuscated position data
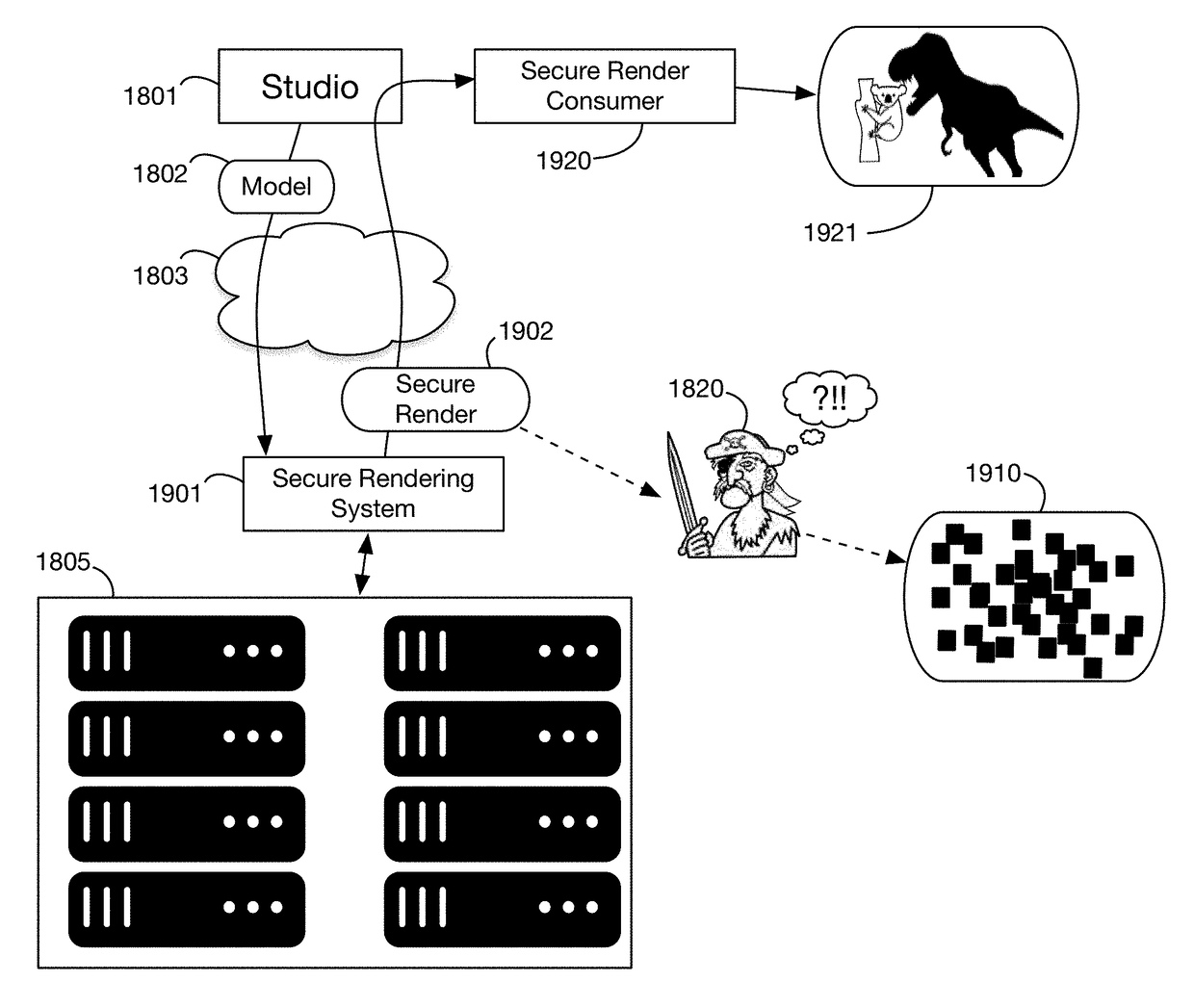
ActiveUS10127392B1Lower potentialEliminate attackPublic key for secure communicationDigital data protectionObfuscationComputer graphics (images)
Secure rendering system that creates ray tracing samples with obfuscated positions, so that images can only be viewed by an authorized consumer able to recover the sample positions. Obfuscation of ray directions is integrated into the rendering process, for example by incorporating encryption into a lens shader. The rendering system never stores or transmits an image without obfuscating positions, so even the rendering system cannot see the image it is rendering. Embodiments may use public key cryptography, so that encryption of sample positions is done with a public key, and only the owner of the secret private key can view the rendered image. Since keys are asymmetric, the rendering system cannot decrypt the obfuscated samples. Piracy of rendered images is therefore mitigated. Some compositing operations may be performed on the secure rendering output prior to decrypting sample positions; for example, colors may be modified globally or for selected objects.
Owner:GO GHOST LLC
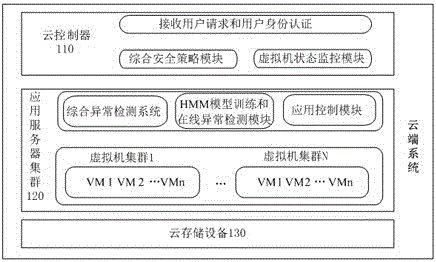
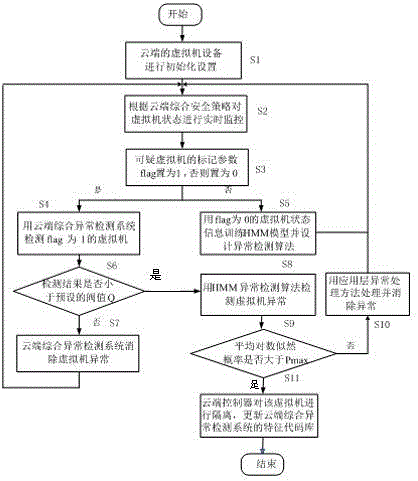
Abnormity detection and processing method of cloud virtual environment
The invention discloses an application layer abnormity detection and processing method of a cloud virtual environment. The method comprises that a cloud controller detects states of virtual machines in real time; if a virtual machine is an abnormal virtual machine, a comprehensive abnormity detection system carries out comprehensive detection to the abnormal virtual machine; if the comprehensive abnormity detection system judges that the comprehensive detection result value of the abnormal virtual machine is less than a preset threshold value Q, the cloud controller calculates the average logarithm likelihood probability value of the abnormity detection of the abnormal virtual machine; if the average logarithm likelihood probability value is more than a Pmax, the abnormal virtual machine is a high risk virtual machine; the abnormal virtual machine is isolated; if the average logarithm likelihood probability value is less than the Pmax, the abnormal virtual machine is a low risk virtual machine; and the abnormal behaviors of the abnormal virtual machine are eliminated. According to the method, the abnormity detection reliability of the cloud virtual machine is ensured; through adoption of multiple detection mechanisms, the abnormal virtual machine can be detected more reliably; false detection will not be carried out to certain normal virtual machines; and the service of the cloud tenants of the normal virtual machines will not be influenced by the false detection.
Owner:SHANGHAI MARITIME UNIVERSITY +1
Non-rasterized image streaming system that uses ray tracing samples
ActiveUS20200159936A1Lower potentialEliminate attackMultiple keys/algorithms usagePublic key for secure communicationPhysicsShader
Secure rendering system that creates ray tracing samples with obfuscated positions, so that images can only be viewed by an authorized consumer able to recover the sample positions. Obfuscation of ray directions is integrated into the rendering process, for example by incorporating encryption into a lens shader. The rendering system never stores or transmits an image without obfuscating positions, so even the rendering system cannot see the image it is rendering. Embodiments may use public key cryptography, so that encryption of sample positions is done with a public key, and only the owner of the secret private key can view the rendered image. Since keys are asymmetric, the rendering system cannot decrypt the obfuscated samples. Piracy of rendered images is therefore mitigated. Some compositing operations may be performed on the secure rendering output prior to decrypting sample positions; for example, colors may be modified globally or for selected objects.
Owner:GO GHOST LLC
Intelligent system infrastructure for financial data computation, report remittance and funds transfer over an interactive communications network
InactiveUS20050119953A1Eliminate eavesdroppingEliminate connection hijackingComplete banking machinesFinanceExtensibilityProtection system
This disclosure relates to a specific, illustrative multilayer architecture for a program controlled system for providing services relating to financial data computation, report remittance and funds transfer services over an interactive communications network. The system comprises a subscriber server for hosting a virtual portal having at least one application for providing e-content to end users, the application including a network browser for accessing, displaying and transmitting data over the network. A first service provider server allows a system administrator to access the system remotely. A first security system for protecting the system from entry of unwanted data during data transfer over the network between the subscriber and service provider servers and the interactive communications network level. Also provided are plurality of primary servers including a primary network server, a primary tax computation server, a primary report generation server and a primary tax remittance server. The network server receives a tax computation transaction request from the subscriber server, transmits the request to the primary tax computation server, and returns data processed by the tax computation server to the subscriber server. In addition, the system has a plurality of secondary servers redundant to the first. The secondary servers include a secondary network server, a secondary tax computation server, a secondary report generation server and a secondary tax remittance server. A load balancing and scalability system is utilized for load directing, routing and switching functions during data transfer from utilization of at least one function at one of the primary servers to a corresponding function at a secondary server for optimum management of system resources.
Owner:DANG HONG M +3
Network attack path prediction method and device and security management platform
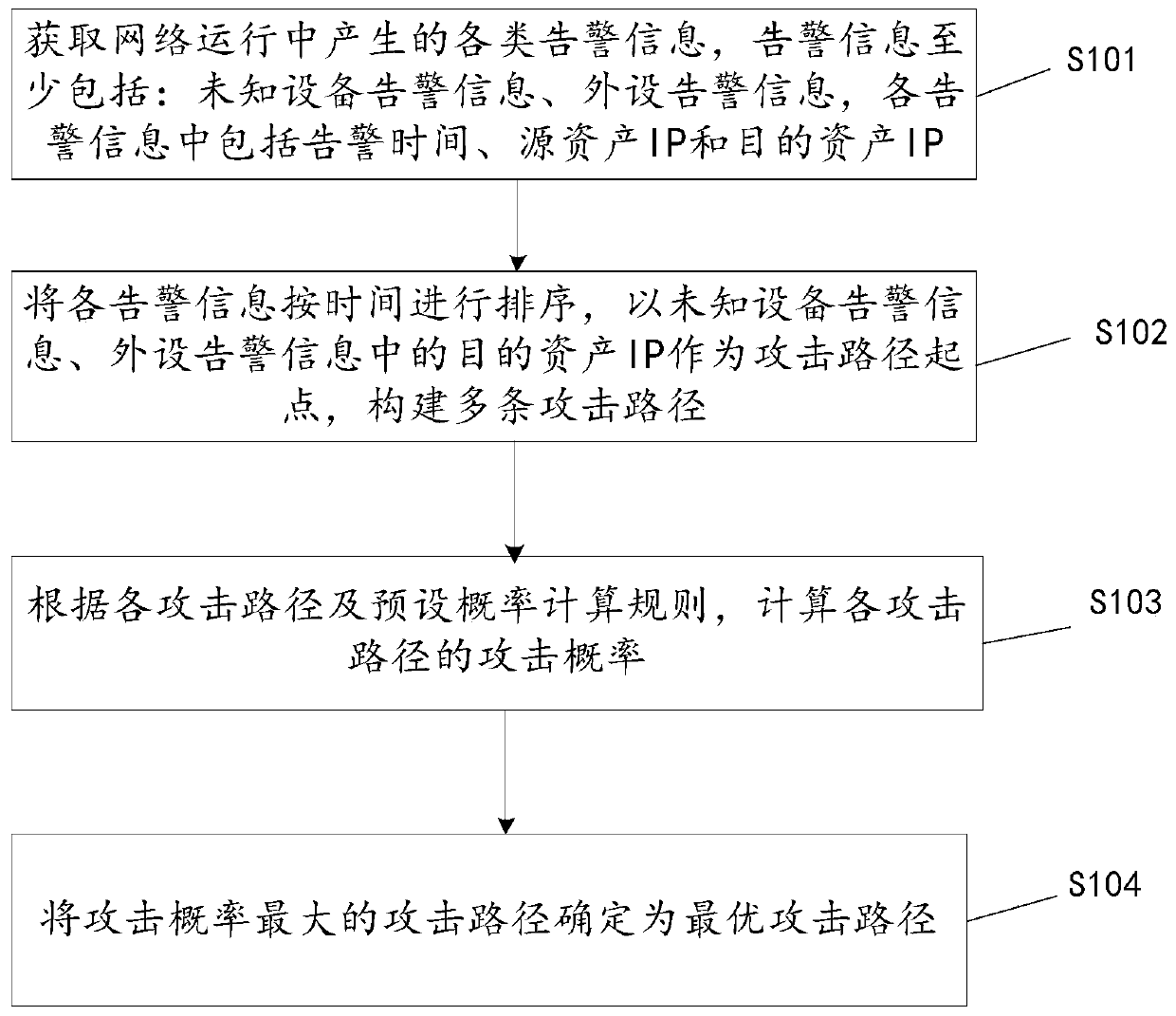
The invention discloses a network attack path prediction method and device and a security management platform, and the method comprises the steps: obtaining various types of alarm information generated in the operation of a network, the alarm information at least comprises unknown equipment alarm information and peripheral alarm information, and each piece of alarm information comprises alarm time, a source asset IP and a target asset IP; sorting the alarm information according to time, and constructing a plurality of attack paths by taking target asset IPs in the unknown equipment alarm information and the peripheral alarm information as attack path starting points; calculating the attack probability of each attack path according to each attack path and a preset probability calculation rule; and determining the attack path with the maximum attack probability as the optimal attack path. According to the optimal attack path determined by the method, an attack source, an attack destination, attacked assets and equipment with potential safety hazards can be clearly checked, so that all assets in the attack process can be specifically analyzed, and the assets which may be attacked aresubjected to safety protection.
Owner:北京威努特技术有限公司
Planting method of rice rich in selenium and chromium
InactiveCN106565368AImprove absorption ratePromote absorptionCalcareous fertilisersMagnesium fertilisersTrace elementNitrogen
The invention provides a planting method of rice rich in selenium and chromium. The planting method comprises the following steps of: soaking seeds, transplanting rice seedlings, applying a fertilizer, carrying out field management, harvesting and the like. The rice seeds are soaked by selenium and chromium solutions, the compound fertilizer which is rich in selenium and chromium is applied for four times in the planting process, and the compound fertilizer which is rich in selenium and chromium contains rich selenium and chromium elements. According to the planting method of the rice rich in selenium and chromium, the compound fertilizer which is rich in the selenium element and high in nitrogen content and comprises high-quality humic acid and organic trace elements is utilized to improve soil fertility and promote the rapid growth of rice plants, the utilizing rate of the fertilizer is increased, fertilizer losses are reduced, rice yield is obviously increased, and the rice is high in quality, healthy to eat and rich in nutrients.
Owner:陈海林
Big data security monitoring system
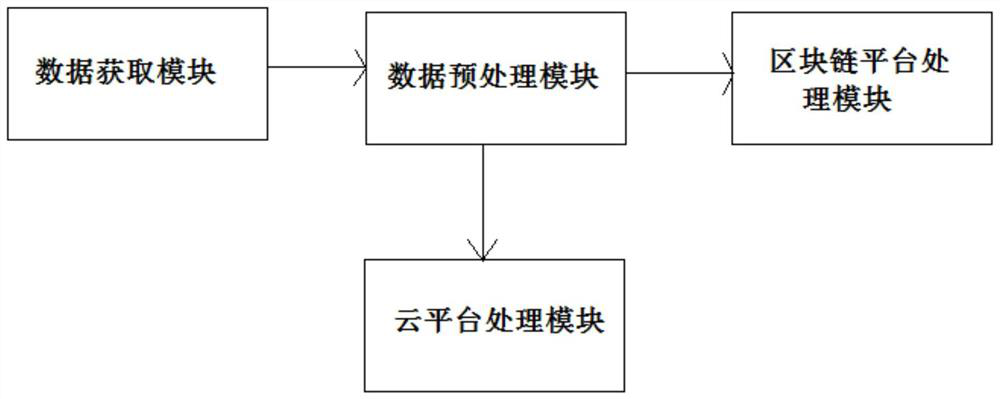
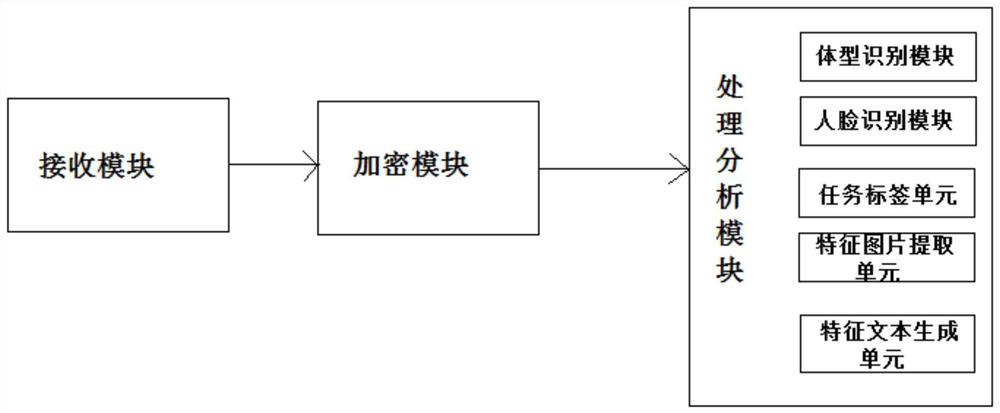
PendingCN111858763AHigh processing efficiency and safety requirementsGuaranteed processing efficiencyDatabase distribution/replicationDigital data protectionMonitoring dataBig data security
The invention discloses a big data security and protection monitoring system, which comprises: a data acquisition module used for acquiring security and protection monitoring data including video monitoring data, audio monitoring data and monitoring position positioning data; a data preprocessing module which is used for preprocessing the obtained security and protection monitoring data, removingabnormal bad point data existing in the security monitoring original data, smoothing or fitting the security and protection monitoring data, and uploading the obtained security and protection data toa cloud platform processing module and a block chain platform processing module through a gateway; a block chain platform processing module which is used for encrypting and analyzing the security data; and a cloud platform processing module which is used for carrying out distributed storage on the security and protection data through a docker mirror image technology and forming mirror image persistent storage in a distributed file system of a docker warehouse. The block chain and docker mirror image technology are combined, and the requirements for high processing efficiency and safety are metat the same time.
Owner:李雯雯
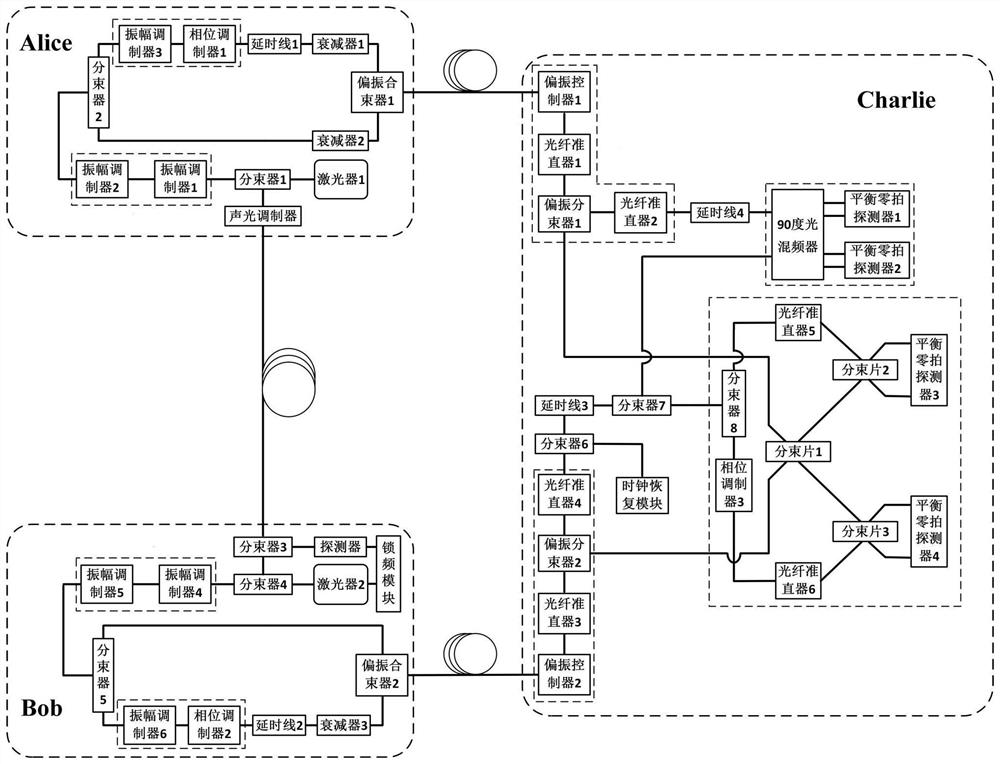
Continuous variable measurement equipment independent quantum key distribution system and phase compensation method
ActiveCN114337847AEliminate attackReliable implementationKey distribution for secure communicationPhotonic quantum communicationSoftware engineeringPolarization multiplexed
The invention belongs to the technical field of quantum communication, and particularly relates to a continuous variable measurement equipment independent quantum key distribution system and a phase compensation method. In order to eliminate all side channel attacks on a measurement end in an actual continuous variable quantum key distribution system, the system comprises two sending ends Alice and Bob and a receiving end Charlie. The transmitting end mainly comprises a laser module, an optical phase locking module, a chopped pulse module, a signal light modulation module and a time division multiplexing and polarization multiplexing module. And the receiving end mainly comprises a polarization demultiplexing module, a clock recovery module, an optical delay module, a 90-degree optical mixer module and a continuous variable Bell state measurement module. The phase compensation method comprises four parts of optical phase locking, slow drift phase estimation, real-time phase feedback and orthogonal component remapping, and continuous variable Bell state measurement of a long-distance independent quantum state can be realized.
Owner:SHANXI UNIV
Secure rendering system that generates ray tracing samples with obfuscated position data
ActiveUS20190088034A1Lower potentialEliminate attackKey distribution for secure communicationStill image data indexingObfuscationComputer graphics (images)
Secure rendering system that creates ray tracing samples with obfuscated positions, so that images can only be viewed by an authorized consumer able to recover the sample positions. Obfuscation of ray directions is integrated into the rendering process, for example by incorporating encryption into a lens shader. The rendering system never stores or transmits an image without obfuscating positions, so even the rendering system cannot see the image it is rendering. Embodiments may use public key cryptography, so that encryption of sample positions is done with a public key, and only the owner of the secret private key can view the rendered image. Since keys are asymmetric, the rendering system cannot decrypt the obfuscated samples. Piracy of rendered images is therefore mitigated. Some compositing operations may be performed on the secure rendering output prior to decrypting sample positions; for example, colors may be modified globally or for selected objects.
Owner:GO GHOST LLC
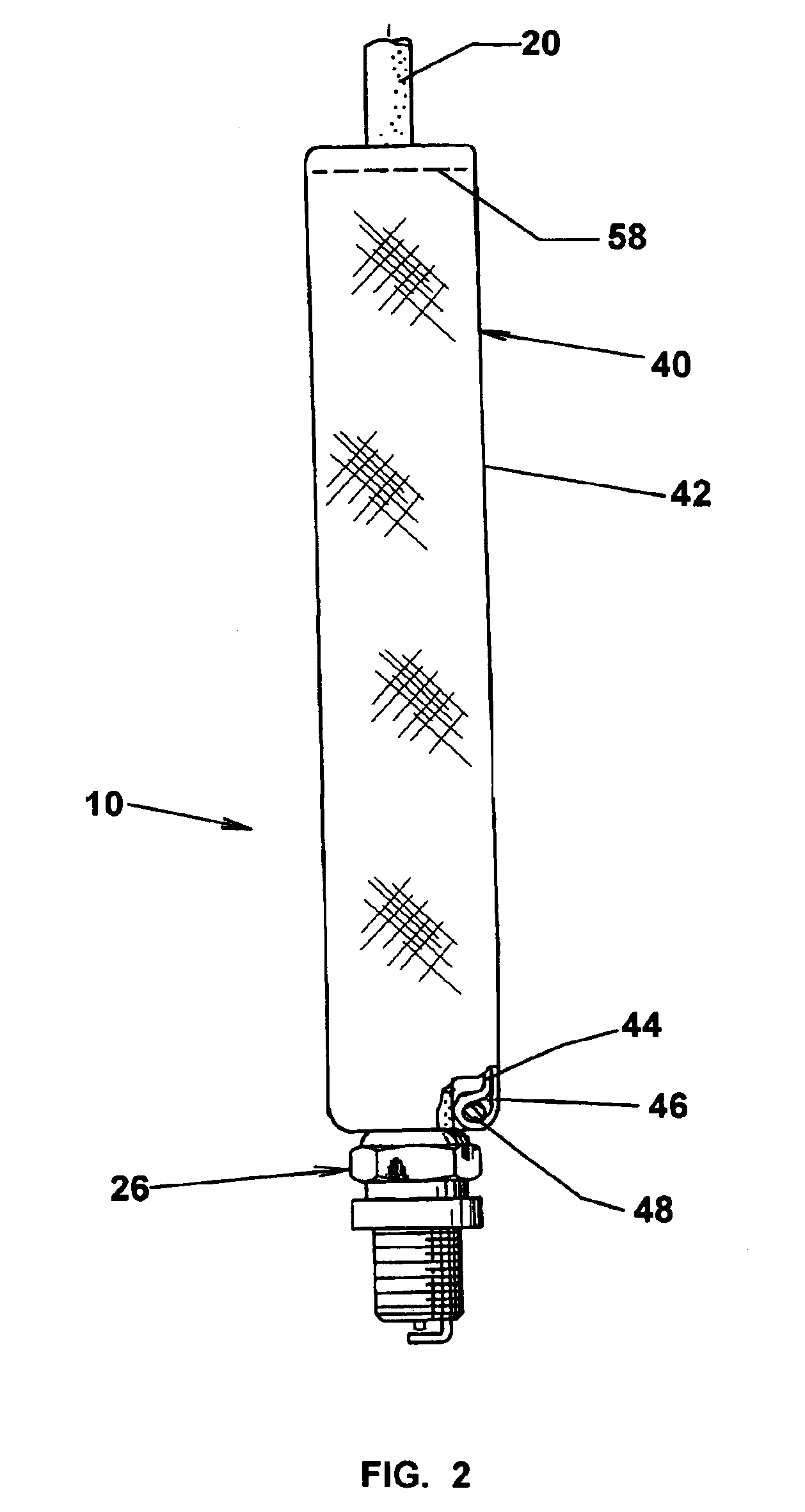
Cover for spark plug, ignition wire and boot
InactiveUS7055482B1Increase thermal resistanceSimple to installSparking plugsGenerator generated ignition energyEngineeringSpark plug
A cover for the spark plug boot and an ignition wire connected with spark plug of an engine includes a woven fiberglass sheath surrounding the spark plug insulator and spark plug boot and having an entrance cuff formed with an inner end flap stitched to form a pocket for capturing the end strands of the sheath, forming a four plug end construction that maintains the circularity of the opening and reduces the harmonic vibration in the sheath during engine operation.
Owner:DELFINGEN FR ANTEUIL
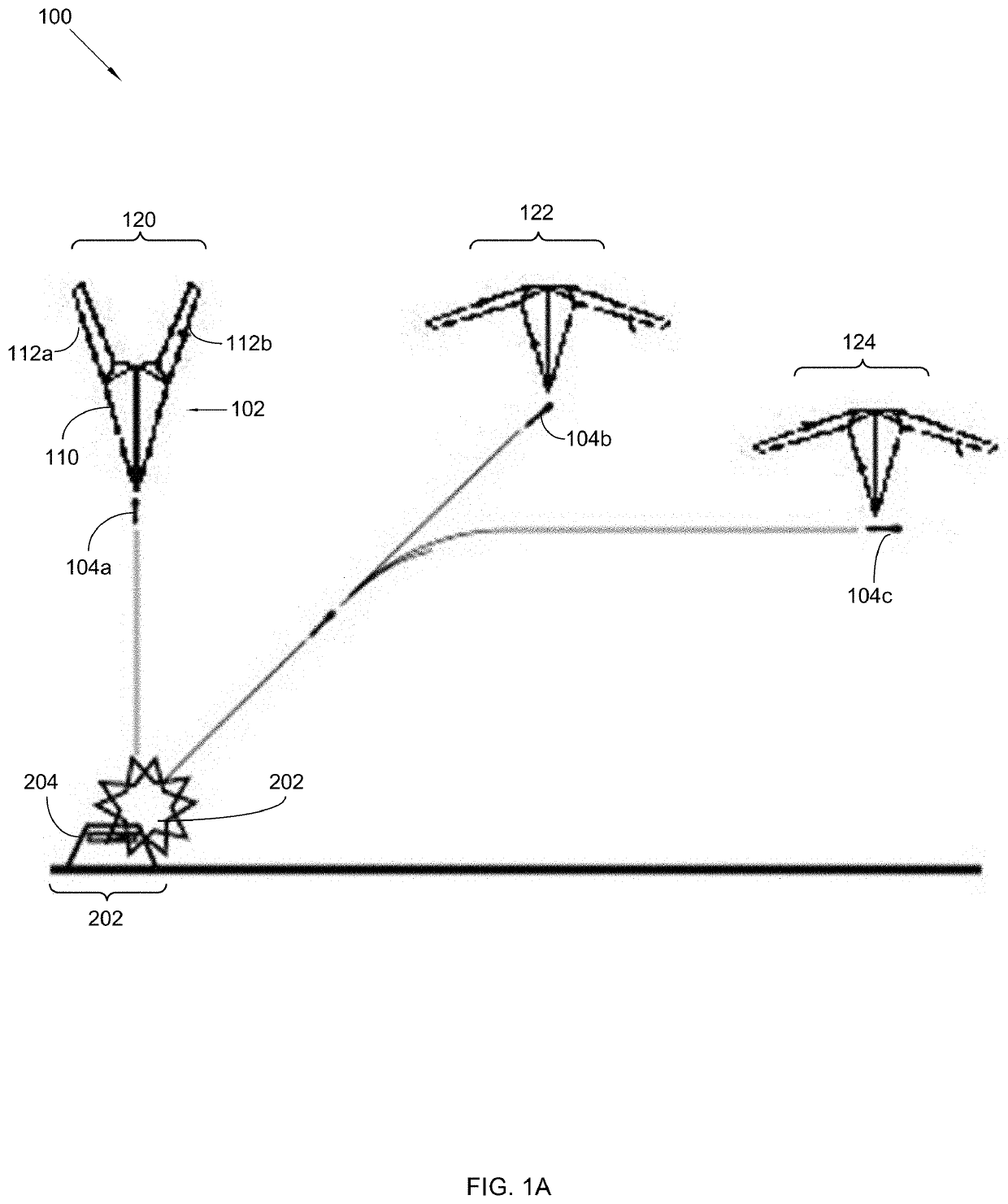
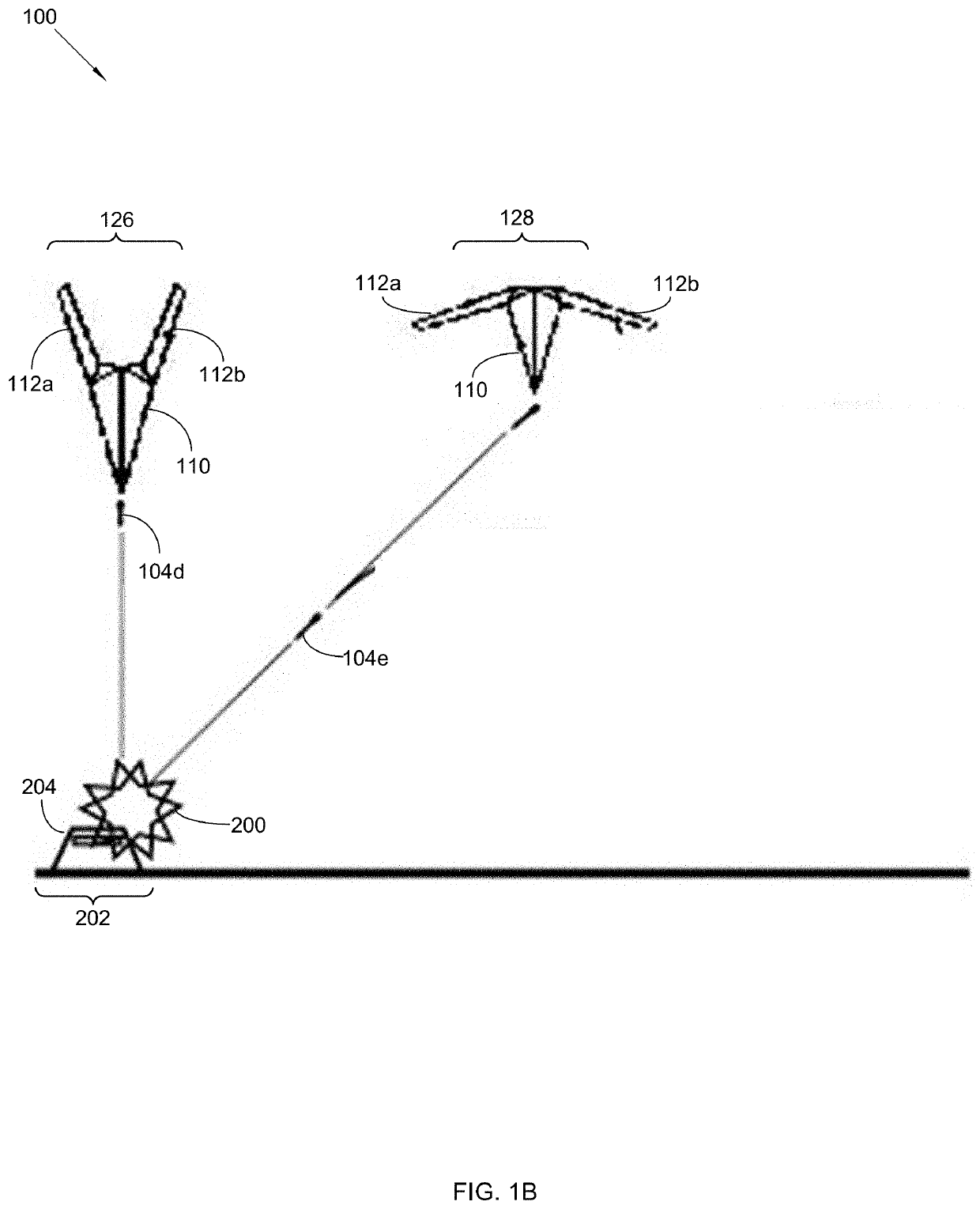
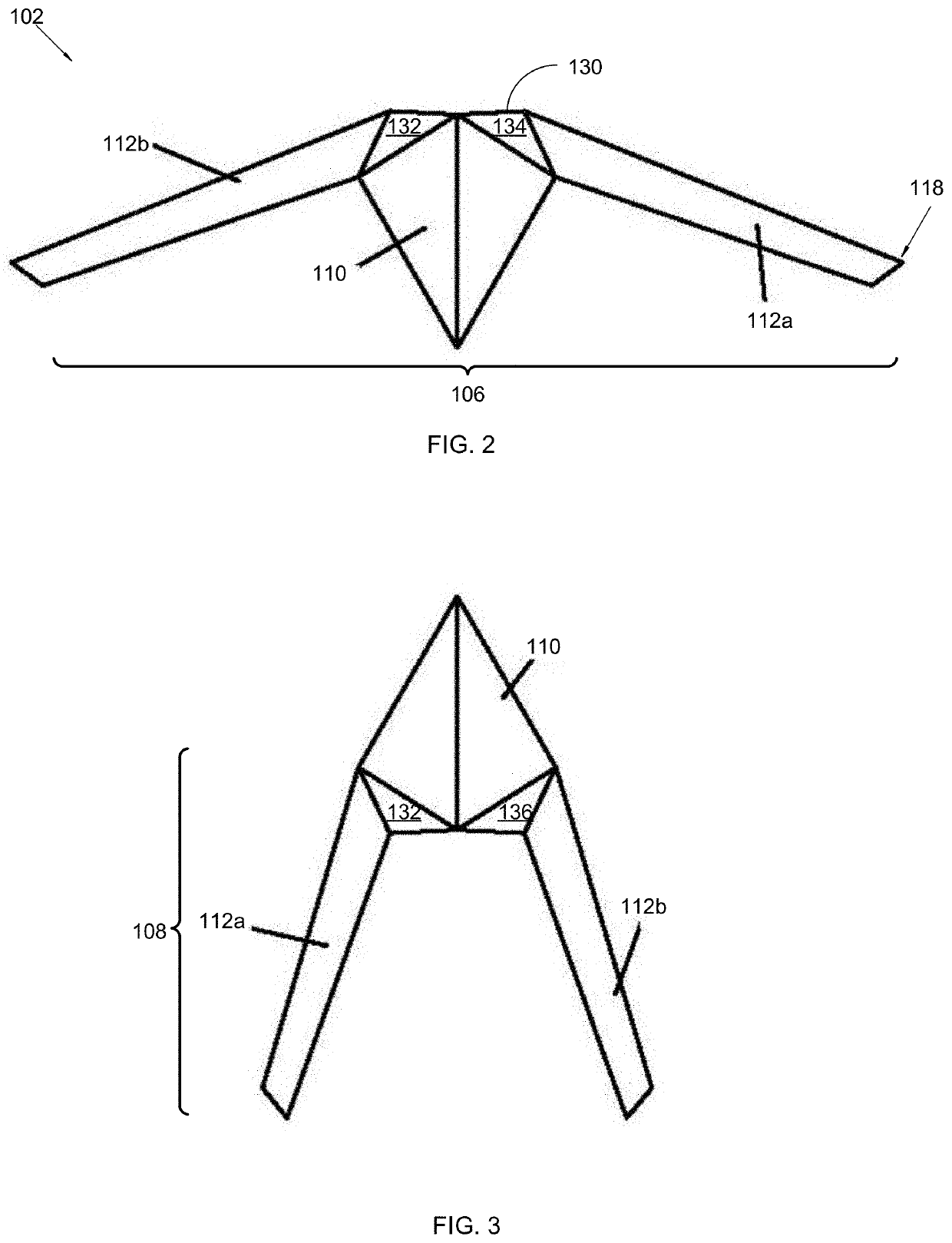
Airborne space Anti-missile system
InactiveUS20190359330A1Efficient deliveryReduce air resistanceDefence devicesWing adjustmentsPlasma jetUltra high speed
An airborne space anti-missile system provides an offensive anti-missile system that provides a supersonic jet flying in space at 10 times the speed of ultra-high speed jet to deliver air-to-surface missiles towards launch site of an attacking missile. The launching missile is targeted prior to launching or during flight. The supersonic jet comprises: a nuclear plasma jet engine operational in thermosphere, and a stamping jet fusion vector engine or anti-material vector engine for flying in lower atmospheres, no vertical tail and rudder, a pointed wing structure; a fuselage having a length of 60 meters and height of 15 meters, a variable swept wing configuration having a 100° range of wing positions, including a forward position where the wing is disposed forwardly, and wingspan is 200 meters from the fuselage, and a full rearward swept position where wingspan is 60 meters from the fuselage; and electromagnetic space for stealth operations.
Owner:SUPERSPACE S&T MFG CO LTD
Composite used for relieving alcoholic intoxication and protecting liver and preparation method and application thereof
ActiveCN101897746AFast metabolismReduce alcoholic liver damageNervous disorderDigestive systemAlcoholic liver damageTraditional medicine
The invention discloses a composite used for relieving alcoholic intoxication and protecting a liver and a preparation method and application thereof. The composite of the invention comprises radix pseudo-ginseng and rosa roxbughii tratt cacti, and can effectively eliminate the attack to large biological molecules caused by free radicals generated due to overdrinking, effectively relieve alcoholic intoxication and prevent alcoholic liver damage, thereby realizing the efficacies of relieving the alcoholic intoxication and protecting the liver, and embodying better component synergism.
Owner:SHANGHAI INST OF BIOLOGICAL SCI CHINESE ACAD OF SCI
Feed promoting growth of cyprinus carpio and preparation method thereof
InactiveCN107114607AAdapt to growth needsPromote growthFood processingClimate change adaptationDiseaseAnti stress
The present invention provides a feed promoting growth of cyprinus carpio and a preparation method thereof, and belongs to the technical field of feed preparations. The feed comprises the following raw materials in parts by weight: 20-30 parts of selenium-enriched fly maggot powder, 8-12 parts of fish meal, 15-20 parts of soybean cake, 5-8 parts of brewer's grains, 2-3 parts of fermented tea seed cake meal, 0.06-0.08 part of vitamin E, 0.02-0.03 part of vitamin C, 0.1-0.2 part of calcium dihydrogen phosphate, 0.05-0.08 part of beta-carotene, 1-2 parts of grape seeds, 3-5 parts of oxytropis myriophylla herbs, 2-4 parts of bidens pilosa, 2-4 parts of hippuris vulgaris, 1-2 parts of herba houttuyniae, 1-2 parts of an attractant and 1-2 parts of a binder. The feed is scientific and reasonable in formula, and stable in performances in water, does not affect aquaculture water quality, can improve an anti-stress ability of the cyprinus carpio, reduces incidence of diseases, can promote growth of the cyprinus carpio, and increases growth rates.
Owner:GUANGXI AGRI VOCATIONAL COLLEGE
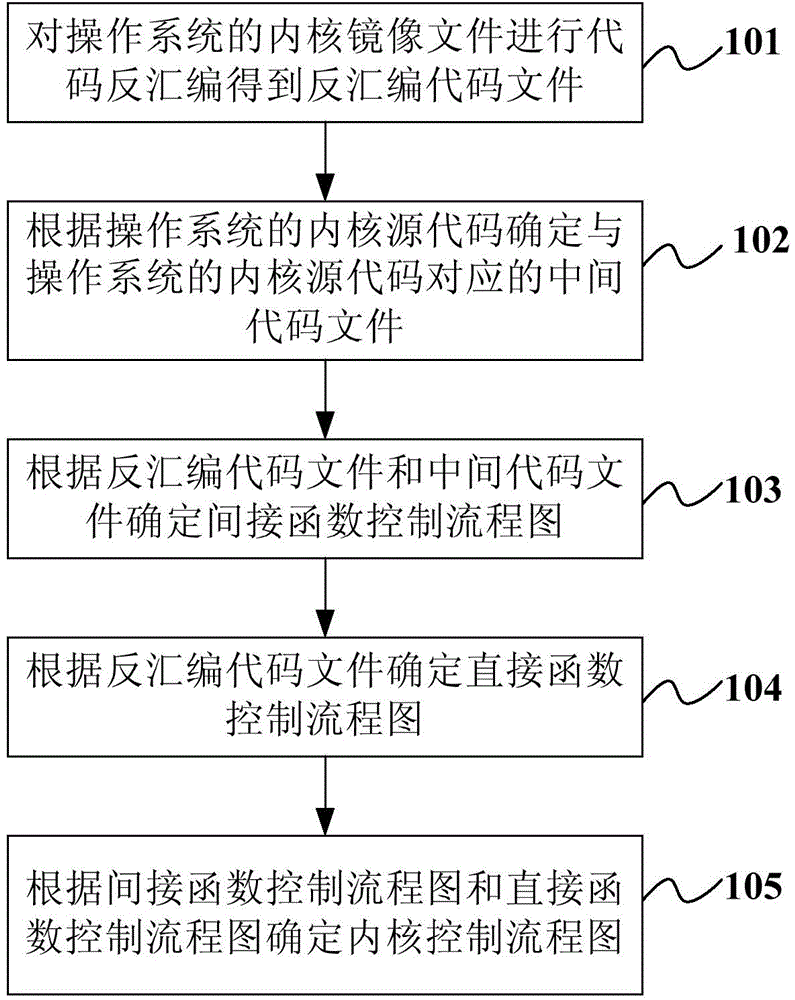
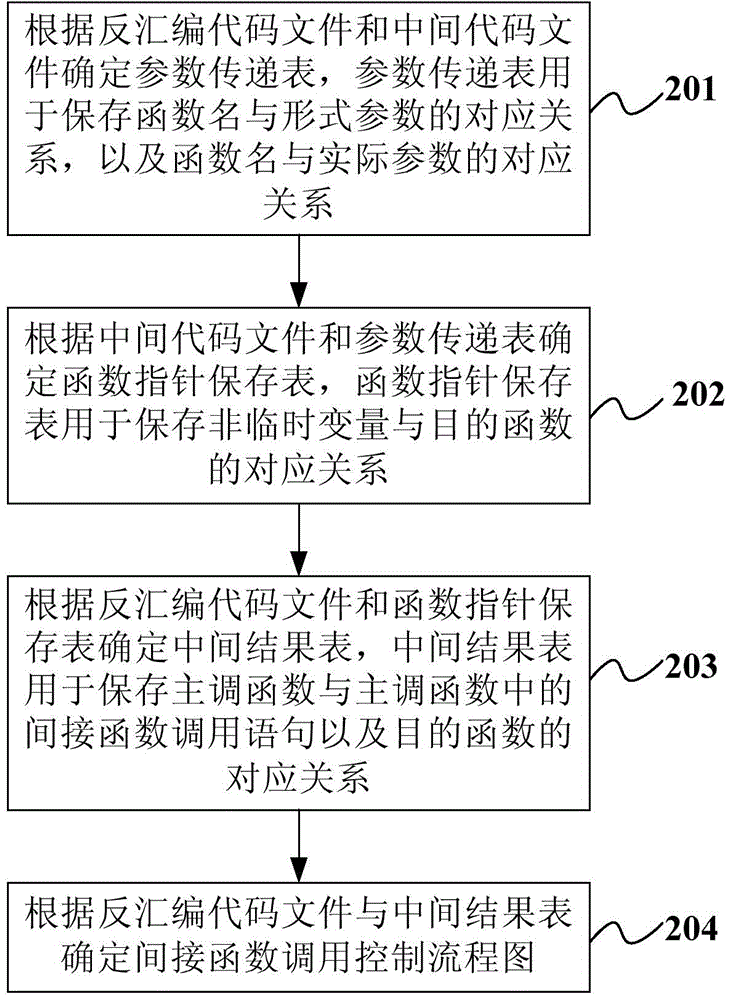
Method and apparatus for obtaining kernel control flow chart of operating system
ActiveCN105988811AImprove accuracyEliminate attackSpecific program execution arrangementsControl flowOperational system
The invention provides a method and an apparatus for obtaining a kernel control flow chart of an operating system. The method comprises the steps of performing code disassembling on the kernel mirror image file of the operating system to obtain a disassembled code file; determining an intermediate code file corresponding to the kernel source code of the operating system according to the kernel source code of the operating system; determining an indirect function control flow chart according to the disassembled code file and the intermediate code file; determining a direct function control flow chart according to the disassembled code file; and determining the kernel control flow chart according to the indirect function control flow chart and the direct function control flow chart. By adoption of the technical scheme provided by the invention, the accuracy of the control flow chart can be improved so as to eliminate attack to a computer.
Owner:HUAWEI TECH CO LTD
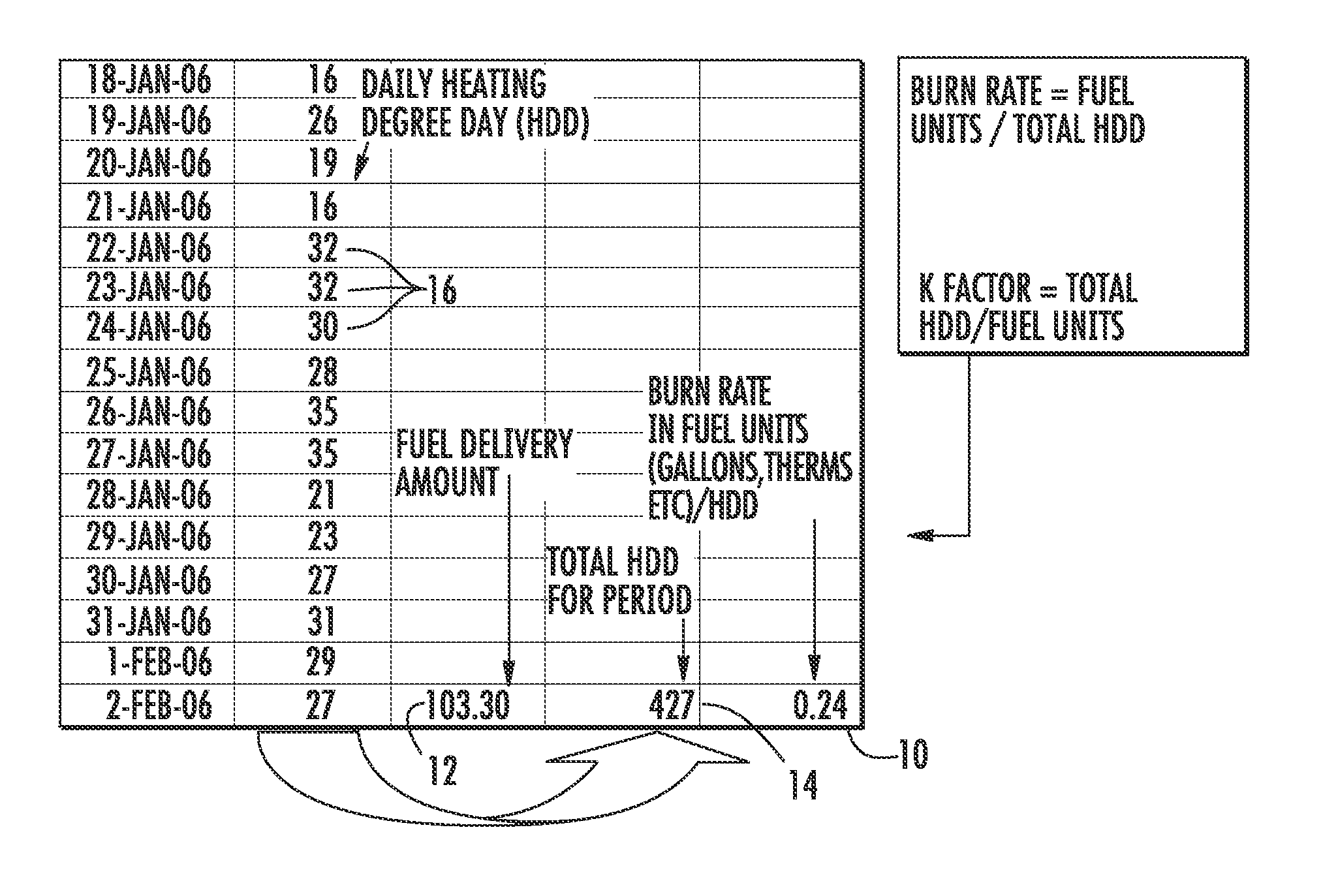
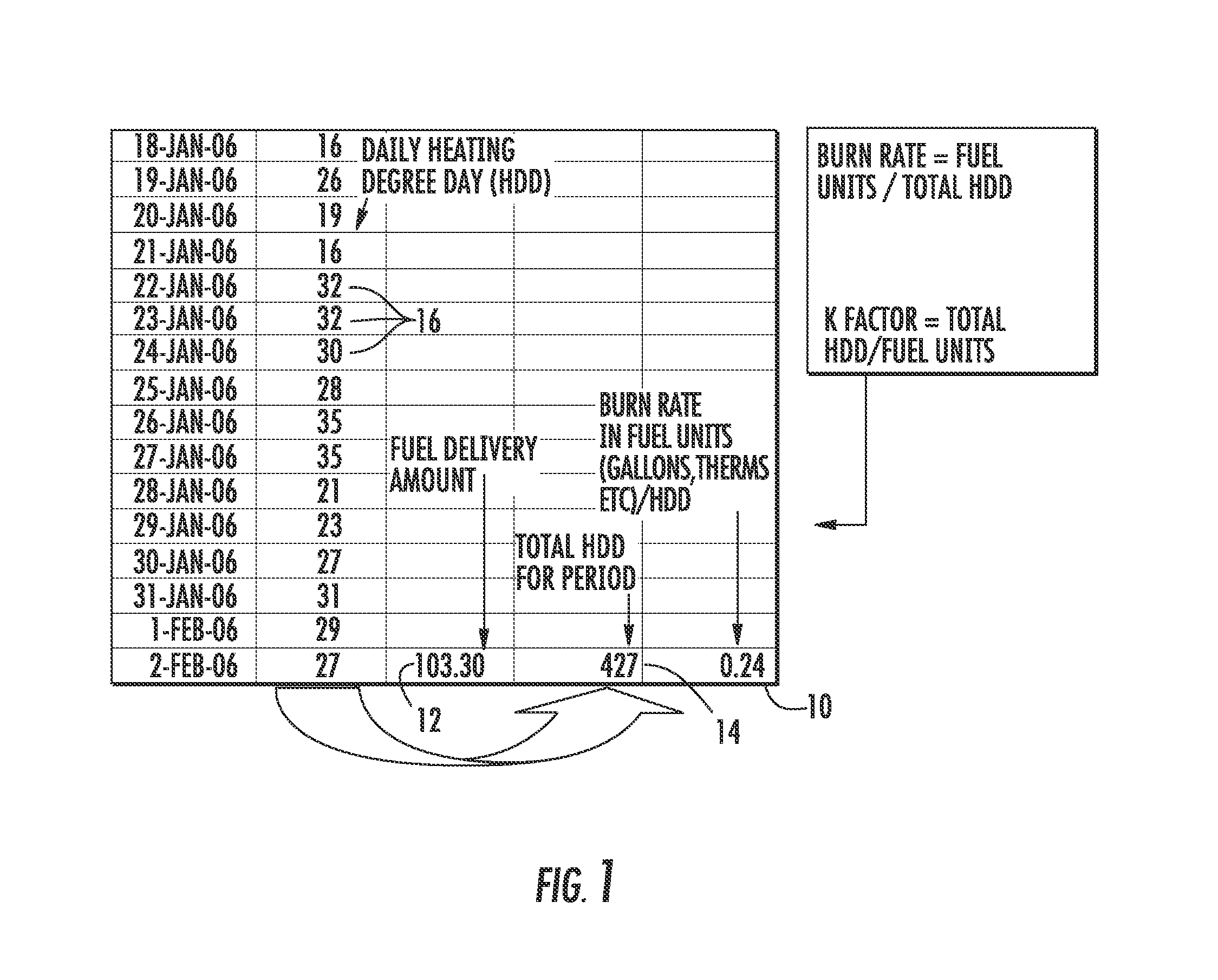
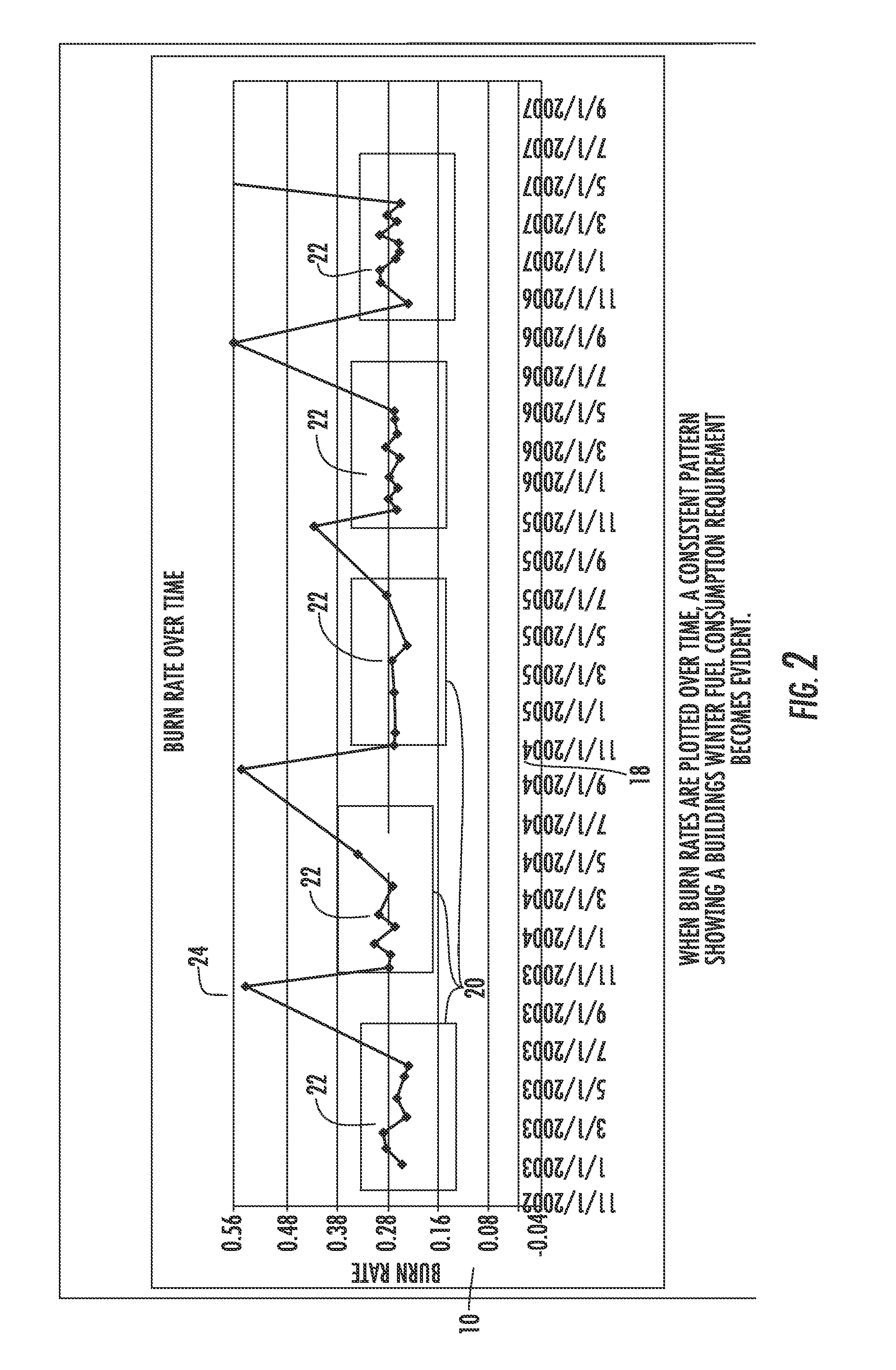
Method and system for determining residential fuel usage
ActiveUS20100017149A1Highly accurate pictureEliminate attackFlow propertiesVolume/mass flow measurementEngineeringPilot light
A method and system that accurately predicts fuel consumption rates in a residential structure is provided. The present invention more accurately determines the amount of fuel required to maintain a residential structure at a consistent temperature, thereby allowing identification of various system anomalies that may occur over time. Further, the method and system accounts for a number of fuel usage variables such as pilot light and domestic hot water usage in a manner that allows improved accuracy in determining the amount of fuel required to maintain a residential structure at a consistent temperature, thereby allowing identification of various system anomalies that may occur over time.
Owner:CERTUSE JOHN
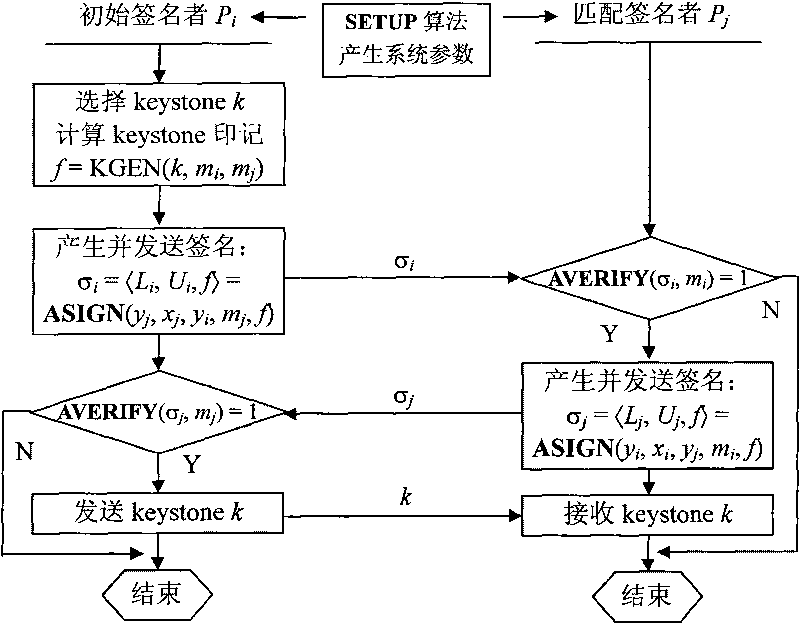
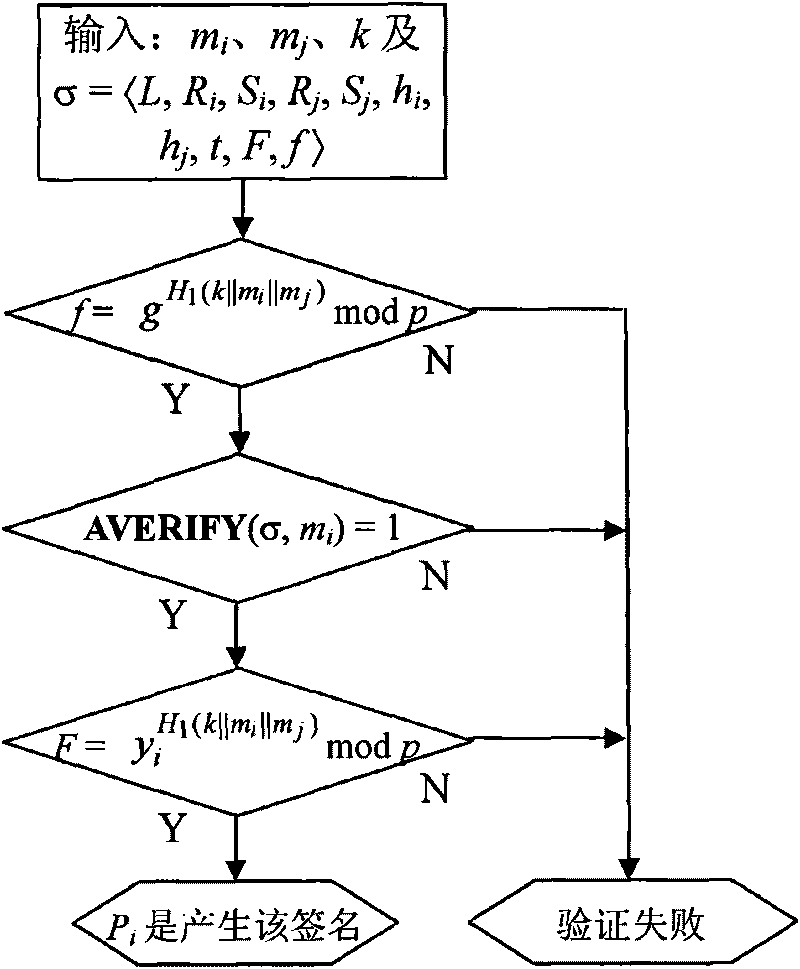
Concurrence signature method with explicitly revocable fuzziness
InactiveCN101729258AAbolition of ambiguityHas the nature of a standard signatureMultiple keys/algorithms usageUser identity/authority verificationComputer security
The invention discloses a concurrence signature method with explicitly revocable fuzziness, which is called as revocable concurrence signature (RCS). The RCS provides a revoking algorithm and comprises the following steps of: setting parameters, generating a signature, authenticating the signature, determining the identity of the signer, and the like. When both sides exchange signatures, the method only needs to generate a keystone, and the fuzziness of the signature can be explicitly revoked according to the published keystone, so that the signatures exchanged by the two parties have the properties of standard signatures, various possible attacks in the aspects of concurrence signature fuzziness are eliminated, and the safety of the signature is greatly improved.
Owner:XI AN JIAOTONG UNIV
Intelligent system infrastructure for financial data computation, report remittance and funds transfer over an interactive communications network
InactiveUS20050119954A1Eliminate eavesdroppingEliminate connection hijackingComplete banking machinesFinanceExtensibilityProtection system
This disclosure relates to a specific, illustrative multilayer architecture for a program controlled system for providing services relating to financial data computation, report remittance and funds transfer services over an interactive communications network. The system comprises a subscriber server for hosting a virtual portal having at least one application for providing e-content to end users, the application including a network browser for accessing, displaying and transmitting data over the network. A first service provider server allows a system administrator to access the system remotely. A first security system for protecting the system from entry of unwanted data during data transfer over the network between the subscriber and service provider servers and the interactive communications network level. Also provided are plurality of primary servers including a primary network server, a primary tax computation server, a primary report generation server and a primary tax remittance server. The network server receives a tax computation transaction request from the subscriber server, transmits the request to the primary tax computation server, and returns data processed by the tax computation server to the subscriber server. In addition, the system has a plurality of secondary servers redundant to the first. The secondary servers include a secondary network server, a secondary tax computation server, a secondary report generation server and a secondary tax remittance server. A load balancing and scalability system is utilized for load directing, routing and switching functions during data transfer from utilization of at least one function at one of the primary servers to a corresponding function at a secondary server for optimum management of system resources.
Owner:DANG HONG M +3
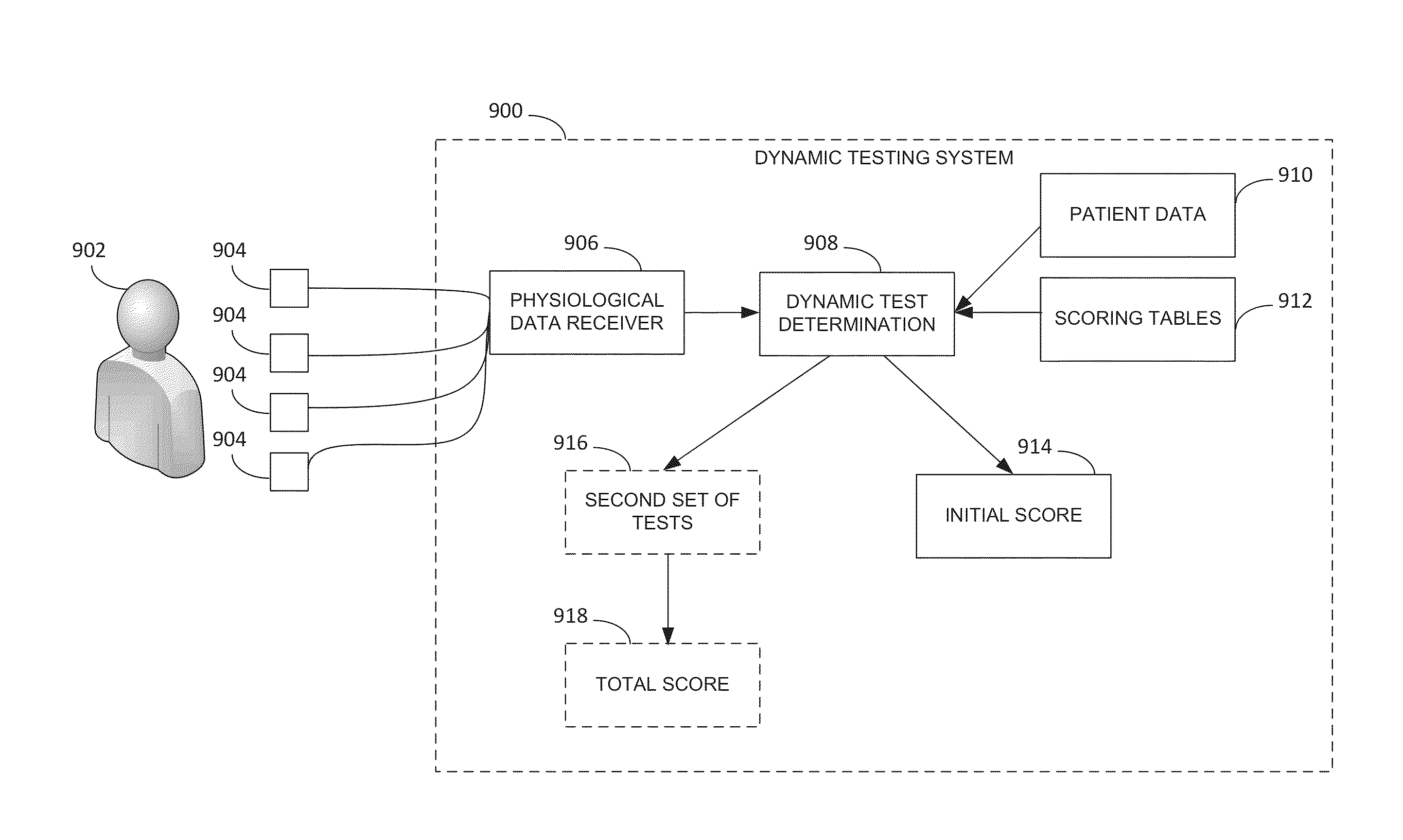
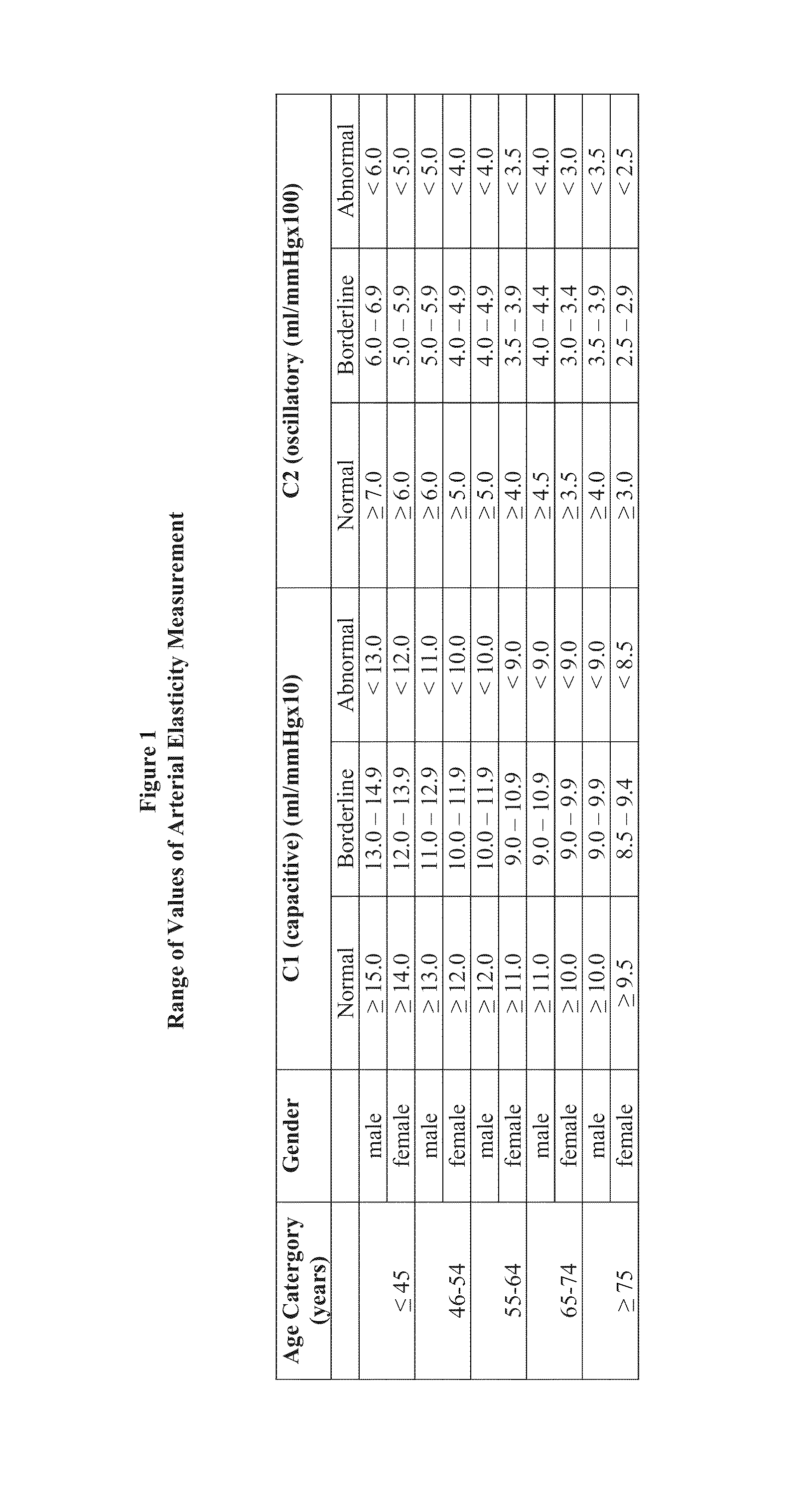
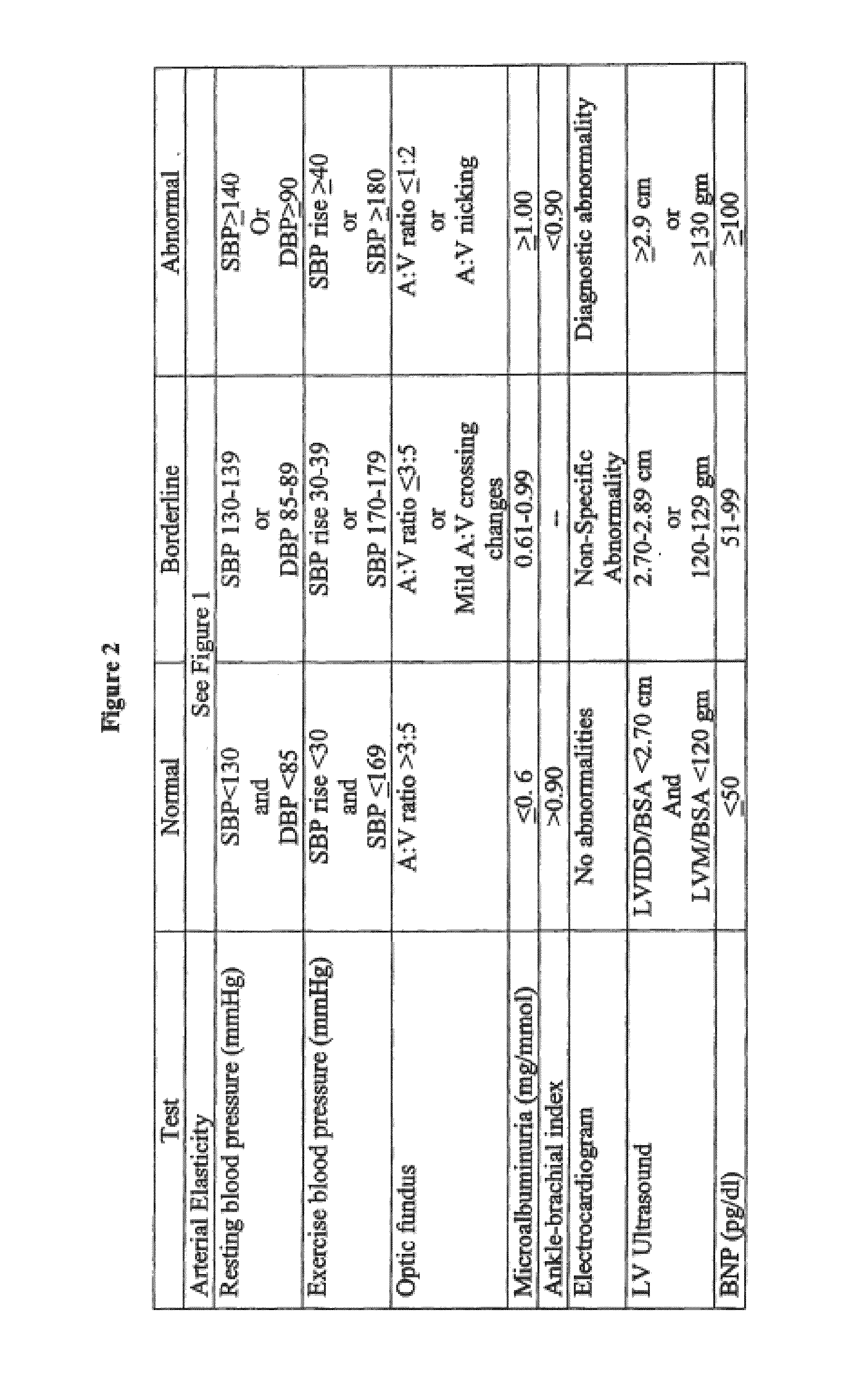
System and method for dynamic multi-stage test administration for detection of cardiovascular disease
ActiveUS8636660B1Delay disease progressionEliminate attackUltrasonic/sonic/infrasonic diagnosticsElectrocardiographyVascular diseaseMedicine
A system and method for dynamic multi-stage test administration for detection of cardiovascular disease may include performing a first set of tests in a first stage of testing on a patient. Physiological results for each of the tests in the first stage may then be received. Then, based on the physiological results, dynamically determining a set of tests to perform on the subject in a second stage of testing. Additionally, the dynamically determined set of tests in the second stage of testing may be performed on the subject.
Owner:RGT UNIV OF MINNESOTA
Organic-inorganic nano-composite reinforced polyethylene material and preparation method thereof
The invention discloses an organic-inorganic nano-composite reinforced polyethylene material and a preparation method thereof. The material is composed of 5-20wt% of rutile type titanium dioxide micrometer particles, 0.5-30wt% of modified carbon nanotubes, 0.5-2wt% of an antioxidant, 0.1-5wt% of an organic UV absorbent and the balance high density polyethylene. The preparation method consists of: firstly mixing sulfuric acid with nitric acid, then placing carbon nanotubes in the mixed acid to carry out stirring reaction, then performing solid-liquid separation, washing and drying treatment, then adding the obtained purified carbon nanotubes into a surface modifier solution to carry out reaction, and then performing drying to obtain modified carbon nanotubes, and then putting the rutile type titanium dioxide micrometer particles, the modified carbon nanotubes, the antioxidant, the organic UV absorbent and the high density polyethylene in a twin-screw extruder to conduct melt blending, and then performing extrusion, thus obtaining the target product. With high long-acting ultraviolet resistance, the organic-inorganic nano-composite reinforced polyethylene material can be widely used as films, pipes, wires and cables, plastic products and packaging materials under outdoor natural conditions.
Owner:HEFEI INSTITUTES OF PHYSICAL SCIENCE - CHINESE ACAD OF SCI
Preparation method for jasmine flower snake gall tea
InactiveCN107232370AHighlight substantiveSignificant progressDispersion deliveryAntipyreticBile JuiceDigestion
The invention relates to a preparation method for jasmine flower snake gall tea. The preparation method is characterized by comprising the following steps: (1) taking snake galls from snakes, cleaning, placing in a shade place, shielding sunlight, naturally airing and standing by; (2) taking the dried snake galls, soaking in cold water for 30-40min or in hot water at 100 DEG C for 5min, taking out the snake galls after swelling and standing by; (3) preparing jasmine flower leaves at the ratio of 1 snake gall to 3-50g of dry flowers and standing by; placing the swelled snake galls obtained in the step (2) above the jasmine flower leaves, penetrating and uniformly dropping the outflow gall into the jasmine flower leaves prepared at an appointed ratio in the step (3); uniformly stirring and then standing by for 2-3 hours; and using a drying machine for drying for 15-20min, filling into stereoscopic tea bags, sealing, bagging according to the external packing size and volume and putting into a box, thereby obtaining the jasmine flower snake gall tea. The jasmine flower snake gall tea is characterized by the effects of refreshing, eliminating summer-heat by cooling, helping digestion, reducing phlegm, removing grease, losing weight, and the like.
Owner:广西小燕蛇业有限公司
Non-rasterized image streaming system that uses ray tracing samples
ActiveUS20190065761A1Lower potentialEliminate attackPublic key for secure communicationDigital data protectionObfuscationComputer graphics (images)
Secure rendering system that creates ray tracing samples with obfuscated positions, so that images can only be viewed by an authorized consumer able to recover the sample positions. Obfuscation of ray directions is integrated into the rendering process, for example by incorporating encryption into a lens shader. The rendering system never stores or transmits an image without obfuscating positions, so even the rendering system cannot see the image it is rendering. Embodiments may use public key cryptography, so that encryption of sample positions is done with a public key, and only the owner of the secret private key can view the rendered image. Since keys are asymmetric, the rendering system cannot decrypt the obfuscated samples. Piracy of rendered images is therefore mitigated. Some compositing operations may be performed on the secure rendering output prior to decrypting sample positions; for example, colors may be modified globally or for selected objects.
Owner:GO GHOST LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com