Automatic identification device for combined address identification
A technology for automatic authentication and verification of devices, which is applied in the fields of collaborative devices, special data processing applications, instruments, etc., and can solve the problems of counterfeiting methods, increasing consumer burden, and failing to inquire about certification.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
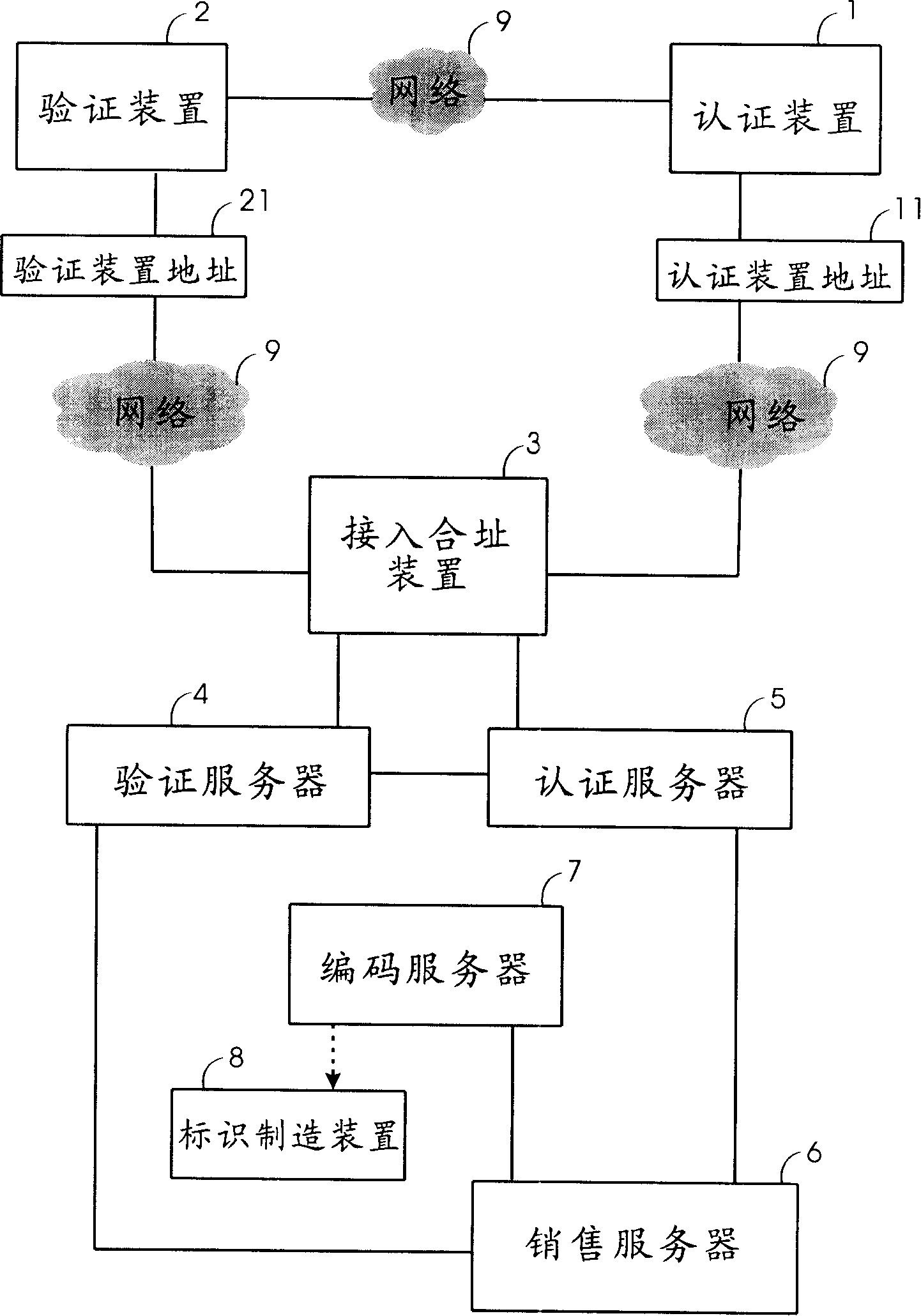
[0073] The structure of the co-location authentication system of the embodiment is as follows: figure 1 shown. The system includes:
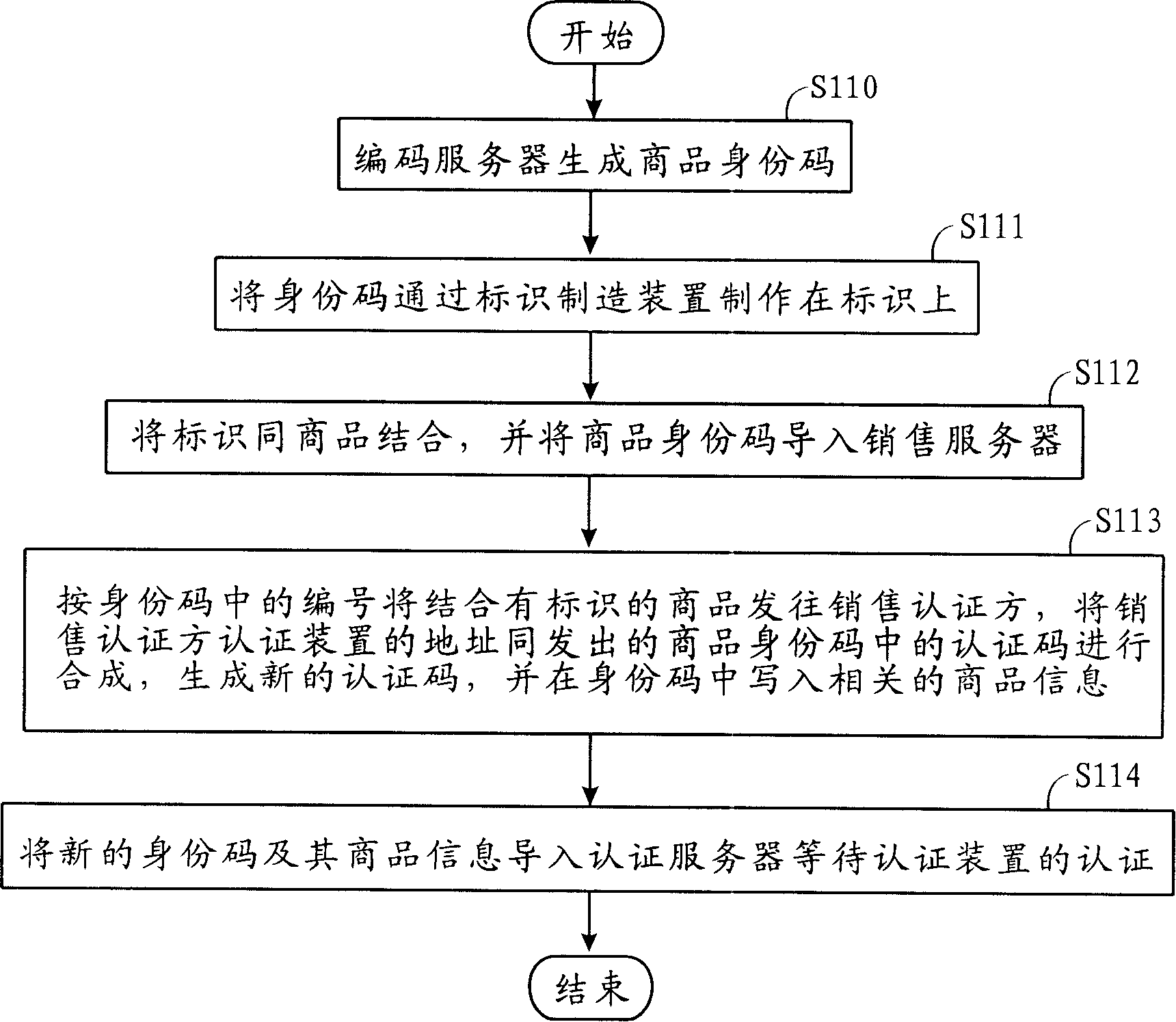
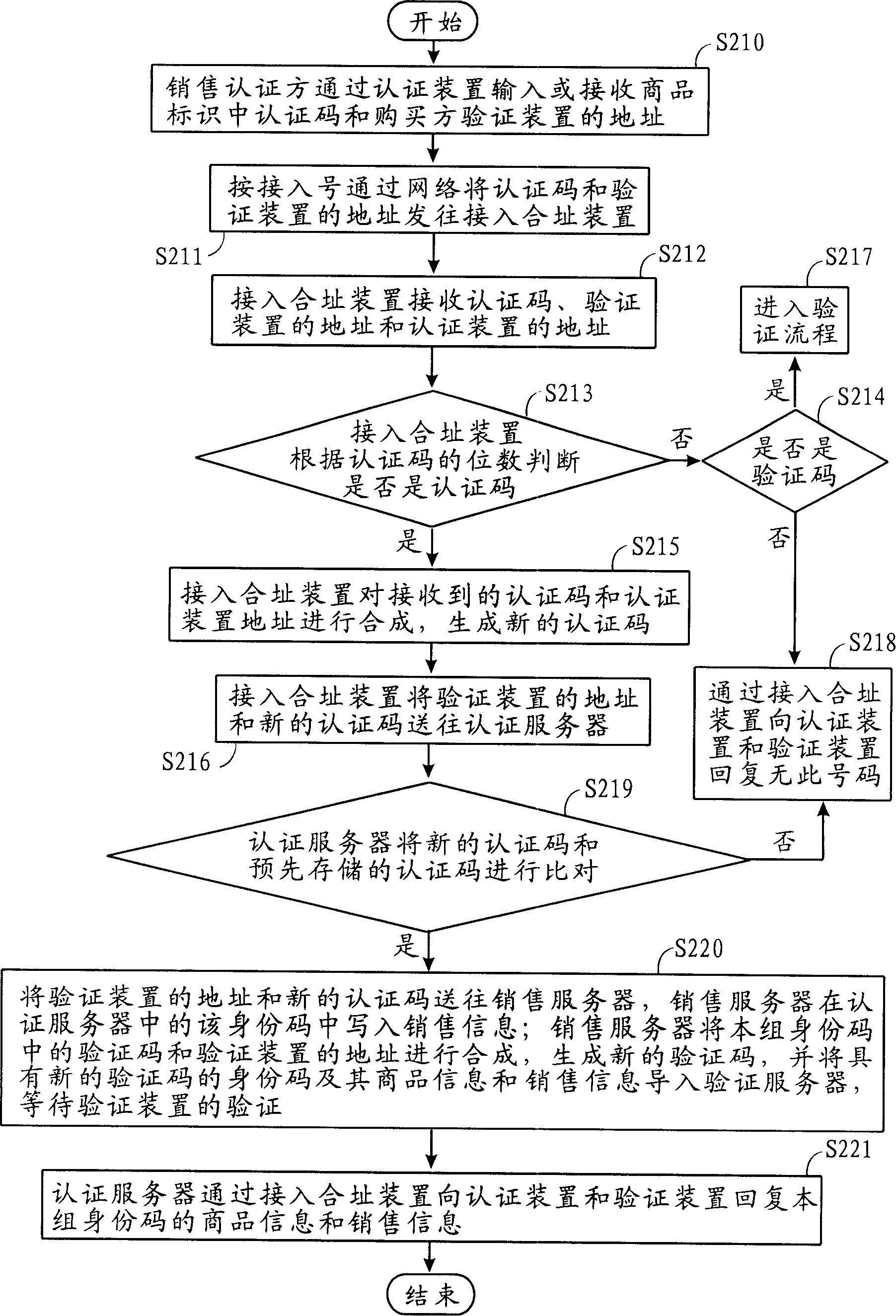
[0074] At least one authentication device 1 and address 11 are connected with the following access addressing device 3 and verification device 2 through the network 9. The authentication device 1 includes: processor, network card, network address, network information receiving and output device, information and address input and receiving device, display, interface, power supply, for inputting or receiving the authentication code in the identity code in the commodity identification and the address 21 of the purchase verification party verification device 2, and send it to the access addressing device 3, with To receive and display the commodity information and sales information sent by the access co-location device 3; the authentication device 1 can use existing network equipment, such as telephones, mobile phones, and PCs, and can also refit o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com