Wireless local area network two-way access authentication system and method based on identity certificates
A wireless local area network and identity certificate technology, applied in the field of wireless local area network two-way access authentication system, can solve the problem of reducing access authentication efficiency, key escrow and key transmission, WLAN security mechanism authentication message interaction delay, digital certificate maintenance cost and application issues such as sexual defects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
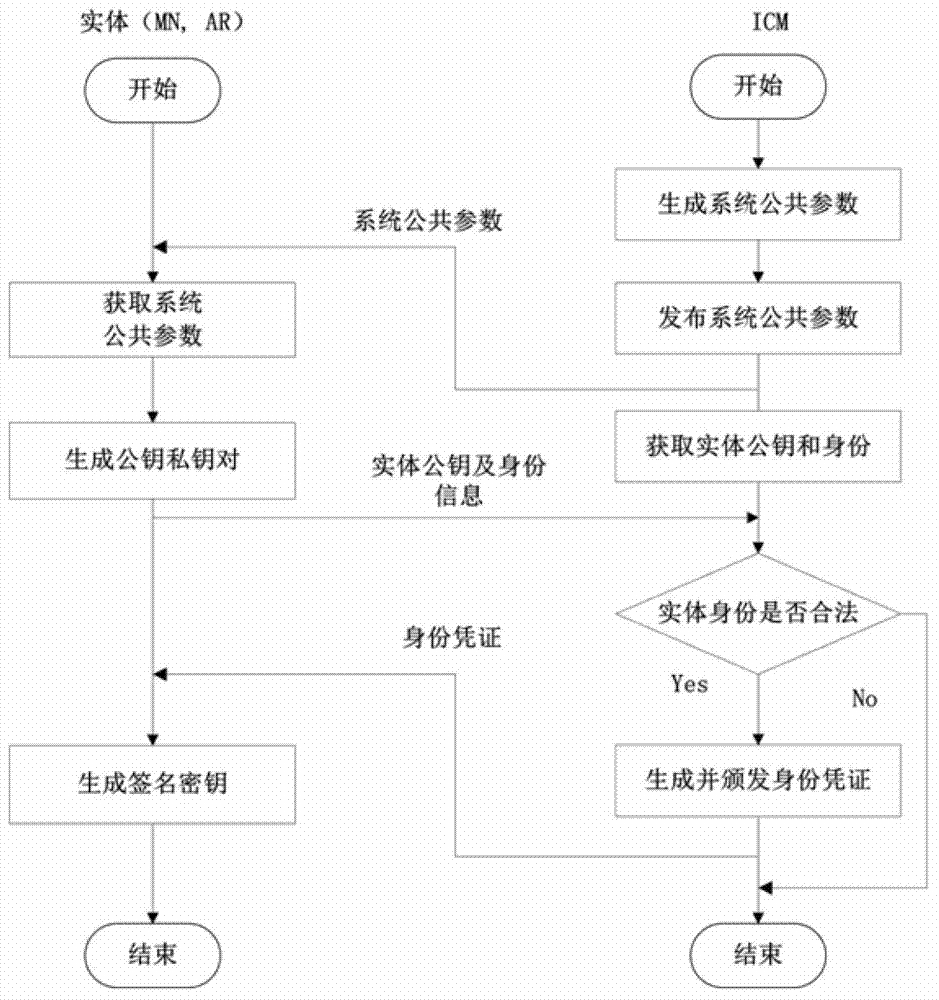
[0084] The specific implementation manners of the present invention will be described in detail below in conjunction with the accompanying drawings.
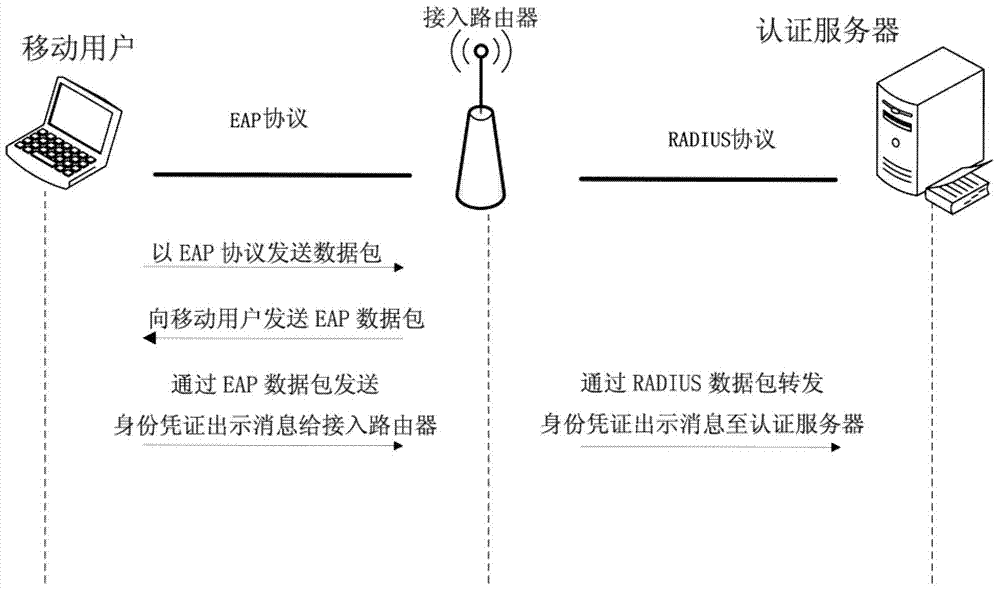
[0085] In this embodiment, the system and method for two-way access authentication of a wireless local area network based on an identity credential are applied to an access authentication link of a wireless local area network. The mature 802.11i authentication framework is used in the implementation process. For the bearer of authentication messages, the EAP protocol is used between the mobile user and the access router, and the RADIUS protocol is used between the access router and the authentication server.
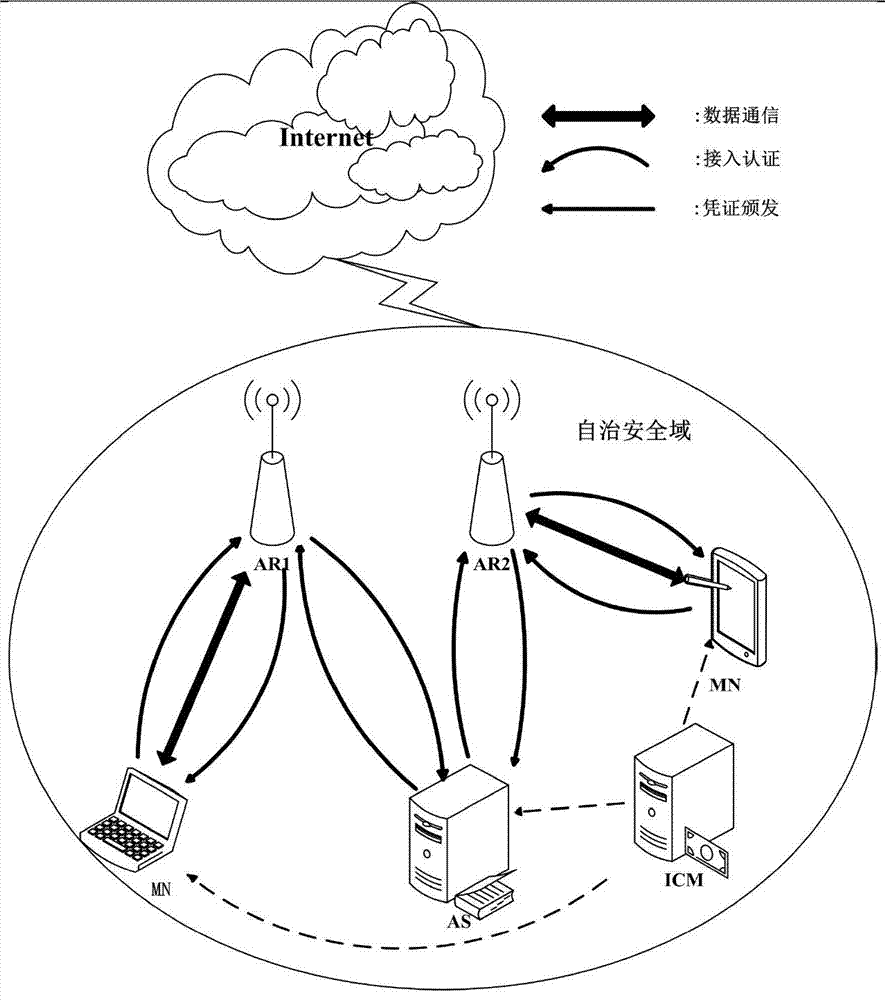
[0086] Such as figure 1 As shown, the two-way access authentication system for WLAN based on identity credentials includes several access routers (including AR1 and AR2), set in an autonomous security domain, and also includes an identity credential management server (ICM) and an authentication server (AS );
[0087] The...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com