Patents
Literature
34results about How to "Avoid authentication failures" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
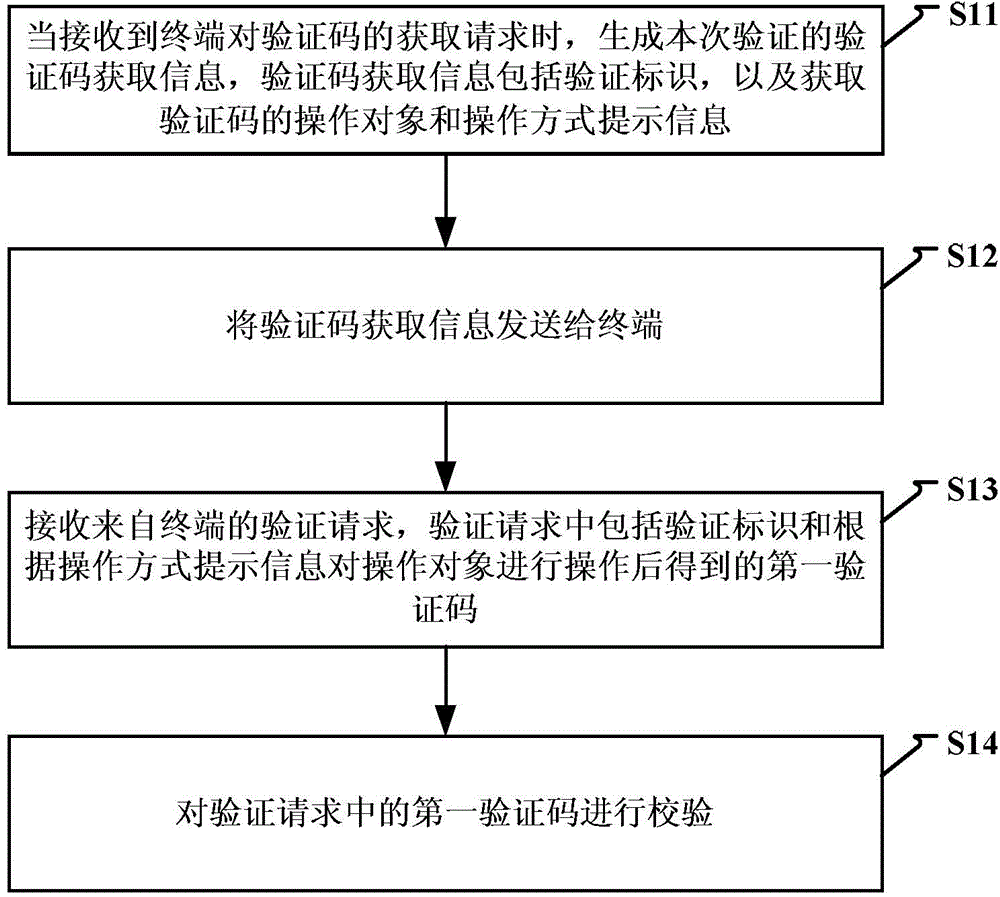
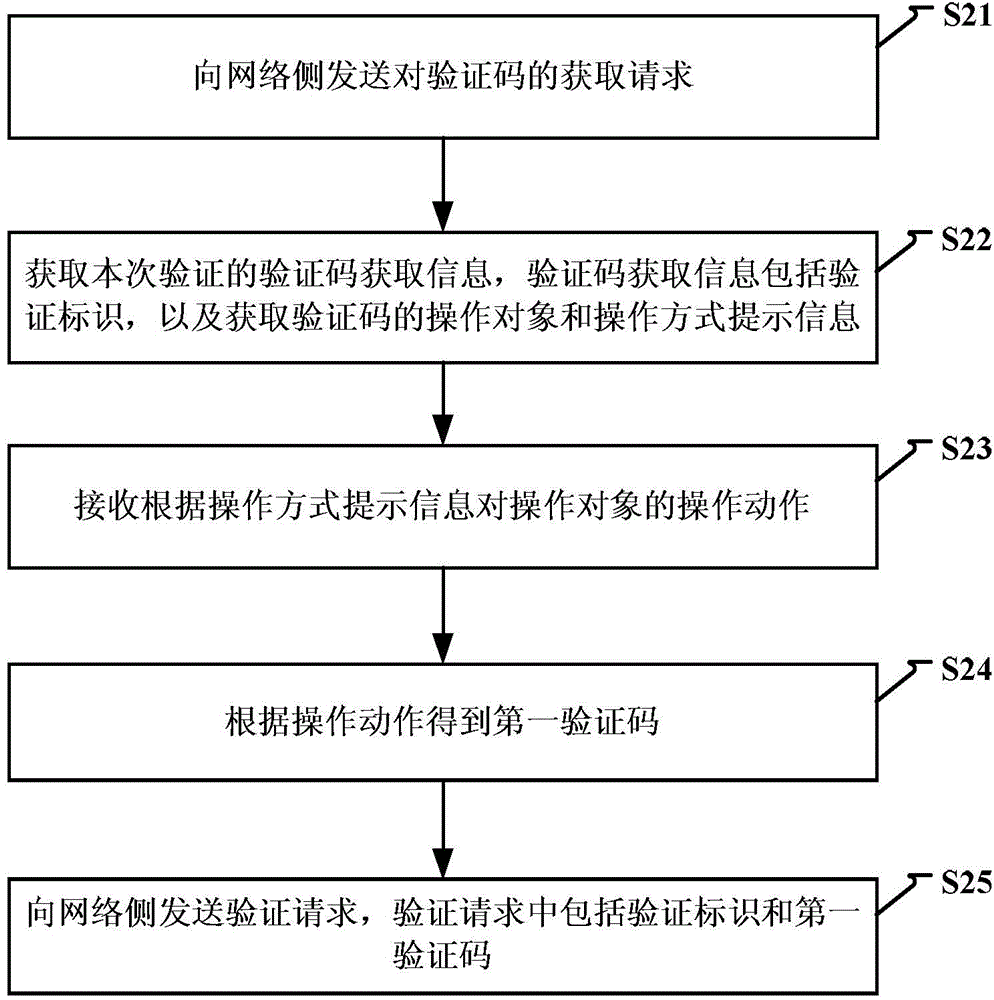
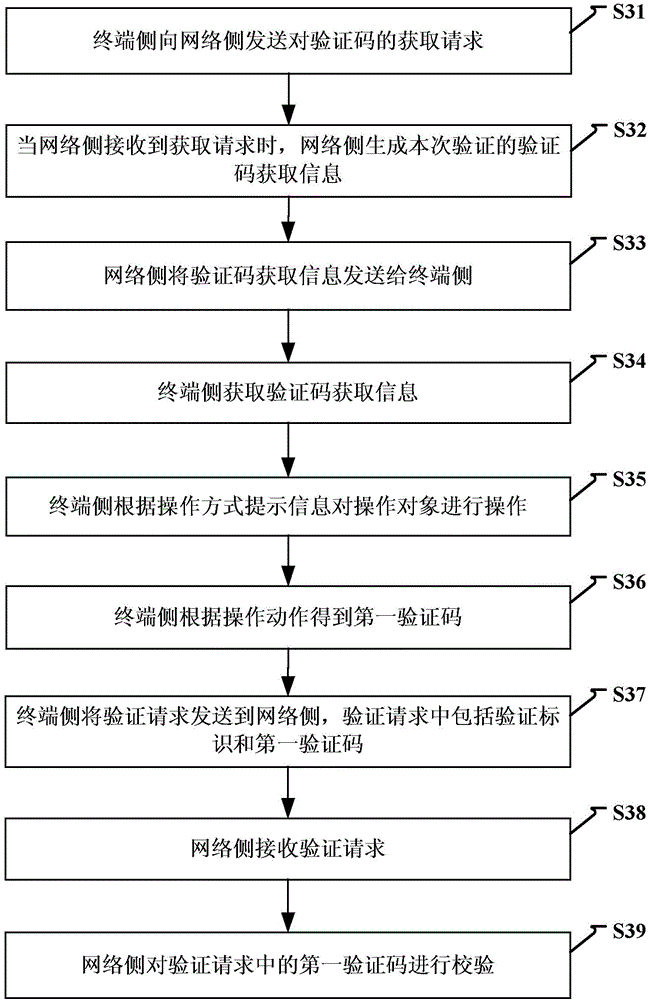
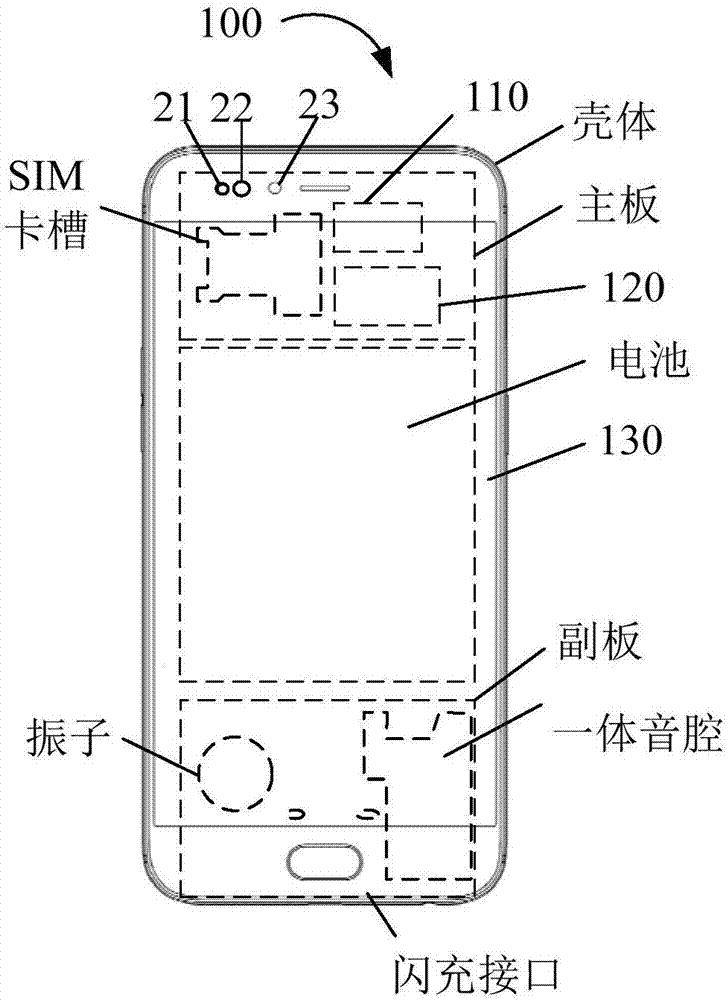
Method and device for identifying by using verification code
InactiveCN104104514AAvoid authentication failuresImprove verification efficiencyUser identity/authority verificationDigital data authenticationObject basedFailure causes
The invention discloses a method and a device for identifying by using a verification code. The method comprises the steps of: when a request of obtaining the verification code from a terminal is received, generating verification code obtaining information including a verification identifier for the verification, and obtaining an operating object of the verification code and operating mode prompting information; sending the verification code obtaining information to the terminal; receiving a verification request from the terminal, wherein the verification request comprises the verification identifier and a first identification code obtained after operation is performed on the operating object based on the operating mode prompting information. A user is unnecessary to input the verification code manually as the operating object is operated based on the operating mode prompting information of the verification code and the result after the operation is verified. Therefore, the verification mode is simplified, verification failure caused by a manual input error of the user is avoided, the verification efficiency of the verification code is improved, and the user experience is increased.
Owner:XIAOMI INC
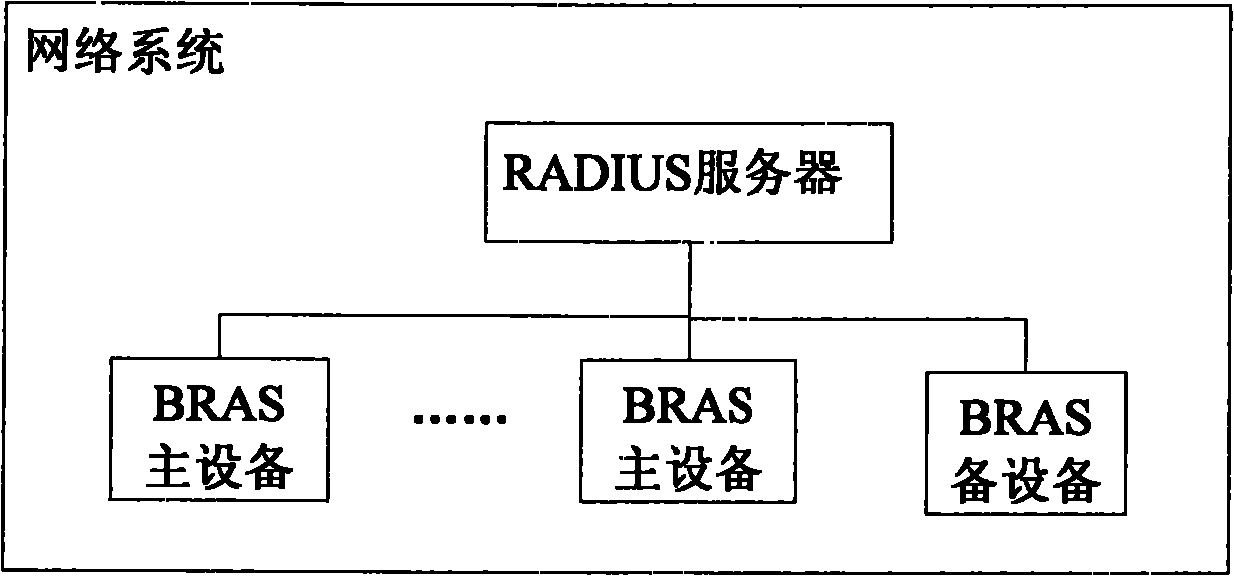
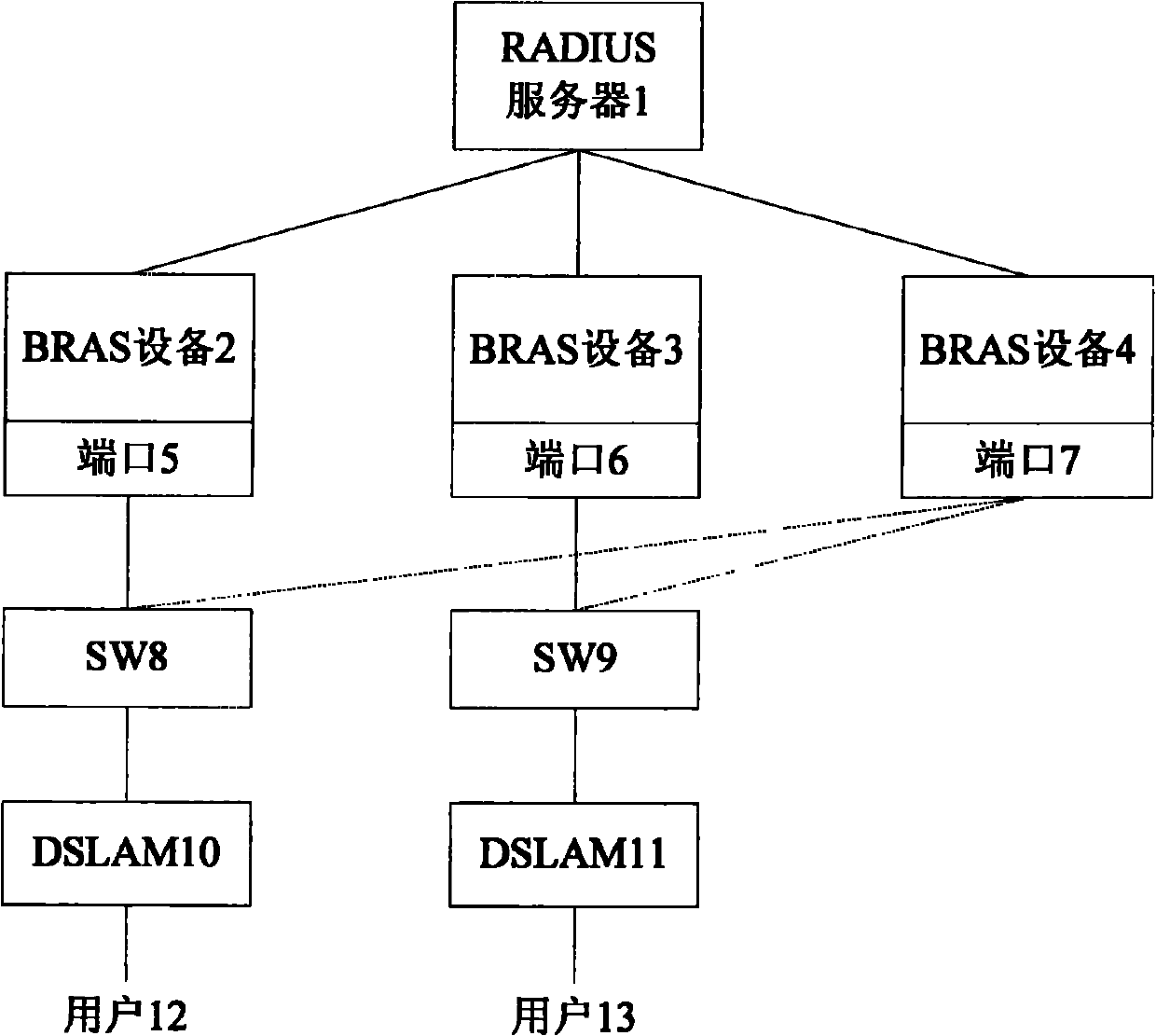
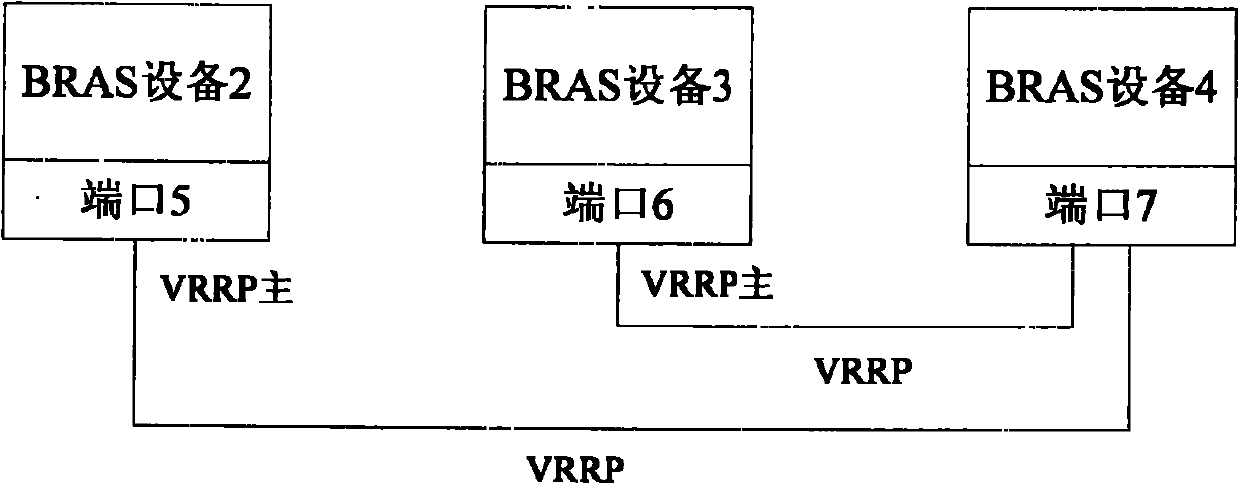
Method for realizing user port positioning in BRAS (Broadband Remote Access Server) multicomputer backup scene and network system
InactiveCN102025476AAvoid authentication failuresError preventionWide area networksNetworked systemAccess line
The invention provides a method for realizing user port positioning in a BRAS (Broadband Remote Access Server) multicomputer backup scene and a network system. The method comprises the following steps of: setting main ports in all backup groups into user interface ports and synchronizing information using the main ports as the user interface ports on a backup port in the backup group, wherein the access port information configured for the user by RADIUS (Remote Authentication Dial In User Service) is the main port of the backup group; and if the main port is abnormal for switching the main port and the backup port, a line is accessed from the corresponding backup port when a user is on line, wherein the BRAS corresponding to the backup port packages an authentication message comprising an DSLAM (Digital Subscriber Line Access Multiplexer) accessed by the user and access line information using the main port as the user access port and transmits the authentication message to the RADIUS so as to solve the problem of authentication failure caused by the change of the positioning line information of the user port after the backup group is switched in the BRAS multicomputer backup scene.
Owner:ZTE CORP
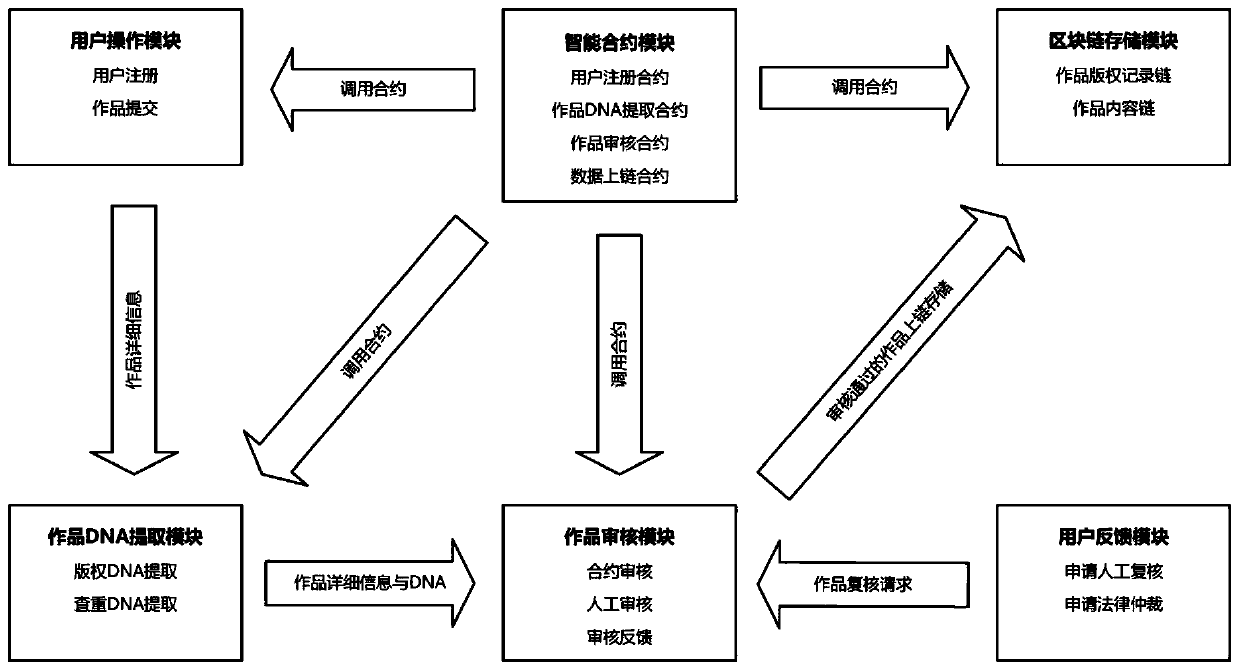
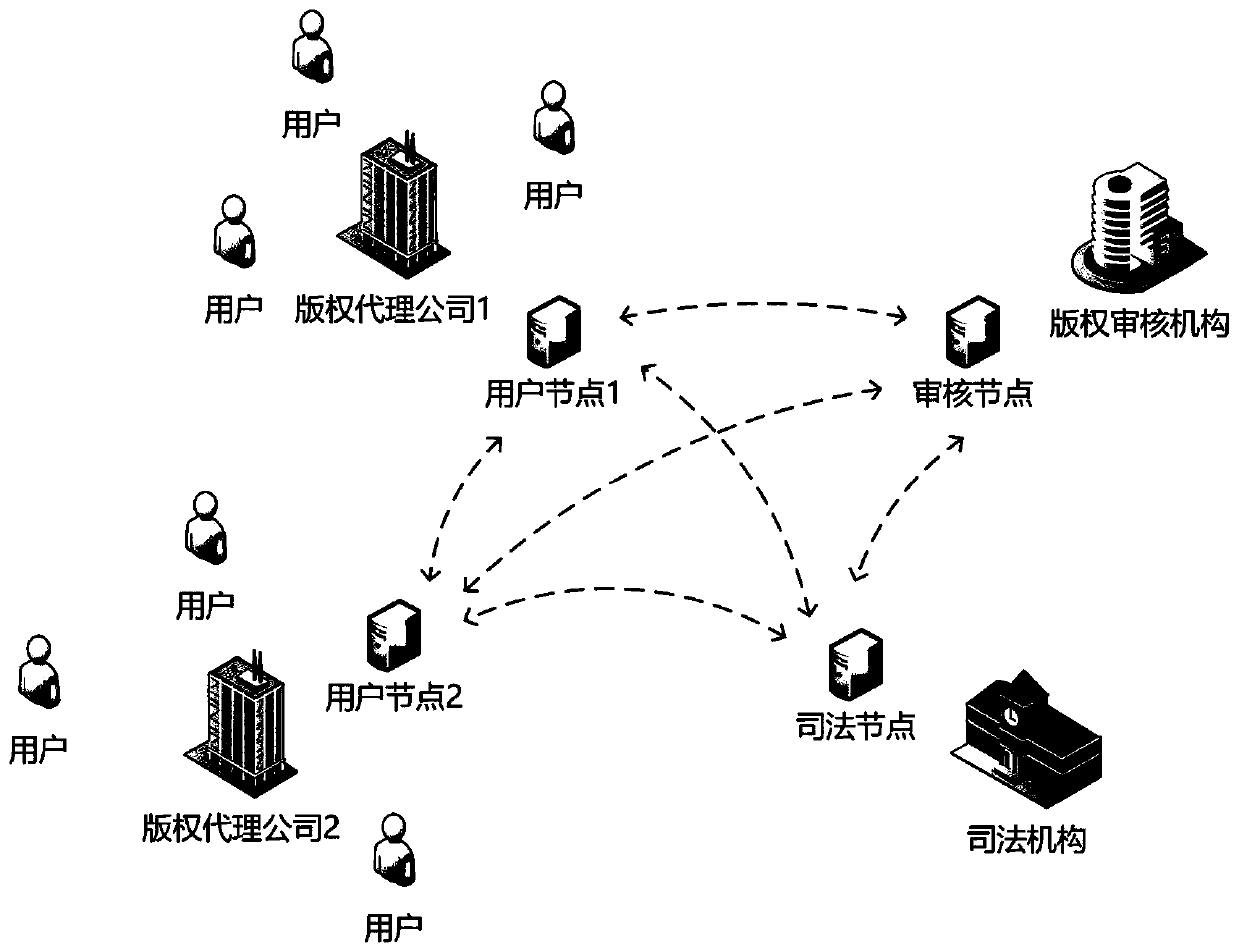
Blockchain copyright protection system and method based on double chains
InactiveCN111538963AImprove authentication efficiencyAvoiding the Problem of Obtaining Copyright CertificationEncryption apparatus with shift registers/memoriesPublic key for secure communicationOperating systemDouble chain
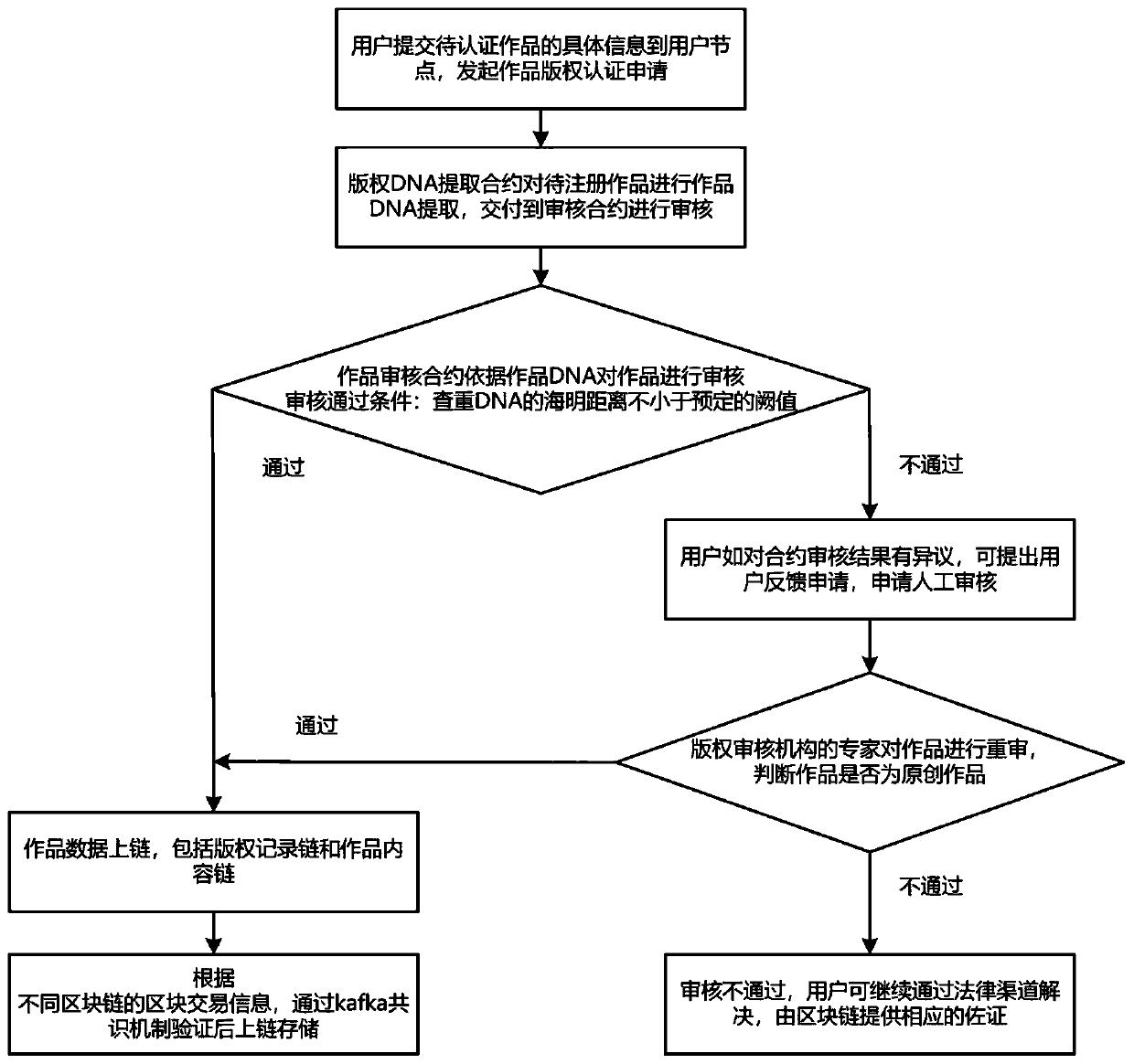
The invention discloses a blockchain copyright protection system and method based on double chains. The blockchain copyright protection system comprises a user operation module, a work DNA extractionmodule, a work auditing module, an intelligent contract module, a blockchain storage module and a user feedback module. The system combines the blockchain technology with the improved Simhash algorithm to realize a duplicate checking detection function before the work applies for the copyright, provides a manual detection verification service for a user, ensures the originality of the chained work, and solves the problem of low auditing efficiency of a copyright registration institution at the same time. A double-chain storage mode is adopted for work copyright information storage. Different nodes are added into channels of corresponding chains, transparency of work transaction information is guaranteed, privacy of work content information is also guaranteed, the problem that work contentis tampered and work copyright DNA cannot be successfully verified due to database storage is avoided, and double-chain storage guarantees data reading and writing efficiency of a block chain system.
Owner:铭数科技(青岛)有限公司
Identity authentication method, system and device based on block chain and computer equipment
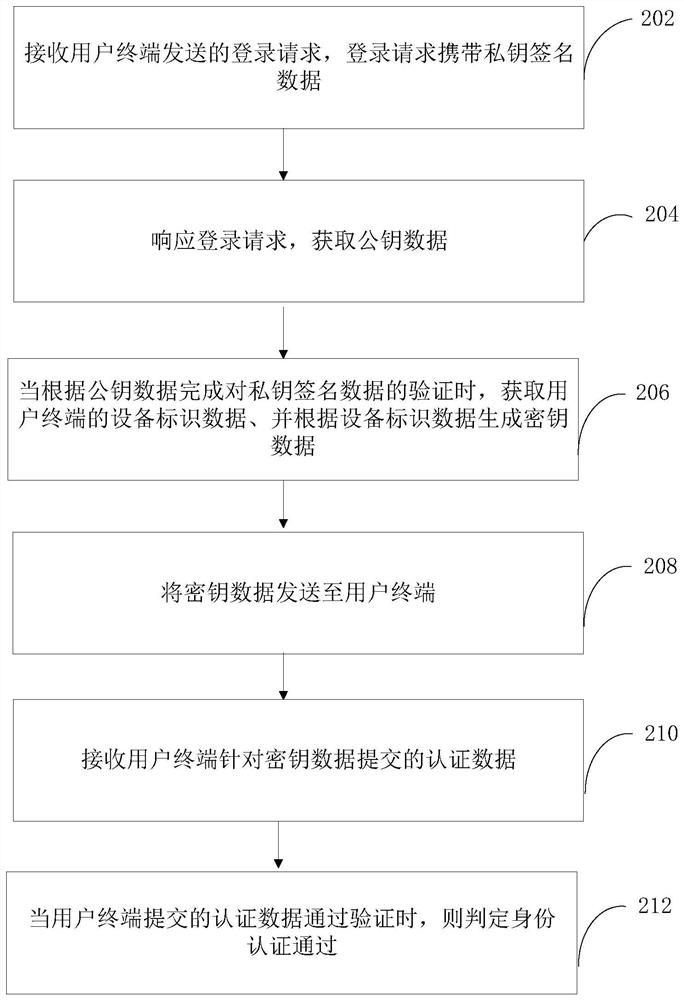
ActiveCN111949953AAvoid authentication failuresImprove rigorDigital data authenticationBlockchainComputer equipment
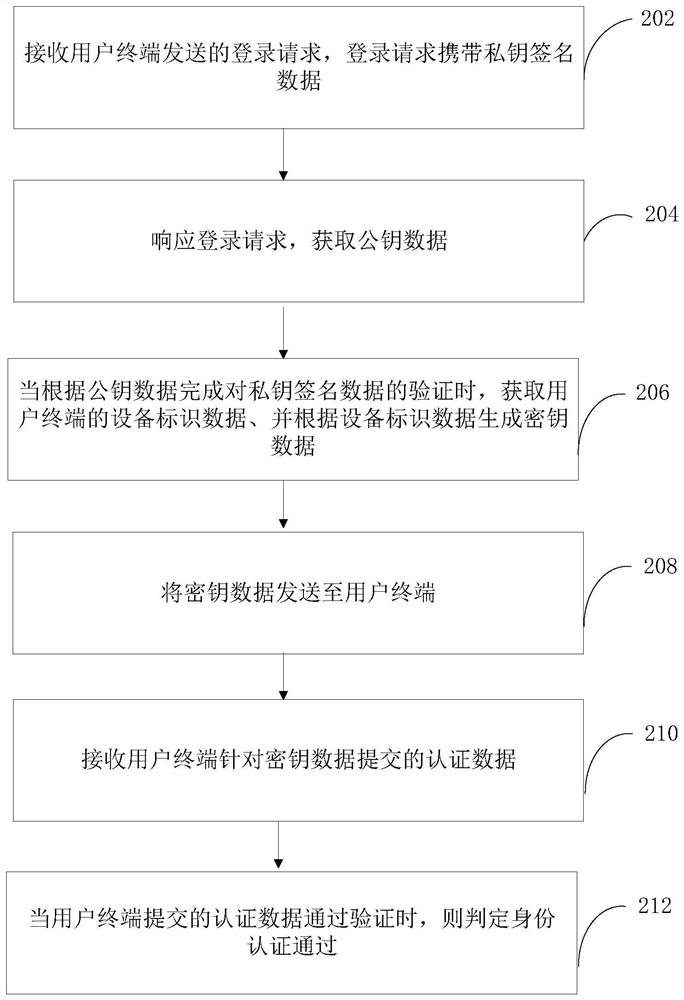
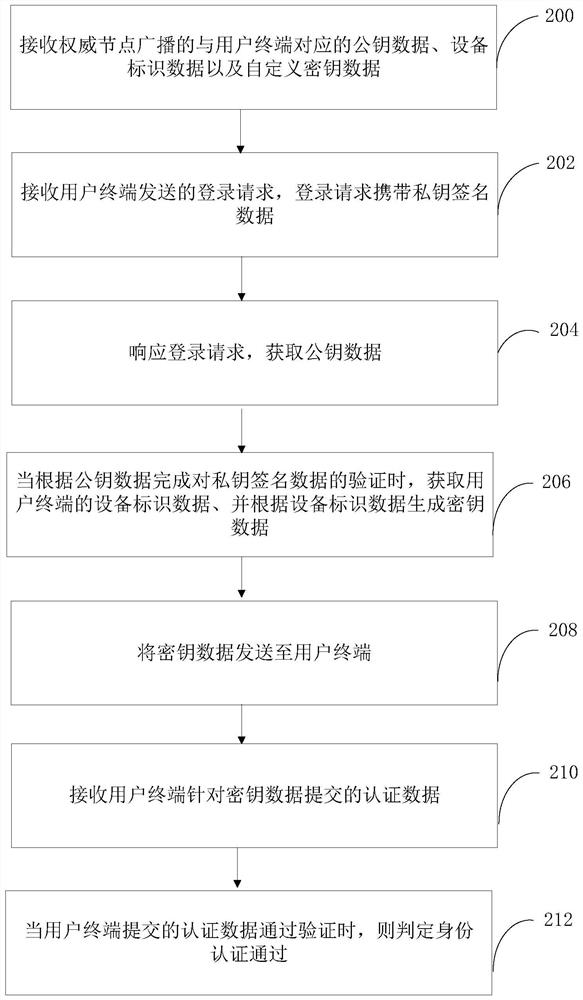
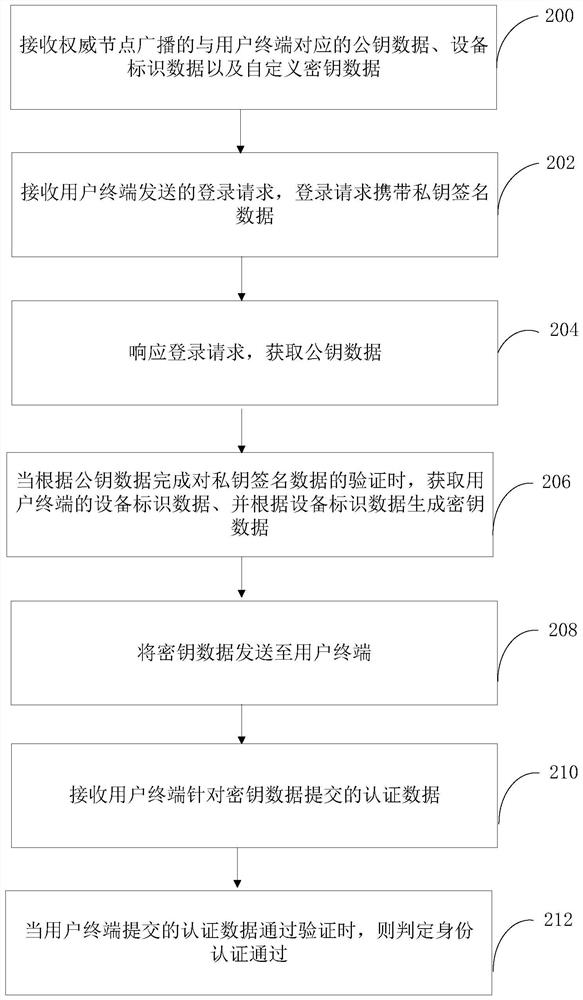
The invention relates to an identity authentication method, system and device based on a block chain, computer equipment and a storage medium. The method comprises the following steps: receiving a login request sent by a user terminal, the login request carrying private key signature data; responding to the login request, obtaining public key data; obtaining equipment identification data of the user terminal when verification of the private key signature data is completed according to the public key data, and generating key data according to the equipment identification data, and sending the key data to the user terminal, receiving authentication data submitted by the user terminal for the key data, and when the authentication data submitted by the user terminal passes the verification, determining that the identity authentication is passed. According to the scheme, decentration is carried out in a blockchain mode, so that authentication failure caused by downtime of the central node is avoided; by introducing a double-authentication mechanism of equipment authentication and key data based on equipment identification data and private key authentication, behaviors such as signaturedenial can be avoided, the identity authentication accuracy is improved, and the data security is guaranteed.
Owner:卓尔智联(武汉)研究院有限公司
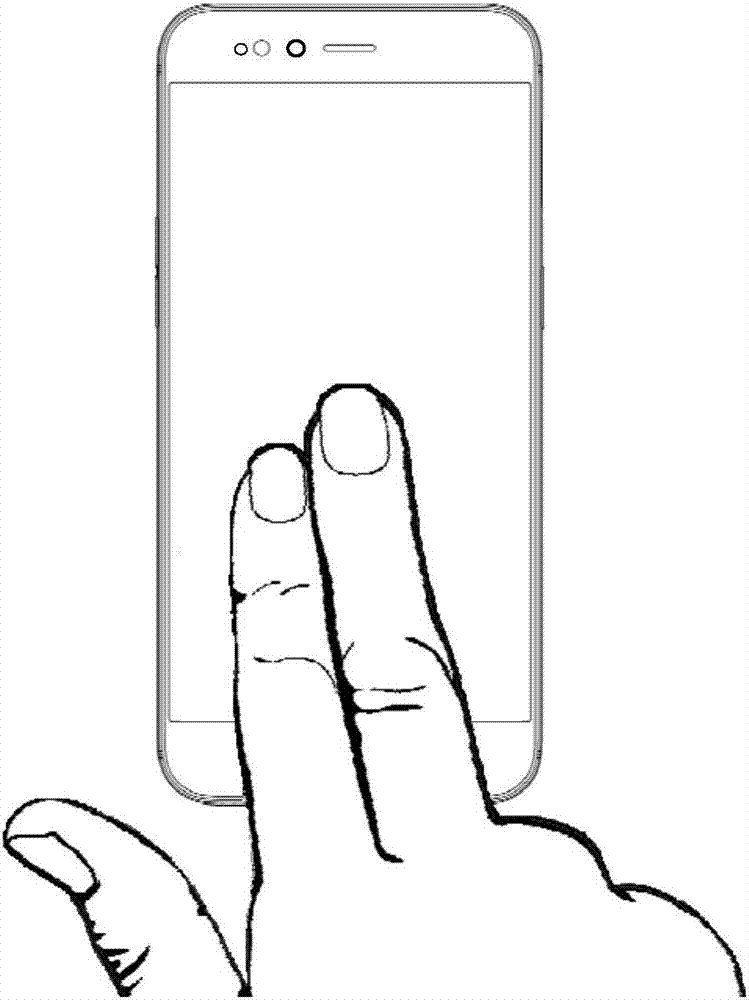
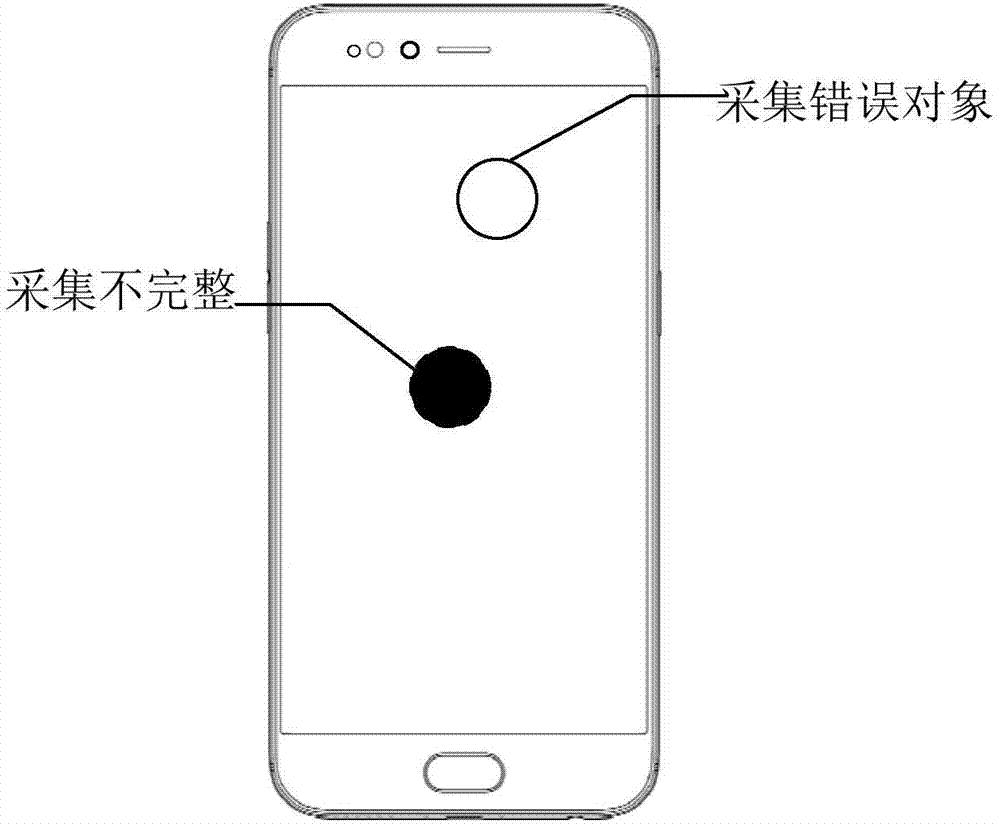
Unlock control method and related products
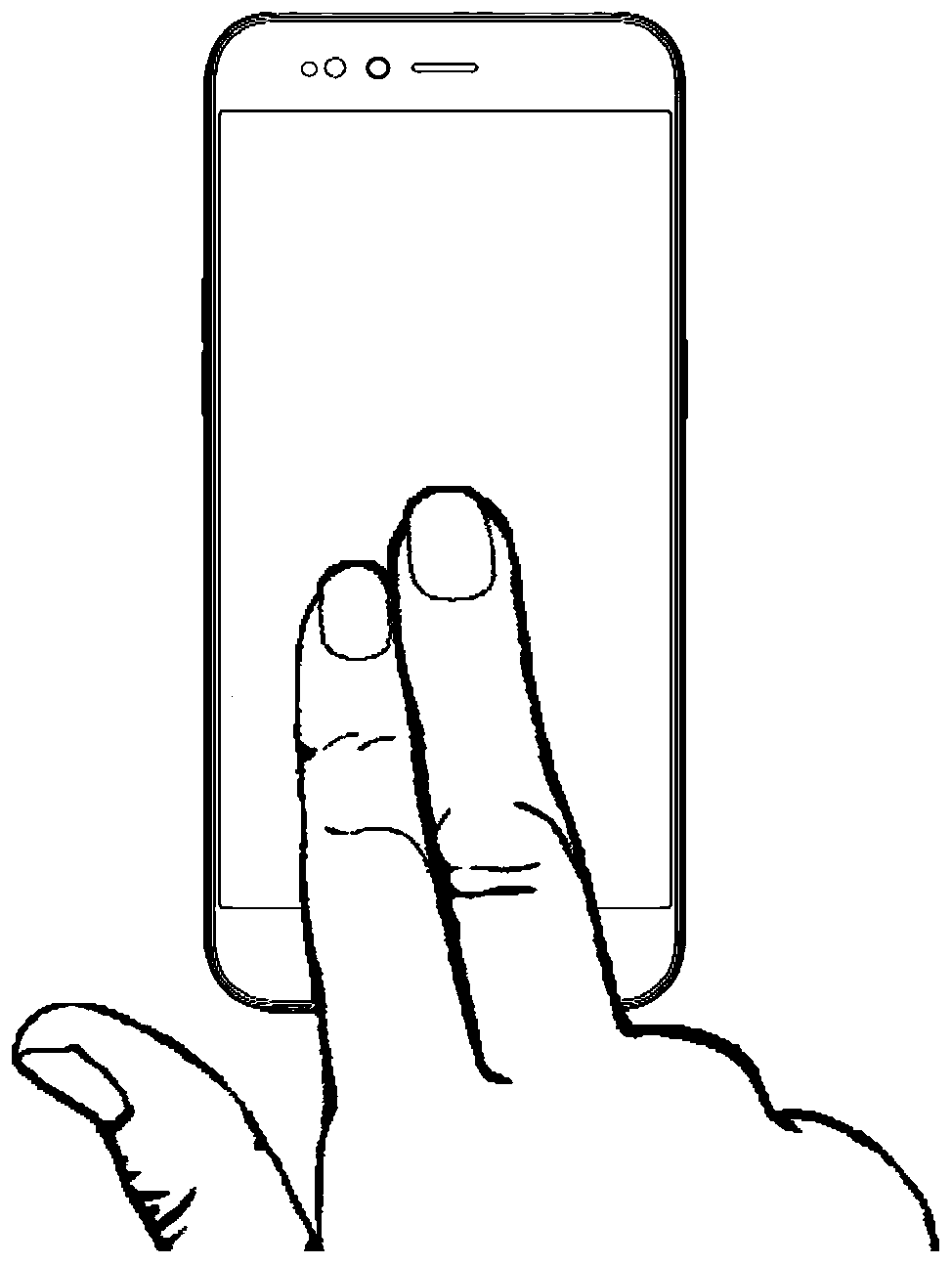
ActiveCN107506629AIncrease success rate and flexibilityAvoid authentication failuresDigital data authenticationSubstation equipmentComputer visionFingerprint
Embodiments of the present invention disclose an unlock control method and related products. The method comprises: obtaining M fingerprint images by using a fingerprint information collecting module when detecting touch operations of M fingers on the touch screen; verifying the M fingerprint images; and when verification of L fingerprint images in the M fingerprint images fails, obtaining a target biometric recognition mode from Q types of pre-stored biometric recognition modes. By virtue of the technical scheme of the present invention, the success rate and flexibility of verification can be improved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
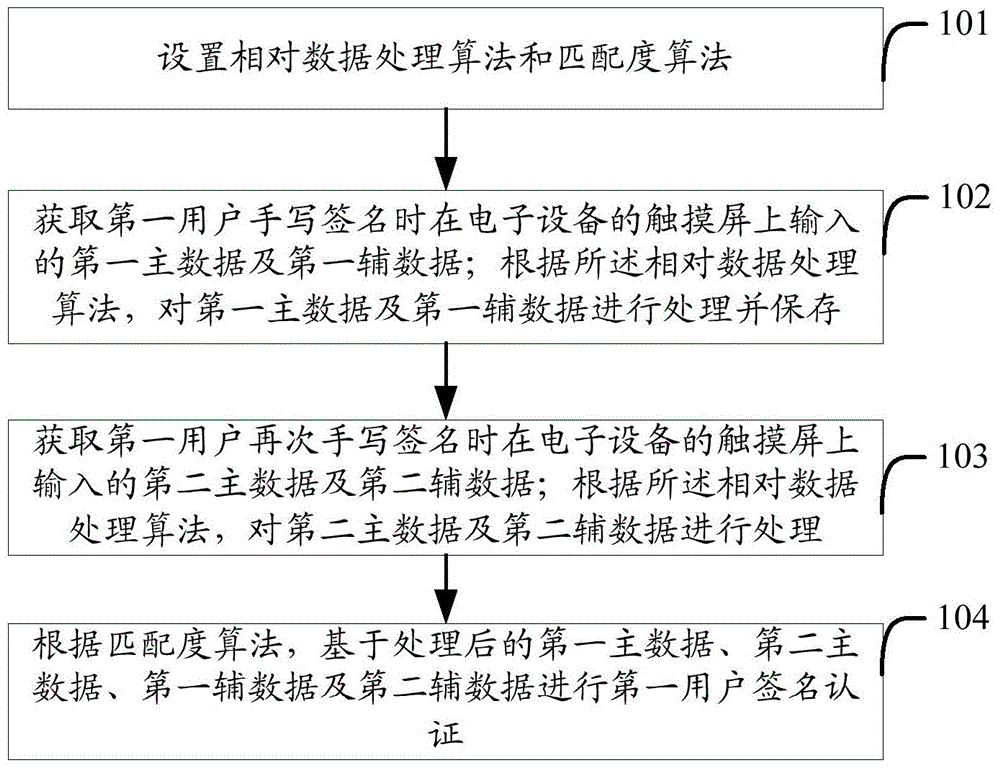
Method and device for achieving handwritten signature verification
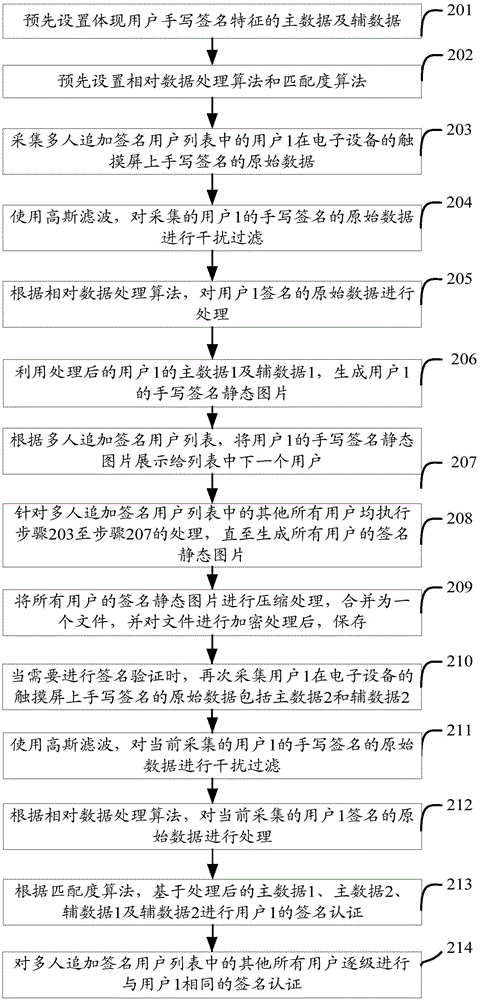
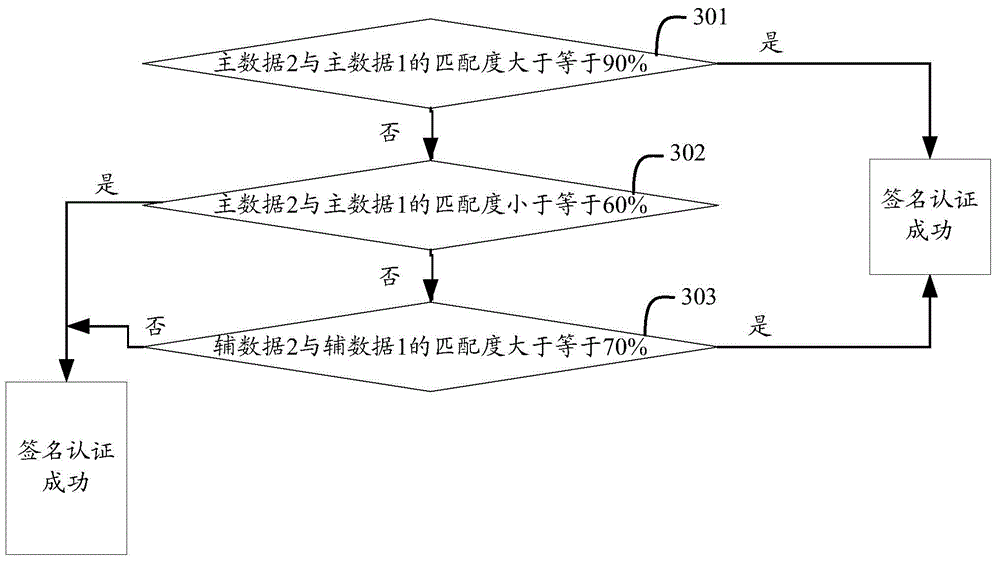
InactiveCN104463147AImprove securityAvoid human interferenceCharacter and pattern recognitionAlgorithmMaster data
The invention provides a method and device for achieving handwritten signature verification. The method includes the following steps of setting a relative data processing algorithm and a matching degree algorithm, obtaining first master data and first auxiliary data input to a touch screen of electronic equipment when a first user handwrites a signature, processing and storing the first master data and the first auxiliary data according to the relative data processing algorithm, obtaining second master data and second auxiliary data input to the touch screen of the electronic equipment when the first user handwrites the signature again, processing the second master data and the second auxiliary data according to the relative data processing algorithm, and conducting first user signature verification according to the matching degree algorithm on the basis of the processed first master data, the processed second main data, the processed first auxiliary data and the processed second auxiliary data, wherein the master data comprise the movement track of the signature. The method and device for achieving handwritten signature verification can improve handwritten signature verification safety.
Owner:INSPUR COMMON SOFTWARE
Recognition method and device for attack message and core device
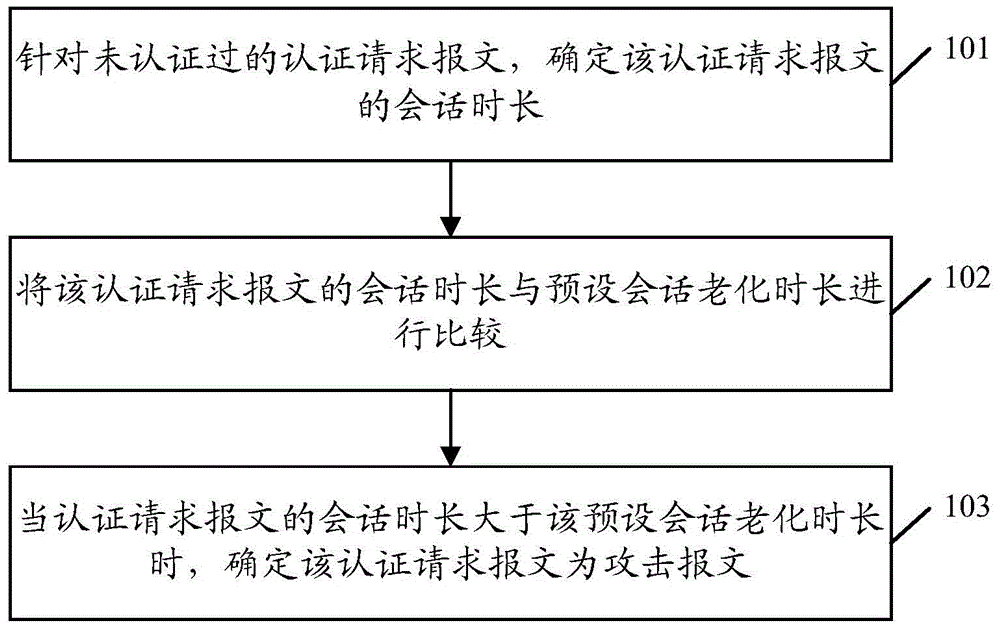
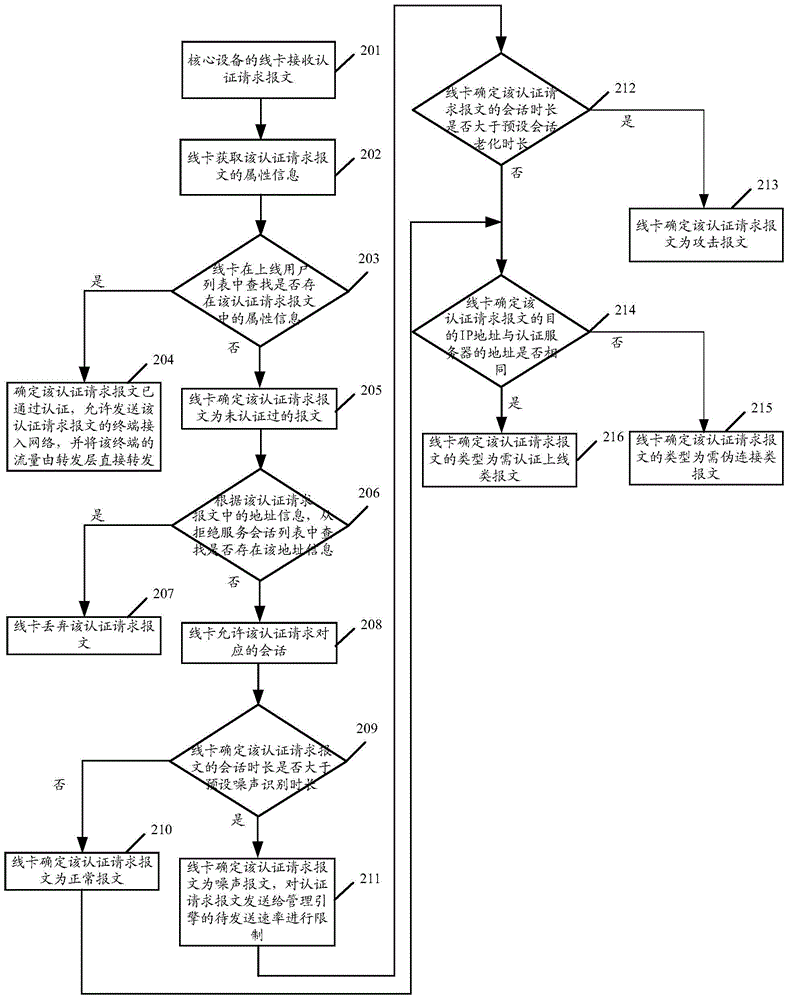
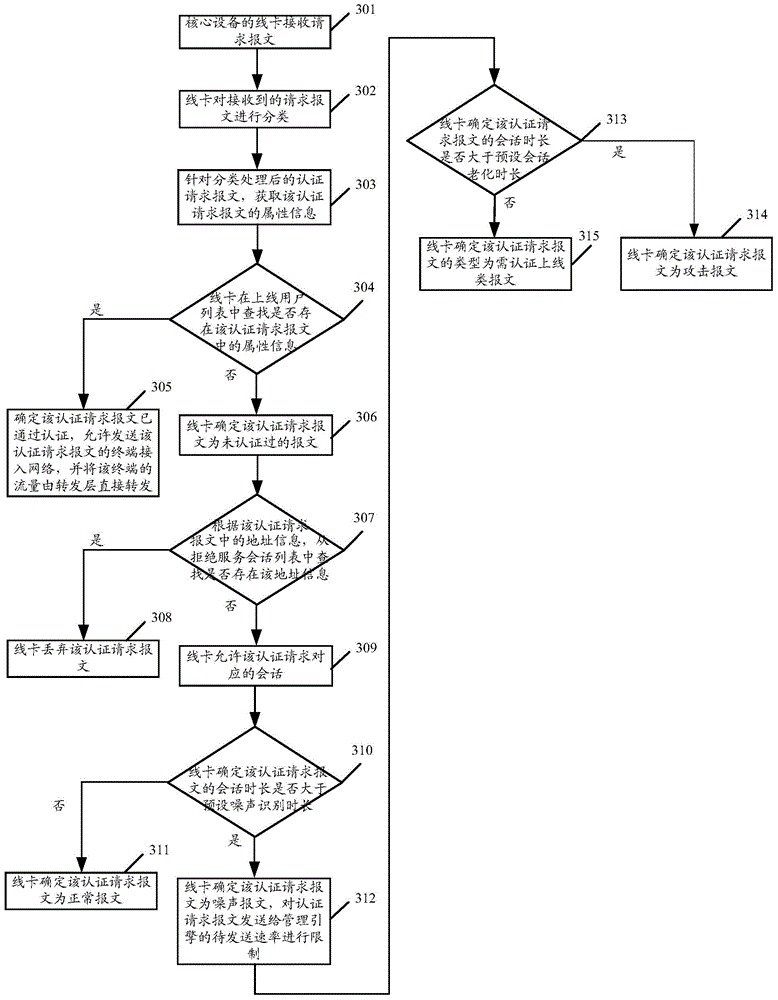
ActiveCN104601578AImprove processing efficiencyAvoid authentication failuresTransmissionAuthentication
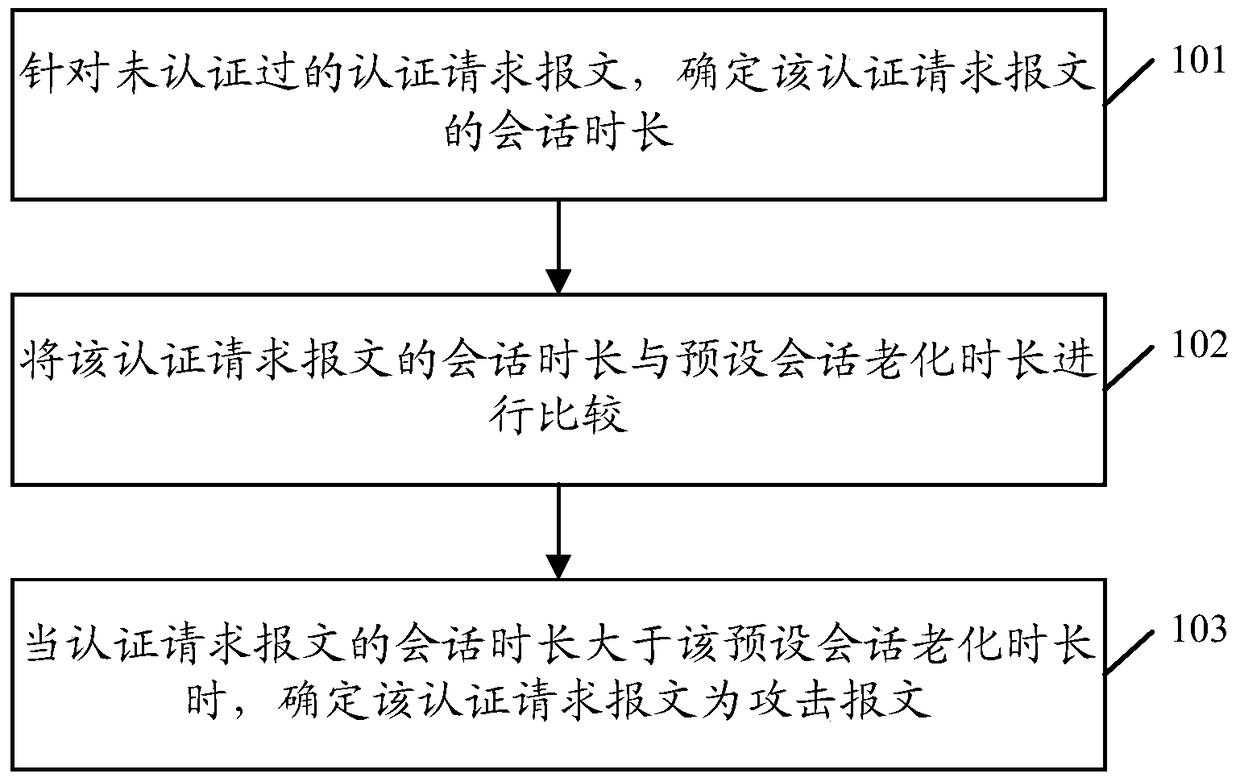
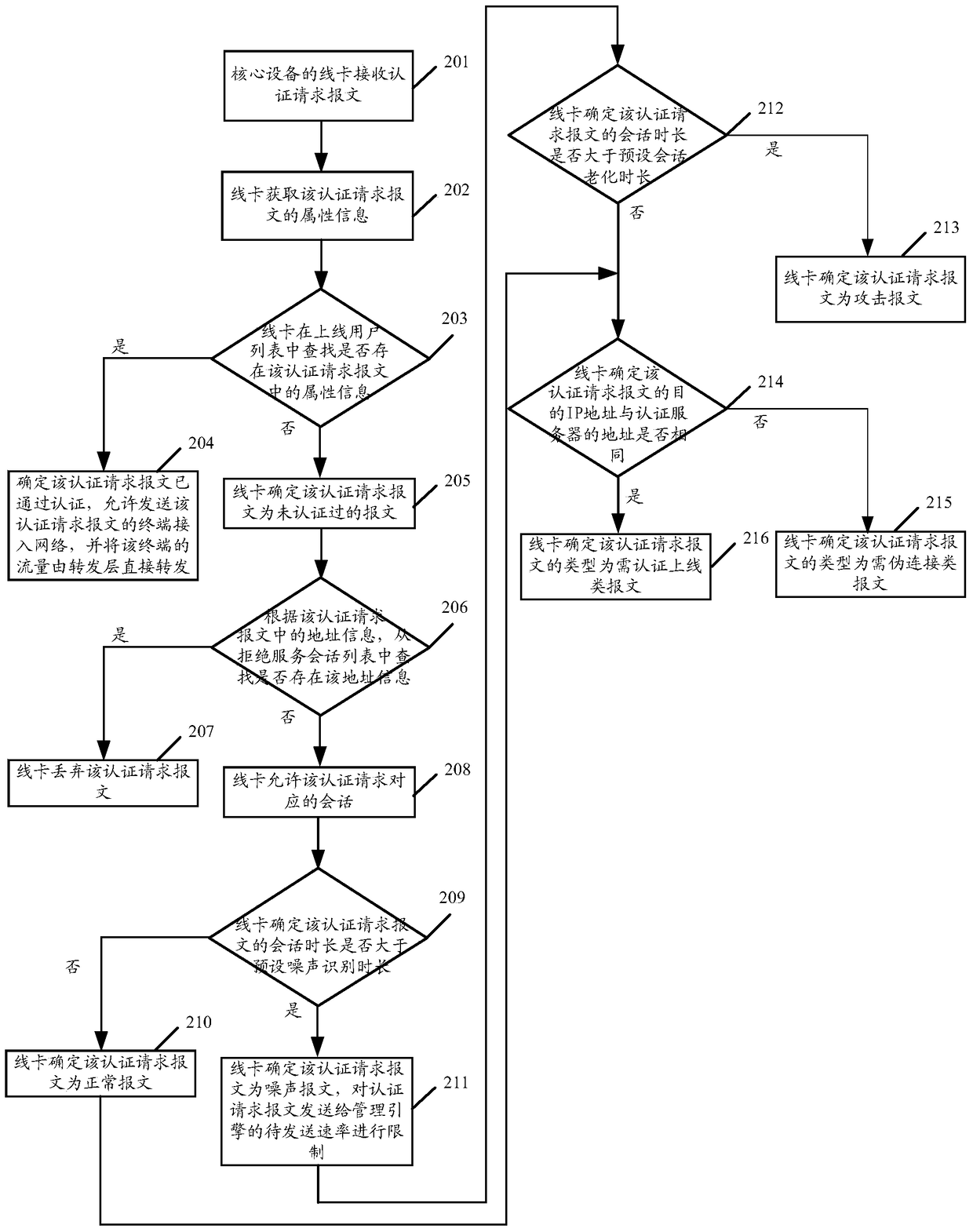
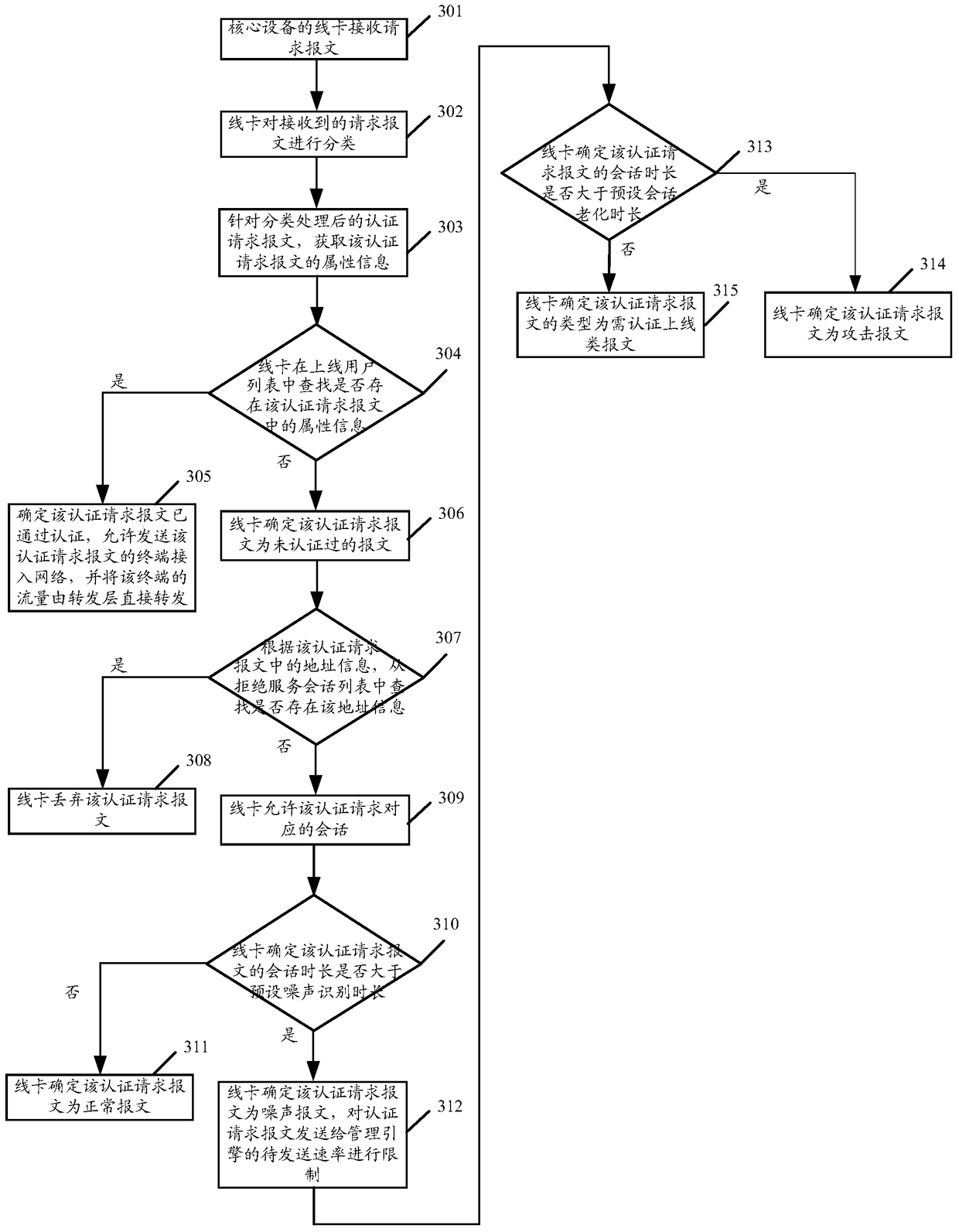
The invention discloses a recognition method and device for an attack message and a core device. The method comprises the steps of determining the length of conversation of authentication request message without being authenticated; comparing the length of the conservation of the authentication request message with the preset ageing length of the conservation; determining that the authentication request message is the attack message when the length of the conservation of the authentication request message exceeds the preset ageing length of the conservation. According to the scheme, the method has the advantage that the authentication request handling efficiency can be increased.
Owner:RUIJIE NETWORKS CO LTD
Method for realizing registering in IP multi-media subsystem
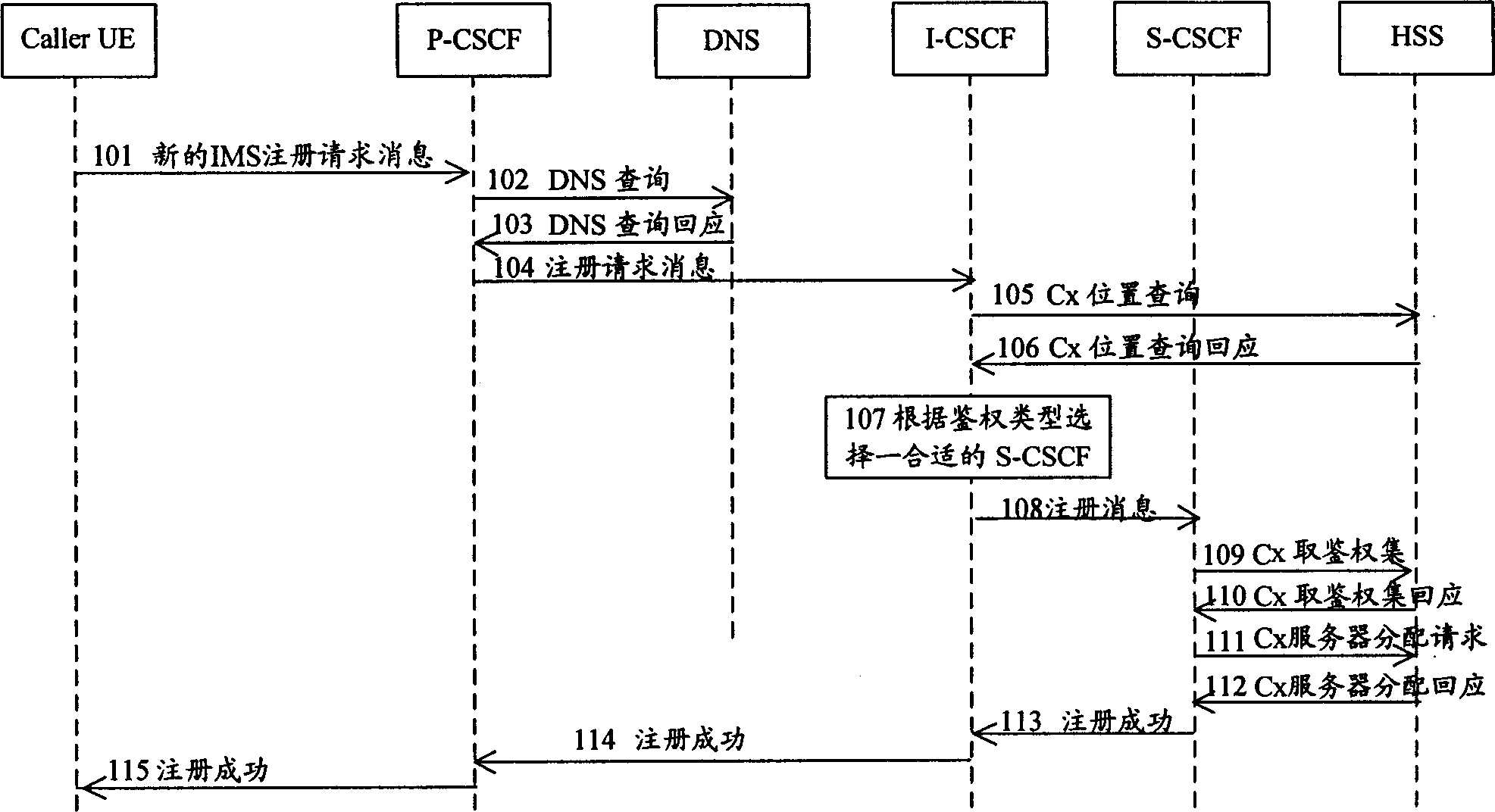
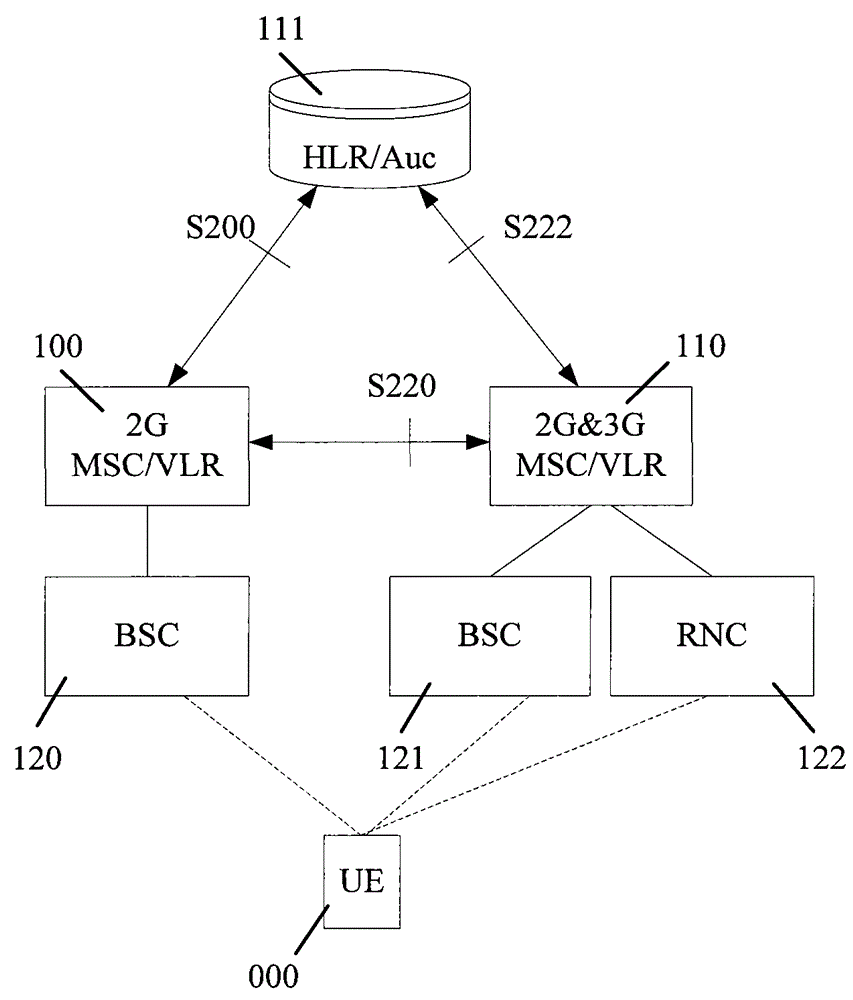
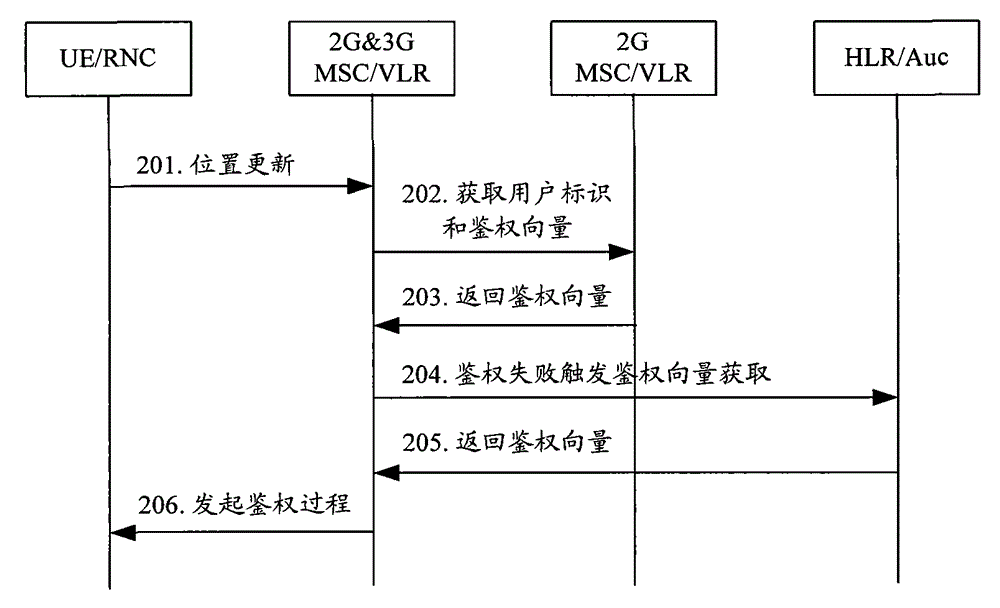
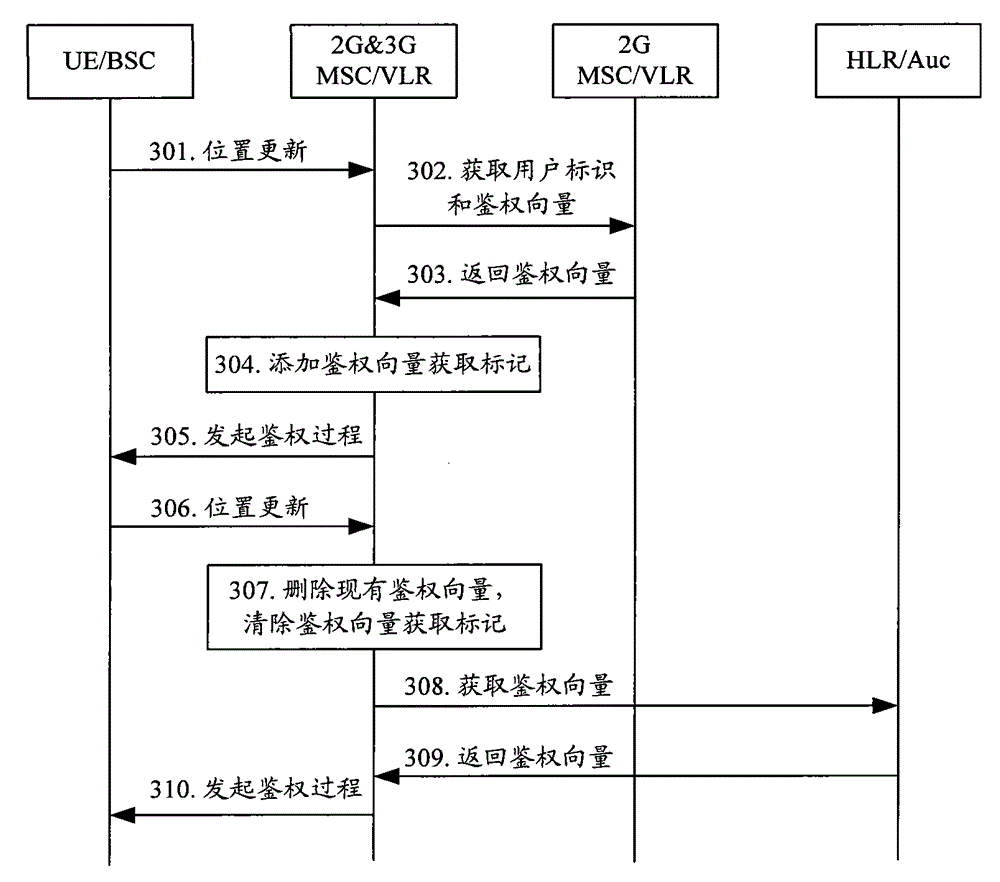
InactiveCN1852556AGuaranteed matchAvoid authentication failuresRadio/inductive link selection arrangementsTransmissionComputer compatibilityAuthentication
Key points of the method are that after obtaining information of S-CSCF capability set capable of providing service for the UE from HSS, I-CSCF determines type of authentication capability supported by UE of initiating request; based on coincidence relation between S-CSCF id in already setup data list and the said type of authentication capability supported, as well as obtained information of S-CSCF capability set capable, I-CSCF selects S-CSCF set, which can satisfy operation capability required by UE, and supports type of authentication capability supported by UE, and chooses one S-CSCF from the selected S-CSCF set; then, according to current method to continue next registration process. The invention guarantees match of types of authentication supported between UE of initiating request and S-CSCF. Features are: small modification to current technical scheme and good compatibility to current technique.
Owner:HUAWEI TECH CO LTD
Combined address identification system and method, and automatic identification device
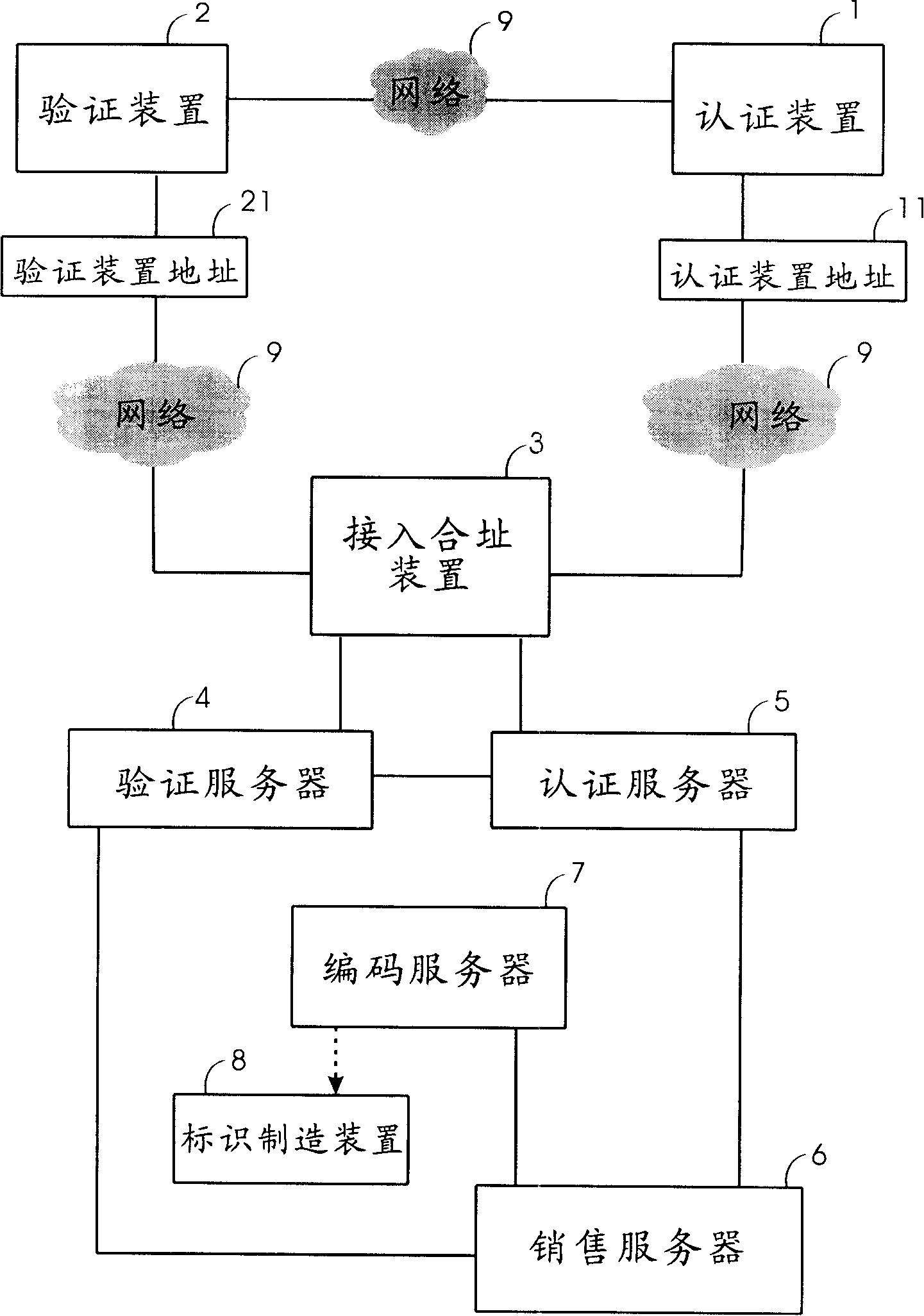
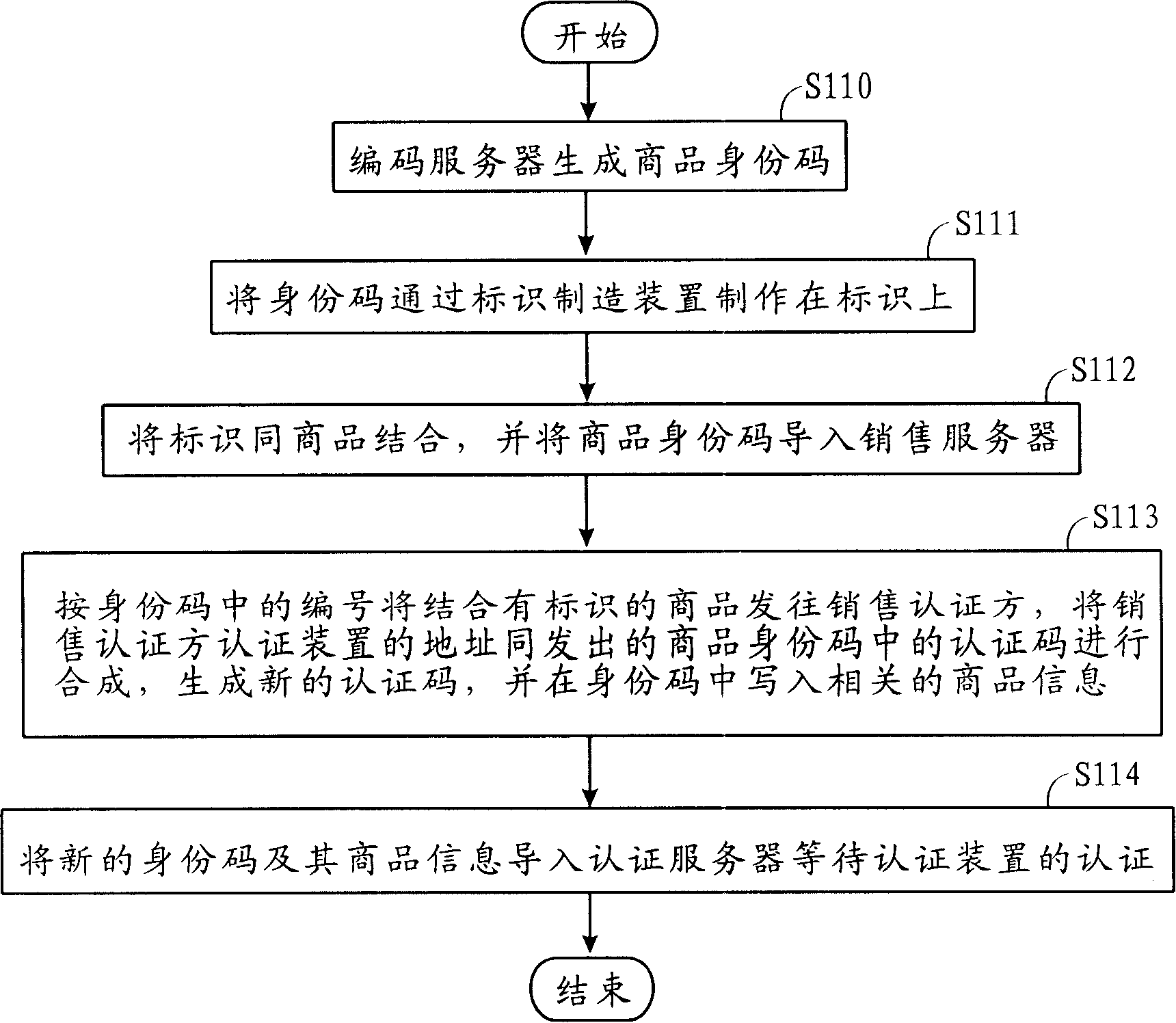
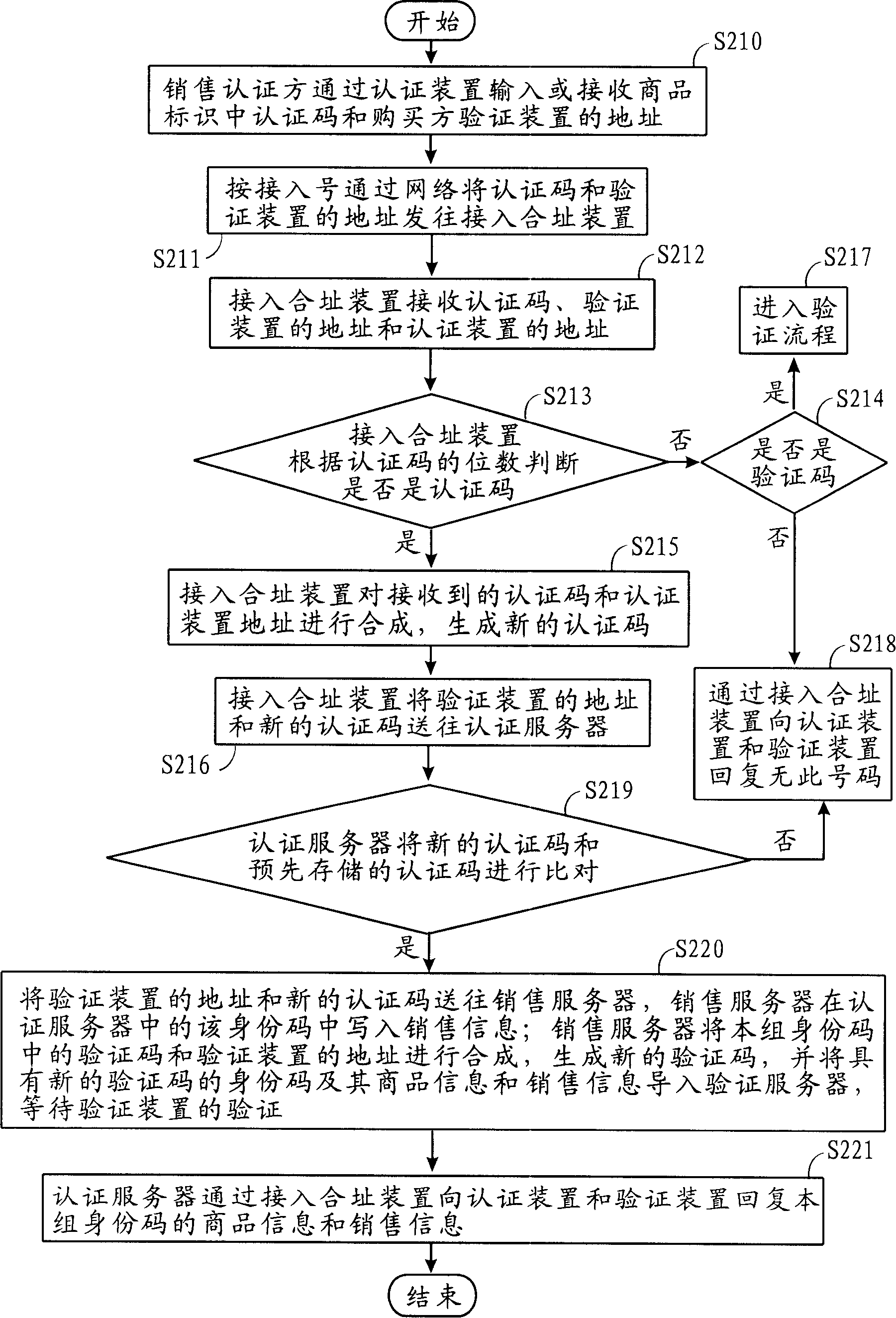
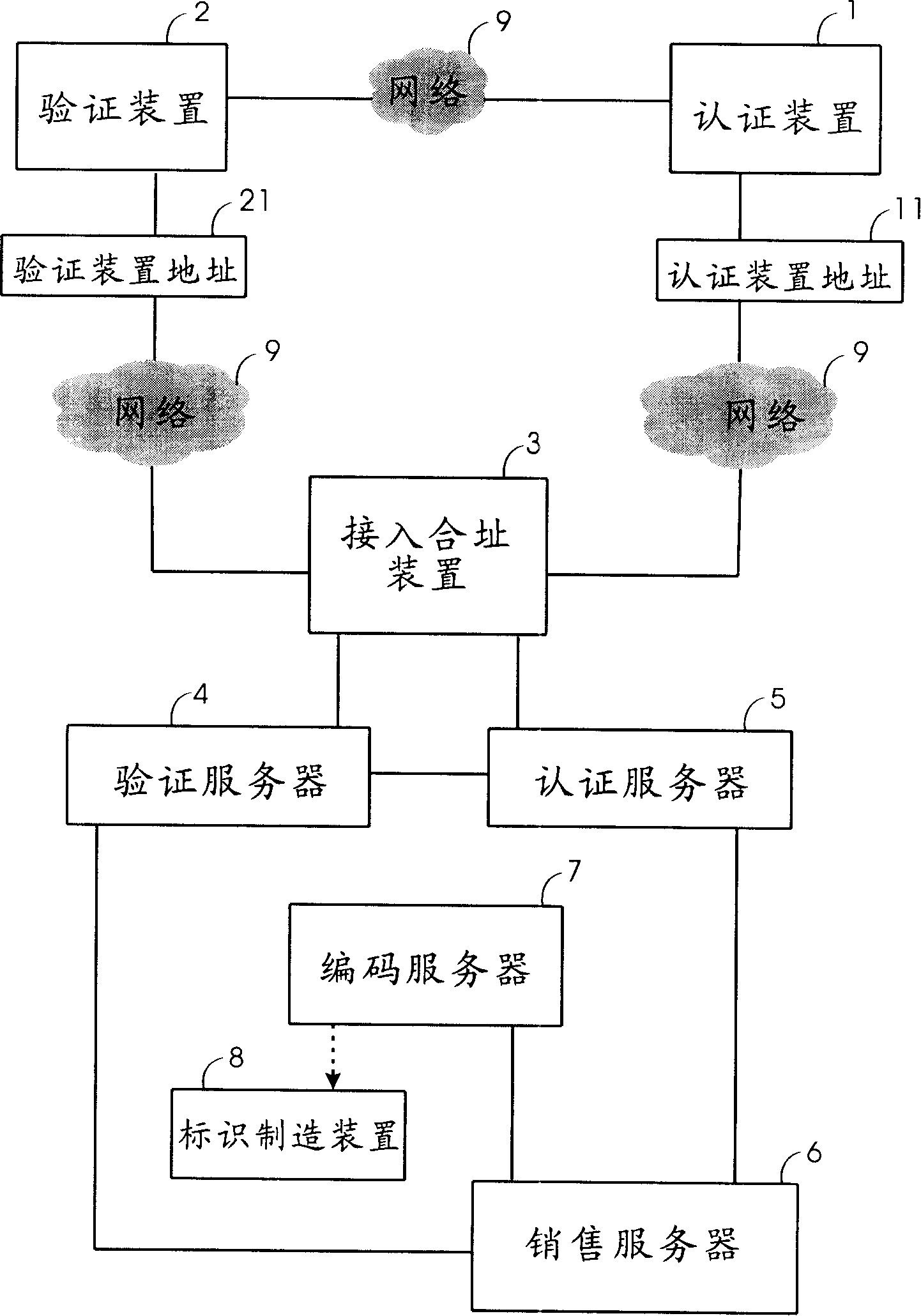
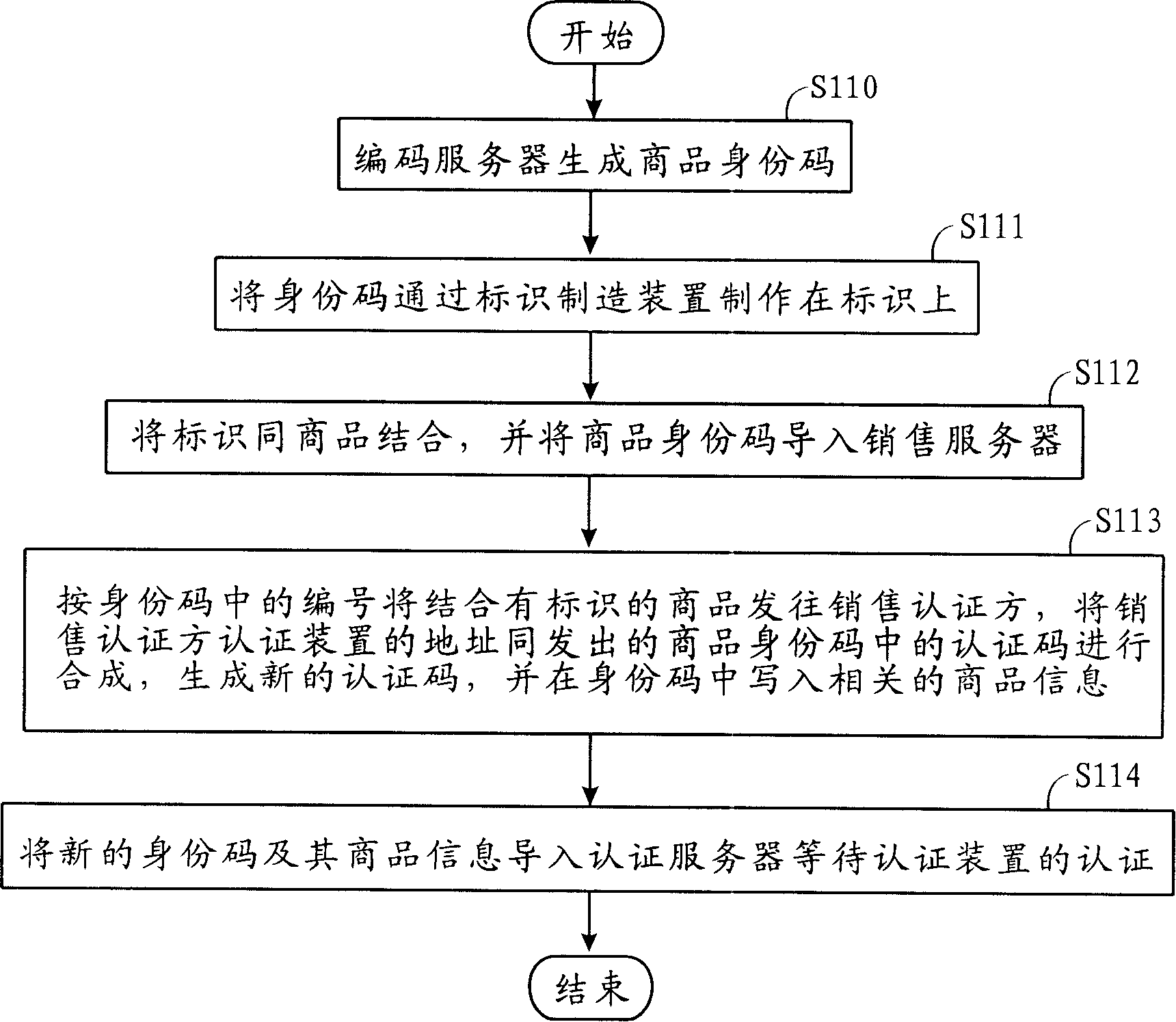
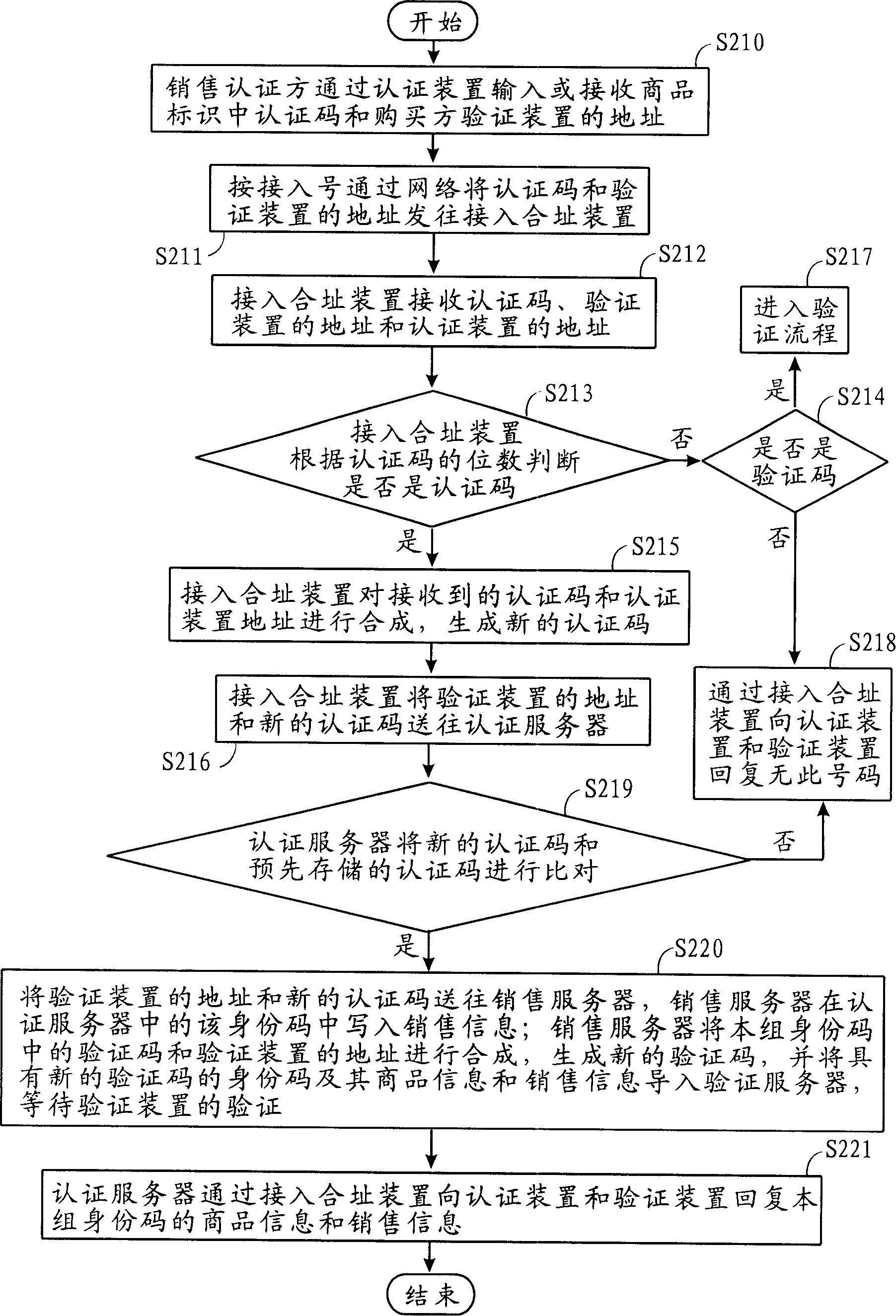
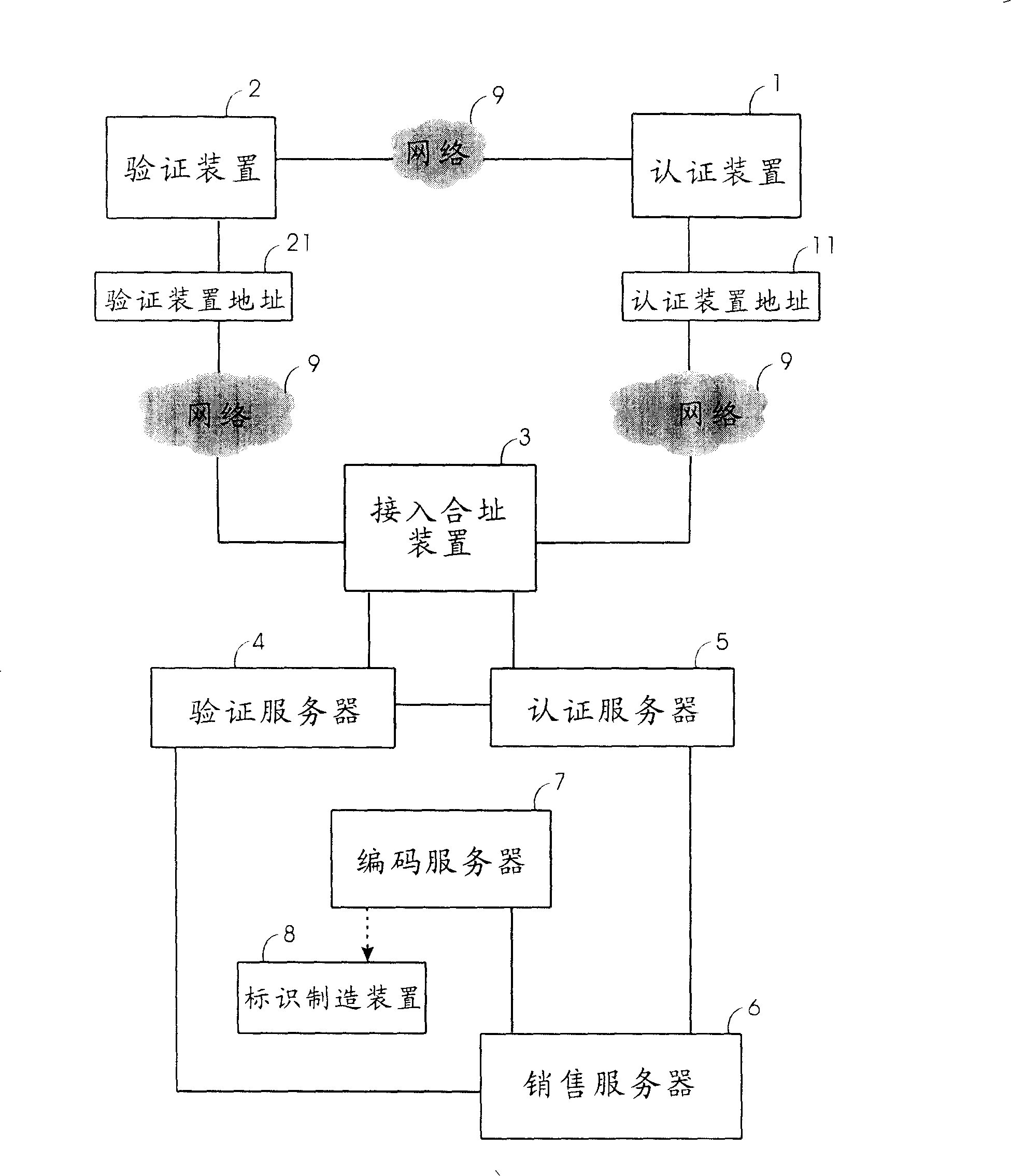
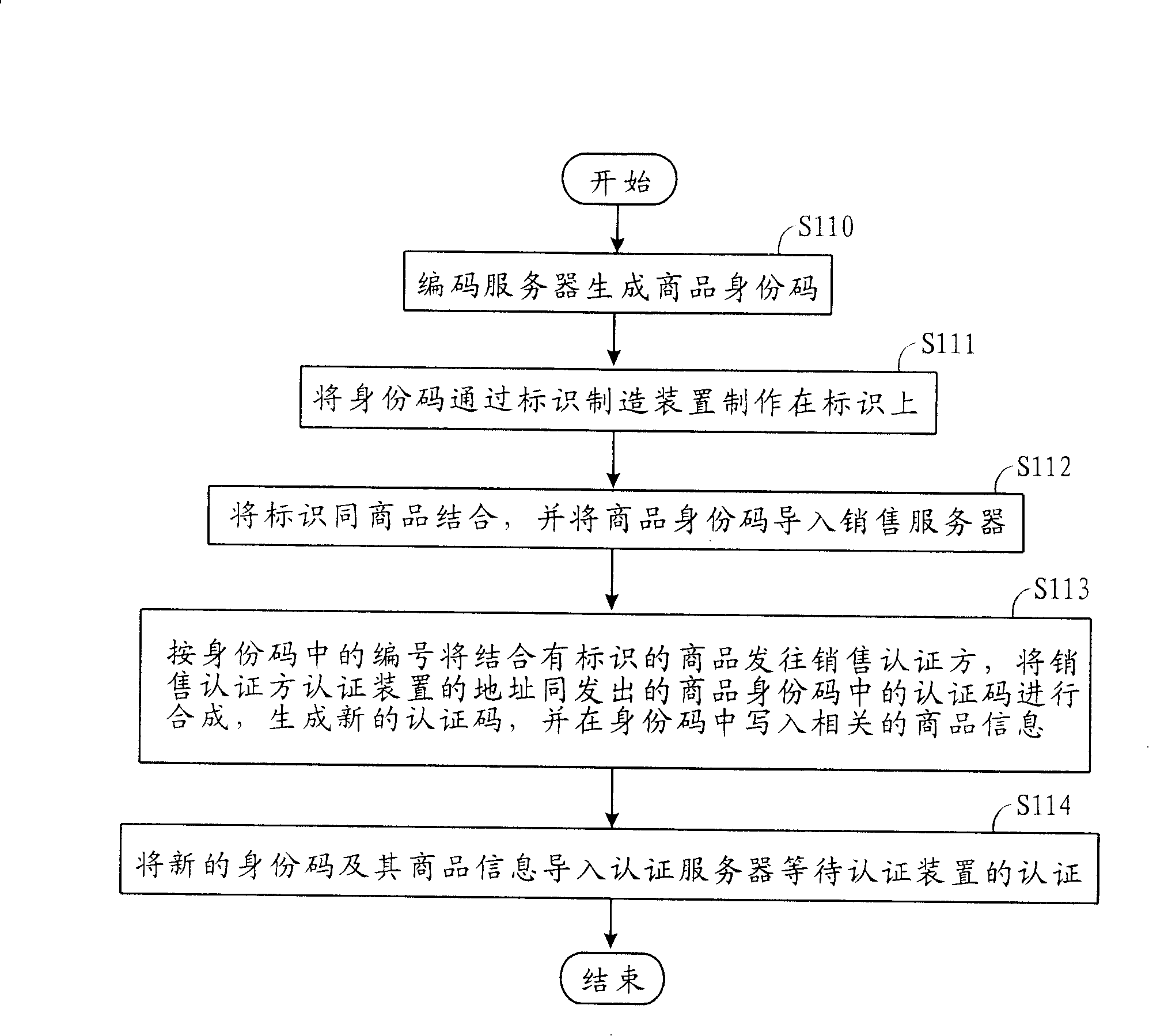
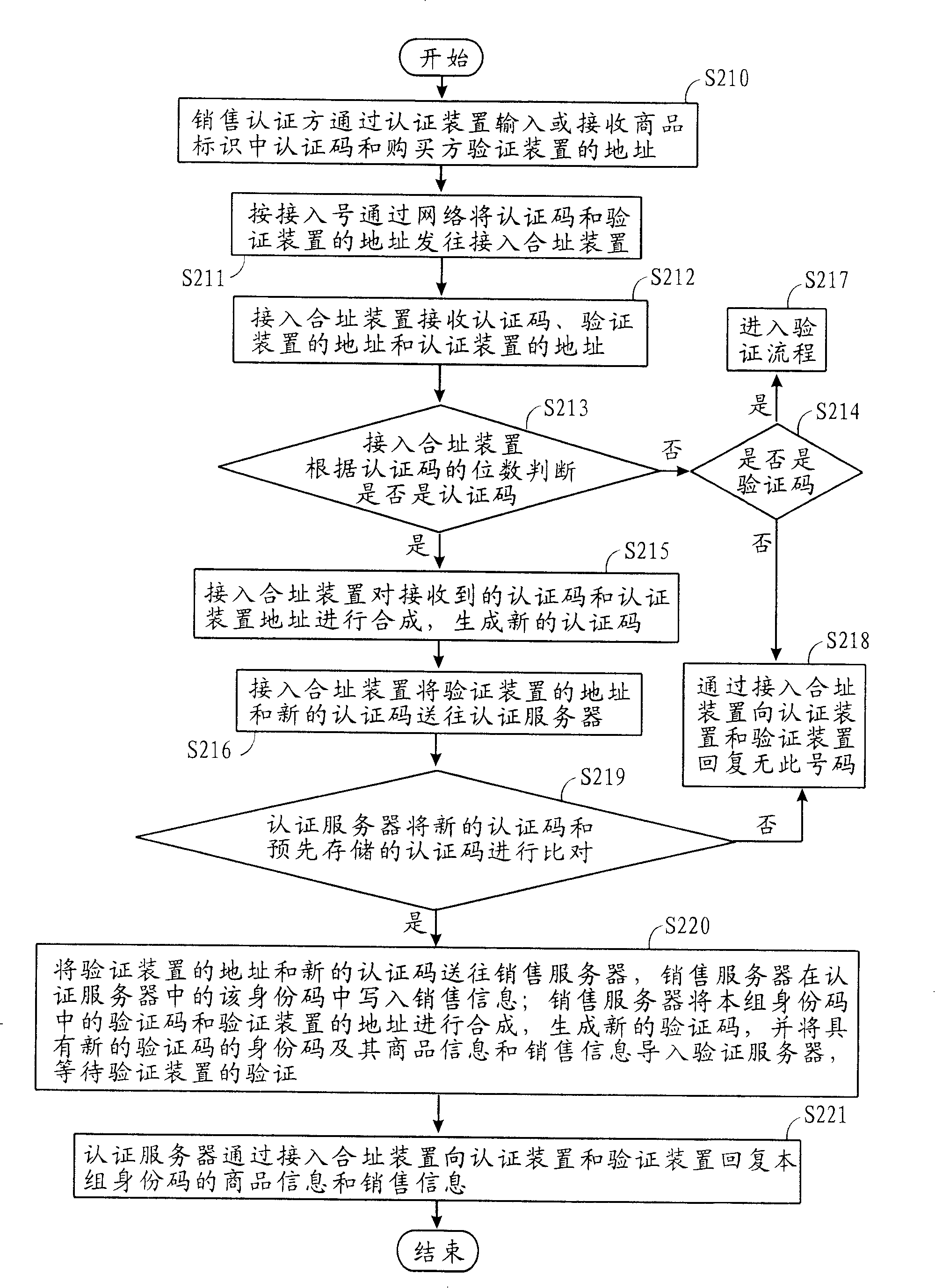
InactiveCN1700246AAvoid circulationAvoid salesCo-operative working arrangementsBuying/selling/leasing transactionsIdentification deviceAuthentication server
The invention relates to an amalgamating address quotation system and method and auto quotation device. Commodity sales send quotation code and supervising device address to switch-in amalgamating address device by quotation device; switch-in amalgamating address device compounds quotation code and quotation device address to generate new quotation code and compares it with quotation code of quotation server, then outputs the result to quotation device and supervising device to assure commodity property; Commodity sales send commodity supervising code to switch-in amalgamating address device by supervising device; switch-in amalgamating address device compounds supervising code and supervising device address to generate new supervising code and compares it with supervising code of supervising server to assure commodity property; commodity producer receives buyer's supervising device address by quotation device, and writes sale information to engage in commodity sales.
Owner:刘小鹏
Automatic identification device for combined address identification
InactiveCN1700247AAvoid circulationAvoid salesCo-operative working arrangementsSpecial data processing applicationsAuthentication serverIdentification device
The invention relates to an auto quotation device used to do amalgamating address quotation. It receives commodity ID quotation code of commodity tag by the auto receiving device and receives quotation device address by network interface card and network device; it sends the quotation code and supervising device address to switch-in amalgamating address device; switch-in amalgamating address device compounds quotation code and quotation device address to generate new quotation code and compares it with quotation code of quotation server, then outputs the result to auto quotation device and buyer's supervising device to assure commodity property and receives commodity information and sale information of quotation commodity which is sent from switch-in amalgamating address device.
Owner:刘小鹏
Information authentication method, electronic equipment and network side equipment
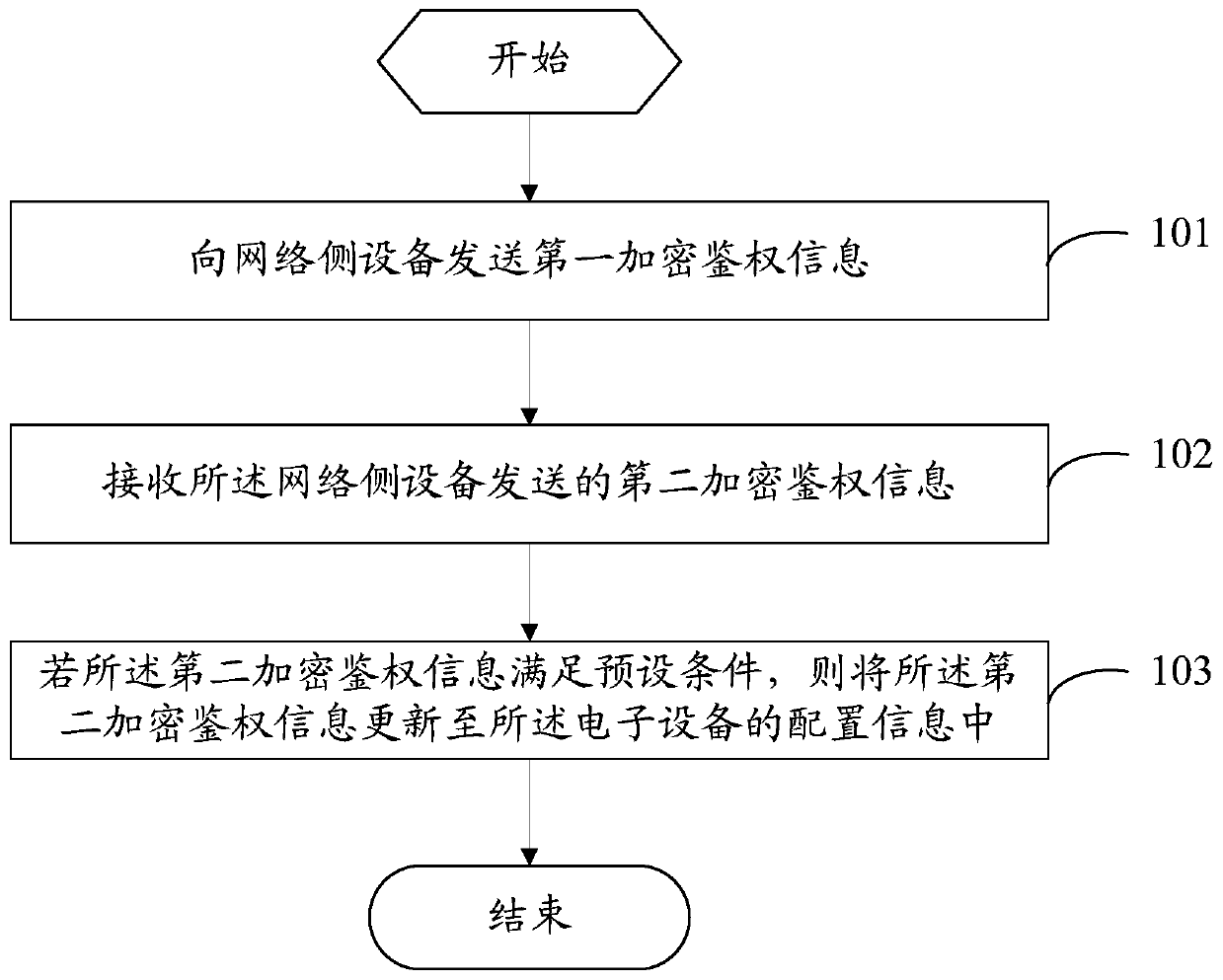
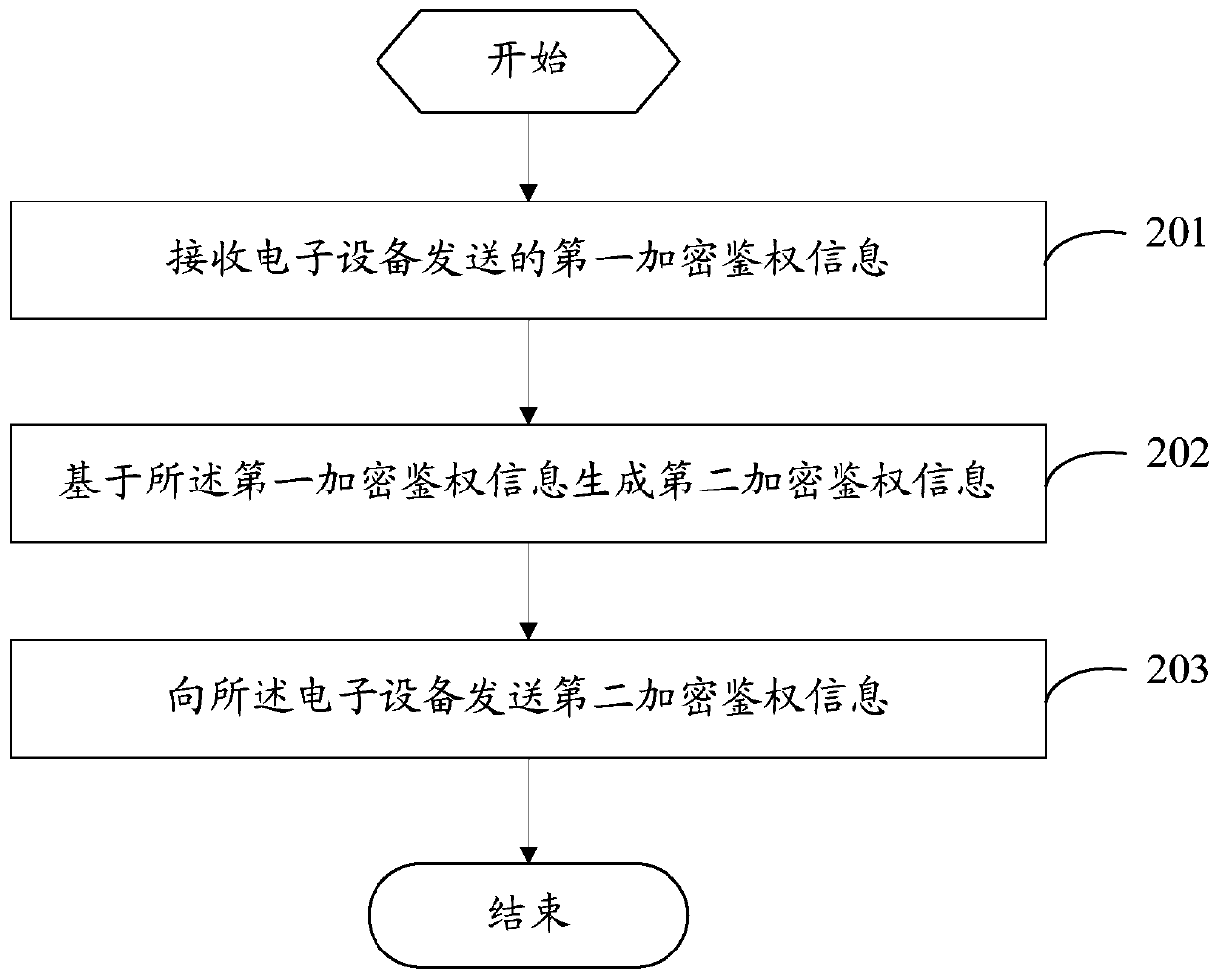
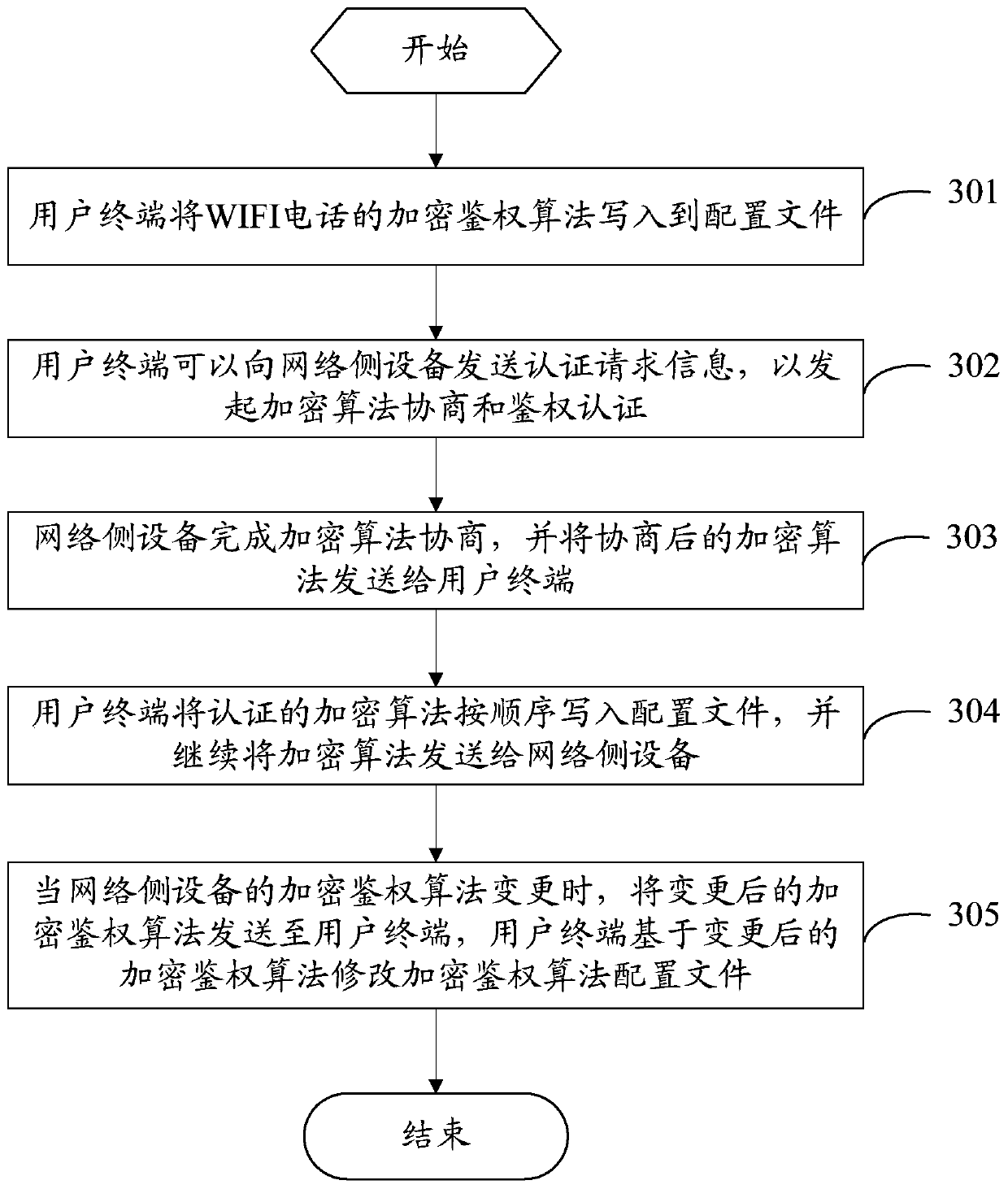
PendingCN110430573AImprove efficiencyIncrease success rateSecurity arrangementFailure causesEncryption
The invention provides an information authentication method, electronic equipment and network side equipment. The method comprises the following steps: sending first encrypted authentication information to the network side equipment; receiving second encryption authentication information sent by the network side equipment, wherein the second encryption authentication information is information obtained after the network side equipment updates the first encryption authentication information; and if the second encryption authentication information satisfies a preset condition, updating the second encryption authentication information to configuration information of the electronic equipment. Therefore, the configuration information of the electronic equipment is updated by using the second encrypted authentication information meeting the preset condition; the phenomenon of authentication failure caused by difference between the second encrypted authentication information and the authentication information in the configuration information can be effectively avoided, and the authentication efficiency and the registration success rate of the WIFI telephone are improved.
Owner:VIVO MOBILE COMM CO LTD
Identity authentication method, server and computer readable storage medium
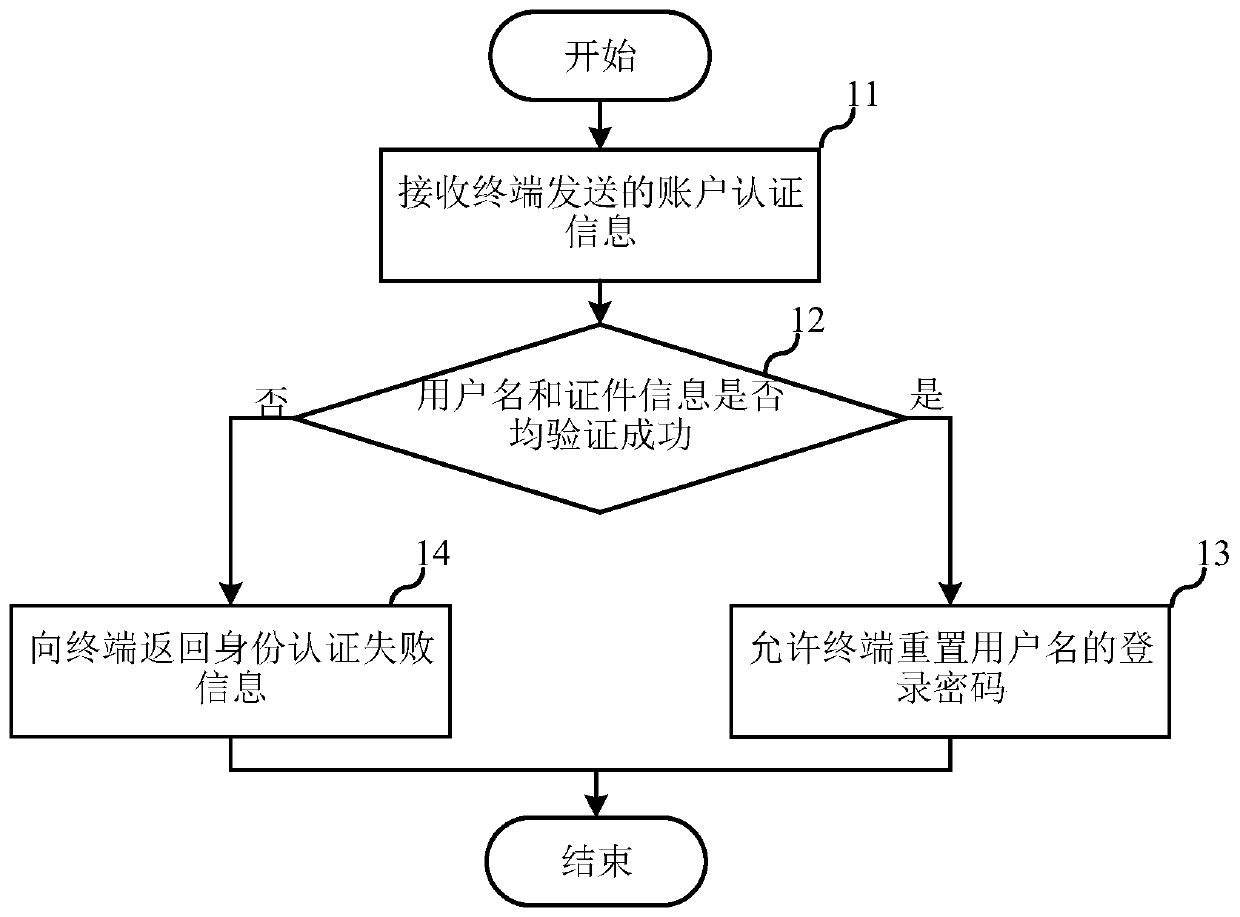
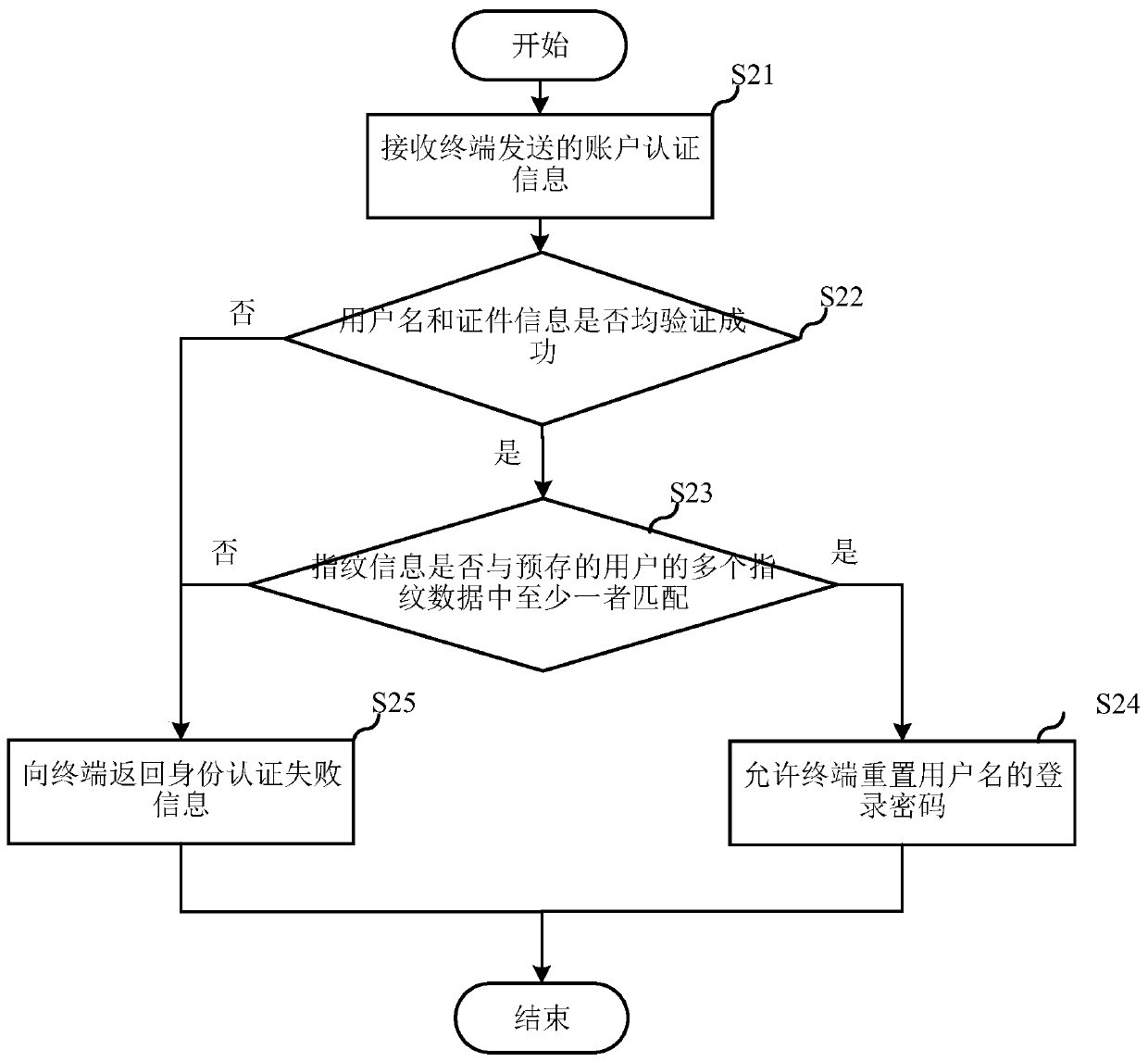
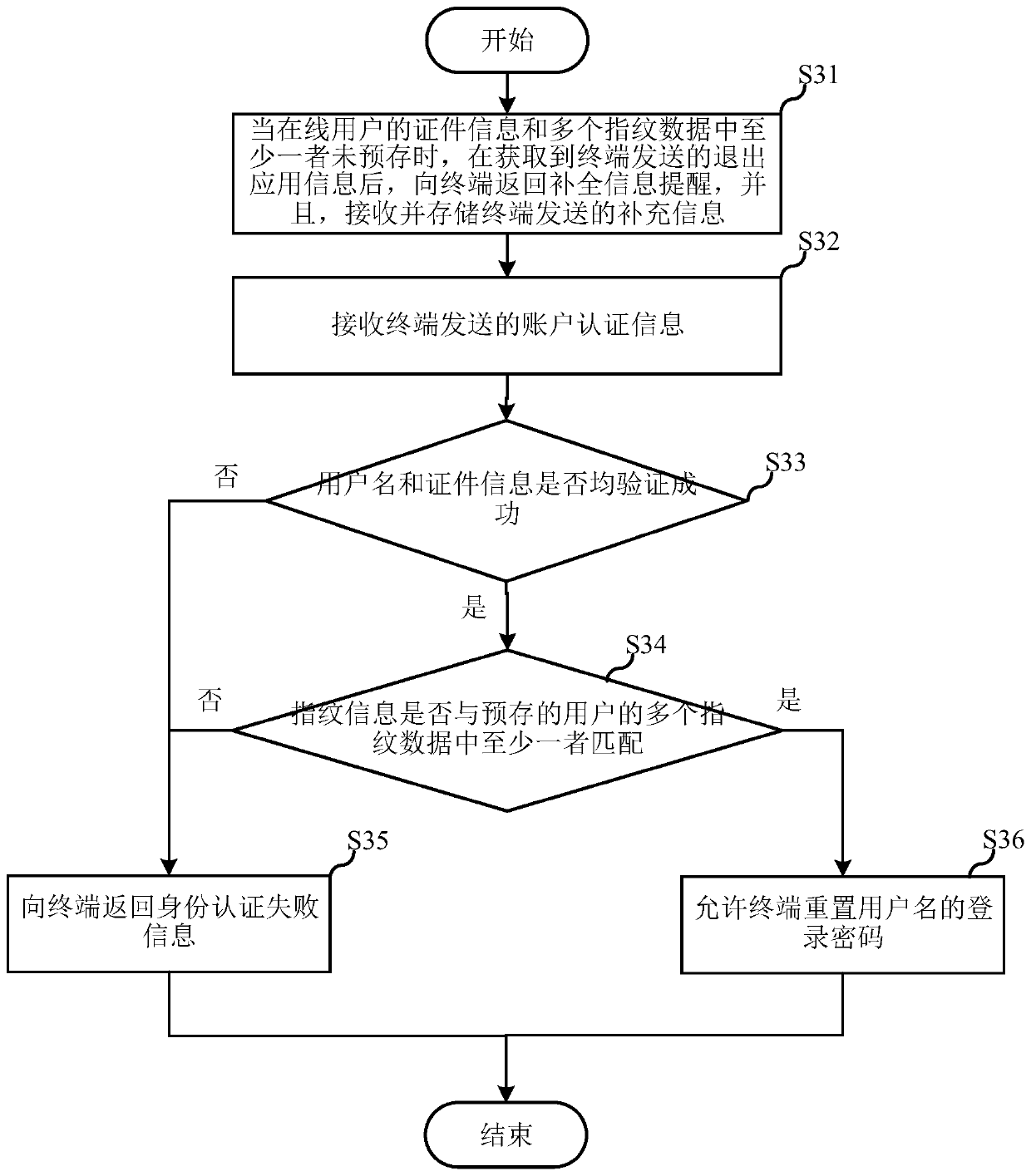
PendingCN111259349AConfidentialImprove convenienceDigital data authenticationInternet privacyPassword
The embodiment of the invention relates to the technical field of communication, and discloses an identity authentication method, a server and a computer readable storage medium. The identity authentication method comprises the steps that account authentication information sent by a terminal is received, and an account authentication request comprises a user name and certificate information; judging whether the user name and the certificate information are successfully verified or not; If yes, allowing the terminal to reset the login password of the user name, If not, returning identity authentication failure information to the terminal. According to the identity authentication method, the server and the computer readable storage medium provided by the invention, on the premise of ensuringthe safety of identity authentication, the convenience of identity authentication is improved.
Owner:CHINA MOBILEHANGZHOUINFORMATION TECH CO LTD +1
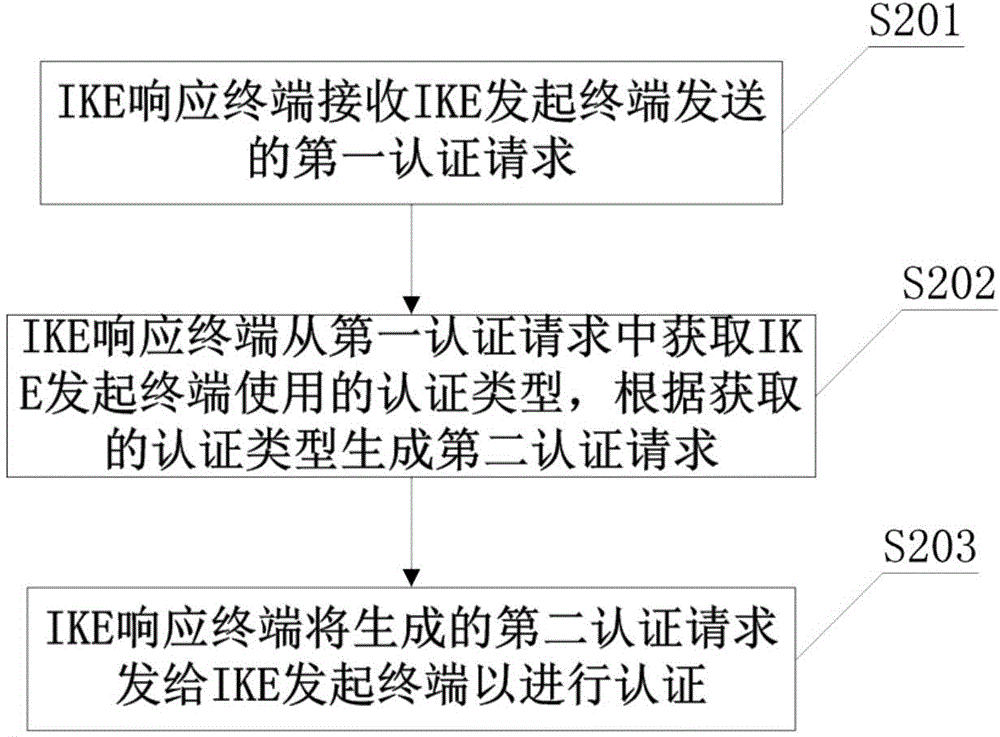
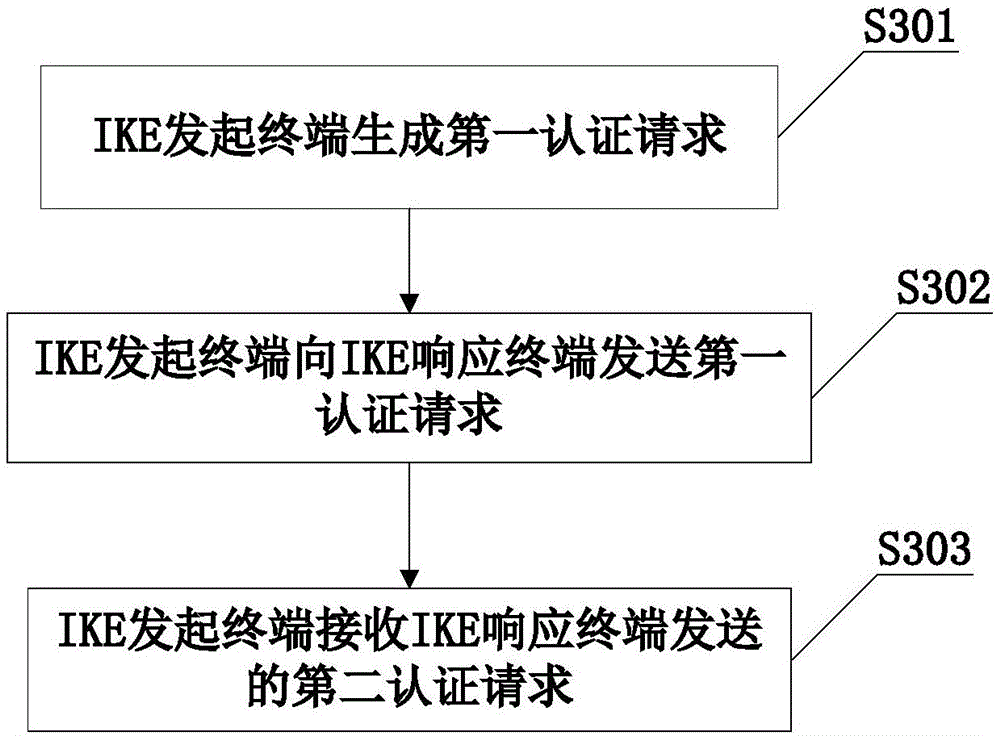
IKE authentication method, IKE initiating terminal, IKE response terminal and IKE authentication system
InactiveCN105450418AAvoid authentication failuresUser identity/authority verificationAuthentication system
The invention discloses an IKE authentication method, an IKE initiating terminal, an IKE response terminal and an IKE authentication system. The IKE initiating terminal generates a first authentication request containing an authentication type currently used by the IKE initiating terminal, and sends the first authentication request to the IKE response terminal; and the IKE response terminal obtains the authentication type used by the IKE initiating terminal after receiving the first authentication request, then generates a second authentication request according to the authentication type and sends the second authentication request to the IKE initiating terminal. It is obvious that, in the invention, the authentication type adopted by the IKE response terminal when generating the second authentication request is obtained from the first authentication request, that is, the authentication type adopted by the IKE response terminal is consistent with the authentication type adopted by the IKE initiating terminal, and the IKE initiating terminal certainly supports the authentication type. Therefore, by adopting the scheme provided by the invention, the IKE response terminal can adapt to authentication types in an intelligent manner for different IKE initiating terminals, thereby avoiding the problem that the authentication fails because the IKE initiating terminal does not support the authentication type adopted by the IKE response terminal.
Owner:ZTE CORP
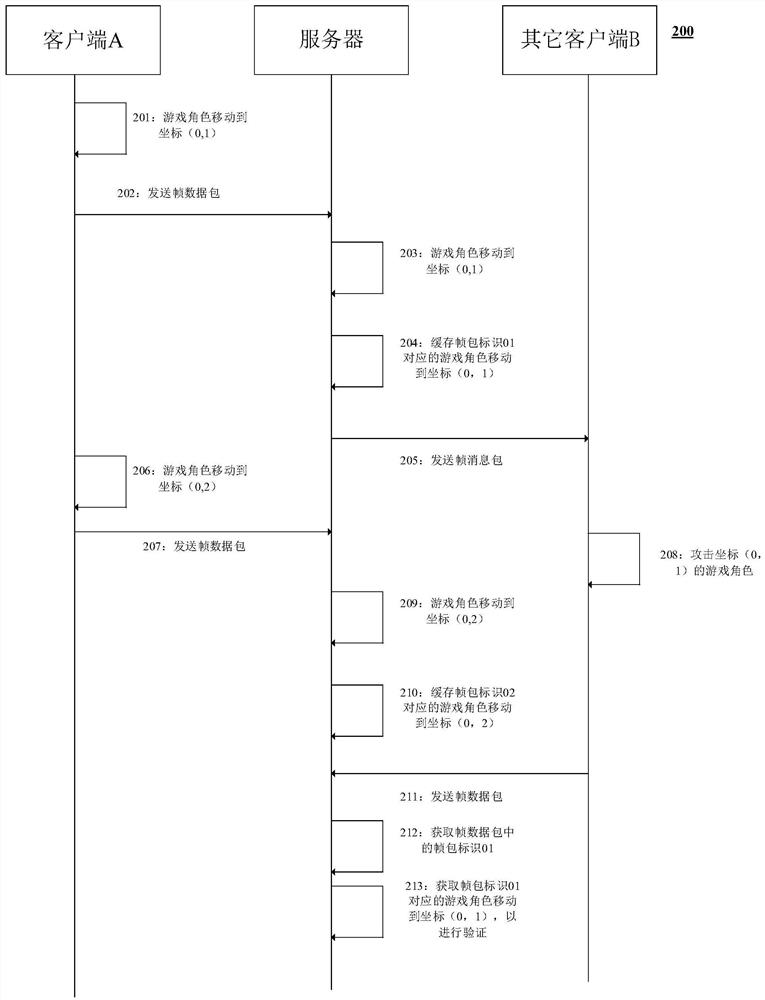
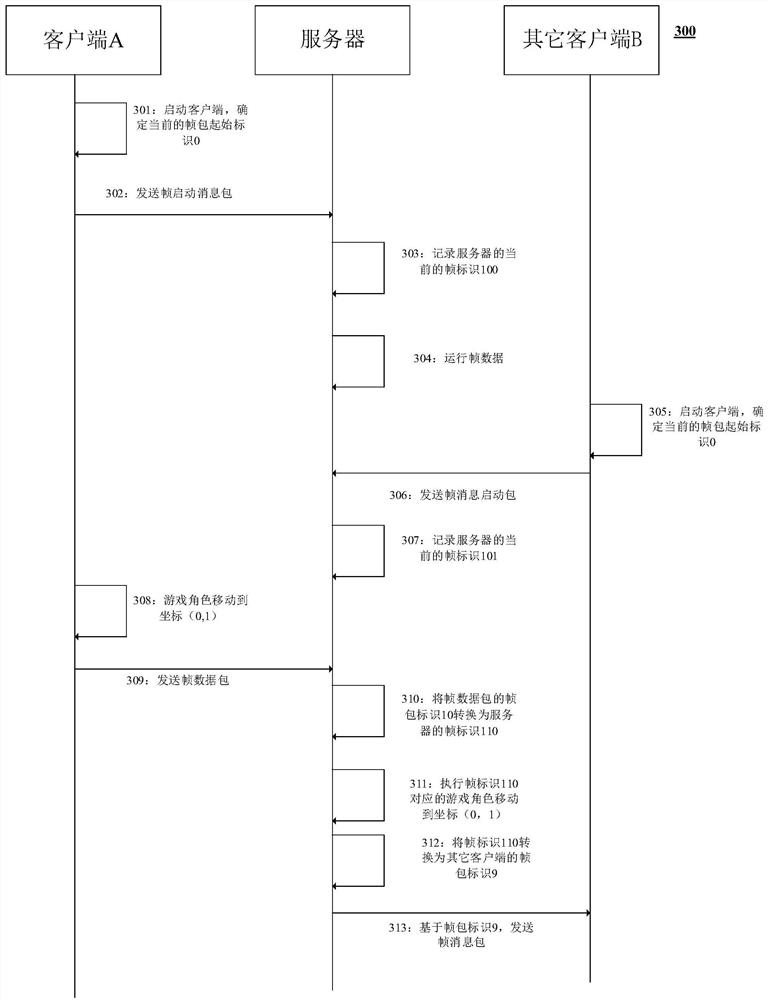
Data synchronization verification method and system, computing equipment and storage medium
PendingCN112169340AImprove experienceAccurate verification of operation resultsVideo gamesData synchronizationData pack
The embodiment of the invention provides a data synchronization verification method and system, computing equipment and a storage medium. According to the embodiment of the invention, the method comprises the steps: receiving a first frame data package, executing a first operation instruction, and obtaining a first operation result when the operation frame rate of a client installed at a terminalis greater than the operation frame rate of a server in a preset range in a preset time; storing a corresponding relationship between the first operation result and a first frame packet identifier toa corresponding cache queue; sending the first operation result to a plurality of corresponding terminals through a frame message packet, the frame message packet carrying a second frame packet identifier corresponding to the first frame packet identifier; and after receiving the frame message packet, enabling the terminal to return a second operation instruction and a frame packet identifier corresponding to the operation result in front of the second operation instruction through a second frame data packet so as to verify the second operation instruction. Therefore, the operation result canbe accurately verified for state synchronization.
Owner:CHENGDU PERFECT TIANZHIYOU BUSINESS CONSULTING CO LTD
Unlock control method and related products
InactiveCN107506629BAvoid authentication failuresIncrease success rateDigital data authenticationSubstation equipmentPattern recognitionComputer graphics (images)
Embodiments of the present invention disclose an unlock control method and related products. The method comprises: obtaining M fingerprint images by using a fingerprint information collecting module when detecting touch operations of M fingers on the touch screen; verifying the M fingerprint images; and when verification of L fingerprint images in the M fingerprint images fails, obtaining a target biometric recognition mode from Q types of pre-stored biometric recognition modes. By virtue of the technical scheme of the present invention, the success rate and flexibility of verification can be improved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
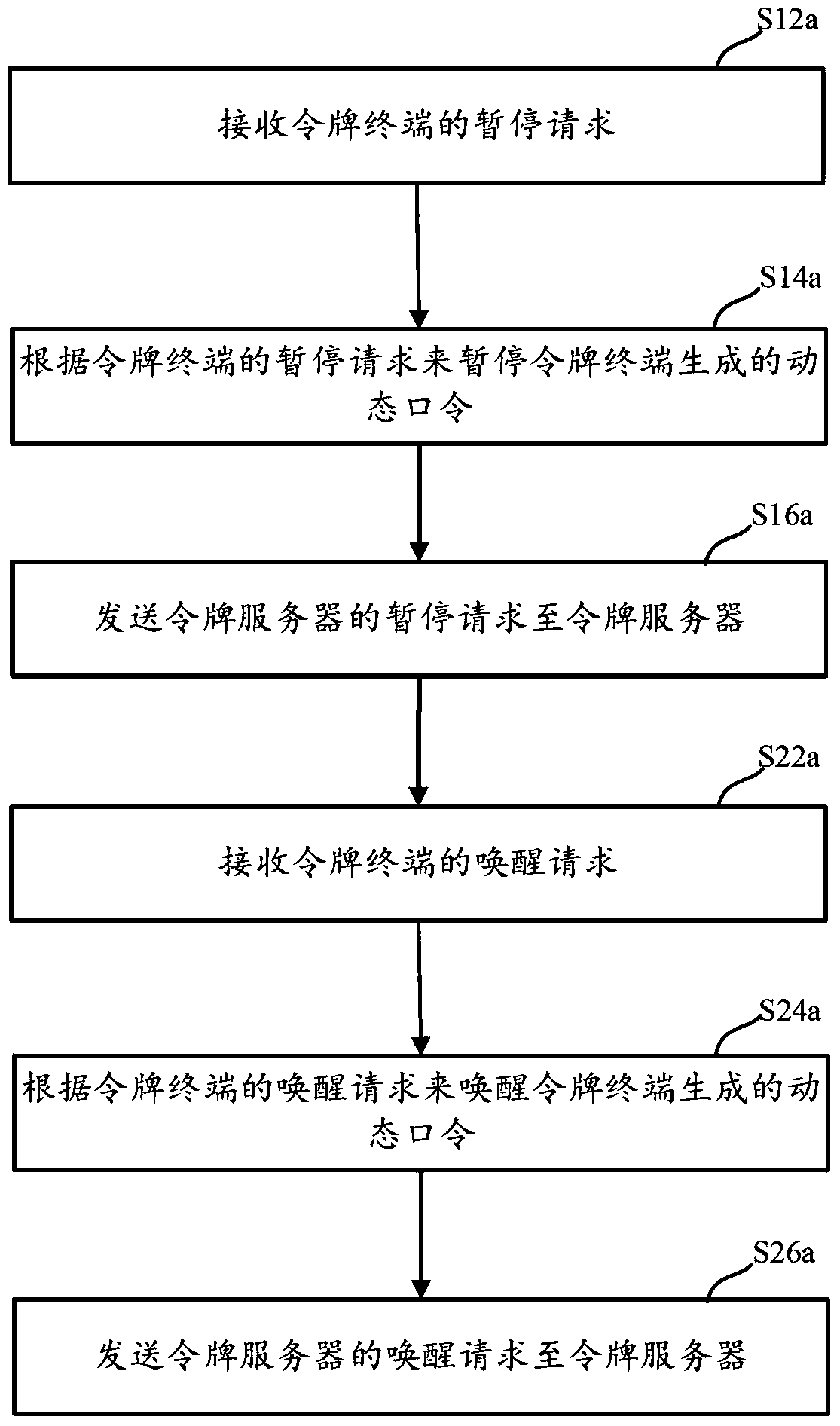
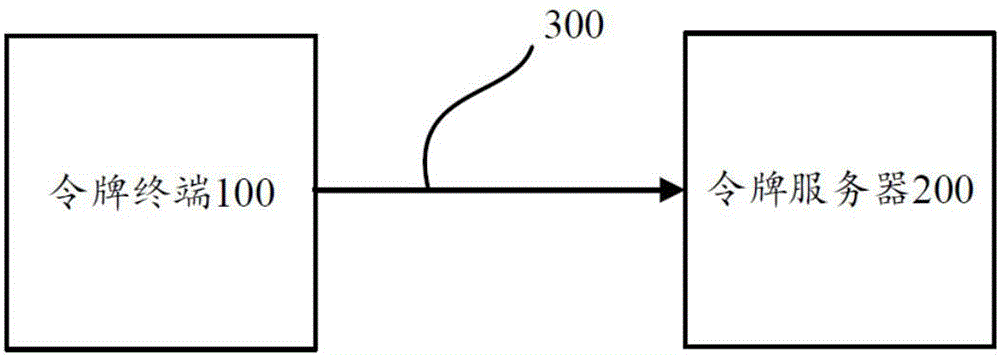
Dynamic token control method and device
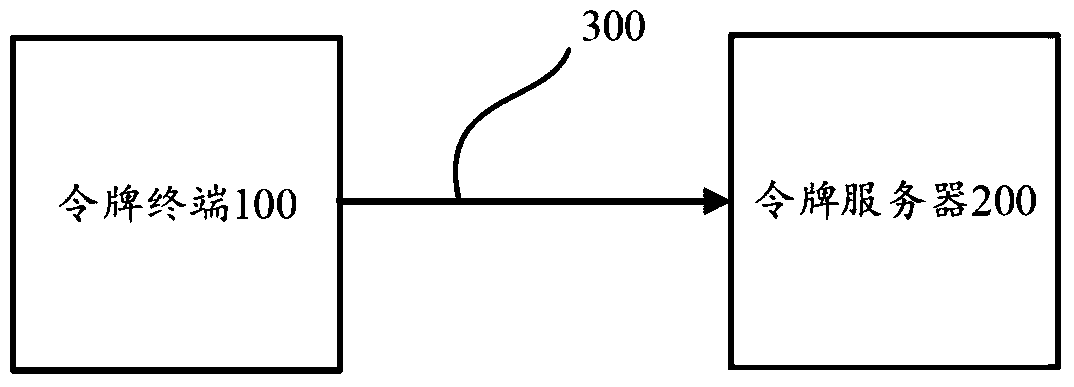
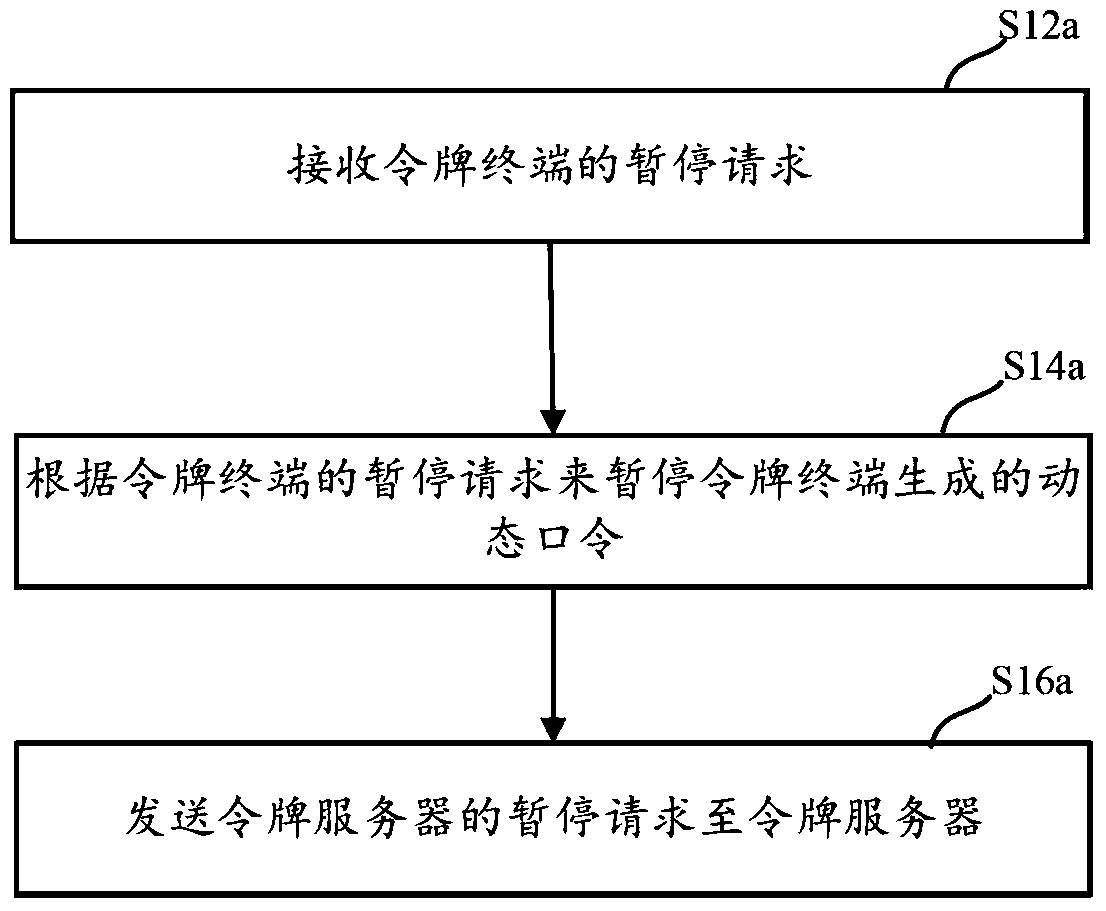
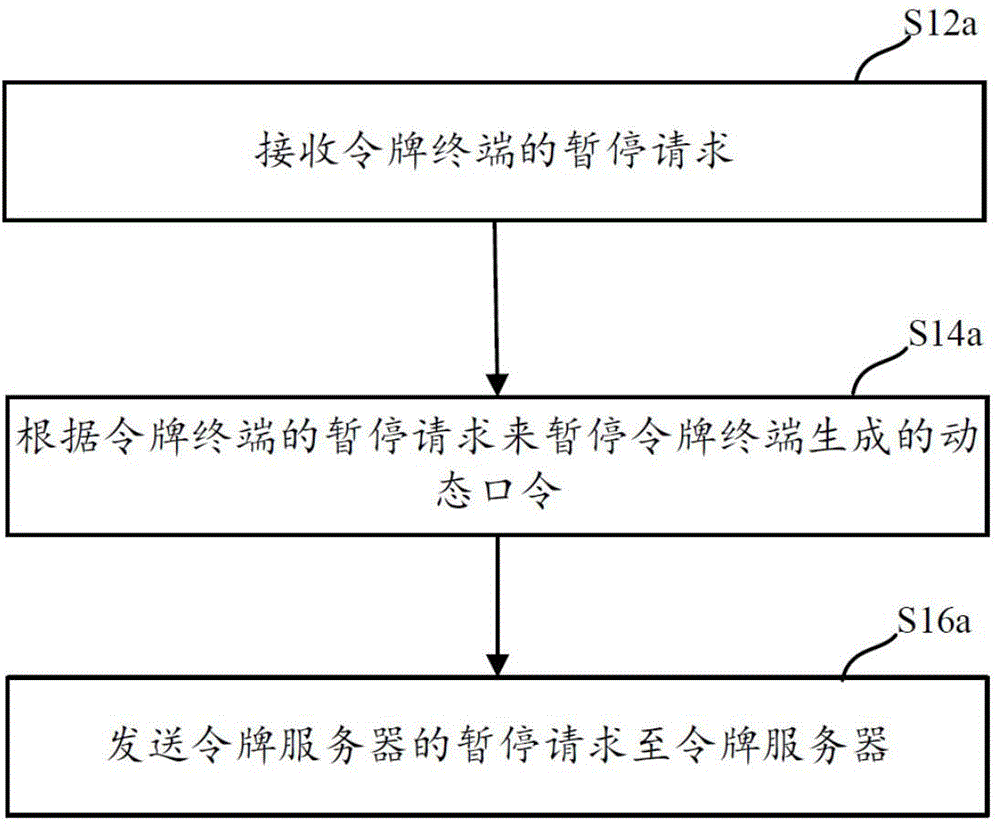
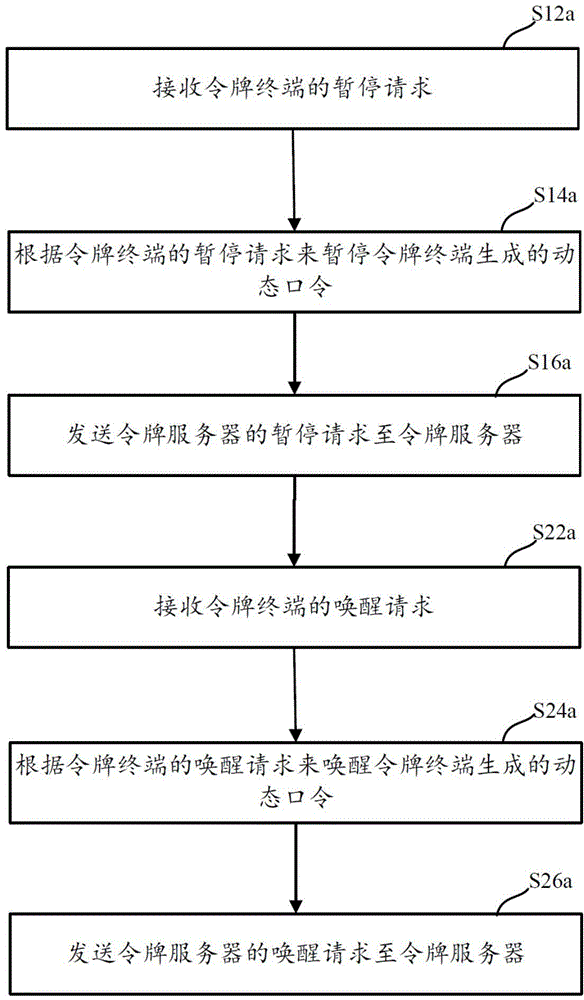
ActiveCN106161029BConvenient verificationImprove typing accuracyUser identity/authority verificationSufficient timePassword
This application discloses a dynamic token control method and device, which solve the problem in the prior art that a password is difficult to be verified existing in the process of using a dynamic token. The token control method includes: receiving a suspend request of a token terminal; suspending a dynamic password generated by the token terminal according to the suspend request of the token terminal; and sending a suspend request of a token server to the token server, wherein the suspend request of the token server is used for suspending a dynamic password generated by the token server. Compared with the prior art, the dynamic token control method and device provided in embodiments of this application enable dynamic passwords generated by a token terminal and a token server to be suspended when a user has dynamic password verification requirements, thereby giving the user sufficient time to input the dynamic passwords, improving the input accuracy of the dynamic passwords, avoiding a dynamic password verification failure due to the change of a dynamic password of a token server end, and making dynamic password verification be simple.
Owner:ADVANCED NEW TECH CO LTD
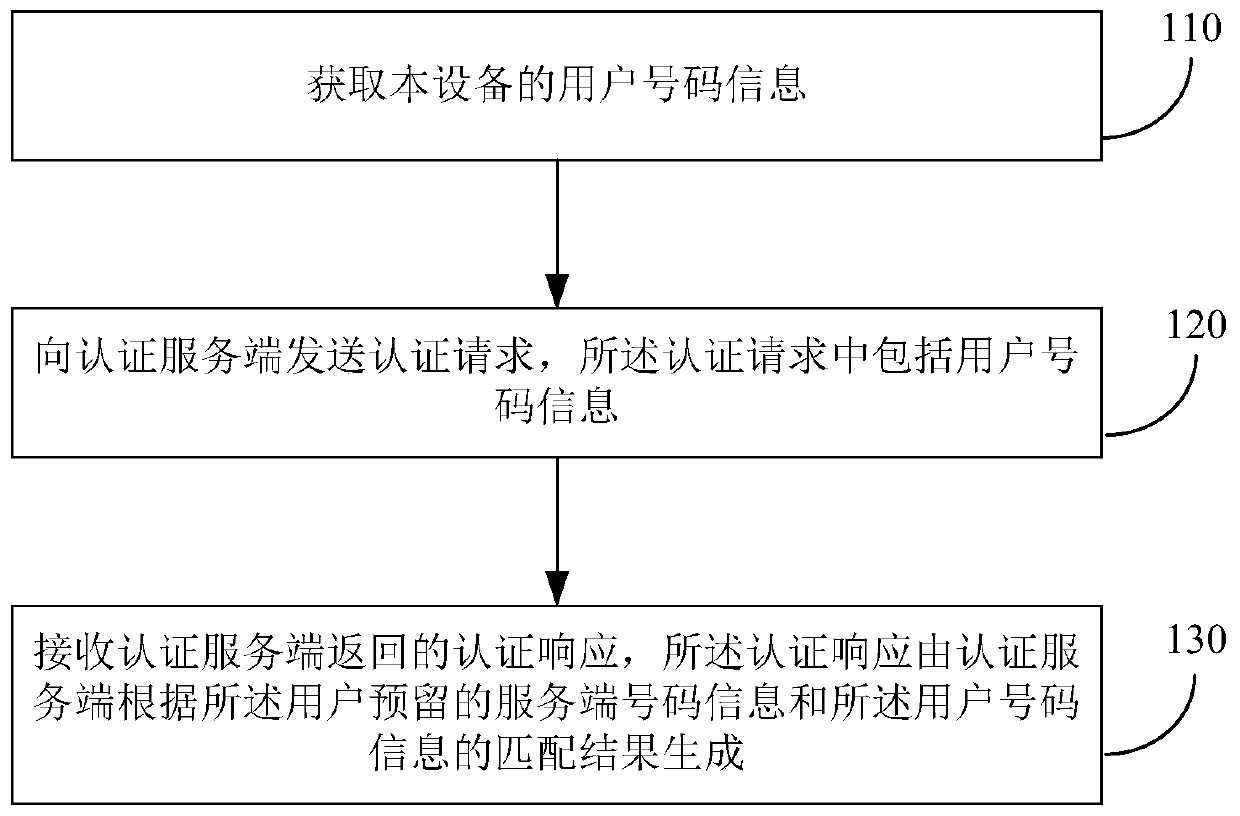
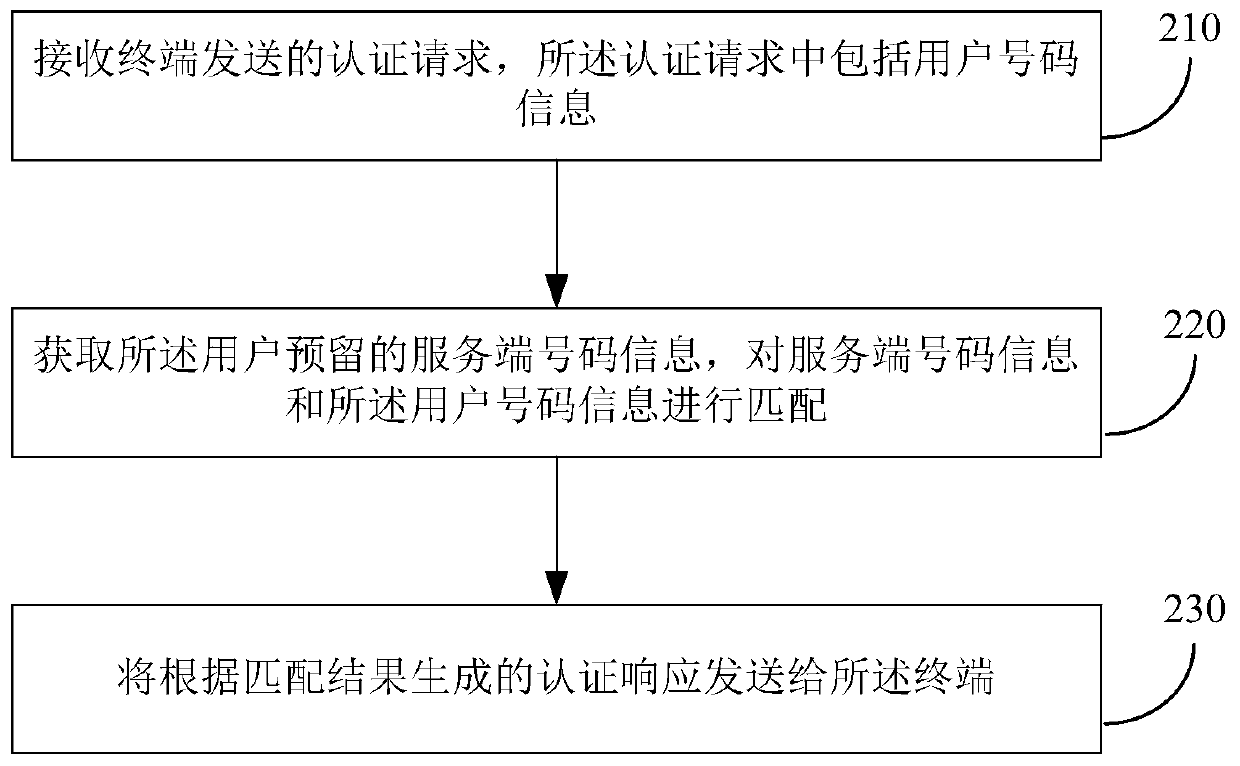
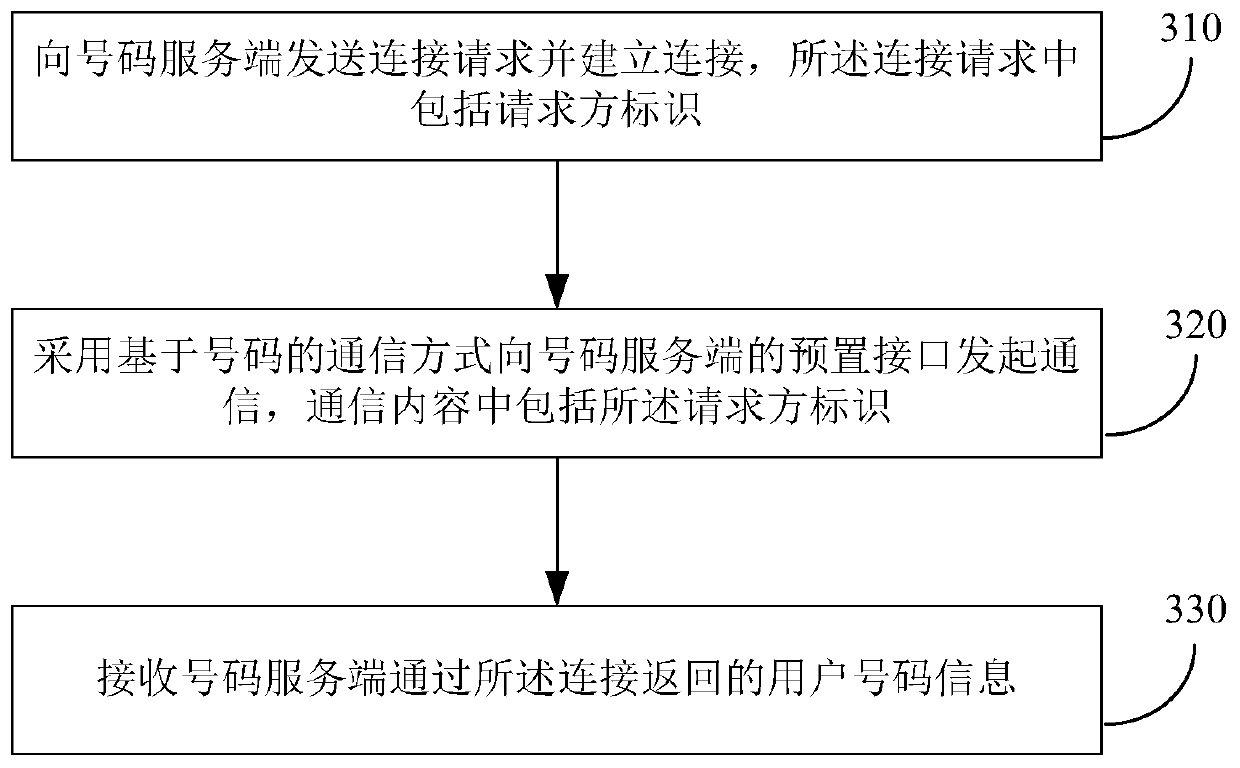
Method and device for user authentication, method and device for acquiring user number information
ActiveCN106878280BEasy to operateAvoid causing authentication failureTransmissionSecurity arrangementUser authenticationText messaging
Owner:ADVANCED NEW TECH CO LTD
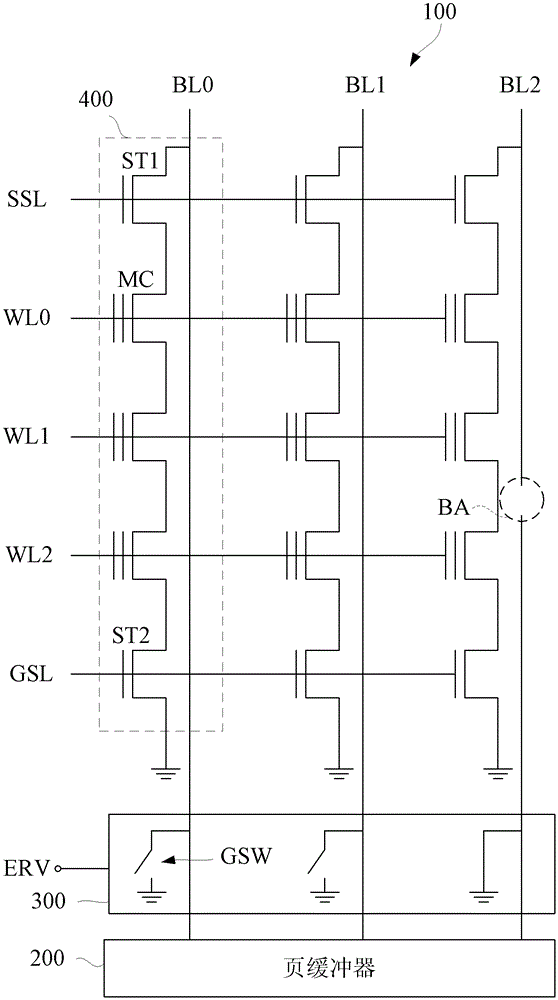
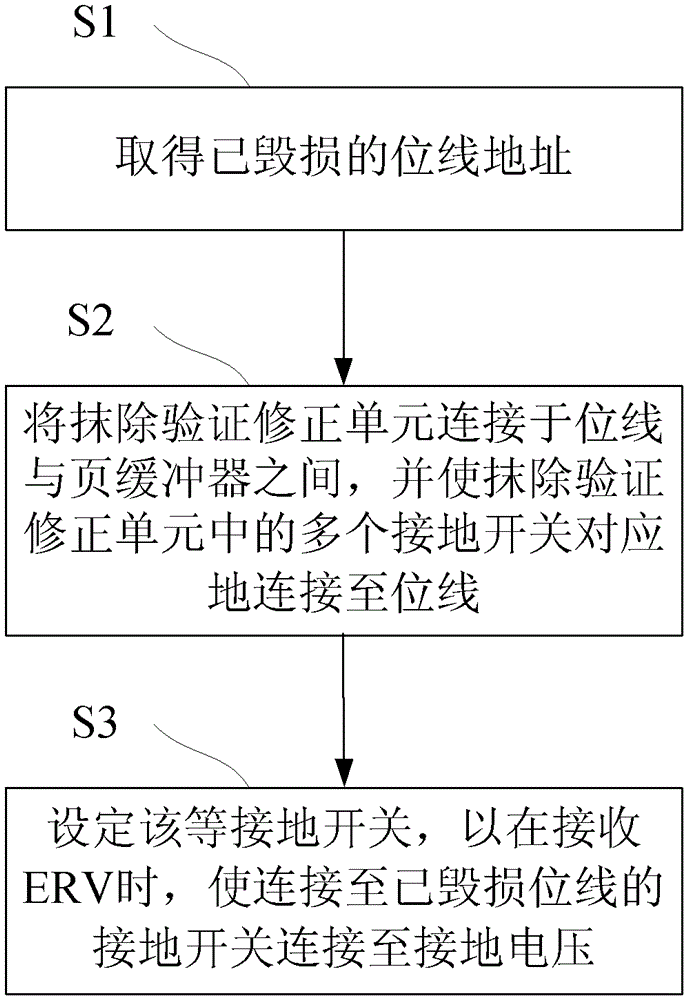
Semiconductor device and method for accelerating erase verification procedure by the same
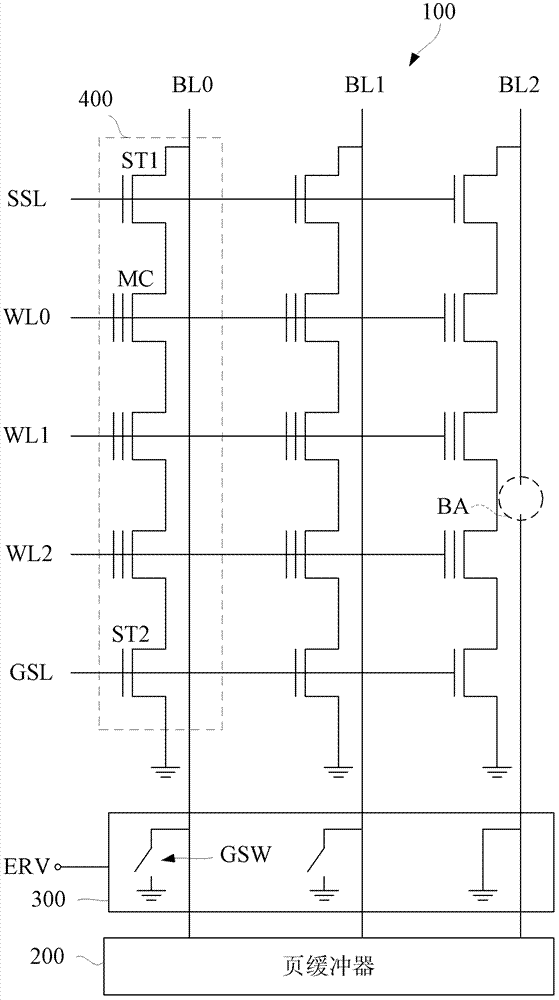
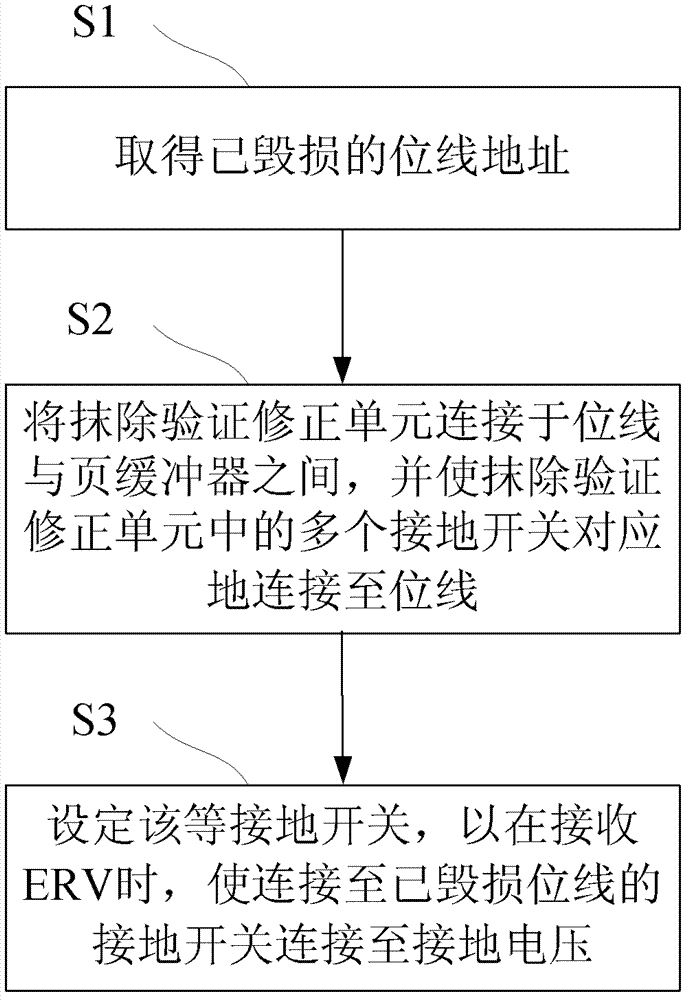
ActiveCN103198853AAvoid long erase verification timesAvoid authentication failuresDigital storagePower semiconductor deviceComputer science
The invention discloses a semiconductor device and a method for accelerating an erase verification procedure by the same. An erase verification correction unit is connected between a damaged bit line in the semiconductor device and a page buffer; through a special line arrangement on the damaged bit line, a grounding switch of the erase verification correction unit can connect the damaged bit line to a grounding voltage during an erase verification procedure, so that the page buffer can receive the grounding voltage to further verify that the damaged bit line has passed the erase verification, thereby substantially saving repeated verification time consumed in the prior art.
Owner:EON SILICON SOLUTION
Block chain-based identity authentication method, system, device and computer equipment
ActiveCN111949953BImprove rigorImprove accuracyDigital data authenticationEngineeringKey authentication
The present application relates to a block chain-based identity authentication method, system, device, computer equipment and storage medium. The method includes: receiving a login request sent by a user terminal, the login request carrying private key signature data, responding to the login request, obtaining public key data, and obtaining the device of the user terminal when the verification of the private key signature data is completed according to the public key data. Identify the data, and generate key data according to the device identification data, send the key data to the user terminal, receive the authentication data submitted by the user terminal for the key data, and when the authentication data submitted by the user terminal passes the verification, it is determined that the identity authentication has passed . The above scheme is decentralized through the blockchain to avoid authentication failures caused by the downtime of the central node; by introducing the dual authentication mechanism of device authentication and key data based on device identification data and private key authentication, it is possible to avoid repudiation of signatures Such behaviors improve the accuracy of identity authentication and ensure data security.
Owner:卓尔智联(武汉)研究院有限公司
Realization method for completely automated public turing test to tell computers and humans apart, and terminal
InactiveCN106302443AAvoid verification processAvoid insteadDigital data authenticationTransmissionTuring testPressure sense
The embodiment of the invention relates to the technical field of the internet and discloses a realization method for a completely automated public turing test to tell computers and humans apart, and a terminal. According to the method and the terminal, the realization method for the completely automated public turing test to tell computers and humans apart comprises the steps of displaying first screen location information and first pressure information, wherein the first screen location information is used for indicating a to-be-pressed screen location of a pressure sensing screen of a user side, and the first pressure information is the pressed pressure information of the to-be-pressed screen location; obtaining second screen location information and second pressure information, wherein the second screen location information indicates the pressed screen location of the pressure sensing screen, and the second pressure information is the pressed pressure information of the pressed screen location; comparing the first screen location information with the second screen location information, comparing the first pressure information with the second pressure information and carrying out verification according to comparison results. The invention also discloses the terminal. According to the embodiment of the method and the terminal, an identification success rate and identification difficulty can be balanced, and a computer program can be prevented from carry out the verification instead of a person.
Owner:XIAN YIPU COMM TECH
An attack message identification method, device and core equipment
ActiveCN104601578BImprove processing efficiencyAvoid authentication failuresTransmissionAuthentication
The invention discloses a recognition method and device for an attack message and a core device. The method comprises the steps of determining the length of conversation of authentication request message without being authenticated; comparing the length of the conservation of the authentication request message with the preset ageing length of the conservation; determining that the authentication request message is the attack message when the length of the conservation of the authentication request message exceeds the preset ageing length of the conservation. According to the scheme, the method has the advantage that the authentication request handling efficiency can be increased.
Owner:RUIJIE NETWORKS CO LTD
Identity verification method and device and electronic equipment
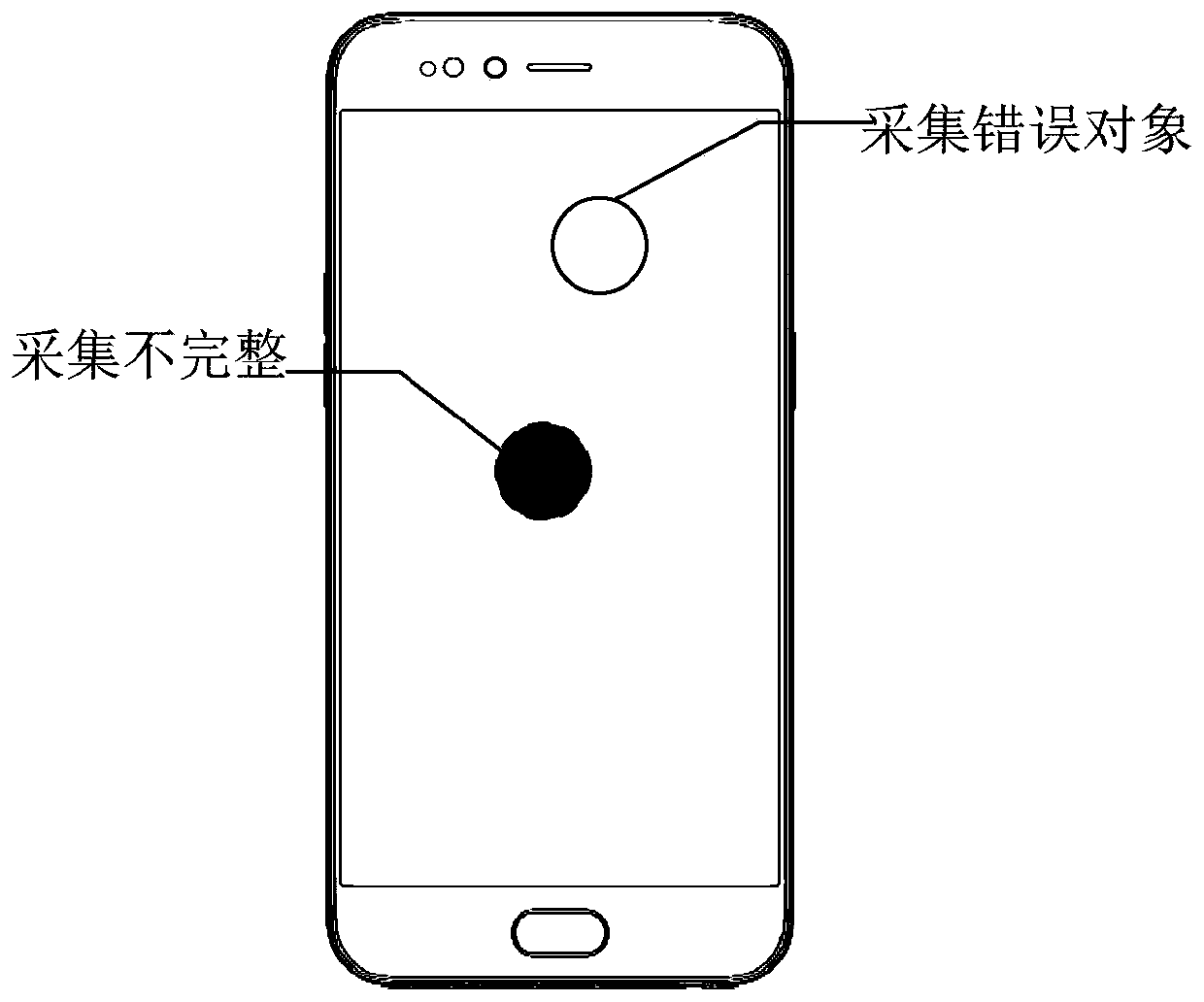
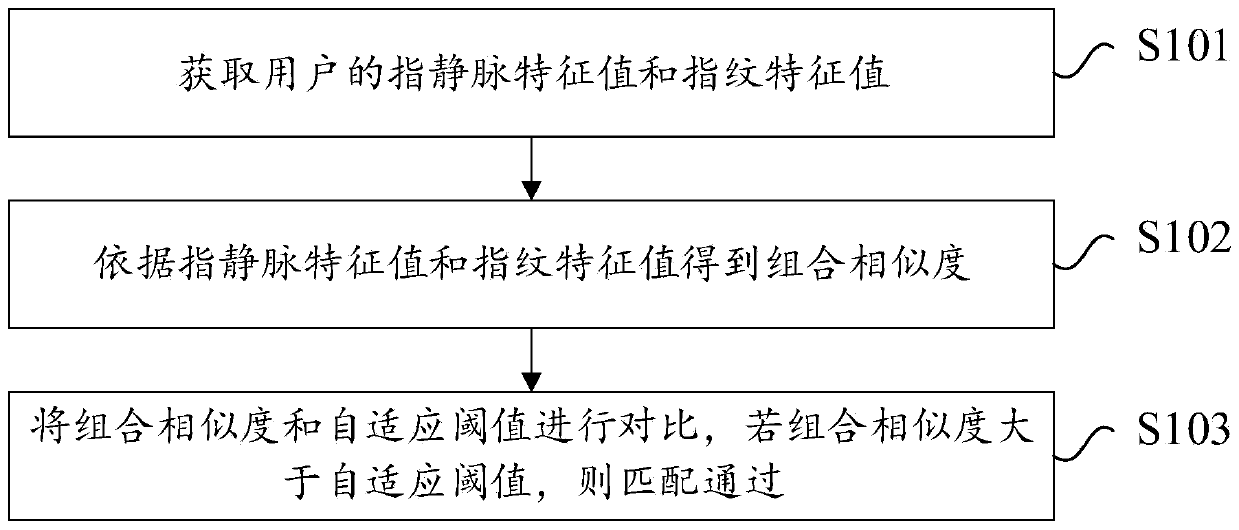
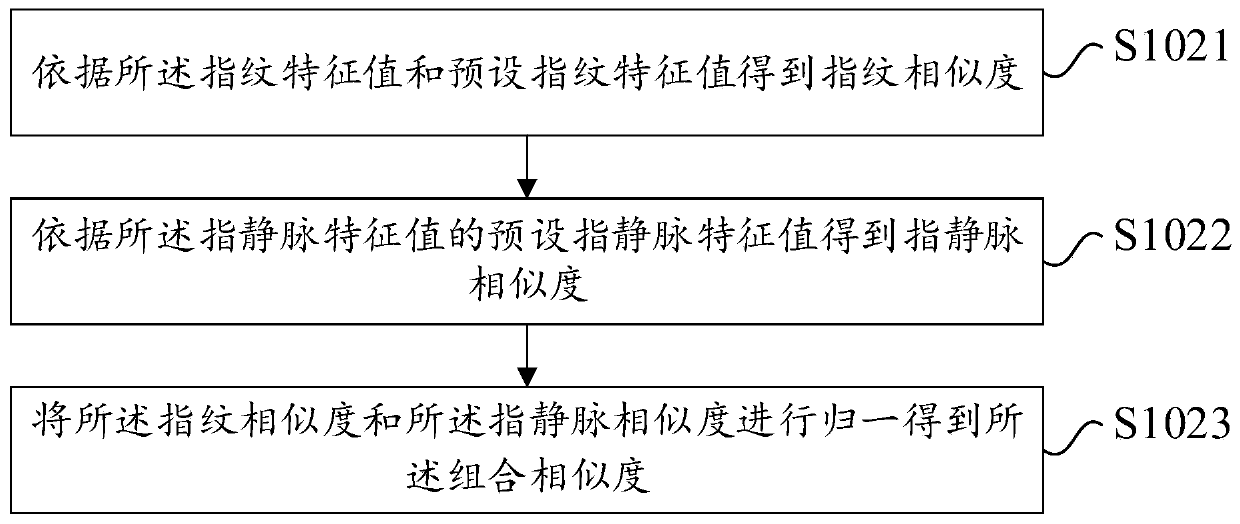
ActiveCN111382593AAvoid validation errorsAvoid authentication failuresMatching and classificationSubcutaneous biometric featuresAlgorithmInformation security
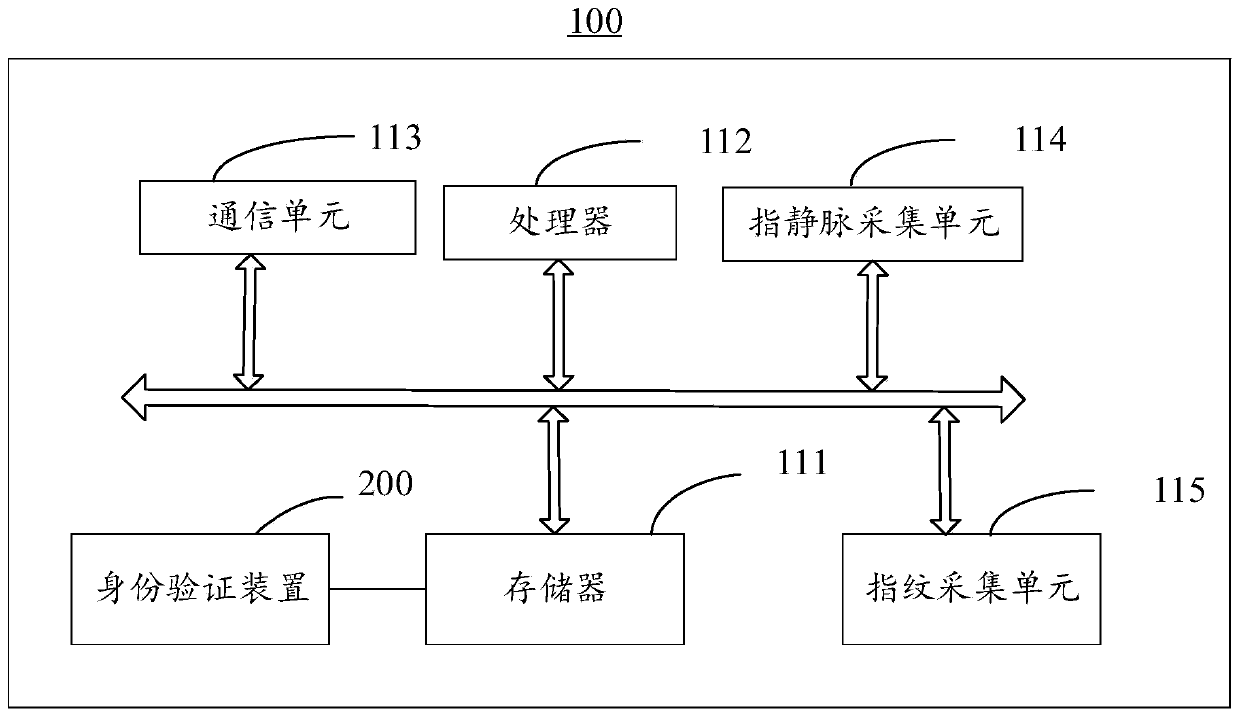
The embodiment of the invention provides an identity verification method and device and electronic equipment and belongs to the technical field of information security. The method comprises the following steps that: a fingerprint characteristic value and a finger vein characteristic value are acquired; a combined similarity according to the fingerprint characteristic value and the finger vein characteristic value is obtained; and the combination similarity is compared with an adaptive threshold, and if the combination similarity is greater than the adaptive threshold, matching is passed. Thus,verification errors caused by fingerprint material counterfeiting are avoided, and meanwhile, verification failure caused by errors in the acquisition of any one of the fingerprint characteristic value and the finger vein characteristic value due to environmental factors is also avoided.
Owner:ZHEJIANG UNIVIEW TECH CO LTD
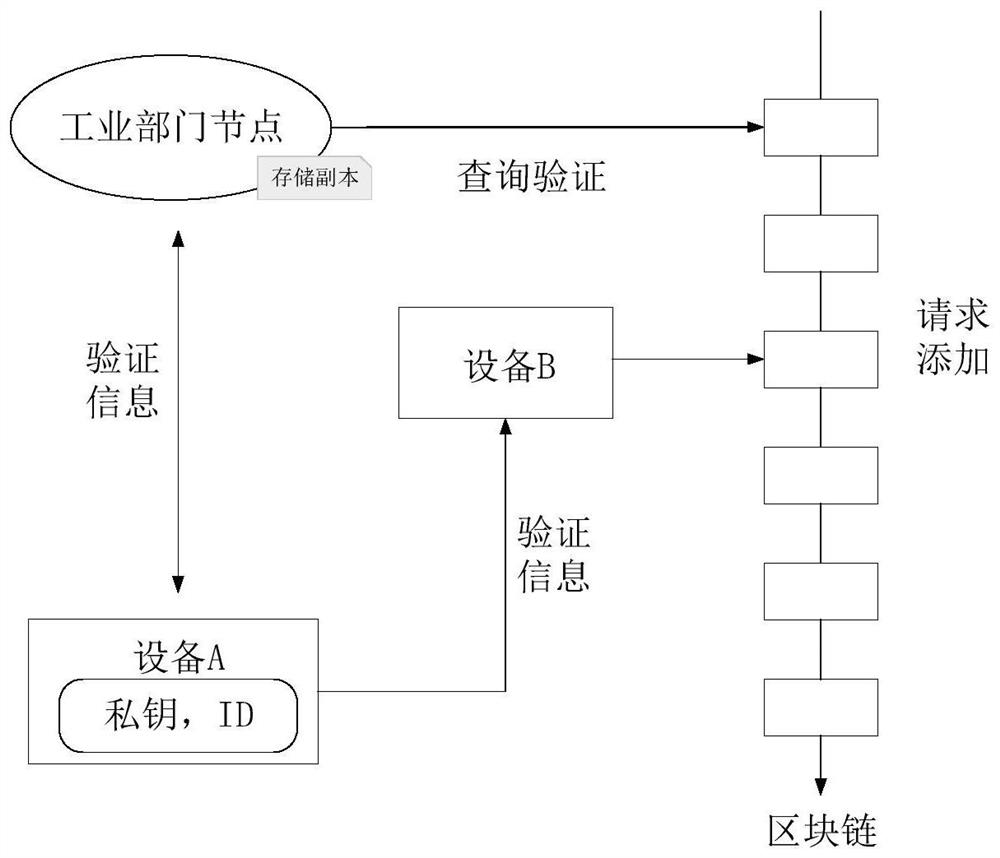
A blockchain-based identity authentication and secure interaction method for industrial Internet of Things devices
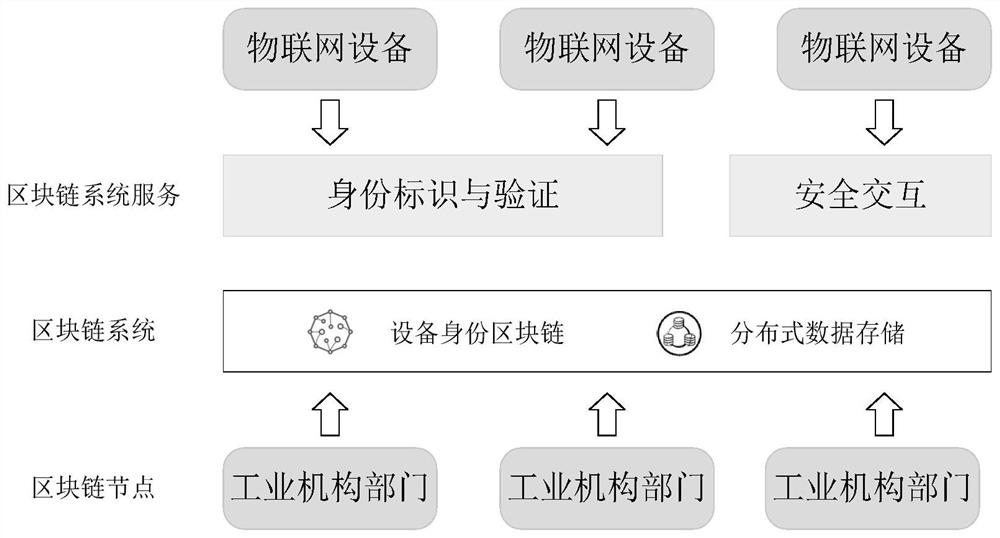
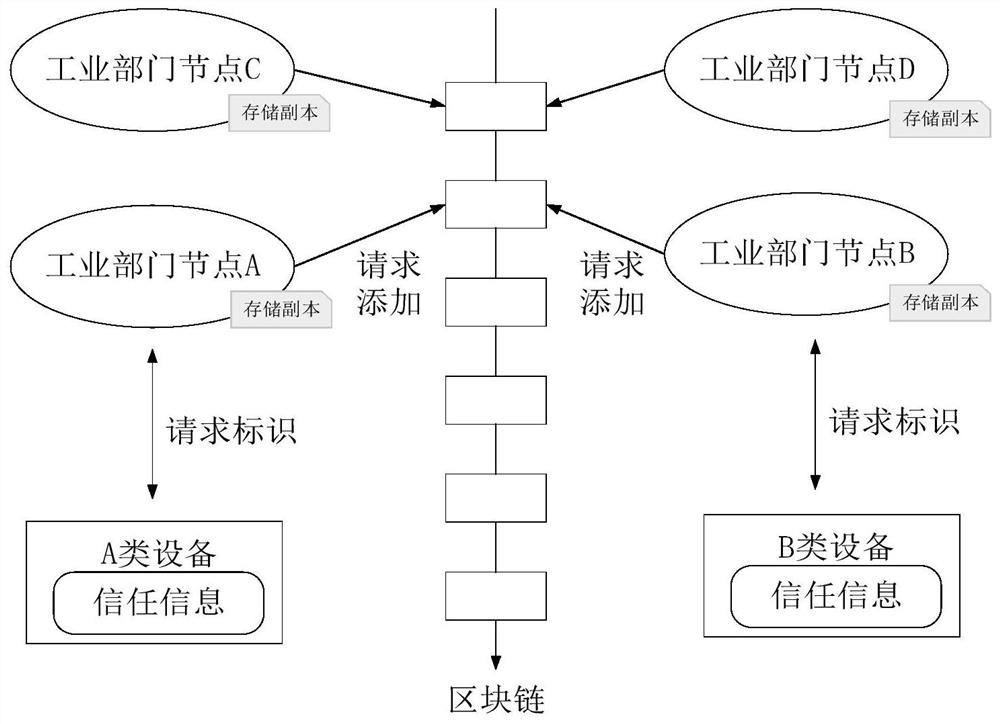
InactiveCN109918878BAvoid authentication failuresIdentity management inefficienciesKey distribution for secure communicationDigital data authenticationBusiness dataIndustrial Internet
The invention relates to a blockchain-based industrial Internet of Things device identity authentication and security interaction method, which presets trust information for the industrial Internet of Things device, and then the device generates identity public and private key information, and uses the device software and hardware information to generate the Industrial Internet of Things The unique fingerprint ID of the device; use the preset trust information to sign the public key + ID of the device and send it to the identity service node on the blockchain. The information is written into the blockchain; the industrial Internet of Things device uses the identity private key to sign the business data and sends it to the business interaction party. Key, use the sender's public key to verify the above signature information; Industrial Internet of Things devices intelligently configure access rights between devices through smart contracts, prevent devices that do not comply with access rules from interacting, and ensure mutual access between authorized devices.
Owner:INST OF INFORMATION ENG CAS
Information acquisition method and device, electronic equipment and storage medium
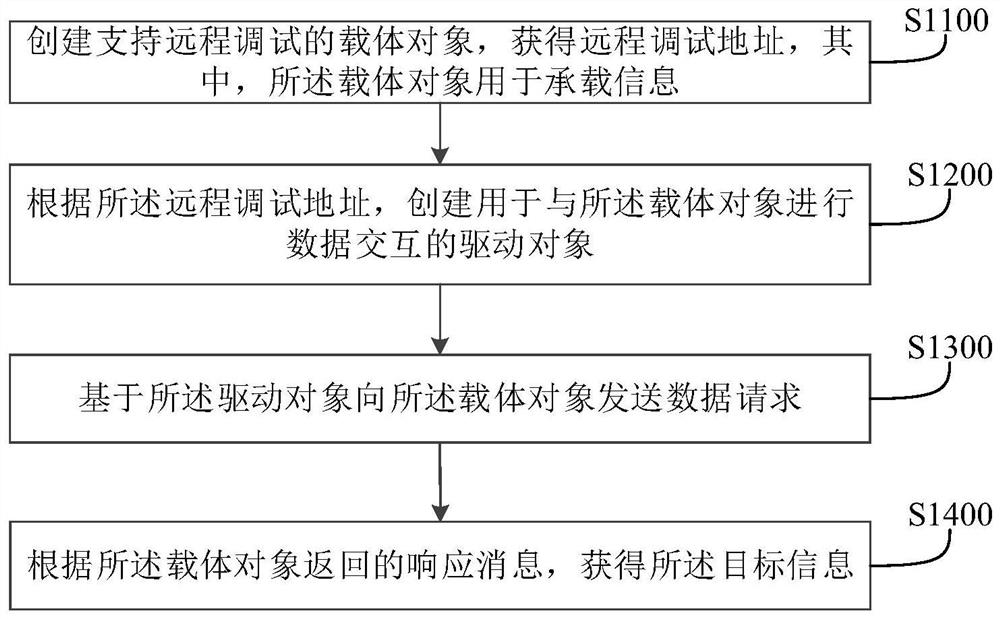
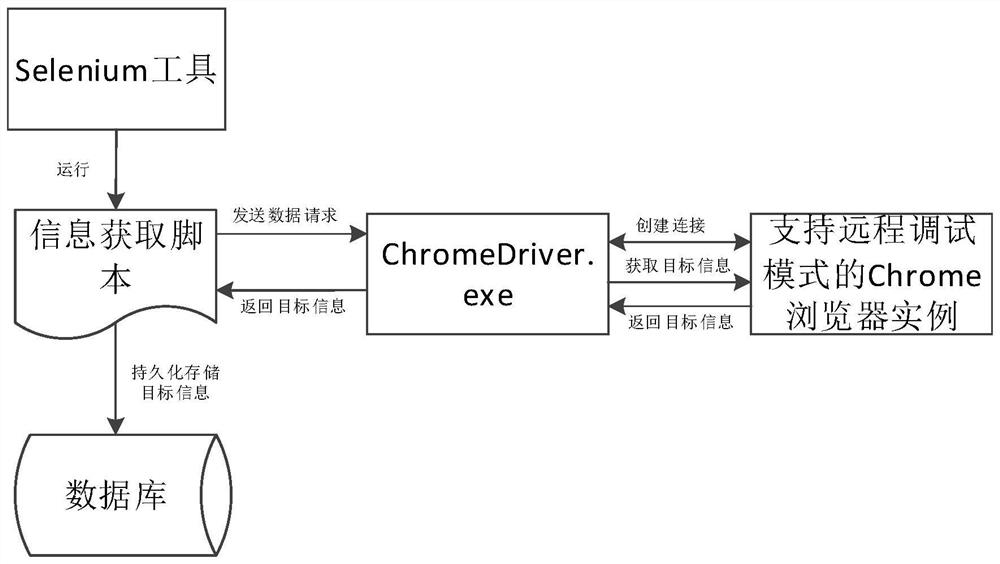
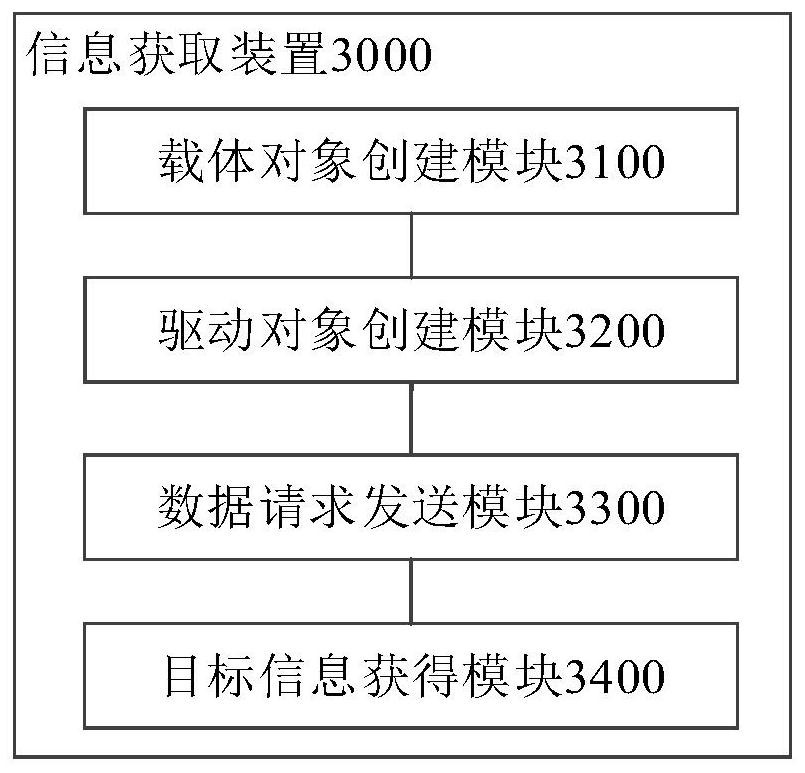
PendingCN113190435AEasy to collectAvoid authentication failuresSoftware testing/debuggingComputer hardwareEngineering
The invention discloses an information acquisition method and device and electronic equipment, and the method comprises the steps: creating a carrier object supporting remote debugging, and obtaining a remote debugging address, the carrier object being used for bearing information; according to the remote debugging address, creating a driving object for performing data interaction with the carrier object; sending a data request to the carrier object based on the driving object; and obtaining the target information according to a response message returned by the carrier object. According to the method, the application program, such as a Selenium tool, can conveniently obtain the target information from the network.
Owner:BIGO TECH PTE LTD
A method and device for realizing authentication
InactiveCN101883362BFacilitate communicationImprove satisfactionTransmissionSecurity arrangementLower gradeComputer terminal
Owner:ZTE CORP
Dynamic token control method and device
ActiveCN106161029AConvenient verificationImprove typing accuracyUser identity/authority verificationSufficient timePassword
This application discloses a dynamic token control method and device, which solve the problem in the prior art that a password is difficult to be verified existing in the process of using a dynamic token. The token control method includes: receiving a suspend request of a token terminal; suspending a dynamic password generated by the token terminal according to the suspend request of the token terminal; and sending a suspend request of a token server to the token server, wherein the suspend request of the token server is used for suspending a dynamic password generated by the token server. Compared with the prior art, the dynamic token control method and device provided in embodiments of this application enable dynamic passwords generated by a token terminal and a token server to be suspended when a user has dynamic password verification requirements, thereby giving the user sufficient time to input the dynamic passwords, improving the input accuracy of the dynamic passwords, avoiding a dynamic password verification failure due to the change of a dynamic password of a token server end, and making dynamic password verification be simple.
Owner:ADVANCED NEW TECH CO LTD
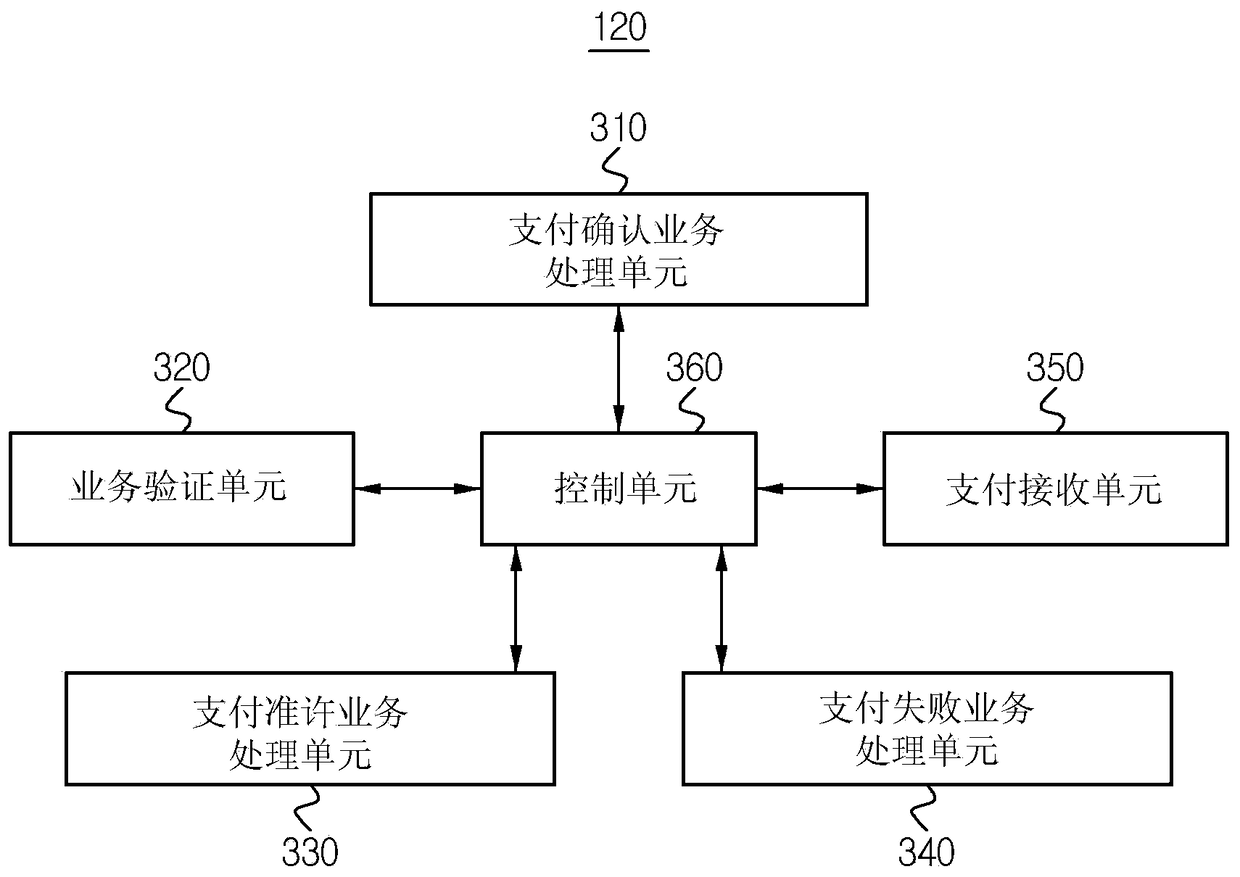
Payment method and payment gateway server, time certificate issuing server and mobile terminal
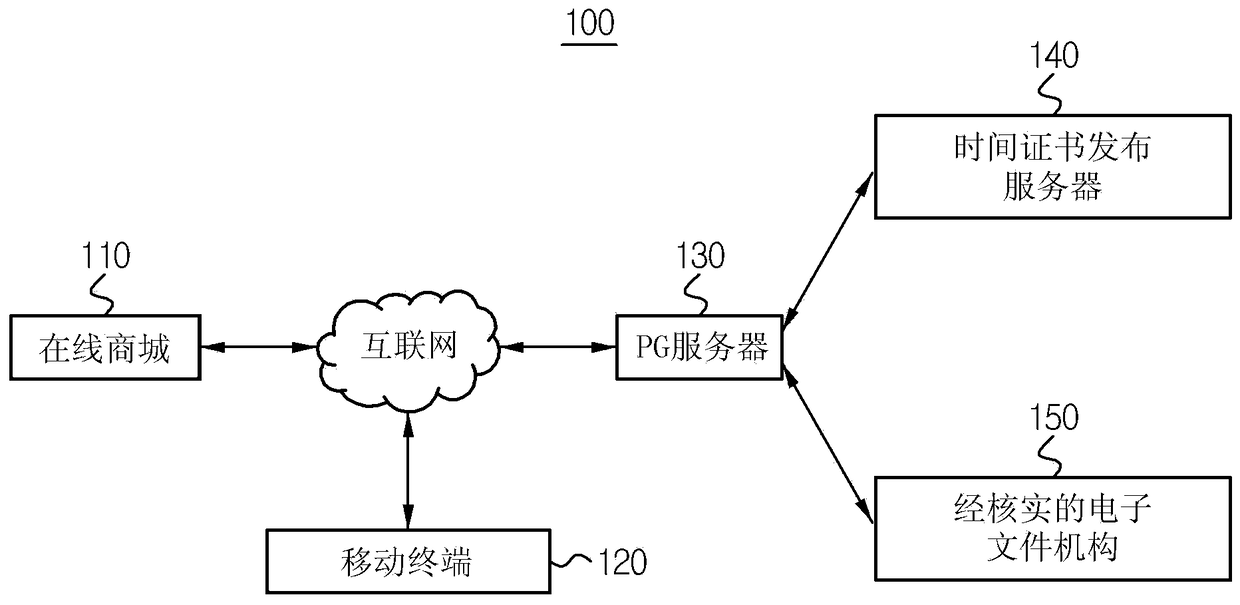
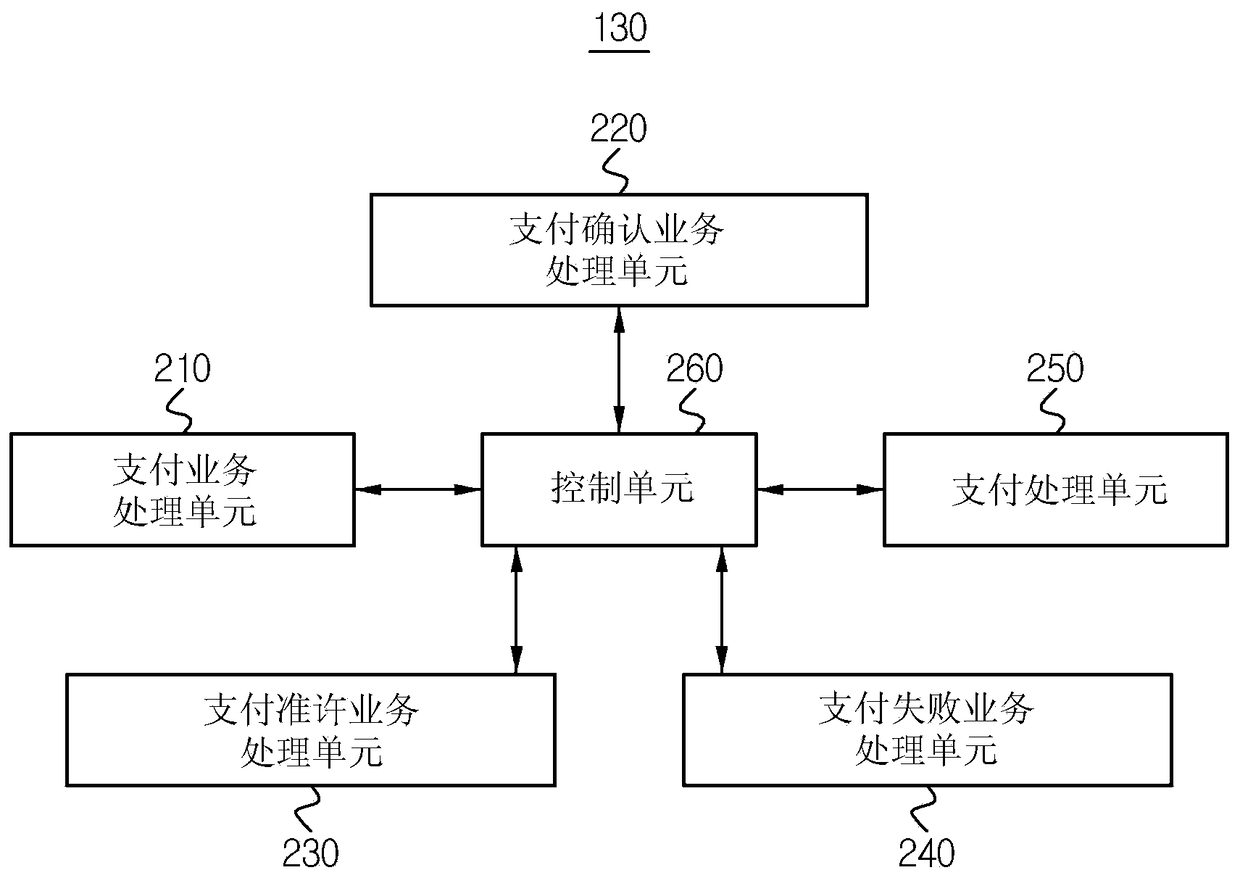
ActiveCN103279865BImprove securityIntegrity guaranteedElectronic credentialsProtocol authorisationPaymentApplication software
The invention provides a payment method, a payment gateway server, a time certificate issuing server and a mobile terminal. The payment method is performed in the PG payment gateway server connectable to the online mall and the mobile terminal. The payment method includes: when receiving a payment business including a payment amount from an online mall, issuing a time certificate to generate a server verification certificate for verifying a PG server that varies according to each business; generating a certificate including a payment amount, time certificate, and The server verifies the payment confirmation service of the certificate to send it to the payment application program; and when the payment confirmation service is successfully approved by the application program, receives from the payment application program including the time certificate and the service-related information for authenticating the mobile terminal. Payment authorization service for terminal verification certificate.
Owner:LG CNS
Semiconductor device and method for accelerating erasure verification procedure
ActiveCN103198853BAvoid long erase verification timesAvoid authentication failuresDigital storagePower semiconductor deviceComputer science
The invention discloses a semiconductor device and a method for accelerating an erase verification procedure by the same. An erase verification correction unit is connected between a damaged bit line in the semiconductor device and a page buffer; through a special line arrangement on the damaged bit line, a grounding switch of the erase verification correction unit can connect the damaged bit line to a grounding voltage during an erase verification procedure, so that the page buffer can receive the grounding voltage to further verify that the damaged bit line has passed the erase verification, thereby substantially saving repeated verification time consumed in the prior art.
Owner:EON SILICON SOLUTION
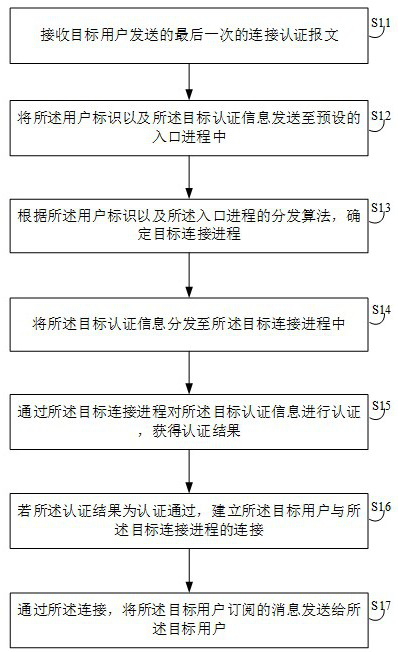
Message sending method, device, server and storage medium
ActiveCN111741014BReduce error rateAvoid authentication failuresTransmissionEngineeringUser identifier
The present invention relates to the technical field of data processing, and provides a message sending method, comprising: receiving the last connection authentication message sent by a target user; sending the user identification and target authentication information carried in the connection authentication message to a preset entry process middle; determine the target connection process according to the user ID and the distribution algorithm of the entry process; distribute the target authentication information to the target connection process; authenticate the target authentication information through the target connection process, and obtain the authentication result; if the authentication result is authentication passed, Establish a connection between the target user and the target connection process; through the connection, send the message subscribed by the target user to the target user. The invention also provides a message sending device, a server and a storage medium. The invention can reduce the error rate of authority authentication. In addition, the present invention also relates to block chain technology, and messages can be stored in the block chain.
Owner:PINGAN INT SMART CITY TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com