Bidirectional access authentication method
一种认证方法、双向接入的技术,应用在用户身份/权限验证、安全装置、计算机安全装置等方向,能够解决手动建立、管理复杂、难用户身份有效性验证等问题
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
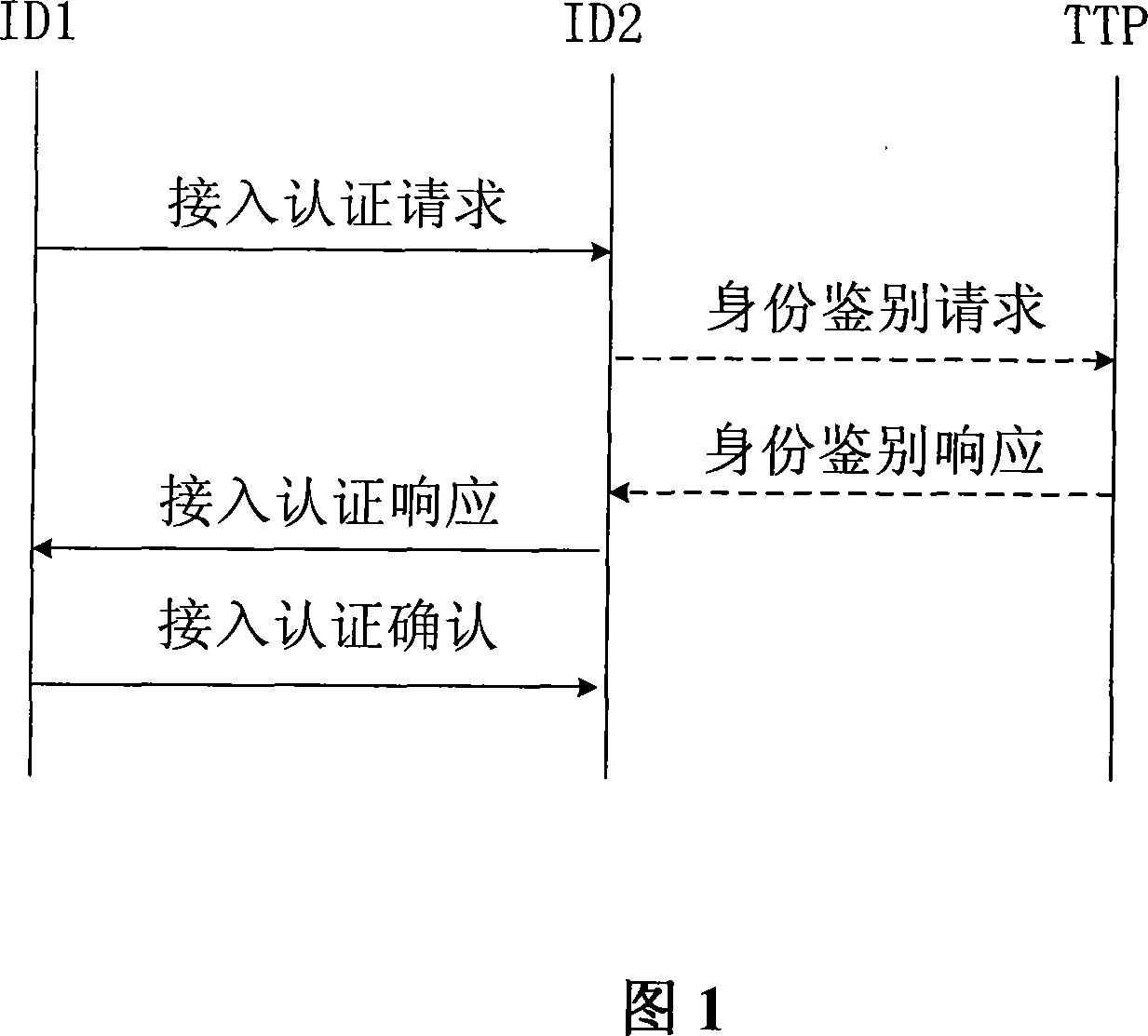
[0103] The method of the present invention is realized by a trusted third party (TTP), and the trusted third party can be an authentication server or other devices that can realize authentication. The trusted third party is responsible for the physical authentication of user entity identity, system parameter generation and User parameter establishment process.
[0104] Referring to Fig. 1, the specific implementation method of the present invention is as follows:
[0105] 1) First, a trusted third party establishes system parameters, which include:
[0106] N: the product of two large prime numbers;
[0107] e: an integer and satisfy gcd(e, φ(N))=1;
[0108] d: an integer that satisfies ed≡1(modφ(N));
[0109] Strong one-way hash function h: {0, 1} * → Z φ(N) .
[0110] Among them, the private key of the system is d(master-key), and the parameters that the system can disclose are (N, e, h).
[0111] A trusted third party is responsible for keeping the system private key...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com