Method for realizing access authentication, device thereof and mobile terminal
An access authentication and mobile terminal technology, applied in security devices, electrical components, wireless communications, etc., can solve the problems of easy cracking of network login passwords, easy cracking and copying of user identification cards, etc., to achieve the effect of improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
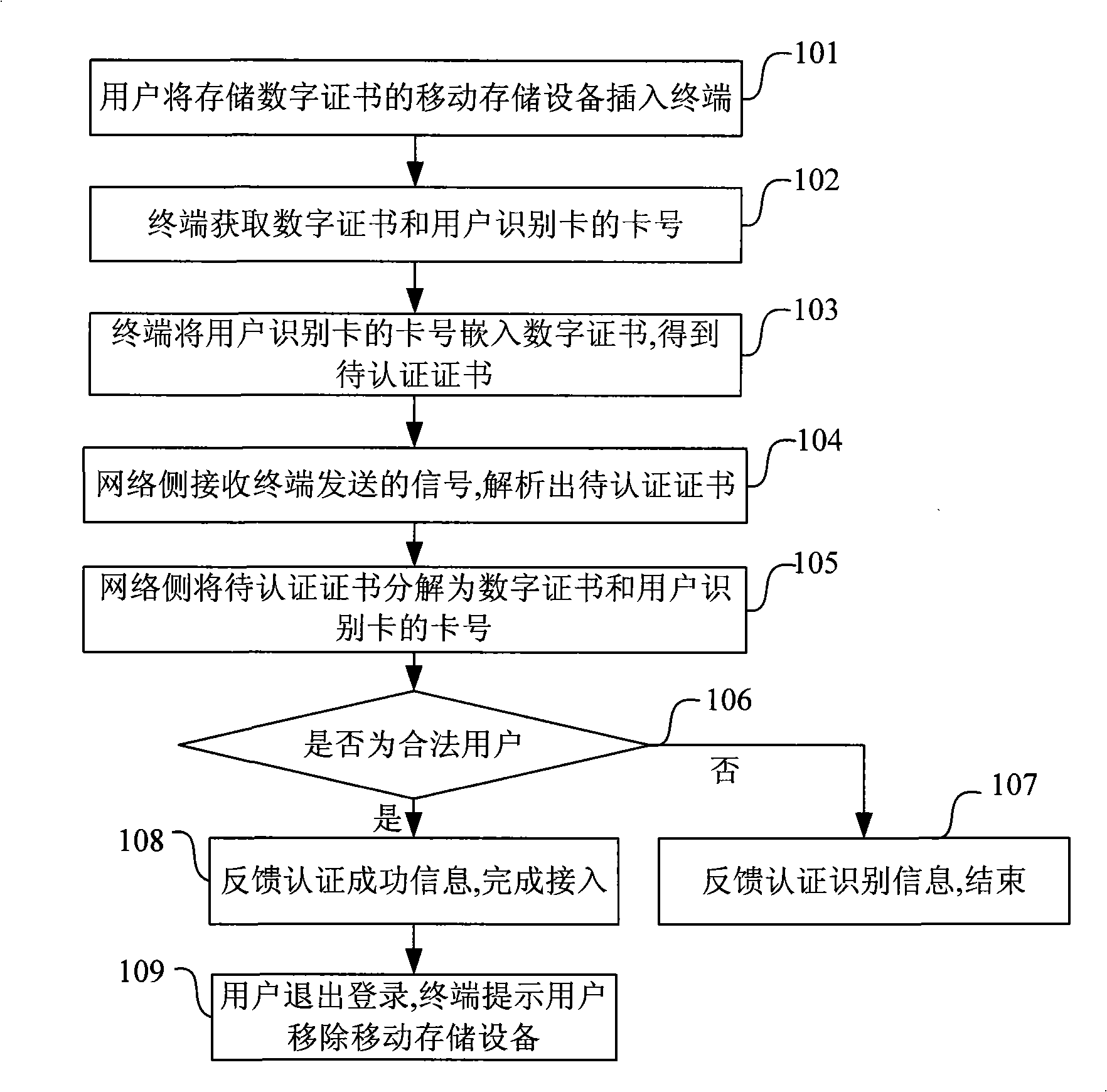
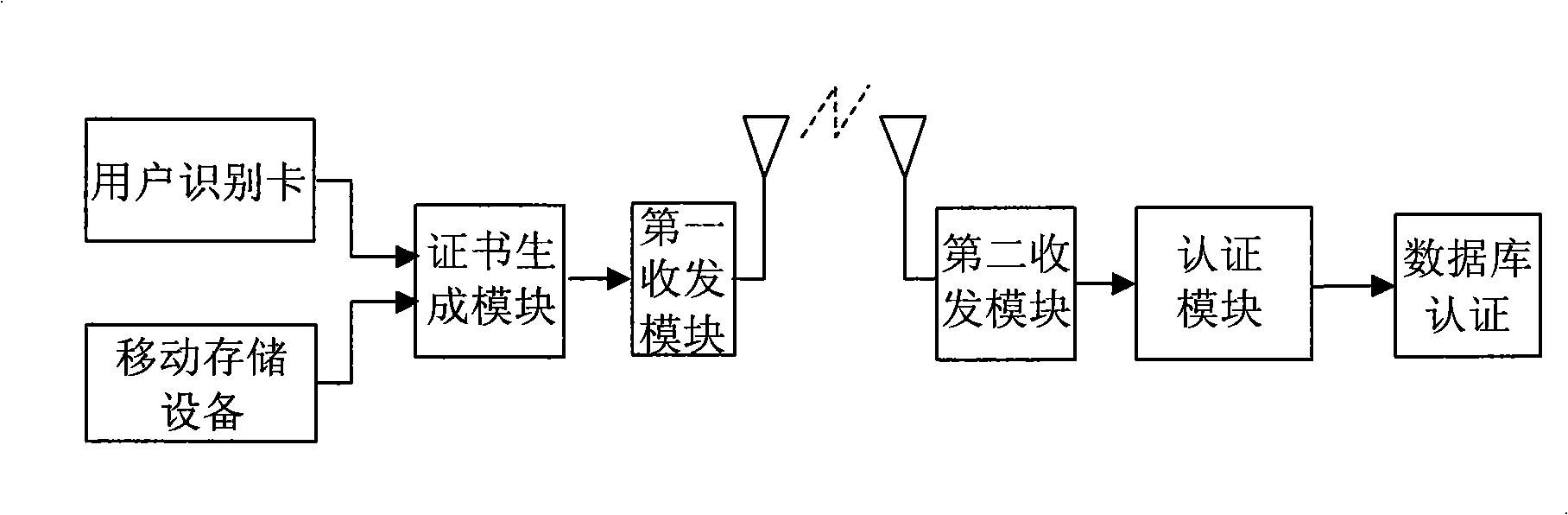
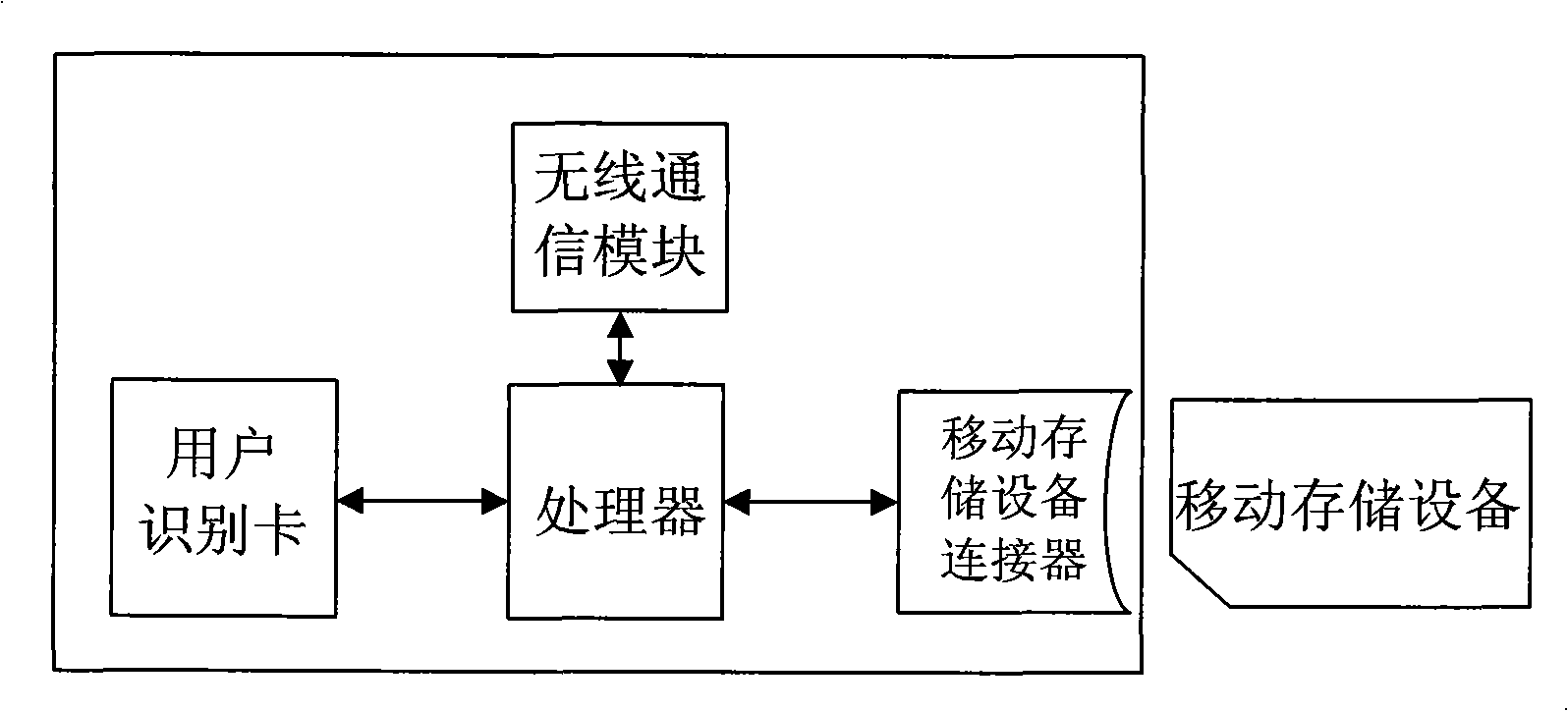
[0036] The present invention stores part or all of the authentication information required by the terminal to access the private network or network server separately in the mobile storage device of the terminal, which is stored separately from the terminal. When accessing, the mobile storage device needs to be inserted, and the terminal uses the stored The authentication information in the device can be connected to the private network or network server. When exiting the private network or network server, the terminal reminds the user to unplug the mobile storage device that stores the authentication information, so that the authentication information is separated from the terminal. Improve the security of access authentication to avoid illegal access.
[0037] The present invention will be described in detail below in conjunction with the accompanying drawings.
[0038] figure 1 Shown is the access authentication method of the present invention. The present invention is base...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com