Secure key authentication and ladder system
a technology of secure key authentication and ladder system, which is applied in the field of conditional access and copy protection systems, can solve the problems of difficult for a third party to perform unauthorized reception, the scrambled signal content cannot be understandable, and the transmitted data bits of unauthorised decoders cannot be decoded
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
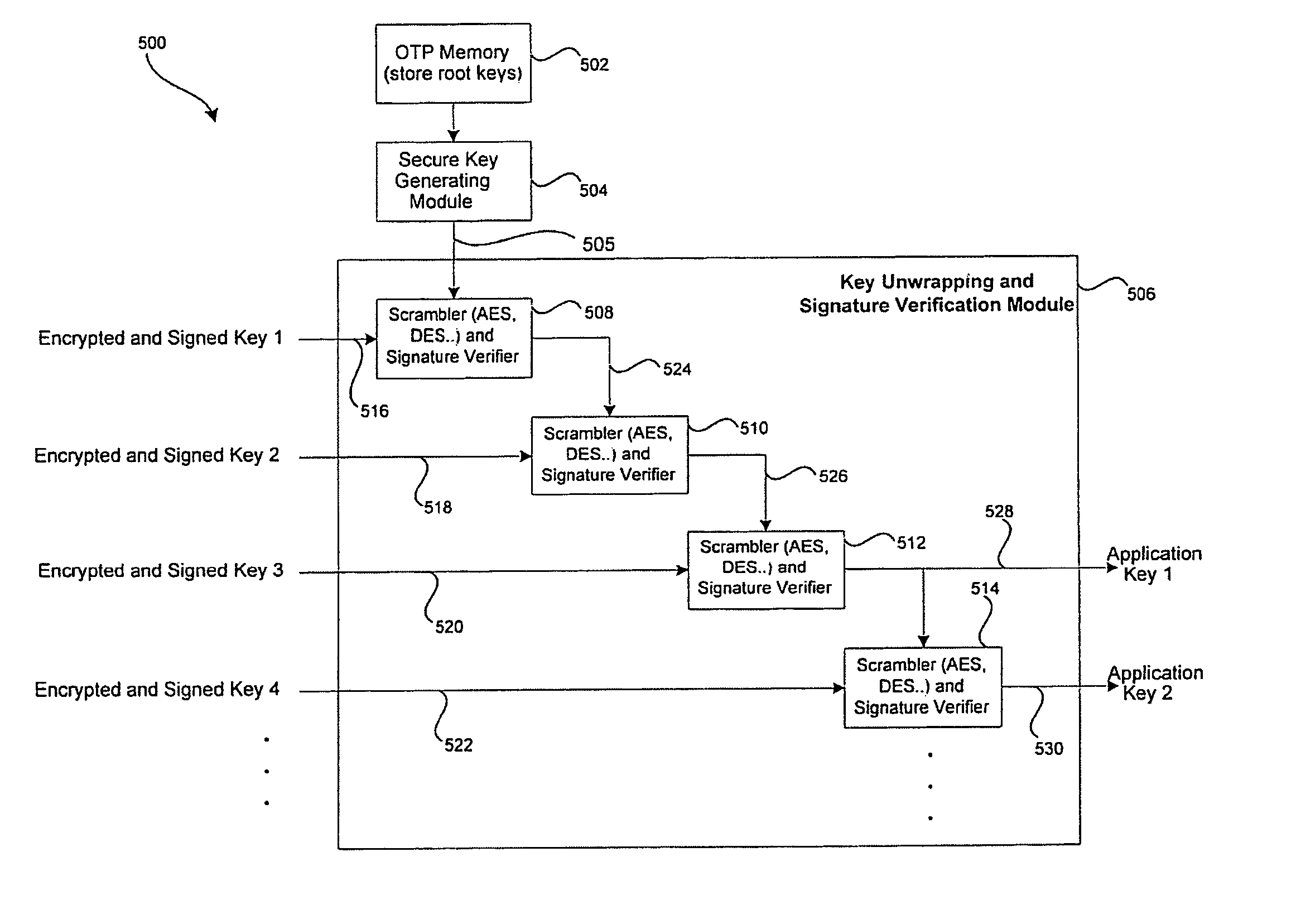
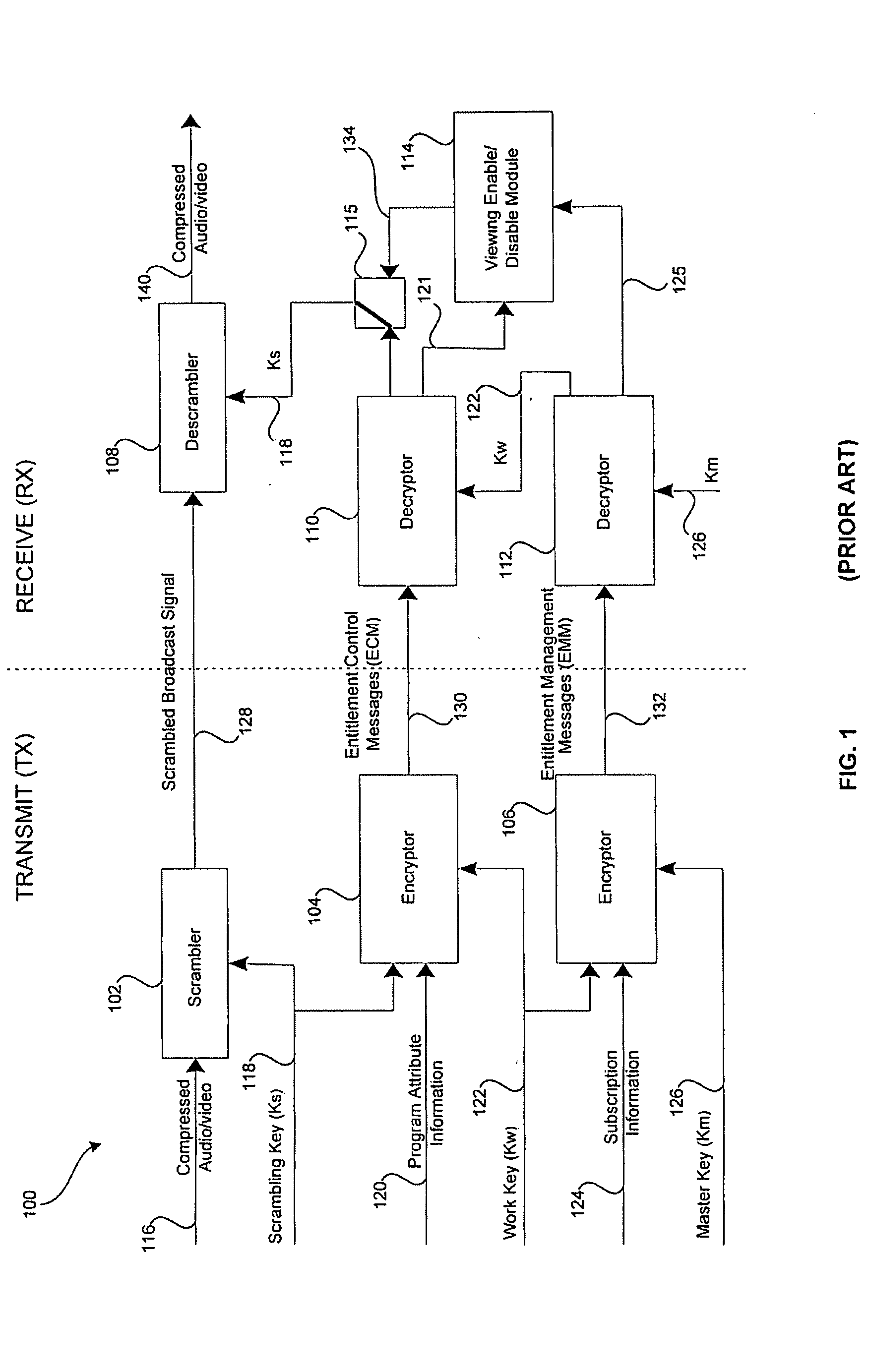
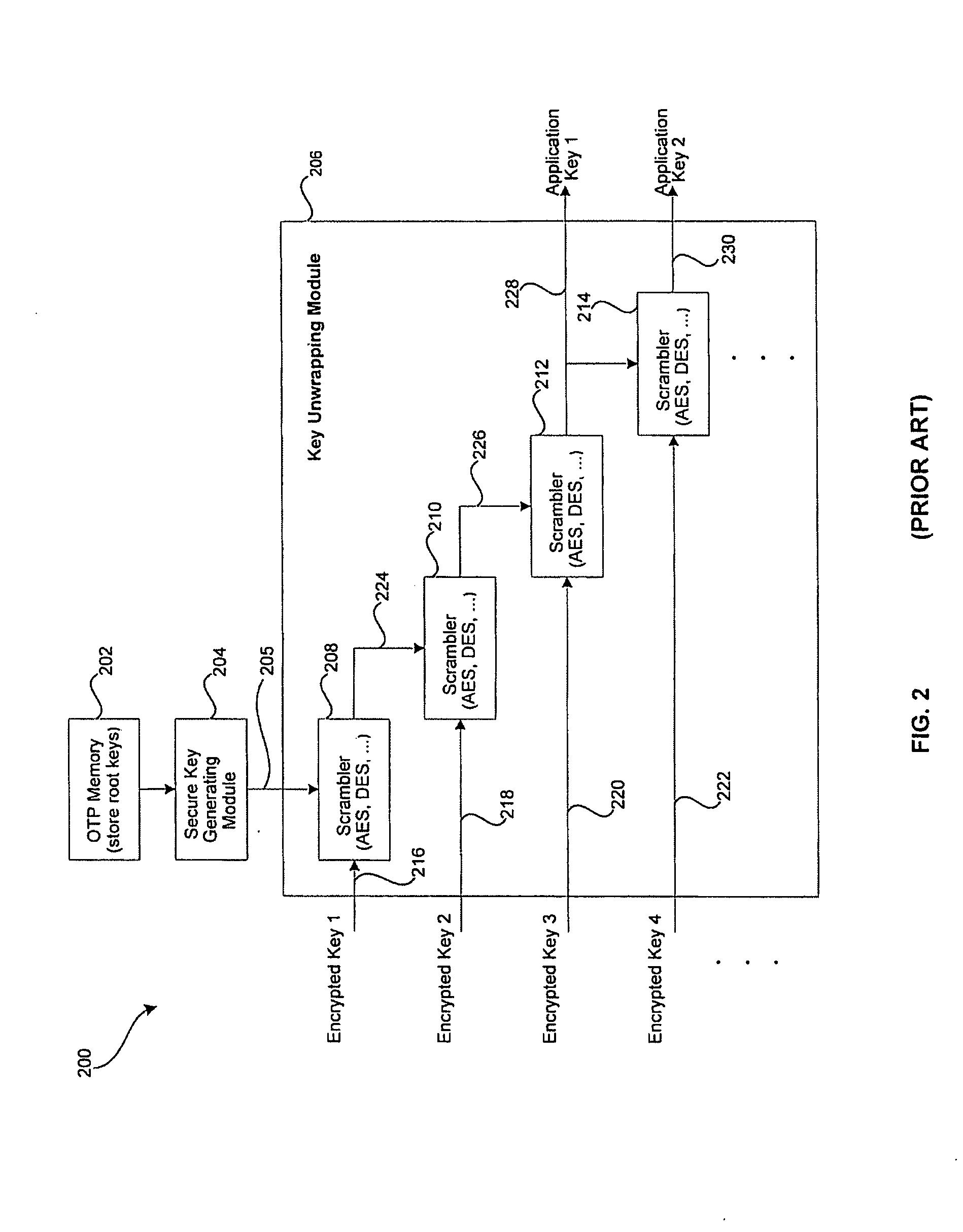
[0040] Certain aspects of the invention may be found in a method and system for secure key authentication and key ladder. The method for secure key authentication may include generating a digital signature of a secure key in order to obtain a digitally signed secure key; and transmitting the digitally signed secure key from a first location to a second location. The digital signature may be generated by utilizing an asymmetric encryption algorithm and / or a symmetric encryption algorithm. The digitally signed secure key may be encrypted prior to transmission. The secure key may be one of a master key, a work key and a scrambling key. The digitally signed secure key may be received at the second location and the digitally signed secure key may be decrypted to obtain a decrypted digitally signed secure key. If the secure key comprises a master key, a decrypted digitally signed master key may be utilized for decrypting an encrypted digitally signed work key. If the secure key comprises ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com