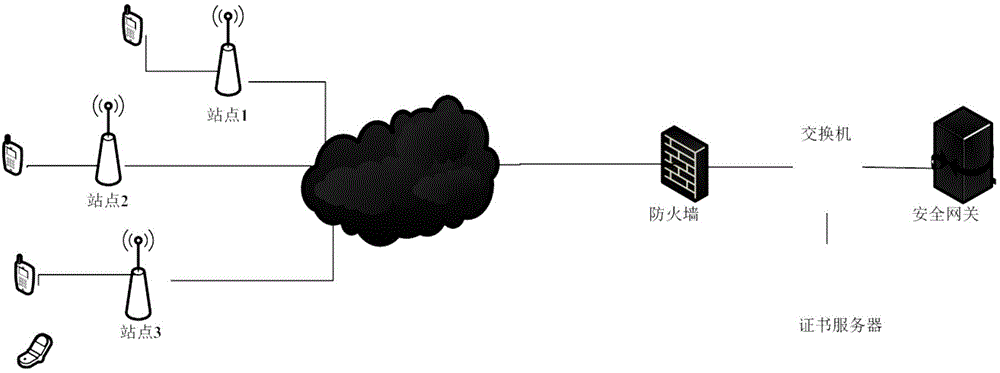
IKE authentication method, IKE initiating terminal, IKE response terminal and IKE authentication system
An authentication method and technology of an authentication system, applied in the field of IKE response terminal and IKE authentication system, can solve problems such as authentication failure and unsupported IKE response terminal authentication type, and achieve the effect of avoiding authentication failure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
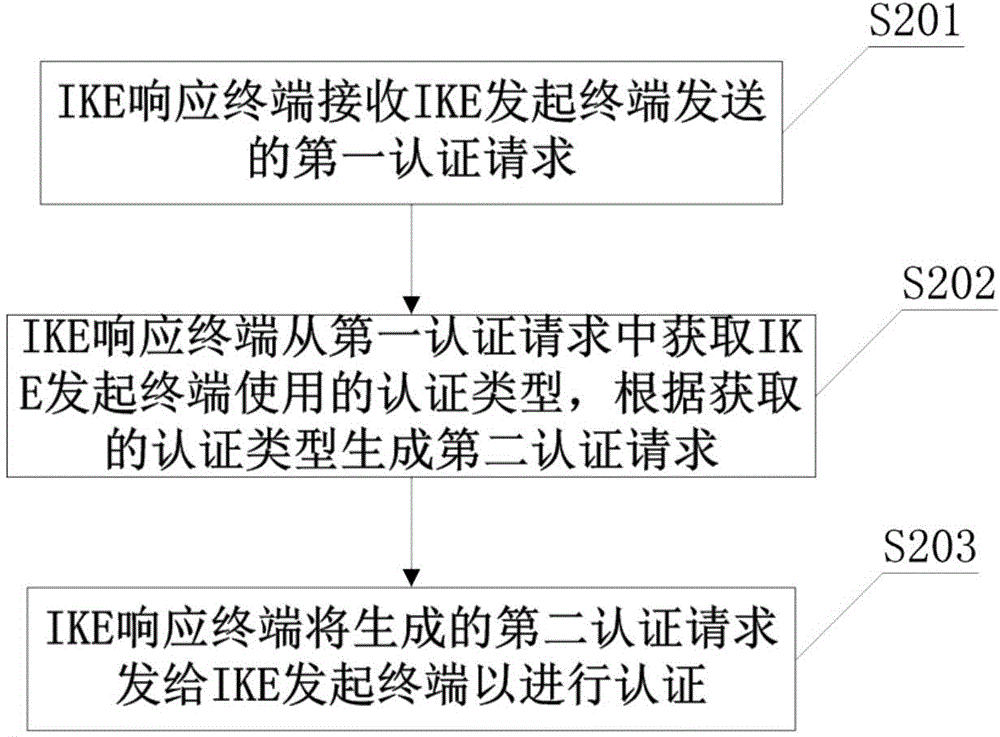
[0048] Please refer to figure 2 As shown, the IKE authentication methods provided in this embodiment include:
[0049] Step 201: The IKE responding terminal receives the first authentication request sent by the IKE initiating terminal, and the first authentication request includes the authentication type used by the IKE initiating terminal;
[0050] Step 202: The IKE responding terminal acquires the authentication type used by the IKE initiating terminal from the first authentication request, and generates a second authentication request according to the acquired authentication type; that is, uses the acquired authentication type to generate a second authentication request to ensure that the IKE initiating terminal Can support the identification of the authentication type;
[0051] Step 203: The IKE responding terminal sends the generated second authentication request to the IKE initiating terminal for authentication.
[0052] In this embodiment, after receiving the first a...
Embodiment 2
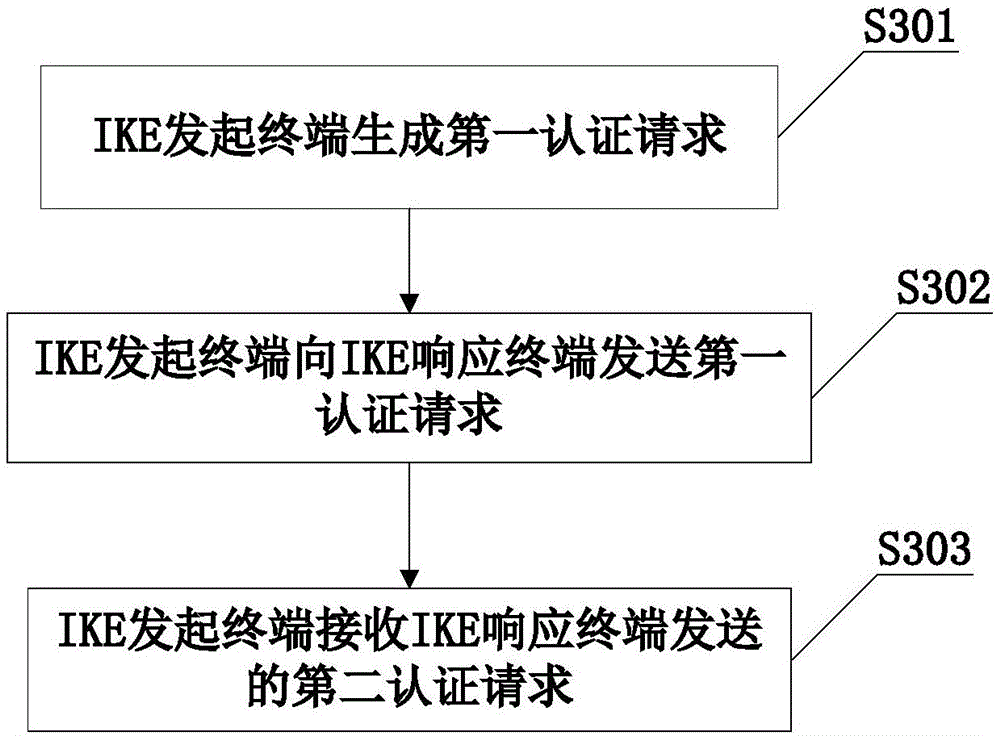
[0060] Please refer to image 3 As shown, the IKE authentication methods provided in this embodiment include:
[0061] Step 301: The IKE initiating terminal generates a first authentication request, and the generated first authentication request includes the authentication type used by the IKE initiating terminal;
[0062] Step 302: the IKE initiating terminal sends a first authentication request to the IKE responding terminal;
[0063] Step 303: The IKE initiating terminal receives the second authentication request sent by the IKE responding terminal; the second authentication request is generated by the IKE responding terminal according to the authentication type included in the first authentication request.
[0064] In this embodiment, the process of generating the first authentication request by the IKE initiating terminal is: the calculation result data obtained by the IKE initiating terminal calculating the first original authentication data according to the locally con...
Embodiment 3
[0070] See Figure 4 As shown, the IKE authentication methods provided in this embodiment include:
[0071] Step 401: The IKE initiating terminal generates a first authentication request, and sends the first authentication request to the IKE responding terminal, where the first authentication request includes the authentication type used by the IKE initiating terminal;
[0072] Step 402: The IKE responding terminal receives the first authentication request sent by the IKE initiating terminal, and obtains the authentication type used by the IKE initiating terminal from the first authentication request;
[0073] Step 403: The IKE responding terminal generates a second authentication request according to the obtained authentication type, and sends the second authentication request to the IKE initiating terminal;
[0074] Step 404: The IKE initiating terminal receives the second authentication request sent by the IKE responding terminal.
[0075] In this embodiment, the IKE init...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com