Login authentication method and login signature procedure
A login authentication and program technology, applied in the field of network communication, information security, and computer software, can solve problems such as failure to take into account the protection of communication transmission links, theft of user account information communication transmission, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
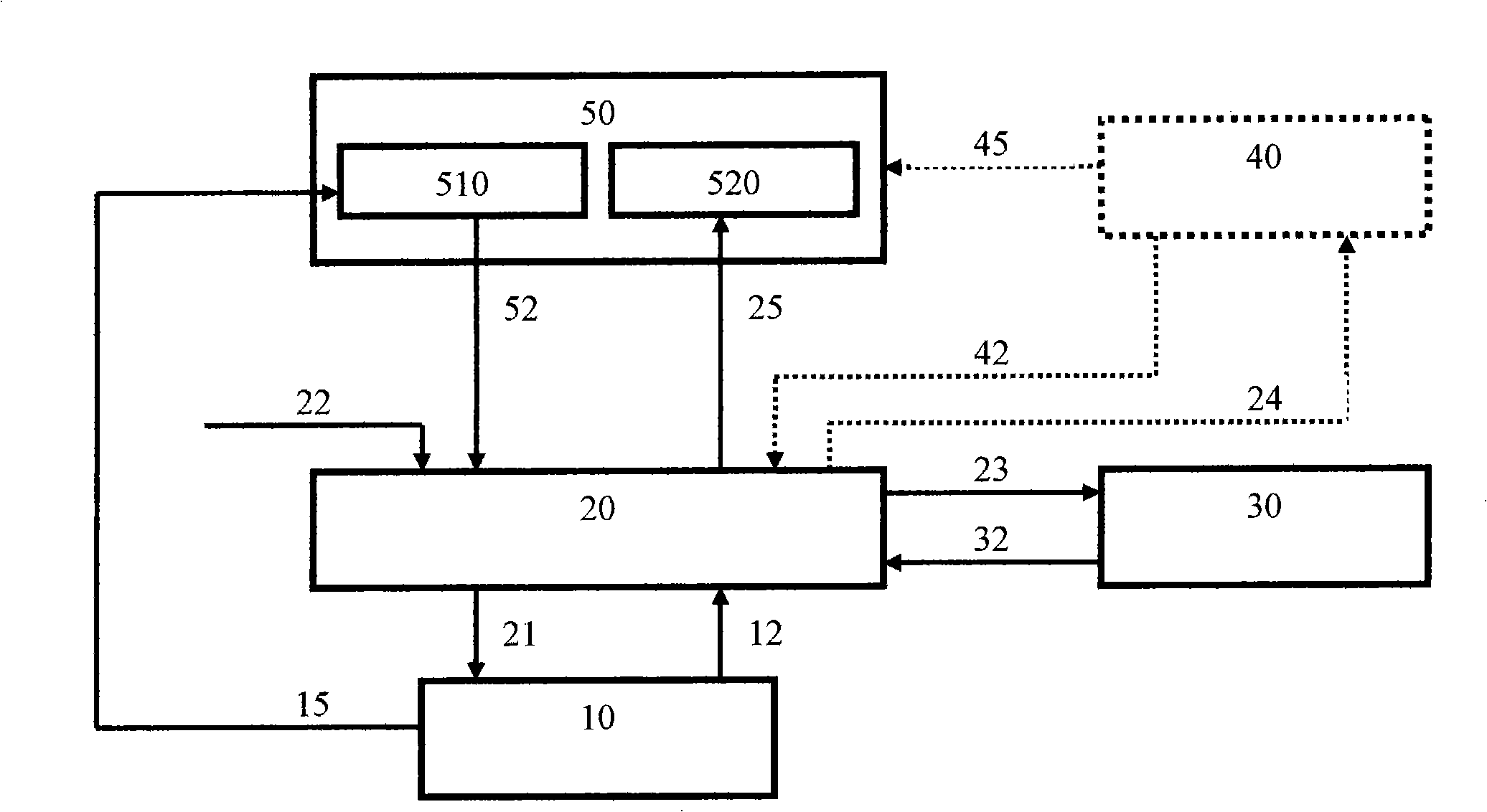
[0019] 1. Implementation of the login authentication method.
[0020] refer to Figure 4to illustrate. During the login acceptance stage, the system presents an interface window as shown in this figure, the title is "User Login Interface", and there is a close and exit button on the right side of the title bar. The user enters login information in this interface: [User Name] edit box enters the name or code of the user account; [Password / Response] edit box displays password characters, enter the user’s password or signature information as a response, depending on the user’s Whether the [Signature Challenge] check box is checked or not; if the [Signature Challenge] check box is checked, the [Password / Response] edit box will be renamed as [Signature Response], the signature information will be entered, and [ Signature Challenge] edit box (read-only) and [Password Algorithm] drop-down list box; if the [Signature Challenge] check box is not checked, the [Password / Response] edit ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com