Threshold and key-based authorization method in software as a service (SaaS)
A software and key technology used in the field of data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0094] Implementation steps of data operations based on threshold keys and authorization in SaaS applications:
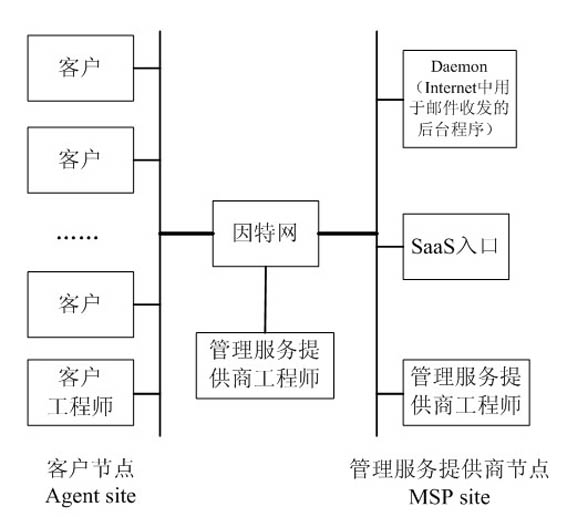
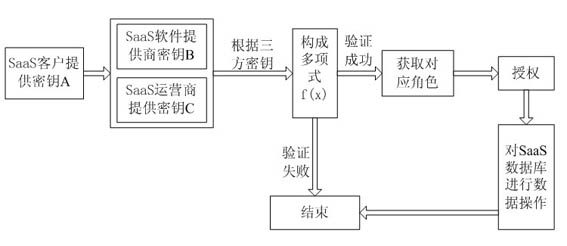
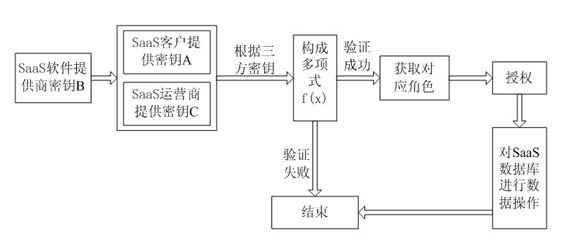
[0095] The research on data security technology based on threshold key and authorization in SaaS is characterized in that the classic Shamir(t, n) secret sharing scheme is used as the construction threshold signature scheme, and the SaaS software developer, operator, and customer share the key. SaaS data operation permissions are graded and permission tables are established, as follows:
[0096] SaaS data operation permission classification and implementation steps of establishing permission table:
[0097] (1) According to the needs of SaaS customers, the data operation authority is classified, and the authority of the corresponding level of personnel is established after the negotiation of the SaaS software developer, operator, and customer.
[0098] (2) Create a permission table on the MSP Site,
[0099] (3) Establish corresponding roles according to the author...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com