Abnormity detection and processing method of cloud virtual environment
An anomaly detection and virtual environment technology, applied in transmission systems, electrical components, etc., can solve the problem of lack of anomaly detection and processing methods for most new application layer attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
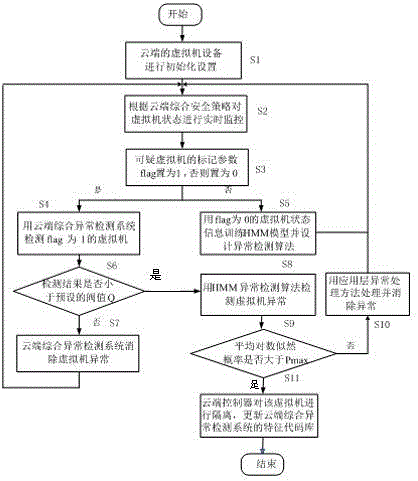
[0045] Specific embodiments of the present invention will be further described below in conjunction with the accompanying drawings.
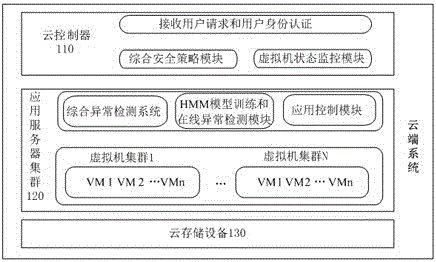
[0046] Such as figure 1 Shown is an embodiment of a cloud system. The cloud system includes: a cloud controller 110 , and an application server cluster 120 and a cloud storage device 130 communicating with the cloud controller 110 .
[0047] The cloud controller 110 includes: a module for receiving user requests and user identity authentication, a comprehensive security policy module and a virtual machine status monitoring module.
[0048] The cloud controller 110 refers to a dedicated server or server cluster, which mainly communicates with other servers in the cloud through a public network or a private network, accepts I / O access requests from various network protocol users and authenticates the user's identity. The user can only access the virtual machine space created by the cloud for the user after the identity authentication of the user...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com