Self arranged net mode shared key authentication and conversation key consulant method of radio LAN
A wireless local area network and shared key technology, which is applied in the field of authentication and session key negotiation between wireless terminals through pre-shared keys, can solve problems such as no authentication method, achieve high security, small amount of calculation, achieve high efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] When the STAs of the WLAN system work in the ad hoc network mode, the shared key can be configured in each STA in advance. The configuration of the shared key can take the practice of entering a password and then mapping the password to the key. Because for ordinary users, passwords are easier to remember and process.
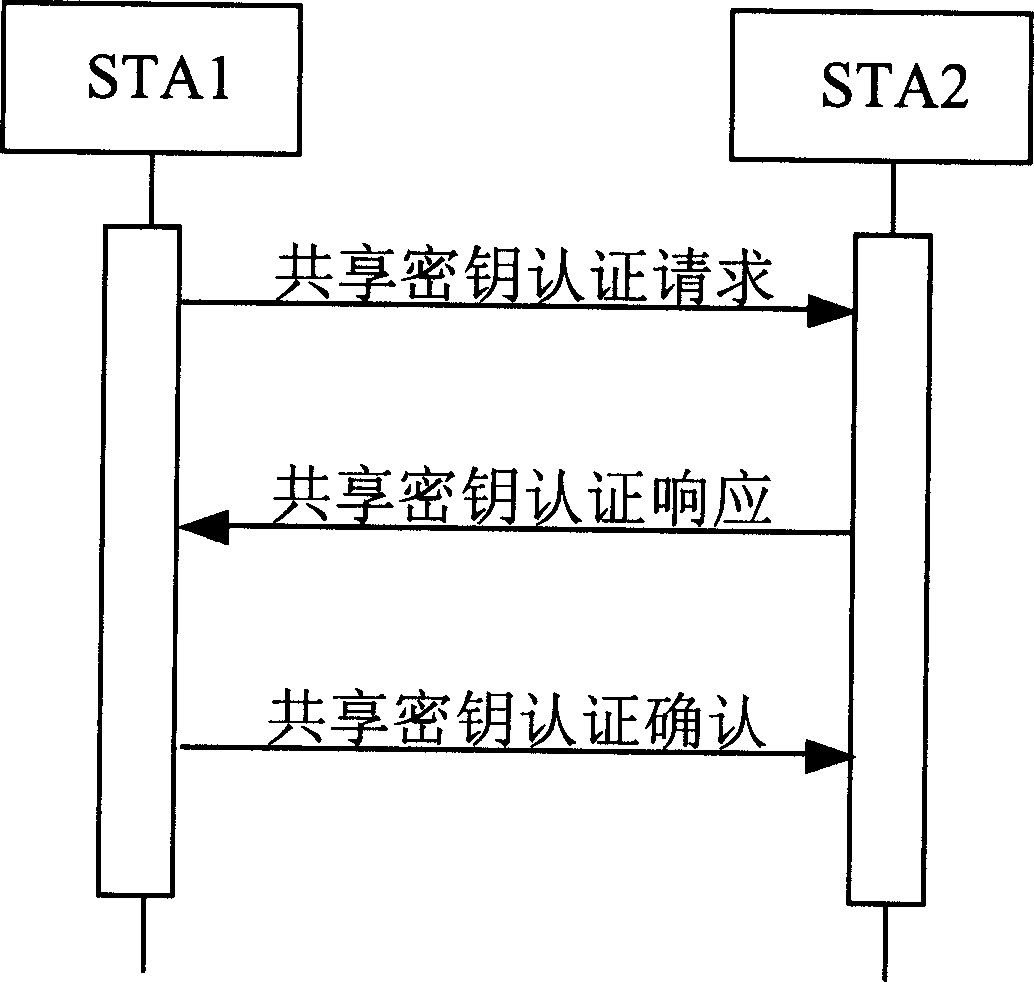
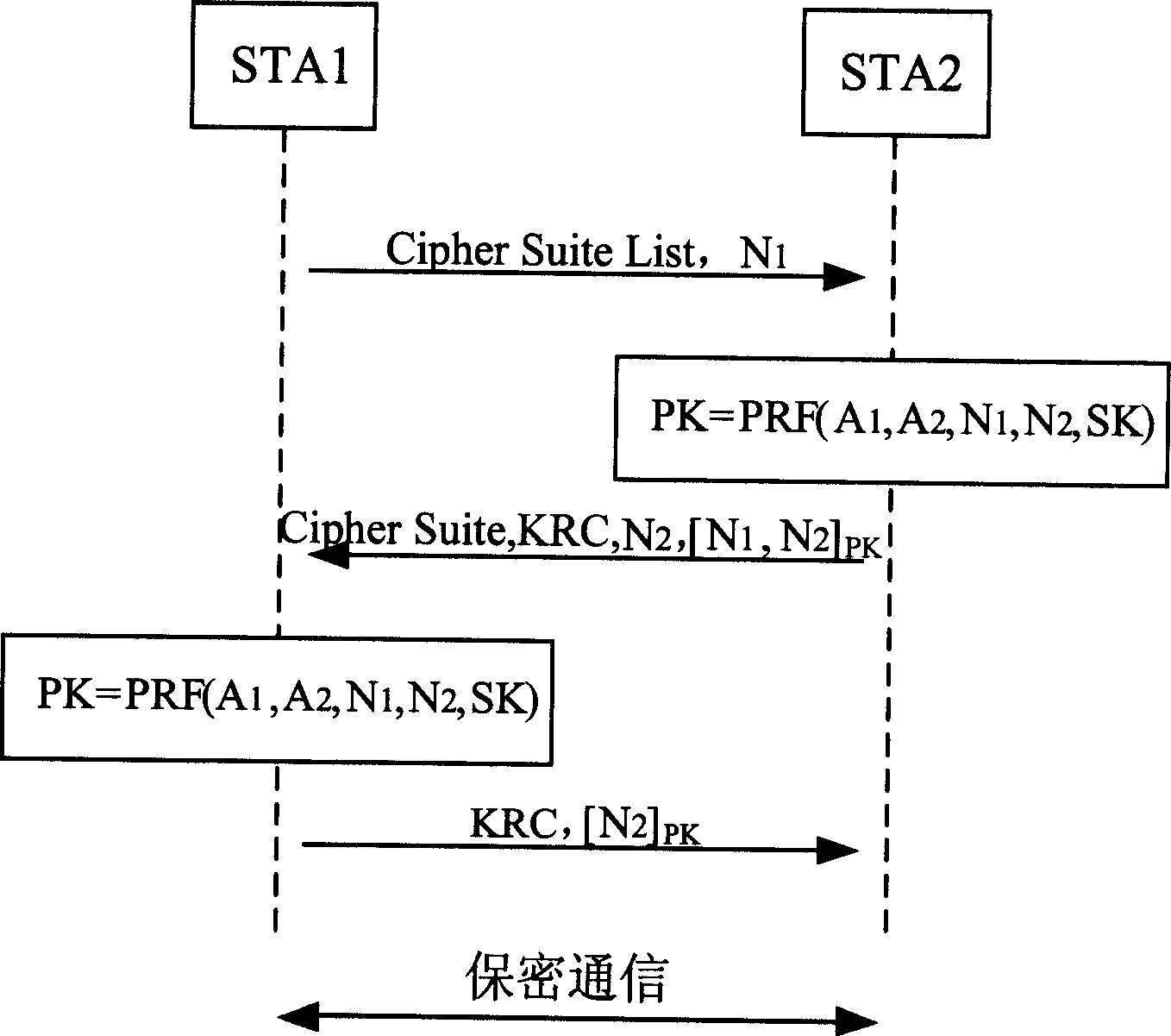
[0017] refer to figure 2 As shown, assuming that two wireless terminals STA1 and STA2 in the ad hoc network already have the same shared key SK, the process of shared key authentication and session key negotiation between them is,
[0018] 1. STA1 generates a secure random number N 1 .
[0019] 2. STA1 sends the random number N 1 It forms a shared key authentication request message with the cipher suite list supported by STA1 and sends it to STA2 in plain text.
[0020] 3. After receiving the shared key authentication request message from STA1, STA2 checks whether there is an algorithm supported by STA2 among the security algorithms supported by ST...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com