A method and device for realizing authentication
An authentication and authentication vector technology, applied in the field of communication, can solve the problems of unfavorable terminals for normal communication, reduce user satisfaction, authentication failure, etc., and achieve benefits for normal communication, avoid authentication failure, and improve user satisfaction Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
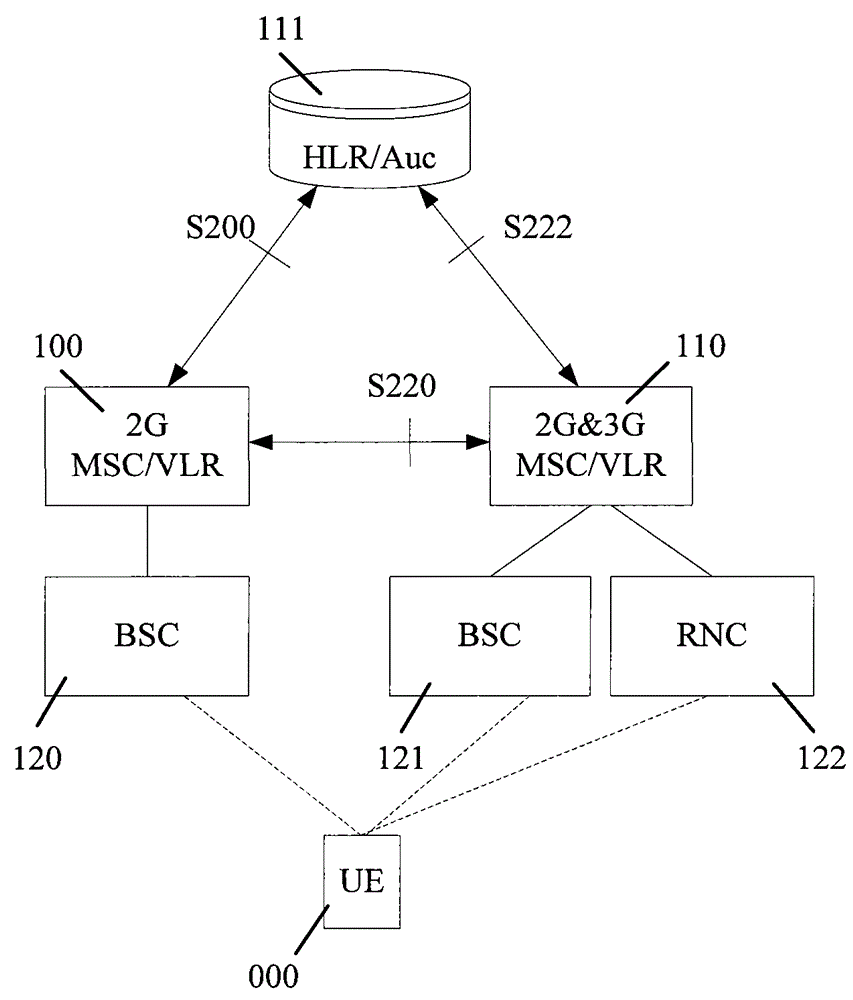
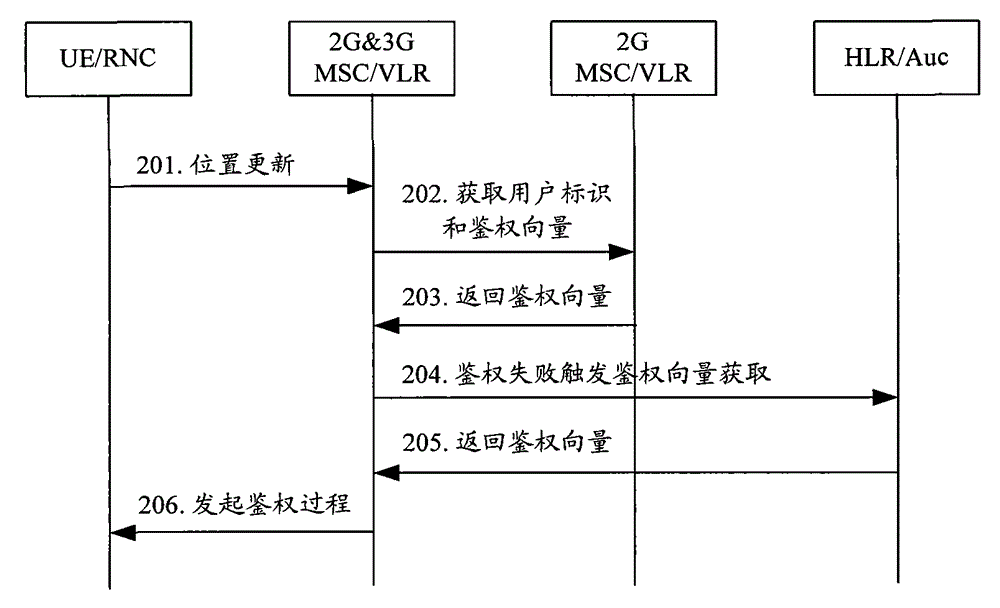
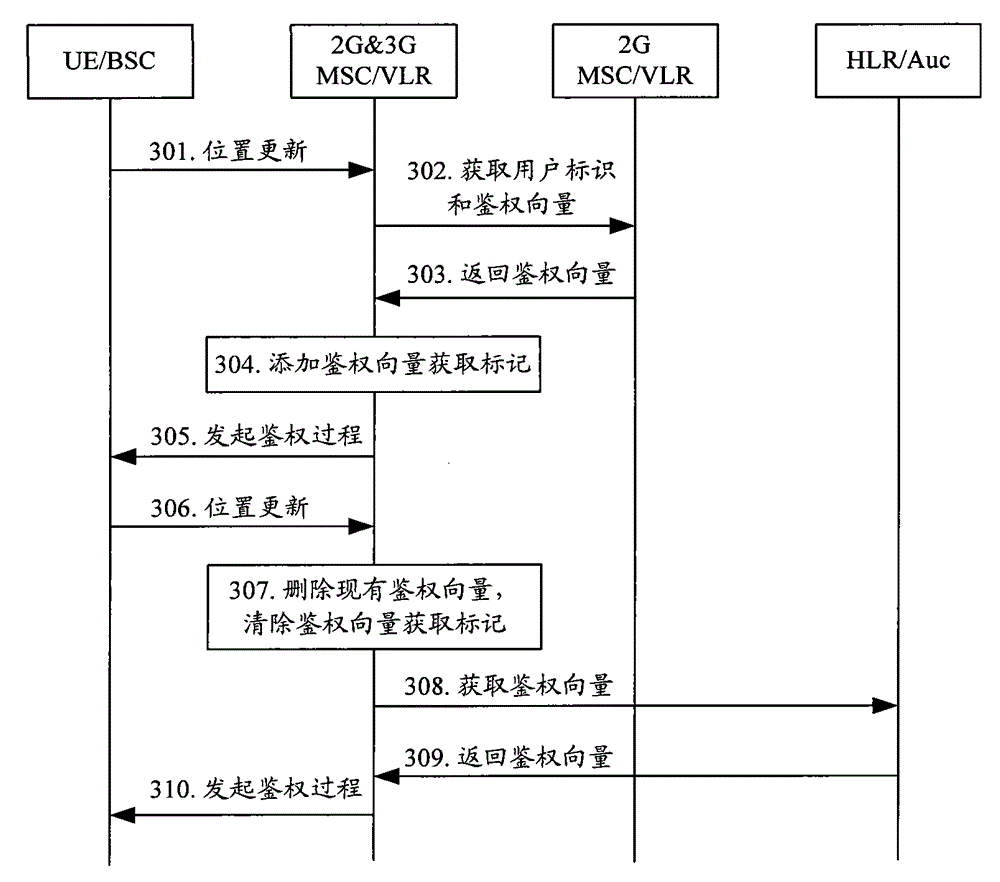
[0048] In practical applications, under the condition of mixed networking, if the authentication vector obtained by 2G&3G MSC / VLR from 2GMSC / VLR is a triplet, in order to reduce the probability of subsequent authentication failure, 2G&3GMSC / VLR can follow the following principles for The authentication vector is processed:
[0049] When the terminal is a 3G terminal and accesses through the 2G network, the 2G&3G MSC / VLR can set the authentication vector acquisition flag related to the user to indicate that the terminal has stored the authentication vector due to the 2G network access. When a terminal roams to a 3G network and accesses a 2G&3G MSC / VLR, it can be judged whether the terminal is set with an authentication vector acquisition flag. If so, it means that the authentication vector stored for the terminal is an inapplicable triplet. Therefore, the authentication vector is directly deleted, and the authentication vector acquisition flag can be cleared, and then the authe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com