Smart password key authentication based cross-platform heterogeneous system login method
An intelligent password key and heterogeneous system technology, applied in the field of cross-platform heterogeneous system login based on intelligent password key authentication, can solve the problem of inconsistent user identity information content and data format, lack of integrity of data security, easy forgetting of passwords or leaks etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
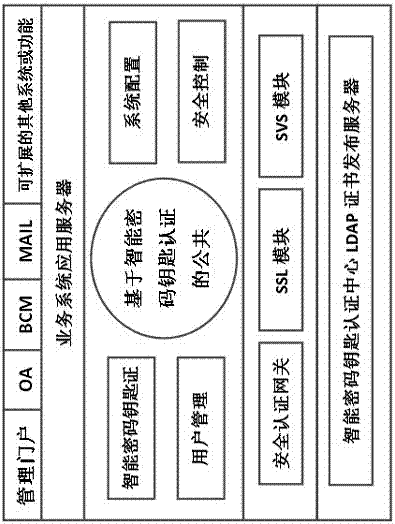
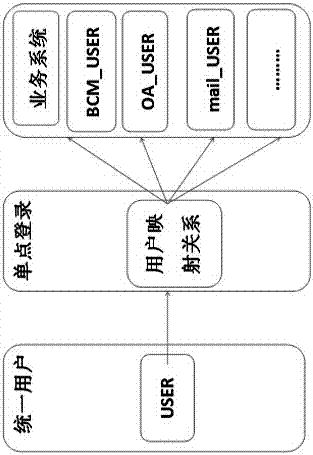
[0059] Such as figure 1 As shown, the method is based on a unified authentication service platform of smart cryptographic keys, with the goal of business system integration, based on smart cryptographic key authentication and PKI technology, and through unified authentication and access control of user identities, various Single sign-on of business systems and integration of information resources, the specific contents include:
[0060] 1. User Management
[0061] Including user information management, user smart password key information, authorized application system, etc. When users access the platform and various application systems, they all use the same credentials (that is, including the user certificate and its hardware protection password PIN), and use digital signature technology to perform identity authentication on the platform to prove the authenticity of their identity;
[0062] 1. User registration
[0063] 1) The user completes the user registration on the plat...
Embodiment 2
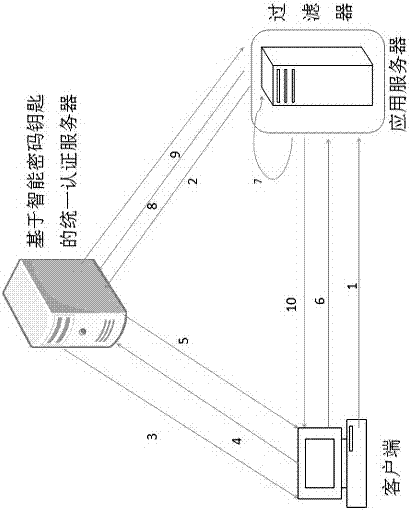
[0124] The method calls the verification service deployed by the unified authentication service platform (CACS) through any one of the following two verification methods, realizes security authentication, and can directly jump to the service platform of the business system:
[0125] 1. The first verification method (POST)
[0126] 1. NET platform implementation
[0127]1) It is necessary to add the Process smart password key SysInfoPage.aspx file and the corresponding Process smart password key SysInfoPage.aspx.cs file to the solution of the business system. In the function, add the processing that your application system needs to do after legal login, and jump to the main interface.
[0128] 2) Refer to excerpts of web.config use cases:
[0129]
[0130]
[0131] 2. JAVA platform implementation
[0132] 1) Add the Process smart password key SysInfoPage.jsp page in the business system, and add the following JAR package references in the LIB folder:
[0133] axis.jar;...
Embodiment 3
[0143] Deployment instructions for the unified authentication service platform:
[0144] 1. Put the CACS folder of the unified authentication service platform and the .CS file inside into the App_Code folder;
[0145] 2. Put the CACS website folder under the WEBPAGE / EXTERNAL folder;
[0146] 3. Modify the Web.Config file
[0147] 1) Add under the configuration section under the configuration section
[0148] 2) Under the configuration section Add two lines under the configuration section:
[0149]
[0150]
[0151] 4. Add the isneedCA(bool) field in the user table
[0152] The user uses a browser to open the login interface, and the login address is http: / / [IP address] / WebPage / External / CACS / Login.aspx
[0153] Enter the user name and password to log in. After successful login, the system will open the CACS main interface.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com