A method, device and system for access authentication
A technology of access authentication and authenticator, applied in the field of network communication, can solve the problems of not being able to perceive the existence of connected users on the RG, not being able to obtain, and not being able to perform fast channel switching control, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
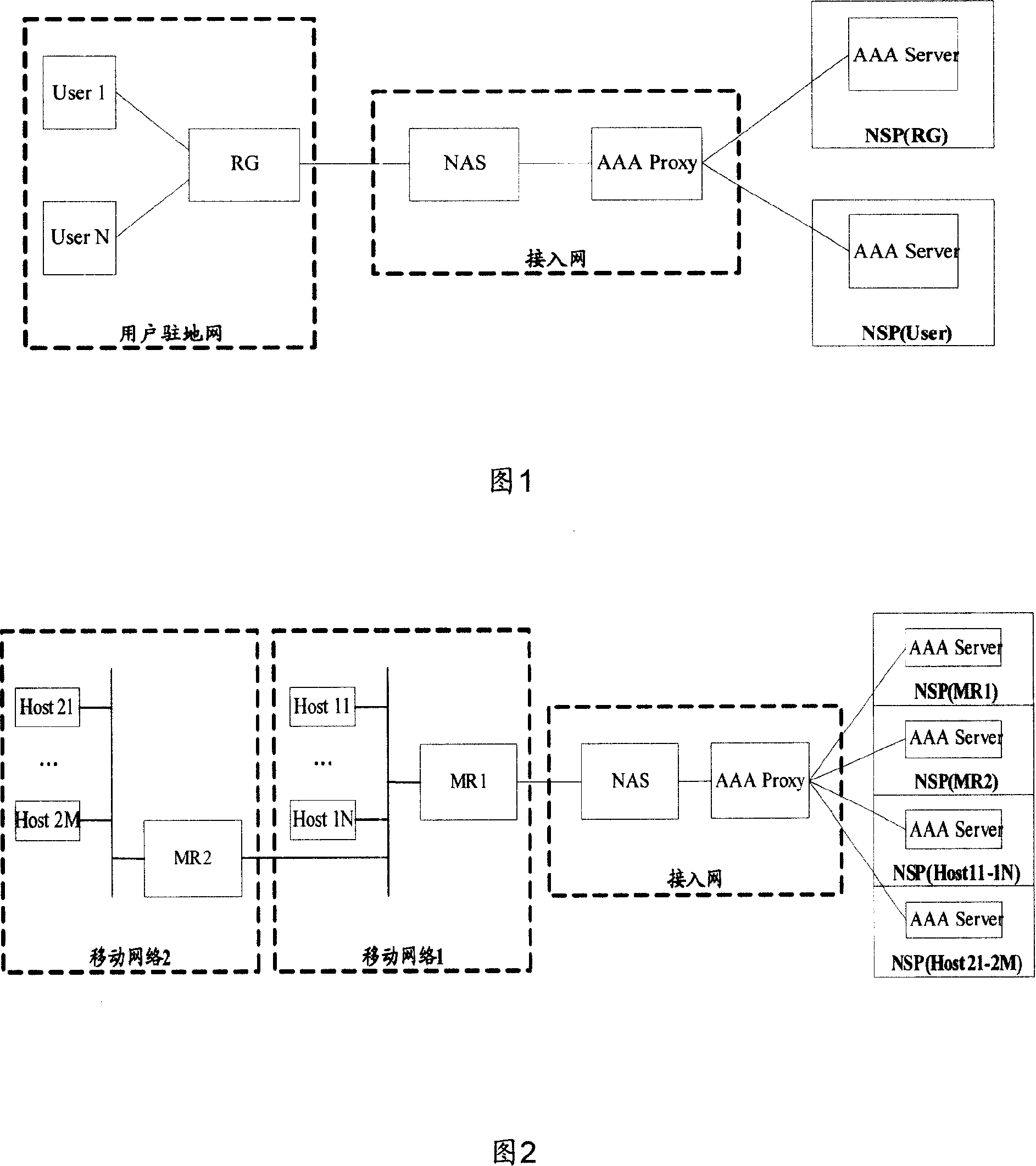
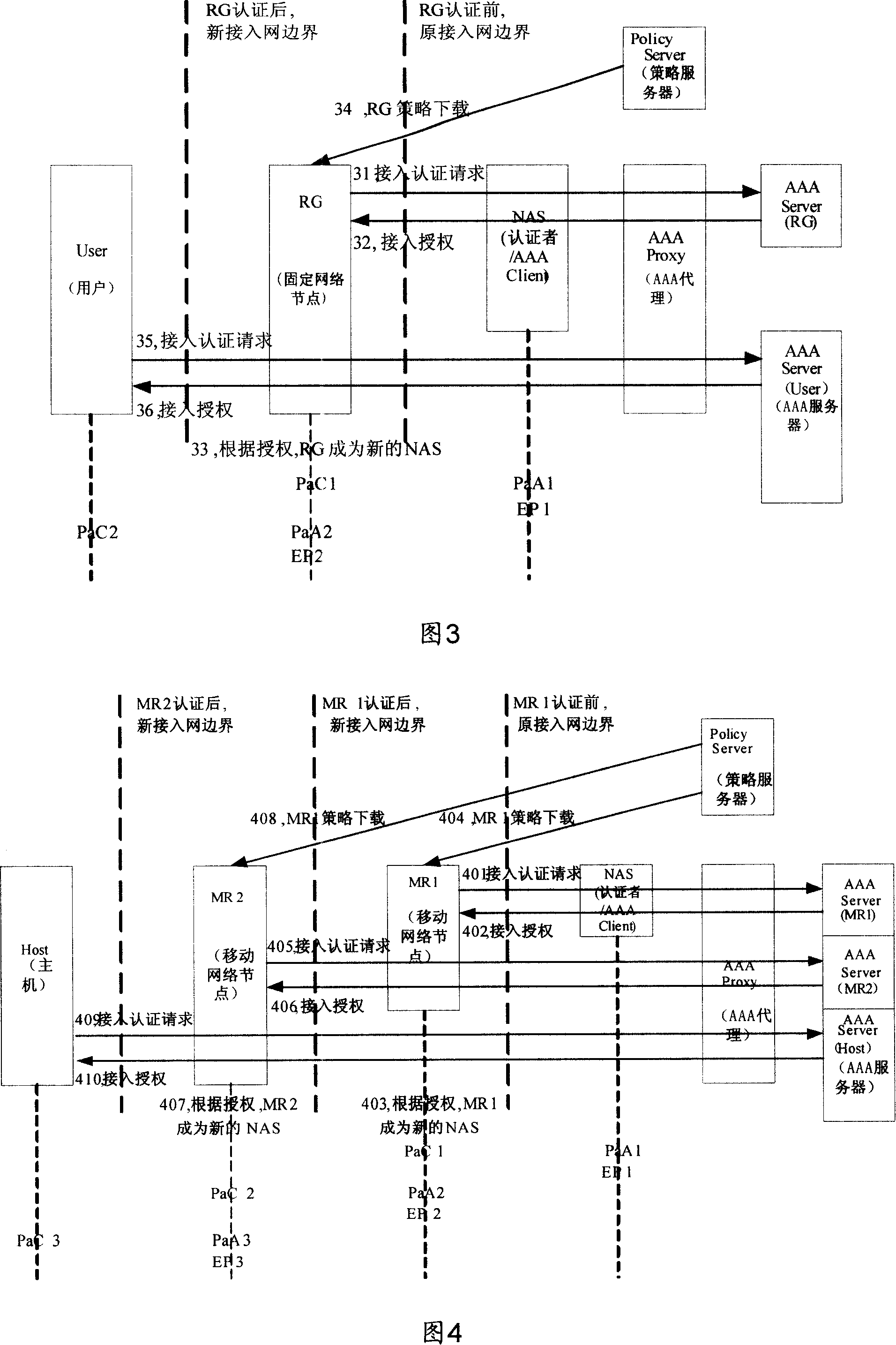
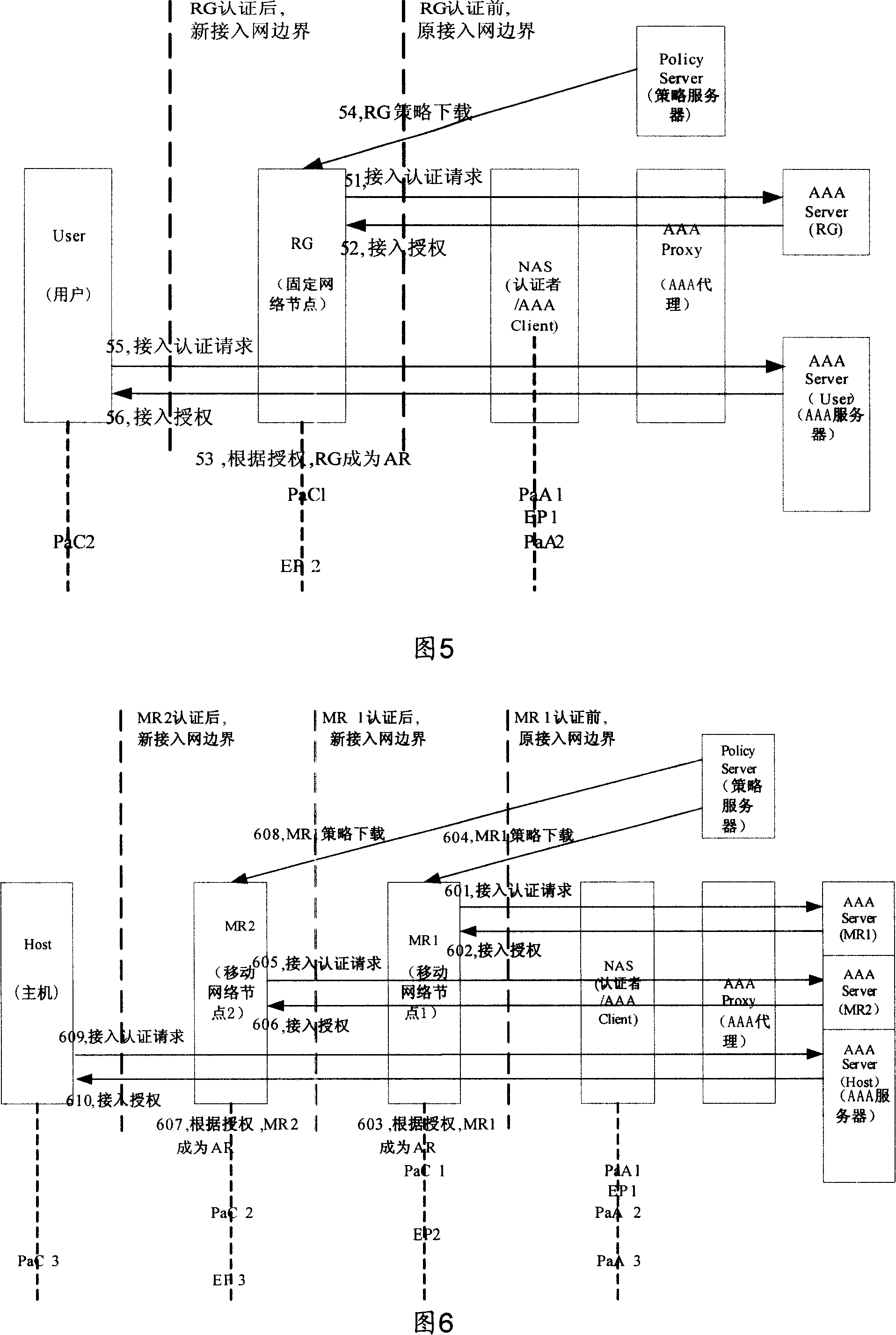
[0101] The present invention mainly provides a method, device and system for realizing access authentication, in which a network node initiates an access authentication operation to an authentication server to which it belongs, and the authentication server authenticates the access authentication operation initiated by the network node processing; if the network node that initiates the access authentication operation and the authentication server still needs to pass through the unauthenticated network node (that is, an untrusted node), then the corresponding untrusted node first needs to initiate the access authentication operation, and after passing the authentication After that, it becomes the authenticator (Authenticator) or authentication transfer node of the network node or user connected to it, and can process the messages involved in the access authentication operation initiated by the network node connected to it.
[0102] In the present invention, the network node that...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com