WAPI-XG1 access and fast switch authentication method
A technology of WAPI-XG1, authentication method, applied in the field of WAPI-XG1 access and fast handover authentication, can solve the problems of inability to access the network, different, lack of error recovery mechanism, etc., to achieve the effect of reducing complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
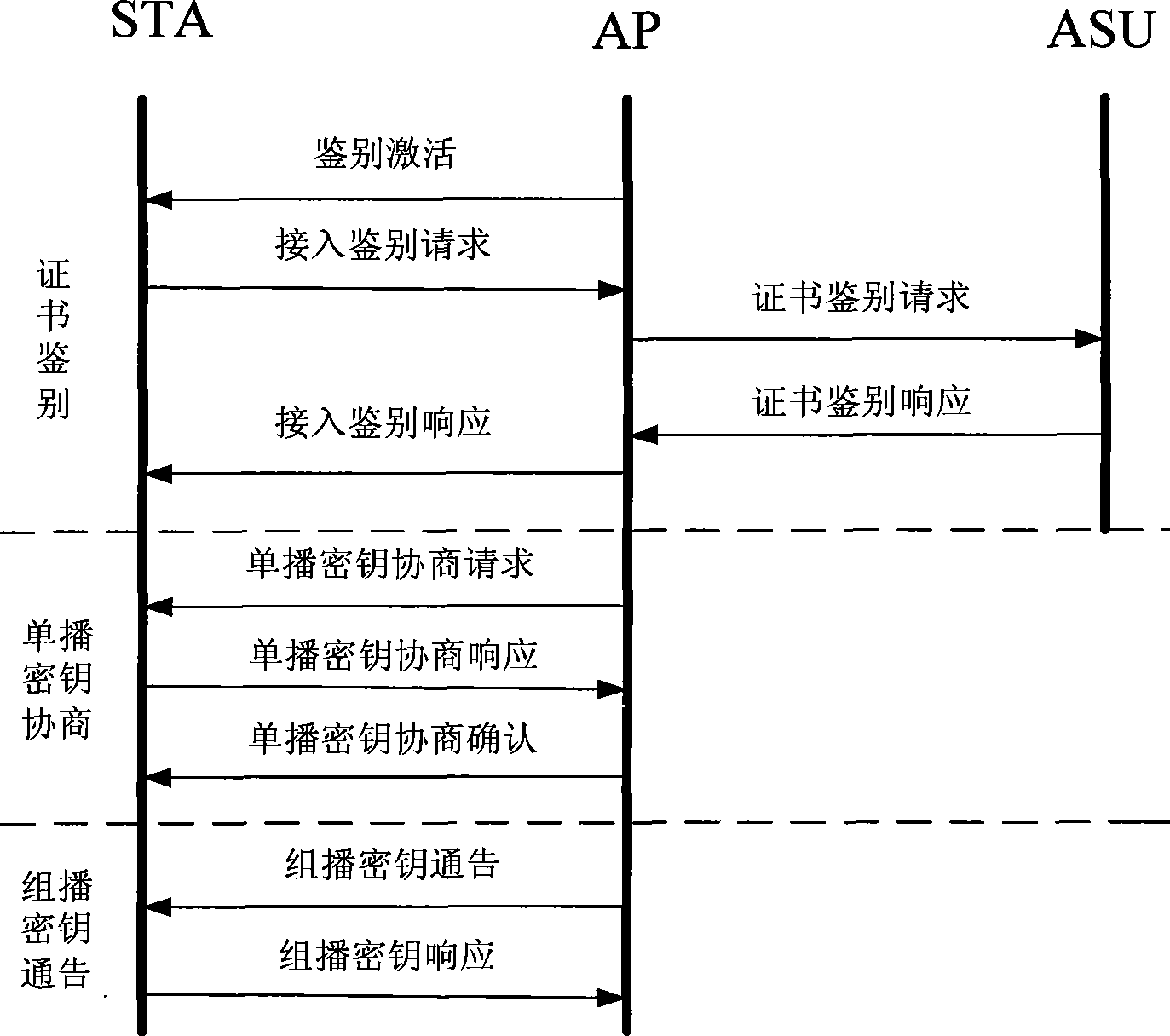
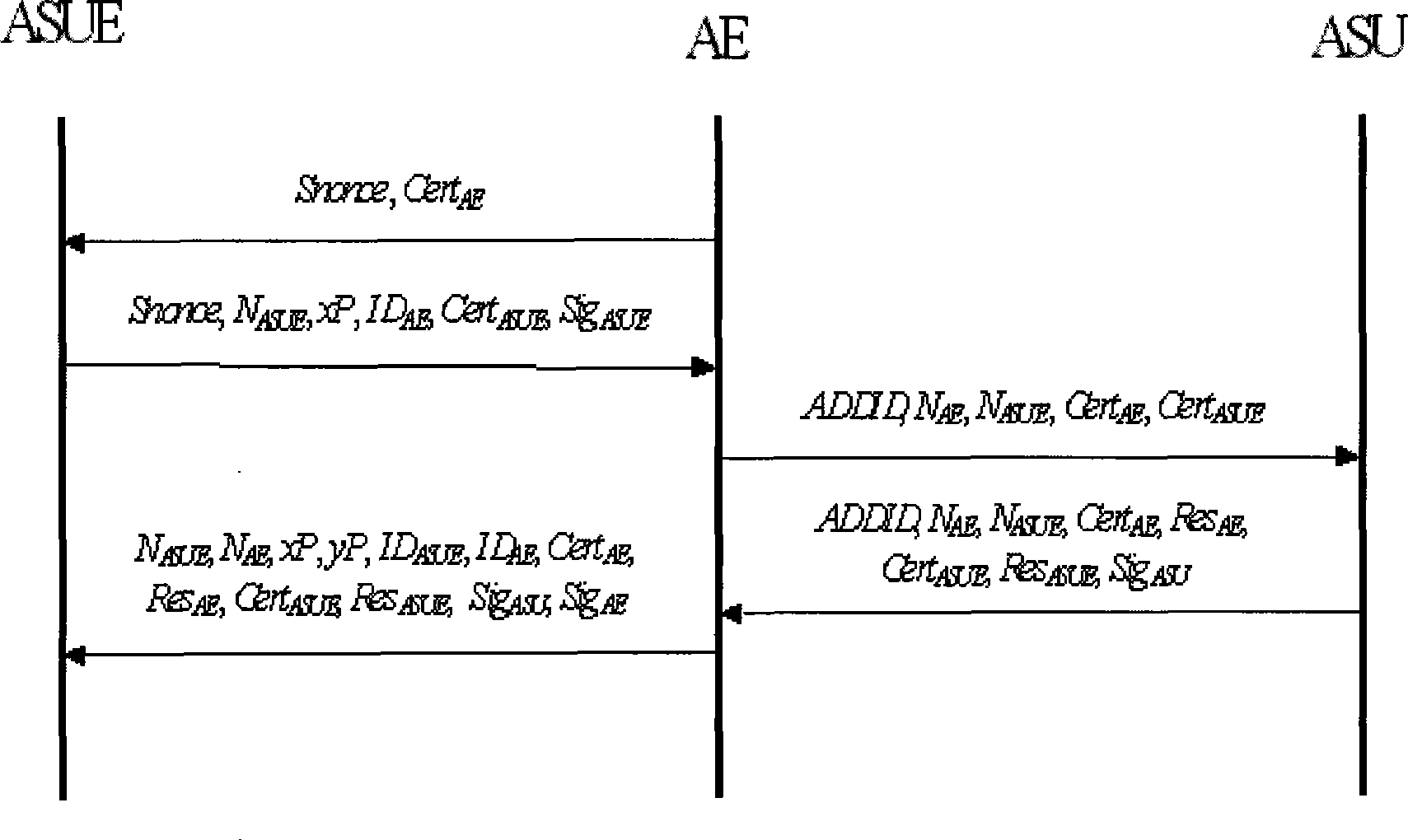
[0140] Such as Figure 9 As shown, the access authentication method WAPI-XG1 of the present invention + Mutual authentication between STA, AP, and ASU is realized through a protocol interaction. Since there is no direct trust relationship between STA and AP, a trusted third-party ASU is required to confirm and transmit authentication information to achieve mutual trust. For the certificate-based authentication mode, the protocol performs two different DH key exchanges between STA and AP, STA and ASU, which are used to generate the shared key USK between STA and AP, and the shared key USK between STA and ASU. Shared key HK. For the PSK-based authentication mode, the protocol also implements explicit key authentication between STA and AP and between STA and ASU. Therefore, after a STA accesses a WLAN through the new authentication protocol, it is no longer necessary to conduct a communication between the STA and the AP. The explicit key authentication based on the shared key ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com