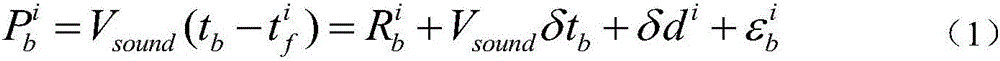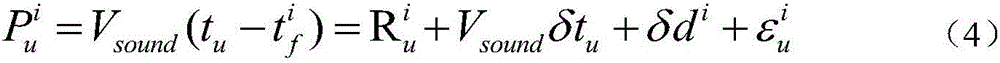Patents
Literature
114results about How to "Confidential" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method suitable for safely migrating data between storage clouds
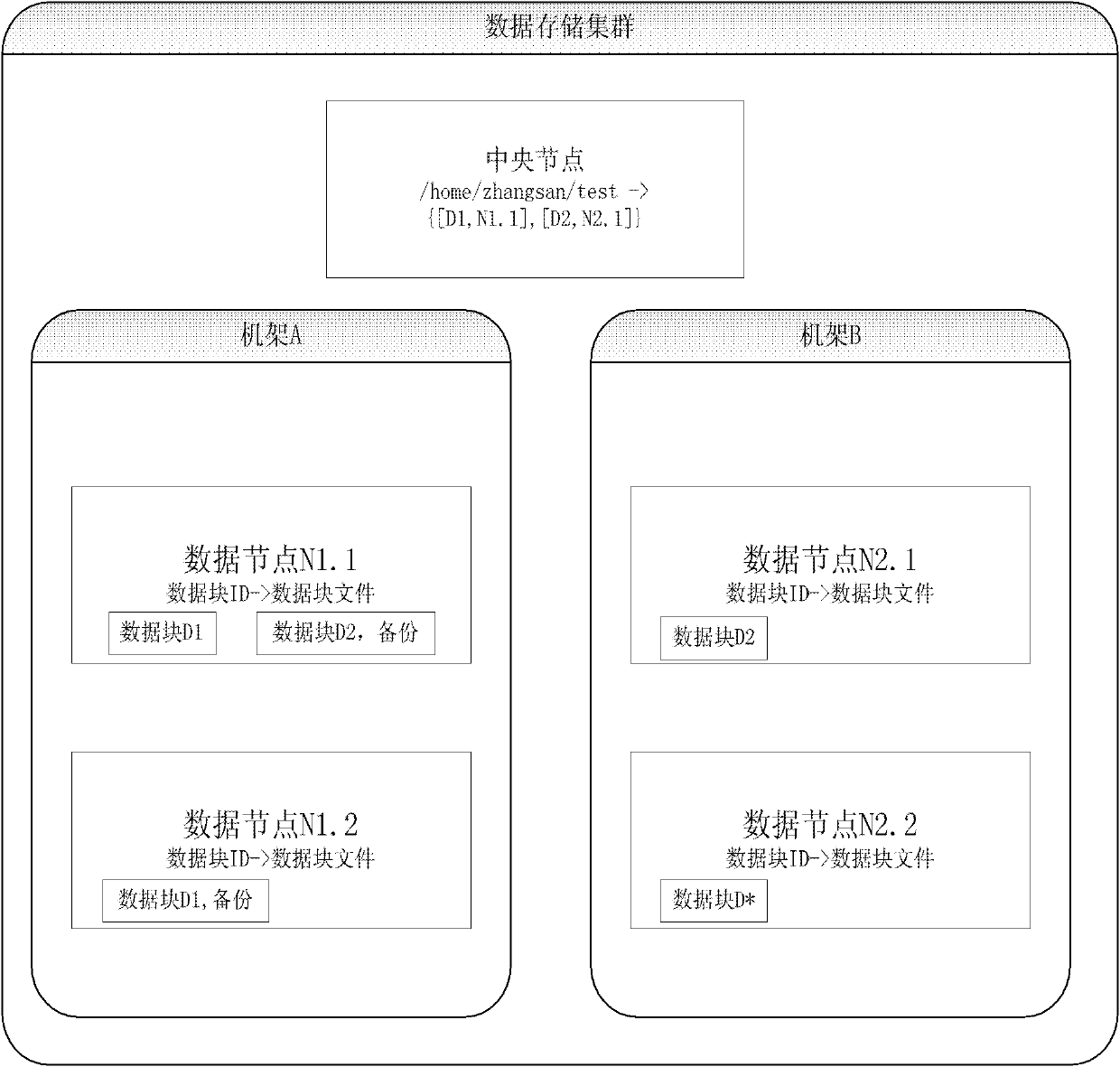
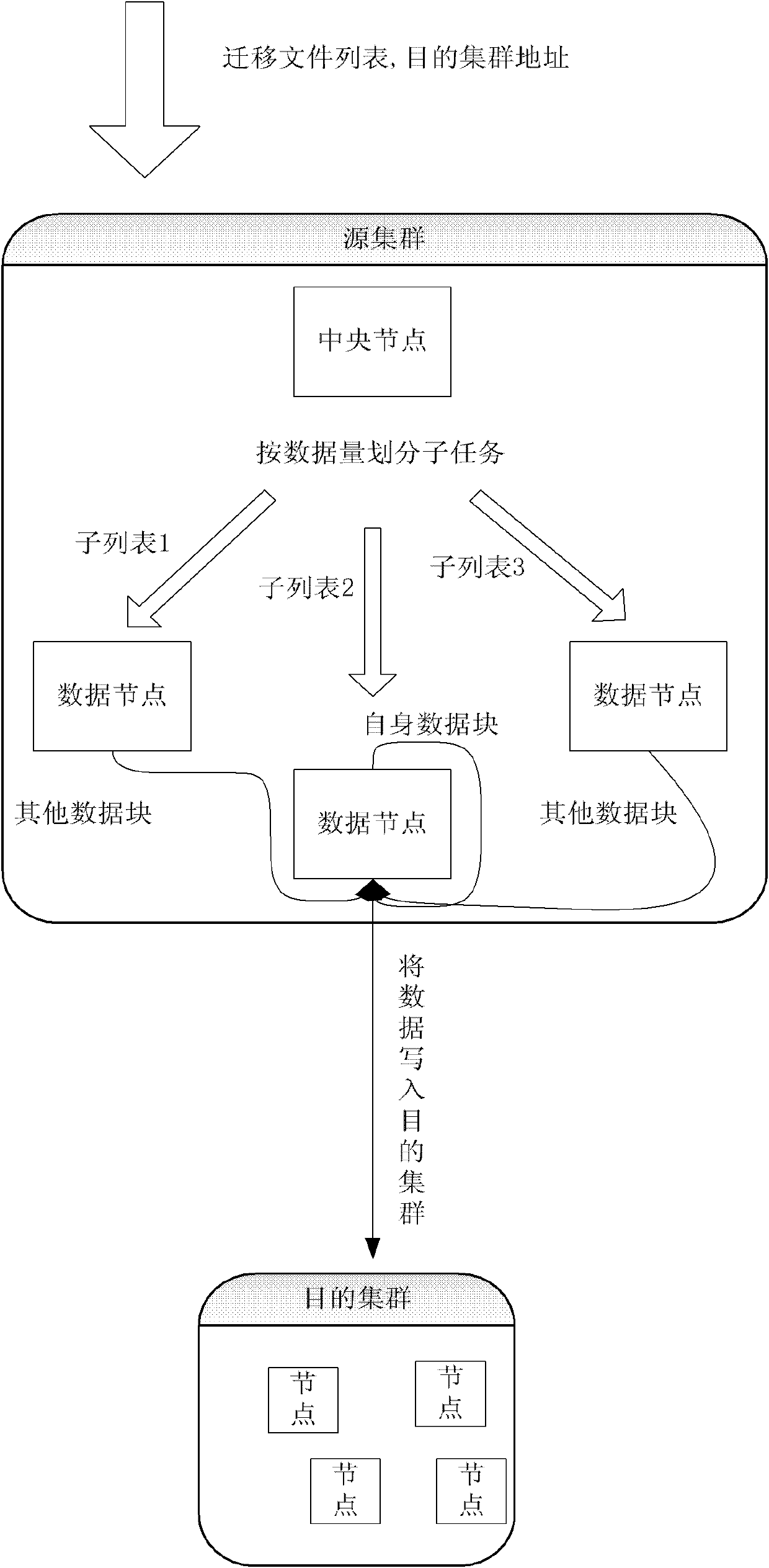
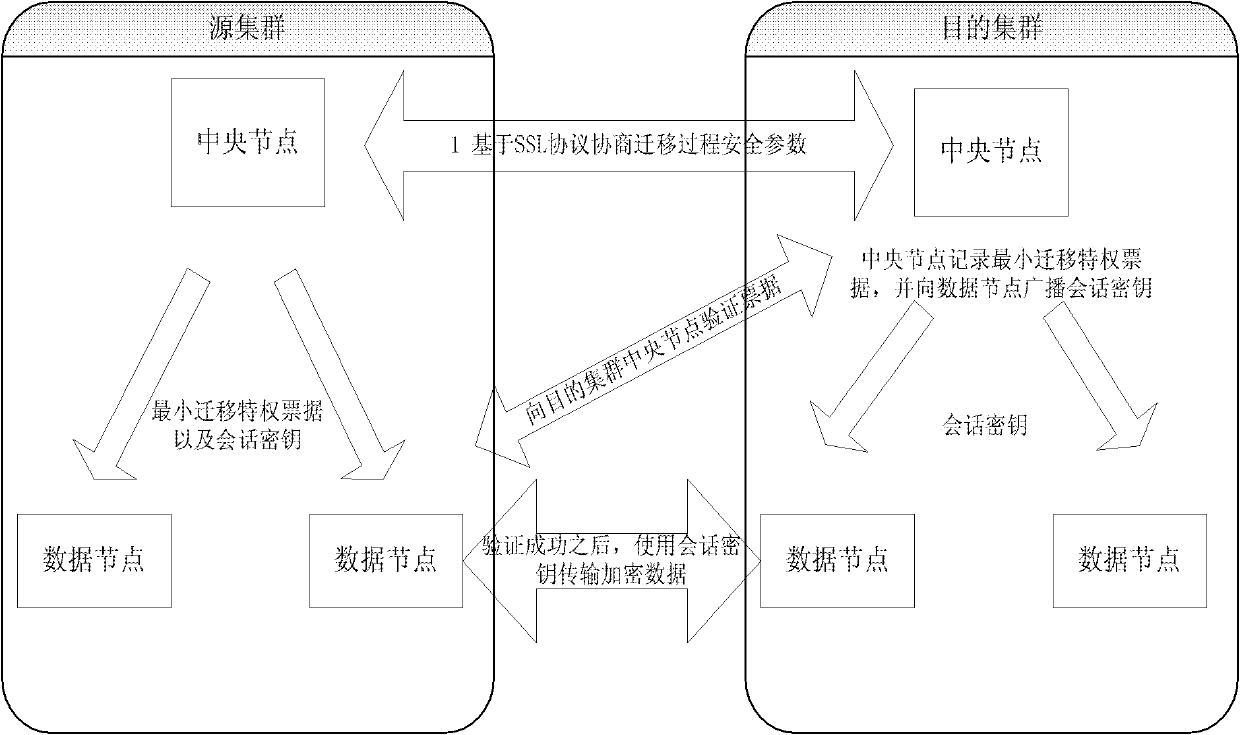
The invention discloses a method suitable for safely migrating data between storage clouds, belonging to the field of a distributed file system. The method comprises the following steps: SSL (Security Socket Layer) connection is set up between a source cluster and a destination cluster; central nodes of the source cluster and the destination cluster generate a secret key through the SSL connection, and the secret key is transmitted to a data node executing the data migration; an approved migration privilege bill is encrypted by the central node of the destination cluster, is then transmitted into the data node executing the data migration in the source cluster, and is recorded; the encrypted migration privilege bill is transmitted to the central node of the destination cluster through the data node executing the data migration to be verified, then the central node of the destination cluster transmits a destination data node address to the data node executing the data migration; and the data node executing the data migration encrypts data to be migrated by the secret key and then transmits the data to the destination data node. The method greatly improves the safety of the data migration between the storage clouds.
Owner:PEKING UNIV
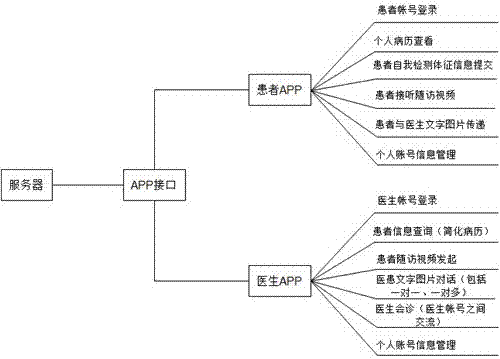
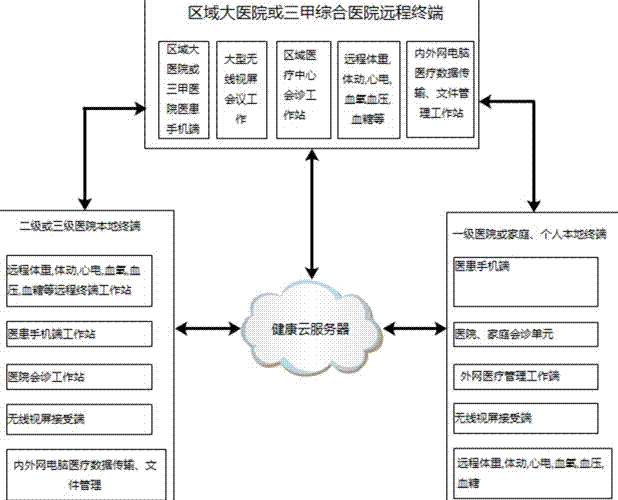
Remote and hierarchical accurate follow-up visit management system for chronic cardiovascular diseases
InactiveCN107169270AConvenient digital health care servicesReliable digital health care servicesSpecial data processing applicationsCommunity orThe Internet
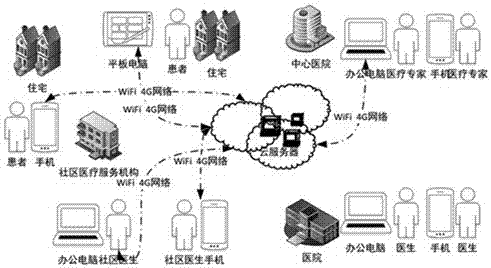
The invention relates to a remote and hierarchical accurate follow-up visit management system for chronic cardiovascular diseases, in particular to remote and accurate follow-up visit of various hospitals, communities or even family members for high-risk patients subjected to mechanotherapy or intervention operations of chronic cardiac failure, auricular fibrillation and cardiovascular diseases. The system comprises a health cloud server, a hierarchical diagnosis and treatment management system and application terminal equipment; multi-permission is set on a client and a server; the system is linked through WiFi (Wireless Fidelity) and / or a network; the health cloud server is provided with a data import function, an information collection function and a data statistic function; and a hierarchical health management platform is constructed. The system can carry out real-time health monitoring, assessment, consultation and diagnosis and treatment at any time and any place on health conditions of chronic disease patients, especially chronic cardiovascular disease patients, provides convenient, reliable, considerate and inexpensive digital health care services and lays a foundation for establishment of an internet hospital.
Owner:NORTHERN JIANGSU PEOPLES HOSPITAL
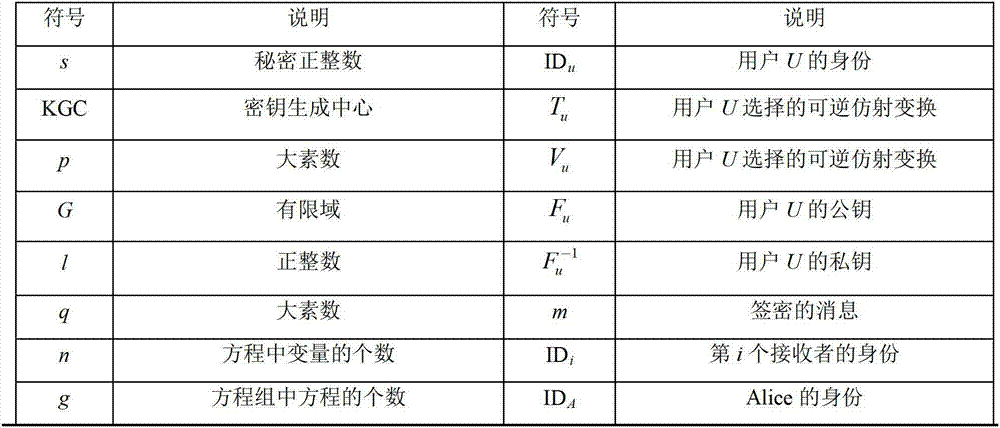
Certificateless multi-receiver signcryption method with multivariate-based cryptosystem
InactiveCN102811125APrivacy protectionImprove securityPublic key for secure communicationUser identity/authority verificationCiphertextConfidentiality
The invention discloses a certificateless multi-receiver signcryption method with a multivariate-based cryptosystem. The certificateless multi-receiver signcryption method is used for solving the technical problem of poor security of an existing certificateless signcryption method. The technical scheme includes that the method includes: firstly, using a key generation center to generate system parameters, and selecting a secure multivariable encryption algorithm to generate keys; and enabling a user U to obtain system private keys of the key generation center and generate the private keys to user keys prior to that a user Alice with the identity IDA sends signcryption messages to a user group L={ID1, ID2,...,IDt}, and accepting or refusing ciphertext sigma by means of un-signcryption. By the aid of the multivariate-based cryptosystem, high security of anti-quantum computation is achieved, and the certificateless multi-receiver signcryption method is still high in security facing attack of a quantum computer. Compared with the background art, the certificateless multi-receiver signcryption method is small in computation and high in security, has the advantages of completeness, confidentiality, unforgeability, forward security, backward security, receiver privacy protection and the like and is capable of resisting existing known attack.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
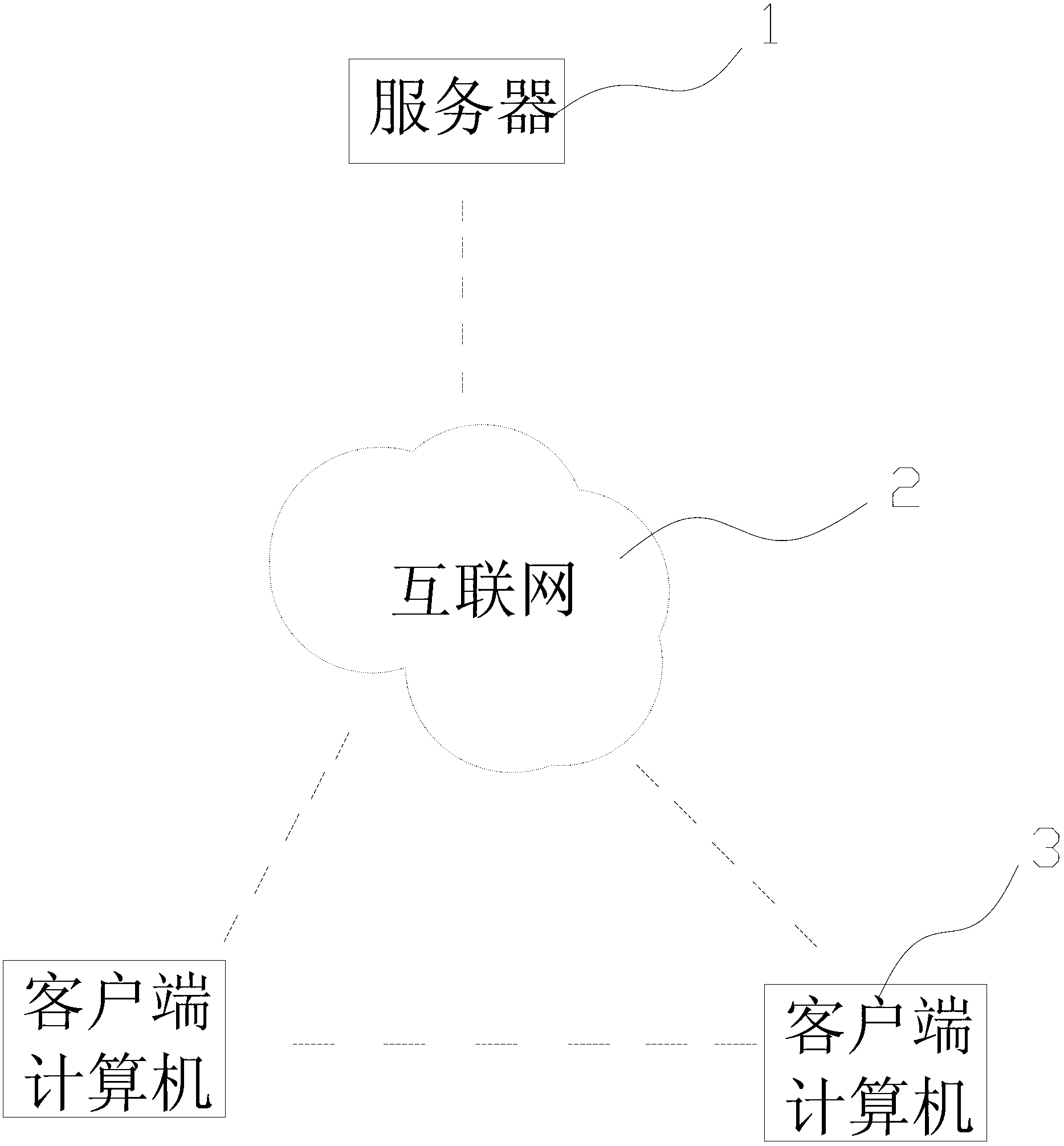
Performance assessment managing method
The invention relates to the field of intelligent management and discloses a performance assessment managing method, adopting a server and at least one client computer, which are connected through Internet or a local area network. The performance assessment managing method comprises the working steps of: step (1), modeling; step (2), inputting information; step (3), requiring assessment; step (4), assessing and analyzing; and step (5), assessing and feeding back. According to the performance assessment managing method, an assessor (manager) can conveniently and rapidly set self-help performance assessment index and rule in a system definition format on any computer terminal based on the Internet, and also can carry out inquiring and operation; and an assessed person can conveniently and rapidly obtain self assessment information from any computer based on the Internet and carries out operation. The method disclosed by the invention is carried out based on the Internet and is not limited by time and space, so that the time and the cost of two parties are extremely saved, and the performance assessment managing method is extremely easy to operate and has certain confidentiality; and therefore, the performance assessment managing method is a helpful tool for carrying out the performance assessment by enterprises and is extremely good for popularizing and using in performance assessment managing work.
Owner:SHENZHEN HALIS IOT TECH
Cluster communication method and network side device
ActiveCN101771439AConfidentialA large amount of synchronous informationSynchronisation arrangementNetwork topologiesConfidentialityDistributed computing
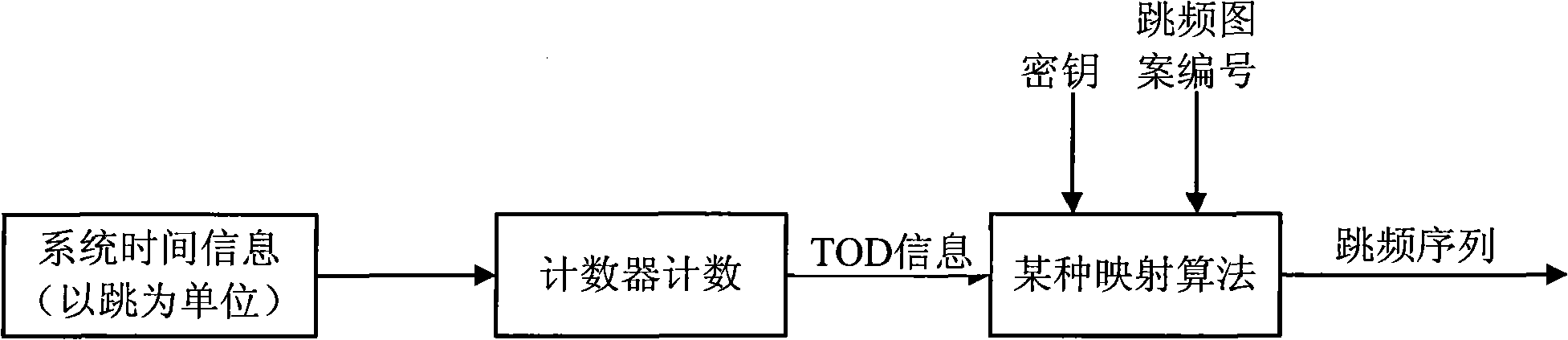
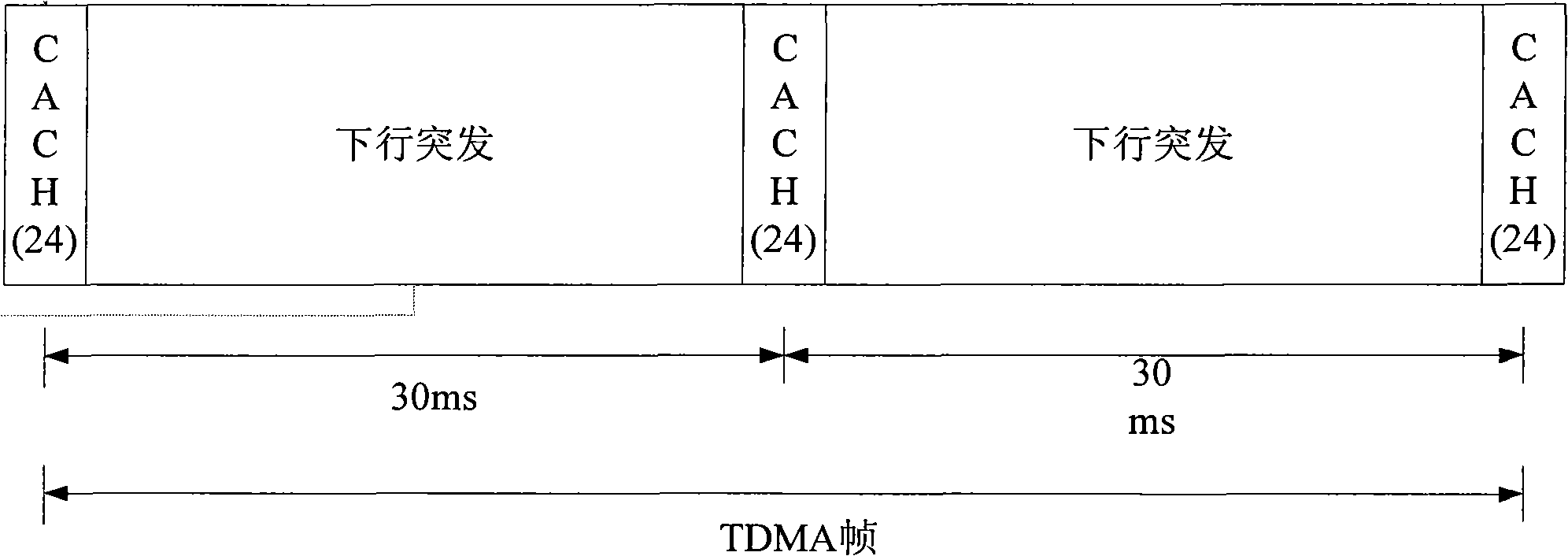
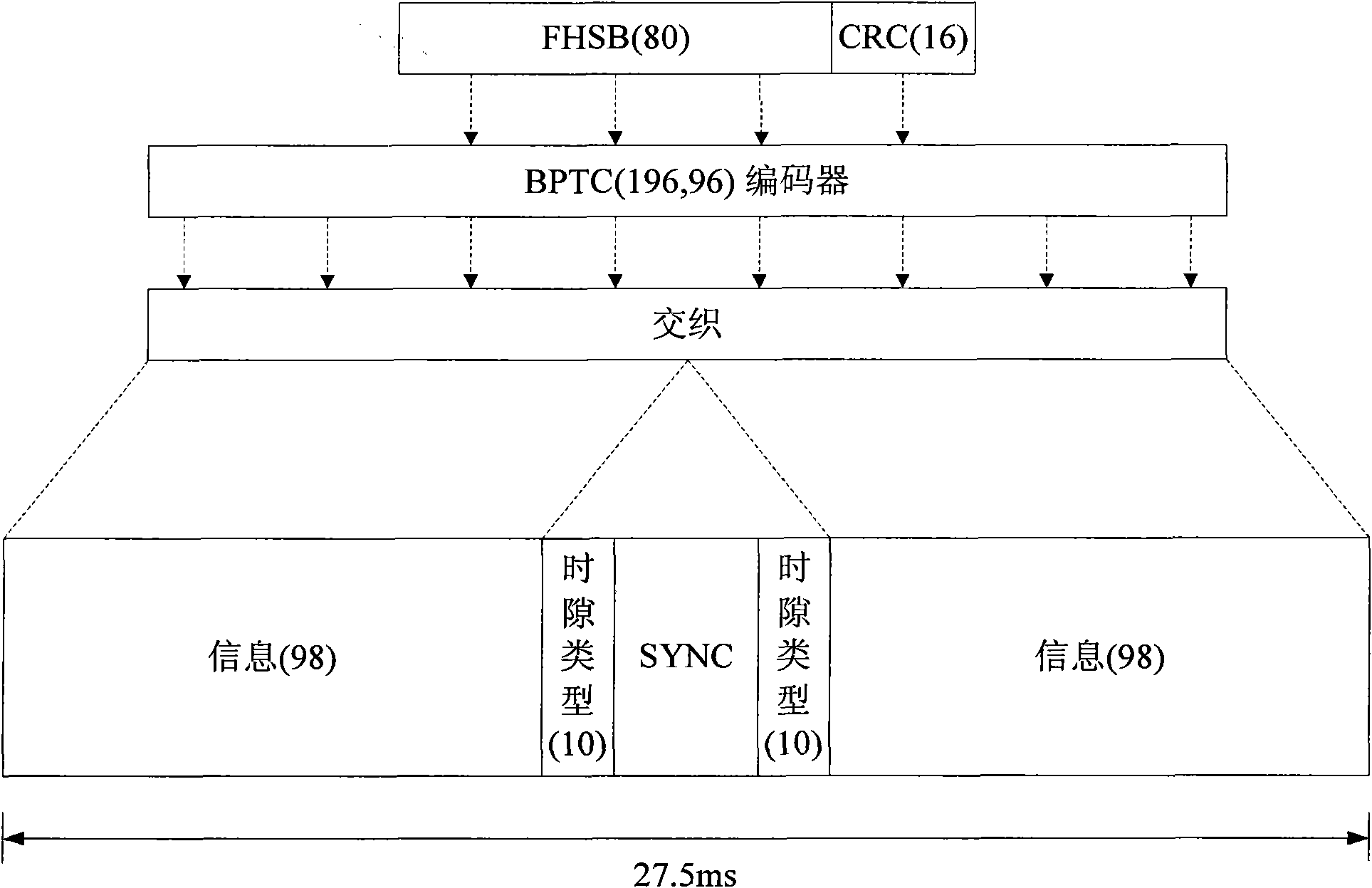
The invention relates to the field of communication and provides a cluster communication method and a network side device. The method comprises the following step: in frequency-hopping synchronization of the cluster communication, a frequency-hopping synchronization information frame which comprises frequency-hopping synchronization information is sent to a mobile terminal which needs communication. As the frequency-hopping synchronization information is sent in a way combining a synchronization prefix method and an independent channel method, the sent synchronization information is abundant; the synchronization establishing time is short, and simultaneously, the format of the sent synchronization information adopts a TOD format which is similar to the synchronization prefix method, thus leading to certain confidentiality; and moreover, the cluster system sends the frequency-hopping synchronization information in an independent traffic channel, and therefore, the realizing technical difficulty is not high.
Owner:HYTERA COMM CORP
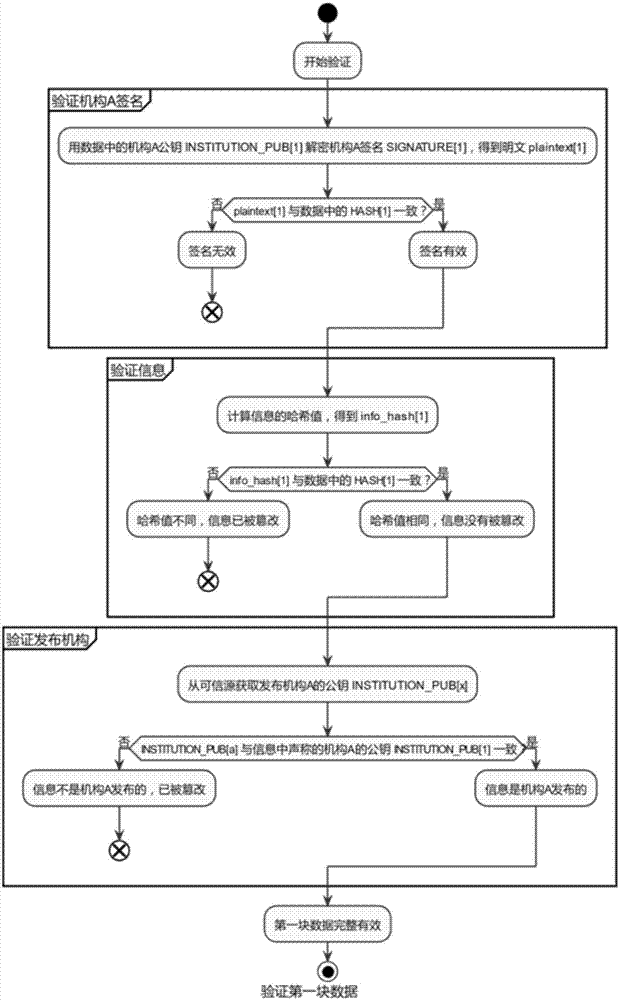
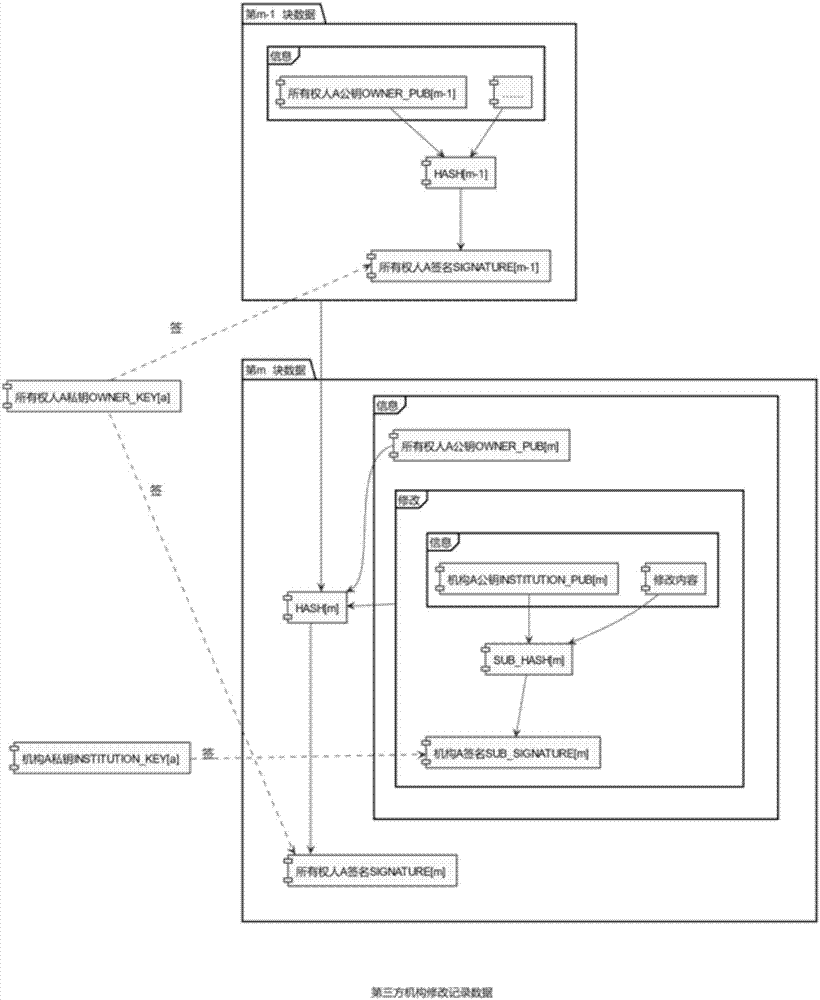
Block chain-based house history generation method
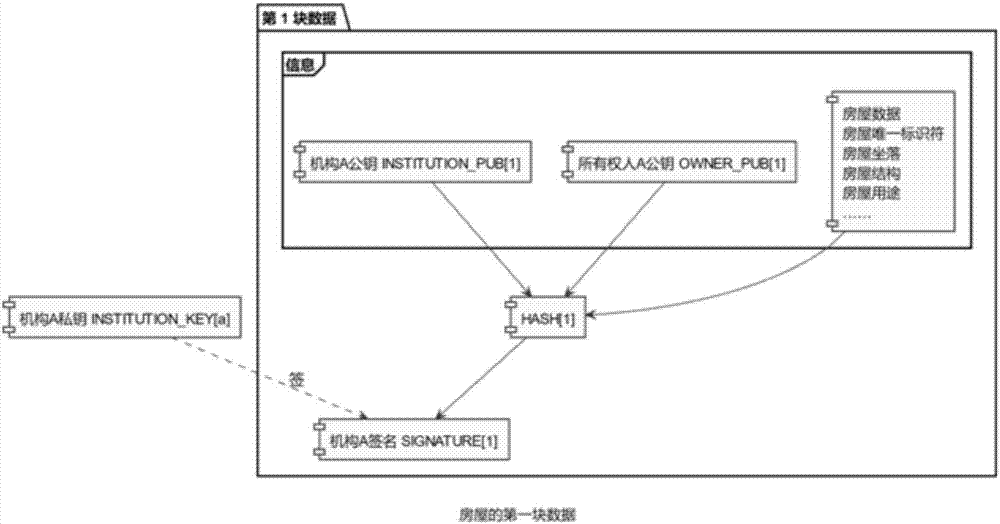
ActiveCN107506661ANon-tamperableOpenData processing applicationsDatabase distribution/replicationTamper resistanceComputer hardware
The invention relates to the field of real estates, and discloses a block chain-based house history generation method. The method comprises the following steps of: firstly filling information, carrying out operation by a block chain, generating first block data of a house, verifying validity of the first block data, and storing the first block data in the whole block chain; when the house state changes, for example, data updating or owner alternation is carried out, obtaining data of the last block from the whole block chain, filling modification content or alternation content, carrying out operation by the block chain, generating the current block data, verifying effectiveness of a signature of the current block data and integrity of the modification content or the alternation content, and storing the current block data in the whole block chain. According to the method, uniform house history is formed, and the disclosed information cannot be tampered, so that the correctness and tamper-resistance of the house information are ensured.
Owner:HENAN ZHENER INTERNET TECH
Three-factor identity authentication and key negotiation method in multi-server environment
ActiveCN108965338AAchieve securityImprove confidentialityKey distribution for secure communicationPublic key for secure communicationConfidentialityKey-agreement protocol
The invention discloses a three-factor identity authentication and key negotiation method in a multi-server environment. The method comprises the following phases: a registration center initializationphase, a server registration phase, a client registration phase and an authentication and key negotiation phase, and a functional portion of client password replacement. By adoption of the three-factor identity authentication and key negotiation method disclosed by the invention, the participation of a trusted third party registration / authentication center is not required in the authentication phase, thus reducing the communication steps and costs, improving the protocol operation efficiency and ensuring the security of the protocol at the same time. The mutual authentication of the two parties is realized by a static DH value shared by the client and the server uniquely, and the confidentiality of a session key is realized by a dynamic DH value shared by both parties uniquely and used for calculating the session key so as to ensure the security of an established channel. The three-factor identity authentication and key negotiation method disclosed by the invention has authenticationproperty and confidentiality, is secure and provides an efficient multi-server three-factor identity authentication and key negotiation protocol on the communication.
Owner:HANGZHOU NORMAL UNIVERSITY
Device for configuring multimedia acquisition devices by using multimedia
ActiveCN102932543AReduce device countLow manufacturing costSubstation equipmentInput/output processes for data processingCommunication interfaceAudio frequency
The invention relates to the technical field of customization of multimedia acquisition devices and discloses a device for configuring multimedia acquisition devices by using multimedia. The method comprises the following steps that: firstly, software is installed on configuration device is operated firstly, and the software automatically encodes configuration information into a picture, a video or an audio on the configuration device according to the information input by a user or information automatically detected by the software or the information automatically detected by configured equipment and acquired by the software; then, the picture, the video or the audio are outputted to the configured device; and finally, the configured device decodes an inputted picture or video or audio, and carries out automatic configuration according to the configuration information obtained through decoding. According to the invention, the configured device and the configuration device are not required to be provided with other specialized communication interface devices, and the transmission of configuration information is implemented by using existing indispensable s image or voice inputting / outputting devices on the two devices, thereby reducing the number of devices on the configured device, and reducing the manufacturing cost of the device.
Owner:深圳市天和荣科技有限公司
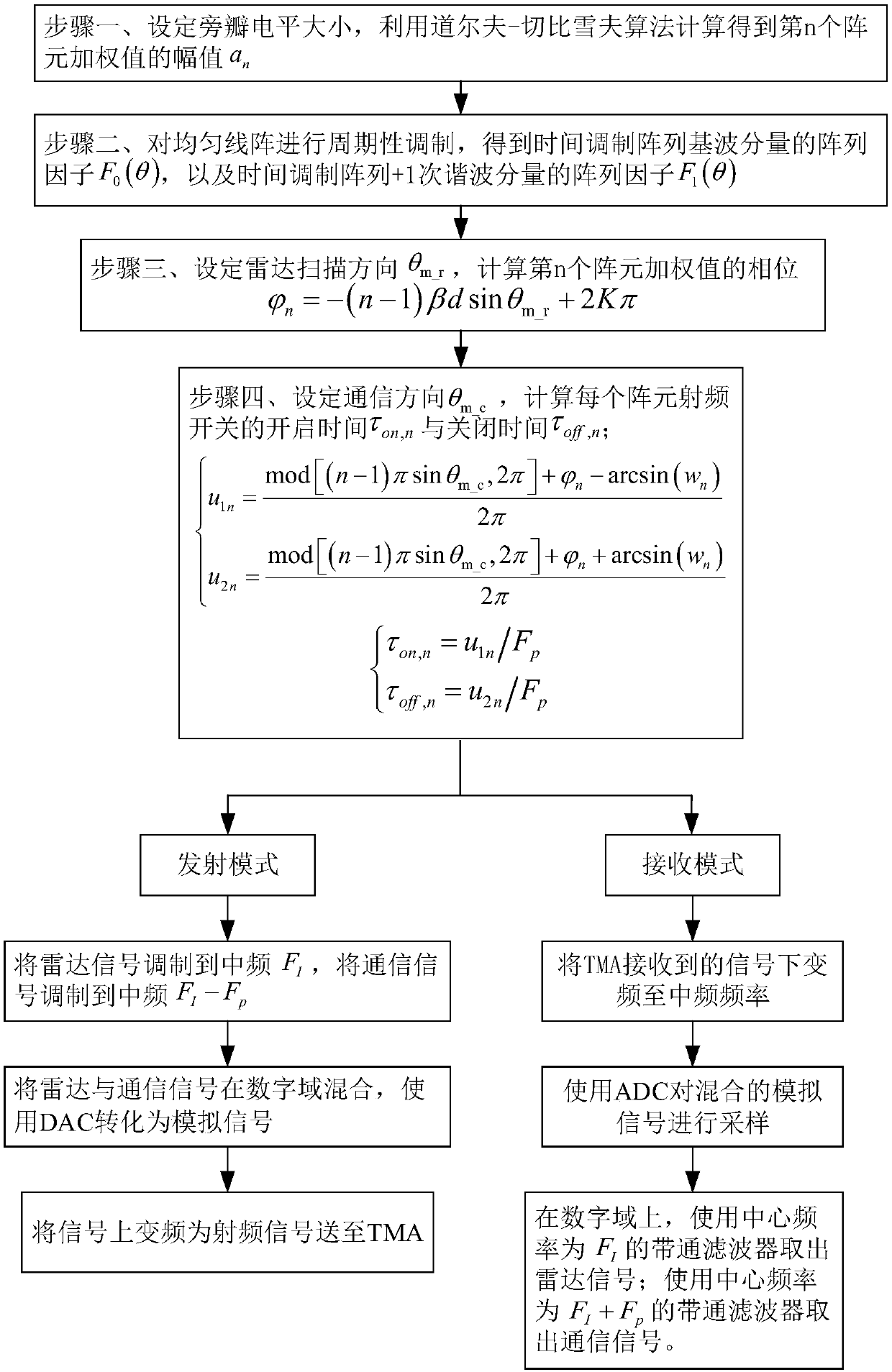
Time modulation array based communication and radar integrated design method
InactiveCN108196229AReduce distractionsSave Spectrum ResourcesWave based measurement systemsBand-pass filterArray element
A time modulation array based communication and radar integrated design method is provided. The invention relates to a communication and radar integrated design method. The invention solves the problem that the existing integrated waveform design methods have high complexity, the time division based integrated methods are low in efficiency, the reliability of the space division based integrated methods are low, and scanning detection cannot be performed. The invention comprises: 1, calculating and obtaining an amplitude of a nth array element weighted value; 2, periodically modulating a uniform linear array, and obtaining an array factor of a fundamental component of a time modulation array and an array factor of the time modulation array +a first harmonic component; 3, calculating a phaseof the nth array element weighted value; 4, calculating the turn-on time and the turn-off time of each array element RF switch; and 5, mixing and sending a radar signal and a communication signal tothe time modulation array in the transmit mode; simultaneously receiving the radar signal and the communication signal in the receiving mode, and using a band pass filter to perform distinguishing. The invention is used in the field of communication and radar integration.
Owner:HARBIN INST OF TECH
Screensaver unlocking method for intelligent terminal
InactiveCN103870152AComplex unlock passwordIncrease the difficulty of crackingDigital data authenticationInput/output processes for data processingGraphicsPassword
The invention discloses a screensaver unlocking method for an intelligent terminal. The method comprises the following steps: (1) presetting an unlocking password, wherein the password is a single password or a composite password selected from time duration, sequence, location, graph and number; (2) pressing a hot key in a screen-saving state; (3) displaying a ball sport scene on a screen, wherein the ball sport scene is displayed in a static or dynamic manner corresponding to a password to be input; (4) inputting the single password or composite password by an operator in the ball sport scene, wherein the ball sport scene generates corresponding dynamic display corresponding to a password inputting process; (5) when the input password is correct, unlocking a screensaver.
Owner:宋小民
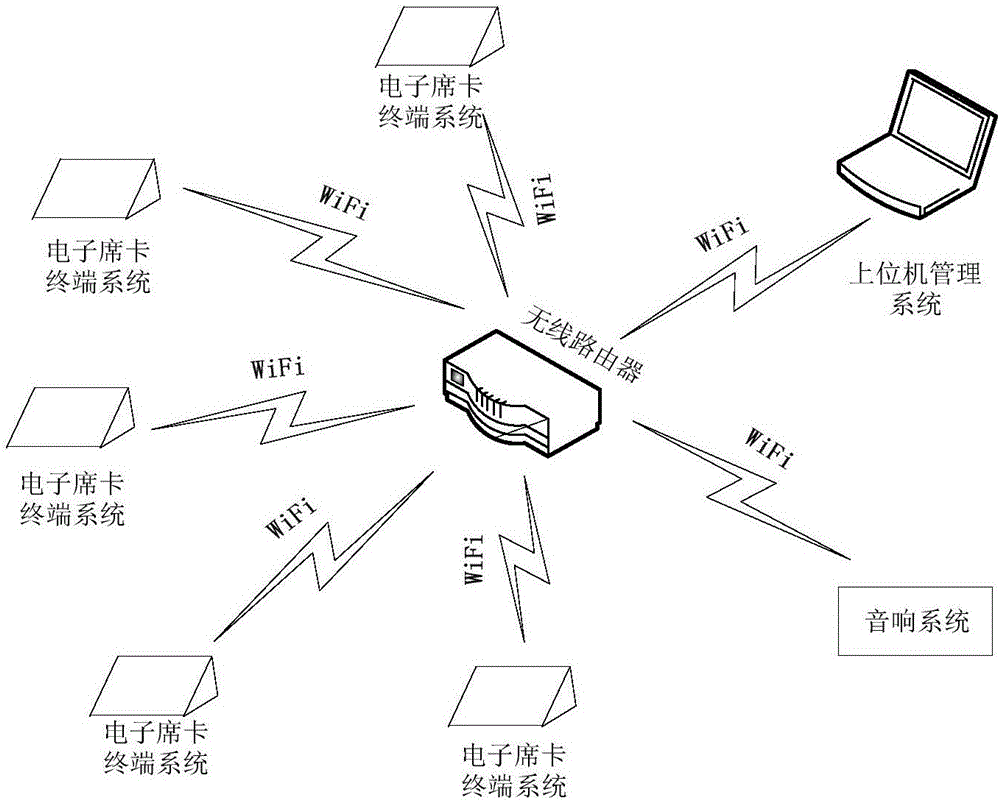
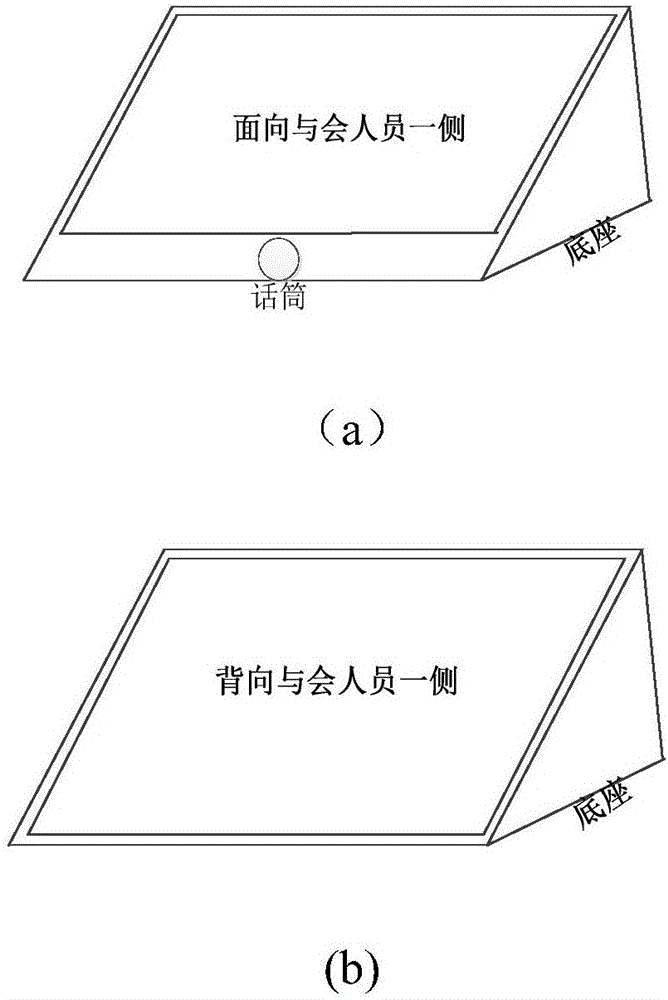
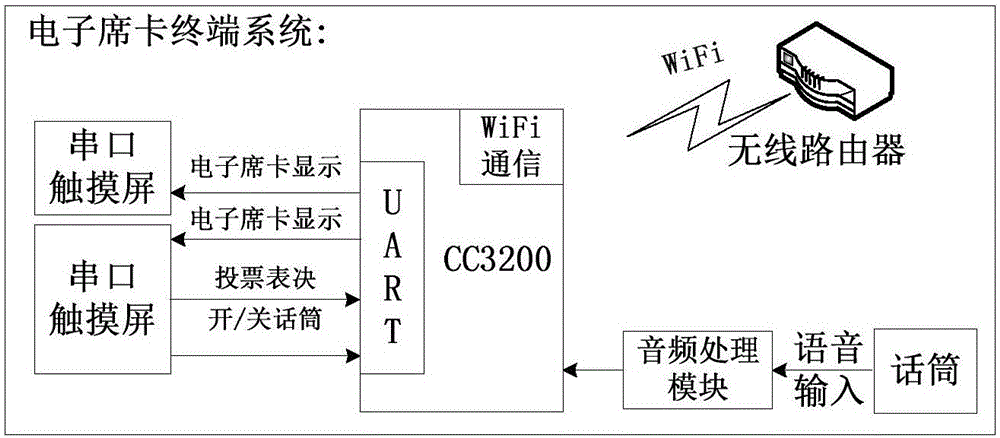
WiFi-based intelligent electronic name card system and operation method
InactiveCN106530997AIncrease flexibilitySave human resourcesVoting apparatusInput/output processes for data processingLoudspeakerAudio electronics
The invention relates to technologies of intelligent electronic name cards and specifically relates to a WiFi-based intelligent electronic name card system and an operation method. The intelligent electronic name card system comprises an upper computer management system, an electronic name card terminal system and a loudspeaker system, wherein the upper computer management system, the electronic name card terminal system and the loudspeaker system are connected in a wireless manner; the upper computer management system is used for intelligent ranking, electronic name card display, voting management, microphone management, system setting and WiFi communication; the electronic name card terminal system is used for the electronic name card display, voting input, microphone input and the WiFi communication; and the loudspeaker system is used receive digital voice signals and convert the signals into analog signal amplified output and the WiFi communication. The intelligent electronic name card system can cope with emergencies, is highly flexible and saves a lot of human resources; additional microphones do not need to be installed, and a voting function avoids injustice brought by manual vote statistics; and a wireless communication manner is used, so complicated equipment and wiring are avoided, so a meeting place becomes concise and efficient.
Owner:HUBEI UNIV OF ARTS & SCI
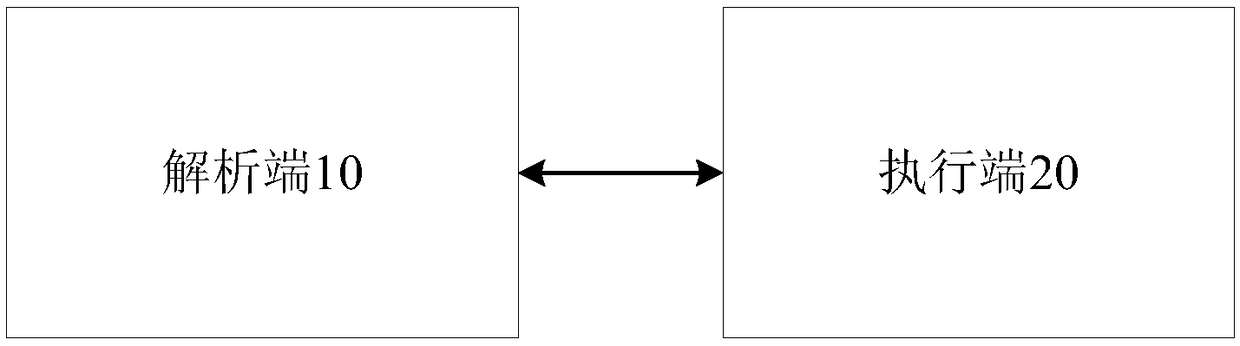
Data processing method, device, apparatus, and storage medium
ActiveCN109255209AProtection of rights and interestsConfidentialDigital data protectionProgram/content distribution protectionDecoding methodsConfidentiality
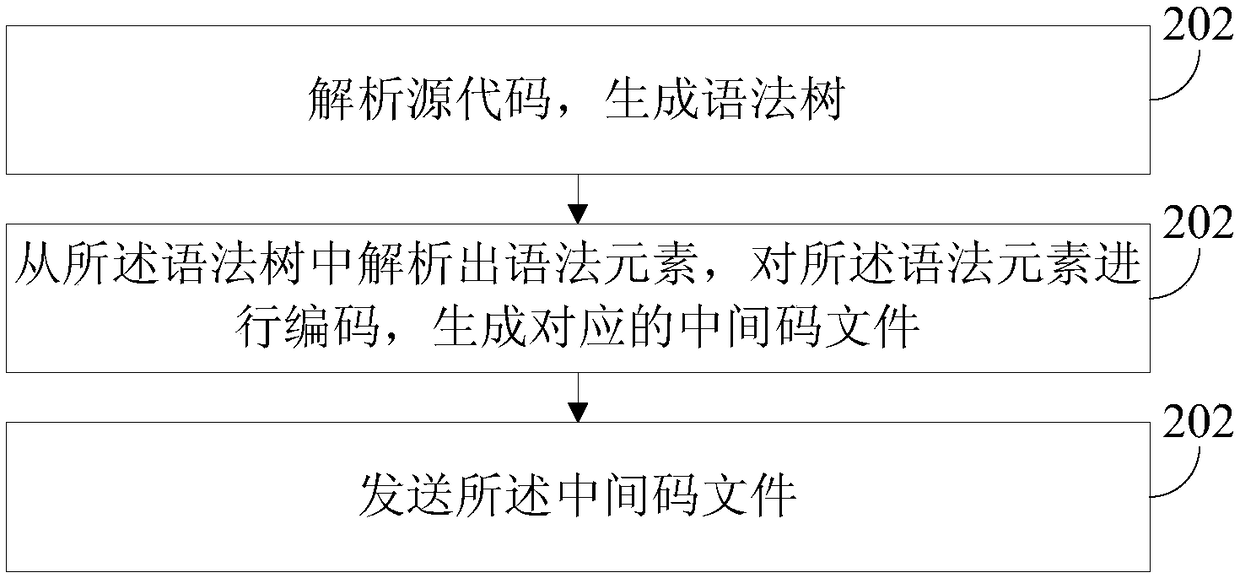
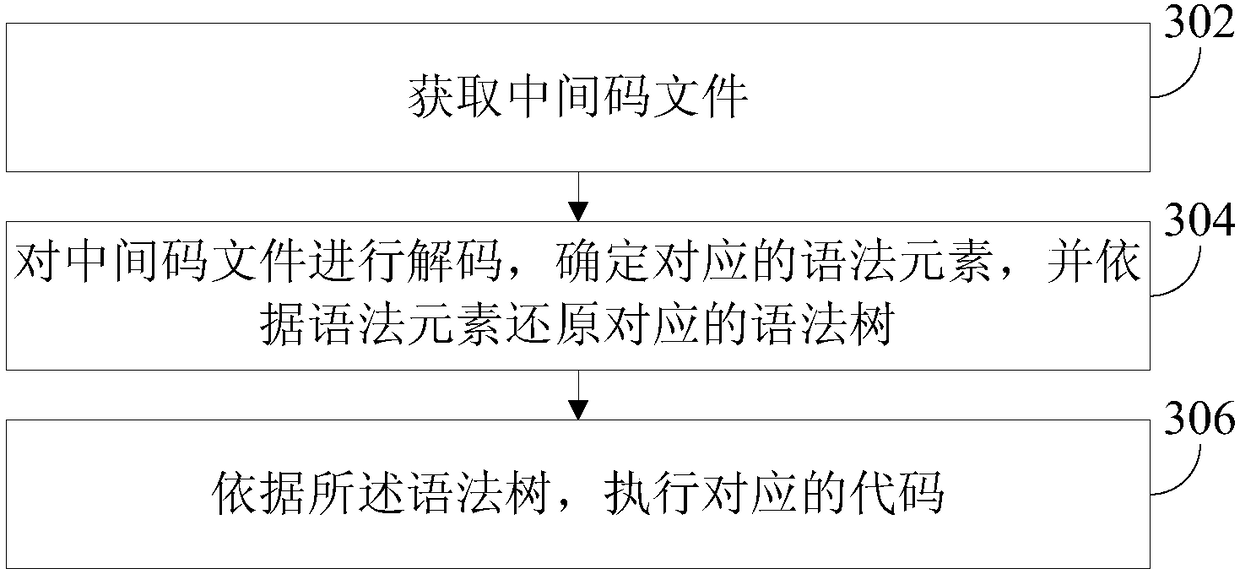
Embodiments of the present application provide a data processing method, device, apparatus, and storage medium to improve the security of source code. The method comprises the following steps: parsingthe source code to generate a syntax tree; Parsing a syntax element from the syntax tree, encoding the syntax element to generate a corresponding intermediate code file; Sending the midamble file. The midamble file is generated in the process of parsing and encoding. The midamble file is unreadable in the case of unknown encoding and decoding method, and has certain confidentiality.
Owner:ALIBABA GRP HLDG LTD
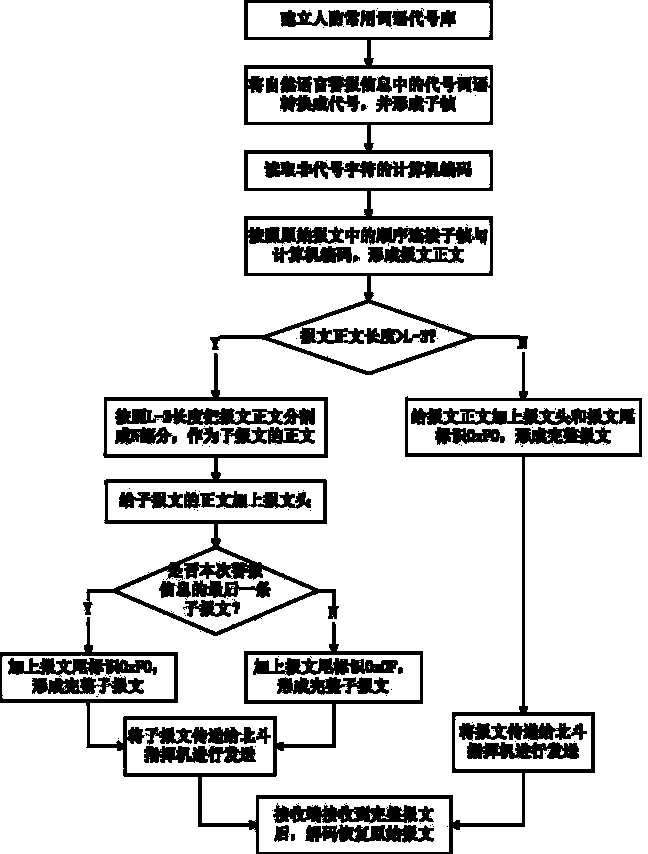
Civil air defense emergency alert information message compression encoding method based on Beidou communication functions
InactiveCN104066117ASend lessShorten sending timeNetwork traffic/resource managementNetwork topologiesComputer number formatCommon word
The invention provides a civil air defense emergency alert information message compression encoding method based on Beidou communication functions. The method comprises: a civil air defense common word code library is built; words included in the code library are expressed with corresponding codes and the codes are encapsulated into subframes; characters not included in the code library are expressed with corresponding computer codes; the computer codes and the subframes are connected according to the order of the original message to form a message text, and a message header and a message tail are added to the message text to form a to-be-sent message; it is determined if the length of the to-be-sent message is greater than the maximum length, L bytes, permitted by the Beidou system, and if so, the to-be-sent message is segmented into a plurality of sub-messages, the length of which is no greater than L bytes, for sending, each sub-message having a message header and a message tail; otherwise, the to-be-sent message is sent directly. The method can reduce the length of the message and the sending times of a long message. The alert information notifying time is shortened, and the flow is saved. The method is simple and easy to implement with good reliability.
Owner:ELECTRONICS ENG COLLEGE PLA
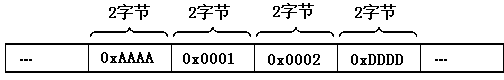
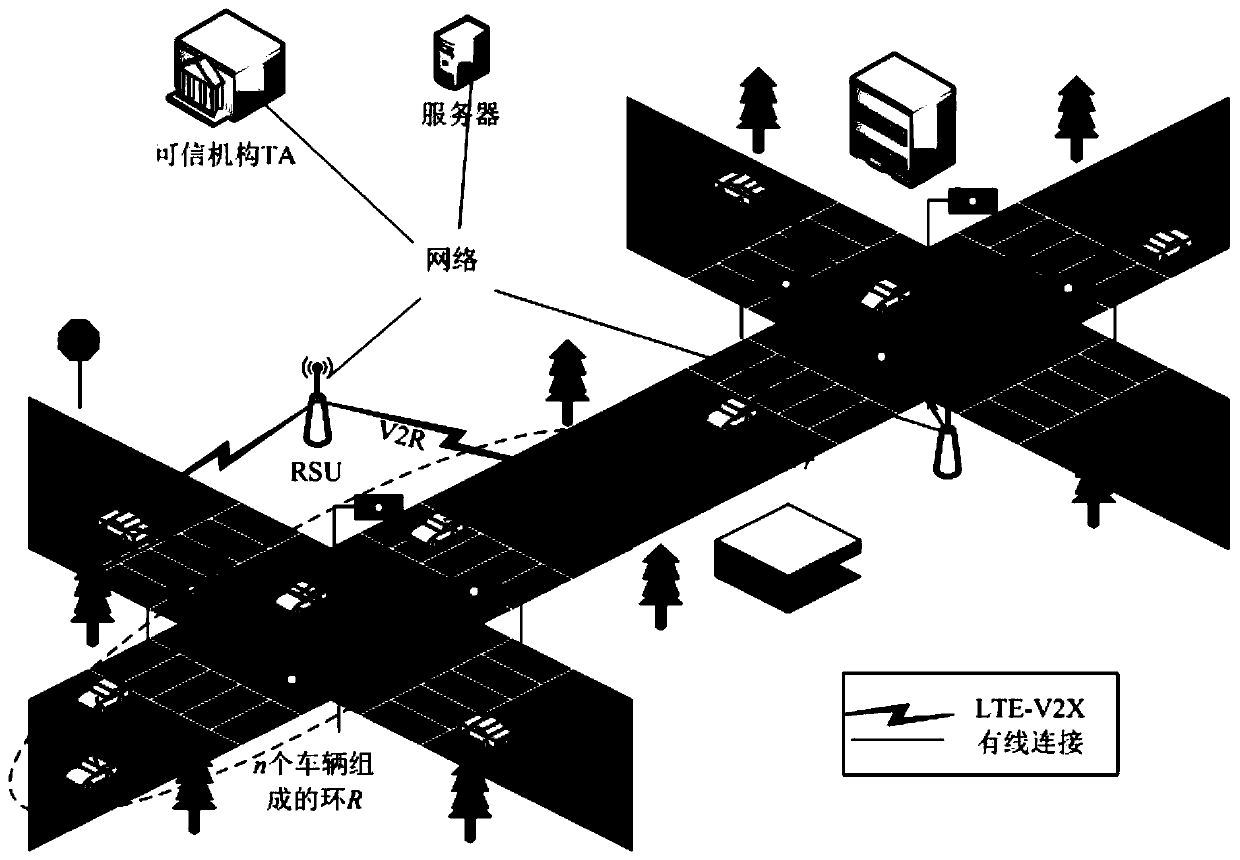
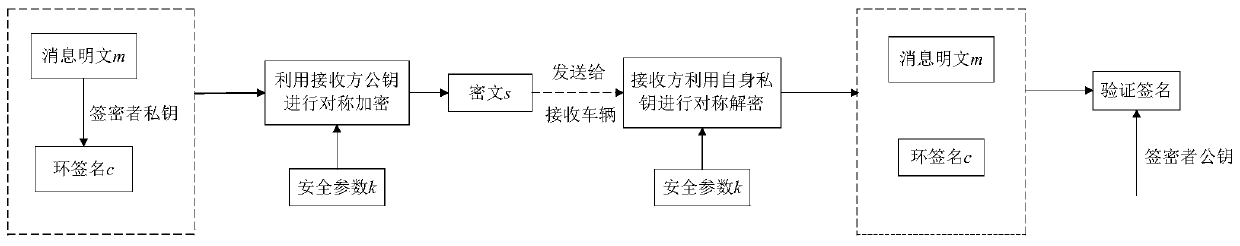
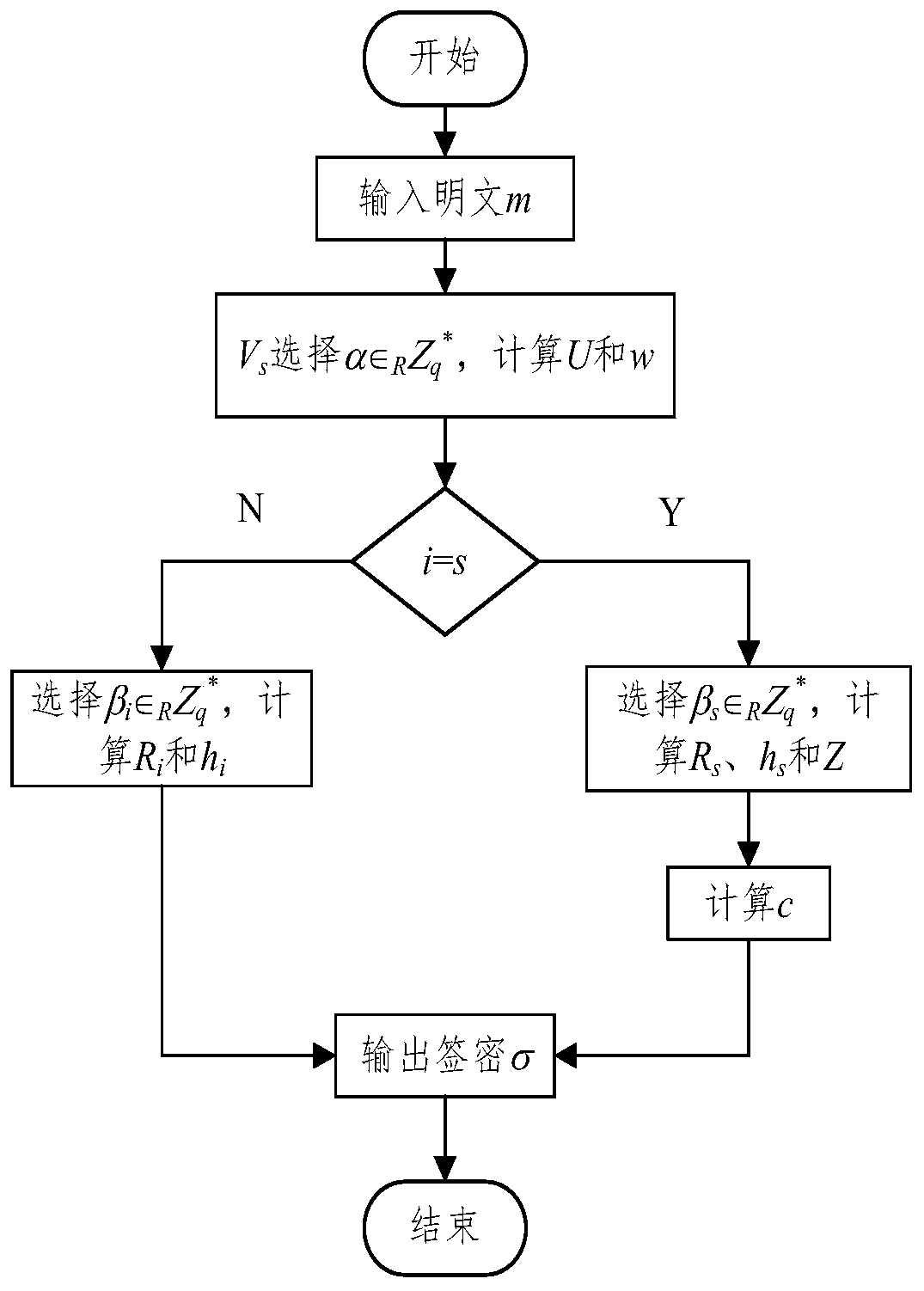
Privacy protection method based on certificateless ring signcryption in vehicle-mounted ad hoc network
ActiveCN110166228AConfidentialReduce computational overheadKey distribution for secure communicationParticular environment based servicesHash functionIn vehicle
The invention relates to a privacy protection method based on certificateless ring signcryption in a vehicle-mounted ad hoc network. After the signcryption vehicle encrypts the message by using the private key of the signcryption vehicle, the ciphertext is secondarily encrypted by using the public key of the out-of-loop receiving vehicle, the out-of-loop receiving vehicle correspondingly decryptsthe ciphertext by using the private key of the signcryption vehicle after receiving the ciphertext, and the validity of the ciphertext is verified by using the public key of the signcryption vehicle,so that the source and the integrity of the communication message can be authenticated. The method has the beneficial effects that when the vehicle has an illegal behavior, the traffic management center tracks the real identity of the vehicle through the unidirectionality of the hash function, and the requirements of anonymity and traceability are met.
Owner:NANTONG UNIVERSITY
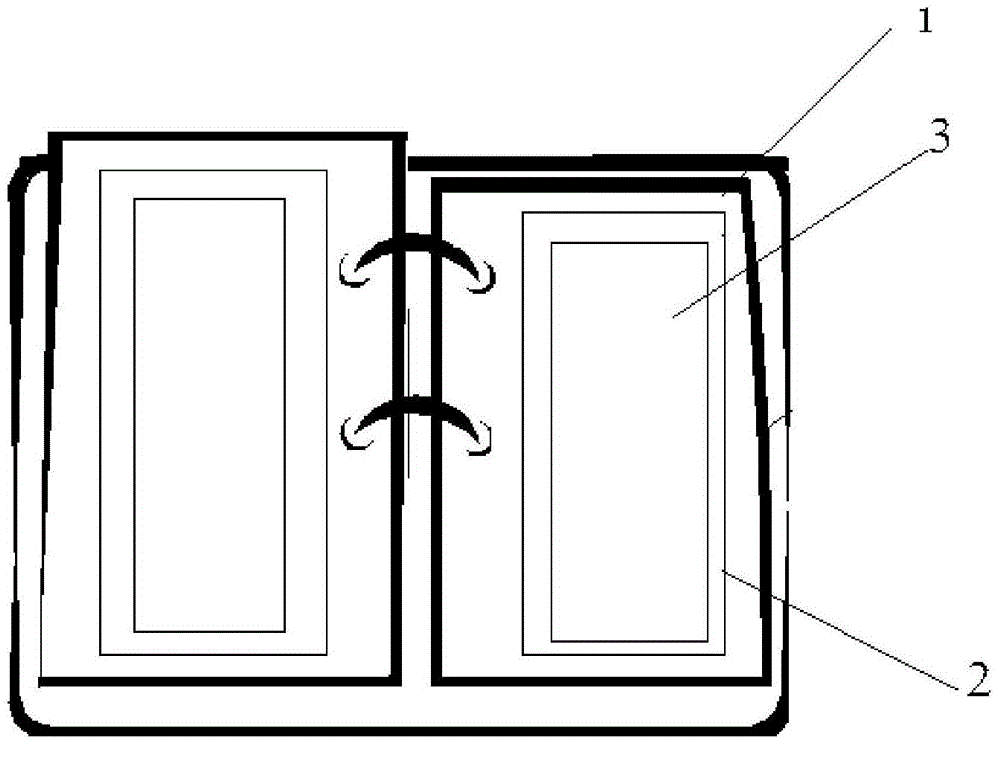
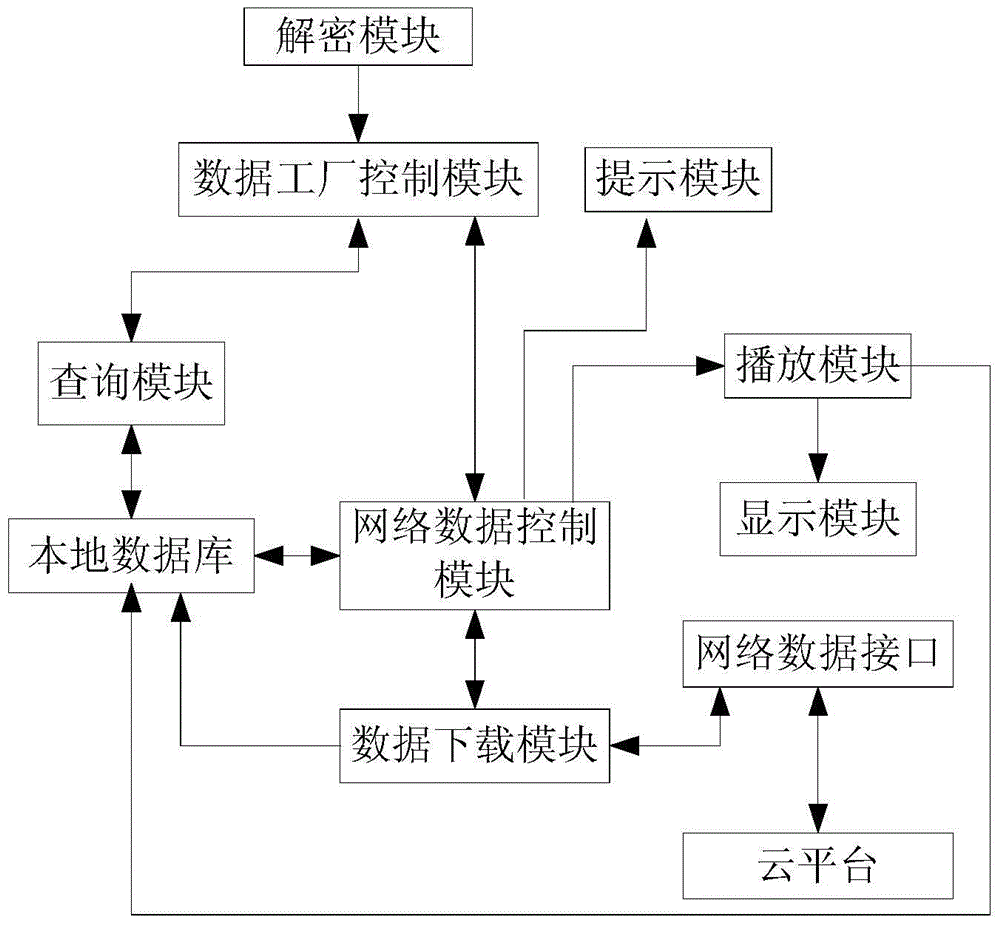
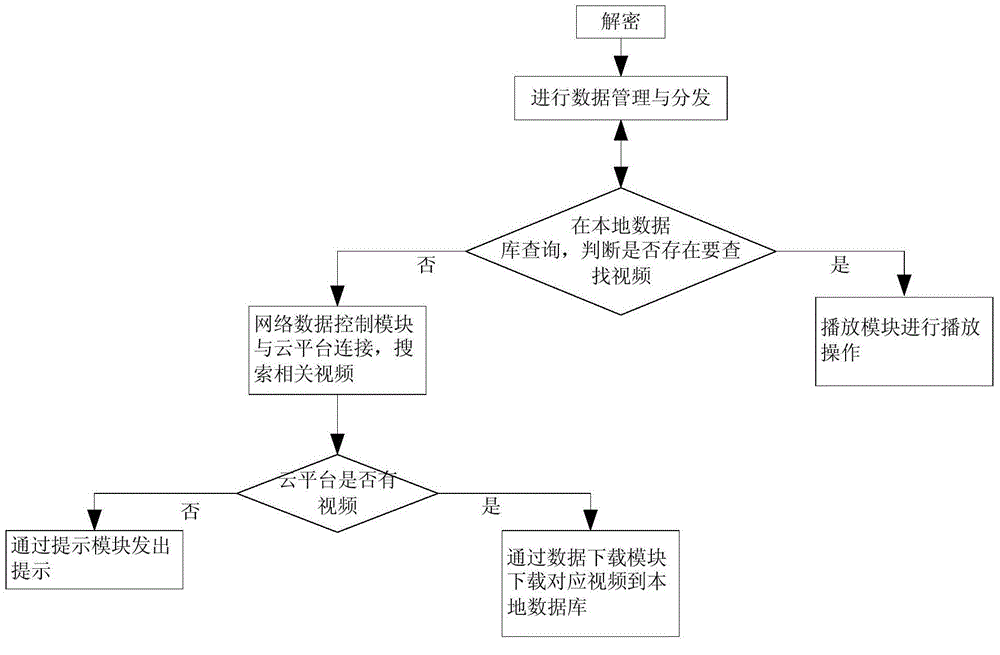
AR book and index augmented reality system and index augmented reality method based on same
ActiveCN104992205AImprove recognition rateQuick responseTransmissionRecord carriers used with machinesGraphicsComputer terminal
The invention relates to an AR book and an index augmented reality system and an index augmented reality method based on the same. The system comprises an AR book, an augmented reality stylus, a terminal, and a display module. The augmented reality stylus is used to read the AR book, parse the OID code of a coding rule carried by an object to obtain feature information, and transmit the feature information to the terminal. The terminal includes a decryption module, a data factory control module, a query module, a playing module, a network data control module, a data downloading module, a network data interface, and a cloud platform. According to the invention, the OID code is adopted, and each OID coded graph is formed by arranging many subtle points which are difficult to see with human eyes in accordance with specific rules and corresponds to a specific set of values. The biggest difference between other optical identification codes and a miniaturized bottom code is that the miniaturized bottom code has the characteristics of secrecy and low visual interference and can be hidden under the color pattern of a printed matter. Therefore, high recognition rate and a fast response mechanism are ensured.
Owner:XIAN EDUCATION & CULTURE DIGITAL CO LTD
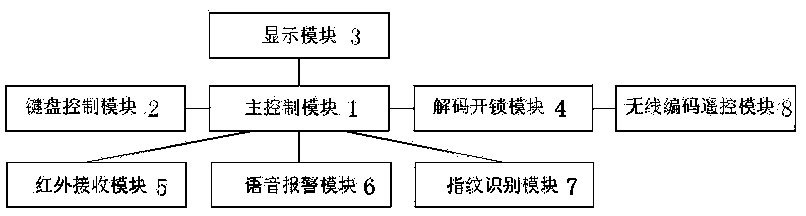
Theft-proof wireless infrared remote control electronic coded lock
InactiveCN104464038ATimely modificationSimple structureIndividual entry/exit registersConfidentialityRemote control
The invention discloses a theft-proof wireless infrared remote control electronic coded lock, relating to the technical field of electronic coded locks. A main control module (1) is respectively connected with a keyboard control module (2), a display module (3), a decoding unlocking module (4), an infrared receiving module (5), a voice alarm module (6) and a fingerprint identification module (7), and the decoding unlocking module (4) is connected with a wireless coding remote control module (8). The electronic coded lock is simple in structure and convenient to use and has double prompts of fingerprint identification and keys; under the condition that password is divulged, the password can be timely modified, or fingerprint identification is used, so the electronic coded lock has certain confidentiality; and the electronic coded lock has high flexibility, is suitable for houses, hotels, private garages and the like and has a relatively high use value.
Owner:ANHUI COSWIT INFORMATION TECH
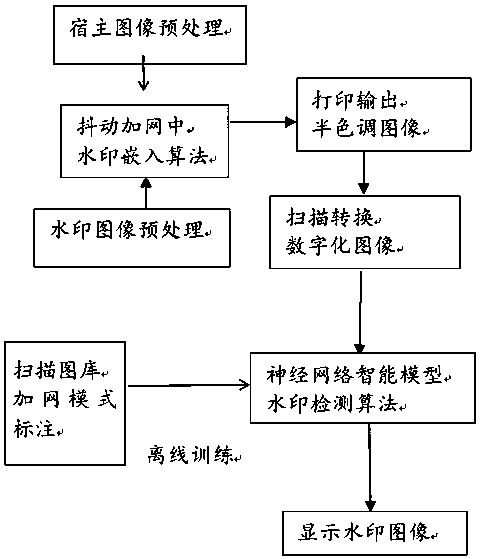
An anti-counterfeit halftone intelligent digital watermark making method of paper medium output
ActiveCN109102451AHiddenPrevent illegal copyingImage data processing detailsImage perceptionNetwork model
The invention discloses an anti-counterfeit halftone intelligent digital watermark making method of paper medium output. The specific steps are as follows: the host image is binarized, at the same time, the embedded watermark image is binarized, forming a binary digit string, and as the embeddable watermark coding information, a series of two-dimensional random number pairs are generated by usingthe random number seed as the key. The watermark coding information formed in S1 is embedded into the selected embedding position as the embedding position of the embeddable watermark coding information, and the host image embedding the watermark coding information is optimized by using the visual iterative algorithm. The trained neural network model is used to extract the watermark image. The invention can produce printing watermark with anti-counterfeiting function, has wide application prospect in copyright identification, anti-counterfeiting packaging and intelligent packaging, has high technical content, has large printing watermark embedding quantity, does not obviously affect image perception quality, and has hiding property and does not affect consumers to use printed matter.
Owner:QILU UNIV OF TECH
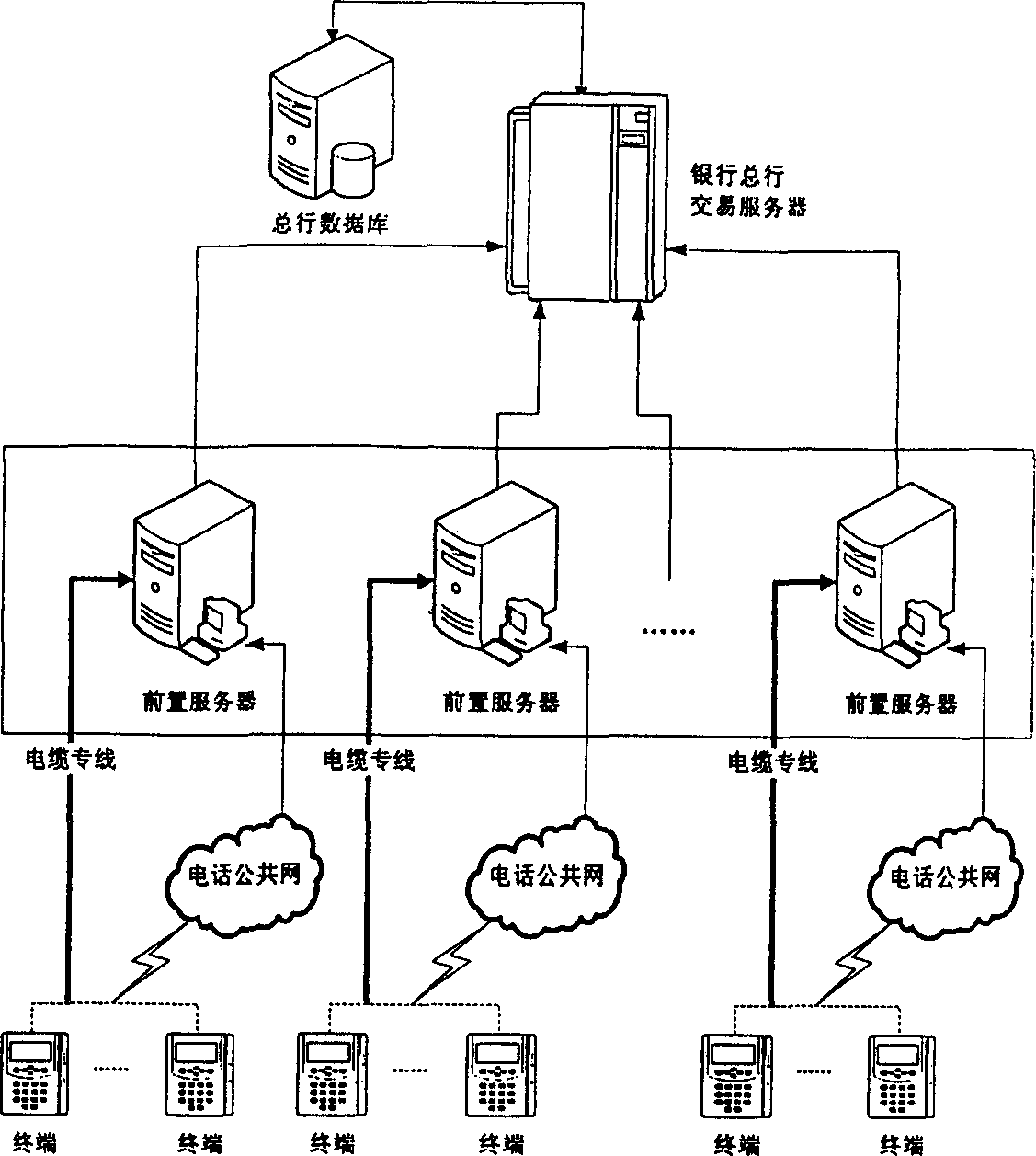
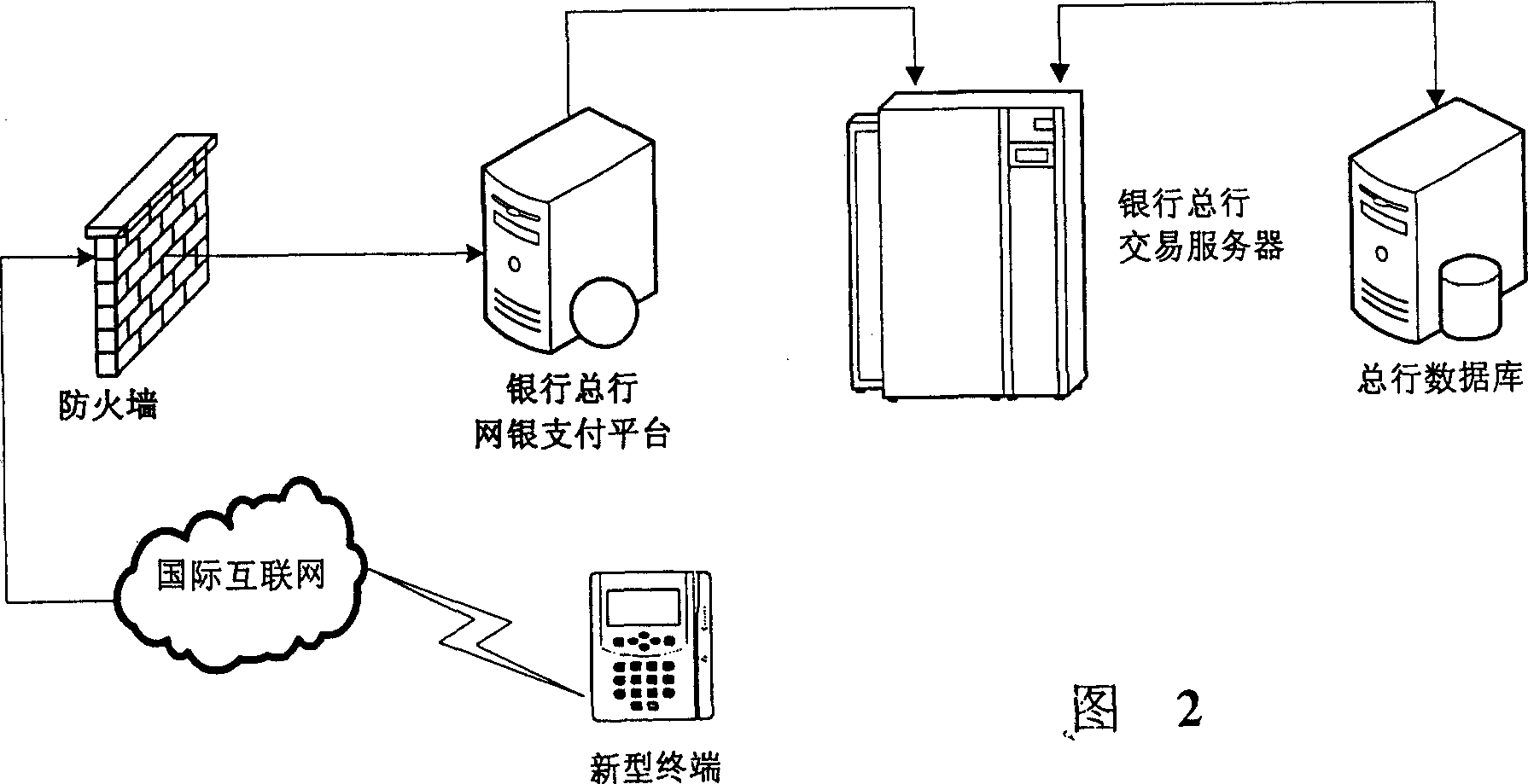
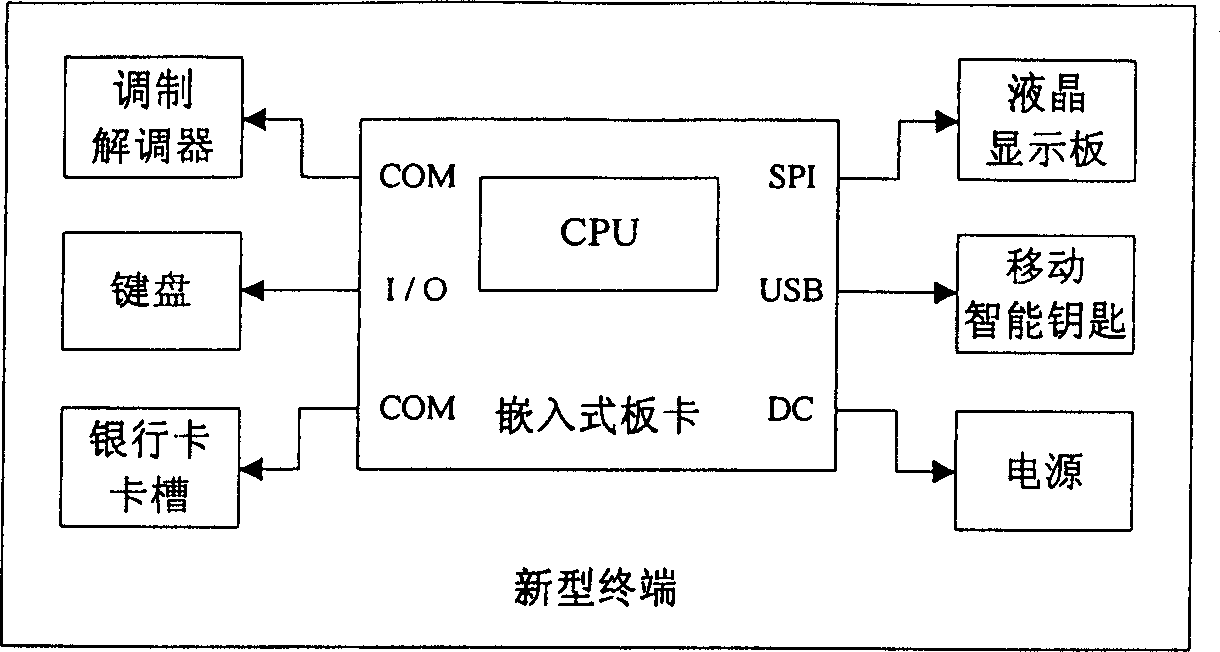
Bank net business processing method based on traditional terminal transaction form
InactiveCN1851740AReduce environmental problemsLow input costFinanceLiquid-crystal displayModem device
Said method designs the traditional terminal as new type terminal capable of connected with internet, setting network bank server in bank headquarter, after said new type terminal connected to internet, capable of execution of tradition bank card deal and network bank service adjoined deal method, Said new type terminal configured with CPU chip and embedded type board card, mobile intelligent unlocking key, liquid crystal display, banker's card slot, keyboard and modem; wherein modem for accessing internet or by ADSL dialing, embedded type board card controlling scheduling peripheral and executing scheduled software, keyboard card slot and liquid crystal display receiving input output result.
Owner:SHANGHAI HUASHEN INTELLIGENT IC CARD APPL SYST
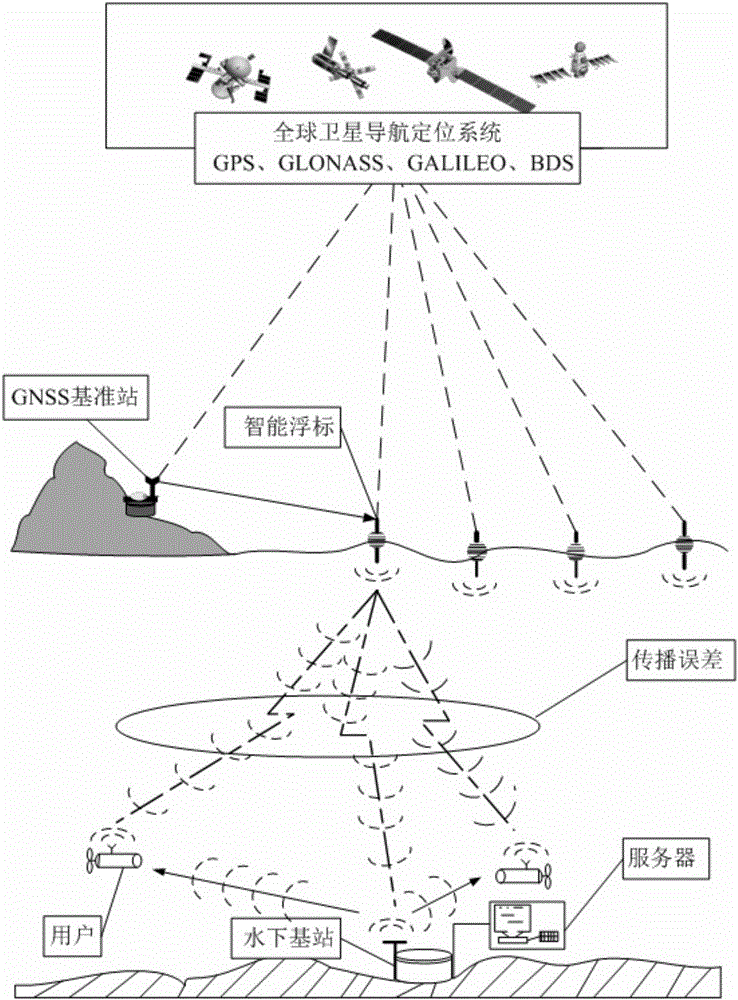
Underwater enhanced positioning method based on acoustic measurement error correlation
The invention belongs to the field of underwater navigation positioning, and specifically relates to an underwater enhanced positioning method based on acoustic measurement error correlation. The underwater enhanced positioning method includes following steps. An underwater navigation transceiver is used to send an acoustic positioning request signal to a smart buoy positioning hydrophone and an underwater reference station through a broadcasting means. Each smart buoy in a referential network, after obtaining a positioning request of an underwater user, conducts overwater difference positioning by simultaneously receiving GNSS satellite signals and the difference correction information of a difference base station, to obtain accurate position coordinate and buoy synchronous time. A data processing module integrated in each smart buoy conducts acoustic encoding and modulating for the position of the data processing module and sending time. The underwater base station receives buoy acoustic positioning signals synchronous with an underwater user, and an acoustical signal spatial correlation error item extracted by the underwater base station serves as acoustical signal propagation difference information. The precision of acoustic measurement signals is improved, advantages in security is ensured, and underwater positioning precision is genuinely improved.
Owner:HARBIN ENG UNIV
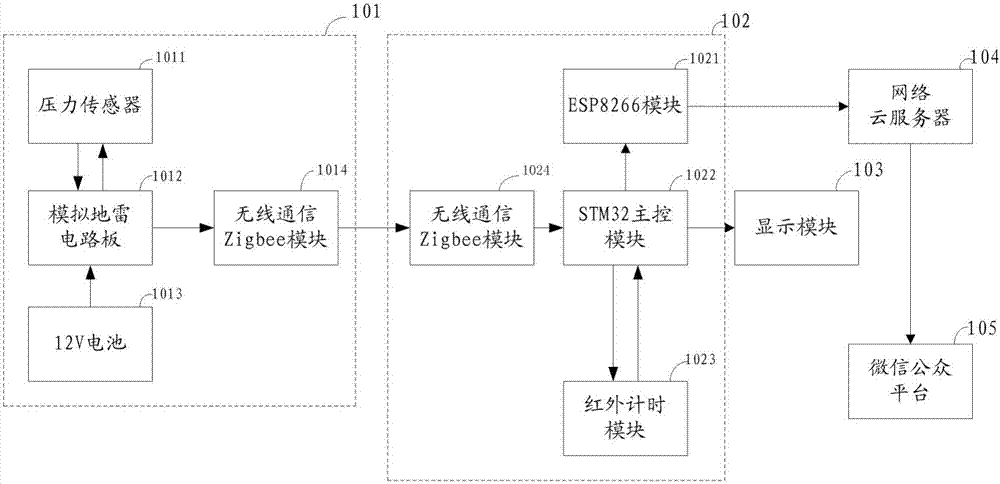
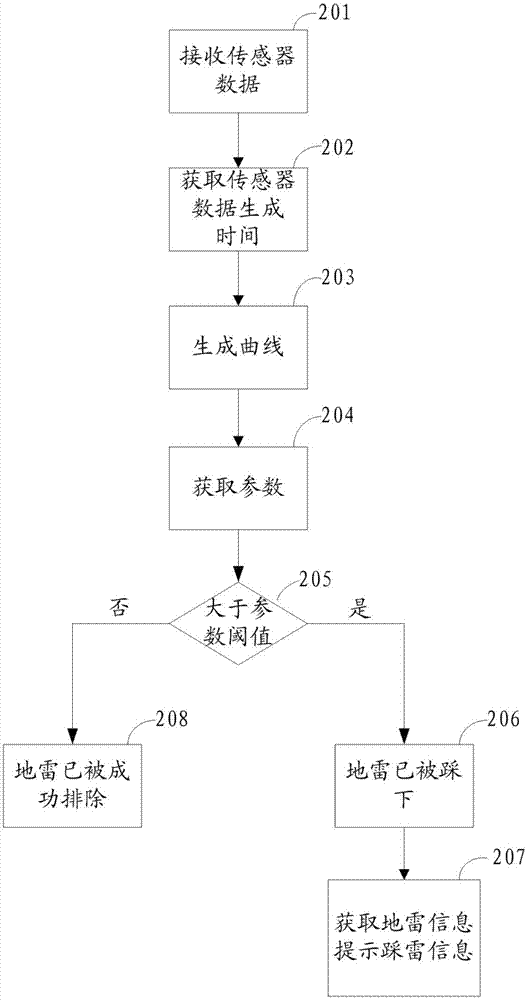
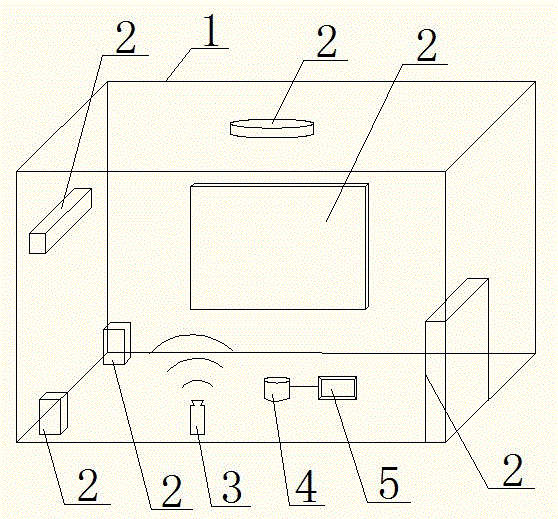
An army simulated mine clearance training apparatus and method
ActiveCN107016895AReal-time monitoring of demining trainingIntuitively and clearly reflect the evaluation and training effectCosmonautic condition simulationsSimulatorsSimulationComputer module
The invention discloses an army simulated mine clearance training apparatus and method. The apparatus comprises a simulated landmine module, a main control module and a display module. The simulated landmine module is connected with the main control module by wireless communication, and the main control module is connected to the display module in a wired mode. The apparatus can monitor mine clearance or mine stepping conditions in real time when an army is trained so as to grasp the training conditions of soldiers.
Owner:XIANGTAN UNIV
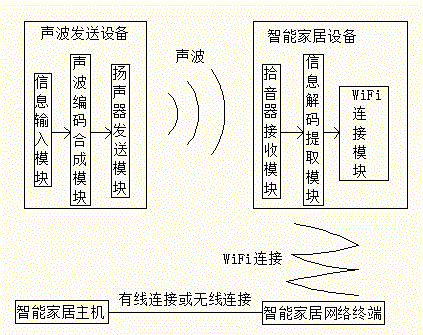
Intelligent home system and authentication connection method on the basis of sound wave authentication connection
InactiveCN105591755AGuaranteed confidentialityEnsure the confidentiality of the sound wave transmission processUser identity/authority verificationConnection managementNetwork terminationAcoustic wave
The invention belongs to the technical field of wireless communication and especially relates to an intelligent home system and an authentication connection method on the basis of sound wave authentication connection. The intelligent home system on the basis of sound wave authentication connection comprises an intelligent home dwelling house which is provided with multiple intelligent home devices. It is characterized in that the intelligent home dwelling house is provided with a sound wave sending device which is used for sending sound wave to the intelligent home devices; the intelligent home dwelling house is provided with an intelligent home network terminal which is used for providing access for the intelligent home devices. The beneficial effects of the invention are: all the intelligent home devices can be simultaneously authenticated and connected to the intelligent home network terminal; devices outside the cannot acquire sound wave signals so that the sound wave transmission process is confidential and error-connection of devices outside the dwelling house will not happen; the system and method have low cost, easy operation, high efficiency, and safe and reliable authentication means.
Owner:JINAN JOVISION TECH CO LTD
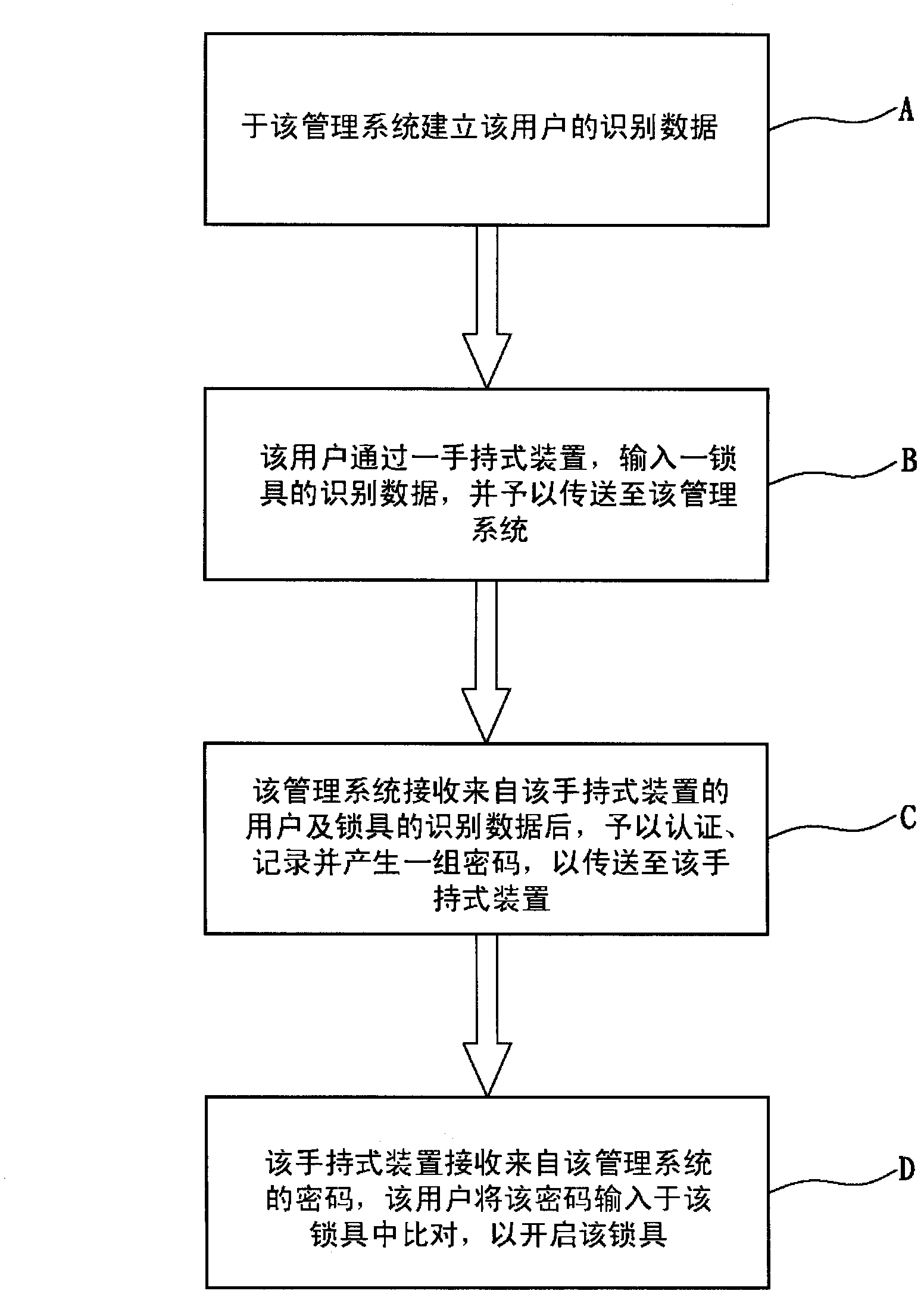
Lock management method capable of realizing long-distance control
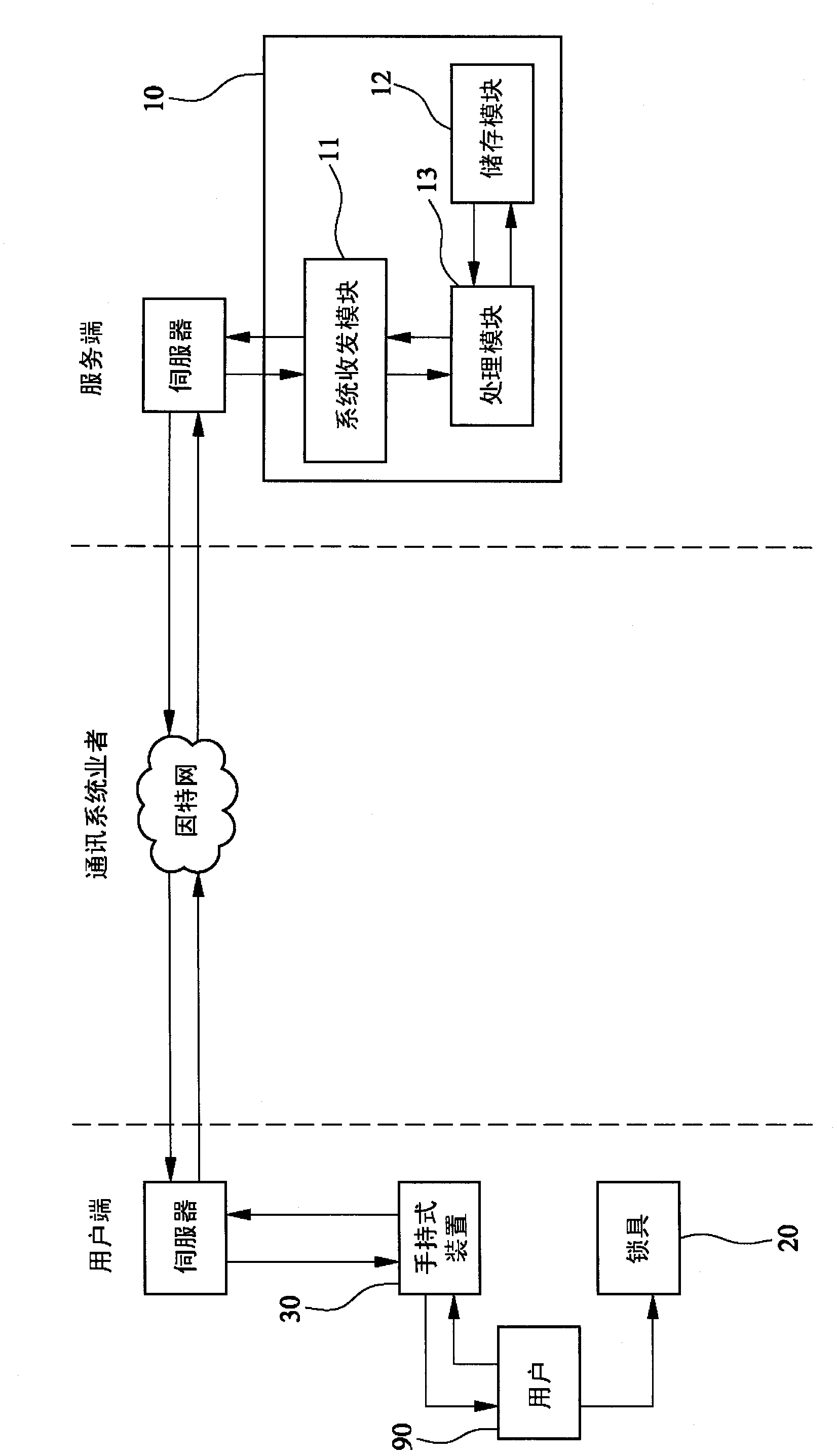
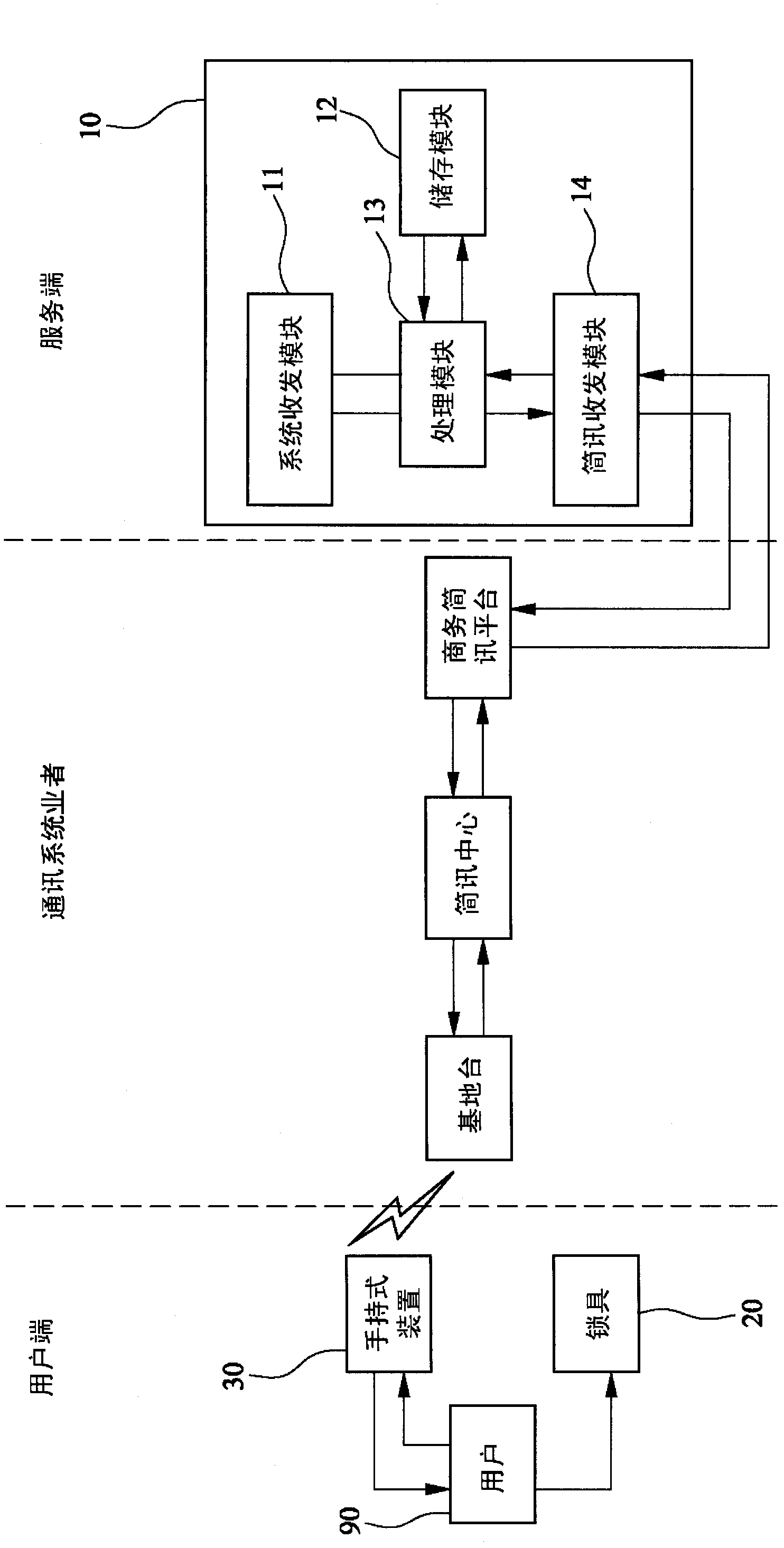
InactiveCN102691444ASolve lost keysSolve forgotten passwordElectric permutation locksComputer hardwareApproaches of management
The invention provides a lock management method capable of realizing long-distance control, which controls a lock in a long-distance manner through a management system, and assists trusteeship behaviors of a user. The lock management method comprises the following steps of: (A) establishing identification data of the user for the management system; (B) inputting the identification data of the lock by the user through a handheld device, and transmitting the identification data to the management system; (C) receiving the identification data of the user and the lock from the handheld device, authenticating, recording and generating a group of codes by the management system, and transmitting the codes to the handheld device by the management system; and (D) receiving the codes from the management system by the handheld device, and inputting the codes in the lock by the user for comparison, so as to unlock the lock. Therefore, the lock management method has the effects of high security, high confidentiality and convenience in use. Furthermore, a using state of the lock can be inspected by recording of the management system, so as to effectively manage and maintain.
Owner:全亿数位科技股份有限公司
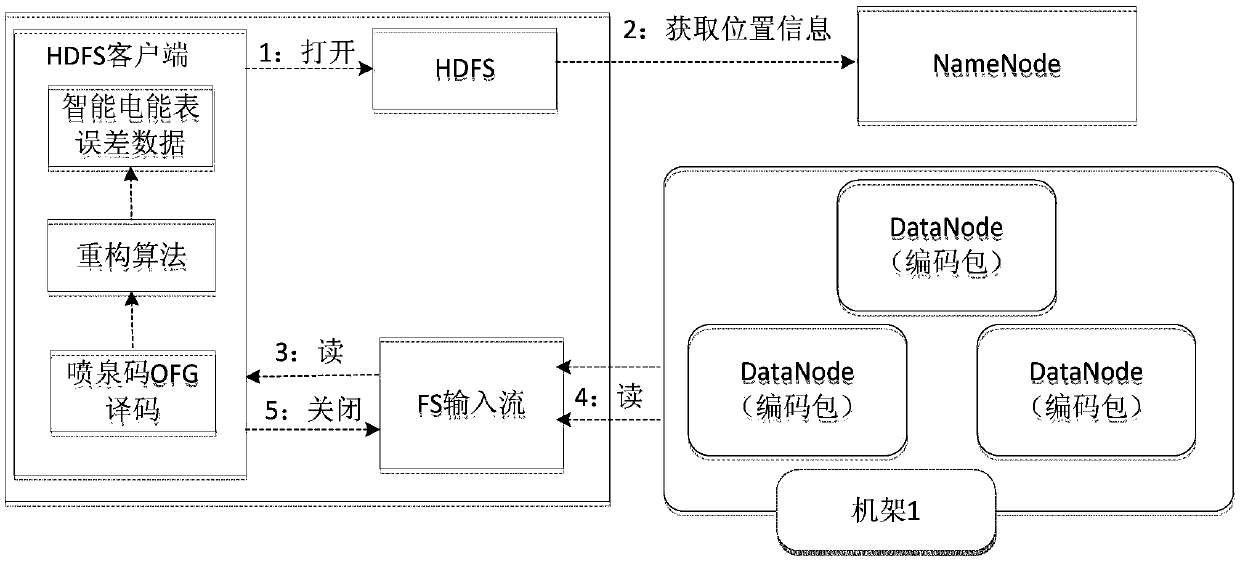
Device and method for safely storing error big data of smart electricity meter based on fountain code
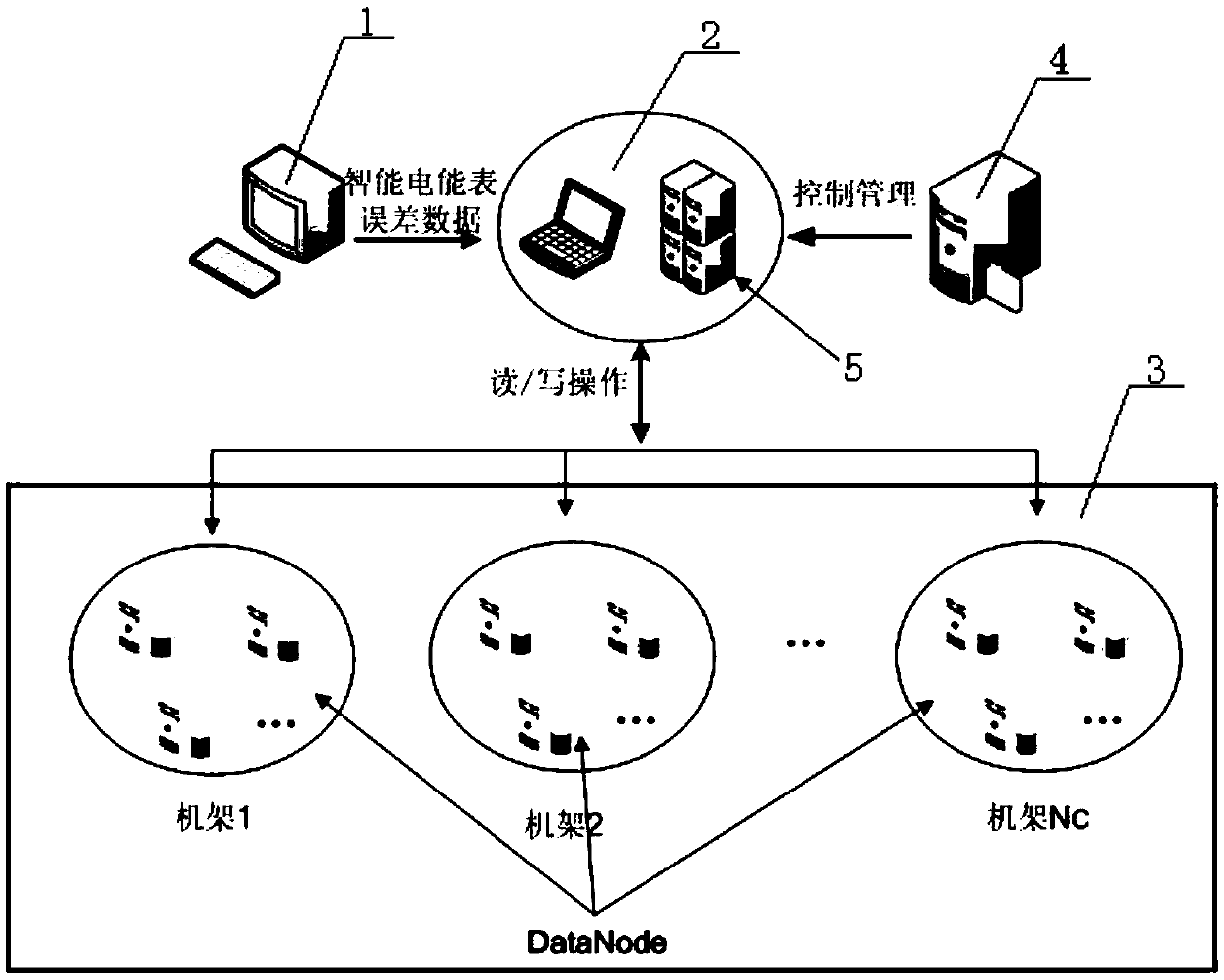
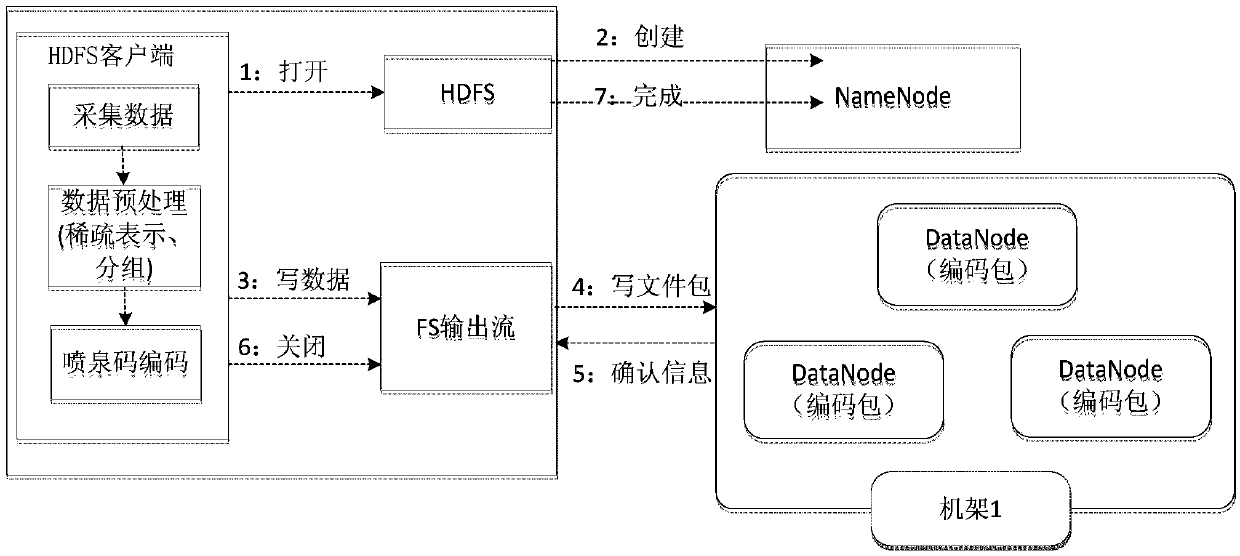
ActiveCN105516355AEnsure Privacy ProtectionImprove storage efficiencyError preventionComputer hardwareFountain code
The invention discloses a device and a method for safely storing error big data of a smart electricity meter based on a fountain code. The device comprises a smart electricity meter self-service error calibration device, an HDFS (Hadoop Distributed File System) client side and a Hadoop big data storage platform, wherein the smart electricity meter self-service error calibration device, the HDFS client side and the Hadoop big data storage platform are sequentially connected; the smart electricity meter self-service error calibration device is used for collecting data of a measured smart electricity meter; the HDFS client side is used for preprocessing the collected data of the smart electricity meter and coding and decoding the preprocessed data; the Hadoop big data storage platform is used for carrying out distributed storage on the error big data of the smart electricity meter. The device and the method disclosed by the invention have the technical effects that the storage efficiency is increased; the utilization rate of storage space is increased; the problem of stored data loss caused by DataNode failure in the prior art is solved; privacy protection of the data of a user is ensured.
Owner:STATE GRID CORP OF CHINA +1
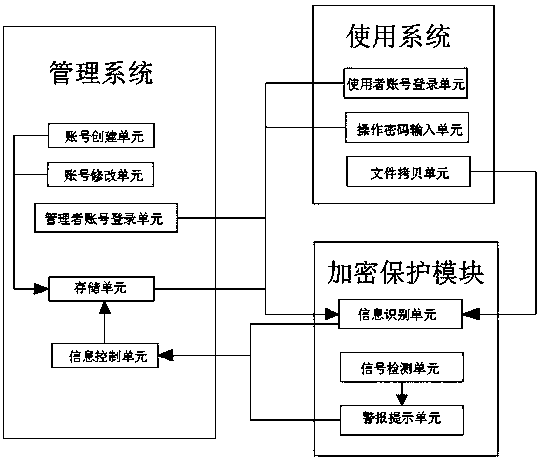
Lightweight image file disk encryption system and method
InactiveCN108985075APrevent theftSafety protectionDigital data protectionInternal/peripheral component protectionDisk encryptionStorage cell
The invention discloses a lightweight image file disk encryption system and method. The system comprises a management system, a use system and an encryption protection module. The management system comprises an account creation unit, an account modification unit, an administrator account login unit, a storage unit, and an information control unit. The administrator account login unit includes an administrator login account and an administrator login password. The use system includes a user account login unit, an operation password input unit and a file copy unit. The encryption protection module includes an information identification unit, a signal detection unit and an alarm prompting unit. The storage unit is connected to the account creation unit and the account modification unit. The output ends of the storage unit, the user account login unit, the file copy unit and the operation password input unit are connected to an input end of the information identification unit. The disk encryption system provided by the invention carries out triple protection on a mirror image file, and the encryption effect is safe and effective.
Owner:成都小娱网络科技有限公司
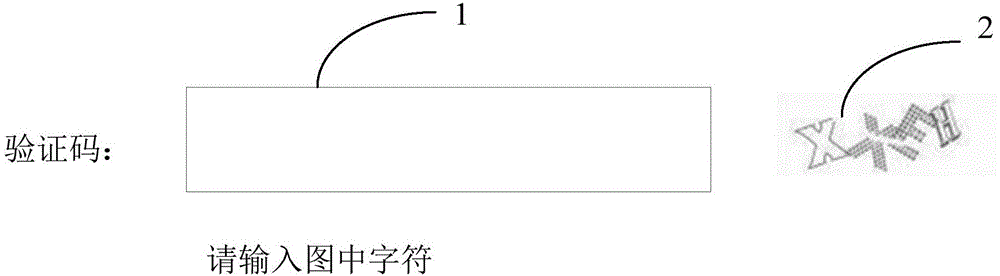
Identity verification method and device
ActiveCN105100005AIncrease the difficultyConfidentialUser identity/authority verificationComputer terminalComputer science
The invention proposes an identity verification method and device which are high in safety. The method comprises the steps that a server receives a verification code pull request transmitted by a user terminal, wherein the verification code pull request contains the account information of the user terminal; a preset theme corresponding to the account information is obtained according to the account information; a plurality of to-be-selected pictures are obtained from an image database; each to-be-selected picture is provided with a corresponding theme; the theme of at least one of the plurality of obtained to-be-selected pictures is the same as the preset theme; the plurality of obtained to-be-selected pictures are transmitted to the user terminal for display; the information of a selected picture returned by the user terminal is received, and the identity of a user is verified according to the theme of the selected picture and the preset theme, wherein the selected picture is selected by the user from the plurality of to-be-selected pictures.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Wireless emission control system
ActiveCN110322675ASimple designImprove reliabilityTransmission systemsTransmission protocolSystems design
A wireless emission control system comprises an aircraft antenna, an aircraft wireless controller, a ground antenna, a ground remote console and a computer. By a special communication transmission protocol, on one hand, the system design is simplified, and on the other hand, the reliability of the communication protocol is ensured. Moreover, a corresponding execution strategy is made for differentinstructions when the system executes a control instruction, the instruction execution efficiency is ensured, and the working safety and reliability of the system is also guaranteed. The wireless emission control system belongs to a test emission control system.
Owner:BEIJING LINJIN SPACE AIRCRAFT SYST ENG INST +1
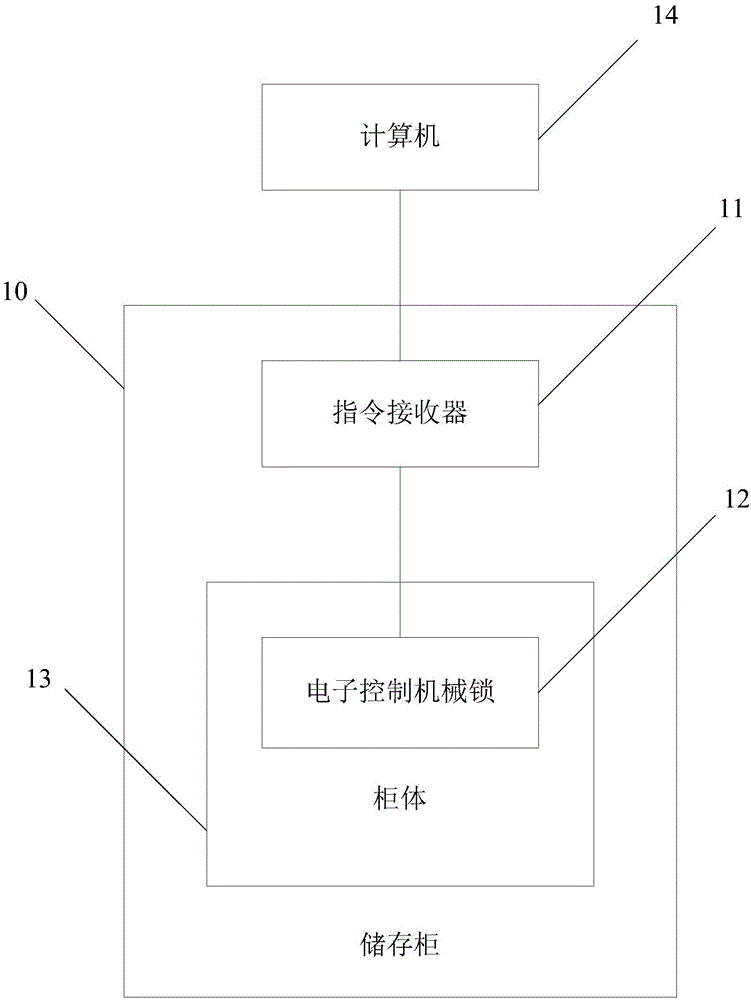
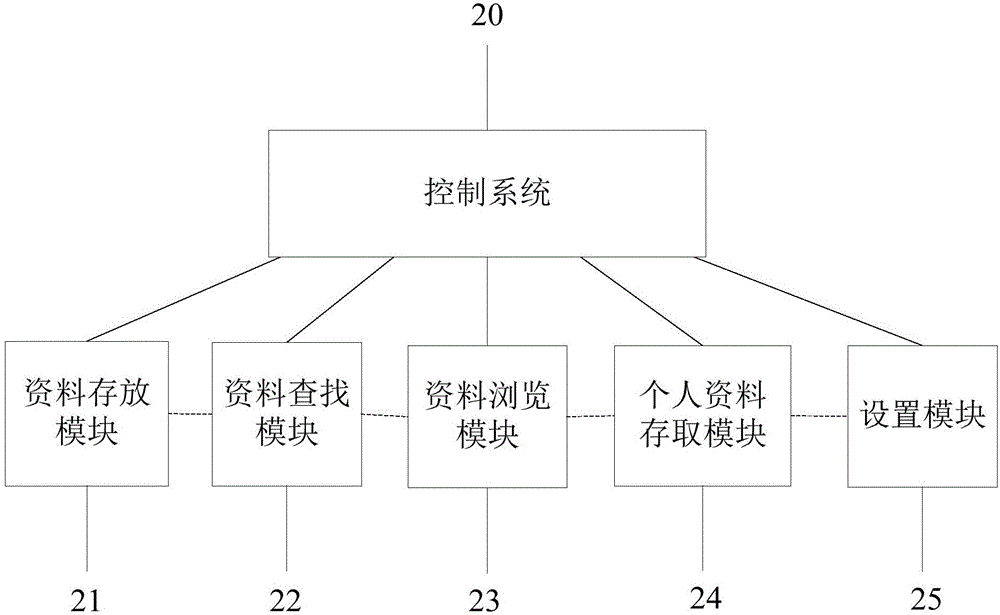
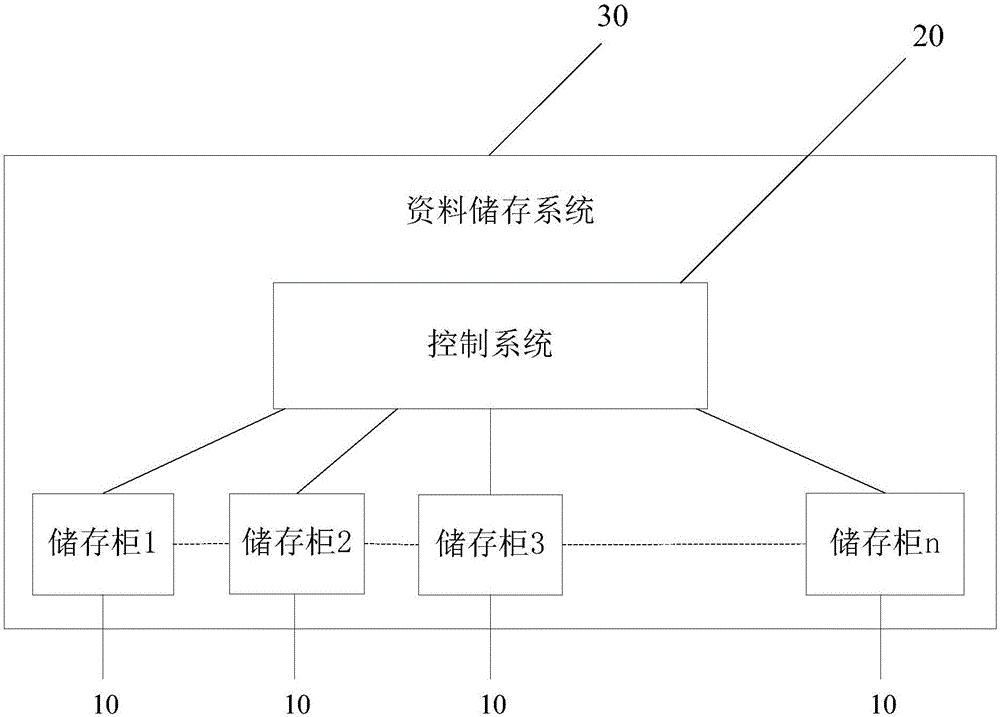
Storage cabinet, control system and data storage system
InactiveCN106473472AImprove ease of useRealize automatic openingBook cabinetsSpecial data processing applicationsControl systemConfidentiality
The invention provides a storage cabinet, a control system an d a data storage system. The data storage system comprises the control system and at least one storage cabinet body; each storage cabinet body comprises a command receiver, an electronic control mechanical lock and multiple cabinet bodies, the electronic control mechanical lock is installed in the cabinet bodies, and one end of the command receiver is used for receiving switch control instructions from a computer and controlling the electronic control mechanical lock according to the instructions; the control system of the storage cabinet bodies comprises a data storage module, a data searching module, a data browsing module, a personal data access module and a setting module. By the arrangement, information index sharing is realized through the control system of the storage cabinet bodies, tedious process in data searching among apartments is avoided, problems about storage disorder and borrowed record disorder can be solved, the storage cabinet bodies have confidentiality, thievery prevention and security functions, information record of the control system is detailed, and convenience and rapidness in searching and storing process of various archive information can be achieved.
Owner:STATE GRID SHANDONG ELECTRIC POWER +1
Fluid regulation type internal insulation structure and its prefabricated method
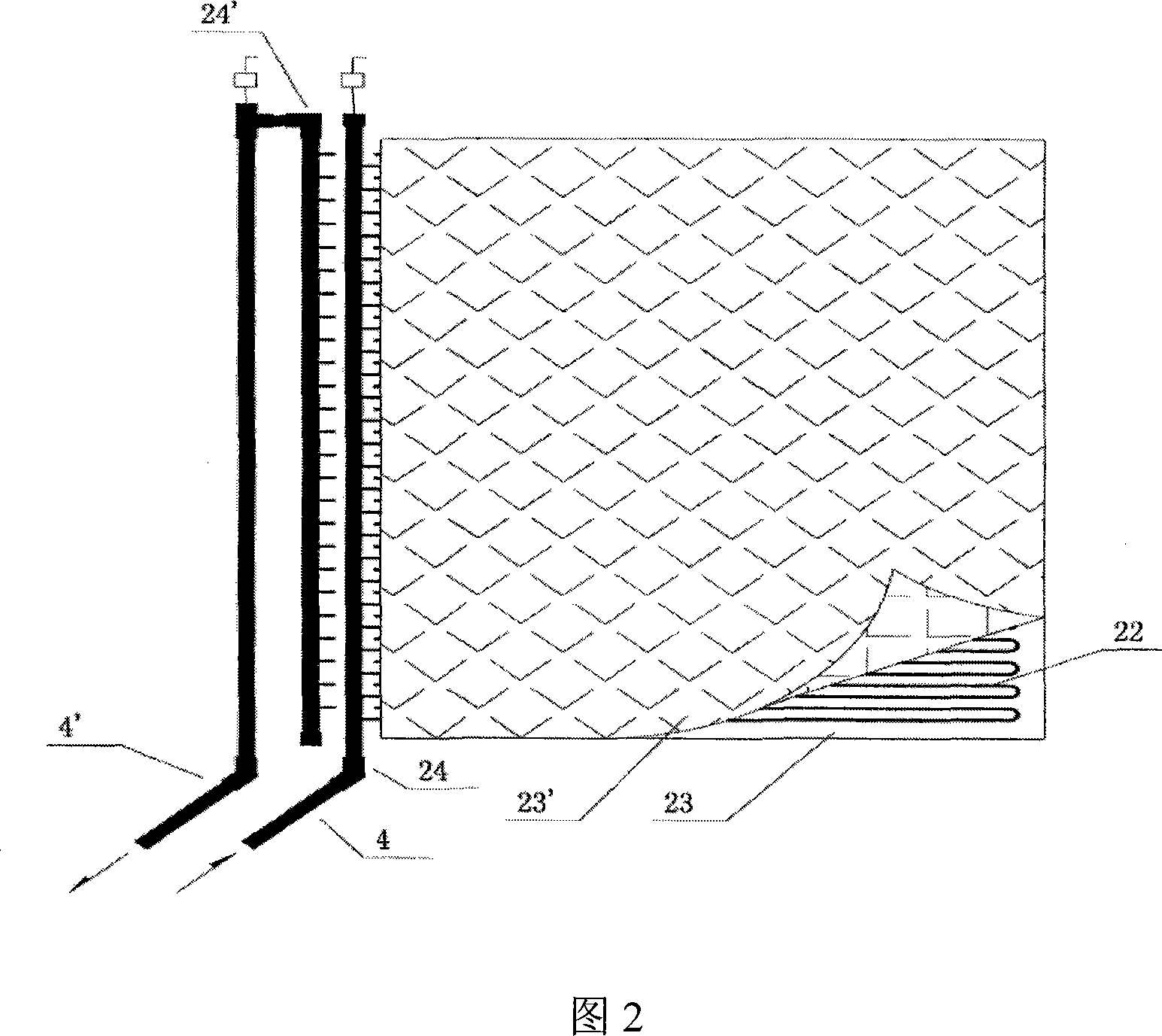
InactiveCN101054820ALight in massSimple structureWallsLighting and heating apparatusInsulation layerCoupling
The invention disclose is wall inner heat preservation structure for building, especially a fluid adjusting type inner heat preservation structure with multifunction for external heat preservation and inner thermoregulation and the making method, which includes a heat emission layer, a diversity water type plastic tubing net and an insulation layer, wherein, the diversity water type plastic tubing net comprises two main tubes and a plurality of capillaries vertical coupling to the two main tubes with two ports communicated with the external heating or refrigerating system, characterized in that, the heat dissipation layer is composed of a double-layer thermal fin, and a plurality of capillaries is clamped between the double-layer thermal fin; wherein the space between the plurality of capillaries and the thermal fin coating the two sides is compactly sticked without air obstruct. One side of the insulation layer is sticked with the outside surface of the thermal fin, and the other side is connected with the wall, which has light weight, thin thickness, even thermolysis, no noise, marked energy saving effect, and not only is suitable for the installation of the new building wall, but also for the heat preservation energy saving reconstruct of the old building, and easy to extend and actualize.
Owner:朱江卫
BRT automatic ticketing system
InactiveCN107798735AEffective combinationEasy to buy ticketsCo-operative working arrangementsMachines for printing and issuing ticketsBus rapid transitAutomatic testing
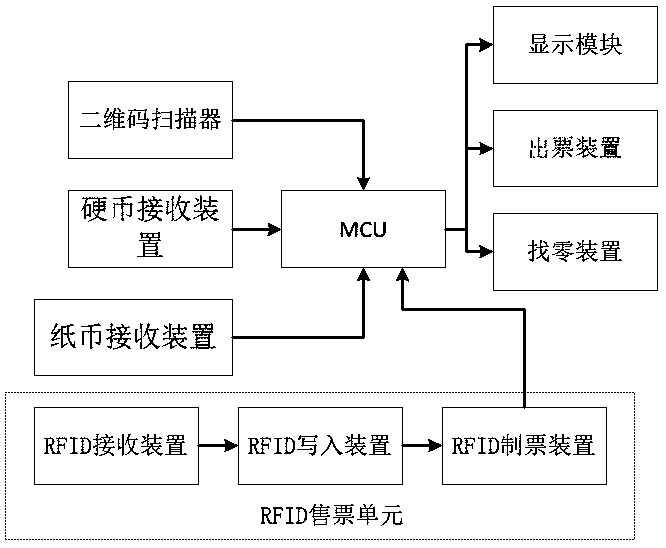
The present invention discloses a BRT (Bus Rapid Transit) automatic ticketing system. The automatic ticketing system is arranged in a ticket vending machine of a bus rapid transit station, and comprises an MCU, a signal input end of the MCU is connected with a two-dimensional scanner, a coin receiving device and a paper currency receiving device, and a change device and a ticket issuance device are connected with a signal output end of the MCU; the automatic ticketing system further comprises a RFID ticketing unit, the RFID ticketing unit comprises a RFID receiving device, a RFID writing device and a RFID ticket printing device which are connected in order, the ticket issuance device is connected with the RFID ticket printing device, the automatic ticketing system further comprises a display module, and the display module is connected with the MCU. The BRT automatic ticketing system can perform accurate control of a passenger flow of the whole bus system while improving the efficiencyof the automatic ticketing system.
Owner:四川久远新方向智能科技有限公司
Method and device for starting processor as well as device for providing IPL (Initial Program Loader)
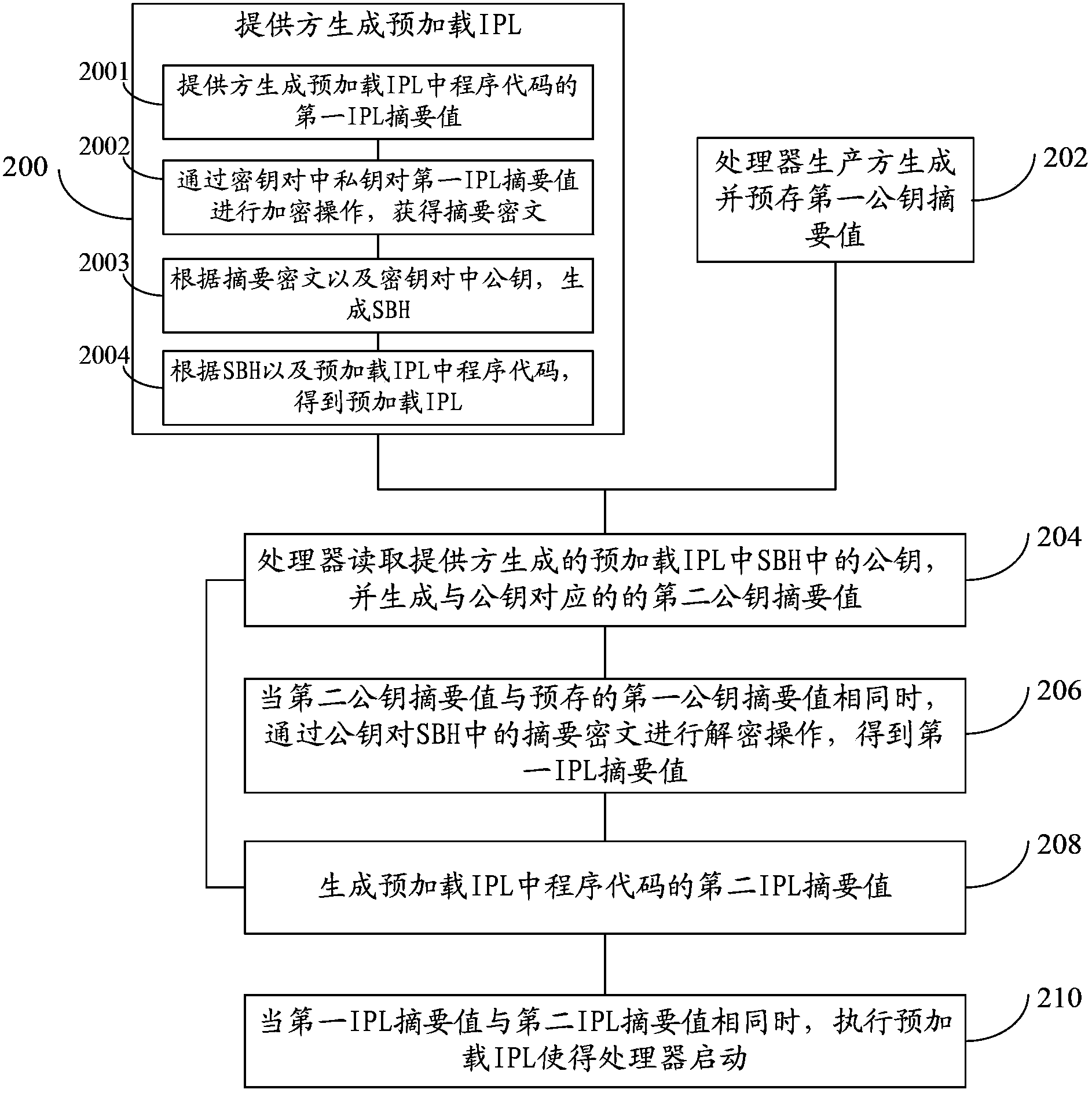
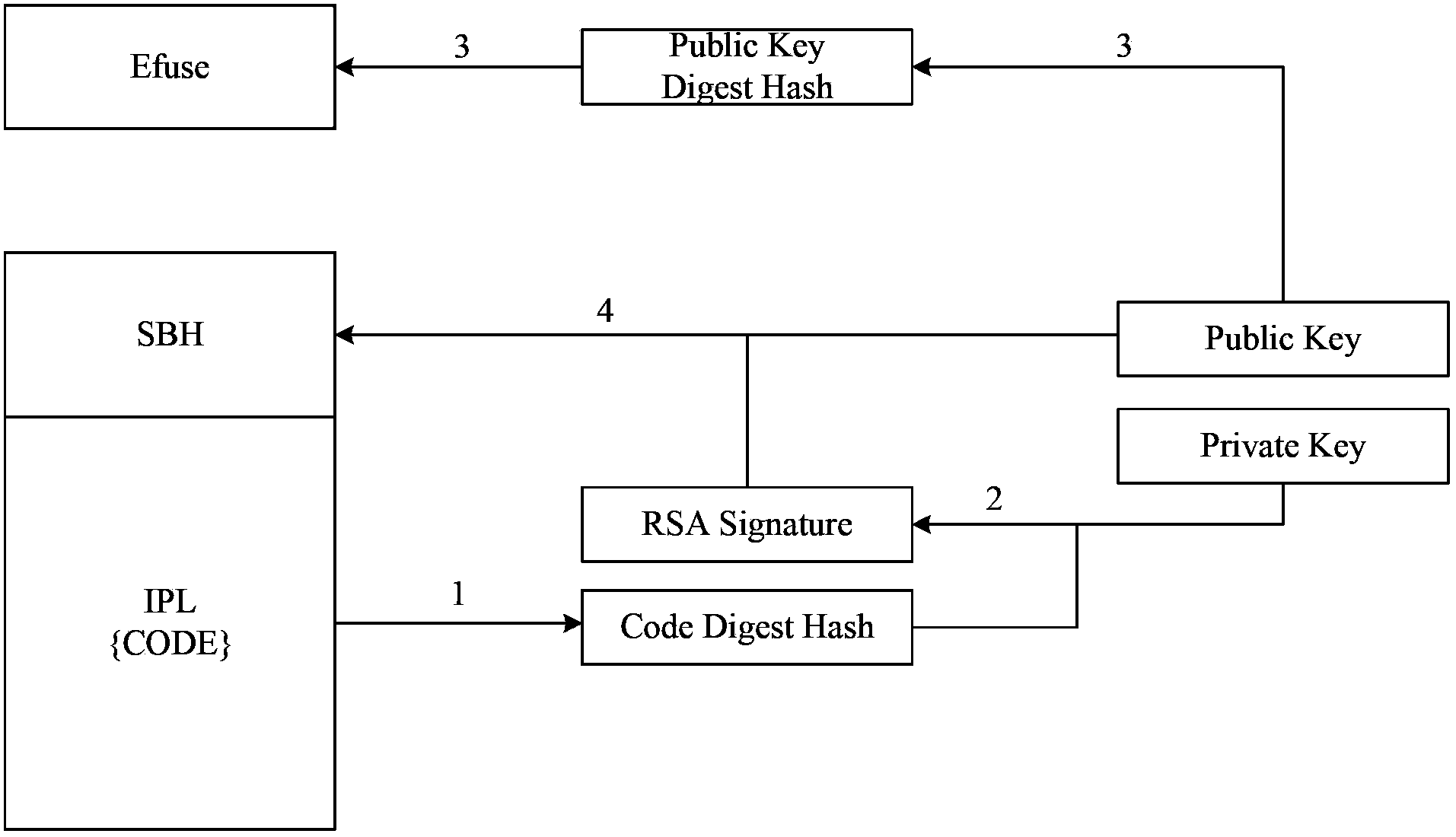
ActiveCN103365687AConfidentialImprove securityComputer security arrangementsProgram loading/initiatingSystem safetyComputer security
The embodiment of the invention discloses a method and device for starting a processor as well as a device for providing an IPL (Initial Program Loader), so as to solve the problem that loading and executing any IPL can have influence on the system safety when a processor starts. The method comprises the following steps: the processor reads a public key, generated by a provider, of an SBH (Security Boot Header) in the preloading IPL, and generates a second public key digest hash corresponding to the public key; when the second public key digest hash is identical with a first public key digest hash, the digest encrypted message in the SBH is decrypted through the public key to obtain a first IPL digest hash; a second IPL digest hash of program codes in the preloading IPL is generated; when the first IPL digest hash is identical with the second IPL digest hash, the preloading IPL is executed to start the processor. According to the embodiment of the invention, the two comparison processes, namely the comparison of the public key digest hashes and the comparison of the IPL digest hashes, are performed in the starting of the processor, so that the system safety is improved as the number of comparison processes is increased.
Owner:新奇点智能科技集团有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com